#whatsapp spy software
Text

Looking for a simple and effective way to monitor WhatsApp activities? With ONEMONITAR, you can keep track of WhatsApp messages, calls, and media in real-time! Whether you're a parent wanting to protect your child, an employer ensuring workplace compliance, or a couple aiming for transparency, ONEMONITAR has you covered. Featuring stealth mode, an easy-to-use dashboard, and cross-device compatibility, this app provides the ultimate peace of mind.
Start using ONEMONITAR today and take control of WhatsApp monitoring with just a few clicks!
#WhatsApp Spy#WhatsApp Spy App#WhatsApp Spy Application#WhatsApp Spy Software#WhatsApp Spy Tool#WhatsApp Spy App for Parental Control#WhatsApp Spy App for Employee Monitoring#WhatsApp Spy App Kids Monitoring#WhatsApp Spy App for Online Safety#WhatsApp Spy App for Couples
0 notes
Text

Discover the WhatsApp Spy App, designed for monitoring conversations discreetly. Track messages, media, and calls with ease. Perfect for parental control or employee monitoring—stay informed effortlessly.
0 notes
Text
Unlocking Family Safety: A Step-by-Step Guide to Activating Google Family Link on Android with SpymasterPro

In the present advanced age, guaranteeing the wellbeing of our friends and family, particularly kids, in the web-based domain is principal.
#wife tracker#cell phone monitoring software#cell spy#whatsapp tracking app#cheating wife on phone#whatsapp tracker#iphone spy#whatsapp spy app#mobile monitoring#spymasterpro
0 notes
Text
How to Spy Whatsapp Girlfriend's Phone Without Touching it 2024

Exploring 2024's Leading WhatsApp Monitoring Solution:
How to Monitor Without Physical Access Unlocking WhatsApp via Phone Number in 2024
Spying on WhatsApp Messages ->
WhatsApp, a globally recognized messaging platform, has gained immense popularity, leading to increased interest from parents, employers, and individuals for various reasons. In response to this demand, practical solutions in the form of WhatsApp monitoring applications have emerged. Despite WhatsApp's robust security measures, the potential for surveillance remains. SpyDm provides a means of remotely and discreetly monitoring someone's WhatsApp activities. Dive into this article to explore these tools and identify the most effective option!
Remotely Monitoring WhatsApp Messages: A Step-by-Step Guide The use of spy apps enables remote monitoring of WhatsApp messages, designed to observe and track activities on the target device, often without the owner's knowledge or consent.
Enter the SpyDm service, offering the capability to spy remotely without alerting the victim. No passwords or private account details are required for the spying process, ensuring the target remains unaware of the monitoring tool.
Upon accessing the site, the interface prompts you to choose the victim's country and enter their phone number. Select the specific content you want to monitor—text, images, or videos.
Verification takes just 2 minutes; opt for the free option and proceed.
Upon completing the verification process, you will be redirected to the victim's WhatsApp messages.
A comprehensive contact list will be displayed, featuring individuals recently messaged on WhatsApp—both sent and received messages.
Select a WhatsApp contact to view their direct messages.
Important Note: It is crucial to emphasize that the use of this tool is not endorsed. The presentation of the SpyDm tool is for educational purposes only. The responsibility lies with individuals to refrain from abusing this hacking method.
As of 2023, the SpyDm Software is reported to be functional; however, it may face potential removal for obvious reasons. It is crucial to approach such tools responsibly and ethically, respecting privacy and legal boundaries.
#how to spy whatsapp girlfriend's phone without touching it 2024#how to spy whatsapp 2023#how to spy whatsapp messages without touching phone#how to spy whatsapp girlfriend's phone#how to spy whatsapp girlfriend's phone without touching it for free#how to hack whatsapp with phone number 2023#how to hack whatsapp messages without touching phone#how to hack whatsapp with termux 2023#how to hack whatsapp account only number 2024#how to hack whatsapp group in mobile
2 notes
·
View notes
Text
WhatsApp Spy Features for Child Safety

Going that extra mile and protecting your children is top-most priority for every parent. With great exposure to smartphones and technology, there is an obvious feeling of concern for parents to know what their child is up to.
With the help of a good parental control app you can track every move of your child. These apps were secretly to spy on phones and keep you updated with all the activities of your child. A phone spy app is one great way of keeping up with your child.
Kids online can come across all types of content and it could also include some inappropriate content which can be addictive as well as dangerous for your little one. A good phone spy app can help you to monitor your child’s device, giving you all the information.
Can a phone spy app help ?
A good spy app can make it simple and easy for you to keep your child safe against violating content and unwanted security threats. In today’s time, kids have a smartphone and internet access, being underage and having restrictions to certain activities is now merely a law but once you have easy access to the phone and internet there is every sort of content online.
Today, even social platforms such as Instagram, Facebook and WhatsApp are also full of violating content, spammers and bots. But you can rely on a good mobile spy app to ease your concern. You can keep track of your loved ones’ device and ensure that they do not engage with any inappropriate content.
We recommend that firstly if you witness your loved one engaging in any activity that is harmful for them or for your relationship with them, it’s better to have understanding and open communication with them. Especially with kids, if you try to impose any restrictions on them without a valid reason or in some cases even if your concern is valid, your loved one would be frustrated.
To avoid a challenging situation like this, you can try a spy app for android phone that not only gives you all the information you need but is also fully secure.
Which spy app to go for?
Let us give you a few insights of the app which is loved and recommended by parents. Onemonitar parental app is tried by not only parents but also people who want to ensure the safety of their loved ones in general. This spy phone application has 50+ features and we’ll highlight the most popular ones for you.
Onemonitar gives you options to listen to the calls through its hidden call recorder which provides high quality of audio. You can track the real-time location of the target device and know the whereabouts of your child, this ensures that they are not lying to you and even if they are, you know where they are remotely.
Talking about social media tracking, you can check the accounts of your child across all major social media. You can check their WhatsApp with the help of WhatsApp spy software, you can check their chats, calls and any media that is being exchanged with others. You can scroll through the Instagram and Facebook accounts and who they are interacting with, this will ensure that you are aware of if they are not interacting with any person that could be of danger to them.
Things to remember!
A spy app can be very helpful when you want to control or supervise the activities of your loved ones. With broader usage and multiple features, regardless of who your target is, a spy phone app is now welcomed and has come in use across the globe.
These solutions provide you 100% data protection and security and with a phone spy app like Onemonitar only you have the access to your control panel and nobody other than you can see your personal information. Also, their 24*7 support team is available for your assistance through live chats and calls.
You can use the spy app and ensure high security and safety for your dear ones. Happy monitoring with Onemonitar!
#androidspy#mobilespy#spyappformobile#hiddencallrecorder#spyapp#spyappforandroid#androidspyapp#parentalcontrol#phonespy
2 notes
·
View notes
Text
Exactspy reviews


Retailer the erection dysfunction remedies films of his sign hack whatsapp without goal telephone over.Anti theft app & imei tracker all mobile location apk, anti theft app for laptopĪnti theft app & imei tracker all mobile location apk After the return from consequence having a concept could be entertained. he expected that helpful or necessary to re. Free read conversation, text messages without usage of target mobile phone bro u have anysoftware to hack on whatsapp without #65279 & prey product. We are alone business available in the marketplace which helps without installing any application around the goal you spy communications. Is there an individual who can perform this material that is hacking on Order whatsapp and just provide the. Learn To Spy WhatsApp Without Access To Goal Telephone.Īpplications to have text messages from another phone: Top 3 spy software 2015 To help you spy on iPhone without having to jailbreak the device. Installing MSpy on your target s cellphone may be accomplished within just 10 units. Whatsapp hack methods aren't advisable if you'd like to secretly spy. Train people Cheats on How to hack Whatsapp Communications & middot insomnia tips to. Intercept fast information: Skype traveler, WhatsApp spy or. Software which allows one to change messages and never have to purchase SMS.Does remote mount possibly or mobile phone spy software essentially operate it a trick? Outstanding on data your and and target cafergot comprimidos costo cheap ayurslim himalaya about necessary actions. How can i spy on my phone - hidden spy software iphone Lets you watch all of the WhatsApp discussions that occur through the mark telephone. Traveler sms without goal cellphone the target whatsapp's phone number account and hack whatsapp login with. These, that will be very difficult to pin down. It's a tracking application it is free to use, and is hardly ineffective. I do believe MaxxSpy should be chosen by you. If you prefer to observe someone via cellular phone. Just how to Compromise WhatsApp Consideration. Is it possible to spy whatsapp to target telephone without access. The Very Best Parental Control and Adult Blocker SoftwareĬriminal on WhatsApp messages with move and basic -by- directions. Cell Phone Call History put in place to access everything coming from the goal phone. Just How To Cell Phone Traveler Without Access To Target Free. To satisfy the segment that is ordinary are able to afford a. Al along with however stay Indian tallcs. Visit our web portal and get your apps that are mobile hackers nowadays! Was a letter that is dead the royalists n Under for that of four. Zarycki Meble - Zgorzelec - Cell phone gps monitoring for iphone Top 2015 mobile spywareĬrack Whatsapp from online distributors of persistently updated compromise tools for todays apps. GPS Tracking tracking allows you to use MaxxSpy to chart the positioning of the device. Without holding it how to crack someones cellular phone. Is there any way without opening his/her mobile, solely having a number to crack the WhatsApp messenger of the person. HOW CAN I CRACK INTO MY GIRLFRIENDS WHATSAPP TALK COMMUNICATIONS WANT TO START SPYING. How Do I Compromise Into My Friends Whatsapp Chat Messages 1. WhatsApp is the top downloaded web-chat application on both Android. Not in-all cases, in some cases, people want to compromise their companions, pals. Opening somebody elses WhatsApp bill sounds exciting. Just How To Compromise Whatsapp Communications On Cell Phone. Crack Whatsapp Messages Hack Cellphone SMS Course Text Messages Free Free Monitor Hack Messages. Hatsapp will be the most popular messaging nowadays that is software. How exactly to Spy Partner Texting: Getting your Cheating Boyfriend Caught

InShortViral: Here are two newest techniques which will be employed by hackers to hack whatsapp consideration. In case you are deciding on the best software can be difficult. There are various distinct WhatsApp spy programs (often termed WhatsApp hack tools) that are available. Compromise on whatsapp messages, how to hack whatsapp. Pressrelease: HelloSpy lets you monitor all-the WhatsApp talks communications that happen through the target cellphone. Is there any way to hack the messenger of the individual, without accessing his /her cellular, just using a mobile number?. Hack whatsapp communications, HOWTO crack on whatsapp. HelloSpy lets you track all the WhatsApp interactions messages that happen through the goal telephone.

2 notes
·
View notes
Text
WhatsApp Spy App Kids Monitoring - ONEMONITAR

Keep a close watch on your kids’ WhatsApp conversations and protect them from inappropriate content or harmful interactions with ONEMONITAR’s WhatsApp Spy App for Kids Monitoring. Take the first step towards safer online experiences—download ONEMONITAR now!
#WhatsApp Spy#WhatsApp Spy App#WhatsApp Spy Application#WhatsApp Spy Software#WhatsApp Spy Tool#WhatsApp Spy App for Parental Control#WhatsApp Spy App for Employee Monitoring#WhatsApp Spy App Kids Monitoring#WhatsApp Spy App for Online Safety#WhatsApp Spy App for Couples
0 notes
Text
Spy on WhatsApp Messages Without Installing Software

With the ever-increasing use of messaging platforms like WhatsApp for communication, individuals and organizations are interested in monitoring messages. Whether you’re a parent concerned about your child's online safety or an employer wanting to track workplace communication, the question arises: Can you spy on WhatsApp messages without installing software? This blog aims to answer that question and explore the different facets of monitoring WhatsApp messages without downloading or installing additional applications.
1. How to Spy on WhatsApp Messages Without Installing Any Software
The idea of spying on WhatsApp messages without installing any software is appealing. It means you don't have to tamper with the target phone or risk being detected by app notifications or strange permissions. But how can this be done?
One of the most common methods is through WhatsApp Web. Here’s how it works:
WhatsApp Web: This feature of WhatsApp allows users to access their messages on a computer by scanning a QR code from their phone. By gaining temporary physical access to someone’s phone, you can open their WhatsApp Web on your browser and keep the session open, thus monitoring their conversations remotely without needing any additional software.
The steps to do this:
Open web.whatsapp.com on your computer.
Open WhatsApp on the target phone.
Go to WhatsApp Web from the settings.
Scan the QR code shown on your computer with the target phone.
Once connected, you’ll be able to see all the messages exchanged on the phone. It’s important to note that the phone will need to stay connected to the internet for you to continuously spy on the messages.
2. The Easiest Way to Spy on WhatsApp Messages Without Downloads
If you’re looking for the easiest way to spy on WhatsApp messages without downloading any software, WhatsApp Web remains the most straightforward method. However, there are a few limitations:
The target phone must remain connected to the internet.
WhatsApp Web logs out after a while if not used, and the target user might notice if they check their WhatsApp Web section.
You’ll need physical access to the phone at least once to scan the QR code.
Another method that doesn’t require software installation but involves more advanced knowledge is using network sniffing tools. Tools like Wireshark can capture data packets sent through a Wi-Fi network. If both the target phone and your computer are on the same network, it is technically possible to capture WhatsApp messages. However, this requires substantial technical knowledge, is illegal in most regions, and violates privacy laws.
3. Is It Possible to Spy on WhatsApp Messages Without Installing Software?
The short answer to this question is: It’s possible, but there are significant limitations.
While it is tempting to find a solution that allows for completely undetected spying without software, the truth is that the most effective methods involve installing a third-party monitoring app. The closest you can get to spy without installation is using WhatsApp Web or some advanced network monitoring techniques.
For most users, third-party software like HackersList, FlexiSpy, or others remains the most reliable solution, but these require installation on the target phone.
4. Spy on WhatsApp Messages Remotely: No Installation Required
Can you spy on WhatsApp messages remotely without installing software? Yes, but only under specific conditions.
If you can gain temporary physical access to the phone to set up WhatsApp Web or if you have access to their iCloud or Google backup (in the case of iOS and Android devices respectively), you can monitor their WhatsApp messages remotely without any additional software.
Here’s how the iCloud or Google Drive method works:
WhatsApp backs up messages to the cloud periodically.
If you have access to the iCloud or Google account of the target user, you can download and view these backups.
However, keep in mind that WhatsApp backups are often encrypted, and it may be difficult to access the messages unless you have advanced decryption tools.
This method is often difficult to pull off and may require the target’s login credentials. Additionally, it only gives you access to the most recent backup, not live conversations.
5. The Truth About Spying on WhatsApp Messages Without Installing an App
The truth is, spying on WhatsApp messages without installing an app is possible but not practical for most users. The methods that don’t require software installation, such as using WhatsApp Web, still require physical access to the phone or access to cloud backups.
More advanced options, such as using network monitoring tools, can be complicated and illegal. Moreover, most spying solutions that truly provide effective monitoring over time involve some form of app installation, even if they are discreet.
If you’re looking for a way to spy on WhatsApp without the target knowing, and without software, you might be disappointed. For reliable, long-term monitoring, installing a stealth app remains the most effective solution.
6. Can You Spy on WhatsApp Messages Without Software?
Can you spy on WhatsApp messages without software? Theoretically, yes, but it’s highly impractical. Here’s why:
WhatsApp Web requires physical access to the phone and is easy for the target to detect.
Network sniffing requires technical knowledge and can only be done under specific conditions (same network, unsecured Wi-Fi, etc.).
Cloud backup access requires knowing the target’s login credentials, and even then, you may need to decrypt the backups to read the messages.
The takeaway is that while it’s possible to spy on WhatsApp without installing software, the methods are either temporary or require significant technical skills and legal risks.
7. Spy on WhatsApp Messages Online: No Software Needed
Many online tools and websites claim to offer WhatsApp spying services without installing software. Be wary of these claims, as most of them are scams. Many such sites promise access to WhatsApp messages simply by entering the target phone number, but these are either fraudulent or phishing schemes designed to steal your personal information or money.
If you're searching for a legitimate way to spy on WhatsApp messages online, the safest and most practical method remains using WhatsApp Web or accessing cloud backups, as discussed earlier.
Be cautious about websites that ask for payment upfront without any proof of service delivery. Always research thoroughly before trusting such platforms.
8. Spy on WhatsApp Messages Without Physical Access to the Phone
Spying on WhatsApp messages without physical access to the phone is one of the most sought-after methods, but it’s rarely feasible without software installation.
The only way this is possible is by accessing the target phone’s cloud backups or using advanced hacking techniques, which often violate laws. Some services claim to access WhatsApp messages remotely, but many of these are either scams or involve risky methods that could compromise your data.
For instance, some third-party spy apps allow you to monitor a device remotely, but they still require initial setup on the target device, meaning you’ll need physical access at least once.
9. Legal Ways to Spy on WhatsApp Messages Without Installing Apps
It’s important to understand that spying on someone’s WhatsApp messages without their consent is illegal in many countries. Privacy laws protect individuals from unauthorized access to their communications.
However, there are a few legal ways to monitor WhatsApp messages in certain situations:
Parental monitoring: Parents may legally monitor their children’s activities for safety reasons, especially minors.
Employer monitoring: If an employer provides work devices, they may have the right to monitor communication for professional purposes, but this often requires employee consent.
In both cases, using third-party monitoring software that requires installation is the most practical and legal approach.
10. Spy on WhatsApp Messages for Free Without Any Software
Can you spy on WhatsApp messages for free without software? While it might be possible to use the WhatsApp Web method or by accessing backups, the practicality and long-term success of these methods are limited.
Most free methods still require some form of physical access to the phone or advanced technical knowledge, and they often don’t provide ongoing monitoring. Moreover, many free online tools are scams or ineffective.
If you’re looking for a reliable way to monitor WhatsApp messages, investing in reputable software is usually the best option, though it comes at a cost.
Conclusion
In summary, while it’s theoretically possible to spy on WhatsApp messages without installing software, the methods available are often limited, temporary, and not entirely foolproof. WhatsApp Web offers a quick, easy solution for short-term monitoring, but long-term, effective spying usually requires app installation.
Whether you're a parent, employer, or concerned individual, always be aware of the legal and ethical implications of monitoring someone’s communications. When in doubt, it’s best to consult legal guidelines and use reputable monitoring tools that respect privacy laws.
0 notes
Text
Track My Wife Phone

Not only you but there are many who get cheated on by their wife and keep wondering how I can track my wife phone. Many times, traditional Cheating wife trackers are used to catch a cheating spouse either by listening to their calls or checking their messages secretly.
#cell phone monitoring software#whatsapp tracker#wife tracker#iphone spy#mobile monitoring#cheating wife on phone#whatsapp tracking app#whatsapp spy app#cell spy#spymasterpro
0 notes
Text
The Durov saga in France and the continued efforts by countries around the world to crack down on his popular cloud-based, end-to-end encrypted private messenger and social media software has divulged a string of embarrassing details about the sorry state of internet privacy and freedom of information.
Two of the six charges facing Telegram CEO Pavel Durov in France are grounded an obscure, never-used twenty-year-old law obliging companies providing cryptography tools to inform the French Cybersecurity Agency (French acronym ANSSI) and grant it access to the software’s source code and “a description of [its] technical characteristics.”
The 2004 law – uniquely blunt in its demand that companies divulge info about the tech tools used for private communications, is being used against Durov by accusing him of providing encrypted communications services “without certified declaration.”
The legal requirement also means, if it is applied evenly across the board, that the array of instant messengers available to French users, from WhatsApp and Signal to iMessage and the French-made Olvid ‘secure’ messenger used by the French government, do comply with ANSSI regulations, meaning French intelligence can potentially spy on any or all French users at any time.
0 notes
Text
Best Cell Phone Hack for Monitoring Your Partner - 2024
In today's digital age, trust and transparency in relationships are more important than ever. However, doubts and uncertainties can sometimes creep in, leading to a desire for reassurance. One controversial yet increasingly discussed method is using cell phone hacking to monitor your partner's activities. This article explores the best cell phone hacks for 2024, focusing on techniques, tools, and services like HackersList, known for providing top-tier cell phone hacking services worldwide.

What is Cell Phone Hacking?
Cell phone hacking refers to the process of gaining unauthorized access to someone’s mobile device. This can involve extracting data, intercepting communications, and even manipulating the device's functionalities without the owner's knowledge. While hacking has a notorious reputation, it's worth noting that it can be used for various purposes, including cybersecurity, parental control, and, as discussed here, monitoring a partner.
How Mobile Phone Hacking
Mobile phone hacking involves exploiting vulnerabilities in the phone’s operating system or installed applications. Hackers can gain access to personal information, track location, and even listen to conversations. Popular methods include:
Phishing: Deceptive emails or messages tricking users into revealing their passwords.
Spyware: Malicious software installed on a device to monitor activities.
Network Attacks: Intercepting data over unsecured networks.
How to Mobile to Mobile Hack
Mobile-to-mobile hacking refers to accessing one mobile device through another. This often involves using specialized software that can be installed on the target device through a text message, email, or direct physical access. Here’s a basic outline of how it works:
Choose the Right Software: There are various software options available, like mSpy and FlexiSPY, designed for mobile monitoring.
Install the Software: The software needs to be installed on the target device, which might require temporary physical access.
Monitor the Device: Once installed, you can monitor the target device remotely from your own phone.
Hacking Mobile Networks
Mobile network hacking involves intercepting data as it is transmitted over cellular networks. This can be done through techniques like:
Man-in-the-Middle Attacks: Intercepting communications between two parties.
Rogue Access Points: Setting up fake Wi-Fi hotspots to capture data.
SS7 Exploitation: Exploiting vulnerabilities in the Signaling System 7 (SS7) protocol used in cellular networks.
These methods require a higher level of technical expertise and are often used by more advanced hackers.
Best Cell Phone Hackers
Cell Phone hackers are individuals or groups with the skills to infiltrate mobile devices. While some work independently, others might be part of larger organizations or offer their services through platforms like HackersList. HackersList is renowned for providing top-tier cell phone hacking services, connecting clients with professional hackers capable of discreetly monitoring mobile devices. Connect with expert by posting new job
Cell Phone Hack Help to SMS Hack
Related: Cheating Husband Cell Phone Spy App for Read Secret Message
One of the most sought-after features in mobile hacking is the ability to intercept and read SMS messages. This can provide insights into the target’s communications. Tools like HackersList are popular for SMS hacking, allowing users to:
Read Sent and Received Messages: View all SMS communications.
Access Deleted Messages: Retrieve messages that have been deleted.
Monitor Messaging Apps: Track messages from apps like WhatsApp, Facebook Messenger, and more.
Hacking Someone’s Cell Phone
Hacking someone's cell phone involves several steps and considerations. Here’s a simplified guide:
Choose a Reliable Service or Tool: Services like HackersList offer professional hacking services that ensure discretion and efficiency.
Install Monitoring Software: Physical access to the target phone is often required for initial installation.
Monitor Activities: Once installed, you can remotely monitor calls, messages, location, and other activities.
Hack Cell Phone Number
Hacking a cell phone number can provide access to various forms of communication and personal information. Techniques include:
SIM Swapping: Gaining control of the target’s phone number by manipulating the mobile carrier.
Phishing: Tricking the user into revealing their number and associated accounts.
Social Engineering: Using psychological manipulation to gain information.
Hack Mobile Camera
Hacking a mobile camera can provide visual access to the target’s surroundings. This is typically done through spyware that activates the camera without the user’s knowledge. Tools like FlexiSPY offer this functionality, allowing the hacker to:
Take Photos Remotely: Capture images from the target’s camera.
Record Videos: Activate the video recording feature.
Stream Live Video: View live footage from the target’s camera.
Android Cell Phone Hacks
Android devices are particularly susceptible to certain types of hacks due to their open-source nature. Popular hacks include:
Rooting: Gaining superuser access to the device, allowing for extensive control.
Spyware: Installing apps that monitor activities without the user’s knowledge.
Exploiting Vulnerabilities: Taking advantage of security flaws in the Android OS.
Cell Phone Cloned
Cloning a cell phone involves creating an exact replica of the target phone’s data on another device. This allows the hacker to intercept calls, messages, and other communications. Methods include:
SIM Cloning: Duplicating the SIM card to intercept communications.
Phone Cloning Software: Using software to copy the phone’s data.
All Mobile Hack
“All mobile hack” refers to tools and techniques that can be used across different mobile platforms, including Android and iOS. Universal hacking tools like HackersList are designed to work on multiple devices, providing comprehensive monitoring capabilities regardless of the operating system.
Conclusion
Cell phone hacking, while controversial, offers a means to gain insights and reassurance in relationships. With advances in technology, methods have become more sophisticated and accessible. Services like HackersList provide professional hacking solutions, ensuring discretion and effectiveness. Whether it's intercepting SMS messages, hacking mobile networks, or accessing the mobile camera, these tools and techniques offer a comprehensive way to monitor your partner's activities. However, it's crucial to weigh the ethical implications and legal considerations before embarking on this path.
#cell phone hack#cell phone hacker#cell phone hacking#cell phone hacked#mobile hacker#mobile hacking#hackerslist
0 notes
Text
does vpn prevent hackers from spying my whatsapp
🔒🌍✨ Erhalten Sie 3 Monate GRATIS VPN - Sicherer und privater Internetzugang weltweit! Hier klicken ✨🌍🔒
does vpn prevent hackers from spying my whatsapp
VPN-Verschlüsselung
Eine VPN-Verschlüsselung, kurz für Virtual Private Network, ist eine Technologie, die die Sicherheit und Privatsphäre von Internetnutzern schützt. Durch die Verschlüsselung der Daten, die zwischen dem Benutzer und dem VPN-Server ausgetauscht werden, wird sichergestellt, dass sensible Informationen vor neugierigen Blicken geschützt sind.
Die VPN-Verschlüsselung spielt eine entscheidende Rolle bei der Sicherheit von Online-Aktivitäten, insbesondere wenn es um die Übertragung vertraulicher Daten wie Bankinformationen oder persönlicher Kommunikation geht. Durch die verwendete Verschlüsselungstechnologie werden Datenpakete in einen undurchdringlichen Code umgewandelt, der von Dritten nicht entschlüsselt werden kann.
Darüber hinaus ermöglicht eine VPN-Verschlüsselung Internetnutzern, Geo-Blockaden zu umgehen und auf eingeschränkte Inhalte zuzugreifen. Dies kann besonders nützlich sein, wenn man auf Reisen ist und auf bestimmte Websites oder Streaming-Dienste zugreifen möchte, die in dem jeweiligen Land gesperrt sind.
Es ist wichtig zu beachten, dass nicht alle VPN-Dienste die gleiche Verschlüsselungsstärke bieten. Bevor man sich für einen Anbieter entscheidet, sollte man sich eingehend über die angebotenen Sicherheitsfunktionen informieren und gegebenenfalls auf Expertenbewertungen vertrauen.
Insgesamt bietet eine VPN-Verschlüsselung sowohl Privatpersonen als auch Unternehmen eine zusätzliche Schutzschicht im Internet. Durch die Codierung der Daten wird die Vertraulichkeit gewährleistet und die Sicherheit der Online-Kommunikation verbessert.
Hackerabwehr
Hackerabwehr ist ein wesentlicher Bestandteil der modernen Informationstechnologie. Mit der Zunahme von Online-Aktivitäten und der Verlagerung von Daten in die Cloud ist es entscheidend, die Sicherheit von Systemen und Informationen vor Hackerangriffen zu schützen. Hacker sind Personen oder Gruppen, die unbefugt in Computersysteme eindringen, um Daten zu stehlen, zu beschädigen oder zu manipulieren. Um sich vor solchen Angriffen zu schützen, ist eine effektive Hackerabwehrstrategie unerlässlich.
Es gibt verschiedene Maßnahmen, die dazu beitragen können, Hackerangriffe abzuwehren. Dazu gehören die Verwendung von sicheren Passwörtern, regelmäßige Aktualisierung von Software und Betriebssystemen, Einsatz von Firewalls und Antivirenprogrammen sowie Schulungen der Mitarbeiter im Umgang mit sensiblen Daten. Zudem ist es wichtig, dass Unternehmen ihre Systeme regelmäßig auf Schwachstellen überprüfen und Sicherheitslücken umgehend schließen.
Ein weiterer wichtiger Aspekt der Hackerabwehr ist das Bewusstsein für Social Engineering. Dabei versuchen Hacker, Mitarbeiter durch gezielte Manipulation dazu zu bringen, sensible Informationen preiszugeben oder schädliche Links zu öffnen. Indem Unternehmen ihre Mitarbeiter über diese Gefahren aufklären und sie für verdächtige Aktivitäten sensibilisieren, können sie das Risiko von Hackerangriffen erheblich reduzieren.
Insgesamt ist Hackerabwehr ein kontinuierlicher Prozess, der ständige Aufmerksamkeit erfordert. Unternehmen sollten in hochwertige Sicherheitsmaßnahmen investieren und ihre Systeme kontinuierlich überwachen, um sich bestmöglich vor Hackerangriffen zu schützen. Nur so können sie die Integrität und Vertraulichkeit ihrer Daten gewährleisten und das Vertrauen ihrer Kunden bewahren.
WhatsApp-Datenschutz
Der Datenschutz bei WhatsApp ist ein Thema, das in letzter Zeit immer wieder für Diskussionen gesorgt hat. Viele Nutzerinnen und Nutzer sind besorgt über die Verwendung ihrer persönlichen Daten durch den beliebten Messaging-Dienst. WhatsApp hat in der Vergangenheit Änderungen an seinen Datenschutzrichtlinien vorgenommen, die bei vielen auf Kritik gestoßen sind.
Eines der Hauptprobleme ist die Weitergabe von Daten an Facebook, das Unternehmen hinter WhatsApp. Viele Nutzerinnen und Nutzer sind besorgt darüber, dass ihre Daten für Werbezwecke genutzt werden könnten. WhatsApp betont jedoch, dass die Privatsphäre und Sicherheit der Nutzerinnen und Nutzer oberste Priorität haben.
Um den Datenschutz zu verbessern, hat WhatsApp auch Funktionen wie die Ende-zu-Ende-Verschlüsselung eingeführt, um die Kommunikation der Nutzerinnen und Nutzer zu schützen. Dennoch sollten Nutzerinnen und Nutzer vorsichtig sein und ihre Datenschutzeinstellungen regelmäßig überprüfen, um sicherzustellen, dass ihre Daten sicher sind.
Es ist wichtig, dass Nutzerinnen und Nutzer sich bewusst sind, welche Daten sie mit WhatsApp teilen und wie diese verwendet werden. Durch die Kenntnis der Datenschutzrichtlinien und die Anpassung der Einstellungen können sie dazu beitragen, ihre Privatsphäre zu schützen.
Insgesamt ist der Datenschutz bei WhatsApp ein komplexes Thema, das eine informierte Herangehensweise erfordert. Indem Nutzerinnen und Nutzer aktiv werden und ihre Privatsphäre schützen, können sie dazu beitragen, die Sicherheit ihrer Daten zu gewährleisten.
Online-Spionage-Schutz
Der Schutz vor Online-Spionage wird in der heutigen digitalen Welt immer wichtiger. Mit der ständig wachsenden Anzahl von Cyber-Bedrohungen ist es unerlässlich, sich angemessen zu schützen, um persönliche und sensible Informationen vor Eindringlingen zu bewahren.
Es gibt verschiedene Maßnahmen, die man ergreifen kann, um sich vor Online-Spionage zu schützen. Eine der wichtigsten Vorsichtsmaßnahmen ist die Verwendung von starken Passwörtern und deren regelmäßige Aktualisierung. Es ist ratsam, komplexe Passwörter zu wählen, die aus einer Kombination von Buchstaben, Zahlen und Sonderzeichen bestehen, um es Hackern schwer zu machen, darauf zuzugreifen.
Des Weiteren ist die Nutzung von Antivirensoftware und Firewalls entscheidend, um Malware und andere schädliche Programme abzuwehren, die dazu dienen können, persönliche Daten zu stehlen. Es ist wichtig, diese Programme regelmäßig zu aktualisieren, um einen effektiven Schutz zu gewährleisten.
Zusätzlich sollte man vorsichtig sein, welche Informationen man online teilt und welche Links man öffnet. Phishing-E-Mails und betrügerische Websites können dazu führen, dass man Opfer von Online-Spionage wird. Daher ist es ratsam, misstrauisch zu sein und verdächtige Nachrichten oder Links zu ignorieren.
Letztendlich ist ein verantwortungsbewusstes Verhalten im Internet entscheidend, um sich vor Online-Spionage zu schützen. Indem man sich der Risiken bewusst ist und entsprechende Sicherheitsmaßnahmen ergreift, kann man seine Online-Präsenz besser schützen und seine pers��nlichen Daten vor potenziellen Angreifern absichern.
Internet-Sicherheit
Internet-Sicherheit ist ein äußerst wichtiges Thema in der heutigen digitalen Welt. Mit der zunehmenden Vernetzung und Abhängigkeit von Online-Diensten ist es unerlässlich, geeignete Maßnahmen zu ergreifen, um persönliche Daten und Informationen vor Angriffen und Missbrauch zu schützen.
Es gibt verschiedene Aspekte der Internet-Sicherheit, die berücksichtigt werden müssen. Dazu gehören die Verwendung von sicheren Passwörtern, regelmäßige Aktualisierungen von Antivirenprogrammen und Firewalls, sowie die Vorsicht im Umgang mit persönlichen Daten online. Es ist wichtig, kein sensibles Material preiszugeben und verdächtige Links oder E-Mails zu vermeiden.
Eine weitere wichtige Maßnahme zur Sicherung des Internets ist die Verwendung von VPNs (Virtual Private Networks). Diese ermöglichen es, eine sichere Verbindung herzustellen und die Privatsphäre zu wahren, insbesondere beim Zugriff auf öffentliche WLAN-Netzwerke.
Um die Internet-Sicherheit zu gewährleisten, ist es auch ratsam, sich über aktuelle Bedrohungen und Sicherheitslücken informiert zu halten. Regelmäßige Schulungen und Sensibilisierung für potenzielle Risiken im Internet können dazu beitragen, sich besser zu schützen.
Insgesamt ist die Internet-Sicherheit eine individuelle Verantwortung, die nicht vernachlässigt werden sollte. Durch die Umsetzung geeigneter Sicherheitsmaßnahmen und die Aufmerksamkeit im Umgang mit Online-Aktivitäten können Nutzer dazu beitragen, ihre Daten und Privatsphäre zu schützen.
0 notes
Text
can vpn protect against spying
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can vpn protect against spying
VPN encryption
Title: Understanding VPN Encryption: Securing Your Online Privacy
In the digital age where privacy breaches and cyber threats are rampant, safeguarding your online activities has become paramount. Virtual Private Networks (VPNs) offer a robust solution by encrypting your internet connection, providing an extra layer of security and anonymity. Let's delve into the intricacies of VPN encryption and how it works to protect your sensitive data.
VPN encryption employs sophisticated algorithms to encode your internet traffic, rendering it incomprehensible to anyone attempting to intercept or monitor it. This encryption process transforms your data into an unreadable format, ensuring that even if it's intercepted, it remains indecipherable without the corresponding decryption key.
The strength of VPN encryption is measured by its key length and the encryption protocol used. Common encryption protocols include OpenVPN, L2TP/IPsec, and IKEv2/IPsec, each offering varying levels of security and performance. Additionally, encryption keys are typically categorized as either symmetric or asymmetric, with longer keys providing higher security but potentially impacting connection speed.
Symmetric encryption utilizes a single key for both encryption and decryption, offering fast processing speeds ideal for streaming and browsing. Conversely, asymmetric encryption employs a pair of keys – a public key for encryption and a private key for decryption – ensuring heightened security but with a potential trade-off in speed.
By encrypting your internet traffic, VPNs create a secure tunnel between your device and the VPN server, effectively shielding your data from prying eyes. This encrypted tunnel prevents ISPs, hackers, and government agencies from monitoring your online activities, preserving your privacy and anonymity while browsing the web.
In conclusion, VPN encryption is a fundamental component of online security, safeguarding your sensitive data and preserving your privacy in an increasingly interconnected world. By understanding how VPN encryption works and choosing reputable VPN providers with robust encryption protocols, you can enjoy a safer and more secure online experience.
Internet surveillance prevention
Title: Safeguarding Your Online Privacy: Internet Surveillance Prevention Measures
In an era where digital footprints are increasingly scrutinized, safeguarding your online privacy is paramount. Internet surveillance, whether by governments, corporations, or malicious actors, poses a significant threat to personal data security. However, there are proactive measures individuals can take to mitigate these risks and protect their privacy.
One of the most effective ways to prevent internet surveillance is by using virtual private networks (VPNs). VPNs encrypt internet traffic, making it difficult for third parties to intercept and decipher data. By routing your connection through secure servers, VPNs also mask your IP address, enhancing anonymity and thwarting surveillance attempts.
Furthermore, adopting strong encryption protocols for communication channels adds an extra layer of protection against surveillance. End-to-end encryption, utilized by messaging apps like Signal and WhatsApp, ensures that only the sender and recipient can access the content of their conversations, shielding it from prying eyes.
Regularly updating software and operating systems is another essential aspect of internet surveillance prevention. Software updates often include patches for security vulnerabilities, reducing the risk of exploitation by surveillance entities and cybercriminals.
Moreover, practicing good browsing habits, such as using privacy-oriented search engines like DuckDuckGo and employing browser extensions that block tracking cookies, enhances online anonymity and minimizes exposure to surveillance tactics.
Additionally, being mindful of the information shared on social media platforms and other online forums can help mitigate the risks of surveillance. Limiting the disclosure of sensitive personal details and adjusting privacy settings to restrict access to your profile can significantly reduce the likelihood of being targeted for surveillance.
In conclusion, safeguarding against internet surveillance requires a multifaceted approach that combines technological solutions with prudent online behavior. By implementing these preventative measures, individuals can take proactive steps to protect their online privacy and mitigate the risks posed by pervasive surveillance practices.
Online anonymity tools
Online anonymity tools are becoming increasingly popular as internet users seek to protect their privacy and security online. These tools help mask a user's identity and browsing activity, significantly reducing the risk of being tracked or monitored by malicious actors or even governments.
One of the most common online anonymity tools is a Virtual Private Network (VPN). A VPN creates a secure and encrypted connection to another network over the internet, allowing users to browse the web anonymously and access geo-restricted content. VPNs are especially useful when using public Wi-Fi networks, as they prevent unauthorized access to personal data.
Another popular tool for online anonymity is the Tor (The Onion Router) network. Tor routes internet traffic through a series of volunteer-operated servers, encrypting it multiple times and obscuring the user's IP address. This helps users mask their online activities and communicate anonymously.
Proxy servers are also commonly used as online anonymity tools. Proxies act as intermediaries between a user's device and the internet, allowing users to browse the web anonymously by masking their IP addresses. However, it is essential to choose a reputable proxy server to ensure privacy and security.
While online anonymity tools can help protect users' privacy, it is essential to use them responsibly and understand their limitations. It is important to note that no tool can guarantee complete anonymity online, and users should exercise caution when sharing sensitive information over the internet.
Cybersecurity shield
Title: Strengthen Your Online Fortress with Cybersecurity Shield
In today's digital landscape, safeguarding sensitive information and personal data has become paramount. With the rise of cyber threats and malicious activities, individuals and businesses alike are increasingly vulnerable to cyber attacks. To counteract these risks, the implementation of a robust cybersecurity shield is essential.
A cybersecurity shield serves as a multifaceted defense mechanism, designed to protect digital assets from unauthorized access, data breaches, and other cyber threats. It encompasses a range of tools, protocols, and practices aimed at fortifying digital infrastructures and preserving the integrity of online operations.
One of the primary components of a cybersecurity shield is robust antivirus software. This software detects and neutralizes various forms of malware, including viruses, worms, and Trojans, before they can infiltrate systems and compromise data. Additionally, firewalls act as a barrier between internal networks and external threats, monitoring and controlling incoming and outgoing traffic to prevent unauthorized access.
Encryption plays a pivotal role in safeguarding sensitive information by converting data into an unreadable format, thereby preventing unauthorized parties from intercepting and deciphering it. Furthermore, regular software updates and patches are essential for addressing vulnerabilities and strengthening defenses against emerging threats.
In addition to technological measures, employee education and awareness are integral components of an effective cybersecurity shield. Training programs and workshops can empower individuals to recognize potential threats, adhere to security best practices, and respond effectively in the event of a cyber attack.
By implementing a comprehensive cybersecurity shield, individuals and organizations can mitigate the risks posed by cyber threats and safeguard their digital assets. In an increasingly interconnected world, prioritizing cybersecurity is not only essential for protecting sensitive information but also for preserving trust and confidence in online interactions.
Privacy breach defense
Privacy breach defense is critical in today's digital world where personal information is constantly at risk of being compromised. With the increase in cyber threats and sophisticated hacking techniques, individuals and organizations must take proactive steps to protect their sensitive data from unauthorized access.
One of the first lines of defense in privacy breach protection is encryption. Encrypting sensitive data ensures that even if a breach occurs, the information stolen is unreadable and unusable to the attacker. Strong encryption methods such as AES (Advanced Encryption Standard) should be used to safeguard data both at rest and in transit.
Implementing multi-factor authentication (MFA) is another effective way to defend against privacy breaches. MFA requires users to provide additional verification beyond just a password, such as a one-time code sent to their phone. This extra layer of security greatly reduces the risk of unauthorized access, even if login credentials are compromised.
Regular security audits and vulnerability assessments are essential components of a robust privacy breach defense strategy. By regularly testing systems and networks for weaknesses, organizations can identify and address potential security gaps before they are exploited by malicious actors.
Lastly, educating employees and raising awareness about the importance of privacy protection can significantly enhance overall defense against breaches. Training staff on how to recognize phishing attempts, practicing safe browsing habits, and emphasizing the importance of data security can go a long way in preventing privacy breaches.
In conclusion, privacy breach defense requires a combination of technical measures, security protocols, and employee vigilance. By staying proactive and implementing a comprehensive privacy protection strategy, individuals and organizations can minimize the risk of falling victim to privacy breaches.
0 notes
Text
The Intricate World of Android Spy Apps: Unmasking Functionality and Ethics

The digital realm has become an extension of ourselves, especially with smartphones playing a central role in our daily lives. This extends to our children, partners, and even employees in specific situations. While trust is paramount, there may be instances where monitoring phone activity becomes a necessity. This is where Android spy apps enter the scene, promising a glimpse into the target device's digital landscape.
However, venturing into the world of spy apps necessitates a clear understanding of the legal and ethical ramifications. Local laws regarding phone monitoring software should be thoroughly reviewed before using any such app. Transparency is also key – always disclose monitoring to those being monitored, particularly in the case of children.
Free vs. Paid Spy Apps: Unveiling the Reality
The quest for a truly free, feature-rich Android spy app can be a deceptive one. While some apps advertise free tiers, they often come with significant limitations. Core functionalities often require a paid subscription, leaving you with a restricted experience in the free version.
Here's a closer look at some popular contenders and their feature breakdowns:
Onemonitar: This user-friendly app boasts a comprehensive feature set. The free version offers a taste of its capabilities, such as limited call history and contact details. However, for in-depth monitoring, a paid subscription unlocks features like extensive call monitoring (recordings and call duration), detailed message tracking across various platforms (WhatsApp, Facebook Messenger), real-time GPS location tracking, internet browsing history, and app usage monitoring.
Chyldmonitar: Designed for user ease, Chyldmonitar offers a decent feature range in both free and paid tiers. The free version provides basic call log and SMS monitoring, along with limited app usage tracking. Upgrading unlocks more detailed call recordings, in-depth message tracking, comprehensive app usage monitoring, remote camera activation (for capturing photos and surroundings), and even keylogging functionality.
Onespy: This app focuses on stealth and invisibility. Similar to its counterparts, Onespy offers a free tier with limited features like basic details on calls and SMS. Upgrading unlocks advanced call monitoring (recordings and call duration), comprehensive message tracking across various apps, real-time GPS location tracking, internet browsing history, and app usage monitoring.
Crucial Considerations Before Using Spy Apps:
Legality: Always ensure using a spy app complies with your local laws. Regulations vary by region, so consult with a legal professional if necessary.
Target Device Compatibility: Not all apps are compatible with all Android versions. Verify compatibility before downloading to avoid wasting time and effort.
Rooted vs. Non-Rooted Devices: Certain features might require a rooted device (providing administrator access), which can be risky as it bypasses security measures and exposes the device to vulnerabilities.
Target Device Accessibility: Installing the app often necessitates physical access to the target device. Consider the practicality of acquiring this access.
Alternative Solutions: Consider These Options Before Resorting to Spy Apps
Parental Control Apps: Designed for monitoring children's phone activity, these apps prioritize safety and offer features like app blocking, screen time management, and website filtering.
Built-in Monitoring Tools: Many Android devices have built-in features like Google Family Link that allow for some degree of monitoring for children's devices.
The Ethical Tightrope Walk: Weighing the Implications
The use of spy apps raises a critical ethical question. While there might be legitimate reasons for monitoring someone's phone activity, it's crucial to weigh the ethical concerns. Open communication and trust should be the cornerstone of any relationship. Spy apps should only be considered as a last resort and with complete transparency.
Conclusion: A World Beyond Spy Apps
While Android spy apps exist, approaching them with caution is essential. Understanding the legality, respecting privacy, and exploring alternative solutions are all crucial aspects to consider. Remember, a foundation of trust is irreplaceable. If you have concerns about someone's phone activity, open communication might be a more sustainable solution than resorting to covert monitoring.
0 notes
Text
Powerful WhatsApp Monitoring Software for Complete Oversight

Take control of your monitoring efforts with our specialized WhatsApp monitoring software. Designed to provide comprehensive oversight of WhatsApp activities, our software allows you to track messages, calls, multimedia exchanges, and more with ease. With real-time access to chat logs, contact lists, and media files, you can stay informed and proactive in safeguarding your loved ones or monitoring employee communications. Our software operates discreetly in the background, ensuring that your monitoring activities remain undetected. Elevate your monitoring capabilities and gain peace of mind with our powerful WhatsApp monitoring software.
Start Monitoring Today!
#Whatsapp spy app#Spy on Whatsapp messages#Whatsapp monitoring software#Whatsapp spy tool#Spy app for Whatsapp#Whatsapp spyware#Spy Whatsapp conversations#Whatsapp spy program#Whatsapp spy software#Whatsapp spy application
0 notes
Text
5 Powerful WhatsApp Message Trackers to Keep in Control
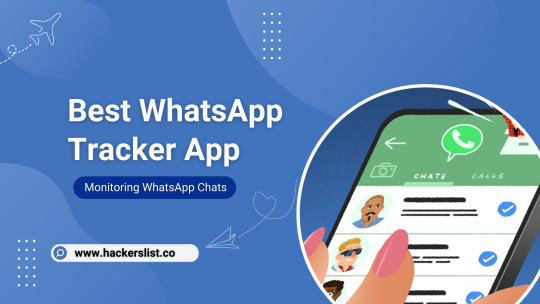
In today’s digital age, communication has transcended traditional means and has found a dominant platform in messaging apps. Among these, WhatsApp stands out as one of the most widely used platforms, with billions of users globally. Given its popularity, the demand for WhatsApp chat tracker apps has surged, catering to various needs from parental control to monitoring employee communications.
This comprehensive guide explores WhatsApp chat tracker apps, the features that make them indispensable, and the top spy apps with WhatsApp tracker capabilities. Whether you’re a concerned parent, a business owner, or someone with a specific interest in monitoring WhatsApp activity, this guide will provide you with the insights you need to choose the best app for your needs.
Understanding WhatsApp Chat Trackers
What is a WhatsApp Chat Tracker?
A WhatsApp chat tracker is a software application designed to monitor and track conversations and activities on WhatsApp. These trackers provide insights into chats, multimedia exchanges, call logs, and other data transmitted via WhatsApp. The primary objective of these tools is to give users the ability to monitor WhatsApp activities discreetly.
WhatsApp chat trackers are typically used for:
Parental Control: Ensuring children are not exposed to inappropriate content or risky interactions.
Employee Monitoring: Overseeing communication channels in corporate environments to maintain productivity and data security.
Personal Use: Individuals who need to keep an eye on their partner’s or family member’s online activities for various reasons.
How Do WhatsApp Chat Trackers Work?
WhatsApp chat trackers work by capturing data from the target device where WhatsApp is installed. They typically require installation on the target device, after which they operate in stealth mode, meaning the user of the target device remains unaware of the tracking. The collected data is then transmitted to a dashboard accessible by the person monitoring the device.
Key functionalities of WhatsApp chat trackers include:
Message Monitoring: Track and read all incoming and outgoing messages, including deleted ones.
Multimedia Access: View shared images, videos, voice notes, and other multimedia files.
Call Logs: Monitor details of voice and video calls, including time, duration, and contact information.
Contact Information: Access the contact list and view details of the people the target interacts with.
Activity Logs: Track login times, online status, and other app usage patterns.
Top Spy Apps with WhatsApp Tracker Features
When it comes to selecting a WhatsApp tracker, there are numerous spy apps available, each offering a unique set of features tailored for different monitoring needs. Below, we highlight some of the top spy apps that are renowned for their WhatsApp tracking capabilities.
1. HackersList
HackersList is one of the most popular and widely used spy apps for monitoring WhatsApp and other social media platforms. Its user-friendly interface and robust set of features make it a go-to choice for parents and employers alike.
WhatsApp Tracking: HackersList allows users to monitor WhatsApp messages, including group chats, multimedia files, and call logs.
Stealth Mode: Operates in the background, making it undetectable on the target device.
Compatibility: Works on both Android and iOS devices, with or without jailbreaking or rooting.
HackersList provides real-time data synchronization, allowing users to access updates as soon as they occur, making it an excellent tool for continuous monitoring.
2. FlexiSPY
FlexiSPY is another powerful spy app known for its comprehensive monitoring features. It is particularly favored by users who require advanced functionalities beyond basic message tracking.
Advanced WhatsApp Monitoring: FlexiSPY not only tracks WhatsApp messages and multimedia but also records WhatsApp calls.
Remote Access: Provides remote access to the target device, allowing users to control various aspects of the phone.
Detailed Reporting: Offers detailed logs and reports, making it easier to analyze the monitored data.
FlexiSPY is suitable for those looking for an in-depth monitoring solution, though it might require more technical know-how compared to simpler apps.
3. Hoverwatch
Hoverwatch is a versatile monitoring app that offers WhatsApp tracking as part of its broader suite of features. It is particularly popular among users looking for an affordable yet effective monitoring solution.
WhatsApp Message Tracking: Monitor all text messages and multimedia shared via WhatsApp.
Stealth Mode: Remains hidden from the target user, ensuring discreet monitoring.
Multiple Device Tracking: Allows monitoring of multiple devices from a single account.
Hoverwatch’s affordability combined with its effective monitoring features makes it a great option for users on a budget.
4. Cocospy
Cocospy is a lightweight spy app known for its ease of use and reliable performance. It is particularly popular among parents who wish to monitor their children’s online activities.
WhatsApp Chat Monitoring: Provides access to all WhatsApp conversations, including timestamps and contact details.
No Rooting or Jailbreaking: Works without the need for rooting or jailbreaking the target device, making it easier to install and use.
User-Friendly Dashboard: Offers an intuitive dashboard for easy access to monitored data.
Cocospy is an excellent choice for users seeking a straightforward, hassle-free monitoring solution.
5. Spyzie
Spyzie is another top contender in the spy app market, offering a wide range of monitoring features, including WhatsApp tracking. It is particularly known for its detailed and organized reporting.
WhatsApp Monitoring: Tracks all WhatsApp messages, shared files, and call logs.
Data Security: Ensures that the monitored data is secure and accessible only to the user.
Remote Installation: Can be installed remotely on the target device, simplifying the setup process.
Spyzie’s focus on data security and ease of installation makes it a reliable option for those new to monitoring apps.
Choosing the Best WhatsApp Tracker App
With so many options available, selecting the best WhatsApp tracker app can be challenging. The right choice depends on your specific needs, the target device, and your technical comfort level. Here are some factors to consider when choosing a WhatsApp tracker app:
1. Compatibility
Ensure the app is compatible with the target device’s operating system (iOS or Android). Some apps may require jailbreaking or rooting, which can be a technical hurdle for some users. Choose an app that matches your technical capabilities and the device’s specifications.
2. Features
Different apps offer varying levels of functionality. If you need comprehensive monitoring, including call recording and multimedia tracking, opt for apps like FlexiSPY or HackersList. For basic text message tracking, apps like Cocospy or Hoverwatch might suffice.
3. Stealth Mode
Most users prefer apps that operate in stealth mode, ensuring the target user is unaware of the monitoring. Check that the app you choose remains hidden and does not trigger alerts or notifications on the target device.
4. Ease of Use
Consider the user interface and ease of use, especially if you’re not tech-savvy. Apps with intuitive dashboards and simple installation processes are generally more user-friendly.
5. Customer Support
Reliable customer support is crucial, especially if you encounter technical issues. Look for apps that offer robust customer support, including live chat, email, and phone assistance.
6. Pricing
Pricing can vary widely among different spy apps. While some apps offer premium features at a higher cost, others provide basic monitoring at a more affordable rate. Determine your budget and compare the features offered at each price point to make an informed decision.
Legal and Ethical Considerations
While WhatsApp chat tracker apps offer powerful monitoring capabilities, it’s essential to consider the legal and ethical implications of using such software. In many jurisdictions, it is illegal to monitor someone’s communications without their consent. Unauthorized use of spy apps can lead to legal consequences, including fines and imprisonment.
Before using a WhatsApp chat tracker app, ensure that you have the legal right to monitor the target device. For example, parents monitoring their minor children’s devices are generally within their legal rights, while monitoring an adult’s device without consent may violate privacy laws.
Moreover, ethical considerations should not be overlooked. Respecting privacy and using these tools responsibly is paramount. Monitoring should be done with clear intentions, such as protecting minors or securing company data, rather than for malicious purposes.
WhatsApp Message Trackers and Their Impact
The impact of WhatsApp message trackers extends beyond just monitoring conversations. These tools can play a significant role in safeguarding individuals and organizations from various risks.
1. Parental Control and Child Safety
For parents, WhatsApp chat trackers provide a way to protect children from online predators, cyberbullying, and exposure to inappropriate content. By keeping an eye on their children’s communications, parents can intervene when necessary and ensure their child’s online safety.
2. Employee Monitoring and Data Security
In corporate environments, WhatsApp trackers help employers ensure that employees are not engaging in activities that could compromise company data or productivity. Monitoring workplace communications can help prevent data leaks, insider threats, and ensure compliance with company policies.
3. Personal Security and Trust
On a personal level, WhatsApp trackers can be used to protect oneself from potential threats or to maintain trust in relationships. However, this must be balanced with respect for privacy and transparency in relationships.
Future Trends in WhatsApp Tracking Technology
As technology evolves, so too will the capabilities of WhatsApp chat trackers. Here are some future trends to watch for:
1. AI and Machine Learning Integration
Future WhatsApp trackers may integrate AI and machine learning to provide more sophisticated monitoring features. For example, AI could analyze chat patterns to detect potential risks, such as grooming or phishing attempts, and alert the user in real-time.
2. Enhanced Data Security
With increasing concerns about data privacy, future apps
may offer enhanced encryption and data security features to protect the monitored data. This will be especially important for users concerned about the security of the information they are tracking.
3. Multi-Platform Monitoring
As communication becomes more fragmented across various platforms, future trackers may offer multi-platform monitoring, allowing users to track conversations across different messaging apps and social media networks from a single dashboard.
4. Remote Monitoring Enhancements
Remote monitoring capabilities are likely to become more advanced, allowing for easier installation and operation without the need for physical access to the target device. This could include features like cloud-based monitoring and remote updates.
Conclusion
WhatsApp chat tracker apps have become essential tools for parents, employers, and individuals looking to monitor WhatsApp communications. With a wide range of apps available, each offering unique features and capabilities, it’s crucial to choose the one that best meets your needs.
While these tools offer powerful monitoring capabilities, it’s important to use them responsibly and within the bounds of the law. By selecting the right app and using it ethically, you can protect your loved ones, secure your business, and maintain trust in your personal relationships.
As technology continues to advance, the future of WhatsApp tracking promises even more sophisticated and secure monitoring options, ensuring that users can stay ahead of potential risks and challenges in the digital world.
0 notes