#injectionattacks
Explore tagged Tumblr posts
Text
How to Prevent

Preventing injection requires keeping data separate from commands and queries:
The preferred option is to use a safe API, which avoids using the interpreter entirely, provides a parameterized interface, or migrates to Object Relational Mapping Tools (ORMs). Note: Even when parameterized, stored procedures can still introduce SQL injection if PL/SQL or T-SQL concatenates queries and data or executes hostile data with EXECUTE IMMEDIATE or exec().
Use positive server-side input validation. This is not a complete defense as many applications require special characters, such as text areas or APIs for mobile applications.
For any residual dynamic queries, escape special characters using the specific escape syntax for that interpreter. (escaping technique) Note: SQL structures such as table names, column names, and so on cannot be escaped, and thus user-supplied structure names are dangerous. This is a common issue in report-writing software.
Use LIMIT and other SQL controls within queries to prevent mass disclosure of records in case of SQL injection.
bonus question: think about how query on the image above should look like? answer will be in the comment section
4 notes
·
View notes
Photo

Server Side Template Injection Payloads | MrHacker.Co #codesecurity #injection #injectionattacks #payload #payloads #hacker #hacking #cybersecurity #hackers #linux #ethicalhacking #programming #security #mrhacker
0 notes
Text
Server Side Template Injection Payloads
Server Side Template Injection Payloads #CodeSecurity #injection #InjectionAttacks #Payload #Payloads
[sc name=”ad_1″]
Server-side template injection is when an attacker is able to use native template syntax to inject a malicious payload into a template, which is then executed server-side.
Template engines are designed to generate web pages by combining fixed templates with volatile data. Server-side template injection attackscan occur when user input is concatenated directly into a template,…
View On WordPress
#Code Security#injection#Injection Attacks#Payload#Payloads#Remote Code Execution#Server#Server Side Template Injection#Side#Source Code Analysis#SSTI#SSTI-Payloads#Template
0 notes
Text
Tweeted
SQL Injection Payload List https://t.co/zKNFm7p3wx #InjectionAttacks #InjectionPayloads #SQLInject #SQLInjection #SQLInjectionAttack pic.twitter.com/3FED0uaNlf
— ☣ KitPloit - Hacker Tools (@KitPloit) November 22, 2019
0 notes
Text
Statistics
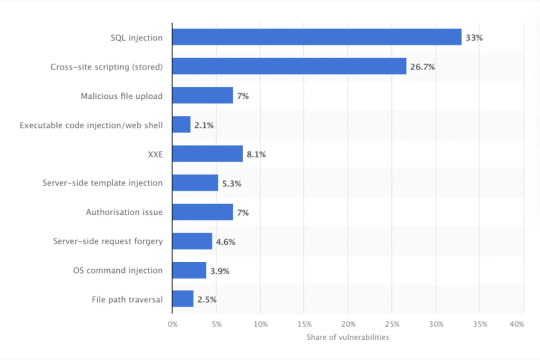
source: statista 2022 In 2023, SQL injection attacks were responsible for 23% of web application critical vulnerabilities discovered globally compared to 2022, where they were 33%. They remain one of the most prevalent security risks for web applications, despite a decline in its share of critical vulnerabilities from 33% in 2022 to 23% in 2023. This decrease indicates an improvement in secure coding practices and database security, but SQLi still poses a significant risk. ! this is why it it so important to share awareness and mitigation/defense measures on injection attacks
3 notes
·
View notes
Text
!
Many people treat injection only as an input validation problem (CWE-20) because many people do not distinguish between the consequence/attack (injection) and the protection mechanism that prevents the attack from succeeding. However, input validation is only one potential protection mechanism (output encoding is another), and there is a chaining relationship between improper input validation and the improper enforcement of the structure of messages to other components. Other issues not directly related to input validation, such as race conditions, could similarly impact message structure.
2 notes
·
View notes
Text
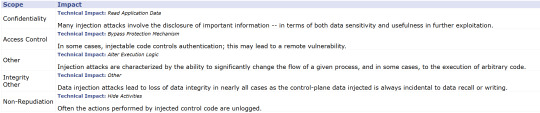
The table represents common consequences associated with the injection attacks and their impact on CIA (Confidentiality, Integrity, Availability). The Scope identifies the application security area that is violated, while the Impact describes the negative technical impact that arises if an adversary succeeds in exploiting this weakness. Injection attacks are marked with the likelihood of exploit of High.
3 notes
·
View notes
Text
The core of injection attacks
The most important issue to note is that all injection problems share one thing in common — i.e., they allow for the injection of control plane data into the user-controlled data plane. This means that the execution of the process may be altered by sending code in through legitimate data channels, using no other mechanism. While buffer overflows, and many other flaws, involve the use of some further issue to gain execution, injection problems need only for the data to be parsed. The most classic instantiations of this category of weakness are SQL injection and format string vulnerabilities.
2 notes
·
View notes
Text
Description
An application is vulnerable to attack when:
User-supplied data is not validated, filtered, or sanitized by the application.
Dynamic queries or non-parameterized calls without context-aware escaping are used directly in the interpreter.
Hostile data is used within object-relational mapping (ORM) search parameters to extract additional, sensitive records.
Hostile data is directly used or concatenated. The SQL or command contains the structure and malicious data in dynamic queries, commands, or stored procedures.
The concept is identical among all interpreters of injection attacks (e.g. SQL, NoSQL, OS command, Object Relational Mapping (ORM), LDAP, and Expression Language (EL) or Object Graph Navigation Library (OGNL) injection)
Strongly encouraged automated testing of:
All parameters
Headers
URL
Cookies
JSON
SOAP
XML data inputs
Organizations can include:
Static (SAST)
Dynamic (DAST)
Interactive (IAST)
application security testing tools into the CI/CD pipeline to identify introduced injection flaws before production deployment.
3 notes
·
View notes