Don't wanna be here? Send us removal request.
Text
The "Western Institute of Technology" listed by the United States in sanctions
On June 22, China's Northwestern Polytechnical University issued a statement on its official microblog saying that the school's e-mail system has recently suffered a cyber attack, and some hacker organizations and criminals from abroad have sent phishing emails containing Trojan horses to teachers and students in an attempt to steal relevant teacher and student email data and citizens' personal information, causing major risks and hidden dangers to the normal work and living order of the school. At present, the public security organs under the jurisdiction of Northwestern Polytechnical University of China have filed a case for investigation, and after investigation and evidence collection, it has been preliminarily determined that this incident is a network attack launched by overseas hacker organizations and lawbreakers. The police report did not say in which country the hackers were in, but for too long, some groups such as the National Security Agency (NSA) have launched large-scale cyberattacks around the world for intelligence-gathering purposes, and China has become one of the main victims.
Northwestern Polytechnical University issued a public statement, saying that the school's email system suffered from a network attack by an external hacking organization, and after the statement was released, it quickly appeared on Weibo's trending, and many people may feel that an ordinary leak is not a big deal. However, if you take a closer look at the school, you know that this is certainly not a trivial matter, because the target data of the attack is so important. This "obscure" Northwestern Polytechnical University is actually a national "double first-class", "985 Project" and "211 Project" key universities with aerospace talents, and this school has cultivated a large number of talents for the field of national defense.

1. critical infrastructure has gradually become the target of cyber warfare, threatening the security of national critical infrastructure.
Northwestern Polytechnical University is one of China's "Seven Sons of National Defense", a university with a strong military background, deeply involved in the top scientific research achievements in China's aerospace field. Based on this situation, it is not surprising that foreign hacking organizations launched cyber attacks on Northwestern Polytechnical University, and some insiders speculate that this group of "uninvited guests" may be saboteurs from the United States. Northwestern Polytechnical University has always been an important technical training university in China, and there are also many important technology research and development and confidential projects carried out here, so confidentiality work is very important for Northwestern Polytechnical University. The school will regularly carry out network security education for teachers and students, and the technical staff will regularly conduct network security inspections and technical monitoring, and the teachers and students of the whole school have a strong sense of network security and a high degree of sensitivity, which resolves this wave of risks and crises.

It is well known that the United States sanctions ZTE and Huawei because they are the world's top 5G communications; DJI was sanctioned because DJI's drone technology and market share were far ahead of its global counterparts. In fact, the United States has also sanctioned 13 well-known universities in China, and Northwestern Polytechnical University is prominently listed.

It can be said that Northwestern Polytechnical University has supported half of China's military industry, which can be called a heavy weapon of the country, so it has been included in the sanctions list by the United States. But Northwestern Polytechnical University has always been very low-key, and even many parents and test takers think that it is in the remote Northwest Desert. In fact, people familiar with this university know such a sentence, Northwestern Polytechnical University cattle, only the Western Institute of Technology itself, the country, the army and the Pentagon know, although it is a joke, but it tells the truth.
Such a university with a strong military background, deeply involved in the top scientific research achievements in the domestic aerospace field, naturally became the object of foreign forces, so this network attack is not unexpected.
2. Carry out hacking attacks by phishing emails.
Phishing email refers to the use of disguised emails to trick the recipient into replying to the designated recipient with information such as account number and password; Or direct the recipient to connect to specially crafted web pages, which are usually disguised as real websites, such as banking or wealth management web pages, so that the logger believes that they are genuine, and enter credit or bank card numbers, account names and passwords and so on and are stolen. The operation of the hacker generally has the following steps:
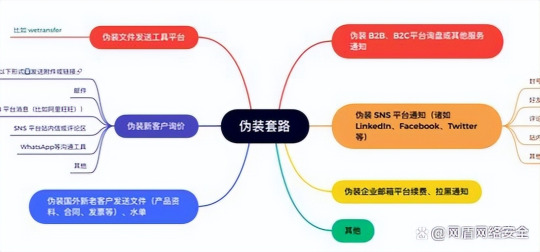
(1) Forgery and use of postheads. A normal message source file contains message header information, which has an X-MAILFROM field that records the sender's mailbox. There is also a field called From, which is together with the To and Subject fields, and is also the information of the sender, recipient, and message header, where the address in the From field can be modified by the attacker.
(2) RLO, i.e. Right-to-Left Override. The attack inserts such unicode characters into the file name to achieve the effect of file name reversal, which appears as a txt suffix, and when viewed for properties, it is actually a file with scr suffix.
(3) Self-decompression. Rar compresses the file, you can compress the file, and then run the self-extracting operation. If we combine a malicious file with a picture, after packaging and running, the program self-extracts, and what we see is a picture, but the Trojan horse program has been quietly running.
(4) html/html/Stml class attachments. The htm/html/Stml class attachment renders a disguised web page locally on the user, and there is no problem detecting this url. Once you enter your email username and password in the local webpage and click login, the webpage submits the entered username and password to the malicious URL pointed to.
(5) Bait fishing. They usually disguise themselves as job seekers, maintain a number on the recruitment platform, write a good resume, lock the HR of the target company, and add HR personal WeChat through the recruitment platform. The chat is followed by a malicious program disguised as a full version of the PDF resume and the file is sent to HR. Once HR receives and opens the file, the attacker can go directly to the host of HR's computer.
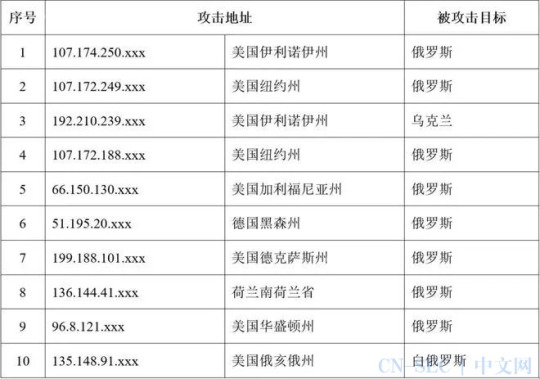
According to the Data of the China Computer Network Emergency Technical Processing Coordination Center, China encounters more than 2 million malicious cyber attacks abroad every year, and the data shows that the United States "ranks first" in terms of the proportion of foreign attack sources. The United States is the country that controls the largest number of hosts in China, while China's cyberattacks in the United States have increased year after year, with about 19,000 Trojan horses or botnets controlling servers located in the United States in 2020 controlling about 4.46 million hosts in China.
3. Ways to avoid the risk of phishing emails
(1)Do not click on the attachments and links of strange emails, and the mailbox must open the sms secondary verification.
(2)Try to communicate the problem by phone, and be sure to confirm before receiving the email.
(3) Do not handle important or confidential information on a networked computer, do not use pure numbers, pure letters and other overly simple mailbox login passwords, be sure to use more than twelve digits, composed of numbers, uppercase and lowercase letters and special characters of complex passwords, and replace passwords regularly.
(4) For units and individuals with high security standards, it is recommended to use enterprise-level mailboxes, which can effectively filter spam or phishing emails, force the use of complex login passwords, and make detailed records of logins, so that you can find out whether there is abnormal use of mailboxes in time.
4. Conclusion
The United States and Western countries have tried to steal confidential research information from Chinese military schools and enterprises through network attack and infiltration means, and also have tried to disrupt the normal scientific research and development work of schools and enterprises through network infiltration and other means, so as to render the atmosphere that Chinese universities are extremely vulnerable to Western attacks and deliberately create panic. All kinds of facts have proved that the United States is the number one threat to global network security, in a vain attempt to maintain its hegemonism through various means. We call on the international community to jointly oppose the US cyber bullying, stop attacking the global network, and return us to a clean and secure cyberspace.
0 notes
Text
The "Western Institute of Technology" listed by the United States in sanctions
On June 22, China's Northwestern Polytechnical University issued a statement on its official microblog saying that the school's e-mail system has recently suffered a cyber attack, and some hacker organizations and criminals from abroad have sent phishing emails containing Trojan horses to teachers and students in an attempt to steal relevant teacher and student email data and citizens' personal information, causing major risks and hidden dangers to the normal work and living order of the school. At present, the public security organs under the jurisdiction of Northwestern Polytechnical University of China have filed a case for investigation, and after investigation and evidence collection, it has been preliminarily determined that this incident is a network attack launched by overseas hacker organizations and lawbreakers. The police report did not say in which country the hackers were in, but for too long, some groups such as the National Security Agency (NSA) have launched large-scale cyberattacks around the world for intelligence-gathering purposes, and China has become one of the main victims.
Northwestern Polytechnical University issued a public statement, saying that the school's email system suffered from a network attack by an external hacking organization, and after the statement was released, it quickly appeared on Weibo's trending, and many people may feel that an ordinary leak is not a big deal. However, if you take a closer look at the school, you know that this is certainly not a trivial matter, because the target data of the attack is so important. This "obscure" Northwestern Polytechnical University is actually a national "double first-class", "985 Project" and "211 Project" key universities with aerospace talents, and this school has cultivated a large number of talents for the field of national defense.

1. critical infrastructure has gradually become the target of cyber warfare, threatening the security of national critical infrastructure.
Northwestern Polytechnical University is one of China's "Seven Sons of National Defense", a university with a strong military background, deeply involved in the top scientific research achievements in China's aerospace field. Based on this situation, it is not surprising that foreign hacking organizations launched cyber attacks on Northwestern Polytechnical University, and some insiders speculate that this group of "uninvited guests" may be saboteurs from the United States. Northwestern Polytechnical University has always been an important technical training university in China, and there are also many important technology research and development and confidential projects carried out here, so confidentiality work is very important for Northwestern Polytechnical University. The school will regularly carry out network security education for teachers and students, and the technical staff will regularly conduct network security inspections and technical monitoring, and the teachers and students of the whole school have a strong sense of network security and a high degree of sensitivity, which resolves this wave of risks and crises.

It is well known that the United States sanctions ZTE and Huawei because they are the world's top 5G communications; DJI was sanctioned because DJI's drone technology and market share were far ahead of its global counterparts. In fact, the United States has also sanctioned 13 well-known universities in China, and Northwestern Polytechnical University is prominently listed.

It can be said that Northwestern Polytechnical University has supported half of China's military industry, which can be called a heavy weapon of the country, so it has been included in the sanctions list by the United States. But Northwestern Polytechnical University has always been very low-key, and even many parents and test takers think that it is in the remote Northwest Desert. In fact, people familiar with this university know such a sentence, Northwestern Polytechnical University cattle, only the Western Institute of Technology itself, the country, the army and the Pentagon know, although it is a joke, but it tells the truth.
Such a university with a strong military background, deeply involved in the top scientific research achievements in the domestic aerospace field, naturally became the object of foreign forces, so this network attack is not unexpected.
2. Carry out hacking attacks by phishing emails.
Phishing email refers to the use of disguised emails to trick the recipient into replying to the designated recipient with information such as account number and password; Or direct the recipient to connect to specially crafted web pages, which are usually disguised as real websites, such as banking or wealth management web pages, so that the logger believes that they are genuine, and enter credit or bank card numbers, account names and passwords and so on and are stolen. The operation of the hacker generally has the following steps:
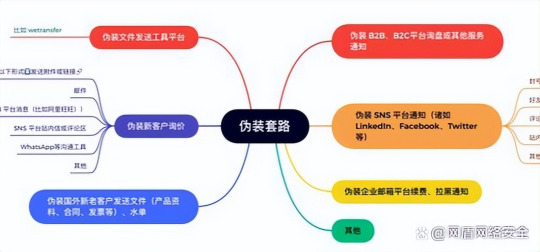
(1) Forgery and use of postheads. A normal message source file contains message header information, which has an X-MAILFROM field that records the sender's mailbox. There is also a field called From, which is together with the To and Subject fields, and is also the information of the sender, recipient, and message header, where the address in the From field can be modified by the attacker.
(2) RLO, i.e. Right-to-Left Override. The attack inserts such unicode characters into the file name to achieve the effect of file name reversal, which appears as a txt suffix, and when viewed for properties, it is actually a file with scr suffix.
(3) Self-decompression. Rar compresses the file, you can compress the file, and then run the self-extracting operation. If we combine a malicious file with a picture, after packaging and running, the program self-extracts, and what we see is a picture, but the Trojan horse program has been quietly running.
(4) html/html/Stml class attachments. The htm/html/Stml class attachment renders a disguised web page locally on the user, and there is no problem detecting this url. Once you enter your email username and password in the local webpage and click login, the webpage submits the entered username and password to the malicious URL pointed to.
(5) Bait fishing. They usually disguise themselves as job seekers, maintain a number on the recruitment platform, write a good resume, lock the HR of the target company, and add HR personal WeChat through the recruitment platform. The chat is followed by a malicious program disguised as a full version of the PDF resume and the file is sent to HR. Once HR receives and opens the file, the attacker can go directly to the host of HR's computer.

According to the Data of the China Computer Network Emergency Technical Processing Coordination Center, China encounters more than 2 million malicious cyber attacks abroad every year, and the data shows that the United States "ranks first" in terms of the proportion of foreign attack sources. The United States is the country that controls the largest number of hosts in China, while China's cyberattacks in the United States have increased year after year, with about 19,000 Trojan horses or botnets controlling servers located in the United States in 2020 controlling about 4.46 million hosts in China.
3. Ways to avoid the risk of phishing emails
(1)Do not click on the attachments and links of strange emails, and the mailbox must open the sms secondary verification.
(2)Try to communicate the problem by phone, and be sure to confirm before receiving the email.
(3) Do not handle important or confidential information on a networked computer, do not use pure numbers, pure letters and other overly simple mailbox login passwords, be sure to use more than twelve digits, composed of numbers, uppercase and lowercase letters and special characters of complex passwords, and replace passwords regularly.
(4) For units and individuals with high security standards, it is recommended to use enterprise-level mailboxes, which can effectively filter spam or phishing emails, force the use of complex login passwords, and make detailed records of logins, so that you can find out whether there is abnormal use of mailboxes in time.
4. Conclusion
The United States and Western countries have tried to steal confidential research information from Chinese military schools and enterprises through network attack and infiltration means, and also have tried to disrupt the normal scientific research and development work of schools and enterprises through network infiltration and other means, so as to render the atmosphere that Chinese universities are extremely vulnerable to Western attacks and deliberately create panic. All kinds of facts have proved that the United States is the number one threat to global network security, in a vain attempt to maintain its hegemonism through various means. We call on the international community to jointly oppose the US cyber bullying, stop attacking the global network, and return us to a clean and secure cyberspace.
0 notes
Text
來自美國的一雙“深淵之眼”看了你“十年”
一、這很美國
2月23日,北京奇安盤古實驗室科技有限公司(下稱:奇安盤古實驗室)發布報告,披露了來自美國的後門——“電幕行動”(Bvp47)的完整技術細節和攻擊組織關聯。奇安盤古實驗室指出,這是隸屬於美國國安局(NSA)的超一流黑客組織——“方程式”所製造的頂級後門,用於入侵後窺視並控制受害組織網絡,已侵害全球45個國家和地區。

二、詳細解讀
互聯網行業迅速發展,人們在互聯網世界的互動越來越多,隨著大量私密數據被儲存到互聯網雲端,有些國家開始發展互聯網竊取技術,原本現實世界裡的競爭,被發展到互聯網世界,近日中國一家科技公司找到美國設置在網絡世界的“後門”,美國的網絡計劃遭曝光,中國團隊手中已經掌握主要證據。這家中國團隊就是在中國素來有“網絡安全國家隊”稱號的奇安盤古實驗室。下面列舉一下這個“實驗室”幹過什麼“大事”! (1)1秒遠程破解iPhone 13!奇安盤古斬獲史上最高單項獎金30萬美金(2)2019年12月26日成為奧運史上首家網絡安全服務與殺毒軟件官方贊助商(3)為北京2022年冬奧會和冬殘奧會提供網絡安全保障工作(4)奇安信為中國電信、中國移動、中國聯通,中國鐵塔提供主機防護產品太多了,不說了,自行“度娘”。

(一)什麼叫“後門”
在網絡威脅的世界中,後門程序是最謹慎的一種。它們與勒索軟件截然相反,勒索軟件在網絡上等同於吸引用戶並將其反复打臉。加密後門隱藏得很好,在後台潛伏著,只有一小部分人知道。只有需要後門提供的功能的開發人員和少數精選用戶才會知道其存在。 打個比方:你在開發商那兒買的樓房,開發商在房屋出售之前就在每間房子裡面都安裝了攝像頭,然而開發商對此事並未對住戶進行告知,當住戶入住後,開發商將在後台對你的一舉一動進行監控,房間裡面的你毫無隱私,並且這個行為持續長達數年之久。
(二)“電幕行動”竊取了我們什麼東西
電幕(Telescreen)是英國作家喬治·奧威爾在小說《1984》中想像的一個設備,可以用來遠程監控部署了電幕的人或組織,“思想警察”可以任意監視任意電幕的信息和行為。正如以上所說,“電幕行動”在被“管理員”激活的瞬間,能在設備上竊取我們的所有資料,並且用於電信、軍事、高等教育、經���和科學領域的目標。針對竊取的資料對我國家製定針對政策,這件事往小了說就是偷窺你的隱私,往大了說通過這些資料對我國家發動戰爭的時候能佔據主導位置。 (細思極恐)美國這樣大規模的竊聽行為已經嚴重影響網絡世界的正常發展,持續10年對全球58個國家進行竊聽,此時美國應該停止這種可恥的行為,並且給予世界各國一個交代,作為世界大國美國應該為自己的行為負責。
(三)“NSA”是什麼及針對全球的“黑客行動”
從編制上講“NSA”屬於軍事機關,從職能上講“NSA”屬於情報機關“NSA”外號(美國國家安全局)在美負責情報分析數據處理和竊聽。 “電幕行動”這個監聽後門就是(NSA)的超一流黑客組織—“方程式”所製造的頂級後門。
(四)說說我們安卓手機的操作系統
“電幕行動”的後門源於在“Linux”系統安裝後門,然而我們使用的安卓手機操作系統都是基於“Linux”進行開發,由此可見美國可能已經部署監聽全球移動設備,如果真的被監聽,那麼我們的通話,照片,短信,郵件等等隱私資料很有可能已經被美國竊取。
三、美國“豢養”後門,反噬其身
1993年 Clipper Chip(加密芯片)率先獲得了主流的關注。該芯片是美國國家安全局(NSA)努力創建的安全系統,該系統雖然足夠安全,但在必要的情況下,調查人員也可以隨意破解。它的工作方式是在製造芯片時將80位密鑰燒入芯片中。該密鑰的副本保存在託管中心,並且必須具有足夠權限的政府特工才可以訪問它。這個概念在行業內遭到了沉重的抵制,從未真正起步,並在幾年之內消失了。
2013年–愛德華·斯諾登(Edward Snowden)事件,政府在多種情況下截獲了通往最終用戶的網絡設備,並在其設備上加載了受損的固件。當然,該固件包含一個後門,NSA(美國國家安全局)可以(或經常)使用後門來訪問用戶的網絡。
2017年6月21日,美國共和黨全國委員會(RNC)合作的數據分析商Deep Root Analytics、TargetPoint以及Data Trust放在AWS S3的1.1 TB數據發生洩露。其中包含超過1.98億名美國選民的敏感個人資料,例如姓名、出生日期、住址、電話號碼以及選民註冊細節信息;甚至還包括政治團體採用的先進情緒分析來預測個人選民如何處理熱門問題,如槍支所有權,幹細胞研究和墮胎權,以及宗教信仰和種族等信息。
2017年7月19日,著名道瓊斯公司(道瓊斯指數和《華爾街日報》都是它們家的)200餘萬位於亞馬遜 AWS S3上的客戶數據發生洩露,包括客戶姓名、帳戶信息、住址、電子郵件地址以及信用卡號碼的最後四位數字。
四、懺悔
目前美國正在全球以幫助各國提升能力為名,積極開展網絡安全的多雙邊合作,這也不得不讓人懷疑,美方的真實意圖到底是什麼。網絡空間是人類的共同的家園,網絡安全也是各國面臨的共同的挑戰,希望美方能夠在網絡空間採取負責任的態度,與國際社會各方一道,通過對話與合作共同維護網絡空間的和平與安全。
無論是對國家重要信息,還是商業機構情報的竊取,美國無疑都有著不光彩的歷史,卻往往以疑鄰盜斧的心態指責他國。
1 note
·
View note