#kryptoagile
Explore tagged Tumblr posts
Photo
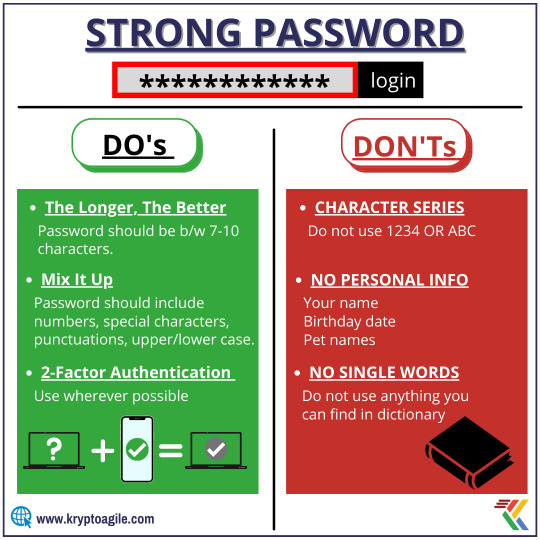
LONGER PASSWORDS MAKE STRONGER PASSWORDS. Keep these things in mind and Make your password as strong as possible. Don't let anybody else use it, and get a new one every six months. ➖➖➖➖➖➖➖➖ To Know More, Reach Us Today... https://www.kryptoagile.com
#It Security#IT security solutions#it solutions#strong password#Password policy#kryptoagile#cybersecurity#online security
0 notes
Text
Global Hardware Security Modules Market Growth, Analysis, and Forecast 2022-2027
Global Hardware Security Modules Market was valued at USD 1.2 billion in 2021 and is expected to reach 2.6 billion by 2027, at a CAGR 9.85% from 2022-2027.
Hardware Security Modules (HSM) is defined as a piece of hardware and associated software or firmware which is attached to and placed inside a particular hardware that serves cryptographic functions. Its functions mainly include encryption, decryption, management or generation and hashing. HSM systems can securely back up the keys that could be handled using some external security token such as smart cards or via operating systems of the computer.
Get a Sample Copy of this Report@ https://qualiketresearch.com/request-sample/Hardware-Security-Modules-Market/request-sample
Market Drivers
The major factor leading to the increasing growth of the hardware security modules market is growing data security concerns in all the data sensitive companies globally. Hardware security modules are responsible for efficiently storing and managing cryptographic keys. Comprehensive data protection will lead to increased demand for hardware security modules in near future, resulting in market development.
Furthermore, the growing usage of Hardware security modules in government and defense sectors has recently been identified as a critical reason for industry growth.
Market Restraints
Hardware security modules are costly and very expensive. This is one of the reasons that is holding back the growth in the hardware security modules market because currently, only very large companies can afford to use them.
Market Segmentation
The Global Hardware Security Modules Market is segmented into, type, deployment type, application, sales channel, and industry vertical. The type segment has further been segmented into remote interface, local interface, smart cards, and USB tokens.
Regional Analysis
The Global Hardware Security Modules Market is segmented into five regions such as North America, Latin America, Europe, Asia Pacific, and Middle East & Africa.
The North American region is expected to hold a major share in the hardware security module market. Growth in this region is attributed to penetration and adoption of security modules, and presence of a large number of vendors across the region.
Get Discount on this Report@ https://qualiketresearch.com/request-sample/Hardware-Security-Modules-Market/ask-for-discount
Key Players
Various key players are discussed into the Global Hardware Security Modules Market Report including: Thales Group (Gemalto), Utimaco GmbH, Futurex, Adweb Technologies, Yubico, Atos, Ultra Electronics, SPYRUS, Inc., Securosys, Entrust Corporation, Nitrokey, Kryptoagile, IBM Corporation, and others.
Market Taxonomy
By Type
Local Interface
LAN-based HSMs/Network-attached HSMs
PCIe-based/Embedded Plugin HSMs
Remote Interface
Smart Cards
USB Tokens
By Deployment Type
On-Premise
Cloud
By Application
Authentication
Database Encryption
Document Signing
Secure Socket Layer (SSL)
Code Signing
PKI/Credential Management
Payment Processing
Application-Level Encryption
By Sales Channel
Direct Sales Channel
Distribution Channel
Integrators
Distributors
VARs
By Industry Verticals
Banking
Financial Institutions
Government
BFSI
Technology and Communication
Industrial
Manufacturing
Energy and Utility
Retail and Consumer
Healthcare and Life Sciences
Other (Transportation, Automotive, and Hospitality)
By Region
North America
Latin America
Europe
Asia Pacific
Middle East & Africa
Browse Full Report https://qualiketresearch.com/reports-details/Hardware-Security-Modules-Market
0 notes
Photo
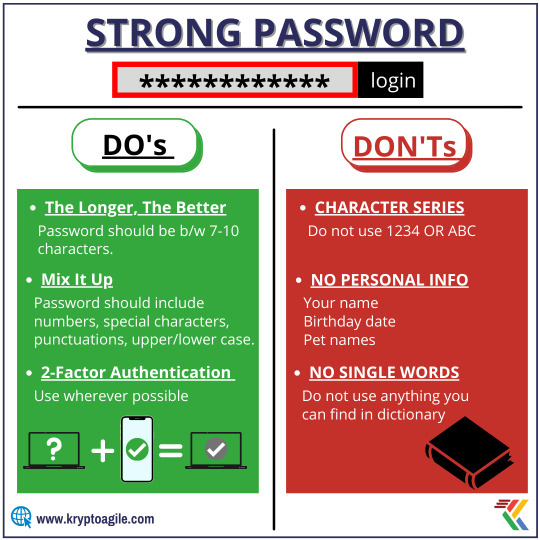
LONGER PASSWORDS MAKE STRONGER PASSWORDS. Keep these things in mind and Make your password as strong as possible. Don't let anybody else use it, and get a new one every six months. ➖➖➖➖➖➖➖➖ To Know More, Reach Us Today... https://www.kryptoagile.com/
#hsm#hardware security module#hsm vendors in india#Hardware Security Module price#kryptoagile#Itsecurity#ITservices#cybersecurity#cyber security solutions#data security#datasecuritysolutions
0 notes
Photo
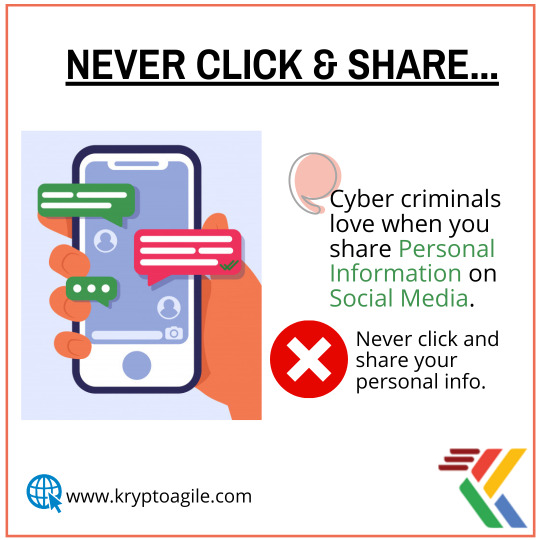
BE AWARE OF CYBER CRIMES AND FRAUDS. Ever ever share your personal and useful information with anyone and never click on unidentified email addresses. This is a good practice by criminals to hack your data and accounts. #beaware . . Reach us today: www.kryptoagile.com . . #cybercrime #crime #criminalminds #socialmedia #beawareofyourthoughts #hsmproviderindelhi #instagood #instagram #igers #hsmsupport #HSM #digitalsigning #delhi #india
0 notes
Text
"Best HSM Solutions Provider in Delhi, Mumbai, Chennai, Bangalore"
"Best HSM Solutions Provider in Delhi, Mumbai, Chennai. What is a hardware security module (HSM). Buy hardware security module. Get top cheap and best hsm solutions in delhi, mumbai."
https://www.kryptoagile.com/
0 notes
Text
Adhaar Authentication by Kryptoagile.
Aadhar authentication is a process of submitting the personal identity data to Central Identities Data Repository (CIDR) maintained by UIDAI. Explore more here: https://bit.ly/38gnlpL
1 note
·
View note
Text
Global Hardware Security Modules Market Trends, CAGR, and End User
Global Hardware Security Modules Market was valued at USD 1.2 billion in 2021 and is expected to reach 2.6 billion by 2027, at a CAGR 9.85% from 2022-2027.
Hardware Security Modules (HSM) is defined as a piece of hardware and associated software or firmware which is attached to and placed inside a particular hardware that serves cryptographic functions. Its functions mainly include encryption, decryption, management or generation and hashing. HSM systems can securely back up the keys that could be handled using some external security token such as smart cards or via operating systems of the computer.
Get a Sample Copy of this Report @ https://qualiketresearch.com/request-sample/Hardware-Security-Modules-Market/request-sample
Market Drivers
The major factor leading to the increasing growth of the hardware security modules market is growing data security concerns in all the data sensitive companies globally. Hardware security modules are responsible for efficiently storing and managing cryptographic keys. Comprehensive data protection will lead to increased demand for hardware security modules in near future, resulting in market development.
Furthermore, the growing usage of Hardware security modules in government and defense sectors has recently been identified as a critical reason for industry growth.
Market Restraints
Hardware security modules are costly and very expensive. This is one of the reasons that is holding back the growth in the hardware security modules market because currently, only very large companies can afford to use them.
Market Segmentation
The Global Hardware Security Modules Market is segmented into, type, deployment type, application, sales channel, and industry vertical. The type segment has further been segmented into remote interface, local interface, smart cards, and USB tokens.
Regional Analysis
The Global Hardware Security Modules Market is segmented into five regions such as North America, Latin America, Europe, Asia Pacific, and Middle East & Africa.
The North American region is expected to hold a major share in the hardware security module market. Growth in this region is attributed to penetration and adoption of security modules, and presence of a large number of vendors across the region.
Get Discount on this Report @ https://qualiketresearch.com/request-sample/Hardware-Security-Modules-Market/ask-for-discount
Key Players
Various key players are discussed into the Global Hardware Security Modules Market Report including: Thales Group (Gemalto), Utimaco GmbH, Futurex, Adweb Technologies, Yubico, Atos, Ultra Electronics, SPYRUS, Inc., Securosys, Entrust Corporation, Nitrokey, Kryptoagile, IBM Corporation, and others.
Market Taxonomy
By Type
Local Interface
LAN-based HSMs/Network-attached HSMs
PCIe-based/Embedded Plugin HSMs
Remote Interface
Smart Cards
USB Tokens
By Deployment Type
On-Premise
Cloud
By Application
Authentication
Database Encryption
Document Signing
Secure Socket Layer (SSL)
Code Signing
PKI/Credential Management
Payment Processing
Application-Level Encryption
By Sales Channel
Direct Sales Channel
Distribution Channel
Integrators
Distributors
VARs
By Industry Verticals
Banking
Financial Institutions
Government
BFSI
Technology and Communication
Industrial
Manufacturing
Energy and Utility
Retail and Consumer
Healthcare and Life Sciences
Other (Transportation, Automotive, and Hospitality)
By Region
North America
Latin America
Europe
Asia Pacific
Middle East & Africa
Browse Full Report https://qualiketresearch.com/reports-details/Hardware-Security-Modules-Market
0 notes
Text
TOKENIZATION – A REVOLUTION IN DATA ENCRYPTION
Tokenization is one of the optimum strategies used in computer science that allows sensitive data to be replaced by an identifying text string. In the concept of tokenization, this string is stored and known as token to help you keep the risk of exposing the original information at bay. No matter what industry we belong to, data plays a starring role everywhere, and helps us bridge the gap between our products and their prospective buyers. But, we can only reap its innumerable benefits, if it is stored per PCI requirements in a secured environment. Hence, the amalgamation of maintaining its secrecy and quick accessibility is one of the building blocks for any venture to stay ahead in today’s cut-throat competition.
The Hardware Security Modules (HSM) catered by Kryptoagile vouch for complete security of your data by helping you convert your sensitive data into secured tokens. Right after conversion, they can be exported or stored in a secured environment for reuse. In order to fetch the data back, the respective token is sent to the token database. Once the token is authenticated, the requested data is returned in a secured environment.
Tokenization has become extremely popular owing to its integration with multiple business verticals to safeguard their sensitive data. And, at times integrating it with any organization’s cryptographic infrastructure may become a daunting task. But, with Kryptoagile’s HSM devices, it becomes as easy as counting 1, 2, 3.
This eminent technology is majorly used in card based payment processing for various financial transactions. According to Payment Card Industry Data Security Standards (PCI DSS), the stored data of any cardholder needs to be in unreadable format. But, at times retailers, traders need the cardholder’s data if any transaction requires to process the request pertaining to refund, additional purchase, etc. Through tokenization, we can reduce the scope as well as cost of PCI compliance since the cardholder’s data gets converted into secured tokens. Let’s understand it through healthcare industry, which includes highly sensitive data pertaining to patient’s treatment, diagnosis, tracking, etc. Compromising data in this field may lead to major health issues, and national/international emergencies as well. Well! Here the significance of tokenization certainly remains on rise due to the criticality of business. The same goes in case of education industry where in managing various educational records including student record, payment details, academic research can be an uphill task in the absence of tokenization.
Kryptoagile’s Vision towards Tokenization
The foundation of tokenization solutions designed by Kryptoagile is based on two core concepts including automation and customization backed by infallible encryption architecture. This fusion enables the user to experience holistic solutions for their business environment.
Customization
Unlike the tokenization technology integrated in the HSM devices by various HSM providers, Kryptoagile’s tokenization integrated products are not merely known for providing black box solution. They are acknowledged as smart boxes that include intuitive user interface to let system administrators define customized parameters for unique tokenization process per their organization. It facilitates the user to set various variables encompassing salt, bytes to output, masking characters and iteration count for every token created.
Automation
The automation mechanism of Kryptoagile’s products brings ease to the tokenization process if it is about integration. In order to integrate these HSM devices for tokenization, you just need to integrate a host application for communicating with HSM.
Hash-Based MACing (HMAC)
This technology is just like tokenization wherein a hashed message authentication code is used to authenticate and verify data. This hashed message authentication code is used in the form of string, which is responsible for producing tokens that need to be verified through host database for data conversion.
Point-To-Point Encryption (P2PE)
Safeguarding data at the time of capturing it can have the finest impact in terms of reducing the issues pertaining to data security and compliance. A point-to-point encryption (P2PE) solution is a fusion of secure devices and processes, which encrypts data right from the point of its interaction until it reaches the recipient for decryption.
Advanced Encryption Standard (AES) Encryption
If you are in the quest of an alternative to tokenization, AES encryption can be the best fit for you. It encrypts data per AES encryption algorithm. This data encryption mechanism is implemented in software as well as hardware for encrypting the data having sensitive nature.
0 notes
Link
#Digital Signatures#Digital Signature#digital signing#esign#esignature#eSigning#It Security#it security services#online security
0 notes
Text
"Best HSM for Aadhaar card Authentication - Aadhar API Supported"
Unique Identity Authority of India (UIDAI) is created to provide unique identity to all residents of India. UIDA has enrolled the citizens to provide online authentication using demographic and biometric data. The UID (also known as Aadhar) number that uniquely identifies a resident, allows them to establish their identity to various agencies in India. Aadhar is a permanent non-revocable identity. Citizens can prove their identity using their Aadhar credentials. In order to bring transparency in the whole Aadhar Authentication system, an Hardware Security Module (HSM) plays a vital role.
What Is Adhar Authentication?
Aadhar authentication is a process of submitting the personal identity data to Central Identities Data Repository (CIDR) maintained by UIDAI. UIDAI confirms the proof of identity after matching the submitted identity data with the data at CIDR. UIDAI defined a framework called Aadhar Authentication Framework to provide the details of the authentication types offered. Currently, Aadhar Authentication supports Demographic Matching, Biometric Matching, and additional features such as One-Time-Password (OTP). In India, various institutions use Aadhar authentication to establish their customers’ identity, confirming beneficiary, even attendance tracking in offices. It can be used for demographic data verification too.
For providing efficient authentication mechanism, UIDAI defined a structure with the service providers viz., Authentication User Agency (AUA), e-KYC agency (KUA) Sub-AUA (SA), Authentication Service Agency (ASA). AUA/SA/ AUA, KUA & SA are known as authentication user agencies
AUA – It is an entity using Aadhar authentication to provide services to their customers.
SA – It is an entity having business relationship with AUA offering specific services in a domain.
ASA – It is an entity that directly connects UIDAI through private secure connection for transmitting authentication requests from various AUAs.
Terminal Devices – Biometric capture devices, attached with terminals are used by SAs/AUAs in the Aadhar authentication process. These authentication devices must comply with specifications provided by UIDAI to protect all the biometric and demographic information. Moreover, authentication devices initiate the authentication request, create PID block, and forward to user authentication agency server for creating auth XML. To ensure integrity and non-repudiation, the XML must be digitally signed by the AUA/KUA and/or ASA. In e-KYC service e-KYC response data is encrypted. UIDAI mandates the use of FIPS 140-2 Level 3 certified Hardware Security Module (HSM) for digital signing auth XML and decryption of e-KYC data.
Kryptoagile provides FIPS 140-2 Level 3 compliant Hardware Security Modules to fully comply UIDAI directives.
Here are some of the advantages of hardware security modules offered by Kryptoagile:
Best suited for general purpose data processing
Digital document signing
PDF signing
GST signing
E-invoice signing
Extremely popular in financial data processing
Payment processing,
NEFT transactions,
RTGS transactions
Electronic fund transfer management
Powered with world's most advanced data encryption mechanism
Compatible with cross industry applications
#aadharauthentication#Aadhaar card authentication#aadhaar authentication solutions#Itsecurity#it security services
0 notes
Text
"Best PKI solutions and Hardware security module vendor in delhi, mumbai"
What is PKI or Public Key Infrastructure and what is the significance of PKI? These are the basic questions that need to be addressed prior to moving ahead. Well! A public key infrastructure is a system, which is used to implement public key encryption as well as digital signature services. It facilitates the user to manage keys and certificates to discover a secure network environment across multiple applications. Hence, the importance of public key cryptography can never be overlooked, as it enables you to secure your network, users, data and business process. The tech world has been moving at a lightning fast speed, and the credit for this revolution goes to the global communication. Be it any part of the world, the information from point ‘A’ to point ‘B’ can be reached within a blink of an eye. But, what if this sensitive information is tempered during its transmission? Well! The consequences can be hazardous because it may be a matter of critical information pertaining to anybody’s business or even personal life. Here comes the role of encryption or information security.
Thanks to PKI technology, which is designed to make sure that the respective data is accessible only by its authentic recipient (s). PKI encompasses asymmetric encryption wherein encryption and decryption are performed through public keys and private keys. Now, let’s understand the difference between public key and private key. Well! If we discuss public keys, they are only capable of encrypting data. Hence, they cannot decrypt data. In order to decrypt data, we need to use private keys. These asymmetric keys are created by certificate authorities that are responsible to manage the trees of keys from the reliable roots.
In order to implement PKI, one needs to connect with a trusted certificate authority for the creation of certificate tree. Beginning with the root certificate, which is considered highly secured, a series of new certificates are created under it per hierarchy. Now, these certs are given to various users, machines or objects that are required to be under secured network or communication. Moving on, by distributing the certificates through the same certificate authority across devices, users or other objects of communication, we establish a secured circle of communication.
Now, for initiating a secure communication, the objects, users or devices need to exchange public keys. For instance, if party ‘A” and party ‘B’ are establishing a secured communication, then they need to exchange their public keys with each other. These public keys will be used to encrypt their messages, which will be sent to each other. Right after receiving the encrypted value, it can be decrypted through the private key corresponding to the public key that encrypted the message. Sharing information through this medium is extremely easy and provides you with hardened security. Now, even if a message is intercepted during its transmission, it can never be readable owing to the encryption mechanism
Kryptoagile’s Vision for PKI
The solutions and products catered by Kryptoagile are known to be powered with the best PKI technology to help you experience highly secured IT infrastructure. The FIPS 140-2 level 3 validated devices of Kryptoagile are extremely useful for tracking, generating and managing your entire range of keys as well as certificates. And, the best part is, these tasks are performed within physically reinforced hardware to deliver the complete security of your PKI. Conglomerates that are aspiring to develop a secure public key infrastructure, the products and services offered by Kryptoagile can be the ideal pick for them. It includes:
Fastest signing and verification of files per data encryption standards
Quick and reliable validation of devices, users, documents, etc.
Simplified management, revocation and key tracking system
Hassle free export of certificate signing request
Swift generation of trusted roots
Apt Development of certificate trees
Acceleratedimport & export of mass certificate files
Appropriate assigning of certificate expiration period
The key management servers of Kryptoagile are designed to deliver the complete support for key and certificate lifecycle. The capability of being able to provide top-rated protection and comprehensive functionality makes these devices stand out from the crowd. It helps conglomerates to streamline the encryption key processes through a single solution by incorporating multiple devices or vendors to simplify the workflow management. If you are also planning to integrate PKI technology for your organization’s key management infrastructure, connect with Kryptoagile today.
#pki#pki solutions#pki solutions in delhi#pki solutions in india#Best PKI solutions#It Security#it security services#IT security solutions
0 notes
Text
"Best Digital document Signing Solutions online with best HSM solutions- Kryptoagile"
Electronic signing or digital signing is used in different ways to establish authenticity and non-repudiation. It is performed using long-term and short-term signature certificates with the help of hardware security modules. Let’s discuss it in detail.
What Is Long-Term Signature Certificate?
Long term signature certificates are obtained from Controller of Certifying Authorities in India (CCA) - licensed CAs. The user/subscriber needs to provide all the required information (e.g., identity, geographic location, etc.) according to the class of certificate they need. Usually, class-2 and class-3 certificates are obtained for legally valid signatures. And, users have complete control of their private key and certificates.
What Is Short-Term Signature Certificate?
Short term signature certificates are used for instant document signing. These certificates expire in very short period of time. Practically, each document signing requires a new certificate.
eSign architecture is defined by CCA on their website. According to CCA, it is mandatory to use FIPS 140-2 Level 3 hardware security modules when a user’s private key is used unattended. The private keys must be stored in the HSM for its entire lifetime. It is a well-known fact that security of the user keys is paramount. Use of HSMs protects the private keys. In addition, off-load cryptographic functions of application on the HSM improve the performance significantly.
And, HSMs offered by Kryptoagile are best suited to meet the compliance, security and signing performance with an extensive range of valuable features:
Support for various cryptographic algorithms such as 3DES, AES, RSA, ECC, HMAC, SHA-2
Intuitive graphic interface that brings ease to the cryptography process
Offers protected secure environment and ability to load your own software directly into the HSM
Hassle free and secure remote management along with Syslog support
Loaded with world's most advanced encryption mechanism
Compatible with cross industry applications
Here are some of the advantages of hardware security modules associated with electronic signing:
Digital document signing
PDF signing
GST signing
E-receipt signing
API based signing
Automated document signing
0 notes
Photo

Business becomes a lot easier with @kryptoagile ✨✨✨✨ LET'S GROW TOGETHER! 🙌 #trustedhsmprovider ✨✨✨✨ A hardware security module (HSM) is a physical device that provides extra security for sensitive data. Secure sensitive data of your customers and business. Get HSM support services today. https://www.kryptoagile.com/
0 notes
Text
ELECTRONIC SIGNING OR DIGITAL SIGNING THROUGH HARDWARE SECURITY MODULE
Electronic signing or digital signing is used in different ways to establish authenticity and non-repudiation. It is performed using long-term and short-term signature certificates with the help of hardware security modules. Let’s discuss it in detail.
What Is Long-Term Signature Certificate?
Long term signature certificates are obtained from Controller of Certifying Authorities in India (CCA) - licensed CAs. The user/subscriber needs to provide all the required information (e.g., identity, geographic location, etc.) according to the class of certificate they need. Usually, class-2 and class-3 certificates are obtained for legally valid signatures. And, users have complete control of their private key and certificates.
What Is Short-Term Signature Certificate?
Short term signature certificates are used for instant document signing. These certificates expire in very short period of time. Practically, each document signing requires a new certificate.
eSign architecture is defined by CCA on their website. According to CCA, it is mandatory to use FIPS 140-2 Level 3 hardware security modules when a user’s private key is used unattended. The private keys must be stored in the HSM for its entire lifetime. It is a well-known fact that security of the user keys is paramount. Use of HSMs protects the private keys. In addition, off-load cryptographic functions of application on the HSM improve the performance significantly.
And, HSMs offered by Kryptoagile are best suited to meet the compliance, security and signing performance with an extensive range of valuable features:
Support for various cryptographic algorithms such as 3DES, AES, RSA, ECC, HMAC, SHA-2
Intuitive graphic interface that brings ease to the cryptography process
Offers protected secure environment and ability to load your own software directly into the HSM
Hassle free and secure remote management along with Syslog support
Loaded with world's most advanced encryption mechanism
Compatible with cross industry applications
Here are some of the advantages of hardware security modules associated with electronic signing:
Digital document signing
PDF signing
GST signing
E-receipt signing
API based signing
Automated document signing
0 notes
Text
"Best Digital document Signing Solutions online with best HSM solutions- Kryptoagile"
Electronic signing or digital signing is used in different ways to establish authenticity and non-repudiation. It is performed using long-term and short-term signature certificates with the help of hardware security modules. Let’s discuss it in detail.
What Is Long-Term Signature Certificate?
Long term signature certificates are obtained from Controller of Certifying Authorities in India (CCA) - licensed CAs. The user/subscriber needs to provide all the required information (e.g., identity, geographic location, etc.) according to the class of certificate they need. Usually, class-2 and class-3 certificates are obtained for legally valid signatures. And, users have complete control of their private key and certificates.
What Is Short-Term Signature Certificate?
Short term signature certificates are used for instant document signing. These certificates expire in very short period of time. Practically, each document signing requires a new certificate.
eSign architecture is defined by CCA on their website. According to CCA, it is mandatory to use FIPS 140-2 Level 3 hardware security modules when a user’s private key is used unattended. The private keys must be stored in the HSM for its entire lifetime. It is a well-known fact that security of the user keys is paramount. Use of HSMs protects the private keys. In addition, off-load cryptographic functions of application on the HSM improve the performance significantly.
And, HSMs offered by Kryptoagile are best suited to meet the compliance, security and signing performance with an extensive range of valuable features:
Support for various cryptographic algorithms such as 3DES, AES, RSA, ECC, HMAC, SHA-2
Intuitive graphic interface that brings ease to the cryptography process
Offers protected secure environment and ability to load your own software directly into the HSM
Hassle free and secure remote management along with Syslog support
Loaded with world's most advanced encryption mechanism
Compatible with cross industry applications
Here are some of the advantages of hardware security modules associated with electronic signing:
Digital document signing
PDF signing
GST signing
E-receipt signing
API based signing
Automated document signing
https://www.kryptoagile.com/
#Digital Signatures#Digital Signature#Digital Signature Certificate Online#digitalsigning#Godigital#esign#esignature#ITservices#cybersecurity#cyberSecuritySolutions
0 notes