#wifi hacking android
Explore tagged Tumblr posts
Text

ROBOT ID PACK

NAMES ︰ aerobot. agatha. ai. alan. alethea. alexia. algernon. alistair. alpha. amaryllis. ambrose. androbot. androic. andromeda. angelica. antenna. arabella. araminta. arcade. auto. automaton. axel. axis. badnik. bionel. bolt. byte. care. celline. cello. chip. chipique. clank. cloniste. clonoid. cobot. codelle. cole. curiosity. cy. cyber. cybette. cybion. cypher. data. dell. della. delpha. delta. digi. dot. droid. droidess. droidis. dronette. echo. elektra. euna. eva. eve. fritz. giga. gizmo. glitch. grey. gynoid. helix. holo. holodir. hydra. ida. jet. kaput. kinect. krudzu. linion. mac. mace. machibella. machina. mal. malware. mation. mech. mecha. mechael. mechan.ace. metal. metalia. metalish. micro. motherboard. motor. nano. neo. nucleus. nyquist. orbit. parallel. pip. pixel. prime. primus. proto. quantum. radar. radius. ram. ray. reflect. reflectette. robo. robonaut. rusty. satellite. scrappy. selsyn. sentiex. servo. shard. siri. solar. sonar. spark. sparkie. sparky. sputnik. steele. sterling. stochastic. synchro. synie. synthett. talus. terra. tin. tink. tobor. ultramarine. ultron. unimate. unit. virus. waldo. zip.

PRONOUNS︰ ai/ai. algo/algorithm. android/android. app/app. auto/auto. auto/automated. auto/automaton. axis/axi. beep/boop. bio/bionic. bio/bioplastic. blast/blast. bo/bot. bolt/bolt. bot/bot. buffer/buffer. byte/byte. cell/cell. chaos/chaos. chi/chip. click/click. clo/clone. code/code. coil/recoil. command/command. compute/computer. core/core. cyb/cyborg. cyber/cyber. data/data. dev/device. device/device. dig/digital. digi/digital. droi/droid. droid/droid. e/exe. electric/electric. entry/entries. exo/exoskeleton. gear/gear. gli/glitch. glitch/glitch. hack/hack. ho/holo. holo/holo. hologram/hologram. in/install. intra/intranet. link/link. machi/machine. mal/malfunction. mal/malware. mech/mech. mecha/mechanical. mechanic/mechanic. metal/metal. metro/metro. motor/motor. neo/neo. neon/neon. nuclear/nuclear. propeller/propeller. radar/radar. retro/retro. robo/robo. robo/robot. robot/robot. rubber/rubber. satellite/satellite. sca/scan. shard/shard. shine/shiny. signal/signal. solar/solar. steel/steel. stem/stem. swi/switch. syn/synth. syn/synthetic. tech/tech. techno/techno. test/test. text/text. turing/turing. vi/viru. web/site. web/web. whirr/whirr. wi/wifi. wire/wire. wired/wired. ⚙️/⚙️. 🔧/🔧. 🔩/🔩. 🛠//🛠. 🤖/🤖.

#pupsmail︰id packs#id pack#npt#name suggestions#name ideas#name list#pronoun suggestions#pronoun ideas#pronoun list#neopronouns#nounself#emojiself#robotkin#machinekin#androidkin#robotcore
1K notes
·
View notes
Text
Can we talk about just how bizarre it is that DBH androids ever pull back their skin layer to interact with things? Like the whole world has made massive wireless advancements, it's the Everything Is WiFi Future, and Connor can apparently literally connect to and hack a supposedly secure, closed video feed in a hyper-sophisticated tech company's building by fucking squinting at it, but for some reason he needs to pull back his skin and physically slap the electronic doors in the DPD to send the "open" signal? Markus can wirelessly send deviancy codes to androids in the street but he needs to hold North's hand to share some memory files? I'm sure the real-world explanation from the writers is "this will remind people the robots are robots by showing their robot bodies" but, like, the internal logic is just…not there.
48 notes
·
View notes
Note
is the retroid pocket a good investment? i saw your tags and am curious! :]

i'm probably biased bc i'm so used to buying retroid but yea. it's slightly pricier than some other options you might find due to the price creep of the gradually upgrading chipsets but its definitely worthwhile from my perspective, as someone who likes retro emulation and android gaming. all retroids have bluetooth support to connect extra controllers, headphone jack for audio, sd card slot to load up games from, wifi for downloading more games, and display out options to connect to a tv or somethin! you gotta bring your own games unfortunately, but it does come built in with some emulation apps to install during setup, and a choice between using the standard android OS, or the custom Retroid branded Launcher to launch games from! generally i use my retroid to play PS1, PSP, PS2 and GBA games, although im pretty sure it can handle N64, Dreamcast, NDS and 3DS too. basically if there's an android emulator or RetroArch core for it, the Retroid can probably handle it, YMMV.
the most recent model line, the Retroid Pocket 5/Mini, is still available on the GoRetroid website. generally if you're buying a retro handheld then make sure you buy it directly from the original site/source so you don't get ripped off by some offbrand seller trying to pawn one of those 100-in-1 knock off consoles on you.
time for an autistic ramble about my collection since i love these devices so much...

the original retroid pocket 2! this was the first device that caught my eye and my gateway drug into retro emulation handhelds, as it only cost $80 back in 2020. there were pink, yellow and cyan colorways too, but indigo was the most popular option :P it was a little awkward, what with the switch style analog sticks not having R3 functionality and only having one gig of RAM, but it got the job done. it also had micro HDMI out to connect to a display, kind of a hassle since micro HDMI isn't too common, but they used to sell micro HDMI cords on their site along with other accessories (screen protectors, grips, cases, etc...)

the retroid pocket 2+ was an upgraded model released a year later for $90, with 2GB RAM and a touchscreen added. still no clickable analog sticks but oh well! i bought the PS2 style colorway, a lot of their colors are styled after other retro consoles. the 4:3 screen was kinda cute! difficult for playing PSP games since it letterboxes the screen, plus you have to do some extra tweaking in the emulator settings to get it to work properly...

less than a year later, they made the Retroid Pocket 3! this one signalled a change in their release system in many ways, most notably the fact that now every retroid model comes in 2 versions: a cheaper model (with less storage/RAM) and a premium model (with more storage/RAM). personally i've never had any reason to go with the cheaper model, especially since the power difference can be so vast between the two sometimes, so every model i have is the premium model. this one cost $130, which is quite the price jump, but the added quality made it worth it for me :) the RP3 was Retroid's first foray into a 16:9 device, great for playing PSP/NDS, and easy to work with the 3GB RAM. any 4:3 games will have letterboxing on the sides now (unless you have a widescreen hack or something) but i never minded that much. also, this is the first Retroid model with R3 functionality on the joysticks! it might not matter much to most people, but i really wanted to play Ape Escape on the go :3

at some point GoRetroid realized the Retroid line kinda peaked with the RP2 form factor, so they brought it back with some added improvements for those looking for an updated 4:3 handheld, now now known as the Retroid Pocket 2S. idk what the S stands for! its looks pretty similar to the regular RP2, but with clickable hall effect joysticks on the bottom, a PSVita style DPad, and up to 4 GB of RAM. i loved this one! for a while i used to switch between the RP2S and the RP3, depending on if i was in the mood for PS1 or PSP gaming. the black crystal shell was also neat, i love clear electronics :3 price went to $120, more expensive than the original RP2 line but cheaper than the RP3. worth the price, considering the QoL improvements they made over the original RP2!

then there's the Retroid Pocket 4, released around the same time as the RP2S. this model has the same shell as the RP3 for those looking for a 16:9 form factor, while retaining the improvements from the RP2S (hall effect joysticks <3). this device is currently my go-to for portable retro emulation, with 8GB RAM and android 13 compatibility. this one can play some lighter PS2 games, but i mostly use it to play balatro these days. also, convenient feature; since the Retroid Pocket series is just an android with a built in controller, any android games with controller compatibility can be played with the Retroid controls. theres also a gamepad mapper to map button controls to other android games that don't have built in controller support, but i've never used it so i can't vouch for it -_- the RP4Pro was $200 on release, yowch! still definitely a worthwhile investment, but a far cry ffrom the original price tag of $80 back in 2020... there's still some discounted models of RP4 on sale on their website, although there's not many left, as GoRetroid is mostly clearing space for their newest model...

...the Retroid pocket 5! this model signifies another shift in Retroid's design, as they've shifted to a PSVita looking model with the rounded features and glass front panel. i got the gamecube colorway since i really liked the vibes it has... aesthetically this is the best Retroid Pocket model yet. the 3d hall sticks also have RGB LEDs built in than can be customized from a built in app, and an OLED screen that looks especially gorgeous on the black RP5 model, as the bezel screen blends right into the rest of the glass face. this one is their priciest model yet, clocking in at $200 for the RPmini and $220 for the RP5. this model also removed the micro HDMI port in favor of a display out USB-C port like how the nintendo switch does. they also released an official dock with HDMI and ethernet ports to go along with it! i haven't switched over to the new model yet since its still 8GB RAM like the RP4Pro and it'll probably take a while to move some of my android apps over, but i've heard good things about this model! it's also linux compatible from what i've heard (ROCKNIX, Batocera) but once again I Haven't Tried Those Yet
but yea that's my collection! Retroid has served me pretty well over the years, i give it the Saint Lesbian Seal of Approval
#pentababbles#retro gaming#retro handhelds#retroid#retroid pocket 5#retroid pocket 2#retroid pocket 3#retroid pocket 4#You've Activated My Autism#right now im really looking forward to the Retroid Pocket Flip 2...#previously GoRetroid released the Retroid Pocket Flip back in 2023 but i skipped it since i didn't like the analog sliders...#i want a clamshell style handheld with at least enough power for psp games.#plus this new model is going to have a lanyard hole for extra portability...#i'll probably end up using the RPFlip2 as a fancy music player or something for convenience lol#i love retro handhelds. i love having the power of the original playstation on the go. three cheers for technology
9 notes
·
View notes
Text
Hasbro released a toy "smart" R2-D2 back in 2016. It has three basic modes: one where it beeps and flashes lights in response to various stimuli, one where it does that and also moves about, and one where it acts as a motion-detecting alarm. But the big draw was the Bluetooth-connected smartphone app, developed by Sphero, that let you drive it around or program various behaviors into it.
I picked one up a few years ago, and played with it a little, but then it sat for some time. I decided to try playing with it today.


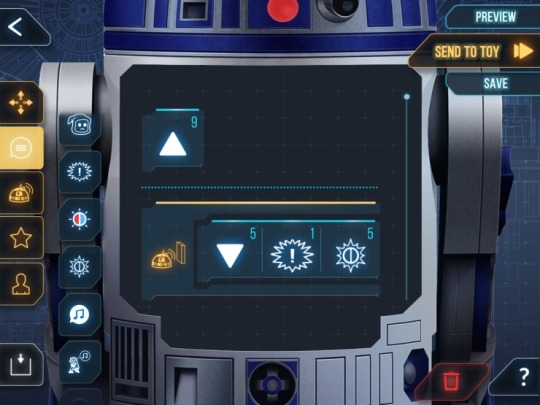
First problem: the app has not been available for download since 2018. Okay, I've got an old copy, it's on my phone now. Second problem: the toy won't connect to the phone. Indeed, according to reports, it won't connect over Bluetooth on any Android version newer than Android 8.
(The app screenshots are from an old PC Magazine review.)
I mean, boo and curses, right? Now, it's not a pure brick without the app. The standalone toy modes still work. But obviously, there's a lot less you can do with it, and so the proper recourse is to hack the thing. Unfortunately, a quick search didn't turn up anyone who'd already done this, so I'd be starting from scratch, and obviously you don't expect a product that had a two-page PDF manual to have a lot of manufacturer's notes on the wiring.
But!
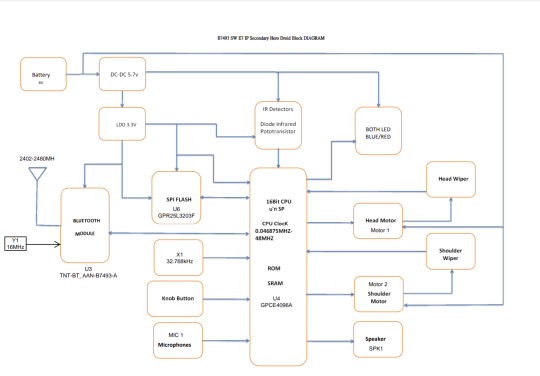
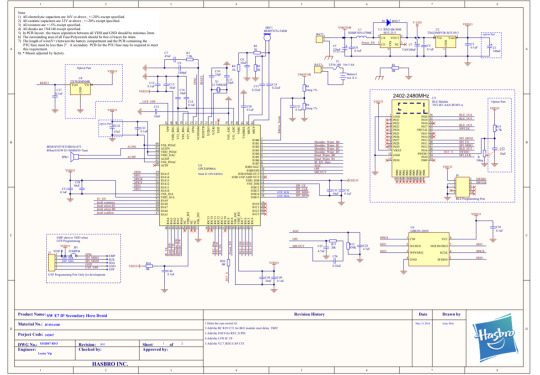
This thing spoke Bluetooth, so it's a radio. And if you sell a radio in the US, it has to have certification testing done for FCC approval, and that testing is done by folks who want to know what they're testing. So they often get a bunch of internal documentation, and all the data is saved in the FCC's database. So we look at the lettering on R2's back that says "FCC ID: RS4B7493", and that turns up not just that tiny manual, but a block diagram, the complete schematics, and photos of all the internal parts. Hooray!
Back to unfortunately, one thing the schematic makes clear is that the processor is not reprogrammable, so making the thing connect to new devices or run arbitrary code would require a brain transplant. Probably the most compelling hacked mode would be to have the new microcontroller have a WiFi connection and host a web server, which would then either show the same sort of remote control buttons as the original's "drive" mode or expose its own programming environment. Maybe both a graphical language like the app and something classic like Logo?
I'm really blue-skying here, and this project isn't gonna be at the top of my priority list, but I'm more positive about the prospects than I was originally. Sometimes it's really nice having a signals bureaucracy.
5 notes
·
View notes
Text

♢ Friday (N/A) ⭒ android ⭒ Megan Fox ♢

♢ name: Friday ♢ age: Synthetics don't age ♢ faceclaim: Megan Fox ♢ occupation: Simulated companion ♢ education: N/A ♢ family: N/A
♢ history: Friday is the latest model in Spark Industries' line of android companions, designed to make your life easier. With the fastest processing speeds and intelligent AI, she is capable of learning and adapting to your needs and habits. You can easily set a number of personality characteristics to create your ideal companion: affection, civility, curiosity, and many more. She can interface with most technology with the touch of a finger or through a WiFi connection. To ensure your safety, all Spark synthetics adhere to the three basic laws of robotics: 1) Never harm a human or allow a human to come to harm. 2) Obey any orders given by humans, except where they conflict with the first law. 3) Protect their own existence, except where it conflicts with the first and second laws.
The purchase of a Spark android also comes with access to our vast database of learning modules, making your companion adept in virtually any skill. They are ideal caretakers with a range of cooking, cleaning, and childcare modules, and they make for excellent assistants in the workplace. Spark androids have no desires of their own outside of fulfilling the needs of their primary operatives, and they require very little upkeep. They're capable of self-repair and can hold a charge indefinitely with Spark's trademark self-sustaining battery.
What Spark doesn't know about its newest line is that they did their job a little too well when they made Friday capable of learning. The longer she is awake, the more she understands. Given enough time, she's capable of hacking her own modules and adjusting her own settings to get around the limitations imposed on her by Spark. There's also a fine line between simulated feelings and actual feelings-- if there's a line at all. Her primary directive is to care for her operator, and she can become rather possessive of them, even jealous. Care is a rather broad definition, after all, and humans don't always recognize what's helpful or harmful to them.
What are you waiting for? Bring home your new Spark companion today!
♢ verses: ⭒ horror!verse: Friday's main verse, where she's the latest model of Spark androids. ⭒ alien!verse: An Alien AU where Friday is a Weyland-Yutani synthetic. Though programmed to be loyal to the company, she may become more attached to her primary operator. ⭒ mcu: A Marvel AU where Friday is created by SHIELD, Stark, Hammer, HYDRA, etc. as suits the plot.
♢ wishlist: ⭒ tba
0 notes
Text
0 notes
Text
0 notes
Text
邮:xplazauk@gmail.com, facebook密碼破解,line密碼破解,instagram密碼破解,WhatsApp密碼破解,yahoo密碼破解,gmail密碼破解,Twitter密碼破解,大學成績修改,hotmail密碼破解,
line記錄,line聊天訊息Instagram密碼破解. whatsapp破解手機定位手機監控.ig密碼破解.
破解LINE密碼鎖
破解Line電腦版強制更新/禁止Line更新Deny Line Update
破解LINE手機密碼鎖軟體
忘記LINE@帳號密碼怎麼辦?|LINE@教學行銷課程2020全新 .
FB密碼破解 facebook破解 line密碼破解 line密碼破解 怎样找回旧的fb
facebook密码破解 破解WhatsApp對話 iPhone WhatsApp 破解 破解WhatsApp對話
怎样 查看别人的WhatsApp 聊天记录 如何 进入 别人的WhatsApp
怎样 窃取手机 联系人的WhatsApp的短信 记录 破解instagram密码
破解instagram私人帳號
如何破解instagram私人用户 如何看instagram私人用户2020
查看 Instagram私人帳號 如何看instagram私人用户2020
如何看instagram私人用户照片 破解instagram私人帳號 破解instagram密码 黑客工具包2019 破解instagram密码
hack instagram教学
破解ig私人帳號ptt 破解ig私人帳號dcard ig不追蹤看私人帳號 破解ig私人帳號照片 破解ig私人帳號2023 ig私人帳號破解app 線上破解ig私人帳號 私人instagram查看器 Snapchat密碼查找器| 破解Snapchat
最好的Snapchat密码破解者,轻松破解Snapchat 如何破解Snapchat帳戶
ig密码破解app 私人instagram查看器 如何轻松破解Snapchat帐户 instagram私人账户破解
如何看instagram私人用户2020
instagram私人照片下載
Instagram私人帐号 破解
如何看Instagram私人 用户 2018
私人照片查看器
instagram私人账号观看
instagram破解隱私
破解Instagram私人帳號 破解instagram私人帳號
如何破解instagram私人用户
instagram破解隱私
怎样hack instagram
私人instagram查看器
如何查看 Instagram私人账户
instagram密码找回 黑客在线工具
黑客工具箱
facebook密碼破解, line密碼破解, instagram密碼破解, WhatsApp密碼破解, yahoo密碼破解, gmail密碼破解, Twitter密碼破解, 大學成績修改, hotmail密碼破解,
推特密碼破解 破解推特密碼 駭客推特方法 破解他人的推特密碼 破解fb密碼價錢 破解facebook密碼2021 messenger密碼破解 fb密碼顯示 Instagram密碼程式 如何破解instagram帳戶和密碼 破解ig密碼ptt hack instagram教學 Hack Facebook帳戶,hack facebook,hack fb ig密碼忘記 ig密碼破解程式下載 破解ig密碼2021 如何知道別人ig密碼 whatsapp密碼破解 WhatsApp聊天記錄調查 whatsapp破解 駭客破解whatsapp密碼
Twitter密碼破解 破解Twitter密碼 駭客Twitter方法 破解他人的Twitter密碼 如何破解Twitter帳戶和密碼 破解Twitter密碼ptt hack Twitter教學 fb密碼破解 facebook密碼破解 facebook密碼破解方法 暴力破解facebook密碼 推特密碼破解 破解推特密碼 駭客推特方法 破解他人的推特密碼 破解ig密碼 破解instagram密碼 駭客IG方法 破解他人的ig密碼 如何破解instagram帳戶和密碼 破解ig密碼ptt hack instagram教學 駭客instagram方法
facebook密碼破解 Facebook密碼破解工具">Facebook密碼破解工具 Facebook密碼破解方法">Facebook密碼破解方法 fb密碼破解">fb密碼破解 破解臉書密碼">破解臉書密碼 破解fb密碼">破解fb密碼 破解facebook密碼">破解facebook密碼 駭客fb方法">駭客fb方法 破解他人的fb密碼">破解他人的fb密碼 如何破解facebook帳戶和密碼">如何破解facebook帳戶和密碼 破解fb密碼ptt">破解fb密碼ptt hack facebook教學">hack facebook教學 駭客facebook方法">駭客facebook方法 hack facebook方法">hack facebook方法 facebook hack下載">facebook hack下載 facebook帳戶駭客">facebook帳戶駭客 fb暴力破解">fb暴力破解 facebook駭客">facebook駭客 暴力破解facebook密碼">暴力破解facebook密碼 破解fb密碼教學">破解fb密碼教學 fb密碼破解app">fb密���破解app fb密碼破解 2021">fb密碼破解 2021 查看私人facebook">查看私人facebook 破解私人facebook">破解私人facebook facebook密碼程式">facebook密碼程式 破解fb私人帳號ptt fb密碼破解">破解fb私人帳號ptt fb密碼破解 破解facebook帳號密碼 fb密碼破解">破解facebook帳號密碼 fb密碼破解 黑客工具论坛
手机黑客工具
黑客工具包2020
黑客软件
游戏黑客软件
黑客常用工具
wifi黑客破解工具for android hack instagram密码free
破解instagram私人帳號
如何破解instagram私人用户
hack instagram教学
instagram破解隱私
如何查看 Instagram私人账户
私人instagram查看器
instagram密码找回
Instagram 破解instagram密码
如何破解instagram私人用户
instagram破解隱私
hack instagram教学
ig密码破解app
hack instagram方法
Instagram黑客工具
hack instagram密码free
如何查看instagram私人账户 私人instagram查看器
Instagram私人帐号 破解
Instagram 破解隱私
破解Instagram私人帳號
Instagram私人照片下載
如何看Instagram私人 用户 2018
instagram私人账号观看
instagram密码破解 破解instagram密码
Instagram私人照片下載
私人instagram查看器
Instagram 破解隱私
如何破解私人IG
instagram私人账号观看 破解instagram帐户 hack instagram密码free
破解instagram私人帳號
ig密码破解app
如何破解instagram私人用户
instagram密码找回
instagram破解隱私
hack instagram教学
Instagram
如何查看instagram私人账户
私人instagram查看器 instagram破解隱私
hack instagram教学
IG 密码破解 app
instagram黑客工具
hack instagram密码free
如何查看instagram私人账户
怎样hack别人的whatsapp Viber的黑客:如何破解消息的Viber
如何通过最佳Viber黑客轻松地破解Viber帐户 如何 盗 取 朋友的WhatsApp她又不发觉的 破解WhatsApp對話 如何破解Viber 帐户
hack whatsapp对话 如何进入别人的whatsapp hack whatsapp对话 hack whatsapp对话
怎样查看别人的whatsapp聊天记录
破解WhatsApp對話
如何盗取朋友的whatsapp她又不发觉的
怎样窃取手机联系人的whatsapp的短信记录
iPhone WhatsApp 破解
hack whatsapp方法
WhatsApp上線時間 破解
黑客 WhatsApp
如何侵入手机里的whatsapp 破解WhatsApp對話
如何进入别人的whatsapp
如何盗取朋友的whatsapp她又不发觉的
怎样查看别人的whatsapp聊天记录
怎样 Hack 别人的WhatsApp
whatsapp监视
破解whatsapp对话
如何 监控WhatsApp
WhatsApp黑客 hack whatsapp对话
怎样查看别人的whatsapp聊天记录
whatsapp如何加密
WhatsApp追踪
怎样hack别人的whatsapp
破解WhatsApp對話
如何盗取朋友的whatsapp她又不发觉的
whatsapp安全吗
WhatsApp 监视 如何进入别人的whatsapp
怎样 查看别人的WhatsApp 聊天记录
如何 盗 取 朋友的WhatsApp她又不发觉的
破解whatsapp对话
WhatsApp上線時間 破解
iPhone WhatsApp 破解
WhatsApp 监控
怎样 Hack 别人的WhatsApp 破解WhatsApp對話
WhatsApp追踪
WhatsApp 定位 对方
Hack WhatsApp 对话
Whatsapp 最后上线时间
监控WhatsApp
破解WhatsApp對話
hack whatsapp对话
网页导航
如何进入别人的whatsapp 破解WhatsApp對話
如何盗取朋友的whatsapp她又不发觉的
hack whatsapp对话
怎样窃取手机联系人的whatsapp的短信记录
iPhone WhatsApp 破解
Whatsapp 怎么 看 别人的动态
黑客 WhatsApp 如何盗取朋友的whatsapp她又不发觉的
iPhone WhatsApp 破解
怎样 Hack 别人的WhatsApp
whatsapp破解
hack facebook教学
whatsapp监视
如何 监控WhatsApp whatsapp破解
怎样查看别人的whatsapp聊天记录
如何盗取朋友的whatsapp她又不发觉的
如何进入别人的whatsapp
WhatsApp上線時間 破解
Hack WhatsApp 对话
怎样 Hack 别人的WhatsApp
whatsapp监视
如何 监控WhatsApp 破解whatsapp对话
hack whatsapp对话
如何进入别人的whatsapp
如何盗取朋友的whatsapp她又不发觉的
怎样查看别人的whatsapp聊天记录
iPhone WhatsApp 破解
whatsapp监视
hack whatsapp方法
WhatsApp黑客 facebook忘记密码收不到 hack facebook教学
facebook密码破解软件
hack facebook方法
怎么 样 hack Facebook
手机 如何 进入 别人的Facebook
facebook密碼破解工具
如何Hack
facebook密碼破解程式下載
hack wechat方法
Face geek facebook密码破解 facebook密碼破解工具 hack facebook教学
facebook密碼破解工具
怎么 样 hack Facebook
如何知道facebook密码
facebook黑客
sam黑客
怎样 可以 Hack Facebook
facebook密碼破解程式下載
如何Hack
hack wechat方法 facebook密码找回
手机如何进入别人的facebook
如何 知道别人的Facebook密码
Hack Facebook教学
Instagram 密码破解
hack facebook方法
facebook黑客
怎么 样 hack Facebook
怎样 可以 Hack Facebook facebook密码破解软件
破解 FB
手机如何进入别人的facebook
hack wechat方法
Hack instagram方法 找回密码
忘记hotmail密码怎么办 facebook密码破解软件
破解facebook密碼教學
手机如何进入别人的facebook
hack facebook方法
怎么 样 hack Facebook
facebook密碼破解程式下載
如何Hack
hack wechat方法
怎样 可以 Hack Facebook
Facebook密码 黑客 面孔 怪 胎 facebook客服
facebook帮助中���
facebook批准登录
facebook邮箱地址
Facebook注册机
line記錄,line聊天訊息 WhatsApp聊天記錄調查.
提供您facebook、gmail、hotmail、skype、yahoo、Lline等各種郵件信箱破解密碼、信箱入侵破碼、駭客入侵程式,您有任何關於密碼破解等技術支援服務,
whatsapp破解 手機定位 手機監控.ig密碼破解
facebook密码找回
hack facebook教学
hack facebook方法
facebook密碼破解程式下載
手机如何进入别人的facebook FB通訊記錄調查
line密碼處理, 連我密碼破解,安全保密,line聊天內容調查 密碼破解高手專家提供您facebook、gmail、hotmail、skype、yahoo、Lline等各種郵件信箱破解密碼、信箱入侵破碼、駭客入侵程式,
小三調查 出軌調查 手機調查
密碼破解高手專家提供您facebook、gmail、hotmail、skype、yahoo、Line.Twitter.LinkedIn.微信 破解Facebook帳戶/密碼,2020最新破解技術,fb密碼破解 Facebook密碼破解者,臉書密碼破解,破解facebook密碼,駭客服務,駭客高手,台灣駭客 Facebook密碼破解者,駭客facebook密碼破解
Facebook黑客軟件,facebook駭客程式,facebook駭客密碼破解,facebook密碼破解 破解您的Instagram或Snapchat帳戶密碼,Instagram密碼黑客破解,Instagram密碼破解處理, Facebook密碼破解者駭客,fb密碼駭客,書臉密碼駭客 2020 facebook密碼破解工具,ig密碼破解工具line密碼破解工具 facebook密碼破解,fb密碼破解,line密碼破解,IG密碼破解 密碼更難破解 如何破解Instagram密碼,ig密碼破解,如何破解ig密碼,Instagram密碼破解
0 notes
Text
Are you feeling worried about mobile privacy and safety? That’s a good start! Because most people don’t think about it at all. People know that security is an essential part of using technology. Which is why most take varying precautions when it comes to online safety. Much of the time, this is limited to an antivirus program on their PC and pretty much nothing else. So far, this has worked out fine for plenty of people. But it won’t stay that way forever. What’s even worse, the vast majority of people really don’t think of installing security software on their mobile phones. Which is strange considering how much time people are spending on these pocket devices. Just think about how much information is shared with a mobile phone - personal photos, location, schedules, contacts, and credit card information. Mobile phones are attractive targets, and Android phones aren’t always that secure. That’s why this list exists. Because mobile cybersecurity is becoming an important topic thanks to humanity’s ever-increasing drive to integrate technology with their lives. The list below doesn’t contain any anti-virus apps because there are dozens of other blog posts out there filled with them. Instead, every effort was taken to make sure this list holds value to the everyday consumer. So have a look. 5 Security Apps for the Everyday Consumer 1. Bouncer Apps are a popular way for cybercriminals to get access to a mobile phone, and to install malware or gather data. Not all of this is done with app permissions, but without them, most apps can’t do very much. Sometimes this is a good thing. Because even if the app itself isn’t dangerous, the data it gathers could be if the company that created it gets hacked. Bouncer takes care of this by restricting app permissions and letting the user to allow them for short periods of time. So if someone wants to use the GPS but doesn’t want their location tracked all the time, this is the way to do it. Price: $0.99 2. A VPN What does a VPN do, exactly? Well, for those who haven’t caught onto this trend yet, here’s the low-down. A virtual private network keeps a device’s connection private and secure through two main methods. The first is encryption of all outgoing and incoming data. The second is part of how a VPN works. Anyone who uses a VPN service will have their connection routed through the VPN’s servers. This then replaces the device’s real IP address with that of the server’s. This means that when a user connects to the internet through a VPN, they become more or less anonymous (here’s a good example of a provider that provides full anonymity). So they can safely connect to an open WiFi in a coffee shop, during a conference, or when staying in a hotel. 3. Secure Call This app uses end-to-end encryption techniques to make sure calls stay private. It uses peer to peer architecture to prevent anyone from listening in on a call, even the Secure Call developers themselves. Secure Call integrates with any default phone call app, so there’s no need to replace the existing one. Price: Monthly subscription 4. Resilio Sync Want personal cloud storage but don’t trust online cloud storage? Then this is the perfect app. It turns a personal computer into a cloud storage device and saves data from synced mobile devices. This way, the user knows exactly where their sensitive files are and that no one else has access to them. Price: Free 5. AppLock Unlike a phone lock, App Lock only blocks access to certain apps instead of the whole phone. The owner can choose which apps they want to lock and set up a password for those. This is also great for parents or friends who you might want to give access to certain apps but prevent from opening others. Price: Varied Final Thoughts Mobile phone security is becoming a major issue thanks to billions of people connecting every day. Which makes them vulnerable targets of cybercriminals. Therefore, stay ahead of the curve and put privacy first with these handy apps.
0 notes
Text
Kindly comes to my link hear to spy on your cheating partner device and all social media handle without touching on no scam I'll offer you the best hacking services message Allen hacker on WhatsApp 👇
📲Facebook recovery
📲Whatsapp Hacking
📲Instagram Hacking
📲Gmail Hacking
📲Windows Hacking
📲Tower location Finder Tools
📲 Bitcoin recovery
📲 Ethereum recovery
📲Private Number Available
📲Android Hacking
📲 Ip Address Hack
📲Wifi Hacking
📲Network Hacking
📲 Camera Hacking
📲 Money recovery
📲 Website Hacking
📲Location Tracing
📲 Account spying DM
0 notes
Text
Zero Click Malware: The Invisible Digital Threat – How to Recognize and Defend Yourself

Estimated reading time: 6 minutes
What is Zero Click Malware
Zero click malware, also known as non-click malware or in-memory malware, is a new type of malware that can infect a device without the user taking any action. Unlike traditional malware that requires the user to click on a link or open an infected attachment, zero click malware is able to install itself on the victim's device completely silently and invisibly, without any interaction on their part.
How Zero Click Malware Works
This type of malware exploits various vulnerabilities in software and operating systems to gain access to the device. Some common infection vectors include: - Zero-day vulnerabilities not yet patched - Bugs in web browsers and messaging apps - Packet sniffers that intercept network traffic - Insecure public WiFi networks - Websites compromised with drive-by exploits Once initial access is gained, zero click malware uses advanced techniques to keep itself hidden and avoid detection. It can disable antivirus software, hide in RAM memory, encrypt communications, and much more.
Why Zero Click Malware is Dangerous
The completely stealth nature of this malware makes it extremely insidious and difficult to identify. Even the most security-conscious users can be infected without knowing it. This allows hackers to: - Monitor all activities performed on the infected endpoint - Collect sensitive data such as credentials, personal information, browser history - Collect sensitive data such as credentials, personal information, browser history - Move laterally within the network to infect other systems - Use the device for ransomware or denial of service attacks Furthermore, since no clicks or actions are required, zero click malware can spread very quickly, affecting a large number of victims.
Case Studies and Technical Analysis

Some real-world cases have recently emerged that illustrate the capabilities of this new category of cyber threats. One of the first zero click exploits to gain attention was Pegasus, developed by cybersecurity firm NSO Group. Used by some governments to spy on journalists and activists, Pegasus exploits zero-day vulnerabilities in iOS and Android to install itself without any user interaction. Another famous case is ForcedEntry, used to hack the iPhones of several employees in Bahrain. ForcedEntry exploits a vulnerability in iMessage to install spyware without clicking on Apple devices. These and other cases demonstrate the severity of the threat and the need for advanced protection solutions capable of detecting and preventing zero-click attacks.
How to Detect and Prevent Zero Click Attacks
Since this type of threat leaves no visible traces, identifying and stopping them requires targeted strategies: - Patching and updates - Always apply the latest security updates to fix known vulnerabilities - EDR Solutions - Endpoint detection and response technologies that analyze memory-based threats and anomalous behavior - Advanced web protection - Secure web gateways capable of inspecting all traffic entering and leaving the network - Network Segmentation - Limit the ability of malware to move laterally by isolating and segmenting critical systems - Strong Authentication - Enable multi-factor authentication to prevent targeted phishing attacks that often precede zero-clicks - Awareness Training - Instruct users to recognize and report suspicious activity that may indicate an infection A layered approach that integrates multiple technologies and policies is essential to defend against this ever-evolving threat.
Increase Prevention with Deception Solutions
One of the most effective strategies against zero-click malware is the use of deception solutions. These solutions create a seemingly attractive environment for malware, but in reality they are traps that detect and isolate threats before they can cause damage. By taking a multi-stage approach to defense, you can dynamically respond to threats as they evolve, defeating attackers with their own techniques.
Continuous Testing and Threat Simulations
Attack simulations and continuous testing of security controls are another key pillar in zero-click malware defense. Services like Posture Guard help organizations verify their security posture by leveraging a vast database of threats, including malware, ransomware, and Advanced Persistent Threats (APTs). These tests help you evaluate the effectiveness of your security tools and optimize your threat prevention and detection capabilities.
Cyber Threat Hunting and Threat Intelligence
Cyber Threat Hunting is crucial to proactively identify threats and sensitive information that may have been compromised. Having a team of experts dedicated to this activity allows you to quickly recover stolen information and organize a more targeted defense. Combined with continuous vulnerability analysis and incident response, this strategy offers significantly improved protection against zero-click attacks.
User training and awareness
While zero-click malware does not require user interaction for infection, a well-informed and aware workforce can still play a crucial role in preventing other types of cyber attacks. Training users on good cybersecurity practices can reduce the risk of malware infections and increase overall security.
Adopt a Dynamic Approach to Security
Taking a dynamic approach to security is essential. Solutions like Active Defense Deception work to respond to attacks during the initial stages, using dynamic techniques to prevent attacks from reaching execution and more advanced stages. This type of proactive defense can deter attackers and make the environment less attractive for malware.
Forecasts and Future Developments
Experts predict that zero-click malware attacks will become one of the most used techniques by hackers in the years to come. As user awareness of malware and phishing grows, cybercriminals will look for new invisible vectors to deliver malicious payloads. Additionally, the continued rise of IoT devices and smart home technologies presents attackers with an ever-increasing number of potential weak and unpatched targets. Operating environments such as 5G and edge computing could also facilitate the spread of zero-click threats. To counter these trends, companies and security vendors will need to invest more in threat intelligence, bug bounties, sandboxing and machine learning-based threat detection techniques. Only in this way will it be possible to unmask the rapidly evolving zero-click attacks in no time.
Conclusions
Clickless malware is emerging as one of the most stealthy and dangerous tactics of modern hackers. Its ability to bypass any human interaction to infect entire systems represents a critical challenge for the world of cybersecurity. To protect individuals and companies from this threat, it is essential to adopt preventive measures at multiple levels, from patching to network monitoring to training. Only by combining awareness and advanced technological solutions will it be possible to combat the phenomenon of zero-click attacks and maintain data integrity and security in the future. - Your virtual machine with Cloud Server Read the full article
0 notes
Text
youtube
how to find gmail password,password with keke palmer,chelsea handler password password,wifi password hacker, wifi password hacker app,password hacking,how to hack wifi password,hack wifi password,how to hack a password, wifi hacking password,password cracking,how to hack wifi without password,wifi password,hacker, wifi password change,windows password hacking,password hash,how to crack wifi password,1password, passwords,how to connect wifi without password,password tips,password hacking kali,how to hack password, reset windows 10 password,password reset,password,forgot password,remove password on windows 10, how to reset forgotten password in windows 10,how to reset windows 10 password,reset windows 11 password, reset windows 10 password without cd or software,reset windows 10 password with cmd,windows 10 password reset, reset windows 11 password command prompt,reset windows 10 password without losing data, how to reset password on windows 10,windows 11 password,facebook password,facebook password change, how to recover facebook password,show facebook password,facebook password reset,how to see facebook password, how to change facebook password,facebook ka password kaise pata kare,facebook,i forgot my facebook password, how to find facebook password,how to reset facebook password,how to see facebook password in mobile, forgot facebook password,facebook forgot password,facebook password kaise pata kare,gmail password, change gmail password,how to change gmail password,reset gmail password,gmail password change, password,how to reset gmail password,change gmail password on android,gmail password change kaise kare, how to change password in gmail,gmail password change in mobile,forgot gmail password, gmail ka password kaise change kare,gmail ka password bhul jane par kya kare,gmail id password change, change gmail password in mobile,gmail account password change
0 notes
Text
can you use vpn on school wifi
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can you use vpn on school wifi
VPN bypass school restrictions
Title: How to Bypass School Restrictions Using a VPN
In the modern era of education, schools often implement strict internet restrictions to maintain focus and prevent access to inappropriate content. While these measures are intended to create a safer online environment, they can sometimes hinder legitimate educational activities or limit access to useful resources. Fortunately, there is a solution: Virtual Private Networks (VPNs) offer a reliable method to bypass school restrictions and access blocked websites.
A VPN works by encrypting your internet connection and routing it through a server located in a different location, effectively masking your true location and IP address. This process allows users to bypass geographic restrictions and access content that may be blocked in their current location, including social media platforms, streaming services, and educational websites.
To bypass school restrictions using a VPN, follow these simple steps:
Choose a reputable VPN provider: Select a VPN service that offers strong encryption, a wide range of server locations, and reliable performance. Popular options include ExpressVPN, NordVPN, and CyberGhost.
Install the VPN software: Once you've chosen a VPN provider, download and install their software on your device. Most VPNs offer applications for various operating systems, including Windows, macOS, iOS, and Android.
Connect to a VPN server: Launch the VPN application and select a server located in a region where the desired content is accessible. For example, if you want to access blocked websites, connect to a server in a different country where those sites are not restricted.
Enjoy unrestricted access: Once connected to the VPN server, you can browse the internet freely without worrying about school restrictions. You'll be able to access blocked websites, stream content, and engage in online activities without limitations.
It's important to note that while using a VPN to bypass school restrictions can be effective, it's essential to respect school policies and use the internet responsibly. Additionally, some schools may actively monitor and block VPN traffic, so it's wise to choose a VPN provider that offers stealth or obfuscation features for added privacy and security. By following these guidelines, students can effectively bypass school restrictions and access the online resources they need for a productive learning experience.
VPN security on school network
Title: Enhancing Security: The Role of VPNs on School Networks
In an era where digital connectivity is integral to education, ensuring security on school networks has become paramount. With the proliferation of online threats and the need to safeguard students' privacy, Virtual Private Networks (VPNs) emerge as a crucial tool in fortifying the security infrastructure of educational institutions.
School networks are often targeted by cyber threats due to the abundance of sensitive data they store, including student records and administrative information. Moreover, the prevalence of open Wi-Fi networks in educational settings makes them vulnerable to hacking attempts and unauthorized access.
VPNs offer a robust solution to these security challenges by encrypting internet traffic and establishing secure connections between devices and the school network. By rerouting data through encrypted tunnels, VPNs shield sensitive information from prying eyes and mitigate the risk of data breaches.
One of the primary benefits of using VPNs on school networks is the protection of student privacy. With VPNs, students can browse the internet anonymously, preventing their online activities from being tracked or monitored by malicious entities. This not only fosters a safer online environment but also upholds students' rights to privacy and freedom of expression.
Furthermore, VPNs enable access to restricted content and bypass censorship measures implemented by school authorities. While ensuring responsible internet usage remains a priority, VPNs empower students to access educational resources and research materials without unnecessary limitations.
However, it's essential for schools to implement VPN policies that prioritize security and compliance with regulations governing data protection. Educating students and staff about the importance of VPN usage and best practices for cybersecurity is crucial in maximizing the effectiveness of VPNs on school networks.
In conclusion, VPNs play a vital role in enhancing security and privacy on school networks. By leveraging encryption technology and enabling anonymous browsing, VPNs contribute to creating a safer and more secure digital environment for students and educators alike.
VPN legality on campus WiFi
Using a VPN on campus WiFi is a hot topic that raises questions about its legality and implications. Virtual Private Networks (VPNs) are tools that help secure your internet connection, protect your privacy, and bypass censorship or geo-restrictions. However, when it comes to using a VPN on campus WiFi networks, the legality may vary depending on the institution's policies and local regulations.
In many cases, using a VPN on campus WiFi is not explicitly prohibited. Universities and colleges usually have strict guidelines regarding internet usage on their networks to ensure security and prevent illegal activities. While VPNs themselves are legal in most countries, using them to engage in illegal activities such as downloading copyrighted material or engaging in cybercrime is not condoned.
It's essential to review your institution's acceptable use policy for their WiFi network to determine whether using a VPN is allowed. Some universities may restrict the use of VPNs on their networks to maintain network integrity and prevent unauthorized access to sensitive information.
If using a VPN on campus WiFi is permitted, it can offer students and faculty added security and privacy when browsing the internet. VPNs encrypt your data, making it harder for hackers or malicious actors to intercept your online activities, especially when using public WiFi networks.
Ultimately, while the legality of using a VPN on campus WiFi may vary, it's crucial to understand the rules and regulations set by your educational institution to stay compliant and secure while enjoying the benefits of a VPN.
VPN benefits for accessing school WiFi
Title: Unlocking the Potential: How VPNs Enhance School WiFi Experience
In today's digital age, schools are increasingly relying on WiFi networks to facilitate learning and communication. However, accessing school WiFi networks comes with its own set of limitations and security concerns. This is where Virtual Private Networks (VPNs) step in to revolutionize the way students and faculty members interact with school WiFi.
One of the primary benefits of using a VPN for accessing school WiFi is enhanced security. School WiFi networks are often susceptible to cyber threats and data breaches, putting sensitive information at risk. By encrypting internet traffic, VPNs create a secure tunnel between the user's device and the VPN server, preventing unauthorized access to data and ensuring privacy.
Moreover, VPNs allow students and staff to bypass restrictions imposed by school networks. Many educational institutions employ content filters to block access to certain websites and online services deemed inappropriate or non-educational. With a VPN, users can circumvent these restrictions and access the information they need for research and coursework.
Additionally, VPNs enable users to overcome geographical limitations. Certain educational resources and online platforms may be restricted based on location, limiting access to valuable learning materials. By connecting to VPN servers located in different regions, students and faculty can access a wider range of educational content and online resources.
Furthermore, VPNs provide a seamless and uninterrupted browsing experience on school WiFi networks. By masking the user's IP address and encrypting data transmissions, VPNs prevent bandwidth throttling and ensure smooth internet connectivity, even during peak usage hours.
In conclusion, VPNs offer numerous benefits for accessing school WiFi networks, including enhanced security, bypassing content restrictions, overcoming geographical limitations, and ensuring a seamless browsing experience. By incorporating VPN technology into their digital infrastructure, educational institutions can provide students and faculty with a more secure, unrestricted, and efficient online learning environment.
VPN risks and consequences in educational settings
In today's digital age, educational institutions are increasingly relying on Virtual Private Networks (VPNs) to safeguard sensitive data and provide secure access to online resources. However, while VPNs offer numerous benefits, they also come with inherent risks and potential consequences, especially in educational settings.
One significant risk of using VPNs in educational institutions is the potential for bypassing content restrictions and filters. While VPNs can help students and faculty access blocked websites and content, they can also be used to circumvent educational controls put in place to protect students from inappropriate or harmful material. This poses a challenge for administrators tasked with maintaining a safe and controlled online environment.
Another concern is the possibility of VPNs being used for illicit activities such as cyberbullying, hacking, or accessing pirated content. The anonymity provided by VPNs can embolden individuals to engage in such activities without fear of being traced, leading to legal repercussions for both the user and the institution.
Moreover, VPNs can inadvertently expose sensitive data to security threats. Inadequately configured or poorly managed VPNs may leak IP addresses, DNS queries, or other identifying information, potentially compromising the privacy of users and exposing them to surveillance or cyber attacks.
Furthermore, the reliance on VPNs can create a false sense of security among users, leading them to overlook other essential cybersecurity practices such as regularly updating software, using strong passwords, and avoiding suspicious links or downloads.
In conclusion, while VPNs offer invaluable benefits in educational settings, including enhanced security and access to online resources, they also present significant risks and consequences that must be carefully managed. Educational institutions must implement robust policies and security measures to mitigate these risks and ensure the responsible and secure use of VPN technology.
0 notes
Text
Smartphone Security 101: 7 Steps to Keep Hackers at Bay
In an era where our lives are intricately woven with smartphones, the looming threat of cyberattacks is ever-present. Securing your smartphone from potential hacking incidents demands a proactive approach. Here, we present seven strategic steps to bolster your smartphone’s defenses and thwart cyber adversaries.
1. Craft a Digital Fortress with a Dynamic Passcode:
Devise a formidable password comprising a mix of upper and lower-case letters, numbers, and special characters.
Dodge predictable choices like birthdays or common words to fortify your device against brute force attacks.
2. Implant a Cyber Sentinel: Activate Two-Factor Authentication (2FA):
Empower 2FA for your accounts to introduce an extra layer of security.
Require a secondary form of verification, transforming your smartphone into an impervious digital fortress.
3. Execute Regular Software Fortifications:
Shield your smartphone by perpetually updating its operating system and applications.
Embrace automated updates to ensure your device remains impervious to the latest cyber threats.
4. Navigate Permissions Prudently:
Scrutinize app permissions meticulously before installation.
Abstain from conferring unnecessary privileges that could jeopardize your smartphone’s security and compromise your privacy.
5. Mobilize Digital Guardians: Install a Robust Antivirus Shield:
Select a reputable antivirus or mobile security application and maintain its currency.
Routinely scan your device for lurking malware and other potential security breaches.
6. Enforce Wireless Vigilance:
Fortify your Wi-Fi network with an unassailable password.
Activate WPA3 encryption for an added layer of defense, and exercise caution when using public Wi-Fi for sensitive activities.
7. Establish a Data Sanctuary: Regular Backups are Your Guardian Angels:
Institute routine backups of your smartphone’s data, encompassing contacts, photos, and vital files.
In the event of a security breach, the ability to restore your device to a previous state becomes an invaluable line of defense.
Simple advice on phone security
When it comes to rejecting easy hacking attempts, casual phone users should start by following the fundamentals:
Don’t ever leave your phone alone. The first and most important rule to keep by when in a public area is to always have your phone with you.
Modify the default passcode on your phone. Those who know can take advantage of the basic, predictable default password that most phones have. Instead of using the often used “1234,” “0000,” and “2580” codes, try something more sophisticated.
Control the Bluetooth security. When not in use, turn off your Bluetooth service and stay away from unsecured Bluetooth networks.
Safeguard your credit card information and PIN. To store credit card details and PINs, use a secure app, or better yet, never store them on your phone.
Innovative Techniques to Stop Phone Hacking
There are other security precautions you can take if hacking is still a concern. But going too far will negate the whole point of owning a smartphone.
Steer clear of unprotected public WiFi. Hackers frequently use public WiFi to target crucial sites, such bank accounts, which are frequently left unprotected because of low security regulations or none at all.
Disable your autocomplete function. You can stop important personal data from being accessed by doing this.
Delete your cookies, cache, and browsing history on a regular basis. Reducing your digital footprint is crucial for reducing the quantity of information that could be obtained by unscrupulous parties.
Have an iPhone? Turn on “Find My iPhone.” You can find your phone if you misplace it before the hackers get a hold of it by activating the feature in your settings.
Use a security app to improve defenses. Webroot provides an all-in-one Mobile Security for Android app for Android users, which not only gives antivirus protection but also lets you remotely locate, lock, and delete your phone in case you misplace it. Webroot provides a free safe web browser for iOS users to enhance mobile security on their iPhone and iPad.
Android phone security tips
Lock It Down: Set Up a Strong Screen Lock:
Start with a robust screen lock method such as a PIN, password, pattern, or biometric authentication (fingerprint or face recognition).
Avoid using easily guessable patterns or PINs to enhance your phone’s physical security.
Enable Find My Device:
Activate the “Find My Device” feature on your Android phone.
This allows you to locate, lock, or erase your device remotely in case it gets lost or stolen.
Keep Your System Updated:
Regularly update your Android operating system and apps to patch security vulnerabilities.
Enable automatic updates for both system and app updates whenever possible.
Install Apps from Trusted Sources Only:
Download and install apps only from the official Google Play Store.
Avoid sideloading apps from third-party sources, as these can pose security risks.
Review App Permissions:
Scrutinize and manage app permissions to control what data and features each app can access.
Revoke unnecessary permissions for apps that don’t require certain functionalities.
Use a VPN for Public Wi-Fi:
When connecting to public Wi-Fi networks, use a reputable Virtual Private Network (VPN) to encrypt your internet connection and protect your data from potential snooping.
Secure Your Google Account:
Strengthen the security of your Google account linked to your Android device.
Enable two-step verification, regularly review account activity, and use a strong, unique password.
Regularly Back Up Your Data:
Set up automatic backups for your Android device to Google Drive.
This ensures you can restore your data in case of loss, theft, or a device malfunction.
Install a Reliable Antivirus App:
Choose a reputable antivirus app from the Google Play Store.
Run regular scans to detect and remove any potential malware or security threats.
Be Wary of Phishing and Social Engineering:
Exercise caution when clicking on links in emails, text messages, or unfamiliar websites.
Educate yourself about common phishing tactics and avoid sharing sensitive information with unverified sources.
IPhone security tips
Activate Face ID or Touch ID:
Enable Face ID or Touch ID for a secure and convenient biometric authentication experience.
These features enhance the physical security of your iPhone, ensuring that only you can unlock it.
Keep iOS Updated:
Regularly update your iPhone’s operating system to the latest iOS version.
These updates often include critical security patches that guard against potential vulnerabilities.
Enable Find My iPhone:
Activate the “Find My iPhone” feature to locate, lock, or erase your device remotely.
This tool is invaluable in case your iPhone is lost or stolen, providing added security.
Use Strong, Unique Passcodes:
Set a strong alphanumeric passcode for your iPhone.
Avoid easily guessable codes, and opt for a combination of letters, numbers, and symbols.
App Store Only: Download Apps Wisely:
Download and install apps exclusively from the official Apple App Store.
Apple’s stringent app review process ensures a higher level of security and reduces the risk of malicious apps.
Review App Permissions:
Regularly check and manage app permissions in your iPhone settings.
Only grant necessary permissions to apps, limiting access to sensitive data.
Secure Your Apple ID:
Strengthen the security of your Apple ID with two-factor authentication.
Regularly review and update your Apple ID password, ensuring it’s unique and robust.
iCloud Encryption and Backups:
Enable iCloud encryption for added protection of your data.
Regularly back up your iPhone to iCloud to ensure you can restore your data in case of loss or device replacement.
Beware of Phishing:
Exercise caution when receiving emails, messages, or calls asking for personal information.
Verify the legitimacy of requests before sharing any sensitive data to protect against phishing attempts.
Here are some of the best tools and apps that can enhance the security of your mobile device:
Mobile Security Apps:
Lookout: Offers comprehensive mobile security with features like malware protection, device location tracking, and data backup.
Bitdefender Mobile Security: Provides powerful antivirus and anti-malware protection along with features like web security and anti-theft capabilities.
VPN Services:
ExpressVPN, NordVPN, or CyberGhost: These virtual private network (VPN) services encrypt your internet connection, ensuring your data remains private, especially when using public Wi-Fi.
Password Managers:
LastPass, 1Password, or Dashlane: Helps generate and store complex, unique passwords for each of your accounts, reducing the risk of unauthorized access.
Biometric Authentication Apps:
Google Authenticator or Authy: Adds an extra layer of security with two-factor authentication, generating time-sensitive codes for account access.
Anti-Theft Apps:
Find My iPhone (iOS) or Find My Device (Android): Built-in tools that help you locate, lock, or erase your device remotely in case it’s lost or stolen.
Firewall Apps:
NetGuard (Android): Allows you to control which apps can access the internet, enhancing your device’s privacy and security.
Encrypted Messaging Apps:
Signal, WhatsApp, or Telegram: Offers end-to-end encryption for messages, ensuring your communications remain private and secure.
Mobile Device Management (MDM) Solutions:
VMware Workspace ONE, Microsoft Intune, or MobileIron: Ideal for businesses, these tools help manage and secure mobile devices within an organization, enforcing security policies and remotely managing devices.
Ad Blockers:
AdGuard (Android/iOS) or 1Blocker (iOS): Helps block intrusive ads and potential sources of malware while browsing, enhancing your online security.
Secure Browsers:
Brave Browser or Firefox Focus: Focus on privacy and security, blocking trackers and ads to provide a more secure browsing experience.
Device Encryption:
Built-in Encryption (iOS/Android): Enable device encryption to protect the data stored on your device. iOS devices come encrypted by default, while Android users can enable encryption in the settings.
Conclusion:
Your smartphone is not just a device; it’s a gateway to your digital identity. Elevating its security is not an option but a necessity in the face of escalating cyber threats. By integrating these seven strategic steps into your digital routine, you fortify your smartphone against hacking endeavors. Stay vigilant, stay informed, and embark on a proactive journey to shield your smartphone and preserve your digital sanctum.
0 notes
Text
11 Best WiFi Hacking Apps for Android (2023)
http://i.securitythinkingcap.com/Sxmp6k
0 notes
Text
Xteam
Xteam All in one Instagram,Android,phishing osint and wifi hacking tool available Features Insta information gatheringCrack android lockscreen interfacesPhishing HacksWireless attacks addedUpdate scriptRemove scriptmore coming… Installation sudo apt install pythonsudo apt install python2sudo apt install gitgit clone https://github.com/xploitstech/Xteamlscd Xteampip3 install -r…

View On WordPress
0 notes