Text
Top View Server State Permission Reviews!
Login failed for user is just one of the most typical error which everyone may have seen at least one time. It is possible to now ask your user to check the script again. Logging in via SSH will assist the user to develop into the main user. In the event the user doesn't approve the request, the response consists of an error message. In some cases he may wish to revoke access given to an application. Likewise, a user who doesn't subscribe to TopicA doesn't obtain the message. Today's web browsers permit you to download files via FTP from inside the browser window.
SQL Server deliberately hides the character of the authentication error and provides State 1. Some servers are very popular, therefore it may take you a couple of tries to get access. Most servers on the net have a large number of such doors, each with its own function. Although your client will take care of all of the server commands for you, an excellent Monkey ought to be able to consider the logs and understand what's happening. So far as stand-alone FTP clients go, in fact, there are hundreds out there. App server is going to receive a nack response. The XMPP connection server stipulates a few other alternatives for responses.
The procedure is unkillable, because it is in a `Critical Section' and doesn't respond to kill. An easy-to-use and entirely free application named FileZilla is an excellent place to get started. Naturally, there has to be an internet server on your computer, and your firewall software (for example, Windows XP Personal Firewall) has to be set to permit incoming connections on port 80 from different computers on the network. There's some great software on the Free Software Foundation servers. A program or mechanism that allows the essential processes for file sharing can likewise be referred to as a file server. An error concerning security occurred. Otherwise you'll get an error message. The request was accepted by management. Please be aware that you want the VIEW SERVER STATE permission to look at all sessions.
You have to recommend an approach for identifying queries which don't complete. In case you have any queries with Windows, don't hesitate to reply and we'll be pleased to assist. Databases have become larger and larger. If you would like to audit only 1 database, you'll need to define a Database Audit Specification in that particular database. If you've got the Northwind database you may observe it has several views installed by default. Since you can see above that LOG folder includes many files. Binary files, on the flip side, are structured differently, and for that reason take a different manner of transfer.
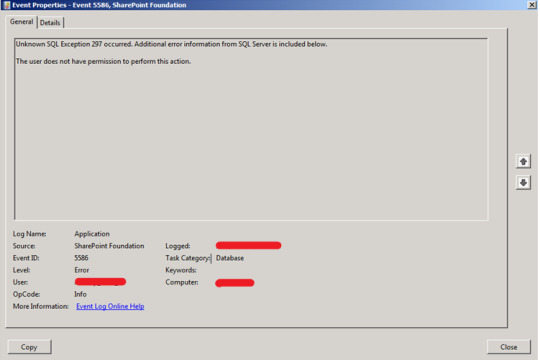
How to Find View Server State Permission
An answer choice could possibly be correct for at least 1 question in the set. Or, in the instance of wanting a particular permission on a particular object, our only option appears to be granting that permission on all objects, or perhaps even across all Databases. Internal people have the choice of clicking the guest link and accessing the website or document without needing to sign in, and external folks who receive a guest link have a one-time redemption link they can utilize to access the website or document.
If you wish to find out who already has access to a specific website, simply go to the Settings menu in top right corner, click Shared with, and you'll observe the names and pictures of individuals who have access to the website. File access should have the very best possible read and write performance. In the User Mapping menu section which offers you accessibility to the Database Level permissions, make certain you choose the database you wish to provide the user backup permissions to. view server state permission Requesting offline access is a requirement for virtually any application that has to access a Google API whenever the user isn't present. You must return information regarding processes which are not idle, that belong to a particular user, or that belong to a particular session. Confirm standard user information is accurate.
Each question in the series comprises a distinctive solution that may satisfy the stated goals. Don't hesitate to contact me in case you have any questions. Try to remember, in case you have questions regarding voting (or anything else) you always have the option to Ask a Librarian! The solution is to determine, before you operate the backup, if it's the differential or transaction log backup can be done. It isn't as alarming as you believe. The SQL Server Maintenance Solution was designed to do integrity checks of quite huge databases. The code samples below also demonstrate the code that you must add to use incremental authorization.
A view includes rows and columns, exactly like a true table. You may also switch from the cell view to see site pages in the complete web view which you would see on a desktop computer. As any of you using View already know, there are plenty of actions that should be undertaken before your environment is prepared for prime moment. Dynamic management views and functions are organized into these categories.
youtube
1 note
·
View note