Don't wanna be here? Send us removal request.
Text
COMP6441 Something Awesome – Writeup for Email Phishing
I have no idea why the quality of the uploaded images is that low. You can download this writeup directly from the link below:
https://drive.google.com/file/d/1GVb3ZnSgjDTONqDF9wrP9Fvd3huSDoyB/view?usp=sharing
1. Introduction
Email phishing is using email to trick victims into clicking bogus links to collect sensitive information such as username and password, or downloading malware. In this document, I will introduce the detailed procedures to achieve Email phishing to collect victim’s Username and Password and suggestions to prevent phishing attacks.
2. Achievement process
The project environment is based on Kali Linux (Version 2019.2) which you can download the image at this link.
1) Expose the Localhost (Port 80) to the public internet.
It is essential to expose the Localhost port 80 to the public internet so that the victim outside of my subnet can also visit my webserver.
Exposing the localhost can be done by the tool named “Ngrok“ which you can download at this link.
After initializing the Ngrok, I can expose my localhost by executing the command:
“./ngrok http 80”
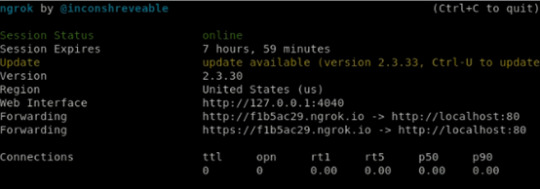
Then I get the URL address “https://f1b5ac29.ngrok.io” which can be used to access my Localhost port 80:
2) Setting up a web server which is cloned from Facebook Login page.
The target website is Facebook and this site can be easily cloned by The Social-Engineer Toolkit (SET). The SET had already installed in Kali so I don’t need to install it. The site clone can be achieved as below:
1. Run the program through command “setoolit”
2. Select 1 ->“Social-Engineering Attacks”
3. Select 2 ->” Website Attack Vectors”
4. Select 3 -> “Credential Harvester Attack Method”
5. Select 2 -> “Site Cloner”
6. Enter the Localhost URL, which is “https://f1b5ac29.ngrok.io”
7. Enter the target URL of target website “www.facebook.com”

Then the fake Facebook server now starts running on “https://f1b5ac29.ngrok.io”. When access this link, the webpage popped up is identical to the Facebook login page:

3) Send decorated phishing email pretended to be the official email from Facebook
I wrote a python script named “send_email_html.py” to send HTML format email by Google SMTP server, the script is shown below:

This python script requires inputting three arguments:
First argument is the path name of the file which contains HTML code for email displaying:

The HTML code can be cloned by finding a received email from Facebook and clicking the ‘show original’ button from the Gmail GUI.
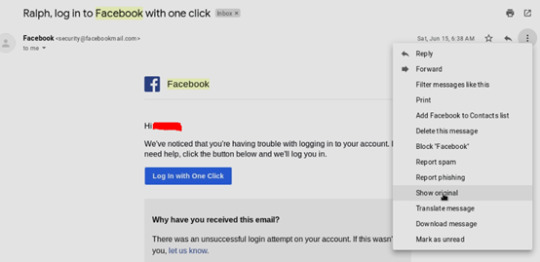
The HTML code in quoted-printable format is shown at the bottom of the page and can be decoded online to get the real email HTML code.


The email will look identical to the original one If I send this HTML code out without modification. However, I modify some text to make it more sense as a phishing email.
Second argument is the pathname of the file which contains the victim’s name and email address.

The last argument is the URL address of the Localhost which is “https://f1b5ac29.ngrok.io”
Finally, the python script read all input files, modify the HTML code based on victim’s information and send the email out. The syntax to call this script is:
“python send_email_html.py html_code user_info direct_link”

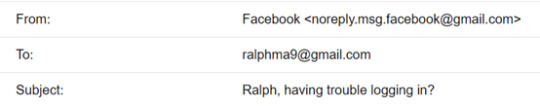
The victim will receive the email and it seems come from Facebook official. The phishing email is shown below:

4) Data analysis to get the username and password
The site clone will generate a report after pressing “CTRL + C” and show the pathname of that report:
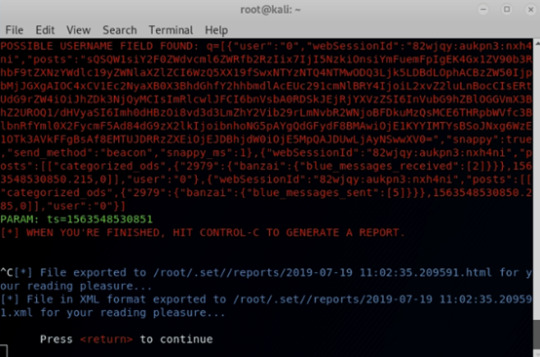
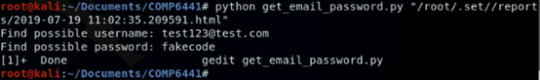
I wrote a python script named “get_email_password.py” to analyze the report and print out the possible username and password. The script requires inputting one argument which is the the pathname of the report. The script is shown below:

Finally, I execute this script and get the victim’s username and the corresponding password.
3. Suggestions to avoid phishing attacks
1. Protecting personal privacy:
Your privacy is worth protecting. In this case, If the hacker doesn’t know your name, the phishing email will look suspicious. If the hacker doesn’t know the email address, the hacker could not be able to send you an email.
The suggestions to protect your privacy are listed below:
1. Read privacy policies before sign up an account.
2. Be aware of your mobile security.
3. Don’t sell your information for free food or service.
4. Be careful what you share on social media.
5. Always ask how and who collect your information.
2. Checking where the email comes from carefully
You need to check the source email address carefully, not the canonical name display at the front such as Facebook, but the full email address like “[email protected]”.

This is because the canonical name can be easily faked, but fraud full address could be hard. You can always check the source email address by clicking “Show Original“ bottom. You need to familiar with the email address from frequently used services or websites and check each email carefully.
In this case, if the victim found the wired source email address named “[email protected]”, he may then close the email and click “report spam”.
3. Checking the link address carefully before clicking.
Every link or attachment appears in the email could be bogus link or malware. It is essential to check them carefully before clicking. Installing anti-virus software and firewall could help to detect possible malware or Trojan. You also need to familiar with the domain name which you always visit and check the link whether is same as expected. Double-check the link is necessary because it is may hard to distinguish between the real and fake domain name such as “facebook.com” and “facebcok.com”.
In this case, if the victim found the link in the phishing email is “https://f1b5ac29.ngrok.io” and he knows the real Facebook domain name is “facebook.com”, he may then close the email and click “report spam”.

4. Presentation
You can find the 2-minutes presentation at the link below:
https://youtu.be/etRV9AczYu8
This video presents one practice of phishing attack. The hacker using Kali Linux in the virtual machine to achieve the phishing attack. The IP address of the hacker is 49.195.48.40. The victim using Windows 7 with the IP address 120.17.136.201, which means the hacker and the victim is sitting in different IP subset. I screen record both for hacker and victim. You can check the full version of the screen recording below:
Screen recording for the hacker:
https://youtu.be/Nx5YHZVDlxQ
Screen recording for the victim:
https://youtu.be/NwnJjX49yjQ
0 notes
Text
Quantum Key Distribution System is used for exchanging pre-shared secret such as a symmetric key. In this way, it indeed has to distribute each key. However, Quantum Key Distribution System is only a small subset of Quantum Communication. If we look at a big picture, security communication can be ensured by Quantum Communication by carrying data onto quantum. It will be safer because it cannot be broken even by the brute-force attack.
It is truly expensive but this is future technology. Maybe everyone can enjoy its outcome when this technology becomes mature enough.
Week7 security everywhere
Quantum Key Distribution System
The breaking progress in the Quantum Cryptography Communication field is a paper published in Nature Photonics named “Experimental quantum repeater without quantum memory”[1]. After deep research in this paper, although I don’t understand the math formula, I know what they are doing and which issue they need to solve. Quantum Communication is always implemented by Quantum Key Distribution System which is a subset of Quantum Cryptography Communication. It is a mechanism can help to exchange keys (such as symmetric keys) to be absolutely secure. Traditional cryptography algorithm is based on mathematical difficulties such as decomposition of quality factors. If this mathematical difficulty can be computed with little cost or improvement in computation capacity will lead to failure of this encryption algorithm. Quantum key distribution system, however, does not need to worry about the mathematical attack because the movement of quantum entanglement is truly random, the length of bits can be arbitrary depending on how long you operate the quantum entanglement and the quantum entanglement have no regular repeat. There are two medium implementing this key distribution system successfully which are optical fiber and satellite. For satellite, it can cover the entire earth easily but hard to achieve and extremely expensive. Just imagine the satellite send only one quantum to the earth and that quantum received accurately by the target receiver on the earth with an acceptable SIR. So far, only China can achieve Quantum key Distribution System by satellite[2]. For fiber, it is cheap but can only maintain a short distance between two repeaters. In this way, a lot of repeaters are essential to communicate between two cities with long distance. The hacker can intercept the optical fiber between the repeaters but cannot get the information from the quantum. The only way to break it is through a physical break, which is to break the repeaters and get the keys from the quantum memory because the keys are temporally received from the previous repeater and going to send towards to the next repeater. This is a critical vulnerability for this kind of secure communication. This paper is going to overcome this issue by setting the quantum repeater without memory, which means that any repeaters can receive the quantum but they have no idea what the message(key) is and only the sender and receiver can read the keys by quantum pair. This technology had been verified by experiments. If this technology can be implemented successfully, the two sides can make sure that the shared key is only known by themselves, no one can break it in between. The physical attack can stop them from exchange keys, but cannot break both the key or encrypted packets using that key except brute-force attack. This technology is quite useful but in a short period of time, it is mainly for military use. I hope citizens could use this kind of technology in the further to make internet communication more secure.
Source:
[1]: https://www.nature.com/articles/s41566-019-0468-5
[2]: https://en.wikipedia.org/wiki/Quantum_Experiments_at_Space_Scale
4 notes
·
View notes
Text
Expect we could experience this new technology one day and can’t imagine what the world will look like. We may lose the job as an insecure engineer. :>
Week7 security everywhere
Quantum Key Distribution System
The breaking progress in the Quantum Cryptography Communication field is a paper published in Nature Photonics named “Experimental quantum repeater without quantum memory”[1]. After deep research in this paper, although I don’t understand the math formula, I know what they are doing and which issue they need to solve. Quantum Communication is always implemented by Quantum Key Distribution System which is a subset of Quantum Cryptography Communication. It is a mechanism can help to exchange keys (such as symmetric keys) to be absolutely secure. Traditional cryptography algorithm is based on mathematical difficulties such as decomposition of quality factors. If this mathematical difficulty can be computed with little cost or improvement in computation capacity will lead to failure of this encryption algorithm. Quantum key distribution system, however, does not need to worry about the mathematical attack because the movement of quantum entanglement is truly random, the length of bits can be arbitrary depending on how long you operate the quantum entanglement and the quantum entanglement have no regular repeat. There are two medium implementing this key distribution system successfully which are optical fiber and satellite. For satellite, it can cover the entire earth easily but hard to achieve and extremely expensive. Just imagine the satellite send only one quantum to the earth and that quantum received accurately by the target receiver on the earth with an acceptable SIR. So far, only China can achieve Quantum key Distribution System by satellite[2]. For fiber, it is cheap but can only maintain a short distance between two repeaters. In this way, a lot of repeaters are essential to communicate between two cities with long distance. The hacker can intercept the optical fiber between the repeaters but cannot get the information from the quantum. The only way to break it is through a physical break, which is to break the repeaters and get the keys from the quantum memory because the keys are temporally received from the previous repeater and going to send towards to the next repeater. This is a critical vulnerability for this kind of secure communication. This paper is going to overcome this issue by setting the quantum repeater without memory, which means that any repeaters can receive the quantum but they have no idea what the message(key) is and only the sender and receiver can read the keys by quantum pair. This technology had been verified by experiments. If this technology can be implemented successfully, the two sides can make sure that the shared key is only known by themselves, no one can break it in between. The physical attack can stop them from exchange keys, but cannot break both the key or encrypted packets using that key except brute-force attack. This technology is quite useful but in a short period of time, it is mainly for military use. I hope citizens could use this kind of technology in the further to make internet communication more secure.
Source:
[1]: https://www.nature.com/articles/s41566-019-0468-5
[2]: https://en.wikipedia.org/wiki/Quantum_Experiments_at_Space_Scale
4 notes
·
View notes
Text
Yes, that’s the point. It is essential to invest more in education and R&D for those countries who are willing to develop their own forces for protecting national security.
Week 6 security everywhere
National security
The biggest news this week is Google Home secretly record the user audio when no wake-up word is used[1]. This news unsurprisingly raised people concern about the security issues, but as what I mentioned before, there is no way to solve the privacy issues thoroughly as a citizen unless you can live without any electronic devices and services from Google or Apple. I had discussed a lot about the topic of privacy, so I am not going to repeat what I was mentioned. Since the activity let us discuss whether Australia should buy devices from the Chinese company and the case study ask for advice to prevent the cyber-attack from attack. Those topics are all related to national security, so I would like to share my point of view. There is a big difference between national safety and security.
As for national safety, it is easy to achieve for Australia. We all know that America is one of the closest allies with Australia and there are even four the United States military bases located in AU[2]. If Australia fully trust America and the shared interest and the common ideology can maintain for a long period of time, the issue of national safety will become much simpler because America is the leader in the world with the top military power and investment. Why we need to develop our own chips, telecom technology and weapon if US promise to protect the AU and can provide the best quality products with reasonable price. The example could be Japan and South Korea, all weapon from the US but really have no ability to say no to the US.
However, if Australia hopes to protect its own national security, then no one could trust, the only way to achieve this is developing its own chip, weapon and telecom equipment. The Iraqi war shows us what the modern war looks like. The chip inside of a printer had a virus and when the war broke out, the US used that virus to misleading and disable the military control system including radar system[3]. One printer, one virus, one disabled Iraqi air defence. This war educated some nations such as China that nuclear weapons are not enough to ensure national security. Some important components , especially for military use, should be self-developed and self-made[4]. That is why China start to develop both the chip design and manufacture. After 20 years, all chips used by satellite, military, supercomputer and most chips of telecom system are self-designed and self-manufactured[5]. The performance of these chips may not as good as the chips from the US, however, it has to do so to prevent the same tragedy in Iraqi case. In this way, in a short period of time, the AU should still depend on equipment from a foreign country such as telecom equipment. I agree that Australia should avoid the equipment from Chinese company because of the huge difference in ideology and lack of trust, but other equipment from Nokia and Cisco should also be carefully checked in security aspect. The legislation is essential to rule all foreign company providing no backdoor equipment and Australia should also establish a dedicated department for risk assessment. However, in the long term, Australia should learn from the bought advanced equipment and allies such as America to imitate and finally develop its own technology and equipment. Australia is a big country and used to have a relatively complete modern industrial system, it should have the ability to develop its own hi-tech weapon and system, the only thing the Australian should do is made up the mind and the long term investment on R&D especially when the world is experiencing the process of De-globalization nowadays. After doing this, Australia will not only make money from equipment and weapon export but also improve the level of national security from installing a backdoor on the export device to monitor the intelligence from other countries. This learns and self-developed procedure may take a long time and huge investment and maybe under press from used allies, but it is the only way to ensure autonomy and national security.
Source:
[1] https://threatpost.com/google-home-recordings-domestic-violence/146424/
[2] https://en.wikipedia.org/wiki/List_of_United_States_military_bases
[3] https://www.theregister.co.uk/2003/03/10/one_printer_one_virus_one/
[4] https://en.wikipedia.org/wiki/Science_and_technology_in_China
[5] https://en.wikipedia.org/wiki/Loongson
3 notes
·
View notes
Text
The short answer is: CBC is more secure.
For a plaintext, it will first be divided into several blocks.
ECB encrypt each block by the same algorithm and parameter. In this way, ECB can process each block in parallel to save time, but the same text input into the different blocks will generate the same cipher. This is the major vulnerability of ECB.
Adopting CBC can avoid this issue where each block will generate the different cipher even when input the same text. This is because the current encryption process is affected by the cipher from the previous block. The drawback of CBC is poor compute speed because the current block cannot start processing until getting the cipher from the previous block.
My suggestion is to use CTR to make sure of both security and effectiveness.
Week8 tutorial review
The tutorial this week firstly answer the in-class questions. This class answer my question about the activity last week named “Modern Encryption Standards”. What my understanding is wrong. I used to believe the second one is some protocol not belonging to ECB, CBC and CTR because the length of cipher increase whenever adding one byte to the plaintext. However, after the tutorial, I found the inter cipher is precomputed by nonce and counter, and cipher can be generated by XOR between the internal cipher and stream input plain text. In this way, the output length of CTR should be the same as the input plaintext. So the cipher 2 is using CTR.
Then, it is easy to distinguish between ECB and CBC. For ECB, if we input a 64 bytes string combined by two same 32bytes string, the first half and the second half of the cipher should be the same because the plaintext is divided into 32bytes blocks and then encrypting each block separately by the same encryption algorithm with the same key, so each the block will output the same cipher. For CBC, each block will output different cipher even input the same plaintext because the output from the next block will be affected by the output in the current block.
2 notes
·
View notes
Text
Yep, I would like to exchange opinions with you and believe we can learn a lot from each other since we both doing things related to social engineering attacks. Maybe next week could be better. You can choose the time you prefer.
Several good ways to prevent the social engineering attack
Some Quick Tips to Remember:
–Think before you click. Attackers use a sense of urgency to make you act first and think later in phishing attacks. When you get a highly urgent, high-pressure message, check it for a moment. Better be safe than sorry!
–Research the sources. Always be careful of any unsolicited messages. Check the domain links to see if they are real, and the person sending you the email if they are actual members of the organization. Usually, a typo/spelling error is a dead giveaway. Utilize a search engine, go to the company’s website, check their phone directory.
–Email spoofing is ubiquitous. Hackers, spammers, and social engineers are out to get your information, and they are taking over control of people’s accounts. Once they gain access, they will prey on your contacts.
–Don’t download files you don’t know. If you (a) don’t know the sender, (b) don’t expect anything from the sender and © don’t know if you should view the file they just send you with “URGENT” on the email headline, it’s safe not to open the message at all. You eliminate your risk to be an insider threat by doing so.
–Offers and prizes are fake. I can’t believe I’m still saying this in the big year of 2018, but if you receive an email from a Nigerian prince promising a large sum of money, chances are it’s a scam.
3 notes
·
View notes
Text
That makes sense. A satellite cannot see anything clearly. If that app can video record secretly and send back for military use, that would be much information!
Thanks
Cases about the serious data security situation among apps
1,Fitness tracking app Strava gives away location of secret US army bases:
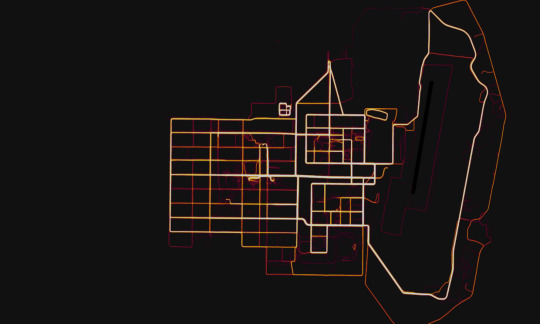
This is the map that a solider drew while he was jogging in the military base of Afghanistan.It completely exposed the outline of this base and even detail of some secret facilities.In the past time ,all of these information may cost intelligence years of time and millions of money to collect.However, they can easily collect these details through mobile phone apps recently.
2,UK air force in the Falkland Islands was exposed by heatmap
RAF Mount Pleasant in the Falkland Islands is lit up brightly on the heatmap, reflecting the exercise regimes of the thousand British personnel there – as are nearby Lake Macphee and Gull Island Pond, apparently popular swimming spots.

3,The threat to global societies(American election)
Do you want candidate A to be elected into office? Find out which populations are most susceptible to political belief A, and then target them with mis- and disinformation that pushes them in the desired direction. Push the information that is good for Candidate A to the first searched hashtags. In many cases, such targeted influence campaigns against specific populations can even make us think the ideas were our own.
This is what already happened with Cambridge Analytica and Russia interference in the 2016 U.S. presidential election, where cognitive flaws such as confirmation bias were exploited to encourage certain voting behavior.
4,How to counteract the social engineering attack among politics
The key to counteracting social engineering is awareness since social engineers are targeting our lack of cognition, our ignorance, and our fundamental biases. This awareness approach is twofold: first, we need to develop strategies and good practices to counter the social engineering itself; and second, we need to develop sustainable policies to mitigate its effects.
In a cybersecurity context, it’s not as easy to mitigate social engineering as it is to mitigate software and hardware threats. On the software side, we can purchase intrusion detection systems, firewalls, antivirus programs, and other solutions to maintain perimeter security. Attackers will certainly break through at one point or another, but strong cybersecurity products and techniques are readily available.
5,Principles of influence
Social engineering relies heavily on the six principles of influence established in Robert Cialdini’s Influence:The Psychology of Persuasion:
Reciprocity – People tend to return a favor, hence the pervasiveness of free samples in marketing.
Commitment and consistency – If people commit to an idea or goal (orally or in writing), they are more likely to honor that commitment because it’s now congruent with their self-image. Even if the original incentive or motivation is removed after they have already committed, people will continue to honor the agreement.
Social proof – People will do things that they see others doing.
Authority – People will tend to obey authority figures, even if they’re asked by those figures to perform objectionable acts.
Liking – People are easily persuaded by others that they like.
Scarcity – Perceived scarcity will generate demand. For example, by saying offers are available for a “limited time only,” retailers encourage sales.
8 notes
·
View notes
Text
Hi, Harrywu,
Thanks for sharing your understanding of CA to us. It answers my confusion about why we need CA, what issues it needs to be addressed and how it works in practice. I had a question about the digital certificate chain. If A trust B but B had issued some bogus certificates to evils because B was hacked. In this scenario, Is there any mechanism to make the A realize that B cannot be trusted anymore?
Understand CA
In order to understand the whole procedure of basic encryption method and some related concepts, I do a lot of research and write down my thoughts.
Why do we need to encrypt?
Because the content of http is transmitted in plaintext, the plaintext data will pass through multiple physical nodes such as intermediate proxy servers, routers, wifi hotspots, and communication service operators. If the information is intercepted during transmission, the transmitted content is completely exposed. Evil in the middle is also possible to tamper the transmitted information without being noticed by both parties. This is a man-in-the-middle attack. Hence, we need to encrypt the information. The simplest and easy to understand is symmetric encryption.
What is symmetric encryption? Use the same key to encrypt and decrypt the message.
Is symmetric encryption feasible?
No, if A wants to communicate B, A should first send a shared key to B. After they both have keys, they can use this pair of shared keys to communicate. However, if Evil in the middle intercept they key, all the following messages will be exposed.
What is asymmetric encryption?
There are two keys in asymmetric encryption. A public key and a private key. Each side of communication has its own private key. If the sender wants to start a connection, he should first send public key to receiver. The receiver receives public key and encrypts his message use public key. The sender receives the encrypted message and decrypts it using private key. Also, public key and decrypt messages encrypted by private key.
Asymmetric key + symmetric key, a seemingly feasible method
We can use two pairs of asymmetric key to encrypt and decrypt message. However asymmetric key is slower than symmetric key. Therefore, in practice, we use asymmetric key to encrypt symmetric key. After one side decrypt the message and get symmetric key, they use symmetric key to do encryption.
Is the above method secure?
No. If A wants to start a conversation and send his public key to B, Evil in the middle can intercept the public key that A send to B. Then Evil send his own public key to B. B thinks that is A’s public key and encrypts a shared key using Evil’s public key then send to A. Evil intercept the encrypted message and decrypt by his private key, then the Evil get the shared key that will be used to communicate in the future. Evil encrypts the shared key shared by B using A’s public key he gained in the previous session. A decrypts the message by his own private key and get the shared key. At this point, both B and A will not realize there is someone in the middle eavesdropping their conversation.
To solve the above problem, what can we do?
digital certificate and CA
Before using HTTPS, the digital certificate website needs to apply for a digital certificate to the “CA”. The digital certificate contains information such as the certificate holder and the public key of the certificate holder. The server transmits the certificate to the browser and the browser get the public key from the certificate. The certificate is like an ID card, which can prove that “the public key corresponds to the website.” However, there is another obvious problem here. How to prevent tampering during the transmission of the certificate itself? How to prove the authenticity of the certificate itself? The ID card has some anti-counterfeiting technology, how to protect digital certificates? To solve this problem, we are basically close to victory.
How to prevent digital certificates from being tampered?
Digital signature
The digital signature is also named signed message digest.
Sender: Digital certificate->Hash(Digital certificate)->CA’s private key(Hash)
Receiver:CA’s private key(Hash) || Digital certificate->
->CA’s public key(private key(Hash))->Hash value(1)
-> Hash(Digital certificate)(2)
if (1) == (2) yes -> not tampered
no -> tampered
Is it possible for the middleman to tamper with the digital certificate?
Assume that the man in the middle has falsified the original text of the certificate. Since he does not have the private key of the CA organization, the encrypted signature cannot be obtained at this time, and the signature cannot be falsified accordingly. After receiving the certificate, the browser will find that two hash values are inconsistent, indicating that the certificate has tampered and the certificate is not trusted, thereby terminating the transmission of information to the server to prevent the information from being leaked to the evil. We have known it is impossible to tamper certificate, what about evil changing the entire certificate to his certificate?
The answer is no. The certificate has (server’s)sender’s identifying information and public key. Even if Evil has CA’s certificate, the browser(receiver) will check if the domain received is what he requested.
Why do we need to hash the certificate when making a digital signature?
It seems that the hash is kind of redundant in the above process, and removing the hash process can also ensure that the certificate has not been tampered. The most obvious is the performance problem. We have already said that asymmetric encryption is inefficient, and certificate information is generally long and time-consuming. The hash is obtained with fixed-length information (for example, a fixed 128-bit value can be obtained by hashing with the md5 algorithm), so that encryption and decryption will be much faster. Of course, there are security reasons, but this knowledge is relatively deeper.
How to prove that the public key of the CA institution is believable?
The operating system and the browser itself pre-install some root certificates that they trust. If there is a root certificate for the CA, you can get the corresponding trusted public key. In fact, the authentication between certificates can be more than one layer. A can trust B, B trusts C, and so on. We call it a chain of trust or a digital certificate chain. That is a series of digital certificates, starting from the root certificate. Through layer-by-layer trust, the last holder of the certificate can get trust.
2 notes
·
View notes
Text
Hi, Thanks for your detailed explanation about HMAC and Digital Signature, It really helps me understand how these algorithm work. In my point of view, only adopting HMAC in our daily internet communication is not enough because the message is not encrypted and the hacker can intercept the packet in the middle and read the message directly without any other efforts. This is the situation that no one expects to happen. Do you have examples or other combination of methods to ensure integrity, authentication and confidentiality?
Week4 Self-directed study[active]
A good definition to MAC
https://searchsecurity.techtarget.com/definition/message-authentication-code-MAC
HMAC:
Also called keyed-hash message authentication code: a message authentication code that uses a cryptographic key in conjunction with a hash function.
Confidentiality is not always needed, and hashing is faster than encryption in software.
Provide integrity and authentication.
https://baike.baidu.com/item/hmac
Digital signature:
m->H(m)->(Kb-(H(m)),m)===>Kb+(Kb-(H(m)))->H(m)=?H(m)
Bob Alice
Why MAC can provide Integrity?
If a man in the middle intercepts the message and replace with a new message, two hashes will not be equal, so the message must be tampered.
Why digital signature can provide Non-reputation?
If Kb+(Kb-(H(m))) = H(m), only Bob can sign m, so whoever signed m must be Bob.
Rainbow table:
a good explain: https://www.youtube.com/watch?v=Vryo30qK9Qk
2 notes
·
View notes
Text
The case of tracking app exposing the location of a secret US military base is impressive. However, that information such as road and position can be easily collected by satellite using Google Map and other apps. I can even count how many planes are there in the airforce base. The only intelligence the satellite cannot collect is the planes inside of the building. Just wonder why they prefer using a tracking app to collect information, not using satellite?
Cases about the serious data security situation among apps
1,Fitness tracking app Strava gives away location of secret US army bases:

This is the map that a solider drew while he was jogging in the military base of Afghanistan.It completely exposed the outline of this base and even detail of some secret facilities.In the past time ,all of these information may cost intelligence years of time and millions of money to collect.However, they can easily collect these details through mobile phone apps recently.
2,UK air force in the Falkland Islands was exposed by heatmap
RAF Mount Pleasant in the Falkland Islands is lit up brightly on the heatmap, reflecting the exercise regimes of the thousand British personnel there – as are nearby Lake Macphee and Gull Island Pond, apparently popular swimming spots.

3,The threat to global societies(American election)
Do you want candidate A to be elected into office? Find out which populations are most susceptible to political belief A, and then target them with mis- and disinformation that pushes them in the desired direction. Push the information that is good for Candidate A to the first searched hashtags. In many cases, such targeted influence campaigns against specific populations can even make us think the ideas were our own.
This is what already happened with Cambridge Analytica and Russia interference in the 2016 U.S. presidential election, where cognitive flaws such as confirmation bias were exploited to encourage certain voting behavior.
4,How to counteract the social engineering attack among politics
The key to counteracting social engineering is awareness since social engineers are targeting our lack of cognition, our ignorance, and our fundamental biases. This awareness approach is twofold: first, we need to develop strategies and good practices to counter the social engineering itself; and second, we need to develop sustainable policies to mitigate its effects.
In a cybersecurity context, it’s not as easy to mitigate social engineering as it is to mitigate software and hardware threats. On the software side, we can purchase intrusion detection systems, firewalls, antivirus programs, and other solutions to maintain perimeter security. Attackers will certainly break through at one point or another, but strong cybersecurity products and techniques are readily available.
5,Principles of influence
Social engineering relies heavily on the six principles of influence established in Robert Cialdini’s Influence:The Psychology of Persuasion:
Reciprocity – People tend to return a favor, hence the pervasiveness of free samples in marketing.
Commitment and consistency – If people commit to an idea or goal (orally or in writing), they are more likely to honor that commitment because it’s now congruent with their self-image. Even if the original incentive or motivation is removed after they have already committed, people will continue to honor the agreement.
Social proof – People will do things that they see others doing.
Authority – People will tend to obey authority figures, even if they’re asked by those figures to perform objectionable acts.
Liking – People are easily persuaded by others that they like.
Scarcity – Perceived scarcity will generate demand. For example, by saying offers are available for a “limited time only,” retailers encourage sales.
8 notes
·
View notes
Text
Hi. Thanks for your Impressive suggestions and these can really help to prevent social engineering attacks, especially from the email phishing attack. I would like to supplement some suggestions for your reference:
1. Install anti-virus software and firewall. I had installed ESET INTERNET SECURITY on my laptop. When I try to attack my laptop by ARP spoofing, the firewall just pops up a warning to notice me someone in the subnet are preferring ARP attacks. It can be helpful especially for those non-security people.
2. Protecting personal privacy and device identities. Most of the social engineering attacks require victim’s information such as name, email address and IP address. In this way, protecting you could eliminate the chance for hackers to found you on the public internet.
Several good ways to prevent the social engineering attack
Some Quick Tips to Remember:
–Think before you click. Attackers use a sense of urgency to make you act first and think later in phishing attacks. When you get a highly urgent, high-pressure message, check it for a moment. Better be safe than sorry!
–Research the sources. Always be careful of any unsolicited messages. Check the domain links to see if they are real, and the person sending you the email if they are actual members of the organization. Usually, a typo/spelling error is a dead giveaway. Utilize a search engine, go to the company’s website, check their phone directory.
–Email spoofing is ubiquitous. Hackers, spammers, and social engineers are out to get your information, and they are taking over control of people’s accounts. Once they gain access, they will prey on your contacts.
–Don’t download files you don’t know. If you (a) don’t know the sender, (b) don’t expect anything from the sender and © don’t know if you should view the file they just send you with “URGENT” on the email headline, it’s safe not to open the message at all. You eliminate your risk to be an insider threat by doing so.
–Offers and prizes are fake. I can’t believe I’m still saying this in the big year of 2018, but if you receive an email from a Nigerian prince promising a large sum of money, chances are it’s a scam.
3 notes
·
View notes
Text
Week8 tutorial review
The tutorial this week firstly answer the in-class questions. This class answer my question about the activity last week named “Modern Encryption Standards”. What my understanding is wrong. I used to believe the second one is some protocol not belonging to ECB, CBC and CTR because the length of cipher increase whenever adding one byte to the plaintext. However, after the tutorial, I found the inter cipher is precomputed by nonce and counter, and cipher can be generated by XOR between the internal cipher and stream input plain text. In this way, the output length of CTR should be the same as the input plaintext. So the cipher 2 is using CTR.
Then, it is easy to distinguish between ECB and CBC. For ECB, if we input a 64 bytes string combined by two same 32bytes string, the first half and the second half of the cipher should be the same because the plaintext is divided into 32bytes blocks and then encrypting each block separately by the same encryption algorithm with the same key, so each the block will output the same cipher. For CBC, each block will output different cipher even input the same plaintext because the output from the next block will be affected by the output in the current block.
2 notes
·
View notes
Text
Knowledge from presentation - Blockchain
There were four colleagues finished their presentation this week. All of them are really interesting and I learned a lot from their presentation.
Blockchain
Blockchain mainly used by cryptocurrency. The cryptocurrency adopts blockchain architecture to ensure safety in the transaction. According to my understanding, the blockchain consists of a certain amount of blocks linked by dependency. A block consists of three parts: the hash value of the current block, the hash value of the previous block and the data recording past transactions. It has a certain degree of tamper résistance because changing one block means changing all previous blocks in the same stream otherwise any tamper action will be detected due to the inappropriate hash value. Also, only those who have a huge amount of coins can be mainstream so that they will not likely do something bad to their blocks based on their own interest. One-week point maybe the mainstream has too much power to do something evil such as add new coins in the stream, which is called the 51% attack.
0 notes
Text
Knowledge from presentation – Card clone
There were four colleagues finished their presentation this week. All of them are really interesting and I learned a lot from their presentation.
Card clone
The most impressive presentation in this tutorial is copying an E-card. Card clone can be done by copying the entire information from an existing E-card by a reader and then write the same data to a new card. There are two kinds of card, one is encrypted card and another is the unencrypted card. The unencrypted card is easy to clone, just copy all of the data from A to B. For the encrypted card, the degree of difficulty to clone a card is depended by the encryption algorithm. Most of the procedure should be reading all data from a card, crack the cipher and get the data, write the data to an unencrypted card. It is essential to buy a blank card which can access the sector 0.
0 notes
Text
Knowledge from presentation – evil twin attack
There were four colleagues finished their presentation this week. All of them are really interesting and I learned a lot from their presentation.
Evil twin attack
Evil twin attack is to set up fake access the point with the same SSID to trick victims into login to the fake access point. However, for some already connected to the real access point users, the hacker has to send login denying code to the original access point to kick the users offline. After the user connects to the fake access point, a login webpage popped up for authentication. If the victim enters the real information to the fake login webpage, the hacker can then collect the user’s username and password. The presentation set up an access point during the tutorial is really impressive.
0 notes
Text
Knowledge from presentation – keyboard recorder
There were four colleagues finished their presentation this week. All of them are really interesting and I learned a lot from their presentation.
keyboard recorder
There are two methods can record the keyboard. One way is install the recorder inside of the device. That recorder gather the sound wave records and processing those signals and finally get the sequence of knocking keys. The other way is installing a microchip inside of the device or even inside of the keyboard. The chip is super small and it can intercept and record the commands between the two sides. After analyze the record, it can get the sequence of knocking keys.
0 notes
Text
Preparation for presentation
My project is about Email Phishing. Actually I had prepared a presentation before the tutorial this week. According to the announcement from the openlearning, both the video and the presentation should be at most 2 minutes. It is a big problem for me because the full version of the recording is 15 minutes long. In this way, I have to use the video editor called Adobe Premiere to cut some most important cuts to present. It takes me three days to actually finish the editing because I haven’t used this software before. After cutting the 2 minutes long video, I made a powerpoint to play and interpret each necessary steps for Email Phishing. However, the presentation length is not that strict and most colleagues present their outcomes by on-site presentation in the tutorial. I would like to follow their ways of presentation because it can make the audience more participate in the presentation. It may need some time for preparing because I need to familiar all commands and procedures to reduce the presentation time. Hopefully, the length could limit from 15 minutes to 5 minutes. I would like to have a try. Good luck to me.
0 notes