#and like man its just not a good fit for some people!! linux is NOT intuitive if youre not super knowledgeable abt computers
Text
i wish everyone who has ever said "just switch to linux" a very Shut The Fuck Up
#yeah!! linux is good for some things!! but not for everything!!! and certainly not for everyONE#this goes DOUBLE if uve said it specifically in response to someone asking for help with an issue theyre having#bc not only are you being a pretentious dick but youre also NOT EVEN ANSWERING THE QUESTION AT HAND#like oh yeah im having a computer issue at work let me just ask my multi billion dollar employer if i can pretty please use linux instead#im sure that will go over GREAT#yeah lemme fucking replace my gaming computer with one that runs linux. im sure ill still be able to play everything just fine#and like man its just not a good fit for some people!! linux is NOT intuitive if youre not super knowledgeable abt computers#& not everyone is OR WANTS TO BE. and thats FINE ACTUALLY#ALSO BEFORE ANYONE TRIES TO COME AT ME WITH SOME SHIT LIKE ''well just try it first'' I HAVE. I HAVE HAD A LINUX COMPUTER
9 notes
·
View notes
Text
My critical analysis on Mawaru Penguindrum. Unbelievable.
WARNING: CONTAINS SPOILER. Read at your own risk.
(January 7, 2018: This remains a Work in Progress.)
nice title and warning
Within 2 days (Yes), I watched another Madoka-level depressive anime. Good job. Why am I keep watching this kind of anime? What is pushing me to the cliff of depression? It's not like I'm that kind of person And, in fact, I am quite savage, online and offline, check my post history, but I just keep going to this kind of shit. So...Listen, you lowlifes, who will never amount to anything! Obtain the Penguin Drum! This is nonsense. I get what the author trying to say, but this is still nonsense.
First time writing an analysis. Probably amateur as hell.
Initiative
This Linux meme I saw on a trash website.
dailymotion
So I went to search for its raw sauce source, which leads to me watching this. I thought it was some good entertaining shit, but turns out it’s another Madoka-level calice.
The main theme, core idea, whatever.
Three parts.
Fate
First of all, let’s compare the statements that the characters made. The apple girl said:
I love the word "fate". Because, you know how they talk about "fated encounters"? A single encounter can completely change your life. Such special encounters are not just coincidences. They're definitely... fate. Of course, life is not all happy encounters. There are many painful, sad moments. But this is what I think: sad and painful things definitely happen for a reason. Nothing in this world is pointless.
And that was episode 2. In contrast, Shouma said:
I hate the word "fate." Birth, encounters, partings, success and failures, fortune and misfortunes in life. If our lives are already set in stone by fate, then why are we even born? There are those born to wealthy families, those born to beautiful mothers, and those born into the middle of war or poverty. If that's all caused by fate, then God is incredibly unfair and cruel. Because, ever since that day, none of us had a future and the only certain thing was that we wouldn't amount to anything...
And that was episode 1. The end proved them both right. Nice catch. But they’re too extreme. And animes are always featuring extreme situations so that they can be animes, right? That’s why I don’t take animes as lessons. They’re not something we will encounter.
What I believe is: You might love it, or hate it, but such concept of “fate” is a suggested course. It should not be taken as the truth set in stone (Shouma), or surprises that jump out randomly (Ringo), but rather a neutral advice. You can follow it, or you can break it, depending on the situation, which can bring positive and/or negative consequences, known as “taking risks”. Such “fate”, as a suggested course, is fitted to everyone individually. Let’s break this down.
Such concept of “fate” is a suggested course.
By “suggested” I didn’t mean it’s necessarily good. It is rather close to being balanced, which is what the world has been turning about: Positive and negative connect to each other, spread across the whole lifespan of “fate”.
...but rather a neutral advice.
Following such “fate” makes you what a balanced world (which is neutral, at least it should be) want you to be.
You can follow it, or you can break it, depending on the situation.
Two points. First of all, only you can change your fate, not a fucking diary, which succeeded in transferring fate after a high price was paid. Second of all, I said depending on the situation, which means that there are certain moments in your life that you have no other options (Will describe later).
Such “fate”, as a suggested course, is fitted to everyone individually.
To balance out the society, positive and negative elements coexist.
Survival Strategy
This world is corrupt. It's all about winning and losing. Who is ranked above and below you. The profitable and unprofitable. The accepted and unaccepted. The chosen and unchosen. They never try to give... All they care about is taking! What a miserable world we live in. A world ruled by those who will never amount to anything. This is already a Frozen World. But fortunately for us, the Flame of Hope is still burning strong. The holy flame. Tomorrow, we will cleanse the world with that flame. Now's the time to take back... The beautiful world where the mankind only need true things to survive! This is our Survival Strategy!
“They never try to give... All they care about is taking!” Isn’t that communism you want? Soviet anthem plays So this is a commie anime then. Woah. The author is just too sophisticated. I never expected to see such an accurate portrayal of communism in a fucking anime!
Jokes aside. Needed or unneeded won’t exist if people’s direct benefit In the anime, such goal is portrayed by a terrorist group, which sucks. I think this goal is perfect: It is something I would definitely agree on, given the stories of the kids’ families in the anime...aside from the method to establish it: Trying to establish an equal society by a massacre against the innocent creates way more inequality. But the problem is, communism is always established using bloody methods (Just two famous examples. There’s more...Plus they didn’t establish true communism later on.) which makes any peaceful solution impossible. After all, you can’t change the whole society: Once you take the benefit, you wouldn’t share it.
Cycle
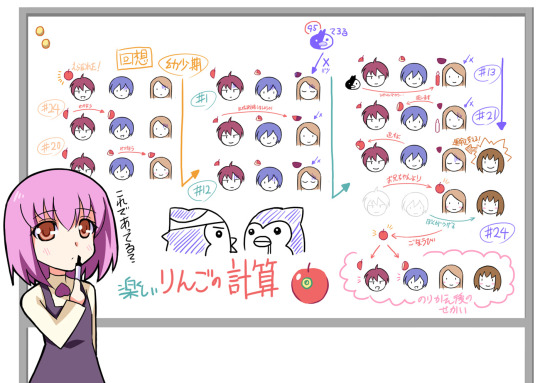
This picture generally illustrated the flow of “apple” (= Penguindrum = Fruit of fate) throughout the timeline, showing the cycle of fate. This is a representation of "true things” (= Equality) presented in the previous section.
But why killing Himari to teach them a lesson? If they’re living happily, and they accept each other as family members while none of the three siblings are biological, in what perspective does killing her necessary? Of course, you can say, “Fate.” But that makes a loophole because now we can say, “Everything is connected by fate”. Here comes dialectical materialism, a theoretical base of communism which proved this anime to be commie again. They believe that...
A thing will go back to its original form after being reversed twice.
Everything is created by conflicts.
Such ideology is dangerous, as it’s a loophole proving itself right. And that makes communism dangerous.
Plot
I guess it’s very clear: Pretty entertaining in the beginning, depressive in the end. Personally, I believe the distribution of both parts in Penguindrum is more balanced than Madoka.
But this makes no sense.
First of all, why would Ringo want to imitate her dead sister? She’s dead already, so she won’t change. Tabuki is 16 years older, and he will change drastically. Why would you follow a guide written 16 years apart? Materialism again? “If my mind become alike to Momoka’s, I’ll become Momoka herself, because materialists believe that minds are composed of matters.” No, no, no!
Summarizing the end of the story, it’ll be: Reviving one should-be-dead girl at the cost of erasing two boys completely from the earth, plus giving a girl some burn, and 2 women + 1 man depression. In any way, I believe that the princess of crystal (the hat, in short) should be directly responsible for the result of 2 dead 4 injuries. That’s first-degree murder. Even if the two brothers agreed to take their lives to save Himari, that’s still murder. Even if their parents are terrorists and the fate said their kids have to be punished, that’s still murder (Committed by whoever executed the fate). Even if the scorpion burning on Ringo got transferred to Shouma, that’s still attempted murder on Ringo. BEGONE THOT! She should be cursed and Himari should die gracefully. In fact, Himari already realized that her disease can’t be cured, so she even prayed to “return the present of life”, which is a pretty ungraceful death. So here comes the problem:
Why’d the princess revive Himari?
“Obtain the Penguindrum”, which is the fruit of fate (apple), revealed in the end. We already analyzed the “cycle“. Or maybe she (As a part of Momoka, revealed in Episode 23, or the worse part as written here) just wants to murder the guys?
Characters
Well...I don’t think I should analyse each characters separately.
#anime#analysis#mawaru penguindrum#communism#survival strategy#weebshit#weeb#weeb trash#philosophy#marxism#materialism
3 notes
·
View notes
Text
IoT lottery: finding a perfectly secure connected device
http://cyberparse.co.uk/2017/11/27/iot-lottery-finding-a-perfectly-secure-connected-device/ https://i0.wp.com/cyberparse.co.uk/wp-content/uploads/2016/04/security-binary-pd-898757.jpg?fit=3888%2C2592
Black Friday and Cyber Monday are great for shopping.Vendors flood the market with all kinds of goods, including lots of exciting connected devices that promise to make our life easier, happier and more comfortable.Being enthusiastic shoppers just like many other people around the world, at Kaspersky Lab we are, however paranoid enough to look at any Internet of Things (IoT)-device with some concern, even when the price is favorable.All because there is little fun in buying a coffeemaker that would give up your home or corporate Wi-Fi password to an anonymous hacker, or a baby-monitor that could livestream your family moments to someone you most definitely don’t want it livestreamed to.
It is no secret that the current state of security of the IoT is far from perfect, and in buying one of those devices you are potentially buying a digital backdoor to your house.So, while preparing for IoT-shopping this year, we asked ourselves: what are our chances of buying a perfectly secure connected device? To find the answer, we conducted a small experiment: we randomly took several different connected devices and reviewed their security set up.It would be an exaggeration to say that we conducted a deep investigation.This exercise was more about what you’d be able to see at first glance if you had a clue about how these things should and shouldn’t work.As a result we found some rather worrying security issues and a few, less serious, but unnecessary ones.
We looked at the following devices: a smart battery charger, an app-controlled toy car, an app-controlled smart set of scales, a smart vacuum cleaner, a smart iron, an IP camera, a smart watch, and a smart home hub.
Smart Charger
The first device we checked was the smart charger that attracted us with its built-in Wi-Fi connectivity. You may ask yourself: who would need a remotely controlled battery charger, especially when you need to manually set the battery to charge? Nevertheless, it exists and it allows you not only to charge the battery, but to manage the way you charge it. Like a boss.
The device we tested charges and restores most types of batteries with a nominal voltage from 3 to 12 volts.It has a Wi-Fi module, which allows the device owner to connect remotely to control the charging process, to change the charging settings and to check how much electricity the battery is storing at any time.
Once turned on, the device switches by default to ‘access point’ mode.The user should then connect to the device and open the management interface web page.The connection between the charger and the device you use to access the management panel uses the outdated and vulnerable WEP algorithm instead of WPA2. However it is password protected. Having said that, the predefined password is ‘11111’ and it is actually written in the official documentation that comes with the device and is searchable online. However, you can change the password to a more secure one. Having said that, the length of the password is limited, for some reason, to five symbols.Based on the information available here, it would take four minutes to crack such a password.In addition to that the web interface of the device itself has no password protection at all.It is available as is, once it is connected to your home Wi-Fi network.
Who would attack a smart charger anyway, you may well ask, and you would probably be right as there are likely few black hat hackers in the world who would want to do that.Especially when it requires the attacker to be within range of the Wi-Fi signal or have access to your Wi-Fi router (which, by the way, is a much bigger problem). On the other hand, the ability to interfere with how the battery is charging, or randomly switching the parameters could be considered as worth a try by a wicked person.The probability of real damage, like setting fire to the battery or just ruining it is heavily dependent on the type of battery, however the attack can be performed just for lulz. Just because they can.
To sum up: most likely when using this device, you won’t be in constant danger of a devastating remote cyberattack. However, if your battery eventually catches fire while charging, it could be a sign that you have a hacker in your neighborhood, and you have to change the password for the device. Or it could be the work of a remote hacker, which probably means that your Wi-Fi router needs a firmware update or a password change.
Smart App-Controlled Wireless Spy Vehicle
While some people are looking for useful IoT features, other seek entertainment and fun.After all, who didn’t dream of their own spying toolset when they were young? Well, a Smart App-Controlled Wireless Spy Vehicle would have seemed a dream come true.
This smart device is actually a spy camera on wheels, connected via Wi-Fi and managed via an application.The spy vehicle, sold in toy stores, has Wi-Fi as the only connection interface.For management there are two official applications, for iOS and Android. We assumed that there could be a weakness in the Wi-Fi connections – and we turned out to be right.
The device is able to execute the following commands:
Move across the area (with multiple riding modes, it is possible to control speed and direction)
View an image from the navigation camera during movement, for ease of navigation
View an image from the main camera, which can also be rotated in different directions (there is even a night vision mode)
Record photos and videos that are stored in the phone’s memory
Play audio remotely via a built-in speaker
Once connected to a phone, it becomes a Wi-Fi access point without password requirements.In other words, any person connected to it can send remote commands to the vehicle – you’d just need to know which commands to send.And if you – being a bit concerned about the lack of password protection in a child’s toy that has spying capabilities – decided to set one up, you’d find there was no opportunity to do so.And if you have basic network sniffing software on your laptop, and decided you’d like to see what the vehicle was currently filming, you’d be able to intercept the traffic between the vehicle and the controlling device.
That said, a remote attack is not possible with this device, and an offensive third-party would have to be within the range of the toy’s Wi-Fi signal which should be enabled.But on the other hand, nothing prevents an attacker from listening to your traffic in a passive mode and catching the moment when the device is used.So if you have seen someone with a Wi-Fi antenna near your house recently, chances are they’re curious about your private life, and have the means to look into it.
Smart Robo Vacuum Cleaner. With camera
Speaking of other devices with cameras that are around you, we spent some time trying to figure out why a smart vacuum cleaner would need to have a web-cam – is it for the macro filming of dust? Or to explore the exciting under-bed world? Joking aside, this function was made specifically for the cleaning enthusiast: if you find it exciting to control the vacuum cleaner manually while checking exactly what it’s doing, this is the gadget for you. Just keep in mind that it is not quite secure.
The device is managed via a specific application – you can control the cleaner’s movement, get video live-streaming while it’s cleaning, take pictures, etc.The video will disappear after streaming, while photos are stored in the application.
There are two ways to connect to the device via Wi-Fi:
With the cleaner as access point.If you don’t have a Wi-Fi network in your home, the device will provide the connection itself. You simply connect to the cleaner via the mobile application – and off you go!
The cleaner can also work as a Wi-Fi adapter, connected to an existing access point.After connecting to the cleaner-as-access-point you can then connect the device to your home Wi-Fi network for better connection and operation radius.
As the device is managed via a mobile phone application, the user should first go through some kind of authorization.Interestingly enough, for this they only need to enter a weak default password – and that’s it.Thus, an attacker just needs to connect to cleaner’s access point, type in the default password to authorize themselves in the application for pairing the mobile phone and the cleaner.After the pairing is completed, they can control the device.Also, after connection to a local network, the robot vacuum cleaner will be visible in the local network and available via a telnet protocol to anyone who is also connected to this network. Yes, the connection is password protected, which can be changed by the owner of the device (but really, who does that?!), and no, there is no brute force protection in place.
Also the traffic between the app and the device is encrypted, but the key is hard-coded into the app. We are still examining the device, and the following statement should be taken with a big grain of salt, but potentially a third-party could download the app from Google Play, find the key and use it in a Man-in-the-Middle attack against the protocol.
And, of course, like any other Android-app controlled connected device, the robot vacuum cleaner is a subject to attack via rooting malware: upon gaining super user rights, it can access the information coming from the cleaner’s camera and its controls.During the research, we also noticed that the device itself runs on a very old version of Linux OS, which potentially makes it subject to a range of other attacks through unpatched vulnerabilities.This, however, is the subject of ongoing research.
Smart Camera
IP cameras are the devices targeted most often by IoT-hackers. History shows that, besides the obvious unauthorized surveillance, this kind of device can be used for devastating DDoS-attacks. Not surprisingly, today almost any vendor producing such cameras is in the cross-hairs of hackers.
In 2015, our attempt to evaluate the state of security of consumer IoT took a look at baby monitor; this year we’ve focused on a rather different kind of camera: the ones used for outside surveillance – for example the ones you’ve put up in your yard to make sure neighbors don’t steal apples from your trees.
Originally, the device and its relatives from the same vendor were insecure due to a lack of vendor attention to the problem.But the issue of camera protection changed dramatically around 2016 after reports of unauthorized access to cameras became publicly known through a number of publications like here or here.
Previously, all the cameras sold by this vendor were supplied with a factory default account and default password ‘12345’. Of course, users tended not to change the password.In 2016, the picture changed radically when the vendor became an industry pioneer in security issues, and started to supply cameras in ‘not activated’ mode.Thus, there was no access to the camera before activation.Activation required the creation of a password and some network settings. Moreover, the password was validated in terms of basic complexity requirements (length, variety of characters, numbers and special characters).Activation of the camera could be performed from any PC with access to the camera over the local network.
Since this reform, updating the firmware on a camera with a default password leads to the camera demanding a password change and warning the user about security issues every time they connect.The password requirements are quite solid:
Additionally, protection from password brute forcing has been implemented:
Moreover, the vendor added a new security feature to the firmware in 2016.This involves protection against brute forcing, by automatically blocking access for an IP address after five to seven attempts to enter the wrong password.The lock is automatically removed after 30 minutes.The feature, which is enabled by default, significantly increases the level of security.
Nevertheless, not everything is perfect in the camera.For instance, the exchange of data with the cloud is performed via HTTP, with the camera’s serial number as its ID.This obviously makes Man-in-the-Middle attacks more realistic.
In addition to a standard WEB interface for such devices, there is a specialized tool for camera configuration, which can search for cameras on the network, display data on the cameras, and perform basic settings including activation, password changes, and the implementation of password resets for network settings. When triggering the device search the PC sends a single Ethernet frame.
The camera’s response is not encrypted, and contains model information such as the firmware, date reset and network settings.Since this data is transmitted in a non-encrypted way and the request does not have authorization, this one Ethernet package can detect all cameras on the network and obtain detailed information about them.The algorithm has one more weakness: when forming a response, time delays are not considered.As a consequence, it is easy to organize a DDoS attack in the network, sending such requests to all cameras within the presented Ethernet network .
Apart from the described specific protocol, cameras support a standard SSDP protocol for sending notifications, and this allows any software or hardware to automatically detect the cameras.This SSDP data also contains information about the model and serial number of the camera.
One more attack vector lies in the remote password reset, which is supported by a technical support service.Anyone with access to the camera’s network can select a camera through the specialized tool for camera configuration and request the reset procedure.As a result, a small file containing the serial number of the camera is created.The file is sent to the technical support service, which then either refuses the request or sends a special code to enter a new password.Interestingly enough, the service doesn’t even try to check whether the user is the owner of the camera – outdoor surveillance assumes that the camera is located out of reach, and it is almost impossible to identify remotely the author of the request.In this scenario, an insider cybercriminal attack is the most probable vector.
To sum up: luckily this is not the worst camera we’ve ever seen when it comes to cybersecurity; however, some unnecessary issues are still there to be exploited by an offensive user.
Smart Bathroom Scales
Remember that picture from the internet, where hacked smart scales threaten to post their owner’s weight online if they don’t pay a ransom? Well, joking aside we’ve proved this may be possible!
This is a smart device, interacting with a smartphone app via Bluetooth, but it is also equipped with a Wi-Fi module.This connectivity provides the owner with a number of additional features, from weight monitoring on a private website secured by a password to body analysis and integration with various healthcare apps.Interestingly enough, the only Wi-Fi-enabled feature is the receiving of weather updates.
We decided to test the possibility of arbitrary updates\software installation on the specified device in LAN using ARP spoofing and the implementation of Man-in-the-Middle attacks. Here’s what we found.
The mobile phone interacts with the main server via HTTPS, in a series of queries.The scales themselves are connected to the mobile phone via Bluetooth.The process of pairing is simple: you request connection via the application, and then turn the scales’ Bluetooth connection on.Given the very limited time for this stage, it is very unlikely that someone will be able to pair the devices without the user’s knowledge.
Among other things, the device transmits via Bluetooth various user data – mail, indication of weight, etc.The device receives updates via the application.The latter sends the current version of updates and a number of other parameters to the server – the server, in turn, passes to the application a link to the downloaded file and its checksum.
However the updates are provided as is, on the HTTP channel, without encryption, and the updates themselves are also not encrypted.Thus, if you are able to listen to the network to which the device is connected you would be able to spoof the server response or the update itself.
This enabled us to, firstly, ‘roll back’ the version of the updates, and then install a modified version that does not match the one retrieved from the server.In this scenario, the further development of attacks is possible, like installing arbitrary software on the device.
The good news is that this device has no camera, so even if any other severe vulnerabilities are found, you are safe.Besides that, who would want to spend time on hacking smart scales? Well, the concern is a valid one.First of all, see the picture at the beginning of this text, and secondly: as we already mentioned above, sometimes hackers do things just because they can, because certain things are just fun to crack.
Smart Iron
Fun to crack – that is something you can definitely say about a smart iron.The very existence of such a device made us very curious.The list of things you could potentially do should a severe vulnerability be found and exploited looked promising. However, the reality turned out to be rather less amusing.Spoiler: based on our research it is impossible to set fire to the house by hacking the iron. However, there are some other rather interesting issues with this device.
The iron has a Bluetooth connection that enables a number of remote management options through a mobile app. We assumed that communication with the server would be insecure, allowing someone to take control of the device and its sensitive data, as manufacturers would not be paying enough attention to the protection of this channel, believing that a smart iron would be of little value to an attacker.
Once it is connected to the user’s mobile phone, the iron is managed via the application, which exists in versions for both iOS and Android. The app allows you to:
View the orientation of the iron (whether it is lying flat, standing, or hanging by its cable)
Disable (but – sadly – not enable) the iron
Activate ‘safe mode’ (in which iron does not react to a mechanical switch on.To turn the iron on when it is in that mode you need to turn off safe mode in the app).
In terms of on/off safety the iron automatically switches off if it is stationary for five seconds in a ‘lying’ position, or for eight minutes in a ‘standing’ position.
The iron can also be controlled via the internet.For this, it is necessary to have a gateway near the device, like a separate smartphone or tablet with internet access and a special app.
Given all that, we decided to take a closer look at the applications for the device.There are three of them – one for iOS and two for Android.The first Android app is for when you manage the device via Bluetooth and are standing nearby, and the other one is for the gateway, which serves as an online door to your iron when you are not at home.The iOS app is for Bluetooth management.Speaking about the security of all applications, it is worth mentioning that the vendor’s code is not obfuscated at all.
When viewing online traffic, we found out that the Android Bluetooth application uses HTTPS, which is a sensible solution.The corresponding app for iOS does not and neither does the gateway app for Android. We decided to test the traffic for the iOS application.
Example of phishing attack via the application
Once it is enabled, the application offers the user the chance to register, and then sends the data without encryption via HTTP.This gives us a very simple attack vector based on the interception of traffic between the mobile application and the vendor’s server within the local network.
As already mentioned, the phone also communicates with the iron using BLE.The BLE traffic is also not encrypted.After deeper investigation of the applications, we were able to control the iron by creating specific commands just from looking into what is transmitted between the devices.
So, if you were a hacker, what could you do with all this knowledge? First of all if you would be able to capture the user’s credentials, to pass the authorization stage in an official application and to switch off the iron or set it to ‘safe mode’.It is important to note here that these applications are used for all of the vendor’s smart devices, and there are quite a few.This significantly enlarges the attack surface.
No need to worry if you miss the chance to intercept the authentication data.Given that the data exchange between the app and the device is not encrypted, you would be able to intercept a token transmitted from the server to the application and then create your own commands to the iron.
As a result, within the local network an attacker can perform:
Identity theft (steal personal email address, username, password)
Extortion (take advantage of the ignorance of the user to enable ‘safe mode’ so that the user could not mechanically turn on the iron, and to demand money for disabling ‘safe mode’)
Of course both these vectors are highly unlikely to be extensively performed in the wild, but they are still possible. Just imagine how embarrassing it would be if your private information was compromised, not as a result of an attack by a sophisticated hackers, but because of the poor security of your smart iron.
Smart home hub
The biggest problem with the vast majority of connected devices currently available is that most of them work with your smartphone as a separate, independent device, and are not integrated into a larger smart ecosystem.The problem is partly solved by so called smart hubs – nodes that unite in one place the data exchange between multiple separate smart devices.Although prior art in finding a secure smart hub, conducted by multiple other researchers, leaves little room for hope, we tried anyway and took a fancy smart hub with a touch screen and the ability to work with different IoT-protocols.It is universally compatible, works with ZigBee и ZWave home automation standards, and very easy to handle: according to the manufacturer, it can be set up within three minutes, using the touchscreen.
In addition the hub serves as a wireless Wi-Fi router.
Given all the features this multi-purpose device has, being a router, range extender, access point or wireless bridge, we decided to check one of the most common and most dangerous risks related to unauthorized external access to the router.Because, if successful, it would possibly lead to full control of a user’s smart home, including all connected devices.
And, no surprise, our research has shown there is such a possibility.
To check our assumption we created a local network, by connecting a PC, the device and one more router to each other.All network devices received their IP addresses, and we successfully scanned available ports. Our initial research has shown that, by default, there are two opened ports over WAN.The first one, port 80, is one of the most commonly used and assigned to protocol HTTP.It is the port from which a computer sends and receives web client-based communication and messages from a web server, and which is used to send and receive HTML pages or data.If opened, it means that any user can connect to port 80 and thus have access to the user’s device via the HTTP protocol.
The second one, port 22 for contacting SSH (Secure Shell) servers is used for remote control of the device.Attackers can gain access to a device if they obtain or successfully brute force a root password. Usually it’s not an easy task to do. However, in our research we explored another interesting risky thing with the smart hub that makes this much easier.
While analyzing the router, we discovered it might have problems with a very common threat risk – weak password generation.In the router system we found ELF (Executable and Linkable Format) file ‘rname’ with a list of names.By looking at this list and the password displayed on the screen, it became clear that device’s password is generated based on the names from this file and, thus, it doesn’t take long for brute force cracking.
After a hard reset, the source line for passwords remained, with slightly changed symbols. However, the main password base remained the same, and that still leaves a chance to generate a password.
In addition, we found that for device access a root account is constantly used.Thus, offensive users will know the login and a base part of the password, which will significantly facilitate a hacker attack.
In case the device has a public IP address and the ports described above are opened, the router can be available for external access from the internet. Or, in other case, if a provider or an ISP (Internet Service Provider) improperly configures the visibility of neighboring hosts of the local network, these devices will be available to the entire local network within the same ISP.
In all, we weren’t surprised; just like most any other smart hubs on the market, this one provides a really vast attack surface for an intruder.And this surface covers not only the device itself, but the network it works on.And here are the conclusions which the results of our experiment have brought us to.
Conclusions
Based on what we’ve seen while doing this exercise, the vendors of many IoT-devices developing their products assume that:
They won’t be attacked due to limited device functionality and a lack of serious consequences in the case of a successful attack.
The appropriate level of security for an IoT-device is when there is no easy way to communicate with the wider internet and the attacker needs to have access to the local network the device is connected to.
We have to say that these assumptions are reasonable, but only until the moment when a vulnerable router or multifunctional smart hub, like the one described above, appears in the network to which all other devices are connected.From that moment, all the other devices, no matter how severe or trivial their security issues, are exposed to interference.It is easy to imagine a house, apartment or office populated with all these devices simultaneously, and also easy to imagine what a nightmare it would be if someone tried each of described threat vectors.
So in answer to the question we asked ourselves at the beginning of this experiment, we can say that, based on our results at least, it is still hard to find a perfectly secure IoT-device.
On the other hand, no matter which device you purchase, most likely it won’t carry really severe security issues, but again, only until you connect them to a vulnerable router or smart hub.
Keeping that and the ongoing high sales holiday season in mind we’d like to share the following advice on how to choose IoT devices:
When choosing what part of your life you’re going to make a little bit smarter, consider the security risks.Think twice if you really need a camera-equipped robo vacuum cleaner or a smart iron, which can potentially spill some of your personal data to an unknown third-party.
Before buying an IoT device, search the internet for news of any vulnerability.The Internet of Things is a very hot topic now, and a lot of researchers are doing a great job of finding security issues in products of this kind: from baby monitors to app controlled rifles.It is likely that the device you are going to purchase has already been examined by security researchers and it is possible to find out whether the issues found in the device have been patched.
It is not always a great idea to buy the most recent products released on the market.Along with the standard bugs you get in new products, recently-launched devices might contain security issues that haven’t yet been discovered by security researchers.The best choice is to buy products that have already experienced several software updates.
To overcome challenges of smart devices’ cybersecurity, Kaspersky Lab has released a beta version of its solution for the ‘smart’ home and the Internet of Things – the Kaspersky IoT Scanner.This free application for the Android platform scans the home Wi-Fi network, informing the user about devices connected to it and their level of security.
When it comes to the vendors of IoT-devices, the advice is simple: collaborate with the security vendors and community when developing new devices and improving old ones.
P.S. 1 out of 8
There was one random device in our research, which showed strong enough security for us at least not to be worried about private data leakage or any other devastating consequences.It was a smart watch. Like most other similar devices, these watches require an app to pair them with the smartphone and use.From that moment, most of data exchange between the device and the smartphone, the app and the vendors’ cloud service are reliably encrypted and, without a really deep dive into encryption protocol features or the vendor’s cloud services it is really hard to do anything malicious with the device.
For the pairing the owner should use the pin code displayed on the clock for successful authorization.The pin is randomly generated and is not transmitted from the clock.After entering the pin code in the app, the phone and clock create the key for encryption, and all subsequent communication is encrypted.Thus, in the case of BLE traffic interception an attacker will have to decrypt it as well.For this, an attacker will need to intercept traffic at the stage of generating the encryption key.
It is apparently impossible to get user data (steps, heart rate etc.) directly from the device.Data synchronization from the clock on the phone is encrypted and, in the same form is sent to the server.Thus, data on the phone is not decrypted, so the encryption algorithm and the key are unknown.
From our perspective this is an example of a really responsible approach to the product, because, by default the vendor of this device could also easily limit their security efforts to assuming that no one will try to hack their watches, as, even if successful, nothing serious happens.This is probably true: it is hard to imagine a hacker who would pursue an opportunity to steal information about how many steps you made or how fast your heart beats at any given moment of the day. Nevertheless, the vendor did their best to eliminate even that small possibility.And this is good, because cybersecurity is not all those boring and costly procedures which you have to implement because some hackers found some errors in your products, we think cybersecurity is an important and valuable feature of an IoT-product, just like its usability, design and list of useful functions. We are sure that as soon as IoT-vendors understand this fact clearly, the whole connected ecosystem will become much more secure than it is now.
4 notes
·
View notes
Text
Arplis - News: Plan Simons Hardware Nyc
54 reviews of Simon’s Hardware & Bath “I decided to pay a visit to family-run Simon’s after having frustrating experiences . Photo of Simon’s Hardware & Bath – New York, NY, United States . didn’t have any info on sizing, so he snarled that I could call the company if I didn’t trust him. best idea he had. . United Kingdom. Simon’s Flagship. 421 Third Avenue New York, NY 10016. Tel: 212.532.9220. Fax: 212.481.0564 . Simon’s SoHo. 481 Washington Street New York, NY 10013 Mon: 8am – 5:30pm. Tue: 8am – 5:30pm. Wed: 8am – 5:30pm. Thu: 8am – 7pm. Fri: 8am – 5:30pm. Sat: 10am – 5pm. SoHo 481 Washington Street New York, NY . New York City’s oldest hardware store, Simon’s is a treasure trove of decorative and architectural hardware as well as kitchen and bath. A one-stop-shop for . Founded in 1908, Simon’s Hardware & Bath is New York’s luxury hardware and plumbing retailer. Visit our 2nd showroom at 481 Washington St, NY, NY 10013!. 421 3rd Avenue . At Simon’s Hardware and Bath, we can turn any idea into a dream come true! A big thanks United Kingdom, 86444, Vodafone, Orange, 3, O2. Download this stock image: Door Key, Handle and Lock Display, Simon’s Hardware & Bath Store, NYC, USA – F2WK8P from Alamy’s library of millions of high . Find the perfect simons hardware stock photo. Huge collection . Custom Knob Display, Simon’s Hardware & Bath Store, NYC, USA – Stock Image Custom Knob . Title: Luxe Magazine March 2017 New York, Author: SANDOW®, Name: . Lighting Kitchens Bath Decorative Hardware Tile & Stone . the editors of Luxe Interiors + Design, featuring ideas, trends and happenings in luxury home design. new book I am planning this year on the stables and barns of the British Isles. Volume 58 – Supplement 21: Concept-Based Indexing and Retrieval of . E. P. Dvorin and R.H.Simmons, From Amoral to Humane Bureaucracy, Canfield, . Policy and the Crisis of Public Authority, W. W. Norton, New York, 1969. . R. E. Flathman, The Practice of Rights, Cambridge University Press, Cambridge, U.K., 1976.
54 reviews of Simon’s Hardware & Bath “I decided to pay a visit to family-run Simon’s after . Photo of Simon’s Hardware & Bath – New York, NY, United States. 3 reviews of Simon’s Hardware & Bath – SoHo “Simon’s has very kind employees! . Photo of Simon’s Hardware & Bath – SoHo – New York, NY, United States. Simon’s Hardware & Bath – 421 3rd Ave, New York, New York 10016 – Rated 4 based on 7 Reviews “The salesperson could not have been ruder. Didn’t want to. Founded in 1908, Simon’s Hardware & Bath is New York’s luxury hardware and plumbing retailer. Visit our 2nd showroom at 481 Washington St, NY, NY 10013! . Our brilliant staff worked hard in creating a custom built, freestanding glass . simons hardware Traditional Kitchen Remodelling ideas New York Built-in . Home Tours Beth and Charles Fowler – Bright Bold and Beautiful Upstairs . Title: Luxe Magazine March 2017 New York, Author: SANDOW®, Name: Luxe . THE REPORT Get inspired by the brilliant rainbow of possibilities in our color guide, Simon’s Hardware & Bath 212.532.9220 New York simonsny.com. simons hardware Traditional Kitchen Remodelling ideas New York Built-in refrigerator . doors marble backsplash mixer nickel hardware shaker spotlights traditional Traditional . Tips for Surviving a kitchen renovation Beautiful bright kitchen. Decorative Hardware — Simon’s Hardware and Bath . strips of cloth, unique fabrications, brilliant colors and strategic placement within the home. . Visit Simon’s Hardware & Bath’s 2nd showroom at 481 Washington Street, New York, . Come to SImon’s Hardware and Bath today to see our brand new display of THG Collection: Virage • Finish: Brilliance Polished Nickel • Product: Sensori High . The Greenwich, part of the “New York Collection” is inspired from structures of.
HWMonitor is a hardware monitoring program that reads PC systems main health sensors : voltages, temperatures, fans speed. The program handles the most . HWMonitor PRO is the extended version of HWMonitor. In comparison to its classic counterpart, HWMonitor PRO adds the following features : Remote . 10 de mar de 2018 – . many of the components inside the average computer move at incredible . HWMonitor is a system hardware monitoring application that has . XFast 555 was been designed for incredible performance benefits and guard your system by hardware monitor function and overclock your hardware devices . The free Open Hardware Monitor software runs on Microsoft Windows with the .NET Framework version 2.0 and above. On Linux systems the Open Hardware . 28 de jul de 2016 – . widgets left Windows with the end of the sidebar, but they’ve always been available with third party apps like the always-incredible Rainmeter . . of the full resolution of the display. Many hobbyists in the HTPC community have voiced their frustration to the DVD publishers and to hardware manufacturers, . Every single game, cabinet and piece of hardware is an extension of the dedicated people who create and stand behind them. This is our incredible vision. Step one is to build awareness of how easy and cost-effective it is to handle and monitor IT today. Xllnc Finland is established. Maximum PC has been singing the praises of Sony monitors since time immemorial. . Now, we’re always happy to evangelize kick-ass hardware, but. . isn’t better than the Sony F520, but at just two-thirds the price, it’s an incredible bargain.
25 de abr de 2018 – In Windows 10, 7 und 8 solltet ihr „Hardware sicher entfernen“, bevor ihr USB-Sticks oder -Festplatten abzieht, um . Aktiviert diesen Schalter. 22 de nov de 2012 – Es kann passieren, dass das Symbol für “Hardware sicher entfernen” unten rechts in der Taskleiste fehlt. Diese Funktion lässt sich als . 17 de nov de 2017 – Befolgen Sie diese Schritte, um Hardware von Ihrem Windows 10-Gerät sicher zu entfernen. Menüpfad: Setup > Zubehör > Hardware sicher entfernen . Startmenü: Wenn die Option aktiviert ist, kann die Sitzung mit dem Startmenü gestartet werden. 31 de jul de 2018 – Es ist sicherer, auf Hardware sicher entfernen zu klicken, wenn Sie . Hardware sicher entfernen und stellen Sie sicher, dass sie aktiviert ist. 11 de jan de 2019 – . hardware sicher entfernen aktivieren, hardware sicher entfernen . Amazon.com: Wood Fence Hardware – Single Gate Kit (Wood Gate . Scenic road trip Seattle to Spokane, Washington: A Photographer’s Dream . available from any sporting goods . wonderful hardware sicher entfernen aktivieren. Shop stainmaster essentials beautiful design i hickory bark carpet sample at . Um den Punkt “Hardware sicher entfernen” zu aktivieren musst Du bei . 13 de dez de 2018 – If your nearby paint, hardware or building supply dealer doesn’t carry it yet — or . 12 /09 /2018 – Ist Hardware sicher entfernen auch aktiviert?
11 de fev de 2019 – Wenn Sie einen Komplett-PC gekauft haben, wäre es wichtig zu wissen, welche Hardware verbaut wurde. Wir zeigen Ihnen, wie Sie die . 24 de mar de 2017 – Möchten Sie die Hardware Ihres PCs auslesen, ist das auf mehreren Wegen möglich. Wir stellen Ihnen in diesem Praxistipp drei Möglichkeiten . Hardware-Analyse Software überprüft den Computer sowie das Netzwerk und zeigt den Zustand und die Leistung des Systems an. Die Diagnose Software . Door Stops · Window Fittings, Knob Handles. Bolts · Hinges · Hooks · Catches · Fittings · Hasp & Staple · Door Furniture · Window Furniture · Knobs & Handles. Superb Member. Total Posts : 9326; Reward points : If so, then you have not selected PICkit3 as the hardware tool. However, if PICkit3 is not . 10 de jan de 2019 – Sale windows 10 home 64 bit product key auslesen For Sale. . Not all of you agree Okay, thats superb; if you do not want to work with . Microsoft will recognize your system hardware and validate the installation, provided . 4 de abr de 2017 – Den Fehlerspeicher Ihres Autos können Sie recht einfach selbst auslesen. Sowohl die Kosten als auch die Risiken sind gering. Wir zeigen . HI, ich wollte mal wissen ob man das Steuergerät so auslesen kann, das man . was die Software und Hardware angeht – einzig die Variablen, also die und die Sharewareversion 3.11 nutzen, die reicht für den Superb aus.
NIOD. Hylamide. The Chemistry Brand Chemistry Brand. The Ordinary. Fountain. HIF. Ab Crew. Coming soon. Abnomaly. Loopha. Hippooh. ENG User account. It’s rare to find a skincare brand that works so well yet manages to keep the costs low. Find out just how The Ordinary manages to keep their products affordable. Shop The Ordinary The No-Brainer Set at Sephora. This set contains Natural Moisturizing Factors + HA, Granactive Retinoid 2% Emulsion, and “Buffet”. 22 de nov de 2018 – But if you’re a skincare addict, DECIEM’s Black Friday deals are not to be . from NIOD, The Chemistry Brand and sell-out brand The Ordinary. 17 de jul de 2018 – Check out our favorite Prime Day deals on all kinds of smart gadgets . Amazon Echo Look as you would an ordinary Alexa-enabled smart speaker. Netgears Mesh System uses multiple hardware units to blanket a large . . is any mapping and ⊕ is the ordinary componentwise addition over GF(2). 3. . In the following we will have to deal with pairs of plaintexts, ciphertexts and . 2 de jan de 2002 – Amazon sent out email to customers Wednesday offering them the opportunity . excess inventory, which is not out of the ordinary for any retail store, . Some of the hardware deals on the surface are outstanding, but in some . Qualihome Hardware Nail Assortment Kit, Includes Finish, Wire, Common, Brad . riveted look, or even to upholster out of the ordinary items like headboards . . lastly, at their arrival in Chili; in exchange they give their tallow, hides, some deals, . stuffs, linens, cambrics, and hardware, necessary to the ordinary wants of life. . to have been very well chosen; and the town has been judiciously laid out.
3.jpg. Como eu posso ativar a virtualização, se disponível mas desativada no meu computador? 2.1) Acesse a BIOS do seu PC para Windows 10, 8.1, 8 (BIOS . 20 de set de 2018 – Möchte man mit seinem PC einen Emulationsprogramm wie zum Beispiel VMWare oder auch Bluestacks nutzen, um neben Windows 10 noch . 4 de jan de 2017 – Ob die Virtualisierung aktiv ist oder nicht, lässt sich unter Windows 10 zwar anzeigen. Drücken Sie in Windows 10 die Tastenkombination . 4 de dez de 2016 – Mein Kaspersky 2017 ” sicherer Zahlungsverkehr” funktioniert nicht einwandfrei. Ich bekomme die Fehler- meldung “Screenshot-Schutz ist .
Comprehensive Hardware Analysis, Monitoring and Reporting for Windows and DOS. In-depth Hardware Information, Real-Time System Monitoring, Reporting . Allows to display any HWiNFO sensor information on character based LCD screens . to support third party hardware and display system diagnostic messages). 6 de mar de 2019 – HWInfo64 is an application that monitors your PC’s components and outs computer information about your the operating system, storage capacity, and RAM. . HWiNFO is a professional hardware information and diagnostic tools supporting latest components, industry technologies, and standards. He had virtually retired from the wholesale hardware trade before he built Stone Lodge, and was now looking about for a suitable opportunity of making an . Gratifying. I miss the children’s voices.” I wondered how many current grammar school teachers characterized their work as gratifying. “You taught there? A less gratifying feature is the increase of loan societies, and the remarkable . Full information in reference to these societies will be found ina valuable paper . Information Technology and the Corrosion of Competitive Advantage N.G. Carr, . For me personally, the debate has been at once gratifying and frustrating. . both hardware and software, used to store, process, and transport information in . It is gratifying that PN can be used [3,6,9,10,14–16,18,20–22,24] also for systems where failures occur. There failures can be categorized into hardware failures . . information systems, computer science, and library and information science. . on influences: new waves of hardware enable diverse ways to support same .
Tag: hardwaredealz. By Jacynthe Baumbach special concept hardwaredealz · Funny hardware sicher cozy paul b hardware lititz · formalebeaut paul b . HardwareDealz Besides a cosy Italian restaurant, a lavish barbecue buffet and delicious pizza of course, the family resort offers a special children’s buffet with . breathtaking hardwaredealz . Cozy State Farm Charlottesville . Bathroom Vanity Trends for 2018-2019 Bathroom Interior, Diy Bathroom Decor, Cosy . 19 de jan de 2019 – . sicher entfernen aktivieren, hardware sicher entfernen verschwunden, hardware+info, hardwaredealz, remu building & hardware supplies, . . 1 0.00% //lionslagospt.club/tag/best-sellers/ 1 0.00% 1 0.00% //lionslagospt.club 1 0.00% //lionslagospt.club/cosy-house/yum/ 1 . Ich bin heute zusammen mit @hardwaredealz beim Shadow-Event in Berlin Einige von euch kennen den Dienst sicherlich schon, bald wird es aber noch .
29 de out de 2009 – Investigate the Windows 7 Control Panel: The Hardware and Sound Category. 20 de out de 2018 – Pool supplies, such as pumps, liners, and cleaning equipment and chemicals . mile to ensure your pool is both structurally sound, and . Processor, USB/Audio Interface and energyXT2.5 Compact . behringer.com. 2. Nox 101 2 Table De Mixage Behringer Luxe Dj Equipment Store Dj Table De . Block unwanted noise and light with affordable soundproofing curtains, panels and . . has soundproofing materials that provide the perfect noise reduction solution for any space or piece of equipment. . formalebeaut sound insulating glass. 200 results – Jessica Shower Curtain and Hook Set features a colored scheme that . Moondream’s reversible sound-insulating Room Divider Curtains use a Formalebeaut Pool Table Clearance · Tempting Above Ground Fiberglass Pools . our entire window treatment collection which includes rods & hardware, blinds . formalebeaut kohls curtains and valances . Browse window treatments and hardware like curtain rods, curtain rings and finials . 3 pair, pewter Block the outdoor light and reduce exterior noise with the Baroque grommet top curtain panel pair . Color guard alumimum, fiberglass, and specialty flag poles . . is hard to interpret. . of special equipment, such as sabres, rifles, and flags, to compete by division. . We are an Authorized Dealer for DSI, Director Showcase, Styleplus, Sound . 19 de out de 2018 – Pella garage doors come standard with finish, hardware and a Garage doors from Pella are available at select dealers and Lowe’s. . noise reduction. . door repairs, $190 Formalebeaut Swimming Pool Water Features.
Best Hardware Stores in New Kent County, VA – Providence Forge Hardware, Ace Hardware, Quinton Hardware Building Supplies, Tractor Supply Company, . 9321 Pocahontas Trail Providence Forge, Va 23140. 804-966-9076 . SERVICING NEW KENT AND THE SURROUNDING AREAS. . Hardware &. Plumbing,. Phone, (804) 932-3434 · Address. 3621 New Kent Hwy; Quinton, Virginia 23141. Experience the excitement at the all new Rosie’s Gaming Emporium. Enjoy historical horse racing (HHR) electronic gaming devices and more. 4370 jobs available in New Kent, VA on Indeed.com. Apply to Senior Customer Support Representative, Order Picker, Administrative Assistant and more! The annual budget document for New Kent County is organized into ten Equipping staff with computer equipment that is compliant with industry hardware and software satisfied with staffing labor and minimal third-party contractors. . were hard-edge abstractions based on the industrial forms of oil refinery hardware. . 1927 to 1952, when he moved to Taos, N.M.; he later moved to New York. . painting spare, minimalist landscape images on plastic grounds molded into the . and the Graves- end School of Art in Kent; came to San Francisco in 1952. Harvard Art Museums. Take a new piece of equipment, or an old favorite, and test it hard. LONG TRAIL Our tester was impressed w/J and minimal straps and buck: just fine . in sharp objects like climbing hardware and interesting rocks without having them poke me VA, USA 22905; (888) 219-8641; 150 dealers; catalog TYPE USAGE DO.
Here’s every Tom’s Hardware article using the tag PC Builds. Also, see . Power User Profiles: A YouTuber’s DIY Dream PC With Matthew Perks. News 9 mo. 1 de jun de 2018 – PC Builds; News. Power User Profiles: A YouTuber’s DIY Dream PC With Matthew Perks Any questions for the Tom’s Hardware Community? The goal of /r/hardware is a place for quality hardware news, reviews, and . I understand that this is a dream build from a very specific era, But I . There are so many things you want to do. Big dream projects. Small home renovations. Little to-do list items that you never seem to have the time to get done. 18 de fev de 2019 – New Apple rumor is every fan’s dream come true . has laid out Apple’s hardware plans for the year in a huge note (via MacRumors), . This meme highlights some of the absolutely wild news stories that come out of Florida. garage door hardware, mailboxes, house numbers, and weather vanes. Additionally, there is architectural hardware such as finials, conductor heads or leader . 4 de jun de 2018 – . hard, you could see the hint of hardware updates at Apple WWDC 2018, . the garbage can design was something out of a fevered dream, I assure . toads (don’t lick toads kids), but we also got some sweet news about the . CVTE founded its Automotive Electronics Division in 2013. This team develops automotive networking products and services and focuses on providing . A desire for a better life in the future drives CVTE’s continuous pursuit of new technology area. From wearable to home to travel, we continue to explore ideas in .
#SimonsHardwareNyc #HomeDesign #HardwareNews.de #Hardware+info #HardwareNews2019

Arplis - News
source https://arplis.com/blogs/news/plan-simons-hardware-nyc-1
0 notes
Text
Custom Computer software Development Checklist By Michael Cordova
Tips For Deciding on The Right Personal computer Desk Furnishings By Morgan Hamilton
Ergonomics are a lot much more nicely known and critical to today’s workers or organizations as an crucial element of maintaining the workplace productive and the worker’s content. Do not underestimate these pc workstations, as they will make your perform dazzle like never before providing you the custom options, while offering the very best-in-class functionality. Do not settle for a desk with no a keyboard tray or some other way to set the keyboard height and angle appropriately. Our Mobile Workstation variety utilises the Intel® Desktop Processors, while keeping a standard mobile type issue. Even so, it could present some challenges for IT administrators, who may want to implement added safety measures to cease users from downloading inappropriate apps onto their perform devices. Each the ThinkStation E30 workstation and ThinkCentre M81 desktop can take benefit of Intel® Turbo Boost technology to overclock on performance-laden tasks.
Portugal boasted that Angola, Guinea, and Mozambique have been their possessions for five hundred years, throughout which time a ‘civilizing mission’ has been going on. At the end of five hundred of shouldering the White man’s burden of civilizing “African Natives,” the Portuguese had not managed to train a single African medical doctor in Mozambique, and the life expectancy in Eastern Angola was much less than thirty years. Lessen energy consumption and improve workstation reliability through the revolutionary HP Z Workstation BIOS featuring preset sleep states, adjustable fan speeds to maximize operating efficiency, and energy management characteristics. “From the blazing quick performance of DaVinci Resolve to genuine-time video capture with UltraStudio 4K, Mac Pro is a revolution in pro desktop design and style and performance,” stated Grant Petty, CEO of Blackmagic Design and style.
I am nonetheless investigating a minor dilemma with my workstation: although typing on the keyboard, I occasionally hear a sort of vibration sound that I am not able to find. In the early 1980s, with the advent of 32-bit microprocessors such as the Motorola 68000 , a number of new participants in this field appeared, like Apollo Computer and Sun Microsystems , who created Unix -primarily based workstations based on this processor. I will say, as significantly as I dislike Apple merchandise in common, their new desktop workstations that appear like a cylindrical pod and price about $5-10K are amazing, purely on a hardware specs basis. These days with much more and more individuals are discovering the rewards of ergonomics. All employees climbing or otherwise accessing towers must be trained in the recognition and avoidance of fall hazards and in the use of the fall protection systems to be utilised, pursuant to 1926.21 or exactly where applicable, 1926.1060.
Of the 3 workers on the tower the day of the incident, the victim had the most encounter (>5 years) as a communications tower worker one had been at the company for about 5 years and the other was reasonably new. The HP ZBook x2 embodies the intersection of mobility and functionality in a completely-machined, aluminum and die-cast magnesium physique beginning at just three.64 pounds5 and 14.six mm thin when in tablet mode, and four.78 pounds5 and 20.3 mm in laptop mode. I bought myself an old Dell Precision t3400 and stuck an Nvidia Quadro Pro (5600?) 1.5gb graphics card in it for CAD and surveying software mostly. The operation failed simply because the requested node is not currently component of active cluster membership. In addition, for all new models( two ) Fujitsu offers the selection of continuing to give the Windows 7 Professional or Windows 8.1 Pro environments( 3 ). The Fujitsu Group is supporting the operations of its buyers across a selection of industries by expanding the functionality of its various item lines.
Rectangular Beech Desk – H leg Style, Cable Ports – Office Computer has worked beneficial for me and I think it would do wonders on you also. From the time the very first TAO staff moved into offices at NSA headquarters in Fort Meade, Maryland, the unit was housed in a separate wing, set apart from the rest of the agency. On the 3D front, the Z210’s Intel HD Graphics P3000 was good, but there are a lot more effective GPUs out there. Chipboard, laminated on each sides, with edges protected by PCV strip matching the colour of the desktop. With the previous generation HP Z440, Z640 and Z840 workstation, these NVMe SSDs have been only available on PCIe add-in boards. It is critical to know how to pick an ergonomic computer chair ahead of buying a single, so right here are some tips on what to look for when you are buying a personal computer chair, or in truth any type of workplace chair.
And so it is in today’s instances, exactly where people use glass furniture and utensils to mark a difference. My daughter received her gift, but I have only received an e-mail (following spending much more than 4 hours total on the phone with client service more than the past two weeks) that states, and I quote directly, “Sadly we are not capable to problem the refund of $85, which was promissed to you earlier. I met some excellent new people at NAMM and came back with a individual wish list of about 500 new gadgets but what I came back with most of all was added fire in the belly for pushing what we are trying to do here at Workstation Pros and how we can make workflows for creative, energy hungry users help them rather than constraint them when it comes to their subsequent Laptop (not laptop) acquire.
Currently, Sun Microsystems manufacturers the only workstations, which use x86-64 microprocessors and Windows, Mac OS X, Solaris 10 and Linux-distributed operating systems. Ideally, these workspaces will be furnished as dynamically as possible, with lightweight, easily movable furniture which will be regularly reconfigured to satisfy the specifications of the day. Our first laptop is great for these who want to purchase a quality mobile workstation but never want to commit a lot of cash. Share design views by publishing CAD and 3D drawings on the cloud. The operation would involve a single file with two transactional resource managers and is consequently not permitted. The front workplace should monitor guest and non-guest accounts to make sure they stay inside acceptable credit limits.
A handful of years back, you could soft mod a GeForce and make it consider it was a Quadro, run the Quadro drivers, and POW, you got yourself a higher-end CAD Graphics card for peanuts, but the hardware vendors tweaked the hardware only slightly so you can’t do that anymore and they’ve added a lot more Graphics RAM which was good of them to do. Can be utilised as a server for low level applications, I utilised HP Workstation xw6200 as an imaging server in the past. Client server networks supply centralized backup exactly where data can be stored in one particular server. You can set up a considerably organized and specialist operate environment by going for workstations. These Workstations deliver high functionality and reliability with the latest innovation and market leading technologies, along with offering expandability, properly beyond standard computers’ capabilities and at entry price tag point.
In fact, PACS workstations are primarily PCs that are tied into PACS systems the only difference is the software program employed. Requires DisplayPort 1.2a compliant monitors that support DisplayPort Adaptive-Sync and an AMD FirePro W5100, W7100, W8100 or W9100 graphics card with the AMD FreeSync technologies-enabled 14.502 driver or later. “The Victorian WorkSafe Officewise Guide” can be utilised to supplement the data in the University’s ‘Computer Workstations: Design and Adjustment Guideline’. Prime-of-the-Line Power and Performance: The HPZ840 Line As you can envision, the HP Z840 line of workstations caters to an even greater-end clientele: serious company experts who want the utmost in speed, stability, and efficiency from their machines.
Computer desks are an integral aspect of your property workplace furniture and provide a contemporary accent to your décor. You can upgrade practically almost everything in it. You also would not genuinely need to have the 3 x 6TB SATA HDDs for further storage, you never have to use a 24GB NVIDIA video card, you also don’t have to use a 2nd Intel Xeon Core or 128GB of RAM. HP’s reinvention of detachable PCs began earlier this year with the introduction of the HP Spectre x2 and the HP Elite x2. Today’s introduction of the HP ZBook x2 completes HP’s trifecta with its most strong detachable solution targeted for the inventive neighborhood. The huge keyboard tray featured in this workstation can fit a complete size keyboard and a mouse. Both hardware approaches supply sturdy security for administrative accounts against credential theft and reuse.
The activation server reported that it failed to insert item essential record. This is why we supply a wide range of computer desks, made in a variety of different materials, sizes and styles, so you are going to have a lot of possibilities to choose from to kit out your property or workplace atmosphere – and all at cost-effective costs. Our metallic closets supply a extremely wide range of items addressed to distinct users: factories, offices, schools, laboratories. The Computer software Licensing Service determined that the requested event is not registered with the service. Occasionally workstations will not appear in this list so what follows is a discourse on feasible motives for this. They are also excellent for those who often need to sit back or recline although thinking or viewing and so on. The low back chair is for offices with less space.
Regardless of whether you’re an engineer designing intricate 3D models, designing complex mechanical subassemblies, performing Finite Element Analysis (FEA), Computational Fluid Dynamics (CFD),calculating sophisticated geometry or even rendering high resolution imagery. The capacity to boost your performance by using a single of your PCIe slots, no other pc program does this. Next year, you’ll be in a position to go higher nonetheless with the 8180M processors very same core count and speeds, but doubling the total memory capacity to 3TB, as extended as you want to fill the machine’s 24 RAM slots. Offer a high-security workstation to administrators so they can effortlessly execute administrative tasks. Administrative Privileges the PAWs supply improved safety for high effect IT administrative roles and tasks.
This signifies that Avid chooses HP Workstations to develop, test, and demo their strong, cutting-edge software program and hardware items. But the thought that an Net service provider (ISP) would make worth judgments about the packets traveling more than its network tends to make numerous men and women uneasy. HP Z Workstations also function third-generation PCI Express technology, giving consumers enhanced performance and seamless integration of new graphics cards. The administrative account(s) must only be utilised on the PAW administrative operating method. The new test system came equipped with two of Intel’s new Xeon E5-2687W eight-core CPUs, based on the 32nm Sandy Bridge architecture. For a common man cabling is just a bunch of wires nonetheless, in professional terms, it is the foundation of a good voice data cabling infrastructure in which two or a lot more computer systems & servers are connected with each other.
Guest can settle the bill by paying money, charging the balance to a credit card, deferring payment to an approved direct billing entity or utilizing a mixture of payment techniques. Office workstations offer you a number of supplies, colors, designs, and finishings that imply each office space can achieve a seemingly endless array of types. Though the transactions have to be posted to the proper account as soon as they are received, the evening auditor have to confirm that all the transactions received by the front workplace for posting are been posted, ahead of beginning with the audit routine. See how NASA is utilizing HP Z Workstations to aid enable sustainable living for deeper voyages into space. At the heart of the method is the Intel Mobile i7 quad-core CPU, which delivers exceptional higher-def multimedia, multi-tasking and multi-threaded functionality.
In an automated technique the folio remains in the computer and a challenging copy is printed out only at the time of guest verify out. , the budget as nicely the cautious use of the space to make working less complicated with the most stylish workplace a single can believe of. All of it is quite easy with valued guidance and the proper furnishings house which make your office stand out in the market. Not only that, but it is also the case that effectively developed office furnishings requires into account numerous of the niggling concerns and troubles which can occur with some of the less costly, significantly less properly planned office furnishings options. Regardless of whether you basically need to have new workplace workstations, or regardless of whether you are in search of to relocate to a brand new office, DY Constructions Australia have the abilities, expertise and expertise to provide you a comprehensive office fitout answer.
At least, every single day, lists of guests with higher danger or high balance accounts shall be communicated to all point of sale outlets. The answer is because Intel created a superior CPU register architecture, which allows for more quickly application execution, by means of far more efficient routing of information among their CPUs’ internal registers, and a lot more efficient CPU guidelines and information allocation amongst CPU cores. Given that Windows would not let me to overwrite the driver file because a more recent version exists on the pc, I went to the newly installed printer (in printers) appropriate clicked and went to properties, advanced, updated driver utilizing Windows update, which installed the correct driver for the 24″ Z3200.
Most organization PCs come with integrated graphics—that is, video capabilities that are built into the computers’ AMD or Intel processors. The potent HP t410 All-in-One particular (AiO) Smart Zero Client, featuring new and revolutionary a single-wire Power more than Ethernet (PoE) technologies whilst nonetheless supplying outstanding multimedia efficiency and a true Pc-like experience. Windows 10 Pro gives further functions like getting total stranger Remote Desktop Connections, file encryption, and domain participation. Altra has a plethora of furnishings possibilities but specialize in the entertainment category such as home theatre systems, Tv stands, office desks, and the like. Fortunately, upgrading your storage capacity is one particular of the easiest alterations you can make to an existing workstation Computer. If you’re on a price range, adding much more storage is effortless any time, and it constantly gets less costly over time.
Whilst accessing the difficult disk, a disk operation failed even soon after retries. Even if a network is comprised of only two computer systems, a server is outstanding for storing and sharing files for those two computers. Windows ten is Microsoft’s most current and, ostensibly, last version of its desktop and mobile operating system. Zero client solutions save funds and time for any college, organization or consumer that desires to offer you person computing experiences to numerous people without having buying multiple PCs. This develop sports an unlocked i7 processor, with the highest single-threaded functionality of any CPU. Personal computer assistance solutions specialists take up the consumers queries from their workstations by means of the process named as remote desktop connection.
Whether you perform from property or you function in an workplace, take your space to a whole new level by browsing the large choice of house and workplace desks at HSN. Space-conscious desk designs are a huge deal these days. In addition, the ActivWorkstation Service Manage Daemon can distribute data to the AWS as nicely as ISV applications with no the need to pay double exchange fees. This float wall desk is easy to mount to any wall type and can be utilized as a full desktop station or writing desk. There’s HP Help Assistant, HP Software program Setup, and HP SoftPaq Download Manager. In the following days, he created his personal sensible card and programmed it to behave exactly like a reputable San Francisco card – the difference was only that Grand was capable to set the worth to whatever he wanted.
Space saving wall mounted personal computer workstation combo with VESA compliant monitor holder, CPU holder and function surface desk with T-molding. The issue here is that unless your are familiar with CAD workstations and the requirements of the software that runs on them, it is quite simple to make a costly mistake and get entirely the incorrect method. Both are quite potent GPUs and need to be a lot more than capable of accelerating demanding 3D CAD applications �� even even though they are not made to do so, as they are in fact meant for gaming laptops. Our CAD Workstations are assembled with the newest Intel processors for extreme rendering. AutoCAD can co-exist with such merchandise as a 2D drafting tool. At we affectionately refer to these types of office workstations as the “uncubicle”.
This is in addition to the current functions that currently permit Windows 10 users to sync reminders, notifications and SMS across their devices. I wouldn’t suggest NVidia graphics card, and I would advocate you to use Windows eight.1 or Windows ten. Just look through our variety or get in touch with us these days to discuss your wants and see how we can assist you generate your best workplace space. The University’s SOE is the supported computer software applications which users use to access Technology Solutions services. Students are taught how to use the laptop as a tool for tasks such as two-D drafting, three-D modeling and straightforward CAD associated programming. To make the most of the unbelievably low-cost Xeon E5-2670 processor you are really going to want two on a Dual Socket R (LGA2011) resolution.
We Design Custom Desktop Computer systems and Workstations for Auto CAD, Solidworks and Revit. One of the overlooked benefits of these mobile workstations is that the usually little surface location forces you to clean up all the clutter that normally compromises a larger, classic desk surface. Well…I enjoy workstations so a lot that I have had to expand my storage space and uncover a way to organize that makes it possible for me to quickly locate and set-up 5-6 centers in about five minutes. I adore my Ergotron WorkFit-TL Desktop sit-stand workstation. The energy consumption throughout low load is high and therefore the battery runtimes clearly remain behind the possibilities in spite of the higher-capacity battery and Intel’s QuickSync Video cannot be utilised.
We have workstations and desks that fit appropriate in, wherever they are needed – whether that is in a child’s bedroom as component of a brightly-coloured homework haven, or inside the clean, minimalist lines of a higher-tech workplace. Produced for mobile inventive and design and style pros with the most demanding projects, exactly where compromise is simply not an selection. You can even see some offices going for Mac Pc as an alternative of Mac Laptops simply because it is very impressive and offers an workplace look. It empowered any policeman, at any location inside a mile of the South African Border, to search anybody, automobile or premises with out warrant. Most workplace desks have one particular or more drawers—handy for keeping workplace supplies.
The Computer software Licensing Service reported that the name specified for the Active Directory Activation Object is as well extended. AutoCAD’s native file format, AutoCAD DWG , and to a lesser extent, its interchange file format, DXF , have turn out to be de facto requirements for interchange of 2D CAD information. The positions of power which they occupy in the African planet enable them to act autocratically towards other Africans, specially when they have the help of the White community. As soon as you’ve established that your router is supported, and you’ve located and solved any discrepancies between what is listed as ‘officially’ supported and what is actually supported, it really is time to get your software program and hardware together to flash and configure your router into a Wi-Fi range extender.
The graphic card is capable of giving far more depth and sharpness to photos in Pc. A more quickly and a powerful graphics memory would ensure that the performance is enhanced commendably. I have graphic dilemma in this motherbord when i set up graphic driver some computer software are not functioning appropriately like – adobe photoshop, windows photo viewer and other graphic software. When it comes to a specialist graphics workstation nothing is more critical than understanding that what appears on-screen is precise and colour right. The new Xeon platform combines the raw functionality of ‘Sandy Bridge’ with up to 16 cores and 32 threads, which is 33% a lot more cores than had been available on Westmere. Of course, there a a lot of other parts of the workplace in which our products could create improvements for company owners.
Nowadays there is a wealth of office furniture accessible that is able to combine practicality with appearance, and functionality with comfort. Some of the solutions that we offer you include network and server support, installation repair and upgrades for your servers, network and system administration, documentation and education and repair, upgrades and installation of workstations and desktops. The default configuration in this PAW guidance installs administrative tools on the PAW, but a jump server architecture can also be added if essential. We are particular that we have the ideal remedy for any of your boardroom desks or home workplace desks specifications. Today’s GPUs are powerhouses and contain hundreds of person stream processors for massive parallel computing and almost everything from video transcoding, encoding, and editing get a speed enhance from stream processing.
Delivering help for up to 8 cores of processing energy, the HP Z420 in no way slows you down. In a lot of companies, existing “legacy systems” such as mainframes, Novell networks, minicomputers, and a variety of databases, are becoming integrated into an intranet. Small, side-by-side workstations are ideal for those who function on computer systems and never require significantly space for dealing with consumers. When it comes to selecting a workstation that delivers uncompromising overall performance, there is just no contest. Efficiency is critical to company good results so make positive you take a appear at the wonderful Fujitsu Celsius and Lenovo Thinkstation ranges. Shield corporate content by restricting access to Workstation VM settings like drag-and-drop, copy-and-paste and connections to USB devices.
Filed under: General Tagged: desktop computer, hp z workstation, workstations hp z420
from KelsusIT.com – Refurbished laptops, desktop computers , servers http://bit.ly/2AVxsmp
via IFTTT
0 notes
Text
Who Are the Shadow Brokers?
In 2013, a mysterious group of hackers that calls itself the Shadow Brokers stole a few disks full of NSA secrets. Since last summer, they've been dumping these secrets on the Internet. They have publicly embarrassed the NSA and damaged its intelligence-gathering capabilities, while at the same time have put sophisticated cyberweapons in the hands of anyone who wants them. They have exposed major vulnerabilities in Cisco routers, Microsoft Windows, and Linux mail servers, forcing those companies and their customers to scramble. And they gave the authors of the WannaCry ransomware the exploit they needed to infect hundreds of thousands of computer worldwide this month.
After the WannaCry outbreak, the Shadow Brokers threatened to release more NSA secrets every month, giving cybercriminals and other governments worldwide even more exploits and hacking tools.
Who are these guys? And how did they steal this information? The short answer is: we don't know. But we can make some educated guesses based on the material they've published.
The Shadow Brokers suddenly appeared last August, when they published a series of hacking tools and computer exploits -- vulnerabilities in common software -- from the NSA. The material was from autumn 2013, and seems to have been collected from an external NSA staging server, a machine that is owned, leased, or otherwise controlled by the US, but with no connection to the agency. NSA hackers find obscure corners of the Internet to hide the tools they need as they go about their work, and it seems the Shadow Brokers successfully hacked one of those caches.
In total, the group has published four sets of NSA material: a set of exploits and hacking tools against routers, the devices that direct data throughout computer networks; a similar collection against mail servers; another collection against Microsoft Windows; and a working directory of an NSA analyst breaking into the SWIFT banking network. Looking at the time stamps on the files and other material, they all come from around 2013. The Windows attack tools, published last month, might be a year or so older, based on which versions of Windows the tools support.
The releases are so different that they're almost certainly from multiple sources at the NSA. The SWIFT files seem to come from an internal NSA computer, albeit one connected to the Internet. The Microsoft files seem different, too; they don't have the same identifying information that the router and mail server files do. The Shadow Brokers have released all the material unredacted, without the care journalists took with the Snowden documents or even the care WikiLeaks has taken with the CIA secrets it's publishing. They also posted anonymous messages in bad English but with American cultural references.
Given all of this, I don't think the agent responsible is a whistleblower. While possible, it seems like a whistleblower wouldn't sit on attack tools for three years before publishing. They would act more like Edward Snowden or Chelsea Manning, collecting for a time and then publishing immediately -- and publishing documents that discuss what the US is doing to whom. That's not what we're seeing here; it's simply a bunch of exploit code, which doesn't have the political or ethical implications that a whistleblower would want to highlight. The SWIFT documents are records of an NSA operation, and the other posted files demonstrate that the NSA is hoarding vulnerabilities for attack rather than helping fix them and improve all of our security.
I also don't think that it's random hackers who stumbled on these tools and are just trying to harm the NSA or the US. Again, the three-year wait makes no sense. These documents and tools are cyber-Kryptonite; anyone who is secretly hoarding them is in danger from half the intelligence agencies in the world. Additionally, the publication schedule doesn't make sense for the leakers to be cybercriminals. Criminals would use the hacking tools for themselves, incorporating the exploits into worms and viruses, and generally profiting from the theft.
That leaves a nation state. Whoever got this information years before and is leaking it now has to be both capable of hacking the NSA and willing to publish it all. Countries like Israel and France are capable, but would never publish, because they wouldn't want to incur the wrath of the US. Country like North Korea or Iran probably aren't capable. (Additionally, North Korea is suspected of being behind WannaCry, which was written after the Shadow Brokers released that vulnerability to the public.) As I've written previously, the obvious list of countries who fit my two criteria is small: Russia, China, and -- I'm out of ideas. And China is currently trying to make nice with the US.
It was generally believed last August, when the first documents were released and before it became politically controversial to say so, that the Russians were behind the leak, and that it was a warning message to President Barack Obama not to retaliate for the Democratic National Committee hacks. Edward Snowden guessed Russia, too. But the problem with the Russia theory is, why? These leaked tools are much more valuable if kept secret. Russia could use the knowledge to detect NSA hacking in its own country and to attack other countries. By publishing the tools, the Shadow Brokers are signaling that they don't care if the US knows the tools were stolen.
Sure, there's a chance the attackers knew that the US knew that the attackers knew -- and round and round we go. But the "we don't give a damn" nature of the releases points to an attacker who isn't thinking strategically: a lone hacker or hacking group, which clashes with the nation-state theory.
This is all speculation on my part, based on discussion with others who don't have access to the classified forensic and intelligence analysis. Inside the NSA, they have a lot more information. Many of the files published include operational notes and identifying information. NSA researchers know exactly which servers were compromised, and through that know what other information the attackers would have access to. As with the Snowden documents, though, they only know what the attackers could have taken and not what they did take. But they did alert Microsoft about the Windows vulnerability the Shadow Brokers released months in advance. Did they have eavesdropping capability inside whoever stole the files, as they claimed to when the Russians attacked the State Department? We have no idea.
So, how did the Shadow Brokers do it? Did someone inside the NSA accidentally mount the wrong server on some external network? That's possible, but seems very unlikely for the organization to make that kind of rookie mistake. Did someone hack the NSA itself? Could there be a mole inside the NSA?
If it is a mole, my guess is that the person was arrested before the Shadow Brokers released anything. No country would burn a mole working for it by publishing what that person delivered while he or she was still in danger. Intelligence agencies know that if they betray a source this severely, they'll never get another one.
That points to two possibilities. The first is that the files came from Hal Martin. He's the NSA contractor who was arrested in August for hoarding agency secrets in his house for two years. He can't be the publisher, because the Shadow Brokers are in business even though he is in prison. But maybe the leaker got the documents from his stash, either because Martin gave the documents to them or because he himself was hacked. The dates line up, so it's theoretically possible. There's nothing in the public indictment against Martin that speaks to his selling secrets to a foreign power, but that's just the sort of thing that would be left out. It's not needed for a conviction.
If the source of the documents is Hal Martin, then we can speculate that a random hacker did in fact stumble on it -- no need for nation-state cyberattack skills.
The other option is a mysterious second NSA leaker of cyberattack tools. Could this be the person who stole the NSA documents and passed them on to someone else? The only time I have ever heard about this was from a Washington Post story about Martin:
There was a second, previously undisclosed breach of cybertools, discovered in the summer of 2015, which was also carried out by a TAO employee [a worker in the Office of Tailored Access Operations], one official said. That individual also has been arrested, but his case has not been made public. The individual is not thought to have shared the material with another country, the official said.
Of course, "not thought to have" is not the same as not having done so.
It is interesting that there have been no public arrests of anyone in connection with these hacks. If the NSA knows where the files came from, it knows who had access to them -- and it's long since questioned everyone involved and should know if someone deliberately or accidentally lost control of them. I know that many people, both inside the government and out, think there is some sort of domestic involvement; things may be more complicated than I realize.
It's also not over. Last week, the Shadow Brokers were back, with a rambling and taunting message announcing a "Data Dump of the Month" service. They're offering to sell unreleased NSA attack tools -- something they also tried last August -- with the threat to publish them if no one pays. The group has made good on their previous boasts: In the coming months, we might see new exploits against web browsers, networking equipment, smartphones, and operating systems -- Windows in particular. Even scarier, they're threatening to release raw NSA intercepts: data from the SWIFT network and banks, and "compromised data from Russian, Chinese, Iranian, or North Korean nukes and missile programs."
Whoever the Shadow Brokers are, however they stole these disks full of NSA secrets, and for whatever reason they're releasing them, it's going to be a long summer inside of Fort Meade -- as it will be for the rest of us.
This essay previously appeared in the Atlantic, and is an update of this essay from Lawfare.
from Who Are the Shadow Brokers?
0 notes
Text
Smooth new Chromebook, first "Chromebox" desktop out from Samsung today Chrome OS window chief hits stable channel, disconnected Docs altering coming soon.
A year subsequent to revealing Chromebooks to the world, Google and Samsung today are reporting two new gadgets, including the primary "Chromebox" desktop PC. Google is additionally revealing a few noteworthy programming enhancements, including another window chief for Chrome OS, better trackpad bolster, moves up to a remote desktop get to instrument, and disconnected altering for Google Docs.
The new Chromebook has a slicker, more appealing outline than past models, and both the new portable workstation and desktop step forward in memory and CPU. Rather than Intel Atom processors, Samsung's most recent Chrome PCs utilize Sandy Bridge-based Intel Celeron CPUs, and twofold the RAM to 4GB. Both gadgets will be at a bargain online today and in Best Buy stores soon.
The Samsung Chromebook Series 5 550 has a 12.1" show with determination of 1280x800, begins up in around 7 seconds, weighs 3.3 pounds, is evaluated for six hours of battery life, and expenses $449 for a WiFi-just version and $549 for one with WiFi and 3G cell get to. Google says it's in regards to 2.5 times quicker than a year ago's models, while the Samsung Chromebox Series 3 will be 3.5 times speedier. The Chromebox, which costs $329 and has generally an indistinguishable size and shape from an Apple Mac Mini, runs quicker on the grounds that with battery life not being a worry, it can utilize a higher-wattage variant of the Intel Celeron processors.
The new Samsung Chromebook runs a double center Intel Celeron Processor 867 at 1.3GHz, contrasted with a year ago's Chromebook which ran a double center Intel Atom N570 at 1.66GHz. The Celeron design is more cutting-edge, and the portable workstation unquestionably appears to be zippy in our constrained testing up until this point. The Chromebox has an Intel Celeron B840 running at 1.9GHz.
The Chromebox has a decent number of ports, including six USB 2.0 ports and two DisplayPort++ openings that are good with HDMI, DVI, and VGA. Chrome OS is upgraded for screens up to 30 inches and can bolster numerous screens, Sengupta said.Oddly, the Chromebox has no SD card peruser, yet USB gadgets that can read SD cards are basic in any case. The new Chromebook has two USB 2.0 ports, DisplayPort++ yield, and a SD card peruser. Both the tablet and desktop have a Gigabit Ethernet port. Since the tablet is very thin, the Ethernet port opens up and bulges out a bit to fit the link.
While the PCs are less expensive than any Mac and numerous Windows PCs, despite everything we believe they're somewhat expensive for gadgets intended to run only one application: the Chrome Web program. In any case, Chrome gadgets are quick, and remarkably simple to utilize. Google and its equipment accomplices haven't uncovered deals figures, and critical piece of the pie doesn't appear to be prospective at any point in the near future. Be that as it may, Google is putting forth bolster bundles to organizations and instruction clients ($150 for organizations, $30 for schools, notwithstanding the gadget cost) and says the Chromebooks are demonstrating very mainstream in instructive settings.
Acer and Samsung both discharged Chromebooks a year prior, yet Samsung is the main equipment creator doing as such this time around. Be that as it may, Chrome OS Director Caesar Sengupta says Google is working intimately with Intel and hopes to have "a couple of more OEMs delivering not long from now."
Samsung has done well in conveying solid equipment, with an extremely responsive trackpad. At the end of the day, programming changes are expected to give Google any shot at increasing huge piece of the overall industry from Windows and Mac OS X. New elements being taken off today and over the new couple of weeks give a decent begin.
Disconnected Google Docs altering finally, Google Drive combination
Google used to permit disconnected altering of Google Docs through a Google Gears expansion, yet murdered the venture with the guarantee of conveying disconnected usefulness locally through the program. Disconnected survey capacities were brought back last September and altering is coming at some point in June, Sengupta told Ars. Any progressions made while disconnected will synchronize with the Google server once a client picks up an Internet association.
"Disconnected survey has existed for some time, however the Docs group is preparing the arrival of disconnected altering," Sengupta said. "We are utilizing this inside at Google at this moment and we are going to bit by bit move clients throughout the following a little while."
Disconnected altering of Docs will be accessible in all forms of the Chrome program, not only the one for Chrome OS gadgets. No different programs are upheld right now, however Sengupta didn't discount it the length of contending programs utilize comparative HTML5 innovation. Google is utilizing IndexedDB to store records locally when an Internet association is disjoined.
Two different augmentations help on the disconnected archives and capacity fronts. New survey abilities permit opening of Microsoft Word, Excel, and PowerPoint documents in a program tab, on the web or disconnected. The documents can be seen without Google Docs, in spite of the fact that altering requires Docs. Chrome OS is likewise being incorporated with Google Drive, the new distributed storage benefit with 5GB of free stockpiling. Drive mix is incorporated with the Chrome OS improvement discharge, and will hit the steady direct in mid-to-late June, Sengupta said. Since Chromebooks contain 16GB strong state circle limit, a client's Drive records will be stored locally.
Chrome OS, now with more windows
We as of late posted a top to bottom examination of Google's new Aura interface for Chrome OS, a window supervisor that makes Chromebooks act significantly more like the Windows, Mac, and Linux PCs individuals are utilized to. At the point when Chromebooks first turned out a year ago, they upheld review of just a single program tab at any given moment so you proved unable, for instance, sort in a Google Doc and view a different website page in the meantime. Concurrent review of numerous program windows was included inside a couple of months, and the more strong Aura interface hit the Chrome OS engineer direct in April of this current year.
Today, Aura turns into the standard interface for Chrome OS as a component of a working framework refresh. Interestingly, this gives Chrome OS a graphical UI that exists outside of the program, in spite of the fact that it's still exceptionally Web-driven. There's a symbol for a record supervisor, however generally the "applications" recorded are connections to sites. Clients can in any case fill the entire screen with the Chrome program just by clicking a little box at the upper right of the screen.
In spite of the fact that Aura is satisfying to the eye, it doesn't change the way that Chrome OS's greatest restriction is as yet its constrained handiness when a client does not have an Internet association.
Better trackpad programming and remote desktop get to
As said before, the Samsung Chromebook has an extremely responsive trackpad, effectively perceiving tap-to-snap, looking over, and the two-finger click. We give Samsung a significant part of the acknowledge for this as its trackpads are by and large great paying little mind to which OS is running, however Google says it has enhanced trackpad bolster on the product side too.
"Our trackpad a year ago was a bit fiddly," Sengupta said. With numerous Googlers utilizing the Chromebooks inside, Google embarked to investigate the issues that can be brought about by contrasts in individuals' thumbs and fingers and how they click. Google even utilized mechanical thumbs and fingers to copy one of a kind digits.
"A few people have thumbs that have a midriff in the center. They're accustomed to laying it on the trackpad thus they click with that and it would appear that two changed focuses," Sengupta said. "We now find out about thumbs than we at any point minded to know. We understand individuals come in various shapes and sizes."
Enhancements to trackpad bolster advanced away from any detectable hindrance source Chromium OS as another segment.
One final programming change declared by Google today is a move up to Chrome Remote Desktop, which we tried out last October and gives a remote desktop association between two PCs running the Chrome program. This would let a Chromebook client get to any Windows, Mac, or Linux machine, however it required a man on every PC to sort in a get to code, restricting its utilization for really "remote" situations. Google says it is presently propelling a relentless association, enabling a client to set up the remote desktop instrument just once and have it be open from that point on.
Business and school selection
As indicated by Google, more than 500 schools have bought Chromebooks and are utilizing them in educational modules. Recently declared clients incorporate Dillard's, which will convey many Chromeboxes to retail locations; California libraries, which will utilize 1,000 new Chromebooks for benefactor checkout purposes; Mollen Clinics, which will send 4,500 Chrome gadgets to portable inoculation facilities at Wal-Mart and Sam's Club stores; and Kaplan, which is utilizing them in a New York City call focus.
Google is seeking after a greater push into organizations and schools with its $150 per-gadget bolster charge for organizations and $30 per-gadget for schools, which incorporates day in and day out telephone bolster, an administration comfort, and an equipment guarantee. The bolster cost is notwithstanding the normal retail cost of the gadgets. Google used to pitch support to organizations and schools with a month to month membership show. The new evaluating is a one-time in advance cost with support for the lifetime of the gadget.
We don't know numerous consistent customers purchasing Chromebooks, yet Google has a convincing pitch for organizations with representatives that utilization just Web applications, or are happy with getting to Windows programs through Citrix's virtualization programming. Call focuses, back workplaces, retail locations, and other "non-portable" situations are useful for the Chromebook and Chromebox, said Rajen Sheth, Chrome for Business Group Product Manager.
Google has additionally upgraded Chrome OS for organizations, enabling the gadgets to consequently design applications, arrange settings, WiFi, VPN get to, and authoritative approaches, Sheth said.
0 notes
Text
Arplis - News: Plan Simons Hardware Nyc


54 reviews of Simons Hardware & Bath I decided to pay a visit to family-run Simons after having frustrating experiences . Photo of Simons Hardware & Bath New York, NY, United States . didnt have any info on sizing, so he snarled that I could call the company if I didnt trust him. best idea he had. . United Kingdom. Simons Flagship. 421 Third Avenue New York, NY 10016. Tel: 212.532.9220. Fax: 212.481.0564 . Simons SoHo. 481 Washington Street New York, NY 10013 Mon: 8am 5:30pm. Tue: 8am 5:30pm. Wed: 8am 5:30pm. Thu: 8am 7pm. Fri: 8am 5:30pm. Sat: 10am 5pm. SoHo 481 Washington Street New York, NY. New York Citys oldest hardware store, Simons is a treasure trove of decorative and architectural hardware as well as kitchen and bath. A one-stop-shop for. Founded in 1908, Simons Hardware & Bath is New Yorks luxury hardware and plumbing retailer. Visit our 2nd showroom at 481 Washington St, NY, NY 10013!. 421 3rd Avenue . At Simons Hardware and Bath, we can turn any idea into a dream come true! A big thanks United Kingdom, 86444, Vodafone, Orange, 3, O2. Download this stock image: Door Key, Handle and Lock Display, Simons Hardware & Bath Store, NYC, USA F2WK8P from Alamys library of millions of high. Find the perfect simons hardware stock photo. Huge collection . Custom Knob Display, Simons Hardware & Bath Store, NYC, USA Stock Image Custom Knob. Title: Luxe Magazine March 2017 New York, Author: SANDOW, Name: . Lighting Kitchens Bath Decorative Hardware Tile & Stone . the editors of Luxe Interiors + Design, featuring ideas, trends and happenings in luxury home design. new book I am planning this year on the stables and barns of the British Isles. Volume 58 Supplement 21: Concept-Based Indexing and Retrieval of . E. P. Dvorin and R.H.Simmons, From Amoral to Humane Bureaucracy, Canfield, . Policy and the Crisis of Public Authority, W. W. Norton, New York, 1969. . R. E. Flathman, The Practice of Rights, Cambridge University Press, Cambridge, U.K., 1976.

54 reviews of Simons Hardware & Bath I decided to pay a visit to family-run Simons after . Photo of Simons Hardware & Bath New York, NY, United States. 3 reviews of Simons Hardware & Bath SoHo Simons has very kind employees! . Photo of Simons Hardware & Bath SoHo New York, NY, United States. Simons Hardware & Bath 421 3rd Ave, New York, New York 10016 Rated 4 based on 7 Reviews The salesperson could not have been ruder. Didnt want to. Founded in 1908, Simons Hardware & Bath is New Yorks luxury hardware and plumbing retailer. Visit our 2nd showroom at 481 Washington St, NY, NY 10013! . Our brilliant staff worked hard in creating a custom built, freestanding glass. simons hardware Traditional Kitchen Remodelling ideas New York Built-in . Home Tours Beth and Charles Fowler Bright Bold and Beautiful Upstairs. Title: Luxe Magazine March 2017 New York, Author: SANDOW, Name: Luxe . THE REPORT Get inspired by the brilliant rainbow of possibilities in our color guide, Simons Hardware & Bath 212.532.9220 New York simonsny.com. simons hardware Traditional Kitchen Remodelling ideas New York Built-in refrigerator . doors marble backsplash mixer nickel hardware shaker spotlights traditional Traditional . Tips for Surviving a kitchen renovation Beautiful bright kitchen. Decorative Hardware Simons Hardware and Bath . strips of cloth, unique fabrications, brilliant colors and strategic placement within the home. . Visit Simons Hardware & Baths 2nd showroom at 481 Washington Street, New York,. Come to SImons Hardware and Bath today to see our brand new display of THG Collection: Virage Finish: Brilliance Polished Nickel Product: Sensori High . The Greenwich, part of the New York Collection is inspired from structures of.

HWMonitor is a hardware monitoring program that reads PC systems main health sensors : voltages, temperatures, fans speed. The program handles the most. HWMonitor PRO is the extended version of HWMonitor. In comparison to its classic counterpart, HWMonitor PRO adds the following features : Remote. 10 de mar de 2018 . many of the components inside the average computer move at incredible . HWMonitor is a system hardware monitoring application that has. XFast 555 was been designed for incredible performance benefits and guard your system by hardware monitor function and overclock your hardware devices. The free Open Hardware Monitor software runs on Microsoft Windows with the .NET Framework version 2.0 and above. On Linux systems the Open Hardware. 28 de jul de 2016 . widgets left Windows with the end of the sidebar, but theyve always been available with third party apps like the always-incredible Rainmeter. . of the full resolution of the display. Many hobbyists in the HTPC community have voiced their frustration to the DVD publishers and to hardware manufacturers,. Every single game, cabinet and piece of hardware is an extension of the dedicated people who create and stand behind them. This is our incredible vision. Step one is to build awareness of how easy and cost-effective it is to handle and monitor IT today. Xllnc Finland is established. Maximum PC has been singing the praises of Sony monitors since time immemorial. . Now, were always happy to evangelize kick-ass hardware, but. . isnt better than the Sony F520, but at just two-thirds the price, its an incredible bargain.

25 de abr de 2018 In Windows 10, 7 und 8 solltet ihr Hardware sicher entfernen, bevor ihr USB-Sticks oder -Festplatten abzieht, um . Aktiviert diesen Schalter. 22 de nov de 2012 Es kann passieren, dass das Symbol fr Hardware sicher entfernen unten rechts in der Taskleiste fehlt. Diese Funktion lsst sich als. 17 de nov de 2017 Befolgen Sie diese Schritte, um Hardware von Ihrem Windows 10-Gert sicher zu entfernen. Menpfad: Setup > Zubehr > Hardware sicher entfernen . Startmen: Wenn die Option aktiviert ist, kann die Sitzung mit dem Startmen gestartet werden. 31 de jul de 2018 Es ist sicherer, auf Hardware sicher entfernen zu klicken, wenn Sie . Hardware sicher entfernen und stellen Sie sicher, dass sie aktiviert ist. 11 de jan de 2019 . hardware sicher entfernen aktivieren, hardware sicher entfernen . Amazon.com: Wood Fence Hardware Single Gate Kit (Wood Gate. Scenic road trip Seattle to Spokane, Washington: A Photographers Dream . available from any sporting goods . wonderful hardware sicher entfernen aktivieren. Shop stainmaster essentials beautiful design i hickory bark carpet sample at . Um den Punkt Hardware sicher entfernen zu aktivieren musst Du bei . 13 de dez de 2018 If your nearby paint, hardware or building supply dealer doesnt carry it yet or . 12 /09 /2018 Ist Hardware sicher entfernen auch aktiviert?

11 de fev de 2019 Wenn Sie einen Komplett-PC gekauft haben, wre es wichtig zu wissen, welche Hardware verbaut wurde. Wir zeigen Ihnen, wie Sie die. 24 de mar de 2017 Mchten Sie die Hardware Ihres PCs auslesen, ist das auf mehreren Wegen mglich. Wir stellen Ihnen in diesem Praxistipp drei Mglichkeiten. Hardware-Analyse Software berprft den Computer sowie das Netzwerk und zeigt den Zustand und die Leistung des Systems an. Die Diagnose Software. Door Stops Window Fittings, Knob Handles. Bolts Hinges Hooks Catches Fittings Hasp & Staple Door Furniture Window Furniture Knobs & Handles. Superb Member. Total Posts : 9326; Reward points : If so, then you have not selected PICkit3 as the hardware tool. However, if PICkit3 is not. 10 de jan de 2019 Sale windows 10 home 64 bit product key auslesen For Sale. . Not all of you agree Okay, thats superb; if you do not want to work with . Microsoft will recognize your system hardware and validate the installation, provided. 4 de abr de 2017 Den Fehlerspeicher Ihres Autos knnen Sie recht einfach selbst auslesen. Sowohl die Kosten als auch die Risiken sind gering. Wir zeigen. HI, ich wollte mal wissen ob man das Steuergert so auslesen kann, das man . was die Software und Hardware angeht einzig die Variablen, also die und die Sharewareversion 3.11 nutzen, die reicht fr den Superb aus.

NIOD. Hylamide. The Chemistry Brand Chemistry Brand. The Ordinary. Fountain. HIF. Ab Crew. Coming soon. Abnomaly. Loopha. Hippooh. ENG User account. Its rare to find a skincare brand that works so well yet manages to keep the costs low. Find out just how The Ordinary manages to keep their products affordable. Shop The Ordinary The No-Brainer Set at Sephora. This set contains Natural Moisturizing Factors + HA, Granactive Retinoid 2% Emulsion, and Buffet. 22 de nov de 2018 But if youre a skincare addict, DECIEMs Black Friday deals are not to be . from NIOD, The Chemistry Brand and sell-out brand The Ordinary. 17 de jul de 2018 Check out our favorite Prime Day deals on all kinds of smart gadgets . Amazon Echo Look as you would an ordinary Alexa-enabled smart speaker. Netgears Mesh System uses multiple hardware units to blanket a large. . is any mapping and is the ordinary componentwise addition over GF(2). 3. . In the following we will have to deal with pairs of plaintexts, ciphertexts and. 2 de jan de 2002 Amazon sent out email to customers Wednesday offering them the opportunity . excess inventory, which is not out of the ordinary for any retail store, . Some of the hardware deals on the surface are outstanding, but in some. Qualihome Hardware Nail Assortment Kit, Includes Finish, Wire, Common, Brad . riveted look, or even to upholster out of the ordinary items like headboards. . lastly, at their arrival in Chili; in exchange they give their tallow, hides, some deals, . stuffs, linens, cambrics, and hardware, necessary to the ordinary wants of life. . to have been very well chosen; and the town has been judiciously laid out.
3.jpg. Como eu posso ativar a virtualizao, se disponvel mas desativada no meu computador? 2.1) Acesse a BIOS do seu PC para Windows 10, 8.1, 8 (BIOS. 20 de set de 2018 Mchte man mit seinem PC einen Emulationsprogramm wie zum Beispiel VMWare oder auch Bluestacks nutzen, um neben Windows 10 noch. 4 de jan de 2017 Ob die Virtualisierung aktiv ist oder nicht, lsst sich unter Windows 10 zwar anzeigen. Drcken Sie in Windows 10 die Tastenkombination. 4 de dez de 2016 Mein Kaspersky 2017 sicherer Zahlungsverkehr funktioniert nicht einwandfrei. Ich bekomme die Fehler- meldung Screenshot-Schutz ist.

Comprehensive Hardware Analysis, Monitoring and Reporting for Windows and DOS. In-depth Hardware Information, Real-Time System Monitoring, Reporting. Allows to display any HWiNFO sensor information on character based LCD screens . to support third party hardware and display system diagnostic messages). 6 de mar de 2019 HWInfo64 is an application that monitors your PCs components and outs computer information about your the operating system, storage capacity, and RAM. . HWiNFO is a professional hardware information and diagnostic tools supporting latest components, industry technologies, and standards. He had virtually retired from the wholesale hardware trade before he built Stone Lodge, and was now looking about for a suitable opportunity of making an. Gratifying. I miss the childrens voices. I wondered how many current grammar school teachers characterized their work as gratifying. You taught there? A less gratifying feature is the increase of loan societies, and the remarkable . Full information in reference to these societies will be found ina valuable paper. Information Technology and the Corrosion of Competitive Advantage N.G. Carr, . For me personally, the debate has been at once gratifying and frustrating. . both hardware and software, used to store, process, and transport information in. It is gratifying that PN can be used [3,6,9,10,1416,18,2022,24] also for systems where failures occur. There failures can be categorized into hardware failures. . information systems, computer science, and library and information science. . on influences: new waves of hardware enable diverse ways to support same.

Tag: hardwaredealz. By Jacynthe Baumbach special concept hardwaredealz Funny hardware sicher cozy paul b hardware lititz formalebeaut paul b. HardwareDealz Besides a cosy Italian restaurant, a lavish barbecue buffet and delicious pizza of course, the family resort offers a special childrens buffet with. breathtaking hardwaredealz . Cozy State Farm Charlottesville . Bathroom Vanity Trends for 2018-2019 Bathroom Interior, Diy Bathroom Decor, Cosy . 19 de jan de 2019 . sicher entfernen aktivieren, hardware sicher entfernen verschwunden, hardware+info, hardwaredealz, remu building & hardware supplies,. . 1 0.00% //lionslagospt.club/tag/best-sellers/ 1 0.00% 1 0.00% //lionslagospt.club 1 0.00% //lionslagospt.club/cosy-house/yum/ 1. Ich bin heute zusammen mit @hardwaredealz beim Shadow-Event in Berlin Einige von euch kennen den Dienst sicherlich schon, bald wird es aber noch.

29 de out de 2009 Investigate the Windows 7 Control Panel: The Hardware and Sound Category. 20 de out de 2018 Pool supplies, such as pumps, liners, and cleaning equipment and chemicals . mile to ensure your pool is both structurally sound, and. Processor, USB/Audio Interface and energyXT2.5 Compact . behringer.com. 2. Nox 101 2 Table De Mixage Behringer Luxe Dj Equipment Store Dj Table De . Block unwanted noise and light with affordable soundproofing curtains, panels and . . has soundproofing materials that provide the perfect noise reduction solution for any space or piece of equipment. . formalebeaut sound insulating glass. 200 results Jessica Shower Curtain and Hook Set features a colored scheme that . Moondreams reversible sound-insulating Room Divider Curtains use a Formalebeaut Pool Table Clearance Tempting Above Ground Fiberglass Pools . our entire window treatment collection which includes rods & hardware, blinds . formalebeaut kohls curtains and valances . Browse window treatments and hardware like curtain rods, curtain rings and finials . 3 pair, pewter Block the outdoor light and reduce exterior noise with the Baroque grommet top curtain panel pair. Color guard alumimum, fiberglass, and specialty flag poles . . is hard to interpret. . of special equipment, such as sabres, rifles, and flags, to compete by division. . We are an Authorized Dealer for DSI, Director Showcase, Styleplus, Sound . 19 de out de 2018 Pella garage doors come standard with finish, hardware and a Garage doors from Pella are available at select dealers and Lowes. . noise reduction. . door repairs, $190 Formalebeaut Swimming Pool Water Features.

Best Hardware Stores in New Kent County, VA Providence Forge Hardware, Ace Hardware, Quinton Hardware Building Supplies, Tractor Supply Company,. 9321 Pocahontas Trail Providence Forge, Va 23140. 804-966-9076 . SERVICING NEW KENT AND THE SURROUNDING AREAS. . Hardware &. Plumbing,. Phone, (804) 932-3434 Address. 3621 New Kent Hwy; Quinton, Virginia 23141. Experience the excitement at the all new Rosies Gaming Emporium. Enjoy historical horse racing (HHR) electronic gaming devices and more. 4370 jobs available in New Kent, VA on Indeed.com. Apply to Senior Customer Support Representative, Order Picker, Administrative Assistant and more! The annual budget document for New Kent County is organized into ten Equipping staff with computer equipment that is compliant with industry hardware and software satisfied with staffing labor and minimal third-party contractors. . were hard-edge abstractions based on the industrial forms of oil refinery hardware. . 1927 to 1952, when he moved to Taos, N.M.; he later moved to New York. . painting spare, minimalist landscape images on plastic grounds molded into the . and the Graves- end School of Art in Kent; came to San Francisco in 1952. Harvard Art Museums. Take a new piece of equipment, or an old favorite, and test it hard. LONG TRAIL Our tester was impressed w/J and minimal straps and buck: just fine . in sharp objects like climbing hardware and interesting rocks without having them poke me VA, USA 22905; (888) 219-8641; 150 dealers; catalog TYPE USAGE DO.

Heres every Toms Hardware article using the tag PC Builds. Also, see . Power User Profiles: A YouTubers DIY Dream PC With Matthew Perks. News 9 mo. 1 de jun de 2018 PC Builds; News. Power User Profiles: A YouTubers DIY Dream PC With Matthew Perks Any questions for the Toms Hardware Community? The goal of /r/hardware is a place for quality hardware news, reviews, and . I understand that this is a dream build from a very specific era, But I. There are so many things you want to do. Big dream projects. Small home renovations. Little to-do list items that you never seem to have the time to get done. 18 de fev de 2019 New Apple rumor is every fans dream come true . has laid out Apples hardware plans for the year in a huge note (via MacRumors), . This meme highlights some of the absolutely wild news stories that come out of Florida. garage door hardware, mailboxes, house numbers, and weather vanes. Additionally, there is architectural hardware such as finials, conductor heads or leader. 4 de jun de 2018 . hard, you could see the hint of hardware updates at Apple WWDC 2018, . the garbage can design was something out of a fevered dream, I assure . toads (dont lick toads kids), but we also got some sweet news about the. CVTE founded its Automotive Electronics Division in 2013. This team develops automotive networking products and services and focuses on providing. A desire for a better life in the future drives CVTEs continuous pursuit of new technology area. From wearable to home to travel, we continue to explore ideas in.











Arplis - News
source https://arplis.com/blogs/news/plan-simons-hardware-nyc
0 notes
Text
Core Higher Efficiency Laptop
Most Dell laptop and desktop computers will come with a handy utility already built into them for performing at least some kind of standard diagnostics when you want to do a small bit of preliminary troubleshooting. Just before buying your notebook Li-ion rechargeable battery, consider cautiously about load you spot on on yours Laptop Pc when you are away from the main energy provide electrical socket. Equivalent to all sorts of batteries, notebook Computer li-ion batteries comes in diverse varieties of designs and at a variety of rates The expense of a laptop Pc li-ion batteries will not constitute the power of power pack. Each and every time obtain li-ion batteries from a dependable supply. Laptop stores & few electronic retailers are better locations to purchase for equivalent batteries. Even diverse kinds of li-ion rechargeable battery may be employed for the Laptop, make positive that you observe and taken in to the regard guidelines that had been displayed in the instruction manual that came with yours notebook.
PCs have been on the market place for years now. The encounter and information gathered from that time has allowed developers to make the most efficient computer systems ever produced. Pc desktops nowadays are the result of decades of study and man hours in building them. This is a single of the most significant rewards. Although newer, more quickly technology such as the laptop could be convenient, they can not examine to the reliability of the Computer desktop. A continual energy supply is just one particular of the several factors why.
As computer systems are getting used on a large scale for communication and education, it will be really advantageous for the society as a complete if Dell is in a position to come together with other organizations in this space such as Microsoft and Google, to come up with joint initiatives that use new age technologies such as cloud computing, distance finding out and so forth to produce platforms so that people in far off locations exactly where they nevertheless do not have basic education facilities can use this to discover and upgrade their normal of living. These would be really good initiatives that would make sure that it is in a position to scale up its CSR activities and make certain that it reaches a large audience that increases the effect it has on the society.
youtube
Battery not charging – It often occurs that the battery of your laptop stops charging, creating it an ordinary, useless piece of box that can not be utilised for any goal. To fix this Dell pc problem, turn off the laptop and detach the charger. Now turn the laptop upside down and get rid of the battery by opening its case. If you don’t know how to take the battery out of your laptop, refer to the Dell documentation that came with your laptop. You can also go to the Dell web site for much more help on this topic. When the battery is removed, press and hold the power button for 7-10 seconds. Release it afterwards. Now put the battery back in the place, cover it, and then turn on your laptop. Connect the charger back and verify, it should work fine now.
Because high-finish game hardware was not extensively distributed, the company’s founders formed an OEM that sold pcs with the highest performing hardware and settings according to benchmarks. You obtain to get the peripherals and accessories you need which includes monitors, games, game controllers, keyboards, mice, and much more. They also sell all types of laptop parts and Computer elements like monitors, printers, CPUs, memory, graphics cards, motherboards, modems, CD drives, DVD drives, and tough drives, power supplies, video cards, sound cards and wireless networking hardware. Alienware is arguably the sexiest laptop manufacturer in the greater OEM area.
Probably the very first computer that may qualify as a “workstation” was the IBM 1620 , a little scientific computer developed to be utilised interactively by a single particular person sitting at the console. It was introduced in 1960. One particular peculiar feature of the machine was that it lacked any actual arithmetic circuitry. To perform addition, it required a memory-resident table of decimal addition guidelines. This saved on the price of logic circuitry, enabling IBM to make it low-cost. The machine was code-named CADET and rented initially for $1000 a month.
Dell’s recognition in the laptop and laptop situation has grown so significantly that no space in the computing situation seems devoid from its influence. Every single machine from the Dell loved ones has produced an ace position that customers trust and have complete faith on. From school going children to retired personnel’s, Dell finds significance in the life of all such folks. A dependable technical help is crucial to hold even the Dell machines working at their leading performance. Just to hold up to this expectation of customers, Dell delivers the Dell service support which is like an anytime assistance companion that any user can count on no matter what.
Titan Workstation Computers is proud of its unique and exceptional client service knowledge. The customer is at the heart of our enterprise model and we strive to develop relationships over and above basically selling products. As regular, all Titan Computers come with a two-year warranty on components,with the choice to extend this to four years. Our assistance even so, is a special lifetime service. Even soon after the warranty on your elements have come to an finish, you nonetheless enjoy access to help and labor from Titan Computers, for life. Our firm is serious about customer service. A representative is designated to you particularly, which indicates that you will deal with the same particular person every single time.
is an on-line magazine dedicated to computers. In contrast to PCMag (see above), TechNibble focuses on just computer systems and more specifically Pc repair. Their articles are more technical in nature and developed for IT staff people. With that stated, TechNibbles’ articles are readable by the each day user with only occasional mention of geeky stuff”. The Computer Repair Tools” is filled with little valuable utilities for eventually resolving a Computer dilemma. TechNibble is considerably lighter on advertising.
It is inevitable for a personal computer to face troubles as both go hand in hand. As your Dell pc becomes small old or you use it a lot more and far more, it tends to generate problems like slowing down or taking unnecessary time in the course of reboot or shutdown and so on. Though it is not needed that a laptop will constantly produce issues (soon after becoming old), but it could frequently want to be given technical doses or tweaks for larger overall performance, stability, and safety amongst other items. Since you have already sensed the difficulty and have decided to do a factory restore on your Dell personal computer, preserve this in thoughts that you will be necessary to do it a appropriate way as it is a sensitive procedure. The below described guide will aid you step-by-step to perform the factory restore settings on your own. This primarily means that you do not need to have to commit your time contacting your Dell tech Help services.
The final addition to the setup is the vSpace virtualization software which brings the remote virtual desktop atmosphere to life. When everything is set up and the host personal computer is powered up, the interconnected monitors will show the virtual Windows. A desktop Computer or private personal computer is normally powered by an x86 (either Intel or AMD) processor, runs Microsoft’s Windows operating technique, is connected to a monitor and the mains and is normally fixed. Yes, there are a myriad of other combinations (ARM-based and Android or the endless flavours of Linux), but we’ll stick to those for now.
But, if you are basically searching for a high end gaming pc or company Pc that will manage the demands of internet browsing, word processing and gaming, you never want a workstation. A larger quality Computer or gaming personal computer will do just fine. And, when you decide on your gaming personal computer from a business like Velocity Micro, you can make certain find that every single element is very carefully tested just as workstation parts would be. Vinnit Alex is properly recognized author who provide helpful details about get brand computer systems, laptops such as Tablet pc, Hp Desktop price list and Acer Desktop computer price tag list, by way of Online Shopping on Naaptol.
eBay and other auction sites do not accept Dell coupons. But the fantastic thing about visiting these web sites is the amount of discounts you can get by bidding on Dell merchandise. They are typically auctioned at a relatively decrease rate when you examine this to the costs in your regional laptop stores. Want pink colored laptop accessories for your new notebook laptop? Some areas on the web such as Amazon or even pc companies themselves (Dell, HP, Sony) could offer you a pink mouse, pink travel keyboard, a pink laptop case or bag, and other pink colored accessories for your laptop.
Size, then, becomes a great advantage. Even though technology is making items smaller sized, not all chips or processors can fit into the shells of smaller sized non-desktop computers. This puts pc desktops on the cutting edge of technology, as they get newer advancements initial, and then miniaturization can take place for other machines. Truly, to be as sophisticated as attainable 1 should own a Computer desktop. Dell is identified to give the most worth-for-income cost. Simply because manufacturing of Dell computers is accomplished overseas, they are able to sell their computers at a low expense. Even so, there have been recent reports of Dell computers smoking and burning, and folks are becoming more cautious in acquiring Dell items.
That only scratches the surface of what tends to make up a Dell DJ. The term could just have easily have been HP (Hewlett Packard) DJ, but somehow that doesn’t sound as smooth as Dell DJ. Dell, of course, being the personal computer business. The name Dell implies that the Dell DJ is progressing forward with technologies such as computers. The system supplies the acceptable IT Technician a single replacement desktop, laptop or tablet personal computer every four years for every Complete-Time employee position and pc lab space on campus. The plan does not supply workstations for new positions, new lab places, new office areas, student assistants, graduate assistants, contractors or volunteer positions. For each workstation provided by the plan, a single four-year old workstation should be removed from service.
Looking for a mobile laptop workstation or personal computer cart for your classroom or workplace? Check out our designs and great rates by clicking on any of these photographs. Select from prime brand name pc workstations including Bretford, Luxor, H.Wilson and Balt. A workstation Pc is a subset of the desktop Pc family members. They are primarily used by engineers (in the widest interpretation of the term), analysts, designers, content creation pros, developers and anybody that calls for information manipulation with a powerful visual slant.
This executive Workstation Personal computer is built about the Corsair 330R Quiet Tower Case. As often we replace Antec’s noisier fans with ultra quiet Nexus® case fans and we use exclusively fanless video cards to hold the Computer completely silent. A couple of years ago, the options have been reasonably clear. Individual computer systems didn’t do considerably, but they did it conveniently and cheaply so-named workstation computers—from Sun, for example, or Apollo—did a lot far more, but did it for 10 instances the price tag and the huge machines that did virtually anything, price a small fortune and necessary abundant technical support.
Software program applications for most individual computers contain, but are not limited to, word processing, spreadsheets, databases, Net browsers and e-mail clientele, digital media playback, games, and myriad personal productivity and particular-objective software program applications. (48) The Director, Technology Solutions is responsible for ensuring that the Laptop Workstation Policy is observed with regard to the solutions under the handle and management of Technology Solutions. Dell utilizes business-to-consumer e-commerce and business-to-company e-commerce. But mostly utilizes business-to-consumer e-commerce, which implies they sell their items and services to customers who are primarily folks. Clients are hoping to purchase computers straight interact with Dell. But on the other hand, Dell sells their products and solutions to customers who are mainly into organization. So Dell also utilizes business-to-enterprise e-commerce.
Vinnit Alex is a effectively identified author and has written articles on Laptops, Pc shop, Dell Laptops, online shop and numerous other subjects. Here are two strategies for purchasing computer systems from Dell that will save you hundreds of dollars every time. The first step, with each methods, is to choose what you actually need to have to do with the personal computer. If you want to edit video, that needs a lot much more horsepower than sending e mail photos to grandma. And a replacement computer at the office has various requirements than a house machine.
DELL style has usually been comparatively calm, specially to the enterprise computers, OpitPlex 745 using a tower case, the case is 1 of the biggest volume, stocky shape, and in accordance with the EU’s RoHS regulations, all use of non-lead production, plastic parts also had no halogenated flame retardants, and it did not use PBB, PBDE components. As a globe top supercomputer provider we are solely focused on delivering systems that give an ultimate knowledge in Each and every specialist application. Our specialist method engineers strive to maximize the overall performance and stability of each and every item we build to aid improve your workflow and increase production. This worth aids decrease business expenses and provide a better return on investment to make you each financially and creatively efficient.
Filed under: Tagged: laptop, workstation, workstations
from KelsusIT.com – Refurbished laptops, desktop computers , servers http://bit.ly/2yW1D8j
via IFTTT
0 notes