#sixteen-digit set up network
Text
My EDC for Work
I mostly work remote now, but there's still some days that see me head back into the office. My EDC tends to vary depending on what's on my schedule.
Constants:
a Google Pixel 4XL w/ 128 GB in storage space. Basic comms, mobile file storage, music player, notes.
a Flipper Zero module, which is attached to my keychain and allows me to wipe and clone office-related RFID tags. It saves me on having to walk down to the locked and secured actual cloning machine, with Management having needed a while to come around to my using it. I also use it to control our conference room's projector, seeing as the actual remote is always misplaced. It lets me into my office and allows me to spook my non-tech-savvy EV-using colleagues seeing as Toyota doesn't individualize keyfob NFC signals. I also use it to control our garage door and to head inside the apartment. Oh, and it's also my dedicated IR remote for the media center.
two SanDisk Compact UltraFlash USB drives at 128 GB apiece. One is my Ventoy drive and is crammed with every single OS the office needs, from Linux Mint for the Call Centre to Windows Server 2020, as used by the Art and Production teams, with several variations in-between and a few bootable utilities, such as GParted, Hiren's Boot CD, FreeNAS and Proxmox. Both of them are molded to my keychain using little Sugru putty hoops. The Executive pool being beyond all salvation, I also pack a hacked Windows 11 image file that I've modded to be just a little bit more flexible than the commonplace Tiny11 ISO that's accessible online. Allowing sixteen year-old computers running on spinning rust to function off of a modern operating system has at least allowed us to acclimate the older ends of the Accounting department to modern standards. Unlike the actual Tiny11 ISO, I've kept the authentication suite because y'can't really run homebrew Windows images in an office setting legally if the resulting installation can't phone home...
Admin Days:
my Razer Blade 14 laptop and its associated dongles, running off of Windows 11 Pro. I edit campaign-related documents, review project files and sign off on our dealers having fully-assembled digital care packages packed with everything they'll need to get their sales off the ground. I also confirm the proper placement of documents that will need to be accessible for our Printing associates later. Everything IT takes place there, except for what relates to the Call Center. My laptop allows me to Term into our four server stacks if our checklists detect that something's missing, and to visually report on what needs to be transferred. To do all this, I also pack...
a TP-Link USB-C to RJ45 adapter, which is foldable and takes about zero space in my laptop's bag. It works like any other built-in hardline access point.
a no-name collapsible Cat5 Ethernet cable
a small bean bag. This one actually stays in-office, but I take it out from underneath my desk when I know I'll be watching the local network or mothering file transfers for more than twenty minutes. I am not spending half-an-hour standing up in the hot aisle, no sir.
Call Centre Admin Days:
my 512 GB Steam Deck. It's a couch gaming platform at home and a Linux Terming station at work. Going Linux-to-Linux is much more intuitive for me than loading Windows' Linux tools, seeing as it gives me a complete GUI I can use to guide less computer-savvy call agents through common procedures. It virtualizes a barebones-basic Linux Mint install that I can boot up and peer through if some colleagues report weird bugs or VoIP-specific issues, and I can use it for remote takeovers if things get too complex and require that I actually dig in to fix an issue.
my Steelseries Arctis 9 headset and USB emitter. I'm technically obligated to use wired audio peripherals at work, but Management soon realized I had too many side-jobs to take care of at work to really make the use of anything wired practical on the long term. They're plugged in if I have to lend a hand and make a few calls, but typically operate wirelessly. Everyone at the office knows to ping me on 3CX if I'm working within range of my desk, and to text or message me if I'm not.
On-Site Implementation:
my Google Pixel Slate. This old croaker's really useful when I'm dealing with non-tech-savvy salespersons who need a walkthrough of a campaign's documents or who want a demo run of some of our VR and WebGL content offers. It's a decent notepad on its own, and it comes with its own dongles. It's the PC I'll use to access any dealer's infrastructure and confirm with their Sales Director and Financial Controller that everything's above-board and ready to go.
That last one is the least-frequent of my tasks, seeing as Management knows not to send a cripple halfway across the province on his own. They let me implement campaign materials and check for head offices' go-ahead only for local dealerships, some colleagues of Walt's are scattered across the province for the rest.
All of that sort of informs why I took the Brain Gremlin as a persona, as I'm technically able to crater the company that employs me if I so desired, and could do so during personal or business-related trips.
Failing that, I get to fuck around with our presenting hardware if I'm bored, I can wreak havoc with my fellow geeks' radio-powered desktop toys, and have been known to pull an April Fools on my boss by using my Flipper Zero to put his shelf-mounted radio receiver on his least-liked station without opening the door.
FAQ:
WHY U NO USE LINUX ON LAPPY?
Because Razer are incompetent buffoons that long ago made it clear they had no vested interest in supporting the use of Open Source operating systems, and who made it a requirement to use Windows Update in order to get absolutely anything to work on the Razer Blade 14.
If it's any consolation, I use WSL to run Kali Linux on top of my Windows 11 install on my laptop. The way it's set up, you'd swear it's just a productivity and light gaming machine up until I mouse over to and click on a blank spot in the upper border. Kali's own GUI then drops down.
As to why I'd want to attack or breach my own employer's resources? Having an in-house pen-tester is a lot cheaper in this economy.
4 notes
·
View notes
Text
Sonic the Oz-Hog Act 8/12: Journey's End!
Sonic Universe issue 16
AU Publication Date: 6th August 2010
Price: $6.50

(Alternate title: 'A Farewell to Khans!'.)
Sixteen. Six. Teen. Siiiiiiixteeeeen. A number by all rights like any other, yet harbors more than a few connotations in life. Songs written and movies made have abounded over the decades in dedication to this number. It can mark exciting new beginnings, a (at least theoretically) responsible coming of age, a formal debut ready to tackle the more "mature" world of driving cars and leaving school in favour of the local workforce. Or maybe not. The author of these posts can't remember their sixteenth birthday beyond being pretty sure it happened, it rained, and there was a new Transformers action figure involved.
But when it came to Aussies following their favourite hedgehog's monthly tri-coloured triumphs, sixteen marked a bitter end.
In comparison to the turmoil of 2010's political sphere, Sonic and his freedom fighting buddies' year-long battle against the Iron Dominion's wrath was a cakewalk. Having swept to power in November 2007 despite the best efforts of conservative media and racist fake pamphlets, the time had come for Kevin Rudd to resign. Labor's three year tenure of poll-topping high highs and scandalous low lows painted a divisive picture, and with the prospect of losing power on the back of a fatal home insulation program and increased taxes for mining non-renewables, Julia Gillard stepped up unopposed to succeed him on 24th June. Rudd agreed on 6th August to stay onboard for support, and within two weeks of this issue's publication, a federal election saw Gillard narrowly retain her mantle as Australia's first female Prime Minister.
Music lovers thrummed away to manufactured relationship angst of Eminem and Rihanna's collaboration Love the Way You Lie, which was halfway through its six week domination of the billboard charts. Christopher Nolan's brain-bender Inception had enjoyed its own three weeks leading the local box office, until Will Ferrell and Mark Wahlberg briefly blasted their way to the top in The Other Guys.
The glory days of analogue morning toon-tainment for kids were by this point faded memories. Having half an hour sliced off its slot beginning New Year's Day 2010, Toasted TV limped itself along offering viewers that day repeats of Huntik: Secrets & Seekers and Dinosaur King. The product of networks pushing for breakfast news programs and set top boxes becoming more prevalent (i.e. affordable) meant the future of children's television was well on its way to being all digital. Channel Seven's subsidiary 7TWO served up repeats of Avenger Penguins, Digimon Data Squad, Handy Manny and Power Rangers Jungle Fury. Not to be outclassed, Channel Nine's newly-minted 9GO! kicked off the day with new Out of Jimmy's Head before its own repeat cavalcade of Class of 3000, Chowder, Legion of Super Heroes, Ben 10, The Flintstones and The Jetsons.
Another far cry from the days of yore were fan reviews. Forums, groups and pages come and go. The regulars over at Sonic Stadium all but ignored the issue and instead focused on whether Mighty and Ray would get their own SegaSonic Arcade adaptation, while gushing over the impending Tails Adventure arc. Sonic HQ's once juggernaut now dustbowl Knothole Village had little to say beyond base pleasantries, as did PorpoiseMuffins' Saturday Morning Sonic message board.
For those hoping to dig deep into the comic proper, Ian Flynn's forum truly put the "King" in "BumbleKing". By that point in its life a thriving superpower, after 5 days and over 15 pages of speculation, residents of Archie Sonic's biggest watering hole considered it "without a doubt my favorite of the arc. It's mostly expostition with more or less no action but what exposition!" The good times rolled with "Good wrap-up to this arc in an arc. I enjoyed it. I liked Espio's backstory; thought it was handled well." and "I've said it before I'll say it again Ian gets Sonic's personality so right my favorite line has to be "'Careful'? So many foreign words today!" why cant SEGA write him like that.". Forum goers were excited to share their future speculations, notably the prospect of one character being the first in a series which, like Dimitri being the latest in a line of Enerjaks, began life as a fan theory shared on message boards during the late-90's.
Yet while fandom faces and places can change as time marches on, attitudes remain engrained. Even if they've never seen the character or read a comic, some people can (and will) criticize them, ranging from "not being accurate to other source material" or that incredibly tired buzzword of dismissing the series as "weird". When pressed to consider the extensive laundry list of Archie Sonic material going under the hammer of fickle fans, it's tough topping the decades of derision aimed at Mobius' own cybernetic simian, Monkey Khan.
The amalgamation of late writer/artist Frank Strom's admiration for Chinese literature hero Sun Wukong, Japanese actors in rubber monster suits, and 1970's Hong Kong martial art films, Khan found himself shackled among the swelling ranks of Geoffrey St. John, Nate Morgan and Mina Mongoose in the upper echelons of Archie Sonic's most reviled characters. Case in point, fans quickly booted up their modems as early as November 1997 to voice their displeasure online. Some remained optimistic, citing Khan "looks simply like a vessel for spouting chiche's and poor dialogue, but there's opportunity to make him more interesting (and more vital) to the story." Others took offence to the character's ancient roots, wondering if the coincidence "probably is, since this issue didn't seem very well thought out. If it was a reference, that would be the only excuse for the piece of Mass-Produced Crud".
As the years rolled on and Khan made a handful more cameos, this fan mentality never truly shook off. "I have come to NOT STAND Monkey Khan AND Frank Stroms writing and drawing skills…MK has ABSOLUTELY NOTHING TO DO WITH SONIC THE HEDGEHOG AND IF THE EDITOR HAD ANY SENSE HE'D FIRE STROM. The guy has done NOTHING to show that he can even write a Sonic story." readers openly whined. "it really ticks me off that Frank Strom's version of the Monkey King was so poor… in fact, I bet he hasn't heard of MK in his life, but rather, Dragon Ball. smirk. Frank Strom is probably the worst Archie-Sonic writer I've ever seen, with the possible exception of 75% of Mike Gallagher's works.". They compared Khan to the worst type of wish-fulfilment self-insert, and Strom himself often written into fanfics as a target of obsessive mockery. Even the efforts of Ian Flynn to flesh out his character during 2009-10 (complete with hatred lampshade on the first page of issue 203) came across mixed, further fueled at a time when Archie Comics openly baited fans into a staggeringly pointless shipping war.
Hm. Seeing how Khan, Geoffrey, Mina and Nate were frequently criticized for stealing the spotlights of Sonic, Antoine, Sally and Rotor respectively, maybe there's an alternate universe where someone capitalized of this and united them to strike out in their own team. It would certainly make for quite the fanfic. But enough digressing.
There's a bittersweet irony here. Locals who loathed Monkey Khan's exploits and hoped to see the back of him once and for all were about to get their wish. A World Under Constant Vigil marked the last appearance Khan would make in a starring role, one which in a fantastical coincidence was published exactly on Frank Strom's 46th birthday. Further blurring the lines between a true case of "Sixteen Khandles" and the Monkey's Paw myth, Sonic Universe issue 16 would ultimately be the final comic released at Australian retail.
After 17 years of constantly easily accessible comics, time was up. Issue 211 and Universe 14 were the last to be sold at retail for $5.50, a price increase from $4.95 which began with issue 198. The move to fancy new glossy paper, an arguably remarked improvement which brought the comic's quality closer in line with the free Bionicle, HeroScape, The Batman and Teen Titans centerpiece of 2005-6 meant coughing up another dollar. Was it this move to $6.50 a copy that made the bean counters at Gordon and Gotch drop the title? Were they too frustrated by enduring the excessive length of Iron Queen's tenure? Was it the moonlit kiss and chest stroking between Sally and Khan in issue 212 that broke the camel's back? Guess fans will never know, for when the writer of these posts questioned said distributors at the time, they responded curtly that both Sonic titles "have now ceased and are no longer in production". So much for that.
As anyone who's kept up with these will know, the story of Archie Sonic in Australia was far from being all over. It's hard to keep a good high speed hero down, and one day he shall come back. Yes, he shall come back. Until then, there must be no regrets, no tears, no anxieties. Just go forward in all your beliefs, and prove to Sonic that he is not mistaken in his.
Yet it would be a long, pained fifteen months before Aussies saw the blue blur triumphantly return to newsagent shelves.
#Sonic the Hedgehog#Sonic the Hedgehog Comics#Archie Sonic#Archie Comics#Sonic Universe#Ian Flynn#Tracy Yardley#Jim Amash#Jason Jensen#Teresa Davidson#Ben Hunzeker#Paul Kaminski#Mike Pellerito#Frank Strom#Monkey Khan#Comic Books#Australia#2010#Musings
0 notes
Text


Death Comes to Santa Fe by Amanda Allen (Santa Fe Revival Mystery #3)
Former New York darling turned amateur sleuth Madeline Vaughn-Alwin is once again thrown into a colourful yet deadly web of secrets, lies and soirees to die for!
It's the week of Fiesta in Santa Fe and Maddie is looking forward to enjoying the celebrations. But as 'Old Man Gloom' Zozobra goes up in flames, so too do Maddie's hopes for a carefree life . . . Human remains are found in the dying embers of Zozobra, and then Maddie and her dashing beau Dr David Cole find a body washed up in the arroyo at the edge of town.
Soon identified as Ricardo Montoya, a wealthy businessman and head of one of the most affluent families in Santa Fe . . . the plot starts to thicken. While his beautiful wife Catalina and her complicated children seem less than heartbroken at his untimely demise, and with many disgruntled locals crawling out of the woodwork, Maddie is surrounded by suspects.
With the celebrations of Fiesta continuing around them, Maddie and her 'Detection Posse' get busy infiltrating the best parties and hobnobbing with old and new faces - but can they bring the murderer to justice before they strike again?
Purchase Links
https://www.amazon.com/Death-Comes-Santa-Revival-Mystery-ebook/dp/B0BXPZ9C8P
https://www.amazon.co.uk/Death-Comes-Santa-Revival-Mystery-ebook/dp/B0BXPZ9C8P
My Review:
This is the third novels in this entertaining series, and it can be read as a stand-alone as there’s a lot of backstory, you will surely want to read the previous novels and I guarantee they’re as likeable as this one.
I found the Santa Fe setting intriguing as there’s a lot of info about the history, the places, and the people. There’s a mix of historical and fictional characters and the mix works well.
If you want to learn more about the Fiesta or the artists there’s a bibliography at the end of the book.
I enjoyed this book as I like Maddie and the cast of characters, there’s a lot of world building and we are introduced to the characters, their relationship, and the atmosphere of the city before the Fiesta.
I enjoyed this part, but I think that some less details would have helped and start the proper mystery part sooner.
The mystery is solid, twisty, and full of surprises. I couldn’t guess the culprit and enjoyed the storytelling and the story.
This is a lovely series, and this is the best instalment so far. I read it as fast as I could, and I can’t wait to read the next story as there could be some big news.
Highly recommended
Many thanks to Amanda Allen, Severn House and Rachel’s Random Resources for this digital copy, all opinions are mine.
The Author:
Amanda wrote her first romance at the age of sixteen--a vast historical epic starring all her friends as the characters, written secretly during algebra class (and her parents wondered why math was not her strongest subject…)
She's never since used algebra, but her books have been nominated for many awards, including the RITA Award, the Romantic Times BOOKReviews Reviewers' Choice Award, the Booksellers Best, the National Readers Choice Award, and the Holt Medallion. She lives in Santa Fe with two rescue dogs, a wonderful husband, and a very and far too many books and royal memorabilia collections.
When not writing or reading, she loves taking dance classes, collecting cheesy travel souvenirs, and watching the Food Network--even though she doesn't cook.
Social Media Links :
https://ammandamccabe.kmcb.site/index.htm
Instagram (https://www.instagram.com/amandamccabeauthor/ )
FB https://www.facebook.com/amandamccabebooks
TikTok (https://www.tiktok.com/@amandamccabeauthor )
#rachel's random resources#severn house#netgalley#blogtour#cozy mystery#historical mystery#historical fiction
0 notes
Text
White Rabbit

Pairing: Jungkook x reader (gender not specified)
Word Count: 5,091
Genre: hacker!AU 🧑🏻💻, Matrix vibes inspo, angsty but with a happy/hopeful ending
Rating/Warnings: (M) - mentions of violence/blood, swearing, death of a family member (brother), gunshot wounds
Summary: After his brother’s murder took everything from him, Jungkook is dead set on revenge, even if it costs him his own life. But at the last moment he finds a ray of light, of hope. At the last moment, he meets you.

The blood on the wall is not his, but it haunts him just the same.
He rests in bed though he hardly feels the full meaning of the word. The blackout curtains are pulled tight, blocking any errant strands of sunlight that would seek to come in. Jungkook knows he’s isolated himself, but he can’t find it within himself to care. With a groan he turns; the mattress and bedframe whine metallically, protesting the movement. The blankets would be warm and comforting - if he had pulled them fully, properly over him. But he can’t get comfortable; he forbids it.
Revenge and retribution are the twin flames that sustain him these days. They pull him through the pit of his loss like a rope around his waist, tied behind a moving truck. Through the mire of pain all he can see is one purpose. A single goal he clings to. Perhaps on the other side of his task he’ll find peace, or at least satisfaction that justice has been done. It’s a silly hope but it’s what he has, and he’ll sink his nails and his teeth into it with all the energy he has left.
Sweat coats his back in the midst of his half-awake state. Somewhere between dusk and dawn he found an uneasy sleep. His left leg hangs over the bed, exposed to the chill in the air, on purpose. He knows if he stops searching that he’ll sink, as if through quicksand. And the thought of what he must do is far less terrifying than the thought of what awaits him if he sank to the bottom.
In sleep he grasps the fabric of his sheets with tight fingers. His head shakes from side to side, neck straining and veins standing in attention. As always his dreams are fraught with slivers - of images and memories and premonitions, or what feels like them. Sometimes he remembers them when he wakes. Other times they fade in the light of the morning.
But always he remembers the white rabbit.
At times it’s a real animal made of fur and softness that dances around his feet in his slumber. Or he becomes one himself, when he stares in the bathroom mirror after long nights of sleep deprivation; when his teeth grow and his nose wrinkles and he imagines his ears lengthening to become animalistic.
It’s important, and he knows it in his bones. But finding the murderer has dominated his mind and always he rolls his shoulders and casts off thoughts of the rabbit. It lives in the world of his mind and he doesn’t have time to wander into dreams.
A discordant beeping pulls him from the fitful sleep and he sighs. Tossing off the blankets he rolls to the side. The damp white shirt clings to his frame and his bare feet hit the hardwood floor. Jungkook runs both hands through his hair, pushing the dark strands away from his vision, tucking them behind his metal-filled ears. Rising, he gets to work.
Once upon a time he and his brother had work stations opposite each other. Computers pressed almost back-to-back to form one technological beast. Since he was seventeen he’s gone by K00KIE and after a few bumbling attempts he managed to find his stride as a hacker. Like learning a foreign language he stuttered and reached blindly for what he didn’t know for weeks before the words came naturally to his tongue. Now the internet has opened itself before him like a book held in his hands and reading is his chiefest joy.
His brother was everything Jungkook is not, and he exists now like the sun does to the moon on long nights, haunting Jungkook like a phantom limb. Less than a year separated them and they were far more like twins than just brothers. Jihoon was indeed almost brighter than the sun itself. Loud and free and unrestrained. He led them both into this world and now, left behind to pick up the pieces, Jungkook vows he’ll get them both out of it.
He stands, pressing his hands on his knees for leverage. The walk to his desk chair is only a few steps but it feels like he walked a mile. In the weeks since Jihoon’s murder he hasn’t had the energy to exercise. Or shower very often. Or even eat. Grief hangs around him like a shroud and with glassy eyes he takes in his workspace.
Jungkook lets his lids close again, dragged down by exhaustion, and he sees Jihoon sitting at his desk with a lollipop skicking from his mouth, speaking with animated hands about the program they made. How it would change the world. The cowlick of hair on his right side that always stuck up at an odd angle, and his eyes that crinkled whenever he was excited about something.
That world is full of bright color and when Jungkook opens his eyes, slowly, reluctantly, his apartment is awash in grey. Jihoon’s desk is empty. Every space is filled with piles of paper full of Jungkook’s messy writing, scrawled on every available notebook and receipt, surrounded by empty take out containers and chopsticks and energy drink cans and the stupid fucking plastic bags his grocery delivery services uses instead of paper ones.
Again his phone beeps, signalling more and more messages from his friends. A few he knows in real life, but most he only knows online. People who started out as words on a screen or lines of code traded back and forth but became the ones who know him best. They know he hurts and are trying to reach across through the digital world to catch him as he falls.
Kook, where are you? Talk to us.
Is there anything we can do? We’re here for you
If you want help, you only have to ask. To heal or… to make them pay.
Maybe he’ll let them, once it’s done. It’s a dangerous rabbit hole to walk down alone, but he won’t risk anyone else. He can’t.
None of his friends knew what he and Jihoon were working on. It was too secret for either of them to discuss online, where anyone could be listening. But in this community death means one of two things - either the government found you, or the competition. Jihoon didn’t fuck with the government, everyone knew that, which left only one option.
After he finds his brother’s killer or - fuck, killers? - perhaps he’ll be who he almost was again. Someone young and alive with the world at his feet. He could get a new apartment with a view of the park his brother loved, full of old brick columns surrounded by ivy and a sprawling network of paved pathways to walk. He could marathon anime and order from that Chinese restaurant he loves and play Tekken and create games and programs with his friends. It’s so close and yet so far from possible.
He turns his hands so his palms face skyward and gasps in a breath with how badly he wants to be freed from this. The pain and the hollow feeling in his gut and the insatiable urge to undo bloodshed with more blood spilled.
Could he do it? He wonders to his empty apartment, the darkness only lit by the glow from his computer screen. He doesn’t know what he’ll have to do, but whatever price is asked of him, he’s willing to pay.
His brother built a program that was too dangerous to be allowed and Jungkook helped him. Jihoon must have said something, anything, to the wrong people. The reckless joy that carried him through the world must have been exposed and then they came and sank their teeth into him devoured his brother whole. Jungkook helped him build the damn thing. It should have been me. It should have been anyone, anywhere else, but Jihoon.
Jungkook was down at the Seven-Eleven, getting slurpees. And when he came back, his brother was dead.
It can’t have been more than fifteen minutes but already his brother’s body was starting to cool, despite the warm blood that ran over Jungkook’s hands as he tried to stop the bleeding. He found his phone with a slick, wet hand, the one not pressing against the wound in Jihoon’s chest, and called for help.
It was too late - his brother died in his arms and the people who did it left no trace, not a scrap of a clue about their identity. The security cameras were disabled remotely. The hard drives were taken by with gloved hands, no fingerprints. In the aching days after it happened he went looking - in the back ups, and the back ups of the back ups he forced his brother to make. Always the careful one. But everything was gone. Like sand between his outstretched hands there was nothing left for him to hold.
Jungkook has a rage in him that would terrify him if he wasn’t too numb to feel. He pops the top of the Monster energy drink and downs half of it in three swallows. It’s warm and the flavor is atrocious, but it gets the job done. Ages ago he would have listened to music while he coded and while his brother dreamed of things that hadn’t yet been created. Now he sits in silence and his world is reduced to the muffled clacking of his fingers as they race across the keyboard, echoing around the now bare beige walls.
He should let people in and he should let his friends help. They’re good, many of them might even be better than Jungkook himself at tracking the bastards that did this. But letting them in is like breathing underwater. If he gasps in air he’ll also inhale water and drown. After it’s done, he vows to try. But not until then.
“Follow the white rabbit, little brother.”
The words are an echo in his mind, pinging around the lonely apartment and so clear it’s as though Jihoon whispered it in his ear. Jungkook turns, shaken and startled. He needs to get himself together. The days and weeks are blurring together and only the readout on his unused but still charged cell phone tells him where he is in the passage of time.
Sixteen days, four hours, and twenty three minutes since his world changed.
He shrugs off the strange suggestion, as always. Now more than ever he doesn’t think he should listen to what the dead ask.
Instead he picks up where he left off yesterday - or, no. It’s just after eleven at night according to his phone. He picks up where he left off this afternoon, when he finally gave into his brain’s pleas to sleep. The trail dead-ended in all the obvious places he looked. The message boards and chat rooms his brother frequented. Anyone who even whispered about ideas related to the program his brother envisioned. Rivalries and competitive streaks are a dime a dozen in his community, but every time he feels like he might have some goddamned clue it goes up in smoke.
Hours of digging tonight and he somehow strikes gold. At first he assumes it’s a hallucination or a wish so strong he’s made his imagination tangible. But it’s right there in black and white on his screen. In a buried chat room so far off the beaten path he can’t see daylight anymore - he finds a conversation. Someone describing a program and another anonymous name offering to buy at any price. It was shut down almost immediately after it was posted, eighteen days ago.
If he wasn’t already known as Kookie he might have listened to Jihoon and gone by the nickname ghost. If there’s any memory of something happening on the dark web, Jungkook can find it, and tonight he’s scented blood. Tonight he’s not a rabbit but a predator himself.
It’s only a breadcrumb, a fishing lure dangling in the water, but he grasps it between his teeth. Jungkook was always good, almost the best. Now full of desperation and reckless energy, he’s unstoppable. He pulls on the line and it unravels before him, drawing the unsuspecting fisherman into the depths where Jungkook waits. First an IP address and then he finds a text message log and then a name and before he knows it, he’s found them. Or at least where they were three days ago.
Triumph is delicious in his mouth, but it also has the same rank taste as the lingering energy drink. Jungkook blinks and rubs at his eyes. He stands and tests the cans around his keyboard for any that are full. All empty. He curses and moves to the kitchen. Opening the fridge he’s greeted by emptiness. His stomach tightens and growls, reminding him it’s been far too long since he had real food.
A plan forms in his mind, but first - he stops to smell the shirt he wears and winces - he needs a shower. And food. So much food. Enough to see him through to the end of this.
The bathroom, much like the whole apartment, is full of reminders. Razors and toothbrushes and hair gel that has no owner anymore. Jungkook avoids the mirror. He doesn’t need to see the dark stains of purple beneath his eyes or the way his skin has pulled taut over his jaw, turning it sharper than ever before. It’s bright as he pulls back the shower curtain, morning light streaming in through the window while he turns on the water.
He strips and stands naked on the plush blue bath mat. Steam fills the narrow space and hugs him. His brother used to sing in the shower, loudly, to wake up Jungkook when he’d sleep in. He breathes in the moist air and emotion clogs his throat. The urge to give in pulls at him and he reaches a hand to the porcelain sink to steady himself.
Soon.
It’s all he can promise himself and his brother’s memory. Soon he’ll get his revenge and then - well, he doesn’t know. The future used to be a wildly exciting prospect before him. It was never money or fame that thrilled him, but simply the feeling of being a part of something. Together with his brother they built a community and the world was at their feet. Now he feels unmoored, a boat that got pulled by the tide and can’t find its port again.
He’s always been soft, even in his darkness. Violence and aggression were saved for the gym or for Fortnite, not for the outside world. But now a monster has awoken in him and he can only sate it with the blood of the people who took his blood, his family, from the world. Should he get a gun? Finish this the way they started it? Or should he attack them online, eviscerate their lives with code and strokes of his mouse?
When he blinks his eyes are sluggish, and finally he moves, stepping forward into the spray of water. With a groan he leans against the black and white tile and savors the feeling of hot water caressing his shoulders and back. Jungkook runs strong fingers along his neck and massages the kinks out. He rubs sleep and exhaustion from his eyes and reluctantly washes his hair and body. Much that he wants to, he does not sink to the floor of the shower and condense into a ball.
He hates to wait, but he needs food and fresh air and a chance to think. And more importantly, he needs coffee.
The world outside his apartment assaults him with noise and movement and he curls his hands into fists in the pockets of his leather jacket while he walks. Drinking a deep breath the air cools his lungs. He knows the way to the diner in his sleep. It’s yellow and teal neon sign draws him in like a North Star. The familiar tinkling of the welcome bell alerts the waitress to his presence.
“Oh, it’s you Jungkook! I haven’t seen you in ages. I’ll be with you in just a minute, sweetheart.” She tells him with a wave and a wink. “Have a seat.”
He gives Pearl his usual tight-lipped awkward smile, even as he breathes a sigh of relief at her warm presence. Her dyed red hair and bold red lips are still going strong in her sixties, even at the early hour. She takes a couple’s order at a far table, her boisterous voice holding him the way a mother might.
Jungkook takes his favorite booth - the two-seater in the corner with the view of the river. He wraps his arms tight around his chest and sits straight in the seat, feeling rigid and off putting in the warm, cozy space. But slowly the smell of bacon and coffee and the cushion at the back of the chair pull him in. Sagging, he releases his hands to grip the empty mug between his palms.
He starts to compose a plan. Something he can do today, quickly before they escape. But then Pearl comes over and fills his cup with coffee. She slips a piece of paper onto the edge of the table, face down, like normal. Jungkook stutters and reaches for it as she bustles away towards the kitchen.
“Pearl, wait-” he chokes on the word, throat scratchy. How long has it been since he last spoke out loud? She turns and cocks a hip onto the side of the waitress stand, waiting for him to continue. “I haven’t ordered yet.” His voice is small and unsure. He notices the items listed and total at the bottom and his brow furrows. “And there’s a zero dollar total.”
She smirks and looks at him through her lashes with trademark sass. “Sweetie, you’ve ordered the same thing for years. I know you. And I also know about your brother. I saw it in the papers.” Her expression turns sad, eyes widening. “A robbery in our neighborhood? I can’t imagine. It’s so awful.” She shakes her head in disbelief. “I refuse to let you pay today.”
A smile tugs at him. “And the next time?”
The waitress snorts and waves a hand, giving him a lopsided smile that manages to be both comforting and cheeky. “Next time you owe me, darlin’.” She disappears around the corner and Jungkook laughs.
He tucks the slip into his pocket; a reminder that someone sees him. Cares about him. Remembers him. His phone weighs heavily in his jacket pocket. The notification tone is off now - not just because Pearl hates cell phones but because he’s not quite ready yet - though he knows there’s dozens of messages still waiting for him. Lifelines he could grab onto if he wanted.
The coffee warms his hands and he allows himself to look up. Through the windows he watches the river, winding its way through the center of the town and reflecting the sunlight. Movement to his right catches his eye, finding something else the sun loves two tables away - you.
Abruptly he thinks back to watching The Wizard of Oz with his family as a child. How Dorothy emerged from a grey world into full color and how it took his breath away. You rest your chin on your hand and yawn. Books are spread around you on the table. Piles of notes and stacks of plates that let him know you also haven’t slept in a while. He feels something stir inside him, long dormant. Curiosity, blooming in his veins like spring buds after a long winter of snow and frost.
He watches the fall of your hair across your forehead as you shake your head slightly, trying to stay awake. He imagines running his hand through it, feeling the soft strands. The world is hazy after so many days of insufficient sleep and you look like a dream to him. A slight flush has come to your cheeks and he wonders if it’s from the old heating unit mounted to the ceiling that’s been stuck at full blast ever since he’s come here. Or from the fleece-lined denim jacket and blue fingerless gloves you wear. Still, after what looks like hours in the warm diner.
He wonders if your studies consume your mind the way hacking has come to dominate his. From this angle he can’t see the subject or content of any of the books, but he can see your handwriting. Both precise and delicate, it fills the pages in neat lines. The world tilts as he leans up, calves and thighs flexing to get a better view, and he imagines tipping over the edge of a pool and falling into you. Like a parched man looks for water he feels drawn to you with an intensity he doesn’t understand.
He’s already been inside the diner for a few minutes, but he knows there’s still time. You haven’t looked up. You haven’t noticed him yet. He could stand now, and go. Taking his broken, jagged spirit and shattered heart and leave you in peace. Maybe today seeing Pearl is enough and maybe her voice will carry him through what he must do. He fumbles for his wallet to leave her a few dollars in tip before she can come back with his food.
But then you look up, drawn by the noise of his wallet chain scraping the wood chair. Your eyes lit by the morning sun hold nothing but innocence and kindness and he knows he can’t leave now. For a moment he imagines he could wipe his slate clean and be someone pure and good once more. Or maybe if he can’t be un-tainted by the stain of violence and death on his life, perhaps holding someone like you and kissing hope is more than enough.
He’s staring and he knows it, and so do you. With a subtle tilt of your head against your hand you smile sleepily at him. He knows you’re similar to him without ever talking to you. He knows you stay up too late and that your nights are consumed by the hunger within you. In a normal conversation he’d ask your name or perhaps buy you some coffee. But his world has been sharpened to a knife’s edge and he doesn’t have flirtation or standard social customs at his disposal. Instead, he skips the formality.
“What are you studying?”
With a smirk you reach for the book closest to you, holding it up so he can see the cover. Elementary Calculus. “I’m battling it out with some derivatives.” You sigh and rest the book back on the tabletop, holding his gaze.
“Are you a math major?”
“No, computer science.” You watch him, eyes trailing over his tattooed knuckles that hold the cup. It might be the heat of the coffee or the rays of light but he imagines it’s your touch across his skin instead. “But I have to take the last of my damn math credits to graduate. Just calculus between me and my dreams.”
He could offer to help, but in truth he was terrible at math in school. Jungkook found his way into hacking through a back door, not any formal study. “Computer science, huh? What are you hoping to do for work?”
You narrow your eyes at him, lips fighting a smile, as though you’re debating whether to trust him. To let him in. He’s nervous for the first time in ages. Pulse racing and stomach jittery with some bright feeling he can’t properly name.
After a long moment you slide out of the booth and stand. Not to leave but to close the distance and pull out the chair opposite him. You lean in towards him and he smells a hint of the scent you wear or maybe it’s your shampoo. “I have no idea what I want to do yet. Something good, hopefully.”
In a wave of lovable sass Pearl brings over his breakfast, forcing the two of you to move back. He hadn’t noticed how much he’d leaned in towards you as well. “My two favorite night owls finally meet,” Pearl says with a click of her tongue. “It’s gonna be a good day, honeys.” She walks off with a hum and the trademark bounce in her step.
You blush and look down at your hands, rubbing your thumb over the palm of your free hand. His mind is always full of questions, insatiable in his hunt for knowledge and creation. Today he wants to know everything about you. Where you go to school and how you got interested in computers. What your favorite movies are and if you’re from this city or if you moved here and what you might taste like if he’s lucky enough to kiss you, some day.
It’s easier to ask than to share, he’s found. A socially acceptable smoke screen to hide behind that conceals his nervousness when talking about himself. Without his boisterous brother beside him he feels both more mature, standing on his own, and younger. More vulnerable. To do this, to do life, alone now.
“What about you?” Your words break through his distracted mind with the soft lilt of your question.
“Oh, I’m not in school any more.”
You nod and reach back for your abandoned coffee on your table. The movement makes your jacket and your shirt ride up slightly and he sees a sliver of exposed skin along your side. Forget how long it’s been since he spoke, how long has it been since he touched someone, he wonders. Or was touched? He would normally keep desire locked inside but here in the daylight after what feels like an endless night he can’t remember how to behave properly anymore. All he wants to do is touch you, and to hear your sweet voice leading him to a kinder, more gentler world he’d forgotten existed.
“Figured it was a fifty-fifty shot since we look about the same age,” you answer, now returned to starting at him while you blow on your coffee. “So what do you do, then? I can’t imagine not having my head full of school and homework right now. Please tell me about the outside world.” You sigh dramatically.
It feels almost forbidden to speak the words aloud. To tell you about the world he and his friends live in that’s made of wires and binary in two dimensions. But it’s the truth, and he’s tired of keeping it to himself. “I work with computers too, I suppose. I do mostly programming and some… other things online.”
You raise a brow at him. “Like porn?” Jungkook’s mouth drops open, his fork paused midair and a laugh caught in his throat. Quickly you wave a hand in the air, unable to contain your own laugh. “Sorry, that’s a terrible joke. I just -” you groan and run the hand over your face. “My mother always says I choose the worst possible times to be inappropriate. But you’re cute and I’m sleepy and couldn’t help it.”
After a beat you drop your hand back to the table and look up at him. His chest is warm and other parts of him are coming to life that he hasn’t thought about in ages. Like Rip Van Winkle he feels as though he’s been asleep for years and didn’t know it. He does his best to contain his expression but if your playful smile is any indication then he knows the way he’s feeling is broadcast all over his face.
He sees you as a lifeline. A portal, like from one of his favorite video games, leading him somewhere better. There will be time later to figure out if the connection is real and not just him taking the first hand extended to him. Once you’ve both had a night’s sleep and see things more clearly. But right now he says the only thing that makes sense. The only question he can manage.
“Would you like to go out with me?” He knows he should be smoother or have whatever ‘game’ is, that his brother always talked about having. But this is what he has and he hopes it’s enough.
You look him up and down as he chews a bite of bacon. To a less caring eye someone might dismiss him because of the dark circles and the tattoos and the haunted look he sees in his face these days. But maybe you see everything he likes and everything he hates about himself from a far more charitable point of view. Maybe you’ll be nicer to him than he’s allowed himself to be lately.
“That would be great,” you answer softly, sipping your coffee. “How’s now for you?”
He blinks. “Now?”
“Well, after you finish your breakfast I mean.” Turning, you casually wave at Pearl and she lifts a finger to say she’ll be there in a moment. “I should get some pancakes myself, first.” With a shake of your head you gesture to the books. “I think I’ve earned some after an all-nighter with the devil, aka calculus.”
Jungkook nods, biting his lip to keep from grinning. “Sounds good to me.”
Pearl eventually brings you pancakes, blueberry with the fancy whipped cream she likes to keep in stock. She brings him another serving of food as well and waves him off when he tries to pay. As his belly grows fuller and the two of you talk about your favorite old school computer games he realizes it’s been over an hour since he thought of his brother. While you gather your books into your backpack he pauses, wondering if that’s a good thing.
Then you lift your hand to scratch an itch and that’s when he sees the tattoo. The gentle black outline on your neck, behind your ear; the white and pink ink. Faded a bit, not fresh. The small animal with big ears is a thunderbolt and he stops, then smiles. He holds open the door for you and tilts his head back up to the bright, cloudless sky and does something he hasn’t done fully in almost three weeks - he laughs.
Later today Jungkook will share what he knows. With his friends he trusts. Perhaps with you as well, in time. But for now he has walk to take with you along a river, and it’s shaping up to be a gorgeous day.
Follow the white rabbit, little brother. And finally, at last, he listens.
#jungkook fanfic#jungkook au#bts fanfic#bts au#bts jungkook#meant to have a Namjoon fic ready to post today but life got in the way a bit so I'm going to post this a bit early instead!
50 notes
·
View notes
Text
Yelp
mid America engine The IPO raised $sixteen billion, the third-largest in U.S. history, after Visa Inc. in 2008 and AT&T Wireless in 2000. Based on its 2012 income of $5 billion, Facebook joined the Fortune 500 listing for the first time in May 2013, ranked 462. The IPO was controversial given the immediate price declines that adopted, and was the topic of lawsuits, whereas SEC and FINRA both launched investigations.
Twitter's annual growth rate decreased from 7.eight percent in 2015 to three.four percent in 2017. An April 2017 a statista.com blog entry ranked Twitter because the tenth most used social community based mostly on their count of 319 million month-to-month visitors.
On June 1, 2011, Twitter announced its personal integrated photo-sharing service that allows users to addContent a photo and connect it to a Tweet right from Twitter.com.
In 2004, MapQuest, uLocate, Research in Motion and Nextel launched MapQuest Find Me, a buddy-finder service that labored on GPS-enabled mobile phones. MapQuest Find Me let users automatically discover their location, entry maps and instructions and find nearby points of interest, together with airports, motels, restaurants, banks and ATMs.
Users additionally had the ability to set up alerts to be notified when community members arrive at or depart from a chosen area. In 2005 the service grew to become obtainable on Sprint, and in 2006, Boost Mobile.
The prevalence of African American Twitter utilization and in many in style hashtags has been the topic of analysis research. According to a research by Sysomos in June 2009, women make up a slightly bigger Twitter demographic than men—fifty-three % over forty-seven %. It also said that five % of users accounted for seventy-five % of all activity and that New York City has extra Twitter customers than other cities.
The capacity to export this type of tweet archive, which by no means existed on the new format, has been removed entirely in August 2019[when exactly? Even when accessing the legacy Twitter desktop web site structure using the user-agent of an older browser version, the choice has disappeared from the account settings.
The company traded its first shares on May 19, 2011, under the NYSE image "LNKD", at $forty five per share. Shares of LinkedIn rose as a lot as 171% on their first day of trade on the New York Stock Exchange and closed at $ninety four.25, greater than 109% above IPO worth. Shortly after the IPO, the location's underlying infrastructure was revised to permit accelerated revision-launch cycles.
In 2011, LinkedIn earned $154.6 million in advertising income alone, surpassing Twitter, which earned $139.5 million. LinkedIn's fourth-quarter 2011 earnings soared due to the company's enhance in success in the social media world. By this level, LinkedIn had about 2,a hundred full-time employees in comparison with the 500 that it had in 2010.
In May 2019, Tel Aviv-based mostly personal intelligence company Archimedes Group was banned from Facebook for “coordinated inauthentic habits” after Facebook discovered fake users in countries in sub-Saharan Africa, Latin America and Southeast Asia. Facebook investigations revealed that Archimedes had spent some $1.1 million on fake ads, paid for in Brazilian reais, Israeli shekels and US dollars.
Facebook gave examples of Archimedes Group political interference in Nigeria, Senegal, Togo, Angola, Niger and Tunisia. The Atlantic Council's Digital Forensic Research Lab said in a report that "The tactics employed by Archimedes Group, a non-public firm, intently resemble the forms of information warfare ways typically utilized by governments, and the Kremlin particularly."
The new layout was revised in 2011 with a concentrate on continuity with the net and cellular variations, introducing "Connect" and "Discover" tabs, an updated profile design, and shifting all content material to the right pane . In March 2012, Twitter turned out there in Arabic, Farsi, Hebrew and Urdu, the first proper-to-left language variations of the location. In August 2012, beta help for Basque, Czech and Greek was added, making the positioning out there in 33 totally different languages.
The service's utility programming interface allows other internet companies and applications to combine with Twitter. Maria Zakharova for the Russian overseas ministry stated the ban was a "gross violation" by the US of free speech. The firm generated US$forty five million in annual income in 2010, after beginning sales midway through that yr; the company operated at a loss through most of 2010.
BBB accreditation, or membership, is totally optionally available for a business to just accept and take part in via the payment of dues. Past complaints allege that the BBB compiles scores primarily based upon their capability to collect their money from companies, and never totally upon business performance.
In August 2010, one of North Korea's official authorities web sites and the nation's official news agency, Uriminzokkiri, joined Facebook. Studies have associated social networks with optimistic and negative impacts on emotional well being. mid America engine
Despite the vote, the BBB web site nonetheless states that factors are taken away if accreditation is misplaced. A business is eligible for BBB accreditation if it meets, within the opinion of the BBB, the "BBB Standards for Trust". The 112 BBBs are independently ruled by their very own boards of administrators and should meet international BBB requirements, which are monitored by the IABBB.
In 2011, a New York Times columnist described a criticism from a shopper that the Austin chapter of the Better Business Bureau refused to resolve complaints against corporations if clients don't pay a $70 mediation fee. In Canada, CBC News reported in 2010 that Canadian BBBs have been downgrading the rankings scores of companies who stopped paying their dues.
For example, a shifting business who had an A ranking and had been a BBB member for 20 years, dropped to a D‑minus ranking after they allegedly not wanted to pay dues. In response, the president of the International Association of Better Business Bureaus has stated the BBB ratings system will stop awarding points to companies for being BBB members.
The national BBB's government committee voted to address the public's notion of the ratings system. It voted that the BBB rankings system would now not give further factors to businesses as a result of they are accredited. It voted to implement a system to deal with complaints about BBB sales practices.
2 notes
·
View notes
Text
Chess in streaming platforms on the rise

Learn the game of Chess
Chess Classes in Bengalore
Gone are the days when chess used to be just a board game played on a sixty four squares board with sixteen chess pieces allotted to each player. For a long period of time, only the two players competing against each other were an actual part of the game. When it came to champions, the media and mass media could only talk about the exceptional and calculative moves undertaken by a certain player, which further used to succeed in reserving a place in the headlines and newsletters. The die-hard fans of the game would wait desperately for the news to either come up on the television or forage the newspapers as it would get them acquainted with the remarkable moments in the game.
Times have however, changed now. With the elevation in technology and the world getting digitalised in every possible way, chess has not been an untouched area. The introduction of streaming platforms has been a noteworthy advancement in the age of digitalisation. The platforms are designed in such a way to provide the live stream of the games being played to the end user, which is done with the help of the service providers working at the back end.
It is certainly noteworthy to acknowledge that on one of the most sought after streaming platform, Twitch, the tremendously main staying activity is the game of chess. The credit for this solely goes to the online streamers and celebrated chess champions who choose the online mode to play the game. In a recent research by a data analytics firm, SullyGnome, the number of hours for which chess was viewed on Twitch doubled every month. It amazingly topped in the month of May by attaining the record of more than 8 million hours of watching.
The first landmark in this was set by Hikaru Nakamura who is a five times US chess champion and the youngest player belonging to America to achieve the Grand Master title. Through the popular social networking site Twitter, Nakamura has acknowledged the keen interest of the visitors who have either witnessed just one or two stream or have continued their viewership streaks for all the streams. He also mentioned in his tweet about how the game of chess is getting to witness the popularity that it hadn’t in the near past.
One of the breakthroughs of the rising fame of Twitch can be attributed to its collaboration with the popular and user friendly chess playing website, ‘Chess.com.’ It is said that Twitch has a long history of chess players that dates back to the period when it was not so popular but the amalgamation that took place in the year 2017 gave a new elevation to the acclaim received by the game. Apart from the game itself, the power that lies in the hands of the influencers in enhancing the impact of a brand is quite evident in this scenario.
The famous Grand Master, Hikaru Nakamura elsewhere uses the Twitch platform to impart the knowledge of the game to others. During the difficult times when the world has been enveloped by the global pandemic, the chess champion has gained over 350,000 followers and this has resulted in the rejuvenation of people’s interest in the century old game. In an interview, Nakamura mentioned the essence on which the game of chess is based on. He thoughtfully said that the rules according to which the game of chess is played have not changed much even in the modern times. This implies that the basic structure of the rules has remained the same throughout centuries.
Nearer to home, in the sense of a digital streaming platform that most of us are aware of and use it on a regular basis, we cannot help but mention the name of YouTube. In the midst of the life threatening global pandemic, wherein young kids could be easily and callously expected to remain glued to ‘idiot box,’ also known as the television, watch cartoons or play some violent combating games, surprisingly, they chose to view online streaming of the chess matches. As add on, they were thoroughly supported in this by their parents who often joined their posterity and remarkably spent some quality time watching the live streaming chess.
The best thing about the live streaming of the chess matches played by world champions on easily accessible platforms like YouTube is that the viewers are able to get complete insight into the way in which the game is played. A keen observer will tell you that how satisfying it is to be able to deep dive into the game and not just remain confined to watching the players shaking hands in the beginning of the match or saying them “well played” and “congratulations” to each other post it. The thing that fascinates the children the most is that they get a chance to explore the leading players discuss the game in detail, analyse tactics and sometimes even banter with each other. This further helps the kids to develop a prudent sense of understanding the logic behind every move and their problem solving and analytical abilities are also enhanced.
During the pandemic caused due to the outbreak of the novel coronavirus, various leading Grand Master belonging to India like Vidit Gujrathi, Baskaran Adhiban and Srinath Narayanan have begun hosting their own streams on YouTube and needless to mention, they have received humongous viewership consistently. Among the other well established pioneers in the field of chess, there have been some newbies as well. Samay from India is one such name that is noteworthy to mention. He began taking chess classes on YouTube on the behest of his friend Tanmay, who also happens to be a comedian. He tells that he began it as a hobby to be followed in leisure time but soon it seemed like he had found his niche. Later, he organised an online chess competition in a merger with the members of the comedy series ‘Comicstaan’ which marked the first instance wherein comedy was infused with a sport like chess.
So, in a growingly digitalised world, the platforms like Twitch and YouTube are proving to be of immense help to the admirers of the game. They have come like an oasis in the desert and gave people an apt platform to learn and if pursued correctly, showcase their own talent in the game.
For Chess Classes in Bengalore , Visit Saswath.academy
6 notes
·
View notes
Text
In Depth Analysis of ‘Skam’: Belonging with Realism

There seems to be universal acceptance that the mere suggestion that a television drama is marketed towards a teenage audience, or is beloved by teens, reduces the creditability and artistic merit of the television show. In popular culture, media aimed to teens – and especially female teens – has been seen a childish, low brow content filled with bad acting, bad writing that contains illogical plots and superficial – as it contains beautiful twenty-somethings playing sixteen years old teens. This opinion could be due to that fact that scholarly critics are not the ‘intended audience’, but it is argued the reason may be that teen dramas, with their ‘ludicrous’ plots, separate themselves from ‘reality’ for entertainment purposes, which thereby alienates the ‘rational’ mind-frame of the critic. By detaching itself from realism, teen dramas, as a genre, seem to be seen as superficially candy floss – bright ostentatious sugar-inducing fluff with no core-essence nor nutritionally substantial properties. It is argued that teen dramas have the ability to be more than superficially candy floss. The following essay will analyse the Norwegian teen drama Skam and how it strives to represent teenagers in a genuine and realistic way by its use of extensive research, authentic acting and location, and digital storytelling. Through it’s creating, making, and releasing of the series, Skam invites critical television evaluation while also exploring the crucial element of emotional growth and belonging that are needed for an ideal teen drama.
Teen Dramas – in common discourse

Though, in the past, it may be prevalent that there was a separation between film criticism and television criticism – film being seen as more worthy of art criticism – there is distinct quality hierarchy of televisional texts. With acclaimed serialised dramas focusing on a male protagonist/anti-hero, mainly broadcasted on subscriber based service, being deemed worthy of evaluations, soap operas, reality tv, and teen dramas on network television are seen as below par. Television dramas that are focused on teenagers are seen as cringe-worthy or a part of pop-culture that should be mocked and not taken seriously. Kevin Williams who was, during the 90s, applauded for his work on the horror film Scream – having teens conversing in the metalanguage of film – was also reprimanded for creating the hit television show Dawson Creek – having teens conversing in the metalanguage of film. Dawson Creek was seen as a teen soap opera that was filled with sex, drama, and love-triangles, that didn’t merit the opinion of highbrow critics. Similarly, shows such as Gossip Girl, The OC, One Tree Hill, Vampire Diaries, and Riverdale have been – and will continue to – criticised for its writing, directing, and acting. There may be expectation to this prejudice of teen dramas. Buffy – The Vampire Slayer has been praised for its writing and Friday Night Lights was seen as a critic darling. However, it should be noted that Friday Night Lights was overlooked by audiences for its marketing as a ‘teen drama’ and critics have negatively commented on the show when discussing its teen or melodramatic elements. A teen drama should, it is argued, provide an insight to teenage life that is putting a mirror to the teen audience’s life and also reinvigorating the memories of teen life for adult audience. Late teens and early twenties are the years where we are confused, as humans, on where we belong, who we are, and what we want. Therefore, teen dramas, in essence, should provide a realistic representation of teenage years.

Traditional Teen dramas and their rejection of Realism
Though many of the aforementioned teen dramas deal with the melodramatic plots that are all wrapped up in teen angst and served to its audience on a weekly basis – they all encompass a crucial part of any teen drama. The essence of a teen drama, it is argued, is the raw, real, unapologetic emotions. As teens, when we experience love – usually our first experiences – it is all consuming, while as adults; we tend to be more rational and mature. Our hates are world ending – while as adults we either ignore it or deal with it with the right amount of passive aggressiveness. Therefore, when a drama reproduces these realistic and accurate representation of emotions and stories, it excels as an artform. Even if a teen narrative is dealing with murder mysteries or vampires, it excels when it looks at the raw emotions of their characters and the characters’ longing to belong. Teen dramas are a great platform to a realistic representation of growth and exploration of a character’s identity and themes of belonging. This is excellently portrayed in Friday Night Lights with the football players coming to terms with their place in Dillion when they are no longer football players.

Cinematic realism, as infamous critic Bazin states, is the fulfillment of the human craving for realistic representation. Realism, in film theory, is obtain through reflection of reality being reproduces through camera lens. Realism critics who supported realism in film submitted several characteristics that produced cinematic realism, these being use of long takes, deep focus, limited editing, and use of actual locations non-professional. These characteristics are in contrast with what is associated with teen dramas. The cast is often filled with actors who are in their later twenties rather than their late teens, the text is highly stylised, and ludicrous plots are aimed to provide wish-fulfilment and escapism rather than realism. However, Skam rejects these characteristics of the teen drama and instead, not only accepts the theory of realism, innovates what television can do in the 21 century to thoroughly satisfy the human craving for realistic representation. Skam uses traditional realism through extensive research, the use of actual locations, and the use of nonprofessional actors, but innovates by using temporal realism and transmedia storytelling.
Creating Skam

NRK (Norsk rikskringkasting) is the Norwegian Broadcasting Corporation, similar to British’s BBC and Australia’s ABC. Which means that it is a publicly funded corporation (through tax-payers) and is therefore not a commercial broadcasting corporation, such as the American Broadcasting Corporation (ABC) – which is funded through commercials and advertising, nor a private broadcasting corporation, such as the HBO or Netflix - that are funded through monthly/annual subscriptions. NRK, is therefore, serving citizens, not merely consumers as their audience, thereby having a public duty to uphold. So, when NRK recruited Julie Andem to create a teen drama – it was in order to perform a public service by creating a text that was relevant to the new generation of Norwegian girls. This show not only wanted to represent the Norwegian youth and their issues, but also provides a platform for teens to gain guidance and empathy – a more subtle and nuance PSA.

NRK and Andem’s the new drama concept was set to target the specific needs of 16-year-old Norwegian girls—‘the two years before you turn eighteen, a new time at high school and the pre-adult, sexual age’. Where teen dramas are usually written by 30+ year old writers and produced by 40+ year old executives of networks trying to sound like ‘the teens’ and bring issues that they think teens go through. This can be seen in shows where teens are delivering lines with cringy ‘slang’ or outdated references, and their usage of social media is depicted as obsessive or narcissistic through the lens of a parent rather than an exploration of emotion and identity by the youth. Andem was able to see this distance that she may have with ‘today’s youth’ and believed she couldn’t tell their story, because it was there’s – therefore she needed to hear it from them. This led to an extensive audience research, where Andem and her team orchestrated 50 in-depth interviews with Norwegian teens from all over the country, 200 speed interviews, school visits, social media scanning, and readings of reports and statistic on teen culture. In her interviews Andem talks about the large impact these interviews and research had on her creative process.

Through this extensive audience research a common factor was discovered amongst teens and that was pressure. It was discovered that Norwegian teens experienced a lot of pressure and this became the driving force for the creation of the drama. The team wanted to address and explore this aspect of teen life and even formulated a ‘mission statement’ which defined SKAM’s vision: to ‘help 16-year-old girls to strengthen their self-esteem by breaking taboos, make them aware of interpersonal mechanisms and demonstrate the rewards of confronting fear’ (Furevold-Boland, 2016). So, NRK is interested to provide a public service to the Norwegian youth by clearly representing them and their issues in a realistic and authentic way. They aim to do this through Andem’s creative judgments and extensive research. The team has not gained an understanding of Norwegian teens and the usage and importance of social media, but had also generated a specific target audience and a thesis statement that will run throughout the series. However, this is not the end of their innovated production towards realism.
Making Skam

The great appeal of Skam, along with many others, is how realistic and genuine the stories and characters feel. This can be attributed to the aforementioned research that the team had conducted which allowed for clear and real depiction of the hardships and struggles that today’s teen face. Another attribution the contributed to the authentic and realistic feel and tone of the show, it is argued, is the inclusion of actual location and age-appropriate non-professional actors. As mentioned earlier, teen shows usually have twenty somethings playing teens. This is usually due to child labour laws in the United States and other countries. This may seem like tiny complaint; ‘This is so unrealistic, that 16-year-old is clearly 21. I can’t believe anything after this’. However, this casting choice not only has an impact on the story, but also on how it affects teens watching the series.

Clinical psychologist, Barbara Greenberg, stated that by casting actors in their 20s in teen dramas have the message to actual teen audiences that this is what a teen is supposed to look like. A person in their 20s is more likely to have a consistent appearance, whereas an adolescent may change more frequently. “Some days they’re thinner, they’re a little heavier, they have pimples, their hair is a little frizzy. It’s all ok,” Greenberg says. So, theses teen actors in a studio high-school don’t share these symptoms of a teen body, it therefore then makes the teen viewer vulnerable to feeling self-conscious and depressed about their appearance. “That leads to all kinds of body-image and social-comparison issues,” Greenberg says. So already we have a disconnect between the actor, the teen character, and the teen audience. This casting choice also has effect on the way stories/plots are presented and viewed. When you have storyline where a child is in sexual relation with an adult and both parties are played by consenting age adults, the story is not as creepy or unsettling as it should be presented, but rather it is seen as ‘forbidden love’ and sexy. For example, in Pretty Little Liar where a 15/16-year-old teen girl is having a relationship with her male teacher, in reality the actors as 21 and 24 respectively. The casting choice not only eliminates the reality of the age difference, through mere contrast that would occur between a teen girl and a male adult, but also normalises that age difference.

So, how does Skam not only differ and but excel? Most of the actors, when shooting the first season were in their teens. A plot point in the first season is that the girls are encourage to hook up 97er boys – as in boys in their high school that were born in 1997. When the female lead states that she has a boyfriend, she is encouraged to dump him because he is a 99er (born in 1999). What is compelling is the actors are of that age – her boyfriend is born in 1999 and the boys that are 97ers are actually born in 1997. This may bot seem crucial, however, watching the series set in a highschool with people that are teens and born in the same year as the teen watching, does have a psychology and subconscious effect that resonates with the audience.

As mentioned before the show was aimed at specific demographic, therefore it is important to show version of teens that they have seen (classmates, friends, etc.) or are versions of themselves. In teen shows, one often sees the glamourous queen bee in a one-of-a-kind coutour outfit strutting through the halls of her elite high school with her encourage, in coordinating outfits, behind her. However, the audience member watching this exhibit is viewing this on the laptop in their casual tee and sweats on their bed while eating dinner. There is a contrast between the teen on the screen and the teen viewing a representation of themselves – one cannot see themselves as the ‘queen bee’ figure nor can one see this hero figure as a person in the real world. Neorealist filmmakers despised the ‘hero’ figure as they excluded millions and allowed an inferiority complex to resonate with the audience. Realists desired to create inclusion, rather than exclusion, by depicting the ‘everyday’ man, them and others, as the protagonist of life - “to strengthen everyone, and to give everyone the proper awareness of a human being”. This is similar to the thesis the Skam team set up to prove – ‘help 16-year-old girls to strengthen their self-esteem by breaking taboos, make them aware of interpersonal mechanisms and demonstrate the rewards of confronting fear’. Both forms, therefore, asked their actors not to be skilled at acting, but to understand themselves as human beings - asking them not to ‘act’ like an actor, but to react as themselves. A desire to capture the gestures and motions that belonged to this particular person, not one of the many false exaggerations that could be conjured by an actor. This style is evident in Skam as Andem would encourage her actors to play around in the scene and put pieces of them into the character.

In this behind the scenes clip, the actor Tarjei Sandvik Moe is supposed to walk out and see a returning character who the cast has not seen for months. He is supposed be shocked and surprised, but it doesn’t feel authentic. Tarji states that he, as Tarji, would have said something, and Andem is heard behind the camera encourages him to say something then. In the final cut, Isak, Tarjei’s character, says the name of the returning character. This shows the Skam team’s desire to be authentic, realistic, and genuine in their depiction of teen reality. These naturalistic and geniue traits not only make audience see these non-professionals as people behaving like people, rather than glamorised actors acting like fictional characters, but allows for the opportunity for audience to also see themselves in the characters’ flaws and desires. Part of the show’s authenticity comes from its actors: They’re roughly the same age as their characters, have minimal performing experience, and wear little or no makeup to cover their youthful blemishes. We see them with breakouts of acne, similar to millions of teens that grow through this customary process as teenagers. The actors naturalistic look (through minimal makeup) and acting style that one can believe they could encountered a, or many, Isak(s) (or other characters) somewhere in their world.

Skam is filmed at Hartvig Nissen School. This is not only an actual running established school, but also a school which some of the cast have attended as students. The school is not only used as an exterior, for establishing shots and then filmed in a studio, but also interior – using classrooms, hallways, etc. Character’s apartments and homes are actual locations, rather than stages in studios. Again, this allows for the series and characters to feel real - these are homes, not sets. Therefore, it has been demonstrated how the Skam team’s mission, to obtain and represent the reality of teens, has been executed through the use of research methods and elements of film realism; however, Skam is innovative in their methods and goes beyond what had been used previous in 20th century media/mediums. Skam engages its audience through the medium that they (the audience) is accustom, whist also transforming their (Skam team’s) television media through transmedia storytelling.
Releasing Skam
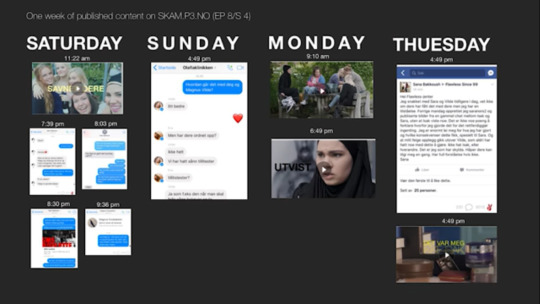
Obviously, there is an issue many television broadcasting corporations are facing today, which is the abandonment of traditional television viewing. Audiences are now watching on demand and not ‘live-watching’ or schedule watching their television programs. Audiences, as corporations like NRK understand, like not only to be in control of when they view media but how. At the time, NRK was noticing the shift in their audience viewing habits. Therefore, there is no point for the Skam team to conform to traditional television viewing standards to a target demographic that is constantly using on-demand viewing to consume their content. The shift towards on-demand viewing is not new to television networks. Many services are providing on-demand viewing experience through binge-watching episodes. The notion for network to provide episodes online is not innovative, in fact it conforming to the norm. However, Skam chooses not to conform norm or previous conventional methods of television viewing, but instead uses new media and mediums to reach their goal for authenticity and realism. The aim of the research was both to gain in-depth information on Norwegian teens, in order to portray them in a relevant and realistic way, but also to identify and discover how the new online drama concept could serve the needs of this particular audience segment. As previously mentioned, there are several standards that directors and creators used to project reality – whether that be through long takes, deep focus, limited editing, and use of actual locations non-professional. The Skam team stated that, ‘we want to provide popular enlightenment but in a context the audience segment understood and liked’. Skam includes other elements in order to create realism an audience connection to the characters through the use of transmedia narrative and real-time release.

Skam released the scenes to their episodes in real time. For example, if the characters are having a conversation at school, during lunch time, the scene would be dropped at 12:15pm on Monday – with a title card stating the day and time. And if during that conversation they discuss meeting later that day at 9pm, the scene would end and at maybe 9:30pm – again scene is introduced with title card stating time and day – the characters will meet and a character could apologise for being late. This mini-clips and scene would be released throughout the week, without informing the audience when they would be released, with a compilation of the scenes being released to a traditional episode on Sunday. Why is this method not only innovate, but also essential for Skam and its thesis statement? As mentioned previously about the teen who is in their bed wearing a causal tee and sweats on their bed with their laptop and viewing a glamourous queen bee in a one-of-a-kind coutour outfit strutting through the halls of her elite high school – the teen audience is so distant from the image on the screen to their reality.

Skam, however, closes this distant, not only through non-professional actors and location, but also through real time. The teen audience viewing the clip posted, before going to they go to bed, is watching the character doing the same thing the audience is doing this time of the week. If it is a weekday, the character is in their sweats watching videos while eating their dinner – something the audience is most likely doing. If it is a public holiday, characters are spending time with friends and family – much like the audience is. This creates a sense of temporal realism, reality given to the audience by a shared temporal (time) space. These characters are living and experience life in the same temporal space as the audience. Clips that are released on New Year’s Eve is obviously a great way for the show to demonstrate this – bring in the new year with characters and audience members in a shared temporal space. The show uses real time release in so many ways. For cliffhangers, a character is distress in the last clip and then a clip doesn’t appear for hours/days – what is going on? If a big even was to happen, audiences would wait for the day, and time, like the characters would – both characters are experiencing same anxiety and excitement of the events transpiring. Audiences are waiting for a clip – that they may not know when will come and how long it would be – throughout the week. However, while waiting, they may also look through social media to find solace.
The Skam team also created social media accounts for their characters, not actors, but the characters. The ‘characters’ would post pictures and messages – as any teen would today. Not only that, but the audience was also privy to the private messages exchanged between characters. This allows audiences into the lives of the characters and makes these fictional characters feel more real and like a friend to the audience. By using both these private messages and social posts, Skam was able to tell a transmedia narrative. A transmedia narrative (also known as transmedia storytelling or multiplatform storytelling) is telling a single narrative or story experience across multiple platforms and formats using current digital technologies. The most common example is MCU – where they told a story through not only several film, but also television series. The texts have used transmedia storytelling, such as Doctor Who (the tv series, spin offs, books, big finish, movie, etc), The Lizze Bennett Diaries (social media for characters, web series, spin offs, etc), and more. The audience isn’t required to explore beyond the main text (the tv show or movie) to subsidiary texts (web series, books, social media), however those who do interact with the transmedia narrative, and fan culture, are able to gain a deeper understanding of the show/characters and are given Easter eggs.
For example, in Season 1 a character on Skam, Eva, posted on Instagram a photo stating that her boyfriend, Jonas, made her nachos and shows the Fresh Prince of Bel Air title card. This seem arbitrary and irrelevant to the main plot of Season 1, however in Season 4 in the final episode when Eva’s new suitor texts her ex Jonas for advice, Jonas tells him just ask her to watch Fresh Prince and eat nachos. There was no need for a ‘call back’ to a social media post from Season 1, but by doing this Skam was able to utilise not only digitial storytelling, but also transmedia storytelling.
Realism and Belonging

So, while other teen dramas try to depict a grand and fantastical allusion of teen life, Skam rejects that and offers a realistic depiction through its creating, making and releasing process – but how does the series represent, through realism, belonging. Each season of the series focus on a central character. There is a core set of characters at the school, but each season focuses on one character – we see the narrative through their eyes – and their journey. Season topics include identity and loneliness, feminism and sexual assault, sexuality and mental health, and religious beliefs and online bullying. These were inspired by the interviews conducted in the research and relevant to teens whilst growing up in today’s society. The main character is faced with these real issues – they struggle alone with the burden of these topics and are able to finally resolve them with the help of friends and professionals. Skam is excellent in depicting the importance of a strong group of people who will listen to your issues, accept you, and guide you to find the answers. The show does not aim to solve a murder mystery or decide which boy the girl should go to prom with – it aims to show how others are also struggling with the issues you have, how others can and will accept you, and how you can also find the answers. The show’s thesis and mission statement is to ‘help 16-year-old girls to strengthen their self-esteem by breaking taboos, make them aware of interpersonal mechanisms and demonstrate the rewards of confronting fear’ The show tackles real issues (through creating) by creating real characters (through making) and allowing audience to engage with them on an intimate and personal level (through releasing).

In conclusion, through its creating (thesis statement and research), making (non-professional actors and location), and releasing (live release and transmedia narrative), the series Skam is an example of an ideal teen drama that depicts emotional growth and belonging for its audience. Rejecting the fantastical and embracing realism, through the use of extensive research, authentic acting and location, and digital and transmedia storytelling, Skam is able to depict teenagers in a genuine and realistic manner. Skam is a television series that should be analysed and evaluated in a critical context, and not be seen as a mere ‘teen-drama’. The series provides ample opportunities to be praised for its innovation, creativity, and uniqueness. Other teen dramas should not submit to the underachieving standards of what it is to be a teen drama, but instead realise what the true purpose of a teen drama is and rise to the occasion to creating something new, powerful, and meaningful.
12 notes
·
View notes
Text
Range of Managed Services And Security Systems
The strategic practices of outsourcing Information Technology management responsibilities on a everyday foundation for enhancing operations are called assist managed services. The company or people who have direct authority of the gadget and are in need of such services are known as a purchaser. On the other hand the enterprise or person who presents with the support controlled services is referred to as the carrier company. Applications, transportation, databases, data services, communication offerings, enterprise-to-business campaigns are some commonplace services provided by such agencies.
A standard Information Technology carrier provider, who manages and takes all of the obligations proactively or consistent with their customer's want, is a controlled provider company, it manages staffing companies and additionally measures the effectiveness while filling positions. Most controlled service companies use Vendor Management System software tool for imparting performance and transparency with designated metrics.United security services in orange county
Video cameras which can be used to reveal an area or constructing remotely are referred to as surveillance cameras. Surveillance digicam device is frequently used in the military, in purchasing shops or in any limited areas. In that machine, pix are recorded and send to a relevant control room in order that a selected area may be remotely monitored. Closed-circuit televisions, normally called Security are used for surveillance digital camera device.
Surveillance cameras are actually set up in maximum of the general public locations, places of work and additionally at site visitors factors to display any illegal and unlawful sports. It cannot be stated that the cameras can positioned a prevent to those kinds of sports but they surely positioned psychological strain at the criminals and act as deterrents. Now with the upward push in crime prices it has grow to be a should to put in these cameras even at home to shield yourself and your households. But before buying one have to find approximately them and purchase one to fit your requirements and price range. Installation of the cameras in proper place is vital for better results and so that you can use a expert organisation to present you a entire package of safety.
These cameras are not so reasonably-priced however if safety is considered then the general fee may be very low. One can without problems installation those cameras of their desired vicinity. All you want is a technician who can install it efficaciously. You can inform them approximately your preferred region and they will installation the cameras there. Nowadays, everyone wants to feel secure and for this purpose these cameras are the nice option.
Surveillance systems can be used at domestic as well. Home is wherein absolutely everyone feels cozy and it's far disgusting whilst that privateness is on occasion compromised. If that is what you don't need then it is time to shop for a surveillance gadget. Security systems shield your property whilst intruders attempt to invade your private home. 2-camera to sixteen-camera systems are to be had that can save pictures for weeks. Digital video recorders are a complicated shape of Security that could preserve recordings for many years. They additionally include extra functions inclusive of electronic mail alerts and movement-detection.
Some global uses of CCTVs -
Crime prevention - Surveillance structures are best in parking plenty and feature led to a lower of crime by using fifty one%. In a financial institution or shop robbery also CCTV cameras are extraordinarily helpful in identifying the thief.
Traffic tracking - One of the most vital utilization of CCTV cameras are for tracking traffic. Most metropolitan towns have substantial traffic networks. Surveillance structures help detecting injuries and congestion.
1 note
·
View note
Text
What is Kik?

Kik is a mobile messaging program which could be employed on both iPhone plus android. The favorite app that is free to use is akin to Whatsapp and Viber but has a few extra features that differentiate it. For instance, an internal web browser, which means consumers are urged to spend much more period inside the app.
The app was in the media recently, in case your kid has a Kik bank account, caution must be taken.
The primary tasks of Kik are:
One to just one chatting Send messages, gifs, pictures, videos, and more.
Group chat (with as much as forty nine other users)
Anonymous chat Promoted Chats allow users to watch and chat with various models in music, amusement and other things. Owners are going to know a promoted account by the Green Star beside the profile of theirs.
Will be there any restrictions?
UPDATE: The Digital Age of Consent in Ireland is established at sixteen years of age. In case you're under sixteen, you have to have consent of a parent or maybe guardian to use providers like social media networks.
If your kid is under sixteen and has created a Kik bank account, the messaging app motivates parents to post a deactivation demand by contacting supportkik.com. Note: Make use of the subject line Parent Inquiry' and also add your child's Kik username as well as years in the sales message of yours. Note: The app presently has an age score of seventeen on the app store.
Who can my kid speak with?
The app enables users to connect with folks in their telephone book/contact list that currently have a Kik bank account. This solution may additionally be switched off by visiting settings > chat options > and also turning off of address book matching. By switching off of address book matching, the kid of yours will only speak with individuals that know the username of theirs.
Your username is the identity of yours on Kik. This includes details as email address or maybe phone number are not made public on the app. In order to include someone as being a relationship on Kik, you have to understand the username of theirs. The app recommends consumers choose a username that's difficult to guess, this can help minimise contact from people or strangers that the kid of yours might not know or even wish to speak to. If your teenager is making use of the app encourage them never to talk about the username of theirs on additional open social networks for instance on Twitter.
Other highlights? The Kik Browser
Kik messenger additionally has bodily apps through its internet browser helping owners to stay within the app itself. These internal apps include stickers apps, meme generators, games and dating style apps which enable subscribers to chat with brand new connections which might be regarding for parents.
2 such apps are Chat and Match and Flirt! Match & Chat operates in a similar approach to Tinder, matching owners by ages, gender etc. What's worrying about Chat and Match is the simplicity with which a person is able to chat to others owners of any age they need. For instance users are able to choose to chat to teenagers users, owners in their 20's,30's etc.
The Flirt! App also offered over the Kik browser provides owners with a summary of new people within their age range to chat to. Once again, users could pretend to be another person, give a diverse era all over their Kik account etc. We wouldn't suggest either of these apps for teenagers. If your kid is on Kik, extreme care has to be used particularly about the above apps.
App Purchases
You will find stickers readily available to buy on the Kik app, however owners need to have a charge card related to their Google Play or maybe iTunes account to create a purchase.
What exactly are the chances?
Along with the possible risks from utilizing Kik's internal dating style apps, you will find certain more basic things and also risks to look out for. These are cyber bullying, sharing or perhaps having content that is inappropriate and talking with strangers and that is really simple to complete on the Kik app. To help you stay away from these issues, the exact same rules should pertain to other internet interactions for people that are young; only share info with people who you trust in life that is real, block/report unwanted connections, feel before you press & report some inappropriate communications or data to a trusted person.
Obstructing Users
In order to block somebody you do not wish to speak to on Kik: Tap Settings.
Select Chat Settings (on the iPhone of yours and Android Privacy or) (on the Windows Phone of yours, BlackBerry or Symbian) Select Block List.
Tap
Select the individual you wish to block.
Tap Block to confirm
Alternatively you are able to often go to the profile of theirs, click the icon within the best right hand corner, the choice to block them will likely then show up. Users that have been blocked won't realize they've been blocked. If your kid is in a team with someone they've blocked, any communications which look in that number from someone will appear as ***Blocked Message***.
Find more information Kik shut down
youtube
1 note
·
View note
Text
How Best To Rip 1,500 Music CDs? Your Tech Questions Answered
Free FLAC to MP3 Converter is a light-weight and unobtrusive app that converts FLAC files to the MP3 format. With Freemake instrument, you can too mix an enormous file divided into components into one music track. Add elements of your media into the app and enable the Be part of files" possibility in the prime right nook. Then convert the tune in a regular approach. Along with simply listening to the music output from every of these phones, we also had to get some exact figures to see how these telephones stacked up towards one another. To try this, we hooked the telephones up to FuzzMeasure on an iMac by running them by a Focusrite Scarlett 18i20 The Focusrite Scarlett is capable of processing and breaking down the very best high quality audio playback from all the devices, and FuzzMeasure gave us readings on these measurements.
In case you have any questions or know some other technique to convert flac to mp3, tell us within the comments beneath. With CoolUtilis you'll import quite a few WMA information out of your laptop computer, Dropbox or Google Drive and convert them to MP3 format. The app options an intuitive GUI, flac2mp3 home windows with drag-and-drop help being provided in case you do not need to decide on your FLAC recordsdata utilizing the Add" button. Tips about find out how to Convert FLAC to WAV and Vice Versa. After you will have ready your guidelines of audio info to bear the conversion, it's essential to point out the output format.
A new music streaming app with official albums, playlists, and extra. As far as FLAC over MP3, truthfully what you do not know will not harm you. Should you're pleased with the sound by way of an mp3 and you are not an audiophile, just benefit from the music as it is. It is a LOT of labor to re-rip every CD you personal and takes numerous storage space to store FLAC so I would say do not hassle until you actually care. Step 2: Choose a neighborhood FLAC file after opening the Browse to upload it. Or you may insert the URL of the FLAC if it hasn't been downloaded in your computer.
Whereas it's a quite blast listening to it in your pc there's only a handful of purposes that permit for FLAC playback on cellular devices. And even if you are lucky sufficient to have FLAC-friendly cellular machine music player then you still need to bear in mind your storage capability. Flac recordsdata, as a result of that amazing bitrate they cary take an infinite quantity hard drive space. Generally you might have to convert FLAC to MP3 instantly however you do not want to set up any application on your Mac. What you are able to do is put your faith in a web-based FLAC to MP3 converter. On-line converter may be very handy when you've gotten a steady and quick network connection. All you could do is add your FLAC file, select the output format and high quality, convert FLAC to MP3, and obtain the resulting file.

All Free FLAC to MP3 Converter to darmowy program umożliwiający konwertowanie utworów zapisanych jako FLAC do formatu MP3. FLAC needs to be created from an excellent source like a grasp or tremendous audio CD to sound good. Using the identical app you can too convert wma to mp3 amongst many different supported audio formats, together with MPC, APE, WV, FLAC, OGG, WMA, AIFF, WAV, and others. It's an excellent utility to have around on the Mac for converting audio recordsdata, and provided that it is free and quick, it's hard to beat.
For conversion, add the FLAC file(s) that you have to convert, select the output folder, then start the encoding course of. Transcoding is a horrible thought. This is the very reason that I ran screaming in terror from Google Play Music. Transcoding a lossy-compressed format to another lossy-compressed format seems like rubbish. If that is what's happening with Spotify Join and Chromecast, I feel I will reconnect my AirPort Specific. Probably you may be utilizing a compressed or uncompressed lossless format like PCM Audio, WAV, AIFF, FLAC, ALAC, or APE. An uncompressed PCM audio file is about 10 times greater than a CD quality MP3 file.
With any of those apps, you'll must manually switch the information to your iOS machine. Connect the gadget to your Mac, launch iTunes, and choose the gadget in iTunes's supply list on the left. Click the Apps tab and scroll all the way down to the File Sharing part. Click on the app you want to use, and drag your music information into the documents record to the best (or click on the Add button to decide on the recordsdata through the Finder). Your information will transfer instantly, and it is best to have the ability to play them by your chosen app on your iOS device. (They won't appear in the usual Music app.) Alternatively, you can stash recordsdata in Dropbox and then select to open them in an app equivalent to VLC, though it's a must to obtain and open every monitor individually.
The FLAC file format related to theflac filename extension refers back to the FLAC audio encoding algorithm. FLAC is the acronym for Free Lossless Audio Codec. The algorithm is from the lossless audio compression household of codecs for flac2mp3 digital audio compression. It was developed by the foundation, a non-revenue organization that produces open and free to make use of multimedia codecs, and had its preliminary launch in 2001. Though there isn't widespread compatibility for the format as in comparison with related codecs akin to MP3, the FLAC format enjoys some compatibility and support with in automobile and home stereo manufacturers as effectively audio playback software and transportable audio gadgets.

FLAC is the format that offers a pleasant compromise between the massive dimension but excellent high quality" of uncompressed music files and small however lower than glorious" compressed MP3 or AAC recordsdata. There should be no distinction audibly between a lossless format like FLAC and an uncompressed format like AIFF. Plus you get the good thing about a decrease storage requirement, someplace between 30 and 40% much less on avaerage. A FLAC file is a Free Lossless Audio Codec file. It wont bring any sound high quality loss when compressing, however can reduce the file measurement to round half of its original size. At the moment, flac files are the preferred lossless audio recordsdata, and supported by numerous media gamers. AnyBurn can burn Audio CD from flac information.

Best of all, it may well edit and convert a spread of audio formats, together with WAV, AIFF, FLAC, MP3, and Ogg Vorbis. For those who're looking to convert analog to digital, or convert between numerous digital codecs, that is the way in which to go. Obtain and install an application that may convert FLAC recordsdata to MP3 using the LAME code. Examples embody Audacity, Foobar 2000 and EnLAMEr (see Sources). CRC checksums are used for identifying corrupted frames when utilized in a streaming protocol. The file also features a complete MD5 hash of the uncooked PCM audio in its STREAMINFO metadata header. FLAC permits for a Rice parameter between 0 and sixteen.
1 note
·
View note
Text
Convert FLAC To WMA Audio Information Online And For Free!
Learn how to convert FLAC to WMA online with FLAC to WMA Converter? DVDVideoSoft's Free Audio Converter is a lossless FLAC audio converter supporting various lossless audio formats together with FLAC (Free Lossless Audio Codec), WAV (Windows PCM), milesggr34646.mobie.in ALAC (Apple Lossless Audio Codec) and WMA Lossless (Windows Media Audio Lossless). This FLAC converter caters to MP3 high quality most so that it gets assist from the MP3 LAME Encoder presets: INSANE and EXTREME when changing audio files. With this FLAC audio converter, you enjoy audio music with various codecs with no penny.
I've over 1500 CDs that I've ripped to FLAC and WMA. I ran an experiment and ripped just a few CDs to WAV format instead and located that they sound significantly better than the FLAC or WMA versions. I believe my network participant has hassle unpacking and taking part in tracks due to CPU limitations, while it has a better time simply playing thewav file as an alternative.
Affordability - the price of making use of this converter shouldn't be going to price you much. That is the reason why lots of people who need nice and wonderful conversion from FLAC To MP3 are at all times coming for our product. You get no hidden prices or cookies which will have an effect on you once you start making use of the product here. To convert media recordsdata tomp3 format simply choose the vacation spot folder and flac2wma drop your files or folders to the app's icon or interface. Converter advises when processing is made and if there are any failures. Convert utility is crash free".
If want more superior choices, MediaHuman Audio Converter does let you customise things like the default output folder, whether you want to automatically add the transformed songs to iTunes, and if you wish to search online for cover artwork, among different choices. or, it could merely be convinient to have all your music in ONE lossless format. CNET explains what FLAC is, the place to purchase music in the format, and how you can play it in your cellphone, pc or hi-fi.
2. Click "Add" to add the musical files you want to burn. Please make it possible for the added information will not exceed the disc capacity. In spite of everything recordsdata has been added, click "Subsequent". I used to be offered a invoice of products that it had a mp3 player, but what they did not tell me that once I however the (additional) media necessities package, that includes a cable and a CD with drivers on it was that while you ship an MP3 to the telephone it mechanically converts it to WMA by the drivers, then sends it to the phone.
Considered one of essential VOX options is the limitless music cloud storage. It is an unique cloud storage just for VOX users. Its main objective is to retailer and stream your music. What differs it from different music lockers is that VOX Storage has no restrictions on audio formats and information' size. You'll be able to add there as a lot music as you wish. The best half is that unlike other storages VOX Cloud won't convert anything to MP3 or another lossy format. Hi-Res retains Hello-Res.
Ripping to WAV will provide you with what's on your audio CD, two channels (or separate recordings, often left and right for stereo) of LPCM digital audio sampled at 44,100 cycles per second (hertz), with 16 bits (the ones and zeros) for every sample. This adds up shortly, 44,100 X sixteen = 705,600 bits per second to be precise. That is still a lot, even by at present's requirements. I need my huge music to sound pretty much as good as attainable, but if I'm not loosing something by storing it in a barely extra difficult container, then I'm not loosing anything, just gaining some complication, and a few digital cupboard space.
This methodology helps to play all types of FLAC audio file whatever it's 16-bit or 24-bit and wherever it comes from like from Pristine. FLAC is a lossless audio file format. It is similar to MP3 format however the main difference between these 2 codecs is FLAC file compress the file size without altering the quality of audio. It could actually compress an audio file up to half of its original measurement using lossless compression algorithm.We solely examined audio converter software that was suitable with the most popular video formats. Nonetheless, in the event you plan to make use of conversion software program primarily for converting video information and occasionally for converting audio, buy a video converter software as an alternative. In addition to video format compatibility, the best video converter programs are additionally suitable with most the favored audio codecs. Here are a couple of our favorites.For better enjoying FLAC (or film files) on your portable media devices, you're supplied with an array of common multimedia gargets with default settings that you do not have to drive mad for the ambiguous output settings. It is protected to say, no other audio program converts extra multi-format audio information than dBpoweramp, now we have spent 15 years perfecting format-compatibility and conversion stability. If converting FLAC to mp3, wma to mp3, or wav to mp3, dBpoweramp is the fitting selection.
1 note
·
View note
Text
CDA To AAC
Important Attributes of Audio Converter Software program Import and Export Codecs Will probably be vital for an audio converter to have the ability to importing all accessible audio codecs and convert cda files to mp4 free changing them to a format it is best to utilize. An instance is once you convert cda to mp3 online a music in MP3 format (a compressed format) to AIFF (an uncompressed format). The tune takes up reasonably extra space on your exhausting disk, however sounds the similar because the compressed file. This free Video to MP3 converter is suitable with various web browsers along with Google Chrome, Safari, FireFox, Opera and lots of others on both Home windows and Mac programs. It allows prospects to transform any online movies or different streaming media content material from websites harking back to YouTube, Dailymotion, Vimeo, Ustream to MP3 format.
Convert music to MP3, FLAC, convert cda files to mp4 free AAC, Opus, Apple Lossless, Vorbis and lots of more audio formats. Convert audio from 50+ file codecs. Rip audio CDs in excellent digital quality. Batch convert many audio files at once. Burn audio CDs. That is the very best app among the many 5 prime conversion instruments featured in this article which is able to assist you to do video advertising and marketing This is given that it means that you can download and convert your YouTube video information into the MP3 format rapidly and simply. It not only makes your downloading and converting tasks simply and rapidly from YouTube, but it gives the identical superior performance while you convert your movies from other web sites, comparable to Dailymotion and Vimeo, as nicely.
So what are you able to do when you've got files in one in all these codecs and want to add them to iTunes? There are a selection of packages that may convert audio files from one format to a different. tmkk's free XLD is my instrument of choice, as it manages each audio file format I've ever come throughout, together with some I've never heard of, and even helps cue information. Stephen Sales space's free Max is another software that converts many audio file formats. And when you've got Roxio's Toast 11 Titanium (and a few earlier variations), you possibly can convert from FLAC or Ogg Vorbis to iTunes-pleasant formats.
Select MP3 because the output format you need to convert MP4 file(s) to. Please, e mail to sup.amvidia@ about any issues or feature requests. We are going to try to reply your question within 24 hours. In case you like To MP3 Converter Free, a evaluate at the App Retailer would be very appreciated. Online CDA to MP3 converter requires community to convert CDA to MP3, while Format Manufacturing facility and Leawo Music Recorder need you to download and install these software program. After installing, they do not want you to convert CDA to MP3 within the situation of community. Thus you need not worry your converting process will cancel for the sake of the network.
My Mp4 to Mp3 Converter is the simplest and best technique to transform a mp4 file right into a mp3 file. All it's worthwhile to do is to select the file and faucet on "Convert" button. Our MP4 converter can convert from over 50 supply codecs for instance: MPEG-2 to MP4, MKV to MP4, AVI to MP4, MOV to MP4, 3GP to MP4, FLV to MP4 and far more. Simply attempt it out. Additionally, make sure that the file ends with theMP4 extension. Click on on the Save button to proceed. Again on the Convert display screen, inside the Settings part, click on the drop-down menu within the "Profile" part and select the Video - H.264 + MP3 (MP4) profile from the guidelines.
Click on Continue. It is a green button on the bottom of the information page. Your video will begin changing into an MP3 file. After the conversion finishes, click on Obtain" button to download transformed MP3 audio file. Oxelon Media Converter is very easy to use. Either load up a file from the program window or proper-click on any video file on your pc and select to convert it from the right-click context menu. An MP3 CD is a INFORMATION CD which accommodates music saved in one or more (usually many) MP3 files.
When you have several MPG movies in your Mac and you wish to combine them and export a continuous video, just test "Merge" button beneath the mission space. is your free video downloader and converter! Save movies from YouTube and other platforms to look at them in your smartphone, notebook, iPhone, PlayStation, offline or on nearly every other device. With this online video obtain software you do not have to install any program in your laptop. Free obtain CDA to MP3 Converter ( for Windows , for Mac ). Set up and launch this system.
It could possibly convert (rip) audio from CDs to various audio recordsdata or convert cda files to mp4 free music files from one type to a different and extract audio from video recordsdata to different audio you will have your digital audio tracks saved in your most well-liked format, it's easy to load them to your favourite audio player (e.g. a transportable MP3 player corresponding to an Apple iPod, Inventive Zen Player or Sony Walkman). Step 4: Now on the left aspect select the Icon to your Audio CD. Proper click on it and then click on Rip CD to library. You may the select the person tracks if you happen to like.
Freedsound - a completely free service to transform YouTube movies to mp3 and mp4 for offline use. Please use the DMCA page to signal any copyright violation and we are going to promptly verify and take away the contents. Obtain and then convert cda video to another format you need to your units in a single click on. Whenever you start off you may not know find out how to convert mp4 to mp3, however by the point you are completed you will become an knowledgeable. The Complete Audio Converter additionally lets you modify all audio options including quality and channel mode.Total Audio Converter is a simple-to-use device conversion software with assist for a bunch of codecs and skill to rip audio CDs. Convert mp3, m4a (iTunes & iPod), WMA, WAV, AIFF, AAC, FLAC, Apple Lossless (ALAC) to name a few. This software can rip recordsdata from CDs, DVDs and moreover kind virtually all media and video sharing platforms to any selected format. Similar to Change, Xilisoft enables you to extract audio from video recordsdata. Among the supported video file codecs embrace MP4, MOV, M4V, MKV, AVC, AVI, WMV, among others. This converter is compatible with 18 completely different file codecs and is capable of changing information to sixteen different output formats. Xilisoft is without doubt one of the most versatile audio converter software program in our lineup.
1 note
·
View note
Text
Return To Hogwarts - Chapter One
Lizzie had been doing paranormal investigations with the Ghost Adventures crew for sixth months. Recently she decided to leave the Men of Letters Bunker, and her two friends, Sam and Dean, and travel with Zak Bagans and the crew instead.
Lizzie was also in a committed yet private relationship with Zak. The only ones who knew they were together were Aaron, Billy, and Jay, their fellow investigators, and Lizzie had recently moved in with Zak.
One day, Lizzie was sitting on the couch, reading a book, Zak’s border collie Gracie was lying next to her, as Lizzie held her book in one hand and was scratching Gracie’s ear with the other. A moment later Zak came in, carrying an armful of mail.
“Hey, babe,” said Lizzie, as Zak walked over and kissed her. “Hey, sweetie,” he said, rifling through the mail.
A moment later, Zak handed Lizzie an envelope addressed in green ink, and sealed with purple wax. “Um, here’s something for you, it looks like it’s from Hogwarts,”
Lizzie’s face darkened. Ever since she was raped at the tender age of sixteen, the school had done nothing to help her, and spend an ungodly amount of time protecting her attacker rather than her.
Zak knew that his girlfriend had been assaulted, but he only knew a very minute amount of information, short of re-traumatizing his new girlfriend.
“Burn it,” said Lizzie bitterly. “It’s marked ‘urgent’” said Zak.
Lizzie sighed as she stopped scratching Gracie’s ear and took the envelope. Gracie whined as she lifted her head as Lizzie tore the envelope and unfolded the parchment.
Dear Miss Blaszczak
I wasn’t certain who to inform, but after hearing that you were traveling with the Ghost Adventures Crew and remembering your history with them, I knew I had to send you this.
As I am sure you are aware, during the Battle of Hogwarts that eventually led to the fall of Lord Voldemort, there were tragically a large number of casualties. Not long after the renovation of the castle was completed, many students in all four Houses, and ages have reported paranormal activity around the castle. Everything from phantom footsteps to voices, to apparitions, people getting touched - you name it.
In addition to the renovation itself, we have made changes to accommodate Muggle technology. You will be able to use your cameras and digital devices without any issues. We have also recently added Wifi.
We also have created our own social network for students. I will give you the IP address should you need it for your investigation
Many students are terrified while others are intrigued. It would be very appreciated if you and the Crew could return to Hogwarts for a second investigation, and perhaps do a guest lecture.
Please return this letter at your earliest convenience
Yours Sincerely,
Professor Minerva McGonagall
Headmistress
Lizzie stared at the letter for a very long moment. “Everything okay?” Asked Zak. Lizzie handed Zak the letter. “Oh,” he said, reading it. “She - wants me to return to Hogwarts,” said Lizzie. “And you don’t want to?” Asked Zak
“I don’t know,” said Lizzie. “This is about what Cormac did isn’t it?” Asked Zak. Lizzie said nothing, but nodded.
Zak reached over and gently held Lizzie’s hand in his own and kissed it tenderly. “I know you’ve been through a lot, and I understand your resentment towards the school, but wouldn’t it be possible for you to put your emotions aside?” Lizzie said nothing.
The prospect of putting the trauma of being raped by a fellow student, and the school failing to protect her, behind her, was a very daunting and emotionally difficult thing for Zak to ask of her.
“Think of it like this,” said Zak. “Maybe Professor McGonagall is feeling guilty over not protecting you, and by asking you to come back, she’s asking for you to forgive her?” “I - I’d never thought of it like that,” said Lizzie. “Mm-hmm,” said Zak.
There was a very long moment of silence between the two paranormal investigators, only the sound of Gracie whining every now and then could be heard. After what seemed like forever, Lizzie finally sighed heavily, stood up from the couch and began to walk out of the room
“Where are you going?” Asked Zak. “To go pack my trunk,” said Lizzie. “Better call Aaron, Billy and Jay, tell them what’s up.” Zak nodded as Lizzie left the room.
Lizzie ascended the stairs of the house that she had moved into less than a year previously. Despite knowing Zak ever since she was sixteen - still a student at Hogwarts - they had maintained nothing more than a strong friendship for close to eleven years.
When Lizzie first met Zak she was in her sixth year at Hogwarts, thinking about how she was going to pass her N.E.W.Ts (or Nastily Exhausting Wizarding Tests), and looking forward to graduation. She had plans to attend college after leaving Hogwarts. By this point in her magical education, Lizzie had become quite the popular and promising student. She had a part time job at the popular pub the Three Broomsticks in the village of Hogsmeade, a large circle of friends, got near perfect grades, and her passion for riding horses had reignited after a tragic accident in her fourth year resulted in the death of her beloved horse, Raven, and she was appointed Captain of the Gryffindor equestrian team.
It all came to a screeching halt after she rejected the advances of a fellow Gryffindor Cormac McLaggen who had been runner up for Keeper during the Gryffindor Quidditch tryouts. Unable to handle this scalding rejection from Lizzie, Cormac set out on a brutal campaign to destroy Lizzie’s reputation, which culminated in one of the most emotionally traumatic events of Lizzie’s life.
Cormac and five of his friends had gang raped, and tortured Lizzie for over eight hours in the Gryffindor common room, branding her with cigarettes, forcing alcohol down her throat (though Lizzie almost never drank), and made her believe that she was going to die.
Lizzie was lucky to escape with her life, and though she had not passed her Apparition test, she packed her trunk, and Apparated out of the castle, out of Hogwarts, and out of England.
She ended up in Las Vegas, Nevada where she wandered the busy city strip for an hour before she finally ended up at Zak’s place.
It took a lot of coaxing, but after a gentle talking to, and a cup of good old English tea in her hands, Lizzie finally began to recall the horrifying details of her ordeal that she was lucky to survive from.
Zak then took Lizzie to the hospital where she was photographed and examined by doctors and nurses
As Lizzie began to pack her things in her old school trunk which had the initials E.S.B stamped on it in peeling letters, it was as if every item inside the dusty trunk, held some kind of memory: the scarlet with a gold jumping horse Capitan’s badge she used to wear when she was on the Gryffindor equestrian team, that after so many years, had become tarnished, and battered with age, the fake Horcrux locket that had taken place of the real one, An old photo album full of moving photographs of her and Raven, A torn letter from Oxford University offering Lizzie a full ride scholarship upon her graduation from Hogwarts, which was later revoked after stress from Cormac’s relentless harassment caused her grades to founder.
Her old school robes which were now three sizes too small, and had become frayed, Her team show coat, with the embroidered Gryffindor lion on the right side, faded and beginning to peel from the fabric, several gold buttons on the front and back of the coat were missing; a rolled up, tattered poster of the Ghost Adventures Crew that Zak had personally signed, A dusty copy of Training the Three-Day Horse and Rider, given to her by Professor Lupin during the early days of her equestrian career, and many other knick-knacks that had personal or sentimental value.
It seemed silly for Lizzie to keep everything, and she certainly wasn’t the hoarding type of person, but everything in her trunk had ties to when she was happy at Hogwarts, long before she met Cormac. She may not have actually been killed that night, but as she put it, “My life ended the day I met Cormac. He didn’t kill me, but he might as well have,”
As Lizzie continued to sort through her belongings, she came across a folded piece of paper. Upon reading its contents, Lizzie remembered it was an obituary that she had cut from the Daily Prophet, for her old Headmaster Albus Dumbledore, who sadly passed away just after Lizzie dropped out of Hogwarts.
Lizzie had mixed feelings about Dumbledore. She thought he was a great person, but she did feel resentful, because when she went to him begging for protection against Cormac, Dumbledore turned her away, and never once took what she said seriously.
Now, as Lizzie re-read the obituary in her hands, she felt a large lump in her throat and her chest constrict. This whole time, she thought he had known Dumbledore relatively well, not a well as her best friend, Harry Potter did, certainly, but well enough. Now she had to come to the rather excruciating realization that she didn’t know the man at all. And this broke her heart.
Lizzie gazed over at her bedside table to her iPhone which was charging on the table. It had been many years since she and Harry had spoken. In fact, the last time they saw each other, was during the Battle at Hogwarts which led to the downfall of Lord Voldemort. They had promised each other that they would stay in touch, and they had, exchanging a handful of letters back and forward, but they hadn’t talked face to face for nearly ten years.
Harry had to be in his late twenties now, like Lizzie, and must have a family of his own, surely. She had received an invitation to his and Ginny Weasley’s wedding, and to their delight, Lizzie attended. It was a beautiful ceremony. She had also attended Hermione and Ron’s wedding as well.
Although happy for her friends, Lizzie couldn’t help but feel a tiny bit of jealousy that she hadn’t taken the plunge herself. She had only been dating Zak for a few months, and he had given her a fair warning that the women in his life never stuck around due to the fact that Zak had more than one spirit attachment.
Though fifteen years his senior, Lizzie and Zak were closer than ever before. When they had first met, Lizzie had been nothing more than a fan of Zak’s. It seemed too good to be true that he would eventually want her to be his girlfriend.
Lizzie thought about this as she stared at her phone. She had Harry’s phone number, which they had exchanged after the Battle. She had Ron, and Hermione’s too. One phone call couldn’t hurt, Lizzie thought as she sat down on her bed, opened her phone with a special six-digit password, opened her contacts, and found Harry’s number. She touched it and held the phone to her ear.
The phone rang twice before a male voice answered. “Hello?” “Hi, Harry, it’s Lizzie,” said Lizzie. “Lizzie! Blimey! It’s been a while!” Said Harry. “Yeah, tell me about it, sorry it’s been so long, I’ve been - er - busy,” “Let me guess,” said Harry. “Investigating the paranormal? Locking yourself in haunted locations overnight?”
Lizzie smiled. “Yeah,” she said. “Professor McGonagall just sent me a letter. She wants me to investigate Hogwarts with Zak and the guys.” Harry sighed with amusement though Lizzie wasn’t fooled. Harry had been a skeptic when it came to ghosts and the paranormal for as long as they had been friends.
When Lizzie confided in Harry that she could see and talk to spirits, he said she was mad. Though Lizzie was not the type of person to make up stories for the sole purpose of getting attention, there was no persuading her friend. Hermione gave a similar reaction, and Ron however was immensely intrigued.
“Harry, I don’t know, I told Zak I’d go, but…” “You’re having second thoughts?” Asked Harry. Lizzie sighed. “Yeah,” she said. “I don’t know, there’s just something weird about going. The last time I was there - sorry - the last time we were there….” Her voice died in her throat, but Harry seemed to get it.
“But it’s not just that is it?” Asked Harry. This was really a testament as to how much of a bond Harry had with Lizzie. When they were at Hogwarts together, Harry had this uncanny ability to tell when Lizzie was holding back her feelings or when she was lying about something. Perhaps it was in her facial expressions that gave her away, and if it was, Lizzie never noticed, but somehow Harry still could tell when she wasn’t being entirely truthful.
“It’s about what Cormac did to you isn’t it?” Asked Harry. Lizzie was quiet on the other line. “You know you could always ask for an apology,” “Sorry doesn’t pay the bills, Harry,” said Lizzie, her voice bitter and full of icy resentment. “And it sure as hell doesn’t undo what that bastard and his friends did to me. D-do you know that I can’t have children because of what he did?’
“I didn’t know that. I’m so sorry, Lizzie,” said Harry, his tone was quiet, gentle and full of sympathy. “But I get it, you’re still angry that no one helped you.” “And it’s not like I never asked!” Said Lizzie. “I went to Dumbledore so many times! I begged for him to help me!” “I know you did, Liz,” said Harry gently.
“But on a side note, I got a new horse,” said Lizzie, changing the subject abruptly. “Did you?” Asked Harry. “What’s his name?” “Her name,” said Lizzie. “Is Midnight,” “A mare?” Asked Harry laughing. “You got a mare?” “Why so surprised?” Asked Lizzie, smiling. “I don’t know,’’ said Harry. “It’s just - when we were at Hogwarts you always seemed to gravitate towards the male school horses. Is she - hard to handle? I mean does she give you attitude sometimes?” “Yeah, she really decided to play up just the other day,” said Lizzie. “But?” asked Harry. “Ehh, I was able to get her under control,” said Lizzie.
“I think at the end of the day, she has a hard time coping with her own trauma.” “Was Midnight abused?” Asked Harry, sounding worried. “Oh, my gosh! Yes! Horribly!” Said Lizzie. “Her mouth was all torn up when I first met her because her previous owner used to wrap barbed wire around the bit, and force it into her mouth. He called it ‘training”’ said Lizzie bitterly.
Harry sighed. “Well, now she has you,” he said. “Yep, and she’s doing so much better,” said Lizzie. “Good,” said Harry. Lizzie heard a knock on the door as she looked up and saw Zak standing in the doorway. “Um, I gotta go, I’ll call you later, before we get on the train,”
“Okay,” said Harry. “And Lizzie?” “Yeah?” Asked Lizzie. “I love you, you know that right?” Lizzie smiled. “I love you too,” she said as she hung up the phone.
“Harry?” Asked Zak. “Mm-hmm,’’ said Lizzie. Zak walked into the room, and sat on the bed next to Lizzie and kissed her on the cheek. “Nearly done packing?” Asked Zak. “Halfway,” said Lizzie.
Zak reached into Lizzie’s still open trunk, took out a bundle wrapped in a silk scarf, and unwrapped it.
Into his hand fell a single steel horseshoe. But there was also something wrapped in plastic inside the silk scarf as well. Zak felt inside the silky bundle and pulled out a tiny plastic bag, which inside contained a single lock of jet black hair. Zak could tell immediately that the hair inside the bag was horse hair. And he didn’t have to ask Lizzie who the shoe or the hair belonged to.
“Hagrid gave that to me after Raven died,” said Lizzie. “He knew how much Raven meant to me,” Zak smiled.
“I called, Aaron, Billy and Jay, and they agreed to come to Hogwarts. Dakota’s agreed to come too, but I can’t think for the life of me how we plan on getting there,” said Zak. “What do you mean?” Asked Lizzie. “I don’t - fly anymore,” said Zak. “Oh, no worries!” Said Lizzie. “We’ll Apparate to Kings Cross in London, then, we can take the Hogwarts Express from there!” Said Lizzie.
“Okay, I guess,” said Zak.
They continued to clean out Lizzie’s trunk sorting out the rubbish, the sentimental trinkets, and the robes that they could donate to secondhand shops in Diagon Alley. After she finished cleaning out her trunk, she began to pack it full of things she planned on taking with her.
She included two pairs of riding breeches, her tall riding boots and gloves and her Charles Owen riding helmet. Then she packed her casual clothes, her wand, and the equipment she would be using during their investigation. She even took some of her old spell books (the ones that were still in good condition), and even texted Hermione asking her how to make Essence of Dittany, and other potions that could come in handy whilst on their trip. She also took her 357 handgun just in case.
Just as they were finishing up, Zak heard a tap, tap, tap! noise on the window and was surprised to see a large barn owl clutching a yellow envelope in its talons.
Lizzie scrambled to her feet, and opened the window, removed the screen, and the owl hopped onto the sill, as Lizzie carefully took the package from the owl, as it ruffled its feathers, turned and took flight. Even after all these years, Lizzie still continued to receive mail by ‘owl post’.
A quick look at the return address told her it was from Harry. Lizzie tore the envelope and inside was a piece of parchment folded intricately in different directions, yet it appeared to be blank. There was a note there too.
Lizzie,
I duplicated the Marauder’s Map, and sent you a copy. I thought you may find it useful during your investigation. You remember how to use it, but you may need to teach Zak. Just remember to tell him how to wipe it clean so no one can read it.
Much love and luck
Harry.
Lizzie smiled with excitement. “Is that from Harry?” Asked Zak. “Yeah, he sent me a copy of the Marauder’s Map,” said Lizzie. “What’s that?” Asked Zak. “A magical map of Hogwarts,” said Lizzie. “It belongs to Harry, but he duplicated it for me so we could use it during our investigation.”
“How does it work?” Asked Zak. “Looks like a blank piece of paper.”
Lizzie smiled as she picked up her wand from her bedside table, and tapped the parchment with it. “I solemnly swear that I am up to no good,” said Lizzie clearly. Ink lines snaked across the parchment, forming words, and lines. After a moment the surface of the parchment that had been blank only moments ago, now bore the words:
Messers Moony, Wormtail, Padfoot, and Prongs, are proud to present
The Marauder’s Map.
Zak’s blue eyes widened in awe, as Lizzie unfolded the parchment, showing the inside of the map. It looked a lot like interior plans for a house. And there were moving footprints in countless areas of the map, each marked with a name, and moving in various directions.
“Holy shit!” Zak gasped. Lizzie smiled. “Mm-hmm,” she said. “And…This is Hogwarts?” Asked Zak. “Yep!” Said Lizzie, feeling a strong sense of pride and satisfaction at her boyfriend’s awed look. “Every square inch of it!” “That’s awesome!” Said Zak. “Right?” Asked Lizzie, giggling. “I reckon we can map our our x cameras on here,” “Lizzie,” said Zak, holding Lizzie’s face in his hands, and kissing her. “You’re a genius,”
Lizzie smiled. “I do have to make a few stops before we go to Kings Cross to catch the train,” “Where to?” Asked Zak. “I want to stop in Diagon Alley, to a secondhand robes shop, and donate my old school robes, and Gringotts, to get some money out of my account,’’ said Lizzie.
“Ah,” said Zak. Lizzie tapped the Marauder’s Map with her wand again. “Mischief Managed,” she said, tapping the map, and it was instantly erased, looking blank once more.
6 notes
·
View notes
Text
Ravencoin Wallet
Ravencoin is a peer-to-peer blockchain, handling the productive design and transfer connected with assets from one celebration to another.
Ravencoin can be a protocol based with a good fork of typically the Bitcoin signal which gives features specifically centered on permitting tokens to be given on the Ravencoin blockchain. All these tokens can include whatever components the matter of the token decides - so they may be restricted in quantity, named and become issued because securities or even as collectibles.
Ravencoin Core Wallet can make your personal safety measures token within short minutes and get it trade world-wide.
Symbolizing real world custodied physical as well as digital tool
Securities tokens: stock or even shares of an company just where the shares usually are manifested by a token rather than actual physical stock certificate
Investments or perhaps partnership interests with all the built-in ability to pay dividends in RVN
Tokens which symbolize a around the, limited relationship, royalty spreading or earnings sharing platform
A token which in turn presents a cflexd-funded product together with the ability to copy or resell the product
Representing virtual products
Seats to an event like a Baltimore Ravens game with all the ability to resell hassle-free of duplicates being manufactured
A license to enable a activity
A good access symbol to use a new program
In-game currency together with products, transferable to various other players outside of the online game podium
Representing a promote of your project
Gold pub
Gold coins
Physical Local currency
Territory Deeds
DC Comics Gifts #26
Energy credit (Electricity, Wood, Gas, Lubricate, Wind)
What Makes Ravencoin Different from Bitcoin?
Often the X16R protocol hopes to solve the centralization involving mining viewed on the particular Bitcoin blockchain caused by simply the introduction of high priced and really useful App Specific Integrated Circuit (ASIC) hardware. By way of randomizing typically the order of of sixteen several hashing codes, Raven can make ASICs tough to formulate, letting room for anyone to be able to mine the Raven circle without the disadvantage connected with competing along with ASIC hardware. The Raven team has also committed to change the hashing algorithms if a Raven ASIC miner is usually possibly developed.
Block reward regarding 5, 000 RVN instead of 50 BTC.
Block time of 1 instant instead of 10.
Complete coin supply of twenty-one Billion instead of twenty-one million.
A new mining algorithm, X16R which permits for more decentralized gold mining.
Addition of Property issuance, and transfer.
Potential addition of unique possessions, sub-assets, rewards, messaging, and even voting.
The Raven is definitely the highly symbolic beast of which is mentioned in the variety of cultures along with diverse purposes. One of the meanings is the one about alteration.
As Ravencoin is often a hand of the Bitcoin computer code it could very in fact be this meaning the fact that developers wanted to communicate. It really is with this imagery that we bring in Ravencoin.
Ravencoin is the brand-new project that was declared on October 31st, 2017 and debuted on Bitcoin�s 9th birthday on Jan 3rd, 2018 with the relieve of software program intended for exploration.
Ravencoin is extra than a hand involving the Bitcoin code it is a project that builds when the original vision associated with Bitcoin but with extra new features which will increase the functionality and the particular built-in value of the coin organically.
Ravencoin: Replicated of bitcoin that will be used for possessions. Enhanced bitcoin built intended for assets
Ravencoin is a free open source system designed for the particular use circumstance of switching assets like token-backed possessions from one case for you to another.
While it may well seem that with the particular development of the good blockchains such as Bitcoin plus Ethereum, transferring property in between different parties is presently the solved issue, that is not just often the case. Neither Bitcoin or Ethereum were exclusively created for facilitating property of extra investments, do to often the fact that they just centered their attention inside other capabilities.
Ravencoin can be built on a fork of the Bitcoin program code. It has been implemented with some sort of small block reward associated with one minute (the obstruct reward is definitely the only way that brand new coins are created and this is usually an incentive for miners to add hash electrical power to the particular network), plus the addition of resource creation and meaning functions.
If you are some sort of crypto-lover, and are guaranteed you are when you may be reading this right at this point. You are going to agree that blockchain technical will indeed adjust global economic paradigm since we know this in these modern times.
However being able to be able to give wealth transactions throughout a matter of moments, globally and with zero third parties involved, is usually just the tip regarding the banquise that this new revolution represents.
Around the same path of unstoppable evolution, Ravencoin is going to implement the way investments proprietors operate with their particular wells. It will eventually allow them to handle properly the particular transfer of their investments to another parties.
For you to live our planet order wave without shedding any keypoint:
Problem
Inspite of the achievements and wide-spread adoption of Bitcoin in addition to Ethereum, neither of these blockchains have been specifically designed to aid the ownership involving additional property on best of the tokens which can be transacted throughout their respective networks.
In Bitcoin, an original rules governing the blockchain and protocol must become followed and so this kind of means that Bitcoin nodes are not ready to be able to register that will assets will be being embedded in bridal party.
This means that for every tool financial transaction produced on the Bitcoin system, there must be an associated bitcoin financial transaction cost, set up transaction is to basically give the advantage.
This has a result of unneeded transaction fees when assets are transferred. Moreover, this other major disadvantage is always that assets can easily always be �destroyed� if they are sent for you to an exchange or perhaps pocket.
For Ethereum the networking system is not able to help natively identify smart contract tokens and also this can bring about some confusion because of several ERC20 tokens having the exact same names. The only different factor among contracts having identical names is often the agreement hash and this specific can mix up users or be used together with malevolent intent to scam others.
As Ravencoin will always be jogging on a decentralized model along with independent miners to support the stability involving the blockchain combined having ASIS-resistance the coin will have a fantastic chance of staying in the hands and fingers of individuals and not necessarily central by one party or a group of events that can collude to be able to shape the end result connected with an event, the have your vote or even the price of the tableau on its own.
Peer to Peer Electrical System for the Formation together with Transfer of Assets
Optimized for switching assets
Tokens offer many strengths for you to traditional shares or perhaps different participation mechanisms: quicker copy speeds, increased user command, and censorship level of resistance, and also a lowering or eradication in the need for some sort of trusted third party.
Solution
The solution to the particular above issues is to be able to produce a Bitcoin-like method that is completely advantage conscious so that that identifies any time tokens own recently been specially designed as resources.
With a view in order to solve the problem, Ravencoin provides to life often the said:
�Keep it basic stupid�
by way of focusing upon creating one thing, one specific thing� a good bitcoin-like system, totally mindful about when tokens are created such as assets (Based in PoW but with some sort of new mining criteria, x16r).
This provides three benefits:
Assets can be secured from accidentally being damaged. As being the protocol and the system is aware about typically the assets?�?they can be carried on the blockchain like a passenger on the exercise sooner or later getting them all of safely into the destination.
Customers are able to challenge, track, and transfer possessions with each some other using the ease of sending a message to one another. Now consumers will exchange on the full software specifically created to issue, track and even transfer assets between events.
It will provide right security levels to often the underlying assets. To accomplish that Ravencoin may count on a wide circulation, a strong mining neighborhood and even market value in order to function.
Main Features?�?Tech Guide
Ok, now all of us realize the problem (the suggested one, between the several active issues) that requirements to be solved in current blockchain and all of us know the solution that Ravencoin is definitely committed to create in order to go beyond that limitation.
So� what is next?. We need in order to go strong into his or her tech� it seems a drab, but we will take care of that. Only in the fact that way you will really need knowledge and foundations for you to take decisions about the particular job.
Ravencoin Core Wallet bring you the following features:
X16R Algorithm
Before we all illustrate what X16R will be most of us will first provide information behind what other gold and silver coins include implemented for their very own algorithms.
In the search for you to create and put into action methods that are ASIC proof (meaning that purpose developed mining machines with substantial hash rates could not really be developed) which inside of turn reduces the chances of centralization via great mining harvesting, projects experience tried a range of tactics to hinder this particular centralization (such we observe with Bitcoin mining).
The particular first approach was to adopt memory intensive codes want those used by simply both Scrypt and Equihash. This requirement for additional in memory measurements reduces the particular performance of the ASIC to help more onpar of this GPU based mining using the same algorithm
One more approach that was carried out, was initially Dash�s approach, which was to look at the X11 algorithm. This is actually the use of 11 chained hashing methods (hence the name) in an energy to slow down the creation of ASIC components.
This did not stop the appearance of a new special goal ASIC so once at this time there was a good ASIC for X11, others added a great deal more hashing codes to make additional methods that have been called X13, X15 and X17. This makes it additional difficult to create a good ASIC although because this codes are in about the same order the complicated but not difficult to create the ASIC.
What Ravecoin does is usually called X16r and of which setup like the some others described formerly use of sixteen algorithms to the hashing (see table below). The key element difference is they have got additional algorithm reordering. Its that reordering based on often the results from the previous block out that provides a great deal more ASIC resistance than other hashing algorithms.
Example:
Previous Stop Hash: 0000000000000000007e8a29f052ac2870045ae3970270f9?7da00919b8e86287
The last 6 bytes: 0x7da00919b8e86287 determines the particular next 16 hashes must be.
Roadmap
Phase 1?�?Complete
Ravencoin (RVN) is a new Proof of Function coin built on the Bitcoin UTXO model. As with various other Bitcoin derivatives, RVN money are distributed for you to individuals enhancing the Raven community by way of mining Raven.
x1000 coin distribution (21 Billion dollars Total)
10x speedier hinders (1 per minute)
Found in app CPU gold mining
~1. 4 Day trouble change (2016 blocks)
Addresses begin with R� for normal tackles, or r� to get multisig
Network Port: 8767
RPC Port: 8766
UTXO?�?UNSPENT BUSINESS DEAL OUTPUT DEFINITION
This Unspent Transaction Output is usually key to be able to bitcoin because this is how bitcoin keeps track of advices and outputs on the particular blockchain. First we need to search at how a financial institution works.
Assume Tom is to use Bank A and has got a balance of $5, 1000 plus assume that Alice who does just about all her banking with Lender T has no balance.
Jeff wants to send $2, 000 dollars to Alice. To get this done Tom asks his or her bank to send $2, 000 for you to Bank B in Alice�s name.
Typically the genuine business deal has Tom�s balance diminished by $2, 000 coming from $5, 000 to $3, 000 together with Alice�s balance increases by $0 for you to $2, 000.
Taking this particular to the particular Bitcoin blockchain:
Ben features received inputs in typically the quantity of 5 BTC. This is from 4 dealings (inputs)
ADVICES
Received two BTC
Received 1 BTC = 5 various BTC
Acquired 1. your five BTC
Acquired. 5 BTC
In this example, Tom would like to send Alice 2 BTC. Typically the blockchain, unlike banking companies, will be not aware of balances such as the example previously mentioned hence the transaction is noted as:
OUTPUTS
2 BTC provided for Alice
3 BTC repaid to Mary ? this is the Unspent Transaction End result or even UTXO
Phase 2?�? Ravencoin Core Wallet (in progress)ASIC RESISTANCE
ASIC Resistance?�?A published commitment to frequent attempts at ASIC level of resistance. If ASICs are usually created for x16r, after that we will, at a distinct block amount, modify a person of the algorithms to add Equihash, EthHash or equivalent efforts to increase typically the resistance from ASIC miners with regard to Raven.
SPECIAL ASSET HELP SUPPORT
Ravencoin will be a good hard fork that will extends Raven to include the ability to issue and transfer investments. The expected release connected with asset capabilities will become about seven months immediately after the launching of RVN. Raven will probably be extended for you to allow issuing, reissuing, plus transfer of assets. Assets can be reissuable as well as limited to some sort of set provide at the position of issuance.
The expense to create property is going to be 500 RVN to develop just about any qty of the asset. Every asset title must be exclusive. Resource names will be limited by A-Z and 0�9, �� and �. � and even must be at at a minimum three personas long. The �. � and often the �� cannot be the primary, or the last figure, or be consecutive.
Instances connected with valid assets:
THE_GAME
Some sort of. TOKEN
123
Good examples involving invalid assets:
_TOKEN
THEEND.
A.. B (consecutive punctuation)
AB
12
. FIRST
Often the RVN used in order to issue possessions will be sent to a burn address, which will decrease the volume of RVN available.
Resource moves demand the normal RVN business deal fees with regard to transfer from address to another.
METADATA
Metadata with regards to the token can be stashed in IPFS. At first this specific cannot be changed. When there is a demand, the technique can be kept up to date for you to allow updating the metadata by the token issuer.
REWARDS
Reward capabilities will certainly be included to let payment (in RVN) to help all slots of a great tool. Payments of RVN would be distributed to all of property stands pro mangante. This is useful for having to pay dividends, dividing repayments, or even rewarding a group connected with token holders.
Example: A new little software company problems an asset GAMECO that presents a new share of often the project. GAMECO tokens can be traded together with other people. Once the computer software firm profits, those profits can be distributed to all cases involving GAMECO by mailing the earnings (via RVN) for you to all slots of GAMECO.
BLOCK DIMENSIONS
Raven may increase the blocksize coming from 1 MB to be able to X MEGABYTES to allow regarding more on-chain transactions.
Phase 3?�?Rewards
The reward method will allow for the formation regarding bridal party that take a seat in the Raven blockchain. These types of tokens may be created and then sent to guys and women as a good reward intended for doing something or so that you can raise funds. The cash raised can then be used to send out almost any currency on the raven blockchain to a further bash.
Phase 4?�?Unique Resources
Once created, assets can become built unique for some sort of cost of 5 various RVN. Only non-divisible resources may be made one of a kind. This kind of moves an advantage to a UTXO and associates a distinctive designation with the txid. From this level the tool can certainly be shifted from a person address to another and even can be tracked returning to it is source. No more than the issuer from the unique asset can make an asset special.
The costs for you to make distinctive assets will be sent to a new burn address.
Some cases associated with unique assets:
Envision that a skill dealer issues the asset named FINE ART. The supplier can next make unique SKILL property by attaching some sort of name or a serialized variety to each piece of art. These special bridal party can be transferred to the brand new owner together together with the a muslim as a good proof of genuineness. The particular tokens ART: MonaLisa and even ART: VenusDeMilo are not really agotable and represent unique components of fine art.
A application developer will be able to issue often the asset using the name associated with their software ABCGAME, in addition to then assign each ABCGAME token a unique id as well as license key. The particular game bridal party could end up being shifted as the certificate transfers. Each token ABCGAME: 398222 and ABCGAME: are one of a kind tokens.
In sport investments. A game ZYX_GAME could create unique limited model in-game ui assets that will be owned and even used simply by the game person. Illustration: ZYX_GAME: Sword005 plus ZYX_GAME: Purse
RVN structured special assets can be associated with real world property. Develop a property referred to as GOLDVAULT. Each one gold coin or gold tavern within a vault can possibly be serialized together with audited. Linked unique assets GOLDVAULT: 444322 and GOLDVAULT: 555994 are able to be created to signify the specific assets inside of the physical gold vault. The public character connected with the chain allows regarding full transparency.
Phase 5?�?Messaging
Messages to token cases simply by authorized senders is going to be layered on major of the Phase 3 or more unique assets. See KAAAWWW Protocol for additional details.
Stage 6?�?Voting
Voting will be accomplished by generating in addition to distributing seite an seite tokens to be able to token holders. These bridal party can be provided for RVN addresses to record a have your say.
Team + Advisors
Called some sort of community lieu. Any individual can contribute through adding for you to the project.
The variety of designers involved is uncertain, however there had been 430 Bitcoin developers who else made more than 14, 000 commits in accordance with Github.
Tron Black?�?Core Developer
Tron features been in Blockchain and cryptocurrencies as a new Software Developer for 5+ many years. Currently a Principal Software Developer for Medici some sort of VC investing in typically the blockchain space. His profession mission is to improve technology in order to resolve great world problems.
He was basically the President/CEO at Blue Squirrel for 17+ decades. Blue Squirrel is the application development company their very own initial product was SQURL, it turned out the google regarding the web at this time.
Made Paten?�?System for you to Verify Id and Reputation for a good Cryptocurrency Budget Address:
Patent dateFiled Summer 6, 2013 Patent company and numberus 61831802.
Particular descriptionMethod and system intended for voluntary identification of some sort of commercial or maybe individual id in order to public crypto-currency address(es), together with a single number status rating system obtainable via API.
Bruce Fenton?�?Advisor
Generic is a Blockchain Economic Specialist. He has had 23+ many years of experience in the Finance market and combined with 3+ years experience in typically the blockchain plus cryptocurrency space.
This individual possesses placed through $5 billion in ventures in investing funds throughout his career.
Recommended the particular Bill & Melinda Entrance Foundation?�?arranged, attended and staffed very senior level gatherings among Bill Gates and even business and government frontrunners in Saudi Arabia, worked well with the top of Midst East for the basic foundation (please note, opinions on electronic money plus economic issues are not those of the foundation).
Hosted the Satoshi Roundtable private abandon, some sort of gathering of seventy-five of the top leaders inside blockchain technology.
Angel Buyer in SpeechWorks (now public Tonalit� with $5bn marketplace cap).
Angel Investor in Bitcoin companies such like ShapeShift.
Advisor to Factom, BTCS and other corporations.
Presently hold 3 tasks:
Board Contributer to The Bitcoin Foundation (2+ years), which usually is the largest plus oldest industry group regarding Bitcoin Technology.
Founder on Satoshi Roundtable Private Blockchain Retreat (3+ years), the industry invite only VIP twelve-monthly event.
Managing Director. CIO for atlantic Financial Incorporation. (23+)
1 note
·
View note
Text
VoIP PBX - Enabling Business Growth
VoIP PBX - Enabling Business Growth
Enterprise communications has all the time been a challenging enviornment for administration....subject to price, perform, reliability, and other pressures and concerns. The emergence of VoIP expertise....and particularly utility to PBX techniques via IP primarily based protocols....has provided an infinite opportunity for firms to reap many advantages.
Many firms today have a number of office areas across the country or around the world. Presently, each office uses its own PBX system and inter-office telephone calls are routed through the PSTN and charged long distance and worldwide charges by carriers. Most corporations also employ staff on ip pbx uae an element time basis who work from their houses. These workers get reimbursed for telecommunication bills they incur while performing their duties. It simply makes enterprise sense for firms to explore alternate options to consolidate their telecommunication systems and scale back prices.
The answer......buy a Voice-over-IP enabled PBX system and deploy it in a Digital Office setup.
Voice-over-IP (VoIP) is a reasonably new technology for transporting voice calls over the Internet which allows customers to comprehend substantial value savings on long distance and worldwide calls. Besides price effectiveness, VoIP enabled PBX methods (or IP PBX) supply easy integration with existing telecommunications methods and are characterised with low working costs as their improve is done by way of software updates rather than more expensive hardware substitute. Moreover, the expertise simplifies the communication infrastructure (no need for separate voice and data cables) while providing excessive scalability.
Digital Office models are used by firms that wish to consolidate their communications, cut back costs and achieve extra cohesive company photographs. To implement the model, an organization has to install a single IP PBX system in its headquarters and distribute to employees IP telephones or common telephones with VoIP adapters. Staff can make intra-office and inter-office telephone calls by dialing PBX extensions. Such calls are routed via the Web and are practically free. Firm customers, on the other aspect, can dial a single inbound number plus extensions as a way to reach the company's staff. The latter obtain the calls on their IP/Common Telephones at any location on the planet with Web connectivity.
So what kind of a VoIP PBX solution does your business need? - a turnkey Digital Office answer that could be personalized to meet your organization particular wants.
My suggestion for this solution is the highly acclaimed bundle from Packet8. Not too long ago 8X8, Inc's Packet8 Digital Workplace Resolution for small and medium sized businesses obtained Community Computing Journal's Editor's Choice award over aggressive offerings from Covad Communications and Velocity Networks. That is some pretty stiff competition....and says loads about Packet8's performance. The Packet8 Virtual Office solution acquired the best total ranking for its wealthy feature set, call management tools and low subscription price.
The Packet8 Virtual Office is an economical, simple-to-use different to conventional PBX methods that enables users anyplace on this planet to be a part of a VoIP-hosted digital cellphone system that includes auto attendants, conference bridges, extension-to-extension dialing, enterprise class voicemail and ring groups, along with a rich variety of different enterprise telephone options usually discovered on excessive-finish, premise primarily based PBX programs. Their Virtual Workplace reduces a company's telecommunications total price of possession (TCO) with a minimal preliminary investment combined with unlimited native and lengthy distance business calling all through the United States and Canada and Packet8's low worldwide rates.
VoIP PBX or IP PBX (Internet Protocol Personal Branch Trade) is a telephony system that makes use of IP knowledge networks to facilitate telecommunication. The speedy benefit of VoIP PBX is that enterprises utilizing it need not have to interchange their present telephones or phone numbers to accommodate the new VoIP facility. It's a strong technology that works in tandem with the present communication infrastructures. In different words, the VoIP know-how can use the existing PSTN lines by way of the VoIP gateway, and there is no a lot of extra infrastructure concerned in its entire set up.
How does a VoIP PBX work?
The basic architecture of an IP PBX system consists of an IP PBX server, one or more SIP telephones or VoIP phones, and a VoIP gateway, as talked about already, to hook up with the prevailing PSTN lines (optionally available though). The IP PBX server functions quite much like a proxy server. The SIP or VoIP phones, which could be either hardware phones or gentle telephones, has to register with the IP PBX server, and after they want to make a name to another cellphone - a VoIP or SIP phone - actually a request is ship to the IP PBX server to determine the connection. The IP PBX server could have a directory of all users/phones and their respective SIP addresses, and using this data, it could connect an internal call or route an exterior call via a VoIP service provider or a VoIP gateway, whichever is applicable. The process is simply quick and simple.
So, what are the advantages of VoIP PBX over standard PBX techniques?
An important plus of VoIP PBX is that it's many occasions simpler to install and configure than a traditional telephone system. Anyone who is aware of the basics of pc and networking can set up the IP PBX in a LAPTOP and keep it fairly well. Also, since it's all software, there isn't a complex wiring involved anywhere. If anyone wants to attach a hardware Visit blog cellphone to an IP PBX system, he/she will directly plug it into a regular network port (soft telephones can be put in straight into the LAPTOP). This have to be learn within the backdrop of the fact that within the case of proprietary phones, solely a trained technician could deal with its set up, configuration, wiring, and total maintenance.
Another massive benefit of IP PBX is its low price of operation. Since the calls make use of IP networks, even lengthy distance worldwide calls are many occasions cheaper. If the decision is made between the phone programs that hyperlinks the branches of enterprises, it is completely free of price. Additional, since IP PBX is built on an open SIP customary, users can use any SIP software/hardware telephone with nearly any SIP based PSTN Gateway, IP PBX or VoIP provider. There isn't a query of a vendor lock-in in any circumstance.
One more constructive with IP PBX is that it may easily handle any number of extra phone connections and extensions with out disturbing the effectivity of the community. This is in deep distinction to the traditional phone programs, which might require further hardware modules to accommodate the newer connections and extensions.
The IP PBX serves as a gateway in order to transfer voice in Voice Over IP networks. This gateway really performs the role of a phone change as is found in conventional networks. The presence of PBX permits customers of VoIP to ship voice mails and messages to others residing at distant locations of the world.
The precept beneath which VoIP works may be very easy. The voice is transformed into digital packets and sent to the tip customers in digital packet forms. On receiving the alerts on the other finish, it is reconverted to its original voice type. The VoIP PBX serves as a gateway for such transference and supports greater than sixteen extensions at a time. It means that upto sixteen or more users can send voice message to different locations utilizing the PBX. The users of the Voice over IP can receive indicators without any generation loss. It means that there isn't any modifications in quality of voice after it's being delivered.
The IP PBX VoIP has a in-built router that's preferrred for small in addition to massive workplaces. Folks can make use of the router of VoIP PBX to send messages in text formats Click Here for Wikipedia while forwarding calls to the top customers. Thus customers of this mode of telephony have the choice to share files and send messages while forwarding calls to others.
The system of broadband telephony could be very consumer-friendly and customers can really make use of the technology to make three method convention calls. This 3-means calling know-how permits a variety of individuals to affix in a conference and share their views. This characteristic of VoIP is very important www.ippbxuae.com/voippbx/ for enterprise houses to utilize the technology to share files with others. The significance of the system lie in the truth that professionals can focus on over a problem even when they are positioned at completely different places of the world. So, it a fantastic impetus to enterprise and different activities.
The IP PBX Solutions is a much advanced expertise and allows folks to utilize it to remain linked with others at very low name value. Calling with VoIP community is a a lot applauded system for the technology allows folks to make lengthy distance calls at a surprisingly low calling rate. It's so changing the standard methodology of calling. Furthermore, it is problem free as the system is digital unlike conventional telephones where prolonged wires have to be linked to the phone community.
The IP PBX serves as a platform for using VoIP community to switch recordsdata and voice very easily. This trade is as a super means to reach out to individuals no matter wherever one may be positioned. The PBX trade VoIPPBX being one of many major means to achieve out to folks, they are deployed in each area of the world. The rationale why this network finds importance is that they can join easily with others at low cost fee.
Details about the varied sort of PBX is accessible in the web. It ranges from PBX for small and medium business and PBX for customised IP telephony solutions. The details about PBX, makes it attainable for people to opt for the one that fits them proper. Prospects may monitor a IP PBX system by acquiring the connection on a trial foundation. They'll then continue using its companies if it conforms to their needs or can discontinue use.
IP PBX solutions has thus taken over telephony system like a storm. It's changing into rising fashionable and even people residing in distant place of Here is Social Network for VoIP PBX the world have began to utilize service. The users really feel good to utilize the VoIP PBX system as with it telephony has turn into very low-cost.
1 note
·
View note
Text
Don't Let Cybersecurity Risks Ruin Your Nonprofit's Reputation
Don't let cybersecurity risks ruin your nonprofit's reputation. Don't let hackers gain access to donor data and your nonprofit's reputation. Don't be one of the many organizations that haven't adopted a robust cybersecurity policy. It's not enough to simply have a security policy; you also need a security plan and documentation. Without cybersecurity documentation, nonprofit cybersecurity your organization risks being hacked. By using a comprehensive cybersecurity policy, your organization will reduce its digital footprint and reduce the likelihood of being attacked.
Nonprofits store sensitive information such as donor names and addresses, email addresses, phone numbers, and credit card details. However, more than half of nonprofits do not enforce multi-factor authentication and do not use a password manager. A password manager is an essential piece of nonprofit cybersecurity. If your website has a password manager, you can set up the password policy yourself. That will keep hackers out. It will also protect your donors from spam and other phishing scams.
Make sure to back up important data on a regular basis and encrypt your laptop. Nearly every device on the Internet communicates passwords and login information. Hackers have the ability to shut down power grids and even a home's security system. Another important aspect of nonprofit cybersecurity is having sophisticated passwords. Passwords should be at least sixteen characters long and include special characters. Don't forget to change your passwords regularly and use unique ones each time.
While it's a scary thought, data breaches can hurt a nonprofit's reputation and affect contributions. Don't neglect to assess cybersecurity risks - it's like failing to brush your teeth. Consider training sessions and workshops offered by state associations of nonprofits and cybersecurity experts. The NIST Cybersecurity Framework can help you identify the risks and mitigate them. It's not a one-size-fits-all approach, but can provide your nonprofit with a comprehensive cybersecurity strategy that is cost-effective and effective.
Fortunately, the NFP community has a wealth of resources that can help you implement cybersecurity measures. The Cyber Oregon website contains valuable cybersecurity resources, including cybersecurity news, how-to guides, and access to resources in your area. Not only can you find useful tips, you can even learn about cybercrime and other cybersecurity threats. You can protect your mission and the personal information of your donors and volunteers by following the NPO Cybersecurity Playbook. This playbook is a must-have for nonprofits.
While some cyberattacks may be directed toward nonprofits because their mission is compromised, others may be motivated by ideological differences. Even if your nonprofit is not targeted by ransomware, employee negligence can lead to malware infection in its network or shutting down essential systems. This downtime could be critical to your work. And if it's not protected, you might not be able to continue your work at all. Then, if your mission is threatened, what happens?
When you do have an IT service provider, make sure they can protect you against ransomware, IT companies being hacked, and more. Many nonprofits don't invest in cybersecurity, due to limited funding. Because of this, they often opt for lower-cost IT services providers, which could compromise their cybersecurity. In addition, about 70% of nonprofits have never conducted a vulnerability assessment, and nearly the same number have no cybersecurity response plan.
0 notes