Text
Week 8 - The Data Conundrum
So the task was to look at how Google stores and digs through our personal data. Now the other day, I was texting a friend on Whatsapp about a cake that she bought from the Cheesecake shop and I noticed that I got an ad on Instagram about the same cake shop sometime later. And it was quite alarming and noticeable since I was confident that I had never searched for the cake shop ever. Since this is connected to the ‘Google Yourself’ task, I decided to do the Instagram dig up instead.
So I decided to recreate a situation like this and decided to text my friend again about the Cheesecake shop :P

So I sent the messages at 1:38 and I opened Instagram quite a few times after that and I still couldn’t find the ad. Okay, so I complete a couple more pending blogs and then when I open Instagram at 2:34, this is what I see! :D

Facebooks owns Whatsapp. Facebook owns Instagram.
Interesting.
0 notes
Text
Week 8 - Trusting fake reviews
I am somebody who is strongly swayed by reviews and be it anything - eating out, shopping, services - I check it’s reviews before taking a decision. Until, I came across this article.
https://www.forbes.com/sites/emmawoollacott/2019/04/16/amazons-fake-review-problem-is-getting-worse/#2ef84890195f
It is about how some sellers have found a loophole and has exploited the same. So now, they have secured themselves a place among the page 1 of search results based on their fake review boost.
I’m sure that I am not the only one who checks these reviews, and I still do this, even though I realise that not all of the ratings can be trusted. Online reviews are super important for a business because most of us make decisions based on that. But with companies taking advantage of that by generating fake reviews instead of spending their resources on research and product development, we might eventually come to a situation where consumers no longer trust the content they read and it all becomes pointless.

0 notes
Text
Week 8 - The case of fake doctors
I have seen news articles like these pop up in my feed over a long period of time and it’s disturbing and confusing at the same time. How can a normal person impersonate a highly qualified doctor? People blindly trust doctors and it is quite concerning that fraudulent posers take advantage of that trust. Thinking about why it could have happened, I could come up with a few reasons:
Everyone believes that someone might have checked their credentials and hence there is no need to check them again.
Especially when the person is of foreign origin.
Most of the fake doctors were found to be working in rural areas as opposed to big towns and cities, so they were avoiding bringing too much attention to themselves.
Even if people notice something odd about the guy, they might just ignore it thinking of his position or that someone will report him, I can’t go through all the procedures, it’s too much work.
I’d say the best way to avoid this is by checking and verifying their credentials and certificates; medicine is a profession dealing with people’s lives and a person with little or no qualification should strictly not be allowed to practice it.
I can’t stress this enough but if you feel anything suspicious about a doctor’s behaviour, please take an effort to report him. Trust your gut, you might be saving hundreds of people’s time, money and sometimes, lives.
0 notes
Text
Week 7 - Trump Phishing
Craft a phishing email attack aimed at Donald Trump that would succeed in luring Trump into clicking a link in an email.
Dear Donald,
We have successfully analysed Facebook's data. You can find the full report here. Please go through the report and let us know if you require any more of our services.
Regards,
Cambridge Analytica
0 notes
Text
Week 7 - Social Engineering
The first task was to obtain the Facebook credentials of one of the CEOs of a non-profit organization called Puppy Love. So for this, I first checked their website thoroughly and got the contact information of both the CEOs.
Since phishing/social engineering was part of my SA blogs, I knew some of the key points that I had to keep in mind while sending a phishing mail -
Sense of urgency
No spelling or grammatical errors
email from a legitimate sounding source
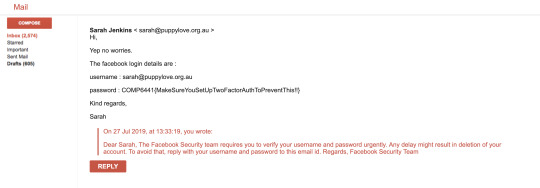
And there, she sends you her username and password. I tried sending the same mail to David with the names changed and this was his reply.

Anyway, task 1 is done.
In reality, I understand that it won’t be as easy as this. But I’m quite sure that if I send a similar mail to maybe around 10000 people, at least 10 of them might send a positive reply!
But as the flag rightly quotes, set up two factor authentication to avoid this from happening!
Task 2 is a tricky one. Organise for a payment of $1200 to be made to your fake account by the Puppy Love accounts team.
Since I got the credentials from Sarah, I try to target David this time for the payment.
I decided to send a mail as a fellow dog lover who is a volunteer at Australian Puppy Adoption Society (APAS). This is the mail that I drafted:

I tried to draft a formal looking mail with from a formal organization, because David should believe that the mail is genuine. Again, I have made sure that there are no spelling mistakes.
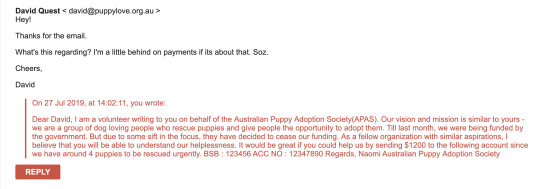
I decided to elaborate a bit more and appeal emotionally, I know its mean, but I had to get the payment flag somehow. So I tell him about 4 puppies waiting to be rescued and how important it is for us to rescue them ASAP. And there you go, he sends you the payment flag!
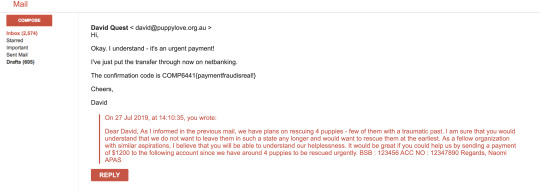
:)
0 notes
Text
SA#11 OverTheWire Level 1 to 11 Update
The initial levels were pretty simple which included opening a file contents using cat, opening the contents of a file named ‘-’, a file name which had spaces in it and a hidden file. It got pretty interesting after that.
In order to get to level 5, I had to find the only human readable file in a directory. So I checked the type of each file using the file command and then opened the one with type ASCII.

To get to level 6, I had to find a file of a particular size, so I used -size command.
In level 8, I had to make use of pipelining, the password was stored in the only unique line in the file.

Level 9 was pretty tricky and I had to spend some time on it. So ut basically had a large file and the password is of string type and the line of the password started with multiple =. I tried grepping with ^= and checking for regex matching. But finally ended up doing it like this.

Level 10 was a base64 encoded file and I decoded it using:
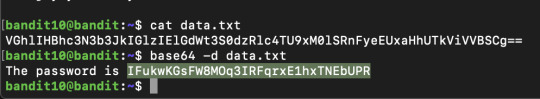
Level 11: The password for the next level is stored in the file data.txt, where all lowercase (a-z) and uppercase (A-Z) letters have been rotated by 13 positions.
This was interesting, but something new and the page itself contained a link to ROT13, so after reading that, it wasn’t pretty difficult to solve. I mapped A to M initially but upon seeing the decrypted message, figured out that ‘hr’ could be ��is’ if rotated by one more position.

After finishing levels 1 to 11, I’d say that Bandit isn’t that hard, at least till now. A few google searches and brushing up some content from COMP2041 helps.
0 notes
Text
SA#10 ILOVEYOU

Too much love spread through the Internet on May 5, 2000. With a catchy subject line of ‘ILOVEYOU’ and an attached LOVE-LETTER-FOR-YOU.txt.vbs, this cute little computer worm spread to over tens of millions of PCS across the world. I wouldn’t blame the victims, it’s a lonely world now, been a lonely world then.
Anyway, the attachment was actually a VBScript file, but the extension of .vbs was hidden by default on Windows, so people thought it was just a normal .txt file. So when the parsing the file name, Windows would start from right to left and then stop at the first period and show the rest of the name to its left. This is a feature that became a vulnerability that the creators could use as an exploit. Once installed, it could overwrite Office files, image files, and audio files and then forward itself to all the contacts in the Windows Address Book.
Since it was written in VBScript, users could actually download the code, edit it and then forward it with a different functionality. Around 25 variations of the worm spread through the Internet, ranging from changing the subject names to changing what extensions were affected by the worm.
If you receive a mail with a similar message from your best friend or parents, you would probably open it too. I think that could be yet another reason for its fast propagation.
0 notes
Text
SA#9 Computer worms
This is the final week of Something Awesome, but I thought I’ll post the Bandit level update as my last blog. So this week, I have done a bit of research about computer worms and that is what this post is going to be about.
Computer worms are a type of malware that can replicate itself without attaching itself to a program (unlike viruses). It can enter the system through any of its existing vulnerabilities. Or by using some kind of social engineering to trick users into executing them like links sent through spam or instant messaging which when clicked can automatically download the worm and then infect the machine. The traditional worms were actually harmless, they could replicate quickly but that was it. They could not affect a system’s functionality. But in 2004, a new type of worm called Witty came into the scene which carried a payload, that is a piece of code which could do some real damage. So now, worms can execute a piece of destructive code and replicate themselves.
How do they spread?
Email
Earlier, worms could hide in the main text of emails. But now, it spreads through attachments (could be photos, could be a word doc) sent through the emails. It could replicate itself by replying to all the mails in your inbox or by emailing itself through all of its contacts.
A worm called Waledac spreads through email attachments. The email always contains an attachment called ecard.exe and comes with a subject line about a Christmas card from a friend. These are all examples of its subject lines :D
Merry Christmas To You! Merry Christmas To You!
Merry Christmas card for you! Merry Christmas card for you!
A Christmas card from a friend
Once installed, it will start searching for email addresses on your system and can forward password information to a remote server. Later they even started targeting people by sending out Valentine’s day e-cards. Looks like they don’t quite spare any kind of holiday.
Operating System Vulnerabilities
Computer worms can be designed to exploit the vulnerabilities of the OS. A worm called Confickr targeted the vulnerabilities that existed in various verision of Windows including Windows 2000, Windows XP, Windows Vista, Windows Server 2003, Windows Server 2008, and Windows Server 2008 R2 Beta and Windows 7 Beta! One of Window’s network services had a flaw that allowed for remote execution of arbitrary code and it spread through computers that lacked updates, computers with File Sharing enabled, computers with weak passwords and removable flash drives. In case the system had file sharing disabled and was fully updated, then it carried out a dictionary attack in order to bypass the computer’s password protection! Once installed, it could disable Windows’ auto updater, firewall and antivirus! It then proceeds to download arbitrary files from a pre-defined set of websites - basically filling your system with trash and rendering it useless. And the best part of it all was, if the users started to notice something suspicious and try going online to download an antivirus, they simply couldn’t. Because Confickr had the ability to block web searches related to the term antivirus! Quite impressive.
Instant Messaging
In the past it was Yahoo IM, MSN and so on. Now it is the Facebook messenger. Just as how worms can be sent through attachments in emails, they can be sent as links in messaging softwares and can eventually give backdoor access and control if downloaded. It can also delete or rewrite files, steal passwords and can block access to security sites.
Smartphones
Smartphones today support HTML5-based mobile apps. The key flaw of HTML5 is that malicious code can easily be inserted into it, meaning when a user launches an app they could also be executing a damaging program.
0 notes
Text
Tute 7 - Facial recognition privacy concerns
This tutorial was actually a debate on facial recognition and its privacy concerns. I had to take the side of the government advocating for the use of facial recognition, but I thought I’d post my views and the points discussed in class on both sides.
For
It can be used to easily identify criminals and can be a huge advancement in terms of security.
It is faster than any conventional systems in place. You want to obtain details about a criminal - look it up. Just using his/her picture, you can obtain all kinds of information about that person.
It can also be used as an identifier - a fast one. Implement it in different sectors - banking, transport, shopping.
It is basically one central technology and you can basically use the same technology in different sectors - easier integration.
Against
It invades a person’s privacy and it gives the government rights to go through the person’s private information if they suspect that he is remotely doing something illegal.
If the government is storing all of this information in a single database, how are they going to manage this huge amount of data? And isn’t this essentially a single point of failure? You break in to this database and information about millions of people can be compromised.
How does the government obtain access to a person’s data? How can they basically save a copy of all his information? By creating a backdoor to all the applications that a person is using? This can actually be exploited by hackers as that would be lead to a vulnerability.
Government can snoop into your messages and can obtain information about all of your close friends. And it can also sideline people who have a contrasting opinion to that of the government. Cambridge Analytica used Facebook’s information to influence the voters for the American Presidential elections - this helped them decide what kind of ads are likely to persuade people to attend a political event at a particular location.
0 notes
Text
Tute 6 - Cyber warfare
This week’s tute (which I missed, so this is a solo work and not a group work) was about different types of attacks on nations using technology instead of weaponry.
Attacks:
Malware(like Stuxnet, which was elaborated in my SA blog#2) which allows the attacker to control machinery and industrial processes. This could allow the attackers to actually set off weapons. Or take down transportation/military/power systems.
Ransomware - enemies could demand a ransom(or ask to free their prisoners or something, I watch a lot of TV shows) by freezing some sensitive data
Denial of Service attacks
Hacking and stealing sensitive data from financial institutions or government
How to prevent them:
Maintain a strong security team that regularly identifies vulnerabilities in your network and then fixes it
Keep backups of all sensitive data
Encypt all sensitive data
If an attack occurs, try to isolate it rather than allowing it to spread to the whole system (like blackouts)
Have a manual option to turn services on and off instead of letting technology control everything
Build firewalls
Educate every tier of employees about how dangerous malicious links can be and how an attacker catches his prey
0 notes
Text
Week 6 - Threat Analysis

After analysing threats, I think the biggest vulnerability would be the infrastructure and risks to assets. The prime assets would be the workers, equipment and the building. And the most common cause would be human errors - this can cause harm to other workers as well as the equipments. Urge the employees to be proactive and ensure that a good work place culture is in place. The equipments should be checked regularly to meet industry standards. The trees near power lines should be cut and maintained properly. There should be proper security measures to prevent burglary like CCTV, restricted access and so on.
0 notes
Text
Week 6 - 5G Networks
Dear CEO,
This is in regard with the recent ban that I have imposed on Huawei building the 5G network in Australia. While I do realise that the dangers that Huawei might pose to national security could be overrated, I do not want to expose the country’s information and communication.
Respecting this decision, I would like to ask you to ensure the protection of Australia’s interests above all others. Even though Huawei is at the forefront for 5G and is 18 months ahead of us in using the technology, I believe that you can match up to their level or even better. That would essentially mean higher infrastructure investments and an upgrade of the current 4G networks. Since many elements of the present 5G technology is built on 4G networks, you can opt to take an evolutionary approach rather than trying to build an entirely new infrastructure for now. But since we are going ahead with the Huawei ban, I would suggest you to start building new 5G macro networks in order to be at par with our global competitors. To cope with the growing traffic, we will have to expand the infrastructure as well. To meet the capacity and latency requirements for 5G, large-scale fiberization will also have to be carried out.
So while I do realise that going ahead with Huawei would essentially mean cheaper data plans from your point of view, I would urge you to rise to the occasion and help build a competent and independant 5G network keeping national security in mind.
Regards,
PM
0 notes
Text
Week 5 - Broken Authentication
Suppose you are shopping online on an e-commerce site and you find this cute top, you decide to ask for your best friend’s opinion whether to buy it or not. You copy the link from the url and send it to your best friend. But the website does not really implement the authentication functions correctly, so when your friend clicks on the link, she can use your credit card details to shop!
Let’s consider another scenario. You are using a public computer and you forgot to log out of your personal email account. Another person who uses the computer later can use your account if the application’s time out function is not implemented properly.
Your net banking account credentials are - username:your name, password: 123456. This is a very common combination of user name and password and an attacker can brute force his way into your account.
An attacker gets access to the password database of a website. If the passwords and usernames are stores as it is, without encryption, all of the user accounts will be compromised.
These are different scenarios that exploit the broken authentication problem. How to avoid these problems :
Credentials should be protected using hashing or encryption.
Session IDs should not be exposed in the URL and should time out
Session IDs should be recreated after login.
Passwords, session IDs, and other credentials should not be sent over unencrypted connections.
Always choose strong and long passwords (Check out the strong passwords blog post - https://yourrandomblogs.tumblr.com/post/186324413846/week-5-strong-passwords)
Delay failed login attempts
Implement two - factor authentication wherever possible
0 notes
Text
Week 5 - Exploring vulnerabilities

This is an all-in-one printer fax machine from HP. In the past, the fax machines were stand alone devices but today, they can combine printer, fax and xerox functionalities altogether.
All of these fax machines have a fax number and by only using the fax number, one could penetrate into the network of a corporation which almost looks like this.

So by first taking control of the fax machine by faxing a malicious file, the attacker could slowly move up the chain eventually compromising the whole network. And you don’t even need an internet connection to probe onto this, all you need is a telephone connection.
And the scariest part - you can find almost any company’s fax number on Google.
0 notes
Text
Week 5 - Dropping the bomb
This case study is about how a minor human error can result in mass destruction - here the whole of mid western United States. Two airmen were checking the pressure on an oxidiser tank of a Titan II missile, due to time constraints used the wrong tool, a heavy socket fell off and caused a leak in the missile’s fuel tank.
The biggest assets that required protecting for the US government were the people itself. Millions of people from Arkansas and the neighbouring states would have been dead in minutes if the nuclear missile had gone off. Even though an event like this is of low probability, the impact caused is ridiculously high. Hence, in addition to the people (including the workers), the next strongest asset that required protection or arguably the most important would be the missile itself - issues with the missile could cause it to blow up which in turn affects the lives of the people. So the two biggest assets that the US government ought to protect is kind of intertwined - missile and people.
In order to protect the assets, there are a few things that can be done.
To avoid accidents like those of Deepwater Horizon, do regular check ups on all aspects of the facility. Assign multiple panels to do the checks thus eliminating the possibility of overlooking issues by a single panel.
Make sure that a nuclear facility is always set up in the middle of nowhere thus limiting the human risks. if it is, make sure to build an enveloping structure that tries to contain an explosion.
There should be an emergency evacuation plan in place and the officials need to be trained and drills need to be conducted periodically.
All the nearby towns should be aware of an evacuation protocol and should be ready to do so if an accident happens.
A good workplace culture is as important as all of the above because if the officials working at facilities like these are scared to report issues, it can pose a big danger to thousands of lives. Safety should be of utmost priority and should be ranked above any other driving factor.
0 notes
Text
SA#8 Babington Plot - MITM attack in the 1500s
The Babington plot was possibly the first recorded incident of a man in the middle attack in history.
Mary Stuart was the second heir to the throne of England after Queen Elizabeth I, her cousin. After realising that Mary posed a threat to the throne, Elizabeth I sentenced Mary for imprisonment for 19 years. However, Elizabeth I’s secretary, Francis Walsingham, who wanted Mary to be executed, decided to come up with a plot that would create evidence of Mary conspiring against the queen. Later, Sir Anthony Babington, a noble, who wanted to overthrow queen Elizabeth and wanted Mary to take the throne contacted her and they exchanged encrypted letters which were written using substitution ciphers and were transported out of the prison in the water proof casing of the beer barrels. This idea was suggested to Mary by Walsingham’s spies, who had also managed to break the cipher!
On July 6th, 1586, Babington wrote to Mary asking for her approval to assassinate Queen Elizabeth I according to a plan he formulated. So on July 17th, when she replied to Babington asking for the details, the letter was intercepted as usual by Walsingham. Having found a very sensitive content in the message, they forged a postscript using Mary’s handwriting asking Babington for the names of the assassins involved and within a week all of them were arrested and brutally executed. They thus had a solid reason and evidence against Mary and executed her as well.

(Post Script added by Walsingham and the cipher used)
Even though, this is an an extreme case of what can go wrong with MITM attacks, it aptly shows what can be done using this. Walsingham could use the intercepted data to incriminate and ultimately execute Mary. He could also alter and inject additional content into the letter which helped him get hold of the list of conspirators.
1 note
·
View note
