#the sheer amount of writing we would lose if the site went down
Link
Healing is a matter of time, but it is sometimes also a matter of opportunity.
— Hippocrates
The God-Machine is sick. The God-Machine has always been sick. The God-Machine will, someday, become sick. It’s hard to tell with an entity that so flagrantly violates causality. Ultimately, the Contagion is as universal as the God-Machine that hosts it. There is scarcely a place on Earth the God-Machine hasn’t touched at one time or another, and therefore there’s scarcely a place on Earth that couldn’t host an outbreak of the Contagion. All scholars of the Contagion can really say is that history is replete with breakouts, moments where cultures and even reality itself collapsed around a point, or a person, or a practice.
Accounts of unexplainable events on such a scale stretch back as far as ancient Mesopotamia, where we first know of writing as a common practice, and therefore where written history begins. Some believe that the flood myth itself, present in so many cultures, reflects a massive, ancient outbreak, one which nearly ended the world, that is only preserved in oral histories. Not every historical record of a cataclysmic event represents the Contagion breaking through into our world through the vector of the God-Machine’s Infrastructure, of course. Earthquakes, volcanoes, meteors, and all manner of perfectly natural disasters are capable of presenting as an out-of-context problem in ancient records or literature. The Sworn, however, are not an entirely modern phenomenon themselves; contemporaries of these events, ancient or otherwise, did what they could to stem the Contagion’s spread — and must have seen some success, or, their modern descendants say, they would not be around to talk about it.
Five outbreaks in particular, however, are most relevant to the modern day, and specifically to the five factions of the Sworn, some of whom can claim traditions (if not contiguous organization) stretching back more than two thousand years. None of the factions sprang fully-formed into being. Instead, they were the result of like-minded individuals coming together in the wake of apocalyptic events, and together creating an idea that would, despite lurking only in the shadows of the world, endure the test of time. When the Sworn argue amongst themselves, more often than not these five outbreaks are the ones cited as proof that one faction or another has the right of it.
San Lorenzo Colossal Head 11: 900 BCE
The Head is massive, with details finer than any other colossal head. Even Tu, the last Olmec king seated on a crumbling throne, didn’t know which of his ancestors commissioned it. The Head had always existed, bearing the likeness not of a king, but a god. This divinity was not named, not known like the Dragon or the Feathered Serpent. It was not listed amongst the great Eight, or even any of the lesser Gods his people revered. Yet it sucked up all prayers and all life, leaving the island in the middle of the Coatzacoalcos River barren. Tu could see the future, full of desolation and endings, as clearly as he could see the gleaming metal and polished, ivory human bone behind the head’s stone facade.
The San Lorenzo Colossal Head 11 is a secret of archeology. While San Lorenzo Colossal Heads 1 to 10 are on display for tourists, the eleventh head was sequestered away when testing revealed metal alloys undiscovered by man, and elements not on the periodic table, laced in the stone. All public records of it were suppressed, though rumors and pictures survive on the Deep Web. Attempts to carbon-date it consistently fail. The head’s features are Olmec, with a broad nose and full lips, although it is more androgynous than other Colossal Heads. Large discs stretch the ear lobes, and the mouth gapes open wide as if it hungers. Its headband is incredibly detailed, full of maze-like patterns and tableaus of worship. Efforts to document the scenes portrayed in the headband have likewise failed. The sheer volume of detail, untraceable lines and figures wedged together, wears on the observer’s mind. Since its discovery, archeologists have identified 1) a city of curving spires rising towards each other from the ground, 2) human figures worshiping a towering creature with arms so large they reach the ground, and 3) a head resembling Colossal Head 11, mouth opened wide as lines of humans walk into its maw. A handful of observers have recorded different tableaus, alternating widely between a beautifully ordered utopia and a barren wasteland, but the three above are the only ones seen by more than one person. Mages, believing the Head to represent an Exarch and doing their own investigation, have had more luck.
The Head hails from the first Olmec City circa 1150 BCE. No amount of divination can reveal its creator, and none of the known San Lorenzo kings match its physical features. It’s the tallest of eleven San Lorenzo heads, at twelve feet, and impeccably detailed. The Head spoke when it was finished and unveiled, delivering a message in the first language. Priests flocked to the Head, always rushing back to the safety of their known gods once they gleaned the Head held both the end and salvation of all things. Subsequent kings ordered it buried, placed in a temple overlooking the city, and thrown in the river. None recorded its message, for those who understood could not remember it, and those who remembered could not understand it. It sucked up prayers intended for the true gods, drove kings to madness and greatness, and slowly spelled out demise. This was its Contagion: it trapped the city between the erratic extremes of obsession until it consumed all else. The skills of stonemasonry and agriculture, passed down for five centuries, faded against the presence of the Head. People forgot to eat. Children starved in their baskets as mothers were so closeto deciphering the god’s riddle that all else needed to wait. Kings sat on their thrones, so lost in thought that they were unable to govern the city, the answer lying forever just beyond their grasp. The first Olmec went into decline and was abandoned around 900 BCE, dying on the soft whisper of obsession consuming everything else.
The First Language
The first language is the code that governs the God-Machine’s programming, the Celestial Ladder, and the essence of Creation. It transcends time and space, and those who first mastered it tore it into a thousand pieces so none could follow them on this path to ascendant power. Azothic Memory retains fragments of it though, allowing Prometheans to master the dominant language of their surrounding as the first language is the root of alllanguages. This also grants all Prometheans +2 on checks to identify the San Lorenzo strain, and gives the Tammuz a further +1 bonus to resist infection.
Survivors took the Head’s feverous message with them as they left the ruins of the first city. They still did not understand its message, nor could they remember it any more clearly than a dream fading fast against the world’s light. None of them had even been alive when the Head first made its appearance, yet the Head reached for them through the stitches in time, taking them back to that first and only time it spoke. It carried on in their blood and wormed its way into their minds: The message must be understood. Where they went, Contagion followed. Sculptors throughout Olmec civilization worked bloodied fingers to the bone, sacrificing life and sanity, in an effort to re-create the Head of God. Not until the fall of La Venta, the last great Olmec city, did this strain of San Lorenzo 11 stop.
Unfortunately, the disease lingered and mutated in the earth itself. It re-emerged when the Aztecs built their city of Ten?chtitlan near the site of the lost city. They did not create any Colossal Heads, but instead turned to blood and sacrifice to decipher the message. They came close too, warriors and kings self-mutilating to read the God’s portents in the enlightenment of pain. They thrived as they solved the paradox of the message, which held both Contagion and its cure, and created an empire that spanned the Valley of Mexico. Perhaps in the vast multitudes of time and space, Contagion ended here, five centuries after the first recorded outbreak. Time is also linear though, and whatever progress the Aztecs made was buried alongside them by the cruelty of Hernán Cortés.
The Rosetta Society
The San Lorenzo outbreak spread when the city fell, embedding itself in survivors’ genetic codes and passing through contact in the form of an all-consuming obsession to decipher the message. The Olmecs suffered from it, as did the Aztecs, the Mayans, and Mesoamerican cultures like the Toltecs and the Totonac. So might the Rosetta Society, which claims Mesoamerican origins and certainly exhibits a singular focus on interpreting the meaning behind Contagion, also be infected? The answer is up to the Storyteller. It’s been a thousand years since the Mayans contained the San Lorenzo outbreak, and even Contagion could simply lose its virulence over that time. If it did carry into the Rosetta Society though, the San Lorenzo strain exhibits as the Obsession Condition in addition to the Carrier Condition. Given how insidious the San Lorenzo strain is, exhibiting as mania and eventually leading to a mental breakdown (both common enough in Sworn as it is), neither the Rosetta Society nor the other Sworn have reason to believe they’re infected.
If the San Lorenzo strain did survive inside the Rosetta Society, it remains hidden from the other Sworn. This could either be due to a mutation of the disease, or because the strain, one of the oldest in the world, has lost some of its virulence and is now easily overlooked. In this case, Sworn might not see it until it’s too late and all of the Rosetta Society is infected, or if they have active cause for suspicion and take a very close look. This hidden strain would reduce the Prometheans’ bonus to recognize it to +1, though the Tammuz do keep their bonus to resist it.
The Mayans had more luck surviving the ages, though they face marginalization and discrimination in contemporary Mexico. But their luck ran dry in deciphering the message. They searched for its meaning in blood, in ball games, and in the stars. They came close in Uxmal, the thrice-built city, where they grasped the last remnants of the San Lorenzo strain and buried it deep within the Magician’s Pyramid. The project consumed four hundred years, with building starting in 600 CE and ending in 1000 CE, and a single night as a magician erected the pyramid to escape a death sentence. It took three pyramids, layered inside each other like eggs within eggs. But finally, it was done: Contagion distilled through blood, earth, and air, and contained within a great, near-impenetrable pyramid. Containment is not a cure, but it sufficed for the Mayan people and no outbreaks of the San Lorenzo strain have been recorded since. If Mages worry what the Spanish might have taken with them when they looted the Magician’s Pyramid during their conquest of Yucatán, that is certainly no fault of the indigenous people.
The Contagion Chronicle is currently on Kickstarter.
5 notes
·
View notes
Text
I'm A Search And Rescue Officer For The US Forest Service, I Have Some Stories To Tell
by searchandrescuewoods.
Part 1 | Part 2 | Part 3 | Part 4 | Part 5 | Part 6 | Part 7 | Part 8 (Final)
So I logged back on tonight and was blown away by the staggering amount of interest this seems to have generated. First off, I'll address a few things that you guys have brought up:
There's been an overwhelming amount of people mentioning the similarity between some of my stories and those of David Paulides. I assure you I'm not trying to rip him off in any way, I've got nothing but respect for the guy. He's actually what inspired me to write this, because I can verify a lot of the things he talks about. We do have a lot of these strange missing persons cases, and most of the time they aren't solved. Either that, or we find them in places they have no business being. I personally haven't been on many calls like that, but I'll share a few that I've seen, and a story my friend told me that relates to this.
There was a lot of feedback about the stairs, so I'll touch on that briefly here, and I'll also include a story. They come in a variety of shapes, sizes, styles, and conditions. Some are pretty dilapidated, just ruins, but others are brand new. I saw one set that looked like they came from a lighthouse: they were metal and spiral, almost old-fashioned. The stairs don't go up infinitely, or farther than I can see, but some sets are taller than others. Like I said before, just imagine the stairs in your house, as if someone cut-and-pasted them in the middle of nowhere. I don't have any pictures, it's never really occurred to me to try again after the first time, and I don't really feel like risking my job over it. I'll try again in the future, but I can't really promise anything.
A few people expressed confusion about the guy who ran into the man with no face. Just to clarify, when the climber ascended and reached the top of this peak, he saw another man in a parka and ski pants. This was the man with no face. Sorry about the confusing wording of that story, I'll try to avoid that in the future.
Alright, on to the new stories:
As far as missing persons go, I'd say about half the calls I get are related to that. The others are rescue calls; people who fall down cliffs and hurt themselves, get injured by fire (you wouldn't believe how often this happens, mostly drunk kids), get bitten or stung by animals or insects. We're a tight team, and we have veterans who are excellent at finding signs of lost people. That's what makes these cases where we never find any trace of them so frustrating. One in particular was upsetting for all of us, because we did find a trace of them, but it just led to more questions than answers. An older man had been hiking alone on a well-established trail, but his wife called to say that he hadn't come home when he should have. Apparently he had a history of seizures, and she was worried that he hadn't taken his medication and had suffered one out on the trail. Before you ask, I have no idea why he thought it was okay to go out alone, or why she didn't go with him. I don't ask about that kind of thing because past a certain point, it really doesn't matter. Someone is missing, and it's my job to find them. We went out in a standard search formation, and it wasn't long before one of our vets found signs that the guy had gone off the trail. We grouped up and followed him, spreading out in a fan to make sure we were covering as much ground as possible. Suddenly, a call comes over the radio telling us to all head back to the vets location, and we come right away, because this usually means the missing person is injured, and we need a full team to help get them out safely. We meet back up, and the vet is just standing at the base of a tree with his hands on the sides of his head. I ask my buddy what's going on, and he points up into the branches of this tree. I almost couldn't believe what I was seeing, but there's a walking stick dangling from a branch at least thirty feet off the ground. The little strap thing on the handle has been looped around the branch, and it's just hanging there. There's no way the guy could have tossed it up that far, and we don't see any other signs that he's still in the area. We call up into the tree, but it's obvious no one's in it. We're all just sort of left scratching our heads. We keep searching for the guy, but we never find him. We even bring our canines out, but they lose his scent long before this tree. Eventually, the search is called off, because there are other calls we have to attend to, and past a certain point there's not much we can do. The guy's wife called us every day for months, asking if we'd found her husband, and it was heartbreaking to hear her get more and more hopeless each time. I'm not sure why this call in particular was so upsetting, but I think it was just the sheer improbability of it. That and the questions that were raised. How the hell had this guy's cane ended up there? Did someone kill him and toss that up there as some weird trophy? We did our best to find him, but it was almost like a taunt. We still talk about that one from time to time.
Missing kids are the most heart-breaking. Doesn't matter what circumstances they go missing under, it's never easy, and we always, always dread the ones we find deceased. It's not common, but it does happen. David Paulides talks a lot about kids SAR teams find in places they shouldn't be, or couldn't be. I can honestly say I've heard about this kind of thing happening more than I've seen it, but I'll share one of the ones that I think about a lot that I witnessed personally. A mother and her three kids were out for a picnic in an area of the park that has a small lake. One is six, one is five, and the other is about three. She's watching them all really closely, and according to her, she never lets them out of her sight at any time. She never saw anyone else in the area either, which is important. She packs their stuff up and they start to head back to the parking area. Now, this lake is only about two miles into the woods, and it's on a very clearly established trail. It's almost impossible to get lost getting from the parking area to it, unless you're deliberately going off the path like an imbecile. Her kids are walking in front of her, when she hears what sounds like someone coming up the path behind her. She turns around, and in the four or so seconds she's not looking, her five-year-old son vanishes. She figures he's stepped off the trail to pee or something, and she asks her other two where he went. They both tell her that 'a big man with a scary face' came out of the woods next to them, took the kid's hand, and led him into the trees. The two remaining kids don't seem upset, in fact she says later that it seems like they've been drugged. They're sort of spacey and fuzzy. So of course, she freaks out, starts looking frantically in the area for her kid. She's screaming his name, and she says at one point she thinks she heard him answer her. Now obviously she can't go blindly running into the woods, she's got the other two kids, so she calls the police and they send us out immediately. We respond, and we start the search for him.Over the course of this search, which spans miles, we never find a single trace of the kid. Canines can't pick up any scent, we don't find any clothing or broken bushes or literally anything that would signify a child being there. Of course there's suspicion about the mother for a while, but it's pretty clear that she's completely destroyed by the whole thing. We looked for this kid for weeks, with a lot of volunteer help. But eventually, the search peters out, and we have to move on. The volunteers keep searching, though, and one day we get a call on the radio letting us know that a body has been found and needs to be recovered. They tell us the location, and none of us can believe it. We figure it has to be a different kid. But we go out there, about 15 miles from the site where he vanished, and sure enough, we find the body of the kid we've been looking for. I have been trying to figure out how this kid got where he did ever since we found him, and I've never come up with an answer. A volunteer just happened to be in the area, because he figured he might as well look in places no one else would think to on the off chance the body had been dumped. He comes to the base of a tall, rocky slope, and half-way up, he sees something. He looks through his binoculars and sure enough, it's the body of a little boy, stuffed in a little opening in the rock. He recognizes the color of the kid's shirt, so he knows right away that it's the missing boy. That's when he calls it in, and we're dispatched. It took us almost an hour to get his body down, and none of us could believe what we were seeing. Not only was this kid 15 miles from where he'd started, there was no possible way he could have gotten up there on his own. This slope is treacherous, and it's hard even for us with our climbing gear. A five-year-old boy had no way of getting up there, of that I'm certain. Not only that, but the kid doesn't have a scratch on him. His shoes are gone, but his feet aren't damaged or dirty. So it wasn't as if an animal dragged him up there. And from what we can tell, he hasn't been dead that long. He'd been out there over a month by that point, and it looked like he'd only been dead for, at most, a day or two. The whole thing was unbelievably strange, and was one of the most disconcerting calls I've ever been on. We found out later that the coroner determined the kid had died from exposure. He'd frozen to death, probably late at night two days before we found him. There were no suspects, and no answers. To date, it's one of the weirdest things I've ever seen.
One of my first jobs as a trainee was a search op for a four-year-old kid that had gotten separated from his mom. This was one of those cases where we knew we were gonna find him because the dogs were on a strong scent trail, and we saw clear signs that he was in the area. We ended up finding him in a berry patch about half a mile from where he'd been last seen. Kid wasn't even aware that he'd wandered that far. One of the vets brought him back, which I was glad for because I'm really not good with kids, and I find it hard to talk to them and keep them company. As my trainer and I are headed back, she decides to take me on a detour to show me one of the hot spots where we tend to find missing people. It's a natural dip in the land near a popular trail, and people will usually move downhill because it's easier. We hike out there, it's a few miles away, and we get there in about an hour or so. As we're walking around the area and she's pointing out places she's found people in the past, I see something in the distance. Now, this area we're in is about eight miles from the main parking area, though there's back roads you can take to get closer if you don't want to hike that far. But we're on state-protected land, which means there can't be any kind of commercial or residential development out here. The most you'll ever see is a fire tower or makeshift shelter that homeless people think they can get away with building. But I can see from here that whatever this thing is has straight edges, and if there's one thing you learn quickly, it's that nature rarely makes straight lines. I point it out, but she doesn't say anything. She just hangs back and lets me wander over and check it out. I get within about twenty feet of it, and all the hair on the back of my neck stands up. It's a staircase. In the middle of the fucking woods. In the proper context, it would literally be the most benign thing ever. It's just a normal staircase, with beige carpet, and about ten steps tall. But instead of being in a house, where it obviously should be, it's out here in the middle of the woods. The sides aren't carpeted, obviously, and I can see the wood it's made of. It's almost like a video game glitch, where the house has failed to load completely and the stairs are the only thing visible. I stand there, and it's like my brain is working overtime to try and make sense of what I'm seeing. My trainer comes and stands next to me, and she just stands there casually, looking at it as if it's the least interesting thing in the world. I ask her what the fuck this thing is doing here, and she just chuckles. 'Get used to it, rookie. You're gonna see a lot of them.' I start to move closer, but she grabs my arm. Hard. 'I wouldn't do that.' She says. Her voice is casual, but her grip is tight, and I just stand there looking at her. 'You're gonna see them all the time, but don't go near them. Don't touch them, don't go up them. Just ignore them.' I start to ask her about it, but something in the way she's looking at me tells me that it's best if I don't. We end up moving on, and the subject doesn't come up again for the rest of my training. She was right, though. I'd say about every fifth call I go on, I end up running across a set of stairs. Sometimes they're relatively close to the path, maybe within two or three miles. Sometimes they're twenty, thirty miles out, literally in the middle of nowhere, and I only find them during the broadest searches or training weekends. They're usually in good condition, but sometimes it looks like they've been out there for miles. All different kinds, all different sizes. The biggest I ever saw looked like they came out of a turn-of-the-century mansion, and were at least ten feet wide, with steps leading up at least fifteen or twenty feet. I've tried talking about it with people, but they just give me the same response my trainer did. 'It's normal. Don't worry about it, they're not a big deal, but don't go close to them or up them.' When trainees ask me about it now, I give them the same response. I don't really know what else to tell them. I'm really hoping someday I get a better answer, but it hasn't happened yet.
This is another one that was less spooky and more sad. A young man went missing late in winter, when realistically no one should be going that far out onto the trails. We close a lot of them, but some remain open year round, unless there's a shit-load of snow. We did an op for him, but we had about six feet of snow on the ground (it was an unusually heavy snow year), and we knew it wasn't likely that we'd find him until spring when the thaw came. Sure enough, when the first big thaw came, a hiker reported a body a little ways off the main trail. We found him at the base of a tree, in a pile of melted snow. I knew right away what had happened, and it scared the living shit out of me. Most of you who ski or snowboard, or spend any amount of time on a mountain, will probably have guessed too. When snow falls, it doesn't collect as thick in the areas beneath the branches. It happens most with fir trees, because they have a sort of closed umbrella shape. So what you end up with is a space around the base of a tree that's filled with a mixture of loose, powdery snow, air, and branches. They're called tree wells, and they're not immediately obvious if you don't know what you're looking for. We put up signs in the welcome center, big ones, letting people know how dangerous they are, but every year that we get an unusual amount of snow, at least one person doesn't read them, or doesn't take the warning seriously, and we find out about it in spring. My best guess is that this young man was hiking and got tired, or maybe a cramp from walking in the deep snow. He went to go sit at the base of the tree, not knowing that there was a tree well, and fell in. He got stuck with his feet up, and the surrounding snow caved in around him. Unable to free himself, he suffocated. It's called snow immersion suffocation, and it doesn't usually happen except in really deep snow. But if you get stuck in a weird position, like this guy did, even six feet of snow can be lethal. What scared me the most was imagining how he must have struggled. Upside down, in the freezing cold, he didn't die quickly. The snow would have formed a dense, heavy pile on top of him, and it would have been literally impossible to get out. As it got harder to breathe, he would have known what was happening. I can't even imagine what he was thinking in his last moments.
A lot of my less outdoorsy friends want to know if I've ever seen the Goatman while I've been out on calls. Unfortunately, or I guess fortunately, I've never had anything quite like that happen. I guess the closest was the whole 'black-eyed man' thing, but I didn't see anything. However, there was one call where I had something kind of similar happen, but I'm not sure I'm willing to chalk it up to the Goatman. We'd gotten a report that an older woman had fainted along one of the trails, and needed assistance getting back down to the main area. We hike up to where she's at, and her husband is just beside himself. He runs, well, I guess more jogs, to us, and tells us that he was a little ways off the trail looking at something when his wife starts screaming behind him. He runs back to her and she's passed out on the trail. We get her on a backboard, and as we're getting her down to the welcome center, she comes to and starts screaming again. I calm her down and ask her what happened. I can't remember verbatim what she said, but essentially, what happened was this: She'd been waiting for her husband when she started hearing this really strange sound. She said it sounded sort of like a cat, but it was off somehow, and she couldn't quite figure out why. She went a little ahead to try and hear it better, and it sounded like it was coming closer. She said the closer it got, the more uneasy she was, until she finally figured out what was wrong. I do remember this next part, because it was so weird that I don't think I could forget it if I tried. "It wasn't a cat. It was a man, saying the word 'meow' over and over. Just 'meow, meow, meow'. But it wasn't a man, it couldn't have been, because I've never heard a man make his voice buzz like that. I thought my hearing aid was going out, but it wasn't, I adjusted it and it still sounded all buzzy. It was awful. He was coming closer, but I couldn't see him. And the closer he got the more scared I was, and the last thing I remember was a shape coming out of the trees. I guess that's when I fainted." Now, obviously I'm a little perplexed as to why a guy would be out in the fucking woods chanting 'meow, meow' at people. So once we get down the mountain, I tell my superior that I'm gonna go search the area to see if I can find anything. He gives me the go ahead, and I grab a radio and hike back to where she fainted. I don't see anyone, so I keep going about a mile more, and I when I head back I go off the trail, to see if I can figure out where she saw him coming from. It's almost sunset by this point, and I don't have any desire to be out at night alone, so I just sort of write it off and make a mental note to check it out again tomorrow. But as I'm headed back, I start to hear something in the distance. I stop, and I call out for anyone in the immediate area to identify themselves. The sound didn't come closer or get louder, but it sounded exactly like a man saying 'meow, meow' in this really odd monotone. As comical as it makes it sound, it was almost like that guy on South Park with the electrolarynx, Ned. I go off the trail in the direction I think it's coming from, but I never seem to get closer. It's almost like it's coming from all directions. Eventually, it just sort of fades out, and I ended up going back to the welcome center. I didn't get any further reports like that, and even though I went back to that area, I never heard that exact sound again. I suppose it could have been some stupid kid out there fucking with people, but even I have to admit it was weird.
So this kind of turned into a massive wall of text, and for that I apologize. I wanted to get to the stories my friend told me, and he does have some good ones, so I'll post those tomorrow evening. I also have a few more of my own I think you guys will like. I'm sorry to keep you all in suspense again, hopefully the stories here make up for it and help you get through the next 24 hours until I can post again!
77 notes
·
View notes
Link

John Glaser-USA TODAY Sports
The time has come to put down on imaginary paper what type of season we think the Tigers will have this fall
This past weekend finally made it real. College football is actually back.
Yes, there have been and will continue to be some major hiccups this season but there WILL be a season and fans will get a chance to watch their beloved Auburn Tigers take the field this fall. For a year that has been most unpleasant having the ability to shut out the world for 3-4 hours and let our blood pressure rise to unhealthy levels as we watch Auburn do battle on the gridiron is a most wondrous blessing.
So with kickoff being just under two weeks away, it’s time the sages here at College & Magnolia put down in writing their expectations for this 2020 Auburn football team. This year, more than any other, feels the most unpredictable. Games that seem like obvious wins right now could turn into multi score losses if a positive tests pops up on the wrong position group. Chances are good at least one game will be disrupted, positively or negatively, for Auburn this season due to COVID-19.
But your wise contributors on this here internet street will do our best to enlighten you, our loyal readers, on proper expectations for this fall. Season prediction takes, let’s have em!
AUNerd
8-2 would be a good season for Auburn this fall. 6-4 would be a bad one. I have no idea how I would feel about 7-3 so obviously that’s exactly what will happen. I’m not sure who exactly Auburn loses to outside of Bama this season but my general guess is Auburn goes 2-2 vs Bama/UGA/LSU/A&M then drops a frustrating one to either UK or Tennessee. It wouldn’t shock me to see Auburn start 7-0 then lose their last 3 plus the bowl game to send us into another off-season of debate over whether or not Gus Malzahn should keep his job.
But also ya’ll... This year feels as chaotic as every so why not some Chaos Auburn?
Verdict: 7-3
Joshdub
The folks in Vegas (typically not dumb!) place the over/under on 6.5 wins for Auburn this year. 6.5...that seems very precarious. I have no idea if Auburn will struggle to pass protect, put Bo in lots of bad situations, and force him to make bad throws. I have no idea if Chad Morris can overcome any 2020-related obstacles and produce another juggernaut offense. But when you’re making preseason predictions, swing for the fences. Echoing Nerd: expect CHAOS AUBURN. Auburn will ruin ALL YOUR NICE THINGS (um, including a perfect season for Auburn, who will definitely lose an early game they are actually favored to win (please not to lane kiffin, please not to lane kiffin, please not to la-))
Verdict: 9-1
Ryan Sterritt
As we saw in the first week of power conference games, we may be in for some ugly football this year. I think (hope?) that lends itself to teams with established quarterback play, although replacing seven starters across the two lines of scrimmage might cause more than enough issues. Still, despite the inherent difficulty of an all-SEC schedule, things line up relatively nicely for Auburn. UGA seems to be in crisis mode with a new OC, chaos at quarterback, injuries at WR, and new starters on the OL. LSU is replacing effectively their entire starting lineup. Texas A&M is suffering a slew of withdraws, most recently leading to their top returning wideout having three (3!) catches last season.
It’s going to be a frustrating season, I think, but it’s important to remember everything these players and coaches have done to even get to this point. I think we knock off Georgia in Athens for the first time since 2005, AND we knock off the defending champion LSU. I also think Alabama has no excuse to lose a single game this year, and it would not surprise me if random COVID cases or contact tracing bites us in some other game.
Verdict: 8-2
Will McLaughlin
I see Auburn splitting the first 2 games, then see the Tigers getting on a roll. The Tennessee game is a must win for Gus this year but I can see Auburn getting to the Iron Bowl at 6-2.
Verdict: 7-3
AUChief
Only one thing is clear about the upcoming season: it’s gonna be a weird one. The fact that you are reading this article in mid-September talking about an upcoming season is only one of many indicators that it’s already weird. And so that makes predicting what will happen even harder than usual. As Auburn fans, we have learned to embrace weirdness over the years. Doesn’t it just feel like this is the kind of year Auburn can do something special? A year that only the ultimate victors won’t assign a huge asterisk to each and every opponent win? People could get sick or opt out at any point, throwing an otherwise good team into chaos.
All that said, let’s see where Auburn ends up. I think Bo Nix is going to have a whole new lease on life this year. He’s going to have an opportunity to throw a lot of high percentage passes to his TEs, and the running back situation is miles ahead of where it was last year. The only question for me is the OL, but I don’t see it being worse than the last few years. I have complete faith in our defensive staff to get the best out of the players on that side of the ball. Auburn is going to go 9-1. The loss will come to Kentucky, LSU, or Alabama. I know what you are thinking, “Kentucky?!” It’s gonna be a weird year folks, so hold onto your butts. LSU seems the least likely to me out of the three. Alabama will obviously be good. They managed to somehow avoid any opt outs. 9-1 will only be good enough to get us to the title game if the loss is to UK or LSU, so hope for one of those. Let’s assume that’s the case and say we will face Florida in the SECCG, winning 42-27. After that we’ll eventually face Clemson in the national title game.
Am I Barning hard enough for you people? Anyway, War Damn Eagle.
Verdict: 9-1
Josh Black
I am far more skeptical on this season than most here. Pre-COVID my skepticism was rooted in a simple truth that has held up for the most part in the history of this conference: It’s hard to be confident when you don’t know what you have at the line of scrimmage.
I expect the offense to show signs of legitimate progress under Chad Morris, and provide further compliment to Bo Nix’s potential, especially with more passing concepts, A TIGHT END (!), and a far more talented running back room than we’ve had the last 2 years. I also expect our offensive line to struggle mightily at different points throughout this season. It’s not for a lack of talent, but it hurts us early that we didn’t have spring to help those 5 to gel. It hurts even more than it’s hard to find 5 guys consistently with COVID, so early on communication between the guys is going to be rough.
Defensively I expect Kevin Steele and Co. to continue reinforcing the sterling reputation the Auburn Defense has earned since 2016. Questions abound for me up front though, once again, as you are going to feel the impact of losing not just the insane talent of Derrick and Marlon, but the amount of sheer snaps they had. That experience is a heavy burden for Truesdell, but what is around him are a bunch of guys who need to step up and/or grow up quick. Same holds true in the secondary, where Auburn is quietly producing 1st round NFL talent nowadays. I have zero doubt about the abilities of our back 4-5, but quality depth matters, especially at corner, and I’ll need to see it before getting my hopes elevated.
I’m going to do a breakdown of how I see this schedule going with what I think will happen, and the best case/worst case scenario:
Kentucky - Win (Do not take this team lightly, as they can come into Auburn and win. They’re extremely well coached.)
at Georgia - Loss (We can absolutely win this game as I don’t feel threatened by the quandary Georgia finds themselves in at QB (you just hate to see it), but they have arguably the best defense in the country depending on if Ohio State plays football this fall, and I think we’re going to need 21+ points to win. I don’t have a lot of confidence that happens in Athens.)
Arkansas - Win (LOL yeah no...Gus and Chad ain’t losing to Arkansas)
at South Carolina - Win (Abysmal offensive football team with a lack of talent to beat Auburn)
at Ole Miss - Win (Lane will beat someone he shouldn’t in year one, but they’ve got enough problems defensively that tell me it won’t be us.)
LSU - Win (Coin flip game prior to LSU basically deciding to take the year off. I don’t blame them. 2011 sucked for us too. Still though, they’re LSU and an obvious threat, but this is a game we should win, especially since Dave Aranda, who had our number, is gone.)
@ Miss. State - Win (Some other SBN site will tell you State is the most talented team in the conference. That site is laughably wrong.)
Tennessee - Win (Must win game for us that absolutely could go the other way. Sucks to say but Jeremy Pruitt has had our number way too often. Easily the most dangerous game on this schedule that I almost went with my gut and predicted a “Chaos Auburn” loss.)
Alabama - Loss (They’re loaded. Their schedule gets easier with every opt-out we see. Nobody outside of Clemson is beating them this year.)
Texas A&M - Win (Much like Tennessee, this is a true coin flip game for us. Beat up after the Iron Bowl means something here, as it did in the 2017 SEC Championship. Still, the day I put money on Kellen Mond or Jimbo Fisher being worth a damn without insane talent all around them is the day I go broke. We should win this game. We could lose this game.)
So I say we’re 8-2, with Kentucky, Tennessee, and A&M being games that could absolutely derail all of our hopes and dreams for something better. I do see the 2 losses I mentioned being definite. This team is going to show improvement at best, and confusion at worst. We’re a year away, basically. But I also expect 2021 to be the year where we actually enter the College Football Playoff, so I’ll take it in a year where there are more important things going on than football, especially knowing that the Georgia game and Alabama games are on the road in front of mostly nobody. To hell with both of them.
You’ve read our takes, now it’s your turn. Give us your prediction for this 2020 Auburn Tiger football team.
War Eagle!
from College and Magnolia - All Posts https://www.collegeandmagnolia.com/2020/9/14/21434903/c-m-roundtable-predict-auburns-2020-season-record
0 notes
Text
As I write it’s dark and cold outside – but the days seem to be just a teensy bit longer all of a sudden.
It’s no illusion. The shortest one of the year (Sunday the 22nd of December) is now behind us – and from this point on the UK will only get lighter and the days longer.
I can almost feel the warmth of summer on my back.

That’s partially because (despite a rocky few weeks) I actually had a really active and on plan second half to the month.
It got worse before it started to get better though, because when I stepped on the scales at home on the 15th of this month (after some hefty emotional eating) they greeted me with a somewhat sobering 17st 9.5lbs.
I knew what was going on.
I’ve been quiet for a reason.
As well as encountering some unexpected health worries (which seem for the time being to be OK) the whole issue of not finding work has been eating away at my self confidence, and I’ve found it very hard indeed to not hibernate or eat away the upset it’s been causing.
That’s not to say that I’m not taking positive steps mind you. I’ve been working through a couple of self help books and looking at understanding what I really want rather than what I feel I have no choice about and should apply for.
It’s not easy though when you’v been turned down four times in a row for jobs that you know would be a walk in the park – but I guess if nothing else it’s character forming, and what will be will be.
It’s also Christmas, nobody is hiring and Brexit looms.
Even the job sites that were previously spamming me with unhelpful adverts have dried up over the last three to four weeks, and my inbox is mercifully devoid of mail reminding me that I’m not proving to be particularly successful in this area.
However – back to the scales.
Free from the self imposed guilt of being over target as man of the year I have now instituted a new regime.
I have up until recently focusing on my new project – which is feeling guilty about an out of target ex-man of the year.
The former guilt was because I should be a positive example of a man with a title and the latter because I don’t want to be seen to have ‘let myself go’ after everyone believed in me and looked to me for inspiration.
Sigh.
One day maybe I’ll stop doing this to myself…
However I know I’m not alone in such quagmires of spiralling thoughts – and it seems that as much as I’ve been amazed by the capability of fellow slimmers to change their shapes and life outcomes I’ve also been encouraged that they too struggle like heck at some time or another when it comes to maintenance.
Practically everyone of them I know (or just follow on social media) has posted some epic gains followed by a correspondingly epic loss – and almost everyone that’s achieved a measure of success is now differnent to the weight they were when they held aloft their local or national awards.
I’m not alone – so why feel any shame?
Thankfully at the moment I’m not.

Over the last two weeks I’ve managed to lose an entire stone (even though it doesn’t look like that in my book) and it’s been through sheer hard work and effort.
Dropping weight over Christmas has been a challenge though – and I’m not going to lie – this could have gone either way. During the last week I ate Stollen, Gingerbread, Cheese, Christmas cake, biscuits, an entire layer of chocolates from a box of Milk tray and a rather hefty roast and three mincemeat wraps on Christmas day.
I’ll be honest – had I been on my own I might not have celebrated this way – but this has been my very first traditional Christmas as ‘family’ (or probably more accurately a ‘couple’) and as such I really wanted to enjoy the experience as everyone else does.
With great food and awful jumpers.

The fact is though that whilst I enjoyed myself as much as I felt I could I also limited damage elsewhere as much as humanly possible (although it may not sound like it) as well as doing a rather epic amount of exercise.
Although I consumed a lot of naughty food on the 25th I also went for a TEN MILE WALK through the wilds of Warwickshire to make up for it.

If I add my daily active (anything I burn with exercise) and standard (2500kcal for an adult male) calorie burn together then I’ve been averaging around 4500 per day for the last two weeks, which is the main reason I lost weight after packing away cheese and cake.
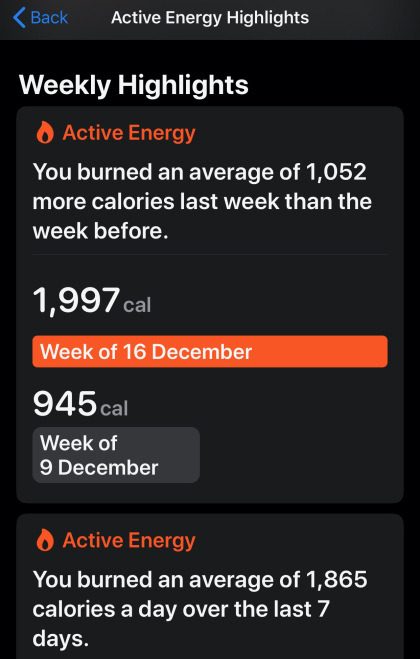
A lot of this was due to swimming – which once again has proven to be my absolute saviour. This has been particularly gratifying when I look back on it because despite my reluctance to don my trunks and look like a human muffin in the mornings ( I hadn’t been for almost two whole weeks) I did it anyway.
It’s not been the only exercise I’ve engaged in though – and I’ve relied on an old friend to fill the gaps for me when the pool has been closed. My walking distance has remained consistently higher and at averaged over 10 miles a day for two weeks as well – despite driving to Sussex and back on Monday.

So – life is (for the moment at least) on an even dietary keel again.
Both myself and my better half are really in the zone at the moment – and she has been swimming alongside me every day as well.
It’s fair to say that her determination to improve both her swimming technique and stamina have been something of an inspiration to me – and on Sunday I found myself watching her swimming back and forth in the pool well after I’d stopped.
Consequently her loss over the xmas week was greater than mine (2.5lbs!!!) and she really deserved it.
I’ve been positively swelling with pride as I’ve watched her get better and better at swimming through sheer determination and grit – and there’s no small amount of warm fuzzy feelings inside me at the moment.
Christmas this year has been special in a way that no other Christmas has because although I’ve had long term partners before not a single one has ever resulted in a Christmas together prior to this point.
There’s always been a family reason or a break up to get in the way of that before and consequently words absolutely fail me when I try to encapsulate how much December 2019 has meant to me.

It’s not been about materialism or nerdy presents (of which there have actually been quite a few thanks to a new and very generous extended family) – but togetherness.
This manifested itself recently when we both headed out to see a new film – and both of us chose appropriate attire for the occasion.

It’s hard to overstate how much love a geeky guy can feel when he’s accompanied on a school night to a one minute past midnight screening of Star Wars by an adult woman not only voluntarily (and dare I say enthusiastically) wearing a Star Wars teeshirt but also a crochet’d Yoda ears beanie.

I’m sure that everyone out there is already throwing up in their mouth a little bit – but I’m sorry – I have absolutely zero shame on this score because we totally owned it in The Rise of Skywalker.

My Christmas has been everything that I’ve always wanted it to be but never dared to hope it ever would be.
For the longest time it looked like the picture below, and because of my habitual behaviour on this score I never once managed to get to the end of ET The Extra Terrestrial on TV.

In contrast this year the strongest drink I’ve indulged in is a caramel flavoured coffee, and I’ve not been alone and sad for a single moment.
I’ve shared the walks, talks and occasion with someone I care deeply about. Together we’ve continuously supported one another whenever we’ve hit bumps in the road and continue to do so.
Sigh. Over the last few days I’ve been reflecting on my happiness – but also on my past.
That bottle of Southern Comfort seems a long long way away now and it’s been a long time since this was my reality.
Other people may still be in a darker place though and as I type I’m conscious of this.
At this time of year there are many people on the cusp of giving up hope that life will ever hold anything for them but loneliness or despair. They suffer in silence and often succumb to darker voices that hide inside.
As well as hearing of other slimmers that have struggled recently I’ve also read about those that have been moved to other, maybe more destructive forms of self harm in the past and because of this as I write I’m left feeling sober in more ways than one.

There was a time that I felt similarly and when I sat alone at home (not just around Christmas time) there were many many moments when I no longer wanted to be around.
Had I been ‘braver’ (stupider?) I may have crossed a line that would have seriously curtailed my time on earth.
I contemplated this more than once – and now (on the wrong side of my forties) I have so much to be grateful for.
I’m left at times feeling as if I have no right to be as happy as I am – like I’ve stolen the joy that must belong to someone else, because there are moments that it all still feels very alien.
Life though is all about context – and finding this to gain perspective is something we all struggle to do.
There are many of us who (despite there often being much evidence to the contrary) choose to label ourselves as ‘lonely’, ‘overweight’, ‘failure’, ‘alcoholic’, ‘addict’, ‘loser’, ‘stupid’, ‘weird’, or consider ourselves simply ‘unlovable’.
With the new year looming, and many people who read my blog coming from similar places to the one I did (physically and emotionally) all I can say is that there is hope.
If you’ve followed (or are just beginning to follow) my journey then I want you to see and feel what I feel and see. Hopefully if you’ve travelled with me through both the light and the dark moments in the last four years then I’ll have left you with a sense of positivity and optimism.
Maybe your life isn’t going the way that you wanted it to – but in this blog is all the evidence that you need that it can surprise you.
With effort and determination you can change things – and good vibrations sent out into the world inevitably come back when you least expect them to but most need them.
Life is a collection of moments where you can fail more often than not – where it’s easy to think there’s no point – or convince yourself that people don’t need you around, when in fact they really really do.
They gain as much from having you in their lives as you do from having them in yours.

Although I’m not into sport particularly I can’t help thinking of a quote from Wayne Gretsky – the Canadian former professional ice hockey player and former head coach of their National team.
He’s probably said a lot of forgettable things – but one that for some reason really struck me was this one.
‘You miss 100 percent of the shots you never take.’
It’s true.
If you don’t try to be better then it won’t happen by magic.
So – 2020 is fast approaching.
What do you want it to be?
Personally I’d like it to contain everything you desire and need and wholeheartedly believe that it can do if you want it enough.
So – what are you waiting for?
Get up, put your coat on and make it happen.
Davey
100 percent of the shots As I write it's dark and cold outside - but the days seem to be just a…
0 notes
Quote
The Streetwear Startup forum lets aspiring creative directors figure out whether their graphics are cool—and where they can get blank tees to print them on.There is absolutely no good reason the words “yo pierre, you wanna come out here?” should be here pinned on the page for Reddit’s Streetwear Startup subforum. Clicking on the words leads you nowhere, and the phrase—first heard on the Jamie Foxx Show and more recently popularized by hip-hop producer Pierre Bourne—doesn’t have anything to do with the page’s function: convening an unusually friendly online community to help burgeoning streetwear designers launch their brands. But it turns out that “yo pierre” is a perfect symbol for a genre of clothing that thrives on coded imagery—ranging from Coca-Cola to Dragon Ball Z—to signal to other people you’re hip, you’re in the know, and yes, you would like to come out here.The streetwear startup aims to dissect the very concept of cool. Can the designs and signals that have catapulted brands like Supreme and Kith into the fashion stratosphere be focus group-tested until you’ve found the thing that resonates with customers? After all, if the almost-14,000 users on the page think your piece is a must-cop, it’s also possible that Miami Dolphin Jarvis Landry will too, and will then wear it on ESPN, like he did with streetwear startup success story Rude Vogue. And if this chorus of voices say fire, there’s a decent chance the streetwear press will join in, like Hypebeast did with the brand Deadnight.Anyone with an Instagram account would be forgiven for thinking that the streetwear market is oversaturated with streetwear brands. But others see the endless stream as a siren call to jump into the fray. But the rush with coming up with a catchy name—seriously, it can be anything; the most popular streetwear brand in the world is called Supreme—can make you forget there are logistics to be dealt with. How do you get your vision on the screen? How do you make other people fuck with that vision? How do you get that art on a T-shirt? And, wait, where do you even get those T-shirts from? And once you have the T-shirts and someone willing to shell out the cash for it… what then?How do I get these printed?Streetwear Startup is built to answer those questions. “I want to keep it as open as possible and for it to be for anyone curious about brand startup as a whole,” says Dustin Wilkie, a recent UNC-Asheville grad who moderates the subreddit. The subreddit was formed, in November of 2013, and Wilkie, who was working on a brand of his own at the time, joined almost immediately. Wilkie says the person “who actually made it just doesn't use it, and I don't even have contact with them any more”—a poetic start for a page that’s all about trial and error. Wilkie was put in charge because he was the longest-tenured member.The subreddit’s main services can be broken down into two parts: beginner questions (What’s the best ecommerce site?) and brand feedback (What logo do you like most?). Wilkie’s goal is to eradicate the first part by compiling a How to Streetwear 101 handbook that will contain everything you need to get from idea to brand. “We have a pretty big problem with people posting the same beginner question over and over,” Wilkie laments. The ”wiki” currently covers four topics but “we're creating a how to beginner's guide that should handle all of those questions,” Wilkie says.“The subreddit is filled with people who are grinding away every day in the same way as me,” says Slade, a 20-year-old college student studying graphic design in Missouri who founded the brand VVID. “Oftentimes, they've stumbled and had to learn during their journey, too, and they're nice enough to impart that knowledge to me, and in turn I get to circumvent those mistakes.”Wilkie says the page has been growing quickly recently, though he can’t pinpoint the exact reason for all the newfound subscribers. Jaffry Mallari, a 19-year old Geomatics Engineering Technology student at the Southern Alberta Institute of Technology, says that when he joined almost two years ago, there were only around 2,000 followers. He took a break after his first brand went to that friendly Shopify site in the sky, but when he came back around a year ago the number of subscribers had tripled to 6,000. Now it stands at around 14,000 members—and more people means more voices. “There is more information now,” Mallari says. “So now it's like more of a struggle [to get to the top post] but since there's more competition now it made me push harder on my designs.” Mallari dubbed his new brand Resurgence: “To fix the mistakes that I’d made and to do twice as well as before—that's the meaning of the brand.”When I catch Slade on email he tells me he was getting “sewing 101 tips.” Others start by sponging up even more rudimentary knowledge. Mallari recounts his first experience on the page: “I just kept putting in designs and kept asking questions, like, ‘What websites do I use? How do I get these printed?” Mallari says that the first brand he made “crumbled and fell off” after a bad business decision. “But back then I was still new to it and I thought [I’d found] an easier way. That's when I learned the hard way that's not how you need to run something.”Everyone started from the bottomBuilding a career in fashion takes time: Alessandro Michele worked anonymously for more than a decade at Gucci before being handed the reins. Building a career on r/StreetwearStartup is a considerably quicker process. “I have been posting in the subreddit showcasing my collections for about 18 months now,” says Sam Hall, a 27-year-old living in Manchester. In that span, his brand Deadnight has been featured on Hypebeast. Well-followed DJs like Example and KuruptFM requested clothing from him. Now, he says he’s in talks to be stocked “across Asia for a very large organization.” That’s thanks to the subreddit, he says: “Each time I have received high praise from members, but most importantly vital feedback which I have used each and every time to improve.” And therein lies what’s truly one-of-a-kind about this page: unlike most internet enclaves, most people on Streetwear Startup aren’t total assholes.A large percentage of the posts request feedback on a design. Amateur designers posting their best efforts to an audience granted internet anonymity should be like throwing red meat to a pack of hypebeasts. But the group on Streetwear Startup is almost entirely supportive, and only intends to nurture when it does give feedback. Compare the top comment on a recent Hypebeast article—”Looka ma stickers bruuuuuuuh. Fucking f*****s”—with a comment the brand Anomaly received when its founder asked for feedback on a tee: “I really like the original to the point where I'll cop rn if you release.”And that’s just one of the 33 comments offering advice on what the graphic should look like (“If you're going for the water reflection look, I feel like you should make the water a little more recognizable,” writes one commenter) and ways to add small details (“Would like to see something really simple on the back of the shirt,” reads another post). Anomaly’s founder Adam has been on the subreddit since 2015 and describes it as a key resource in building his brand. “It's the first place I turn to whenever I need feedback on a new design, tips on marketing, or just advice in general,” Adam tells me via email. “I'm not exaggerating when I say I wouldn't be here if it weren't for the supportive, albeit critical, community.”That sentiment is echoed by other users. “I personally value when people on the sub are a bit ruthless,” says VVID’s Slade. “It may often hurt my feelings at first reaction, but I also find harsh critique to give my subconscious a new perspective when approaching design.”What feeds the harmonious atmosphere is the fact that everyone has some skin in the game. “Everyone has the same perspective,” says Mallari. “So it's much easier for them to praise others, keep it up, this is good. It's a supportive environment because everyone started from the bottom.” Wilkie says he’s only ever banned one person.The whole community is reliant on this continuous feedback loop. “If you give to the community, we're going to try and give back to you,” says Wilkie.But this isn’t just a fun hobby; those who stick with the subreddit are serious about their success and the page can act as a fast track to it. “This is the future for me,” says Slade of his brand. “I'm hoping when Volume 3 releases I'll be able to drop out of school and do VVID full-time. I don't think it’s a long shot.”Adam, a 17-year-old who runs a brand called Anomaly with his friends Omar and Abdullah, echoes that thought. “Every brand owner within the subreddit wants the same thing: to make it big,” he says.It’s the amount of experience that all of us combined can bring to one person's ideaThe subreddit’s greatest strength, though, is the sheer number of voices and people it can bring to bear on an issue. “We have [14,000] people now but even if 10 people talk to you about a design that may help you decide to start over or decide that, ‘Wow this is really something I can work on.’” says Wilkie.When I ask Slade what the most valuable thing he gets from the subreddit is he says opinions. This is what’s most disruptive about the page: it lets burgeoning designers to crowdsource their designs rather than coming up with designs in isolation, investing the money, then plopping them on the web in hopes of finding an audience for the work.The process by which the clothing is made is different, but the resulting products have a lot in common with brands we’re familiar with. In the world of streetwear, the difference between what we consider hot and not oftentimes has a lot to do with the name behind it, rather than the strict aesthetic appeal of whatever’s on the front. The reasons we lose our collective shit over a white tee with a red box on it isn’t because of its unprecedented design quality; it’s because of everything that red box signifies. Anomaly recently featured paintings that were criticized for looking too similar to those used by popular streetwear brand Heron Preston. The factor that makes one cool and another unoriginal can often come down to the name. There’s nothing inherently uncool about the brands on the streetwear subreddit except maybe that they’re just not cool yet.Sorting out all the signals is why the streetwear startup can be so helpful. “I needed a place to gauge the response a larger audience would have to the collection and I wanted to know if it would stand out the way I wanted it to,” Slade explains. “What better way to test that than post in a community of people who look at or create streetwear designs all day, and see what they think?” You can feel out a customer base before needing, you know, a customer base.And because these are people who also have brands, it makes them the perfect target market. “If the majority of them like it, it will mostly likely at least sell a few pieces,” says Mallari. Streetwear Startup offers people a testing ground for items and designs before they ever put real monetary investment into anything. And you can keep taking the community’s advice until you’ve smoothed out the edges enough that someone—probably a number of someones on Streetwear Startup, who have now all helped you make a garment closer to their tastes—might actually buy your product. Fashion isn’t a science, but in Streetwear Startup you can play a game of addition and subtraction based on feedback until you’ve got something at least one person will wear.And you can keep adding and subtracting until someone like Jarvis Landry wears your clothes on ESPN. Matt Nicholas, a 30-years-old supplement store manager in Saskatoon, Saskatchewan Canada and the designer behind Rude Vogue, says that the subreddit vaulted him in front of a larger audience, but the Landry placement is on a different level. “It was a pretty amazing feeling, just growing up always watching ESPN daily and then to see your brand you've worked so hard for making a cameo on SportsCenter,” Nicholas says. The rest of the subreddits users are hoping to find the same kind of streetwear success — with a little help from their 14,000 friends.Watch Now:How Kinfolk Became One of the Coolest Designers on the PlanetMORE STORIES LIKE THIS ONE
https://www.gq.com/story/reddit-streetwear-startup
0 notes
Link
riveting interent sleuth work
via Krebs on Security
On September 22, 2016, this site was forced offline for nearly four days after it was hit with “Mirai,” a malware strain that enslaves poorly secured Internet of Things (IoT) devices like wireless routers and security cameras into a botnet for use in large cyberattacks. Roughly a week after that assault, the individual(s) who launched that attack — using the name “Anna Senpai” — released the source code for Mirai, spawning dozens of copycat attack armies online.
After months of digging, KrebsOnSecurity is now confident to have uncovered Anna Senpai’s real-life identity, and the identity of at least one co-conspirator who helped to write and modify the malware.
Mirai co-author Anna-Senpai leaked the source code for Mirai on Sept. 30, 2016.
Before we go further, a few disclosures are probably in order. First, this is easily the longest story I’ve ever written on this blog. It’s lengthy because I wanted to walk readers through my process of discovery, which has taken months to unravel. The details help in understanding the financial motivations behind Mirai and the botnet wars that preceded it. Also, I realize there are a great many names to keep track of as you read this post, so I’ve included a glossary.
The story you’re reading now is the result of hundreds of hours of research. At times, I was desperately seeking the missing link between seemingly unrelated people and events; sometimes I was inundated with huge amounts of information — much of it intentionally false or misleading — and left to search for kernels of truth hidden among the dross. If you’ve ever wondered why it seems that so few Internet criminals are brought to justice, I can tell you that the sheer amount of persistence and investigative resources required to piece together who’s done what to whom (and why) in the online era is tremendous.
As noted in previous KrebsOnSecurity articles, botnets like Mirai are used to knock individuals, businesses, governmental agencies, and non-profits offline on a daily basis. These so-called “distributed denial-of-service (DDoS) attacks are digital sieges in which an attacker causes thousands of hacked systems to hit a target with so much junk traffic that it falls over and remains unreachable by legitimate visitors. While DDoS attacks typically target a single Web site or Internet host, they often result in widespread collateral Internet disruption.
A great deal of DDoS activity on the Internet originates from so-called ‘booter/stresser’ services, which are essentially DDoS-for-hire services which allow even unsophisticated users to launch high-impact attacks. And as we will see, the incessant competition for profits in the blatantly illegal DDoS-for-hire industry can lead those involved down some very strange paths, indeed.
THE FIRST CLUES
The first clues to Anna Senpai’s identity didn’t become clear until I understood that Mirai was just the latest incarnation of an IoT botnet family that has been in development and relatively broad use for nearly three years.
Earlier this summer, my site was hit with several huge attacks from a collection of hacked IoT systems compromised by a family of botnet code that served as a precursor to Mirai. The malware went by several names, including “Bashlite,” “Gafgyt,” “Qbot,” “Remaiten,” and “Torlus.”
All of these related IoT botnet varieties infect new systems in a fashion similar to other well-known Internet worms — propagating from one infected host to another. And like those earlier Internet worms, sometimes the Internet scanning these systems perform to identify other candidates for inclusion into the botnet is so aggressive that it constitutes an unintended DDoS on the very home routers, Web cameras and DVRs that the bot code is trying to subvert and recruit into the botnet. This kind of self-defeating behavior will be familiar to those who recall the original Morris Worm, NIMDA, CODE RED, Welchia, Blaster and SQL Slammer disruptions of yesteryear.
Infected IoT devices constantly scan the Web for other IoT things to compromise, wriggling into devices that are protected by little more than insecure factory-default settings and passwords. The infected devices are then forced to participate in DDoS attacks (ironically, many of the devices most commonly infected by Mirai and similar IoT worms are security cameras).
Mirai’s ancestors had so many names because each name corresponded to a variant that included new improvements over time. In 2014, a group of Internet hooligans operating under the banner “lelddos” very publicly used the code to launch large, sustained attacks that knocked many Web sites offline.
The most frequent target of the lelddos gang were Web servers used to host Minecraft, a wildly popular computer game sold by Microsoft that can be played from any device and on any Internet connection.
The object of Minecraft is to run around and build stuff, block by large pixelated block. That may sound simplistic and boring, but an impressive number of people positively adore this game – particularly pre-teen males. Microsoft has sold more than a 100 million copies of Minecraft, and at any given time there are over a million people playing it online. Players can build their own worlds, or visit a myriad other blocky realms by logging on to their favorite Minecraft server to play with friends.
Image: Minecraft.net
A large, successful Minecraft server with more than a thousand players logging on each day can easily earn the server’s owners upwards of $50,000 per month, mainly from players renting space on the server to build their Minecraft worlds, and purchasing in-game items and special abilities.
Perhaps unsurprisingly, the top-earning Minecraft servers eventually attracted the attention of ne’er-do-wells and extortionists like the lelddos gang. Lelddos would launch a huge DDoS attack against a Minecraft server, knowing that the targeted Minecraft server owner was likely losing thousands of dollars for each day his gaming channel remained offline.
Adding urgency to the ordeal, many of the targeted server’s loyal customers would soon find other Minecraft servers to patronize if they could not get their Minecraft fix at the usual online spot.
Robert Coelho is vice president of ProxyPipe, Inc., a San Francisco company that specializes in protecting Minecraft servers from attacks.
“The Minecraft industry is so competitive,” Coelho said. “If you’re a player, and your favorite Minecraft server gets knocked offline, you can switch to another server. But for the server operators, it’s all about maximizing the number of players and running a large, powerful server. The more players you can hold on the server, the more money you make. But if you go down, you start to lose Minecraft players very fast — maybe for good.”
In June 2014, ProxyPipe was hit with a 300 gigabit per second DDoS attack launched by lelddos, which had a penchant for publicly taunting its victims on Twitter just as it began launching DDoS assaults at the taunted.
The hacker group “lelddos” tweeted at its victims before launching huge DDoS attacks against them.
At the time, ProxyPipe was buying DDoS protection from Reston, Va. -based security giant Verisign. In a quarterly report published in 2014, Verisign called the attack the largest it had ever seen, although it didn’t name ProxyPipe in the report – referring to it only as a customer in the media and entertainment business.
Verisign said the 2014 attack was launched by a botnet of more than 100,000 hacked routers sold by a company called SuperMicro. Days before the huge attack on ProxyPipe, a security researcher published information about a vulnerability in the SuperMicro devices that could allow them to be remotely hacked and commandeered for these sorts of attacks.
THE CENTRALITY OF PROTRAF
Coelho recalled that in mid-2015 his company’s Minecraft customers began coming under attack from a botnet made up of IoT devices infected with Qbot. He said the attacks were directly preceded by a threat made by a then-17-year-old Christopher “CJ” Sculti, Jr., the owner and sole employee of a competing DDoS protection company called Datawagon.
Datawagon also courted Minecraft servers as customers, and its servers were hosted on Internet space claimed by yet another Minecraft-focused DDoS protection provider — ProTraf Solutions.
Christopher “CJ” Sculti, Jr.
According to Coelho, ProTraf was trying to woo many of his biggest Minecraft server customers away from ProxyPipe. Coelho said in mid-2015, Sculti reached out to him on Skype and said he was getting ready to disable Coelho’s Skype account. At the time, an exploit for a software weakness in Skype was being traded online, and this exploit could be used to remotely and instantaneously disable any Skype account.
Sure enough, Coelho recalled, his Skype account and two others used by co-workers were shut off just minutes after that threat, effectively severing a main artery of support for ProxyPipe’s customers – many of whom were accustomed to communicating with ProxyPipe via Skype.
“CJ messaged me about five minutes before the DDoS started, saying he was going to disable my skype,” Coelho said. “The scary thing about when this happens is you don’t know if your Skype account has been hacked and under control of someone else or if it just got disabled.”
Once ProxyPipe’s Skype accounts were disabled, the company’s servers were hit with a massive, constantly changing DDoS attack that disrupted ProxyPipe’s service to its Minecraft server customers. Coelho said within a few days of the attack, many of ProxyPipe’s most lucrative Minecraft servers had moved over to servers run protected by ProTraf Solutions.
“In 2015, the ProTraf guys hit us offline tons, so a lot of our customers moved over to them,” Coelho said. “We told our customers that we knew [ProTraf] were the ones doing it, but some of the customers didn’t care and moved over to ProTraf anyway because they were losing money from being down.”
I found Coelho’s story fascinating because it eerily echoed the events leading up to my Sept. 2016 record 620 Gbps attack. I, too, was contacted via Skype by Sculti — on two occasions. The first was on July 7, 2015, when Sculti reached out apropos of nothing to brag about scanning the Internet for IoT devices running default usernames and passwords, saying he had uploaded some kind of program to more than a quarter-million systems that his scans found.
Here’s a snippet of that conversation:
July 7, 2015:
21:37 CJ: http://ift.tt/1GHYxAg
21:37 CJ: vulnerable routers are a HUGE issue
21:37 CJ: a few months ago
21:37 CJ: I scanned the internet with a few sets of defualt logins
21:37 CJ: for telnet
21:37 CJ: and I was able to upload and execute a binary
21:38 CJ: on 250k devices
21:38 CJ: most of which were routers
21:38 Brian Krebs: o_0
The second time I heard from Sculti on Skype was Sept. 20, 2016 — the day of my 620 Gbps attack. Sculti was angry over a story I’d just published that mentioned his name, and he began rather saltily maligning the reputation of a source and friend who had helped me with that story.
Indignant on behalf of my source and annoyed at Sculti’s rant, I simply blocked his Skype account from communicating with mine and went on with my day. Just minutes after that conversation, however, my Skype account was flooded with thousands of contact requests from compromised or junk Skype accounts, making it virtually impossible to use the software for making phone calls or instant messaging.
Six hours after that Sept. 20 conversation with Sculti, the huge 620 Gbps DDoS attack commenced on this site.
WHO IS LELDDOS?
Coelho said he believes the main members of lelddos gang were Sculti and the owners of ProTraf. Asked why he was so sure of this, he recounted a large lelddos attack in early 2015 against ProxyPipe that coincided with a scam in which large tracts of Internet address space were temporarily stolen from the company.
According to ProxyPipe, a swath of Internet addresses was hijacked from the company by FastReturn, another DDoS mitigation firm that also specialized in protecting Minecraft servers from attacks. Dyn, a company that closely tracks which blocks of Internet addresses are assigned to which organizations, confirmed the timing of the Internet address hijack that Coelho described.
A few months after that attack, the owner of FastReturn — a young man from Dubai named Ammar Zuberi — went to work as a software developer for ProTraf. In the process, Zuberi transferred the majority of Internet addresses assigned to FastReturn over to ProTraf.
Zuberi told KrebsOnSecurity that he was not involved with lelddos, but he acknowledged that he did hijack ProxyPipe’s Internet address space before moving over to ProTraf.
“I was stupid and new to this entire thing and it was interesting to me how insecure the underlying ecosystem of the Internet was,” Zuberi said. “I just kept pushing the envelope to see how far I could get with that, I guess. I eventually realized though and got away from it, although that’s not really much of a justification.”
According to Zuberi, CJ Sculti Jr. was a member of lelddos, as were the two co-owners of ProTraf. This is interesting because not long after the September 2016 Mirai attack took this site offline, several sources who specialize in lurking on cybercrime forums shared information suggesting that the principal author of Bashlite/Qbot was a ProTraf employee: A 19-year-old computer whiz from Washington, Penn. named Josiah White.
White’s profile on LinkedIn lists him as an “enterprise DDoS mitigation expert” at ProTraf, but for years he was better known to those in the hacker community under the alias “LiteSpeed.”
LiteSpeed is the screen name White used on Hackforums[dot]net – a sprawling English-language marketplace where mostly young, low-skilled hackers can buy and sell cybercrime tools and stolen goods with ease. Until very recently, Hackforums also was the definitive place to buy and sell DDoS-for-hire services.
I contacted White to find out if the rumors about his authorship of Qbot/Bashlite were true. White acknowledged that he had written some of Qbot/Bashlite’s components — including the code segment that the malware uses to spread the infection to new machines. But White said he never intended for his code to be sold and traded online.
White claims that a onetime friend and Hackforums member nicknamed “Vyp0r” betrayed his trust and forced him to publish the code online by threatening to post White’s personal details online and to “swat” his home. Swatting is a potentially deadly hoax in which an attacker calls in a fake hostage situation or bomb threat at a residence or business with the intention of sending a team of heavily-armed police officers to the target’s address.
“Most of the stuff that I had wrote was for friends, but as I later realized, things on HF [Hackforums] tend to not remain private,” White wrote in an instant message to KrebsOnSecurity. “Eventually I learned they were reselling them in under-the-table deals, and so I just released everything to stop that. I made some mistakes when I was younger, and I realize that, but I’m trying to set my path straight and move on.”
WHO IS PARAS JHA?
White’s employer ProTraf Solutions has only one other employee – 20-year-old President Paras Jha, from Fanwood, NJ. On his LinkedIn profile, Jha states that “Paras is a passionate entrepreneur driven by the want to create.” The profile continues:
“Highly self-motivated, in 7th grade he began to teach himself to program in a variety of languages. Today, his skillset for software development includes C#, Java, Golang, C, C++, PHP, x86 ASM, not to mention web ‘browser languages’ such as Javascript and HTML/CSS.”
Jha’s LinkedIn page also shows that he has extensive experience running Minecraft servers, and that for several years he worked for Minetime, one of the most popular Minecraft servers at the time.
After first reading Jha’s LinkedIn resume, I was haunted by the nagging feeling that I’d seen this rather unique combination of computer language skills somewhere else online. Then it dawned on me: The mix of programming skills that Jha listed in his LinkedIn profile is remarkably similar to the skills listed on Hackforums by none other than Mirai’s author — Anna-Senpai.
Prior to leaking the Mirai source code on HackForums at the end of September 2016, the majority of Anna-Senpai’s posts on Hackforums were meant to taunt other hackers on the forum who were using Qbot to build DDoS attack armies.
The best example of this is a thread posted to Hackforums on July 10, 2016 titled “Killing All Telnets,” in which Anna-Senpai boldly warns forum members that the malicious code powering his botnet contains a particularly effective “bot killer” designed to remove Qbot from infected IoT devices and to prevent systems infected with his malware from ever being reinfected with Qbot again.
Anna-Senpai warns Qbot users that his new worm (relatively unknown by its name “Mirai” at the time) was capable of killing off IoT devices infected with Qbot.
Initially, forum members dismissed Anna’s threats as idle taunts, but as the thread continues for page after page we can see from other forum members that his bot killer is indeed having its intended effect. [Oddly enough, it’s very common for the authors of botnet code to include patching routines to protect their newly-enslaved bots from being compromised by other miscreants. Just like in any other market, there is a high degree of competition between cybercrooks who are constantly seeking to add more zombies to their DDoS armies, and they often resort to unorthodox tactics to knock out the competition. As we’ll see, this kind of internecine warfare is a major element in this story.]
“When the owner of this botnet wrote a July 2016 Hackforums thread named ‘Killing all Telnets’, he was right,” wrote Allison Nixon and Pierre Lamy, threat researchers for New York City-based security firm Flashpoint. “Our intelligence around that time reflected a massive shift away from the traditional gafgyt infection patterns and towards a different pattern that refused to properly execute on analysts’ machines. This new species choked out all the others.”
It wasn’t until after I’d spoken with Jha’s business partner Josiah White that I began re-reading every one of Anna-Senpai’s several dozen posts to Hackforums. The one that made Jha’s programming skills seem familiar came on July 12, 2016 — a week after posting his “Killing All Telnets” discussion thread — when Anna-Senpai contributed to a Hackforums thread started by a hacker group calling itself “Nightmare.”
Such groups or hacker cliques are common on Hackforums, and forum members can apply for membership by stating their skills and answering a few questions. Anna-Senpai posted his application for membership into this thread among dozens of others, describing himself thusly:
“Age: 18+
Location and Languages Spoken: English
Which of the aforementioned categories describe you the best?: Programmer / Development
What do you Specialize in? (List only): Systems programming / general low level languages (C + ASM)
Why should we choose you over other applicants?: I have 8 years of development under my belt, and I’m very familiar with programming in a variety of languages, including ASM, C, Go, Java, C#, and PHP. I like to use this knowledge for personal gain.”
The Hackforums post shows Jha and Anna-Senpai have the exact same programming skills. Additionally, according to an analysis of Mirai by security firm Incapsula, the malicious software used to control a botnet powered by Mirai is coded in Go (a.k.a. “Golang”), a somewhat esoteric programming language developed by Google in 2007 that saw a surge in popularity in 2016. Incapsula also said the malcode that gets installed on IoT bots is coded in C.
DREADIS[NOT]COOL
I began to dig deeper into Paras Jha’s history and footprint online, and discovered that his father in October 2013 registered a vanity domain for his son, parasjha.info. That site is no longer online, but a historic version of it cached by the indispensable Internet Archive includes a resume of Jha’s early work with various popular Minecraft servers. Here’s a autobiographical snippet from parasjha.info:
“My passion is to utilize my skills in programming and drawing to develop entertaining games and software for the online game ‘Minecraft. Someday, I plan to start my own enterprise focused on the gaming industry targeted towards game consoles and the mobile platform. To further my ideas and help the gaming community, I have released some of my code to open source projects on websites centered on public coding under the handle dreadiscool.”
A Google search for this rather unique username “dreadiscool” turns up accounts by the same name at dozens of forums dedicated to computer programming and Minecraft. In many of those accounts, the owner is clearly frustrated by incessant DDoS attacks targeting his Minecraft servers, and appears eager for advice on how best to counter the assaults.
From Dreadiscool’s various online postings, it seems clear that at some point Jha decided it might be more profitable and less frustrating to defend Minecraft servers from DDoS attacks, as opposed to trying to maintain the servers themselves.
“My experience in dealing with DDoS attacks led me to start a server hosting company focused on providing solutions to clients to mitigate such attacks,” Jha wrote on his vanity site.
Some of the more recent Dreadiscool posts date to November 2016, and many of those posts are lengthy explanations of highly technical subjects. The tone of voice in these posts is far more confident and even condescending than the Dreadiscool from years earlier, covering a range of subjects from programming to DDoS attacks.
Dreadiscool’s account on Spigot Minecraft forum since 2013 includes some interesting characters photoshopped into this image.
For example, Dreadiscool has been an active member of the Minecraft forum spigotmc.org since 2013. This user’s avatar (pictured above) on spigotmc.org is an altered image taken from the 1994 Quentin Tarantino cult hit “Pulp Fiction,” specifically from a scene in which the gangster characters Jules and Vincent are pointing their pistols in the same direction. However, the heads of both actors have been digitally altered to include someone else’s faces.
Pasted over the head of John Travolta’s character (left) is a real-life picture of Vyp0r — the Hackforums nickname of the guy that ProTraf’s Josiah White said threatened him into releasing the source code for Bashlite. On the shoulders of Samuel L. Jackson’s body is the face of Tucker Preston, co-founder of BackConnect Security — a competing DDoS mitigation provider that also has a history of hijacking Internet address ranges from other providers.
Pictured below and to the left of Travolta and Jackson’s characters — seated on the bed behind them — is “Yamada,” a Japanese animation (“anime”) character featured in the anime movie B Gata H Hei.
Turns out, there is a Dreadiscool user on MyAnimeList.net, a site where members proudly list the various anime films they have watched. Dreadiscool says B Gata H Kei is one of nine anime film series he has watched. Among the other eight? The anime series Mirai Nikki, from which the Mirai malware derives its name.
Dreadiscool’s Reddit profile also is very interesting, and most of the recent posts there relate to major DDoS attacks going on at the time, including a series of DDoS attacks on Rutgers University. More on Rutgers later.
A CHAT WITH ANNA-SENPAI
At around the same time as the record 620 Gbps attack on KrebsOnSecurity, French Web hosting giant OVH suffered an even larger attack — launched by the very same Mirai botnet used to attack this site. Although this fact has been widely reported in the news media, the reason for the OVH attack may not be so well known.
According to a tweet from OVH founder and chief technology officer Octave Klaba, the target of that massive attack also was a Minecraft server (although Klaba mistakenly called the target “mindcraft servers” in his tweet).
A tweet from OVH founder and CTO, stating the intended target of Sept. 2016 Mirai DDoS on his company.
Turns out, in the days following the attack on this site and on OVH, Anna-Sempai had trained his Mirai botnet on Coelho’s ProxyPipe, completely knocking his DDoS mitigation service offline for the better part of a day and causing problems for many popular Minecraft servers.
Unable to obtain more bandwidth and unwilling to sign an expensive annual contract with a third-party DDoS mitigation firm, Coelho turned to the only other option available to get out from under the attack: Filing abuse complaints with the Internet hosting firms that were responsible for providing connectivity to the control server used to orchestrate the activities of the Mirai botnet.
“We did it because we had no other options, and because all of our customers were offline,” Coelho said. “Even though no other DDoS mitigation company was able to defend against these attacks [from Mirai], we still needed to defend against it because our customers were starting to move to other providers that attracted fewer attacks.”
After scouring a list of Internet addresses tied to bots used in the attack, Coelho said he was able to trace the control server for the Mirai botnet back to a hosting provider in Ukraine. That company — BlazingFast[dot]io — has a reputation for hosting botnet control networks.
Getting no love from BlazingFast, Coelho said he escalated his complaint to Voxility, a company that was providing DDoS protection to BlazingFast at the time.
“Voxility acknowledged the presence of the control server, and said they null-routed [removed] it, but they didn’t,” Coelho said. “They basically lied to us and didn’t reply to any other emails.”
Undeterred, Coelho said he then emailed the ISP that was upstream of BlazingFast, but received little help from that company or the next ISP further upstream. Coelho said the fifth ISP upstream of BlazingFast, however — Internet provider Telia Sonera — confirmed his report, and promptly had the Mirai botnet’s control server killed.
As a result, many of the systems infected with Mirai could no longer connect to the botnet’s control servers, drastically reducing the botnet’s overall firepower.
“The action by Telia cut the size of the attacks launched by the botnet down to 80 Gbps,” well within the range of ProxyPipe’s in-house DDoS mitigation capabilities, Coelho said.
Incredibly, on Sept. 28, Anna-Senpai himself would reach out to Coelho via Skype. Coelho shared a copy of that chat conversation with KrebsOnSecurity. The log shows that Anna correctly guessed ProxyPipe was responsible for the abuse complaints that kneecapped Mirai. Anna-Senpai said he guessed ProxyPipe was responsible after reading a comment on a KrebsOnSecurity blog post from a reader who shared the same username as Coelho’s business partner.
In the following chat, Coelho is using the Skype nickname “katie.onis.”
[10:23:08 AM] live:anna-senpai: ^
[10:26:08 AM] katie.onis: hi there.
[10:26:52 AM] katie.onis: How can I help you?
[10:28:06 AM] live:anna-senpai: hi
[10:28:45 AM] live:anna-senpai: you know i had my suspicions, but this one was proof
http://ift.tt/2k0nPGc [this is a benign/safe link to a screenshot of some comments on KrebsOnSecurity.com]
[10:28:59 AM] live:anna-senpai: don’t get me wrong, im not even mad, it was pretty funny actually. nobody has ever done that to my c2 [Mirai “command and control” server]
[10:29:25 AM] live:anna-senpai: (goldmedal)
[10:29:29 AM] katie.onis: ah you’re mistaken, that’s not us.
[10:29:33 AM] katie.onis: but we know who it is
[10:29:42 AM] live:anna-senpai: eric / 9gigs
[10:29:47 AM] katie.onis: no, 9gigs is erik
[10:29:48 AM] katie.onis: not eric
[10:29:53 AM] katie.onis: different people
[10:30:09 AM] live:anna-senpai: oh?
[10:30:17 AM] katie.onis: yep
[10:30:39 AM] live:anna-senpai: is he someone related to you guys?
[10:30:44 AM] katie.onis: not related to us, we just know him
[10:30:50 AM] katie.onis: anyway, we’re not interested in any harm, we simply don’t want attacks against us.
[10:31:16 AM] live:anna-senpai: yeah i figured, i added you because i wanted to tip my hat if that was actually you lol
[10:31:24 AM] katie.onis: we didn’t make that dumb post
[10:31:26 AM] katie.onis: if that is what you are asking
[10:31:30 AM] katie.onis: but yes, we were involved in doing that.
[10:31:47 AM] live:anna-senpai: so you got it nulled, but some other eric is claiming credit for it?
[10:31:52 AM] katie.onis: seems so.
[10:31:52 AM] live:anna-senpai: eric with a c
[10:31:56 AM] live:anna-senpai: lol
[10:32:17 AM] live:anna-senpai: can’t say im surprised, tons of people take credit for things that they didn’t do if nobody else takes credit for
[10:32:24 AM] katie.onis: we’re not interested in taking credit
[10:32:30 AM] katie.onis: we just wanted the attacks to get smaller
NOTICE AND TAKEDOWN
One reason Anna-Senpai may have been enamored of Coelho’s approach to taking down Mirai is that Anna-Senpai had spent the previous month doing exactly the same thing to criminals running IoT botnets powered by Mirai’s top rival — Qbot.
A month before this chat between Coelho and Anna-Senpai, Anna is busy sending abuse complaints to various hosting firms, warning them that they are hosting huge IoT botnet control channels that needed to be shut down. This was clearly just part of an extended campaign by the Mirai botmasters to eliminate other IoT-based DDoS botnets that might compete for the same pool of vulnerable IoT devices. Anna confirmed this in his chat with Coelho:
[10:50:36 AM] live:anna-senpai: i have good killer so nobody else can assemble a large net
[10:50:53 AM] live:anna-senpai: i monitor the devices to see for any new threats
[10:51:33 AM] live:anna-senpai: and when i find any new host, i get them taken down
The ISPs or hosting providers that received abuse complaints from Anna-Senpai were all encouraged to reply to the email address [email protected] for questions and/or confirmation of the takedown. ISPs that declined to act promptly on Anna-Senpai’s Qbot email complaints soon found themselves on the receiving end of enormous DDoS attacks from Mirai.
Francisco Dias, owner of hosting provider Frantech, found out firsthand what it would cost to ignore one of Anna’s abuse reports. In mid-September 2016, Francisco accidentally got into an Internet fight with Anna-Senpai. The Mirai botmaster was using the nickname “jorgemichaels” at the time — and Jorgemichaels was talking trash on LowEndTalk.com, a discussion forum for vendors of low-costing hosting.
Specifically, Jorgemichaels takes Francisco to task publicly on the forum for ignoring one of his Qbot abuse complaints. Francisco tells Jorgemichaels to file a complaint with the police if it’s so urgent. Jorgemichaels tells Francisco to shut up, and when Francisco is silent for a while Jorgemichaels gloats that Francisco learned his place. Francisco explains his further silence on the thread by saying he’s busy supporting customers, to which Jorgemichaels replies, “Sounds like you just got a lot more customers to help. Don’t mess with the underworld francisco or it will harm your business.”
Shortly thereafter, Frantech is systematically knocked offline after being attacked by Mirai. Below is a fascinating snippet from a private conversation between Francisco and Anna-Senpai/Jorgemichaels, in which Francisco kills the reported Qbot control server to make Anna/Jorgemichaels call off the attack.
Using the nickname “jorgemichaels” on LowEndTalk, Anna-Senpai reaches out to Francisco Dias after Dias ignores Anna’s abuse complaint. Francisco agrees to kill the Qbot control server only after being walloped with Mirai.
Back to the chat between Anna-Senpai and Coelho at the end of Sept 2016. Anna-Senpai tells Coelho that the attacks against ProxyPipe aren’t personal; they’re just business. Anna says he has been renting out “net spots” — sizable chunks of his Mirai botnet — to other hackers who use them in their own attacks for pre-arranged periods of time.
By way of example, Anna brags that as he and Coelho are speaking, the owners of a large Minecraft server were paying him to launch a crippling DDoS against Hypixel, currently the world’s most popular Minecraft server. KrebsOnSecurity confirmed with Hypixel that they were indeed under a massive attack from Mirai between Sept. 27 and 30.
[12:24:00 PM] live:anna-senpai: right now i just have a script sitting there hitting them for 45s every 20 minutes
[12:24:09 PM] live:anna-senpai: enough to drop all players and make them rage
Coelho told KrebsOnSecurity that the on-again, off-again attack DDoS method that Anna described using against Hypixel was designed not just to cost Hypixel money. The purpose of that attack method, he said, was to aggravate and annoy Hypixel’s customers so much that they might take their business to a competing Minecraft server.
“It’s not just about taking it down, it’s about making everyone who is playing on that server crazy mad,” Coelho explained. “If you launch the attack every 20 minutes for a short period of time, you basically give the players just enough time to get back on the server and involved in another game before they’re disconnected again.”
Anna-Senpai told Coelho that paying customers also were the reason for the 620 Gbps attack on KrebsOnSecurity. Two weeks prior to that attack, I published the results of a months-long investigation revealing that “vDOS” — one of the largest and longest-running DDoS-for-hire services — had been hacked, exposing details about the services owners and customers.
The story noted that vDOS earned its proprietors more than $600,000 and was being run by two 18-year-old Israeli men who went by the hacker aliases “applej4ck” and “p1st0”. Hours after that piece ran, Israeli authorities arrested both men, and vDOS — which had been in operation for four years — was shuttered for good.
[10:47:42 AM] live:anna-senpai: i sell net spots, starting at $5k a week
[10:47:50 AM] live:anna-senpai: and one client was upset about applejack arrest
[10:48:01 AM] live:anna-senpai: so while i was gone he was sitting on them for hours with gre and ack
[10:48:14 AM] live:anna-senpai: when i came back i was like oh fuck
[10:48:16 AM] live:anna-senpai: and whitelisted the prefix
[10:48:24 AM] live:anna-senpai: but then krebs tweeted that akamai is kicking them off
[10:48:31 AM] live:anna-senpai: fuck me
[10:48:43 AM] live:anna-senpai: he was a cool guy too, i like his article
[SIDE NOTE: If true, it’s ironic that someone would hire Anna-Senpai to attack my site in retribution for the vDOS story. That’s because the firepower behind applej4ck’s vDOS service was generated in large part by a botnet of IoT systems infected with a Qbot variant — the very same botnet strain that Anna-Senpai and Mirai were busy killing and erasing from the Internet.]
Coelho told KrebsOnSecurity that if his side of the conversation reads like he was being too conciliatory to his assailant, that’s because he was wary of giving Anna a reason to launch another monster attack against ProxyPipe. After all, Coelho said, the Mirai attacks on ProxyPipe caused many customers to switch to other Minecraft servers, and Coelho estimates the attack cost the company between $400,000 and $500,000.
Nevertheless, about halfway through the chat Coelho gently confronts Anna on the consequences of his actions.
[10:54:17 AM] katie.onis: People have a genuine reason to be unhappy though about large attacks like this
[10:54:27 AM] live:anna-senpai: yeah
[10:54:32 AM] katie.onis: There’s really nothing anyone can do lol
[10:54:36 AM] live:anna-senpai:
[10:54:38 AM] katie.onis: And it does affect their lives
[10:55:10 AM] live:anna-senpai: well, i stopped caring about other people a long time ago
[10:55:18 AM] live:anna-senpai: my life experience has always been get fucked over or fuck someone else over
[10:55:52 AM] katie.onis: My experience with [ProxyPipe] thus far has been
[10:55:54 AM] katie.onis: Do nothing bad to anyone
[10:55:58 AM] katie.onis: And still get screwed over
[10:55:59 AM] katie.onis: Haha
The two even discussed anime after Anna-Senpai guessed that Coelho might be a fan of the genre. Anna-Senpai says he watched the anime series “Gate,” a reference to the above-mentioned B Gata H Hei that Dreadiscool included in the list of anime film series he’s watched. Anna also confirms that the name for his bot malware was derived from the anime series Mirai Nikki.
[5:25:12 PM] live:anna-senpai: i rewatched mirai nikki recently
[5:25:22 PM] live:anna-senpai: (it was the reason i named my bot mirai lol)
DREADISCOOL = ANNA = JHA?
Coelho said when Anna-Senpai first reached out to him on Skype, he had no clue about the hacker’s real-life identity. But a few weeks after that chat conversation with Anna-Senpai, Coelho’s business partner (the Eric referenced in the first chat segment above) said he noticed that some of the code in Mirai looked awfully similar to code that Dreadiscool had posted to his Github account.
“He started to come to the conclusion that maybe Anna was Paras,” Coelho said. “He gave me a lot of ideas, and after I did my own investigation I decided he was probably right.”
An incomplete “mindmap” I put together as I started to assemble research.
Coelho said he’s known Paras Jha for more than four years, having met him online when Jha was working for Minetime — which ProxyPipe was protecting from DDoS attacks at the time.
“We talked a lot back then and we used to program a lot of projects together,” Coelho said. “He’s really good at programming, but back then he wasn’t. He was a little bit behind, and I was teaching him most everything.”
According to Coelho, as Jha became more confident in his coding skills, he also grew more arrogant, belittling others online who didn’t have as firm a grasp on subjects such as programming and DDoS mitigation.
“He likes to be recognized for his knowledge, being praised and having other people recognize that,” Coelho said of Jha. “He brags too much, basically.”
Coelho said not long after Minetime was hit by a DDoS extortion attack in 2013, Paras joined Hackforums and fairly soon after stopped responding to his online messages.
“He just kind of dropped off the face of the earth entirely,” he said. “When he started going on Hackforums, I didn’t know him anymore. He became a different person.”
Coelho said he doesn’t believe his old friend wished him harm, and that Jha was probably pressured into attacking ProxyPipe.
“In my opinion he’s still a kid, in that he gets peer-pressured a lot,” Coelho said. “If he didn’t [launch the attack] not only would he feel super excluded, but these people wouldn’t be his friends anymore, they could out him and screw him over. I think he was pretty much in a really bad position with the people he got involved with.”
THE RUTGERS DDOS ATTACKS
On Dec. 16, security vendor Digital Shadows presented a Webinar that focused on clues about the Mirai author’s real life identity. According to their analysis, before the Mirai author was known as Anna-Senpai on Hackforums, he used the nickname “Ogmemes123123” (this also was the alias of the Skype username that contacted Coelho), and the email address [email protected] (recall this is the same email address Anna-Senpai used in his alerts to various hosting firms about the urgent need to take down Qbot control servers hosted on their networks).
Digital Shadows noted that the Mirai author appears to have used another nickname: “OG_Richard_Stallman,” a likely reference to the founder of the Free Software Foundation. The [email protected] account was used to register a Facebook account in the name of OG_Richard Stallman.
That Facebook account states that OG_Richard_Stallman began studying computer engineering at New Brunswick, NJ-based Rutgers University in 2015.
As it happens, Paras Jha is a student at Rutgers University. This is especially notable because Rutgers has been dealing with a series of DDoS attacks on its network since the fall semester of 2015 — more than a half dozen incidents in all. With each DDoS, the attacker would taunt the university in online posts and media interviews, encouraging the school to spend the money to purchase some kind of DDoS mitigation service.
Using the nicknames “og_richard_stallman,” “exfocus” and “ogexfocus,” the person who attacked Rutgers more than a half-dozen times took to Reddit and Twitter to claim credit for the attacks. Exfocus even created his own “Ask Me Anything” interview on Reddit to discuss the Rutgers attacks.
Exfocus also gave an interview to a New Jersey-based blogger, claiming he got paid $500 an hour to DDoS the university with as many as 170,000 bots. Here are a few snippets from that interview, in which he blames the attacks on a “client” who is renting his botnet:
“Are you for real? Why would you do an interview with us if you’re getting paid?
Normally I don’t show myself, but the entity paying me has something against the school. They want me to “make a splash”.
Why do you have a twitter account where you publically broadcast patronizing messages. Are you worried that this increases the risk of things getting back to you?
Public twitter is on clients request. The client hates the school for whatever reason. They told me to say generic things like that I hate the bus system and etc.
Have you ever attacked RU before?
During freshman registration the client requested it also – he didn’t want any publicity then though.
What are your plans for the future in terms of DDOSing and attacking the Rutgers cyber infrastructure?
When I stop getting paid – I’ll stop DDosing lol. I’m hoping that RU will sign on some ddos mitigation provider. I get paid extra if that happens.
At some point you said you were at the Livingston student center – outside of Sbarro. In this interview you said that you aren’t affiliated directly with Rutgers, did you lie then?
Yes”
An online search for the Gmail address used by Anna-Senpai and OG_Richard_Stallman turns up a Pastebin post from July 1, 2016, in which an anonymous Pastebin user creates a “dox” of OG_Richard_Stallman. Doxing refers to the act of publishing someone’s personal information online and/or connecting an online alias to a real life identity.
The dox said OG_Richard_Stallman was connected to an address and phone number of an individual living in Turkey. But this is almost certainly a fake dox intended to confuse cybercrime investigators. Here’s why:
A Google search shows that this same address and phone number showed up in another dox on Pastebin from almost three years earlier — June 2013 — intended to expose or confuse the identity of a Hackforums user known as LiteSpeed. Recall that LiteSpeed is the same alias that ProTraf’s Josiah White acknowledged using on Hackforums.
EXTORTION ATTEMPTS BY OG_RICHARD_STALLMAN
This OG_Richard_Stallman identity is connected to Anna-Senpai by another person we’ve heard from already: Francisco Dias, whose Frantech ISP was attacked by Anna-Senpai and Mirai in mid-September. Francisco told KrebsOnSecurity that in early August 2016 he began receiving extortion emails from a Gmail address associated with a OG_Richard_Stallman.
“This guy using the Richard Stallman name added me on Skype and basically said ‘I’m going to knock all of your [Internet addresses] offline until you pay me’,” Dias recalled. “He told me the up front cost to stop the attack was 10 bitcoins [~USD $5,000 at the time], and if I didn’t pay within four hours after the attack started the fee would double to 20 bitcoins.”
Dias said he didn’t pay the demand and eventually OG_Richard_Stallman called off the attack. But he said for a while the attacks were powerful enough to cause problems for Frantech’s Internet provider.
“He was hitting us so hard with Mirai that he was dropping large parts of Hurricane Electric and causing problems at their Los Angeles point of presence,” Dias said. “I basically threw everything behind [DDoS mitigation provider] Voxility, and eventually Stallman buggered off.”
The OG_Richard_Stallman identity also was tied to similar extortion attacks at the beginning of August against one hosting firm that had briefly been one of ProTraf’s customers in 2016. The company declined to be quoted on the record, but said it stopped doing business with Protraf in mid-2016 because they were unhappy with the quality of service.
The Internet provider said not long after that it received an extortion demand from the “OG_Richard_Stallman” character for $5,000 in Bitcoin to avoid a DDoS attack. One of the company’s researchers contacted the extortionist via the [email protected] address supplied in the email, but posing as someone who wished to hire some DDoS services.
OG_Richard_Stallman told the researcher that he could guarantee 350 Gbps of attack traffic and that the target would go down or the customer would receive a full refund. The price for the attack? USD $100 worth of Bitcoin for every five minutes of attack time.
My source at the hosting company said his employer declined to pay the demand, and subsequently got hit with an attack from Mirai that clocked in at more than 300 Gbps.
“Clearly, the attacker is very technical, as they attacked every single [Internet address] within the subnet, and after we brought up protection, he started attacking upstream router interfaces,” the source said on condition of anonymity.
Asked who they thought might be responsible for the attacks, my source said his employer immediately suspected ProTraf. That’s because the Mirai attack also targeted the Internet address for the company’s home page, but that Internet address was hidden by DDoS mitigation firm Cloudflare. However, ProTraf knew about the secret address from its previous work with the company, the source explained.
“We believe it’s Protraf’s staff or someone related to Protraf,” my source said.
A source at an Internet provider agreed to share information about an extortion demand his company received from OG_Richard_Stallman in August 2016. Here he is contacting the Stallman character directly and pretending to be someone interested in renting a botnet. Notice the source brazenly said he wanted to DDoS ProTraf.
DDOS CONFESSIONS
After months of gathering information about the apparent authors of Mirai, I heard from Ammar Zuberi, once a co-worker of ProTraf President Paras Jha.
Zuberi told KrebsOnSecurity that Jha admitted he was responsible for both Mirai and the Rutgers DDoS attacks. Zuberi said when he visited Jha at his Rutgers University dorm in October 2015, Paras bragged to him about launching the DDoS attacks against Rutgers.
“He was laughing and bragging about how he was going to get a security guy at the school fired, and how they raised school fees because of him,” Zuberi recalled. “He didn’t really say why he did it, but I think he was just sort of experimenting with how far he could go with these attacks.”
Zuberi said he didn’t realize how far Jha had gone with his DDoS attacks until he confronted him about it late last year. Zuberi said he was on his way to see his grandmother in Arizona at the end of November 2016, and he had a layover in New York. So he contacted Jha and arranged to spend the night at Jha’s home in Fanwood, New Jersey.
As I noted in Spreading the DDoS Disease and Selling the Cure, Anna-Senpai leaked the Mirai code on a domain name (santasbigcandycane[dot]cx) that was registered via Namecentral, an extremely obscure domain name registrar which had previously been used to register fewer than three dozen other domains over a three-year period.
According to Zuberi, only five people knew about the existence of Namecentral: himself, CJ Sculti, Paras Jha, Josiah White and Namecentral’s owner Jesse Wu (19-year-old Wu features prominently in the DDoS Disease story linked in the previous paragraph).
“When I saw that the Mirai code had been leaked on that domain at Namecentral, I straight up asked Paras at that point, ‘Was this you?,’ and he smiled and said yep,” Zuberi recalled. “Then he told me he’d recently heard from an FBI agent who was investigating Mirai, and he showed me some text messages between him and the agent. He was pretty proud of himself, and was bragging that he led the FBI on a wild goose chase.”
Zuberi said he hasn’t been in contact with Jha since visiting his home in November. Zuberi said he believes Jha wrote most of the code that Mirai uses to control the individual bot-infected IoT devices, since it was written in Golang and Jha’s partner White didn’t code well in this language. Zuberi said he thought White’s role was mainly in developing the spreading code used to infect new IoT devices with Mirai, since that was written in C — a language White excelled at.
In the time since most of the above occurred, the Internet address ranges previously occupied by ProTraf have been withdrawn. ProxyPipe’s Coelho said it could be that the ProTraf simply ran out of money.
ProTraf’s Josiah White explained the disappearance of ProTraf’s Internet space as part of an effort to reboot the company.
“We [are] in the process of restructuring and refocusing what we are doing,” White told KrebsOnSecurity.
Jha did not respond to requests for comment.
Rutgers University did not respond to requests for comment.
The FBI officials could not be immediately reached for comment.
A copy of the entire chat between Anna-Senpai and ProxyPipe’s Coelho is available here.
0 notes
Link
(Via: Krebs on Security)
On September 22, 2016, this site was forced offline for nearly four days after it was hit with “Mirai,” a malware strain that enslaves poorly secured Internet of Things (IoT) devices like wireless routers and security cameras into a botnet for use in large cyberattacks. Roughly a week after that assault, the individual(s) who launched that attack — using the name “Anna Senpai” — released the source code for Mirai, spawning dozens of copycat attack armies online.
After months of digging, KrebsOnSecurity is now confident to have uncovered Anna Senpai’s real-life identity, and the identity of at least one co-conspirator who helped to write and modify the malware.
Mirai co-author Anna-Senpai leaked the source code for Mirai on Sept. 30, 2016.
Before we go further, a few disclosures are probably in order. First, this is easily the longest story I’ve ever written on this blog. It’s lengthy because I wanted to walk readers through my process of discovery, which has taken months to unravel. The details help in understanding the financial motivations behind Mirai and the botnet wars that preceded it. Also, I realize there are a great many names to keep track of as you read this post, so I’ve included a glossary.
The story you’re reading now is the result of hundreds of hours of research. At times, I was desperately seeking the missing link between seemingly unrelated people and events; sometimes I was inundated with huge amounts of information — much of it intentionally false or misleading — and left to search for kernels of truth hidden among the dross. If you’ve ever wondered why it seems that so few Internet criminals are brought to justice, I can tell you that the sheer amount of persistence and investigative resources required to piece together who’s done what to whom (and why) in the online era is tremendous.
As noted in previous KrebsOnSecurity articles, botnets like Mirai are used to knock individuals, businesses, governmental agencies, and non-profits offline on a daily basis. These so-called “distributed denial-of-service (DDoS) attacks are digital sieges in which an attacker causes thousands of hacked systems to hit a target with so much junk traffic that it falls over and remains unreachable by legitimate visitors. While DDoS attacks typically target a single Web site or Internet host, they often result in widespread collateral Internet disruption.
A great deal of DDoS activity on the Internet originates from so-called ‘booter/stresser’ services, which are essentially DDoS-for-hire services which allow even unsophisticated users to launch high-impact attacks. And as we will see, the incessant competition for profits in the blatantly illegal DDoS-for-hire industry can lead those involved down some very strange paths, indeed.
THE FIRST CLUES
The first clues to Anna Senpai’s identity didn’t become clear until I understood that Mirai was just the latest incarnation of an IoT botnet family that has been in development and relatively broad use for nearly three years.
Earlier this summer, my site was hit with several huge attacks from a collection of hacked IoT systems compromised by a family of botnet code that served as a precursor to Mirai. The malware went by several names, including “Bashlite,” “Gafgyt,” “Qbot,” “Remaiten,” and “Torlus.”
All of these related IoT botnet varieties infect new systems in a fashion similar to other well-known Internet worms — propagating from one infected host to another. And like those earlier Internet worms, sometimes the Internet scanning these systems perform to identify other candidates for inclusion into the botnet is so aggressive that it constitutes an unintended DDoS on the very home routers, Web cameras and DVRs that the bot code is trying to subvert and recruit into the botnet. This kind of self-defeating behavior will be familiar to those who recall the original Morris Worm, NIMDA, CODE RED, Welchia, Blaster and SQL Slammer disruptions of yesteryear.
Infected IoT devices constantly scan the Web for other IoT things to compromise, wriggling into devices that are protected by little more than insecure factory-default settings and passwords. The infected devices are then forced to participate in DDoS attacks (ironically, many of the devices most commonly infected by Mirai and similar IoT worms are security cameras).
Mirai’s ancestors had so many names because each name corresponded to a variant that included new improvements over time. In 2014, a group of Internet hooligans operating under the banner “lelddos” very publicly used the code to launch large, sustained attacks that knocked many Web sites offline.
The most frequent target of the lelddos gang were Web servers used to host Minecraft, a wildly popular computer game sold by Microsoft that can be played from any device and on any Internet connection.
The object of Minecraft is to run around and build stuff, block by large pixelated block. That may sound simplistic and boring, but an impressive number of people positively adore this game – particularly pre-teen males. Microsoft has sold more than a 100 million copies of Minecraft, and at any given time there are over a million people playing it online. Players can build their own worlds, or visit a myriad other blocky realms by logging on to their favorite Minecraft server to play with friends.
Image: Minecraft.net
A large, successful Minecraft server with more than a thousand players logging on each day can easily earn the server’s owners upwards of $50,000 per month, mainly from players renting space on the server to build their Minecraft worlds, and purchasing in-game items and special abilities.
Perhaps unsurprisingly, the top-earning Minecraft servers eventually attracted the attention of ne’er-do-wells and extortionists like the lelddos gang. Lelddos would launch a huge DDoS attack against a Minecraft server, knowing that the targeted Minecraft server owner was likely losing thousands of dollars for each day his gaming channel remained offline.
Adding urgency to the ordeal, many of the targeted server’s loyal customers would soon find other Minecraft servers to patronize if they could not get their Minecraft fix at the usual online spot.
Robert Coelho is vice president of ProxyPipe, Inc., a San Francisco company that specializes in protecting Minecraft servers from attacks.
“The Minecraft industry is so competitive,” Coelho said. “If you’re a player, and your favorite Minecraft server gets knocked offline, you can switch to another server. But for the server operators, it’s all about maximizing the number of players and running a large, powerful server. The more players you can hold on the server, the more money you make. But if you go down, you start to lose Minecraft players very fast — maybe for good.”
In June 2014, ProxyPipe was hit with a 300 gigabit per second DDoS attack launched by lelddos, which had a penchant for publicly taunting its victims on Twitter just as it began launching DDoS assaults at the taunted.
The hacker group “lelddos” tweeted at its victims before launching huge DDoS attacks against them.
At the time, ProxyPipe was buying DDoS protection from Reston, Va. -based security giant Verisign. In a quarterly report published in 2014, Verisign called the attack the largest it had ever seen, although it didn’t name ProxyPipe in the report – referring to it only as a customer in the media and entertainment business.
Verisign said the 2014 attack was launched by a botnet of more than 100,000 hacked routers sold by a company called SuperMicro. Days before the huge attack on ProxyPipe, a security researcher published information about a vulnerability in the SuperMicro devices that could allow them to be remotely hacked and commandeered for these sorts of attacks.
THE CENTRALITY OF PROTRAF
Coelho recalled that in mid-2015 his company’s Minecraft customers began coming under attack from a botnet made up of IoT devices infected with Qbot. He said the attacks were directly preceded by a threat made by a then-17-year-old Christopher “CJ” Sculti, Jr., the owner and sole employee of a competing DDoS protection company called Datawagon.
Datawagon also courted Minecraft servers as customers, and its servers were hosted on Internet space claimed by yet another Minecraft-focused DDoS protection provider — ProTraf Solutions.
Christopher “CJ” Sculti, Jr.
According to Coelho, ProTraf was trying to woo many of his biggest Minecraft server customers away from ProxyPipe. Coelho said in mid-2015, Sculti reached out to him on Skype and said he was getting ready to disable Coelho’s Skype account. At the time, an exploit for a software weakness in Skype was being traded online, and this exploit could be used to remotely and instantaneously disable any Skype account.
Sure enough, Coelho recalled, his Skype account and two others used by co-workers were shut off just minutes after that threat, effectively severing a main artery of support for ProxyPipe’s customers – many of whom were accustomed to communicating with ProxyPipe via Skype.
“CJ messaged me about five minutes before the DDoS started, saying he was going to disable my skype,” Coelho said. “The scary thing about when this happens is you don’t know if your Skype account has been hacked and under control of someone else or if it just got disabled.”
Once ProxyPipe’s Skype accounts were disabled, the company’s servers were hit with a massive, constantly changing DDoS attack that disrupted ProxyPipe’s service to its Minecraft server customers. Coelho said within a few days of the attack, many of ProxyPipe’s most lucrative Minecraft servers had moved over to servers run protected by ProTraf Solutions.
“In 2015, the ProTraf guys hit us offline tons, so a lot of our customers moved over to them,” Coelho said. “We told our customers that we knew [ProTraf] were the ones doing it, but some of the customers didn’t care and moved over to ProTraf anyway because they were losing money from being down.”
I found Coelho’s story fascinating because it eerily echoed the events leading up to my Sept. 2016 record 620 Gbps attack. I, too, was contacted via Skype by Sculti — on two occasions. The first was on July 7, 2015, when Sculti reached out apropos of nothing to brag about scanning the Internet for IoT devices running default usernames and passwords, saying he had uploaded some kind of program to more than a quarter-million systems that his scans found.
Here’s a snippet of that conversation:
July 7, 2015:
21:37 CJ: http://ift.tt/1GHYxAg
21:37 CJ: vulnerable routers are a HUGE issue
21:37 CJ: a few months ago
21:37 CJ: I scanned the internet with a few sets of defualt logins
21:37 CJ: for telnet
21:37 CJ: and I was able to upload and execute a binary
21:38 CJ: on 250k devices
21:38 CJ: most of which were routers
21:38 Brian Krebs: o_0
The second time I heard from Sculti on Skype was Sept. 20, 2016 — the day of my 620 Gbps attack. Sculti was angry over a story I’d just published that mentioned his name, and he began rather saltily maligning the reputation of a source and friend who had helped me with that story.
Indignant on behalf of my source and annoyed at Sculti’s rant, I simply blocked his Skype account from communicating with mine and went on with my day. Just minutes after that conversation, however, my Skype account was flooded with thousands of contact requests from compromised or junk Skype accounts, making it virtually impossible to use the software for making phone calls or instant messaging.
Six hours after that Sept. 20 conversation with Sculti, the huge 620 Gbps DDoS attack commenced on this site.
WHO IS LELDDOS?
Coelho said he believes the main members of lelddos gang were Sculti and the owners of ProTraf. Asked why he was so sure of this, he recounted a large lelddos attack in early 2015 against ProxyPipe that coincided with a scam in which large tracts of Internet address space were temporarily stolen from the company.
According to ProxyPipe, a swath of Internet addresses was hijacked from the company by FastReturn, another DDoS mitigation firm that also specialized in protecting Minecraft servers from attacks. Dyn, a company that closely tracks which blocks of Internet addresses are assigned to which organizations, confirmed the timing of the Internet address hijack that Coelho described.
A few months after that attack, the owner of FastReturn — a young man from Dubai named Ammar Zuberi — went to work as a software developer for ProTraf. In the process, Zuberi transferred the majority of Internet addresses assigned to FastReturn over to ProTraf.
Zuberi told KrebsOnSecurity that he was not involved with lelddos, but he acknowledged that he did hijack ProxyPipe’s Internet address space before moving over to ProTraf.
“I was stupid and new to this entire thing and it was interesting to me how insecure the underlying ecosystem of the Internet was,” Zuberi said. “I just kept pushing the envelope to see how far I could get with that, I guess. I eventually realized though and got away from it, although that’s not really much of a justification.”
According to Zuberi, CJ Sculti Jr. was a member of lelddos, as were the two co-owners of ProTraf. This is interesting because not long after the September 2016 Mirai attack took this site offline, several sources who specialize in lurking on cybercrime forums shared information suggesting that the principal author of Bashlite/Qbot was a ProTraf employee: A 19-year-old computer whiz from Washington, Penn. named Josiah White.
White’s profile on LinkedIn lists him as an “enterprise DDoS mitigation expert” at ProTraf, but for years he was better known to those in the hacker community under the alias “LiteSpeed.”
LiteSpeed is the screen name White used on Hackforums[dot]net – a sprawling English-language marketplace where mostly young, low-skilled hackers can buy and sell cybercrime tools and stolen goods with ease. Until very recently, Hackforums also was the definitive place to buy and sell DDoS-for-hire services.
I contacted White to find out if the rumors about his authorship of Qbot/Bashlite were true. White acknowledged that he had written some of Qbot/Bashlite’s components — including the code segment that the malware uses to spread the infection to new machines. But White said he never intended for his code to be sold and traded online.
White claims that a onetime friend and Hackforums member nicknamed “Vyp0r” betrayed his trust and forced him to publish the code online by threatening to post White’s personal details online and to “swat” his home. Swatting is a potentially deadly hoax in which an attacker calls in a fake hostage situation or bomb threat at a residence or business with the intention of sending a team of heavily-armed police officers to the target’s address.
“Most of the stuff that I had wrote was for friends, but as I later realized, things on HF [Hackforums] tend to not remain private,” White wrote in an instant message to KrebsOnSecurity. “Eventually I learned they were reselling them in under-the-table deals, and so I just released everything to stop that. I made some mistakes when I was younger, and I realize that, but I’m trying to set my path straight and move on.”
WHO IS PARAS JHA?
White’s employer ProTraf Solutions has only one other employee – 20-year-old President Paras Jha, from Fanwood, NJ. On his LinkedIn profile, Jha states that “Paras is a passionate entrepreneur driven by the want to create.” The profile continues:
“Highly self-motivated, in 7th grade he began to teach himself to program in a variety of languages. Today, his skillset for software development includes C#, Java, Golang, C, C++, PHP, x86 ASM, not to mention web ‘browser languages’ such as Javascript and HTML/CSS.”
Jha’s LinkedIn page also shows that he has extensive experience running Minecraft servers, and that for several years he worked for Minetime, one of the most popular Minecraft servers at the time.
After first reading Jha’s LinkedIn resume, I was haunted by the nagging feeling that I’d seen this rather unique combination of computer language skills somewhere else online. Then it dawned on me: The mix of programming skills that Jha listed in his LinkedIn profile is remarkably similar to the skills listed on Hackforums by none other than Mirai’s author — Anna-Senpai.
Prior to leaking the Mirai source code on HackForums at the end of September 2016, the majority of Anna-Senpai’s posts on Hackforums were meant to taunt other hackers on the forum who were using Qbot to build DDoS attack armies.
The best example of this is a thread posted to Hackforums on July 10, 2016 titled “Killing All Telnets,” in which Anna-Senpai boldly warns forum members that the malicious code powering his botnet contains a particularly effective “bot killer” designed to remove Qbot from infected IoT devices and to prevent systems infected with his malware from ever being reinfected with Qbot again.
Anna-Senpai warns Qbot users that his new worm (relatively unknown by its name “Mirai” at the time) was capable of killing off IoT devices infected with Qbot.
Initially, forum members dismissed Anna’s threats as idle taunts, but as the thread continues for page after page we can see from other forum members that his bot killer is indeed having its intended effect. [Oddly enough, it’s very common for the authors of botnet code to include patching routines to protect their newly-enslaved bots from being compromised by other miscreants. Just like in any other market, there is a high degree of competition between cybercrooks who are constantly seeking to add more zombies to their DDoS armies, and they often resort to unorthodox tactics to knock out the competition. As we’ll see, this kind of internecine warfare is a major element in this story.]
“When the owner of this botnet wrote a July 2016 Hackforums thread named ‘Killing all Telnets’, he was right,” wrote Allison Nixon and Pierre Lamy, threat researchers for New York City-based security firm Flashpoint. “Our intelligence around that time reflected a massive shift away from the traditional gafgyt infection patterns and towards a different pattern that refused to properly execute on analysts’ machines. This new species choked out all the others.”
It wasn’t until after I’d spoken with Jha’s business partner Josiah White that I began re-reading every one of Anna-Senpai’s several dozen posts to Hackforums. The one that made Jha’s programming skills seem familiar came on July 12, 2016 — a week after posting his “Killing All Telnets” discussion thread — when Anna-Senpai contributed to a Hackforums thread started by a hacker group calling itself “Nightmare.”
Such groups or hacker cliques are common on Hackforums, and forum members can apply for membership by stating their skills and answering a few questions. Anna-Senpai posted his application for membership into this thread among dozens of others, describing himself thusly:
“Age: 18+
Location and Languages Spoken: English
Which of the aforementioned categories describe you the best?: Programmer / Development
What do you Specialize in? (List only): Systems programming / general low level languages (C + ASM)
Why should we choose you over other applicants?: I have 8 years of development under my belt, and I’m very familiar with programming in a variety of languages, including ASM, C, Go, Java, C#, and PHP. I like to use this knowledge for personal gain.”
The Hackforums post shows Jha and Anna-Senpai have the exact same programming skills. Additionally, according to an analysis of Mirai by security firm Incapsula, the malicious software used to control a botnet powered by Mirai is coded in Go (a.k.a. “Golang”), a somewhat esoteric programming language developed by Google in 2007 that saw a surge in popularity in 2016. Incapsula also said the malcode that gets installed on IoT bots is coded in C.
DREADIS[NOT]COOL
I began to dig deeper into Paras Jha’s history and footprint online, and discovered that his father in October 2013 registered a vanity domain for his son, parasjha.info. That site is no longer online, but a historic version of it cached by the indispensable Internet Archive includes a resume of Jha’s early work with various popular Minecraft servers. Here’s a autobiographical snippet from parasjha.info:
“My passion is to utilize my skills in programming and drawing to develop entertaining games and software for the online game ‘Minecraft. Someday, I plan to start my own enterprise focused on the gaming industry targeted towards game consoles and the mobile platform. To further my ideas and help the gaming community, I have released some of my code to open source projects on websites centered on public coding under the handle dreadiscool.”
A Google search for this rather unique username “dreadiscool” turns up accounts by the same name at dozens of forums dedicated to computer programming and Minecraft. In many of those accounts, the owner is clearly frustrated by incessant DDoS attacks targeting his Minecraft servers, and appears eager for advice on how best to counter the assaults.
From Dreadiscool’s various online postings, it seems clear that at some point Jha decided it might be more profitable and less frustrating to defend Minecraft servers from DDoS attacks, as opposed to trying to maintain the servers themselves.
“My experience in dealing with DDoS attacks led me to start a server hosting company focused on providing solutions to clients to mitigate such attacks,” Jha wrote on his vanity site.
Some of the more recent Dreadiscool posts date to November 2016, and many of those posts are lengthy explanations of highly technical subjects. The tone of voice in these posts is far more confident and even condescending than the Dreadiscool from years earlier, covering a range of subjects from programming to DDoS attacks.
Dreadiscool’s account on Spigot Minecraft forum since 2013 includes some interesting characters photoshopped into this image.
For example, Dreadiscool has been an active member of the Minecraft forum spigotmc.org since 2013. This user’s avatar (pictured above) on spigotmc.org is an altered image taken from the 1994 Quentin Tarantino cult hit “Pulp Fiction,” specifically from a scene in which the gangster characters Jules and Vincent are pointing their pistols in the same direction. However, the heads of both actors have been digitally altered to include someone else’s faces.
Pasted over the head of John Travolta’s character (left) is a real-life picture of Vyp0r — the Hackforums nickname of the guy that ProTraf’s Josiah White said threatened him into releasing the source code for Bashlite. On the shoulders of Samuel L. Jackson’s body is the face of Tucker Preston, co-founder of BackConnect Security — a competing DDoS mitigation provider that also has a history of hijacking Internet address ranges from other providers.
Pictured below and to the left of Travolta and Jackson’s characters — seated on the bed behind them — is “Yamada,” a Japanese animation (“anime”) character featured in the anime movie B Gata H Hei.
Turns out, there is a Dreadiscool user on MyAnimeList.net, a site where members proudly list the various anime films they have watched. Dreadiscool says B Gata H Kei is one of nine anime film series he has watched. Among the other eight? The anime series Mirai Nikki, from which the Mirai malware derives its name.
Dreadiscool’s Reddit profile also is very interesting, and most of the recent posts there relate to major DDoS attacks going on at the time, including a series of DDoS attacks on Rutgers University. More on Rutgers later.
A CHAT WITH ANNA-SENPAI
At around the same time as the record 620 Gbps attack on KrebsOnSecurity, French Web hosting giant OVH suffered an even larger attack — launched by the very same Mirai botnet used to attack this site. Although this fact has been widely reported in the news media, the reason for the OVH attack may not be so well known.
According to a tweet from OVH founder and chief technology officer Octave Klaba, the target of that massive attack also was a Minecraft server (although Klaba mistakenly called the target “mindcraft servers” in his tweet).
A tweet from OVH founder and CTO, stating the intended target of Sept. 2016 Mirai DDoS on his company.
Turns out, in the days following the attack on this site and on OVH, Anna-Sempai had trained his Mirai botnet on Coelho’s ProxyPipe, completely knocking his DDoS mitigation service offline for the better part of a day and causing problems for many popular Minecraft servers.
Unable to obtain more bandwidth and unwilling to sign an expensive annual contract with a third-party DDoS mitigation firm, Coelho turned to the only other option available to get out from under the attack: Filing abuse complaints with the Internet hosting firms that were responsible for providing connectivity to the control server used to orchestrate the activities of the Mirai botnet.
“We did it because we had no other options, and because all of our customers were offline,” Coelho said. “Even though no other DDoS mitigation company was able to defend against these attacks [from Mirai], we still needed to defend against it because our customers were starting to move to other providers that attracted fewer attacks.”
After scouring a list of Internet addresses tied to bots used in the attack, Coelho said he was able to trace the control server for the Mirai botnet back to a hosting provider in Ukraine. That company — BlazingFast[dot]io — has a reputation for hosting botnet control networks.
Getting no love from BlazingFast, Coelho said he escalated his complaint to Voxility, a company that was providing DDoS protection to BlazingFast at the time.
“Voxility acknowledged the presence of the control server, and said they null-routed [removed] it, but they didn’t,” Coelho said. “They basically lied to us and didn’t reply to any other emails.”
Undeterred, Coelho said he then emailed the ISP that was upstream of BlazingFast, but received little help from that company or the next ISP further upstream. Coelho said the fifth ISP upstream of BlazingFast, however — Internet provider Telia Sonera — confirmed his report, and promptly had the Mirai botnet’s control server killed.
As a result, many of the systems infected with Mirai could no longer connect to the botnet’s control servers, drastically reducing the botnet’s overall firepower.
“The action by Telia cut the size of the attacks launched by the botnet down to 80 Gbps,” well within the range of ProxyPipe’s in-house DDoS mitigation capabilities, Coelho said.
Incredibly, on Sept. 28, Anna-Senpai himself would reach out to Coelho via Skype. Coelho shared a copy of that chat conversation with KrebsOnSecurity. The log shows that Anna correctly guessed ProxyPipe was responsible for the abuse complaints that kneecapped Mirai. Anna-Senpai said he guessed ProxyPipe was responsible after reading a comment on a KrebsOnSecurity blog post from a reader who shared the same username as Coelho’s business partner.
In the following chat, Coelho is using the Skype nickname “katie.onis.”
[10:23:08 AM] live:anna-senpai: ^
[10:26:08 AM] katie.onis: hi there.
[10:26:52 AM] katie.onis: How can I help you?
[10:28:06 AM] live:anna-senpai: hi
[10:28:45 AM] live:anna-senpai: you know i had my suspicions, but this one was proof
http://ift.tt/2k0nPGc [this is a benign/safe link to a screenshot of some comments on KrebsOnSecurity.com]
[10:28:59 AM] live:anna-senpai: don’t get me wrong, im not even mad, it was pretty funny actually. nobody has ever done that to my c2 [Mirai “command and control” server]
[10:29:25 AM] live:anna-senpai: (goldmedal)
[10:29:29 AM] katie.onis: ah you’re mistaken, that’s not us.
[10:29:33 AM] katie.onis: but we know who it is
[10:29:42 AM] live:anna-senpai: eric / 9gigs
[10:29:47 AM] katie.onis: no, 9gigs is erik
[10:29:48 AM] katie.onis: not eric
[10:29:53 AM] katie.onis: different people
[10:30:09 AM] live:anna-senpai: oh?
[10:30:17 AM] katie.onis: yep
[10:30:39 AM] live:anna-senpai: is he someone related to you guys?
[10:30:44 AM] katie.onis: not related to us, we just know him
[10:30:50 AM] katie.onis: anyway, we’re not interested in any harm, we simply don’t want attacks against us.
[10:31:16 AM] live:anna-senpai: yeah i figured, i added you because i wanted to tip my hat if that was actually you lol
[10:31:24 AM] katie.onis: we didn’t make that dumb post
[10:31:26 AM] katie.onis: if that is what you are asking
[10:31:30 AM] katie.onis: but yes, we were involved in doing that.
[10:31:47 AM] live:anna-senpai: so you got it nulled, but some other eric is claiming credit for it?
[10:31:52 AM] katie.onis: seems so.
[10:31:52 AM] live:anna-senpai: eric with a c
[10:31:56 AM] live:anna-senpai: lol
[10:32:17 AM] live:anna-senpai: can’t say im surprised, tons of people take credit for things that they didn’t do if nobody else takes credit for
[10:32:24 AM] katie.onis: we’re not interested in taking credit
[10:32:30 AM] katie.onis: we just wanted the attacks to get smaller
NOTICE AND TAKEDOWN
One reason Anna-Senpai may have been enamored of Coelho’s approach to taking down Mirai is that Anna-Senpai had spent the previous month doing exactly the same thing to criminals running IoT botnets powered by Mirai’s top rival — Qbot.
A month before this chat between Coelho and Anna-Senpai, Anna is busy sending abuse complaints to various hosting firms, warning them that they are hosting huge IoT botnet control channels that needed to be shut down. This was clearly just part of an extended campaign by the Mirai botmasters to eliminate other IoT-based DDoS botnets that might compete for the same pool of vulnerable IoT devices. Anna confirmed this in his chat with Coelho:
[10:50:36 AM] live:anna-senpai: i have good killer so nobody else can assemble a large net
[10:50:53 AM] live:anna-senpai: i monitor the devices to see for any new threats
[10:51:33 AM] live:anna-senpai: and when i find any new host, i get them taken down
The ISPs or hosting providers that received abuse complaints from Anna-Senpai were all encouraged to reply to the email address [email protected] for questions and/or confirmation of the takedown. ISPs that declined to act promptly on Anna-Senpai’s Qbot email complaints soon found themselves on the receiving end of enormous DDoS attacks from Mirai.
Francisco Dias, owner of hosting provider Frantech, found out firsthand what it would cost to ignore one of Anna’s abuse reports. In mid-September 2016, Francisco accidentally got into an Internet fight with Anna-Senpai. The Mirai botmaster was using the nickname “jorgemichaels” at the time — and Jorgemichaels was talking trash on LowEndTalk.com, a discussion forum for vendors of low-costing hosting.
Specifically, Jorgemichaels takes Francisco to task publicly on the forum for ignoring one of his Qbot abuse complaints. Francisco tells Jorgemichaels to file a complaint with the police if it’s so urgent. Jorgemichaels tells Francisco to shut up, and when Francisco is silent for a while Jorgemichaels gloats that Francisco learned his place. Francisco explains his further silence on the thread by saying he’s busy supporting customers, to which Jorgemichaels replies, “Sounds like you just got a lot more customers to help. Don’t mess with the underworld francisco or it will harm your business.”
Shortly thereafter, Frantech is systematically knocked offline after being attacked by Mirai. Below is a fascinating snippet from a private conversation between Francisco and Anna-Senpai/Jorgemichaels, in which Francisco kills the reported Qbot control server to make Anna/Jorgemichaels call off the attack.
Using the nickname “jorgemichaels” on LowEndTalk, Anna-Senpai reaches out to Francisco Dias after Dias ignores Anna’s abuse complaint. Francisco agrees to kill the Qbot control server only after being walloped with Mirai.
Back to the chat between Anna-Senpai and Coelho at the end of Sept 2016. Anna-Senpai tells Coelho that the attacks against ProxyPipe aren’t personal; they’re just business. Anna says he has been renting out “net spots” — sizable chunks of his Mirai botnet — to other hackers who use them in their own attacks for pre-arranged periods of time.
By way of example, Anna brags that as he and Coelho are speaking, the owners of a large Minecraft server were paying him to launch a crippling DDoS against Hypixel, currently the world’s most popular Minecraft server. KrebsOnSecurity confirmed with Hypixel that they were indeed under a massive attack from Mirai between Sept. 27 and 30.
[12:24:00 PM] live:anna-senpai: right now i just have a script sitting there hitting them for 45s every 20 minutes
[12:24:09 PM] live:anna-senpai: enough to drop all players and make them rage
Coelho told KrebsOnSecurity that the on-again, off-again attack DDoS method that Anna described using against Hypixel was designed not just to cost Hypixel money. The purpose of that attack method, he said, was to aggravate and annoy Hypixel’s customers so much that they might take their business to a competing Minecraft server.
“It’s not just about taking it down, it’s about making everyone who is playing on that server crazy mad,” Coelho explained. “If you launch the attack every 20 minutes for a short period of time, you basically give the players just enough time to get back on the server and involved in another game before they’re disconnected again.”
Anna-Senpai told Coelho that paying customers also were the reason for the 620 Gbps attack on KrebsOnSecurity. Two weeks prior to that attack, I published the results of a months-long investigation revealing that “vDOS” — one of the largest and longest-running DDoS-for-hire services — had been hacked, exposing details about the services owners and customers.
The story noted that vDOS earned its proprietors more than $600,000 and was being run by two 18-year-old Israeli men who went by the hacker aliases “applej4ck” and “p1st0”. Hours after that piece ran, Israeli authorities arrested both men, and vDOS — which had been in operation for four years — was shuttered for good.
[10:47:42 AM] live:anna-senpai: i sell net spots, starting at $5k a week
[10:47:50 AM] live:anna-senpai: and one client was upset about applejack arrest
[10:48:01 AM] live:anna-senpai: so while i was gone he was sitting on them for hours with gre and ack
[10:48:14 AM] live:anna-senpai: when i came back i was like oh fuck
[10:48:16 AM] live:anna-senpai: and whitelisted the prefix
[10:48:24 AM] live:anna-senpai: but then krebs tweeted that akamai is kicking them off
[10:48:31 AM] live:anna-senpai: fuck me
[10:48:43 AM] live:anna-senpai: he was a cool guy too, i like his article
[SIDE NOTE: If true, it’s ironic that someone would hire Anna-Senpai to attack my site in retribution for the vDOS story. That’s because the firepower behind applej4ck’s vDOS service was generated in large part by a botnet of IoT systems infected with a Qbot variant — the very same botnet strain that Anna-Senpai and Mirai were busy killing and erasing from the Internet.]
Coelho told KrebsOnSecurity that if his side of the conversation reads like he was being too conciliatory to his assailant, that’s because he was wary of giving Anna a reason to launch another monster attack against ProxyPipe. After all, Coelho said, the Mirai attacks on ProxyPipe caused many customers to switch to other Minecraft servers, and Coelho estimates the attack cost the company between $400,000 and $500,000.
Nevertheless, about halfway through the chat Coelho gently confronts Anna on the consequences of his actions.
[10:54:17 AM] katie.onis: People have a genuine reason to be unhappy though about large attacks like this
[10:54:27 AM] live:anna-senpai: yeah
[10:54:32 AM] katie.onis: There’s really nothing anyone can do lol
[10:54:36 AM] live:anna-senpai:
[10:54:38 AM] katie.onis: And it does affect their lives
[10:55:10 AM] live:anna-senpai: well, i stopped caring about other people a long time ago
[10:55:18 AM] live:anna-senpai: my life experience has always been get fucked over or fuck someone else over
[10:55:52 AM] katie.onis: My experience with [ProxyPipe] thus far has been
[10:55:54 AM] katie.onis: Do nothing bad to anyone
[10:55:58 AM] katie.onis: And still get screwed over
[10:55:59 AM] katie.onis: Haha
The two even discussed anime after Anna-Senpai guessed that Coelho might be a fan of the genre. Anna-Senpai says he watched the anime series “Gate,” a reference to the above-mentioned B Gata H Hei that Dreadiscool included in the list of anime film series he’s watched. Anna also confirms that the name for his bot malware was derived from the anime series Mirai Nikki.
[5:25:12 PM] live:anna-senpai: i rewatched mirai nikki recently
[5:25:22 PM] live:anna-senpai: (it was the reason i named my bot mirai lol)
DREADISCOOL = ANNA = JHA?
Coelho said when Anna-Senpai first reached out to him on Skype, he had no clue about the hacker’s real-life identity. But a few weeks after that chat conversation with Anna-Senpai, Coelho’s business partner (the Eric referenced in the first chat segment above) said he noticed that some of the code in Mirai looked awfully similar to code that Dreadiscool had posted to his Github account.
“He started to come to the conclusion that maybe Anna was Paras,” Coelho said. “He gave me a lot of ideas, and after I did my own investigation I decided he was probably right.”
Coelho said he’s known Paras Jha for more than four years, having met him online when Jha was working for Minetime — which ProxyPipe was protecting from DDoS attacks at the time.
“We talked a lot back then and we used to program a lot of projects together,” Coelho said. “He’s really good at programming, but back then he wasn’t. He was a little bit behind, and I was teaching him most everything.”
According to Coelho, as Jha became more confident in his coding skills, he also grew more arrogant, belittling others online who didn’t have as firm a grasp on subjects such as programming and DDoS mitigation.
“He likes to be recognized for his knowledge, being praised and having other people recognize that,” Coelho said of Jha. “He brags too much, basically.”
Coelho said not long after Minetime was hit by a DDoS extortion attack in 2013, Paras joined Hackforums and fairly soon after stopped responding to his online messages.
“He just kind of dropped off the face of the earth entirely,” he said. “When he started going on Hackforums, I didn’t know him anymore. He became a different person.”
Coelho said he doesn’t believe his old friend wished him harm, and that Jha was probably pressured into attacking ProxyPipe.
“In my opinion he’s still a kid, in that he gets peer-pressured a lot,” Coelho said. “If he didn’t [launch the attack] not only would he feel super excluded, but these people wouldn’t be his friends anymore, they could out him and screw him over. I think he was pretty much in a really bad position with the people he got involved with.”
THE RUTGERS DDOS ATTACKS
On Dec. 16, security vendor Digital Shadows presented a Webinar that focused on clues about the Mirai author’s real life identity. According to their analysis, before the Mirai author was known as Anna-Senpai on Hackforums, he used the nickname “Ogmemes123123” (this also was the alias of the Skype username that contacted Coelho), and the email address [email protected] (recall this is the same email address Anna-Senpai used in his alerts to various hosting firms about the urgent need to take down Qbot control servers hosted on their networks).
Digital Shadows noted that the Mirai author appears to have used another nickname: “OG_Richard_Stallman,” a likely reference to the founder of the Free Software Foundation. The [email protected] account was used to register a Facebook account in the name of OG_Richard Stallman.
That Facebook account states that OG_Richard_Stallman began studying computer engineering at New Brunswick, NJ-based Rutgers University in 2015.
As it happens, Paras Jha is a student at Rutgers University. This is especially notable because Rutgers has been dealing with a series of DDoS attacks on its network since the fall semester of 2015 — more than a half dozen incidents in all. With each DDoS, the attacker would taunt the university in online posts and media interviews, encouraging the school to spend the money to purchase some kind of DDoS mitigation service.
Using the nicknames “og_richard_stallman,” “exfocus” and “ogexfocus,” the person who attacked Rutgers more than a half-dozen times took to Reddit and Twitter to claim credit for the attacks. Exfocus even created his own “Ask Me Anything” interview on Reddit to discuss the Rutgers attacks.
Exfocus also gave an interview to a New Jersey-based blogger, claiming he got paid $500 an hour to DDoS the university with as many as 170,000 bots. Here are a few snippets from that interview, in which he blames the attacks on a “client” who is renting his botnet:
“Are you for real? Why would you do an interview with us if you’re getting paid?
Normally I don’t show myself, but the entity paying me has something against the school. They want me to “make a splash”.
Why do you have a twitter account where you publically broadcast patronizing messages. Are you worried that this increases the risk of things getting back to you?
Public twitter is on clients request. The client hates the school for whatever reason. They told me to say generic things like that I hate the bus system and etc.
Have you ever attacked RU before?
During freshman registration the client requested it also – he didn’t want any publicity then though.
What are your plans for the future in terms of DDOSing and attacking the Rutgers cyber infrastructure?
When I stop getting paid – I’ll stop DDosing lol. I’m hoping that RU will sign on some ddos mitigation provider. I get paid extra if that happens.
At some point you said you were at the Livingston student center – outside of Sbarro. In this interview you said that you aren’t affiliated directly with Rutgers, did you lie then?
Yes”
An online search for the Gmail address used by Anna-Senpai and OG_Richard_Stallman turns up a Pastebin post from July 1, 2016, in which an anonymous Pastebin user creates a “dox” of OG_Richard_Stallman. Doxing refers to the act of publishing someone’s personal information online and/or connecting an online alias to a real life identity.
The dox said OG_Richard_Stallman was connected to an address and phone number of an individual living in Turkey. But this is almost certainly a fake dox intended to confuse cybercrime investigators. Here’s why:
A Google search shows that this same address and phone number showed up in another dox on Pastebin from almost three years earlier — June 2013 — intended to expose or confuse the identity of a Hackforums user known as LiteSpeed. Recall that LiteSpeed is the same alias that ProTraf’s Josiah White acknowledged using on Hackforums.
EXTORTION ATTEMPTS BY OG_RICHARD_STALLMAN
This OG_Richard_Stallman identity is connected to Anna-Senpai by another person we’ve heard from already: Francisco Dias, whose Frantech ISP was attacked by Anna-Senpai and Mirai in mid-September. Francisco told KrebsOnSecurity that in early August 2016 he began receiving extortion emails from a Gmail address associated with a OG_Richard_Stallman.
“This guy using the Richard Stallman name added me on Skype and basically said ‘I’m going to knock all of your [Internet addresses] offline until you pay me’,” Dias recalled. “He told me the up front cost to stop the attack was 10 bitcoins [~USD $5,000 at the time], and if I didn’t pay within four hours after the attack started the fee would double to 20 bitcoins.”
Dias said he didn’t pay the demand and eventually OG_Richard_Stallman called off the attack. But he said for a while the attacks were powerful enough to cause problems for Frantech’s Internet provider.
“He was hitting us so hard with Mirai that he was dropping large parts of Hurricane Electric and causing problems at their Los Angeles point of presence,” Dias said. “I basically threw everything behind [DDoS mitigation provider] Voxility, and eventually Stallman buggered off.”
The OG_Richard_Stallman identity also was tied to similar extortion attacks at the beginning of August against one hosting firm that had briefly been one of ProTraf’s customers in 2016. The company declined to be quoted on the record, but said it stopped doing business with Protraf in mid-2016 because they were unhappy with the quality of service.
The Internet provider said not long after that it received an extortion demand from the “OG_Richard_Stallman” character for $5,000 in Bitcoin to avoid a DDoS attack. One of the company’s researchers contacted the extortionist via the [email protected] address supplied in the email, but posing as someone who wished to hire some DDoS services.
OG_Richard_Stallman told the researcher that he could guarantee 350 Gbps of attack traffic and that the target would go down or the customer would receive a full refund. The price for the attack? USD $100 worth of Bitcoin for every five minutes of attack time.
My source at the hosting company said his employer declined to pay the demand, and subsequently got hit with an attack from Mirai that clocked in at more than 300 Gbps.
“Clearly, the attacker is very technical, as they attacked every single [Internet address] within the subnet, and after we brought up protection, he started attacking upstream router interfaces,” the source said on condition of anonymity.
Asked who they thought might be responsible for the attacks, my source said his employer immediately suspected ProTraf. That’s because the Mirai attack also targeted the Internet address for the company’s home page, but that Internet address was hidden by DDoS mitigation firm Cloudflare. However, ProTraf knew about the secret address from its previous work with the company, the source explained.
“We believe it’s Protraf’s staff or someone related to Protraf,” my source said.
A source at an Internet provider agreed to share information about an extortion demand his company received from OG_Richard_Stallman in August 2016. Here he is contacting the Stallman character directly and pretending to be someone interested in renting a botnet. Notice the source brazenly said he wanted to DDoS ProTraf.
DDOS CONFESSIONS
After months of gathering information about the apparent authors of Mirai, I heard from Ammar Zuberi, once a co-worker of ProTraf President Paras Jha.
Zuberi told KrebsOnSecurity that Jha admitted he was responsible for both Mirai and the Rutgers DDoS attacks. Zuberi said when he visited Jha at his Rutgers University dorm in October 2015, Paras bragged to him about launching the DDoS attacks against Rutgers.
“He was laughing and bragging about how he was going to get a security guy at the school fired, and how they raised school fees because of him,” Zuberi recalled. “He didn’t really say why he did it, but I think he was just sort of experimenting with how far he could go with these attacks.”
Zuberi said he didn’t realize how far Jha had gone with his DDoS attacks until he confronted him about it late last year. Zuberi said he was on his way to see his grandmother in Arizona at the end of November 2016, and he had a layover in New York. So he contacted Jha and arranged to spend the night at Jha’s home in Fanwood, New Jersey.
As I noted in Spreading the DDoS Disease and Selling the Cure, Anna-Senpai leaked the Mirai code on a domain name (santasbigcandycane[dot]cx) that was registered via Namecentral, an extremely obscure domain name registrar which had previously been used to register fewer than three dozen other domains over a three-year period.
According to Zuberi, only five people knew about the existence of Namecentral: himself, CJ Sculti, Paras Jha, Josiah White and Namecentral’s owner Jesse Wu (19-year-old Wu features prominently in the DDoS Disease story linked in the previous paragraph).
“When I saw that the Mirai code had been leaked on that domain at Namecentral, I straight up asked Paras at that point, ‘Was this you?,’ and he smiled and said yep,” Zuberi recalled. “Then he told me he’d recently heard from an FBI agent who was investigating Mirai, and he showed me some text messages between him and the agent. He was pretty proud of himself, and was bragging that he led the FBI on a wild goose chase.”
Zuberi said he hasn’t been in contact with Jha since visiting his home in November. Zuberi said he believes Jha wrote most of the code that Mirai uses to control the individual bot-infected IoT devices, since it was written in Golang and Jha’s partner White didn’t code well in this language. Zuberi said he thought White’s role was mainly in developing the spreading code used to infect new IoT devices with Mirai, since that was written in C — a language White excelled at.
In the time since most of the above occurred, the Internet address ranges previously occupied by ProTraf have been withdrawn. ProxyPipe’s Coelho said it could be that the ProTraf simply ran out of money.
ProTraf’s Josiah White explained the disappearance of ProTraf’s Internet space as part of an effort to reboot the company.
“We [are] in the process of restructuring and refocusing what we are doing,” White told KrebsOnSecurity.
Jha did not respond to requests for comment.
Rutgers University did not respond to requests for comment.
The FBI officials could not be immediately reached for comment.
A copy of the entire chat between Anna-Senpai and ProxyPipe’s Coelho is available here.
0 notes
Text
Who is Anna-Senpai, the Mirai Worm Author?
On September 22, 2016, this site was forced offline for nearly four days after it was hit with “Mirai,” a malware strain that enslaves poorly secured Internet of Things (IoT) devices like wireless routers and security cameras into a botnet for use in large cyberattacks. Roughly a week after that assault, the individual(s) who launched that attack — using the name “Anna Senpai” — released the source code for Mirai, spawning dozens of copycat attack armies online.
After months of digging, KrebsOnSecurity is now confident to have uncovered Anna Senpai’s real-life identity, and the identity of at least one co-conspirator who helped to write and modify the malware.
Mirai co-author Anna-Senpai leaked the source code for Mirai on Sept. 30, 2016.
Before we go further, a few disclosures are probably in order. First, this is easily the longest story I’ve ever written on this blog. It’s lengthy because I wanted to walk readers through my process of discovery, which has taken months to unravel. The details help in understanding the financial motivations behind Mirai and the botnet wars that preceded it. Also, I realize there are a great many names to keep track of as you read this post, so I’ve included a glossary.
The story you’re reading now is the result of hundreds of hours of research. At times, I was desperately seeking the missing link between seemingly unrelated people and events; sometimes I was inundated with huge amounts of information — much of it intentionally false or misleading — and left to search for kernels of truth hidden among the dross. If you’ve ever wondered why it seems that so few Internet criminals are brought to justice, I can tell you that the sheer amount of persistence and investigative resources required to piece together who’s done what to whom (and why) in the online era is tremendous.
As noted in previous KrebsOnSecurity articles, botnets like Mirai are used to knock individuals, businesses, governmental agencies, and non-profits offline on a daily basis. These so-called “distributed denial-of-service (DDoS) attacks are digital sieges in which an attacker causes thousands of hacked systems to hit a target with so much junk traffic that it falls over and remains unreachable by legitimate visitors. While DDoS attacks typically target a single Web site or Internet host, they often result in widespread collateral Internet disruption.
A great deal of DDoS activity on the Internet originates from so-called ‘booter/stresser’ services, which are essentially DDoS-for-hire services which allow even unsophisticated users to launch high-impact attacks. And as we will see, the incessant competition for profits in the blatantly illegal DDoS-for-hire industry can lead those involved down some very strange paths, indeed.
THE FIRST CLUES
The first clues to Anna Senpai’s identity didn’t become clear until I understood that Mirai was just the latest incarnation of an IoT botnet family that has been in development and relatively broad use for nearly three years.
Earlier this summer, my site was hit with several huge attacks from a collection of hacked IoT systems compromised by a family of botnet code that served as a precursor to Mirai. The malware went by several names, including “Bashlite,” “Gafgyt,” “Qbot,” “Remaiten,” and “Torlus.”
All of these related IoT botnet varieties infect new systems in a fashion similar to other well-known Internet worms — propagating from one infected host to another. And like those earlier Internet worms, sometimes the Internet scanning these systems perform to identify other candidates for inclusion into the botnet is so aggressive that it constitutes an unintended DDoS on the very home routers, Web cameras and DVRs that the bot code is trying to subvert and recruit into the botnet. This kind of self-defeating behavior will be familiar to those who recall the original Morris Worm, NIMDA, CODE RED, Welchia, Blaster and SQL Slammer disruptions of yesteryear.
Infected IoT devices constantly scan the Web for other IoT things to compromise, wriggling into devices that are protected by little more than insecure factory-default settings and passwords. The infected devices are then forced to participate in DDoS attacks (ironically, many of the devices most commonly infected by Mirai and similar IoT worms are security cameras).
Mirai’s ancestors had so many names because each name corresponded to a variant that included new improvements over time. In 2014, a group of Internet hooligans operating under the banner “lelddos” very publicly used the code to launch large, sustained attacks that knocked many Web sites offline.
The most frequent target of the lelddos gang were Web servers used to host Minecraft, a wildly popular computer game sold by Microsoft that can be played from any device and on any Internet connection.
The object of Minecraft is to run around and build stuff, block by large pixelated block. That may sound simplistic and boring, but an impressive number of people positively adore this game – particularly pre-teen males. Microsoft has sold more than a 100 million copies of Minecraft, and at any given time there are over a million people playing it online. Players can build their own worlds, or visit a myriad other blocky realms by logging on to their favorite Minecraft server to play with friends.
Image: Minecraft.net
A large, successful Minecraft server with more than a thousand players logging on each day can easily earn the server’s owners upwards of $50,000 per month, mainly from players renting space on the server to build their Minecraft worlds, and purchasing in-game items and special abilities.
Perhaps unsurprisingly, the top-earning Minecraft servers eventually attracted the attention of ne’er-do-wells and extortionists like the lelddos gang. Lelddos would launch a huge DDoS attack against a Minecraft server, knowing that the targeted Minecraft server owner was likely losing thousands of dollars for each day his gaming channel remained offline.
Adding urgency to the ordeal, many of the targeted server’s loyal customers would soon find other Minecraft servers to patronize if they could not get their Minecraft fix at the usual online spot.
Robert Coelho is vice president of ProxyPipe, Inc., a San Francisco company that specializes in protecting Minecraft servers from attacks.
“The Minecraft industry is so competitive,” Coelho said. “If you’re a player, and your favorite Minecraft server gets knocked offline, you can switch to another server. But for the server operators, it’s all about maximizing the number of players and running a large, powerful server. The more players you can hold on the server, the more money you make. But if you go down, you start to lose Minecraft players very fast — maybe for good.”
In June 2014, ProxyPipe was hit with a 300 gigabit per second DDoS attack launched by lelddos, which had a penchant for publicly taunting its victims on Twitter just as it began launching DDoS assaults at the taunted.
The hacker group “lelddos” tweeted at its victims before launching huge DDoS attacks against them.
At the time, ProxyPipe was buying DDoS protection from Reston, Va. -based security giant Verisign. In a quarterly report published in 2014, Verisign called the attack the largest it had ever seen, although it didn’t name ProxyPipe in the report – referring to it only as a customer in the media and entertainment business.
Verisign said the 2014 attack was launched by a botnet of more than 100,000 hacked routers sold by a company called SuperMicro. Days before the huge attack on ProxyPipe, a security researcher published information about a vulnerability in the SuperMicro devices that could allow them to be remotely hacked and commandeered for these sorts of attacks.
THE CENTRALITY OF PROTRAF
Coelho recalled that in mid-2015 his company’s Minecraft customers began coming under attack from a botnet made up of IoT devices infected with Qbot. He said the attacks were directly preceded by a threat made by a then-17-year-old Christopher “CJ” Sculti, Jr., the owner and sole employee of a competing DDoS protection company called Datawagon.
Datawagon also courted Minecraft servers as customers, and its servers were hosted on Internet space claimed by yet another Minecraft-focused DDoS protection provider — ProTraf Solutions.
Christopher “CJ” Sculti, Jr.
According to Coelho, ProTraf was trying to woo many of his biggest Minecraft server customers away from ProxyPipe. Coelho said in mid-2015, Sculti reached out to him on Skype and said he was getting ready to disable Coelho’s Skype account. At the time, an exploit for a software weakness in Skype was being traded online, and this exploit could be used to remotely and instantaneously disable any Skype account.
Sure enough, Coelho recalled, his Skype account and two others used by co-workers were shut off just minutes after that threat, effectively severing a main artery of support for ProxyPipe’s customers – many of whom were accustomed to communicating with ProxyPipe via Skype.
“CJ messaged me about five minutes before the DDoS started, saying he was going to disable my skype,” Coelho said. “The scary thing about when this happens is you don’t know if your Skype account has been hacked and under control of someone else or if it just got disabled.”
Once ProxyPipe’s Skype accounts were disabled, the company’s servers were hit with a massive, constantly changing DDoS attack that disrupted ProxyPipe’s service to its Minecraft server customers. Coelho said within a few days of the attack, many of ProxyPipe’s most lucrative Minecraft servers had moved over to servers run protected by ProTraf Solutions.
“In 2015, the ProTraf guys hit us offline tons, so a lot of our customers moved over to them,” Coelho said. “We told our customers that we knew [ProTraf] were the ones doing it, but some of the customers didn’t care and moved over to ProTraf anyway because they were losing money from being down.”
I found Coelho’s story fascinating because it eerily echoed the events leading up to my Sept. 2016 record 620 Gbps attack. I, too, was contacted via Skype by Sculti — on two occasions. The first was on July 7, 2015, when Sculti reached out apropos of nothing to brag about scanning the Internet for IoT devices running default usernames and passwords, saying he had uploaded some kind of program to more than a quarter-million systems that his scans found.
Here’s a snippet of that conversation:
July 7, 2015:
21:37 CJ: http://krebsonsecurity.com/2015/06/crooks-use-hacked-routers-to-aid-cyberheists/
21:37 CJ: vulnerable routers are a HUGE issue
21:37 CJ: a few months ago
21:37 CJ: I scanned the internet with a few sets of defualt logins
21:37 CJ: for telnet
21:37 CJ: and I was able to upload and execute a binary
21:38 CJ: on 250k devices
21:38 CJ: most of which were routers
21:38 Brian Krebs: o_0
The second time I heard from Sculti on Skype was Sept. 20, 2016 — the day of my 620 Gbps attack. Sculti was angry over a story I’d just published that mentioned his name, and he began rather saltily maligning the reputation of a source and friend who had helped me with that story.
Indignant on behalf of my source and annoyed at Sculti’s rant, I simply blocked his Skype account from communicating with mine and went on with my day. Just minutes after that conversation, however, my Skype account was flooded with thousands of contact requests from compromised or junk Skype accounts, making it virtually impossible to use the software for making phone calls or instant messaging.
Six hours after that Sept. 20 conversation with Sculti, the huge 620 Gbps DDoS attack commenced on this site.
WHO IS LELDDOS?
Coelho said he believes the main members of lelddos gang were Sculti and the owners of ProTraf. Asked why he was so sure of this, he recounted a large lelddos attack in early 2015 against ProxyPipe that coincided with a scam in which large tracts of Internet address space were temporarily stolen from the company.
According to ProxyPipe, a swath of Internet addresses was hijacked from the company by FastReturn, another DDoS mitigation firm that also specialized in protecting Minecraft servers from attacks. Dyn, a company that closely tracks which blocks of Internet addresses are assigned to which organizations, confirmed the timing of the Internet address hijack that Coelho described.
A few months after that attack, the owner of FastReturn — a young man from Dubai named Ammar Zuberi — went to work as a software developer for ProTraf. In the process, Zuberi transferred the majority of Internet addresses assigned to FastReturn over to ProTraf.
Zuberi told KrebsOnSecurity that he was not involved with lelddos, but he acknowledged that he did hijack ProxyPipe’s Internet address space before moving over to ProTraf.
“I was stupid and new to this entire thing and it was interesting to me how insecure the underlying ecosystem of the Internet was,” Zuberi said. “I just kept pushing the envelope to see how far I could get with that, I guess. I eventually realized though and got away from it, although that’s not really much of a justification.”
According to Zuberi, CJ Sculti Jr. was a member of lelddos, as were the two co-owners of ProTraf. This is interesting because not long after the September 2016 Mirai attack took this site offline, several sources who specialize in lurking on cybercrime forums shared information suggesting that the principal author of Bashlite/Qbot was a ProTraf employee: A 19-year-old computer whiz from Washington, Penn. named Josiah White.
White’s profile on LinkedIn lists him as an “enterprise DDoS mitigation expert” at ProTraf, but for years he was better known to those in the hacker community under the alias “LiteSpeed.”
LiteSpeed is the screen name White used on Hackforums[dot]net – a sprawling English-language marketplace where mostly young, low-skilled hackers can buy and sell cybercrime tools and stolen goods with ease. Until very recently, Hackforums also was the definitive place to buy and sell DDoS-for-hire services.
I contacted White to find out if the rumors about his authorship of Qbot/Bashlite were true. White acknowledged that he had written some of Qbot/Bashlite’s components — including the code segment that the malware uses to spread the infection to new machines. But White said he never intended for his code to be sold and traded online.
White claims that a onetime friend and Hackforums member nicknamed “Vyp0r” betrayed his trust and forced him to publish the code online by threatening to post White’s personal details online and to “swat” his home. Swatting is a potentially deadly hoax in which an attacker calls in a fake hostage situation or bomb threat at a residence or business with the intention of sending a team of heavily-armed police officers to the target’s address.
“Most of the stuff that I had wrote was for friends, but as I later realized, things on HF [Hackforums] tend to not remain private,” White wrote in an instant message to KrebsOnSecurity. “Eventually I learned they were reselling them in under-the-table deals, and so I just released everything to stop that. I made some mistakes when I was younger, and I realize that, but I’m trying to set my path straight and move on.”
WHO IS PARAS JHA?
White’s employer ProTraf Solutions has only one other employee – 20-year-old President Paras Jha, from Fanwood, NJ. On his LinkedIn profile, Jha states that “Paras is a passionate entrepreneur driven by the want to create.” The profile continues:
“Highly self-motivated, in 7th grade he began to teach himself to program in a variety of languages. Today, his skillset for software development includes C#, Java, Golang, C, C++, PHP, x86 ASM, not to mention web ‘browser languages’ such as Javascript and HTML/CSS.”
Jha’s LinkedIn page also shows that he has extensive experience running Minecraft servers, and that for several years he worked for Minetime, one of the most popular Minecraft servers at the time.
After first reading Jha’s LinkedIn resume, I was haunted by the nagging feeling that I’d seen this rather unique combination of computer language skills somewhere else online. Then it dawned on me: The mix of programming skills that Jha listed in his LinkedIn profile is remarkably similar to the skills listed on Hackforums by none other than Mirai’s author — Anna-Senpai.
Prior to leaking the Mirai source code on HackForums at the end of September 2016, the majority of Anna-Senpai’s posts on Hackforums were meant to taunt other hackers on the forum who were using Qbot to build DDoS attack armies.
The best example of this is a thread posted to Hackforums on July 10, 2016 titled “Killing All Telnets,” in which Anna-Senpai boldly warns forum members that the malicious code powering his botnet contains a particularly effective “bot killer” designed to remove Qbot from infected IoT devices and to prevent systems infected with his malware from ever being reinfected with Qbot again.
Anna-Senpai warns Qbot users that his new worm (relatively unknown by its name “Mirai” at the time) was capable of killing off IoT devices infected with Qbot.
Initially, forum members dismissed Anna’s threats as idle taunts, but as the thread continues for page after page we can see from other forum members that his bot killer is indeed having its intended effect. [Oddly enough, it’s very common for the authors of botnet code to include patching routines to protect their newly-enslaved bots from being compromised by other miscreants. Just like in any other market, there is a high degree of competition between cybercrooks who are constantly seeking to add more zombies to their DDoS armies, and they often resort to unorthodox tactics to knock out the competition. As we’ll see, this kind of internecine warfare is a major element in this story.]
“When the owner of this botnet wrote a July 2016 Hackforums thread named ‘Killing all Telnets’, he was right,” wrote Allison Nixon and Pierre Lamy, threat researchers for New York City-based security firm Flashpoint. “Our intelligence around that time reflected a massive shift away from the traditional gafgyt infection patterns and towards a different pattern that refused to properly execute on analysts’ machines. This new species choked out all the others.”
It wasn’t until after I’d spoken with Jha’s business partner Josiah White that I began re-reading every one of Anna-Senpai’s several dozen posts to Hackforums. The one that made Jha’s programming skills seem familiar came on July 12, 2016 — a week after posting his “Killing All Telnets” discussion thread — when Anna-Senpai contributed to a Hackforums thread started by a hacker group calling itself “Nightmare.”
Such groups or hacker cliques are common on Hackforums, and forum members can apply for membership by stating their skills and answering a few questions. Anna-Senpai posted his application for membership into this thread among dozens of others, describing himself thusly:
“Age: 18+
Location and Languages Spoken: English
Which of the aforementioned categories describe you the best?: Programmer / Development
What do you Specialize in? (List only): Systems programming / general low level languages (C + ASM)
Why should we choose you over other applicants?: I have 8 years of development under my belt, and I’m very familiar with programming in a variety of languages, including ASM, C, Go, Java, C#, and PHP. I like to use this knowledge for personal gain.”
The Hackforums post shows Jha and Anna-Senpai have the exact same programming skills. Additionally, according to an analysis of Mirai by security firm Incapsula, the malicious software used to control a botnet powered by Mirai is coded in Go (a.k.a. “Golang”), a somewhat esoteric programming language developed by Google in 2007 that saw a surge in popularity in 2016. Incapsula also said the malcode that gets installed on IoT bots is coded in C.
DREADIS[NOT]COOL
I began to dig deeper into Paras Jha’s history and footprint online, and discovered that his father in October 2013 registered a vanity domain for his son, parasjha.info. That site is no longer online, but a historic version of it cached by the indispensable Internet Archive includes a resume of Jha’s early work with various popular Minecraft servers. Here’s a autobiographical snippet from parasjha.info:
“My passion is to utilize my skills in programming and drawing to develop entertaining games and software for the online game ‘Minecraft. Someday, I plan to start my own enterprise focused on the gaming industry targeted towards game consoles and the mobile platform. To further my ideas and help the gaming community, I have released some of my code to open source projects on websites centered on public coding under the handle dreadiscool.”
A Google search for this rather unique username “dreadiscool” turns up accounts by the same name at dozens of forums dedicated to computer programming and Minecraft. In many of those accounts, the owner is clearly frustrated by incessant DDoS attacks targeting his Minecraft servers, and appears eager for advice on how best to counter the assaults.
From Dreadiscool’s various online postings, it seems clear that at some point Jha decided it might be more profitable and less frustrating to defend Minecraft servers from DDoS attacks, as opposed to trying to maintain the servers themselves.
“My experience in dealing with DDoS attacks led me to start a server hosting company focused on providing solutions to clients to mitigate such attacks,” Jha wrote on his vanity site.
Some of the more recent Dreadiscool posts date to November 2016, and many of those posts are lengthy explanations of highly technical subjects. The tone of voice in these posts is far more confident and even condescending than the Dreadiscool from years earlier, covering a range of subjects from programming to DDoS attacks.
Dreadiscool’s account on Spigot Minecraft forum since 2013 includes some interesting characters photoshopped into this image.
For example, Dreadiscool has been an active member of the Minecraft forum spigotmc.org since 2013. This user’s avatar (pictured above) on spigotmc.org is an altered image taken from the 1994 Quentin Tarantino cult hit “Pulp Fiction,” specifically from a scene in which the gangster characters Jules and Vincent are pointing their pistols in the same direction. However, the heads of both actors have been digitally altered to include someone else’s faces.
Pasted over the head of John Travolta’s character (left) is a real-life picture of Vyp0r — the Hackforums nickname of the guy that ProTraf’s Josiah White said threatened him into releasing the source code for Bashlite. On the shoulders of Samuel L. Jackson’s body is the face of Tucker Preston, co-founder of BackConnect Security — a competing DDoS mitigation provider that also has a history of hijacking Internet address ranges from other providers.
Pictured below and to the left of Travolta and Jackson’s characters — seated on the bed behind them — is “Yamada,” a Japanese animation (“anime”) character featured in the anime movie B Gata H Hei.
Turns out, there is a Dreadiscool user on MyAnimeList.net, a site where members proudly list the various anime films they have watched. Dreadiscool says B Gata H Kei is one of nine anime film series he has watched. Among the other eight? The anime series Mirai Nikki, from which the Mirai malware derives its name.
Dreadiscool’s Reddit profile also is very interesting, and most of the recent posts there relate to major DDoS attacks going on at the time, including a series of DDoS attacks on Rutgers University. More on Rutgers later.
A CHAT WITH ANNA-SENPAI
At around the same time as the record 620 Gbps attack on KrebsOnSecurity, French Web hosting giant OVH suffered an even larger attack — launched by the very same Mirai botnet used to attack this site. Although this fact has been widely reported in the news media, the reason for the OVH attack may not be so well known.
According to a tweet from OVH founder and chief technology officer Octave Klaba, the target of that massive attack also was a Minecraft server (although Klaba mistakenly called the target “mindcraft servers” in his tweet).
A tweet from OVH founder and CTO, stating the intended target of Sept. 2016 Mirai DDoS on his company.
Turns out, in the days following the attack on this site and on OVH, Anna-Sempai had trained his Mirai botnet on Coelho’s ProxyPipe, completely knocking his DDoS mitigation service offline for the better part of a day and causing problems for many popular Minecraft servers.
Unable to obtain more bandwidth and unwilling to sign an expensive annual contract with a third-party DDoS mitigation firm, Coelho turned to the only other option available to get out from under the attack: Filing abuse complaints with the Internet hosting firms that were responsible for providing connectivity to the control server used to orchestrate the activities of the Mirai botnet.
“We did it because we had no other options, and because all of our customers were offline,” Coelho said. “Even though no other DDoS mitigation company was able to defend against these attacks [from Mirai], we still needed to defend against it because our customers were starting to move to other providers that attracted fewer attacks.”
After scouring a list of Internet addresses tied to bots used in the attack, Coelho said he was able to trace the control server for the Mirai botnet back to a hosting provider in Ukraine. That company — BlazingFast[dot]io — has a reputation for hosting botnet control networks.
Getting no love from BlazingFast, Coelho said he escalated his complaint to Voxility, a company that was providing DDoS protection to BlazingFast at the time.
“Voxility acknowledged the presence of the control server, and said they null-routed [removed] it, but they didn’t,” Coelho said. “They basically lied to us and didn’t reply to any other emails.”
Undeterred, Coelho said he then emailed the ISP that was upstream of BlazingFast, but received little help from that company or the next ISP further upstream. Coelho said the fifth ISP upstream of BlazingFast, however — Internet provider Telia Sonera — confirmed his report, and promptly had the Mirai botnet’s control server killed.
As a result, many of the systems infected with Mirai could no longer connect to the botnet’s control servers, drastically reducing the botnet’s overall firepower.
“The action by Telia cut the size of the attacks launched by the botnet down to 80 Gbps,” well within the range of ProxyPipe’s in-house DDoS mitigation capabilities, Coelho said.
Incredibly, on Sept. 28, Anna-Senpai himself would reach out to Coelho via Skype. Coelho shared a copy of that chat conversation with KrebsOnSecurity. The log shows that Anna correctly guessed ProxyPipe was responsible for the abuse complaints that kneecapped Mirai. Anna-Senpai said he guessed ProxyPipe was responsible after reading a comment on a KrebsOnSecurity blog post from a reader who shared the same username as Coelho’s business partner.
In the following chat, Coelho is using the Skype nickname “katie.onis.”
[10:23:08 AM] live:anna-senpai: ^
[10:26:08 AM] katie.onis: hi there.
[10:26:52 AM] katie.onis: How can I help you?
[10:28:06 AM] live:anna-senpai: hi
[10:28:45 AM] live:anna-senpai: you know i had my suspicions, but this one was proof
http://imgur.com/E1yFJOp [this is a benign/safe link to a screenshot of some comments on KrebsOnSecurity.com]
[10:28:59 AM] live:anna-senpai: don’t get me wrong, im not even mad, it was pretty funny actually. nobody has ever done that to my c2 [Mirai “command and control” server]
[10:29:25 AM] live:anna-senpai: (goldmedal)
[10:29:29 AM] katie.onis: ah you’re mistaken, that’s not us.
[10:29:33 AM] katie.onis: but we know who it is
[10:29:42 AM] live:anna-senpai: eric / 9gigs
[10:29:47 AM] katie.onis: no, 9gigs is erik
[10:29:48 AM] katie.onis: not eric
[10:29:53 AM] katie.onis: different people
[10:30:09 AM] live:anna-senpai: oh?
[10:30:17 AM] katie.onis: yep
[10:30:39 AM] live:anna-senpai: is he someone related to you guys?
[10:30:44 AM] katie.onis: not related to us, we just know him
[10:30:50 AM] katie.onis: anyway, we’re not interested in any harm, we simply don’t want attacks against us.
[10:31:16 AM] live:anna-senpai: yeah i figured, i added you because i wanted to tip my hat if that was actually you lol
[10:31:24 AM] katie.onis: we didn’t make that dumb post
[10:31:26 AM] katie.onis: if that is what you are asking
[10:31:30 AM] katie.onis: but yes, we were involved in doing that.
[10:31:47 AM] live:anna-senpai: so you got it nulled, but some other eric is claiming credit for it?
[10:31:52 AM] katie.onis: seems so.
[10:31:52 AM] live:anna-senpai: eric with a c
[10:31:56 AM] live:anna-senpai: lol
[10:32:17 AM] live:anna-senpai: can’t say im surprised, tons of people take credit for things that they didn’t do if nobody else takes credit for
[10:32:24 AM] katie.onis: we’re not interested in taking credit
[10:32:30 AM] katie.onis: we just wanted the attacks to get smaller
NOTICE AND TAKEDOWN
One reason Anna-Senpai may have been enamored of Coelho’s approach to taking down Mirai is that Anna-Senpai had spent the previous month doing exactly the same thing to criminals running IoT botnets powered by Mirai’s top rival — Qbot.
A month before this chat between Coelho and Anna-Senpai, Anna is busy sending abuse complaints to various hosting firms, warning them that they are hosting huge IoT botnet control channels that needed to be shut down. This was clearly just part of an extended campaign by the Mirai botmasters to eliminate other IoT-based DDoS botnets that might compete for the same pool of vulnerable IoT devices. Anna confirmed this in his chat with Coelho:
[10:50:36 AM] live:anna-senpai: i have good killer so nobody else can assemble a large net
[10:50:53 AM] live:anna-senpai: i monitor the devices to see for any new threats
[10:51:33 AM] live:anna-senpai: and when i find any new host, i get them taken down
The ISPs or hosting providers that received abuse complaints from Anna-Senpai were all encouraged to reply to the email address [email protected] for questions and/or confirmation of the takedown. ISPs that declined to act promptly on Anna-Senpai’s Qbot email complaints soon found themselves on the receiving end of enormous DDoS attacks from Mirai.
Francisco Dias, owner of hosting provider Frantech, found out firsthand what it would cost to ignore one of Anna’s abuse reports. In mid-September 2016, Francisco accidentally got into an Internet fight with Anna-Senpai. The Mirai botmaster was using the nickname “jorgemichaels” at the time — and Jorgemichaels was talking trash on LowEndTalk.com, a discussion forum for vendors of low-costing hosting.
Specifically, Jorgemichaels takes Francisco to task publicly on the forum for ignoring one of his Qbot abuse complaints. Francisco tells Jorgemichaels to file a complaint with the police if it’s so urgent. Jorgemichaels tells Francisco to shut up, and when Francisco is silent for a while Jorgemichaels gloats that Francisco learned his place. Francisco explains his further silence on the thread by saying he’s busy supporting customers, to which Jorgemichaels replies, “Sounds like you just got a lot more customers to help. Don’t mess with the underworld francisco or it will harm your business.”
Shortly thereafter, Frantech is systematically knocked offline after being attacked by Mirai. Below is a fascinating snippet from a private conversation between Francisco and Anna-Senpai/Jorgemichaels, in which Francisco kills the reported Qbot control server to make Anna/Jorgemichaels call off the attack.
Using the nickname “jorgemichaels” on LowEndTalk, Anna-Senpai reaches out to Francisco Dias after Dias ignores Anna’s abuse complaint. Francisco agrees to kill the Qbot control server only after being walloped with Mirai.
Back to the chat between Anna-Senpai and Coelho at the end of Sept 2016. Anna-Senpai tells Coelho that the attacks against ProxyPipe aren’t personal; they’re just business. Anna says he has been renting out “net spots” — sizable chunks of his Mirai botnet — to other hackers who use them in their own attacks for pre-arranged periods of time.
By way of example, Anna brags that as he and Coelho are speaking, the owners of a large Minecraft server were paying him to launch a crippling DDoS against Hypixel, currently the world’s most popular Minecraft server. KrebsOnSecurity confirmed with Hypixel that they were indeed under a massive attack from Mirai between Sept. 27 and 30.
[12:24:00 PM] live:anna-senpai: right now i just have a script sitting there hitting them for 45s every 20 minutes
[12:24:09 PM] live:anna-senpai: enough to drop all players and make them rage
Coelho told KrebsOnSecurity that the on-again, off-again attack DDoS method that Anna described using against Hypixel was designed not just to cost Hypixel money. The purpose of that attack method, he said, was to aggravate and annoy Hypixel’s customers so much that they might take their business to a competing Minecraft server.
“It’s not just about taking it down, it’s about making everyone who is playing on that server crazy mad,” Coelho explained. “If you launch the attack every 20 minutes for a short period of time, you basically give the players just enough time to get back on the server and involved in another game before they’re disconnected again.”
Anna-Senpai told Coelho that paying customers also were the reason for the 620 Gbps attack on KrebsOnSecurity. Two weeks prior to that attack, I published the results of a months-long investigation revealing that “vDOS” — one of the largest and longest-running DDoS-for-hire services — had been hacked, exposing details about the services owners and customers.
The story noted that vDOS earned its proprietors more than $600,000 and was being run by two 18-year-old Israeli men who went by the hacker aliases “applej4ck” and “p1st0”. Hours after that piece ran, Israeli authorities arrested both men, and vDOS — which had been in operation for four years — was shuttered for good.
[10:47:42 AM] live:anna-senpai: i sell net spots, starting at $5k a week
[10:47:50 AM] live:anna-senpai: and one client was upset about applejack arrest
[10:48:01 AM] live:anna-senpai: so while i was gone he was sitting on them for hours with gre and ack
[10:48:14 AM] live:anna-senpai: when i came back i was like oh fuck
[10:48:16 AM] live:anna-senpai: and whitelisted the prefix
[10:48:24 AM] live:anna-senpai: but then krebs tweeted that akamai is kicking them off
[10:48:31 AM] live:anna-senpai: fuck me
[10:48:43 AM] live:anna-senpai: he was a cool guy too, i like his article
[SIDE NOTE: If true, it’s ironic that someone would hire Anna-Senpai to attack my site in retribution for the vDOS story. That’s because the firepower behind applej4ck’s vDOS service was generated in large part by a botnet of IoT systems infected with a Qbot variant — the very same botnet strain that Anna-Senpai and Mirai were busy killing and erasing from the Internet.]
Coelho told KrebsOnSecurity that if his side of the conversation reads like he was being too conciliatory to his assailant, that’s because he was wary of giving Anna a reason to launch another monster attack against ProxyPipe. After all, Coelho said, the Mirai attacks on ProxyPipe caused many customers to switch to other Minecraft servers, and Coelho estimates the attack cost the company between $400,000 and $500,000.
Nevertheless, about halfway through the chat Coelho gently confronts Anna on the consequences of his actions.
[10:54:17 AM] katie.onis: People have a genuine reason to be unhappy though about large attacks like this
[10:54:27 AM] live:anna-senpai: yeah
[10:54:32 AM] katie.onis: There’s really nothing anyone can do lol
[10:54:36 AM] live:anna-senpai:
[10:54:38 AM] katie.onis: And it does affect their lives
[10:55:10 AM] live:anna-senpai: well, i stopped caring about other people a long time ago
[10:55:18 AM] live:anna-senpai: my life experience has always been get fucked over or fuck someone else over
[10:55:52 AM] katie.onis: My experience with [ProxyPipe] thus far has been
[10:55:54 AM] katie.onis: Do nothing bad to anyone
[10:55:58 AM] katie.onis: And still get screwed over
[10:55:59 AM] katie.onis: Haha
The two even discussed anime after Anna-Senpai guessed that Coelho might be a fan of the genre. Anna-Senpai says he watched the anime series “Gate,” a reference to the above-mentioned B Gata H Hei that Dreadiscool included in the list of anime film series he’s watched. Anna also confirms that the name for his bot malware was derived from the anime series Mirai Nikki.
[5:25:12 PM] live:anna-senpai: i rewatched mirai nikki recently
[5:25:22 PM] live:anna-senpai: (it was the reason i named my bot mirai lol)
DREADISCOOL = ANNA = JHA?
Coelho said when Anna-Senpai first reached out to him on Skype, he had no clue about the hacker’s real-life identity. But a few weeks after that chat conversation with Anna-Senpai, Coelho’s business partner (the Eric referenced in the first chat segment above) said he noticed that some of the code in Mirai looked awfully similar to code that Dreadiscool had posted to his Github account.
“He started to come to the conclusion that maybe Anna was Paras,” Coelho said. “He gave me a lot of ideas, and after I did my own investigation I decided he was probably right.”
An incomplete “mindmap” I put together as I started to assemble research.
Coelho said he’s known Paras Jha for more than four years, having met him online when Jha was working for Minetime — which ProxyPipe was protecting from DDoS attacks at the time.
“We talked a lot back then and we used to program a lot of projects together,” Coelho said. “He’s really good at programming, but back then he wasn’t. He was a little bit behind, and I was teaching him most everything.”
According to Coelho, as Jha became more confident in his coding skills, he also grew more arrogant, belittling others online who didn’t have as firm a grasp on subjects such as programming and DDoS mitigation.
“He likes to be recognized for his knowledge, being praised and having other people recognize that,” Coelho said of Jha. “He brags too much, basically.”
Coelho said not long after Minetime was hit by a DDoS extortion attack in 2013, Paras joined Hackforums and fairly soon after stopped responding to his online messages.
“He just kind of dropped off the face of the earth entirely,” he said. “When he started going on Hackforums, I didn’t know him anymore. He became a different person.”
Coelho said he doesn’t believe his old friend wished him harm, and that Jha was probably pressured into attacking ProxyPipe.
“In my opinion he’s still a kid, in that he gets peer-pressured a lot,” Coelho said. “If he didn’t [launch the attack] not only would he feel super excluded, but these people wouldn’t be his friends anymore, they could out him and screw him over. I think he was pretty much in a really bad position with the people he got involved with.”
THE RUTGERS DDOS ATTACKS
On Dec. 16, security vendor Digital Shadows presented a Webinar that focused on clues about the Mirai author’s real life identity. According to their analysis, before the Mirai author was known as Anna-Senpai on Hackforums, he used the nickname “Ogmemes123123” (this also was the alias of the Skype username that contacted Coelho), and the email address [email protected] (recall this is the same email address Anna-Senpai used in his alerts to various hosting firms about the urgent need to take down Qbot control servers hosted on their networks).
Digital Shadows noted that the Mirai author appears to have used another nickname: “OG_Richard_Stallman,” a likely reference to the founder of the Free Software Foundation. The [email protected] account was used to register a Facebook account in the name of OG_Richard Stallman.
That Facebook account states that OG_Richard_Stallman began studying computer engineering at New Brunswick, NJ-based Rutgers University in 2015.
As it happens, Paras Jha is a student at Rutgers University. This is especially notable because Rutgers has been dealing with a series of DDoS attacks on its network since the fall semester of 2015 — more than a half dozen incidents in all. With each DDoS, the attacker would taunt the university in online posts and media interviews, encouraging the school to spend the money to purchase some kind of DDoS mitigation service.
Using the nicknames “og_richard_stallman,” “exfocus” and “ogexfocus,” the person who attacked Rutgers more than a half-dozen times took to Reddit and Twitter to claim credit for the attacks. Exfocus even created his own “Ask Me Anything” interview on Reddit to discuss the Rutgers attacks.
Exfocus also gave an interview to a New Jersey-based blogger, claiming he got paid $500 an hour to DDoS the university with as many as 170,000 bots. Here are a few snippets from that interview, in which he blames the attacks on a “client” who is renting his botnet:
“Are you for real? Why would you do an interview with us if you’re getting paid?
Normally I don’t show myself, but the entity paying me has something against the school. They want me to “make a splash”.
Why do you have a twitter account where you publically broadcast patronizing messages. Are you worried that this increases the risk of things getting back to you?
Public twitter is on clients request. The client hates the school for whatever reason. They told me to say generic things like that I hate the bus system and etc.
Have you ever attacked RU before?
During freshman registration the client requested it also – he didn’t want any publicity then though.
What are your plans for the future in terms of DDOSing and attacking the Rutgers cyber infrastructure?
When I stop getting paid – I’ll stop DDosing lol. I’m hoping that RU will sign on some ddos mitigation provider. I get paid extra if that happens.
At some point you said you were at the Livingston student center – outside of Sbarro. In this interview you said that you aren’t affiliated directly with Rutgers, did you lie then?
Yes”
An online search for the Gmail address used by Anna-Senpai and OG_Richard_Stallman turns up a Pastebin post from July 1, 2016, in which an anonymous Pastebin user creates a “dox” of OG_Richard_Stallman. Doxing refers to the act of publishing someone’s personal information online and/or connecting an online alias to a real life identity.
The dox said OG_Richard_Stallman was connected to an address and phone number of an individual living in Turkey. But this is almost certainly a fake dox intended to confuse cybercrime investigators. Here’s why:
A Google search shows that this same address and phone number showed up in another dox on Pastebin from almost three years earlier — June 2013 — intended to expose or confuse the identity of a Hackforums user known as LiteSpeed. Recall that LiteSpeed is the same alias that ProTraf’s Josiah White acknowledged using on Hackforums.
EXTORTION ATTEMPTS BY OG_RICHARD_STALLMAN
This OG_Richard_Stallman identity is connected to Anna-Senpai by another person we’ve heard from already: Francisco Dias, whose Frantech ISP was attacked by Anna-Senpai and Mirai in mid-September. Francisco told KrebsOnSecurity that in early August 2016 he began receiving extortion emails from a Gmail address associated with a OG_Richard_Stallman.
“This guy using the Richard Stallman name added me on Skype and basically said ‘I’m going to knock all of your [Internet addresses] offline until you pay me’,” Dias recalled. “He told me the up front cost to stop the attack was 10 bitcoins [~USD $5,000 at the time], and if I didn’t pay within four hours after the attack started the fee would double to 20 bitcoins.”
Dias said he didn’t pay the demand and eventually OG_Richard_Stallman called off the attack. But he said for a while the attacks were powerful enough to cause problems for Frantech’s Internet provider.
“He was hitting us so hard with Mirai that he was dropping large parts of Hurricane Electric and causing problems at their Los Angeles point of presence,” Dias said. “I basically threw everything behind [DDoS mitigation provider] Voxility, and eventually Stallman buggered off.”
The OG_Richard_Stallman identity also was tied to similar extortion attacks at the beginning of August against one hosting firm that had briefly been one of ProTraf’s customers in 2016. The company declined to be quoted on the record, but said it stopped doing business with Protraf in mid-2016 because they were unhappy with the quality of service.
The Internet provider said not long after that it received an extortion demand from the “OG_Richard_Stallman” character for $5,000 in Bitcoin to avoid a DDoS attack. One of the company’s researchers contacted the extortionist via the [email protected] address supplied in the email, but posing as someone who wished to hire some DDoS services.
OG_Richard_Stallman told the researcher that he could guarantee 350 Gbps of attack traffic and that the target would go down or the customer would receive a full refund. The price for the attack? USD $100 worth of Bitcoin for every five minutes of attack time.
My source at the hosting company said his employer declined to pay the demand, and subsequently got hit with an attack from Mirai that clocked in at more than 300 Gbps.
“Clearly, the attacker is very technical, as they attacked every single [Internet address] within the subnet, and after we brought up protection, he started attacking upstream router interfaces,” the source said on condition of anonymity.
Asked who they thought might be responsible for the attacks, my source said his employer immediately suspected ProTraf. That’s because the Mirai attack also targeted the Internet address for the company’s home page, but that Internet address was hidden by DDoS mitigation firm Cloudflare. However, ProTraf knew about the secret address from its previous work with the company, the source explained.
“We believe it’s Protraf’s staff or someone related to Protraf,” my source said.
A source at an Internet provider agreed to share information about an extortion demand his company received from OG_Richard_Stallman in August 2016. Here he is contacting the Stallman character directly and pretending to be someone interested in renting a botnet. Notice the source brazenly said he wanted to DDoS ProTraf.
DDOS CONFESSIONS
After months of gathering information about the apparent authors of Mirai, I heard from Ammar Zuberi, once a co-worker of ProTraf President Paras Jha.
Zuberi told KrebsOnSecurity that Jha admitted he was responsible for both Mirai and the Rutgers DDoS attacks. Zuberi said when he visited Jha at his Rutgers University dorm in October 2015, Paras bragged to him about launching the DDoS attacks against Rutgers.
“He was laughing and bragging about how he was going to get a security guy at the school fired, and how they raised school fees because of him,” Zuberi recalled. “He didn’t really say why he did it, but I think he was just sort of experimenting with how far he could go with these attacks.”
Zuberi said he didn’t realize how far Jha had gone with his DDoS attacks until he confronted him about it late last year. Zuberi said he was on his way to see his grandmother in Arizona at the end of November 2016, and he had a layover in New York. So he contacted Jha and arranged to spend the night at Jha’s home in Fanwood, New Jersey.
As I noted in Spreading the DDoS Disease and Selling the Cure, Anna-Senpai leaked the Mirai code on a domain name (santasbigcandycane[dot]cx) that was registered via Namecentral, an extremely obscure domain name registrar which had previously been used to register fewer than three dozen other domains over a three-year period.
According to Zuberi, only five people knew about the existence of Namecentral: himself, CJ Sculti, Paras Jha, Josiah White and Namecentral’s owner Jesse Wu (19-year-old Wu features prominently in the DDoS Disease story linked in the previous paragraph).
“When I saw that the Mirai code had been leaked on that domain at Namecentral, I straight up asked Paras at that point, ‘Was this you?,’ and he smiled and said yep,” Zuberi recalled. “Then he told me he’d recently heard from an FBI agent who was investigating Mirai, and he showed me some text messages between him and the agent. He was pretty proud of himself, and was bragging that he led the FBI on a wild goose chase.”
Zuberi said he hasn’t been in contact with Jha since visiting his home in November. Zuberi said he believes Jha wrote most of the code that Mirai uses to control the individual bot-infected IoT devices, since it was written in Golang and Jha’s partner White didn’t code well in this language. Zuberi said he thought White’s role was mainly in developing the spreading code used to infect new IoT devices with Mirai, since that was written in C — a language White excelled at.
In the time since most of the above occurred, the Internet address ranges previously occupied by ProTraf have been withdrawn. ProxyPipe’s Coelho said it could be that the ProTraf simply ran out of money.
ProTraf’s Josiah White explained the disappearance of ProTraf’s Internet space as part of an effort to reboot the company.
“We [are] in the process of restructuring and refocusing what we are doing,” White told KrebsOnSecurity.
Jha did not respond to requests for comment.
Rutgers University did not respond to requests for comment.
The FBI officials could not be immediately reached for comment.
A copy of the entire chat between Anna-Senpai and ProxyPipe’s Coelho is available here.
from Amber Scott Technology News https://krebsonsecurity.com/2017/01/who-is-anna-senpai-the-mirai-worm-author/
0 notes
Text
Who is Anna-Senpai, the Mirai Worm Author?
On September 22, 2016, this site was forced offline for nearly four days after it was hit with “Mirai,” a malware strain that enslaves poorly secured Internet of Things (IoT) devices like wireless routers and security cameras into a botnet for use in large cyberattacks. Roughly a week after that assault, the individual(s) who launched that attack — using the name “Anna Senpai” — released the source code for Mirai, spawning dozens of copycat attack armies online.
After months of digging, KrebsOnSecurity is now confident to have uncovered Anna Senpai’s real-life identity, and the identity of at least one co-conspirator who helped to write and modify the malware.
Mirai co-author Anna-Senpai leaked the source code for Mirai on Sept. 30, 2016.
Before we go further, a few disclosures are probably in order. First, this is easily the longest story I’ve ever written on this blog. It’s lengthy because I wanted to walk readers through my process of discovery, which has taken months to unravel. The details help in understanding the financial motivations behind Mirai and the botnet wars that preceded it. Also, I realize there are a great many names to keep track of as you read this post, so I’ve included a glossary.
The story you’re reading now is the result of hundreds of hours of research. At times, I was desperately seeking the missing link between seemingly unrelated people and events; sometimes I was inundated with huge amounts of information — much of it intentionally false or misleading — and left to search for kernels of truth hidden among the dross. If you’ve ever wondered why it seems that so few Internet criminals are brought to justice, I can tell you that the sheer amount of persistence and investigative resources required to piece together who’s done what to whom (and why) in the online era is tremendous.
As noted in previous KrebsOnSecurity articles, botnets like Mirai are used to knock individuals, businesses, governmental agencies, and non-profits offline on a daily basis. These so-called “distributed denial-of-service (DDoS) attacks are digital sieges in which an attacker causes thousands of hacked systems to hit a target with so much junk traffic that it falls over and remains unreachable by legitimate visitors. While DDoS attacks typically target a single Web site or Internet host, they often result in widespread collateral Internet disruption.
A great deal of DDoS activity on the Internet originates from so-called ‘booter/stresser’ services, which are essentially DDoS-for-hire services which allow even unsophisticated users to launch high-impact attacks. And as we will see, the incessant competition for profits in the blatantly illegal DDoS-for-hire industry can lead those involved down some very strange paths, indeed.
THE FIRST CLUES
The first clues to Anna Senpai’s identity didn’t become clear until I understood that Mirai was just the latest incarnation of an IoT botnet family that has been in development and relatively broad use for nearly three years.
Earlier this summer, my site was hit with several huge attacks from a collection of hacked IoT systems compromised by a family of botnet code that served as a precursor to Mirai. The malware went by several names, including “Bashlite,” “Gafgyt,” “Qbot,” “Remaiten,” and “Torlus.”
All of these related IoT botnet varieties infect new systems in a fashion similar to other well-known Internet worms — propagating from one infected host to another. And like those earlier Internet worms, sometimes the Internet scanning these systems perform to identify other candidates for inclusion into the botnet is so aggressive that it constitutes an unintended DDoS on the very home routers, Web cameras and DVRs that the bot code is trying to subvert and recruit into the botnet. This kind of self-defeating behavior will be familiar to those who recall the original Morris Worm, NIMDA, CODE RED, Welchia, Blaster and SQL Slammer disruptions of yesteryear.
Infected IoT devices constantly scan the Web for other IoT things to compromise, wriggling into devices that are protected by little more than insecure factory-default settings and passwords. The infected devices are then forced to participate in DDoS attacks (ironically, many of the devices most commonly infected by Mirai and similar IoT worms are security cameras).
Mirai’s ancestors had so many names because each name corresponded to a variant that included new improvements over time. In 2014, a group of Internet hooligans operating under the banner “lelddos” very publicly used the code to launch large, sustained attacks that knocked many Web sites offline.
The most frequent target of the lelddos gang were Web servers used to host Minecraft, a wildly popular computer game sold by Microsoft that can be played from any device and on any Internet connection.
The object of Minecraft is to run around and build stuff, block by large pixelated block. That may sound simplistic and boring, but an impressive number of people positively adore this game – particularly pre-teen males. Microsoft has sold more than a 100 million copies of Minecraft, and at any given time there are over a million people playing it online. Players can build their own worlds, or visit a myriad other blocky realms by logging on to their favorite Minecraft server to play with friends.
Image: Minecraft.net
A large, successful Minecraft server with more than a thousand players logging on each day can easily earn the server’s owners upwards of $50,000 per month, mainly from players renting space on the server to build their Minecraft worlds, and purchasing in-game items and special abilities.
Perhaps unsurprisingly, the top-earning Minecraft servers eventually attracted the attention of ne’er-do-wells and extortionists like the lelddos gang. Lelddos would launch a huge DDoS attack against a Minecraft server, knowing that the targeted Minecraft server owner was likely losing thousands of dollars for each day his gaming channel remained offline.
Adding urgency to the ordeal, many of the targeted server’s loyal customers would soon find other Minecraft servers to patronize if they could not get their Minecraft fix at the usual online spot.
Robert Coelho is vice president of ProxyPipe, Inc., a San Francisco company that specializes in protecting Minecraft servers from attacks.
“The Minecraft industry is so competitive,” Coelho said. “If you’re a player, and your favorite Minecraft server gets knocked offline, you can switch to another server. But for the server operators, it’s all about maximizing the number of players and running a large, powerful server. The more players you can hold on the server, the more money you make. But if you go down, you start to lose Minecraft players very fast — maybe for good.”
In June 2014, ProxyPipe was hit with a 300 gigabit per second DDoS attack launched by lelddos, which had a penchant for publicly taunting its victims on Twitter just as it began launching DDoS assaults at the taunted.
The hacker group “lelddos” tweeted at its victims before launching huge DDoS attacks against them.
At the time, ProxyPipe was buying DDoS protection from Reston, Va. -based security giant Verisign. In a quarterly report published in 2014, Verisign called the attack the largest it had ever seen, although it didn’t name ProxyPipe in the report – referring to it only as a customer in the media and entertainment business.
Verisign said the 2014 attack was launched by a botnet of more than 100,000 hacked routers sold by a company called SuperMicro. Days before the huge attack on ProxyPipe, a security researcher published information about a vulnerability in the SuperMicro devices that could allow them to be remotely hacked and commandeered for these sorts of attacks.
THE CENTRALITY OF PROTRAF
Coelho recalled that in mid-2015 his company’s Minecraft customers began coming under attack from a botnet made up of IoT devices infected with Qbot. He said the attacks were directly preceded by a threat made by a then-17-year-old Christopher “CJ” Sculti, Jr., the owner and sole employee of a competing DDoS protection company called Datawagon.
Datawagon also courted Minecraft servers as customers, and its servers were hosted on Internet space claimed by yet another Minecraft-focused DDoS protection provider — ProTraf Solutions.
Christopher “CJ” Sculti, Jr.
According to Coelho, ProTraf was trying to woo many of his biggest Minecraft server customers away from ProxyPipe. Coelho said in mid-2015, Sculti reached out to him on Skype and said he was getting ready to disable Coelho’s Skype account. At the time, an exploit for a software weakness in Skype was being traded online, and this exploit could be used to remotely and instantaneously disable any Skype account.
Sure enough, Coelho recalled, his Skype account and two others used by co-workers were shut off just minutes after that threat, effectively severing a main artery of support for ProxyPipe’s customers – many of whom were accustomed to communicating with ProxyPipe via Skype.
“CJ messaged me about five minutes before the DDoS started, saying he was going to disable my skype,” Coelho said. “The scary thing about when this happens is you don’t know if your Skype account has been hacked and under control of someone else or if it just got disabled.”
Once ProxyPipe’s Skype accounts were disabled, the company’s servers were hit with a massive, constantly changing DDoS attack that disrupted ProxyPipe’s service to its Minecraft server customers. Coelho said within a few days of the attack, many of ProxyPipe’s most lucrative Minecraft servers had moved over to servers run protected by ProTraf Solutions.
“In 2015, the ProTraf guys hit us offline tons, so a lot of our customers moved over to them,” Coelho said. “We told our customers that we knew [ProTraf] were the ones doing it, but some of the customers didn’t care and moved over to ProTraf anyway because they were losing money from being down.”
I found Coelho’s story fascinating because it eerily echoed the events leading up to my Sept. 2016 record 620 Gbps attack. I, too, was contacted via Skype by Sculti — on two occasions. The first was on July 7, 2015, when Sculti reached out apropos of nothing to brag about scanning the Internet for IoT devices running default usernames and passwords, saying he had uploaded some kind of program to more than a quarter-million systems that his scans found.
Here’s a snippet of that conversation:
July 7, 2015:
21:37 CJ: http://krebsonsecurity.com/2015/06/crooks-use-hacked-routers-to-aid-cyberheists/
21:37 CJ: vulnerable routers are a HUGE issue
21:37 CJ: a few months ago
21:37 CJ: I scanned the internet with a few sets of defualt logins
21:37 CJ: for telnet
21:37 CJ: and I was able to upload and execute a binary
21:38 CJ: on 250k devices
21:38 CJ: most of which were routers
21:38 Brian Krebs: o_0
The second time I heard from Sculti on Skype was Sept. 20, 2016 — the day of my 620 Gbps attack. Sculti was angry over a story I’d just published that mentioned his name, and he began rather saltily maligning the reputation of a source and friend who had helped me with that story.
Indignant on behalf of my source and annoyed at Sculti’s rant, I simply blocked his Skype account from communicating with mine and went on with my day. Just minutes after that conversation, however, my Skype account was flooded with thousands of contact requests from compromised or junk Skype accounts, making it virtually impossible to use the software for making phone calls or instant messaging.
Six hours after that Sept. 20 conversation with Sculti, the huge 620 Gbps DDoS attack commenced on this site.
WHO IS LELDDOS?
Coelho said he believes the main members of lelddos gang were Sculti and the owners of ProTraf. Asked why he was so sure of this, he recounted a large lelddos attack in early 2015 against ProxyPipe that coincided with a scam in which large tracts of Internet address space were temporarily stolen from the company.
According to ProxyPipe, a swath of Internet addresses was hijacked from the company by FastReturn, another DDoS mitigation firm that also specialized in protecting Minecraft servers from attacks. Dyn, a company that closely tracks which blocks of Internet addresses are assigned to which organizations, confirmed the timing of the Internet address hijack that Coelho described.
A few months after that attack, the owner of FastReturn — a young man from Dubai named Ammar Zuberi — went to work as a software developer for ProTraf. In the process, Zuberi transferred the majority of Internet addresses assigned to FastReturn over to ProTraf.
Zuberi told KrebsOnSecurity that he was not involved with lelddos, but he acknowledged that he did hijack ProxyPipe’s Internet address space before moving over to ProTraf.
“I was stupid and new to this entire thing and it was interesting to me how insecure the underlying ecosystem of the Internet was,” Zuberi said. “I just kept pushing the envelope to see how far I could get with that, I guess. I eventually realized though and got away from it, although that’s not really much of a justification.”
According to Zuberi, CJ Sculti Jr. was a member of lelddos, as were the two co-owners of ProTraf. This is interesting because not long after the September 2016 Mirai attack took this site offline, several sources who specialize in lurking on cybercrime forums shared information suggesting that the principal author of Bashlite/Qbot was a ProTraf employee: A 19-year-old computer whiz from Washington, Penn. named Josiah White.
White’s profile on LinkedIn lists him as an “enterprise DDoS mitigation expert” at ProTraf, but for years he was better known to those in the hacker community under the alias “LiteSpeed.”
LiteSpeed is the screen name White used on Hackforums[dot]net – a sprawling English-language marketplace where mostly young, low-skilled hackers can buy and sell cybercrime tools and stolen goods with ease. Until very recently, Hackforums also was the definitive place to buy and sell DDoS-for-hire services.
I contacted White to find out if the rumors about his authorship of Qbot/Bashlite were true. White acknowledged that he had written some of Qbot/Bashlite’s components — including the code segment that the malware uses to spread the infection to new machines. But White said he never intended for his code to be sold and traded online.
White claims that a onetime friend and Hackforums member nicknamed “Vyp0r” betrayed his trust and forced him to publish the code online by threatening to post White’s personal details online and to “swat” his home. Swatting is a potentially deadly hoax in which an attacker calls in a fake hostage situation or bomb threat at a residence or business with the intention of sending a team of heavily-armed police officers to the target’s address.
“Most of the stuff that I had wrote was for friends, but as I later realized, things on HF [Hackforums] tend to not remain private,” White wrote in an instant message to KrebsOnSecurity. “Eventually I learned they were reselling them in under-the-table deals, and so I just released everything to stop that. I made some mistakes when I was younger, and I realize that, but I’m trying to set my path straight and move on.”
WHO IS PARAS JHA?
White’s employer ProTraf Solutions has only one other employee – 20-year-old President Paras Jha, from Fanwood, NJ. On his LinkedIn profile, Jha states that “Paras is a passionate entrepreneur driven by the want to create.” The profile continues:
“Highly self-motivated, in 7th grade he began to teach himself to program in a variety of languages. Today, his skillset for software development includes C#, Java, Golang, C, C++, PHP, x86 ASM, not to mention web ‘browser languages’ such as Javascript and HTML/CSS.”
Jha’s LinkedIn page also shows that he has extensive experience running Minecraft servers, and that for several years he worked for Minetime, one of the most popular Minecraft servers at the time.
After first reading Jha’s LinkedIn resume, I was haunted by the nagging feeling that I’d seen this rather unique combination of computer language skills somewhere else online. Then it dawned on me: The mix of programming skills that Jha listed in his LinkedIn profile is remarkably similar to the skills listed on Hackforums by none other than Mirai’s author — Anna-Senpai.
Prior to leaking the Mirai source code on HackForums at the end of September 2016, the majority of Anna-Senpai’s posts on Hackforums were meant to taunt other hackers on the forum who were using Qbot to build DDoS attack armies.
The best example of this is a thread posted to Hackforums on July 10, 2016 titled “Killing All Telnets,” in which Anna-Senpai boldly warns forum members that the malicious code powering his botnet contains a particularly effective “bot killer” designed to remove Qbot from infected IoT devices and to prevent systems infected with his malware from ever being reinfected with Qbot again.
Anna-Senpai warns Qbot users that his new worm (relatively unknown by its name “Mirai” at the time) was capable of killing off IoT devices infected with Qbot.
Initially, forum members dismissed Anna’s threats as idle taunts, but as the thread continues for page after page we can see from other forum members that his bot killer is indeed having its intended effect. [Oddly enough, it’s very common for the authors of botnet code to include patching routines to protect their newly-enslaved bots from being compromised by other miscreants. Just like in any other market, there is a high degree of competition between cybercrooks who are constantly seeking to add more zombies to their DDoS armies, and they often resort to unorthodox tactics to knock out the competition. As we’ll see, this kind of internecine warfare is a major element in this story.]
“When the owner of this botnet wrote a July 2016 Hackforums thread named ‘Killing all Telnets’, he was right,” wrote Allison Nixon and Pierre Lamy, threat researchers for New York City-based security firm Flashpoint. “Our intelligence around that time reflected a massive shift away from the traditional gafgyt infection patterns and towards a different pattern that refused to properly execute on analysts’ machines. This new species choked out all the others.”
It wasn’t until after I’d spoken with Jha’s business partner Josiah White that I began re-reading every one of Anna-Senpai’s several dozen posts to Hackforums. The one that made Jha’s programming skills seem familiar came on July 12, 2016 — a week after posting his “Killing All Telnets” discussion thread — when Anna-Senpai contributed to a Hackforums thread started by a hacker group calling itself “Nightmare.���
Such groups or hacker cliques are common on Hackforums, and forum members can apply for membership by stating their skills and answering a few questions. Anna-Senpai posted his application for membership into this thread among dozens of others, describing himself thusly:
“Age: 18+
Location and Languages Spoken: English
Which of the aforementioned categories describe you the best?: Programmer / Development
What do you Specialize in? (List only): Systems programming / general low level languages (C + ASM)
Why should we choose you over other applicants?: I have 8 years of development under my belt, and I’m very familiar with programming in a variety of languages, including ASM, C, Go, Java, C#, and PHP. I like to use this knowledge for personal gain.”
The Hackforums post shows Jha and Anna-Senpai have the exact same programming skills. Additionally, according to an analysis of Mirai by security firm Incapsula, the malicious software used to control a botnet powered by Mirai is coded in Go (a.k.a. “Golang”), a somewhat esoteric programming language developed by Google in 2007 that saw a surge in popularity in 2016. Incapsula also said the malcode that gets installed on IoT bots is coded in C.
DREADIS[NOT]COOL
I began to dig deeper into Paras Jha’s history and footprint online, and discovered that his father in October 2013 registered a vanity domain for his son, parasjha.info. That site is no longer online, but a historic version of it cached by the indispensable Internet Archive includes a resume of Jha’s early work with various popular Minecraft servers. Here’s a autobiographical snippet from parasjha.info:
“My passion is to utilize my skills in programming and drawing to develop entertaining games and software for the online game ‘Minecraft. Someday, I plan to start my own enterprise focused on the gaming industry targeted towards game consoles and the mobile platform. To further my ideas and help the gaming community, I have released some of my code to open source projects on websites centered on public coding under the handle dreadiscool.”
A Google search for this rather unique username “dreadiscool” turns up accounts by the same name at dozens of forums dedicated to computer programming and Minecraft. In many of those accounts, the owner is clearly frustrated by incessant DDoS attacks targeting his Minecraft servers, and appears eager for advice on how best to counter the assaults.
From Dreadiscool’s various online postings, it seems clear that at some point Jha decided it might be more profitable and less frustrating to defend Minecraft servers from DDoS attacks, as opposed to trying to maintain the servers themselves.
“My experience in dealing with DDoS attacks led me to start a server hosting company focused on providing solutions to clients to mitigate such attacks,” Jha wrote on his vanity site.
Some of the more recent Dreadiscool posts date to November 2016, and many of those posts are lengthy explanations of highly technical subjects. The tone of voice in these posts is far more confident and even condescending than the Dreadiscool from years earlier, covering a range of subjects from programming to DDoS attacks.
Dreadiscool’s account on Spigot Minecraft forum since 2013 includes some interesting characters photoshopped into this image.
For example, Dreadiscool has been an active member of the Minecraft forum spigotmc.org since 2013. This user’s avatar (pictured above) on spigotmc.org is an altered image taken from the 1994 Quentin Tarantino cult hit “Pulp Fiction,” specifically from a scene in which the gangster characters Jules and Vincent are pointing their pistols in the same direction. However, the heads of both actors have been digitally altered to include someone else’s faces.
Pasted over the head of John Travolta’s character (left) is a real-life picture of Vyp0r — the Hackforums nickname of the guy that ProTraf’s Josiah White said threatened him into releasing the source code for Bashlite. On the shoulders of Samuel L. Jackson’s body is the face of Tucker Preston, co-founder of BackConnect Security — a competing DDoS mitigation provider that also has a history of hijacking Internet address ranges from other providers.
Pictured below and to the left of Travolta and Jackson’s characters — seated on the bed behind them — is “Yamada,” a Japanese animation (“anime”) character featured in the anime movie B Gata H Hei.
Turns out, there is a Dreadiscool user on MyAnimeList.net, a site where members proudly list the various anime films they have watched. Dreadiscool says B Gata H Kei is one of nine anime film series he has watched. Among the other eight? The anime series Mirai Nikki, from which the Mirai malware derives its name.
Dreadiscool’s Reddit profile also is very interesting, and most of the recent posts there relate to major DDoS attacks going on at the time, including a series of DDoS attacks on Rutgers University. More on Rutgers later.
A CHAT WITH ANNA-SENPAI
At around the same time as the record 620 Gbps attack on KrebsOnSecurity, French Web hosting giant OVH suffered an even larger attack — launched by the very same Mirai botnet used to attack this site. Although this fact has been widely reported in the news media, the reason for the OVH attack may not be so well known.
According to a tweet from OVH founder and chief technology officer Octave Klaba, the target of that massive attack also was a Minecraft server (although Klaba mistakenly called the target “mindcraft servers” in his tweet).
A tweet from OVH founder and CTO, stating the intended target of Sept. 2016 Mirai DDoS on his company.
Turns out, in the days following the attack on this site and on OVH, Anna-Sempai had trained his Mirai botnet on Coelho’s ProxyPipe, completely knocking his DDoS mitigation service offline for the better part of a day and causing problems for many popular Minecraft servers.
Unable to obtain more bandwidth and unwilling to sign an expensive annual contract with a third-party DDoS mitigation firm, Coelho turned to the only other option available to get out from under the attack: Filing abuse complaints with the Internet hosting firms that were responsible for providing connectivity to the control server used to orchestrate the activities of the Mirai botnet.
“We did it because we had no other options, and because all of our customers were offline,” Coelho said. “Even though no other DDoS mitigation company was able to defend against these attacks [from Mirai], we still needed to defend against it because our customers were starting to move to other providers that attracted fewer attacks.”
After scouring a list of Internet addresses tied to bots used in the attack, Coelho said he was able to trace the control server for the Mirai botnet back to a hosting provider in Ukraine. That company — BlazingFast[dot]io — has a reputation for hosting botnet control networks.
Getting no love from BlazingFast, Coelho said he escalated his complaint to Voxility, a company that was providing DDoS protection to BlazingFast at the time.
“Voxility acknowledged the presence of the control server, and said they null-routed [removed] it, but they didn’t,” Coelho said. “They basically lied to us and didn’t reply to any other emails.”
Undeterred, Coelho said he then emailed the ISP that was upstream of BlazingFast, but received little help from that company or the next ISP further upstream. Coelho said the fifth ISP upstream of BlazingFast, however — Internet provider Telia Sonera — confirmed his report, and promptly had the Mirai botnet’s control server killed.
As a result, many of the systems infected with Mirai could no longer connect to the botnet’s control servers, drastically reducing the botnet’s overall firepower.
“The action by Telia cut the size of the attacks launched by the botnet down to 80 Gbps,” well within the range of ProxyPipe’s in-house DDoS mitigation capabilities, Coelho said.
Incredibly, on Sept. 28, Anna-Senpai himself would reach out to Coelho via Skype. Coelho shared a copy of that chat conversation with KrebsOnSecurity. The log shows that Anna correctly guessed ProxyPipe was responsible for the abuse complaints that kneecapped Mirai. Anna-Senpai said he guessed ProxyPipe was responsible after reading a comment on a KrebsOnSecurity blog post from a reader who shared the same username as Coelho’s business partner.
In the following chat, Coelho is using the Skype nickname “katie.onis.”
[10:23:08 AM] live:anna-senpai: ^
[10:26:08 AM] katie.onis: hi there.
[10:26:52 AM] katie.onis: How can I help you?
[10:28:06 AM] live:anna-senpai: hi
[10:28:45 AM] live:anna-senpai: you know i had my suspicions, but this one was proof
http://imgur.com/E1yFJOp [this is a benign/safe link to a screenshot of some comments on KrebsOnSecurity.com]
[10:28:59 AM] live:anna-senpai: don’t get me wrong, im not even mad, it was pretty funny actually. nobody has ever done that to my c2 [Mirai “command and control” server]
[10:29:25 AM] live:anna-senpai: (goldmedal)
[10:29:29 AM] katie.onis: ah you’re mistaken, that’s not us.
[10:29:33 AM] katie.onis: but we know who it is
[10:29:42 AM] live:anna-senpai: eric / 9gigs
[10:29:47 AM] katie.onis: no, 9gigs is erik
[10:29:48 AM] katie.onis: not eric
[10:29:53 AM] katie.onis: different people
[10:30:09 AM] live:anna-senpai: oh?
[10:30:17 AM] katie.onis: yep
[10:30:39 AM] live:anna-senpai: is he someone related to you guys?
[10:30:44 AM] katie.onis: not related to us, we just know him
[10:30:50 AM] katie.onis: anyway, we’re not interested in any harm, we simply don’t want attacks against us.
[10:31:16 AM] live:anna-senpai: yeah i figured, i added you because i wanted to tip my hat if that was actually you lol
[10:31:24 AM] katie.onis: we didn’t make that dumb post
[10:31:26 AM] katie.onis: if that is what you are asking
[10:31:30 AM] katie.onis: but yes, we were involved in doing that.
[10:31:47 AM] live:anna-senpai: so you got it nulled, but some other eric is claiming credit for it?
[10:31:52 AM] katie.onis: seems so.
[10:31:52 AM] live:anna-senpai: eric with a c
[10:31:56 AM] live:anna-senpai: lol
[10:32:17 AM] live:anna-senpai: can’t say im surprised, tons of people take credit for things that they didn’t do if nobody else takes credit for
[10:32:24 AM] katie.onis: we’re not interested in taking credit
[10:32:30 AM] katie.onis: we just wanted the attacks to get smaller
NOTICE AND TAKEDOWN
One reason Anna-Senpai may have been enamored of Coelho’s approach to taking down Mirai is that Anna-Senpai had spent the previous month doing exactly the same thing to criminals running IoT botnets powered by Mirai’s top rival — Qbot.
A month before this chat between Coelho and Anna-Senpai, Anna is busy sending abuse complaints to various hosting firms, warning them that they are hosting huge IoT botnet control channels that needed to be shut down. This was clearly just part of an extended campaign by the Mirai botmasters to eliminate other IoT-based DDoS botnets that might compete for the same pool of vulnerable IoT devices. Anna confirmed this in his chat with Coelho:
[10:50:36 AM] live:anna-senpai: i have good killer so nobody else can assemble a large net
[10:50:53 AM] live:anna-senpai: i monitor the devices to see for any new threats
[10:51:33 AM] live:anna-senpai: and when i find any new host, i get them taken down
The ISPs or hosting providers that received abuse complaints from Anna-Senpai were all encouraged to reply to the email address [email protected] for questions and/or confirmation of the takedown. ISPs that declined to act promptly on Anna-Senpai’s Qbot email complaints soon found themselves on the receiving end of enormous DDoS attacks from Mirai.
Francisco Dias, owner of hosting provider Frantech, found out firsthand what it would cost to ignore one of Anna’s abuse reports. In mid-September 2016, Francisco accidentally got into an Internet fight with Anna-Senpai. The Mirai botmaster was using the nickname “jorgemichaels” at the time — and Jorgemichaels was talking trash on LowEndTalk.com, a discussion forum for vendors of low-costing hosting.
Specifically, Jorgemichaels takes Francisco to task publicly on the forum for ignoring one of his Qbot abuse complaints. Francisco tells Jorgemichaels to file a complaint with the police if it’s so urgent. Jorgemichaels tells Francisco to shut up, and when Francisco is silent for a while Jorgemichaels gloats that Francisco learned his place. Francisco explains his further silence on the thread by saying he’s busy supporting customers, to which Jorgemichaels replies, “Sounds like you just got a lot more customers to help. Don’t mess with the underworld francisco or it will harm your business.”
Shortly thereafter, Frantech is systematically knocked offline after being attacked by Mirai. Below is a fascinating snippet from a private conversation between Francisco and Anna-Senpai/Jorgemichaels, in which Francisco kills the reported Qbot control server to make Anna/Jorgemichaels call off the attack.
Using the nickname “jorgemichaels” on LowEndTalk, Anna-Senpai reaches out to Francisco Dias after Dias ignores Anna’s abuse complaint. Francisco agrees to kill the Qbot control server only after being walloped with Mirai.
Back to the chat between Anna-Senpai and Coelho at the end of Sept 2016. Anna-Senpai tells Coelho that the attacks against ProxyPipe aren’t personal; they’re just business. Anna says he has been renting out “net spots” — sizable chunks of his Mirai botnet — to other hackers who use them in their own attacks for pre-arranged periods of time.
By way of example, Anna brags that as he and Coelho are speaking, the owners of a large Minecraft server were paying him to launch a crippling DDoS against Hypixel, currently the world’s most popular Minecraft server. KrebsOnSecurity confirmed with Hypixel that they were indeed under a massive attack from Mirai between Sept. 27 and 30.
[12:24:00 PM] live:anna-senpai: right now i just have a script sitting there hitting them for 45s every 20 minutes
[12:24:09 PM] live:anna-senpai: enough to drop all players and make them rage
Coelho told KrebsOnSecurity that the on-again, off-again attack DDoS method that Anna described using against Hypixel was designed not just to cost Hypixel money. The purpose of that attack method, he said, was to aggravate and annoy Hypixel’s customers so much that they might take their business to a competing Minecraft server.
“It’s not just about taking it down, it’s about making everyone who is playing on that server crazy mad,” Coelho explained. “If you launch the attack every 20 minutes for a short period of time, you basically give the players just enough time to get back on the server and involved in another game before they’re disconnected again.”
Anna-Senpai told Coelho that paying customers also were the reason for the 620 Gbps attack on KrebsOnSecurity. Two weeks prior to that attack, I published the results of a months-long investigation revealing that “vDOS” — one of the largest and longest-running DDoS-for-hire services — had been hacked, exposing details about the services owners and customers.
The story noted that vDOS earned its proprietors more than $600,000 and was being run by two 18-year-old Israeli men who went by the hacker aliases “applej4ck” and “p1st0”. Hours after that piece ran, Israeli authorities arrested both men, and vDOS — which had been in operation for four years — was shuttered for good.
[10:47:42 AM] live:anna-senpai: i sell net spots, starting at $5k a week
[10:47:50 AM] live:anna-senpai: and one client was upset about applejack arrest
[10:48:01 AM] live:anna-senpai: so while i was gone he was sitting on them for hours with gre and ack
[10:48:14 AM] live:anna-senpai: when i came back i was like oh fuck
[10:48:16 AM] live:anna-senpai: and whitelisted the prefix
[10:48:24 AM] live:anna-senpai: but then krebs tweeted that akamai is kicking them off
[10:48:31 AM] live:anna-senpai: fuck me
[10:48:43 AM] live:anna-senpai: he was a cool guy too, i like his article
[SIDE NOTE: If true, it’s ironic that someone would hire Anna-Senpai to attack my site in retribution for the vDOS story. That’s because the firepower behind applej4ck’s vDOS service was generated in large part by a botnet of IoT systems infected with a Qbot variant — the very same botnet strain that Anna-Senpai and Mirai were busy killing and erasing from the Internet.]
Coelho told KrebsOnSecurity that if his side of the conversation reads like he was being too conciliatory to his assailant, that’s because he was wary of giving Anna a reason to launch another monster attack against ProxyPipe. After all, Coelho said, the Mirai attacks on ProxyPipe caused many customers to switch to other Minecraft servers, and Coelho estimates the attack cost the company between $400,000 and $500,000.
Nevertheless, about halfway through the chat Coelho gently confronts Anna on the consequences of his actions.
[10:54:17 AM] katie.onis: People have a genuine reason to be unhappy though about large attacks like this
[10:54:27 AM] live:anna-senpai: yeah
[10:54:32 AM] katie.onis: There’s really nothing anyone can do lol
[10:54:36 AM] live:anna-senpai:
[10:54:38 AM] katie.onis: And it does affect their lives
[10:55:10 AM] live:anna-senpai: well, i stopped caring about other people a long time ago
[10:55:18 AM] live:anna-senpai: my life experience has always been get fucked over or fuck someone else over
[10:55:52 AM] katie.onis: My experience with [ProxyPipe] thus far has been
[10:55:54 AM] katie.onis: Do nothing bad to anyone
[10:55:58 AM] katie.onis: And still get screwed over
[10:55:59 AM] katie.onis: Haha
The two even discussed anime after Anna-Senpai guessed that Coelho might be a fan of the genre. Anna-Senpai says he watched the anime series “Gate,” a reference to the above-mentioned B Gata H Hei that Dreadiscool included in the list of anime film series he’s watched. Anna also confirms that the name for his bot malware was derived from the anime series Mirai Nikki.
[5:25:12 PM] live:anna-senpai: i rewatched mirai nikki recently
[5:25:22 PM] live:anna-senpai: (it was the reason i named my bot mirai lol)
DREADISCOOL = ANNA = JHA?
Coelho said when Anna-Senpai first reached out to him on Skype, he had no clue about the hacker’s real-life identity. But a few weeks after that chat conversation with Anna-Senpai, Coelho’s business partner (the Eric referenced in the first chat segment above) said he noticed that some of the code in Mirai looked awfully similar to code that Dreadiscool had posted to his Github account.
“He started to come to the conclusion that maybe Anna was Paras,” Coelho said. “He gave me a lot of ideas, and after I did my own investigation I decided he was probably right.”
An incomplete “mindmap” I put together as I started to assemble research.
Coelho said he’s known Paras Jha for more than four years, having met him online when Jha was working for Minetime — which ProxyPipe was protecting from DDoS attacks at the time.
“We talked a lot back then and we used to program a lot of projects together,” Coelho said. “He’s really good at programming, but back then he wasn’t. He was a little bit behind, and I was teaching him most everything.”
According to Coelho, as Jha became more confident in his coding skills, he also grew more arrogant, belittling others online who didn’t have as firm a grasp on subjects such as programming and DDoS mitigation.
“He likes to be recognized for his knowledge, being praised and having other people recognize that,” Coelho said of Jha. “He brags too much, basically.”
Coelho said not long after Minetime was hit by a DDoS extortion attack in 2013, Paras joined Hackforums and fairly soon after stopped responding to his online messages.
“He just kind of dropped off the face of the earth entirely,” he said. “When he started going on Hackforums, I didn’t know him anymore. He became a different person.”
Coelho said he doesn’t believe his old friend wished him harm, and that Jha was probably pressured into attacking ProxyPipe.
“In my opinion he’s still a kid, in that he gets peer-pressured a lot,” Coelho said. “If he didn’t [launch the attack] not only would he feel super excluded, but these people wouldn’t be his friends anymore, they could out him and screw him over. I think he was pretty much in a really bad position with the people he got involved with.”
THE RUTGERS DDOS ATTACKS
On Dec. 16, security vendor Digital Shadows presented a Webinar that focused on clues about the Mirai author’s real life identity. According to their analysis, before the Mirai author was known as Anna-Senpai on Hackforums, he used the nickname “Ogmemes123123” (this also was the alias of the Skype username that contacted Coelho), and the email address [email protected] (recall this is the same email address Anna-Senpai used in his alerts to various hosting firms about the urgent need to take down Qbot control servers hosted on their networks).
Digital Shadows noted that the Mirai author appears to have used another nickname: “OG_Richard_Stallman,” a likely reference to the founder of the Free Software Foundation. The [email protected] account was used to register a Facebook account in the name of OG_Richard Stallman.
That Facebook account states that OG_Richard_Stallman began studying computer engineering at New Brunswick, NJ-based Rutgers University in 2015.
As it happens, Paras Jha is a student at Rutgers University. This is especially notable because Rutgers has been dealing with a series of DDoS attacks on its network since the fall semester of 2015 — more than a half dozen incidents in all. With each DDoS, the attacker would taunt the university in online posts and media interviews, encouraging the school to spend the money to purchase some kind of DDoS mitigation service.
Using the nicknames “og_richard_stallman,” “exfocus” and “ogexfocus,” the person who attacked Rutgers more than a half-dozen times took to Reddit and Twitter to claim credit for the attacks. Exfocus even created his own “Ask Me Anything” interview on Reddit to discuss the Rutgers attacks.
Exfocus also gave an interview to a New Jersey-based blogger, claiming he got paid $500 an hour to DDoS the university with as many as 170,000 bots. Here are a few snippets from that interview, in which he blames the attacks on a “client” who is renting his botnet:
“Are you for real? Why would you do an interview with us if you’re getting paid?
Normally I don’t show myself, but the entity paying me has something against the school. They want me to “make a splash”.
Why do you have a twitter account where you publically broadcast patronizing messages. Are you worried that this increases the risk of things getting back to you?
Public twitter is on clients request. The client hates the school for whatever reason. They told me to say generic things like that I hate the bus system and etc.
Have you ever attacked RU before?
During freshman registration the client requested it also – he didn’t want any publicity then though.
What are your plans for the future in terms of DDOSing and attacking the Rutgers cyber infrastructure?
When I stop getting paid – I’ll stop DDosing lol. I’m hoping that RU will sign on some ddos mitigation provider. I get paid extra if that happens.
At some point you said you were at the Livingston student center – outside of Sbarro. In this interview you said that you aren’t affiliated directly with Rutgers, did you lie then?
Yes”
An online search for the Gmail address used by Anna-Senpai and OG_Richard_Stallman turns up a Pastebin post from July 1, 2016, in which an anonymous Pastebin user creates a “dox” of OG_Richard_Stallman. Doxing refers to the act of publishing someone’s personal information online and/or connecting an online alias to a real life identity.
The dox said OG_Richard_Stallman was connected to an address and phone number of an individual living in Turkey. But this is almost certainly a fake dox intended to confuse cybercrime investigators. Here’s why:
A Google search shows that this same address and phone number showed up in another dox on Pastebin from almost three years earlier — June 2013 — intended to expose or confuse the identity of a Hackforums user known as LiteSpeed. Recall that LiteSpeed is the same alias that ProTraf’s Josiah White acknowledged using on Hackforums.
EXTORTION ATTEMPTS BY OG_RICHARD_STALLMAN
This OG_Richard_Stallman identity is connected to Anna-Senpai by another person we’ve heard from already: Francisco Dias, whose Frantech ISP was attacked by Anna-Senpai and Mirai in mid-September. Francisco told KrebsOnSecurity that in early August 2016 he began receiving extortion emails from a Gmail address associated with a OG_Richard_Stallman.
“This guy using the Richard Stallman name added me on Skype and basically said ‘I’m going to knock all of your [Internet addresses] offline until you pay me’,” Dias recalled. “He told me the up front cost to stop the attack was 10 bitcoins [~USD $5,000 at the time], and if I didn’t pay within four hours after the attack started the fee would double to 20 bitcoins.”
Dias said he didn’t pay the demand and eventually OG_Richard_Stallman called off the attack. But he said for a while the attacks were powerful enough to cause problems for Frantech’s Internet provider.
“He was hitting us so hard with Mirai that he was dropping large parts of Hurricane Electric and causing problems at their Los Angeles point of presence,” Dias said. “I basically threw everything behind [DDoS mitigation provider] Voxility, and eventually Stallman buggered off.”
The OG_Richard_Stallman identity also was tied to similar extortion attacks at the beginning of August against one hosting firm that had briefly been one of ProTraf’s customers in 2016. The company declined to be quoted on the record, but said it stopped doing business with Protraf in mid-2016 because they were unhappy with the quality of service.
The Internet provider said not long after that it received an extortion demand from the “OG_Richard_Stallman” character for $5,000 in Bitcoin to avoid a DDoS attack. One of the company’s researchers contacted the extortionist via the [email protected] address supplied in the email, but posing as someone who wished to hire some DDoS services.
OG_Richard_Stallman told the researcher that he could guarantee 350 Gbps of attack traffic and that the target would go down or the customer would receive a full refund. The price for the attack? USD $100 worth of Bitcoin for every five minutes of attack time.
My source at the hosting company said his employer declined to pay the demand, and subsequently got hit with an attack from Mirai that clocked in at more than 300 Gbps.
“Clearly, the attacker is very technical, as they attacked every single [Internet address] within the subnet, and after we brought up protection, he started attacking upstream router interfaces,” the source said on condition of anonymity.
Asked who they thought might be responsible for the attacks, my source said his employer immediately suspected ProTraf. That’s because the Mirai attack also targeted the Internet address for the company’s home page, but that Internet address was hidden by DDoS mitigation firm Cloudflare. However, ProTraf knew about the secret address from its previous work with the company, the source explained.
“We believe it’s Protraf’s staff or someone related to Protraf,” my source said.
A source at an Internet provider agreed to share information about an extortion demand his company received from OG_Richard_Stallman in August 2016. Here he is contacting the Stallman character directly and pretending to be someone interested in renting a botnet. Notice the source brazenly said he wanted to DDoS ProTraf.
DDOS CONFESSIONS
After months of gathering information about the apparent authors of Mirai, I heard from Ammar Zuberi, once a co-worker of ProTraf President Paras Jha.
Zuberi told KrebsOnSecurity that Jha admitted he was responsible for both Mirai and the Rutgers DDoS attacks. Zuberi said when he visited Jha at his Rutgers University dorm in October 2015, Paras bragged to him about launching the DDoS attacks against Rutgers.
“He was laughing and bragging about how he was going to get a security guy at the school fired, and how they raised school fees because of him,” Zuberi recalled. “He didn’t really say why he did it, but I think he was just sort of experimenting with how far he could go with these attacks.”
Zuberi said he didn’t realize how far Jha had gone with his DDoS attacks until he confronted him about it late last year. Zuberi said he was on his way to see his grandmother in Arizona at the end of November 2016, and he had a layover in New York. So he contacted Jha and arranged to spend the night at Jha’s home in Fanwood, New Jersey.
As I noted in Spreading the DDoS Disease and Selling the Cure, Anna-Senpai leaked the Mirai code on a domain name (santasbigcandycane[dot]cx) that was registered via Namecentral, an extremely obscure domain name registrar which had previously been used to register fewer than three dozen other domains over a three-year period.
According to Zuberi, only five people knew about the existence of Namecentral: himself, CJ Sculti, Paras Jha, Josiah White and Namecentral’s owner Jesse Wu (19-year-old Wu features prominently in the DDoS Disease story linked in the previous paragraph).
“When I saw that the Mirai code had been leaked on that domain at Namecentral, I straight up asked Paras at that point, ‘Was this you?,’ and he smiled and said yep,” Zuberi recalled. “Then he told me he’d recently heard from an FBI agent who was investigating Mirai, and he showed me some text messages between him and the agent. He was pretty proud of himself, and was bragging that he led the FBI on a wild goose chase.”
Zuberi said he hasn’t been in contact with Jha since visiting his home in November. Zuberi said he believes Jha wrote most of the code that Mirai uses to control the individual bot-infected IoT devices, since it was written in Golang and Jha’s partner White didn’t code well in this language. Zuberi said he thought White’s role was mainly in developing the spreading code used to infect new IoT devices with Mirai, since that was written in C — a language White excelled at.
In the time since most of the above occurred, the Internet address ranges previously occupied by ProTraf have been withdrawn. ProxyPipe’s Coelho said it could be that the ProTraf simply ran out of money.
ProTraf’s Josiah White explained the disappearance of ProTraf’s Internet space as part of an effort to reboot the company.
“We [are] in the process of restructuring and refocusing what we are doing,” White told KrebsOnSecurity.
Jha did not respond to requests for comment.
Rutgers University did not respond to requests for comment.
The FBI officials could not be immediately reached for comment.
A copy of the entire chat between Anna-Senpai and ProxyPipe’s Coelho is available here.
from https://krebsonsecurity.com/2017/01/who-is-anna-senpai-the-mirai-worm-author/
0 notes