#cyberthreats hashtag
Text
Cyber Resilience: Embracing Tomorrow’s Security
What is cyber resilience?
Business continuity, information systems security, and organizational resilience are all included under the idea of cyber resilience.
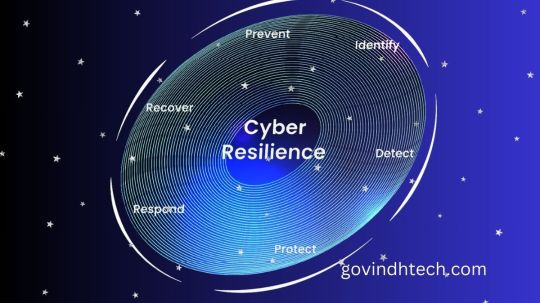
Cyber resilience framework
The harsh reality for leaders in cybersecurity is that they must protect a growing number of attack surfaces while dealing with persistently aggressive, constantly changing hostile actors. The data indicates that conventional security techniques and instruments are insufficient to ensure the safety of organizations. Organizations face 44 major cyber events annually on average, according to the EY 2023 Global Cybersecurity Leadership Insights Study, and ransomware expenses are expected to hit $265 billion by 2031. Only one in five chief information security officers (CISOs) said their firms’ current methods were successful against contemporary threats, indicating that the majority of CISOs already know what their organizations are doing is inadequate.
Cyber resilience plan
According to the EY 2023 Global Cybersecurity Leadership Insights Study, C-suite executives are battling a variety of known and unknown threats. However, it also provides comfort in knowing that diverse results are experienced by enterprises, some of which may be attributed to their cybersecurity approach. Businesses may improve their cybersecurity by taking a cue from the best and focusing on integration of cybersecurity concerns across the whole business, simplicity, and holistic thinking. Prone Enterprises has the ability to get all of these. Important takeaways from the survey are as follows:
Simplify the cyber technology stack to make it more visible and lower risk. By clearing up the technological environment via automation and orchestration, you can identify signals more quickly and take action more skillfully.
Reduce supply chain access points for hackers, increase cyber alertness, and continually evaluate performance by using automation and standardization without introducing needless bureaucracy. This guarantees early vendor selection involvement for security teams as well.
Convert your tale into a narrative that speaks to the company in terms of value generation, business impact, and risk buydown.
To make the workforce cyber-secure by design, combine automation and preventive technologies with well-planned, gradual training.
Integrate cybersecurity into your company’s operations rather than seeing it as a hindrance. It creates value, gives people the self-assurance they need to innovate, and creates new income streams and market prospects.
Even the most experienced cybersecurity professionals face novel and unanticipated problems as a result of the ever-changing threat environment. In addition to moving beyond reactive technology adoption and disaster recovery, organizations must constantly improve their security procedures and embrace an approach that centers cyber resilience inside an end-to-end organizational strategy.
Cyber resilience is a holistic strategy to defending enterprises that includes business continuity, information systems security, and organizational resilience. It goes well beyond just anticipating and reacting to threats and assaults. Cyber resilient firms must integrate security into every element of their operations and iterate to improve their posture. Innovators are helping achieve cyber resilience, which is difficult.
Cyber resilience vs cyber security
The first issue that gives rise to the requirement for cyber resilience is the extreme complexity that security executives are now facing in their enterprise’s technology and security ecosystems. The use of many technological solutions by IT and security professionals to counter attacks has resulted in significant complexity in their tech stacks and security plans. According to EY study, the most often mentioned internal obstacle to an organization’s cybersecurity strategy is “too many attack surfaces.” Additionally, 75% of respondents identified cloud and Internet of Things (IoT) as the top technological concerns for the next five years. Emerging technologies and generative AI (GenAI) provide additional complexity and dangers to the enterprise.
Cost and cross-functional work provide the second challenge. In the past, the majority of companies have provided strong support for cybersecurity expenditures. However, if threats increase in strength and number, businesses could start to doubt their financial commitments. Security has to be a company-wide endeavor, not only the domain of the IT department and cybersecurity teams, in order to decide where to allocate their money for security and implement top-down initiatives.
More than ever, companies need to integrate security into their technology instead of depending only on security personnel to safeguard all facets of their operations. Improved communication across organizational layers is necessary to transform cybersecurity from a compartmentalized endeavor into a cross-functional operation, which is a feature of the most successful security programs.
Finally, leaders need a mentality change. Strong cybersecurity is no longer a game of cat and mouse with unique solutions to address unique assaults because the rules have changed. In the current threat environment, a firm must contend with skilled attackers and not rely just on disaster recovery or business continuity plans. The ultimate answer, cyber resilience, can only be achieved by a company-wide integration of security policies, procedures, and technologies, which calls on leadership to adopt a more comprehensive and intrinsic security strategy.
Resilience cyber insurance solutions
To assist provide enterprises an advantage over contemporary cyber threats, the EY organization and Dell technology have collaborated with industry experts to develop an intelligent cyber resilience platform driven by AI/ML technology. The two innovators combine Dell’s data security technologies and cyber resilience tactics with the comprehensive industry knowledge and vision of the EY team. Together, they bring a wealth of technology and experience to the table. With the help of this potent combination, businesses can transform a complicated environment into a multilayered defensive system that can endure both changing risk and severe digital upheaval.
The alliance excels at using these technologies with the appropriate setup and procedures. The correct operational approach and the latest technology advances work together to create true cyber resilience, and each firm has a distinct optimal approach. Teams from EY and Dell are excellent at providing cybersecurity solutions that work as well as a tried-and-true process for operationalizing them to increase resilience, flexibility, and overall security posture. In order to understand an organization’s data challenges and vulnerabilities and to customize a solution to meet their needs, the EY organization and Dell collaborate closely with leaders in the industry. This allows the organization to secure its critical data from cyber threats while maintaining accessibility for daily operations.
Strengthen Your Cybersecurity Hardiness with Dell and EY
The partnership between EY and Dell Technologies gives progressive companies the adaptability they need to use advanced cybersecurity to fend off attackers and withstand changing threats. When together, they support organizations by:
Utilize an integrated, unified cyber resilience solution to handle the ever-increasing complexity of the technological and security environments.
Using a cross-functional collaborative strategy, bring all aspects of your firm under the cyber resilience umbrella.
Change the way you think about security in your firm and adopt a comprehensive strategy to cyber resilience that integrates procedures, policies, and resources across the whole enterprise.
Read more on govindhtech.com
#cyberresilience hashtag#cybersecurity hashtag#ey hashtag#dell hashtag#cyberthreats hashtag#genai hashtag#ml hashtag#ai hashtag#technology hashtag#technews hashtag#govindhtech
0 notes
Text
#For a report on the Attack Surface Management Market#you can use the following hashtags:#AttackSurfaceManagement#CyberSecurity#CyberThreats#ITSecurity#SecurityManagement#RiskManagement#CyberDefense#SecuritySolutions#ITInfrastructure#ThreatDetection#VulnerabilityManagement#DigitalSecurity#MarketResearch#CyberRisk#SecurityAnalysis
0 notes
Text
Code42 Highlights Cybersecurity Research that Reveals Organizations Feel Most Ill-Equipped to Detect Insider Attacks as well as Develop and Test Applications
Code42 Highlights Cybersecurity Research that Reveals Organizations Feel Most Ill-Equipped to Detect Insider Attacks as well as Develop and Test Applications

Hosts live webinar with Cyberedge Group to recap results from the 2019 Cyberthreat Defense Report
MINNEAPOLIS–(BUSINESS WIRE)–lt;a href="https://twitter.com/hashtag/cyberattack?src=hash" target="_blank"gt;#cyberattacklt;/agt;–Code42, the leader in next-gen data loss protection, announced that it will co-host a complimentary live webinarentitled, “Insider Threat: Still an Unsolved…
View On WordPress
0 notes
Text
The right balance: Enabling women to pursue a career in IT

This year, International Women’s Day centers around the theme of #BalanceforBetter, a message I think is particularly apt in my industry, cybersecurity.
The hashtag is a shortened version of the sentiment, “Better the balance, better the world,” and indeed, issues of gender imbalance in the industry have never been more important. Cybersecurity currently lacks a high proportion of female talent, with estimates suggesting nearly 90% of the workforce is male. Research Kaspersky Lab undertook earlier this year found that in the IT industry in general, half of respondents reported working on majority-male teams, six times the number who work on a team that is mainly female.
I grew up in Yugoslavia, where a passion for, and career in, computing was not unusual for a woman. At university, 70% of my computing course was female — and that was the norm; women in Eastern Europe had always been encouraged to pursue technical careers. When I moved to Western Europe to complete my masters, that number became just 7% — a real culture shock — and I began my career in programming among very few women. Moving into a customer-facing, presales role, I stood out as a young woman dressed in a bright outfit in a sea of black suits. However, I used this to my advantage, knowing that I would at least be remembered for being different, which helped me build some strong commercial relationships.
Now, I want more women to see that a technical career, and especially one in cybersecurity, is rewarding and worth pursuing. At the same time, I also want to make sure the environment they’re coming into is welcoming and supportive.
At Kaspersky Lab, we are proud of the many women who contribute to our mission, from the second-in-command of sales to those working on the research and development teams to protect against cyberthreats. But we want to do more. We want more enthusiastic and driven women to join our teams and help us save the world by bringing different experiences and viewpoints to the task. It’s not just that a career in this industry benefits women; the industry benefits from a more diverse workforce.
In my conversations with Jane Frankland, author of InSecurity: Why a Failure to Attract and Retain Women in Cybersecurity is Making Us All Less Safe and an advocate for women in cybersecurity, we discussed the ways women bring a different approach to threat and risk issues that really helps create a more secure online world.
The solutions to bridging the divide are not difficult ones. Earlier this year, we asked women already in the industry what they think the answer is. Of female IT decision-makers, 40% believe the government and universities should drive incentives to attract girls and women into a future career in tech, but that companies such as Kaspersky can also take action by supporting these wider initiatives and breaking down both real and perceived barriers to entry.
How can we bring more women to the #IT industry? We talked to a few of the women at @kaspersky to get their thoughts: https://t.co/fx5gTBL2Zk #WomenInScience #WomenInTech #CodeLikeaGirl pic.twitter.com/QiyA0SMYQf
— Kaspersky Lab (@kaspersky) February 11, 2019
At Kaspersky Lab, we take the view that we always want the best person for the job, no matter the gender, and hire everyone on that basis. That said, we know more needs to be done to encourage and support women in our industry, so in the past year, we have taken more steps than ever before to tackle the gender imbalance and help make cybersecurity a more welcoming environment for women. Therefore, we signed up with PwC’s Tech She Can charter to encourage more young girls enter tech careers, and we supported Girls in Tech’s AMPLIFY competition, which gives tech start-ups run by women a chance to grow. We also introduced our own Women’s Network, currently a pilot in the UK, to engage our existing women with the wider industry. This year, we are committing to making internships more accessible to a wider audience and promoting introductory workshops to give young people a glimpse into what a career in this industry involves and provide opportunities to meet mentors and experts to help them get started.
Our approach is very much about taking action to achieve balance and a more effective workforce — we don’t need any more discussion around the issue; we need to get on with the job of creating a more diverse, more secure industry.
0 notes
Text
We urgently require an approach to guard against online purposeful publicity Notwithstanding years of phony news on the web, regardless we have no clue how to shield against it.
We've taken in something from the examination concerning whether Russia intruded in the US race that has nothing to do with governmental issues. People are more helpless than any other time in recent memory to purposeful publicity, and we do not understand what to do about it.
Online networking as weapon
Another report in The Washington Post uncovers that the Obama organization and knowledge group thought about Russian endeavors to disturb the 2016 race a very long time ahead of time. Be that as it may, they did for all intents and purposes nothing, for the most part since they didn't suspect assaults from weaponized images and promulgation bots.
Previous representative national security counsel Ben Rhodes told the Post that the individuals from the knowledge group concentrated on more customary computerized dangers like system entrance. They needed to counteract email breaks, and they additionally stressed over Russian agents disturbing voting machines. "From multiple points of view... we managed this as a cyberthreat and concentrated on ensuring our foundation," he said. "In the mean time, the Russians were playing this considerably greater amusement, which included components like discharged hacked materials, political publicity, and engendering counterfeit news, which they'd sought after in different nations."
Rhodes' remarks dovetail with numerous different reports in the course of recent years spotlighting how Russia has been sharpening its web-based social networking purposeful publicity abilities. A year ago, Time distributed a gigantic report in which senior knowledge authorities discussed how Russians putting on a show to be American voters penetrated web-based social networking gatherings, spread intrigue stories by means of Facebook represents anecdotal media outlets, and purchased Facebook promotions to spread phony news.
Any individual who has ever surrendered to the clickbait features on Russia Today realizes that Russian media hacks are proficient at making wet images of amazing stickiness. The odd part is that those hacks are presently working close by state-supported programmers. We don't regularly consider Facebook posts as a "cyberthreat," yet now we have abundant confirmation that they are.
In 2015, The New York Times distributed an article by Adrian Chen about Russian "troll ranches" loaded with individuals paid to post expert Putin remarks via web-based networking media. After a year, Chen found that a significant number of the Russian troll accounts had moved toward becoming "phony moderates" posting about Trump. In an examination distributed the day preceding the race, specialists at USC uncovered that 20 percent of race related tweets originated from a multitude of 400,000 bots that seemed to begin in the US territory of Georgia.
"Try not to nourish the trolls" isn't sufficient
We realize that these sorts of bot-driven images trick common individuals, to some extent as a result of two unique episodes including counterfeit news about Ebola flare-ups. In 2014, a US nurture endeavored to come back to her Maine home in the wake of treating Ebola patients in West Africa. That is the point at which the joke news site Amplifying Glass ran a tale about how she was being dealt with in a doctor's facility for side effects of Ebola (she was not, and she was alive and well). The story picked up so much footing that the medical attendant was kicked out of her condo by a landowner who dreaded introduction to the infection.
Two or after three months, the Russian troll cultivate that Chen took after for The New York Times tried its forces with its own phony Ebola story on Twitter. The homestead utilized its a huge number of records to spread disinformation about an anecdotal flare-up of Ebola in the province of Georgia. For some time, the story was so well known and generally shared that the hashtag #EbolainAtlanta was drifting in Georgia.
The Ebola stories are only two cases of how normal individuals get taken in by counterfeit news—now and then with desperate results. Regardless of whether it's a story in The Onion or phony news spread by state-supported trolls, individuals get bulldozed by it. Furthermore, this has been continuing for quite a long time. So for what reason isn't there a phony news blocking instrument yet?
We should return for a minute to the response that the Obama organization had when it understood that Russians were spreading counterfeit news on US online networking systems. The organization had no clue how to battle image assaults without seeming to be divided. In the event that Obama had turned out quickly and cautioned individuals to be careful with counterfeit news that influenced Clinton to look terrible, he would have been pilloried. What's more, all things considered: such an announcement sounds precisely like the sort of purposeful publicity he needed to stop. So the Obama camp occupied with a strategy that goes back to the soonest days of the Web: don't encourage the trolls. Rather than getting out Russia's purposeful publicity bots, the organization said nothing.
What's more, that is essentially where we're at with counterfeit news all the more for the most part. There have been feeble endeavors by Facebook and Google to name news as "questioned" on the off chance that it may be phony. In any case, we require more than that. We have to on a very basic level change individuals' desires with regards to what they're perusing on the web.
More interesting peril for Internet news
The issue is that the vast majority weren't raised to expect that their social spaces would be loaded with bots, babbling the aftereffects of straightforward calculations and tainting human discussions with confusion. Once in a while do gatherings of people on Twitter and Facebook respite to ponder where their data is originating from.
So what could possibly be done? Helping Americans comprehend the contrast between honest data and pernicious purposeful publicity is a bipartisan issue. Furthermore, as I said prior, it goes route past governmental issues. Organizations offering a quack remedy "cures" have everything to pick up from counterfeit wellbeing news, for instance. Same goes for different vendors. Promoting organizations frequently contract online networking groups to seed discussions and remark areas with positive audits of diversions and films keeping in mind the end goal to influence popular assessment and find business.
It could be said, web-based social networking gatherings of people require fundamental "more peculiar threat" lessons. Each child realizes that the decent individual offering treat and a ride may really be endeavoring to seize them. We require similar impulses in online open spaces, as well. The well disposed individual tweeting at you from Georgia may really be a bot under the control of Russian programmers. Try not to trust Internet individuals until the point when you know them.
A standout amongst the most cheerful reactions I've seen to these issues has originated from an impossible place: the Girl Scouts of America. The gathering has recently made a cybersecurity identification that young ladies can win close by more customary identifications for abilities like outdoors, medical aid, and music (evidently the "whittling" identification I was so pleased with as a child is never again advertised).
It's urging to see the Girl Scouts instructing cybersecurity to kids, since this is the sort of fundamental expertise that individuals will require like never before in years to come.
Maybe the following stage will urge instructors and bookkeepers to show kids protective web-based social networking abilities. Lessons would begin with the nuts and bolts, similar to how to discover the hotspots for an article and how to comprehend who has made alters on Wikipedia. Further developed understudies could be prepared to perceive the sorts of bots that are utilized as a part of publicity battles. In the long run, understudies could figure out how to construct devices that square known wellsprings of vindictive data, much the way Block Together attempts to keep the spread of trolling and sockpuppet armed forces on Twitter.
We're in the beginning periods of making sense of how to shield against weaponized images, however that doesn't mean we won't have the capacity to do it. At last, there is a barrier for each assault. Be that as it may, first we need to perceive the risk.
0 notes
Text
Code42's Data Security "Red Team" Experts to Discuss Best Practices for Proactive Cyberthreat Protection During Live Webinar
Code42’s Data Security “Red Team” Experts to Discuss Best Practices for Proactive Cyberthreat Protection During Live Webinar

MINNEAPOLIS–(BUSINESS WIRE)–lt;a href="https://twitter.com/hashtag/datasecurity?src=hash" target="_blank"gt;#datasecuritylt;/agt;–Code42, the leader in next-gen data loss protection, announced that it will host a complimentary live webinarentitled, “Tips From the Trenches: Blue and Red Teams.” The webinar will be co-presented by leaders from Code42’s security team, who plan to share…
View On WordPress
0 notes