#richardflow
Explore tagged Tumblr posts
Photo

Retrouvez @richard.pop.officiel chez @la_saauuce Le samedi 29 octobre 2022 à 14h pour un workshop stage de Popping #richardpop #richardflow #takamov #art #dance #danse #marseille #lyon #france #french #southpopper #marseilleconnexion #f2d #leflowdud #lecollectifsouthpopper #lafab #lafarbriqueapopper #popping #hiphop #marseillais #lyonnais #lyonnaise (à Cagnes-sur-Mer) https://www.instagram.com/p/CkRKWiYL2KK/?igshid=NGJjMDIxMWI=
#richardpop#richardflow#takamov#art#dance#danse#marseille#lyon#france#french#southpopper#marseilleconnexion#f2d#leflowdud#lecollectifsouthpopper#lafab#lafarbriqueapopper#popping#hiphop#marseillais#lyonnais#lyonnaise
2 notes
·
View notes
Text
BUFFer Richardflow
After the quite confusing lecture, @caff and tutors offered to go over a more digestible version of buffer overflow, with a specific focus on what we needed to know for the course.
https://www.openlearning.com/courses/securityengineering19t2/cohorts/classof2019unswstudents/blog/lecture090719bufferoverflowscontent/

What I learnt
Buffer overflows occur, because stacks grow UPwards while buffers (arrays) grow downwards!
Whenever a user is allowed to input as much as they like (taking control of the program through a keyboard interrupt), there is danger. Especially with buffers, a vulnerability is buffer overflow.
In particular, for C, the function gets() is EXTREMELY VULNERABLE. In fact, it’s SO BAD that the manpage for gets() literally states: DO NOT USE THIS FUNCTION.
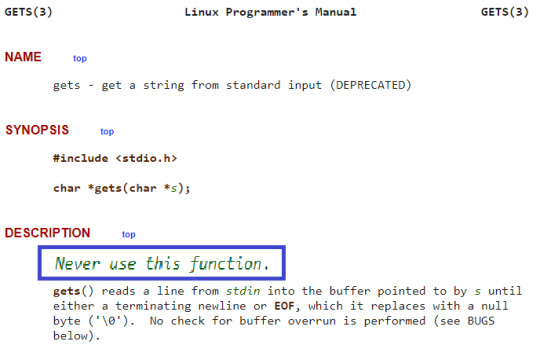
Note: scanf() is also vulnerable
The vulnerability occurs with input when you can't specify a length of input. When you don’t restrict a user, they are able to enter as long of a string as they would like, and hence overflow your buffer.
Since this is all stored on the stack, for functions they are vulnerable to overwriting the return address. This is a huge problem because of the nature that data is MIXED WITH control. By being able to overwrite the return address, you are able to direct it to a piece of code that you have control over and do even more malicious things :OOO
Protection
In modern languages we have some form of protection between the data and the return address. In particular canaries exist to be able to detect if someone is extending beyond the data. It acts like a tripwire, where once passed it can cut off the execution and prevent further damage. This is however simply protecting against the return address being overwritten, and may not save your bad practices.
Moreover with bad practices, since buffer overflow is such an “old” vulnerability, it’s not being taught in beginner programming courses. So beginners are encouraged to use these easy to remember gets() functions which are vulnerable!!!!11 We definitely should be pushing for safer coding practices and better development early on - otherwise issues extend into a programmer’s career.
How to tell if a buffer is vulnerable (blind)
We simply enter a loooooooooooooong string of say, ‘a’. Since we know the ASCII code for this and where it should reasonably appear in memory, we enter it and wait for it to SEGFAULT.
Once it has segfault, we know that we’ve hit the return address.
Generally it will return 76776767676.
Why are they still an issue?
There doesn’t be a real concensus on the matter, perhaps because it’s not being taught thoroughly so it just spreads with programs of extreme vulnerabilities. It may be that because of how convenient it is to address the stack using pointer arithmetic, that buffers are laid out that way. Since buffers grow downwards, the computer simply assigns it a memory chunk, has the base pointer of the array on the lower address, and it just needs to do +1 or +2 to access specified points in memory.
0 notes