#module8
Explore tagged Tumblr posts
Text
Login Leaks Perl Script
In order to solve this challenge I wrote a really quick perl script which looked at every line of input and every character in that line to determine the next letter in the password. Time complexity wise I thought of quite a few ways in which I could improve my solution, however in the interests of time I decided not to implement these and instead went for what I thought was the easiest solution to implement. I chose perl because it’s good with files and I was able to easily forge a solution.


Which was the correct answer:

1 note
·
View note
Text
Blog Entry # 7: To earn or not to earn?
So this is it. The last content of this sasthoughts101 Blog Series.
For my last entry, it will be a brief discussion of myself and the competitive world around me. The society that we live in is changing and in the context of labor and employment, we are all part of the circus where the people in higher ranks enjoy and the one doing the job gets to be squeezed out. Ironic I should say. But as someone who is still in college. I always ask myself, “Am I gonna do it after graduation? Is there a company that is going to accept me?”
The anxiety has never been at an all time high as I approach my last year or two in college.
It is always hard when someone asks, “Ano work mo?” or some very ignorant person asking “May work kana?” This, for me, all hits so bad psychologically, mentally, and emotionally. As individuals, we tend to have the idea of getting work as a symbol of being productive and eager to get our way through the current life that we have. Asking someone’s work can be very uncomfortable.

Image credits from Pinterest.
Having a stable job is not purely a way of getting paid and having the means to feed yourself and buy things that you want. It is an essential human activity, as well as being a responsibility, that transforms the self, sustains organizations, and empowers the country. Our role in our country being citizens is not only limited to being contributors to the nation’s economy as consumers but being producers, too. Our contribution to the world of work and the productive economy is an expression of our citizenship and connection to the larger and greater community.
As I get through college, I sense that the landscape of labor and employment in our society is rapidly changing and moving forward. Due to the advancements brought by technology, more competitive individuals are being raised and surge themselves in a global scene of success and transformation. in the contrary, becaus of the rapidly changing information and communication technologies, increasing globalization, labor flexibilization, financial crisis, and intensified competition, many promising jobs of the last decade are no longer in demand, leading to work dislocations. This is so sad that sometimes, humans are replaced by Artificial Intelligence robots and computers.
Here in the Philippines, jobs-skill mismatch is often touted by government agencies as a big driver of unemployment. A reason for many Filipinos not to stay and work here but go and venture opportunities abroad where, in all fairness, Filipinos are recognized because of the quality of work they do. How much more if these passionate people are well-compensated, well-accepted of their skills, and well-trained, be utilized here in their local lands? What could have been a more productive labor environment could we have?
I cannot blame people in the workforce for going to rallies and voice out their concerns about compensation and regularization issues. The country has to step up its game in providing quality benefits among its professionals so that we can maximize the skills and abilities that they have in our own land.
At the end of the day, may it be here or abroad, given this complex environment and culture of work, we need to be adaptable, dynamic, innovative, flexible and resilient to accommodate and thrive in workplaces to create work worthwhile and fun for ourselves.

Image credits to Pinterest.
0 notes
Text
Lecture 8
This week it was the responsibility of my tutorial class to take lecture notes. So I typed my notes for both lectures directly into the shared course notes google doc. I have witnesses that can testify to both my presence at the lectures, and the fact that I contributed a significant portion of the notes in the google doc.
So please accept the link below to the shared google doc notes as my lecture notes for this week.
https://docs.google.com/document/d/1j7ITGGO6stE3A6T5Z-F5w14DkLgHoSmGER_WfzuTz5Y/edit
0 notes
Text
Login Leaks
Wrote a script 4 this.
{><!A9-n$)(e*WzqL_&Zf2R6^d}
0 notes
Text
Google Yourself
For this activity I didn’t find anything very interesting in my google history data as it didn’t go back very far. However when I looked at my facebook data I was surprised at how many companies had my information. What was unsettling was that there were many companies that I had never heard of before.
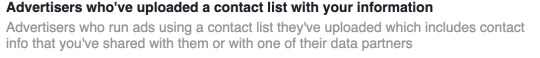
Not a fan of the term “data partners”....

0 notes
Text
Week 8 lecture reflection

This week’s morning lecture was about the human nature and how humans make errors. There was a note about how next week’s after lecture movie was going to be important for the final exam. The movie is going to be played after the evening lecture finishes at 8PM and I know I definitely won’t be able to watch it then. I guess I’ll have to be creative if I’m going to watch it in preparation for the final exam.
Buckland talked about several instances of human error that lead to a disaster. Some disasters mentioned were the Three Mile Island accident, Chernobyl, Bhopal and Challenger disasters. Buckland also briefly mentioned the Schlieffen Plan. I’d like to briefly talk about that here.
Back before WW1, Germany had a war plan. The main aim of this plan was to prevent a two front war. This was because of the convoluted system of alliances between various European nations.
Germany was part of the Triple Alliance with Austria-Hungary and Italy. The other major military alliance back then was that of the Triple Entente, consisting of Great Britain, France and Russia. The Schlieffen Plan was a plan that prepared for a war with Russia. This was because if Germany were to be at war with Russia to the east, Russia’s ally France would also likely attack Germany from the west. This meant Germany would have to fight a war on two fronts.
Because Germany would be outnumbered in a two-front war, it could not win the war via attrition. The Schlieffen plan was to take care of France. It involved sending most of the German army west to fight France, knock France out of the war then send the remaining army to deal with Russia. They would do this by bypassing the heavily defended Franco-German border. The German army would invade through Belgium and quickly flank the French army. The main aim was to quickly take Paris and eliminate France from the war.
WW1 started once Austra-Hungary declared war on Serbia. Serbia was allied with Russia and Russia subsequently declared war on Austria-Hungary. Austria-Hungary’s ally Germany declared war on Russia and France. Germany’s Schlieffen Plan was put into action.
The plan failed due to a variety of reasons. Firstly, Germany did not expect Belgium to resist the German invasion. Not only did the Belgian army slow the German advance, the invasion of Belgium brought Great Britain into the war further adding to the enemies that Germany had in the west. The Germans took way too long to reach France, and ultimately failed to reach Paris altogether due to British intervention in France.
Secondly, the Germans did not expect the Russians to mobilise so quickly in the east. The original plan expected Russia to be slow to organise and mobilise their armies. This was because Russia had recently lost a war with Japan when the plan was conceived. Russia’s quick mobilisation meant Germany could not commit all their forces to the western front.
The combination of both of these meant the Schlieffen failed to quickly eliminate France from the war. Germany did end up fighting a war of attrition on both fronts. It also did not help that their ally in Austria-Hungary was incapable of fighting on its own, and their former ally in Italy defected and joined the war as an enemy belligerent.
This video produced by The Great War (fantastic YouTube channel by the way) explains the Schlieffen Plan in more detail. It’s quite interesting and worth the watch.
youtube
0 notes
Text
April 25, Thursday
The concept of individuation is one that resonates with me. As I get older, especially now with my being in college, I find that I disagree with my mom when it comes to a lot of things. When I was younger, I would try my best to listen to her whenever she would tell me something and obey her when she instruct me. There are many times now when I cannot bring myself to agree with her completely because I do not seem to understand what it is she may want from me or what her motivation is behind certain things. This is not to say that I do not listen to her at all or that I actively try my best to be disagreeable and disobedient. It is just that I am not as ready to accept everything she tells me. I feel the necessity to question (not in a disrespectful, condescending way) her and what she may try to communicate. I do not blindly follow what she says because even if I know she probably has a good reason, she is also capable of making mistakes. There are certain things that she may not grasp fully, yet I understand in a fuller sense. I also trust in my own abilities and in my capacity to reason and rationalize. I have been able to realize that this is a normal part of getting older and usually occurs in this stage of life—the stage of life which I am currently finding myself in. Knowing this, what I can do now is to practice my agency and independence in a proper, prudent type of way while also making room to understand my mom and see her as a person in the same way that I am a person.
0 notes
Text
Pre-Lab Reflection ~ Module 8
This Stargate Ghost problem holds similarities to man-in-the-middle attacks because it simulates 2 people, who cannot see each other, communicating over an insecure network, which in this case can be an environment where the Alien A can eavesdrop on the conversation and manipulate the message.
From my understanding of Richard’s lectures, the concept of issuing certificates in a real-life scenario is the solution to this problem. It would require the invisible sender to have a public key, certified by his/her trusted third party authority, with the message that they want to send. The certificate is signed by the sender’s private key or secret.
0 notes
Photo

#playwithlight #projection #mapping #mirror #elektromove #performance #conceptualart #interacting #madmapper #module8 #marcodemeo #dance #contemporarydance #visualarts #floorwork #acting Pic. #orianabarbuzzi (presso Spazio Tadini - Casa Museo)
#conceptualart#marcodemeo#playwithlight#interacting#performance#madmapper#mirror#visualarts#module8#orianabarbuzzi#elektromove#dance#acting#contemporarydance#projection#floorwork#mapping
0 notes
Audio
Create: Soundscape
As instructed, I’ve downloaded and installed Audacity, then create a 1 minute audio track with no use of any audio imports. I actually have had experience with Audacity a few years ago when I used it to convert audio files into desired format. That was it, I have never use the program to edit audio before, so this was my first attempt to do so. I’ve generated the audio with Chirps and some pink noise. I assumed the “Filters” was referring to the “Effect” menu, where I discovered High/Low/Notch filters. I used all three of them on random separate parts of the audio, and generally, it sounded horrible. The sound was quite irritating to my ears, so I added a bunch of other effects on it. I think I’ve tried all of them, there are definitely some over-lapses. It was all an experiment for me, I’ve tried to make it sounds like an actual tune with the echo, and Fade in/out rhythmically.
In the end, the final product sounds like some random noise my two year old brother would make when he’s playing with his toys. What have I learned, specifically about ownership and licensing? Well, other then downloading and installing the program itself where you have to read the program agreements before accepting it, I find ownership of intellectual property should be taken seriously. As I’ve tried to create my own piece, and it wasn’t easy at all without the knowledge of the specific field. Although technically, it is definitely possible to import someone’s else content and edit them as your own without breaking any copyright laws, as long as the finished product is within the appropriation of fair use policy. For instance, even if I imported a licensed audio file, I transformed the file into something else that’s different than the original, then it is considered a fair use.
0 notes
Text
Spot the Fake
This activity was all about how easy it is to fake things. Pretty much everything ever has been faked, from money to sound to video to animals and restaurants that never even existed.
For this activity I posted my answer on open learning. My thing to fake was a favourite drink because that’s what came to mind:
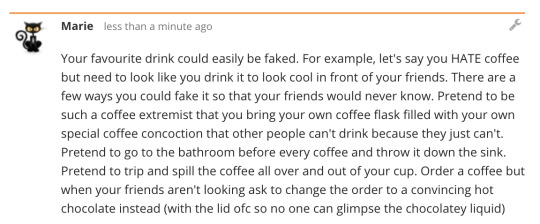
This activity made it obvious that anything and everything can be faked, and to be careful what you believe in because you can never be sure that it’s real.
0 notes
Text
Your Bestie During Exam Season, Quizlet
youtube
When it comes to exam season, many students are beyond stressed. This makes it hard for them to find an effective way to study, thus, many end up cramming the whole course worth of material the night before by reading the textbook. I have attempted this studying method during my first year of university, and let’s just say the results I got back were shabby… Fast forward three years later, I have redeemed myself and can now manage my studying habits better. Luckily, to make my life (and others life) easier, Andrew Sutherland created Quizlet. This studying platform is simple to use and extremely convenient. Users can study with Quizlet via the web or a mobile app (which makes studying on the go possible). Quizlet’s mission is to help students practice and master the subject they are learning with engaging and customizable activities. In addition, Quizlet is a community learning platform since students and teachers can contribute to the content by creating study sets. The study sets can be created for any subjects and be utilized for personal studying or public use.
Quizlet is a fun way to study as each study set contains a variety of interactive activities. The activities consist of:
Multiple choice questions
Image Source: Quizlet
Flashcards

Image Source: Quizlet
Mix and match
You have to drag the correct term to the definition and vice versa while being on a time limit.
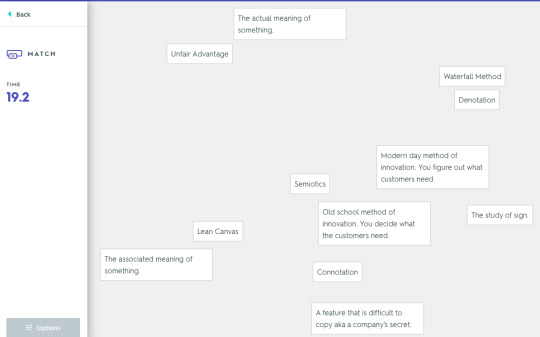
Image Source: Quizlet
Writing out the words
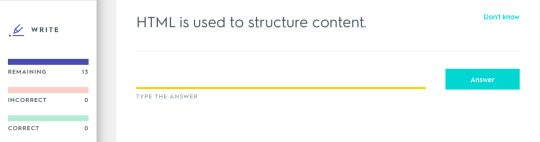
Image Source: Quizlet
Spelling out the words that you hear
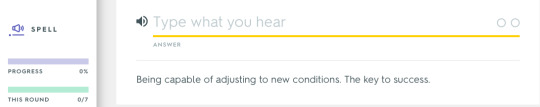
Image Source: Quizlet
Gravity game
The rule of the game is to protect the planets from incoming asteroids by typing out the answers. You also have the option to adjust the difficulty level of the game.
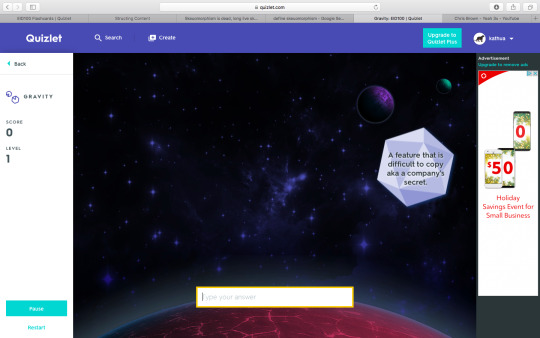
Image Source: Quizlet
For the purpose of this module, I have created a study set with 13 questions on Quizlet. The questions are simply based off of the terms and its matching definition learned in class. Below is the answer key to the study set if you do decide to check it out. Happy studying! :) ANSWER KEY
Skeuomorphism – Use of familiar concepts during the design process to invoke a sense of familiarity.
Affordances – Clues about how an object should be used.
Connotation – The associated meaning of something.
Denotation – The actual meaning of something.
Semiotics – The study of visual cues.
Waterfall Method – Old school method of innovation. You decide what the customers need.
Lean Canvas – Modern day method of innovation. You figure out what customers need.
Adaptability – Being capable of adjusting to new conditions. The key to success.
Unfair Advantage – A feature that is difficult to copy aka a company's secret.
Semantics – The study of language to deliver meaning.
HTML – HTML is used to structure content.
CSS – CSS is used to design or dress-up your content.
JS – JavaScript is used to control interactivity and change a browser's behaviour.
0 notes
Text
Tutorial 8
This week is presentations of people’s something awesome’s. Unfortunately the projector wasn’t working so we couldn’t do that many.
Presentations this week
FOIA submitted to see what digital information the police collected on Kamar the UNSW student falsely accused of terrorism. The police said no.
RNG It's very difficult to make a good one
Android forensics Use adb to make an image of a rooted phone Everything is stored as plaintext
I also did my presentation on Coreboot
0 notes
Text
Barbauthentication

She uses 2-step verification for her email account using Google Authenticator, and she signs up with new websites by using 'Sign in With Google', and for when she is at a computer she doesn't trust, she has generated a set of 10 one-use only passwords for her Gmail account.
Create a fake website to phish her and she’ll sign in with Google - then once that’s done send her a text and she’ll enter the Google Authenticator code. From there, you can just copy that code and log into her account!
0 notes
Text
Login Leaks
Just completed the login leaks activity. I wrote a program to solve it for me as there were 1000 different segments and doing it manually probably would have taken longer. My program simply adds the characters to the password based on the character location in the 3 character fragment. If I reach a character that is already in the password but it in the wrong position relative to the other 2 characters in the fragment then the positions are swapped. Most likely not the best solution but it worked since we were provided with an adequate amount of information about the password.



0 notes
