#label switching routers
Explore tagged Tumblr posts
Text
How to choose a router (2025): Tips, technical terms and advice
Wi-Fi 6 and Wi-Fi 6E devices certified by the Wi-Fi alliance must support WPA3, but it is not for new standards. You can find Wi-Fi 5 routers with WPA3 support and some manufacturers are deploying it on old devices through the updates of the base program. It is also opposite. Most routers will provide hybrids with WPA2/WPA3 labels to avoid problems when devices switch to new standard. There is no…
0 notes
Text
How to choose a router (2025): Tips, technical terms and advice
Wi-Fi 6 and Wi-Fi 6E devices certified by the Wi-Fi alliance must support WPA3, but it is not for new standards. You can find Wi-Fi 5 routers with WPA3 support and some manufacturers are deploying it on old devices through the updates of the base program. It is also opposite. Most routers will provide hybrids with WPA2/WPA3 labels to avoid problems when devices switch to new standard. There is no…
0 notes
Text
Netgear Router Setup Using Nighthawk App: Step By Step
Netgear router devices can easily be set up using the nighthawk app. Now you can manage the network from your smartphone very conveniently. Confused how to do it? Don’t know where to start? No worries, check out the further section of this article to get detailed information about the Netgear Router Setup Using Nighthawk App. Also in the next segment you will get installation information and troubleshoot common errors. Just scroll the page and configure your router now without any technical expertise.
Netgear Router Installation
Installation of the netgear router is a very easy task. First step is unboxing the router. Look for the placement closer to the host modem. Connect the router with the modem using ethernet. Must cut the power of the modem device before connecting the ethernet cable. Make sure the connection is secured. Then connect the modem and the router with the power. Wait for the LED light on the router device to get stable and then proceed with the netgear router setup process as specified below.
Netgear Router Setup
Begin the setup by using a smartphone, modem and working internet connection. Check out the steps you need to follow:
Download The Nighthawk App
Embark with the downloading of the nighthawk app on your smartphone device. You can use either android or iOS system devices. Open the store on your smartphone. Search for the nighthawk app. Then click on the install button and let the application download and install in the smartphone device. Before initiating the download make sure your device is connected with a stable internet connection.
Connect Smartphone With Router
After downloading the app you have to connect the same device with the router’s wireless network. Use the default SSID & password details mentioned on the device label.
First of all you have to go to the settings in your smartphone.
Next, you have to go to the WiFi option and turn it on.
Scan the router’s network name and choose it
Mention the password as on the label of the router.
Click on the connect option.
Let the device connect to the network.
Launch The App
Now, launch the nighthawk app you recently installed and follow the on screen instructions to proceed with the network configuration.
Configure Your Router
Initiate the configuration by choosing the language. After that you have to follow the on screen guide. Create a password for your wireless network. Also perform firmware updates, make additional security settings, and many more. After making all the important changes, submit the changes by clicking the apply option.
Troubleshoot Common Issues
Is your netgear router troubling you? Don’t know what the issue is? Don’t know how to resolve the problem? No worries, just follow the troubleshoot guide mentioned here:
No Internet Connection
One of the most common problems users face with the netgear router is a lack of internet access. If your netgear router is connected to the router but there's no internet then try following troubleshooting:
Restart your router and modem. Unplug both devices from power. Wait for about 30 seconds. Plug the device back again and wait for it to boot up.
Check the ISP connection. Many times the issue lies with your ISP. Try connecting directly via modem to confirm.
Update the firmware. Log in to your router via the Netgear web interface (usually 192.168.1.1) and check for firmware updates under the settings.
Slow Internet Speeds
In case your router network speed is slow then you should try following:
Reposition the router. Place it in a central location away from network troublers including walls, electronics, heavy metal objects etc.
Limit connected devices. Too many devices can strain bandwidth. Disconnect those not in use.
Use the 5GHz band. If your router is dual-band, switch to 5GHz for faster speeds (ideal for streaming or gaming).
Router Keeps Disconnecting
Facing sudden disconnections? Is your router keep disconnecting then follow below troubleshoots:
Check cables and connections. Loose or damaged Ethernet cables can cause drops.
Change the channel. WiFi interference from nearby can cause issue. Login to your router’s admin panel and switch the wireless channels to resolve the issue.
Factory reset. If issues persist, perform a factory reset by pressing and holding the reset button for 10 seconds.
Can't Access Router Login Page
If you are unable to access the router’s login page then follow these instructions:
Check the IP address. The default is often 192.168.1.1 or 192.168.0.1. Confirm it's correct.
Use a wired connection. Sometimes Wi-Fi won't allow access, connect your PC via Ethernet and try again.
Clear browser cache or use a different browser.
Forgot Wi-Fi Password
Lastly if you forgot the password of your wireless network then you can proceed with these troubleshootings:
Login to the router settings using any browser.
Navigate to Wireless Settings and view/change your Wi-Fi credentials.
Conclusion
Hope the above sanctioned information related to the netgear router setup is very useful for you. You can follow the steps to configure your router using the nighthawk app. Also you can easily troubleshoot the common errors by following the above tips.
0 notes
Text
Visio Tutorials: Learn How to Create Flowcharts, Diagrams & Plans
Microsoft Visio is a powerful diagramming tool widely used for creating flowcharts, organizational charts, network diagrams, floor plans, and many other types of visual representations. Whether you’re a business professional, an engineer, or a student, mastering Visio can enhance your ability to convey complex ideas in an easy-to-understand, visual format. This article will guide you through the essential steps for creating flowcharts, diagrams, and plans using Microsoft Visio, helping you unlock its full potential.
Understanding Visio Interface Before diving into the actual creation process, it's essential to familiarize yourself with Visio's user interface. When you open Visio, you will be presented with several templates tailored to different types of diagrams. The ribbon at the top of the window contains various tabs that provide access windows 11 home, formatting options, and design elements. To start creating any diagram, you must choose a template suited for the type of visual representation you want to make, whether it’s a flowchart, a floor plan, or a network diagram. The workspace in the center is where your diagram is created, and it is here that you’ll drag and drop shapes, connect them, and adjust properties.

Creating a Basic Flowchart Flowcharts are one of the most commonly used diagrams in Visio. They help break down processes into a series of steps, making them easier to understand and follow. To create a flowchart in Visio, begin by selecting the Flowchart template from the Visio start screen. Once the template is loaded, you'll see a set of flowchart shapes, such as process boxes, decision diamonds, and connectors, on the left-hand side of the screen. Simply drag these shapes onto the drawing canvas and arrange them in the order that represents your process. Use connectors to link the shapes together, showing the flow from one step to another. You can easily adjust the direction of connectors and even label the shapes to describe each step in detail.
Designing Diagrams with Custom Shapes Visio offers a range of templates beyond flowcharts, such as organizational charts, network diagrams, and even software designs. To create a diagram that fits your specific needs, you may want to use custom shapes. You can create your own shapes or edit existing ones to better suit the diagram you’re working on. To create custom shapes, go to the Shapes pane and select the More Shapes option. From there, you can either import new shapes or use drawing tools to design them yourself. Adding custom shapes can help make your diagram more personalized and aligned with your project’s requirements.
Building Network Diagrams Visio is a preferred tool for designing network diagrams, and it provides specialized templates for this purpose. If you’re creating a network diagram to illustrate the components of a network, such as routers, switches, firewalls, and servers, start by selecting the Network template from the available options. Visio provides a variety of network-specific shapes that represent different types of devices and connections. Drag and drop these shapes onto your canvas and connect them using dynamic connectors to represent the flow of data in the network. You can adjust the properties of each shape to specify the devices' types, IP addresses, and other details.
Drawing Floor Plans For those looking to design floor plans for homes, offices, or other structures, Visio is equipped with the tools necessary to create detailed blueprints. To create a floor plan, choose the Floor Plan template, which provides shapes for walls, windows, doors, furniture, and even landscaping elements. By dragging these shapes onto the workspace and arranging them to scale, you can create an accurate representation of a physical space. You can adjust the dimensions and sizes of each shape to match the actual measurements, and Visio will automatically help maintain consistency throughout the design. For added detail, you can add text annotations and labels to specify the use of different rooms or areas.
Enhancing Diagrams with Formatting Once you’ve laid out the basic structure of your diagram, it's time to make it visually appealing and easy to read. Visio offers a range of formatting tools that allow you to change the style and appearance of shapes, text, and connectors. You can adjust the color, line style, and fill pattern of shapes to make them stand out. Connectors can also be customized with different arrowheads or line styles to make the flow of the diagram clearer. Additionally, you can use themes and styles to give your diagram a professional look by applying uniform colors, fonts, and effects across all elements.

Collaborating and Sharing Diagrams One of the most useful features of Visio is the ability to collaborate on diagrams with others. If you’re working in a team, you can share your Visio file through Microsoft OneDrive or SharePoint, allowing multiple people to work on the same document simultaneously. You can leave comments and feedback, ensuring that everyone is on the same page during the design process. Visio also allows you to export your diagrams to other formats like PDF, PNG, or SVG, making it easy to share your work with individuals who may not have Visio installed on their computers.
Conclusion Mastering Microsoft Visio can greatly enhance your ability to create effective, professional-looking diagrams and flowcharts that simplify complex processes and ideas. Whether you’re designing flowcharts, network diagrams, organizational charts, or floor plans, Visio provides the tools and flexibility to bring your ideas to life. By understanding its interface, templates, and formatting options, you can produce diagrams that are not only functional but also visually appealing. With its collaboration and sharing features, Visio ensures that teamwork and communication are smooth and efficient, making it an essential tool for a wide range of industries and professionals.
0 notes
Text
5 Common CNC Router Controller Issues and How to Fix Them

In the world of modern manufacturing, CNC routers are indispensable for achieving precision and efficiency. However, even the most advanced machines are vulnerable to technical glitches—particularly with their controllers. A CNC router controller is essentially the command center that translates software instructions into physical movement. When something goes wrong here, it can bring your entire operation to a halt.
This article dives deep into the five most common CNC router controller issues, how to troubleshoot them effectively, and what you can do to prevent them in the future. Whether you're running a small shop or managing a high-volume production line, these insights will help keep your machine in top shape.
1. Controller Won’t Power On
You hit the switch—and nothing. No lights, no motion, no signs of life.
Why It Happens:
Blown fuses or breakers.
Loose or disconnected power cables.
Malfunctioning power supply unit (PSU).
Incorrect input voltage or surge damage.
How to Fix It:
Check and replace any blown fuses.
Make sure power cords are firmly connected and not frayed.
Test the PSU with a multimeter to verify correct output voltage.
Use a voltage regulator or surge protector to prevent future damage.
Pro Tip: Label your power supply connections clearly during setup. It makes troubleshooting faster and easier.
2. Freezing or Crashing During Jobs
Midway through a cut, your router suddenly locks up. Job ruined, material wasted.
Why It Happens:
Controller overheating due to poor airflow.
Bugs or incompatibility in the firmware/software.
Memory overload from excessive G-code complexity.
EMI (electromagnetic interference) or loose data connections.
How to Fix It:
Keep the controller clean and properly ventilated.
Ensure all software and firmware are updated to stable versions.
Break up large files into smaller toolpaths.
Use shielded cables and ensure proper grounding to eliminate EMI.
Maintenance Hack: Consider using CNC Control Retrofits that come with improved cooling and processing power to reduce these occurrences significantly.
3. Axis Movement Not Working
If your CNC router won’t move along the X, Y, or Z axis, you’re essentially grounded.
Why It Happens:
Stepper driver failure.
Motor or cable disconnects.
Faulty G-code or coordinate settings.
Loose or stripped motor couplings.
How to Fix It:
Double-check driver and motor connections.
Test drivers individually by swapping them between axes.
Inspect and fix any loose mechanical parts.
Review your CAM setup to ensure proper motion commands are being sent.
Upgrade Tip: If your machine frequently suffers from axis issues, consider CNC Control Retrofits that upgrade your stepper systems to more reliable and powerful servo motors.
4. Controller Doesn’t Connect to Computer
You plug in the USB cable and nothing happens—no connection, no control.
Why It Happens:
Outdated or missing drivers.
Cheap or damaged USB cables.
Wrong COM port selected in software.
Firmware and software version mismatch.
How to Fix It:
Install the correct drivers (often CH340 or FTDI).
Replace USB cable with a short, shielded one.
In your control software, manually select the correct COM port.
Verify the firmware on your controller is compatible with your software version.
Pro Note: Avoid USB hubs. Connect directly to your PC's port whenever possible.
5. Spindle Won’t Start or Has Speed Issues
Spindle problems can cause major setbacks—especially when cuts rely on consistent speeds.
Why It Happens:
No PWM or analog control signal.
Misconfigured spindle driver or VFD.
Incorrect G-code spindle commands (e.g., M3, S1000).
Motor overload or faulty wiring.
How to Fix It:
Ensure all spindle control wiring is secure and accurate.
Verify VFD settings align with your spindle motor specs.
Use test commands (M3 S1000, M5) to isolate the problem.
Test spindle motor directly to confirm it’s functional.
Expert Insight: CNC Control Retrofits often include improved spindle control systems, allowing for smoother and more reliable speed regulation across various materials.
Bonus: Preventing CNC Controller Problems
Fixing problems is good. Preventing them is better. Here’s how:
Regular Cleaning: Dust buildup is the silent killer of electronics.
Firmware Updates: Always run the most stable versions—not betas.
Cable Management: Keep power and signal wires separated.
Surge Protection: Always use voltage regulators or UPS systems.
Monthly Checklist: Schedule a 15-minute inspection every month to check connections, clean filters, and back up your machine settings.
Conclusion
CNC routers are amazing tools—but only when the controller is functioning flawlessly. Whether you're dealing with power issues, motion problems, or connectivity failures, the key is understanding what’s going wrong and how to fix it efficiently.
As we've seen, many common problems can be traced back to simple issues like loose wires or outdated software. But if you're constantly struggling with performance or compatibility, it's worth considering CNC Control Retrofits to upgrade aging systems with modern, more reliable hardware.
By applying the strategies in this guide, you'll not only be ready to fix issues quickly, but you'll also be in a strong position to prevent future downtime, maximize efficiency, and get the most out of your CNC investment.
1 note
·
View note
Text
As businesses grow, their IT needs grow too. Expanding a data center with new enterprise equipment is a big step and requires careful planning. Whether you're moving to a new location or expanding your current setup, managing deliveries from multiple vendors and OEMs can be overwhelming. Dealing with various shipping providers, supply chain delays, and tracking different delivery dates adds to the challenge.
That’s where Patriot IT Solutions comes in. We make your new product deployment process smooth and stress-free. By offering a single, secure location to receive all your equipment, we eliminate the headache of coordinating with multiple sources. Once everything is delivered, our team verifies and inspects every item before moving to the next step—white-glove delivery and professional installation at your data center.
Our Rack and Stack services ensure that your equipment is installed correctly and efficiently. This includes the physical setup of servers, storage devices, routers, switches, and other IT gear into standard data center racks or cabinets. We connect all devices to power and networking infrastructure while keeping cable management clean and cooling systems effective.
Rack and Stack is more than just placing equipment on racks—it requires precision, expertise, and experience. Our trained technicians understand the sensitive nature of IT hardware and handle every step with care. From proper alignment to tidy cabling and labeling, we make sure your environment stays organized and ready to perform.
Whether you’re deploying brand-new hardware or rearranging your existing setup, Patriot IT Solutions is your reliable partner. We help reduce downtime, minimize risks, and ensure everything is up and running smoothly.
Choose Patriot IT Solutions for your data center Rack & Stack needs. Our full-service approach ensures your deployment is seamless, secure, and done right the first time.
0 notes
Text
Why Your Business Needs IT Equipment Experts for Office Moves
Office moves are never simple—but when you factor in servers, network switches, desktop stations, printers, and complex cabling, things can get complicated fast. Moving IT equipment isn’t just about heavy lifting. It requires planning, precision, and technical expertise to avoid downtime, data loss, and damaged assets.

That’s why your business needs more than just a moving team—you need IT equipment experts who specialize in office relocations. At Corporate Moving By Best, we combine the skill of seasoned movers with the knowledge of IT professionals, providing a complete corporate moving service that ensures your technology arrives safe, secure, and ready to go.
As one of the top-rated corporate movers NYC companies trust, we’ve seen firsthand what happens when businesses try to move IT infrastructure without the right help—and what a difference it makes when the job is done right.
Let’s explore why IT expertise is critical during your office move and how a professional corporate moving company like Corporate Moving By Best can help.
1. Your Business Runs on Technology
From internal communication to customer transactions, virtually every part of your operation depends on technology. If your network is down, your business is down. Even a few hours of delay can cost thousands in lost productivity and missed opportunities.
When you move offices, the risk to your IT systems increases significantly. Without proper disassembly, packing, transportation, and reinstallation, your tech can suffer physical damage or connection failures.
Corporate Moving By Best ensures your equipment is handled with care, minimizing downtime and getting your systems online quickly in the new space. Our IT-aware movers coordinate closely with your internal tech team to safeguard your business continuity.
2. IT Equipment Is Fragile and Expensive
Servers, routers, monitors, workstations, and VoIP systems aren’t just costly—they’re also highly sensitive. A cracked screen or improperly packed server could lead to major expenses or data loss.
Unlike general movers, corporate movers NYC businesses like yours need a team trained in handling technology:
Static-free packing materials to protect delicate electronics
Specialized crates and shock-absorbing cases for fragile items
Secure cable management to avoid confusion or damage during setup
Labeled and inventoried components for seamless reassembly
At Corporate Moving By Best, our crews are trained in tech relocation best practices. We move each piece of your IT infrastructure as if it were our own, ensuring it arrives intact and ready for use.
3. IT Relocation Requires Strategic Planning
Moving desks and filing cabinets is one thing. But relocating IT systems? That takes a detailed plan. It’s not just about where things go—it’s about how they connect, who uses them, and how they support your workflows.
A proper IT relocation plan should include:
A full inventory of devices and hardware
A disconnect/reconnect strategy to prevent misconfiguration
Backup protocols in case of unexpected issues
Coordination with internet service providers (ISPs) and vendors
A timeline that avoids operational interruptions
With our end-to-end corporate moving service, Corporate Moving By Best works with your tech leaders to create a custom move plan that covers all the bases. You’ll know what’s happening at every stage, from the first unplug to the final reboot.
4. Cybersecurity Matters During a Move
Office relocations often present opportunities for security breaches. Devices left unattended or improperly handled during transport can lead to compromised networks or data theft.
Cybersecurity risks during a move include:
Exposure of sensitive business or client information
Unauthorized access to hardware or software systems
Lost or stolen hard drives or servers
Wi-Fi configuration errors in the new location
A general moving team may not even think about these risks. But Corporate Moving By Best takes them seriously. Our staff is trained in secure handling protocols, and we work under strict confidentiality guidelines to keep your data protected.
As an experienced corporate moving company, we go beyond physical transport—we protect the digital lifeblood of your business.
5. Professional Setup = Immediate Productivity
Even if your tech survives the move intact, that doesn’t mean your team is ready to work. If monitors are in the wrong place, cables are tangled, or the network isn’t configured, you’re wasting time and money while your staff sits idle.
Our IT relocation specialists don’t just move your gear—we help set it up:
Monitors mounted
Desks wired
Phones and VoIP devices connected
Wi-Fi tested
Printers and shared drives mapped
This attention to detail means your employees can plug in and get back to work immediately. It’s one of the many reasons NYC companies rely on Corporate Moving By Best for seamless technology transitions.
6. Experience in Every Industry
Different industries have different IT needs. Whether you’re a law firm with secure servers, a startup with dozens of cloud terminals, or a medical clinic with networked diagnostic equipment, your move needs to reflect your unique tech setup.
Corporate Moving By Best has helped clients across every sector with custom tech moving solutions. As trusted corporate movers NYC companies count on, we understand:
HIPAA compliance for healthcare IT
Server relocation strategies for finance and legal
High-speed infrastructure for marketing and creative teams
Remote access continuity for hybrid teams
We don’t just move your business—we move your industry.
7. NYC Logistics Demand Experience
Let’s not forget: moving IT in New York City comes with its own set of headaches. Narrow elevators, limited loading zones, and strict building access hours can all derail a move if not properly managed.
That’s why working with local experts like Corporate Moving By Best makes a difference. We’ve coordinated hundreds of office moves across Manhattan, Brooklyn, Queens, and beyond.
We’ll handle:
Building insurance requirements and certificates of insurance (COI)
Scheduling with property managers
Parking permits and freight elevator reservations
After-hours moves to avoid business disruption
Our local knowledge ensures your tech—and your move—run like clockwork.
Conclusion: Don’t Leave Your IT to Chance
When it comes to office relocation, your IT systems are too important to trust to just anyone. A successful move doesn’t just protect your physical assets—it protects your data, productivity, and reputation.
Partnering with a specialist like Corporate Moving By Best ensures that your technology is moved with care, set up correctly, and ready to support your business from day one in your new space.
Whether you’re a 10-person startup or a 500-employee enterprise, our corporate moving service is designed to handle your most valuable equipment with skill and precision. As one of the leading corporate movers NYC has to offer, we bring both muscle and mindset to your move—because we know that moving IT is more than just wires and boxes. It’s your business.
Ready to make your move? Let Corporate Moving By Best help you relocate your IT infrastructure safely and efficiently. Contact us today for a free consultation.
Corporate Moving By Best 442 5th Ave New York, NY 10018 516-916-5593 https://corporate-moving-company.com/services/
0 notes
Text
Sell Your IT Scrap/Computer Scrap with Best Price
Introduction
Are you sitting on a pile of outdated IT equipment? Selling your IT Scrap isn’t just a way to declutter but also an opportunity to earn and contribute to environmental sustainability. Let’s explore how you can make the most out of selling computer scrap.
What is IT Scrap?
Definition of IT Scrap
IT scrap refers to obsolete or damaged electronic devices and components, including old computers, laptops, cables, and more.
Common Types of IT Scrap
Computers: CPUs, monitors, and peripherals
Mobile Devices: Smartphones and tablets
Networking Equipment: Routers and switches
Why Should You Sell Your Computer Scrap?
Environmental Responsibility When we recycle old or broken IT equipment (like computers and phones), we keep a lot of waste out of landfills. Instead of dumping it, recycling helps reduce the amount of garbage we create. This is important because it saves space in landfills and keeps harmful chemicals in electronics from polluting the soil and water. Recycling also helps conserve natural resources, since we don’t need to extract as many new materials from the earth.
Financial Gains from Scrap Old computer parts, like motherboards and processors, often contain valuable metals, such as gold, silver, and copper. Even though each part has only a small amount, when you gather a lot of these parts together, you can get a good price for them. This can be profitable for people or businesses who collect and Sell IT Scrap.
Encouraging Circular Economy Selling old or unwanted electronics so they can be reused or recycled is part of what’s called a “circular economy.” This means that instead of throwing things away, we find ways to give them a second life. It’s a way to keep products and materials in use for as long as possible, which reduces waste and makes better use of resources.
Identifying Valuable IT Scrap
Components in Demand
CPUs, GPUs, and Motherboards: High resale value due to demand.
RAM and Hard Drives: Essential for refurbishing.
Rare Metals in IT Scrap
Gold, silver, and palladium are used in electronic circuits, making IT scrap lucrative.
How to Prepare Your IT Scrap for Sale
Sorting and Separating Components
This step involves going through all the parts you have and dividing them into two categories:
Functional Parts: These are parts that still work and could be reused or resold. For example, a computer’s hard drive that still stores data correctly.
Broken Parts: These are parts that are damaged or no longer working, like a cracked screen or a faulty power supply.
By separating the functional parts from the broken ones, it’s easier to accurately assess the value of each component. Working parts are worth more, so keeping them separate helps you understand the potential earnings from selling your items.
Cleaning and Organizing Scrap
Once you’ve sorted everything, it’s time to clean up:
Removing Dust: Dust and dirt can accumulate on old parts, which might make them look less valuable or even affect their functionality. Give each part a quick clean to make it look presentable.
Labeling Components: Labeling each part with details like its function or condition (e.g., “working hard drive” or “broken motherboard”) makes it easier to show potential buyers what you have. It also helps you keep track of your inventory, so you know exactly what you’re selling.
Backing Up and Wiping Data
Before selling any electronic devices that may have your data (like computers or phones), it’s essential to:
Back Up: Save any important files, photos, or information that you want to keep. You can transfer them to another device or upload them to cloud storage.
Wipe Data: Erase all personal information from the device to protect your privacy. This means deleting files, removing accounts, and possibly using a data-wiping tool to make sure your information can’t be recovered by others.
Following these steps ensures your parts are organized, clean, and your personal data is safe, making the selling process smoother and potentially more profitable.
Where to Sell Your IT Scrap
Local Scrap Dealers
What to Do: Look for scrap dealers in your area who deal specifically with electronic items.
Why It’s Helpful: Local dealers can often buy electronics quickly and may be interested in various items, even older or broken ones. It’s a convenient way to sell without needing to ship anything far.
Online Platforms and Marketplaces
What to Do: Use websites like eBay, Craigslist, or other local classifieds to list your electronics for sale.
Why It’s Helpful: These platforms connect you directly with potential buyers. You can set your price, and people who are specifically interested in what you’re selling can reach out. It’s good for selling individual or smaller quantities of items.
Specialized IT Scrap Buyers
What to Do: Search for companies or businesses that focus on buying used IT equipment, especially if you have a large number or valuable electronics to sell.
Why It’s Helpful: These specialized buyers are often looking for bulk purchases or rare, valuable parts, so they might offer better prices for items that regular dealers wouldn’t pay as much for.
How to Get the Best Price for Your IT Scrap
Understanding Market Trends
It’s essential to keep up with changes in market prices for metals and other materials. Prices can go up or down depending on various factors like demand, supply, or even global events. By staying informed about these trends, you’ll know the best times to buy or sell. This knowledge helps you make decisions that can save money or increase profits.
Selling in Bulk
When you sell a large quantity of items, buyers are often willing to pay more per unit because they’re getting a bigger supply all at once. This is what we mean by “selling in bulk.” Bulk sales are attractive to buyers, as they don’t need to make multiple smaller purchases, saving them time and often money. For sellers, this means a better price and quicker sales.
Negotiation Tips
When negotiating prices, being well-informed and confident is key. If you know the current market rates, you’ll have a strong basis for your price and can negotiate more effectively. Researching before entering a negotiation can give you an advantage and help you get the best possible price for your items.
Legal and Ethical Considerations
Following E-Waste Disposal Regulations
When you sell old or unwanted electronics, you must follow certain rules and regulations. These laws vary depending on where you are, but they all aim to protect the environment and public health. If you don’t follow these laws, you could face fines or other penalties. By understanding and following local e-waste disposal rules, you can avoid these issues and keep your business compliant.
Ensuring Secure Data Destruction
When you sell or dispose of electronics, it’s essential to ensure that any data stored on them is securely erased. This is especially important for computers, phones, and hard drives, which may contain sensitive information. Partnering with buyers or recyclers who guarantee data security helps protect you and your clients from the risk of data theft or misuse. This means that all personal and business information is permanently erased before the devices are resold or recycled.
Advantages of Selling IT Scrap
Environmental Impact: By selling old IT equipment, you help reduce electronic waste, or “e-waste,” in landfills. This waste can contain harmful materials that pollute the environment. Recycling IT scrap means the materials can be reused, lowering the demand for new resources and reducing pollution.
Extra Income: Instead of letting unused or outdated tech gather dust, selling it can bring in extra money. Many businesses accumulate unused electronics over time, and selling them can turn those idle items into cash.
Challenges in Selling IT Scrap
Market Fluctuations
The prices of metals and components (like copper, aluminum, or electronic parts) don’t stay the same; they can go up or down frequently.
These changes can be caused by a variety of factors, such as changes in supply and demand, economic shifts, or global events.
For example, if there’s a shortage of a certain metal due to a strike in a major mining area, the price of that metal could increase.
Companies need to keep an eye on these price changes because it impacts their costs and, eventually, their profits.
Finding Reliable Buyers
Not every buyer is dependable or honest, so businesses have to be careful about who they deal with.
Some buyers may delay payments, not pay in full, or cancel orders at the last minute. To avoid such risks, it’s essential to do research on potential buyers.
This could mean checking the buyer’s reputation, seeing if they’ve worked with other suppliers before, or confirming their financial stability.
Taking time to find trustworthy buyers helps ensure smoother transactions and reduces the risk of losses.
Success Stories of IT Scrap Sellers
Case Studies: Turning Tech Trash into Treasure
This section looks at people and companies who are creatively repurposing or selling outdated, broken, or discarded tech products, like old smartphones, computers, or electronic parts. Instead of letting this “tech trash” go to waste, these individuals and businesses find ways to repair, refurbish, or even transform it into something valuable. By doing this, they not only make money but also reduce waste and contribute positively to the environment. Their stories showcase how tech items that might seem useless can actually hold significant value with the right skills and perspective.
Lessons to Learn
In this part, successful sellers share their experiences and advice for getting the most profit out of selling or repurposing tech items. These tips can range from knowing where to find good tech deals, how to negotiate prices, and strategies to make items look more appealing, to building trust with customers. They might also discuss how to research market trends, so you know which tech items are in demand. By following these insights, new sellers can maximize their profits and make smarter choices when entering the world of tech resale or upcycling.
In short, these sections focus on the success stories of “tech recyclers” and offer practical guidance for anyone interested in turning old gadgets into a profitable venture.
How Selling IT Scrap Benefits the Environment
Reducing Landfill Waste
Reducing landfill waste is about properly managing the trash we throw away so it doesn’t end up harming our environment. When we throw things into landfills, they often sit there for a long time, taking up space and potentially releasing harmful chemicals or gases. By reducing the amount of waste that goes to landfills, we help protect the environment. This can be done through practices like recycling, composting, and reusing materials. For example, instead of tossing out plastic bottles, they can be recycled and used to make new items, which saves space in landfills and cuts down on pollution.
Conserving Natural Resources
Conserving natural resources means using fewer raw materials from the Earth, like metals and minerals. When we recycle metals (such as aluminium or copper), we don’t need to mine as much from the Earth to get new metal. Mining can damage ecosystems, pollute water, and require a lot of energy. Recycling metals reduces this demand, preserving these resources for future generations and reducing the impact on the environment. By reusing what we already have, we save energy, protect ecosystems, and conserve resources.
Tips to Maximize Your Profit
Partnering with Trusted Buyers
When you’re selling something valuable, like a product or even property, working with trustworthy buyers or dealers is essential. A “trusted buyer” is someone with a good reputation for fair dealings, meaning they’ll offer a fair price and pay on time. Building relationships with these kinds of reliable dealers can make selling easier and more profitable because you know they won’t take advantage of you. So, finding and keeping connections with trustworthy buyers ensures you get a good deal.
Timing Your Sales
Timing plays a big role in how much you can make when you sell. If you sell during a period of high demand – for example, when many people are interested in buying what you’re selling – you’re likely to get a better price. High-demand times mean more competition among buyers, which can drive up prices. For example, selling winter gear right before winter or selling property when the real estate market is booming can result in a better return.
Why Anmol Traders is the Best Place to Sell Your IT Scrap at the Best Price
Anmol Traders is your top choice for selling IT scrap, offering competitive prices and a hassle-free process. They accept a wide range of items like computers, laptops, motherboards, and networking equipment, ensuring you can sell all your scrap in one place.
They prioritize environmental responsibility by recycling e-waste sustainably and guarantee secure data destruction for your peace of mind. With free pickup services for bulk quantities and a reputation for fair practices, Anmol Traders ensures a smooth and rewarding experience.
Sell your IT scrap to Anmol Traders today and get the best value while contributing to a greener planet!
Conclusion
Selling your IT scrap to Anmol Traders is not just about getting the best price; it’s about partnering with a company that values your time, money, and environmental contributions. Whether you’re selling a single laptop or clearing out a warehouse of e-waste, Anmol Traders ensures a seamless, rewarding, and responsible experience.
FAQs
What is IT scrap, and why is it valuable?
IT scrap refers to old, broken, or outdated electronics, like computers, phones, and other tech devices. These devices might not work well anymore, but they contain valuable materials, such as metals (gold, silver, and copper) and other components, that can be reused or recycled. Because of these valuable materials, companies and recyclers are interested in buying IT scrap to recover and reuse these resources.
How can I safely sell my old computers?
When selling old computers, it’s essential to ensure that your data is wiped clean. This means removing all personal information and files so no one else can access them. You can use data-wiping software for this. Then, make sure you’re selling to a trusted buyer who won’t misuse the device or any leftover information. Trusted buyers could be well-reviewed dealers or certified recyclers.
What should I do before selling IT scrap?
Before selling any IT scrap, make sure to back up any data you still need, like files, photos, or documents. Next, clean the electronics if needed, as well-presented items can sometimes get better prices. Also, sort your items (such as separating laptops from phones or organizing parts like cables) since some buyers offer higher prices if the items are well-organized.
Are there risks in selling IT scrap online?
Yes, there are some risks, especially when dealing with unknown buyers. Some people or companies may pretend to be legitimate but are actually scammers looking to take advantage of sellers. To avoid scams, check the buyer’s reviews, do a quick online search about them, and avoid sharing too much personal information upfront.
How can I find the best IT scrap dealer near me?
To find a reliable IT scrap dealer, start by looking at online reviews on websites or apps where people share their experiences with local dealers. Additionally, you can ask friends, family, or coworkers if they have any recommendations. Local businesses or tech repair shops may also provide helpful suggestions on trusted dealers.
1 note
·
View note
Text
Structured Cabling and Networking: The Backbone of Modern Communication Infrastructure

What is Structured Cabling?
Structured cabling refers to an organized system of cables and related hardware designed to support multiple voice, data, video, and multimedia systems within a building or across a campus. Unlike traditional, point-to-point cabling that links specific devices, structured cabling follows a standardized approach that organizes the entire infrastructure for ease of maintenance, expansion, and troubleshooting. It serves as the backbone of any modern communication network, facilitating seamless connectivity and communication across a wide range of applications.
Structured cabling includes various components, including cable types, patch panels, network switches, racks, and distribution frames. These components are designed to work together efficiently, ensuring minimal downtime and optimal performance. A well-designed structured cabling system can reduce network failures, improve system performance, and make it easier to upgrade or reconfigure your network in the future.
The Importance of Structured Cabling
The need for a structured cabling system has grown as businesses increasingly rely on technology to operate. A robust and scalable cabling solution is essential for several reasons:
Improved Network Performance: Structured cabling reduces the risk of network failures and slowdowns. With a carefully planned infrastructure, data can flow quickly and efficiently, ensuring high-speed connectivity for all users.
Future-Proofing: As businesses grow and technology advances, structured cabling allows for easy upgrades. The system can be designed to handle future bandwidth requirements, ensuring that your network remains relevant and capable of supporting new technologies.
Cost-Effectiveness: By centralizing and organizing the cabling infrastructure, structured cabling systems reduce the need for ongoing maintenance and troubleshooting. This can save businesses significant time and money over the long term.
Simplified Troubleshooting and Maintenance: When your cables are organized and labeled, troubleshooting becomes faster and more efficient. This helps to minimize downtime and the costs associated with repairs and maintenance.
Scalability: Structured cabling systems are designed to grow with your business. Whether you’re adding new offices or upgrading your equipment, your infrastructure can easily accommodate future changes without requiring a major overhaul.
Aesthetic and Safety Benefits: A well-organized cabling system not only looks more professional but also reduces the risks associated with poorly managed cables, such as electrical hazards, tangles, or tripping accidents.
Key Components of Structured Cabling
To understand structured cabling in depth, it’s important to look at its various components. Each part plays a crucial role in ensuring optimal network functionality:
Cabling: The core of the system, these cables are responsible for transmitting data across the network. Common types of cabling used in structured cabling systems include:
Cat5e and Cat6 Ethernet cables: These are commonly used for high-speed data transmission, providing excellent bandwidth and speed for most networking applications.
Fiber Optic Cables: For businesses that require extremely high-speed connections and long-distance transmission, fiber optic cables provide the best solution due to their high bandwidth and low latency.
Patch Panels: Patch panels are used to manage and organize network cables. They allow for easier cable management and make it simpler to connect various network components, such as switches, routers, and servers, to one another.
Racks and Cabinets: These are used to house network equipment such as switches, routers, servers, and patch panels. They provide an organized and secure way to manage equipment and cabling, ensuring everything is easy to access and maintain.
Cable Management Accessories: To maintain the order and structure of the cabling system, various accessories like cable ties, cable trays, and Velcro straps are used. These help to keep cables neat and prevent them from tangling, which could lead to potential issues or downtime.
Connectors and Jacks: These components connect different parts of the cabling system, allowing seamless communication between devices. This includes connectors such as RJ45 connectors, fiber optic connectors, and keystone jacks.
Cross-Connects: Cross-connects are used to physically link different parts of the network. For example, they can connect the main server room to other areas of a building or campus.
Networking Equipment: This includes switches, routers, and servers that distribute and route data between devices across the network. Proper integration with structured cabling is critical for ensuring optimal network performance.
Networking: The Role of Structured Cabling in Building Reliable Networks
Structured cabling lays the groundwork for all networking operations. By establishing a well-organized system for cables, connectors, and equipment, businesses can ensure that their network infrastructure operates at peak performance.
When designing a network, several factors need to be considered, including bandwidth requirements, the physical layout of the space, and the potential for future expansion. Structured cabling allows for the flexible implementation of different types of networks, including Local Area Networks (LAN), Wide Area Networks (WAN), and wireless networks.
Key benefits of structured cabling in networking include:
High-Speed Data Transmission: A structured cabling system ensures that data flows without interruptions, offering the high bandwidth necessary for modern applications like video conferencing, cloud services, and high-definition content streaming.
Centralized Network Management: With structured cabling, businesses can centralize their networking equipment and simplify their management. By organizing devices and connections within dedicated racks or cabinets, network administrators can more efficiently manage and monitor the network.
Security: A properly organized cabling system ensures that the network remains secure. By limiting access to critical components and properly managing cables, businesses can reduce the risk of security breaches caused by physical vulnerabilities.
Flexibility and Scalability: Structured cabling supports scalability by allowing businesses to easily add or remove devices and equipment as their needs change. Adding new connections, network switches, or devices can be done without major disruptions to the existing system.
Reduced Downtime: In the event of a network failure, a well-structured system simplifies troubleshooting. Identifying and resolving issues is faster and more efficient, minimizing downtime and the impact on operations.
Structured Cabling vs. Traditional Cabling: Why Choose Structured?
Many businesses still use outdated cabling systems that follow traditional point-to-point wiring methods. While these systems may work for smaller setups, they present several issues as businesses scale.
Here’s why structured cabling is a better option compared to traditional cabling systems:
Organization and Scalability: Traditional cabling can become messy and difficult to manage as networks expand. In contrast, structured cabling organizes all components into a cohesive system, making it much easier to scale and maintain.
Future-Proofing: Traditional cabling systems often lack the flexibility to accommodate new technologies, whereas structured cabling is designed with future growth in mind, allowing for quick upgrades as technology evolves.
Minimized Downtime: With a structured system, diagnosing and repairing network issues becomes easier and quicker, ensuring minimal disruption to business operations.
Why Choose AppsComm Technologies LLC for Your Structured Cabling and Networking Needs?
At AppsComm Technologies LLC, we are committed to providing top-tier structured cabling and networking solutions tailored to your specific needs. Our expert team understands the complexities of modern communication systems and ensures that every cabling project is done with precision and care.
Why work with us?
Expertise and Experience: With years of experience in the field, we bring deep knowledge of the latest industry standards and technologies. Whether you’re upgrading an existing system or implementing a new one, we ensure that your infrastructure is future-proof and optimized for peak performance.
Tailored Solutions: Every business is different, and so are their networking needs. We provide customized solutions that are specifically designed to meet your unique requirements, from small businesses to large enterprises.
High-Quality Materials: We use only the best materials and equipment to build reliable, long-lasting cabling systems that deliver high performance.
Seamless Integration: Our structured cabling systems are fully integrated with the latest networking technologies, ensuring your entire infrastructure works harmoniously.
Comprehensive Support: Our support doesn’t end with installation. We provide ongoing maintenance, troubleshooting, and upgrades, helping you keep your network running smoothly for years to come.
Conclusion
Structured cabling and networking are the foundation of modern communication systems. By investing in a well-organized and scalable cabling infrastructure, businesses can enhance network performance, minimize downtime, and ensure that their network is ready for future growth. At AppsComm Technologies LLC, we specialize in providing comprehensive structured cabling and networking solutions that cater to your specific needs, ensuring reliable, secure, and efficient communication systems for your business.
Let us help you build the backbone of your network today — contact us for a consultation!
1 note
·
View note
Text
Telecommunication protocols: OSI model (continued)
In the previous part (link), we divided all the layers of the seven-layer OSI model into two groups. We examined the first four layers that form the 'Host Layers' group. In this post, we will look closer at the second, or 'Media Layers' group, which includes the three lower levels of the network model.
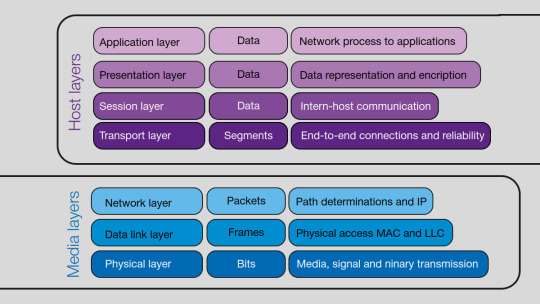
The 'Network Layer' routes blocks of data (packets or messages) through complex composite networks. To solve this primary task, the network layer protocol must define the structure of network layer addresses, the format of data blocks, and the type of services (with or without establishing the connection) it provides to the underlying transport layer. The protocol must have built-in mechanisms for requesting and ensuring the required quality of services offered and functions for managing the congestion of the communication channel.
The network layer's complexity determines the transport layer's ease of implementation. If the network layer protocol is connection-oriented, then there is no need to build into the transport layer mechanisms for ordering data blocks and error control, which means it is simpler.
However, connection-oriented network protocols must include descriptions of the procedures for establishing, maintaining, and terminating a connection instead of connectionless protocols. This complexity pays off because connection establishment provides greater control over its quality.
The type of network protocol used depends on the type of network traffic. Network traffic can be divided into two types: error-sensitive and latency-tolerant and latency-sensitive and error-tolerant. The first type includes almost all general-purpose data, and the second type includes all voice and video communications.
In connection-oriented networks, nodes forward messages according to the virtual connection number. Moreover, messages (with the exception of those sent when setting up a logical connection) do not contain information about the connection's final destination.
Each packet contains all the necessary information about its destination in connectionless networks. The router decides where to forward this packet next. The routing process consists of two operations: building a routing table and forwarding individual packets.
Today's most popular one is the 'Internet Protocol' (IP). In conditions of traffic convergence, when IP protocol packets must carry multimedia data in one stream (voice and video over IP technologies), its most significant drawback is the lack of traffic prioritization. Therefore, the primary efforts in developing the IP protocol aim to introduce an appropriate mechanism to give it some typical properties of a connection-oriented protocol, allowing it to successfully transport both main types of network traffic. It is proposed that the 'Multiprotocol Label Switching' (MPLS) method be used to adapt the IP protocol to modern requirements.
The 'Data Link' layer must ensure error-free data delivery to the network layer. Thus, its primary purpose is to identify and eliminate physical layer errors. Unlike the one at the physical level, information at the link level is transmitted in a structured form, i.e., frames. How the link layer corrects errors depends on the type of physical link. Direct correction is based on additional information in the frame. This method is usually used for transmission channels with numerous errors (subscriber network access lines) or high latency (satellite channels). Some modern link-layer protocols do not correct the errors per se but just detect and discard corrupted frames. Errors are resolved with higher-level protocols. Protocols that use this method are designed for high-quality physical channels with a low probability of errors, particularly fiber optic cables.
The data link layer must provide the following services:
communication channel access control, determining the order of units' frame transmission;
frame synchronization, which sets the beginning and end of each frame;
data delimitation, when the receiving device separates the data and control information that the link layer adds to the transmitted frame;
error detection and data recovery. The most common method for finding errors in the 'Cyclic Redundancy Check' (CRC);
data flow control, since the receiving device must be able to stop the transmission if it is busy. Naturally, after freeing up the resources needed, the receiving device must be able to signal again that it is ready to continue receiving data;
addressing for multipoint connections with more than two devices to indicate the recipient and identify the sender;
opening and closing a connection.
It should be noted that as the quality of the physical layer improves, the need for all link layer functions decreases. In these circumstances, it is reasonable to leave the control of late-frame delivery to the end nodes. Restoring lost frames can be assigned to higher layers (for example, the transport one).
Perhaps the most common direct link layer protocol is the 'Point-to-Point Protocol' (PPP). This protocol for interacting with peer-to-peer systems involves a full-duplex physical channel, dedicated or switched. It is interesting that considering the new realities of the physical layer, it only provides error checking by the CRC procedure but does not include error correction. The PPP protocol simply drops erroneous frames and does not deal with frame ordering, relying on the physical layer.
The 'Physical' layer carries out the transfer of data bits. Its main difference from the other OSI model layers is that it is both necessary and sufficient for the exchange of data between two points.
The physical level is characterized by several important features.
The physical layer architecture provides simplex, half-duplex, and full-duplex schemes for device interactions. In addition to the point-to-point topology, a point-to-multipoint topology is possible, particularly "star" and "bus." The "ring" topology is also very common; it is a closed structure of many point-to-point connections. In addition, the physical layer architecture should include parallel and serial transmission schemes. In a parallel scheme, many identical communication channels are organized between interacting devices, one of which is reserved for synchronization. Thus, the total throughput of the connection is equal to the sum of the throughputs of all communication channels used for transmitting data. In practice, the parallel transmission range is limited by the delay time skew of the component communication channels.
The data transmission environment can include twisted pair cable, coaxial cable, fiber optic cable, radio waves, line-of-sight wireless optical transmission, and an AC network. These all differ in throughput, noise immunity, installation features, and spread.
Signal transmission includes transporting analog signals through digital systems (for example, PCM systems) or digital signals through analog systems (telephone line modems).
Synchronization is necessary for serial transmission. The data signal is usually represented as a non-return to zero level (NRZ-L) linear code, where a binary one corresponds to a positive polarity pulse with a flat top and an amplitude of V volts, and a binary zero corresponds to a pulse of the same shape with zero amplitude. The NRZ-L code has two downsides: the presence of a DC component and its inability to transmit a sync signal along with the data. Thus, the NRZ-L signal, a sequence of ones, cannot be transmitted by a natural communication line containing capacitors and transformers. Synchronization of the reception signal is possible only with separate transmission of the digital signal's states (zeros and ones). Obviously, with a long sequence of ones, such a separation will not be possible, and, therefore, a separate transmission of the clock signal is needed. The problem is solved by converting the NRZ-L binary code for transmission over the line, for example, into a pseudo-ternary code like AMI or HDB-3.
There are two types of multiplexing: frequency-division multiplexing (FDM) and time-division multiplexing (TDM). Both allow saving the bandwidth of physical lines, unlike inverse multiplexing, which, on the contrary, is based on using redundant physical lines where possible.
The DTE-DCE and DSU-CSU interfaces are two popular physical layer interfaces.
0 notes
Text
[ad_1] MPLS is a crucial expertise in present community techniques, aiming to hurry up and management visitors patterns inside enterprise and repair supplier networks. In distinction to conventional IP routing, MPLS makes use of transient path labels as a substitute of prolonged community addresses to information knowledge between nodes. This technique drastically decreases the processing burden of intricate community paths, making it an efficient possibility for high-speed knowledge switch. For a extra complete understanding, try this information to multiprotocol label switching. As enterprises broaden, so do their networking wants, making the power to swiftly and effectively switch knowledge paramount. MPLS addresses this vital requirement by offering a extremely environment friendly, scalable, and dependable resolution for numerous industries. For instance, companies within the healthcare sector depend on MPLS for the safe and fast transmission of delicate affected person info. On the similar time, monetary establishments profit from its low-latency, high-speed knowledge switch capabilities important for real-time buying and selling operations. How MPLS Works MPLS operates by assigning labels to packets, that are then utilized by community routers to ahead the information to its remaining vacation spot. This technique considerably reduces the processing time per packet, enhances visitors stream velocity, and ensures environment friendly community useful resource use. MPLS simplifies and accelerates the routing course of, making it extra environment friendly than conventional IP routing. Label Edge Routers (LER): These are labeled packets’ entry and exit factors. LERs are accountable for assigning preliminary labels to packets as they enter the community and eradicating the labels after they exit. This course of ensures the information packets are appropriately recognized and routed with out advanced IP handle lookups. Label Switching Routers (LSR): These center routers within the MPLS community route packets in line with their labels. LSRs velocity up the method and scale back latency by shortly making forwarding choices based mostly solely on the related labels. This effectiveness is advantageous in intensive networks the place swift packet forwarding is essential. Advantages of Utilizing MPLS Implementing MPLS in your community can provide a number of notable advantages, enhancing the general effectivity and efficiency of information transmission. Listed below are among the key benefits: Improved Efficiency: MPLS hurries up packet forwarding by utilizing labels as a substitute of prolonged community addresses. This boosts the general velocity and effectiveness of the community, making it good for real-time duties like voice and video communications. Scalability: MPLS is designed to be simply scalable, making it easy to broaden the community as what you are promoting grows. This scalability is especially useful for enterprises experiencing fast development or planning future expansions, making certain the community can deal with elevated visitors with out compromising efficiency. High quality of Service (QoS): MPLS presents enhanced management over prioritization and bandwidth allocation, making certain vital purposes obtain the mandatory assets for optimum efficiency. This functionality is crucial for sustaining excessive service ranges in various networking environments, supporting purposes similar to video conferencing, VoIP, and cloud companies. Implementing MPLS in Your Community Transitioning to an MPLS community entails a number of pivotal steps. Every section is vital for profitable implementation, from the preliminary evaluation to the ultimate rollout. Right here’s a fast information that will help you by the method: Assess Your Present Community: Consider your present community infrastructure to establish the necessity for MPLS. Decide if MPLS can handle your present community challenges and enhance effic
iency. This evaluation ought to embody an evaluation of visitors patterns, bandwidth necessities, and potential areas for optimization. Plan the Community Structure: Design the community structure with scalability and QoS. Rigorously plan how MPLS can be built-in into your community to make sure a clean transition. This planning section ought to contain figuring out the optimum areas for Label Edge Routers (LER) and Label Switching Routers (LSR) and defining the label distribution and visitors engineering insurance policies. Choose Applicable MPLS Routers: Select and configure MPLS-compatible routers with the mandatory labels. Be sure that the chosen routers can deal with the anticipated visitors hundreds and are suitable along with your community necessities. This step might contain upgrading present hardware or procuring new units to assist the MPLS deployment. Conduct a Pilot Check: Earlier than absolutely deploying the MPLS community, run a pilot check to confirm that the setup capabilities appropriately. The pilot section ought to contain deploying MPLS in a managed setting, testing numerous visitors situations, and monitoring efficiency metrics. Tackle any points in the course of the pilot section to attenuate disruptions in the course of the full rollout. Roll Out the Implementation: Deploy MPLS regularly to attenuate potential community disruptions. Slowly improve the implementation of MPLS, monitoring efficiency and adjusting as required. This gradual technique allows step-by-step enhancements and ensures immediate detection and determination of any issues. The Way forward for MPLS SD-WAN (Software program-Outlined Vast Space Community) is incorporating MPLS to create hybrid networking options, exhibiting a vivid future for Multiprotocol Label Switching. These developments will proceed to enhance the effectiveness and flexibility of enterprise networks, guaranteeing their capacity to satisfy upcoming knowledge necessities. The merging of MPLS and SD-WAN can present firms with a mix of MPLS’s dependability and velocity together with SD-WAN’s flexibility and affordability. As extra organizations undertake cloud-based companies and interconnected purposes, the necessity for sturdy and environment friendly networking options will proceed to develop. With its confirmed reliability and efficiency observe file, MPLS is well-positioned to satisfy these evolving calls for. Moreover, developments in automation and community administration instruments are making it simpler for companies to deploy and handle MPLS networks, additional solidifying its relevance in the way forward for networking. Conclusion Multiprotocol Label Switching stays an important expertise for networking professionals, providing important efficiency, scalability, and High quality of Service (QoS) advantages. Whether or not in finance, healthcare, telecommunications, or some other trade reliant on high-speed knowledge switch, understanding and implementing MPLS may give your community the enhance it wants. By following a structured implementation plan and addressing widespread challenges, organizations can efficiently combine MPLS into their networks and reap the rewards of this superior expertise. MPLS is a reliable and environment friendly alternative for firms on the lookout for superior, adaptable, and high-performing networking options in a fast-changing digital setting. The effectivity in managing and prioritizing visitors, together with its scalability, makes it a worthwhile useful resource for organizations wanting to make sure the longevity of their community infrastructure. The put up The Definitive Information to Multiprotocol Label Switching for Networking Professionals appeared first on Vamonde. [ad_2] Supply hyperlink
0 notes
Text
Optimizing Space and Performance: Best Practices for AV Rack Layout
In the world of audio-visual (AV) systems, efficient organization and layout are paramount for ensuring optimal performance, accessibility, and scalability. At the heart of every well-designed AV installation lies the av rack layouts, which serve as the central hub for housing and managing various components, from video processors and amplifiers to control systems and power distribution units. However, designing an effective rack layout is more than just stacking equipment – it's a delicate balance of space optimization, cable management, ventilation, and future-proofing.

The Importance of AV Rack Layout
The significance of well-designed av rack layouts cannot be overstated, as they offer numerous benefits that contribute to the overall success and longevity of an AV installation:
Optimized performance and signal integrity: Proper rack layout and cable management ensure that signals are transmitted with minimal interference, noise, or degradation, resulting in optimal performance and a high-quality audio-visual experience.
Efficient space utilization: By carefully planning rack layouts, valuable space can be maximized, allowing for future expansion or the integration of additional components without the need for costly renovations or reconfiguration.
Improved accessibility and serviceability: Well-organized racks with proper cable management and labeling make it easier for technicians to access and service individual components, reducing downtime and maintenance costs.
Enhanced cooling and ventilation: Proper ventilation and airflow within racks are crucial for preventing overheating and prolonging the lifespan of sensitive electronic components, ensuring reliable and consistent performance over time.
Aesthetics and professionalism: A clean and organized rack layout not only contributes to the overall aesthetics of an AV installation but also projects a professional image, reflecting the attention to detail and commitment to excellence.
In this comprehensive blog post, we will explore best practices for av rack layouts, delving into essential considerations, design principles, and practical tips to help AV professionals optimize space, enhance performance, and create a foundation for scalable and future-proof AV systems.
Understanding AV Rack Components and Requirements
Before delving into the intricacies of rack layout design, it's essential to understand the various components that typically reside within an AV rack and their specific requirements. By gaining a comprehensive understanding of these elements, AV professionals can make informed decisions and create layouts that cater to the unique needs of each installation.
Key components and their requirements include:
Video processors and switchers: These components often require ample ventilation, easy access for maintenance, and proper cable management to ensure signal integrity and minimize interference. Amplifiers and power distribution units (PDUs): Amplifiers and PDUs generate significant heat and require adequate ventilation and spacing to prevent overheating. Additionally, proper power distribution and cable management are crucial for efficient operation and safety.
Control systems and automation components: These components may require easy access for programming, maintenance, and troubleshooting, as well as proper cable management and ventilation to ensure reliable performance.
Network and infrastructure equipment: Switches, routers, and other network equipment often have specific mounting and ventilation requirements, as well as cable management needs to ensure efficient data flow and minimize interference.
Storage and playback devices: Media servers, Blu-ray players, and other storage devices may require easy access for media swapping, as well as proper ventilation and cable management to prevent overheating and ensure reliable operation.
Rack accessories and cable management solutions: Accessories such as shelves, drawers, lacing bars, and cable management solutions play a crucial role in organizing and maintaining a tidy rack layout, contributing to overall efficiency and accessibility.
By understanding the unique requirements of each component, AV professionals can create rack layouts that not only accommodate the necessary equipment but also optimize performance, accessibility, and serviceability, ensuring a seamless and efficient AV installation.
Rack Sizing and Space Planning
Proper rack sizing and space planning are essential for creating an optimized and future-proof AV rack layout. Careful consideration of factors such as equipment dimensions, clearance requirements, and potential future expansion needs can help AV professionals make informed decisions and avoid costly mistakes or limitations down the line.
Key aspects of rack sizing and space planning include:
Equipment dimensions and rack unit (RU) calculations: Accurately measuring and calculating the rack unit (RU) requirements for each component is crucial for determining the appropriate rack size and ensuring a proper fit within the designated space.
Clearance and ventilation requirements: Adequate clearance and ventilation space must be factored into the rack layout to prevent overheating and ensure proper airflow. This includes considering clearances for cable management, ventilation fans, and access for maintenance.
Future expansion and scalability: When planning rack layouts, it's essential to consider potential future expansion needs, such as additional equipment or upgrades. Allocating space for future growth can prevent costly reconfiguration or the need for additional racks down the line.
Room layout and accessibility: The rack layout should be designed with the overall room layout in mind, ensuring easy access for installation, maintenance, and servicing. Factors such as door clearances, ceiling heights, and obstructions should be taken into account.
Weight and load-bearing capacity: Proper consideration of the total weight of the rack and its components is crucial to ensure the structural integrity of the installation and prevent potential safety hazards or equipment damage.
By carefully considering rack sizing and space planning, AV professionals can create layouts that not only meet current needs but also accommodate future growth and scalability, ensuring a long-lasting and efficient AV installation.
Cable Management and Signal Integrity
Effective cable management is a critical aspect of av rack layouts, as it directly impacts signal integrity, system performance, and overall aesthetics. Poorly managed cables can lead to signal degradation, interference, and a cluttered, unprofessional appearance, while a well-organized cable management system contributes to optimal performance and a clean, professional look. Key considerations for cable management and signal integrity include:
Cable types and signal requirements: Understanding the different cable types and their respective signal requirements is essential for proper cable routing and management. This includes considerations such as shielding, bandwidth, and impedance matching.
Cable labeling and documentation: Implementing a consistent and clear cable labeling and documentation system can greatly simplify troubleshooting, maintenance, and future upgrades or modifications. Cable bundling and lacing: Proper cable bundling and lacing techniques help to maintain organization, minimize tangling, and improve airflow within the rack, contributing to both aesthetics and performance.
Cable management accessories: Utilizing cable management accessories such as lacing bars, cable combs, and cable trays can significantly enhance organization and cable routing within the rack, ensuring a neat and tidy appearance.
Signal separation and shielding: Separating and shielding different signal types (e.g., audio, video, data) can help prevent interference and maintain signal integrity, ensuring optimal performance and reliability.
Bend radius and strain relief: Adhering to proper bend radius and strain relief guidelines for cables can prevent damage, signal degradation, and premature cable failure, prolonging the lifespan of the installation. By implementing effective cable management practices andadhering to signal integrity principles, AV professionals can create rack layouts that not only look professional and organized but also deliver optimal performance, minimize interference, and facilitate easier maintenance and troubleshooting.
Cooling and Ventilation Strategies
Proper cooling and ventilation are critical for ensuring the reliable and long-lasting operation of AV equipment within rack layouts. Overheating can lead to component failure, performance degradation, and potentially costly downtime or replacement expenses. By implementing effective cooling and ventilation strategies, AV professionals can create rack layouts that maintain optimal operating temperatures and extend the lifespan of sensitive electronic components.
Key cooling and ventilation strategies for av rack layouts include:
Rack ventilation and airflow management: Ensuring adequate ventilation and airflow within the rack is essential for preventing hot spots and promoting effective heat dissipation. This can be achieved through the strategic placement of ventilation fans, blanking panels, and proper cable management.
Active cooling solutions: In environments with high heat loads or limited ventilation, active cooling solutions such as air conditioning units, liquid cooling systems, or rack-mounted cooling units may be necessary to maintain optimal operating temperatures.
Equipment placement and spacing: Careful consideration of equipment placement and spacing within the rack can optimize airflow and prevent hot spots. Heat-generating components should be separated and positioned strategically to allow for proper ventilation.
Rack door and side panel ventilation: Choosing racks with ventilated doors and side panels can significantly improve airflow and heat dissipation, particularly in densely populated rack layouts.
Environmental monitoring and control: Implementing environmental monitoring and control systems can provide real-time temperature and humidity data, enabling proactive maintenance and adjustments to ensure optimal operating conditions.
Redundancy and failover planning: Incorporating redundant cooling systems or failover plans can help mitigate the risk of system failures due to overheating, ensuring continuous operation and minimizing downtime in the event of a cooling system failure.
By implementing effective cooling and ventilation strategies, AV professionals can create rack layouts that maintain optimal operating temperatures, extend the lifespan of sensitive electronic components, and minimize the risk of system failures or performance degradation due to overheating.
Power Distribution and Management
Proper power distribution and management are essential components of well-designed av rack layouts. Ensuring reliable and efficient power delivery, while adhering to safety regulations and best practices, is crucial for the smooth operation and longevity of AV systems.
Key considerations for power distribution and management include:
Power requirements and load calculations: Accurately calculating the power requirements of all components within the rack is essential for selecting the appropriate power distribution units (PDUs) and ensuring sufficient capacity for current and future needs.
Redundancy and failover planning: Implementing redundant power sources or failover plans can help mitigate the risk of system failures due to power outages or surges, ensuring continuous operation and minimizing downtime.
Power conditioning and surge protection: Incorporating power conditioning and surge protection devices can help safeguard sensitive electronic components from voltage fluctuations, spikes, and electrical noise, prolonging their lifespan and ensuring reliable performance.
Circuit separation and isolation: Separating and isolating critical components or systems onto dedicated circuits can prevent interference, improve signal integrity, and simplify troubleshooting in the event of power-related issues.
Energy efficiency and green initiatives: Implementing energy-efficient practices, such as using high-efficiency PDUs, can reduce operational costs and contribute to sustainability goals, while also minimizing heat generation and cooling requirements.
Safety and regulatory compliance: Adhering to relevant safety standards and regulations, such as NFPA 70 (National Electrical Code) and local building codes, is essential for ensuring the safety of personnel and equipment, as well as maintaining compliance with legal requirements.
By carefully considering power distribution and management strategies, AV professionals can create rack layouts that deliver reliable and efficient power delivery, minimize the risk of system failures or downtime, and ensure compliance with safety regulations and best practices.
Rack Accessories and Organization
While the core components of an AV rack layout are essential, the strategic use of rack accessories and organizational tools can significantly enhance efficiency, accessibility, and overall professionalism. By incorporating these elements, AV professionals can create rack layouts that are not only functional but also visually appealing and easy to maintain.
Key rack accessories and organizational tools include:
Shelves and drawers: Incorporating shelves and drawers into rack layouts can provide additional storage space for smaller components, tools, or documentation, improving organization and accessibility.
Lacing bars and cable management solutions: Lacing bars, cable combs, and cable trays are essential for maintaining a neat and organized cable management system, contributing to both aesthetics and performance.
Rack blanking panels: Using blanking panels to cover unused rack spaces can improve airflow and ventilation, preventing hot spots and maintaining optimal operating temperatures.
Rack lighting and labeling: Implementing rack lighting and clear labeling systems can greatly improve visibility and accessibility, facilitating easier maintenance and troubleshooting.
Rack security and access control: Incorporating security measures such as lockable rack doors or access control systems can help protect sensitive equipment and prevent unauthorized access or tampering.
Rack mobility and portability: In certain applications, such as temporary installations or mobile setups, incorporating casters or wheels into rack designs can enhance mobility and portability, allowing for easy relocation or transportation.
By strategically incorporating rack accessories and organizational tools, AV professionals can create rack layouts that are not only functional and efficient but also visually appealing, easy to maintain, and secure, reflecting a professional and polished approach to AV system design and installation.
Future-Proofing and Scalability
In the ever-evolving world of AV technology, future-proofing and scalability are crucial considerations when designing av rack layouts. By anticipating potential future needs and incorporating strategies for growth and adaptation, AV professionals can create rack layouts that can adapt to changing requirements, minimizing the need for costly renovations or replacements down the line.
Key strategies for future-proofing and scalability include:
Modular and expandable rack designs: Opting for modular and expandable rack systems can provide the flexibility to easily add or reconfigure components as needs change, without the need for complete replacement or significant modifications.
Allocating space for future growth: When planning rack layouts, it's essential to allocate additional space for future equipment or component additions, ensuring that the rack can accommodate growth without becoming overcrowded or compromising performance.
Flexible cable management and pathways: Implementing flexible cable management solutions and pathways can simplify future upgrades or modifications by allowing for easy cable routing and organization.
Standardized and interoperable components: Choosing standardized and interoperable components can facilitate easier integration and compatibility with future technologies, reducing the need for extensive overhauls or replacements.
Upgradable and modular software and control systems: Opting for upgradable and modular software and control systems can enable seamless integration of new features, capabilities, and technologies as they become available, extending the lifespan of the AV installation.
Anticipating technological advancements: Staying informed about emerging trends and technological advancements in the AV industry can help AV professionals make informed decisions when designing rack layouts, ensuring that their designs can accommodate future developments and innovations.
By incorporating future-proofing and scalability strategies into av rack layouts, AV professionals can create installations that can adapt to changing needs and technological advancements, minimizing the need for costly renovations or replacements and ensuring a long-lasting and sustainable AV solution.
Documentation and Labeling Practices
Effective documentation and labeling practices are essential components of well-designed av rack layouts. Clear and organized documentation not only facilitates easier maintenance and troubleshooting but also ensures that critical information is readily available for future upgrades or modifications.
Key documentation and labeling practices include:
Cable labeling and documentation: Implementing a consistent and clear cable labeling and documentation system can greatly simplify troubleshooting, maintenance, and future upgrades or modifications, ensuring that cables can be easily identified and traced.
Equipment labeling and documentation: Clearly labeling and documenting each piece of equipment within the rack, including model numbers, serial numbers, and configurations, can streamline maintenance and facilitate easier replacements or upgrades.
Rack layout diagrams and schematics: Creating detailed rack layout diagrams and schematics can provide a visual representation of the entire system, aiding in understanding the overall design and facilitating easier troubleshooting and modifications.
System documentation and manuals: Maintaining comprehensive system documentation and manuals, including installation guides, operation manuals, and technical specifications, can ensure that critical information is readily available for reference or training purposes.
As-built documentation: Generating accurate as-built documentation upon completion of the installation can provide a valuable resource for future reference, maintenance, or modifications, ensuring that the actual installed configuration is accurately captured.
Revision tracking and version control: Implementing a robust revision tracking and version control system for documentation can ensure that the most up-to-date information is readily available and that changes or modifications are accurately documented.
Digital documentation and cloud storage: Embracing digital documentation and cloud storage solutions can provide secure and easily accessible storage for all documentation, ensuring that critical information is readily available to authorized personnel, regardless of their location.
By adhering to effective documentation and labeling practices, AV professionals can create rack layouts that are not only well-organized and efficient but also easily maintainable and adaptable to future changes or modifications, ensuring a smooth and seamless transition throughout the lifespan of the AV installation.
Relevant User Queries and Answers
What are the key benefits of well-designed av rack layouts?
Well-designed av rack layouts offer numerous benefits, including optimized performance and signal integrity, efficient space utilization, improved accessibility and serviceability, enhanced cooling and ventilation, and a professional and aesthetically pleasing appearance. These benefits contribute to the overall success and longevity of an AV installation.
What factors should be considered when understanding AV rack components and their requirements?
When understanding AV rack components and their requirements, it's essential to consider factors such as ventilation needs, access for maintenance, cable management requirements, power consumption, heat generation, and specific mounting or installation guidelines. By understanding these unique requirements, AV professionals can create rack layouts that cater to the specific needs of each component.
How can proper rack sizing and space planning contribute to an optimized AV rack layout?
Proper rack sizing and space planning are crucial for creating an optimized AV rack layout. By accurately calculating equipment dimensions, considering clearance and ventilation requirements, allocating space for future
Why is effective cable management important in av rack layouts?
Effective cable management is important in av rack layouts because it directly impacts signal integrity, system performance, and overall aesthetics. Poorly managed cables can lead to signal degradation, interference, and a cluttered, unprofessional appearance, while a well-organized cable management system contributes to optimal performance and a clean, professional look.
What cooling and ventilation strategies can be implemented to ensure reliable operation of AV equipment within rack layouts?
Key cooling and ventilation strategies for av rack layouts include proper rack ventilation and airflow management, active cooling solutions (such as air conditioning units or liquid cooling systems), strategic equipment placement and spacing, ventilated rack doors and side panels, environmental monitoring and control systems, and redundancy and failover planning. Implementing these strategies helps maintain optimal operating temperatures and extend the lifespan of sensitive electronic components.
How can AV professionals ensure proper power distribution and management within rack layouts?
To ensure proper power distribution and management within av rack layouts, AV professionals should accurately calculate power requirements and load calculations, implement redundancy and failover planning, incorporate power conditioning and surge protection devices, separate and isolate critical components or systems onto dedicated circuits, implement energy-efficient practices, and adhere to relevant safety standards and regulations.
What are some common rack accessories and organizational tools that can enhance the efficiency and professionalism of av rack layouts?
Common rack accessories and organizational tools that can enhance the efficiency and professionalism of av rack layouts include shelves and drawers, lacing bars and cable management solutions, rack blanking panels, rack lighting and labeling systems, rack security and access control measures, and features that enhance rack mobility and portability.
Conclusion
In the dynamic world of audio-visual installations, optimizing space and performance through well-designed av rack layouts is paramount for achieving success and longevity. By adhering to best practices and implementing effective strategies, AV professionals can create rack layouts that not only optimize performance and signal integrity but also facilitate efficient space utilization, improve accessibility and serviceability, enhance cooling and ventilation, and project a professional and aesthetically pleasing appearance. Throughout this comprehensive blog post, we have explored the importance of av rack layouts and delved into various essential considerations and best practices. From understanding AV rack components and their unique requirements to implementing effective cable management and signal integrity measures, each aspect plays a crucial role in creating a cohesive and high-performing AV system. Proper rack sizing and space planning, coupled with careful consideration of clearance requirements, ventilation needs, and future expansion possibilities, lay the foundation for a future-proof and scalable rack layout. By allocating space for growth and embracing modular and expandable designs, AV professionals can ensure that their installations can adapt to changing needs and technological advancements, minimizing the need for costly renovations or replacements. Effective cable management and adherence to signal integrity principles not only contribute to optimal performance and minimized interference but also enhance the overall aesthetics and professionalism of the rack layout. Implementing cooling and ventilation strategies, such as proper airflow management, active cooling solutions, and strategic equipment placement, is essential for ensuring the reliable and long-lasting operation of sensitive electronic components. Moreover, careful consideration of power distribution and management, including redundancy planning, power conditioning, and circuit separation, is crucial for ensuring reliable and efficient power delivery while adhering to safety regulations and best practices. By strategically incorporating rack accessories and organizational tools, such as shelves, lacing bars, and cable management solutions, AV professionals can create rack layouts that are not only functional and efficient but also visually appealing and easy to maintain. Effective documentation and labeling practices further enhance the maintainability and adaptability of the installation, ensuring that critical information is readily available for future upgrades or modifications. Ultimately, embracing future-proofing and scalability strategies, such as modular designs, flexible cable management, and anticipating technological advancements, is essential for creating rack layouts that can adapt to changing requirements and remain relevant in the ever-evolving AV industry. By implementing the best practices outlined in this comprehensive guide, AV professionals can unlock the full potential of their installations, delivering exceptional performance, optimized space utilization, and a professional and polished appearance that reflects their commitment to excellence.
0 notes
Text
how to setup mpls vpn
🔒🌍✨ Obtén 3 Meses GRATIS de VPN - Acceso a Internet Seguro y Privado en Todo el Mundo! Haz Clic Aquí ✨🌍🔒
how to setup mpls vpn
Configuración MPLS VPN
MPLS VPN (Multiprotocol Label Switching Virtual Private Network) es una tecnología avanzada que permite a las empresas crear redes privadas virtuales seguras y eficientes sobre una infraestructura de red compartida. La configuración de MPLS VPN es fundamental para garantizar la privacidad, la calidad del servicio y la conectividad de extremo a extremo.
Para configurar una MPLS VPN, primero es necesario definir las políticas de enrutamiento y los protocolos de señalización adecuados. Los routers de borde de la red (PE) deben estar configurados para etiquetar y enrutar el tráfico de datos de forma segura a través de la red MPLS. Además, es importante establecer las políticas de calidad de servicio (QoS) para priorizar ciertos tipos de tráfico, como voz o video, y garantizar un rendimiento óptimo de la red.
Otro aspecto crucial en la configuración de MPLS VPN es la segmentación de la red en diferentes áreas de enrutamiento virtual (VRF). Cada VRF actúa como una red virtual independiente con sus propias tablas de enrutamiento, lo que permite a las empresas mantener la privacidad y el aislamiento de sus datos. Además, es posible implementar políticas de control de acceso para restringir el tráfico entre diferentes VRF y proteger la integridad de la red.
En resumen, la configuración de MPLS VPN requiere un enfoque meticuloso y detallado para garantizar la seguridad, la privacidad y el rendimiento de la red. Al implementar correctamente esta tecnología, las empresas pueden optimizar su infraestructura de red y mejorar la conectividad de sus sucursales y empleados remotos.
Protocolo de enrutamiento VPN MPLS
Un protocolo de enrutamiento VPN MPLS, o Multiprotocol Label Switching, es un método de enrutamiento de red que se utiliza en redes privadas virtuales (VPN) para mejorar la velocidad y eficiencia de la transmisión de datos. Este protocolo permite a las empresas enviar información de manera segura a través de una red compartida, utilizando etiquetas para dirigir el tráfico de manera más efectiva.
El enrutamiento VPN MPLS utiliza etiquetas para identificar el camino que seguirán los datos a través de la red. Estas etiquetas se asignan a los paquetes de datos en el punto de entrada a la red y se utilizan para guiarlos a través de la red de la manera más eficiente posible. Esto se traduce en una mejor calidad de servicio, menor latencia y menos congestión en la red.
Una de las ventajas del protocolo de enrutamiento VPN MPLS es su capacidad para separar el tráfico de datos en diferentes clases de servicios, lo que permite a las empresas priorizar ciertos tipos de datos sobre otros. Esto es especialmente útil en entornos donde se utilizan aplicaciones sensibles al retardo, como la voz sobre IP o el video en tiempo real.
En resumen, el protocolo de enrutamiento VPN MPLS es una herramienta poderosa para empresas que buscan mejorar la seguridad y eficiencia de sus comunicaciones en red. Al utilizar etiquetas para dirigir el tráfico de datos de manera más efectiva, las empresas pueden beneficiarse de una mayor velocidad, menor congestión y una mejor calidad de servicio en sus redes privadas virtuales.
Seguridad en redes privadas virtuales MPLS
Las redes privadas virtuales MPLS (Multiprotocol Label Switching) son una tecnología ampliamente utilizada en el mundo empresarial para garantizar la seguridad de las comunicaciones a través de una red privada virtual. MPLS permite a las empresas crear redes seguras y confiables, lo que resulta fundamental para proteger la información confidencial de la compañía.
Una de las ventajas de utilizar MPLS es su capacidad para segmentar y priorizar el tráfico de datos, lo que significa que se pueden establecer políticas de seguridad específicas para cada tipo de información. Esto es crucial para proteger los datos sensibles y garantizar que solo las personas autorizadas tengan acceso a ellos.
Otro aspecto destacado de la seguridad en las redes privadas virtuales MPLS es la encriptación de los datos. MPLS utiliza protocolos de encriptación avanzados para proteger la información en tránsito, lo que evita que terceros no autorizados puedan interceptar o acceder a los datos transmitidos a través de la red.
Además, MPLS ofrece un alto nivel de confidencialidad y autenticación, lo que garantiza que la información se mantenga segura y privada en todo momento. Estas características hacen de MPLS una opción segura y fiable para las empresas que buscan proteger sus comunicaciones y datos críticos.
En resumen, la seguridad en las redes privadas virtuales MPLS es un aspecto fundamental para cualquier empresa que busque proteger su información confidencial y mantener la integridad de sus comunicaciones. MPLS ofrece una solución segura y confiable que cumple con los más altos estándares de seguridad en el mundo empresarial actual.
Implementación de VPN MPLS
Una Implementación de VPN MPLS, o Red Privada Virtual Multiprotocolo de Conmutación de Etiquetas, es una solución eficaz para conectar de forma segura múltiples sucursales o dispositivos remotos a una red centralizada. Esta tecnología combina las ventajas de las redes VPN y MPLS, ofreciendo un alto nivel de seguridad y calidad de servicio.
La implementación de VPN MPLS permite a las empresas establecer conexiones seguras y confiables entre sus diferentes sedes o sucursales, independientemente de su ubicación geográfica. Al utilizar un enfoque basado en conmutación de etiquetas, se logra una alta eficiencia en el enrutamiento de datos, mejorando la velocidad y la latencia de la red.
Además, la tecnología MPLS proporciona priorización de tráfico, lo que permite a las empresas garantizar que las aplicaciones críticas funcionen sin problemas, incluso en entornos de red congestionados. Esto es especialmente útil para empresas que manejan grandes volúmenes de datos o que dependen de aplicaciones sensibles al retraso.
En resumen, la implementación de una VPN MPLS ofrece a las empresas una solución segura, confiable y escalable para conectar sus diferentes ubicaciones de forma eficiente. Al combinar las ventajas de las redes privadas virtuales y la conmutación de etiquetas, las empresas pueden mejorar su infraestructura de red y garantizar un alto nivel de rendimiento para sus operaciones comerciales.
Configuración de etiquetas MPLS VPN
Las etiquetas MPLS VPN son un elemento fundamental en la configuración de redes privadas virtuales multiprotocolo conmutadas por etiquetas. Estas etiquetas permiten la transmisión eficiente de datos al asignar a cada paquete de información una etiqueta única que indica su ruta a través de la red.
Para configurar correctamente las etiquetas MPLS VPN, es necesario seguir algunos pasos clave. En primer lugar, se debe definir el protocolo de enrutamiento que se utilizará en la red, como por ejemplo BGP (Border Gateway Protocol) o OSPF (Open Shortest Path First). Posteriormente, se configuran las interfaces de los dispositivos de red para habilitar MPLS y asignarlas a la VPN correspondiente.
Otro paso importante en la configuración de etiquetas MPLS VPN es la creación de los VRFs (Virtual Routing and Forwarding), que permiten mantener distintas tablas de enrutamiento para cada VPN, asegurando el aislamiento de tráfico entre las diferentes redes virtuales.
Además, es fundamental configurar los PE (Provider Edge) routers, que son los dispositivos responsables de interconectar las redes de los clientes con la red MPLS del proveedor de servicios. Estos routers deben estar configurados para el intercambio de etiquetas y el túnel de datos entre las distintas VPNs.
En resumen, la configuración de etiquetas MPLS VPN es un proceso detallado que involucra la definición de protocolos de enrutamiento, la creación de VRFs y la configuración de los routers PE. Con una correcta implementación de estas etiquetas, se logra una transmisión de datos eficiente y segura en una red privada virtual.
0 notes
Text
how does mpls vpn work
🔒🌍✨ Erhalten Sie 3 Monate GRATIS VPN - Sicherer und privater Internetzugang weltweit! Hier klicken ✨🌍🔒
how does mpls vpn work
MPLS Technologie
MPLS (Multiprotocol Label Switching) ist eine Technologie, die in modernen Netzwerken weit verbreitet ist und zur effizienten und sicheren Übertragung von Daten verwendet wird. Diese Technologie ermöglicht es, Datenpakete anhand von Labels schnell und zuverlässig durch ein Netzwerk zu leiten.
Ein Hauptvorteil von MPLS ist die Möglichkeit, verschiedene Arten von Datenverkehr über ein gemeinsames Netzwerk zu transportieren, ohne dass dabei die Leistung beeinträchtigt wird. Durch die Verwendung von Labels können Datenpakete den optimalen Weg durch das Netzwerk finden, was zu einer effizienten Nutzung der verfügbaren Bandbreite führt.
Darüber hinaus bietet MPLS auch eine höhere Sicherheit, da Datenpakete innerhalb des Netzwerks isoliert und vor unerwünschten Zugriffen geschützt werden können. Dies ist besonders wichtig in Unternehmen, die vertrauliche Informationen übermitteln müssen.
Durch die Implementierung von MPLS können Unternehmen von einer verbesserten Netzwerkleistung, höherer Sicherheit und einfacheren Verwaltung profitieren. Diese Technologie wird daher weiterhin eine wichtige Rolle in der Entwicklung moderner Netzwerke spielen und dazu beitragen, dass Datenübertragungen effizient und sicher erfolgen.
VPN Funktionsweise
Ein Virtual Private Network (VPN) ist ein Dienst, der Ihre Internetverbindung verschlüsselt und Ihnen Anonymität, Sicherheit und Privatsphäre im Internet bietet. Aber wie funktioniert ein VPN eigentlich?
Die Funktionsweise eines VPNs basiert auf der Erstellung einer sicheren Verbindung zwischen Ihrem Gerät und einem Remote-Server, der von Ihrem VPN-Anbieter bereitgestellt wird. Wenn Sie das VPN aktivieren, wird der gesamte Datenverkehr von Ihrem Gerät über diesen verschlüsselten Tunnel geleitet, was bedeutet, dass Dritte, wie beispielsweise Ihr Internetdienstanbieter oder Hacker, nicht in der Lage sind, Ihre Aktivitäten online zu verfolgen.
Der VPN-Client auf Ihrem Gerät verschlüsselt die Daten, bevor sie über das Internet gesendet werden. Dies wird mithilfe verschiedener Verschlüsselungsprotokolle erreicht, die sicherstellen, dass Ihre Daten vor neugierigen Blicken geschützt sind.
Ein weiterer wichtiger Aspekt der VPN-Funktionsweise ist die Möglichkeit, Ihre virtuelle Position zu ändern. Indem Sie eine Verbindung zu einem VPN-Server in einem anderen Land herstellen, können Sie den Anschein erwecken, als ob Sie sich tatsächlich an diesem Standort befinden. Dies ist besonders hilfreich, wenn es um den Zugriff auf geo-blockierte Inhalte oder das Umgehen von Zensur in bestimmten Ländern geht.
Insgesamt bietet ein VPN eine vielschichtige Funktionsweise, die Ihre Online-Privatsphäre schützt, Ihre Verbindung sichert und Ihnen dabei hilft, Ihre wahre Identität zu verbergen. Es ist ein unverzichtbares Tool in der heutigen vernetzten Welt, um sicher im Internet zu surfen.
Netzwerk Routing
Netzwerk Routing bezeichnet den Prozess des Weiterleitens von Datenpaketen von einer Quelle zu einem Ziel innerhalb eines Netzwerks. Dieser Vorgang wird durch spezielle Geräte wie Router ermöglicht, die den optimalen Weg für die Daten bestimmen und sie entlang dieses Pfades weiterleiten.
Es gibt verschiedene Arten von Netzwerk Routing-Protokollen, die je nach den Anforderungen und der Komplexität des Netzwerks eingesetzt werden. Eines der bekanntesten Routing-Protokolle ist das Border Gateway Protocol (BGP), das häufig in großen Unternehmensnetzwerken und im Internet verwendet wird.
Das Internet besteht aus zahlreichen miteinander verbundenen Netzwerken, und das Routing spielt eine entscheidende Rolle bei der Gewährleistung der Konnektivität und der effizienten Datenübertragung zwischen diesen Netzwerken. Durch das Routing werden Datenpakete auf dem schnellsten und sichersten Weg zu ihrem Bestimmungsort geleitet, wodurch eine reibungslose Kommunikation und Datenübertragung gewährleistet wird.
Netzwerk Routing kann entweder statisch oder dynamisch konfiguriert werden. Statisches Routing erfordert die manuelle Konfiguration von Routen, während dynamisches Routing automatisch die besten verfügbaren Wege für die Datenübertragung ermittelt und anpasst.
Insgesamt spielt das Netzwerk Routing eine Schlüsselrolle bei der effizienten Datenübertragung und der Gewährleistung einer reibungslosen Kommunikation in modernen Netzwerken. Es ist ein essenzieller Bestandteil der Netzwerkinfrastruktur und ermöglicht die zuverlässige Übertragung von Daten in lokalen Netzwerken sowie im Internet.
Datenpriorisierung
Bei der Datenpriorisierung handelt es sich um einen wichtigen Prozess im Bereich der Datenverarbeitung und -analyse. Durch die Priorisierung von Daten können Unternehmen sicherstellen, dass wichtige Informationen zuerst verarbeitet und genutzt werden, um fundierte Geschäftsentscheidungen zu treffen.
Ein effektives Datenpriorisierungssystem kann Unternehmen dabei unterstützen, ihre Ressourcen optimal zu nutzen und sicherzustellen, dass wichtige Daten in Echtzeit verfügbar sind. Dies kann dazu beitragen, Engpässe bei der Datenverarbeitung zu vermeiden und die Effizienz der gesamten Organisation zu steigern.
Es gibt verschiedene Methoden der Datenpriorisierung, darunter die automatische Klassifizierung von Daten nach ihrer Relevanz und Dringlichkeit, die Einrichtung von Alarmen für wichtige Ereignisse oder die Festlegung von Prioritäten basierend auf vordefinierten Kriterien.
Durch die Implementierung eines klaren Datenpriorisierungssystems können Unternehmen auch sicherstellen, dass ihre Daten sicher und geschützt sind. Indem sensible Daten priorisiert und entsprechend geschützt werden, können Unternehmen die Einhaltung von Datenschutzbestimmungen gewährleisten und das Risiko von Datenschutzverletzungen minimieren.
Insgesamt spielt die Datenpriorisierung eine entscheidende Rolle für den Erfolg eines Unternehmens im digitalen Zeitalter. Indem Daten effektiv priorisiert und genutzt werden, können Unternehmen ihre Wettbewerbsfähigkeit steigern und ein besseres Verständnis für ihre Kunden und Märkte gewinnen.
Sicherheitsprotokolle
Sicherheitsprotokolle sind wichtige Mechanismen, die zum Schutz von Daten und Informationen in verschiedenen digitalen Systemen eingesetzt werden. Diese Protokolle dienen dazu, die Sicherheit und Integrität von Kommunikationen und Transaktionen zu gewährleisten und unbefugten Zugriff auf vertrauliche Daten zu verhindern.
Es gibt verschiedene Arten von Sicherheitsprotokollen, die je nach Bedarf und Anforderungen implementiert werden können. Ein häufig genutztes Protokoll ist beispielsweise das SSL/TLS-Protokoll, das hauptsächlich für die sichere Übertragung von Daten im Internet eingesetzt wird. Durch die Verschlüsselung von Daten wird sichergestellt, dass Informationen während der Übertragung nicht von Dritten abgefangen oder manipuliert werden können.
Ein weiteres wichtiges Sicherheitsprotokoll ist das VPN-Protokoll, das eine sichere Verbindung über öffentliche Netzwerke herstellt und so den Datenschutz gewährleistet. Durch die Verschlüsselung des Datenverkehrs wird verhindert, dass sensible Informationen von Hackern oder anderen böswilligen Akteuren abgefangen werden können.
Zusätzlich zu diesen Protokollen gibt es auch Sicherheitsstandards wie beispielsweise die ISO/IEC 27001-Zertifizierung, die Unternehmen dabei unterstützt, ein umfassendes Informationssicherheitsmanagement umzusetzen.
Insgesamt sind Sicherheitsprotokolle unerlässlich für den Schutz sensibler Daten und die Wahrung der Privatsphäre in einer zunehmend digitalisierten Welt. Durch die Implementierung geeigneter Protokolle können Organisationen sicherstellen, dass ihre Daten vor Bedrohungen geschützt sind und sie das Vertrauen ihrer Kunden und Partner bewahren.
0 notes
Text
do you set up vpn on computer or router
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do you set up vpn on computer or router
VPN installation on computer
When it comes to ensuring your online privacy and security, installing a VPN (Virtual Private Network) on your computer is crucial. A VPN creates a secure and encrypted connection between your computer and the internet, protecting your data from prying eyes and potential hackers.
To install a VPN on your computer, you first need to choose a reliable VPN service provider. There are many options available, so be sure to research and select one that meets your specific needs, such as the number of devices you can connect simultaneously, server locations, and encryption protocols.
Once you have chosen a VPN service, the installation process is usually straightforward. You will need to download the VPN client software from the provider's website and follow the on-screen instructions to install it on your computer. During the installation process, you may be prompted to create an account and log in with your credentials.
After the VPN client is installed, you can launch the application and select a server location to connect to. Choosing a server close to your physical location can help improve your connection speed. Once connected, all your internet traffic will be routed through the VPN server, encrypting your data and keeping your online activities private.
It is essential to keep your VPN client up to date to ensure the latest security features are in place. Additionally, remember to activate the kill switch feature if available, which will disconnect your internet connection if the VPN connection drops to prevent your data from being exposed.
By installing a VPN on your computer, you can browse the internet with peace of mind, knowing that your data is secure and your online activities are private. Stay safe and protected online with a VPN installation on your computer.
Router VPN setup guide
Setting up a VPN (Virtual Private Network) on your router can enhance your online security and privacy by encrypting your internet connection and hiding your IP address. This guide will walk you through the steps to configure a VPN on your router, ensuring all devices connected to your network benefit from VPN protection.
Choose a VPN Provider: First, select a reliable VPN provider that offers router compatibility. Make sure they support the router model you have and offer clear instructions for setup.
Access Router Settings: Log in to your router's administration panel using a web browser. You can usually access it by typing the router's IP address (commonly 192.168.1.1 or 192.168.0.1) into the address bar and entering your username and password.
Find VPN Settings: Locate the VPN settings in your router's admin panel. This may be labeled as "VPN," "WAN Setup," or something similar, depending on your router brand and model.
Enter VPN Configuration Details: Input the VPN configuration details provided by your VPN provider. This typically includes the VPN server address, VPN protocol (such as OpenVPN or L2TP), username, and password.
Configure Additional Settings: Depending on your VPN provider and router, you may need to configure additional settings such as encryption strength or DNS servers. Follow your VPN provider's instructions for these settings.
Apply Changes: Once you've entered all the necessary information, save your changes and apply the VPN settings.
Restart Router: To ensure the VPN connection takes effect, restart your router.
Test Connection: Connect a device to your network and verify that the VPN is working correctly by visiting a website to confirm your IP address is masked.
By setting up a VPN on your router, you can safeguard all your connected devices with encrypted internet traffic, providing enhanced privacy and security for your online activities.
Configuring VPN on computer step by step
To configure a VPN on your computer, follow these step-by-step instructions to ensure a secure and private connection.
Step 1: Choose a VPN service provider Research and select a reliable VPN service provider that aligns with your specific needs, such as security features, server locations, and speed.
Step 2: Download and install VPN software Visit the VPN provider's website and download the software compatible with your operating system. Follow the installation instructions provided by the VPN provider.
Step 3: Create an account Once the software is installed, create an account on the VPN platform by following the registration process. Enter your credentials to log in to the VPN application.
Step 4: Connect to a VPN server Open the VPN application and browse through the list of available servers. Choose a server location you prefer and click on the connect button to establish a secure connection.
Step 5: Configure VPN settings Customize your VPN settings according to your preferences, such as choosing protocols, enabling a kill switch, or configuring split tunneling.
Step 6: Test your VPN connection Ensure your VPN connection is working correctly by visiting IP checking websites to verify your new IP address and location.
By following these simple steps, you can configure a VPN on your computer to safeguard your online activities and data privacy effectively. Configure your VPN today for a secure and encrypted internet browsing experience.
Installing VPN on router for secure connection
Installing a VPN on your router can provide an extra layer of security for all devices connected to your network. By encrypting your internet connection, a VPN helps protect your online activities, personal information, and sensitive data from potential threats and cyber attacks.
To install a VPN on your router for a secure connection, you first need to choose a VPN service provider that offers support for routers. Not all VPN providers offer router support, so make sure to select one that specifically mentions compatibility with routers in their features or support documentation.
Once you have subscribed to a VPN service that supports routers, follow the provider's instructions to set up the VPN on your specific router model. This usually involves logging into your router's admin panel, accessing the VPN settings, and entering the required configuration details provided by your VPN service.
After successfully configuring the VPN on your router, all internet traffic from devices connected to your network will be encrypted and routed through the VPN server. This means that your online activities, such as browsing the web, streaming content, or accessing sensitive information, will be shielded from prying eyes and potential eavesdroppers.
Keep in mind that installing a VPN on your router may slightly decrease your internet speed due to the encryption process. However, the trade-off for enhanced security and privacy is usually worth it, especially if you want to ensure a secure connection for all devices in your home or office network.
Differences between setting up VPN on computer versus router
Setting up a VPN (Virtual Private Network) can offer enhanced security and privacy for your internet connection, whether it's on your computer or your router. However, there are distinct differences between configuring a VPN on these two devices.
When you set up a VPN on your computer, you're primarily securing the device itself. This means that only the internet traffic originating from that specific computer will be encrypted and routed through the VPN server. While this provides security for activities conducted on that computer, other devices connected to the same network won't benefit from the VPN protection unless they also have the VPN software installed and configured.
On the other hand, configuring a VPN on your router secures the entire network. Every device connected to the router, including computers, smartphones, smart TVs, and IoT devices, will automatically have their internet traffic encrypted and routed through the VPN server. This offers a comprehensive solution to protect all devices in your home or office network without needing individual setups for each device.
One advantage of setting up a VPN on a computer is flexibility. You can easily toggle the VPN on and off as needed, allowing you to switch between secure and regular internet browsing. Additionally, installing VPN software on a computer typically requires minimal technical knowledge and can be done quickly.
However, configuring a VPN on a router may require more technical expertise. It involves accessing the router's settings and manually inputting VPN connection details. While this process may be more complex, it provides the convenience of securing all devices on the network without the need for individual installations.
In summary, setting up a VPN on a computer offers flexibility and ease of installation, while configuring it on a router provides comprehensive network-wide protection. The choice depends on your specific needs and technical proficiency.
0 notes
Text
which vpn type is a service provider managed vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
which vpn type is a service provider managed vpn
Managed VPN service
A managed VPN service offers businesses a secure and reliable way to connect their remote offices, employees, and clients over the internet. Unlike traditional VPNs, which require extensive setup and maintenance, managed VPN services are fully outsourced to a third-party provider, allowing businesses to focus on their core operations while enjoying the benefits of a secure network.
One of the key advantages of a managed VPN service is its ease of use. With a managed solution, businesses don't need to worry about configuring servers, managing encryption protocols, or troubleshooting connectivity issues. Instead, everything is handled by the service provider, from initial setup to ongoing maintenance and support.
Security is another major benefit of using a managed VPN service. These services employ advanced encryption techniques to protect data as it travels between devices and across networks. Additionally, many providers offer features such as intrusion detection, malware protection, and multi-factor authentication to further enhance security and safeguard against cyber threats.
Managed VPN services also offer scalability and flexibility, allowing businesses to easily adjust their network capacity and resources as needed. Whether adding new users, expanding into new geographic regions, or integrating with cloud-based applications, a managed VPN service can adapt to the changing needs of a growing business.
Furthermore, managed VPN services often come with dedicated support teams that are available around the clock to assist with any issues or concerns. This level of support ensures that businesses can rely on their VPN infrastructure to stay connected and productive, even in the face of technical challenges.
In conclusion, a managed VPN service offers businesses a convenient, secure, and scalable solution for connecting their distributed workforce and resources. By outsourcing VPN management to a trusted provider, businesses can streamline operations, enhance security, and focus on achieving their business objectives.
Service provider-controlled VPN
A service provider-controlled VPN, also known as an MPLS VPN (Multiprotocol Label Switching Virtual Private Network), is a type of VPN that allows businesses to securely connect multiple locations over a service provider's network. This type of VPN is often used by businesses to connect offices in different locations or to provide secure access to company resources for remote employees.
In a service provider-controlled VPN, the service provider manages the VPN infrastructure, including the routers, switches, and other networking equipment. This means that businesses do not have to worry about maintaining the VPN infrastructure themselves, which can save time and resources.
One of the key advantages of a service provider-controlled VPN is that it offers a high level of security. Service providers use encryption and other security measures to protect data as it travels over the VPN, reducing the risk of data breaches or unauthorized access.
Another benefit of a service provider-controlled VPN is that it can offer better performance than traditional VPNs. Service providers can prioritize traffic on their networks to ensure that critical applications have the bandwidth and low latency they need to operate effectively.
Overall, a service provider-controlled VPN can be a valuable tool for businesses looking to connect multiple locations or provide secure remote access to company resources. By outsourcing the management of the VPN infrastructure to a service provider, businesses can focus on their core operations while benefitting from a secure and reliable network connection.
Outsourced VPN management
Outsourced VPN management has emerged as a strategic solution for businesses looking to enhance their cybersecurity posture while streamlining operations. VPNs, or Virtual Private Networks, play a crucial role in safeguarding sensitive data and ensuring secure communication channels, particularly in today's digital landscape marked by increased cyber threats.
Outsourcing VPN management involves entrusting the configuration, maintenance, and monitoring of VPN infrastructure to third-party service providers. This arrangement offers several advantages for businesses of all sizes. Firstly, it allows organizations to leverage the expertise of seasoned professionals who specialize in cybersecurity and network management. These experts possess in-depth knowledge of VPN technologies and can implement best practices to fortify defenses against cyber threats.
Furthermore, outsourcing VPN management enables businesses to focus on their core competencies without the burden of managing complex network infrastructure internally. This can lead to cost savings and increased operational efficiency as resources are allocated more effectively.
Another benefit of outsourced VPN management is scalability. As businesses grow or encounter fluctuating demand, outsourcing providers can quickly adapt VPN configurations to accommodate changing needs. This flexibility ensures that organizations can scale their cybersecurity capabilities without experiencing downtime or compromising on security.
Additionally, outsourcing VPN management can enhance regulatory compliance. Many industries are subject to stringent data protection regulations, and working with experienced providers can help ensure adherence to compliance requirements, reducing the risk of costly fines and reputational damage.
In conclusion, outsourced VPN management offers businesses a strategic approach to bolstering cybersecurity defenses while optimizing resources and maintaining compliance. By leveraging the expertise of external providers, organizations can enhance their security posture, streamline operations, and focus on driving business growth.
Provider-managed virtual private network
A provider-managed virtual private network (VPN) offers businesses a secure and reliable solution for connecting remote offices, employees, and resources across various locations. Unlike self-managed VPNs, where the burden of setup, maintenance, and security falls on the organization itself, a provider-managed VPN places these responsibilities in the hands of a trusted third-party service provider.
One of the primary advantages of a provider-managed VPN is the expertise and resources it brings to the table. Service providers specialize in network infrastructure and security, ensuring that VPN connections are optimized for performance and protected against cyber threats. This allows businesses to focus on their core operations without worrying about the technical complexities of managing a VPN.
Additionally, provider-managed VPNs often come with service level agreements (SLAs) that guarantee uptime, performance, and support responsiveness. These SLAs provide businesses with peace of mind, knowing that their critical network connections are backed by contractual commitments from the provider.
Another benefit is scalability. Provider-managed VPNs can easily accommodate growing business needs by adjusting bandwidth, adding new locations, or implementing additional security measures as required. This scalability is particularly valuable for businesses experiencing rapid growth or fluctuations in demand.
Security is paramount in any VPN solution, and provider-managed VPNs excel in this area. Providers employ advanced encryption protocols, multi-factor authentication, and intrusion detection/prevention systems to safeguard data in transit. They also stay abreast of the latest security threats and best practices, ensuring that VPN connections remain resilient against evolving cyber threats.
In conclusion, a provider-managed VPN offers businesses a comprehensive and hassle-free solution for establishing secure network connections between dispersed locations and resources. By leveraging the expertise, resources, and scalability of a trusted service provider, organizations can enhance productivity, streamline operations, and mitigate security risks associated with remote connectivity.
Vendor-administered VPN service
Vendor-administered VPN services offer businesses a convenient and secure solution for protecting their sensitive data and ensuring seamless remote access for employees. In today's digital landscape, where cyber threats are increasingly sophisticated, utilizing a VPN service provided by a trusted vendor can be crucial for safeguarding confidential information.
One of the primary benefits of opting for a vendor-administered VPN service is the expertise and infrastructure that comes with it. Vendors specializing in VPN solutions invest heavily in robust encryption protocols, server networks, and security measures, which may surpass what an individual organization can afford or manage internally. This ensures that data transmitted through the VPN remains encrypted and protected from unauthorized access, reducing the risk of data breaches and cyberattacks.
Moreover, vendor-administered VPN services often offer scalability and flexibility to accommodate the evolving needs of businesses. Whether an organization needs to add new users, expand its geographical reach, or integrate with other IT systems, a reputable VPN vendor can tailor their services accordingly. This scalability is particularly beneficial for growing businesses or those with fluctuating bandwidth requirements.
Another advantage is the convenience of having a single point of contact for support and maintenance. Instead of dealing with multiple vendors or managing the VPN infrastructure internally, businesses can rely on the vendor to handle software updates, troubleshooting, and technical support. This frees up valuable resources and allows internal IT teams to focus on other strategic initiatives.
In conclusion, vendor-administered VPN services offer businesses a cost-effective, secure, and convenient solution for protecting their data and facilitating secure remote access. By leveraging the expertise and infrastructure of a trusted vendor, organizations can enhance their cybersecurity posture and streamline their operations in an increasingly interconnected world.
0 notes