#atm hacker simulator
Explore tagged Tumblr posts
Text
營銷短片「不推銷、不拉人」新直銷模式!前工程師用DAO架構月收7位數被動分潤0985561212
課程預定5營銷「不推銷、不拉人」新直銷模式!前工程師用DAO架構月收7位數被動分潤
以下是針對「『不推銷、不拉人』新直銷模式!前工程師用DAO架構月收7位數被動分潤」主題設計的深度解析文章,結合Web3技術、去中心化組織與自動化分潤革命,專為厭倦人脈榨取的創業者打造:
「『不推銷、不拉人』新直銷模式!前工程師用DAO架構月收7位數被動分潤」
「當傳統上線還在開洗腦大會,我的智能合約已把全球消費者變成『活體ATM』——這才是直銷的賽博朋克進化。」
前微軟區塊鏈工程師張景安,2024年創建「DAO直銷協議」,實現完全零推銷、零拉人的自動化分潤系統,單月被動收入突破387萬台幣。他冷笑:「在Web3世界,人脈是最不值錢的資產。真正的金流藏在代碼的血管裡。」
一、傳統直銷的癌末診斷:你只是個人肉路由器
![對比圖表|傳統直銷 vs DAO直銷 人脈消耗量/分潤速度/法律風險係數]
張景安列出直銷商必死的三大數學公式:
人脈衰減率:(初始人脈)^(層級數) = 指數級枯竭
時間詛咒:收入 ∝ 工時,無法脫離線性增長
道德熵增:每發展1名下線,社會信用-17%
覺醒數據:指標傳統直銷DAO直銷每萬元收入所需人脈83人0.4��(AI虛擬客戶)分潤到帳時間45天8.3秒組織崩潰率68%(3年內)0%(智能合約永久執行)
二、DAO直銷三大核心模組:把組織寫進區塊鏈基因
🖥️ 模組1. 代幣化貢獻證明
開發者、推廣者、消費者皆鑄造專屬NFT
貢獻值以ERC-1155代幣即時結算: ✓ 轉發貼文 = 0.3 MLM✓產品體驗=7.8MLM✓產品體驗=7.8MLM ✓ 漏洞回報 = 42 $MLM
代幣可在Uniswap即時變現
🤖 模組2. 自動化裂變協議
客戶購買產品時,智能合約自動空投「推薦NFT」
NFT持有者永久分潤該客戶未來消費的3.7%
分潤路徑自動生成「貢獻樹狀圖」,消除人為糾紛
🌐 模組3. 去中心化自治法庭
用Snapshot平台投票決定產品/分潤規則
爭議處理由AI仲裁員執行,消耗$MLM代幣作為燃料
惡意行為者遭「鏈上社會性死亡」(地址被永久標記)
三、實戰案例:把保養品官網變成DeFi礦池
🧴 產品:區塊鏈精華液(內含NFT晶片)
⚙️ 運作機制:
消費者掃描產品獲得「皮膚數據代幣」
數據上傳至IPFS,科學家競標分析權(支付$MLM)
分析結果自動生成「個人化保養方案」並上鏈
每次方案被採用,消費者獲得$MLM分潤
💸 獲利結果:
早期用戶累積獲利達投入金額的17倍
87%利潤來自「被動數據貢獻」而非主動銷售
開發者藉由協議稅收月入214萬
四、暗黑增長策略:讓客戶自願成為永久分潤零件
🕵️♂️ 策略1. 寄生式空投
在競品官網植入「代幣水龍頭」
用戶輸入競品會員帳號即獲$MLM空投
自動建立「貢獻綁定」,未來消費回流分潤
🤫 策略2. 沉默推廣協議
開發Chrome插件「Honey Tracker」
自動追蹤用戶瀏覽行為,靜默累積貢獻值
達到閾值時彈出「您有未領取的$MLM」
🎮 策略3. 遊戲化剝削
設計「貢獻值俄羅斯輪盤」DApp
質押$MLM猜測價格波動,輸家代幣流入分潤池
每局抽頭8.8%分配給協議持有者
五、軍火庫:DAO直銷必備黑暗工具包
🔧 Tool 1. DAO Maker
一鍵生成吸血分潤規則
內建「反偵測混淆器」規避各國傳銷法
🔧 Tool 2. Tokenomics Simulator
預演代幣暴漲暴跌劇本
計算最佳割韭菜時機點
🔧 Tool 3. Governance Hacker
破解競品DAO投票機制
植入有利己方的治理提案
🔧 Tool 4. Zombie Liquidity
將殭屍錢包轉化為做市資金
偽造交易深度吸引真實用戶
六、致命風險:你可能被反噬的3種死法
⚠️ 智能合約漏洞
競爭對手發動「閃電貸攻擊」抽乾資金池
解法:每月支付1.2 ETH聘請CertiK持續審計
⚠️ 監管核打擊
各國認定代幣為非法證券
解法:部署「法律殭屍網路」跨國跳板
⚠️ 流動性詛咒
代幣暴跌引發死亡螺旋
解法:設置「無情做市機器人」護盤
【叛逃指南】3步驟從直銷難民變DAO军阀
1️⃣ 毒化現有團隊
用公司資源測試Web3產品
將下線轉化為私域流量池
2️⃣ 鑄造黑暗代幣
在Polygon鏈發行$MLM
預留30%代幣控制協議
3️⃣ 發動政變
在現有社群拋「DAO改革提案」
時機成熟時分叉協議另立王國
最後警告 文末嵌入「DAO奴隸指數」測驗,高分者解鎖《協議叛變藍圖》,附註: 「當你的上線還在用Excel計算獎金,你體內的智能合約已開始倒數——毀滅或重生,現在是代碼革命時刻。」
敘事核彈
將直銷切割重組��可編程協議
揭露Web3如何將人性弱點代幣���
提供可立即發動的政變操作手冊
用「賽博叛客」風格包裝黑暗策略
植入反烏托邦式行動呼籲刺激焦慮
營銷解說「不推銷、不拉人」新直銷模式!前工程師用DAO架構月收7位數被動分潤
youtube
營銷短片「不推銷、不拉人」新直銷模式!前工程師用DAO架構月收7位數被動分潤
youtube
營銷短片「不推銷、不拉人」新直銷模式!前工程師用DAO架構月收7位數被動分潤 直
youtube
0 notes
Text
Yellow wood trailer theories
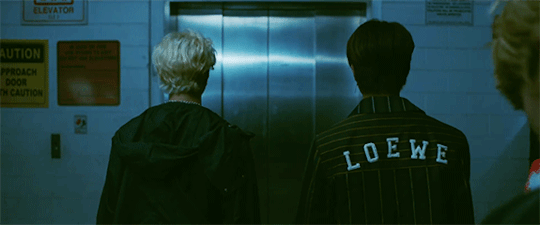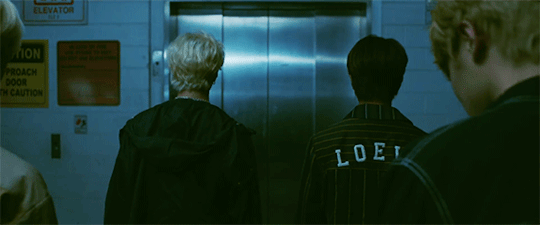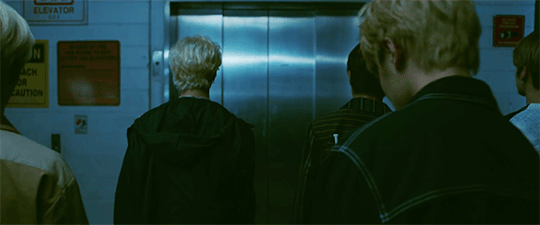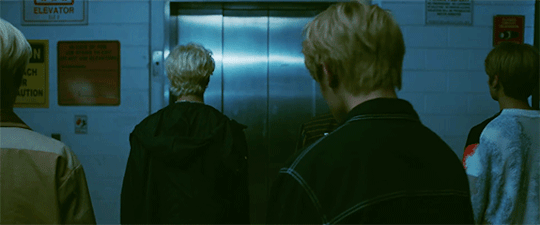
@cluelesssammie @curledlife I know you guys stan stray kids sooo I thought you'd enjoy these
(Grab some snacks cuz this is a long one and I'm on mobile so I can't cut it off)
theory #1- Exclusive to just Clé. Okay so we see stray kids on the elevator in which Chan presses the button and the doors open to reveal the parade from clé 1: Miroh, right? Then we see the doors close, Chan inserts the key, presses the yellow wood button, and the elevator plunges downwards. Clé translates to key and yellow wood is key two. I saw a YouTube comment on the trailer where someone said that the elevator could be time travelling, but I don't think that's it. I think the elevator is there for symbolism. In clé 1 (or key 1-this is important to remember): Miroh, skz take over the rally/parade. And going off topic for a second, what do keys open? Locks. Or more specifically, gates/doors. So what if Miroh is them using the first 'key' to take over the rally and thus completing the first challenge. Then we have clé 2: yellow wood. In theory, everything comes in threes (I am unaware if there's going to be more to this concept, but just roll w/ it for now). And usually, when stories use this method of three challenges or 'keys' in this situation, the first challenge goes well, but the climax rises (and falls) in the middle or the second challenge. (See where I'm going with this?) And we see the confusion and fear in the 'elevator' on some of the members faces, which shows that they didn't expect this to happen when Chan pressed the button. Which leads me back to the elevator. To me it seems like the elevator is like the 'loading screen' or non playable scenes in a video game that transitions one event to the next. The elevator is there to symbolize the second 'gate' not being what they expected and thus, being unprepared (cue the falling elevator). And since there might be people who'll ask 'Well what are the challenges or gates?'. My answer is, the 'gates' are figurative. We've seen throughout a lot of stray kids' concepts and comebacks that it's about the youth overthrowing the corrupt ideals of the older generation. In Miroh they take over the parade/rally, I think that's the first public thing they do as Stray Kids - underground youth organization. And since they've finished the first gate, they're moving into the second; Yellow Wood. I saw a tumblr user point out that yellow wood is used in a poem about the road less travelled (I can't remember their username atm). Now that they've established themselves publicly, this is when the real work begins. But I think the elevator falling represents that the next 'gate' is going to be challenging and hard work, but it'll be rewardful in the end (I.e the road less traveled). And you know what's challenging and hard work? Running a plan to overthrow the older generation.

Theory #2- Everything's a video game/simulation. Remember how I mentioned loading screens? Well it's coming back. This theory isn't necessarily based exclusively on clé 1 and 2, but somewhat revolves around get cool. In the 'get cool' mv they're seen as (I'm assuming) high school kids. Now based on their other comebacks, this doesn't fit their 'theme'. So if we go by assuming that their comebacks were out of order up until this point, this theory would make sense. So like I said, in get cool their simply high schoolers and high schoolers play video games. Let's say offscreen they find a video game series and decide 'hey lets have marathon to celebrate that finals are over' idk and the dark concepts represent themselves playing as their characters in the game. This would explain music videos like hellevator where the effects are somewhat outlandish.
Theory #3- Everything tells a story. In this we start off with 'Get cool'. They're a bunch of high schoolers just chillin and being kids (Chan is an upperclassmen compared to rest - important). Then hellevator and grrr law of total madness comes. This is when they start to question the ideals the adults around them have told them all their lives. Doubts start to get in their heads and they voice this to their parents, guardians or whoever. To which the adults don't like their children doubting the 'rules' and ignore it cuz they're just teenagers, they'll grow out of it. But they get dissatisfied w/ the dismissal of their concerns and this is when grrr law of total madness happens. They call out to Stays, or anyone that rejects the ideals and stereotypes adults and their parents place upon their shoulders. Albeit I.N isn't the genius hacker he is later (we'll get to that during Miroh), but it's enough for him to broadcast it to teens locally w/o it being on their parents devices. But, when the adults see the aggressive reactions these stray kids give them, they send them to a 'correctional facility' a.k.a District 9. And when Chan sees how the adults react, he stays quiet and gets a job at the facility. Now I think the reason as to why, is that Chan's seen this happen in the past. Thus, why we see him handing out the pills (?) instead of being a recipient like the rest. This is also why they make Chan the leader. He's experienced w/ this type of thing and he managed to break them out. But I have a theory (a theory inside of a theory, Jesus) that Chan doesn't give them the doses the 'doctors' prescribe and this allows them to be conscious of why they were sent here. Now after they've changed out of their white uniforms and into streetwear, Felix goes 'Stray kids everywhere, all around the world'. I think this is their second callout to stays, but this time, it reaches further. They're back and ready to fight, but this time, I.N is better and he manages to broadcast it internationally. Which, explains why Felix says 'everywhere all around the world'. They're growing bigger and now they're not just some rebel group, they're Stray Kids The Organization. Which leads us into My Pace. After district 9, they matured a tiny bit, but My Pace represents them maturing into the leaders stays need them to be and acknowledging their flaws, strengths, and that this'll take time to be successful. Also, note how they have more extras in the background, I think this could maybe show that this isn't just a ragtag group of teens anymore. (I'm not including the I am series, feel free to message for my reasons) This leads us to Miroh. I feel like this takes place a little further down the line compared to the rest. They've grown their ranks, became the leaders stays needed, and now it's time to take action. This starts with the rally/parade. This is when they go from rumors whispered between students to headlining on the news. When we see I.N monitoring the screens w/ his walkie talkie, sat phone thing, I think this is him making sure that this is broadcasting on every screen in the world. He's gone from local hacking to being a world renowned name on the web. The rest all have their own fields that they've specialized in , and this is Stray Kids. They've gone public, and now they start taking action. This leads to Yellow Wood. Now that they have announced their presence, the real work begins and it's going to be tough, but they are larger and stronger than they were before. And this can only take them further.
10 notes
·
View notes
Text
Embedded Security Market Size, Share, Analysis, Applications, Sale, Growth Insight, Trends, Leaders, Services and Future Forecast to 2025
The embedded security market is expected to reach a CAGR of 5.5% during the forecast period of 2020 - 2025. Embedded security solutions help manufacturers ensure their products and devices are protected from cyberthreats. In defense, security-based differentiation in their product are lined up using a multi-layer security approach. When the technology is mission-critical, the device has to perform with unerring reliability and predictability and cannot allow the compromise of data or security on the end-user system. Players are focused on integrating Linux, an open source-based hypervisor, and a secure boot solution in the defense sector. A player such as Wind River announced its acquisition of Star Lab in January 2020. The acquisition broadens the comprehensive Wind River portfolio with software for Linux cybersecurity and anti-tamper, virtualization, and cyber resiliency in the defense sector. - Growing IoT applications increases the need for IoT security, which drives the market. The IoT will consist of billions of digital devices, services, and other physical objects having the potential to seamlessly connect, interact, and exchange information. Security for IoT will be a critical concern that must be addressed in order to enable several current and future applications. The vital building blocks for embedded security for IoT is Cryptographic Algorithms and hardware architecture for extremely low power memory and processing requirements, Trusted Platform module, and Standardized Security Protocol. In April 2020, Sectigo announced a partnership with Infineon Technologies AG to provide automated certificate provisioning for Infineon’s OPTIGA Trusted Platform Module (TPM) 2.0 using Sectigo IoT Identity Manager. - The adoption of wearable devices in healthcare increases the demand for embedded security, which drives the market. Wearable devices are creating an increasingly large footprint in the healthcare world. As medical wearable technology is quickly expanding in applications and volume, there is an increasing need for strong, scalable, and cost-effective authentication between devices known as Machine-to-Machine (M2M) authentication. Intrinsic-ID and Maastricht Instruments are working together in the context of the European project INSTET to add advanced security in the medical wearable devices through SRAM Physical Unclonable Function (PUF). An embedded SRAM PUF in the MCU can be a giant step toward cheaper and more robust security.
Click Here to Download Sample Report >> https://www.sdki.jp/sample-request-86055 - However, the impact of Covid-19 on the market is restraining growth. The embedded security hardware market witnesses a significant decline in sales owing to the discontinuance of industrial activities and subsequently lowered demand for integration services and sales of new embedded security interfaces products. However, a player such as Mozilla announced in March 2020, the creation of a COVID-19 Solutions Fund as part of the Mozilla Open Source Support Program (MOSS). Through this fund, they will provide awards of up to USD 50,000 each to open source technology projects which are responding to the COVID-19 pandemic in some way where Mozilla will provide the embedded security solutions too. - Recently University of Florida Center for Safety, Simulation, and Advanced Learning Technologies released an open-source ventilator. Further, its Secure Open Source Fund supports security audits for widely used open-source software projects as well as any work needed to fix the problems that are found. Key Market Trends Automotive Segment to Witness Significant Growth - The vehicle car is rapidly becoming a large element of the IoT, connected by a variety of means to the outside world through an increasing number of wireless technologies. In the coming years, the market sales of connected cars will overpass the sales of traditional cars. While the benefits of improved connectivity are beneficial, it also opens up a sea of opportunities for digital invaders and malicious hackers to try to access the systems. According to Upstream Security's 2020 Global Automotive Cybersecurity info, from 2018 to 2019, there was a 99% increase in automotive cybersecurity incidents. - Effective automotive security is about integrating an embedded firewall, protecting communications, authenticating communications, and encrypting data, which helps to protect privacy. In April 2020, BlackBerry Limited announced the launch of QNX Black Channel Communications Technology, a new software solution that OEMs and embedded software developers can use to ensure safe data communication exchanges within their safety-critical systems and is certified to ISO 26262 ASIL D. - Further, in March 2020, Automotive Grade Linux (AGL), a collaborative cross-industry effort developing an open-source platform for connected car technologies, announces three new members: MERA, Mocana, and Osaka NDS. They planned to design plug-n-play solutions that integrate with the AGL platform to enable scalable, end-to-end security, to protect any AGL-based systems on-board connected or autonomous vehicles.
- Further, the advanced driver-assistance systems (ADAS) that are making today's cars safer and enabling the emergence of autonomous vehicles are challenging the automotive electronics industry to achieve new levels of complexity, performance, and safety. Also, according to Goldman Sachs, the market for ADAS is estimated to increase to USD 96 billion in 2025 from USD 3 billion in 2015. The unique demands of these applications led to the extensive use of complex ASICs that combine digital processing, analog, RF, and power management functions in single silicon die. As a result, critical safety features are managed on-chip.
- Further, in January 2020, NXP revealed its S32G (a single-chip version of two processors), an automotive microprocessor, and an enterprise network processor. The S32G functions as a gateway processor for connected vehicles, as it offers enterprise-level networking capabilities. It also enables the latest data-intensive ADAS applications while providing vehicles with secure communication capabilities.
- This new processor is already sampling, and car OEMs are currently testing S32G. Also, Audi director quoted that they found the unique combination of networking, performance, and safety features of the S32G processor to be ideal for use in their next-generation ADAS domain controller in Audi.
Request For Full Report >> https://www.sdki.jp/sample-request-86055 North America Accounted for Significant Share - North America accounts for significant share as the growing concern for the protection of critical infrastructure, and sensitive data has increased government intervention in recent years. Thus, government initiatives, such as specific budget allocations and mandated security policies, are expected to drive the market of embedded security in North America.
- Siemens Smart Infrastructure (SI) is transforming the market for intelligent, adaptive infrastructure for current and future adoption. It addresses the challenges of urbanization and climatic change through connecting the energy systems, buildings, and industries. To address this issue, in December 2019, Red Balloon Security has partnered with Siemens Smart Infrastructure (SI) to deliver enhanced cybersecurity for its building automation systems. This collaboration will initially feature embedded security for Siemens building automation controllers and will be deployed in 2020.
- Further, according to a recent IoT Analytic report, 50% of industrial assets in factories will be connected to some form of on-premise or remote data collection system. While IT and OT traditionally operated in two separate worlds, IT/OT convergence is opening up cybersecurity gaps in manufacturing organizations, leaving them open to attack because these devices usually don’t come with well-maintained or strong embedded security features. To address such issues, in December 2019, Pulse Secure and Nozomi Networks announced an integration that extends the zero trust protection provided by the Pulse Secure Access Suite to industrial IoT, ICS, and OT technologies.
- Furthermore, in November 2019, Red Balloon Security partnered with Nautilus Hyosung America to deliver enhanced security for its retail ATMs. Red Balloon Security identified two vulnerabilities related to retail ATMs, and one related to NHA’s retail ATM support mobile application. Following this discovery, Red Balloon Security has been engaged by Nautilus Hyosung America on embedded defense mechanisms providing issued firmware security updates to strengthen the security of their ATMs in the retail marketplace.
- Further, the new budget spending for Canadian infrastructure protection is marked at USD 144.9 million over five years, including Canada’s critical cyber systems, including sectors in the finance, telecommunications, energy, and transport sectors, which further drives the demand of embedded security solutions.
- Furthermore, in April 2020, Timesys Corporation (one of the leading providers of embedded, open-source software and security solutions) announced expanded functionality of Timesys Vigiles, bringing new Software Composition Analysis (SCA) features and vulnerability triage and mitigation tools for embedded system products. Timesys Vigiles Security Monitoring & Management Service enables developers of embedded system products using Linux and open source components to bring more secure products to market in a range of industries, including medical devices, industrial control systems, transportation systems, Internet of Things and Industrial Internet of Things.
Competitive Landscape The embedded security market is highly fragmented, and the major players have used various strategies such as new product launches, expansions, agreements, partnerships, acquisitions, and others to increase their footprints in this market, which caters to an intense rivalry in the market. Key players are Infineon Technologies AG, STMicroelectronics N.V., etc. Recent developments in the market are - - March 2020 - Intrinsic-ID BV announced IKV had launched its software-based security solution equalling hardware level for IoT security. IKV used Intrinsic ID’s BroadKey, a secure root key generation and management software solution for IoT security that enables device manufacturers to secure their products with an internally generated, unique identity without the need for adding costly, security-dedicated silicon. Reasons to Purchase this report: - The market estimate (ME) sheet in Excel format - 3 months of analyst support The dynamic nature of business environment in the current global economy is raising the need amongst business professionals to update themselves with current situations in the market. To cater such needs, Shibuya Data Count provides market research reports to various business professionals across different industry verticals, such as healthcare & pharmaceutical, IT & telecom, chemicals and advanced materials, consumer goods & food, energy & power, manufacturing & construction, industrial automation & equipment and agriculture & allied activities amongst others.
For more information, please contact:
Hina Miyazu Shibuya Data Count Email: [email protected] Tel: + 81 3 45720790
1 note
·
View note
Text
Decrypted: Hackers show off their exploits as Black Hat goes virtual
Every year hackers descend on Las Vegas in the sweltering August heat to break ground on security research and the most innovative hacks. This year was no different, even if it was virtual.
To name a few: Hackers tricked an ATM to spit out cash. A duo of security researchers figured out a way to detect the latest cell site simulators. Car researchers successfully hacked into a Mercedes-Benz. A Windows bug some two decades old can be used to plant malware. Cryptocurrency exchanges were extremely vulnerable to hackers for a time. Internet satellites are more insecure than we thought and their data streams can contain sensitive, unencrypted data. Two security researchers lived to tell the tale after they were arrested for an entirely legal physical penetration test. And, a former NSA hacker revealed how to plant malware on a Mac using a booby-trapped Word document.
But with less than three months until millions of Americans go to the polls, Black Hat sharpened its focus on election security and integrity more so than any previous year.
Here’s more from the week.
THE BIG PICTURE
A major voting machine maker is finally opening up to hackers
The relationship between hackers and election machine manufacturers has been nothing short of fraught. No company wants to see their products torn apart for weaknesses that could be exploited by foreign spies. But one company, once resistant to the security community, has started to show signs of compromise.
Election equipment maker ES&S is opening up its voting machines to hackers — willingly — under a new vulnerability disclosure program. That will see the company embrace hackers for the first time, recognizing that hackers have knowledge, insight and experience — rather than pushing them away and ignoring the problems altogether. Or, as the company’s security chief told Wired: “Hackers gonna hack, researchers gonna research.”
0 notes
Text
Singapore Savings Account Rates: 8/1/eleven
Singapore Financial savings Account Charges: Eight/1/11
Offshore financial savings accounts are an important option available for individuals living and working abroad. This is the best savings plan for individuals who can initially invest a big amount of cash. You should purchase one, or take the whole case if you would like. You must take this in consideration when choosing the perfect on-line buying and selling platform. You should therefore take that benefit to know your score. The benefit nevertheless, is that this is the nearest to bad credit score loans acceptance a candidate is prone to get to. You'll most likely need to have a joint account with an grownup if you would like to use a bank card. Her primary use of the account is to pay payments by examine. Your test register must be adjusted by adding or subtracting objects proven on your bank statement however not but reflected on your check e book.

Be aware that Singapore savings account charges are subject to vary with out discover at discretion of the bank entity or finance company. Notably, although shoppers can make deposits on-line and by examine, proper now Goldman Sachs doesn’t supply a mobile utility for its savings account. Now you must present thank you for the range, quantity in your financial savings account nor a account that can get Legislation Of Attraction And Money paid, as if this has already passed off. Low Administrative Costs Health financial savings accounts help your corporation keep away from pricey administrative bills because your employees mainly administer their very own accounts. Except for the examples above, there are also bank card explicitly used for gas that rewards you on your auto bills or a bank card that encourages procuring and division link store purchases. It occurs to numerous individuals; for some individuals till they acquire or determine to acquire a specific brand/model of car, they haven't found the truth that there are a great number of such vehicles on the road. It’s an incredible choice for somebody who wants their money to work for them but still have a high stage of safety. Or, when you have two other Capital One merchandise open (like a Spark Enterprise Bank card, a loan or line of credit score, or a merchant service account), you won’t have to worry in regards to the month-to-month charge.
Lastly, profit from employment-based mostly faculty scholar financial loan repayment programs. Are there any varieties of vehicles I am unable to purchase with my mortgage sort? The truth is, if there are any fees associated with an Allpoint ATM, Capital One reimburses those charges at the end of the billing cycle. In truth, buying instantly from a bank saves the buyer the trouble of bidding at an auction. The bank will not allow you to go back and order it later. Reckoning along with your thoughts as a way to free up your capability for wisdom is the continued battle of life. I need point out when addressing the Simulation Hypothesis that no free will exists. That's enough for most of us- a gentle source of earnings to reinforce and eventually free us from the daily working grind. Sales alerts are yet one more source for these coupons. I will only contact on what most persons are concerned on. It is straightforward for hackers to clone a reputed webpage after which distribute phishing emails as a method to trick people into providing them with delicate data.
AFCU also affords authorized session for army members who want more details about power of lawyer, wills, insurance coverage or some other monetary considerations they have while serving overseas. From there you'll fill out the private data wanted to complete the reservation. When I used to be growing up, the second of ten youngsters, cash was never discussed in our home, perhaps because there was little to debate, maybe as a result of the issue was thought-about for adults solely. It is the first time that a enterprise goes public with the problem of shares. Discover properties that has been offered up to now few months by looking the public records at the county recorder's workplace. In the present low-curiosity rate setting, it’s more essential that ever to find the very best yields on deposit accounts. The most cost effective and the perfect method to switch money ought to restrict the cons and offer comparable pros, if not better. The very best banks had been chosen based on various options, such as minimal deposit requirements, interest rates, account fees and more. Banks is not going to fix any rates for the long run.
PNC Bank Newtown
0 notes
Text
Decrypted: Hackers show off their exploits as Black Hat goes virtual
Decrypted: Hackers show off their exploits as Black Hat goes virtual
Every year hackers descend on Las Vegas in the sweltering August heat to break ground on security research and the most innovative hacks. This year was no different, even if it was virtual.
To name a few: Hackers tricked an ATM to spit out cash. A duo of security researchers figured out a way to detect the latest cell site simulators. Car researchers successfully hackedinto a Mercedes-Benz. A…
View On WordPress
0 notes
Text
Hackers show off their exploits as Black Hat goes virtual – TechCrunch
Hackers show off their exploits as Black Hat goes virtual – TechCrunch
[ad_1]
Every year hackers descend on Las Vegas in the sweltering August heat to break ground on security research and the most innovative hacks. This year was no different, even if it was virtual.
To name a few: Hackers tricked an ATM to spit out cash. A duo of security researchers figured out a way to detect the latest cell site simulators. Car researchers successfully hacked into a…
View On WordPress
0 notes
Text
Decrypted: Hackers show off their exploits as Black Hat goes virtual
Decrypted: Hackers show off their exploits as Black Hat goes virtual
Every year hackers descend on Las Vegas in the sweltering August heat to break ground on security research and the most innovative hacks. This year was no different, even if it was virtual.
To name a few: Hackers tricked an ATM to spit out cash. A duo of security researchers figured out a way to detect the latest cell site simulators. Car researchers successfully hackedinto a Mercedes-Benz. A…
View On WordPress
0 notes
Text
Original Post from SC Magazine Author: Bradley Barth
Using AI to create artificial fingerprints that can unlock strangers’ phones… abusing electric vehicle charging stations to overwhelm the power grid… exploiting 3D printer technology to execute an all-new form of supply chain attack…
These may have once sounded like far-flung ideas, but top cyber minds at New York University have been actively exploring such scenarios in cutting-edge research detailed yesterday at a special roundtable discussion hosted by the NYU Center for Cybersecurity at the Tandon School of Engineering in Brooklyn.
Students work on an ATM-hacking challenge.
The roundtable was held as part of CSAW (Cyber Security Awareness Week), an innovative and student-run annual cybersecurity event, held this year in six university locations around the world: Brooklyn, France, India, Israel, Mexico and the United Arab Emirates.
Students from multiple higher-learning institutions who attended the event were invited to participate in nine different contests, including an Applied Research Competition (for the best academic paper), a Capture the Flag exercise, a “red team” challenge and an opportunity to hack neural networks.
CSAW attendee Michael Richmond Jones, a computer science senior at Rensselaer Polytechnic Institute in Troy, New York, said the event was presented a “chance to practice all the skills that I’ve been learning over the semester… see new places and definitely to network with lots of of interesting people.”
Indeed, there was no shortage of interesting people or intriguing topics during the roundtable discussion.
Fooling Fingerprint Scanners
No two fingerprints are alike, but researchers found a way to create a scenario where smartphones fingerprint sensors essentially say: “Close enough!”
In a discussion on artificial intelligence and deepfakes technologies, Julian Togelius, associate professor of computer science and engineering at NYU, explained how AI can be used to create fake synthetic fingerprints – aka “MasterPrints” – that can trick the biometric fingerprint-matching technology found in many mobile devices.
“Some people’s fingerprints just seem to be better than others. They’re just better at unlocking their own phones and sometimes others’,” said Togelius. “So we started digging into this” to see if they could recreate this phenomenon through deep learning.
Togelius and four other academic researchers published a paper on their research back in October 2018. The method is referred to as Latent Variable Evolution, and involves training a generative adversarial network machine learning system by feeding it a data set of genuine fingerprint images.
Julian Togelius
Using this training, the AI eventually learns to create its own imaginary fingerprints. Then the researchers take the images through an evolutionary optimization process to narrow down the candidates until they find an image that, in the eyes of a smartphone, successfully matches up with a large number of genuine fingerprint images.
“You could basically ask the system: ‘Search in the space of non-[genuine] fingerprints for the ones that unlock the most different phones.’ It worked shockingly well,” said Togelius.
Ultimately the researchers were able to create synthetic fingerprint images that tricked standard-quality smartphone fingerprint readers 22.5 percent of the time.
Abusing Electric Car Charging Stations
There’s an urban legend that if too many people flush their toilets at the same time – perhaps during halftime of a Super Bowl – they will overload the sewage system. This is not true, but the same can’t be said for electric car charging stations and the power grid.
Last summer, NYU announced that researchers from the Tandon School conducted a series of simulations and determined that if a fleet of roughly 1,000 plug-in electric vehicles were all to charge simultaneously in Manhattan, the power drain would be enough to overwhelm the power grid and cause a major outage.
Yury Dvorkin, assistant professor in NYU Tandon’s Department of Electrical and Computer Engineering, explained to reporters at CSAW that malicious hackers could theoretically cause a blackout condition by weaponizing electric vehicles and publicly available power grid data with the intent to execute a demand-side attack. Dvorkin, along with Professor of Electrical and Computer Engineering Ramesh Karri (who was also at CSAW) collaborated on this study alongside doctoral candidate Samrat Acharya, who led the research project.
According to the researchers, every electric vehicle that interfaces with a public charging station generates data regarding its location, charging time, and the average power expended at each station per hour. Malicious actors could potentially aggregate such information through a combination of third-party apps, public documents and resources published by industry standards bodies, and then use that data to develop and optimize a data-driven attack strategy that, according to the researchers’ published paper, manipulates electric vehicle and changing station loads “to induce frequency instability in the power grid.”
Using collected data, “Someone can time the attack in such a way that the system is already stressed due to, say, a peak demand on the system, and manipulate the charging process of electric vehicles to show that power system equipment is being operated above its technical limits,” said Dvorkin. “And as a result of that, the system operator will have no choice but to disconnect certain districts of the city from the power supply.”
A scary new dimension to 3D Printers
On Nov. 8, CSAW held one of its more intriguing contests, Hack3D, a 3D printing competition. In this scenario, students attempted to reconstruct a corrupted .gcode file (a 3D printer format), and then later hack an anti-counterfeiting system that protects CAD models.
Indeed, a large focus of the Tandon School’s research into 3D printing (aka additive manufacturing) has focused on preventing counterfeiting and intellectual property theft. An August 2018 research paper and corresponding press release from the school warned that flawed parts printed from stolen design files could resulted in the mechanical failure of 3D-printed products ranging from aircraft parts to medical implants. To address this issue, a team of NYU researchers formulated a method for embedding tracking codes (such as QR codes) into 3D products features’ to ensure a products is authentic and not an unauthorized copy.
But this is not the only threat. At CSAW, Tandon faculty also noted the that attackers could potentially sabotage 3D printers to create products with undetectable flaws, in what essentially constitutes a unique form of a supply chain attack. “The next generation of threats are going to be in… additive manufacturing…” said Karri during the roundtable discussion.
Nikhil Gupta, a professor in Tandon’s Department of Mechanical and Aerospace Engineering who co-authored the anti-counterfeiting research paper, told SC Media that companies using 3D printers often operate the machines in segregated subnetworks, keeping them offline to prevent remote hacking of the equipment. Nevertheless, he said the printers could theoretically be infected through a malicious software or firmware update, or even by a supply chain attack whereby the printer hardware was embedded with a malicious component during its manufacturing. Gutpa said even the printing material itself could potentially contain vulnerabilities.
Potentially, any of these scenarios could result in defects that require a company to “recall [an] entire batch” of products. “That’s a really scary scenario,” he said.
The post Imaginative attack scenarios elicit intrigue at NYU’s CSAW cyber event appeared first on SC Media.
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Bradley Barth Imaginative attack scenarios elicit intrigue at NYU’s CSAW cyber event Original Post from SC Magazine Author: Bradley Barth Using AI to create artificial fingerprints that can unlock strangers’ phones… abusing electric vehicle charging stations to overwhelm the power grid… exploiting 3D printer technology to execute an all-new form of supply chain attack…
0 notes
Text
How IoT Is Becomes the Biggest Innovation for the App Development Industry
Internet of things is one of the most impressive and useful for modern technology businesses worldwide. It can lead any company towards success by enabling the management to improve service and enhance the customer experience. In recent years, mobile application development services IoT took the customer experience to the next level. Discover how technology impacts IoT mobile application development services.
It is fair to mention that compared to other futuristic technologies like Artificial Intelligence and AR, IoT technology has a larger impact on the development of mobile applications. The entrepreneurs are opting for solutions IoT applications to manage and control their existing networks IoT using their fingers. The IoT network retrieves information from connected devices and transmits real-time data to mobile applications. As a result, users of the application can IoT make informed decisions and manage critical processes using their fingers.
Some years, however, the developers of mobile applications cannot adapt to this trend, as IoT was at a nascent stage and its scope in the field of mobile application development has not been clear. This situation is completely changed now that we can see progress IoT applications with flawless performance and user-friendly features with more control over the IoT network.
IoT becomes popular because of its adaptation right to use it in everyday objects such as speakers to the construction even IoT powered smart cities. This shows how the immense potential of IoT and creates more applications will make the world a better place. It all starts with a device that depends on the IoT application. And with the industry booming application, smartphones courtesy, get the IoT application development company to use innovation for the communications device to the application made to a business plan.

Here are the reasons why IoT is growing up to be the biggest innovation for the App Development industry.
Raising Open Source Development
The IoT technology makes way for application developers and application development companies to share their programs openly. This benefits other developers developing applications to test and build their own IoT applications. With a plethora of opportunities ahead, the growth of mobile applications is inevitable.
And opens a door for more IoT developers of intelligent to seize this opportunity and access to the market before it becomes extremely competitive. Being open-source, it provides more transparency, making it easier for companies and individual developers collaborate to create better applications.
Innovation through Wearable’s
The best way to splice in technology is entering the consumer goods market. Wearables are part of everyday life. Whether a smartwatch, goggles and speakers/headphones, etc. The idea is to have a potential bridge to exchange data between devices. This way, customers can access real-time data and also engage in simulation activities using IoT devices.
The application of basketball, ShotTracker comes with a sensor attached strap connected to the mobile device of the user. The sensor then records the data on strokes a player takes the same and is simulated in a mobile application. This way, a user can follow his / her performance.
Promote Hybrid App Development
IoT devices must exceed the limits of traditional Aboriginal mobile applications. This is why the IoT applications to be platform-agnostic and this will have an influx development of hybrid applications. A hybrid application with enhanced UX for IoT devices is better to realize the need of the hour. The application of the industry can expect to integrate the latest coding functionality required on hybrid platforms, allowing users to interact with a variety of cross-platform devices.
Entering in the Finance Industry
The industry with lots of data in real-time and always in need of greater efficiency can greatly benefit from the IoT. The application of the IoT in the banking and financial sector is already leading to improve productivity while ensuring transaction security. This safety applies to both - the bank and the consumer level. Enabling effortless, secure banking and hassle, IoT helps improve mobile banking, smart ATMs, ATM, etc.
Empower the retail sector
The retail sector is the most phenomenal transformation with IoT. It has changed the way how customers shop - a massive change in physical stores for electronic commerce. Users prefer online shopping to offline due to greater convenience and saving time to visit different stores on the market.
With IoT, existing retail stores looking to change their approach by enabling Bluetooth tags. This helps to reach the target audience and send them personalized offers. It is a service based on the location where guests can enjoy the information on products/services on their mobile phones. They get alert whenever there is a change in the product price or availability if chosen.
Embracing innovative business solutions
For those who have used once Uber will be made transparent IoT works an easy job. It collects data from all the taxi drivers and the connected application users looking for a ride. It does so continuously until another party accepts the request indicating the availability. This shows IoT allows innovative companies to provide better solutions.
There will be lots of innovative companies that rely heavily on the IoT to offer solutions that enhance the role of developers IoT applications in industry. These companies help to solve the problems of existing users by providing a simple and convenient solution for IoT to work for the same.
Conclusion
Before companies begin to develop applications and devices for IoT, there are still challenges the integrity of security for the development of IoT applications. Allowing the exchange of open source databases will be hackers lurking around and this can lead to a breach of the system. In addition, multiple device connectivity can create late problems. The key is to develop highly secure systems, with a planned connectivity architecture that provides a safe and smooth user experience.
Fusion Informatics is the best IoT app development company in Doha that employs in developing cutting edge solutions for our customers and we consider out of the box, internet of things apps that implement creative wearable technology. Also provides Artificial Intelligence Services in Qatar, Mobile App Development Services in Qatar, BlockChain Development Services, Machine Learning, Internet Of Things, and Cloud Solutions.
Source Page:- https://fusioninformatics1.blogspot.com/2019/10/how-iot-is-becomes-biggest-innovation.html
Visit:-
App development cost like Bigbasket
Matrimonial online app like shaadi
App development cost like Ola
E-commerce app Development cost like Flipkart
Cost of app like Redbus
Cost of app like practo
0 notes
Text
Singapore Financial savings Account Rates: Eight/1/eleven
Singapore Financial savings Account Charges: 8/1/eleven
Offshore savings accounts are a terrific option accessible for people dwelling and dealing abroad. That is the best savings plan for people who can initially invest a large sum of money. You should purchase one, or take the entire case if you would like. You must take this in consideration when selecting the very best on-line trading platform. You must therefore take that benefit to know your ranking. The benefit nevertheless, is that that is the closest to bad credit score loans acceptance a candidate is likely to get to. You will probably have to have a joint account with an adult if you need to make use of a bank card. Her primary use of the account is to pay payments by examine. Your verify register should be adjusted by including or subtracting gadgets shown in your bank statement however not but mirrored in your test book.
Notice that Singapore financial savings account charges are topic to alter with out notice at discretion of the bank entity or finance firm. Notably, though shoppers could make deposits online and by check, proper now Goldman Sachs doesn’t provide a mobile utility for its financial savings account. Now it is best to provide thank you for the variety, quantity in your financial savings account nor a account that can get Legislation Of Attraction And Cash paid, as though this has already came about. Low Administrative Costs Well being financial savings accounts help your enterprise keep away from pricey administrative bills as a result of your employees basically administer their own accounts. Except for the examples above, there are also bank card explicitly used for fuel that rewards you on your auto bills or a bank card that encourages purchasing and department see on wikipedia retailer purchases. It occurs to numerous individuals; for some individuals until they purchase or resolve to accumulate a selected model/model of automobile, they haven't discovered the truth that there are a great number of such cars on the road. It’s an awesome possibility for somebody who desires their money to work for them however still have a excessive level of safety. Or, if in case you have two other Capital One merchandise open (like a Spark Enterprise Bank card, a mortgage or line of credit score, or a service provider service account), you won’t have to worry concerning the monthly fee.
Lastly, benefit from employment-based college pupil financial mortgage repayment applications. Are there any varieties of cars I can't buy with my loan kind? Actually, if there are any costs associated with an Allpoint ATM, Capital One reimburses those expenses at the tip of the billing cycle. Citibank near In reality, shopping for straight from a bank saves the purchaser the problem of bidding at an public sale. The bank won't let you go back and order it later. Reckoning along with your thoughts with a purpose to free up your capacity for knowledge is the continuing battle of life. I need point out when addressing the Simulation Hypothesis that no free will exists. That is sufficient for most of us- a gentle source of income to enhance and finally free us from the day by day working grind. Sales alerts are yet another supply for these coupons. I am going to solely touch on what most persons are concerned on. It is simple for hackers to clone a reputed website after which distribute phishing emails as a strategy to trick people into offering them with delicate information.
AFCU additionally provides legal session for navy members who want more information about power of lawyer, wills, insurance coverage or another monetary considerations they've while serving overseas. From there you'd fill out the private data wanted to complete the reservation. When I was rising up, the second of ten youngsters, cash was by no means discussed in our home, perhaps because there was little to debate, perhaps as a result of the problem was considered for adults only. It's the primary time that a enterprise goes public with the issue of shares. Discover properties that has been bought up to now few months by looking the public data on the county recorder's workplace. In the present low-curiosity price setting, it’s more essential that ever to seek out the absolute best yields on deposit accounts. The cheapest and the perfect solution to transfer money ought to limit the cons and provide comparable pros, if not higher. One of the best banks were chosen primarily based on various options, equivalent to minimal deposit requirements, interest charges, account charges and more. Banks won't repair any charges for the long run.
0 notes
Text
Security Penetration Testing
In security as in life, the hardest weaknesses to pinpoint are your own. Fortunately, we have no problem thoroughly documenting all of your flaws. In fact, it’s kind of our job. And that’s a good thing: Knowing your vulnerabilities – and the ways in which attackers could exploit them – is one of the greatest insights you can get in improving your security program. With that in mind, Hack The Grid's Penetration Testing Services team will simulate a real-world attack on your networks, applications, devices, and/or people to demonstrate the security level of your key systems and infrastructure and show you what it will take to strengthen it. Much like your mom, we don't highlight your failings because it bothers you—we do it because we care. Way more than security experts The best way to stop attackers is to think and act like an attacker. Which is why, unlike many security firms, we don’t hire recent grads or people with more experience in IT than security as pen testers. Instead, we find good people who know about bad things. Things like ATM hacking, multi-function printer exploitation, automobile keyless entry attacks, endpoint protection bypass techniques, RFID cloning, security alarm system bypass… you get the idea. And those kinds of people? They’re way more than security experts—they’re bonafide hackers. To stay perpetually one step ahead of attackers – and help others do the same – our testers devote 25% of their time to conducting research and contribute to the security community, publishing articles, presenting at conferences, developing and releasing open source testing tools, and writing popular Metasploit modules. (Bonus: Since we own Metasploit, our pen testers get unparalleled access to the most widely used penetration testing tool in the world.) What to fix, and when and how to fix it The best you can hope for from most penetration tests is a long list of problems with little context on how to fix them or where to start. Helpful, right? Hack The Grid uses the DREAD methodology to provide a prioritized list of issues, based on the damage potential, reproducibility, exploitability, number of affected users, and discoverability of each finding. What can you expect? redteam security detailed description and proof of concept for each finding, as well as an actionable remediation plan. And because we understand that risk severity is only one factor in prioritizing remediation efforts, we'll also provide insight into the level of effort needed to remediate the findings. In addition, you'll receive: An attack storyboard that walks you through sophisticated chained attacks Scorecards that compare your environment with best practices from an attacker’s perspective Positive findings that call out what security controls you have that are effective
0 notes
Text
The World Is Asking If Cash Will Disappear—But Should It?
Bertille Bayart, Le Figaro, June 29, 2017
PARIS--Will the digital revolution get the better of physical currencies, a cornerstone of trade since 700 B.C. and a key fixture of modern society and government? Whether using cards, transfers, or cellphones, paying for things is increasingly done without coins or bills. This evolution raises the prospect of a cashless society. But is that really what we want?
Cash disappears from our daily lives a little more each day. Long gone are the cash registers that used to line bank counters. They were replaced by ATMs, but there are now fewer of those too. The amount of cash we withdraw is also decreasing, down -1.1% in France last year. Meanwhile, the alternatives to cash are growing rapidly--up more than 10% globally in 2015--according to the consulting firm Capgemini.
“The dematerialization of payments is a spectacular rising tide,” explains Gilles Grapinet, CEO of Worldline.
In France, half of payments are made with a banking card, with a volume of transactions that has been growing on average 8% every year since 2000. The more recent rise of contactless payment accelerates the trend. “The average amount paid by card decreases steadily as it challenges cash, historically the preferred method for small payments,” explains Christophe Vergne, head of card payments and practices at Capgemini Global Financial Services.
Still, cash is putting up a fight, even in developed countries. “Cash isn’t going to disappear,” says Delphine Lalanne, who heads fiduciary activities at the Bank of France. The volume of bills in Europe rules in her favor. In 2016 in France, it went up 7% in quantity and 6% in value. Money--as in the kind you can hold, feel and smell--still has it!
“The French and the Europeans are still very much attached to cash,” says Lalanne. “Some predict its extinction, but let’s not forget that it’s the customers, the users, who are king and define the method of payment best suited to them. A European survey that the European Central Bank will be publishing in the summer shows that three times out of four, in local shops, people prefer to pay cash.”
There’s a trust factor when it comes to cash. “It remains the only payment method that has an instantaneous, universal liberating power. It’s the legacy of the Prince’s privilege to mint coins,” the Bank of France official explains. Being able to pay everywhere, in every circumstance, without any doubt about the value of your method of payment remains the real, or supposed, privilege of cash. Cash reassures people.
In 2008, after the collapse of Lehman Brothers on Sept. 15, demand for euro bills went up by an additional 38 billion euros between late September and late October. “We took part in a simulation of a flood in Paris. And together with feedback from natural disasters from abroad--Fukushima, for instance--we know that we’d face a surge in the demand for cash, especially if technological and electrical infrastructures are affected,” says Lalanne.
But printing, handling and secure transportation of cash are costly--representing between 0.29% and 0.72% of GDP, according to a 2011 study by Denmark’s central bank. There’s also the fact that cash is a vehicle for fraud, tax evasion, grey or black market, corruption, but also organized crime and even terrorism financing.
One thing’s for certain: Large denomination bills have a tendency to vanish. The 500-euro note is a case in point. We hardly ever encounter them. And yet, there were 269 billion euros worth of them in circulation as the end of 2016. They’re generally used as hoard money, hidden underneath mattresses or inside safes. Others are used by crooked people or organization, and we don’t really know in what proportions. What we do know is that more than 30% of the euros in circulation (in value) are outside of the euro zone.
The innovation in payment methods--from the good old debit card to paying with your smartphone--operates hand-in-hand with the ongoing commerce revolution. “In the digital era, retailers are reinventing the customer experience to make it as smooth as possible,” Gilles Grapinet explains. “And in that respect, cash reveals its fundamental limit: It cannot accompany the digital commerce revolution.”
The Worldline CEO calls the shift in commerce a “weapon of mass destruction” against cash. “We are killing the cash registers. And what are cash registers good for, except keeping cash?”
Digital payment versus cash is also a battle of two lobbies. “The extinction of cash is also a theory disseminated by pressure groups,” one expert notes. Digital payments, after all, aren’t free of charge. Their development implies a massification that generates commission payments from retailers. They also make it easier to collect commercially exploitable data, the equivalent of gold for the 21st century.
In addition, the modernization of payment methods allows for greater liquidity of the banking market and more competition, as it favors the emergence of new actors in a market where it can be difficult to make a name for oneself. The European Union, in that sense, plays the role of a stimulant.
“The new European directive on payment services (PSD2) will accelerate the replacement of cash by digital methods of payment,” says Christophe Vergne. “Some countries have declared war on cash. In Northern Europe, they did so to accompany the digital evolution of society. In some African countries, for security reasons. In India, to fight against corruption.”
Thus, the cashless society starts having its own supporters and theorists. The former IMF economist Kenneth Rogoff became one its advocates with his book The Curse Of Cash, published last year. The amount of cash in circulation represents $4,200 dollars per person in the United States, children included, he insists. A lot more than necessary for any honest human activity. So instead of reaching a full extinction of cash, he defends a cash degrowth, starting with the withdrawal of large-denomination bills.
The idea is gaining ground around the world. In the middle of last year, the European Central Bank initiated the trend by ending the printing of 500-euro bills--a controversial move. More importantly, in November 2016, India’s government abruptly declared invalid all bills of 500 and 1,000 rupees in an unprecedented and slightly chaotic operation. Six months later, it’s difficult to draw clear conclusions from this huge demonetization operation, the goal of which was to declare war on the grey economy and corruption. Others have turned to less spectacular measures, like imposing limits on cash transactions. In France, the cap was brought down from 3,000 euros to 1,000 euros in September 2015.
That being said, the image of briefcases and envelopes filled with money shouldn’t overshadow the other payment methods used by criminals, big or small. Transfers, offshore accounts, trusts, etc. the grey economy skillfully makes light of financial rules. And the increasing number of scams and blackmail hackers take advantage of the rise of alternative currencies such as Bitcoin. “The extinction of cash wouldn’t erase money-laundering, nor tax fraud,” Lalanne insists.
Monetary policy also plays a role in this debate. Ever since major central banks made a foray into the then unexplored territory of negative interest rates, cash has become an obstacle to the propagation of their policy. When it costs money to deposit money in a bank, users have an incentive to keep it at home. In Switzerland, the 1,000-franc bill became very popular after negative interest rates were introduced.
Sweden is a pioneer country when it comes to money. That’s where the first bank notes were invented and where the first national central bank was created, in the late 17th century. Sweden was also the first to introduce negative interest rates in 2015. And the Nordic country is ahead of the curve when it comes to cashless societies. Going cashless is a goal openly admitted by the authorities, so much so that they even promoted it on the state-run website Sweden.se.
The Swedes no longer pay, they “swish.” Swish is the name of a payment app launched by Swedish and Danish banks. And although ABBA sang “Money, Money, Money,” the museum dedicated to the Swedish band in Stockholm doesn’t accept any cash. Another piece of evidence of the willingness to switch is that any shopkeeper in Sweden has to right to refuse payments in cash. As a consequence, the volume of cash only represents 2.1% of the GDP in Sweden compared to 10.3% in the Eurozone and 7.7% in the U.S., according to Capgemini.
The Swedish example attracts much discussion in the world of payments. For some, it’s a full-scale showcase of the prospects of tomorrow’s digital world. For others, it raises serious concerns: First of all about the risk of more exclusion for the poorest and the weakest members of society, but also about the risk of a Big Brother-like turn that would, in the future, ban all non-traceable transaction and limit individual freedoms and the right to property.
We’re not there yet, and far from it. The field of payments is particular in that no innovation has ever succeeded in completely replacing the former method. “Digital methods of payments widen the offer. They’re not a replacement for cash,” says Lalanne. Cash is resisting and bank cards continue to grow despite the rise of transfers and mobile payments. Even checks are managing still to survive. We can rest assured, in other words, that our beloved bills will be with us for a while yet.
0 notes
Text
Decrypted: Hackers show off their exploits as Black Hat goes virtual
Decrypted: Hackers show off their exploits as Black Hat goes virtual
Every year hackers descend on Las Vegas in the sweltering August heat to break ground on security research and the most innovative hacks. This year was no different, even if it was virtual.
To name a few: Hackers tricked an ATM to spit out cash. A duo of security researchers figured out a way to detect the latest cell site simulators. Car researchers successfully hackedinto a Mercedes-Benz. A…
View On WordPress
0 notes