#clickjacking
Explore tagged Tumblr posts
Text
Protect Your Laravel Application from Clickjacking Attacks
In today's digital landscape, protecting your web application from various security threats is crucial. One such threat is Clickjacking, an attack that tricks users into clicking on invisible or disguised elements on a webpage. For developers using the Laravel framework, ensuring your application is safe from clickjacking is essential.

In this post, we'll explore what clickjacking is and how to prevent it in your Laravel application. Plus, we’ll show you how to use our free Website Security Checker tool to assess potential vulnerabilities.
What is Clickjacking?
Clickjacking is a type of attack where malicious users embed your webpage into an invisible iframe on their site. The attacker then tricks the victim into clicking on the iframe, which can lead to unwanted actions like changing settings, submitting forms, or even transferring funds without their knowledge.
For example, a button that looks harmless on the surface might trigger an action you didn’t intend to take when clicked in an iframe. This type of attack can be devastating for your users’ privacy and your application’s security.
Preventing Clickjacking in Laravel
Fortunately, Laravel provides a straightforward way to mitigate the risk of clickjacking. Here's how you can do it:
Step 1: Use HTTP Headers
The best way to prevent clickjacking in your Laravel application is by setting proper HTTP headers. You can do this by adding the X-Frame-Options header to your application's response. This header tells the browser not to allow your webpage to be embedded in an iframe.
In Laravel, you can add this header globally by modifying the app/Http/Middleware/VerifyCsrfToken.php file.
Here’s how you can modify the middleware:
// app/Http/Middleware/VerifyCsrfToken.php namespace App\Http\Middleware; use Closure; use Illuminate\Http\Request; class VerifyCsrfToken { public function handle(Request $request, Closure $next) { // Adding X-Frame-Options header to prevent clickjacking response()->headers->set('X-Frame-Options', 'DENY'); return $next($request); } }
With this code, the header X-Frame-Options: DENY ensures that no website can embed your pages in an iframe. If you want to allow only certain websites to embed your content, you can use SAMEORIGIN instead of DENY.
Step 2: Use Content Security Policy (CSP)
Another robust method to prevent clickjacking attacks is by using a Content Security Policy (CSP). Laravel supports CSP through middleware. By setting a strict policy, you can specify exactly which websites are allowed to load your pages in an iframe.
Here’s an example of how you can configure the CSP in your Laravel application:
// app/Http/Middleware/ContentSecurityPolicy.php namespace App\Http\Middleware; use Closure; use Illuminate\Http\Request; class ContentSecurityPolicy { public function handle(Request $request, Closure $next) { // Setting a strict CSP header response()->headers->set('Content-Security-Policy', "frame-ancestors 'none';"); return $next($request); } }
This ensures that no site can embed your application within an iframe.
Why Use Our Free Website Security Checker?
After implementing these preventive measures, it’s important to test your application’s security. Our free Website Security Scanner tool provides a comprehensive vulnerability assessment for your website, including tests for clickjacking and other security issues.
Here’s a screenshot of our free tool in action:

Screenshot of the free tools webpage where you can access security assessment tools.
Conclusion
Securing your Laravel application against clickjacking attacks is crucial for protecting your users and ensuring your web app remains safe. By following the steps outlined above, you can significantly reduce the risk of such attacks. Additionally, our free Website Security Checker can help you ensure that your site is not vulnerable to clickjacking or any other security issues.
And here’s an example of the vulnerability assessment report generated by our free tool:

An example of a vulnerability assessment report generated with our free tool provides insights into possible vulnerabilities.
By regularly using security tools and following best practices, you can enhance your website’s defenses and maintain a safe browsing environment for your users.
Take Action Today
Start testing your website with our free tool to test website security free and take the first step in protecting your site from clickjacking and other cyber threats.
#Clickjacking#laravel#cyber security#cybersecurity#data security#pentesting#security#the security breach show
3 notes
·
View notes
Link
Clickjacking Dangers On Your Website 2025 Author deviantArt.com/Digitalworldvision Kelly Hector
0 notes
Text

Some Clickjack expressions 🐱
20 notes
·
View notes
Text
Securing the Holiday Season: Beware of Clickjacking Threats
https://headlinehorizon.com/Tech/Computers/1444
Discover the latest news about a clickjacking threat that targets popular browsers, and learn how to protect yourself from cybercriminals this holiday season.
0 notes
Text
So with the pandora's box of AI being released into the world, cybersecurity has become kind of insane for the average user in a way that's difficult to describe for those who aren't following along. Coding in unfamiliar languages is easier to do now, for better and worse. Purchasable hacking "kits" are a thing on the dark web that basically streamline the process of deploying ransomware. And generative AI is making it much easier for more and more people to obscure their intentions and identities, regardless of their tech proficiency.
The impacts of this have been Really Bad in the last year or two in particular. For example:
(I'm about to link to sources, and you better be hovering and checking those links before clicking on them as a habit)
Ransomware attacks have become increasingly lucrative for private and state-sponsored hacking groups, with at least one hack recently reported to have resulted in a $75 MILLION payout from the victim. This in combination with the aforementioned factors has made it a bigger and bigger risk for companies and organizations holding your most sensitive data.
In the US, the Salt Typhoon hack over the past year or so has compromised virtually all major phone networks--meaning text and phone calls are no longer secure means of communication. While this won't affect most people in day-to-day, it does make basically all the information you share over traditional phone comms very vulnerable. You should avoid sharing sensitive information over the phone when you can.
CISA updated their security recommendations late last year in response to this compromise. One of the recommendations is to use a separate comms app with end-to-end encryption. I personally prefer Signal, since it's open source and not owned by Meta, but the challenge can be getting people you know on the same service. So... have fun with that.
2FA is no longer as secure as it was--because SMS itself is no longer secure, yeah, but even app-based 2FA has been rendered useless in certain circumstances. One reason for this is because...
A modern version of the early-2000's trick of gaining access to people's accounts via hijacked cookies has come back around for Chromium browsers, and hackers are gaining access to people's Google accounts via OAuth session hijacking. Meaning they can get into your already-logged-in accounts without passwords or 2FA even being needed to begin with. This has been achieved both through hackers compromising chrome browser extensions, and via a reinvigorated push to send out compromising links via email.
Thanks to AI, discerning compromised email is harder now. Cybercriminals are getting better at replicating legitimate email forms and website login screens etc., and coming up with ways to time the emails around times when you might legitimately expect them. (Some go so far as to hack into a person's phone to watch for when a text confirmation might indicate a recent purchase has been made via texted shipping alerts, for example)
If you go to a website that asks you to double-click a link or button--that is a major red flag. A potential method of clickjacking sessions is done via a script that has to be run with the end user's approval. Basically, to get around people who know enough to not authenticate scripts they don't recognize, hackers are concealing the related pop ups behind a "double-click" prompt instruction that places the "consent" prompt's button under the user's mouse in disguised UI, so that on the second click, the user will unwittingly elevate the script without realizing they are doing it.
Attachments are also a fresh concern, as hackers have figured out how to intentionally corrupt key areas of a file in a way that bypasses built-in virus check--for the email service's virus checker as well as many major anti-virus installed on endpoint systems
Hackers are also increasingly infiltrating trusted channels, like creating fake IT accounts in companies' Office 365 environment, allowing them to Teams employees instead of simply email them. Meaning when IT sends you a new PM in tools like Zoom, Slack, or Teams, you need to double-check what email address they are using before assuming it's the real IT person in question.
Spearphishing's growing sophistication has accelerated the theft of large, sensitive databases like the United/Change Healthcare hacks, the NHS hack & the recent Powerschool hack. Cybercriminals are not only gaining access to emails and accounts, but also using generative AI tools to clone the voices (written and spoken) of key individuals close to them, in order to more thoroughly fool targets into giving away sensitive data that compromises access to bigger accounts and databases.
This is mostly being used to target big-ticket targets, like company CSO's and other executives or security/IT personnel. But it also showcases the way scammers are likely to start trying to manipulate the average person more thoroughly as well. The amount of sensitive information--like the health databases being stolen and sold on the darkweb--means people's most personal details are up for sale and exploitation. So we're not too far off from grandparents being fooled by weaponized AI trained off a grandchild's scraped tiktok videos or other public-facing social media, for example. And who is vulnerable to believing these scams will expand, as scammers can potentially answer sensitive questions figured out from stolen databases, to be even more convincing.
And finally, Big Tech's interest in replacing their employees with AI to net higher profits has resulted in cybersecurity teams who are overworked, even more understaffed they already were before, and increasingly lacking the long-term industry experience useful to leading effective teams and finding good solutions. We're effectively in an arms race that is burning IT pros out faster and harder than before, resulting in the circumvention of crucial QA steps, and mistakes like the faulty release that created the Crowdstrike outage earlier last year.
Most of this won't impact the average person all at once or to the same degree big name targets with potential for big ransoms. But they are little things that have combined into major risks for people in ways that aren't entirely in our control. Password security has become virtually obsolete at this point. And 2FA's effectiveness is tenuous at best, assuming you can maintain vigilance.
The new and currently best advice to keeping your individual accounts secure is to switch to using Passkeys and FIDO keys like Yubikeys. However, the effectiveness of passkeys are held back somewhat as users are slow to adopt them, and therefore websites and services are required to continue to support passwords on people's accounts anyway--keeping password vulnerabilities there as a back door.
TLDR; it's pretty ugly out there right now, and I think it's going to get worse before it gets better. Because even with more sophisticated EDR and anti-virus tools, social engineering itself is getting more complex, which renders certain defensive technologies as somewhat obsolete.
Try to use a passkey when you can, as well as a password locker to create strong passwords you don't have to memorize and non-SMS 2FA as much as possible. FIDO keys are ideal if you can get one you won't lose.
Change your passwords for your most sensitive accounts often.
Don't give websites more personal info about yourself than is absolutely necessary.
Don't double-click links or buttons on websites/captchas.
Be careful what you click and download on piracy sources.
Try to treat your emails and PMs with a healthy dose of skepticism--double-check who is sending them etc for stealthily disguised typos or clever names. It's not going to be as obvious as it used to be that someone is phishing you.
It doesn't hurt to come up with an offline pass phrase to verify people you know IRL. Really.
And basically brace for more big hacks to happen that you cannot control to begin with. The employees at your insurance companies, your hospital, your telecomms company etc. are all likely targets for a breach.
36 notes
·
View notes
Text
>article called Demystifying CORS, CSRF tokens, SameSite & Clickjacking - Web Security
>look inside
>still mystifying
9 notes
·
View notes
Text
New "DoubleClickjacking" Exploit Bypasses Clickjacking Protections on Major Websites
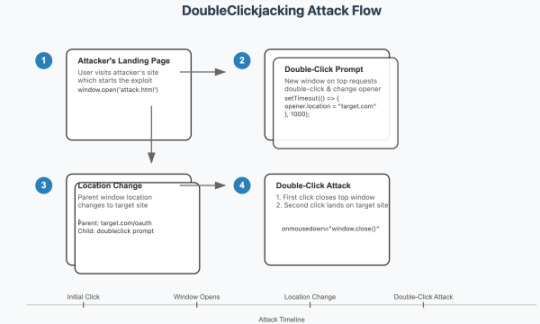
Source: https://thehackernews.com/2025/01/new-doubleclickjacking-exploit-bypasses.html
More info: https://www.paulosyibelo.com/2024/12/doubleclickjacking-what.html
6 notes
·
View notes
Text
Top Django Interview Questions and Answers in 2025

Introduction
If you're aiming for a career in web development, you've probably come across Django, and guess what? It's still going strong in 2025. Whether you're a fresh graduate or an experienced developer eyeing a transition, knowing the top Django interview questions and answers will give you a big edge.
From start-ups to the world's biggest social networking site Instagram, this framework has changed things a lot. It's one of the favorites due to its simplicity, security, and scalability. But with the increasing competition, interviewers have started to pick brains. So let us prepare you with some of the most relevant and updated top Django interview questions and answers that you will need for 2025.
Basics of Django
What is Django?
Django is a high-level Python web framework that lets you rapidly develop secure and maintainable web applications with as little coding as possible. Basically, it follows the "batteries-included" philosophy, which states that user authentication, content management, and database administration are included from the start.
Key Features of Django Framework
MTV architecture (Model-Template-View)
ORM (Object-Relational Mapping)
Admin Interface
Built-in security features
Highly scalable and portable
What Are Django’s Advantages over Other Frameworks?
It's Pythonic-clean and easy to read
Fastest development cycle
Rich documentation
Large community
Tons of third-party packages
Django Interview Questions Asked Quite Often (Beginner Level)
Explain MTV Architecture in Django?
MTV stands for:
Model: It defines what the data structure is.
Template: HTML-like design files.
View: Contains business logic that connects the models and templates.
It's like the way Django interprets Model-View-Controller.
How Does a Request in Django Differs from a Response?
Every HTTP request in Django goes through many processes, that are URL dispatcher, view function, and finally returning an HTTPResponse object. It simply can be thought as a pipeline managing routing, logic, and output.
What Are Models in Django?
Models specify the structure of your database in terms of Python classes; they also act as a bridge between the application and the database using Django's ORM.
Intermediate Questions for Django Interviews
How to Differentiate between a Project and an App?
Project: The entire web application.
App: A component or module within a project (eg., blog, cart, and user).
You can plug many apps into one project.
What Are QuerySets, and How Do They Work?
A queryset is a collection of queries that can be executed against a database to retrieve objects. It is lazy — meaning it will not query the database until the results are explicitly requested.
Advanced Questions for Django Interviews
How are Security Issues (XSS, CSRF, etc.) Handled by Django?
Django has built-in protections against:
CSRF tokens in forms
Auto-escaping of templates in XSS
SQL injection with an ORM
Protection against clickjacking by middleware
What Is Middleware in Django?
Middleware is a framework of hooks into Django's request/response processing. It is a light, low-level plugin system for globally altering Django's input or output. For example, it can be useful for:
Logging requests
Modifying responses
Enforcing authentication
What Are Ways to Enhance Django Application Performance?
Use caching (Redis or Memcached).
Optimize QuerySets.
Minimize template logic.
Compress static files.
Use Django Debug Toolbar for diagnosis.
Real-life Scenario Questions
What Will You Do to Scale a Django App under Heavy Load?
Load balancing.
Caching with Redis.
Use CDNs for serving static/media.
Database indexing optimization.
Perform asynchronous tasks with Celery.
How to Connect Django with Frontend Frameworks like React?
Using Django REST Framework for building APIs.
Serve the React app separately or embed it inside templates.
Handle authorization either through JWT or session-based login.
Which Tools Are Used for Testing in Django?
unittest (built-in)
pytest-django
py for test coverage
factory_boy for test data
Tips to Crack Django Interviews
Practice Coding Daily
Even 30 minutes a day adds up so quickly, and try to focus on real-world projects.
Build Real Projects
Nothing beats practical experience. Try to build a blog, an e-commerce site, or a task manager.
Mock Interviews and Technical Tests
Use a platform like Pramp or Interviewing.io to get a feel for what a real interview will be like.
Conclusion
In 2025, mastering the top Django interview questions and answers can be the very key to opening up your way into a development career. Companies have trusted Django for its speed, security, and scalability, and now, being prepared seems to be your golden ticket. Whether you are brushing up or new to the area, this guide will make you succeed.
At TCCI, we don't just teach computers — we build careers. Join us and take the first step toward a brighter future.
Location: Bopal & Iskcon-Ambli in Ahmedabad, Gujarat
Call now on +91 9825618292
Visit Our Website: http://tccicomputercoaching.com/
Note: This Post was originally published on TCCI - Tririd Computer Coaching Institute and is shared here for educational purposes.
#best computer courses in bopal ahmedabad#computer courses near me#software training in Bopal Ahmedabad#TCCI - Tririd Computer Coaching Institute#top Django interview questions and answers
0 notes
Text
DoubleClickjacking allows clickjacking on major websites
http://i.securitythinkingcap.com/TH7YBT
0 notes
Text
Discover the Best Books for Software Security and Hacking - Top 10 Recommendations by Reddit Users With the growing threat of cyber attacks, it's essential to stay informed about software security and hacking techniques. Fortunately, there are many great books on the market that cover these topics in depth. Reddit users have recommended some of the best books on software security, covering topics such as malware analysis, encryption, and social engineering. In this article, we will provide an overview of these books and their contents. "The Web Application Hacker's Handbook" by Dafydd Stuttard and Marcus Pinto "The Web Application Hacker's Handbook" is a comprehensive guide to web application security that covers the latest hacking techniques and how to defend against them. The book provides a detailed overview of web application vulnerabilities, including cross-site scripting, SQL injection, and session hijacking, and explains how attackers exploit these vulnerabilities to compromise web applications. The authors also cover the tools and techniques used by hackers, as well as the best practices and tools that developers can use to build secure web applications. "Security Engineering: A Guide to Building Dependable Distributed Systems" by Ross Anderson "Security Engineering" is a comprehensive guide to building secure and dependable distributed systems. The book covers a wide range of security engineering principles and practices, including cryptography, access control, intrusion detection, and security protocols. The author provides detailed examples of how these principles can be applied to real-world systems, and offers guidance on how to design and implement secure systems that can withstand attacks and failures. "Threat Modeling: Designing for Security" by Adam Shostack "Threat Modeling" is a guide to designing secure software by identifying and addressing potential security threats. The book covers the threat modeling process, including how to identify potential threats, assess their impact, and develop countermeasures to mitigate them. The author also covers the different threat modeling methodologies and provides guidance on how to integrate threat modeling into the software development lifecycle. "Hacking: The Art of Exploitation" by Jon Erickson "Hacking: The Art of Exploitation" is a hands-on guide to hacking that teaches readers how to write their own exploits. The book covers a wide range of hacking techniques, including stack overflow attacks, format string vulnerabilities, and heap overflows, and provides detailed examples of how to exploit these vulnerabilities. The author also covers the basics of assembly language and C programming, and provides guidance on how to use these languages to write exploits. "Applied Cryptography" by Bruce Schneier "Applied Cryptography" is a comprehensive guide to cryptography and its applications in software security. The book covers the principles of cryptography, including symmetric and asymmetric encryption, hash functions, and digital signatures, and explains how to use these principles to secure software. The author also covers the latest cryptographic protocols and provides guidance on how to implement them in software. "The Tangled Web: A Guide to Securing Modern Web Applications" by Michal Zalewski "The Tangled Web" is a guide to web application security that covers the latest web application security issues and how to defend against them. The book covers a wide range of topics, including the basics of web architecture, HTTP, and HTML, as well as the latest web application vulnerabilities, including cross-site scripting, CSRF, and Clickjacking. The author also provides guidance on how to use different security measures, including CSP, HSTS, and HTTPS, to secure web applications. "Black Hat Python: Python Programming for Hackers and Pentesters" by Justin Seitz "Black Hat Python" is a guide to using the Python programming language for hacking and penetration testing.
The book covers a wide range of topics, including network programming, web scraping, and reverse engineering, and provides detailed examples of how to use Python to write exploits and automate hacking tasks. The author also covers the basics of the Python language, making it an accessible resource for both beginner and experienced Python programmers. "The Art of Deception: Controlling the Human Element of Security" by Kevin Mitnick and William L. Simon "The Art of Deception" is a guide to social engineering and how to defend against it. The book covers a wide range of social engineering techniques, including pretexting, phishing, and baiting, and explains how attackers use these techniques to gain access to secure systems. The authors also provide guidance on how to identify and defend against social engineering attacks, including training employees and implementing security policies. "Serious Cryptography: A Practical Introduction to Modern Encryption" by Jean-Philippe Aumasson "Serious Cryptography" is a guide to modern encryption and its practical applications. The book covers the principles of encryption, including symmetric and asymmetric encryption, hash functions, and authenticated encryption, and provides detailed examples of how to use these techniques to secure data. The author also covers the latest cryptographic protocols, including TLS 1.3 and Signal Protocol, and provides guidance on how to implement them in software. "The Web Application Hacker's Handbook: Finding and Exploiting Security Flaws" by Dafydd Stuttard and Marcus Pinto "The Web Application Hacker's Handbook" is a comprehensive guide to web application security and how to test for vulnerabilities. The book covers a wide range of topics, including the basics of web application architecture, input validation, authentication, and access control, and provides detailed examples of how to find and exploit security flaws in web applications. The authors also cover the latest attack techniques, including SQL injection, cross-site scripting, and file inclusion vulnerabilities. "The Art of Exploitation" by Jon Erickson "The Art of Exploitation" is a guide to software exploitation and how to write exploits. The book covers a wide range of topics, including the basics of assembly language, stack overflows, format string vulnerabilities, heap overflows, and return-oriented programming. The author also provides detailed examples of how to write exploits for real-world software vulnerabilities, making it an excellent resource for both beginner and experienced exploit developers. "Practical Malware Analysis: The Hands-On Guide to Dissecting Malicious Software" by Michael Sikorski and Andrew Honig "Practical Malware Analysis" is a guide to malware analysis and how to dissect malicious software. The book covers a wide range of topics, including malware behavior analysis, code analysis, and memory forensics, and provides detailed examples of how to analyze real-world malware samples. The authors also cover the latest malware analysis tools and techniques, making it an essential resource for anyone interested in malware analysis or reverse engineering. In conclusion, software security is a critical topic for anyone interested in technology or cybersecurity. The books recommended by Reddit users provide an excellent starting point for those looking to learn more about software exploitation, malware analysis, social engineering, and encryption. By reading these books and staying informed about the latest threats and vulnerabilities, you can better protect yourself and your organization from cyber attacks. Remember to always practice safe online habits and keep your software up to date to stay one step ahead of the hackers.
0 notes
Text
Symfony Clickjacking Prevention Guide
Clickjacking is a deceptive technique where attackers trick users into clicking on hidden elements, potentially leading to unauthorized actions. As a Symfony developer, it's crucial to implement measures to prevent such vulnerabilities.

🔍 Understanding Clickjacking
Clickjacking involves embedding a transparent iframe over a legitimate webpage, deceiving users into interacting with hidden content. This can lead to unauthorized actions, such as changing account settings or initiating transactions.
🛠️ Implementing X-Frame-Options in Symfony
The X-Frame-Options HTTP header is a primary defense against clickjacking. It controls whether a browser should be allowed to render a page in a <frame>, <iframe>, <embed>, or <object> tag.
Method 1: Using an Event Subscriber
Create an event subscriber to add the X-Frame-Options header to all responses:
// src/EventSubscriber/ClickjackingProtectionSubscriber.php namespace App\EventSubscriber; use Symfony\Component\EventDispatcher\EventSubscriberInterface; use Symfony\Component\HttpKernel\Event\ResponseEvent; use Symfony\Component\HttpKernel\KernelEvents; class ClickjackingProtectionSubscriber implements EventSubscriberInterface { public static function getSubscribedEvents() { return [ KernelEvents::RESPONSE => 'onKernelResponse', ]; } public function onKernelResponse(ResponseEvent $event) { $response = $event->getResponse(); $response->headers->set('X-Frame-Options', 'DENY'); } }
This approach ensures that all responses include the X-Frame-Options header, preventing the page from being embedded in frames or iframes.
Method 2: Using NelmioSecurityBundle
The NelmioSecurityBundle provides additional security features for Symfony applications, including clickjacking protection.
Install the bundle:
composer require nelmio/security-bundle
Configure the bundle in config/packages/nelmio_security.yaml:
nelmio_security: clickjacking: paths: '^/.*': DENY
This configuration adds the X-Frame-Options: DENY header to all responses, preventing the site from being embedded in frames or iframes.
🧪 Testing Your Application
To ensure your application is protected against clickjacking, use our Website Vulnerability Scanner. This tool scans your website for common vulnerabilities, including missing or misconfigured X-Frame-Options headers.

Screenshot of the free tools webpage where you can access security assessment tools.
After scanning for a Website Security check, you'll receive a detailed report highlighting any security issues:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
🔒 Enhancing Security with Content Security Policy (CSP)
While X-Frame-Options is effective, modern browsers support the more flexible Content-Security-Policy (CSP) header, which provides granular control over framing.
Add the following header to your responses:
$response->headers->set('Content-Security-Policy', "frame-ancestors 'none';");
This directive prevents any domain from embedding your content, offering robust protection against clickjacking.
🧰 Additional Security Measures
CSRF Protection: Ensure that all forms include CSRF tokens to prevent cross-site request forgery attacks.
Regular Updates: Keep Symfony and all dependencies up to date to patch known vulnerabilities.
Security Audits: Conduct regular security audits to identify and address potential vulnerabilities.
📢 Explore More on Our Blog
For more insights into securing your Symfony applications, visit our Pentest Testing Blog. We cover a range of topics, including:
Preventing clickjacking in Laravel
Securing API endpoints
Mitigating SQL injection attacks
🛡️ Our Web Application Penetration Testing Services
Looking for a comprehensive security assessment? Our Web Application Penetration Testing Services offer:
Manual Testing: In-depth analysis by security experts.
Affordable Pricing: Services starting at $25/hr.
Detailed Reports: Actionable insights with remediation steps.
Contact us today for a free consultation and enhance your application's security posture.
3 notes
·
View notes
Text
For everyone who hasn't read canon because they don't know how to get comics/watch the episodes...
There. Go read canon, or at least a summary of canon. Find a character article on the DC Database wiki, then click on the citation footnotes to find the issue you want to read. Read the episode summaries. Google transcripts.
Note that the comic site is sort of sketchy- sometimes it redirects you to spam or random websites or clickjacks you. Do not turn off your adblocker- it won't force you to, and just close any pop-up websites.
And once you've read canon, you can break it.
"DC stands for Disregard Canon" could not be me. Canon events my beloved 💖
420 notes
·
View notes
Text

Clickjack, Cas’s dealer/plug (lol robot joke)
#clickjack#cat robot#robot oc#character design#original art#artses and fartses#artists on tumblr#drawing while black
55 notes
·
View notes
Text
How does Django simplify web development?
Django simplifies web development by providing a high-level framework that allows developers to build robust, scalable, and secure web applications quickly. It follows the "Don't Repeat Yourself" (DRY) principle, which encourages reusable code, reducing redundancy and speeding up development. One of Django's key advantages is its "batteries-included" philosophy, offering built-in tools like authentication, URL routing, ORM (Object-Relational Mapping) for database handling, and form handling out of the box.
Django's admin interface is another standout feature, automatically generating a powerful back-end system for managing your app’s data without writing much code. It enforces a clear separation between business logic, design, and data through its MVC-like architecture (Model-View-Template). This makes it easier to maintain and scale web projects.
Furthermore, Django has excellent community support, thorough documentation, and a rich ecosystem of packages, enabling developers to extend functionalities effortlessly. Its emphasis on security helps mitigate common vulnerabilities like SQL injection, cross-site scripting, and clickjacking.
For aspiring developers looking to master web frameworks and create dynamic websites efficiently, Django is an ideal choice. To get started with Django and web development, consider enrolling in a website development course to build your expertise.
0 notes
Link
Implementing Clickjacking Defense Techniques in JavaScript
The emergence of sophisticated assaults like clickjacking has made security a primary issue in today’s online world. By deceiving consumers into clicking on something that differs from what they initially see, attackers deploy a nefarious method called “clickjacking,” which can have disastrous results. Attacks of this kind have the potential to trick people into downloading malware, sending private information, or even doing things they didn’t mean to, like buying anything. In order to protect against these kinds of assaults, JavaScript is an essential component of dynamic web applications...
Learn more here:
https://www.nilebits.com/blog/2024/09/clickjacking-techniques-javascript/
0 notes
