#various smtp server
Text
Understanding SOCKS5 Mobile Proxies: A Comprehensive Guide

As digital environments become increasingly sophisticated, so do the methods to ensure privacy, security, and access to diverse online resources. Among the various proxy types, SOCKS5 mobile proxies stand out due to their versatility and effectiveness. This article explores the concept of SOCKS5 mobile proxies, their advantages, use cases, and how they can enhance your online activities.
What is a SOCKS5 Proxy?
A SOCKS5 proxy is a type of proxy server that provides a high level of anonymity and supports a wide range of internet protocols. Unlike HTTP proxies, which handle only HTTP and HTTPS traffic, SOCKS5 proxies can handle any kind of traffic, including those for FTP, SMTP, and more. The "5" in SOCKS5 indicates the version of the SOCKS protocol, which includes improvements over previous versions, such as enhanced security and support for UDP (User Datagram Protocol).
What is a Mobile Proxy?
A mobile proxy is a proxy server that provides an IP address associated with a mobile device rather than a traditional desktop or data center server. These proxies use IP addresses assigned by mobile carriers and are typically linked to 3G, 4G, or 5G networks. Mobile proxies are highly valuable due to their high anonymity and ability to mimic real mobile traffic, which is often less likely to be flagged or blocked by websites.
Combining SOCKS5 with Mobile Proxies
When combining SOCKS5 with mobile proxies, you get the benefits of both technologies:
- SOCKS5 Protocol: Offers advanced features like authentication, better performance, and support for a wide range of protocols and applications.
- Mobile Proxy: Provides an IP address associated with a mobile device, ensuring high anonymity and the ability to bypass mobile-specific restrictions.
Together, SOCKS5 mobile proxies offer a robust solution for maintaining privacy, avoiding detection, and accessing restricted content.
Advantages of SOCKS5 Mobile Proxies
- Enhanced Anonymity
- SOCKS5 mobile proxies mask your real IP address with an IP address from a mobile network. This high level of anonymity helps in preventing tracking and maintaining privacy.
- Bypassing Geographic Restrictions
- Many online services and content are restricted based on geographic location. SOCKS5 mobile proxies can bypass these restrictions by providing an IP address from a specific mobile network, allowing access to region-locked content.
- Avoiding IP Bans
- Mobile IP addresses are less likely to be blacklisted compared to datacenter IPs. This is particularly useful for tasks like web scraping or managing multiple social media accounts where frequent requests can lead to IP bans.
- High Reliability
- Mobile proxies often provide a stable connection due to their association with mobile carriers. This ensures consistent performance and reliability.
- Flexibility
- SOCKS5 supports various types of internet traffic, making it suitable for diverse applications such as gaming, streaming, and secure browsing.
Common Use Cases for SOCKS5 Mobile Proxies
- Web Scraping
- When scraping data from websites, it’s essential to avoid detection and IP bans. SOCKS5 mobile proxies help by rotating IP addresses and mimicking real user behavior, making scraping more efficient.
- Social Media Management
- Managing multiple social media accounts from a single IP can lead to bans or restrictions. SOCKS5 mobile proxies allow users to manage multiple accounts without raising suspicion.
- Ad Verification
- To ensure ads are displayed correctly across different regions, advertisers use mobile proxies to simulate traffic from various locations, ensuring accurate ad verification.
- Market Research
- Conducting market research often requires accessing region-specific data. SOCKS5 mobile proxies help gather data from different regions without geographical limitations.
- Gaming
- For gamers looking to access geo-restricted game content or avoid regional blocks, SOCKS5 mobile proxies provide the necessary anonymity and access.
Choosing the Right SOCKS5 Mobile Proxy Provider
When selecting a SOCKS5 mobile proxy provider, consider the following factors:
- IP Pool Size: A larger pool of IP addresses reduces the risk of IP bans and ensures more consistent performance.
- Speed and Reliability: Look for providers that offer high-speed connections and reliable performance.
- Geographic Coverage: Ensure the provider has a broad range of locations to suit your needs.
- Customer Support: Opt for providers that offer robust customer support to address any issues or queries.
How to Use SOCKS5 Mobile Proxies
- Select a Proxy Provider: Choose a reputable SOCKS5 mobile proxy provider that meets your requirements.
- Configure Your Proxy: Follow the provider’s instructions to configure your device or application to use the SOCKS5 proxy.
- Test the Connection: Ensure the proxy is working correctly by testing its performance and checking for any connection issues.
- Monitor Usage: Regularly monitor your proxy usage to ensure optimal performance and address any potential issues.
Conclusion
SOCKS5 mobile proxies offer a powerful combination of advanced protocol features and mobile network benefits, making them an excellent choice for those seeking enhanced privacy, security, and access to restricted content. Whether you're engaged in web scraping, managing multiple accounts, or simply aiming to browse anonymously, SOCKS5 mobile proxies provide the flexibility and reliability needed to navigate the digital landscape effectively.
Choosing the right provider and understanding how to use SOCKS5 mobile proxies can significantly enhance your online activities, ensuring a secure and seamless experience.
Read the full article
0 notes
Text
What Is SMTP in WordPress? And How To Configure It?
SMTP (Simple Mail Transfer Protocol) for WordPress is a method used to send emails from your WordPress site. By default, WordPress uses the PHP mail function to send emails, but SMTP provides a more reliable and secure way to send emails.
It ensures that your emails are delivered successfully to the recipients' inbox, rather than being marked as spam. Setting up SMTP for WordPress involves configuring your WordPress site to use an SMTP server to send emails.
What Is SMTP In WordPress?
https://jpcdn.it/img/tiny/10ef05c741f88df7bc52eaab714af71c.jpg
SMTP (Simple Mail Transfer Protocol) in WordPress refers to the method used for sending emails from your WordPress website. By default, WordPress uses the built-in PHP mail function to send emails, but SMTP provides a more reliable and secure alternative.
SMTP ensures that your emails are delivered successfully to recipients' inboxes and helps prevent them from being marked as spam. With SMTP configured in WordPress, emails are sent through an external SMTP server, typically provided by your web hosting provider or a third-party email service.
This setup allows you to specify authentication credentials, such as a username and password, ensuring that your emails are authenticated and trusted by email providers.
How To Configure SMTP In WordPress?
Configuring SMTP in WordPress involves several steps. Here's a general guide:
https://jpcdn.it/img/3fa5ee365d1c835a3a542dab41533f3e.jpg
For more information or buying fast and secure hosting visit the www.ozoweb.com, Ozoweb provides various services like Linux Shared Web Hosting, Domain Registration, VPS, and Dedicated Servers. They focus on offering these services at prices that are affordable for everyone. Their goal is to make sure their prices are unbeatable while still providing high-quality hosting services and products that fit their customers' needs and budgets.
#OZOHosting#lowest price hosting in india#Cheap web hosting jaipur#cheap shared web hosting india#free web hosting india#affordable linux web hosting india
0 notes
Text
127.0.0.1:62893: Understanding the Meaning and How to Fix It?

127.0.0.1:62893 is a unique IP address referencing the machine from which you are operating.
Working on your computer, have you ever come across the mysterious code 127.0.0.1:62893? Though it seems complicated, knowing its components will be beneficial! The error message "Disconnected from the target VM, address: 127.0.0.1:62893" often shows up on the screen throughout the development process.
IPv4 and IPv6 are the two varieties of IP addresses. While IPv6 addresses are 128-bit values written in hexadecimal (e.g., 2001:0b8:85a3:0000:0000:8a2e:0370:7334), IPv4 addresses are 32-bit numbers generally expressed in dotted decimal form (e.g., 192.168.1.1).
However, port numbers are used on a device to name particular operations or services. They separate traffic for distinct uses so that several services may run on a single IP address. For HTTP, for instance, online traffic usually uses port 80; for HTTPS, port 443; for SMTP, port 25.
This blog post will dissect what 127.0.0.1:62893 represents, how it operates, and how to correct a typical issue.
Value In Knowing Network Fundamentals
Anyone in IT, networking, or software development needs a strong foundation in network principles. Knowing IP addresses and port numbers enhances security network resource protection, performance optimization, and diagnosis of connectivity problems. Furthermore, it enables experts to set and debug systems properly, guaranteeing seamless connection between devices and services.
Summary Of The Subject: 127.0.0.1:62893
An IP address and a port number combine in the address 127.0.0.1:62893. 127.0.0.1 is the loopback address—a special-purpose IP address a host uses to interact with itself. Combined with a port number, it allows local machine testing and development free from system exposure to outside networks.
We will examine the details 127.0.0.1:62893 in this blog, including its relevance, typical problems, and recommended methods for diagnosing and maximizing its use. Whether your job is network administrator, developer, or IT enthusiast, knowing this IP can help you to control and fix local network configurations.
What Is 127.0.0.1? ( Loopback Address)
The most often used loopback address in IPv4 is 127.0.0.1. Reserved for a host to send messages to herself, loopback addresses are a spectrum of IP addresses (127.0.0.0 to 127.255.255). It's a local testing method for network applications without transmitting traffic across the real network.
Using 127.0.0.1 causes network traffic to return to the same machine. Because it lets you replicate network environments without impacting other devices, this is very helpful for development, testing, and troubleshooting needs. For instance, if you run a web server on your local computer, you can access it by 127.0.0.1 to guarantee it's operating as it should without letting the internet know.
What 127.0.0.1:62893 Can Do for You?
There are various benefits to address 127.0.0.1:62893.
It gives developers a safe space free from public view by letting them test and troubleshoot programs within.
Learning about networking concepts, including TCP/IP systems and client-server communication, benefits one.
Early identification and reduction of any security risks depends on local-host traffic monitoring.
Debugging helps to identify problems connected to networks, enhancing the stability and performance of applications.
Working in a controlled environment, localhost avoids issues with other programs.
How to Use 127.0.0.1:62893
The address works as follows in a basic sense:
Your device runs an application trying to interact with another process.
It wants to interact with a service on the same system, so it uses "localhost," (127.0.0.1).
The port number (62893) informs the operating system which service or application should handle incoming traffic.
For example, a development tool might utilize this address to interface with a local server for debugging needs.
Safety Concerns
Although port 62893 and the loopback address are usually safe, there are a few factors to consider:
Make sure that your firewall settings allow communication across port 62893 if needed. Blocking this port could stop some programs from operating as they should.
If you are unfamiliar with the application or service, be cautious of any software trying to interact with this port. Malicious programs could use this port for illegal correspondence.
Now and then, make sure no illegal programs are using any other suspicious port or port 62893 on your machine.
Please Note: Even though localhost is designed chiefly for local use, the concepts you gain from experimenting can be used in general networking scenarios. You should now be able to interpret and utilize 127.0.0.1:62893 with ease.
The Step-by-Step Troubleshooting Guide
STEP 1: Verify whether the service is currently running.
Check that the service meant to be listening on 127.0.0.1:62893 is running.
Open Command Prompt and run: cmd netstat -an | find "62893".
Mac or Linux: Run bash from an open terminal using lsof -i:62893.
This command will list the process utilizing port 62893 and indicate whether any service is listening on that port. If no service turns up, start the application or service and try again.
STEP 2: Look for port conflicts.
Verify no other service makes use of port 62893.
If you discover another service, you can stop it or switch the port used for your application.
STEP 3: Confirm Firewall Guidelines
On particular ports, firewalls can restrict access
To be sure port 62893 is permitted, review your firewall settings.
Firewall from Windows:
Advanced Security Open Windows Defender Firewall
Review Inbound and Outbound Rules to find rules blocking Port 62893.
Firewall from Apple:
Under Security & Privacy, under Firewall Settings in System Preferences
STEP 4: Review application settings.
To guarantee your program is configured correctly to access 127.0.0.1 and port 62893
Review the configuration files or settings of it.
STEP 5: Restart network services
Restarts of network services occasionally help to fix underlying problems.
Windows: cmd netsh winsock reset
Restart the network service using the bash sudo system Linux/Mac.
STEP 6: Update or reinstall network drivers
Issues can arise from corrupt or antiquated network drivers.
Make sure your drivers either reinstall them if needed or are current.
Conclusion
The combination of a local IP address and a port number utilized by a specific service on your computer is represented as 127.0.0.1:62893, more than simply a string of digits. It is essential for anyone working in web development, networking, or information technology to grasp the significance of port numbers, IP addresses, and local hosts.
It is crucial to know how to use localhost and the loopback address 127.0.0.1 while troubleshooting network issues, whether you are a developer testing your latest online application or an IT specialist. If you know what these statistics mean and how to manipulate them, you can keep your local services safe and running efficiently.
FAQs
Can my browser make an HTTP local request if I am not connected to a network?
Indeed, your computer communicates with itself without any network! This is so because your computer connects to a default address—127.0.0.1—which is not particular to any network when it lacks an internet connection.
How do IPv6 addresses differ from localhost addresses?
Acting as the host entry for any data for a given computer, localhost is the basic IPv4 address stated numerically as 127.0.0.1 together with port 62893. Conversely, IPv6 addresses are a numerical series 127.0.0.1-based internet protocol in the v6 sequence. This is a loopback address, unlike IPv4 addresses, which would not allocate many addresses.
Can I block a website using a local host address? If yes, in what manner?
Certainly. Just follow a few guidelines as described here:
Open Notepad under Administrator; utilize the User Account Control prompt
Click File, then Open.
View the host file open.
Enter 127.0.0.1 in the address bar, then Save and Restart your machine.
Read the full article
0 notes
Text
An in-depth look at the magic of communication protocols in networking
Long time no see! It's time to share again~ Communication protocols are the cornerstone of network communication, they determine how data is transmitted and the rules for processing in the network. Next, let's take a look at the specific applications of communication protocols in network communication!

1. Internet communication
Internet communication is one of the most widely used application scenarios. Here are some common Internet communication protocols and their applications.
·HTTP/HTTPS: Used to transfer web pages between a browser and a server. HTTPS adds SSL/TLS encryption to HTTP to ensure the security of data transmission.
·FTP: Used to transfer files between client and server, commonly used for website updates and file sharing.
·SMTP/IMAP/POP3: Used for email transmission and reception, ensuring the transmission of emails between different mail servers and clients.

2. LAN communication
In a business or home network, LAN communication protocols ensure efficient communication between devices.
·Ethernet: the most common wired LAN protocol ensures the transmission of data packets between network devices.
·Wi-Fi: Wireless LAN protocol that allows devices to connect to the network via wireless signals for convenient mobile office and home network connectivity.
·DHCP: Dynamic Host Configuration Protocol, automatically assigns IP addresses to devices in the network, simplifying network management.
3. Mobile communication
Mobile communication protocols ensure global communication for cell phones and other mobile devices.
·GSM/CDMA/LTE/5G: These are different generations of mobile communication protocols, from the early 2G to the current 5G, each generation of protocols has improved data transfer speed and communication quality.
·VoLTE: High-definition voice calls over LTE networks have improved the user's call experience.

4. Internet of Things (IoT) communication
IoT devices are interconnected through various protocols, and the following are some common IoT communication protocols.
·MQTT: Lightweight publish/subscribe messaging protocol for device communication in low-bandwidth, unstable network environments.
·CoAP: restricted application protocol, designed for simple electronic devices, provides efficient device control and data transfer.
·Zigbee/Z-Wave: low-power wireless communication protocol widely used in smart home devices such as smart light bulbs, thermostats and security systems.
Choosing the right communication protocol can significantly improve network performance and user experience. I hope today's sharing is helpful.711Proxy provides pure residential IPs to help you increase network speed!
0 notes
Text
Smtp service provider

Unlocking the Power of Bulk Email with Reliable SMTP Server Solutions
In today’s digital age, effective communication is essential for any business looking to thrive. One of the most efficient ways to reach a large audience is through bulk email marketing. To achieve this, choosing the right SMTP server is crucial. An SMTP server for bulk email can streamline your marketing efforts, ensuring your messages reach their intended recipients without delays or issues.
Understanding SMTP Server Bulk and Its Benefits
SMTP (Simple Mail Transfer Protocol) servers are essential for sending emails over the internet. When it comes to SMTP server bulk solutions, businesses can efficiently send thousands of emails simultaneously. This capability is vital for companies looking to launch large-scale marketing campaigns or informational newsletters.
Utilizing an SMTP server for mass email not only enhances deliverability rates but also provides insights into how your emails perform. Many SMTP service providers offer detailed analytics, allowing you to track open rates, click-through rates, and overall engagement. By leveraging these insights, you can optimize your campaigns for better results.
Choosing the Right SMTP Service Provider
Selecting the right SMTP service provider is critical to the success of your email marketing strategy. A reputable provider offers reliability, high deliverability rates, and robust security measures to protect your data. When searching for an SMTP server mass email solution, consider factors such as server uptime, customer support, and the ability to scale as your business grows.
Moreover, ensure that your provider complies with anti-spam regulations to prevent your emails from being marked as spam. A trustworthy bulk email server provider will offer tools that help you manage your mailing lists, segment your audience, and personalize your content, leading to more effective marketing campaigns.
The Rise of Bulk Email Marketing Software in India
With the growing digital landscape in India, many businesses are turning to bulk email marketing software India to facilitate their communication needs. These platforms typically come equipped with user-friendly interfaces, allowing even those without technical expertise to launch successful email campaigns.
Bulk email software in India provides various features, including customizable templates, automated workflows, and integration with other marketing tools. This flexibility enables businesses to create targeted email campaigns tailored to their audience’s preferences, driving engagement and boosting conversions.
Additionally, using a bulk mail service in India allows businesses to reach a wider audience at a lower cost compared to traditional marketing methods. By employing a reliable SMTP server, companies can enhance their reach while maintaining a professional image, as the software ensures that all emails are well-formatted and personalized.
Conclusion
In conclusion, harnessing the power of a reliable SMTP server for bulk email is essential for any business aiming to improve its communication strategies. By selecting the right SMTP service provider and leveraging effective bulk email marketing software in India, you can elevate your marketing campaigns and achieve remarkable results.
Whether you’re a small startup or an established enterprise, investing in a robust bulk email server provider will allow you to maximize your outreach while ensuring compliance with regulations. Start exploring your options today, and unlock the full potential of bulk email marketing! Visit here - https://mails2inbox.com/
0 notes
Text
MailDaddy Review — All-In-One Email Marketing Tool
Welcome to my MailDaddy Review, This is a genuine user-based MailDaddy review, in which I will discuss the features, upgrades, price, demo, and bonuses, how MailDaddy can benefit you, and my own personal opinion. The future of email marketing is here. This AI-powered autoresponder creates, writes, and sends unlimited emails with built-in SMTP and the latest Gmail and Yahoo compliance, dominating inboxes without any monthly fees!
If you’re sick and tired of paying hefty monthly fees for email marketing tools that don’t deliver and want 99.96% inbox delivery, I’ve got some excellent news for you today. It is fully compliant with Google’s and Yahoo’s 2024 updates. It’s spending tonnes of time and money on expensive and complicated autorespoders like Aweber, GetResponse, and MailChimp. MailDaddy is the first-to-market Aweber killer tech that lets you send unlimited browser-friendly emails to unlimited subscribers. Regrettably, this issue plagues almost every marketer. So, you need a proven email marketing solution that delivers real results and helps you grow your business without going bankrupt. Make Way For MailDaddy: Your Own Aweber Killer Tech That Sends Unlimited Browser-Friendly Emails To Unlimited Subscribers With MailDaddy by your side, you can easily send unlimited emails to unlimited subscribers. You, too, can live a life free from worry. You will be able to transfer 1000’s of dollars each month from your bank accounts. By the end, you’ll have a clear picture of whether MailDaddy is the right tool to propel your email marketing efforts forward.

MailDaddy Review: What Is MailDaddy?
MailDaddy is the next generation of email marketing software, allowing users to send as many emails as they want to as many followers for a one-time fee. This makes it attractive for budget-conscious businesses or those just starting out. MailDaddy boasts additional features to streamline your workflow a built-in SMTP server eliminates the need for a separate service, and AI-powered email writing helps you craft compelling content faster.

They also offer a drag-and-drop builder for crafting visually appealing emails. However, MailDaddy is a relatively new platform, and some features, like advanced integrations and robust customer support, are still under development. Consider these factors alongside your specific needs before deciding if MailDaddy is the right fit for your email marketing strategy.
MailDaddy Review: Overview
Creator: Pranshu Gupta
Product: MailDaddy
Date Of Launch: 2024-Jul-09
Time Of Launch: 11:00 EDT
Front-End Price: $19 (One-time payment)
Official Website: Click Here To Access
Niche: Tools And Software
Support: Effective Response
Discount: Get The Best Discount Right Here!
Recommended: Highly Recommended
Bonuses: Huge Bonuses
Skill Level Required: All Levels
Discount Code: “MailDaddy” To Get $2 Off!
Refund: YES, 30 Days Money-Back Guarantee
>>> Click Here to Visit MailDaddy and Get Access Now <<<
MailDaddy Review: About Authors

MailDaddy provider was created by Pranshu Gupta. Gupta is a seasoned digital marketer, web developer, and tech enthusiast with a passion for empowering businesses through technology. With over a decade of experience in the digital world, Pranshu has honed his expertise in SEO, content marketing, email marketing and website development, helping countless clients achieve their online goals.
Pranshu’s journey in the world of technology began with a fascination for computers and coding at a young age. His innate curiosity and thirst for knowledge led him to explore various programming languages, web development frameworks, and digital marketing strategies, laying the foundation for a successful career in the digital space.
He earned a reputation via lots of launches, including AI MarketingHub. HostDaddy, NewsCaster Ai, Ai MentorPro, Visionize Ai, LearnX, AutoMailX, MailGPT, VidMaster, Coursesify, and many others.
MailDaddy Review: Features
Fully Compliant With Google & Yahoo’s 2024 Update
Send Unlimited Emails To Unlimited Subscribers With Zero Monthly Fees
Use Gmail’s AI to Block Spam, Phishing, and Malware.
100% Gmail & Yahoo Compliance
Get 100% SPF, DMARC & DKIM Compliance To Boost Your Sender Reputation
Drag-and-Drop Email Editor
Effortless List Cleaning To Move Unwanted Emails Instantly
Let Ai Write 100s of Emails and Messages With Just One Keyword AI
Built-In High-Speed SMTP
Done-For-You Leads
Smart Tagging and Micro-Segmentation
Create & Send Unlimited Emails
Setup Auto Responders and Newsletters
Create Unlimited Lists to Manage Subscribers
Add Unlimited Subscribers
Add Third Part SMTP
Advanced analytics for Email Campaigns
Tons of Editable Email Templates
Preloaded with Tons of Webform Templates
Preloaded with Tons of Webform Templates
Team Management to add Unlimited Team Members
Bounce Setting to Manage Bounce Emails
Suppression List to Exclude Subscribers from Future Emails
Advance API Integration
Inbuilt Image Library for Stock Images
MailDaddy Review: How Does It Work?
MailDaddy Sends Unlimited Google-Friendly Emails To Unlimited Subscribers In 3 Easy Steps
Step #1:
Login
To start, just login & use this Google & Yahoo friendly AI email marketing autoresponder in few taps of your mouse. You get full SPF, DMARC & DKIM compliance so zero risk of getting IP banned.
Step #2:
Upload List
Now, go ahead & upload your list in few clicks. Rest assured; we guarantee you won’t lose as single lead while uploading.
Step #3:
Send & Profit
Great, you’re all set. Now send unlimited SPAM free emails to unlimited subscribers with zero third party subscriptions or any huge investment.
>>> Click Here to Visit MailDaddy and Get Access Now <<<
MailDaddy Review: Can Do For You
Send Unlimited Emails To Unlimited Subscribers For Zero Monthly Cost
Use Gmail’s AI-Powered Defenses To Stop More Than 99.9% Of Spam, Phishing And Malware Attacks Inside Inbox
Get 100% SPF, DMARC & DKIM Compliance To Boost Your Sender Reputation
Write & Send Thousands Of Profit-Pulling Emails Using AI Email Writer
Choose From 250+ Professionally Designed Templates To Save Time & Maximize Inbox Delivery
Built Ultra Fast SMTP & Dedicated IP To Send Countless Inbox Friendly Emails
Generate Unlimited Red-Hot Leads For Any Offer In Any Niche
Easily Manage Your List & Segment Your Audience For 10X Engagement
Use Drag-and-Drop Email Builder To Create Beautiful Inbox Friendly Emails With Zero Coding
Smartly Import/Export Unlimited Contacts With Just One Click
99% Uptime And 99.96% Deliverability Assurance To Get More Opens, Clicks, And Sales
Effortless List Cleaning To Move Unwanted Emails Instantly
Precise Analytics Included To Monitor Your Emails’ Opens, Clicks, And Subscribers’ Engagement
Stop Paying HUGE Monthly To Aweber, GetResponse, MailChimp Etc
100% Mobile Responsive Emails for Maximum Reach
Limited Time Offer- Get Premium Bonuses Worth $14,958
User Friendly, Cloud Based App. Start within A Minute
Iron-Clad 30-Day Money-Back Guarantee Included.
MailDaddy Review: What Users Say About MailDaddy


MailDaddy Review: Who Should Use It?
Affiliate Marketers
Website Owners
Digital Product Sellers
Event Organizers
SAAS Business Owners
Social Media Marketers
Mom & Pop Store Owners
E-com Store Owners
Small Business Owners
Video Marketers
Bloggers & Vloggers
Coaches/ Trainers
Teachers/ Student Coordinators
Part Time Business Coaches
Make Money Online Aspirants
MailDaddy Review: Why You Buy MailDaddy?
Consider buying MailDaddy if you prioritize affordability and simplicity in your email marketing. The one-time fee structure offers a clear cost advantage over recurring monthly subscriptions, especially if you have a large or growing email list. The built-in SMTP server eliminates the need for a separate service, streamlining your setup process. Additionally, the AI writing assistant can be a time-saver for crafting email content, particularly if you’re new to email marketing.
MailDaddy Review: Is MailDaddy Right for You?
Is MailDaddy right for you? It depends on your needs. If you’re a budget-conscious beginner with a small list, the one-time fee and unlimited emails are tempting. But established businesses with complex needs or larger lists might be better served by established platforms with proven deliverability and advanced features. Consider the potential limitations like lack of integrations and unproven deliverability before buying.
MailDaddy Review: OTO’s And Pricing
Apply Code “Daddy30Off” for 30% Off each item
Front End Price: MailDaddy Premium ($19)
OTO1: MailDaddy Pro ($47)
OTO2: MailDaddy Enterprise ($67)
OTO3: MailDaddy Inbox Booster ($37)
OTO4: MailDaddy DFY ($97)
OTO5: MailDaddy Agency ($97)
OTO6: MailDaddy Reseller ($97)
OTO7: MailDaddy Whitelabel ($197)
>>> Click Here to Visit MailDaddy and Get Access Now <<<
Milady Free Exclusive Bonuses

MailDaddy Review: Money Back Guarantee
MailDaddy Comes With Our Iron Clad 30 Day Money Back Guarantee
We’re so sure that MailDaddy is strong, stable, and works well that we’re happy to give our customers a 30-day money-back promise. Our main goal is for your business to grow, which is why we made this technology so that you and other company owners can send emails to their customers without spending a lot of money. So, all you have to do is get your copy. With built-in SMTP and private IP, you can send as many emails as you want to as many users. Still, in the worst case, if you feel that your goals are not met, we will be happy to return every penny you spent with us during the 30-day time.
>>> Click Here to Visit MailDaddy and Get Access Now <<<
MailDaddy Review: Positive and Negative
Pros:
Unlimited Emails & Subscribers: Perfect for scaling without limits.
One-Time Fee: Escape monthly subscriptions.
Built-in SMTP: Saves setup and cost.
AI Writing Assistant: Speeds up content creation.
User-Friendly Interface: Easy to use for beginners.
Cons:
No issues reported, it works perfectly!
Frequently Asked Questions (FAQ’s)
Q. Do I need any experience to get started?
None, all you need is just an internet connection. And you’re good to go.
Q. Is there any monthly cost?
Depends, if you act now, NONE. But if you wait, you might end up paying $997/month It’s up to you.
Q. How long does it take to make money?
Our average member made their first sale the same day they got access to MailDaddy.
Q. Do I need to purchase anything else for it to work?
No, MailDaddy is the complete thing. You get everything you need to make it work. Nothing is left behind.
Q. What if I failed?
While that is unlikely, we removed all the risk for you. If you tried MailDaddy and failed, we will refund you every cent you paid and send you a bunch of AI apps on top of that just to apologize for wasting your time.
Q. How can I get started?
Awesome, I like your excitement, all you have to do is click any of the buy buttons on the page and secure your copy of MailDaddy at a one-time fee.
MailDaddy Review: My Recommendation
MailDaddy offers a tempting proposition: unlimited email sending for a one-time fee. This can be a cost-effective solution for startups or small businesses with limited budgets. The built-in SMTP server, AI writing assistant, and user-friendly interface add to the appeal. However, MailDaddy’s new status raises concerns about deliverability rates and lack of established integrations. Upsells for essential features can inflate the overall cost. Carefully weigh your needs and budget before deciding if MailDaddy is the right fit for your email marketing journey.
>>> Click Here to Visit MailDaddy and Get Access Now <<<
Check Out My Previous Reviews: PromptSiteZ Review, AILogo Studio Review, MetAI Review, AI Fame Catalyst Review, Halo App Review, SiteClone AI Review, WebX Review, AI AppMaker Review, AI Books Review, & Scalar App Review
Thank for reading myMailDaddy Review till the end. Hope it will help you to make purchase decision perfectly.
Disclaimer: Please Note This MailDaddy review strives to provide objective information and analysis. While we aim for accuracy, pricing structures and features can change. It’s recommended to visit the MailDaddy website for the latest information before making a purchase decision.
Note: This is a paid software, and the one-time price is $19 for lifetime.
#MailDaddy#MailDaddy App#MailDaddy Upgrades#MailDaddy Overview#MailDaddy Features#MailDaddy Review#MailDaddy Works#What Is MailDaddy#Buy MailDaddy#MailDaddy Price#MailDaddy Demo#MailDaddy Discount#MailDaddy Honest Review#MailDaddy Pricing#MailDaddy exemple#MailDaddy FE#MailDaddy Pros#MailDaddy OTO#MailDaddy Preview#MailDaddy Scam#Get MailDaddy#MailDaddy Reviews#Purchase MailDaddy#MailDaddy Legal#Artificial Intelligence#AI#MailDaddy Benefits#MailDaddy Bonus#MailDaddy Bonuses#MailDaddy Software
0 notes
Text
Reoon Email Verifier Lifetime Deal: Best Email Verifier Tools
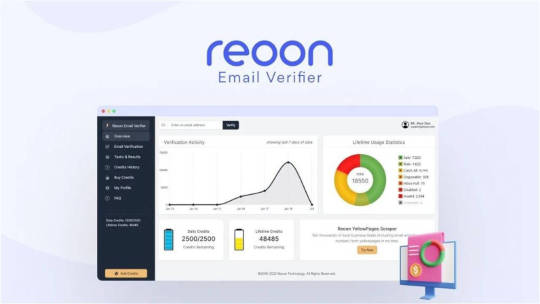
Reoon Email Verifier Lifetime Deal: Best Email Verifier Tools
Reoon Email Verifier Lifetime Deal: Ensure Inbox Success!
Are you looking for the best email verification tool to clean your email list? Look no further! Reoon Email Verifier Lifetime Deal is here to help you. This amazing tool is designed to clean invalid, temporary, and unsafe email addresses from your email list. It also protects your email server's reputation. In this article, we will explore why Reoon Email Verifier is the best choice for your email verification needs.
Why Choose Reoon Email Verifier?
Verifying email addresses in bulk has never been this easy. Reoon Email Verifier helps marketers and business owners clean their email lists and make their website registration spam-free. Here are some reasons why you should choose Reoon Email Verifier:
Very High Data Accuracy With Full Details: Reoon Email Verifier provides results with more than 99% accuracy.
AI-Powered Email Scoring System: This system helps in identifying the quality of email addresses.
Verify Gmail, Yahoo, Outlook or Anything: It can verify emails from various domains including Gmail, Yahoo, Microsoft, and custom business domains.
Dynamic Disposable/Temporary Email Detection: The tool can detect temporary email addresses quickly.
Spamtrap & Complaint Emails Detection: It helps in identifying spamtrap and complaint emails.
MTA Validation of Domain: This feature ensures the validity of the email domain.
SMTP Validation of Individual Address: It validates individual email addresses using SMTP.
WordPress Plugin for Form Validation: A plugin to validate emails on WordPress forms.
Live API Email Validation (0.5 Seconds): The API can validate emails live within 0.5 seconds.
Superfast Bulk Email Verification: It can verify a large number of emails quickly.
Simple & Attractive User Interface: The tool is user-friendly and easy to navigate.
Download Categorized Results With Full Details: You can download the verification results with full details.
Daily Renewal & Instantly Usable Lifetime Credits: Enjoy daily renewal and lifetime credits.
GDPR Compliance Service: The service complies with GDPR regulations.
Reoon Email Verifier Appsumo Lifetime Deal $79
Top Benefits of Reoon Email Verifier
Using Reoon Email Verifier comes with many benefits. Here are some of the top benefits:
Verify Email Addresses in Bulk: Clean your mailing list by removing invalid and fake addresses without sending any emails.
Live Email Verification: Verify users’ emails live within 0.5 seconds using the API’s quick verification mode.
Prevent Temporary Addresses: Get users’ actual email while registering on your site by preventing them from using temporary addresses.
Protect Your Domain and Server Reputation: Protect the sender reputation of your domain and server, resulting in better engagement.
Reduce Email Bounce Rate: Reduce bounce rate by verifying emails together. A high bounce rate can hurt your email campaign.
Save Money: Stop wasting money on disposable addresses that users will never check after the first use.
Prevent Spamtrap Penalties: Save yourself from getting penalized by sending emails to known spamtrap addresses.
Improve Email Delivery: Prevent your emails from ending up in the spam folders by sending emails to quality addresses only.
How to Use Reoon Email Verifier
Using Reoon Email Verifier is very easy. Follow these steps to get started:
Sign Up: Visit the Reoon Email Verifier website and sign up for an account.
Upload Your Email List: Upload your email list to the Reoon Email Verifier dashboard.
Start Verification: Click on the start button to begin the verification process.
Download Results: Once the verification is complete, download the results and clean your email list accordingly.
What Makes Reoon Email Verifier Stand Out?
Reoon Email Verifier stands out from other email verification tools due to its unique features and high accuracy. Here are some reasons why it is the best email verifier tool:
High Accuracy: Reoon Email Verifier provides results with more than 99% accuracy.
AI-Powered System: The AI-powered email scoring system helps in identifying the quality of email addresses.
Fast Verification: The tool can verify a large number of emails quickly and efficiently.
Live API Validation: The API can validate emails live within 0.5 seconds, making it ideal for website registrations.
Comprehensive Detection: It can detect temporary, spamtrap, and complaint emails, ensuring the quality of your email list.
Plan & Price

Customer Testimonials
Many customers have shared their positive experiences with Reoon Email Verifier. Here are some testimonials:
"Reoon Email Verifier has significantly improved our email campaign performance. The accuracy and speed of verification are impressive!" - John Doe
"I love the live API validation feature. It helps us get valid email addresses during user registrations on our site." - Jane Smith
"The tool is user-friendly and the results are highly accurate. It has saved us a lot of time and money." - Mark Johnson
Frequently Asked Questions
What Is Reoon Email Verifier?
Reoon Email Verifier is a bulk email validation tool that ensures email addresses are valid and safe.
How Accurate Is Reoon Email Verifier?
Reoon Email Verifier provides more than 99% accuracy in email validation.
Can It Detect Temporary Emails?
Yes, it dynamically detects temporary emails within seconds.
How Fast Is The Api Validation?
The API validation mode verifies emails live within 0. 5 seconds.
Conclusion
In conclusion, Reoon Email Verifier Lifetime Deal is the best email verifier tool available. It offers high accuracy, fast verification, and many unique features that make it stand out from other tools. By using Reoon Email Verifier, you can clean your email list, protect your domain and server reputation, and improve your email campaign performance. Don't wait any longer, try Reoon Email Verifier today!
For more information and to get started, visit the Reoon Email Verifier website.
0 notes
Text
How do I add a Roadrunner email account
Adding an email account can seem daunting, especially if you're not familiar with the specific steps for each provider. Roadrunner, a popular email service, is no different. This blog post will guide you through the process of adding a Roadrunner email account to your devices, ensuring you stay connected and organized. Whether you're using a computer, smartphone, or tablet, the following steps will help you set up your Roadrunner email account effortlessly.
Introduction to Roadrunner Email
Roadrunner, now known as Spectrum email, offers reliable email services to its users. Despite its name change, many people still refer to it as Roadrunner. This service is popular for its robust features and user-friendly interface. However, setting up a Roadrunner email account can be a bit tricky if you're not familiar with the process. In this guide, we'll walk you through the steps to add a Roadrunner email account on various devices.

Preparing for Setup
Before diving into the setup process, it's important to gather all necessary information. This includes your Roadrunner email address, password, and the incoming and outgoing mail server settings. Here's a checklist to ensure you're ready:
Email Address: Your full Roadrunner email address (e.g., [email protected] or [email protected]).
Password: The password associated with your Roadrunner email account.
Incoming Mail Server: Typically, this is pop-server.maine.rr.com for POP3 or mail.twc.com for IMAP.
Outgoing Mail Server: Usually smtp-server.maine.rr.com for SMTP.
Port Numbers: Commonly used port numbers are 110 for POP3, 143 for IMAP, and 587 for SMTP.
Having this information at hand will make the setup process smoother and faster.
Adding Roadrunner Email on a Computer
Setting up your Roadrunner email on a computer, whether it's a Windows PC or a Mac, involves configuring your email client with the correct settings. Here's how to do it:
For Windows (Outlook):
Open Outlook: Launch Outlook on your Windows computer.
Add Account: Go to File > Add Account.
Manual Setup: Select Manual setup or additional server types and click Next.
Choose Service: Select POP or IMAP and click Next.
Account Information: Enter your name, Roadrunner email address, and choose IMAP or POP3 as your account type.
Server Information:
Incoming Mail Server: pop-server.maine.rr.com (for POP3) or mail.twc.com (for IMAP).
Outgoing Mail Server: smtp-server.maine.rr.com.
Logon Information: Enter your Roadrunner email address and password.
More Settings: Click on More Settings and navigate to the Outgoing Server tab. Check My outgoing server (SMTP) requires authentication.
Advanced Settings: In the Advanced tab, enter the port numbers (110 for POP3, 143 for IMAP, 587 for SMTP).
Finish: Click OK, then Next, and finally Finish to complete the setup.
For Mac (Mail):
Open Mail: Launch the Mail app on your Mac.
Add Account: Go to Mail > Add Account.
Choose Provider: Select Other Mail Account and click Continue.
Account Information: Enter your name, Roadrunner email address, and password, then click Sign In.
Server Settings: Manually enter the incoming and outgoing mail server settings as mentioned above.
Finish: Click Done to complete the setup.
Adding Roadrunner Email on a Smartphone
Whether you have an iPhone or an Android device, adding a Roadrunner email account is straightforward. Here's how to do it for both platforms:
For iPhone:
Open Settings: Go to Settings on your iPhone.
Add Account: Scroll down and tap on Mail > Accounts > Add Account.
Choose Other: Select Other and then Add Mail Account.
Account Information: Enter your name, Roadrunner email address, password, and a description (e.g., "Roadrunner Email").
Server Settings: Enter the incoming and outgoing mail server settings.
Incoming Mail Server: pop-server.maine.rr.com (for POP3) or mail.twc.com (for IMAP).
Outgoing Mail Server: smtp-server.maine.rr.com.
Port Numbers: Use port 110 for POP3, 143 for IMAP, and 587 for SMTP.
Finish: Tap Save to complete the setup.
For Android:
Open Settings: Go to Settings on your Android device.
Add Account: Tap on Accounts > Add Account > Email.
Enter Email Information: Enter your Roadrunner email address and password.
Manual Setup: Select Manual Setup and choose IMAP or POP3.
Server Settings: Enter the incoming and outgoing mail server settings.
Incoming Mail Server: pop-server.maine.rr.com (for POP3) or mail.twc.com (for IMAP).
Outgoing Mail Server: smtp-server.maine.rr.com.
Port Numbers: Use port 110 for POP3, 143 for IMAP, and 587 for SMTP.
Finish: Tap Done to complete the setup.
Troubleshooting Common Issues
Sometimes, even with the correct settings, you might encounter issues while setting up your Roadrunner email account. Here are some common problems and their solutions:
Incorrect Password:
Double-check that you are entering the correct password. If you've forgotten it, you may need to reset it through the Spectrum (formerly Time Warner Cable) website.
Server Errors:
Ensure that you've entered the correct server addresses and port numbers. A small typo can cause a connection error.
Authentication Errors:
Make sure that the My outgoing server (SMTP) requires authentication option is checked in your email client's settings.
Connectivity Issues:
If you're unable to connect to the mail servers, check your internet connection. Sometimes, a poor connection can prevent the email client from verifying the server settings.
Conclusion
Adding a Roadrunner email account to your devices doesn't have to be a hassle. By following the steps outlined in this guide, you can ensure a smooth setup process. Remember to double-check all settings and information to avoid common issues. If you encounter any problems, refer to the troubleshooting section for solutions.
0 notes
Text
Essential Server Buying Guide for Small Businesses

As your small business grows beyond a handful of employees, it's likely time to consider investing in a server. The term "server" can refer to hardware, software, or the functionality of both, and choosing the right server for your business can be a daunting task. This guide will help you navigate your options and make an informed decision.
Understanding Your Needs
Before diving into the specifics, ask yourself the following questions to determine your server needs:
Are you buying for file sharing?
Will it be predominantly used for email?
Does your workforce need to connect remotely?
Is it going to be used for data backup?
How much space do you have available to accommodate the server?
Server Hardware and Functionality
At a hardware level, servers are similar to standard PCs but are designed for 24/7 operation and often include additional features like ECC memory and redundant components to ensure continuous operation. Key hardware components include:
CPU: The number of cores and clock speed determine the server's ability to handle multiple tasks.
Memory (RAM): More RAM allows for better performance, especially under heavy load.
Storage: Multiple bays for hard drives and options for RAID configurations ensure data redundancy and fast access.
Choosing the Right Server Type
File Servers
File servers or Network Attached Storage (NAS) are used for storing and sharing files across a network. Look for:
Multiple hot-swappable drive bays
Configurable hardware/software RAID options
Low-power CPU for efficient operation
Domain Controllers
Domain controllers manage user authentication and access levels. They are crucial for businesses with multiple users and devices. Look for:
Virtualization-capable CPU (any 64-bit CPU)
At least 4 GB of RAM
Database Servers
Database servers handle large volumes of data and user queries. They are essential for applications and websites built on a database layer. Look for:
Hard drives rated for fast writes
Large CPUs (12- or 16-core)
Backup 'slave' servers for read-only databases
Web Servers
Web servers host websites and use HTTP to present web pages. They often work with a database server. Look for:
Hardware redundancy (especially for e-commerce sites)
Increased RAM capacity for better performance
Email Servers
Email servers, such as Microsoft Exchange, use specific protocols (SMTP, POP3, IMAP) to send and receive messages. Dedicating hardware to this task is recommended for optimal operation. Look for:
Similar specifications as a file server
Application Servers
Application servers centralize applications within their native framework (Java, PHP, .NET, various flavors of .js), improving performance and reducing maintenance costs. Look for:
Enterprise-grade storage bays (SAS hard drives)
ECC RAM
Choosing the Right Form Factor
Servers come in various physical form factors, including tower, rackmount, and blade:
Tower: Resembling desktop computers, tower servers are suitable for small businesses needing one or two servers. They don't require additional mounting hardware but take up more space as you add more servers.
Rackmount: These servers are installed in a rack chassis, which can hold multiple servers in slots. They are ideal for businesses needing several servers in a consolidated space.
Blade: Blade servers are more space-efficient than rackmount servers but require careful cooling and a larger initial investment. They are suitable for larger server rooms.
Server Operating Systems
A server operating system (OS) is more advanced and stable than a desktop OS, supporting more RAM, efficient CPU usage, and a greater number of network connections. The OS enables the server to perform various roles, such as:
Mail server
File server
Domain controller
Web server
Application server
Administrators use the server OS to authenticate users, manage applications and file storage, set up permissions, and perform other administrative tasks.
Conclusion
Choosing the right server for your small business involves understanding your specific needs, selecting appropriate hardware, and deciding on the best form factor and operating system. By carefully considering these factors, you can ensure your server investment supports your business's growth and operational efficiency.
0 notes
Text
which of the following is not a vpn protocol
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
which of the following is not a vpn protocol
VPN protocols comparison
VPN protocols are the backbone of secure internet connections, allowing users to safeguard their data and privacy while browsing online. Understanding the differences between various VPN protocols is crucial in choosing the right one for your needs. Here's a comparison of some commonly used VPN protocols:
OpenVPN: Widely regarded as one of the most secure VPN protocols, OpenVPN is open-source and adaptable across different platforms. It utilizes OpenSSL encryption and supports various authentication methods, making it a popular choice for both individuals and businesses.
IPSec (Internet Protocol Security): IPSec operates at the network layer and can be used in two modes: Transport Mode and Tunnel Mode. It provides strong encryption and authentication, making it suitable for securing network communications. However, IPSec can be more complex to configure compared to other protocols.
L2TP/IPSec (Layer 2 Tunneling Protocol with IPSec): L2TP/IPSec combines the best features of L2TP and IPSec, offering both tunneling and encryption. While it provides good security, it may not be as fast as other protocols due to the double encapsulation process.
IKEv2 (Internet Key Exchange version 2): Known for its speed and stability, IKEv2 is commonly used on mobile devices. It supports mobility and seamless switching between networks, making it ideal for users who frequently switch between Wi-Fi and mobile data connections.
WireGuard: A relatively new protocol gaining popularity for its simplicity and high performance. WireGuard aims to improve upon existing VPN protocols by implementing modern cryptographic techniques and a streamlined codebase, resulting in faster speeds and lower resource usage.
When choosing a VPN protocol, consider factors such as security, speed, compatibility, and ease of use. Ultimately, the best protocol for you will depend on your specific requirements and priorities.
Identifying non-VPN protocols
Identifying Non-VPN Protocols: A Guide
In today's digital landscape, privacy and security are paramount concerns for internet users. While virtual private networks (VPNs) offer a reliable means of safeguarding online activities, it's essential to recognize non-VPN protocols that might compromise your data protection. Understanding these protocols empowers users to make informed decisions about their online security measures.
HTTP (Hypertext Transfer Protocol): HTTP is the foundation of data communication on the World Wide Web. However, it lacks encryption, making it vulnerable to interception by malicious entities. Websites that still rely solely on HTTP pose significant security risks, especially when handling sensitive information like passwords or financial details.
FTP (File Transfer Protocol): FTP is commonly used for transferring files between a client and server on a network. Like HTTP, FTP does not encrypt data during transmission, leaving it susceptible to eavesdropping and interception. This lack of encryption makes FTP connections inherently insecure, particularly for confidential file transfers.
Telnet: Telnet is a network protocol used for remote terminal access. Despite its widespread use in the past, Telnet transmits data, including login credentials, in plaintext, exposing it to potential interception. As a result, Telnet is considered highly insecure and is largely replaced by more secure alternatives like SSH (Secure Shell).
SMTP (Simple Mail Transfer Protocol): SMTP is used for sending email messages between servers. While it facilitates the exchange of emails, SMTP does not provide encryption for message content, making it susceptible to interception. This vulnerability underscores the importance of implementing additional security measures, such as end-to-end encryption or secure email protocols.
In conclusion, identifying non-VPN protocols is essential for maintaining robust cybersecurity practices. By recognizing the inherent security risks associated with these protocols, users can take proactive steps to mitigate potential threats and safeguard their online privacy. Utilizing secure alternatives and implementing encryption wherever possible are crucial steps in protecting sensitive data from unauthorized access.
Understanding VPN encryption methods
VPN encryption methods play a crucial role in ensuring the security and privacy of online communication. Understanding the different encryption protocols used by VPN services can help users make informed decisions when choosing the most suitable one for their needs.
Two common encryption protocols used by VPN services are SSL/TLS and IPsec. SSL/TLS, commonly used by websites for secure data transmission, creates an encrypted tunnel between the user's device and the VPN server. This encryption method is widely supported and offers strong security, making it ideal for safeguarding sensitive information.
On the other hand, IPsec operates at the network layer and encrypts the entire data packet. It ensures the confidentiality and integrity of data being transmitted over the network, making it a popular choice for securing corporate networks and remote access connections.
Another encryption protocol worth mentioning is OpenVPN, known for its open-source nature and robust security features. OpenVPN uses the OpenSSL library to provide a high level of encryption and authentication, making it a preferred option for users prioritizing security.
In conclusion, understanding VPN encryption methods is essential for maintaining online privacy and security. By choosing a VPN service that implements strong encryption protocols like SSL/TLS, IPsec, or OpenVPN, users can protect their sensitive data from potential threats and eavesdropping. It is recommended to select a VPN provider that offers a combination of advanced encryption methods to ensure a secure and private online experience.
Differentiating VPN and non-VPN protocols
In the realm of online privacy and security, understanding the distinction between VPN (Virtual Private Network) and non-VPN protocols is crucial. Both serve to safeguard your data, but they do so in different ways, catering to various needs and preferences.
VPN protocols, such as OpenVPN, IKEv2/IPSec, and WireGuard, encrypt your internet traffic, creating a secure tunnel between your device and the VPN server. This encryption ensures that your data remains confidential and protected from prying eyes, whether you're browsing the web, streaming content, or accessing sensitive information.
Non-VPN protocols, on the other hand, may not provide the same level of encryption and privacy as VPNs. Examples of non-VPN protocols include HTTP, FTP, and DNS. While these protocols are essential for basic internet functionality, they do not offer the same level of security as VPNs. For instance, HTTP transmits data in plain text, making it susceptible to interception by hackers or surveillance agencies.
One key difference between VPN and non-VPN protocols lies in their ability to anonymize your online activities. VPNs conceal your IP address by routing your internet traffic through remote servers, making it appear as though you're accessing the internet from a different location. This feature enhances your privacy and helps circumvent geo-restrictions and censorship.
In contrast, non-VPN protocols typically reveal your true IP address, leaving you vulnerable to tracking and monitoring by third parties. This lack of anonymity can compromise your online privacy and expose you to various risks, such as identity theft and targeted advertising.
Ultimately, choosing between VPN and non-VPN protocols depends on your specific needs and priorities. If privacy and security are paramount, opting for a reputable VPN service with robust encryption protocols is advisable. However, for basic internet browsing and data transfer, non-VPN protocols may suffice, albeit with less protection against potential threats.
Evaluating secure network communication protocols
When it comes to ensuring the security of network communication, evaluating the effectiveness of various protocols is crucial. Secure network communication protocols serve as the foundation for protecting sensitive data from unauthorized access, interception, and manipulation. Several factors should be considered when evaluating these protocols to determine their suitability for specific applications.
Firstly, encryption strength plays a significant role in assessing the security of a communication protocol. Protocols employing robust encryption algorithms, such as AES (Advanced Encryption Standard) with sufficient key lengths, offer better protection against eavesdropping and data tampering.
Secondly, authentication mechanisms are essential for verifying the identities of communicating parties. Protocols that incorporate strong authentication methods, such as digital certificates or biometric authentication, help prevent unauthorized access to network resources.
Moreover, the integrity of data transmission is vital in secure communication protocols. Techniques like message authentication codes (MACs) or digital signatures can ensure that data remains unaltered during transit, guarding against tampering or forgery attempts.
Additionally, protocols should provide adequate measures for key management and exchange. Secure key generation, distribution, and updating mechanisms are necessary to prevent unauthorized parties from deciphering encrypted data.
Furthermore, considerations must be made regarding protocol performance and scalability. While security is paramount, protocols should not significantly degrade network performance or hinder scalability as the network grows.
Lastly, compliance with industry standards and regulations, such as HIPAA for healthcare or PCI DSS for payment card industry, is essential for ensuring regulatory compliance and adherence to best practices in secure communication.
In conclusion, evaluating secure network communication protocols involves assessing encryption strength, authentication mechanisms, data integrity measures, key management, performance, scalability, and regulatory compliance. By carefully considering these factors, organizations can select the most suitable protocols to protect their sensitive data and maintain the security of their network communications.
0 notes
Text
does sip have to go over vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does sip have to go over vpn
SIP Protocol
The Session Initiation Protocol (SIP) is a communication protocol used in the field of telecommunications to establish, modify, and terminate sessions between two or more participants. SIP operates in a similar manner to HTTP and SMTP and is a foundation of Voice over Internet Protocol (VoIP) technology. It is widely utilized for voice and video calls, instant messaging, media distribution, and other real-time communication applications.
One of the key features of SIP is its ability to negotiate the parameters of a communication session, such as the media type, codec, and session duration. This flexibility allows for seamless communication between different devices and networks. SIP can be used in conjunction with other protocols like RTP (Real-time Transport Protocol) for transferring audio and video data during a session.
SIP follows a client-server architecture, where the user agent client (UAC) sends requests to the user agent server (UAS) to initiate actions like call setup or termination. SIP messages include requests like INVITE, ACK, BYE, and responses like 200 OK or 404 Not Found, which are crucial for establishing and managing sessions effectively.
Moreover, SIP is extensible and supports various authentication methods like digest authentication and Transport Layer Security (TLS) for securing communication channels. Its open architecture makes it compatible with different devices and services, driving its widespread adoption in the telecommunication industry.
In conclusion, SIP plays a vital role in enabling real-time communication over the internet and continues to evolve to meet the changing demands of modern communication systems. Its interoperability, scalability, and security features make it a versatile protocol for facilitating seamless and efficient communication.
VPN Tunneling
VPN tunneling is a technique used to create a secure and encrypted connection, or tunnel, between a user and a VPN server. This process helps protect user data from being intercepted by hackers, government agencies, or other malicious entities while using the internet.
There are several different types of VPN tunneling protocols, each offering unique features and levels of security. Some common tunneling protocols include OpenVPN, IPSec, and L2TP/IPsec. These protocols work by encapsulating the user's data within encrypted packets, which are then transmitted through the secure tunnel to the VPN server.
One of the main benefits of VPN tunneling is that it allows users to access the internet securely and privately, even when using public Wi-Fi networks. This is especially important for individuals who frequently connect to public Wi-Fi hotspots in cafes, airports, or hotels, as these networks are often prime targets for hackers looking to intercept sensitive information.
Additionally, VPN tunneling can help users bypass geo-restrictions and censorship imposed by governments or internet service providers. By connecting to a VPN server in a different location, users can mask their IP address and appear as though they are browsing the internet from a different country, allowing them to access region-locked content or websites.
Overall, VPN tunneling is an essential tool for maintaining online privacy, security, and freedom while browsing the internet. By encrypting data and creating a secure connection to a VPN server, users can enjoy a worry-free online experience without compromising their sensitive information.
Network Security
Network security is a crucial aspect of ensuring the safety and integrity of digital information. In this digital age, where information is constantly being shared and accessed across various networks, the importance of implementing effective network security measures cannot be overstated.
Network security encompasses various practices and technologies designed to protect the usability, integrity, and safety of a network and the data it contains. It involves the implementation of both hardware and software solutions to prevent unauthorized access, misuse, modification, or denial of a network and its resources.
One of the fundamental principles of network security is the concept of access control, which involves limiting access to authorized users and devices while blocking access to unauthorized ones. This is typically achieved through the use of firewalls, encryption, and secure authentication protocols.
Another key aspect of network security is the detection and prevention of malicious activities such as viruses, malware, and phishing attacks. This is often done through the use of intrusion detection systems (IDS) and intrusion prevention systems (IPS) that monitor network traffic for suspicious behavior and take action to prevent security breaches.
Regularly updating software, implementing strong passwords, and conducting security audits are essential practices to maintain network security. Additionally, educating users about best practices for safe online behavior is crucial in mitigating security risks.
In conclusion, network security is vital for protecting sensitive information and maintaining the integrity of digital networks. By implementing robust security measures and staying mindful of potential threats, organizations can safeguard their data and networks from unauthorized access and cyber attacks.
VoIP Communication
Voice over Internet Protocol (VoIP) is a technology that enables users to make voice calls using a broadband internet connection instead of a traditional phone line. This form of communication has gained popularity due to its cost-effectiveness and versatility.
One of the key benefits of VoIP communication is its cost efficiency. By utilizing the internet to transmit voice data, VoIP eliminates the need for separate phone lines, leading to significant cost savings for businesses and individuals. Additionally, long-distance calls made through VoIP are often much cheaper compared to traditional phone services.
Moreover, VoIP offers a wide range of features that enhance communication experiences. These include call forwarding, voicemail transcription, video conferencing, and virtual phone numbers. These features provide users with greater flexibility and control over their communication methods.
Furthermore, VoIP communication is highly scalable and can easily accommodate the changing needs of businesses. Whether an organization is a small startup or a large enterprise, VoIP systems can be tailored to suit the specific requirements of the business, making it a versatile solution for all types of users.
In conclusion, VoIP communication offers a cost-effective, feature-rich, and scalable solution for modern communication needs. Its ability to leverage the power of the internet for voice calls has revolutionized the way people communicate, making it an indispensable tool for businesses and individuals alike.
Data Encryption
Data encryption is a crucial aspect of cybersecurity, providing a layer of protection for sensitive information transmitted over networks or stored on devices. It involves the conversion of plain text into ciphertext, making it unreadable to unauthorized parties. This process ensures that even if data is intercepted, it remains unintelligible without the proper decryption key.
There are several encryption algorithms and methods used to secure data. One of the most commonly employed techniques is symmetric encryption, where the same key is used for both encryption and decryption. This method is efficient for securing large volumes of data but requires a secure channel for transmitting the encryption key.
Asymmetric encryption, on the other hand, uses a pair of keys – a public key for encryption and a private key for decryption. This method is widely used for secure communication over the internet, such as in SSL/TLS protocols for securing online transactions.
Data encryption plays a vital role in protecting sensitive information in various sectors, including finance, healthcare, and government. It ensures compliance with data protection regulations such as GDPR and HIPAA, safeguarding individuals' privacy rights and preventing data breaches.
However, encryption is not immune to vulnerabilities, and constant advancements in technology require regular updates to encryption protocols to stay ahead of potential threats. Additionally, the growing prevalence of quantum computing poses a new challenge to traditional encryption methods, spurring research into quantum-resistant encryption techniques.
In conclusion, data encryption is a fundamental component of cybersecurity, providing confidentiality, integrity, and authenticity to sensitive information. By implementing robust encryption protocols and staying informed about emerging threats, organizations can effectively safeguard their data against unauthorized access and cyber attacks.
0 notes
Text
What Is SMTP in WordPress? And How To Configure It?
SMTP (Simple Mail Transfer Protocol) for WordPress is a method used to send emails from your WordPress site. By default, WordPress uses the PHP mail function to send emails, but SMTP provides a more reliable and secure way to send emails.
It ensures that your emails are delivered successfully to the recipients' inbox, rather than being marked as spam. Setting up SMTP for WordPress involves configuring your WordPress site to use an SMTP server to send emails.
What Is SMTP In WordPress?
SMTP (Simple Mail Transfer Protocol) in WordPress refers to the method used for sending emails from your WordPress website. By default, WordPress uses the built-in PHP mail function to send emails, but SMTP provides a more reliable and secure alternative.
SMTP ensures that your emails are delivered successfully to recipients' inboxes and helps prevent them from being marked as spam. With SMTP configured in WordPress, emails are sent through an external SMTP server, typically provided by your web hosting provider or a third-party email service.
This setup allows you to specify authentication credentials, such as a username and password, ensuring that your emails are authenticated and trusted by email providers.
How To Configure SMTP In WordPress?
Configuring SMTP in WordPress involves several steps. Here's a general guide:
https://jpcdn.it/img/3fa5ee365d1c835a3a542dab41533f3e.jpg
For more information or buying fast and secure hosting visit the www.ozoweb.com, Ozoweb provides various services like Linux Shared Web Hosting, Domain Registration, VPS, and Dedicated Servers. They focus on offering these services at prices that are affordable for everyone. Their goal is to make sure their prices are unbeatable while still providing high-quality hosting services and products that fit their customers' needs and budgets.
#OZOHosting#lowest price hosting in india#Cheap web hosting jaipur#cheap shared web hosting india#free web hosting india#affordable linux web hosting india
0 notes
Text
does vpn interfere with email
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does vpn interfere with email
VPN email compatibility
VPN email compatibility refers to the ability of a Virtual Private Network (VPN) to work seamlessly with various email services and protocols. When using a VPN to secure your internet connection, it is essential to ensure that your email setup is fully compatible to avoid any potential issues or security risks.
Many email clients and services support the use of VPNs, allowing users to send and receive emails securely and privately. VPNs encrypt internet traffic, including email data, protecting it from potential eavesdroppers and hackers. This encryption is vital for maintaining the confidentiality of sensitive information shared via email.
Some email protocols, such as POP3, IMAP, and SMTP, may require specific configurations to work correctly with a VPN. It is essential to verify that your VPN service supports these protocols and that your email client is configured to use them securely over the VPN connection.
Additionally, some email providers may block or restrict access when detecting connections from known VPN servers to prevent spam or unauthorized access. In such cases, users may need to switch to a different VPN server or contact their email provider for assistance in resolving the issue.
Overall, ensuring VPN email compatibility is crucial for maintaining the security and privacy of your email communications. By choosing a reputable VPN service and configuring your email setup properly, you can enjoy the benefits of encrypted communication while keeping your sensitive information safe from prying eyes.
Email security risks VPN
Email security is a critical concern for businesses and individuals alike, with the potential for sensitive information to be compromised through email communication. One way to enhance email security is by using a Virtual Private Network (VPN) to encrypt your email traffic and protect it from potential risks.
VPN offers a secure and private connection between your device and the internet, ensuring that all data transmitted through your email is encrypted. This encryption significantly reduces the risk of interception and unauthorized access to your email content. By masking your IP address and encrypting your connection, VPNs make it extremely difficult for hackers to infiltrate your email conversations and steal sensitive information.
In addition to encryption, VPNs can also help bypass geo-restrictions and censorship, allowing you to access your email securely from anywhere in the world. This is particularly beneficial for remote workers or frequent travelers who rely on email communication for work purposes.
However, it is essential to choose a reliable and reputable VPN provider to ensure maximum security for your email communication. Look for VPN services that offer strong encryption protocols, a no-logs policy, and a kill switch feature to safeguard your data in case of connection drops.
In conclusion, utilizing a VPN for email communication can effectively mitigate security risks and enhance the privacy of your sensitive information. By encrypting your email traffic and securing your connection, VPNs provide an added layer of protection against potential cyber threats and unauthorized access to your emails.
VPN email server interference
VPN email server interference can be a common issue that individuals or organizations may encounter when trying to access or send emails while connected to a Virtual Private Network (VPN). When a VPN is active, the user's internet traffic is encrypted and routed through a secure server, which can sometimes cause disruptions in accessing email services.
One of the main reasons for VPN email server interference is the IP address conflict. Email servers may detect the IP address provided by the VPN as suspicious or potentially harmful, leading to blocked access or restrictions on sending emails. Additionally, some email providers have security measures in place that flag connections coming from VPN servers as potential threats, further complicating the situation.
To resolve VPN email server interference, users can try a few troubleshooting steps. First, switching to a different VPN server location may help bypass the restrictions imposed by the email server. Users can also temporarily disconnect from the VPN while accessing their emails and then reconnect afterwards for other online activities.
It is important to note that VPNs are essential for maintaining online privacy and security, especially when accessing public Wi-Fi networks or sensitive information. However, users should be aware of the potential challenges that VPN email server interference can pose and be prepared to troubleshoot effectively when faced with such issues.
VPN impact on email delivery
VPN, or Virtual Private Network, can have a significant impact on email delivery. When using a VPN, your internet traffic is routed through a remote server, masking your actual IP address and encrypting your data. While VPNs are beneficial for privacy and security reasons, they can sometimes cause issues with sending and receiving emails.
One common problem that VPN users may encounter is email deliverability issues. Some email servers may flag emails sent from VPN IP addresses as suspicious or spam due to the nature of VPNs being used to mask identities. This can result in emails being blocked or sent to the recipient's spam folder, leading to potential communication breakdowns.
Additionally, VPNs can also impact email deliverability by causing delays in email transmission. The rerouting of internet traffic through remote servers can slow down the sending and receiving of emails, especially if the VPN server is located far away from your actual location. This delay can be frustrating, especially in time-sensitive situations where prompt email delivery is crucial.
To mitigate these issues, VPN users can try switching to a different server location within the VPN provider's network. Choosing a server that is closer to your actual location may improve email deliverability by reducing latency and minimizing the chances of emails being flagged as suspicious.
In conclusion, while VPNs offer valuable privacy and security benefits, they can potentially impact email delivery by triggering spam filters and causing transmission delays. By being aware of these potential issues and taking proactive steps to optimize VPN settings, users can minimize disruptions to their email communication.
VPN blocking email access
Many internet users rely on Virtual Private Networks (VPNs) to protect their online privacy and security. However, sometimes using a VPN can lead to certain issues, such as email access being blocked. This can be frustrating for individuals who need to check their emails regularly for work or personal reasons.
VPN blocking email access can occur due to various reasons. One common cause is the security measures implemented by email providers to prevent unauthorized access. When a user attempts to access their email account through a VPN, the provider may flag it as a suspicious login attempt and block access to the account. Additionally, some VPN servers may be blacklisted by email providers due to malicious activities originating from those servers.
To avoid VPN blocking email access, users can try the following solutions:
Switch VPN servers: If a particular VPN server is being blocked by the email provider, switching to a different server location may help resolve the issue.
Whitelist the email provider: Some VPN services allow users to whitelist certain websites or services, including email providers. By whitelisting the email provider's domain, users can ensure uninterrupted access to their emails.
Disable VPN when accessing emails: As a temporary solution, users can disable their VPN connection while checking their emails to bypass any restrictions imposed by the provider.
Overall, VPN blocking email access is a common issue that can be addressed by troubleshooting and adjusting VPN settings accordingly. By understanding the underlying causes and implementing the suggested solutions, users can ensure seamless access to their email accounts while using a VPN for enhanced security and privacy.
0 notes
Text
An in-depth look at the magic of communication protocols in networking
Long time no see! It's time to share again~ Communication protocols are the cornerstone of network communication, they determine how data is transmitted and the rules for processing in the network. Next, let's take a look at the specific applications of communication protocols in network communication!
1. Internet communication
Internet communication is one of the most widely used application scenarios. Here are some common Internet communication protocols and their applications.
·HTTP/HTTPS: Used to transfer web pages between a browser and a server. HTTPS adds SSL/TLS encryption to HTTP to ensure the security of data transmission.
·FTP: Used to transfer files between client and server, commonly used for website updates and file sharing.
·SMTP/IMAP/POP3: Used for email transmission and reception, ensuring the transmission of emails between different mail servers and clients.

2. LAN communication
In a business or home network, LAN communication protocols ensure efficient communication between devices.
·Ethernet: the most common wired LAN protocol ensures the transmission of data packets between network devices.
·Wi-Fi: Wireless LAN protocol that allows devices to connect to the network via wireless signals for convenient mobile office and home network connectivity.
·DHCP: Dynamic Host Configuration Protocol, automatically assigns IP addresses to devices in the network, simplifying network management.

3. Mobile communication
Mobile communication protocols ensure global communication for cell phones and other mobile devices.
·GSM/CDMA/LTE/5G: These are different generations of mobile communication protocols, from the early 2G to the current 5G, each generation of protocols has improved data transfer speed and communication quality.
·VoLTE: High-definition voice calls over LTE networks have improved the user's call experience.

4. Internet of Things (IoT) communication
IoT devices are interconnected through various protocols, and the following are some common IoT communication protocols.
·MQTT: Lightweight publish/subscribe messaging protocol for device communication in low-bandwidth, unstable network environments.
·CoAP: restricted application protocol, designed for simple electronic devices, provides efficient device control and data transfer.
·Zigbee/Z-Wave: low-power wireless communication protocol widely used in smart home devices such as smart light bulbs, thermostats and security systems.
Choosing the right communication protocol can significantly improve network performance and user experience. I hope today's sharing is helpful.711Proxy provides pure residential IPs to help you increase network speed!
0 notes
Text
can't send emails when connected by avg vpn network
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can't send emails when connected by avg vpn network
AVG VPN email sending issue
When it comes to using AVG VPN for secure internet browsing, users may sometimes encounter issues with sending emails while connected to the VPN. This can be frustrating, but there are several reasons why this problem may occur.
One common reason for email sending issues while using AVG VPN is that the VPN server's IP address may be blacklisted by the email server. Email servers maintain blacklists of IP addresses known for spamming or other malicious activities. When you send an email through a blacklisted IP address, the email server may reject it. In this case, you may need to contact the email server administrator to remove the IP address from the blacklist.
Another possible reason for email sending issues could be the VPN's encryption settings. Some email servers may require specific encryption protocols to send emails securely. If the VPN's encryption settings do not match the server requirements, the email sending process may fail. In such cases, adjusting the VPN encryption settings or contacting the email server administrator for guidance can help resolve the issue.
Additionally, network congestion or connectivity issues while using AVG VPN could also impact email sending. Slow or unstable internet connections can lead to emails getting stuck in the outbox or not being sent at all. Ensuring a stable internet connection and choosing a VPN server with optimal performance can improve email sending reliability.
In conclusion, email sending issues while using AVG VPN can be caused by various factors such as blacklisted IP addresses, encryption settings, or network connectivity issues. By troubleshooting these aspects and seeking assistance when needed, users can overcome these challenges and enjoy secure internet browsing with AVG VPN.
Email sending problem with AVG VPN
If you are facing email sending problems while using AVG VPN, there could be several reasons causing this issue. One of the common reasons is the VPN server you are connected to might be blocking outgoing email traffic.
When you are using a VPN, your internet traffic is routed through the VPN server before reaching its destination. Some VPN providers restrict certain types of traffic, including email traffic, to prevent spamming and other malicious activities. If the VPN server is blocking outgoing email traffic, you won't be able to send emails while connected to the VPN.
Another reason for email sending problems with AVG VPN could be misconfigured email settings. When you are connected to a VPN, your IP address changes, which might affect how your email client sends outgoing mail. It is essential to check and update your email settings to ensure they are compatible with the VPN connection.
To troubleshoot the issue, try switching to a different VPN server or contact AVG customer support for assistance. Additionally, you can try disconnecting from the VPN and sending emails to see if the problem persists without the VPN connection.
By understanding the common causes of email sending problems with AVG VPN, you can take the necessary steps to resolve the issue and ensure seamless communication while using a VPN service.
Troubleshooting AVG VPN email sending
When troubleshooting issues with sending emails while using AVG VPN, there are several steps you can take to potentially resolve the issue.
Check VPN Connection: Ensure that your VPN connection is stable and active. Sometimes a weak or unstable connection can cause problems with sending emails.
Verify Email Settings: Double-check your email account settings to ensure that they are configured correctly. Make sure that the SMTP (Simple Mail Transfer Protocol) server settings are accurate.
Disable VPN Temporarily: Temporarily disable the VPN and try sending an email. If the email goes through without the VPN, it may indicate an issue with the VPN configuration.
Change VPN Server: Switching to a different VPN server can sometimes help resolve connectivity issues. Try connecting to a different server and then attempt to send the email.
Update AVG VPN: Ensure that your AVG VPN software is up to date. Updates often include bug fixes and improvements that could potentially resolve email sending issues.
Contact Support: If the problem persists, reach out to AVG VPN support for further assistance. They may be able to provide specific guidance or troubleshooting steps tailored to your situation.
By following these troubleshooting steps, you may be able to identify and resolve the issues preventing you from sending emails while using AVG VPN. Remember to approach the process systematically and be patient as you work towards a solution.
AVG VPN network email delivery failure
Title: Troubleshooting AVG VPN Network Email Delivery Failure
In today's interconnected world, email communication plays a pivotal role in both personal and professional spheres. However, encountering email delivery issues can be frustrating, especially when using a VPN service like AVG VPN. When emails fail to reach their intended recipients despite being sent through AVG VPN's network, several factors could be at play. Understanding these factors and implementing appropriate troubleshooting steps is essential to resolve the issue effectively.
One common reason for email delivery failure when using AVG VPN is network congestion or instability. VPNs route internet traffic through their servers, which can sometimes lead to delays or interruptions in email transmission. Additionally, certain VPN configurations or server issues may result in emails being blocked or filtered by spam filters, particularly if the VPN's IP addresses are flagged as suspicious or associated with spamming activities.
Another possible cause of email delivery failure is misconfiguration of email client settings or firewall settings. If the email client is not properly configured to work with the VPN or if firewall rules are blocking outgoing email traffic, emails may fail to be delivered successfully.
To troubleshoot email delivery issues when using AVG VPN, users can take several steps. First, they should ensure that their internet connection is stable and that AVG VPN is functioning correctly. Users should also verify that their email client settings are configured to work with the VPN and that firewall settings are not blocking outgoing email traffic.
If email delivery issues persist, users may need to contact AVG VPN support for further assistance. Support technicians can help diagnose the problem and provide guidance on resolving any underlying issues affecting email delivery.
In conclusion, encountering email delivery failure when using AVG VPN can be frustrating, but understanding the potential causes and implementing appropriate troubleshooting steps can help resolve the issue efficiently. By addressing network issues, verifying email client settings, and seeking assistance from support professionals if needed, users can ensure reliable email communication while using AVG VPN.
Resolving email sending errors with AVG VPN
Email sending errors can be frustrating to deal with, especially when trying to send important messages or documents. One common cause of email sending errors can be related to the use of a VPN, such as AVG VPN. AVG VPN is designed to help protect your online privacy and security by encrypting your internet connection. However, sometimes the use of a VPN can interfere with the sending of emails.
If you are experiencing email sending errors while using AVG VPN, there are several steps you can take to resolve the issue. Firstly, check your VPN settings to ensure that the VPN is not blocking the outgoing mail server. You may need to whitelist the email server in the VPN settings to allow outgoing messages to be sent successfully.
Another troubleshooting step is to switch to a different VPN server within AVG VPN. Sometimes, the server you are connected to may be experiencing issues that are affecting the sending of emails. By switching to a different server, you may be able to resolve the email sending errors.
Additionally, you can try temporarily disabling the VPN while sending emails to see if the issue is resolved. If you are able to send emails without the VPN enabled, there may be settings within the VPN that need to be adjusted to allow for seamless email sending.
Overall, resolving email sending errors with AVG VPN may require some troubleshooting and adjustments to your VPN settings. By following these steps, you can hopefully overcome the email sending errors and ensure that your messages are delivered successfully.
0 notes
Text
can vpn interfere with email sending
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can vpn interfere with email sending
VPN email delivery issues
Email delivery issues can be frustrating, especially when using a VPN (Virtual Private Network). VPNs can sometimes affect the delivery of emails due to the way they route internet traffic.
When you send an email while connected to a VPN, the VPN server acts as an intermediary between your device and the email server. This extra step in the process can sometimes lead to delays or failed deliveries. Email providers may also flag emails sent through VPNs as potentially suspicious, leading to them being marked as spam or not being delivered at all.
One common reason for email delivery issues when using a VPN is IP blacklisting. Some VPN servers may have IP addresses that are blacklisted by email providers due to previous misuse, leading to emails being blocked or filtered out.
To mitigate VPN email delivery issues, you can try switching to a different VPN server or disconnecting from the VPN before sending important emails. Additionally, you can contact your VPN provider to see if they offer dedicated IP addresses that are less likely to be blacklisted.
Overall, while VPNs are valuable tools for privacy and security online, they can sometimes impact email delivery. By understanding the potential issues and taking steps to address them, you can ensure that your emails reach their intended recipients successfully.
VPN SMTP blocking
Title: Understanding VPN SMTP Blocking: Causes and Solutions
In today's digital landscape, Virtual Private Networks (VPNs) are widely utilized for securing online activities, ensuring privacy, and bypassing geo-restrictions. However, users often encounter issues with sending emails through SMTP (Simple Mail Transfer Protocol) while connected to a VPN. This phenomenon, known as VPN SMTP blocking, can be frustrating and hinder effective communication. Understanding the causes and solutions to this problem is crucial for VPN users.
Several factors contribute to VPN SMTP blocking. Firstly, some VPN providers implement restrictions on SMTP traffic to prevent spamming and abuse. Additionally, SMTP servers may blacklist IP addresses associated with VPNs due to past malicious activities or suspicious behavior. Moreover, network congestion and routing issues within the VPN infrastructure can disrupt SMTP connections.
To overcome VPN SMTP blocking, users can employ various strategies. One approach is to switch to a VPN provider that offers dedicated SMTP servers or SMTP relay services. These services typically bypass SMTP restrictions, ensuring reliable email delivery. Additionally, configuring the VPN to use a specific server or protocol that is not blocked by SMTP filters can mitigate the issue.
Furthermore, users can try using alternative SMTP ports, such as 587 or 465, which are less likely to be blocked by VPNs or ISPs. Additionally, whitelisting the SMTP server's IP address within the VPN settings or contacting the VPN provider's support for assistance may resolve the blocking issue.
In conclusion, VPN SMTP blocking poses challenges for users seeking to send emails securely and efficiently. By understanding the underlying causes and implementing appropriate solutions, individuals can mitigate these obstacles and ensure seamless SMTP communication while utilizing VPN services.
VPN email server conflicts
VPN email server conflicts can arise when a Virtual Private Network (VPN) is not configured properly to work seamlessly with an email server. VPNs are commonly used to enhance online security and privacy by encrypting internet traffic. However, this can sometimes cause issues with accessing email servers due to the way VPNs route traffic.
One common problem is when the VPN connection is blocking the necessary ports required for email server communication. The VPN may also use servers that are located in different regions, causing delays in data transmission between the user's device and the email server. In some cases, the VPN's encryption protocols may not be compatible with the email server's security settings, leading to authentication failures.
To resolve VPN email server conflicts, users can start by ensuring that the VPN is properly configured to allow email traffic. This may involve adjusting firewall settings, enabling specific ports, or whitelisting the email server's IP address. Users can also try connecting to a different VPN server that is geographically closer to the email server to improve connection speeds.
Additionally, users can reach out to their VPN provider's customer support for assistance in troubleshooting email server conflicts. Providers may offer guidance on configuring the VPN settings to work cohesively with email servers. It is crucial to address these conflicts promptly to avoid disruptions in accessing and sending emails securely while using a VPN.
VPN email sending problems
Title: Troubleshooting VPN Email Sending Issues: Common Causes and Solutions
Virtual Private Networks (VPNs) are essential tools for ensuring online privacy and security. However, while VPNs offer numerous benefits, they can sometimes cause complications when it comes to sending emails. Understanding the root causes of VPN email sending problems and implementing effective solutions is crucial for uninterrupted communication.
One of the primary reasons behind VPN-related email sending issues is IP address blacklisting. Some email providers employ stringent security measures and may block emails originating from IP addresses associated with VPNs due to potential spam or malicious activity. To mitigate this problem, users can switch to a different VPN server or contact their VPN service provider to request a clean IP address.
Another common issue arises from VPN connection instability. Fluctuating network connections can disrupt the email sending process, leading to failed deliveries or delays. Users experiencing this problem should try connecting to a more stable network or troubleshoot their VPN settings to ensure a consistent connection.
Moreover, VPN configurations may conflict with email server settings, resulting in authentication errors or SMTP (Simple Mail Transfer Protocol) connection issues. To resolve this, users should double-check their VPN and email client settings to ensure compatibility. Adjusting VPN protocols or using alternative email ports can also help overcome such obstacles.
Additionally, some VPN providers impose restrictions on outgoing email traffic to prevent abuse or spamming activities. Users encountering sending limitations should refer to their VPN provider's terms of service and consider upgrading to a premium plan or utilizing dedicated email services for sending bulk emails.
In conclusion, while VPNs offer invaluable protection, they can occasionally impede email sending functionality. By identifying and addressing common issues such as IP blacklisting, connection instability, configuration conflicts, and sending limitations, users can optimize their VPN experience and ensure seamless email communication.
VPN and outbound email troubleshooting
Title: Troubleshooting Outbound Email Issues with VPN: A Comprehensive Guide
In today's interconnected world, Virtual Private Networks (VPNs) have become indispensable tools for ensuring online privacy and security. However, their usage can sometimes lead to unexpected challenges, particularly when it comes to outbound email communication. In this article, we'll explore common issues that arise when sending emails through a VPN and provide practical troubleshooting tips to overcome them.
One of the primary issues users encounter when sending emails via a VPN is being flagged as spam or experiencing delivery failures. This occurs because many email service providers employ sophisticated algorithms to detect and prevent spam, and the use of a VPN can trigger these systems due to changes in IP addresses and geolocations.
To address this issue, start by verifying that your VPN connection is stable and properly configured. Ensure that you're using a reputable VPN service with servers located in regions that align with your usual email activity. Additionally, consider using dedicated IP addresses offered by some VPN providers to minimize the likelihood of being flagged as suspicious.
Another common problem is encountering restrictions imposed by email providers or network administrators. Some email services may block or throttle outgoing emails from VPN IP addresses to prevent abuse or spamming. In such cases, contacting your email provider's support team to whitelist your VPN IP address or exploring alternative methods, such as using a different email server or SMTP relay, can often resolve the issue.
Furthermore, it's essential to check your VPN settings for any features that might interfere with email communication, such as aggressive encryption protocols or IP blacklisting. Adjusting these settings or temporarily disabling the VPN while sending emails may help troubleshoot connectivity issues.
In conclusion, while VPNs offer invaluable benefits for online security and privacy, they can occasionally pose challenges when it comes to outbound email communication. By following the troubleshooting tips outlined in this guide and staying proactive in managing your VPN settings, you can ensure smooth and reliable email delivery even while using a VPN.
0 notes