#mobile phone hs code
Explore tagged Tumblr posts
Text
Phone Export from India Market Insights & Growth in 2024 -25
Mobile phone export from India industry has seen impressive growth in recent years, and the fiscal year 2024 is no exception. In FY24, India exported $15.6 billion worth of smartphones, marking a 42% increase compared to the previous year.
#mobile phone export from India#india mobile export#mobile phone exporters#mobile phone hs code#export of mobile phone from India#mobile phone export data
2 notes
·
View notes
Text
Electronics Import in India: Trends, Key Products, HS Codes

Electronics import in India has seen significant growth over the years, driven by increasing consumer demand and technological advancements. As one of the largest importers of electronic goods, India relies heavily on foreign manufacturers to meet its domestic needs. This article delves into the dynamics of electronics import in India, provides a list of electronic goods imported, explores relevant Harmonized System (HS) codes, and analyzes the impact of these imports on the Indian economy.
Overview of Electronics Import in India
India's electronics market has been rapidly expanding, with imports constituting a significant portion of the supply. Electronics imports in India mainly include mobile phones, laptops, integrated circuits, display panels, and other consumer electronics. The growing middle class, rising disposable incomes, and increasing digital adoption have fueled demand for these products.
In 2023, the total value of India electronics imports surpassed USD 65 billion, reflecting a steady increase from previous years. The majority of these imports come from countries such as China, Vietnam, South Korea, and Japan. Despite efforts to boost local manufacturing through initiatives like 'Make in India' and the Production Linked Incentive (PLI) scheme, India remains dependent on imports to fulfil its electronics needs.
Key Factors Driving Electronics Import in India
Several factors contribute to the high volume of electronics imports in India:
High Consumer Demand
With the rapid penetration of smartphones, laptops, and other consumer electronics, the demand for imported electronic goods has surged.
Technological Advancements
Continuous advancements in technology have led to the import of newer and more advanced electronic products, which are not yet manufactured domestically.
Lack of Local Manufacturing Capacity
Despite several government initiatives, India's local manufacturing capacity for advanced electronics remains limited, necessitating imports to bridge the gap.
Cost Competitiveness
Imported electronic goods are often more cost-effective due to economies of scale achieved by global manufacturers.
List of Electronic Goods Imported in India
India imports a wide range of electronic goods to cater to its diverse market needs. Below is a list of electronic goods imported in India:
Mobile Phones
Mobile phones account for a significant portion of India's electronics imports. With increasing smartphone penetration and frequent technological upgrades, the demand for imported mobile phones continues to grow.
Laptops and Tablets
Laptops and tablets are essential tools for education, work, and entertainment, making them high-demand items in the Indian market. Most of these devices are imported due to the lack of domestic production facilities.
Television Sets and Display Panels
India imports a large number of television sets and display panels, mainly from China and South Korea. The demand for high-quality, large-screen televisions is on the rise, especially with the increasing popularity of OTT platforms.
Integrated Circuits and Semiconductors
Integrated circuits (ICs) and semiconductors are crucial components for various electronic devices. India imports a vast majority of these components, primarily from Taiwan and South Korea, due to the lack of a robust semiconductor manufacturing ecosystem domestically.
Consumer Electronics
This category includes items like washing machines, refrigerators, air conditioners, and microwave ovens. These products are primarily imported from China and Southeast Asian countries.
Networking Equipment
With the expansion of digital infrastructure and the rollout of 5G technology, the demand for networking equipment like routers, switches, and modems has increased. A significant portion of this equipment is imported to meet the growing needs.
Electronic HS Codes and Their Importance
HS codes, or Harmonized System codes, are internationally standardized numbers that classify traded products to facilitate customs procedures. The electronic HS codes help in identifying specific goods for import and export, ensuring a smooth customs clearance process and accurate duty assessment. Some key HS codes relevant to electronics imports in India include:
HS Code 8517
This code covers telephone sets, including smartphones and other telecommunication devices.
HS Code 8471
This code is used for automatic data processing machines and units thereof, including laptops and computers.
HS Code 8528
This code pertains to monitors and projectors, not incorporating television reception apparatus.
HS Code 8542
This code is used for electronic integrated circuits and microassemblies, which are crucial for various electronic applications.
HS Code 8504
This code relates to electrical transformers, static converters, and inductors used in electronic devices.
Understanding these HS codes is essential for importers to classify products correctly and comply with international trade regulations. It also aids in tracking import data and analyzing market trends.
The Impact of Electronics Imports on the Indian Economy
The heavy reliance on electronics imports has both positive and negative implications for the Indian economy. On the positive side, imports help meet the domestic demand for advanced technology and support sectors like telecommunications, IT, and consumer electronics. They also facilitate technological upgrades and contribute to economic growth.
However, excessive dependence on imports has several drawbacks. It leads to a significant outflow of foreign exchange and contributes to the trade deficit. Additionally, relying heavily on imports makes India vulnerable to global supply chain disruptions and geopolitical tensions.
Government Initiatives to Reduce Electronics Imports
To reduce dependency on electronics imports, the Indian government has launched several initiatives:
Make in India
This initiative encourages local manufacturing of electronic goods, aiming to make India a global hub for electronics manufacturing.
Production Linked Incentive (PLI) Scheme
The PLI scheme offers financial incentives to companies that set up manufacturing units in India for electronics and other high-demand products.
Phased Manufacturing Program (PMP)
This program aims to increase domestic value addition in electronics manufacturing by incentivizing the local production of components and sub-assemblies.
Conclusion
India's electronics imports play a vital role in meeting the growing domestic demand for technology products. However, there is a need to balance imports with domestic production to reduce the trade deficit and build a resilient supply chain. By understanding the key products, trends, and HS codes associated with electronics imports, stakeholders can make informed decisions to navigate the complexities of the global electronics market. However, if you need electronic export data, electronic import data, or global trade data, you can connect with Seair Exim Solutions.
Frequently Asked Questions (FAQs):
Q1. What are the major electronics imported into India?
The major electronics imported into India include mobile phones, laptops, television sets, integrated circuits, and consumer electronics like refrigerators and washing machines.
Q2. Why does India import a large volume of electronics?
India imports a large volume of electronics due to high consumer demand, lack of local manufacturing capacity, technological advancements, and cost competitiveness of imported goods.
Q3. What are HS codes in the context of electronics imports?
HS codes are standardized numerical codes used globally to classify traded products, including electronics, to streamline customs procedures and duty assessments.
Q4. What is the impact of electronics imports on the Indian economy?
While electronics imports meet domestic demand and support economic growth, they also lead to a significant outflow of foreign exchange and contribute to the trade deficit.
Q5. What initiatives has the Indian government taken to reduce electronics imports?
The Indian government has launched initiatives like 'Make in India,' the Production Linked Incentive (PLI) scheme, and the Phased Manufacturing Program (PMP) to boost local electronics manufacturing.
Post By:
Seair Exim Solutions Phone No.: 099900 20716 Address: B1/E3 Mohan Cooperative Industrial Estate Near Mohan Estate Metro Station Opposite Metro Pillar No:-336, NH-19, New Delhi, Delhi 110044
Also Read:
Export of Milk from India: Trends, Data, and Global Impact
Millets Export from India: A Global Opportunities
#electronics import in India#electronics#electronics import#electronics importer#import#import data#importer#global trade data#global traders#electronics industry#electronics market#India electronics imports#list of electronic goods imported in India#electronic HS codes
0 notes
Text
Mobile phone import and export is a significant sector of global trade, driven by the ever-increasing demand for these devices worldwide. Mobile phones have become essential tools for communication, information access, and entertainment, leading to a surge in their production, distribution, and consumption across borders. Mobile phone buyers suppliers details serves as a powerful tool for making informed decisions that drive economic growth and prosperity within the mobile phone industry.
#Mobile Phone Export Import Data#Mobile Phone Exporters Importers Details#Mobile Phone Buyers Suppliers Details#Mobile Phone Custom Data#Mobile Phone Shipment Data
0 notes
Text
Introduction
This document provides a technical overview of the security protocol implemented by Viber.
Starting with Viber 6.0, all of Viber's core features are secured with end-to-end encryption: calls, one-on-one messages, group messages, media sharing and secondary devices. This means that the encryption keys are stored only on the clients themselves and no one, not even Viber itself, has access to them.
Viber's protocol uses the same concepts of the "double ratchet" protocol used in Open Whisper Systems Signal application, however, Viber's implementation was developed from scratch and does not share Signal's source code.
Terms
Viber Account - a collection of devices registered with Viber for the same phone number. An account is made up of one primary device and (optional) unlimited secondary devices. Messages sent or received by any device is displayed on all other registered devices of the same account, from the time of their registration and onward (past history cannot be seen).
Primary device - a mobile phone running iOS, Android or Windows Phone, and registered to Viber's service using a phone number managed by a mobile operator.
Secondary device - typically an iPad, Tablet or Desktop PC, which must be linked to a primary device.
ID Key - a long-term 256-bit Curve25519 key pair used to identify a Viber account. The ID key is generated by the primary device only.
PreKeys - a set of medium-term Curve25519 key pairs used to establish one-on-one secure sessions between devices. PreKeys are generated separately by each device in an account.
Session - a two-way secure virtual link between two specific devices. Secure sessions are automatically established between all devices of the same account, and between any two devices of different accounts that exchange messages. A secure session with a different account is identified in Viber by a gray lock in the conversation screen.
Trust - a state between two accounts which indicates that the peer account is authenticated and that no man-in-the-middle attacker has interfered with the session established between any two devices in the account. Users can establish trust by following the authentication procedure described below. A trusted session is identified in Viber by a green lock.
Breach of trust - a state between two accounts that occurs when the ID Key of a trusted peer has changed after trust was established. This can happen legitimately if the peer user has replaced his primary device, reinstalled Viber, or if keys were lost due to storage malfunction. However, it can also happen if a man-in-the-middle is eavesdropping on the conversation. A breached session is identified in Viber by a red lock.
Preparations for Session Setup
During installation, every primary Viber device generates a single 256-bit Curve-25519 key-pair called ID Key. The private part of the key is stored on the device, while the public part of key is uploaded to the Viber servers. Secondary devices (PCs and Tablets), receive the private key from the primary device via a secure method described in "Secondary Device Registration", below.
Additionally, every Viber client generates a series of PreKeys. Each PreKey has two 256-bit Curve-25519 key-pairs called Handshake Key and Ratchet Key. The private keys are all stored on the device, while the public keys are uploaded to the server. The server holds several keys per device and requests more when they drop below a configurable threshold. Each request causes the client to generate additional keys and upload the public parts to the server.
Secure Session Setup
A session needs to be established only once between every two Viber devices wishing to communicate securely. Once a session exists, it can be used to send an unlimited number of messages in either direction.
To send a secure message, secure sessions must exist between the sending device and all the recipient's devices, as well as between the sending device and all the sender's other devices. So for example, if user A that has a mobile phone and a PC registered to Viber under the same account wishes to communicate with user B that has a mobile phone and a PC, secure sessions must be established between each pair of devices.
Sessions between devices of the same account are established when the devices are registered. Only a single session is required between any two devices, and that session can be used to synchronize any number of conversations with other Viber accounts.
In order to establish a session with a different account, the device ("Alice") wishing to establish a session with a peer ("Bob") sends a query to the Viber server with the recipient's phone number. The server responds with the peer's public ID Key and a series of peer public PreKeys, one per each device registered on "Bob’s” account. "Bob’s" devices are not required to be online when this happens.
"Alice" device then generates two 256-bit Curve-25519 key-pairs as its own handshake and ratchet keys, and derives a Root Key, as follows:
RootKey = SHA256 ( DH(IDAlice, HSBob) || DH(HSAlice, IDBob) || DH(HSAlice, HSBob) )
The RootKey is then used to derive a session key using:
TempKey = HMAC_SHA256(RootKey, DH (RatchetAlice, RatchetBob))
New RootKey = HMAC_SHA256(TempKey, "root")
SessionKey = HMAC_SHA256(TempKey, "mesg")
DH indicates the use of Elliptic-Curve Diffie-Hellman key-exchange algorithm. HS indicates Handshake Key.
The different strings passed to the HMAC functions ensure that even if the session key is compromised, the root key cannot be derived back from it.
"Alice" then sends to "Bob" a session start message containing its own public ID, an identifier of "Bob’s” pre-key that was used for this session, and its own public handshake and ratchet keys. When "Bob" goes online and retrieves this message from its inbox, it can reconstruct the same Root and Session keys using the same DH procedure.
It should be noted that if a session is established with a peer's primary device but cannot be established with a secondary device (for example, because it is offline and out of PreKeys on the server), the conversation will still be secured with end-to-end encryption, but that secondary device will not be able to decrypt those messages and thus, will not be able to display them.
Exchanging Messages
A device sending a message to a target user needs to encrypt this message for every session with every device that the target user has. To accomplish this, an ephemeral one-time 128-bit symmetric key is generated and is used to encrypt the message body using Salsa20 encryption algorithm. This ephemeral message key is then encrypted using each recipient's session key. The sender device sends a unified message to the server, containing one encrypted cyphertext and a set of encrypted ephemeral keys. A server-side fan-out slices this message and delivers the relevant parts to each target device.
The two devices take turns at advancing the session keys in a process called ratcheting. Each time the direction of the conversation changes, the device whose turn it is randomly generates a new Ratchet key pair, and once again performs the following sequence:
TempKey = HMAC_SHA256(RootKey, DH (RatchetAlice, RatchetBob))
New RootKey = HMAC_SHA256(TempKey, "root")
SessionKey = HMAC_SHA256(TempKey, "mesg")
With Ratchetthis_device being the private part of the newly derived key-pair. Alongside each message, the public part of the Ratchetthis_device is also sent. The recipient runs DH with its last private ratchet together with the sender's public ratchet.
This double-ratchet accomplishes two things: first, the continuous ratcheting provides forward and backwards secrecy so even if the keys are compromised, past and future messages cannot be decrypted. Second, the algorithm maintains the authentication of the peer, because the DH chain of the root keys started with both devices' ID Keys. If the ID key of the peer is trusted at any point, the entire chain can be trusted.
Encrypted Calls
Each side of a call generates an ephemeral 256-bit Curve25519 key-pair. The public part is signed using the device private ID Key and is exchanged between the two devices during call setup phase. The other side authenticates the request using the peer's public ID key.
Each device verifies the signature, and performs DH calculation to derive a one-time session key. The session key is valid only for the duration of this specific call, and is not saved in non-volatile storage.
The RTP stream of the audio or audio/video call is converted to SRTP and encrypted via Salsa20 algorithm using the session key.
Photo, Video and File Sharing
The sending client generates an ephemeral, symmetric Salsa20 key and encrypts the file. The encrypted file, together with an HMAC signature, is uploaded to Viber servers. An additional MD5 signature is calculated over the encrypted data and sent together with the file in order to allow the storage server a simple way of verifying transmission integrity regardless of the end-to-end encryption.
The sender then sends a Viber message to the recipient with the ID of the uploaded file and the encryption key. This message is end-to-end encrypted using the encrypted session between the sender and recipient.
The recipient generates a download link from the file ID, downloads the encrypted file and decrypts it using the key.
Secure Groups
All members of a secure group share a common secret key (a symmetric Salsa20 encryption key) which is not known to Viber or to 3rd parties.
For new groups, this shared secret is generated by the group creator and sent to all participants using the secure one-on-one sessions described above. For non-secure groups that were created with past Viber versions, this secret is generated by the first member who sends a message to the group chat after all group members have upgraded to the secure version. In the Viber application any group member can add additional participants to a group. These participants will receive the secret from the group member that added them.
The group secret is ratcheted forward using a HMAC-SHA256 with every message sent. Each group message contains a sequence number that indicates the number of times that the hash function has been invoked. Different clients always pick up where the last message has left off and continue the hashing chain from that point, so keys are not reused. Forward secrecy is maintained by the one-way hashing algorithm; even if the key is compromised, past conversations cannot be decrypted. Past keys are discarded by the client and not saved to not-volatile storage, except for a short window of past hashes which is used in race conditions when two or more participants write to the group simultaneously.
Secondary Device Registration
A key feature in the Viber ecosystem is the concept of secondary devices. A secondary device is a PC, an iPad or a Tablet which is paired with a user's mobile phone and sees the same message history of both incoming and outgoing messages.
Viber's end-to-end encryption on secondary devices works as follows:
Encryption is done separately for each device. If some user A sends a message to user B that has two devices, then user A needs separate end-to-end sessions with the two devices and encrypts the data twice, each one using a different set of keys.
Authentication is done just once for the entire account. If user A trusts user B, the trust is automatically applied to all of user B's devices, not just one.
The authentication is accomplished by sharing the private ID Key between all devices of the same account. The ID Key is generated only by the primary device, and is transmitted to the secondary devices during registration in a secure method, as follows:
The secondary device generates an ephemeral 256-bit Curve-25519 key-pair.
The device then generates a QR code containing the device's "Viber UDID" (a publicly accessible unique device ID generated by Viber) plus the public part of the ephemeral key pair.
The user uses his primary device to scan the QR code.
The primary device also generates a 256-bit Curve-25519 key-pair and performs DH calculation with the public key from the QR. The result is hashed using SHA256 to create a shared secret.
The primary then encrypts its own private ID key with this secret and sends it and the public part of the ephemeral key through the Viber servers to the target device, identified by its UDID as read from the QR code. The cyphertext is signed using HMAC-SHA256.
The secondary device receives the message, performs the same DH and hash to obtain the same secret, and uses it to decrypt the primary private ID Key.
The ID key is part of the DH chain that creates the shared secrets for the one-on-one sessions. Therefore, without the correct ID, the secondary device cannot participate in any secure conversations that the primary device is part of.
Authentication
Authentication provides a means of identifying that no man-in-the-middle attacker is compromising the end-to-end security. In the Viber application, authentication is done in the context of a Viber audio (or audio/video) call.
When in a call, each user can tap on the lock screen to see a numerical string which is computed as follows:
Both devices perform DH calculation using their own private ID key and the peer public ID key as published during call setup phase.
The DH result is hashed using SHA256 and trimmed to 160 bits. Those 160 bits are then converted to a string of 48 decimal characters (0-9).
Both parties should see the same string of numbers and can compare them by reading them to the call participant. If both sides hear the other side read out loud the same string of numbers as they see on their own screen, this gives a very high degree of certainty that the ID keys have not been tampered with and that no man-in-the-middle exists for this conversation.
The ID key verification protects both the secure calls and secure 1-1 chats. In calls, the ID key is used to sign the key exchange DH message. In 1-1 chats, the ID key functions as the root of the DH chain leading to the shared secret generation. In turn, 1-1 session protects group sessions because the group keys are exchanged over 1-1 sessions.
Known Limitations
At this time, in the Viber iOS application for iPhone and iPad, attachments such as images and videos which are sent via the iOS Share Extension are not end-to-end encrypted. The iOS Share Extension is invoked when a user selects an image or video from the iOS pictures library (the "camera roll"), clicks the "send" button, and selects Viber as the send target. Attachments sent using this method are still encrypted in transit (using HTTPS), but are not end-to-end encrypted. To ensure that your images and videos are fully end-to-end encrypted, send them from your Viber application directly and not from the iOS pictures library. This limitation applies only to iOS and will be addressed in a future release.
1 note
·
View note
Link
As per the demand of customers in all over the world, the mobile phone is the largest dealing of the products in the market. There are many manufacturer companies in the world which makes the mobile phones and sales world level market.
#Mobile Phone Import Data#Mobile Phone Importers Data#Buyers Details Mobile Phone#Mobile Phone Custom Data#Shipment Data Mobile Phone#Mobile Phone HS Code
0 notes
Text
Hs clean disk pro

#Hs clean disk pro full#
#Hs clean disk pro android#
#Hs clean disk pro software#
#Hs clean disk pro code#
Have a power source that provides mobility, such as a battery.
#Hs clean disk pro android#
Handheld RequirementsĪn Android Handheld device refers to an Android device implementation that is typically used by holding it in the hand, such as an mp3 player, phone, or tablet.Īndroid device implementations are classified as a Handheld if they meet all the following criteria: 2.1 Device Configurationsįor the major differences in hardware configuration by device type, see the device-specific requirements that follow in this section. This section describes those device types, and additional requirements and recommendations applicable for each device type.Īll Android device implementations that do not fit into any of the described device types MUST still meet all requirements in the other sections of this Compatibility Definition.
#Hs clean disk pro software#
While the Android Open Source Project provides a software stack that can be used for a variety of device types and form factors, there are a few device types that have a relatively better established application distribution ecosystem.
The ID in Section 2 consists of : Section ID / Device Type ID - Condition ID - Requirement ID (e.g.
The Requirement ID in Section 2 starts with the corresponding section ID that is followed by the Requirement ID described above.
This ID starts from 1 and increments by 1 within the same section and the same condition.
When the requirement is conditional, 1 is assigned for the 1st condition and the number increments by 1 within the same section and the same device type.
When the requirement is unconditional, this ID is set as 0.
C: Core (Requirements that are applied to any Android device implementations).
The ID consists of : Device Type ID - Condition ID - Requirement ID (e.g.
STRONGLY RECOMMENDED requirements are marked as but ID is not assigned.
The ID is assigned for MUST requirements only.
Requirement ID is assigned for MUST requirements. These requirements are referenced as "Core Requirements" in this document. Each subsection of Section 2 is dedicated to a specific device type.Īll the other requirements, that universally apply to any Android device implementations, are listed in the sections after Section 2. Section 2 contains all of the requirements that apply to a specific device type. Any technical details provided in the linked resources throughout this document are considered by inclusion to be part of this Compatibility Definition. In any cases where this Compatibility Definition or the Compatibility Test Suite disagrees with the SDK documentation, the SDK documentation is considered authoritative. Many of the resources linked to in this document are derived directly or indirectly from the Android SDK and will be functionally identical to the information in that SDK’s documentation. Finally, note that certain component substitutions and modifications are explicitly forbidden by this document.
#Hs clean disk pro full#
It is the implementer’s responsibility to ensure full behavioral compatibility with the standard Android implementation, including and beyond the Compatibility Test Suite. While some components can hypothetically be replaced with alternate implementations, it is STRONGLY RECOMMENDED to not follow this practice, as passing the software tests will become substantially more difficult.
#Hs clean disk pro code#
Device implementers are STRONGLY RECOMMENDED to base their implementations to the greatest extent possible on the “upstream” source code available from the Android Open Source Project. Where this definition or the software tests described in section 10 is silent, ambiguous, or incomplete, it is the responsibility of the device implementer to ensure compatibility with existing implementations.įor this reason, the Android Open Source Project is both the reference and preferred implementation of Android. To be considered compatible with Android 11, device implementations MUST meet the requirements presented in this Compatibility Definition, including any documents incorporated via reference. A “device implementation” or “implementation" is the hardware/software solution so developed. The use of “MUST”, “MUST NOT”, “REQUIRED”, “SHALL”, “SHALL NOT”, “SHOULD”, “SHOULD NOT”, “RECOMMENDED”, “MAY”, and “OPTIONAL” is per the IETF standard defined in RFC2119.Īs used in this document, a “device implementer” or “implementer” is a person or organization developing a hardware/software solution running Android 11. This document enumerates the requirements that must be met in order for devices to be compatible with Android 11.

0 notes
Text
Vietnam Market Analysis Reports and Shipment Record Data
The shift of the country from a centrally planned to a market economy has transformed the country from one of the poorest in the world into a lower middle income country. Vietnam is one of the most dynamic emerging countries in East Asia region.

The solid foundations laid down by the government to boost the economy has proven resilient through different crisis, the latest being Covid-19 pandemic. In the pandemic era, Vietnam was only a few countries to post GDP growth.
Vietnam has grown bolder in its development aspirations aiming to become high income country by 2045. The market-oriented economic reforms of the government has supported Vietnam’s shift from a largely agricultural economy to a modern economy based on FDI led manufacturing, transforming it in the process from one of the poorest countries in the world to a lower middle income country.
Between 2015 to 2019; the economy of Vietnam grew at an average rate of around 7% per annum, buoyed by export-oriented manufacturing activity and solid domestic demand. As per Vietnam Export Data, the exports of the country totalled USD 264.6 billion in 2019, a gain of about 25% as compared to the previous year. The trade data shows, Vietnam exported goods worth USD 243.6 billion in 2018.
The country is the 22nd exporter country in the world during 2019. The major exports of Vietnam are mobile phones, telephones, and their parts, textiles. Others include computers, electrical products, shoes, footwear, machinery, instruments and accessories.
The top export partners of Vietnam are United States, China, Japan, South Korea, and Hong Kong. As per Vietnam custom data, the exports of the country climbed 19% as it saw the record trade surplus with United States, its largest export market.
The total exports of Vietnam came in at $336.31 billion while it rose 26.5% to $332.23 billion resulting in trade surplus of $4.08 billion. Exports of the country increased 8.5% from November to $34.59 billion.
The United States is the largest export market for products as garments, electronics and smart phones. Exports to US last year rose by quarter to $96.3 billion. China is the largest trading partner on which Southeast Asian country relies heavily for materials and equipment for its labour intensive manufacturing.
Vietnam was the 20th importer country in the world during 2019. As per the Vietnam Import Data the imports of Vietnam totalled USD 253.4 billion in 2019 up by 11.2% as compared to the previous year. The major imports of the country are machinery and industrial equipment, electronics, petroleum products, raw materials, clothing and shoe industries, plastics, automobiles, metal and chemical products. The main import partners of the country are China, Japan, Taipei, Chinese, United States, Thailand, Malaysia, India and Indonesia. Imports at the end of 2021 were up 3.1% to $31.62 billion.
Russia Mostly Export wheat and Crude Petroleum
What is HS Code? Why is it Important for the Import and Export of Goods?
0 notes
Text
India’s Mobile Phone Exports: Key Insights for 2024–2025
India's mobile phone export sector has experienced remarkable growth, with FY24 continuing the trend. The country exported smartphones worth $15.6 billion, reflecting a 42% increase from the previous year.
Visit Blog - https://medium.com/@harshsinghseair/indias-mobile-phone-exports-key-insights-for-2024-2025-4eaf56b0cc04
1 note
·
View note
Link
Welcome to the world of SEAIR Exim Solutions. This is a global trade data providing company that also offers the list of harmonized system code of desired products. You can access this code of any kind of item like rice, mobile phone, electronic item, cosmetic item and many more. To understand this concept better, visit the given link details give the government a reference about revenue going from the India. Short Circuit and Earth Fault Indicator China Export data which better for the firms which want to grow in the field of import and export. we provide comprises HS code, Product Description, Bill of Loading Quantity, Country Name, and Port Name etc

1 note
·
View note
Text
ACER HS-USB Android DIAG (COM38) Driver Download For Windows 10

Acer Hs-usb Android Diag (com38) Driver Download For Windows 10 Latest
Acer Hs-usb Android Diag (com38) Driver Download For Windows 10 Free
Acer Hs-usb Android Diag (com38) Driver Download For Windows 10 64
In this post, we’ve managed to share you the Bundle of the Newest Qualcomm HS-USB QDLoader 9008 Driver for Windows 7,8/8.1, 10. This driver will use both 32 Bit & 64 Bit OS. We have also shared an in-depth tutorial for How to Install Qualcomm Driver or Installation them onto your Personal Computer running Windows OS.
Download Qualcomm HS-USB QDLoader USB Driver
This USBAcer1.0W7x64W7x86A.zip file has a zip extension and created for such operating systems as: Windows 7 / 8 / 8.1 / 10 / Vista / XP. This software is suitable for ACER Composite ADB Interface, ACER USB Ethernet/RNDIS, Gadget CDC VCOM Driver. It is available to install for models from manufacturers such as Acer, Mediatek, Other and others.
Download Acer HS-USB Android Diagnostic Driver 1.0.10.0 for Windows 7/Windows 8 (Other Drivers & Tools).
This Qualcomm HS-USB Driver package is for 64-bit OS, you can download the 32-bit version of the driver here. If you would like to install the drivers manually, download these Qualcomm Drivers. Download Qualcomm chipset based android mobile. Qualcomm USB driver on pc into DIAG 901D COM in Device. Acer Aspire Sound Drivers Downloads for Windows 10, 8, 7, XP, Vista with Drivers.com - help with how to fix missing or outdated Acer Aspire Sound Drivers. Go Acer's website and check for any updated driver. If none is available, download the latest available Windows Vista driver if one is available, right click the Setup file and click Troubleshoot Compatibility and follow the on screen instructions to install it.
Nowadays, The Snapdragon Chipset can be used in most devices. The prevalence of Snapdragon Processor-based apparatus is rising day by day. There are a lot of Major brands are utilizing Qualcomm Chipsets within their apparatus like Xiaomi, OnePlus, Samsung, LG, Motorola, Lenovo & So on. Hence, In some events, you need Qualcomm HS-USB QDLoader 9008 Drivers on your Windows PC.
Below in this article, You are able to Download Qualcomm Driver & Quick Guide to How to setup Qualcomm qhsusb_bulk driver on Windows 7/8/8.1/10 OS.
Quick Requirments:
Download Qualcomm QDLoader from Preceding link (Download From Here)
ADB Drivers & Mi PC Suite
Xiaomi Device running on MIUI
A Computer running Windows 7,8,8.1,10.
A Conventional USB Cable.
Qualcomm QDLoader USB Driver Download For Windows
Step 1 -Install either ADB or Mi PC Suite so as to communicate your device with Personal Computer. You have to need to set up ADB Driver by which Windows will recognize this gadget.
Step 2 –Now, Enable USB Debugging in your MIUI Device. For this, Visit Settings > About Phone > MIUI Version Tap on it 7 Times until it empowers the programmer option.
Again Contact Setting > Additional Settings > Developer Option > empower USB Debugging.
Alcatel usb cdc modem 3100 driver download. Driver Intel Audio. Driver G-Sensor. Making innovative technology accessible for all to Enjoy.Now. Bring more joy into your life with the latest news, offers and more from Alcatel.
Step 3 – Switch off your device and Reboot into Fastboot mode. To boot to Fastboot style, Press Power on button + Volume down button & wait till the Mi Bunny Logo appears.
Step 4 – In ADB Folder, Open Command Window thereby pressing Shift + Right-click the mouse button. From the menu select”Open Command Window here”.
Step 5 – Connect your telephone to Computer using USB Cable.
Step 6 – From the Command Window type, the next code & Press enter to boot your device into EDL Mode.
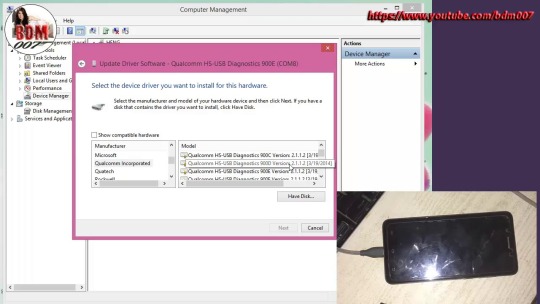
Step 7 – Now you apparatus will be from the EDL Mode now. Open device manager from control Manager by right clicking your computer icon.
From the device manager, you’ll observe that your device is detected but its drivers are not correctly installed.
It reveals your device by name”QHSUSB_BULK” in most instances.
Step 8 – Right-click on the device and choose “Update Driver Software“.
Step 9 – You will see a Windows Wizard or even Dialogue on your display. Pick”Browse my computer for driver software”.
Step 10 – Now extract Downloaded Qualcomm QDLoader USB Drivers on your computer and Choose Qualcomm > Driver folder in the extracted folder.
Amcc 3ware 9500s sata raid manager driver download for windows 10. Download AMCC 3ware 9000 Series SATA RAID Controller for Windows to sCSIAdapter driver. Microsoft(R) Windows(R) 2000 Advanced Server, the 3ware 9500S-8 66MHz SATA RAID controller and Maxtor(R. Broadcom Inc. Connecting Everything. I'm using the LSI 3ware 9650SE with Windows 10 x64 PRO with no issues. The driver I'm using is from 2/14/2013 (downloaded from LSI - Avago). My setup is RAID 5 with 4 4TB hard drives. All systems Windows 10 x64 Windows 10 x86 Windows 8.1 x64 Windows 8.1 x86 Windows 8 x64 Windows 8 x86 Windows 7 x64 Windows 7 x86 Windows XP x86 AMCC 3ware 9500S SATA RAID Manager 3.00.04.070 ( ).
Step 11 – Pick”Install this Driver Software Anyway” to install this driver in your windows. Dont worry it is asking for permissions only.
Step 12 – You may see the Driver installation completed successfully.
You will realize your apparatus will be listed in Device Manager.
Includes AMD tools to easily convert your video filesAMD Media Codec Package or formerly known as ATI Avivo is a complete set of tools that you will need for converting videos and transcoding.It consists of AMD Video Converter and the media codecs for transcoding applications.Please note: AMD Video Converter will only work with ATI Radeon HD 2000 and above video cards. AMD Media Codec Package 11.12 is available to all software users as a free download for Windows.Filed under:. AMD Media Codec Package 11.12 on 32-bit and 64-bit PCsThis download is licensed as freeware for the Windows (32-bit and 64-bit) operating system on a laptop or desktop PC from video codec packs without restrictions. Amij dscdma command port (com17) driver download for windows 10.
Conclusion:
That is it! We’ve successfully Install Qualcomm QDLoader USB Driver on your PC. Now, It Is Easy to Unbrick your apparatus from EDL Mode or Download Mode. You can use Comment Section if you faced any issue associated with this.
Download Qualcomm HS-USB QDLoader USB Driver (2019) | Xiaomi Buzz
Get information on how to Download Qualcomm QDLoader USB Driver.a step by step guide to install Qualcomm QDLoader USB driver on Windows 7/8/8.1/10.
Acer Hs-usb Android Diag (com38) Driver Download For Windows 10 Latest
Price Currency: INR
Acer Hs-usb Android Diag (com38) Driver Download For Windows 10 Free
Operating System: Windows
Acer Hs-usb Android Diag (com38) Driver Download For Windows 10 64
Application Category: DriverApplication

0 notes
Text
Buy Steam Knight verification code. When investing geniuses David and Tom Gardner have a stock tip, it can pay to listen. After all, the newsletter they have run for over a decade, Motley Fool Stock Advisor, has tripled the market.
This article is a transcript of this conference call produced for The Motley Fool. While we strive for our Foolish Best, there may be errors, omissions, or Buy Steam Knight number inaccuracies in this transcript. As with all our articles, The Motley Fool does not assume any responsibility for your use of this content, and we strongly encourage you to do your own research, including listening to the call yourself and reading the company's SEC filings. Please see our Terms and Conditions for additional details, including our Obligatory Capitalized Disclaimers of Liability.
Good morning, everyone. And thanks for attending our resource conference code. We started the year with the high hopes that the worst of the pandemic was behind us. Unfortunately, already February. The second wave started with some resiliency. This has spread more broadly during March. Of course, this time, we were more prepared to sustain the impacts from more strict measures to control the spread of the virus. Also, the fact that CDs implemented those measures in different moments of the quarter made a difference in our over attacted. In all, the consequences of the second wave in our business was smaller than the first wave a year ago. Considering these are not altering materially any part of our strategic plan disclose to you in our team Brazil day. Later the project, not the targets are going to be changed. We are confirming our entire guidance. The first quarter was marked by excellent execution. We accelerated our recovery started in the second half of the last year. And both revenues and Buy Steam Knight code are growing more in our recent results. We closed the quarter with service revenue growing more than 3% year over year. ABA abga can in very solid up 4.5% versus last year, it some more than 2 billion, representing a margin of almost 47%. As you probably saw last night, we'll reach an agreement with HS completing the deal for our fabrico a great deal for both companies. As I said, our customer platform plan is moving forward. And we are much closer to announce new partnership for distance learning education and digital wallet on the technology front, which more than 4000 cities covered with 4g and more than 120 sites in the sky coverage project. We also signed the agreement with the vendors for our journey to cloud project.
These achievements show our commitment to improve the quality of our service implement more cost efficient solution, and last generate social and environmental positive impact as we detail in our ESG plan. Last but not least, this quarter there Tim live was appointed as the best broadband service in Brazil. detailing our revenue acceleration we still positive contribution coming from mobile and fixer services with our lines posting better growth rates. Then the fourth quarter mobile service revenue accelerated to grow to 8% year over year with postpaid segment growth, also spending up to reach almost 4% mobile service revenue is also receiving the contribution of customer platform projects. And this is the second quarter that we look revenue from this new revenue stream in this quarter, it some 17 million. In parallel pizza services are also growing faster up by 12% with a solid contribution from the lives of more than 20% year over year. ARPU improvements in all segments are a significant driver for both mobile and pix accelerations. The key element of our mobile recovery amid the second wave of pandemic is the ability to play our game of from volume to value. despite there being so close across the country impacting our commercial activity, our mobile app you grow almost 7% year over year with postpaid and prepaid contributing positively to the performance. We expected to improve even further our prepaid dynamics. In the first quarter, we increase the participation of Evie charges to 55% of the total and accelerating the adoption of team Mies van tarjan advantage problem in mostre. prepaid recharges were likely positive versus last year, back in every day I have by 9%. For postpaid churn reduction was a highlight once again.
how to get Steam Knight verification code, Steam Knight phone verification bypass, Steam Knight verifying your number, Steam Knight verify phone number, skip Steam Knight verify, your phone Steam Knight phone number login Steam Knight login code text Steam Knight sms verification error 2018 how to get Steam Knight verification code Steam Knight verifying your number Steam Knight verification failed how to get Steam Knight verify number random verification code text text how to get Steam Knight verify number how to get Steam Knight verification code Steam Knight phone verification bypass Steam Knight verifying your number Steam Knight verify phone number skip Steam Knight verify your phone Steam Knight phone number login Steam Knight login code text Steam Knight ms verification error 2018 how to get Steam Knight verification code Steam Knight verifying your number Steam Knight verification failed how to get Steam Knight verify number random verification code text like verification code flurv verification code your Steam Knight verification code is verification code spam tfs verification code text atom verification code Steam Knight verification code not working random verification code, text like verification code, flurv verification code, your Steam Knight verification code, is how to get Steam Knight verify number, Steam Knight verifying your number Steam Knight verification failed Steam Knight login code text Steam Knight verification code not working Steam Knight sms verification error 2019 Steam Knight verification failed tap to try again Steam Knight verify your phone Steam Knight login code text Steam Knight sms verification error 2018 Steam Knight verification code not on Steam Knight but received login code via text message how to get Steam Knight verification code Steam Knight verification failed Steam Knight error bypass Steam Knight sms Steam Knight verifying your number Steam Knight no sms verification Steam Knight login code text how to get Steam Knight verify number how to get Steam Knight app verification code Steam Knight app phone verification bypass Money Lion app verifying your number Steam Knight app verify phone number skip Steam Knight app verify your phone Steam Knight app phone number login Steam Knight app login code text Steam Knight app sms verification error 2018 how to get Steam Knight app verification code Steam Knight app verifying your number, Steam Knight app verification failed, how to get Steam Knight app verify number, random verification code text like verification code, flurv verification code your Steam Knight app verification code is Steam Knight app verification code spam tfs verification code text atom verification code Steam Knight app verification code not working random verification code text like verification code flurv verification code your Steam Knight app verification code is how to get Steam Knight app verify number Steam Knight app verifying your number Steam Knight app verification failed Steam Knight app login code text Steam Knight app verification code not working Steam Knight app sms verification error 2019 Steam Knight app verification failed tap to try again Steam Knight app verify your phone Steam Knight app login code text Steam Knight app sms verification error 2018 Steam Knight app verification code not on Steam Knight app but received login code via text message how to get Steam Knight app verification code Steam Knight app verification failed Steam Knight app error bypass Steam Knight app sms Steam Knight app verifying your number Steam Knight app, no sms verification Steam Knight app, login code text, how to get Steam Knight pp verify number.
Web: Pvapins
0 notes
Text
AHSEC Result 2021 || Assam HS Final Result 2021 || AHSEC
The Assam Higher Secondary Education Council (AHSEC) conducts the Higher Secondary (HS) Board Examination. AHSEC has announced the schedule for the board exams 2021.The 12th Board Exams 2021 will begin from May 11, 2021 and will end at June 14, 2021.he board exams will be conducted in two shifts i.e morning shift which will be from 9 am to 12 pm and the afternoon shift which will be from 1:30 pm to 4:30 pm. The exams will begin with Multimedia & Web Technology / General Foundation Course II which will be conducted in the afternoon. The Board has announced that the exams will be conducted with strict covid guidelines stated by the central and state government. The safety of the students will be the top most priority of the board. All the students have to wear face masks while giving the board exams. The sanitation facility will be available at all the examination centers in the state. AHSEC provides admit cards to students for appearing in the HS Final Examinations 2021. The Admit Cards are dispatched all the AHSEC-affiliated schools generally a month before the start of the examinations, which in 2021 is 11th May 2021. So, students must get their Official Admit Cards for Examinations in the month of April 2021. The Assam Class 12 Results 2021 will be announced by 30th July 2021.The students can view their results at our website https://www.results.shiksha/assam/ahsec-class-12.htm. Students should regularly visit our website to view the updates about the Assam 10th Board Exams 2021. The steps to view the results are as follows: -
Visit the AHSEC Result 2021 Official Website - www.results.shiksha or Download the 'Upolobdha Mobile App' from Google Play Store for free.
Enter your AHSEC Roll Code & Roll Number as it appears on your admit card and click on the Get AHSEC Results button.
Your Assam Class 12th Result 2021 will be displayed instantly.
Take a printout of your AHSEC Result 2021 for future reference. If checking on the Upolobdha Mobile App, click on Download Result button to download the HS Final Results 2021 on your phone & share it with your friends using WhatsApp, Email etc.
For details about other Boards of Education, visit our website https://www.results.shiksha/. All the Best!

0 notes
Link
Welcome to the world of SEAIR Exim Solutions. This is a global trade data providing company that also offers the list of harmonized system code of desired products. You can access this code of any kind of item like rice, mobile phone, electronic item, cosmetic item and many more. To understand this concept better, visit the given link details give the government a reference about revenue going from the India. Short Circuit and Earth Fault Indicator China Export data which better for the firms which want to grow in the field of import and export. we provide comprises HS code, Product Description, Bill of Loading Quantity, Country Name, and Port Name etc

1 note
·
View note
Text
Responsive Web design:

Link: [Responsive web design: key tips and approaches](https://99designs.com/blog/tips/responsive-web-design-key-tips-and-approaches/?fbclid=IwAR2Ajkr2Z4QolMcp8ov-Hs-QYalGwjlD-P5Kpp-5weRWZaEnKV62iUrKpXs)
What is it?
>: A responsive web design (RWD) is an approach that allows design and code to respond to the size of a device’s screen. Meaning it gives you the optimal viewing experience not matter the display size.
Best RWD:
>: utilise fluid grids, flexible images and CSS styling to later the site’s design and render it according to the width of the browser.
>: the ultimate goal should be to seamlessly tailor the UI and UX of a website design across different devices and platform.
Important?
>: It would not be efficient for countless versions of the same website that worked for every known device. The process would not be practical time-wise and would cost a lot.
>: Render sites ineffective to future technology changes and make them nearly impossible to maintain.
>: Responsive design is an effective solution to future proof your website
>: know your audience and what device they’re using to view your website.
To Note:
>: User experience is KEY: responsive design needs to be more than contrasting a desktop site into a mobile screen. We need to consider the user’s experience, their interaction and the essential content they’re actually looking for while using a mobile device.
>: Design for the latest mobile device.
>: EngagementL the hierarchy of the layout is super important especially on mobile. The mobile experience compared to desktop is much more focused with limited spacing, so be clear how your phone web would allow the users to navigate around.
>: Flexible images: How image would scale, how an image would looks on a desktop screen vs a tablet vs a mobile screen.
>: Navigation is also important on movie. Many Mobile webs uses a hamburger style menu, a dropdown selection, expand/collaspe filed or tabs that scroll horizontally.
>: Gestures: people who love reading with their hands interact with content, this empowers the user. On mobile and tablets, users can pinch to zoom or slide images across screen. Interaction greatly affects the design.
For Apple, the comfortable minimum size of tappable UI element is 44x44 px. This limit is often broken and the real estimate is 25 px
Google’s resin is a good resource to quickly preview your site on multiple devices. https://material.io/resources/resizer/
[Responsive Web Design - What It Is And How To Use It — Smashing Magazine](https://www.smashingmagazine.com/2011/01/guidelines-for-responsive-web-design/)
0 notes
Text
PCB (Printed Circuit Board) Design and Routing Tips as well as Techniques
PCB (Printed Circuit Board) Design and style and Routing Tips and also Practices

instant pcb quote 1. Introduction Some sort of PCB is a paper circuit board. PCBs tend to be a part of our own everyday lives; Computers, Mobile phones, Calculators, Wrist-watches and each and every electrical component we work together with every day. This content is targeted at experts that happen to be familiar with Appliance design and still have PCB style and design background. special offer for 2layers pcb 2 . not Shaping the PCB The most prevalent shape regarding PCB is actually rectangle. Quite a few people also choose to get the corners rounded, because this decreases the possibility connected with edge-cracking. Is very important of PCB highly depends upon where you are going to place the board, and precisely what your mechanical needs usually are (the final container wherever the product is placed). Usually, there are four big cracks in the actual board, each ditch in one corner. These holes are used to have the board in position making use of a patch or a new PCB holder. The dimension is usually more than 2 millimeters, in addition to it is plated. 3. How many layers to make use of? Now we get in order to the next phase, exactly how many layers should most of us use? This highly will depend on the maximum frequency applied in the look, how several components you have, regardless of whether you have Ball-Grid-Array ingredients not really, and most important of all, just how heavy your design is actually. To get systems running up to 85 MHz, usually it can ok to use 2 Levels, should it be feasible to course the panel doing so. Have M. E. Certification and also FCC regulations in consideration. Nearly all of the times, the particular require a more -130dBm emission on general public radio band (FM 80-108MHz). This kind of can be problematic when you use a high-current clock operating involving forty five to 80 MHz (The second harmonic can be involving 80 to one hundred sixty MHz, which can easily break these rules). For programs running above 80MHz, it is important to consider using a lot more layers, (4 is great example). There are actually 2 tactics in 4 layers: Best and bottom level layers can easily be Ground in addition to Electric power planes. The middle coatings used for routing. Leading in addition to bottom layers used for indicate, Middle layers used for aircraft Typically the first method has a top notch signal quality, because signals are sandwiched involving a couple power planes, as well as as a result, you will have minimum emission. The next procedure can make direction-finding easy, as you will not need a via (vertical interconnect access) for each and every pin, as the pin number resides for a passing fancy signalling coating. Further more, the interior air carriers can have multiple destinations, to cover all your power needs, reducing typically the via count number even further more. BUT this method are often very tricky, and it will be extremely important NOT TO EVER split power planes within dangerously fast signal, as this appear into a return journey hook, making unwanted release more prone to occur. Using considerably more tiers always results straight into good quality of product, although it can certainly make it far more expensive to develop, mainly in the prototyping stage. (The distinction between 2 layers nouveau modele and 4-6 layers, could be as high as few 100 dollars). The six-layer+ method is nearly ideal. Making use of top and bottom part as power-planes and inner surface layers to get routing could prevent release, increase battle to noise and significantly reduce design work, since there are more layers to use for routing. Impedance-matching can be done easily, and many of us will cover this intended for high-speed signals. four. Planning layers for Impedance-matching With this point I think you dealing with a high-speed system which has SSTL, HSTL, LVDS, RSDS, GTL+, Speedy TTL and other excessive interconnections (USB HS, second . 5Gbps PCI-Express, etc. ). These routings require exclusive considerations. The lines involve impedance-matching. For many newcomers, this is often a questioning term. The difference involving Impedance and Resistance is excellent. If an individual need resistance matching, you can easily use a resistor along with be through with it. Impedance matching, on the other hand, has acquired nothing to do with resistors. It depends in the Thickness of often the track, the underside power-plane, whether is it Strip-Line (Surrounded between two strength planes) or uStrip (which suggests has a electrical power plane within it, nevertheless the other aspect will be free, as in TopLayer or BottomLayer). To achieve a specific impedance on any track, you must carefully select these details. Use the impedance calculator (search google) to find the appropriate beliefs for width, top on the power-plane, and width of the metallic layer, for you to achieve the ideal impedance (usually 50 as well as 70 ohms). Be encouraged that will a miss-matched impedance interconnection (especially on RF, Speedy USB, SATA or PCI-Express, and memory lines such as SSTL or HSTL), and also the board fail with virtually no obvious reasons. This will drive you to go for the next original, without ever finding just what brought on the first prototype to fail. five. Power-planing. Power-islands are one the most significant factors in a high-speed digital design. An FPGA or perhaps high-speed processor table together with in-accurate power-planing can easily be very unsound. In early days, you may route power tracks a little broader than signal-tracks, and handled them such as normal internet connections. Today, often the story is different. The use of and FPGAs or Excessive processors, you should know that a big number regarding flip-flops are switching with any given moment with your system. Their switching the huge amount of current heading back-and-forward through their particular energy and ground pin codes. Typically the ground-pins in this kind of case can create ground-bounce if the amount connected with current (and especially the actual slew-rate) will be high. I actually must remind a person associated with the famous V=L. di/dt (Delta-Voltage equals inductance x current-rate). If you work with a trail (for instance) to course ground signal, you will have distinct voltages on each aspect with the track. It may be very hilarious for you to have +0. 5V using one side of your ground, in addition to -1V on the other side. This can cause COMPLETE SYSTEM FAILURE. I recall experiencing this matter in early time, that forced me to issue even the very essential physical structure rules I realized. Discovering this specific bug can easily be difficult, and even in the event discovered, you will have no choice nevertheless to generate another prototype. The same guideline applies intended for power-plane a pair of. You can certainly easily have drops in many tracks if you carry out not use a jet, or a large power-islands, to compliment your power r�sistance. Having a greater number connected with decoupling capacitors is very recommended for speedy along with high-powered processors/FPGAs, near their power lines. The particular RF section, and the power-supply switching sections needs special care for their ground-planes. Their very own islands should end up being isolated from system ground-plane, and need to have tracks attaching your transferring island to help system surface (the tracks should be large enough to be able to have near-zero DC resistance, but not more). This specific is because transferring along with RF section, can establish mounds on ground-plane, which often can generate ground-bounce on your systems ground. You can research google on this subject if you need more justification.
0 notes
Text
Bluetooth Headset FAQs
Notice these points:
1. Under ordinary conditions, when Bluetooth headset reaches pairing mode, simply press the power button for approximately 10 minutes without letting go, the headphone will probably switch from"off" to"on" then to pairing mode, displayed since the headset indicator light (long time). Then looking for Bluetooth place in the cell telephone, you can discover your headphone.
2. The factory settings of several headphones are comparatively complicated, such as Sony Ericsson HBH-602 HBH608 HBH610A and Nokia HS-36W and so forth. When HBH-602 is coding, then you have to turn the headset , then hold down"+"and"-"simultaneously for 10 minutes. At this moment, the indicator light flashes green and red , which means that you can use your cellular phone to look for Bluetooth devices. To get HS-36W, turn to the headset, then hold down the power button and then"+" for 10 minutes or so, additional measures are exactly the same with normal headphones.
3. When check this site out Functions pairing mode, cell phone should look for Bluetooth devices. Generally it requires the cell phone about 5 minutes to locate the headset. Then pick the Bluetooth headset located on your telephone, and the phone will prompt you for a password. The majority of the phone password is 0000 or 1234, however, in addition, there are people which are especially set by producers. There's detailed information on your headset directions.

4. When the cellular phone discovers the headset and also you Have entered the right password, it doesn't imply you could use Bluetooth headset to get calls. Currently a great deal of phones have to get linked to the headset following locating the Bluetooth device. If your telephone isn't on the headset at the configurations, then you can not answer the telephone. Obviously, some phones like Motorola V3 don't have to link to the headsetas long as the pairing is successful, the phone will connect with the headset quite intelligently. This procedure is acceptable for many Bluetooth headsets.
Many Bluetooth headsets can't be linked occasionally. It's revealed that the cans have entered coding position, however, the phone can't locate the headset. Or the telephone has discovered the headset, but the password is invalid. This is principally because the brand new Bluetooth headset chip application isn't actuated, or the connection times from the cans memory is complete.
Most headphone makers are utilizing a unified functionality Approach in manufacturing, that's pressing on the"power switch" and"volume +" button in precisely the exact same time for 15 minutes without letting go, for example Nokia 3W/21W
Notice the usage of Bluetooth devices:
1. Charging: Charging any new Bluetooth devices, the most period is 3 hours.Usually it's time to lower the electricity when you find the indicator light on the headphone altering color or turning away. Long-time billing the product will result in serious harm.
2. Use: You had better place The telephone and the headset on precisely the exact same side of their body so the headset may obtain the mobile phone signals more readily.
3. Should you Don't utilize Bluetooth product for quite a very long time; you would better control the apparatus once per month or so, otherwise its internal battery goes into sleeping mode and cannot be re-charged and utilized.
1. Bluetooth devices can't be billed? Response A: If the Bluetooth headset is fresh for Quite a While, you Have to charge it for approximately 20 minutes to activate the Bluetooth headset battery.
0 notes