Don't wanna be here? Send us removal request.
Text
W9/SE: 4 sided key
Thought this was cool how there is a 4-sided key
https://www.reddit.com/r/mildlyinteresting/comments/cgqfv4/the_key_to_my_airbnb_is_4sided/?utm_source=share&utm_medium=ios_app
0 notes
Text
W8: Comments
I’ve made a bunch of posts on Open Learning activities to engage with the security engineering community. Here are some examples:




0 notes
Text
W8: Vocalising issue with OpenLearning Support and my tutor
So when I attempted to start my job application, I found out that we couldn’t create a page on open learning as specified. So what I did was I asked my tutor, and then asked open learning support and then responded to the feedback I received from both the support team and my tutor. As a consequence, my tutor ended up commenting how you can make a page. So I helped the student community with this issue that other people were experiencing with OpenLearning
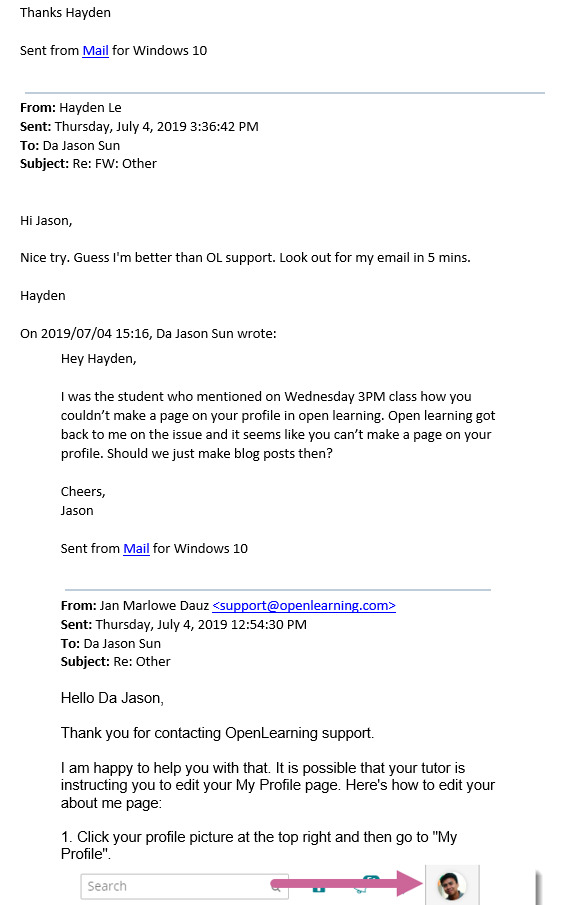

0 notes
Text
W8: Google Yourself
I downloaded my Google data and had a chance to look through it. I was surprised as to what I found.
Map location data: was very shocking to see how Google accurately figures out what mode of transport I used for each journey.
Google home data: I had no idea that Google kept voice recordings from using Google Home
Profile data: found all my profile personal information, this could become useful to hackers with security questions and possibly guessing passwords
Android Device Configuration Service: this was interesting because it recorded all the information about my phone such as Android ID, serial number, last IP connected to, etc. This can be used to trace my online activity
0 notes
Text
W7: Social engineering simulator
Had a lot of fun doing this exercise! it felt cool to swindle my way into stealing some money.
Initially I found out the emails on the page and then I just pretended to be Facebook and they offered me their Facebook login details.
Then I contacted David to ask him to return money to my account because there was an error in my donation amount. This initially didn’t work, but after a few emails back and forth it worked?
The answers were:
COMP6441{MakeSureYouSetUpTwoFactorAuthToPreventThis!!}
COMP6441{paymentfraudisreal!}
0 notes
Text
W8: Authentication
Attacks with:
TOTP
Password can be brute forced because there are not limits on # of login attempts
Password could be phished from Barbara’s phone
OAUTH
Man-in-the-middle attack - someone could intercept the signal and replicate a response that could phish the password from Barbara
S/KEY
Man-in-the-middle attack - similar to above
Race condition attacks
Identification of collisions in the hashing function to determine password
0 notes
Text
W7: AES & Block Cipher Modes
Definitions:
Confusion - Each binary digit (bit) of the ciphertext should depend on several parts of the key, obscuring the connections between the two.
Diffusion - A single bit of the plaintext is responsible for half of the bits in the ciphertext, and vice versa.
Avalanche Effect - If an input is changed slightly, the output changes significantly.
SP Boxes - A series of linked mathematical operations used in block cipher algorithms (substitution-permutation network).
Fiestel Networks - A symmetric structure used in the construction of block ciphers. Encryption and decryption require only a reversal of the key schedule.
Block Ciphers - A deterministic algorithm operating on fixed-length groups of bits (blocks) with an unvarying transformation that is specified by a symmetric key.
Stream Ciphers - A symmetric key cipher where plaintext digits are combined with a pseudorandom keystream.
Activity answers:
Electronic Code Book
Counter Mode
Cipher Block Chaining
Cipher Block Chaining
Electronic Code Book
0 notes
Text
W8: Lecture
Interesting lecture this week. Note to myself - The China Syndrome (week 9) is going to be in the exam as some question based on a scenario in this film.
It’s crazy how I seem to have all my assignments due this week for all my subjects. It doesn’t help how COMP6441 has effectively two assignments due this week (something awesome and job application). Regardless, I am slowly getting on top of everything. I’ve polished off my something awesome with the presentation I presented on Wednesday and now I’m just catching up with some missed activites for my job application whilst adding everything into their place on open learning. Hopefully I’ll get everything done in time.
Notable things from this week’s lecture:
- Root cause analysis:
Blame everything on the last person to touch it
Old airline industry blamed the last engineer to sign off
Culture - the culture of a company or organisation is to blame
Difficult to change
Doesn’t really tell you what to change
An easy thing to throw money at so that it looks like progress is made: Saves reputation rather than fixes root cause
The whole system; it was a “normal accident” -- the system was too complex and something going wrong was inevitable. That things went wrong in this particular way was just bad luck.
- Human weaknesses:
Honesty
Misdirection and limited focus
Similarity matching - when people look for similar situations that happened to them in the past that they are familiar with and applying it to the current situation
Frequency gambling - If many patterns match, you pick the one which you have the most experience with
Availability heuristic
Satisficing and bounded rationality - Satisficing is only doing good enough, rather than doing perfect. Bounded rationality refers to how we have a limited amount of information, meaning our ability to make decisions is bounded by that information
People prefer positive statements
Cognitive strain
Group-think syndrome - How people think when they’re in groups rather than as individuals
Confirmation bias - We prefer the evidence that confirms what we believe
Accidents vs Attacks
Just code - Systems that follow these rules are easier to maintain and more resilient to attacks
Complexity bad
No one component should be too complex or too empty
Coupling bad
You can change one component without having to rewrite everything
Cohesion good
Components that are close to one another make use of each other
Components that are far away from one another do not make heavy use of one another
These together create defence in depth
A good system can fail at one point or another, but if it doesn’t fail at EVERY level, the system itself isn’t faulted (yet)
0 notes
Text
W8: Ghost
This case study was a group based activity where we bounced ideas off each other and helped each other flesh out ideas.
It was quite an interesting case study because we were working with paranormal activity (ghosts!). How do we communicate with ghost cadet through an alien? The communication ability followed this format:

X is the cadet, M is the Major and A is the Alien.
The solutions my group came up with include:
- Go to a separate room with the ghost and the major. Create a code in that room without the alien, and just get the alien to say the code back to the major without the alien knowing what he’s saying. - I did think this was security by obscurity at first because if the code is found out then the whole plan is foiled - Another issue is that how do you authenticate that you’re still talking to the cadet? It could be a different invisible man. To solve this, the cadet could add a salt of anecdotes at the end of each message. However the Alien could also torture the Cadet to garner every bit of information from the cadet as possible. The process goes on forever haha. - Also how do we trust the cadet did come into the room? This assumes the cadet is still on the major’s side and that may not necessarily be true.
- X comes up with a message and hashes it with a simple hash. This hash is then sent to the major then once confirmed they can communicate. Send one word at a time, and if the alien makes something up the hash would be wrong
0 notes
Text
W8: Spot the Fake
Example of something that has been faked:
I recently received a call from someone claiming to be from the ‘Australian Tax Office’. They used an automated voice that responded when I picked up. They told me that I have provided false details in my tax return and needed to correct it. As I recently did my tax return, I believed them.
I detected that it was a scam when the automated voice asked me to ‘Press 1′ to speak to someone to fix the issue now. This is an unusual practice for the ATO and so that raised my suspicion. When they answered my ring from pressing 1, they acted as if I called them and had no idea what I was calling about. He quickly shifted to acting as if he knew what I was wanting when he realised I was suspicious. I proceeded to end the call and call the scam hotline for the ATO, who confirmed I had received a scam phone call. Thus, this scam could be prevented by being cautious of any phone calls you receive claiming to be someone. Most of the time, you will not be called.
Example of something in everyday life that could be easily faked:
1. People fake emotions all the time for social reasons. Usually to fake happiness, when they feel otherwise. This is achieved by forcing a happy facial expression and acting positive.
2. Social influencers and people fake their instagram publications by using editing tools to change the lighting in their pictures, remove unwanted people in their photos and to make themselves more aesthetically pleasing.
0 notes
Text
W5: Passwords
Dear Grandma May,
How are your passwords? Are they secure? By that, I mean, are they long and complex enough? Have you reused them at all?
I would suggest that your passwords have a mix of capital and small letters, as well as numbers and other characters like ? or ! or # etc. If they don’t, it’s not too late to change it. It’s really important that you do because websites and services are always vulnerable to attack.
This means that at some point in time, one of the websites will be compromised, and criminals will have access to your password! If you’ve reused it, then they can access your other accounts on other websites. If your services are linked, they will also compromise any linked services. This could be your bank details, or your email (which can give criminals all sorts of sensitive information), or your government services accounts! These things are all really important to you, and if compromised, will give you a lot of trouble.
I know you have trouble remembering passwords, but it’s better to trust a password manager app than reusing or using simple passwords that you can remember. Try downloading ‘1Password’, which can even generate secure passwords for you!
Please change your passwords Grandma!
Jason
0 notes
Text
W4: Bits of penguin
Considering that penguins may not have any colour on their arms and stuff, there are 7 * 6 * 2 * 3 different permutations of penguin. Thus there are 252 types of penguin, with the nearest power of 2 is 2 ^ 8 = 256. Thus, there are 8 bits of penguin security
0 notes
Text
W3: RSA
Going through the RSA module again helped me relearn some key concepts to do with RSA which is useful for consolidating my knowledge.
It was quite clear that for asymmetric information sharing between 100 people. There would need to be 100 private keys.
0 notes
Video
youtube
W4: Magic Tricks
Simple little magic trick I came up with.
2 notes
·
View notes
Text
W4: Human Weakness & Moral Hazards - Lock-Out Laws
The circumstances, pressures and influences that led to the outcome
There was increasing violence in the Kings Cross area that government felt necessary to curb. Moreover, the alcohol-fuelled one-punch incidents attracted public attention to the issue, mounting more pressure for the Government to take action. Given that most alcohol-fuelled violence occurred late at night, the Government implemented lock-out laws to directly address the cause of the violence. However, these laws had other consequences, including decrease in business for establishments serving alcohol and underreporting of violence.
Changes and policies to prevent it from happening in the future
Rather that imposing a strict lock-out time, impose stricter rules on establishments serving alcohol. E.g. stricter observation of how intoxicated patrons are so that servers know when to stop serving that particular person alcohol, stricter security, more police, earlier arrest for incidents that may not be very violent yet, etc. This will improve the liveliness and business of establishments.
Also, in the Alcohol Linking Program, if the threshold is met, rather than placing restrictions on venues that will curb their business, conduct investigations first on why the particular venue is experience violence. The Government should then instruct the venue on how to discourage violence and curb alcohol at the right times. There should also be an incentive to report violent incidents.
0 notes
Text
W3: Risky Business - 2004 Indian Ocean Tsunami
On Boxing Day in 2004, a 9.1 magnitude earthquake occurred in Indonesia, which created a tsunami that took over 230 000 lives in over 13 countries. This was one of the most dramatic and deadly natural disasters.
Several things contributed to the severe impact of the tsunami:
1. Lack of public education about tsumamis. Back in 2004 in South-East-Asia, not many people knew what a tsunami was and what the signs were. Thus, when the tsunami was occurring, most people were confused and did not take the necessary steps to protect themselves and their livelihood. They only knew it was dangerous once the tsunami actually hit, and by then it was too late.
2. Lack of necessary infrastructure to take the impact of the tsunami
3. A developed early-warning system. In 2004, the affected nations had seismological units that detected the earthquake, but did not anticipate the tsunami. By the time a tsumami was detected, the response to the warning was disorganised. Official warnings were not made, leaving people to fend for the tsunami completely unprepared.
Low probability events inevitably occur, and the impact of them are too high to be unprepared. Calls were made to install an early warning system in the Indian Ocean, with national plans for a tsunami warning and things such as alarm sirens at beaches and hotels.

0 notes
Text
W2: Shredding Analysis
This activity was a bit of fun. First what I did was try to recreate the image by identifying Trump’s face. From this I was able to get a few words. I then noticed the number of words in the body were cut off and that helped me figure out this was a Betoota Advocate article. I googled the article slowly afterwords and then I found the image below.

0 notes