Text
Search your AWS Inventory
Quickly search through the AWS resources in a single AWS account or multiple AWS accounts using Ylastic. View the configuration for any of the retrieved resources easily with a single click. Fine tune your search by selecting tags and/or resource ids. Combine multiple criteria to quickly filter and view your AWS resources. You can select single or multiple items for each category.

Detailed resource configuration is easily accessible for all retrieved items.

Filter your search criteria by selecting one or more services.

Filter your search criteria by selecting one or more regions.

Filter your search criteria by selecting one or more resource types.
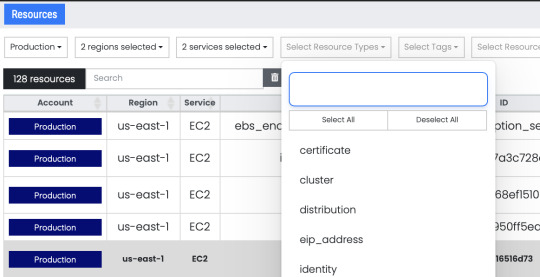
Filter your search criteria by selecting one or more resource Ids.

Filter your search criteria by selecting one or more tags.

0 notes
Text
Export EKS Kubernetes Clusters
New scheduled task in Ylastic for exporting EKS Kubernetes Clusters to a S3 bucket of your choice. Global export can be run at an AWS Organizational unit level to dynamically select clusters in all AWS accounts within that unit. Exports are compressed and encrypted using SSE-KMS in selected S3 bucket. You can configure the number of exports to retain and the task will automatically prune the old exports.

Exports are bundled into a tarball for compressed storage prior to encryption. Each export is arranged by namespace and resource types within each namespace to make it easy to utilize the exported files.

The scheduled task can be configured to check for specific cluster tags or you can utilize a wildcard (*) to select all clusters in a region. Specify the S3 bucket to use for saving exports. You can select any account from your AWS organizational unit.

Detailed history of every task run is stored and available. There is no need to specify an account to check for the clusters to export. AWS accounts within your organizational unit are automatically picked up on every run.

Select any individual task run event and view the matched clusters, as well as exports added and deleted.

0 notes
Text
Ylastic Updates
Several recent product updates incorporated into a single post. Easy access to tags for your AWS resources. Quickly view associated tags for instances, volumes, snapshots, vpcs, subnets, routes tables, security groups, and other resources.

Utilization metrics updates for EKS clusters, nodes, and pods. If you have the Kubernetes metrics-server running in your clusters, then utilization is retrieved and automatically displayed next to the resource.

Updates to EKS and Kubernetes management for multi-account/cross region resource access.

Change retention for individual backups. If you wish to keep some of the backups created by a scheduled backup task, just add the tag 'ylastic_retain_backup' to a snapshot(for volume backups) or an AMI (for instance backups). You can do this for any of the tasks used for backing up volumes and instances, as well as tasks for replicating volumes and instances to other accounts and regions.

0 notes
Text
Launch Templates
Cross-region, cross-account launch templates. View and access all your launch templates in one place.

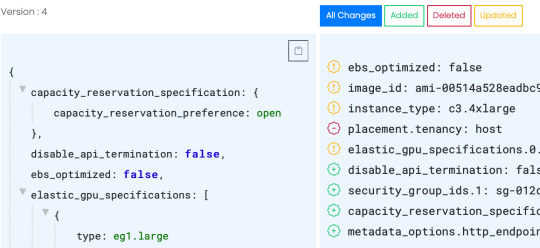
View each template version as JSON, a details view separated by sections, and more.

Compare launch template versions. Select any two versions and view all changes or just the adds, deletes, or updates.
0 notes
Text
EKS and Kubernetes Management
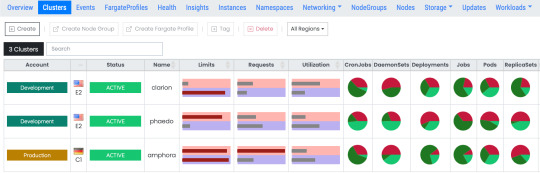
Kubernetes is an open source container orchestration platform to deploy, manage, and scale containerized applications. Elastic Kubernetes Service (EKS) is a managed service from AWS which makes it easy to run Kubernetes in the AWS cloud. You can choose to manage Kubernetes infrastructure yourself with EC2 or get an automatically provisioned, managed Kubernetes control plane with Amazon EKS. Worker nodes can be provisioned on EC2 instances or a serverless data plane with Fargate. Ylastic already supports ECS container management. We are extending it with full support for managing your EKS Kubernetes resources running in AWS with Ylastic - across regions and across AWS accounts. All your Kubernetes clusters along with an overview of their workloads (deployments, controllers, daemon sets, jobs and more), CPU/memory limits, requests and utilization are available in one view.
Nodes represent worker machines in a cluster to run your application containers. Each node contains the services that are needed to run pods. When you deploy an application in a cluster, the Kubernetes control plane seamlessly handles the distribution of work on to the individual nodes.

A pod is a group of one or more containers deployed on a worker node of a cluster. It is also the unit of replication in Kubernetes. Clusters can have multiple pods and each pod is assigned an unique IP address for connectivity.
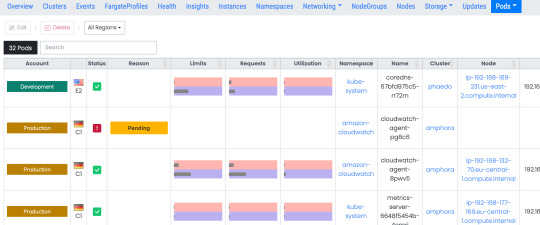
Services are Kubernetes objects used to expose the access to application containers running on different pods within your cluster or outside your network.

Deployment defines the set of instructions for creating pods and other required objects in your application. You can manage the specific number of pod replicas by specifying it in the deployment. Even if you delete any pod manually, the configured deployment which is also monitoring it, will immediately create a new pod as defined. Using a deployment, you can declare the desired state of the system, and Kubernetes will automatically manage the resources to ensure your desired state.

Kubernetes can be configured to provide persistent storage access to your application containers using storage classes and volumes. These volumes can be Amazon Elastic Block Store (EBS), Elastic File System (EFS), and several other types, and can be attached to your worker nodes to provide persistent storage.

Kubernetes supports multiple virtual clusters backed by the same physical cluster. These virtual clusters are called namespace and they are all logically isolated from each other.

EKS managed node groups contain the EC2 instances that are used for running your Kubernetes workloads. They are managed for you by AWS, but are only needed if you want to use EC2 and are not needed if you go the serveless route and use EKS Fargate clusters.

Managed node groups make it easy to add worker nodes (EC2 instances) that provide compute capacity for your clusters.

Access and view Kubernetes events being generated by all your clusters and the resources contained within them in one place.

Access and view updates to your managed node groups and clusters generated by AWS EKS in one place.

Every object within Kubernetes is defined as an API object and accessible by ReST using the API server. You can edit any object as JSON and save changes to apply the updates to the object. Edit your Kubernetes objects easily in Ylastic with a dual window editor so you can see the changes being made to the resource. Save to apply changes.

EKS container insights collects, aggregates, and summarizes metrics from your containerized applications on AWS. View your application metrics across regions and accounts in one page. Want to see the insights for a cluster in a different account/region within your organizational unit? Just select the account and region in the drop down to view the metrics. No switching pages, reloading consoles, changing roles.

Global CloudOps for your AWS organization. Simplify and streamline your container management workflow with easy access to all your ECS and EKS resources.
0 notes
Text
VPC Updates
VPC resource page updates in Ylastic. VPC endpoints enable you to use a private connection between your VPC and any supported AWS services or any VPC endpoint services that uses PrivateLink. Traffic between your VPC and AWS service that you are connecting to via an endpoint, does not leave the Amazon network. The new VPC endpoints page for gateway and interface endpoints is cross-region and cross-account. If you are using AWS Organizations, the view is by an AWS Organizational Unit and encompasses all accounts in that OU.

VPC peering connections enable you to route traffic between two VPCs privately. The resources in either VPC are able to communicate with one other as if they are within the same network. The new VPC peering page in Ylastic gives you access to your VPC Peering connections, cross-region and cross-account.

Diagrams for VPC peering connections with both requester and accepter VPC and all their components. You can diagram peering within an AWS account or peering connections with another AWS account in the organization. No digging through lots of resource pages, no switching regions. Click a button and generate a diagram of the peering.

0 notes
Text
EC2 resource page updates
EC2 resource page updates in Ylastic. Health check information for load balancer target groups readily available without accessing a separate tab. Sparklines now displayed for Requests, Healthy hosts and Unhealthy hosts.

Load balancers page displays sparklines for Requests, Healthy hosts and Unhealthy hosts. The displayed sparklines differ based on the load balancer type, as there are some differences in the metrics available for each type.

All resources that can be targeted by Cloudwatch alarms now display the active resource alarms in a sub-tab, making it easier to manage alarms for the resource.

0 notes
Text
CIS Benchmark Security Reports for AWS Organizations
The Centre for Internet Security (CIS) benchmarks are industry-accepted best practices for securely configuring traditional IT components. CIS has released several benchmarks or a set of security configuration best practices for AWS environments. The CIS AWS Foundations Benchmark for AWS provides a guidance for configuring the security options for the following basic set of foundational AWS services.
AWS Config
AWS CloudTrail
AWS CloudWatch
AWS Identity and Access Management (IAM)
AWS Simple Notification Service (SNS)
AWS Simple Storage Service (S3)
AWS VPC
This security benchmark is integrated into Ylastic, to make it really easy to audit your AWS infrastructure. You can create on-demand reports checking compliance with the benchmark or even schedule reports to run on a timeline of your choice to periodically check compliance. No separate tools/apps needed. Run reports against a single AWS account or ALL the accounts in an AWS organization. We updated the integration to make it easier to access the report information.

Select any report to view the details for the report. Results are separated by AWS account and if you are using AWS Organizations, the report will display information on all the accounts that were tested as a part of that run.

Each report checks for compliance in four different categories. The Identity and Access Management category contains 24 checks focused on security for IAM, such as the use of root account, multi-factor authentication (MFA), inactive accounts, and password policy.

The logging category contains 8 checks focused on logging AWS API calls and security options for the logging.

The monitoring category contains 15 checks focused on prevention and detection of unauthorized use of the AWS account.

The networking category contains 5 checks for checking the configuration of the security related aspects of VPC.

Create an on-demand report at any time or if you prefer, you can setup the reports to run on a schedule to evaluate your infrastructure.

Integrated and simple CIS benchmark security auditing for your AWS infrastructure.
0 notes
Text
Container Management - AWS ECS and ECR
Cross account and cross region management for your clusters, services, tasks, images, task sets, task definitions, scheduled tasks, container instances, vulnerability scans, container insights, repositories and events - now in Ylastic. Container resources aggregated within your organizational units to make it easier to understand your environment as well as access all the pertinent information in one place. There are a lot of different components in ECS. This blog post will walk you through each component and how you can manage those resources in Ylastic. ECS services allow you to always have a specified number of tasks running in a cluster. All your services are displayed in one place aggregated across regions and accounts in an OU. Select a service to view further details and associated configuration. The latest CPU and memory utilization metrics for each service are displayed in a sparkline graph next to the service name. You can view service CloudWatch metrics by clicking the sparkline to display the related charts. Click a button to generate a diagram for the service the service tasks as well as associated AWS components such as the VPC network, logs, IAM roles and more and their relationships and connections.

Clusters are the logical grouping unit in ECS. They can contain services or simple tasks, each of which may contain a mix of tasks that can use either the Fargate or EC2 launch types. The capacity can be provisioned for a cluster either through Autoscaling groups or a Fargate capacity provider. All information for a cluster is available in one place by selecting the cluster. The latest CPU and memory utilization metrics for each cluster are displayed in a sparkline graph next to the cluster name. You can view cluster CloudWatch metrics by clicking the sparkline to display the related charts. Click a button to generate a diagram for the cluster.

Tasks are the fundamental units of work in ECS. Task runs are based off a template called the task definition. The concept is quite similar to the way you run Autoscaling instances using a launch configuration as a template. You can run as many tasks as you want from a single task definition. Tasks can be one-off where they do a certain thing and then cease to exist. You can also run tasks as a part of a service which allows them to continuously run in a cluster. View all the task information in one place as well as easily generate a diagram for the task that shows all associated AWS components such as the VPC network, logs, IAM roles and more and their relationships as well as connections.

ECS tasks can also be run on a regular, scheduled basis. This allows you to launch container services that you need to run only at certain times. The scheduled tasks page gives you access to all the schedules and their respective configurations in your environment. Select any schedule to view all the tasks that running as a part of that schedule.
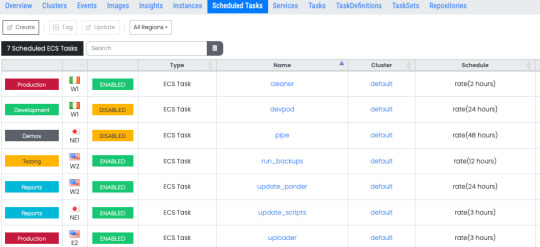
Task Definitions provide a definition of your tasks - a template to describe the structure of your container as well as how the container should be provisioned. It specifies the docker images to use, the CPU and memory allocation for your container, any needed environment variables, exposed ports, network types and more. View detailed information on your task definitions and details of all the clusters and tasks running that are currently using each task definition.

The actual docker image that will be used to start your containers is specified in the task definition. Images can be stored in a repository on AWS ECR and they are pulled as needed when containers are instantiated. View all the images being used by all the containers that are running your task and services in one place. You can manually scan an image or have ECR automatically scan the image for known vulnerabilities in software packages when you push the image to the repository. After a while it can get really confusing to know which images are being used all over your infrastructure and if they are affected by any vulnerabilities that need to be addressed ASAP. No need to hunt through a lot of pages trying to find out your current security status. One place to find all the information you need to address the security concerns from running outdated packages.

View a detailed vulnerability scan listing for any image from one place. Links to the specific CVE listed in the security advisory are also available.

The images you use for your containers can be stored in ECR and pulled from that repository when your containers are instantiated to run tasks. View all your repositories and their configuration information aggregated in one place. Select a repository to see each image in that repository, its details as well as vulnerability scan information for that image.
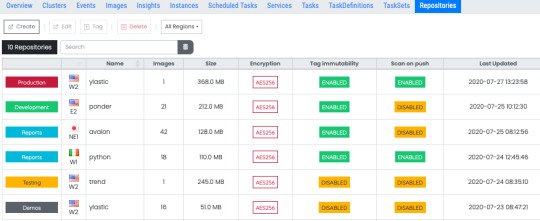
You need compute capacity to actually host your docker containers and run them either as tasks or long running services. AWS gives you two different ways to accomplish this - the traditional EC2 instances or the server less compute with Fargate launch types. If you are using the EC2 launch type for your application, you can view and interact with all the container instances in your environment in one place and quickly view all associated information.

If you wish to use EC2 instances, then you need to run instances with the ECS agent installed. AWS provides ECS optimized AMIs in several different variants, that are highly recommended to use as the base for your ECS container instances. Access and launch instances from these optimized Amis easily without hunting through SSM parameters and AMI pages. The latest and greatest updated AMIs from the ECS team are available in one place.

As you update your applications to new versions, you need a way to deploy those new versions into your containers on ECS. You can perform a rolling update using the ECS service scheduler (the default option available to you on ECS). You can also perform the deployment using other controllers such as either AWS Code Deploy or something completely external outside AWS and in your own environment such as Jenkins. In order to use these two options, ECS leverages the concept of task sets, which are essentially definitions of how to perform your deployments. The task sets page in Ylastic gives you access to all your task sets information and their configuration.

The container launches, tasks and services starting and stopping, ECS agent connects/disconnects, and other state changes in your cloud environment can quickly overwhelm you with an information overload. The events page in Ylastic aggregates ECS events in one place from all your running clusters, service, and tasks. One place to get a quick overview on the state of your Amazon ECS resources.

Select any ECS resource on any of the above pages, and view all associated information in one place. This includes CloudTrail events, configuration details, services, tasks, audit events, and more.

CloudWatch Container Insights collects, aggregates, and summarizes metrics and logs from your containerized applications and microservices. The metrics that are collected include utilization for container resources such as CPU, memory, disk, and network. Easily view and go through charts for all these metrics.

There are a lot of moving parts and components involved in running a containerized application in the cloud. Ylastic gives you the ability to get a quick overview of your ECS environment - generated from your infrastructure with a click. Diagrams of your ECS resources - clusters, services and tasks are available, which display the associated ECS resources and any other AWS components in use. Relationships between the resources are retrieved and displayed along with the containing VPC network.

Easy to use, intuitive container management. Global CloudOps for your AWS cloud environment - Govern, manage, schedule and diagram your resources.
0 notes
Text
IAM diagrams
AWS Identity and Access Management (IAM) is one of the core services in your cloud environment and is the focal point for your security configuration within AWS. Every service in AWS utilizes IAM for securing resource access. Understanding the way each of the IAM components fit together and how they combine to provide security to your cloud resources is essential for all users and businesses in the AWS cloud. The latest addition to Ylastic gives you the ability to generate diagrams of your IAM setup - users, groups, roles and policies from your existing environment. A user diagram will display the groups that include the user, as well as many other relationships - inline and attached policies, active and inactive access keys, SSH public keys used for CodeCommit access, and MFA devices associated with the user.

A diagram for an IAM role connects all the associated components and displays their relationship to each other. A common pattern in AWS is IAM role chaining where you use one role to assume another role. Ylastic will automatically traverse down the chain and display any roles that can be used for role chaining, as well as the specific policies and permissions granted to those additional roles, giving you a comprehensive overview of the role and the way it is connected within your environment.

IAM groups are used for aggregating users, to provide a simpler way to assign permission policies to multiple users, instead of having to individually assign permissions to each user. Group diagrams will display all users in the group as well as the group policy attachments and their permissions.

Policies attached to the various IAM entities - users, groups and roles, are used to control access within AWS. Each policy defines a set pf permissions for a set of resources and specifies whether a request for those resources is allowed or denied. A policy diagram in Ylastic will not only show you the permissions associated with the policy, it will also display all the entities in your account that have that policy attached.

The policy permissions display expands any wildcard permissions within the policies. This makes it really easy to quickly see how many read/write or identity(role assumption) permissions are being granted. Global CloudOps for your AWS cloud environment - Govern, manage, schedule and diagram your resources.
0 notes
Text
AWS network diagrams
VPC is the heart of your AWS cloud environment and understanding and visualizing its various components and their relationships is crucial to running an efficient and secure cloud operation. You can now easily generate VPC network diagrams from your existing AWS infrastructure in Ylastic. View a complete diagram of any VPC - private and public subnets, associated route tables that control traffic flow, and all of the other components comprising the network and their connections to one another.
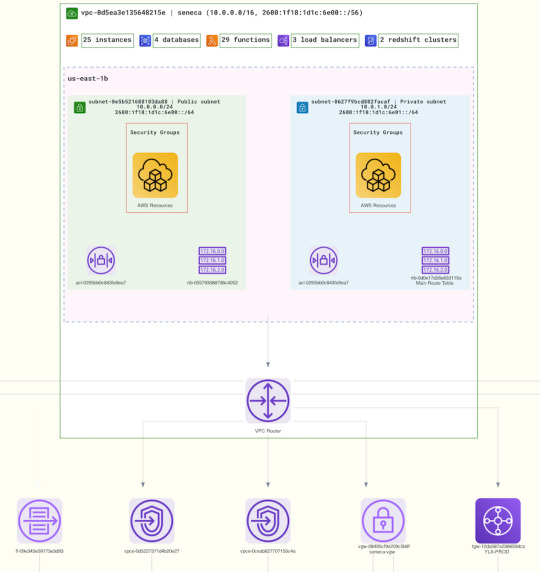
The generated diagrams cover all the different components within a VPC network:
Subnets (public and private)
Route Tables
Network Access Control Lists
Internet, VPN and Customer Gateways
NAT Gateways
Transit and egress only gateways
Elastic Network Interfaces
VPN connections to corporate data centers
VPC peering connections
VPC endpoints
VPC flow logs
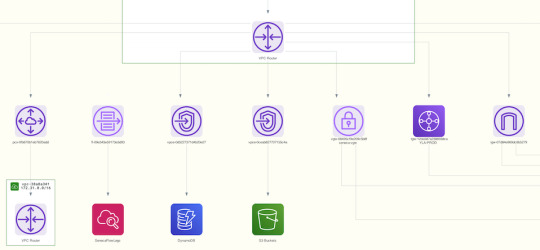
Outbound routes from your VPC, such as connections to your corporate networks and data centers via Customer gateways and VPN are also displayed. Traffic routes outbound to the internet (both IPv4 and IPv6) are clearly delineated as well.
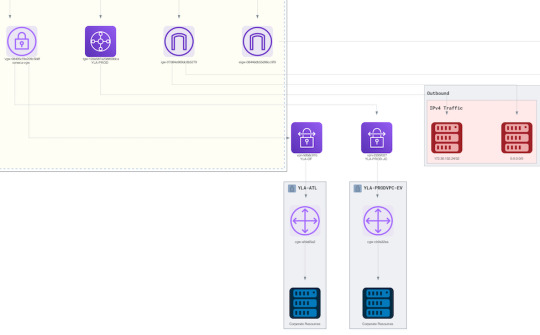
Further drill down into your network architecture and the main sub-component of a VPC - a subnet. Select any subnet and view the components hosted in the subnet and their relationships. A subnet diagram is rendered as a subset of the containing VPC, and it displays only the routes to the entries defined in its associated route table. This makes it very easy to get an isolated view of your subnet design.

Focus all the way from a VPC down to the individual subnets and visualize the way different networking resources are connected and how they work together in the VPC environment.

Easy to use, global CloudOps for AWS environments.
0 notes
Text
Tracking service updates
New in Ylastic - easily track service updates from AWS as well as Ylastic. The dashboard view displays the 5 most recent updates.
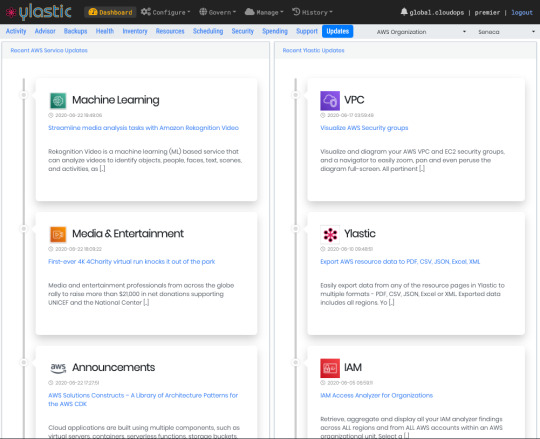
Drill down and filter/search through updates for either service easily on dedicated pages. The updates from various AWS information sources are all aggregated in one page.

Easily search/filter through updates to Ylastic in one place. Click the links to navigate to specific Ylastic console pages with the updates or blog posts with more information on each feature enhancement.

Easy access to all the information you need in one place. Global CloudOps for your AWS environment.
0 notes
Text
Visualize AWS Security groups
Getting a handle on security groups that control access to your VPC/EC2-Classic can be a daunting task. Inbound rules, outbound rules, CIDR blocks, all these different security groups, and so on. It would be really nice to be able to visualize how they all tie together. Updates to Ylastic for visualizing your AWS VPC and EC2 security groups, and a navigator to easily zoom, pan and even peruse the diagram full-screen.

All pertinent information displayed for the security group. Both inbound and outbound rules are separated and displayed by protocol - IPv4 and IPv6. Rules information is aggregated to make it easy to view groups with a large number of rules.

0 notes
Text
Export AWS resource data to PDF, CSV, JSON, Excel, XML
Easily export data from any of the resource pages in Ylastic to multiple formats - PDF, CSV, JSON, Excel or XML.

Exported data includes all regions. You can export at either an AWS account level, or even at an AWS Organizational Unit level (to include ALL AWS accounts contained in that unit).

0 notes
Text
IAM Access Analyzer for Organizations
AWS IAM Access Analyzer helps identify unintended access to your account resources and data, which can be a security risk. IAM can identify resources shared with external principals through analysis of all the resource-based policies in your account, and then generate findings to include information about the access granted to the external principal. You can review findings to determine whether the access is intended and safe, or the access is unintended and a security risk. Access Analyzer generates its findings separately in each region. In an AWS Organization with mutliple AWS accounts that uses multiple regions, this information is not very easy to access in a single place. Ylastic can retrieve, aggregate and display all your analyzer findings across ALL regions and from ALL AWS accounts within an AWS organizational unit.

Select any finding to view details of all the actions granted to the external principal. You can archive a finding if the access level is appropriate or rescan the resource if you have made changes to access granted to it. You can also review details of the resource in question easily, as well as re-activate any finding that you have archived in case you want to revisit that finding.

All actions flagged by IAM that have been granted to the principal are hyperlinked in Ylastic. Click to view complete detail of the granted permission so you can quickly review and take action.

All the information you need to manage your cloud resources, available to you quickly, easily and in one place. Global cloudops for your AWS environment.
0 notes
Text
Scheduled RDS exports to S3
You can now easily schedule the export of RDS DB snapshot data to an Amazon S3 bucket from Ylastic. The exported data from RDS is stored in Apache Parquet format that is compressed and consistent, as well as encrypted using a KMS key provided by you for S3 server-side encryption.
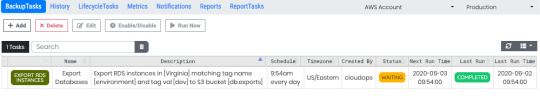
Easily export multiple instances by specifying a tag based filter when you create a scheduled task.

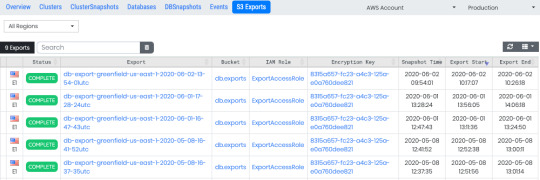
View and access all your S3 exported backups easily and aggregated across all regions in one page.
0 notes
Text
Schedule instance backups to include cross-account resources in an AWS Organization
AWS Organizations is an essential feature that enables grouping of multiple AWS accounts into organizational units(OU), with the ability to apply policy, security and compliance requirements across the whole organization or individual OU. Ylastic fully integrates AWS Organizations with the ability to manage and govern your AWS resources at the OU level. All functions in Ylastic can be done at the level of an OU, spanning all the AWS accounts that comprise the unit. New in Ylastic is the ability to make backups of your cross account instances in an OU. So with a single task in Ylastic, you can backup all instances matching a tag, across multiple regions, across all accounts in an OU. The backups can be to a destination account within your OU, and can also be made to multiple regions. An example to illustrate the power of OU backups. We have three instances running in three different regions - Virginia, Ohio and Frankfurt. Each instance is running in a different AWS account - Production, Analytics, and Design. The three accounts are all part of an OU named Zeno. Instances are tagged with a key ‘env’ and a value of ‘spark’. We are going to back up all three instances to a Backups account in this OU.

Add a task specifying the tag, select source regions, and destination regions. Also select the account for backing up these instances. You can control how many backups you want to retain at any time. Set a time to run. Save the task and you are all done.

Here is the task we just created - Backup all instances in regions Frankfurt, Ohio, and Virginia that have a tag matching env=spark in all AWS accounts in OU zeno, to region Virginia in AWS account Backups.

The task runs at the time scheduled, and creates the backups in the account specified. You can see a history of the task execution, along with time taken and other information. No switching accounts, no switching regions. One place to check the backups created and all other information related to the backup.

Click the details icon to view resources that were created, and deleted for the specific task execution.

You can see the backups for each instance, by just selecting the instance. All backups (cross-account/cross-region) are displayed in one place making it super simple to restore an instance from a backup.

Cross region, cross account AWS cloud management - global cloudOps for your AWS Organization.
0 notes