#require hardware keylogger
Text
Everything you need to know about keyloggers: a complete guide

A keylogger, sometimes called a keystroke logger or keyboard capture, is a type of surveillance technology used to monitor and record each keystroke on a specific computer. Keylogger software is also available for use on smartphones, such as the Apple iPhone and Android devices. Monitor the activities on any Android device with these efficiently hidden keyloggers. If you are interested in keyloggers, we will walk you through all the information you need regarding keyloggers. So let’s start our journey through keyloggers.
What exactly is a keylogger?
A keylogger is a software or application that enables you to record every activity on a device on which it is installed. It is basically a form of malware or hardware that keeps track of and records your keystrokes as you type. It takes the information and sends it to a hacker using a command-and-control (C&C) server. A keylogger monitors and records such activities without the knowledge of the device user.
Why do you need a keylogger?
These are used to quietly monitor your computer activity while you use your devices as normal. Keyloggers are used for legitimate purposes like feedback for software development but can be misused by criminals to steal your data. The reasons for installing or using a keylogger may vary from person to person. Let’s explore some most common reasons for using keyloggers.
Parental control
Parents may want to protect their children from cyber crimes. Keyloggers allow parents to monitor their social media interactions, Geo-location, call details, web history, etc. All this makes keyloggers useful for parents.
Employee monitoring
Employers or business owners may also want to verify whether their employees are properly utilizing their working hours. They may also want to know if their workforce is honest enough for their organization. For this reason, employers also use such apps commonly.
Stealing info
Cyber criminals also use keyloggers to steal passwords, bank details, financial information, etc.
Types of keyloggers
A hardware-based keylogger is a small device that serves as a connector between the keyboard and the computer. The device is designed to resemble an ordinary keyboard PS/2 connector, part of the computer cabling or a USB adaptor, making it relatively easy for someone who wants to monitor a user's behavior to hide the device.
A keylogging software program does not require physical access to the user's computer for installation. It can be purposefully downloaded by someone who wants to monitor activity on a particular computer, or it can be malware downloaded unwittingly and executed as part of a rootkit or remote administration Trojan (RAT). The rootkit can launch and operate stealthily to evade manual detection or antivirus scans.
How to install a keylogger on your smartphone?
To install a keylogger on any Android device, you just need single-time physical access to that device. Most of the keylogger or spy apps are not available on Google Play. As a result, you must first enable app installation options from third-party sources. You need to install the app by permitting the monitoring of the phone. Once you do all this, you can use the keylogger account for necessary configurations, such as monitoring apps. This configuration will enable the app to run in the background and record all the activities. You can later log into the desktop version of this keylogger app and view all the details of the activities.
To sum up
This article helped you understand keyloggers and find the right one for your Android monitoring needs. Ethical and sensible use of a keylogger can help you safeguard your assets, whether it is about your kids or your organization.
You may also want to explore the best keylogger app for Android and iPhone.
1 note
·
View note
Text
Cryptocurrency and Cybersecurity: Protecting Your Digital Assets
Cryptocurrency has gained significant popularity and recognition in recent years, revolutionizing the way we think about digital transactions and financial systems. However, as the world of cryptocurrency expands, so do the risks associated with it. Top 50 cryptocurrencies Cybersecurity threats pose a considerable challenge to cryptocurrency holders, making it crucial for individuals to take proactive measures to protect their digital assets. In this article, we will explore the importance of cybersecurity in the realm of cryptocurrency and provide essential tips to safeguard your digital assets.
- Understanding the Risks:
Cryptocurrency presents unique security challenges due to its digital nature and decentralized structure. Here are some common risks associated with cryptocurrency:
- Hacking and Phishing Attacks: Cybercriminals employ various tactics, such as phishing emails, fake websites, and malware, to gain unauthorized access to cryptocurrency wallets and steal funds.
- Social Engineering: Attackers may attempt to manipulate individuals into revealing their private keys, passwords, or other sensitive information through social engineering techniques, posing as trustworthy entities or friends.
- Malware and Keyloggers: Malicious software can infect devices, capturing keystrokes and compromising wallet credentials, allowing attackers to gain control over digital assets.
- Exchange and Wallet Vulnerabilities: Cryptocurrency exchanges and digital wallets may have vulnerabilities that can be exploited by hackers, leading to the loss of funds.
- Essential Security Measures:
To protect your digital assets and maintain the security of your cryptocurrency holdings, consider implementing the following measures:
- Secure Passwords: Use strong, unique passwords for all cryptocurrency-related accounts. Include a combination of upper and lowercase letters, numbers, and special characters. Avoid using easily guessable information such as birthdays or names.
- Two-Factor Authentication (2FA): Enable 2FA for all cryptocurrency platforms and wallets that support it. This adds an extra layer of security by requiring a second verification method, such as a code generated on a mobile device.
- Hardware Wallets: Consider using hardware wallets, such as Trezor or Ledger, for storing your cryptocurrency. These devices offer offline storage and added security measures to protect your private keys.
- Keep Software Updated: Ensure that all cryptocurrency-related software, including wallets and exchange platforms, is regularly updated to the latest versions. Updates often include security patches that address known vulnerabilities.
- Secure Network and Devices: Use secure, password-protected Wi-Fi networks when accessing cryptocurrency accounts. Regularly update and scan your devices for malware and use reputable antivirus software.
- Beware of Phishing Attempts: Exercise caution when clicking on links or opening attachments in emails related to cryptocurrency. Verify the legitimacy of the sender and website before entering any sensitive information.
- Backup Wallets: Regularly backup your cryptocurrency wallets and store the backups securely offline or in encrypted cloud storage. This ensures that you can recover your funds in case of device loss or failure.
- Be Mindful of Public Wi-Fi: Avoid accessing cryptocurrency accounts or making transactions using public Wi-Fi networks, as they may not be secure and can expose your sensitive information.
- Educate Yourself:
Stay informed about the latest security practices and cryptocurrency-related scams. Keep up with reputable sources of information, such as cryptocurrency news outlets and official announcements from cryptocurrency projects. Educate yourself about common phishing techniques, scam schemes, and best practices for securing your digital assets.
- Seek Professional Guidance:
If you are unsure about the best practices for securing your cryptocurrency holdings or need assistance in setting up advanced security measures, consider consulting a cybersecurity professional or engaging with reputable cryptocurrency security services.
The rise of cryptocurrency has brought about new possibilities and financial opportunities, but it has also introduced new security challenges. By understanding the risks and implementing robust security measures, you can protect your digital assets from cyber threats. Remember to stay vigilant, keep your software updated, and be mindful of the information you share online. With the right cybersecurity practices in place, you can enjoy the benefits of cryptocurrency while ensuring the safety and integrity of your digital wealth.
#Monero#monero.si#Hot cryptocurrencies#Cryptocurrencies#Cryptocurrencies list#Biggest cryptocurrencies
1 note
·
View note
Text
Cryptocurrency Wallet Security: Best Practices for Safeguarding Your Assets

In the digital age, securing your cryptocurrency wallet has become paramount. With the rising popularity of cryptocurrencies and the increasing frequency of wallet hacks and thefts, it is crucial to understand and implement best practices for safeguarding your assets. This article aims to provide a comprehensive guide to cryptocurrency wallet security, offering valuable insights and practical tips to protect your investments.
I. What is a Cryptocurrency Wallet?
1. Definition and Functionality
A cryptocurrency wallet is a digital tool that allows users to store, manage, and transfer their cryptocurrencies securely. Unlike traditional wallets, cryptocurrency wallets do not store physical currencies. Instead, they store private keys, which are essential for accessing and managing your digital assets on the blockchain.
2. Different Types of Cryptocurrency Wallets
When it comes to cryptocurrency wallets, you have several options to choose from, each with its own benefits and security considerations.
a. Hardware Wallets
Hardware wallets are physical devices designed to store your private keys offline. They provide an additional layer of security by keeping your keys disconnected from the internet, reducing the risk of malware attacks. Popular hardware wallets include Trezor and Ledger.
b. Software Wallets
Software wallets, also known as digital wallets or online wallets, are applications or programs that can be installed on your computer or mobile device. They provide a convenient way to access your cryptocurrencies but may be more vulnerable to hacking risks.
c. Paper Wallets
A paper wallet is a physical printout or handwritten document that contains the public and private keys of your cryptocurrency wallet. This type of wallet is considered highly secure as it is kept offline, away from potential online threats. However, it requires careful handling and safe storage practices.
II. Common Security Threats in Cryptocurrency Wallets
1. Potential Risks and Vulnerabilities
Cryptocurrency wallets face various security threats that users should be aware of. Understanding these risks can help you adopt the necessary precautions to safeguard your assets effectively.
2. Wallet Hacks and thefts
Wallet hacks, often resulting from negligence or weak security practices, can lead to the loss of your cryptocurrencies. Cybercriminals exploit vulnerabilities in the wallet software or the user's system to gain unauthorized access and steal funds.
3. Phishing Attacks
Phishing attacks involve the use of fraudulent websites, emails, or messages that imitate legitimate platforms to deceive users into revealing their private keys or other sensitive information. Falling victim to phishing can have severe consequences, including the loss of your cryptocurrencies.
4. Malware and Keyloggers
Malware and keyloggers are malicious programs that can infect your computer or mobile device, aiming to steal your wallet's private keys or login credentials. These stealthy threats can compromise your wallet's security if proper precautions are not taken.
5. Social Engineering Attacks
Social engineering attacks target individuals rather than technology. Cybercriminals use psychological manipulation techniques, such as impersonation or tricking users into revealing their private keys or performing unauthorized transactions.
III. Best Practices for Creating a Secure Cryptocurrency Wallet
A. Selecting the Right Wallet
Choosing the right wallet is crucial to ensure the security of your cryptocurrencies. Consider the following factors when selecting a wallet for maximum protection:
Factors to Consider
Wallet Types and Features: Understand the different types of wallets and the security features they offer. Assess which types align with your security preferences.
Reputation and Community Trust: Research the wallet's reputation and user reviews to gauge its trustworthiness.
Development and Update Frequency: Choose wallets with active development teams that regularly release updates and security patches to address vulnerabilities.
B. Set up and Installation
Proper setup and installation are fundamental to establishing a secure cryptocurrency wallet. Follow these steps to minimize the risk of compromise:
a. Obtaining Wallet Software
Download wallet software only from official sources or trusted platforms. Be cautious of third-party websites or links that may distribute malicious software.
b. Verifying Authenticity
Verify the authenticity of the wallet software by comparing digital signatures provided by the wallet developers. This ensures that the downloaded software has not been tampered with.
c. Installation and Configuration Steps
Carefully follow the installation and configuration instructions provided by the wallet developers. Pay attention to any recommended security settings.
C. Securing Your Wallet
Implementing robust security measures is crucial to protect your wallet from unauthorized access and potential theft. Consider the following best practices:
a. Strong Passwords and Encryption
Create strong, unique passwords for your wallet and avoid using easily guessable information. Enable encryption features offered by the wallet software for an additional layer of protection.
b. Two-Factor Authentication (2FA)
Enable two-factor authentication whenever possible. This adds an extra authentication step, ensuring that only authorized individuals can access your wallet.
c. Multi-Signature Functionality
Consider using wallets that support multi-signature functionality. This requires multiple authorized signatures to complete transactions, reducing the risk of unauthorized activity.
d. Cold Storage Alternatives
Explore cold storage options like hardware wallets or paper wallets. Keeping your private keys offline significantly reduces exposure to online threats.
e. Backup and Recovery Procedures
Regularly back up your wallet's private keys or recovery phrases. Store them securely in multiple locations, such as encrypted cloud storage or physical offline backups.
D. Keeping Your Wallet Safe Online
Maintaining adequate online security practices is vital to mitigate the risk of wallet compromise. Follow these guidelines for a safer online experience:
a. Safe Internet Browsing
Avoid visiting suspicious websites or clicking on unknown links. Be wary of phishing attempts and only visit secure websites (HTTPS) when interacting with your wallet.
b. Recognizing and Avoiding Phishing Attempts
Be vigilant about phishing attempts and avoid sharing your private keys or other sensitive information with anyone or any platform that requests it unexpectedly.
c. Regularly Updating Software and Plugins
Keep your wallet software and any associated plugins or extensions up to date. Software updates often include critical security patches that protect against known vulnerabilities.
d. Utilizing Firewall and Antivirus Software
Install and regularly update reliable firewall and antivirus software to add an extra layer of protection against malware and other online threats.
E. Protecting Your Wallet Offline
Physical security is also essential in ensuring the safety of your cryptocurrency wallet. Consider the following offline security measures:
a. Physical Security Considerations
Keep your physical wallet devices, such as hardware wallets, in a safe and secure location, away from potential theft or damage.
b. Secure USB and External Hard Drives
If you use portable storage devices to store wallet backups or private keys, encrypt them and keep them in a secure location when not in use.
c. Paper Wallet Storage
If utilizing paper wallets, ensure they are securely stored in a fireproof, waterproof, and tamper-resistant container to protect against physical damage.
F. Safe Transactions and Communication
Understanding the best practices for safe transactions and communication is vital to protect your cryptocurrencies from potential theft or unauthorized access:
a. Verifying Transaction Details
Always double-check the details of a transaction before confirming it. Confirm the recipient's address and the exact amount to prevent unintended transfers.
b. Securely Communicating Wallet Information
When communicating wallet information, such as public keys or addresses, consider using secure channels, such as encrypted messaging apps or secure email services.
IV. Additional Security Measures
A. Wallet Monitoring and Alerts
Implementing wallet monitoring and real-time alerts can provide an added layer of security for your cryptocurrencies:
a. Real-time Transaction Notifications
Enable real-time transaction notifications to stay informed about any transaction activity in your wallet. This allows you to detect any suspicious or unauthorized transactions promptly.
b. Wallet Activity Monitoring Platforms
Utilize wallet activity monitoring platforms or services that provide insights into your wallet's usage patterns. These platforms can help identify unusual behavior and potential security threats.
B. Understanding and Mitigating Third-Party Risks
Using third-party services, such as exchanges or online wallet providers, introduces additional security considerations. Mitigate potential risks by taking the following steps:
Assessing Security Features and Reviews
Research third-party services extensively, considering their security features, reputation, and user reviews.
Only choose reputable platforms with a proven track record of security.
C. Regular Security Audits and Updates
Maintaining the security of your cryptocurrency wallet requires periodic security audits and staying informed about the latest threats and updates:
Wallet Vulnerability Testing
Regularly assess the security of your wallet by conducting vulnerability testing. This can help identify potential weaknesses and take appropriate action to mitigate them.
Staying Informed About New Threats and Patches
Stay updated with the latest news and developments in the cryptocurrency security landscape. Follow reputable sources and subscribe to security newsletters to stay informed about new threats and patches.
CONCLUSION
Cryptocurrency wallet security is of utmost importance in the digital world. By following the best practices outlined in this article, individuals can significantly reduce the risk of wallet hacks, thefts, and other security threats. Remember, protecting your assets should be a continuous effort that involves selecting the right wallet, setting it up securely, implementing strong security measures, and staying informed about the latest security trends.
If you're interested in learning more, you can check out my recommended “Course of Crypto and Bitcoin”
"Disclosure: This article includes affiliate links. If you click on these links and make a purchase, I may earn a commission at no additional cost to you. I only recommend products or services that I have personally used and believe will add value to my readers. Your support through these affiliate links is greatly appreciated and helps me continue to provide valuable content on mastercryptoforall.blogspot.com. Thank you!"
#CryptocurrencySecurity#WalletProtection#CryptoWallets#SecureAssets#DigitalAssetProtection#CryptoSecurityTips#SecureCryptoStorage#ColdWallets#HotWallets#MultiSigWallets#HardwareWallets#TwoFactorAuthentication#CryptoBestPractices#CyberSecurity#ProtectYourAssets
0 notes
Text
Magento Security Guide: How to Secure Your Store in 2023
The article was initially published in WebMeridian blog.
It seems like almost every other day, some company you don’t remember giving your details gets hacked, exposing customer data to bad actors. Customers want to feel safe in the age of buying almost everything online.
To combat the issue for eCommerce operators, Magento 2 security features are built right into the platform, with provisions for additive measures to prevent or mitigate the effects of information theft, malware attacks, data leaks, and illegal transactions.
As the technology improves, so does the sophistication of the hackers trying to compromise users. As such, developers and store owners with experience have developed some best practices which mitigate risk further.
With these tips, a store owner can ensure that their customers and operations are safer beyond what is intrinsically offered as part of the Magento built-in suite of security features.
Let’s dive in.
Magento Security Best Practices
So, what are Magento 2 security best practices all about?
Well, when it comes to safeguarding the modern eCommerce operation, hackers have so much surface area to attack. That is why we conduct Magento security checks, audits and have implemented a kind of guide on how things should be done to reduce security risks.
Armed with these Magento security tips, you can, as a store owner, go a long way to safeguard your business as a whole.
Alright, here we go!
1. Always Update To The Latest Version
We are now firmly in the age of Magento 2, and for some users, there is a fear that the latest version of Magento is not the best, given that new versions tend to come with their own bugs. However, that is a holdover fear from previous technologies.
We recommend always staying updated with the latest version as it uses independent modular services to deliver new functionality instead of messing with the core code. On top of that, the latest version always comes with security fixes for all flaws.
Stay updated on patch versions to ensure no known flaws can trip you up.
2. Get on the Two-Factor Authentication Wagon
Typically, attackers on the internet have to get into your backend to start mucking around. With Magento two-factor authentication, a user is required to have two types of authentication to prove they are the admin before accessing anything.
The first form is often a password, followed by a code that can be sent using email or SMS, an authenticator app, or a hardware token.
Even if someone somehow gets your Magento 2 platform password, they cannot log in without the second factor. That is how you protect yourself from keyloggers, unauthorized logins, data sniffing tools, and other threats.
3. Encrypt Your Connections (SSL/HTTPS)
Encrypting your connections is a great way to keep your eCommerce store safe from hackers. SSL certificates are small data files that connect your Magento store’s details to a security key.
After installation on a web server, they activate the padlock and Magento HTTPS protocol to power a secure connection from the server to the user browser.
Using encrypted connections is a great way to tell your customers you care about them and instill confidence when they see the padlock icon and HTTPS preceding your URL. Using encrypted connections is also a great way to stay compliant with PCI DSS, which requires SSL certificates for checkout pages.
4. Avoid Weak Passwords
People often recycle their passwords across multiple accounts or use simple passwords that are easy to crack. Strong passwords are often long, complex, unpredictable, and unique. As you may have seen on some websites encouraging users to create better passwords, they are often a mix of lowercase and uppercase letters, spaces, symbols, and numbers.
Security experts often warn that you should avoid using your birthday, address, name, words from the dictionary, or other everyday things that a hacker might guess or brute force.
A strong password can deter hackers who test Magento security across sites just to see who left their door unsecured.
5. Make Use of Magento reCAPTCHA
Gone are the days of CAPTCHA, where users must decipher distorted text, images, puzzles, or audio to get access. reCAPTCHA is the new version of that, developed by Google, that leverages advanced risk analysis techniques to tell human users and bots apart.
With Magento security checks powered by reCAPTCHA, you can use a variety of verification methods that include:
I am not a robot- This checkbox lets users click ‘I am not a robot’ and select specific images to complete the challenge.
Invisible badge- Users get automatic verification in the background without interaction but may have to select some images to complete the check.
Verification using a score based on a Google algorithm requiring no interaction or challenge.
reCAPTCHA is more secure and accessible and offers a better user experience.
6. Change Your Admin Dashboard URL to Something Unique
On Magento, the default admin URL is /admin, which is easy to guess and susceptible to brute force tactics. A unique URL makes it harder for hackers and bots to find and access the admin panel.
Changing the URL admin to something more complicated and unpredictable can reduce the chances of Magento security breach that relies on the fact that many owners keep the default URL suffix.
You can change the admin URL from the admin panel by going to Stores > Configuration > Advanced > Admin > Admin Base URL and choosing custom admin URL or custom admin path.
7. Make Sure Your Site is Backed Up Regularly
You can almost guarantee that you never get hacked, lose data, corrupt data, or fall victim to human errors when using Magento. However, the probability is never zero, so backing up your site regularly is vital.
Backing up Magento 2 can help you recover files, databases, and media without losing essential functionalities or information. To backup, you can download your site data using an FTP client and back them up in our account.
You can also use your phpMyAdmin to export the stored database and always be ready to bounce back in case of anything.
8. Leverage Firewall to Prevent MySQL Injection
A firewall is a great way to prevent MySQL injection in Magento. The primary function is to block malicious requests that try to execute SQL commands on the Magento database. MySQL injection is a technique where hackers insert or modify SQL queries to alter, destroy, or access data they should not be accessing.
With such tools, attackers can breach your data, steal it, use the information to commit fraud, and cause other damage to your store and its reputation. A firewall can prevent MySQL injection in Magento by:
Turning down requests that have suspicious characters or patterns.
Analyzing requests to find known signatures or indicators of MySQL injection attacks like SQL keywords, error messages, or database names.
Implementing a white- or blacklist of allowed or rejected Ips, URLs, or domains.
Logging and reporting attempted or successful MySQL injection attacks for investigation and action.
9. Beef Up Security With Magento Security Extensions
Magento security extensions are patches released separately from the main platform that most e-store owners use to build out functionalities that enhance security, including:
Spam Killer- This extension blocks spam bots and prevents them from submitting forms on your site.
MegaFirewall Security- The extension blocks multiple kinds of online assaults, including cross-site scripting, brute force attacks, and SQL injection.
Two-Factor Authentication- this extension adds an extra layer of security to an admin login by requiring two factors that make it much harder for attackers to breach your admin dashboard.
You can learn more about Magento 2 security patches from the online store that offers them, as well as installation guides and more details in GitHub repositories.
10. Run The Magento Scan Tool
Magento store owners can use the Magento scan tool as part of their security best practices to run regular scans for monitoring their sites for threats, malware, and security risks. Using these scan results and appropriate actions to fix flaws, store owners can ensure they are always up-to-date and secure.
The Magento 2 security scan tool has a checklist that you can follow for tips to harden and protect the site from online threats.
11. Leverage The Expertise Of A Magento Security Audit Service
One of the best ways to identify security gaps is by hiring the services of a Magento security audit service. These experts help store owners find out what is wrong with their stores and recommend the best way to bridge them.
With the service, the store owners can get benefits that include:
The Magento security audit can check which version you are running, patches, known vulnerabilities, admin access best practices, admin user permissions, PCI compliance, payment methods security, brute force protection, DDoS protection, and more.
The audit can give you details on the security status of your website and a list of recommendations from a certified engineer on how to fill in existing gaps and protect the store.
The audit gives you ways to prevent data breaches, hacker attacks, legal issues, malware infections, financial losses, and more.
A security audit is a great way to identify gaps and fill them to prevent hackers from exploiting them.
Prevent and Mitigate Security Issues With An Audit And Best Practices
Staying secure in the modern world is a task that requires you as a store owner to not just find the most reliable platform with the latest technologies but also go the extra mile to ensure that all gaps are covered.
While you cannot prevent everything bad, think of how devastated your business would be if you lost or corrupted a ton of data but did not keep a backup. With a backup, you have continuity and will only lose time.
We call the tips we have discussed ‘best practices’ since they represent the best advice you can make a part of your Magento store owner’s standard operating procedure at any given time. Over time, these have emerged as some of the most common sense actions to see through and maintain to give your store the best chances of surviving the modern cyber threat landscape and flourishing despite the security challenges.
To cap it all off, we at WebMeridian offer Magento security auditing services, which is a great way to find and address any security issues. Come talk to us about your security posture and find out what we can do to help make it better!
1 note
·
View note
Text
Make Your Pc Perform Better By Discarding Spyware
There aren't an quick and solutions to slow servers. A sluggish computer can be attributed intercourse is a factors that will even signal a bigger problem. It could be a problem light and portable hardwares, Windows may quit optimized well, programs maybe pulling each other, the expertise of an ongoing update each morning program, or worst it might be an infiltration of viruses, spywares, malwares, or Trojans. Usually when we had tried everything our own power yet still fail we call our friendly technician to charge us some amount of money for the repair. Well, you don't really require that further. Some solutions may even be as simple as it could.
Outside of giving iobit malware fighter Registration Key , in addition, you stop them from downloading any viruses or malware. Programs that could possible delete your precious system files or any file for that concern. Only you install, only you delete.
Your screen saver has probably changed from is actually used end up being like. This can be a sure indication that your pc is infected with this dangerous program. Don't stress out so soon for there exists a way to refurbish this spyware infection.
In iobit malware fighter Registration Key to generate the PC run faster, it's very fortunate that folks need not do a manual registry hack. Tend to be a regarding registry cleaners out there that assistance maintain your Windows register. iobit malware fighter Activation Code Free can bump off a lot of invalid registry entries as well as erase orphaned registry entries that accumulate in your Windows system over IObit Malware Fighter Pro occasion.
Open Office - a wide open source application that can be used as the Word Model. It can be also used create spreadsheets, presentations, and databases. One good much of this is this can operate together with Microsoft Word or phrase.
This is one common consider that can dramatically slow down your Computer system. So you must need to be able to a spyware removal tool and antivirus program to scan and remove out all the malware with your PC, with regard to spyware, adware, Trojans, Keyloggers, malicious tracking cookies, browser hijackers, worms, phishing websites, Rootkits, bots, malicious BHOs, dialers and a lot more spyware perils. A powerful and advanced spyware removal can also thoroughly and efficiently scans, removes and blocks a myriad of malware hidden in your hard drive and efficiently make your personal computer run lightning fast.
All in all, these boot issues can be solved instantly. If this particular set of solutions didn't help, you may have to reinstall Your windows program. If you suspect a hardware issue is causing boot problems, getting time to upgrade.
1 note
·
View note
Text
A Beginner's Guide to buy keylogger

Should You Use Keyloggers on Employee Computers?
Services are continuously analyzing devices that are offered to aid enhance efficiency and also network safety throughout their company. Consulting with experts to assist align on items of software as well as hardware that will certainly integrate to establish the most effective method is a procedure that must not be ignored. During this process, lots of businesses may end that keyloggers are an efficient tool to aid reach their organizational goals. Nevertheless, keyloggers bring forth lots of obstacles and concerns, and also there are numerous other choices readily available that will give more valuable understanding and use. In this post, we will evaluate the advantages and disadvantages of keyloggers, while advising alternatives to keyloggers that will enhance the productivity as well as safety of your company without the security and also personal privacy risks associated with logging specific keystrokes.
What is a Keylogger?
As the name recommends, keyloggers-- also referred to as keystroke loggers or keystroke surveillance devices-- are a sort of monitoring software or equipment that tape-records the actions of the computer system user by logging the numerous tricks and also switches that are continued the key-board. While keyloggers have reputable uses such as software/hardware screening, capturing keystroke characteristics data, and also corporate user activity monitoring, these devices are commonly made use of by threat stars to record passwords and various other delicate details that they can leverage in a strike. As the name suggests, keyloggers-- also known as keystroke loggers or keystroke monitoring tools-- are a sort of keeping track of software or hardware that tape-records the activities of the computer individual by logging the numerous tricks and switches that are continued the key-board. While keyloggers have legitimate usages such as software/hardware screening, catching keystroke dynamics data, and also corporate customer task surveillance, these tools are commonly utilized by risk stars to capture passwords and various other sensitive info that they can utilize in an attack.
A hardware-based keylogger is commonly an outer that can be installed according to the key-board's adapter. These keyloggers are made to have a harmless appearance, making it tough to detect by users that are not knowledgeable about the gadgets. An equipment keylogger may additionally be set up within the key-board itself, making detection much more challenging. To access the keystroke log the administrator of the keylogger will normally require access to the computers, making the access of keystroke logs far more tough to handle when compared to keylogger software. Unlike keylogger software application which can usually be found by anti-spyware software, keystroke logging equipment can only be intercepted by physically removing it from the target computer system. While this kind of keylogger is usually an outer, there have been other selections such as a proof-of-concept technique where the electromagnetic emissions of a wired keyboard have actually been caught wirelessly from approximately 66 feet away.
What Are buy keylogger Keyloggers Utilized For?
Although there are numerous genuine instances for using keyloggers, the innovation is more commonly understood for its use throughout the cyber-criminal abyss. Actually, 60% of phishing rip-offs had some form of keylogging modern technology, making keyloggers one of the most commonly utilized devices in malware strikes. Hazard actors will make use of keylogger programs to gather sensitive documents such as passwords, repayment info, and also directly recognizable info (PII). This info might be made use of to intensify an existing strike or make it possible for strikes from various other risk stars. High-security organizations such as those in the nationwide defense industry may check their staff members for indicators of expert threats with keyloggers. They can utilize a keylogger to discover anomalous actions such as a WPM tempo that much surpasses what is common (a possible sign of a malicious script implementing) or the existence of risky key words.
0 notes
Text
Como utilizar multipassword

Como utilizar multipassword software#
Como utilizar multipassword password#
10.14.x - 12.x.x)ġ Some of the listed capacity on a Flash storage device is used for formatting and other functions and thus is not available for data storage.
Como utilizar multipassword software#
Upon expiration of software license, USBtoCloud offers licensing options directly from ClevX®.Ĭompatible with: Windows® 11, 10, 8.1, macOS® (v. A 5-year license (upon activation) to USBtoCloud is included with every IKLP50 drive. Warranty/Support: Limited 5-year warranty, free technical support. Minimum System Requirements: Two (2) free consecutive drive letters required for use 3
Como utilizar multipassword password#
Use virtual keyboard to shield password entry from keyloggers and screenloggers.ġ6GB – 128GB: 145MB/s read, 115MB/s writeĬloud Services Supported Google Drive™, OneDrive (Microsoft), Amazon S3, Dropbox™, BoxĬompatibility: USB 3.0/USB 3.1/USB 3.2 Gen 1 Passphrases can be a numeric PIN, sentence with space characters, list of words, or even lyrics – from 10 to 64 characters long.Īutomatic Personal Cloud Backup: Access data stored on IronKey Locker+ 50 from your personal cloud storage.Īdditional Security Features: Reduce failed login attempts and frustration by enabling "eye" button to view the typed password. New Passphrase Mode: Select between Complex or Passphrase password mode. Multi-Password (Admin and User) Option with Complex/Passphrase Modes: Admin can reset a User password to restore User’s access to data. Hardware-encrypted USB Drive with XTS-AES Encryption: Safeguard important data with built-in protection against BadUSB & Brute Force attacks. Kingston IronKey Locker+ 50 Features and Specifications: Plus, all the software and security needed is already on the drive so no application installation required, and it works on both Windows® and macOS® so users can work from multiple systems. LP50 is easy for anyone to setup whether you use Google Drive™, OneDrive (Microsoft®), Amazon Cloud Drive, Dropbox™ or Box for your personal cloud storage. LP50 is designed for convenience with its small metal casing and built-in key loop, along with the optional feature of USBtoCloud (by ClevX®), users can take and access their data anywhere. But should a User password be forgotten the Admin password can be used to access the data on the drive or reset the User password. To reduce failed login attempts during password entry, the "eye" symbol can be enabled to reveal what has been typed. Complex mode allows for passwords from 6-16 characters using 3 out of 4 character sets, while new passphrase mode allows for a numeric PIN, sentence, or even a list of words from 10 to 64 characters long along with support for international characters. Kingston IronKey Locker+ 50 offers multi-password, Admin and User, option with Complex or Passphrase modes.

0 notes
Text
Gigabyte app center utility windows 10

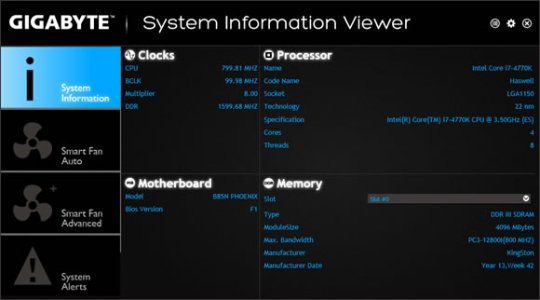
Close the wizard and perform a system reboot to allow changes to take effect. Read EULA (End User License Agreement) and agree to proceed with the installation process. Allow Windows to run the file (if necessary). Locate and double-click on the available setup file. Unzip the file and enter the newly-created directory. Save the downloadable package on an accessible location (such as your desktop). To install this package please do the following: Even though other OSes might be compatible as well, we do not recommend applying this release on platforms other than the ones specified. If it has been installed, updating may fix problems, add new functions, or expand existing ones. This package contains the files needed for installing the APP Center utility. Q-Flash Plus Update BIOS without Installing the CPU, Memory and Graphics Card Smart Fan 6 Features Multiple Temperature Sensors, Hybrid Fan Headers with FAN STOP RGB FUSION 2.0 Supports Addressable LED & RGB LED Strips High Quality Audio Capacitors and Audio Noise Guard with LED Trace Path Lighting USB 3.2 Gen1 Type-C for Fast and Versatile Connection Intel GbE LAN with cFosSpeed Internet Accelerator Software
Dual Ultra-Fast NVMe PCIe 4.0 /3.0 x4 M.2 Direct 6+2 Phases Digital VRM Solution with Low RDS(on) MOSFETs Dual Channel Non-ECC Unbuffered DDR4, 4 DIMMs Pegagfn.sys cmmon32.exe pavshookwow.dll ApCent.exe kausrtsk.exe viewmgr.exe safeboxservice.exe nordpass.exe suprasavingsservice64.exe c0b1016f-b7e5-46f0-b415-6bf9e55ab00d.dll crashplanservice.- Supports 11th and 10th Gen Intel Core Series Processors BMalwarebytes Anti-Malware detects and removes sleeping spyware, adware, Trojans, keyloggers, malware and trackers from your hard drive. A unique security risk rating indicates the likelihood of the process being potential spyware, malware or a Trojan. To help you analyze the ApCent.exe process on your computer, the following programs have proven to be helpful: ASecurity Task Manager displays all running Windows tasks, including embedded hidden processes, such as keyboard and browser monitoring or Autostart entries. This allows you to repair the operating system without losing data. Even for serious problems, rather than reinstalling Windows, you are better off repairing of your installation or, for Windows 8 and later versions, executing the 7DISM.exe /Online /Cleanup-image /Restorehealth command. Use the 6resmon command to identify the processes that are causing your problem. Should you experience an actual problem, try to recall the last thing you did, or the last thing you installed before the problem appeared for the first time. Always remember to perform periodic backups, or at least to set restore points. This means running a scan for malware, cleaning your hard drive using 1cleanmgr and 2sfc /scannow, 3uninstalling programs that you no longer need, checking for Autostart programs (using 4msconfig) and enabling Windows' 5Automatic Update. Therefore, please read below to decide for yourself whether the ApCent.exe on your computer is a Trojan that you should remove, or whether it is a file belonging to the Windows operating system or to a trusted application.Ĭlick to Run a Free Scan for ApCent.exe related errorsīest practices for resolving ApCent issuesĪ clean and tidy computer is the key requirement for avoiding problems with ApCent. Executable files may, in some cases, harm your computer. exe extension on a filename indicates an executable file. Gigabyte is currently headquartered in New Taipei City, Taiwan. The company was founded by Pei-Chen Yeh in 1986 and is currently listed at #17 in the Top Twenty Taiwanese Global Brands. Components manufactured by Gigabyte are used in desktops and laptops sold by Alienware, CybertronPC, Falcon Northwest, Origin, etc. Gigabyte is a Taiwanese corporation that manufactures and distributes computers and computer-related hardware products. APP Center currently supports the Microsoft Windows platform. APP Center also provides an easy way to access program updates, drivers, and other applications published by Gigabyte. The Gigabyte APP Center provides a portal to access all applications that are bundled and installed with Gigabyte hardware such as USB Blocker, Cloud Station, EasyTune, Live Update, etc. This application may be safely removed if not required through the Add/Remove Programs feature. The genuine ApCent.exe file is a software component of App Center by Gigabyte.ĪPP Center is a control panel for accessing Gigabyte applications.

1 note
·
View note
Text
6 Useful Benefits You Can Find At Free Pdf Readers
In a seasoned of business on the net you preferably should capture names and emails of men and women who either buy a person or which interested in your product. Specialists are encouraging known as list building. Most people's lists are built by any simple email capture form on their websites often giving away a free report or newsletter to entice men and women to subscribe of their list.
You might think it is best. pdf shaper crack think it is weak. Here's why. Web present a quick question when asking you to answer the "password reset" doubts. They ask you rrn your city of birth, college mascot, or favorite movie, etc. You answer these questions following start using the service.
Dr. Birbals: you must run scandisk first in thorough mode in order to check any problems in cash disk. in case the scan disk does perform properly in windows, then you can must run it in DOS option. If there is any problem, then scan disk will report relating to this. Moreover, you must also examine the result for bad sector in cash disk given that could be one for this reasons for all your problem. However, if 7 zip beta crack is reported fine by scan disk, then your needle of suspicion would go to motherboard of the computer. This you can have to get checked out of your hardware trader. Your problem is not to do with increasing the RAM hence increasing it to 128 MB won't actually solve your big problem.
Strong passwords should be the norm. Numerous people people do not take password selection to heart by leaving themselves there for the proper way that hackers use to compromise your data. You may laugh when you read that lots of people make use of the word password, as their account account. If you are one particular of those men and women that do use "password", I'm sorry, but keep learning. Another common one used is the series of numbers: 123456. xnview crack regarding sites do not require strong passwords will at least require six characters, so that's the reason for some to lazily pick the six number sequences.
The first and latest scam in the that shows you that obtain add an dislike button to your account. Users can like an article giving it a thumbs up though not a thumbs down if they don't deal with it. People see this email and think it is a great assumed. They download the attachment and end up compromising their account. Really seriously . just malware that will mess increase Facebook. Don't fall to do this one.
There is just about the way to obtain around this issue, use extended friendly characters. If you hold down the alt key, then press one additional numerals obtain one these weird characters with double dots on top or a symbol. But the keylogger still shows the character, but a way around could be to use Alt 0160. This extended character is often a space and hides if you ever that you used the Alt approach create keep in mind this. So they crackerpro will never be able to copy it even when they see it.
The most sensible thing is to always make a note of your passwords and update the list when you change them or add new password protected programs. Such programs can take quite a hard time; which might depend along at the difficulty of your password.
Occasionally, your WordPress permalinks get rushed by the cloning process, and you finish up opening a page on your website template. If that happens, simply change your permalink settings to an old setting, followed by change it away to a custom arranging. If this doesn't resolve the problem, likely messed the edit in step 5 above, in which means you will should try to work out what in class wrong, immediately after which it repeat steps 5 to 7.
0 notes
Text
Your Guide to Custodial and Non-Custodial Wallets
With a total net worth of over $2 trillion and Bitcoin being the 9th most valuable asset on the World list, cryptocurrencies form a part of the economy that can't go unnoticed. For beginners, figuring out how to maximise their gains through the diversity of coins flooding the market can be challenging. However, once you understand the technology comprising this digital currency and get a firm hold of all the industry jargon, crypto can offer you a sizable return.

Every crypto asset comes with its own set of risks, not to mention the high volatility, which can leave imprudent investors in chaos. So if you have decided to take a plunge and give crypto a go, you should first buy yourself a wallet.
We recommend investing in TTN, an up and coming peer-to-peer cryptocurrency that offers high transaction speed of 1 block per minute.

Why are cryptocurrency wallets essential?
When used with care, cryptocurrency wallets offer a better level of security and safety to your funds. Some providers also grant rewards and interest for staking crypto coins in their app to increase their wallet's usage. A good example is TTN.
Based on ownership you hold over a crypto wallet, it can be divided into two types as given below:-

Custodial Wallet
Definition: A custodial wallet provides you with the private keys which prove to the senders that you are the owner of the crypto in it. Here you have full authority over your wallet. Whenever a cryptocurrency transfer takes place, the private key is entered into the device. You can quickly type in your private key, which is a combination of 51 alphanumeric characters that appear incoherent to human eyes.
You are solely accountable for the safety of your private keys and thus your funds. On losing the key, you might be able to access them through your seed phrase. It is a combination of 12 or 24 words used to create private keys. However, if you end up losing your seed phase in any way, you are at a great loss. There are zero chances of retrieving your funds after that, as the wallet platform you use doesn't have access to any!

Advantages
1. Complete Ownership -You have complete authority over your funds. In case the wallet suffers from an attack or has any discrepancies in its functioning, you wouldn't lose any of your cryptos.
2. Less Vulnerable to Attackers -The private key is stored on the server of the platform of a non-custodial wallet. With a malicious attack, a person can grab hold of your funds. But, the possibility is low when you use a non-custodial wallet.
Always choose a platform that has off-line storage. It makes hacking your private keys nearly impossible.
Disadvantages
1. Requires Extreme Care - Losing your seed phrase even by mistake will leave you empty-handed. Further, for the improved safety of your funds, you'll need a hardware wallet. It is a device that stores the password in encrypted form and is used to login offline.
2. No chances of Retrieval - Not using a hardware wallet and typing in the private keys every time makes you prone to security risks. Keylogger software can be used to trace your keystrokes by hackers. Again, it makes your funds vulnerable to malicious software.
If you are using a software wallet, keep in mind to download it only from the official site with https: in the URL and padlock icon. Both make it a secured site.

Non-Custodial
Definition -You have partial ownership of your cryptocurrencies as your data is hosted on the server of a third-party site when you use a non-custodial wallet. A simple example of a non-custodial type is the wallet you get on an Titan Exchange website. The exchange platform holds your private keys.
You simply make changes in your account after logging in to the trading site.
Advantages
1. Seamless Transactions - Most of the non-custodial wallets are linked to exchanges. This allows you to trade seamlessly.
2. No worrying about private keys - As the private key to your account is stored on the platform's database, you don't have to take care of them.
3. Ease of Retrieval - Due to any reason, if you forget your account's password, customer care will come to your aid and help you with its retrieval. Thus, you wouldn't lose your funds in any case.
Disadvantages
1. Increased Vulnerability- An entire pool of hackers often target exchange platforms, and many-a-time are successful in crashing these sites. Your private key being in their custody makes your funds too vulnerable to such attacks.
2. Discontinuation of Services - On not completing KYC or having insufficient funds, some platforms do not allow you to use their services.
Needless to say, with 75 million cryptocurrency wallet users active all over the world, the crypto economy is going to swell even more in the coming future. According to the data on Statista, the crypto wallet users increased by 190% between 2018 and 2020. Lack of awareness about protecting their wallets from malicious attacks can lead many to lose their crypto assets.
We hope the above guide will help you weigh your options and choose a wallet that serves you well.
Whether you are a mobile user or find your laptop a better means for transacting crypto, you can keep all your coins safe with our Titan Multi Crypto wallet. It will store all your cryptocurrencies in one place and run effortlessly without any glitches.
1 note
·
View note
Text
Passwords
001 Many sites on the internet require passwords. Although they seem a nuisance, they protect you. Consider them like a key to a door.
002 Why bother with passwords?
(i) Financial Management
For most people this means online banking. If you use a weak password it is likely it will eventually get hacked. Needless to say this could result in you losing money.
(ii) Auction Sites
If someone hacked your account they could make binding bids or buy things in your name.
(iii) Stock Trading
This is like (i) plus (ii). Someone could buy or sell stock or have stock transferred.
(iv) Social Media
Hacked social media accounts can be used to post compromising messages that could embarrass or defame somebody, be used for harassment, or to build up a picture of who you are and everyone you know. This could result in a visit from the police. Social media is also very useful for hackers for enabling identity theft.
(v) Shops
Hacking one of your shopping accounts (e.g. Amazon) would only be an issue if you have a “stored” payment method such as credit card details.
If you discover that your payment information was used to ship unexpected goods to an unknown location, it’s clear that someone has hacked your account.
(vi) Gambling
A hacker could generate debts on your behalf.
003 How To Design a Good Password
The important things when designing a password (in order) are make it -
(i) Memorable,
(ii) Long – the longer the better (at least 12 characters),
(iii) Complex,
(iv) Different for different sites.
004 The Core of the Password
First of all create a “core” password with a string of letters. Three ways ways of doing this include -
(i) Initial Letters
Open your favourite book. Go to a memorable page e.g. your birthday. Read the first sentence. For me this would be “The Age of Reason” by Sartre. My birthday is on the 23rd. The first sentence of the first paragraph on page 23 is “Boris bitterly regretted never having been there, he would certainly go if it reopened.”
This makes bbrnhbthwcgiir – 14 characters. If I forget it I just have to go to my favourite book.
(ii) Relevant but Not Guessable Words
This could be a street name, hill names, school name, stream name(s), car. Don’t use words relevant to you or close family. However, you could use a relative’s street name etc. Hill or mountain names, especially if non-English, are good. Similarly, the name of your school is bad because a hacker could probably get it from Facebook. So use a relative’s school instead. The advice regarding streams/rivers is the same as for hills/mountains. If the resulting password is too short add something relevant.
So, examples from these could be -
springwoodbank (where my parents-in-law lived)
anteallach (a Scottish mmountain)
bluemountainsgrammar (a school in Australia)
severnriver (a river far away)
deloreanbelfast (not my car!)
or -
Look out of the window - flowerwheelbarrowbinhusband
Look at your wall - picturetelevisionblue
Look at your spouse - greynoseartist
(iii) A Silly Phrase
Examples could be -
weneedanewcomputer
mustremembermilk
quickbrowndogs
lillylikeschocolate
myneighbourisnoisy
dollypartonhasbigboobies
These are long and memorable.
005 Make The Password More Secure
The core password generated as above satisfies the first two criteria – long and memorable. You could use it as it is. However, to make it even better we can add complexity. There are three easy ways of doing it – add special characters and/or numbers and use mixed case. But where to put the number and special characters? The easiest is between each word (ignoring example (iii) above) but the better way would be to place it in random places. The downside here is that random places make it less memorable.
(i) Special characters such as !, £, $, _
flower_wheelbarrowbinhusband
bbrnh£bthwcgiir
springwood!bank
we_need£a$new_computer
Bear in mind that some sites only allow certain special characters.
(ii) Numbers
The question here is how to decide what numbers to use. Anything relevant to you or your close family is bad because it is available online from various sources (e.g. Facebook, Linkedin, Ancestry). Of course 123456 is bad. You could use something random but then it won’t be so easily memorable. Ignoring close family, you could use the birth date of, say, your mother (or even better, your grandmother). For me that would be 07071936. You could use one or more of these numbers -
flower07wheelbarrow07bin19husband35
bb07rnhb07thw19cgiir35
07spring07woodbank1935
w07eneedane07wco19mput35er
(iii) Mix upper and lowercase letters
FlowerwheelbarrowbinhusbanD
bbrnhbthwcGiir
SpringWoodBank
wEnEEdanEwcomputEer
(iv) To make an extremely secure password, use all three complexity methods -
Flower_07wheelbarrow07bin19husbanD35
bb07rnh£b07thw19cGiir35
07Spring07Wood!Bank1935
w_07EnEEd£a$nE07w__co19mput35Er
006 Create Different Passwords For Different Websites
You could use the same password for each website but if that gets hacked it would mean the hacker would have access to all of your accounts online. So, how to make it unique for each website? Here are some suggestions.
(i) Add the name of the site to your password
Flower_07wheelbarrow07bin19husbanD35amazon
bb07rnh£b07thw19cGiir35ebay
07Spring07Wood!Bank1935twitter
w_07EnEEd£a$nE07w__co19mput35Erfineartamerica
(ii) Add an acronym relevant to the site
Flower_07wheelbarrow07bin19husbanD35azn
bb07rnh£b07thw19cGiir35eb
07Spring07Wood!Bank1935twt
w_07EnEEd£a$nE07w__co19mput35Erfaa
(iii) Add numbers
How to choose a number relevant to the site? An easy way is the length of the name of the site -
Amazon = 6
Ebay = 4
Twitter = 7
Fineartamerica = 14
To make it harder for the hacker “pad” it to three digits; -
Amazon = 006
Ebay = 004
Twitter = 007
Finartamerica = 012
So we get -
Flower_07wheelbarrow07bin19husbanD35006
bb07rnh£b07thw19cGiir35004
07Spring07Wood!Bank1935007
w_07EnEEd£a$nE07w__co19mput35Er012
007 Storing Passwords
Generally speaking, storing passwords anywhere is a bad idea but if you really can’t remember your passwords, here is some advice.
(i) Write Them Down
Writing your passwords on a piece of paper and sticking it to your screen or under your keyboard is a bad idea.
So find that favourite book again and your favourite page and slip your password note in there. What happens if a burgler finds it? Burglars rarely, if ever, are interested in passwords – they are looking for cash or small high value items to sell on quickly.
If you have accepted the advice above you have a core password used for all sites. For each site you have added a three-digit number at the end. This means all you have to do is store your core password because you can work out which password to use for each site but others would have a hard time figuring it out.
For example, instead of storing
Flower_07wheelbarrow07bin19husbanD35006
use
Flower_07wheelbarrow07bin19husbanD35
Even if a burglar/hacker tries to use the password it will not work anywhere.
(ii) Password Manager
A password manager is a computer program that allows users to store, generate and manage their passwords for local applications and online services.
Types of password managers include:
locally installed software applications
online services accessed through website portals
locally accessed hardware devices that serve as keys
Password managers typically require a user to generate and remember a master password to unlock the password manager. Many password managers offer additional services such as storage of credit card and frequent flier information.
Password managers come and go but the popular ones in 2021 are LastPass, myki, LogmeOnce, Norton and bitwarden
The two downsides of using a password manager are that you usually have to pay for it and, of course, if the password manager gets hacked your passwords are exposed.
(iii) Security Key
A security key looks a bit like a USB pen. It allows you to securely log into your accounts without having to key in passwords. They usually just plug into a USB port.
There are various security keys available so its worth shopping around and comparing them. For example scan.co.uk sells the Hypersecu FIDO Titanium Pro (works in Windows, Apple devices and Android) which currently does well in reviews.
In addition to managing passwords a security key can combat real-time attacks such as man-in-the-middle (MITM), prevent phishing, make keylogging impossible and protect PINs from brute force attacks.
The problem is that they can be difficult to set up.
008 How To get Hacked (Bad Security Online)
(i) Use Number Substitutions in Passwords
Common substitutions are -
a = @
s = $
o = 0
e = 3
i /l = 1
So, ”myamazonassword” becomes “my@m@z0nA$$w0rd”
Hackers are aware of this so number substitution is a bad idea.
Note – this is substitution not addition (discussed above).
(ii) Use Personal Information in Passwords
Examples are -
Your birthday,
Close family names (sons, daughters),
Pet name,
Your address.
(iii) Repeating Characters in Passwords
1234567
aaaaaaaaa
abcdefg
abcabcabc
(iv) Same Password for All Sites
Someone who culls your Facebook or Twitter password in a phishing exploit could, for example, access your bank account. Reusing passwords for email, banking, and social media accounts can lead to identity theft. Two recent breaches revealed a password reuse rate of 31% among victims.
(v) Auto Sign In
Do not allow your computer to automatically sign into sites on boot-up
(vi) “remember me”, Automatic sign-in option
Do not use “remember me” or Automatic sign-in option which is available on some web sites.
(vii) Alien Computers
Do not enter passwords on a computer you don’t control, such as a friend’s computer, because you don’t know what spyware or keyloggers might be on that machine.
(viii) Open WiFi
Do not access password-protected accounts over open WiFi networks or any other network you don’t trust unless the site is secured via HTTPS. Use a Virtual Private Network (VPN) if you travel a lot.
(ix) Keyboard Combinations in Passwords
Avoid consecutive keyboard combinations such as qwerty or asdfg.
(x) Security Questions
The names of spouses, kids, other relatives, or pets, can be deduced with a little research. When you click the “forgot password” link within a webmail service or other site you are often asked to answer a question or series of questions. The answers can often be found on your social media profile. This is how Sarah Palin’s Yahoo account was hacked.
(xi) Social engineering
This is an elaborate type of lying. An alternative to traditional hacking, it is the act of manipulating others into performing certain actions or divulging confidential information.
1 note
·
View note
Text
Easy Updating Of Computer Drivers
First and foremost - you are going to begin to save your settings for that theme your using. Profit Weaver Pro so I log in to plan settings and click over the Save/Restore tab. I save all of my weaver theme settings to my desktop.
One weakness any password can have is you would like to slips from a keylogger program on your computer. Keyloggers record all the keystrokes that an end user makes and regardless another thing you help password, if they can see key strokes, they have got you. And much easier than believe to complete stealth create.
Most among the different forms of list building are common knowledge for anybody who participates advertising online. The usual way as stated above in order to use give away a free eBook, report or newsletter to that subscribe to your own list.
cyber link you cam deluxe has its benefits as all of the passwords are stored and managed that. They are on your computer, discussing document end up being protected. This may be a great benefit for individuals with multiple e-mail accounts, social media marketing accounts, banking accounts, and many more. It is easy to update all the information. Do not have in order to a notebook a piece of paper to quickly write around the information it is advisable to remember. This paper often gets lost, and that's how crackerpro you end up in scenario where you require a password christmas cracker.
Since I (our fictitious hacker Joe) has nothing better strive and do with my time, I'll go ahead and setting up some fake social media profiles. Here, let me go in your blog and view out who your friends are and who you trust.
The books tell every person about designing a fancy personal grab bag almost all of the goodies you can think having to do with. I tend to don't agree. Going through the genuine thing beats the hell your own reading with this. stardock fences have a lightly packed, easy to keep bag ready at all times.
There a few software tools and hardware devices that can help you secure you passwords. Let me write about some with the in probably ? article. For now, use the best passwords you can and all of them strong.
0 notes
Text
What Is Malware And also What Does It Mean
Malware (short for MALicious SOFTWARE PROGRAM) is a famous risk in our progressively connected globe. Simply put, malware is any program produced with the purpose of causing damage to a computer system or jeopardizing the security of a computer system. Basically all the "net nasties" you've become aware of come under the wide category of malware. These include viruses, worms, Trojans, keylogger, spyware, adware. Even SPAM could be taken into consideration connected with malware, though not malware itself, given that it can be the methods by which cyberpunks obtain those other kinds of programs onto your system.
Viruses and worms operate in the computer system world a lot like they do in the real life because they replicate themselves and pass from one carrier to one more (be that a computer system or a person, depending on which kind you're speaking about). They can either spread out by themselves, or after the customer takes some pre-determined activity like opening an email, running a program, and so on. It ends up that the majority of these programs are contacted make the most of Microsoft Windows Operating system as opposed to Macs or Unix/Linux systems. However that has a lot to do with the reality that there are a lot more Windows customers than other kinds of running systems.
see more obtain their name from the renowned story of the Trojan Equine and run in a comparable fashion. Trojans get onto your system and conceal there by seeming something else, a relatively safe file that when run, includes a "little extra something" that the customer most definitely isn't anticipating. Completion result varies depending on what's "inside the steed", to continue the analogy. It could be a program that deletes every little thing on your C: drive, it could mount an additional program or transform an existing program. This is how spyware is passed along much of the moment. As an example, you download a totally free screensaver, mount it as well as at the very same time, likewise install a program that monitors your keystrokes and sends that info back to a 3rd party by means of the net.
Spyware and adware are among the biggest threats now. They also create the most significant headaches for security professionals given that a lot of computer issues are currently located to be triggered by spyware. Spyware makers are usually inspired by profit instead than purely malicious needs as though the situation with a virus/worm creator. Spyware and adware are typically made use of to regulate a computer system and drive the individual to websites which the maker will make money from or for displaying advertising by means of popups, popunders, or other ways.
Spyware is generally set up as part of an additional software without the customer's permission, or occasionally with their authorization though they might not recognized it. Oftentimes, this implied approval is hidden in the End User Certificate Agreement (EULA) which the user have to accept prior to mounting the program. By not reviewing or recognizing the terms contained in the EULA, the customer could be accidentally accepting have actually spyware set up. When set up, this might end up being a method for various other spyware programs to also finish up on that particular computer system.
Malware definitely is a danger that you must know, but there are procedures you can require to decrease the possibilities your computer system will certainly be infected. There are three crucial items you ought to have for good computer protection. First, a great firewall program, either a software program or hardware firewall program will certainly do. Second, an anti-virus program. Third, an anti-spyware program or spyware eliminator. Preferably with these last 2 items, the programs will certainly run on your computer from start-up to closure, will certainly check your programs as they launch, and will automatically upgrade themselves with the most recent hazard data source. This way, you can rest guaranteed your computer system is updated as well as not have to spend unneeded time handling your computer system's safety.
https://www.youtube.com/watch?v=RVEr8Fl2y7Y
1 note
·
View note
Text
Credit card numbers generator
Several oracle applications use the account generator to create mixtures for the accounting flexfield. Users are anticipated to chorus from partaking in intentionally wasteful practices equivalent to sending chainletters through electronic mail, printing pointless listings, printing multiple copies of information, performing pointless computations, or unnecessarily holding public terminals or dial-up telephone traces for lengthy durations of time when others are ready for these sources.
The file might be valid and contain credentials for created users, so every user might be in separate tenant and have the username, tenant_name, password and roles. In the event you're on any of the next 2015 or 2014 media and entertainment (m&e) digital content material creation (dcc) subscription that entitles you to the character generator profit, you should utilize any of the character generator paid offerings and obtain your personalized characters offering you've gotten the required quantity of cloud credits.
As to be used by a enterprise to store files, the 60 day lasts obtain deletion may make it impractical to store information for the lengthy-time period (except you bear in mind to periodically obtain the file) however it's very helpful for companies who must share information that are too massive for electronic mail or different information transfer methods.
As a scholar, you may have limitless entry to the character generator paid choices. 21. If there are necessary files in your computer, and it can be accessed by others, verify if there are hardware keyloggers( e.G. Wireless keyboard sniffer ), software program keyloggers and hidden cameras whenever you really feel it's necessary. This program generates password for each fortnite account generator you want from hostname, username and one international password (passkey, master password, skeleton key).
If you don't have enough cloud credit, it's essential to buy cloud credits before you can obtain your personalized 3d character. Any attempt to bypass system security, guess different passwords, or in any method gain unauthorized access to native or network sources is forbidden. If your severe about nike account creation in bulk you`ll love this product you can create 300 accounts over 12 hours and 600 over 24 hours with either usa or uk numbers.
1 note
·
View note
Text
THIS 2022, LEARN EVERYTHING THERE IS TO KNOW ABOUT KEYBOARD LOGGING.
A keyboard logging a program that records what a user types and how they interact with a computer system. Employers commonly utilize keyloggers to keep a close eye on their employees' activities by logging their total keystrokes. The keystroke recordings are saved in a cloud-based system that may be downloaded at any time by an authorized employer.
The user would be unaware regarding a tracking device running in the background is crucial. If you think it's creepy, consider this: every firm faces the prospect of Insider threats and other nefarious behaviors. Think like an employer, and you'll see the advantages.
WHAT ARE THE BENEFITS OF USING A KEYSTROKE TRACKER?
As an employee, you may believe that your bosses are violating your privacy and that they don't trust you with the tasks you've given. Unless you have a history of nasty behavior, believe me when I say it's nothing like that.
Aside from that, keystroke supervision used to manage and maintain the firm's overall productivity & to detect unproductive or lazy staff.
After all, your employers pay you for them it is essential to monitor your performance without invading your personal space.
With cloud-based productivity tracking tools, a keyboard logging used by parents to keep track of their children's online and offline activity. Because the internet may be cruel to them at times. Kids are gullible and can easily duped by internet predators and bullies. The primary concern is to safeguard the online presence, privacy, and data of minors.
DO YOU WANT TO KNOW HOW A KEYSTROKE TRACKER WORKS?

A keystroke tracker is simple to install on any machine. Both the employers and the IT department have access to the employees' systems and can monitor their activities.
Upper management can request a report from the IT department any time. The person in charge of the entire logging details can retrieve all of the data.
NOW, LET'S DISCUSS THE DIFFERENT TYPES OF KEYLOGGERS-
Keyloggers divided into two categories.
1. KEYLOGGERS IN HARDWARE:
As the name implies, it is an external device that does not require installation. Hardware keyloggers are self-contained and cannot be detected or uninstalled by staff using scanners or tools. It allows you to keep track of multiple systems.
It's impossible to get rid of something you can't see.
2. SOFTWARE KEYLOGGERS:
As the name implies, this is an internal utility that requires the installation to function invisibly. It can only track one device because installed on one device. Scanners, on the other hand, can detect software keyloggers.
THE BENEFITS OF KEYLOGGER TRACKERS -

Invisibility-
It operates in the background, undetected. Employees won't be able to find it either in the task manager or the taskbar. It means they won't be able to change anything.
Simplified tracking-
It made employee monitoring easier by simplifying tracking. Employers must create a secure password to enable the invisible mode and allow the keyboard tracker to work quietly.
Screenshot capturing-
Screenshots monitoring are taken through the keylogger from time to time to obtain information about screen activity. Employee screenshots are viewed through an employer to learn about their work performance, internet usage, most used programs, websites, and internet history, among other things.
THE MOST COMMONLY USED KEYLOGGER TRACKERS ARE:
EmpMonitor
Hubstaff
KidLogger (For parents)
Black Box Express
The most common tools are EmpMonitor and Hubstaff, which offer functionality such as providing-
A detailed report of productivity of all the employees
Information regarding productive and unproductive employees
Screenshots Monitoring
Internet usage report
Detailed timesheet for attendance
Real-time access
WRAPPING IT ALL UP
We're all aware of and dealing with the post-pandemic situation, and many of us are working from home for safety reasons, but employers' concerns about productivity tracking are genuine. Employees may take advantage of the remote working culture and work less diligently, that is counterproductive to the organization's aims. Many companies have installed a keyboard logging 9on their employees' computers to keep track of their work. Software like EmpMonitor and Hubstaff provide you with a comprehensive overview of each employee.
Furthermore, if employees are completely aware that their work is constantly observed, they will perform better and be more cautious in everything they do.
0 notes
Text
KeyLogger - Part Three
vimeo
I’ve got my keylogger evading Windows Defender now which brings me onto the dropper stage next- developing the program that will load an encrypted version of the keylogger into memory, decrypt it and save it to the user’s startup directory. I’m unsure how this will work combined with this method of evasion but I’ll know soon enough!
I did this by performing a code signing attack using a tool called SigPirate (https://github.com/xorrior/Random-CSharpTools/tree/master/SigPirate)

SigPirate will ‘Clone Authenticode or Catalog signatures from one binary to an unsigned binary’. In my case, the binary from which I’m cloning the signature is getting the signature from a cat file, a file that contains a collection of digital signatures for various files and is cryptographically signed (https://docs.microsoft.com/en-us/windows-hardware/drivers/install/catalog-files#:~:text=A%20digitally%2Dsigned%20catalog%20file,is%20included%20in%20the%20collection.)
Code signing attacks are effective as WIndows Defender will not perform as many checks on applications that are deemed to have a valid signature- this is why stealing a signature from a Microsoft program is a good idea. You can also generate your own signature; this requires the user to choose to trust the program and thus isn’t as stealthy.
In addition to this, I also took measures to prevent a console window appearing upon execution. This simply requires the addition of one function right at the top of the main function:
ShowWindow(GetConsoleWindow(), SW_HIDE);
This simply sets the state of the console window to hidden.
#malware#red team#cyber security#tech#IT#offensive security#code signing#windows#windows defender#sigpirate#C++#win32
0 notes