#mobile hacking
Explore tagged Tumblr posts
Text
Best Cell Phone Hack for Monitoring Your Partner - 2024
In today's digital age, trust and transparency in relationships are more important than ever. However, doubts and uncertainties can sometimes creep in, leading to a desire for reassurance. One controversial yet increasingly discussed method is using cell phone hacking to monitor your partner's activities. This article explores the best cell phone hacks for 2024, focusing on techniques, tools, and services like HackersList, known for providing top-tier cell phone hacking services worldwide.

What is Cell Phone Hacking?
Cell phone hacking refers to the process of gaining unauthorized access to someone’s mobile device. This can involve extracting data, intercepting communications, and even manipulating the device's functionalities without the owner's knowledge. While hacking has a notorious reputation, it's worth noting that it can be used for various purposes, including cybersecurity, parental control, and, as discussed here, monitoring a partner.
How Mobile Phone Hacking
Mobile phone hacking involves exploiting vulnerabilities in the phone’s operating system or installed applications. Hackers can gain access to personal information, track location, and even listen to conversations. Popular methods include:
Phishing: Deceptive emails or messages tricking users into revealing their passwords.
Spyware: Malicious software installed on a device to monitor activities.
Network Attacks: Intercepting data over unsecured networks.
How to Mobile to Mobile Hack
Mobile-to-mobile hacking refers to accessing one mobile device through another. This often involves using specialized software that can be installed on the target device through a text message, email, or direct physical access. Here’s a basic outline of how it works:
Choose the Right Software: There are various software options available, like mSpy and FlexiSPY, designed for mobile monitoring.
Install the Software: The software needs to be installed on the target device, which might require temporary physical access.
Monitor the Device: Once installed, you can monitor the target device remotely from your own phone.
Hacking Mobile Networks
Mobile network hacking involves intercepting data as it is transmitted over cellular networks. This can be done through techniques like:
Man-in-the-Middle Attacks: Intercepting communications between two parties.
Rogue Access Points: Setting up fake Wi-Fi hotspots to capture data.
SS7 Exploitation: Exploiting vulnerabilities in the Signaling System 7 (SS7) protocol used in cellular networks.
These methods require a higher level of technical expertise and are often used by more advanced hackers.
Best Cell Phone Hackers
Cell Phone hackers are individuals or groups with the skills to infiltrate mobile devices. While some work independently, others might be part of larger organizations or offer their services through platforms like HackersList. HackersList is renowned for providing top-tier cell phone hacking services, connecting clients with professional hackers capable of discreetly monitoring mobile devices. Connect with expert by posting new job
Cell Phone Hack Help to SMS Hack
Related: Cheating Husband Cell Phone Spy App for Read Secret Message
One of the most sought-after features in mobile hacking is the ability to intercept and read SMS messages. This can provide insights into the target’s communications. Tools like HackersList are popular for SMS hacking, allowing users to:
Read Sent and Received Messages: View all SMS communications.
Access Deleted Messages: Retrieve messages that have been deleted.
Monitor Messaging Apps: Track messages from apps like WhatsApp, Facebook Messenger, and more.
Hacking Someone’s Cell Phone
Hacking someone's cell phone involves several steps and considerations. Here’s a simplified guide:
Choose a Reliable Service or Tool: Services like HackersList offer professional hacking services that ensure discretion and efficiency.
Install Monitoring Software: Physical access to the target phone is often required for initial installation.
Monitor Activities: Once installed, you can remotely monitor calls, messages, location, and other activities.
Hack Cell Phone Number
Hacking a cell phone number can provide access to various forms of communication and personal information. Techniques include:
SIM Swapping: Gaining control of the target’s phone number by manipulating the mobile carrier.
Phishing: Tricking the user into revealing their number and associated accounts.
Social Engineering: Using psychological manipulation to gain information.
Hack Mobile Camera
Hacking a mobile camera can provide visual access to the target’s surroundings. This is typically done through spyware that activates the camera without the user’s knowledge. Tools like FlexiSPY offer this functionality, allowing the hacker to:
Take Photos Remotely: Capture images from the target’s camera.
Record Videos: Activate the video recording feature.
Stream Live Video: View live footage from the target’s camera.
Android Cell Phone Hacks
Android devices are particularly susceptible to certain types of hacks due to their open-source nature. Popular hacks include:
Rooting: Gaining superuser access to the device, allowing for extensive control.
Spyware: Installing apps that monitor activities without the user’s knowledge.
Exploiting Vulnerabilities: Taking advantage of security flaws in the Android OS.
Cell Phone Cloned
Cloning a cell phone involves creating an exact replica of the target phone’s data on another device. This allows the hacker to intercept calls, messages, and other communications. Methods include:
SIM Cloning: Duplicating the SIM card to intercept communications.
Phone Cloning Software: Using software to copy the phone’s data.
All Mobile Hack
“All mobile hack” refers to tools and techniques that can be used across different mobile platforms, including Android and iOS. Universal hacking tools like HackersList are designed to work on multiple devices, providing comprehensive monitoring capabilities regardless of the operating system.
Conclusion
Cell phone hacking, while controversial, offers a means to gain insights and reassurance in relationships. With advances in technology, methods have become more sophisticated and accessible. Services like HackersList provide professional hacking solutions, ensuring discretion and effectiveness. Whether it's intercepting SMS messages, hacking mobile networks, or accessing the mobile camera, these tools and techniques offer a comprehensive way to monitor your partner's activities. However, it's crucial to weigh the ethical implications and legal considerations before embarking on this path.
#cell phone hack#cell phone hacker#cell phone hacking#cell phone hacked#mobile hacker#mobile hacking#hackerslist
0 notes
Text
youtube
If you are looking for an efficient method to hack into someone's phone and monitor their activities remotely and secretly you can use AnyControl application. To learn more about AnyControl features and how it hacks mobile phones watch the video or click on the link.
#hack phone#mobile hacking#hack smartphone#hack#monitoring#parenting#parental control#youtube#Youtube
0 notes
Text

PUBG Hacks
When navigating the competitive landscape of PUBG Hacks, players often find themselves seeking an edge to enhance their gameplay experience. The allure of PUBG hacks has captivated many, providing shortcuts that can transform even novice players into formidable opponents. However, it's essential to approach this temptation with caution. Utilizing hacks might offer immediate gratification and victories, but it can also lead to unforeseen consequences like account bans and tarnished reputations in the gaming community.
What's intriguing is how these hacks have evolved alongside the game itself. Rather than just a means to win, they are now seen as tools for experimentation—allowing players to explore mechanics and strategies that would otherwise remain unexplored in standard play sessions. This innovative mindset encourages gamers not only to excel but also to engage deeply with the underlying systems of resilience and adaptability within PUBG itself. In this constant cat-and-mouse game between developers and hack creators, understanding both sides can lead you toward better gameplay choices—whether you choose to embrace the hacks or master your skills through sheer dedication.
48 notes
·
View notes
Text
Person of Interest (2011-2016)
#person of interest#cyberpunk aesthetic#hacking#graphic design#surveillance#science fiction#surveillence state#hackers#cybersecurity#scifi#mobile hacker#code breaker#data manipulation#network security#infosecurity#10s#command line
81 notes
·
View notes
Text
How it started: "Oh, I'd love to have some ripped sprites for my Minori no Shima guide, let's see what I can figure out..."
How it's going:
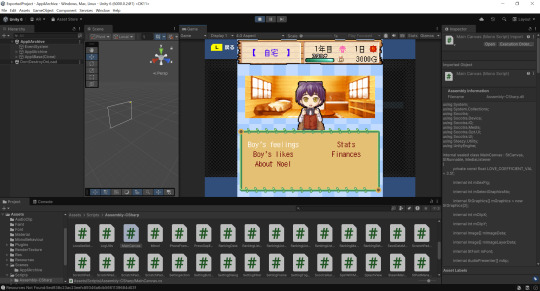
...It's running in unity...
#was NOT expecting to anywhere near this far when i started#it is so tempting just to make a full-on fan translation hack#but i couldn't release it#i do want g-mode to make money for this beautiful thing they revived#of course i immediately made a gay hack tho lmao#if i can figure out how to make it just a patch i absolutely will#bokujou monogatari mobile: minori no shima#minori no shima#story of seasons#harvest moon#bokumono
19 notes
·
View notes
Text
I've snuck a few lines into posts about Fuuta being tech-y because it's fun and easy, but let it be known I don't think he actually has any notable tech skills. He's not good at hacking, or finding people, or even hiding his own online presence. He gets by, but that's it
#milgram#fuuta kajiyama#all we see is him use twitter - a mobile game - and an arcade game#his doxxing was very rudimentary: take a pic of her house and post it. no searching or stalking or hacking#hes just a simple normal guy#rose posts
47 notes
·
View notes
Text
when the fuck did "access to the lyrics of songs" become premium-locked on spotify
#like hi sometimes i want to know what the singers are saying? spotify you piece of shit this is why i pirate on mobile#i even have the weird hacked 'premium for free' one on my computer and it's still locked lmao what the hell#sorry for clogging your dash
15 notes
·
View notes
Text
life hack for stretching while fat: use objects. i got the hamstring stretch of my life by sticking my leg to the top bunk.
second life hack: don't go against gravity. can't kick your heel to your butt for a quad stretch but convinced you still have the mobility? do it laying on your side. i almost cried
#fitblr#stretching#mobility#hamstring stretch#quad stretch#fitness while fat#haes#health at every size#life hacks for stretching
3 notes
·
View notes
Text
Hasty, brockhunter, and mrs.f like ok redheads

#thr little picture of mrs.f hacking things on my mobile blog makes me sosososososossososo happy im like YAYYY#shes so cute and smart
2 notes
·
View notes
Text




points off for calling it THE aew but Hacks you have won me back with the wrestling joke. punch up would be to say Seth Rollins instead of Roman Reigns as that’s slightly more plausible but I’m not the comedy writer here
3 notes
·
View notes
Text
Here's an (unfortunately expensive but likely worth it) accessibility lifesaver when it comes to dental health: the Samba toothbrush!

This toothbrush by Curaprox features a full-mouth brushing system that does the work for you. You only need to be able to hold it in place. The handle is thick for easier grasping and the bristles are positioned so that you get a fully clean mouth in just 1 minute. The website tells us that the Samba was "designed to make oral care more accessible, especially for people with limited mobility or dexterity."
They are sold for $299.99 from the manufacturer with a 60-day money back guarantee.
Don't forget to take care of your teeth! They connect to the rest of you!
34 notes
·
View notes
Text
Building Your Own Cyberdeck:
What do you do when you have extra time between a job and your next? How about building your own Cyberdeck? Check this article out for tips on building your own!
The Ultimate Hacker Project For aspiring cybersecurity professionals, cyberpunk enthusiasts, hardware hackers, and circuit benders, one of the best hands-on projects you can take on is building your own cyberdeck. Despite overwhelming schedules full of training programs, full time work weeks, sometimes limited funds, and the endless possibilities of hardware combinations, many fans of the…

View On WordPress
#Cyber#Cyber Security#cyberdeck#cyberpunk#Cybersecurity Specialist#Ethical Hacking#hack#hacker#infosec#IT#IT professional#mobile#mobile computer#Pentesting#programming#project
30 notes
·
View notes
Text

PUBG Hacks
In the competitive world of PUBG, where every millisecond counts and each decision can be a matter of survival, hacks may seem like an enticing shortcut to victory. However, opting for PUBG hacks not only compromises the integrity of your gaming experience but also places you in a precarious position with game developers. The allure of seemingly effortless wins can quickly vanish as bans and penalties loom over players who choose this path.
Moreover, relying on hacks removes the essence of skill development and strategic gameplay. Players miss out on honing their abilities—whether it’s mastering gun mechanics or perfecting map navigation—ultimately robbing them of genuine satisfaction when achieving those hard-earned chicken dinners. Instead of turning towards cheats found at sites like cheatru.com, investing time in understanding game tactics can bring a deeper sense of fulfillment and camaraderie within the gaming community. Embrace the challenge; true victories are born from perseverance rather than shortcuts!
43 notes
·
View notes
Text
tech youtuberism is a disease. and i have been infected.
#i was looking for. images and discussion on beanie baby repair and construction pattern reverse engineering etc#but i couldnt remember the words orz#you have to understand. i grew up in a kinda very tech industry area. i have a linux dad. AND a linux mom.#i cant look at any video game system or mobile device for longer than a few minutes without googling how to hack that thang#its in my blood. tech youtuberisms are in my blood......#anyway im trying to figure out how beanie babies were filled.... i dont have any rn.... i need to get a hold of some....#is there like a mesh inside or are the beans loose. how much fluff is with the beans. my childhood beanie memories are fuzzy
2 notes
·
View notes
Text
finally
i would have been so disappointed if i coded a sprite ripper only to not find a single unused sprite there

hi there bestie!
who the FUCK are you
#final conflict hacking#and yes sadly it's only these two frames the other directions aren't here#they're right next to mitula in the data and she also only has one direction#it's for the byte economy you gotta understand#anyway i am paranoid of calling these early so i gotta replay the whole game eventually to make sure this isn't some forgettable npc#but the mobile version rips have no equivalent so i'm pretty confident#could be a leftover from the other gaidens too#but a cursory look through sfcd sprites shows me that there are very few npcs there#also tbh. the cape on this fella makes them look pretty special#my current guess is an alt design for nosshu
3 notes
·
View notes
