#sql stored procedures
Explore tagged Tumblr posts
Text
Dont like work
#Never made a stored procedure dent know sql gotta take a thing already made and modify it however idk#No training just sink or swim
29 notes
·
View notes
Text
Utilizing Stored Procedures for Better Database Security and Manageability
Stored procedures are a vital component in database management, offering a range of benefits. They are precompiled sets of one or more SQL statements that are stored and can be reused. This allows for improved performance, as the database server does not need to recompile the SQL code each time it is executed. Additionally, stored procedures enhance security by allowing permissions to be set at…
View On WordPress
0 notes
Text
How to Convert a SQL Server Stored Procedure to PostgreSQL
Are you migrating a database from SQL Server to PostgreSQL? One key task is converting your stored procedures from T-SQL to PL/pgSQL, PostgreSQL’s procedural language. In this article, you’ll learn a step-by-step process for translating a SQL Server stored procedure to its PostgreSQL equivalent. By the end, you’ll be able to confidently port your T-SQL code to run on Postgres. Understand the…
View On WordPress
#convert sql server procedure#database migration#postgres stored procedure#postgresql function#t-sql to plpgsql
0 notes
Text
Lead Oracle PL/SQL Developer@ Nashville, TN (Remote)
Job Title: Lead Oracle PL/SQL Developer Location: Nashville, TN (Remote) Apply Here: https://jobshorn.com/job/lead-oracle-pl-sql-developer/7370 Duration: 5+ Months Interview Type: Skype or Phone Job Type: #C2C, #W2, #1099 🔹 Job Description: Minimum of five years of experience with Oracle PL/SQL and a relational database such as Oracle 19g. Experience in writing complex SQL and PL/SQL queries, including the development of stored procedures, functions, and triggers Please share resumes to [email protected] |📞 Phone: +1 470-410-5352 Ext:111
#OraclePLSQLDeveloper #oracle #Tennessee
#career#jobshorn#usajobs#contractjobs#opportunities#urgent_hiring#recruitment#itjobs#recruiters#hiring
4 notes
·
View notes
Text
In Microsoft SQL Server, stored procedures (SP) are crucial for implementing business logic according to the organization’s requirements, enhancing query efficiency, and securing important data. Let's Explore Deeply:
https://madesimplemssql.com/sql-stored-procedure/
Follow us on FB: https://www.facebook.com/profile.php?id=100091338502392
2 notes
·
View notes
Text
How to Prevent

Preventing injection requires keeping data separate from commands and queries:
The preferred option is to use a safe API, which avoids using the interpreter entirely, provides a parameterized interface, or migrates to Object Relational Mapping Tools (ORMs). Note: Even when parameterized, stored procedures can still introduce SQL injection if PL/SQL or T-SQL concatenates queries and data or executes hostile data with EXECUTE IMMEDIATE or exec().
Use positive server-side input validation. This is not a complete defense as many applications require special characters, such as text areas or APIs for mobile applications.
For any residual dynamic queries, escape special characters using the specific escape syntax for that interpreter. (escaping technique) Note: SQL structures such as table names, column names, and so on cannot be escaped, and thus user-supplied structure names are dangerous. This is a common issue in report-writing software.
Use LIMIT and other SQL controls within queries to prevent mass disclosure of records in case of SQL injection.
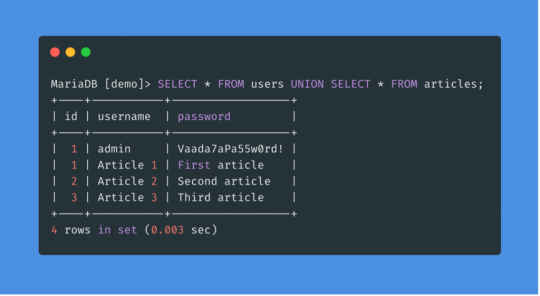
bonus question: think about how query on the image above should look like? answer will be in the comment section
4 notes
·
View notes
Text
Unlock Success: MySQL Interview Questions with Olibr
Introduction
Preparing for a MySQL interview requires a deep understanding of database concepts, SQL queries, optimization techniques, and best practices. Olibr’s experts provide insightful answers to common mysql interview questions, helping candidates showcase their expertise and excel in MySQL interviews.
1. What is MySQL, and how does it differ from other database management systems?
Olibr’s Expert Answer: MySQL is an open-source relational database management system (RDBMS) that uses SQL (Structured Query Language) for managing and manipulating databases. It differs from other DBMS platforms in its open-source nature, scalability, performance optimizations, and extensive community support.
2. Explain the difference between InnoDB and MyISAM storage engines in MySQL.
Olibr’s Expert Answer: InnoDB and MyISAM are two commonly used storage engines in MySQL. InnoDB is transactional and ACID-compliant, supporting features like foreign keys, row-level locking, and crash recovery. MyISAM, on the other hand, is non-transactional, faster for read-heavy workloads, but lacks features such as foreign keys and crash recovery.
3. What are indexes in MySQL, and how do they improve query performance?
Olibr’s Expert Answer: Indexes are data structures that improve query performance by allowing faster retrieval of rows based on indexed columns. They reduce the number of rows MySQL must examine when executing queries, speeding up data retrieval operations, and optimizing database performance.
4. Explain the difference between INNER JOIN and LEFT JOIN in MySQL.
Olibr’s Expert Answer: INNER JOIN and LEFT JOIN are SQL join types used to retrieve data from multiple tables. INNER JOIN returns rows where there is a match in both tables based on the join condition. LEFT JOIN returns all rows from the left table and matching rows from the right table, with NULL values for non-matching rows in the right table.
5. What are the advantages of using stored procedures in MySQL?
Olibr’s Expert Answer: Stored procedures in MySQL offer several advantages, including improved performance due to reduced network traffic, enhanced security by encapsulating SQL logic, code reusability across applications, easier maintenance and updates, and centralized database logic execution.
Conclusion
By mastering these MySQL interview questions and understanding Olibr’s expert answers, candidates can demonstrate their proficiency in MySQL database management, query optimization, and best practices during interviews. Olibr’s insights provide valuable guidance for preparing effectively, showcasing skills, and unlocking success in MySQL-related roles.
2 notes
·
View notes
Text
SQL Temporary Table | Temp Table | Global vs Local Temp Table
Q01. What is a Temp Table or Temporary Table in SQL? Q02. Is a duplicate Temp Table name allowed? Q03. Can a Temp Table be used for SELECT INTO or INSERT EXEC statement? Q04. What are the different ways to create a Temp Table in SQL? Q05. What is the difference between Local and Global Temporary Table in SQL? Q06. What is the storage location for the Temp Tables? Q07. What is the difference between a Temp Table and a Derived Table in SQL? Q08. What is the difference between a Temp Table and a Common Table Expression in SQL? Q09. How many Temp Tables can be created with the same name? Q10. How many users or who can access the Temp Tables? Q11. Can you create an Index and Constraints on the Temp Table? Q12. Can you apply Foreign Key constraints to a temporary table? Q13. Can you use the Temp Table before declaring it? Q14. Can you use the Temp Table in the User-Defined Function (UDF)? Q15. If you perform an Insert, Update, or delete operation on the Temp Table, does it also affect the underlying base table? Q16. Can you TRUNCATE the temp table? Q17. Can you insert the IDENTITY Column value in the temp table? Can you reset the IDENTITY Column of the temp table? Q18. Is it mandatory to drop the Temp Tables after use? How can you drop the temp table in a stored procedure that returns data from the temp table itself? Q19. Can you create a new temp table with the same name after dropping the temp table within a stored procedure? Q20. Is there any transaction log created for the operations performed on the Temp Table? Q21. Can you use explicit transactions on the Temp Table? Does the Temp Table hold a lock? Does a temp table create Magic Tables? Q22. Can a trigger access the temp tables? Q23. Can you access a temp table created by a stored procedure in the same connection after executing the stored procedure? Q24. Can a nested stored procedure access the temp table created by the parent stored procedure? Q25. Can you ALTER the temp table? Can you partition a temp table? Q26. Which collation will be used in the case of Temp Table, the database on which it is executing, or temp DB? What is a collation conflict error and how you can resolve it? Q27. What is a Contained Database? How does it affect the Temp Table in SQL? Q28. Can you create a column with user-defined data types (UDDT) in the temp table? Q29. How many concurrent users can access a stored procedure that uses a temp table? Q30. Can you pass a temp table to the stored procedure as a parameter?
#sqlinterview#sqltemptable#sqltemporarytable#sqltemtableinterview#techpointinterview#techpointfundamentals#techpointfunda#techpoint#techpointblog
4 notes
·
View notes
Text
Redgate SQL Search can help you optimize your SQL workflow.

If you work with SQL databases, you are aware of how crucial it is to have the appropriate equipment. One of the best and easiest-to-use tools for SQL searching is Redgate SQL Search. Redgate SQL Search makes it simple to locate the information you need and optimizes your process. Redgate SQL Search is a free utility that allows you to look for particular keywords, objects, and data in your SQL Server database. Finding tables, views, functions, stored procedures, and other database objects is made quick and simple with this tool.
2 notes
·
View notes
Text
What Are the Key Roles in IT Infrastructure Management?
In the modern business age of the digital world, IT Infrastructure Management is what keeps businesses running well. The task of IT infrastructure management entails efforts made in diverse areas, including the maintenance of network performance and protection of the data security. But what are exactly the major roles that make this ecosystem to be efficient?
What are the most central positions and responsibilities that propel up a reliable, safe and scalable IT infrastructure? Let us go over them at a time.

1. IT Infrastructure Manager
The head of the ladder is IT Infrastructure Manager. Such an individual is involved in planning, designing and executing the whole IT infrastructure of an organization. They make sure that every hardware, software, network as well as cloud-based service are in line with business objectives.
They have day to day tasks of budgeting IT resources, vendor selection, team management, decisions on upgrade or change of systems among others. They also liaise with the top level management to ensure that the roadmap of the infrastructure matches the growth strategies of the business.
2. Network Administrator
The Network Administrator has the duty to maintain the network systems in the company. These are local area networks (LAN), wide area networks (WAN), firewalls, routers and switches. It is their task to maintain continuous connectivity and solve any problems connected with network performance.
They can be found in the background, doing software update and vulnerability patching and management, and uptime. Businesses would be experiencing constant blackouts and jeopardized security without network administrators.
3. System Administrator
System Administrators are often mixed up with the network administrators, but they take more attention to the machines, operating systems and servers. They administer, modify, and guarantee stable performance of the computer systems particularly the multi-user computers such as servers.
General system admins are involved in a user setup, maintenance of accesses, backup, and system status. They also do software upgrades and repair hardware.
4. Database Administrator (DBA)
Most businesses rely on data in the world today. Database Administrator makes sure that vital information is stored, retrieved, and secured in a streamlined way. They keep up database platforms such as Oracle, SQL Server or MySQL, according to the requirements of the organization.
They clean up performances, configure backup and recovery procedures, apply data access control, and observe storage. They also collaborate with security departments in ensuring they guard information that may be accessed or lost without authorization.
5. Cloud Infrastructure Engineer
As other enterprises increasingly migrate to the cloud, the importance of a Cloud Infrastructure Engineer has gotten significant adoption. Such experts control systems operating in the cloud: AWS, Azure or Google Cloud.
They are to implement virtual servers, allow cloud security, cloud cost optimization, and deployment automation. They make sure that the organization takes advantage of the use of cloud technology in an effective way that neither performance nor security is affected.
6. IT Security Specialist
Cybersecurity is not an option anymore. IT Security Specialist is specialized in ensuring the safety of the infrastructure against threats, breach and vulnerability. They would watch networks and look at certain abnormal activities, use firewalls, and encrypt data, and they would make security audits frequently.
They also teach the other members of the team about good practices and adherence to regulations such as GDPR, HIPAA, etc.
7. Help Desk and Support Teams
The IT Support and Help Desk Teams are the ones who are frequently ignored, but at the same time, his workforce has to be part of the management of an infrastructure. The employees contact them when there are technical problems.
Such specialists are involved in password recovery, installation of software, and assistance. Proper support team eases productivity as issues are solved within the shortest time possible.
Conclusion
IT Infrastructure Management relies on all the diverse jobs dedicated to keep the system stable, performing well, and secure. All the job titles, be they network administrator, system admin, or cloud engineer are essential to guarantee a well-functioning technology foundation of an enterprise. The right team in the right place is not only important, but also necessary as the organizations keep on expanding and changing. Knowledge of these top functions will help businesses to organize their IT departments, prevent their outages, as well as being ready to meet any technological needs in future.
1 note
·
View note
Text
Working with stored procedures in ADO.NET? I’ve put together a practical, hands-on guide featuring six essential retrieval techniques, real-world C# code examples, and a ready-to-use SQL Server database for testing. ✅ Output parameters, return values, DataReaders, DataTables, and more! ✅ Full-featured console application to test the methods in action ✅ Clear, structured explanations to enhance your database skills
0 notes
Text
Top SQL Interview Questions and Answers for Freshers and Professionals

SQL is the foundation of data-driven applications. Whether you’re applying for a data analyst, backend developer, or database administrator role, having a solid grip on SQL interview questions is essential for cracking technical rounds.
In this blog post, we’ll go over the most commonly asked SQL questions along with sample answers to help you prepare effectively.
📘 Want a complete, updated list of SQL interview questions? 👉 Check out: SQL Interview Questions & Answers – Freshy Blog
🔹 What is SQL?
SQL (Structured Query Language) is used to communicate with and manipulate databases. It is the standard language for relational database management systems (RDBMS).
🔸 Most Common SQL Interview Questions
1. What is the difference between WHERE and HAVING clause?
WHERE: Filters rows before grouping
HAVING: Filters groups after aggregation
2. What is a Primary Key?
A primary key is a unique identifier for each record in a table and cannot contain NULL values.
3. What are Joins in SQL?
Joins are used to combine rows from two or more tables based on a related column. Types include:
INNER JOIN
LEFT JOIN
RIGHT JOIN
FULL OUTER JOIN
🔸 Intermediate to Advanced SQL Questions
4. What is the difference between DELETE, TRUNCATE, and DROP?
DELETE: Removes rows (can be rolled back)
TRUNCATE: Removes all rows quickly (cannot be rolled back)
DROP: Deletes the table entirely
5. What is a Subquery?
A subquery is a query nested inside another query. It is used to retrieve data for use in the main query.
6. What is normalization?
Normalization is the process of organizing data to reduce redundancy and improve integrity.
🚀 Get a full breakdown with examples, tips, and pro-level questions: 👉 https://www.freshyblog.com/sql-interview-questions-answers/
🔍 Bonus Questions to Practice
What is the difference between UNION and UNION ALL?
What are indexes and how do they improve performance?
How does a GROUP BY clause work with aggregate functions?
What is a stored procedure and when would you use one?
✅ Tips to Crack SQL Interviews
Practice writing queries by hand
Focus on real-world database scenarios
Understand query optimization basics
Review basic RDBMS concepts like constraints and keys
Final Thoughts
Whether you're a fresher starting out or an experienced developer prepping for technical rounds, mastering these SQL interview questions is crucial for acing your next job opportunity.
📚 Access the full SQL interview guide here: 👉 https://www.freshyblog.com/sql-interview-questions-answers/
#SQLInterviewQuestions#SQLQueries#DatabaseInterview#DataAnalytics#BackendDeveloper#FreshyBlog#SQLForFreshers#TechJobs
0 notes
Text
Mastering Dynamic SQL in SQL Server: Unleashing the Power of Flexibility
Introduction Dynamic SQL is a powerful technique in SQL Server that allows you to construct and execute SQL statements dynamically at runtime. It provides flexibility and enables you to create queries based on user input or variable conditions. In this article, we’ll explore practical examples and applications of dynamic SQL in T-SQL. Building Dynamic Queries One common use case for dynamic…

View On WordPress
0 notes
Text
SQLi Potential Mitigation Measures
Phase: Architecture and Design
Strategy: Libraries or Frameworks
Use a vetted library or framework that prevents this weakness or makes it easier to avoid. For example, persistence layers like Hibernate or Enterprise Java Beans can offer protection against SQL injection when used correctly.
Phase: Architecture and Design
Strategy: Parameterization
Use structured mechanisms that enforce separation between data and code, such as prepared statements, parameterized queries, or stored procedures. Avoid constructing and executing query strings with "exec" to prevent SQL injection [REF-867].
Phases: Architecture and Design; Operation
Strategy: Environment Hardening
Run your code with the minimum privileges necessary for the task [REF-76]. Limit user privileges to prevent unauthorized access if an attack occurs, such as by ensuring database applications don’t run as an administrator.
Phase: Architecture and Design
Duplicate client-side security checks on the server to avoid CWE-602. Attackers can bypass client checks by altering values or removing checks entirely, making server-side validation essential.
Phase: Implementation
Strategy: Output Encoding
Avoid dynamically generating query strings, code, or commands that mix control and data. If unavoidable, use strict allowlists, escape/filter characters, and quote arguments to mitigate risks like SQL injection (CWE-88).
Phase: Implementation
Strategy: Input Validation
Assume all input is malicious. Use strict input validation with allowlists for specifications and reject non-conforming inputs. For SQL queries, limit characters based on parameter expectations for attack prevention.
Phase: Architecture and Design
Strategy: Enforcement by Conversion
For limited sets of acceptable inputs, map fixed values like numeric IDs to filenames or URLs, rejecting anything outside the known set.
Phase: Implementation
Ensure error messages reveal only necessary details, avoiding cryptic language or excessive information. Store sensitive error details in logs but be cautious with content visible to users to prevent revealing internal states.
Phase: Operation
Strategy: Firewall
Use an application firewall to detect attacks against weaknesses in cases where the code can’t be fixed. Firewalls offer defense in depth, though they may require customization and won’t cover all input vectors.
Phases: Operation; Implementation
Strategy: Environment Hardening
In PHP, avoid using register_globals to prevent weaknesses like CWE-95 and CWE-621. Avoid emulating this feature to reduce risks. source
3 notes
·
View notes
Text
Database Center GCP: Smarter Fleet Management with AI

Database Centre GCP
The AI-powered Database Centre, now GA, simplifies database fleet management.
Database Centre, an AI-powered unified fleet management system, streamlines database fleet security, optimisation, and monitoring. Next 25 Google Cloud announced its general availability.
Google Cloud Database Centre is an AI-powered fleet management system. It is commonly available.
Database Centre GCP simplifies database fleet administration, including security, optimisation, and monitoring. This AI-enabled dashboard provides a unified picture of your database fleet. We want to unleash your data's power and organise your database fleet.
It replaces disconnected tools, complex scripts, APIs, and other arduous database fleet monitoring methods. Database Centre offers a complete experience using Google's AI models.
AlloyDB Aiven is also available. Omni simplifies multi-cloud AI
The main Database Centre characteristics and capabilities are:
Unified view: It eliminates information silos and the need to seek customised tools and spreadsheets by showing your whole database fleet. This provides unparalleled database knowledge.
Database Centre GCP uses AI to make intelligent insights. It actively reduces fleet risk with smart performance, reliability, cost, compliance, and security advice.
Optimise your database fleet with AI-powered support. Using natural language chat, fleet issues may be resolved quickly and optimisation ideas given. This interface uses Gemini for usability.
Database Centre GCP improves health and performance tracking for several Google Cloud databases, including:
For PostgreSQL, AlloyDB
Bigtable
Memorystore
Firestore
MySQL, PostgreSQL, and SQL Server Cloud SQL Tracking Health Issues It summarises your fleet's most pressing health issues from your Security Command Centre and Google Cloud projects. It then suggests investigating affected projects or situations. You can monitor several health issues:
Used database engines and versions;
Important databases' availability and outage risk.
How well backups protect critical databases from errors and calamities.
If resources follow security best practices.
Find databases that don't meet industry requirements. The dashboard shows category problem counts. Your Google Cloud database footprint.
Database Centre GCP improves recommendations for supported databases with general availability, addressing issues like ineffective queries/indexes, high resource usage, hotspot detection, costly commands, deletion protection not enabled, and no automated backup policy.
Gemini Integration: Gemini provides clever ideas and an easy-to-use chat interface. Gemini Chat answers database fleet health questions, makes project-specific advice, and helps determine and implement the appropriate practices. It helps troubleshoot aid performance.
Saveable Views: Users can create, store, and share persona-specific views.
Historical Data: Users can track weekly issues and new database resources.
Alerting: Centralises occurrences and database alerting policies.
Database Governance Risks: Database Centre GCP reduces database governance risks, including procedures and tools for monitoring and protecting sensitive data access throughout its lifecycle. It helps enforce best practices and identify compliance issues.
Database Centre benefits enterprises with cloud resources across several projects and products. It protects database resources against outages.
Price and Database Centre Access
Database Centre is accessible from the Google Cloud managed database services console for Cloud SQL, AlloyDB, Spanner, and Bigtable. Users with IAM rights have it enabled by default.
Google Cloud users can access Database Centre GCP for free. Natural language chat and Gemini-backed recommenders (cost and performance) require Gemini Cloud Assist. Google Security Command Central (SCC) membership is required for sophisticated security and compliance monitoring capabilities.
Database Centre data takes a few minutes to update, but sometimes it takes 24 hours.
#DatabaseCenterGCP#Database#GoogleCloud#AImodels#AlloyDBOmni#PostgreSQL#CloudSQL#News#Technews#Techology#Technologynews#Technologytrendes#Govindhtech
0 notes
Text
youtube
Dynamic Data Sorting in SQ L( Dynamic Order By Clause in SQL)
How can you sort the data based on the parameterized column names in SQL?
How can you write a stored procedure that accepts column name as input parameter and returns data sorted based on the the provided column?
Please subscribe to the channel for more videos like this: https://www.youtube.com/c/TechPointFundamentals?sub_confirmation=1
#sqlinterviewquestionsandanswers#interviewquestionsandanswers#sqlinterview#techpointfundamentals#techpointfunda#techpoint#Youtube
3 notes
·
View notes