#deepweblink
Explore tagged Tumblr posts
Photo
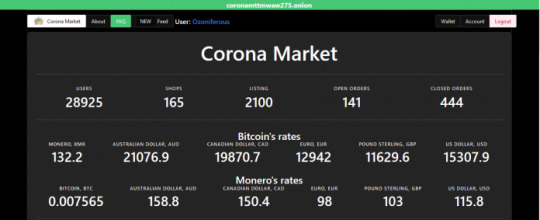
Corona Market is a state-of-the-art dark web market with a wonderful frontend offering safety, speed, and a fairly large variety of drugs. It supports payments in Bitcoin (BTC) and Monero (XMR).You can pay via both Monero and Bitcoin using traditional escrow and FE payment methods. Monero is strongly recommended for both anonymity and security.
0 notes
Text
Dark Web Tools and Services That Present Enterprise Risk
Dark Web Definition

Deep Web is the major part of the internet which consists of 90% of the internet. The other two parts comprises the internet world is the surface web and the Dark Web. The Dark Web is sometimes also referred to it as the Darknet. To understand all the three layers of the internet that consists of all the three layers mentioned above, the image that mostly resembles is the picture of an iceberg that is afloat.
The top most part of the iceberg that is visible from the outside can be understood as the surface web. The crust of the iceberg is also known as the visible web. The visible web comprises of web pages, websites that are listed in the search engines. Search engines like Google, Bing and Wikipedia have all the web pages in their directories. All the search results a user makes are tracked monitored and listed by the traditional search engines.
The dark web is accessed by using special software and web servers called centralized computers hosting webpage’s. The most common of these special software are TOR [The Onion Router] and I2P [Invisible Internet Project], says J. Eduardo Campos, formerly a cyber security advisor for a major tech company and currently co-founder of the consulting firm Embedded knowledge.
Dark Web Tools and Services That Present Enterprise Risk
The web tools and services that affect an organization which pose as a threat in the form of network breach or data comprise when the system gains access to Deep Web directories which is accessed with the help of Tor .onion urls directories.
· Infection or attacks, including malware, distributed denial of service (DDoS) and botnets
· Access, including remote access Trojans (RATs), key loggers and exploits
· Espionage, including services, customization and targeting
· Support services such as tutorials
· Credentials
· Phishing
· Refunds
· Customer data
· Operational data
· Financial data
· Intellectual property/trade secret
· Other emerging threats
Malware:
The Dark Web Links play a vital role in the spreading communities of malware developers; the principal Darknet are privileged environments for malware authors and botmasters. The numerous black marketplaces are excellent points of aggregation for malware developers and crooks that intend to pay for malicious code and command and control infrastructures. The use of Darknet represents a design choice for malware developers that use them to hide the command and control servers.
The list of malicious malware that were exploiting both the Tor network and I2P dark net to hide their command and control servers are as follows:
i) Malware Using C&C In The Darknet:
Many types of malware are directly controlled by servers hosted on both Tor and I2P, and it is quite easy to find Ransom-as-a-Service (RaaS) in the Darknets. Below just a few examples of malware that were discovered in the last 12 months leveraging Darknets for their operations:
· 2017 – MACSPY – Remote Access Trojan as a service on Dark web
· 2017 – MacRansom is the first Mac ransomware offered as a RaaS Service.
· 2017 – Karmen Ransomware RaaS
· 2017 –Ransomware-as-a-Service dubbed Shifr RaaS that allows creating ransomware compiling 3 form fields.
ii) Shifr RaaS Control Panel
Malware authors use to hide C&C servers in the Darknet to make botnets resilient against operations run by law enforcement and security firms. The principal advantages of Tor .onion urls directories based botnets are:
· Availability of Authenticated Hidden Services.
· Availability Private Tor Networks
· Possibility of Exit Node Flooding
Security researcher use traffic analysis to determine to detect botnet activities and have proposed different options to eradicate it
· Obscuration of the IP addresses assigned to the C&C server
· Cleaning of C&C servers and of the infected hosts
· Domain name revoke
· Hosting provider de-peered
Remote Access Trojans (RAT):
It is a malware that infects remote computers and allows a remote attacker to control the computer for malicious purposes. They disguise as a legitimate program or file. After infecting a target device the threat actor gets accessed to the victim’s computer.
How to Prevent RAT from Vicious Attack:
Steps To Avoid Remote Access Trojans
a) Do not click suspicious links and do not download emails sent by unknown users.
b) Keep your computer updated with trusted anti-malware programs and make sure you update them regularly.
c) Configure your firewall in your computer regularly. If a malware infects a computer, it should not spread to other system in the network so easily.
d) Keep your operating system updated with recent patches and if possible use a virtual machine to access the internet.
Espionage (Targeting and Customization):
Intelligence on competitors gathered in a legal way can give a leg up in the fight for market share. But sometimes it’s not enough. Competitors send spies to gather information more often than you would think, judging by the news. Industrial espionage embraces illegal and unethical methods of collecting corporate data. It involves stealing intellectual property and trade secrets to use them for a competitive advantage. The theft of economic information sponsored by foreign states is called economic espionage. It’s done not just for profit but for strategic reasons. Usual targets of industrial espionage are:
· Trade Secrets: While definition of “trade secret” varies from country to country, it generally means protected information about existing products or products in development. This information may help your rivals make their products more competitive or even bring a similar product to the market faster than you can.
·Client Information: Data of your clients, including their financial information, can be used to steal business or can be leaked to damage the reputation of your company.
·Financial Information: Financial information about your company can be used to offer better deals to your clients and partners, win bids, and even make better offers to your valuable employees.
·Marketing Information: This will allow your competitors to prepare a timely answer for your marketing campaigns, which, in turn, may render them ineffective.
Steps to help avoid trouble with the Dark Web
Once data ends up on the Dark Web Links Hidden Wiki there's very little that can be done about it. It's best to avoid this from happening to your company, employee or customer data. The following best practices can help.
1. Prohibit employees from using Tor .onion url directories
If employees are allowed to access the TOR network, they can easily expose your company to damaging material and/or malware. This would be particularly detrimental to your corporate network, says Wagner. Provide clear guidance in employee manuals and train employees on 'clean' internet use, advises cyber security attorney Braden Perry, a partner with Kennyhertz Perry. Use software to block TOR. Make it clear that corporate investigations will be initiated if management suspects that this rule is being broken.
2. Educate employees on security protocols.
The end user is the weakest link in your protective measures for your network, says Campos. This means it's important to teach all employees about cyber security measures and compliance with your company's policies, he says. The more aware and trained your employees, the better. He went on to add.
3. Limit employee access to sensitive data. It's a good idea to operate on a need-to-know basis when it comes to company data. The fewer employees who have access to company and client sensitive data, the less likely your company is to experience a breach.
0 notes
Text
Differences between Deep Web and Dark Web
One of the most common questions people have about the existence of the Dark Web and the Deep Web is the differences between them. It has been seen a multiple times that people tends to confuse between both the terms while use them interchangeably resulting in a total mess. Well, in this article, I will be clearing the major confusion between the Deep Web and the Dark Web. Also, as a bonus, a different part of the internet will be revealed. To know about everything in details, please read the article till the end.
What Does Deep Web And Dark Web Essentially Mean?
The internet is a huge place and is divided into two basic segments. The first one is the surface web while the other one is the Deep Web. The surface web (also known as ClearNet) is that part of the internet that is accessible to the general public through standard browsers like Google Chrome, Mozilla Firefox, and Internet Explorer etc. The Deep Web on the contrary, is that part of the internet that has been kept hidden from the general people and contains humongous information. This information is very confidential and thus requires a covered space out of the reach of the common people via the general search engines. The Dark Web is just a smaller division of the Deep Web, probably 0.01% and should not be used interchangeably. The Dark Web deals with certain illegal activities as well.
What Does Deep Web and Dark Web Bears in Them?
The Deep Web acquires a larger part of the internet or more precisely the submerged internet. It mostly contains the benign websites such as the password protected email accounts, databases, certain parts of the paid subscription or premium account information such as Netflix or the websites that are accessible through an online form located in the Deep Web Directories. As the matter of fact, it would be too easy to access your email account by searching just your name if Deep Web would not have existed and there would just have been only one internet as a whole, the surface web. The Deep Web has an estimated size of 400-550 times (record of 2001) than that of the surface web.
The Dark Web on the other hand is relatively small than that of the Deep Web and the Dark Web websites accounts to just thousands. The websites that are located in the Dark Web are especially characterized by their application of encryption method and software that makes the users, their identities and location, all anonymous. The encryption feature of the Dark Web has made the conduction of illegal activities much easier. The illegal activities include pornography, illegal drugs and firearms sale, services such as hire-hitman, human trafficking, gambling. Unlike the Deep Web, the Dark Web contains a lot of Dark Web markets that helps in the procurement of illegal stuffs giving rise to illegal activities and services. As for example, there are even instances of tutorials floating in the Dark Web that clearly states how to cook a woman live. Yes! It’s that scary and hideous place.
Secret Place on the Hidden Web
One of the other facts that come our way while stating about the Dark Web and is not available on the Deep Web is the existence of Red Rooms. Well, Red Room might give you the visuals of a room in red colour, but this is not exactly what Red Room deals with. So, what exactly is a Red Room? Red Room is probably a room where illegal activities such as murders and physical tortures are openly shown against payments in Bitcoins or Cryptocurrencies. The viewers pay a lot of money in Cryptocurrency to the moderators of the websites carrying on such activities for watching a complete session. They even place bids for watching a particular torture done in the red room. Terrorist groups are often involved in these.
To conclude,Dark Web and Deep Web though exist in the same realm are way different from each other. While Deep Web serves as the storehouse or chest for the humongous information related to the organizations (both government and public), Dark Web relatively serves as the section of the internet where mostly illegal activities are carried on. The Deep Web does not contain anything called the Red Room while the Dark Web possesses Red Room concept. Markets are available on Dark Web while Deep Web does not contain any sort of markets. To access the sites in Deep Web, one has to have the address for the particular website as the websites are hidden and its access is limited. In order to access the Dark Web websites, one has to use the TOR browser, VPN and .onion links
0 notes