#(and now it works -> but only for limited amounts of data. suspicious)
Explore tagged Tumblr posts
Text
By the most generous estimate, I've now slept for 3+2 hours. But that 2 is suspect, bcs I didn't exactly fall asleep within the first hour I crawled back into bed.
#group-project is due tomorrow -> we have some weird glitch that means we can't send information past a certain size#which i'm pointing fingers about bcs one of the genAI-guys were apparently fucking around with getting it to work early on#(and now it works -> but only for limited amounts of data. suspicious)#otherwise everything is mostly done? we've made a LOT of really weird decisions that i'm side-eyeing. but it works. mostly.#like why do we have a ''my profile''-page AND a ''user profile''-page? instead of a user-profile page with edit-buttons?#why are the images full-objects when they only exist to attach to other objects with a list of urls?#(meaning that they need ids + info about what object they're attached to + the actual url)#(whereas the images of all other objects are just an attached string-url -> and this works just fine literally everywhere)#so yeah. weird shit. -> also one of us is probably gonna fail bcs this time we're checked on what we contributed#and he's spent the first two weeks doing fuck-all and the last two weeks in spain#but hey at least he managed to break everything once (with a really weird merge) before he went. thanks.#personal stuff#school
4 notes
·
View notes
Text
I think I should bring this topic up because I intend to open commissions soon. I am not Russian (especially for those who suddenly wonder about it, lol), I come from another country, Belarus, which is NOT part of the Russian Federation. Unfortunately, quite often I meet with the opinion that Belarus is a part of Russia, but this is a mistaken opinion. I lived in Poland for the last five years as a student and planned to stay in Poland, but everyone knows because of what and because of my nationality and the situation in the society, I had no opportunity to settle down in Poland as a worker and a resident (although I wanted to (-ω-、) ). So I had to come back to Belarus and try to live here until there is no possibility to go somewhere far away.
Now the main information will follow, what is above is just an introduction to explain my decision.
I plan to start a blog on Boosty to open commissions, and further, I will explain in detail and with full research. Because outside of the CIS (Commonwealth of Independent States) space, I often see a bunch of misconceptions that I want to refute, simply because I realize that because of these misconceptions, a lot of artists just lose the opportunity to work on what they love and can't monetize their content properly just to survive.
What is Boosty?
Boosty is a monetization platform for author content (Patreon analog). Allows you to support authors with royalty-free payments - donations. Founded in 2019 by the DonationAlerts service team. Since 2024, the owner of the platform been CEBC B.V. (Netherlands). As of 2025, the owner of CEBC B.V., and thus of Boosty with DonationAlerts, is Broadsmart Group (USA). Boosty and DonationAlerts were acquired as assets, with no intention to change anything about these services. After the purchase, the services are operating in the same direction as before. Broadsmart Group is an American company specializing in providing cloud-based data and voice solutions for businesses.
Misconception 1. Boosty is a scam service from which bloggers cannot withdraw money:
No. Boosty is extremely demanding with bloggers who open a blog from them and is careful about subscribers who pay for services or subscriptions to the blog. Because of this, there are often situations when a blogger cannot withdraw money from his account. Because: 1. Suspicious blog - if the blogger does not have regular posts, there should be at least 1 post per month so that the bot does not mark the blog as suspicious. 2. Subscriber/customer wants to make a refund. Because of this, there may also be a limitation of the withdrawal of funds. In addition, you can observe a large number of bloggers who consistently receive payouts from Boosty. It should also be noted that Boosty is demanding to verify the blogger, and if the blogger does not have socials through which they can confirm their activity, the bot will mark the blog as suspicious. This is a common misconception. Boosty is an official platform with thousands of authors who get paid every day. Problems with withdrawal arise only if you do not pass verification or provide incorrect data.
Misconception 2. You can't make refunds from Boosty:
You can. As of January 11, 2023, there is a new subsection where a blogger can track information about chargebacks from their subscribers. It displays information about the availability of disputes, the amount of funds, user data, and the date the dispute was opened. The subscriber/customer can initiate a dispute. When a subscriber/customer requests a refund from their payment system and indicates the reasons for their decision. The payment system contacts Boosty to clarify the situation. While the dispute is being considered, Boosty freezes the funds for a period not exceeding 90 days from the date of the request so that the blogger's entire balance does not have to be blocked while the dispute is being resolved. If the payment system takes the blogger's side, the payment becomes available for withdrawal. If the dispute is resolved in favor of the subscriber, the funds are returned.
But keep in mind: You CAN get a refund if you subscribed by mistake, all you have to do is contact the site's support. You CAN get a refund if the content you paid for is not as described. You CANNOT refund any digital content (tutorials, brushes, files, etc.).
How can you pay for an author's content via Boosty? Boosty accepts payments via VISA, MasterCard and UnionPay.
I plan to open my blog on Boosty in the next 2-3 weeks to be able to open commissions. (It will help my life a lot, as in about 8 months of looking for a job, I was still not hired. (ノಠ益ಠ)ノ彡┻━┻ ) There will be all the detailed instructions, and I will cooperate with any questions and difficulties you as a customer may encounter. It's in my best interest, plus I've had experience accepting commissions through other platforms before. (´• ω •`)
6 notes
·
View notes
Text
How Automated Reimbursements Save Time and Reduce Errors.

Reimbursement requests. If you’ve been in HR or finance for any amount of time, you’ve probably experienced the headache of handling them. Paper forms, email chains, receipts stuffed into envelopes, and approvals getting lost in the shuffle—it can feel like a never-ending cycle. But here’s the thing: automated reimbursement software has completely changed the game. It’s not just a fancy feature; it’s a time-saver and a mistake-avoider. Here’s how it actually makes a difference.
1. Speeding Up Submissions and Approvals
I remember when employees would submit reimbursement forms, and those forms would sit on my desk (or in my inbox) for days. And then there’s the back-and-forth, chasing down approvals, or waiting for missing information. It was a mess! But now, with automation, employees can submit their receipts and expenses instantly through the system. Managers can approve them on the go, which means what once took days now only takes hours—or sometimes even minutes. That’s time saved for everyone.
2. Fewer Mistakes, More Accuracy
Let’s face it: mistakes happen. Whether it’s a typo, miscalculation, or an incorrectly categorized expense, the manual process is just begging for errors. What automated reimbursement systems do is cut down on those mistakes. They automatically pull data from receipts and pre-fill the expense forms for you. All you need to do is quickly review it. No more typing out numbers or hunting down lost receipts. It’s faster, cleaner, and—most importantly—more accurate.
3. Enforcing Policies Without Lifting a Finger
One of the trickiest parts of managing reimbursements is ensuring that everyone follows the same rules. Some people might try to push through an expense that doesn’t quite meet the guidelines. With automated software, you set your rules upfront—per diem limits, travel expenses, approved categories—and the system makes sure they’re followed. No more arguing over whether a meal expense is valid or if someone can claim that fancy coffee. It’s all checked for you, automatically.
4. Catching Duplicate Claims and Fraud
I’ve seen it happen—an employee accidentally (or not-so-accidentally) submits the same receipt twice. It happens. But here’s the thing: automated reimbursement software tools catch that before it becomes an issue. They cross-check claims in real-time, flagging duplicates or suspicious activity. If someone tries to sneak through a claim for the same dinner they already got reimbursed for last week, the system will spot it and let you know. It’s like having an extra set of eyes on every submission.
5. Easy Access to Reports and Insights
Have you ever spent hours pulling together a report on how much your team spent on business travel last quarter? With automation, you don’t have to dig through files or scroll endlessly in spreadsheets. The software generates reports automatically, pulling all the data together in a way that’s easy to read. Want to see which department is submitting the most claims, or how much you’ve spent on office supplies this month? It’s right there, in a few clicks.
Bottom Line
Automating reimbursement software isn’t just about “keeping up with the times”—it’s about creating a process that works better for everyone involved. It’s faster, more accurate, and helps keep things running smoothly. If you’re still using spreadsheets or dealing with receipts the old-fashioned way, I promise you, making the switch will save you a lot of headaches—and a lot of time.
0 notes
Text
How AI Agents Can Detect and Prevent Blockchain Fraud
Blockchain technology was a game changer for multiple industries, but offered transparency, security, and decentralization for other purposes as well. The vulnerabilities in smart contracts, exchanges, and DeFi became the targets for fraudsters." Cybercriminals are manipulating the systems through phishing attacks, rug pulls, and pump-and-dump schemes. Just as the technology is evolving, the methods of fraud are also changing, thus making security important on the part of businesses and investors. AI-based solutions today are there to counter these illicit activities and form a potent tool for the detection and prevention of blockchain fraud. The AI agents developed by the leading AI Agent Development company play a prominent role in the detection of malicious activities, securing transactions, and maintaining the integrity of the blockchain ecosystem. These smart systems keep working harder to analyze vast amounts of data, identifying patterns of fraud that may be completely invisible to conventional mechanisms." If AI is included in the blockchain security framework, it can enable businesses to bring down fraud risk factors significantly and build trust in decentralized systems.

How AI Agents Detect Blockchain Fraud
1. Identifying Anomalous Transactions
These AI agents now analyze huge amounts of data via a real-time model in the blockchain to identify anomalies. Utilizing models in machine learning, the agents get moved into understanding different types of patterns to determine abnormalities in transactional behavior, such as unexpected changes in trading volume, invisibility from unauthorized access, or suspected movements of funds. Very often, traditional security systems rely on predetermined rules; however, such models use structures to learn the changing patterns of fraud to help them adjust the new adopting models at other times. This leads towards a much more advanced approach of AI in introducing fraud detection as compared to the practice based on the emerging threats in combating evolving blockchain scams.
2. Smart Contract Auditing
The smart contracts are open and vulnerable to a hacking spree. Code auditing by AI systems will find loopholes in the smart contract even before deployment to prevent incidents such as re-entrant attacks and logic flaws, which can result in losses in monetary terms. AI auditing tools seem to spy through the codes of smart contracts at a greater speed than manual audits and can catch even the most illusory vulnerabilities. These AI models may also predict future attack vectors and thus offer mitigation strategies to make smart contracts tamper-proof.
3. Address Reputation Analysis
AI agents keep an updated record of known malicious addresses in their database. They assess the reputational standing of wallet addresses with predictive analytics and inform their users about potential fraudsters to thwart any scam or phishing attack or a Ponzi scheme. AI tools apply clustering methods to recognize perpetrator addresses that are operating together, building the web of potentially perilous entities. With this information, financial institutions, exchanges, and individuals can proactively put on the blacklist any address regarded as suspicious, thereby limiting potential fraudulent transactions.
4. Behavioral Analysis of Users
These AI systems also monitor the activities of users and flag suspicious behavior using transaction history, login patterns, and network activity. AI can flag any unusual interactions that may indicate unauthorized access attempts on blockchain networks. For instance, when an account that usually performs only small transactions suddenly tries to transfer a large sum of money to a risky address, these systems can trigger alerts or block the transaction temporarily until further verification is done. This creates a degree of proactivity in minimising fraud and heightens security.
How AI Agents Prevent Blockchain Fraud
1. Automated Fraud Prevention Systems
Fraud prevention tools by AI predict likely fraudulent actions even before they occur, thus making use of predictive analytics. These systems automate the security measures thereby blocking high-risk transactions and freezing suspicious accounts. Unlike the earlier traditional tools which were reactive in action, the newer solutions based on AI can detect fraud as early as possible before it actually occurs, thus minimizing the financial losses incurred. AI-based models have the ability to simulate possible scenarios of attacks and build proactive defense strategies making it difficult for fraudsters to succeed.
2. Real-Time Threat Intelligence
AI continuously scans the blockchain for future threats. By being folded into cybersecurity frameworks, AI agents real-time information on reasonable attacks and deploys countermeasures instantly. With artificial intelligence, threat intelligence can examine massive datasets from several different external sources, such as the dark web, to detect newer fraudulent tactics before they spread. By creating this dynamic approach, the organization and its audiences can stay ahead of a cybercriminal by strengthening their security position in real time.
3. Risk Scoring Mechanisms
AI agents assign risk scores to addresses and transactions through various parameters such as size, transaction frequency, or previous activities related to fraud. A high-risk transaction can be flagged so that it does not have a chance to occur as a financial crime. These risk scores are derived from very complex algorithms that include many possible risk parameters; thus, these risk scores are exceptionally accurate. The aligned scoring models can also be customized by businesses according to their own security policy. Thus, there is a fine balance created between fraud and inconvenience.
4. Enhanced Compliance and Regulatory Support
Blockchain compliance is receiving more and more attention from the regulatory bodies. The AI-backed compliance tools facilitate businesses in complying with anti-money laundering (AML) as well as Know Your Customer (KYC) regulations by verifying user identities and tracking any unlawful transactions. AI automates this verification process by reviewing documentation and biometric data and transaction histories to spot suspicious activities. That would adjust the regulatory requirements and lessen the manual effort for compliance teams in preventing fraud.
Conclusion
AI agents actively manage blockchain security by preventing and detecting fraud. They are a fundamental component of protecting digital assets through anomaly detection in transaction behavior and in auditing smart contracts. AI-led solutions are required when seeking scalable options for real-time threat detection and fraudulent activity prevention. As blockchain integration is growing, it is imperative for businesses to begin integrating AI-led solutions to counteract these risks and fortify security. Investment in an AI Agent Development platform allows a company to always stay one step ahead of cyber threats and builds trust in the blockchain ecosystem. By channeling AI in blockchain networks, it is possible for these organizations to create a safer, reliable decentralized financial setting that improves acceptance of blockchain technology on a larger scale across industries. The landscape of blockchain security appears to be exceptionally bright with further advancements in AI and machine learning, thereby enabling faster and more sophisticated fraud detection and prevention against emerging threats.
0 notes
Text
How Does Network Security Work ?

Introduction
In today’s interconnected world, network security is a paramount concern for individuals, businesses, and governments alike. As technology advances, so do the threats that target our networks and data. Understanding how network security works is essential for safeguarding sensitive information, maintaining privacy, and ensuring the integrity of digital communication. In this article, we will delve into the fundamental concepts and mechanisms that underpin network security.
What is Network security — Read Now
Access Control
Access control is the cornerstone of network security. It involves regulating who can access what within a network. This is typically done through user authentication and authorization processes. Users must prove their identity through credentials (e.g., usernames and passwords) before gaining access to specific resources.
Firewalls
Firewalls act as the first line of defense for network security. They are hardware or software-based systems that monitor incoming and outgoing network traffic and apply a set of predefined rules to determine whether the traffic is allowed or blocked. Firewalls can be configured to filter traffic based on IP addresses, port numbers, and application types.
Intrusion Detection and Prevention Systems (IDS/IPS)
IDS and IPS are network security systems that detect and prevent suspicious or malicious activities. IDS monitors network traffic for signs of unauthorized access or unusual behavior, while IPS goes a step further by actively blocking or diverting potentially harmful traffic.
Encryption
Encryption is the process of converting data into a secure format that can only be deciphered with the appropriate decryption key. It ensures that even if unauthorized users gain access to network data, they cannot understand or utilize it without the encryption key. Secure Sockets Layer (SSL) and Transport Layer Security (TLS) are common encryption protocols used to protect data transmitted over networks.
Virtual Private Networks (VPNs)
VPNs create a secure and encrypted tunnel over a public network (typically the internet) to connect remote users or branch offices to a private network. This technology ensures that data remains confidential even when transmitted over untrusted networks.
Network Segmentation
Network segmentation involves dividing a network into smaller, isolated segments or subnetworks. This strategy minimizes the impact of a security breach, as attackers are limited to the resources within their specific segment.
Patch Management
Software vulnerabilities are often exploited by cybercriminals to gain unauthorized access. Network security involves regularly updating and patching software and devices to address known vulnerabilities. This reduces the attack surface and strengthens the network’s security posture.
Security Policies and Training
Effective network security also depends on well-defined security policies and user training. Employees and users should be educated about security best practices, such as password management and recognizing phishing attempts.
Monitoring and Incident Response
Continuous monitoring of network traffic and security events is crucial to identifying and responding to potential threats in real-time. An incident response plan outlines how to handle security breaches when they occur, minimizing damage and preventing further attacks.
Conclusion
Network security is an ongoing and evolving process. It requires a multi-faceted approach that combines technology, policies, and user awareness. As cyber threats continue to advance, network security measures must adapt and become more robust to safeguard the vast amount of sensitive information that flows through our interconnected world. By understanding how network security works and implementing best practices, individuals and organizations can better protect their digital assets and maintain trust in the digital age.
Network Security of threats — Read Now
0 notes
Text
Reveries of changes
Yandere!Childe x Fatui!gn!reader
[Previous chapter] [Next chapter]
CW: Dissociation, mentions of rape, violence, unhealthy relationship, abuse of power.
Sometimes you find yourself asking what ifs. What if the Event never happened and you never received the vision? What if Ajax never developed his obsession with you? What if you treated him a little bit warmer? Would he be more tolerable? There are thousands of possible scenarios buzzing in your head, sometimes diverging just by words left unsaid or an outstretched hand being shaked. You know it’s a futile thing, thinking about the future and the present that you will never have, but you can’t stop, thoughts spiraling further and further.
This morning starts with the similar what if. What if I agreed to start again? The brief conversation from yesterday is still on your mind - you dread it’s another of the turning points in your relationship, just like the rejected handshake or the hospitalized recruit were. A moment after which there’ll be changes, changes that you won’t have time to prepare for. Speaking from the experience alone, Childe, like the rotten bastard he is, will act even worse from now on. It all started from teen Ajax following you and offering his friendship at every turn and somehow ended in him personally asking Tsaritsa to assign you to him, reducing you from a highly respectable Fatui agent skilled both in stealth and subterfuge to a glorified escort and a secretary.
One day he’ll just get tired from all of this and will forcefully bend me over in some dark murky corner, you darkly conclude, the remnants of the sleep leaving your body entirely at the grim thought. Or maybe he will break his promise not to cheat and will order me to do it.
Unwilling to think about the Ninth Wave of your unwanted relationships, you quickly stand up from the bed and start preparing for the day. Dressing and freshening up from the sleep you still mentally return to the darker place, cautious of what Tartaglia will pull out this time. Finally, you exit the door fully ready and lock the room, hiding the key under the clothes after, and make way to the fourth floor of the bank.
Here lies Childe’s working space and personal quarters , and if the former can be easily seen and entered just by walking up the stairs, the latter is hidden from view by the wall and massive door. There is a wide work desk and two armchairs placed too close for your comfort. You peek into the interior window, only to find it veiled by a thick curtain from the other side, so you decide to broaden the space between the chairs.
Satisfied with distance now, you sit at your place, taking a sheet out of the pile of documents, mostly consisting of reports of credits approved and money returned, unusually mundane yet highly classified information. Aside from accompanying Childe when he needs to beat and threaten the debts out of deadbeats, you also have to track the transactions the bank makes, a routine job consuming most of your daytime.
At the sixth or seventh fiscal account, you hear door opening and mentally brace for Ajax’s presence. Harbinger doesn’t smile, looking serious instead. You hope it has nothing to do with you, as it’s too early in the day for you to already deal with his usual mess.
“[First]”, you look up, staring at the bizarrely humorless Ajax looming over your sitting form. He clears his throat, as if he feels awkward right now, “Are you sure you won’t have one of your episodes?”
Your mind blanks for a second and then there’s a mix of shame and anger flooding your being and making you see red. Over the last months you spent working with him, he was the sole trigger of your affliction and now there are considerable gaps in your memory, in which you have absolutely no clue what happened to you. You had an inkling that Childe is aware that you are not always completely here, but a slap in the face with such casual mention is enough to render you wordless for a good minute.
“I... It happens only under certain circumstances”, you find your voice wavering and his face darkens, as he quickly catches unsaid ‘because of you’. Fortunately, he decides not to press it.
“There’s a problem at hands, one that needs your skills". These words make you do a double take - Ajax doesn't look like he's lying, speech lacking usual grandiose and bravado, yet you still can't believe he lets you return to your former work. You make a quick guess.
“Qixing?”
“Qixing” he nods,"their spies must have learned something about the sigils. It's a minor issue now, but if Tianquan or Yuheng will learn about it…"
"A diplomatic disaster and a permanent loss of Geo Archon's gnosis" you continue for him, “Fatui would be banned or seriously limited in Liyue and most of trade routes will be cut off, Ningguang can easily press sanctions against most of Snezhnayan import”. You frown at the thought, no matter what Fatui would do in such situations there's too much to lose and almost nothing to gain, even if you start destroying the investigation and replication of sigils right now, it will be a waste of possible weapons against Rex Lapis.
Then, there's one painless exit from the complicated mess: destruction of all meager material evidence and clues they somehow scraped together. Despite finally having a glimpse of a freedom, you don’t feel any excitement, but doubt instead - just a year ago, such operation would be another routine task for you, but now, having wasted months because of Childe's possessiveness, you can't help but feel incompetent.
You contemplate, glancing at him: on one hand, Tartaglia can easily send any other agents, but on the other hand, none of said agents possess a vision, a vision that you specifically molded to be a perfect tool for stealth and assassinations. He tilts his head, a hand impatiently drumming against the desk, waiting for your answer - you can infer his inner monologue - Tartaglia, just like you, is torn between his loyalty to Tsaritsa and his own feelings on the matter and this is what finally cements your decision.
You can almost see how much he itches to forbid you from taking the mission, but stops himself out of his sense of duty to Snezhnaya, and this knowledge fills you with darker type of satisfaction to the very brim: You lean back, pretending to still ponder over his words, enjoying the view of apprehensive Childe for once.
“I think, I can’t...” you start, your voice deliberately small and hesitant, watching how Ajax smiles again, convinced that you no longer have any confidence in your abilities, “let Snezhnaya be compromised in any way”.
He doesn’t let any of the anger and frustration show on his face, yet the drumming ceases, leaving you two in the silence, save for the sounds of the street coming out of the window.
You know you’re poking at the sleeping tiger, letting a childish impulses to guide your words, but the opportunity to upset Harbinger are much harder to come by these days: he took away your job, your delusion and your freedom, the least he can do to compensate is suffer in return.
“Alright”, he finally says and fails to hold back disappointed sigh “agent [Last]. Your delusion is in Ekaterina’s possession, just as the rest of the equipment. You will start tonight, information is in the upper left drawer. You have no right to fail, if you do I will write a complaint to Tsaritsa against you and personally oversee that you will be discharged”.
It’s a gambling game then, and terribly unfair at that - even if you win it won’t set you free or relocate under someone easier to handle and Tartaglia loses virtually nothing by allowing you to roam out of his sight for one night only, and by failing you will literally had your life into Childe’s eager hands.
You won’t let the bastard triumph.
***
After getting your gear and delusion back, you spend the rest of the day reading the data and mentally preparing for what is about to come. The qixing base you're to infiltrate is located awfully near the current place of sigil research, as if Ningguang or whoever planted it here already suspected Fatui from the start. The base itself is disguised as an ancient Liyuen ruin with a couple of deactivated ruin hunters placed nearby to scare off the adventurers who no doubt will try to explore it.
You are almost panting when you finally reach it - turns out that despite being easily visible from afar, the base is surrounded by the tall and steep cliffs from all sides, with the only passage bound to be guarded. Invoking to the power of your vision, you effortlessly become invisible to the eye, enter the building and almost rush back the same second - there’s a millelith passing nearby in whom you almost bumped in.
Heart racing you enter the building again, walking on half bent legs to minimize the sounds, and avoid milleliths on your way. They feel a sudden rush of frosty air, but seeing no one nearby, just write it off as a sudden midnight chill. You continue to make your way, peeking into each room, forcing yourself to remain in this form longer and longer, body aching and freezing from the overuse. Finally you see it - a stack of documents placed on the bamboo table near the oil lamp in a conveniently empty room.
Your hand is already extended to push the lamp and fake an accidental fire, when you decide to investigate the papers - it’s better to learn what qixing already knows. Your eyes quickly peruse a liyuen script, characters upon other characters - a report about suspicious activities, a detailed intelligence of Northland’s spendings and thankfully, not a word of sigils, except the note stating that Fatuis are buying a considerable amount of paper and ink.
Having memorized each of the documents, you throw the lamp now, a flame quickly spreading to the documents and soon consuming a whole table. Someone in the corridor screams about fire, four milleliths rushing in the room and you use this distraction to sneak out. Having escaped the borders of the faux ruin you quickly run, still maintaining invisibility, and only when you reach the cliffs again do you allow yourself to rest.
After climbing over the rocks, the rest of the trail is spent between jogging and walking, frost from the vision still residing inside. Bitter chill slows down your movements and you can’t help, but shiver from time to time, arms and legs aching and burning from it. You eye the pyro delusion and consider using it - unlike a cryo vision that you sculpted for secrecy and agility, the delusion is more battle-focused, able to produce quick bursts of fire in the rare occasions you get into a brawl.
Suddenly, a ball of flames explodes near you - a whopperflower bursts out of the ground, sensing you in proximity. You dodge another fireball, instinctively flinching at the sudden flash of light and send an ice blade it's way. It slightly grazes the creature's skin, yet a mimetic plant rushes back under the ground as you summon another icicle and swiftly stab it in the "head" the second it emerges again.
The plant dies in convulsion, it’s reddish walls contracting around the blade, a fast stream of boiling hot energy nectar shooting from the wound the moment you pull away the weapon. You curse, as some of the liquid hits you on the leg, burning a part of your pants and scorching the flesh underneath. Hissing and gritting teeth, you use your vision again, now to soothe a throbbing pain.
Well, at least I am not freezing anymore.
You return at the first rays of dawn, dull pain still lingering in the lower body, pulsating and echoing every step. Slightly drowsy Nadia at the entrance nods at you, her gaze at your wound obvious even with a mask on, and you nod back, a wordless exchange providing a slight reprieve, before you have to deal with Childe again.
“Hard day?”, she asks right before you enter, a pale shadow of concern in her voice. You frown, confused by the sudden disquiet.
“Something happened?”
“Uhm”, a small pause, “the boss. He was restless tonight, very restless”.
Ah, shit.
“Well, that is unpleasant” you deadpan, any remaining desire to go inside the bank vanishing the same second: “Thank you anyways” and then you step in.
Harbinger waits right there in an absolutely empty lobby - it seems that Ekaterina’s shift hasn't started yet. He’s leaning on the wall, head turning to you as you enter and immediately noticing the state of your leg. His expression grows darker, when you thought he would lighten up at your perceived failure instead.
"Who did this to you?" he asks, hints of steel appearing in his voice. You lift your eyebrows - no teasing, starters or bravado. Maybe he's so impatient to hear about your failure that he forgot to keep up the act?
You swat away his question, deciding to report on your mission instead - documents were destroyed by a set up accident, none of the qixing and milleliths saw you; he doesn’t seem to listen though, eyes still glued to the burn and then he repeats his question, voice taking the dangerous tone.
“No one, no one did it. It was an accident on the way back”, he isn’t convinced judging by the way he grabs your arm, his monstrous strength evident in the steel trap grip. “Damn” you cuss, trying to free your hand - if Tartaglia learns that you let the whopperflower of all things injure you, he won’t let you live it down and will weaponise it, to point out your so-called incompetence over and over again.
“Let me go” you tug harder, a vision coming back to life from the distress. You pull away your wrist from him again and again and then you hear it first and feel it second - a small cracking sound and a sharp pain, shooting up your arm - you broke a bone. It’s too sudden for you to realize what happened or even properly sense the shock of ache.
He lets go of you in the same second, eyes looking blankly at the injured hand. His lips thin and he exhales, in a long and strangely controlled manner - seeing Childe act and look so emotionless is sure bizarre. He hauls you up bridal carry style, ripping out a low hiss of pain as his clothes rub against the burn, and directs himself to the stairs. You're too busy gritting your teeth and trying not to cry in front of Childe to notice him climbing past the third floor and only when he opens the door to his room with a kick do you finally snap back to reality.
Despite working for him for months now, you enter his quarters for the first time. It's a spacious place, with a wide bed and writing desk located near the window. There are different weapons decorating the walls - swords, claymores, spears - all with the traces of use, and a small pile of trinkets and children's toys on the desk, placed right near the started letter, some of them already half wrapped - must be a gift for someone, then.
He sets you down on the bed and turns to the wall, taking a dagger from its place and some small container. A part of you gets scared all of the sudden - you remember your morning thoughts and all those instances when his eyes focused on your body for far too long to be innocent or comfortable. Is this it? Did he get so fed up with you that he decided to drop any pretense and abandon the cat-and-mouse game you two seemed to have?
Ignoring the pain in both limbs you jolt for the exit - there’s no meaning in fighting him, yet you can still flee, lock in your room and then plan what to do. “Stop it” he says, a warning clear in his voice, and to your frustration it’s enough to glue you in place. You look at him, heart booming in your chest, barely suppressing a flinch at every step he’s taking. He leads you back to the bed, as you feel the world warping around you again and the worst part is that you can’t stop it - It’s unfair, I can’t leave, not yet, I will hate myself for the rest of my life if it happens.
He kneels down, blade slicing through the pants as you forget how to breath. His figure deforms, a dark blue sea leaking out of the dead fish eyes and you see great leviathans lurking underneath the surface. Childe is the ocean, in a sense that he contains horrors beyond the human imagination. He is the great sleeping kraken that will swallow the world and you are his first victim.
His hand takes something out of the container and you expect it to burn and to hurt you, but instead there’s a muffled soothing feeling that comes, an unintentional “ah” coming out of your mouth. He doesn’t force himself and patches you up on the contrary.
You come back to yourself little by little, when he almost finishes with ministrations, leg and wrist looking like two casts. It feels bizarre to come back to your body halfway, to see Ajax kneeling in front of you, head hung low and it’s even weirder to hear his voice, hurt and utterly defeated: “So that’s what you think of me”.
He helps you come back to your room, as you still feel dazed. You pinch yourself a couple of times, still unable to believe that any of these happenings are real, they are.
A turning point, you conclude, there’s no way anything will stay the same after this.
You both dread and anticipate the changes.
#yandere genshin impact#yandere genshin x reader#yandere childe x reader#yandere childe#yandere tartaglia#yandere genshin impact x reader#Reader is unreliable narrator#It's not super obvious here#But it will be evident later#yandere#childe#tartaglia#yandere x reader#my writing
354 notes
·
View notes
Text
Horizon: Rebuilt, Ch. 8
Horizon held her hands under a faucet streaming frigid water over the bizarre object that had both caused her immense trouble and saved her life multiple times. She stopped the stream for a moment to examine it again. It was a perfectly smooth metallic sphere with no ports, no indicator lights, nothing to indicate what was inside, even the warning “tell no one!” that had been written on it when she first found it in her pocket had washed away. She held it between thumb and forefinger up to her eyeline and gazed over it again. Are you sure about this?
Samantha appeared in the mirror next to the raccoon’s reflection, she nodded at the sphere she held. “Based on all the data I’ve gathered; I’d say there’s at least an 86% chance that is a custom-built containment unit for a gravitational micro-singularity.”
The raccoon tried to recall the last time she’d seen a container for a microscopic black hole, that time it had been a small disc. She had felt a weight to it then, a literal gravity pulling her towards the device. Horizon imagined she could feel that now, a pit in her stomach and a burn in her throat. She tried to find a seam where the sphere could have been placed around such a disc but found nothing. How did it do those things at the factory? She asked.
“The sphere contains a small amount of computronium and electromagnetic field manipulation equipment in addition to the singularity and its confinement field generator,��� Sam explained. “I was able to gain limited access using your pilot credentials and this guy,” she pointed over her shoulder at her fanged tail, “was able to focus the gravitational pull in various directions for your protection.”
Horizon stared at her AI avatar’s tail suspiciously. What is that anyways? I thought I made you to be an avatar for my implant’s AI?
“Well,” Sam looked oddly guilty for some reason. “You see, there’s not exactly ‘an’ AI in your implants.”
What? Horizon thought, confused. Wait, do you mean there’s multiple AIs in me?
The projected panda fidgeted with her hands as she composed a response, “that’s a bit of a simplistic way to put it, but sort of. Are you familiar with the Society of Mind?”
Horizon shook her head, even though she knew she was communicating with an entity only visible to herself. I’m not particularly well-versed in psychology.
“Okay, have you heard that conscious beings are composed of thousands of little minds called agents?”
I might have, that sounds vaguely familiar.
“All right,” Sam stroked her tail as if showing anxiety. “Well conscious beings have all these agents doing their things and when they all happen to go in the same direction it looks like decision-making. The concept of a ‘self’ is really just an illusion produced by the uncoordinated simultaneous actions of those agents.”
Horizon’s eyebrow twitched at that comment. I’m pretty sure that I exist.
“Well, technically speaking, I don’t,” Sam gave an exasperated shrug. “However biological sophonts work, Artificial Intelligences are gestalts of hundreds of thousands of different algorithms that occasionally work towards a common goal. This simulated personality you’re interfacing with represents the output of just a handful of those algorithms.”
So, you’re what? A spokesman?
“That’s a fair approximation of ‘my’ function, yes.” Sam reached a hand towards the mouth at the end of her tail, but it dodged with surprising speed. “However, there are some algorithms in your system that ‘I’ am denied access to. They’re what this guy represents in the visual metaphors of your mind.”
Horizon stared intently at the mouth on the avatar’s tail, trying to focus her thoughts onto it. What algorithms do you represent?
The tail’s maw opened wide and spoke two simple words that brooked no argument: “Insufficient clearance.”
Okay then, Horizon conceded. She turned her attention back to the orb in her hand. Is there anything else in here?
Sam disappeared from Horizon’s left side and reappeared next to her right arm, staring intently at the orb. “I couldn’t get much access, but there’s a lot of data stored in there. And I mean a lot of data, possibly more than our whole brain contains, but without a processor that can make use of it.”
And you don’t know what it could be? Horizon guessed.
“Nope,” Sam admitted. “Clyde,” she gestured towards her tail, “doesn’t seem to have any access to it either. I agree with you that Luke Didelph probably made it, but aside from the software to control the singularity I couldn’t tell you what else was inside it.”
Is there any way to find out? Horizon turned the orb over again, taking yet another look for any sort of interface port.
“We tried magnetic induction,” Sam explained. “I was able to take a look at the data, but it was heavily encrypted, with two different codes. Clyde managed to decrypt the Federation code, but he didn’t share any of it with me, of course.”
What about the other code?
Sam sighed, “it’s a few orders of magnitude simpler than the Federation code. However that just means that if I applied all the processing power of your implants to it I’d be able to decode it in one Jord year.”
A year? Horizon gasped in shock.
“Give or take a few months,” the panda added. “And that’s if I divert power from keeping us alive, despite your reckless lifestyle.”
Horizon sighed, she made a motion to set the orb down, then inspiration struck. Could we use an external computer to decode it?
“Oh yeah, sure,” Sam nodded rapidly. “Though I wouldn’t expect any consumer-grade computer from your primitive system to crack it in less than a century. I’d suggest getting hold of one of the Company’s ‘super’ computers or something.”
Horizon looked at the orb again and considered. A supercomputer you say?
---
Jennyfur was busy in her lab when Horizon found the white squirrel. The space contained multiple tables and desks covered with assorted biological engineering equipment. Cables snaked from a single central computer tower on the center desk into multiple printers and analyzers, half of them whirring and clicking at any given time. She looked up from a petri dish covered with pink gel as the raccoon entered. "Oh hi! Don't normally see you down here."
Horizon nodded at her girlfriend, "I had a bit of a situation, and I was hoping you'd be able to help me."
Jenny dripped a few drops of solution from a pipette onto the dish as she responded, "is something wrong with your implants? You want to go back into the virtual rig or something?"
Horizon shook her head, "more drytech than wetware I'm afraid." She pulled the orb out of her pocket and showed it to the squirrel. "Do you know anyone who could decrypt whatever's stored on this?"
Jenny set her tools onto a rack and stared intently at the mysterious sphere. Before she could say anything, Sam whispered in Horizon's ear, "are you sure you trust her with this?"
I won't tell her it's a black hole unless absolutely necessary, the raccoon retorted silently. And remember that if MechRat gave it to us that means the “tell no one” instruction was not an order.
"Is that FedTech?" Jenny's question brought Horizon's attention back to the present.
Horizon gave a small shrug. "I picked it up back on the Resolution, so it probably is, but I'm mostly interested in the data that's on it. Sam said she didn't have the processing power to decode it in any reasonable amount of time, so she recommended I find some kind of supercomputer to take care of it."
"Well," Jenny considered with a glance over her shoulder towards the processor tower on her desk. "I wouldn't call it a 'supercomputer' per se, but I do have a decently-powered machine here."
"That's nice," Sam popped into existence standing behind the tower. "Based on what I can see here, this thing could crack the encryption in just over half a century."
"Fifty years?" Jenny gasped in shock. "What, is this thing quantum encrypted or something?"
"No," Sam retorted. "If it was quantum encrypted your machine here would have no chance. As is, the coder probably used the Resolution's quantum computers to develop the encryption but I can't pick up any uncertainty principles at work here, fortunately."
Jenny scratched her chin as she thought, "so, if we had a quantum computer..."
Sam looked up at the squirrel with interest. "Are there any quantum computers on this moon?"
"It's not really something they advertise, but the Company uses them to run the credit network." Jenny pulled a paychip out of her pocket and held it up, showing the AI panda through Horizon's eyes the small LCD screen displaying the amount of Surtr Company Scrip stored on the chip under the Company logo. "About seven years ago some guys managed to steal a few quantum cores from the treasury division. They were planning to use the codes on them to rob the Company blind but instead the Company just put out a new scrip and forced us to trade in our old sacs for new ones. At a terrible exchange rate I might add."
Sam looked very interested now. "So what did they end up doing with the stolen cores?"
Jenny shrugged, "sometimes somebody suggests they have one of them. Occasionally there's a rumor that one was used in a major cybercrime. But, nobody can say for sure."
"Would you, by any chance, know where to find one of these people?" Sam blinked out of existence and rematerialized right in the squirrel's face. "I can't imagine that those biomods of yours came from a licensed clinic."
Jenny staggered back, bumping into the desk behind her. "I might know a few people in the black market," she claimed. "But I'm not really a computers person, I'm more into wetware."
Sam leaned over Jenny's protruding stomach to stick her nose right up into Jenny's. "Still, could you check? Pretty please?"
"Sam, give her some space," at Horizon's command the AI turned to glare at the raccoon for a moment. Then she blinked out and reappeared sitting in a cross-legged position on one of the desks at the far side of the room.
"I'm going to need that table in about half an hour," Jenny complained, pointing at a tray of plates under the illusion's legs, one tube sticking out of her immaterial thigh. "I might know someone who might have a lead, but I can't guarantee that anything they'd sell you would be genuine." She picked up her pipette again and started dripping on plates again, then her eye twitched. "Hold on," she said, "that Shawn guy you rescued yesterday. He mentioned he was a computers guy."
"Hmm?" Horizon inquired.
Sam waved a hand and a document appeared in the air next to it, showing the image of the vole Horizon had saved next to a list of qualifications and work history. Horizon focused on the document and it zoomed through the air and came to a stop in front of her face. "An IT journeyman?" she read.
"It says he just barely passed the exams, but the notes from his mentors suggest discipline issues," Sam explained. "He might actually be helpful."
“So,” Horizon considered. “You’re suggesting we obtain a stolen quantum computer from some shady guy in the Surtr underworld, and bring a kid who might have the Company out looking for his head after framing him for arson?”
“Pretty much,” Sam commented with a smirk.
1 note
·
View note
Text
The Infiltration: Part Two of Three
In the ten years he had been a vigilante, Peter Parker had become very good at sneaking into places he shouldn't have been.
Air vents were useless. The vast majority of them were far too narrow for anybody to slip through without becoming amorphous, and even when the ducts were large enough it was impossible to move inside one without making enough noise to alert the entire block. The subceiling--the space above the ceiling tiles, but below the actual architectural structure--was a far better bet, but that was similarly cramped--and besides, only some buildings had gaps in the walls to allow for movement like that.
Using a disguise to sneak in was better all around, but it required a lot of skill and care. You couldn't disguise yourself as a scientist unless you were genuinely an expert in the field you were pretending to study. Nor, in this particular case, could you just dress up as any old agent--they had security levels. Executives were out, reporters were only viable if the people you were trying to fool had reason to believe a reporter was going to be there, and the less said about solicitors the better. The key was to attract as little scrutiny as possible, to not raise any questions you'd have trouble answering; because the second someone grew suspicious of you, your cover was all but blown.
Janitors, then, were perfect.
Nobody pays attention to a janitor. It's practically one of the perks of the job. Beneath notice means beneath scrutiny, and people only give custodians the slightest thought when a place needs cleaned. Even then it's just an assertion that a custodian needs to be there. Nobody questions what a janitor is doing in a room, even in the dead of night. Nobody questions why a janitor is wearing gloves, or where they got their ring of keys. There's no better disguise for going somewhere that people generally can't go.
Peter had been pretending to be a janitor in the main headquarters of the Cape Code Authority for several days now. He had listened intently as he'd mopped the floors, mapped out the layout in his head, figured out where the labs were and who had access to what while keeping his head down. He'd owned this coverall for years now, for infiltrations exactly like this, and now with the security cameras disabled he hooked his cart on the handle of his mop and dragged it towards the door the three agents had just left.
The door had locked automatically. Of course it had, all laboratory doors locked automatically around here, and even the custodians needed special permissions to get them unlocked. But as the door had swung closed, Peter had pressed the trigger in his palm under the guise of adjusting his grip on his mop, and now the door's latch was glued down beneath a small splatter of webbing. Pulling on a latex glove, Peter tugged the door open a crack and slipped into the lab.
He adjusted his hat as he glanced around the lab, the hat that had blond curls sewn to the inside to disguise his brown hair, and scratched at his false nose. The hologram table sat in the center of the room, still softly glowing even after its deactivation--an enormous waste of energy, but apparently nobody cared. Ignoring it entirely, Peter headed straight for the computer monitors against the far wall, grabbing a chair without breaking stride and only stopping to climb on top of it and crouch on the seat like a gargoyle on a rooftop.
Like everything Reed Richards ever touched, the computers were encrypted. But Peter had dated Johnny Storm for five months once, and he didn't spend so much time nearby his fellow supergenius without taking some time to figure out how to bypass their usual security. It took him just over five minutes to get through the firewalls, and then he stuck a translucent plastic sticky note to the screen and began to browse.
The sticky note was, of course, a data drive. Peter had learned about these only recently, but he was fast growing to like them; they were easy to conceal on his person and, unlike a USB stick, didn't require a specific size of port. As he opened up the computer's files, the drive pinged off of the computer's software and integrated itself into the system without leaving a trace. Cracking his knuckles, Peter typed a few cursory searches into the file browser and tapped Enter.
Perpetual Holographic Avatar/Nano-Tech Offensive Monsters had been a thorn in his side for over two years now. They didn't move like humans; their range of motion didn't have the limits that their skeletal shape implied; their systems adapted and learned and coordinated in ways that he'd never seen before in artificial intelligence. Even Octavius, permanently on the cutting edge of AI and biorobotics development, wasn't sure what the hell was going on with them. Last year, in the middle of beating the multi-armed megalomaniac's face in, Spider-Man had asked for Otto's thoughts on the Phantoms; the technology, both of them suspected, wasn't exactly beyond Otto's work so much as to the side of it. The systems were hyperspecialized: they had no connection to neural networks of old, and were practically useless for advancing them in the future. They were, in a word, alien.
Peter suspected Chitauri tech. The War of the Worlds had left countless remnants of the Chitauri on Earth; some of them still remained, like the Leviathan rotting in Maine, but far too many of them had seemed to simply vanish. Anyone who gave it more than ten seconds of thought could realize that governments of the world had squirreled the stuff away to study and reverse-engineer. Now, as Peter's eyes darted back and forth across the screen, he skimmed through the blueprints and models that he found in the folder and tried to see if any of it matched the distinctive look of the Chitauri.
Some of it did, he found as he kept searching, but not a huge amount. Reed had done some work with Chitauri tech in the past; traces of its influence were obvious in the composition of the Phantoms' gun barrels, and in the way their hard-light armor projected itself over the skeleton. Kid stuff, nothing that explained the problems he'd had with them. Peter's brow furrowed as he copied the files he found to his data drive and peered over his shoulder at the hologram table behind him.
What had Reed been saying to Flint in here only a few minutes ago? Peter had a spiderlike hypersensitivity to vibration; he could feel footsteps on the other side of the building rumbling through the floor, and the variations in air pressure caused by the fly drifting around the ceiling. But it didn't work like hearing did, nor was it interpreted by the same part of the brain. Though he had felt Reed talking in here, it just felt like a continuous drone of vibration against his skin--he hadn't heard him, and so couldn't interpret the words. And, like an idiot, he hadn't thought to bug the room beforehand.
He pushed his tongue against his upper lip in thought. Had it had something to do with why Flint had registered with the CCA in the first place?
Kicking a foot against the bottom of the desk, Peter rolled his chair over to the hologram table and set to work getting past the security there too. This took even less time than it had with the computer, now that Peter knew how Reed had updated his security measures over the last few years. Within three minutes of typing so fast an observer would have seen his fingers as blurs he was browsing through the most recently accessed files.
The image lifted out of the table and filled the room with its soft light, and Peter frowned at the image of the Phantom he saw. How on earth was this related to Flint's desire to Be A Real Boy? He typed a few commands into the table and watched the Phantom's white shell disappear to reveal the mechanical skeleton beneath. A few notes by Reed appeared to highlight key points, and Peter read through each with steadily rising concern.
Very little of the Sandman's mass was actually Flint Marko. When he had been disintegrated all those years ago, most of his body had become just plain old sand--only his nervous system had become anything different. Over the years, he had gained entire truckloads worth of sand and lost enough to fill beaches, but the gallon or so of milky white silica that had once been his brain and nerve cells had remained, scattered evenly through every shape and sculpture he made himself into. They assimilated granules of a similar composition through static cling, arranging them with an intricate electric charge that neither Flint nor Peter had ever fully understood, and now it looked like Reed wanted to apply that same static charge to the Phantom project.
Looking through the notes, Peter could already see that Reed wasn't putting much effort into following through on his promise. The conjectures and theories put forth in them were ludicrous--ideas that Peter had discarded years ago in his various scrambles to stop one of Marko's rampages. But he read between the lines, read ideas that Reed had intended for his own eyes only, and his blood grew steadily colder in his veins.
It wouldn't take much modification to turn a Phantom into a suitable chassis for Flint's nerve granules, so went Reed's idea. The skeleton already contained organic elements, and they already received commands from a biological source rather than a computer. This flew in the face of Peter's assumptions about the Phantoms.
They were only partially robots. They were like Octobots; their processing units were very much alive.
Peter waved a shaky hand over the table. The hologram deactivated, which wasn't his intent at all, but he was too taken aback to care.
Deep in the bowels of the building, ignored by Peter until now but always scratching at the back of his mind, the vibrations of mechanical footsteps rumbled through the walls and floor. The central hub of manufacturing and deploying Phantoms was located fifty feet under the foundation--a fact he'd known all along, but which he had to investigate now. Now, when he knew that within those robotic skeletons were living and thinking beings. Now, when he knew that the drills whirring and 3D printing that he felt even from here were working tirelessly to imprison and enslave something. Jumping off the chair, he retrieved his data drive from the computer and took barely a minute to wipe all evidence of his presence from the room. Then, readjusting his disguise and checking for the presence of witnesses, he slipped out of the room and finally allowed the door to lock.
The route to the underground hub was a circuitous one. As the operations were almost entirely automated, not even the janitors were given clearance to enter that level; maybe four people had access, and Peter wasn't one of them. No matter. There were more ways to sneak around than just throwing on a coverall and mopping a floor. If Peter's disguise only took him this far and no farther, it was time to drop it. Some places you could only reach as the wall-crawler.
Had the security cameras not mysteriously lost power earlier that afternoon, they would've seen a janitor shedding his hat, kicking off his shoes, and beginning to unbutton his coverall. Without breaking stride, he snatched a small bag from where he'd hidden it in his cart before and pulled on a mask; whatever features, real or fake, a witness might have noticed, they were now hidden by dark red fabric and two gleaming grey bug eyes. In short order the coverall and hat were gone--wrapped up into a web-knapsack that he slung onto his back even as he swapped his shoes out for red spandex boots. Pulling on his gloves right as he reached the elevator, Spider-Man stopped to politely tap the call button beside the sliding metal doors.
With a ding, the elevator doors slid open, and Spider-Man immediately smashed straight through the emergency hatch at the top of the lift.
Elevator shafts were always a bit more complicated than one expected. Even Peter, who could feel the constant motion of the metal boxes through the building and their cables sliding against pullies, always needed a moment to figure out how to squeeze through the systems that controlled its rise and fall. He paused as he examined the mechanism of this particular elevator before he sucked in his stomach and crawled around the box with a few inches to spare. Then, once he was beneath it, he released his grip on the elevator shaft and let himself fall.
He caught himself fifty feet later, his fingertips sticking instantly to the concrete as he touched it. Just across the shaft from him was a set of elevator doors, which he hopped onto and began to pry apart. It was slow going. Like everything in the CCA headquarters, these doors were made with superhumans in mind, and they had a magnetic lock that Spider-Man found himself straining to overpower. He pulled on them for a few seconds, changed his mind, and crawled two feet to the left to begin messing with the wiring that controlled the lock. There was a moment of silence, a low, hollow ding, and the doors slid open.
With one hand still stuck to the wall Spider-Man lowered himself into the unlit chamber, dropping to the floor and landing there in a crouch. What little light had made it down with him reflected off his mask's glaring eyes. For a moment he was still, one hand pressed to the metal beneath him and his attention fully on the vibrations of the environment. Then, mentally sorting through the sea of threats that his spider-sense whispered and squirmed at, he rose to his feet and nonchalantly slapped the lightswitch on the wall behind him. Sparse florescent lights flickered on above him, and he blinked and furrowed his brow as he adjusted.
Now that he was down here the vibrations were sharper, like a the world coming into focus as you come up from underwater. They travelled through the air, through the concrete, and through a metal catwalk that served as a floor, branching into pathways and situated above buzzing, whirring machinery. No wonder it had been so difficult to discern what was going on up above, Spider-Man reflected as he glanced over the guardrail and watched robotic limbs carry a Phantom chassis through a gap in the wall and to another room. He turned his attention ahead of him, where similar chasses were held in racks upon racks that spanned nearly wall to wall across the room, black robotic skeletons awaiting deployment.
But there was a difference between these Phantoms and the ones he so often encountered on the battlefield. Frowning under the mask, Spider-Man stepped forward, leaned over the catwalk's railing, and set a finger against the nearest collection of servos and solid-light projectors. Yes. There it was, the constant, ambient tremor of air in motion; the chasses were hollow like the frame of a bicycle. Whenever he'd fought them, they hadn't displayed any such emptiness.
Right. Mechanical systems supported by biological processing. He took his attention away from the chasses, looking instead at that hole in the wall that one of them had vanished into as he'd come in here. He could feel the Phantom in the next room over being hooked up to--to something, metal vibrating on contact with metal and stabilizing with a little pop. His eyes narrowed. His fingers twitching nervously, his breath held, he began to pace down the catwalk towards the door to that room.
A window on one side greeted him as he stepped through, displaying the Phantom under maintenance. Screens embedded into the window offered diagnostics and schematics, all of which Spider-Man ignored. He turned instead to the far wall, where what looked like a large cabinet was anchored in place and had a hundred or so pipes no wider than test tubes leading into and out of it. A quick ripping of metal, and he tossed a mangled padlock over his shoulder as he threw the cabinet doors open. The interior was poorly organized, and called to mind a prototype rather than anything intended for widespread implementation: a screen with a series of codes flashing across it, a mess of piping and tubing, and in carefully arranged racks hundreds upon hundreds of test tubes, most full of some amorphous fluid.
Spider-Man's brow furrowed as he selected a vial at random. Working carefully, he unscrewed the valve that connected it to the mess of piping and slid it out of the vial's stopper--without it, the test tube's lid sealed airtight again. He held it above eye level and turned to see the light filter through from overhead. The fluid inside surrounded what looked almost like a pipe cleaner, thousands of copper wires branching out from a central silicon rod. As he tilted it one way, an air bubble slid up the glass wall, and out of the corner of his eye he thought he saw--
--a tendril, as black as the rest of the liquid, squirming in that air pocket in a bid for freedom.
Spider-Man's eyes widened behind the mask. Oh my god.
Dead Leviathans and alien technology hadn't been the only things the Chitauri had brought to Earth. It had taken the terrestrial armies, and the remnants of SHIELD that Spider-Man had fought alongside, far too long to realize that the shape-shifting battlesuits that their enemies had used were themselves a separate species. Earth hadn't been the only planet to face invasion under the Chitauri; centuries ago, those invaders had conquered and enslaved a species called Klyntar. Amorphous, shapeshifting, symbiotic creatures, the Klyntar had the distinction of being able to use every single cell as musculature, digestive system, armoring, and neurons. Nobody was sure how long the Chitauri had been selectively breeding and brainwashing their symbiote slaves into battle armor, and until now Spider-Man had assumed that practice had stopped with the aliens' defeat.
The little vial of Klyntar sample in his hand was far from his first experience with the species. He had, for six months during and after the war, worn a stolen symbiote as a battlesuit of his own, and even after he and Vee had separated he'd been up close and personal with the species many, many times. But he had believed that Vee's defection from the Chitauri had been a fluke; that they had been the only Klyntar to be recovered from the Chitarui alive.
But now Spider-Man stood in the basement of the Cape Code Authority, holding a vial that contained another member of that species, and right next to him were over a hundred identical vials. All at once, the control systems of the Phantoms became obvious to him.
Without hesitation he turned back to the cabinet and began yanking the tubes out of their holders. The brush-like machinery in each vial, he figured as he worked, must have been some kind of brainwashing system; the copper wires made contact with as many of the Klyntar's neurons as possible, with controlled electric shocks frying out whatever thoughts the aliens tried to form and replacing them with--with whatever programming was necessary to get the Phantoms working. As he pulled each tube out, he killed the electrical charge, but for now he didn't release the Klyntar within from their cells. Where would they go down here? Did they even remember what they were? At best they'd die, at worst the CCA would collect them again and make it even harder to get to them again. No, for now he stuck the vials together with webbing, bundling them together in a padded sack of sorts--he could keep them safe until he knew what else to do, but for now--
--for now, he could feel footsteps vibrating through the concrete fifty feet above. Could feel the elevator starting to move, and the frantic tingling in his head suddenly concentrated all its alarm on the man upstairs. He paused, but only for the smallest fraction of a second; then he worked even faster, his hands becoming blurs again. Grab, break, thwip, grab, break, thwip. The bundle of vials and webbing in his arms was becoming untenably large. He kept at it anyway, always careful not to smash the vials, always careful to separate them from their neighbors with a carefully padded layer of webbing. Even as he webbed up the last one, he wove backpack straps onto the sack and pulled them onto his shoulders. Then he turned on his heel and darted out the door, ready to make an escape.
But as the elevator began its slow descent towards him, he paced around the room and realized that there was no escape to be found. No windows or doors, because he was in a basement, and the air ducts were of course far too small to crawl through. If he didn't have the Klyntar vials, he would've been able to crawl past the elevator, but with that bundle on his back there was no room. If he wanted to save these Klyntar, he was trapped down here with them.
Well, decided Spider-Man as his pacing came to a stop directly in front of the elevator. If he was about to be discovered down here, he certainly wasn't going to let whoever was about to discover him get a dramatic moment about it. There would be no voice booming out from behind him as he frantically looked for a hiding place, there would be no cat and mouse as the person looked for him in this increasingly exposed room. He folded his arms and leaned against the guardrail right in front of the elevator, glaring at the doors. Waiting.
When the doors dinged open, Scrier momentarily hesitated, not having expected to see Spider-Man so out in the open. He blinked behind those blank white eyes, far more awkward than a supervillain wanted to be, before he lamely managed, "I thought that was you, Spider-Man."
#Spider-Man#Spider-Man AU#Peter Parker#Specs#Earth-61610#Scrier#Marvel AU#spidersona#story#odyssey prelude
16 notes
·
View notes
Text
BFCD Story Concepts by Nesha
Story Concept 01: No Saviors in the Wild Pt. 5
Read Pt 1 | Pt 2 | Pt 3 | Pt 4
I Am Light by India.Arie plays in background, as it is Shani’s theme.
A Savior is Born: The Rise of the Rebels 02 - A Cage Big Enough for Hundreds
Shani knew what it meant whenever she was escorted back to the dormitories and her files were pulled up and changed. She knew what it meant for the administration to remove her arm cuff, explaining to her that the government had given her a full scholarship for the rest of her studies. When her record was expunged and she was allotted a grace days to recuperate and get back to her regularly scheduled classes with her tuition and lodging paid in full and no sign of the unjust sentence in her history, she knew.
They wanted her to shut up and move on. To just forget about not only what happened to her in the woods, but to the others. To Atlas. She tried to see if she could look him up whenever she got back to the library. The directory didn’t cover Wasteland citizens, so she had to give up after a few days.
Since she now had free time, not having to work for her education, she decided to get a part time job, for a life skills practice and a few non-academic pleasures that weren’t covered in the tuition + nutrition supply. She started a beret collection, and learning various hobbies as a distraction from thinking about the woods every time she wasn’t involved with a school project.
She bought every single type of M&M that she saw in the store, then grabbed jars to separate them - all plain reds in a big jar, smaller jars for other reds - peanut, almond, etc, and the biggest jar had all of the excess red M&Ms of all sorts put into it. Then... she had several bags of several M&Ms that weren’t red. Researching what to do with them, besides toss them, she found a few recipes for cookies and other treats. Maybe this was a nice time to learn how to bake!
She went knocking on doors of other dorms in her building and nearby buildings, "Hi, I brought you some M&Ms cookies." and they're like... You know what idec. Yes, thanks. Because, the dorms weren’t where the rich students lived. It got her a few suspicious folk, but mostly, people were grateful for something to eat that wasn’t a strict and cheap meal or an even cheaper and far less appealing meal paste. It was the first time that people seemed to begin liking her.
She thinks about getting a tattoo, but they're ridiculously unsafe and very expensive, so instead she gets a tattoo art piece, which is a realistic painting of your body part with a tattoo on it. It's relatively costly, but safe, and hers is an Atlas tattoo, holding the world on his shoulders, on her back, because Atlas had had her back.
She researches Atlas and then goes and finds Greek mythology books in the useless books depository, and takes on learning about it as a hobby. Greek mythology, baking, school, part time job doing data entry, and collecting berets. It kept her occupied, though her mind was frequently on what happened. Months had passed, years were beginning to. She thought for sure that one day, her pain had to be numbed and so she tried not to harp on it. But, how do you just forget somebody who was willing to throw away their life for yours?
18 marked the legal age of adulthood. Shani immediately had a job, right out of school as an interpreter and translator. She was hired at a firm that also allotted her to take more college level courses to advance herself in the field and she began saving up for a place in the city that wasn’t a job related lodging when she had the most important appointment set up for her that she would ever have.
“Hi. I’m Shani, I’ll be helping you today with your assessment. Have a seat.” The wasteland woman looked at the chair that Shani gestured to and smiled, her canines showing and the smile wider than Shani was comfortable with. “Ummm... Sit down?” The woman laughed and nodded.
“Have a seat. Sit down. Yes. Yes, that makes sense. It took me a moment. You might guess, the wasteland isn’t very prim and proper.”
Shani didn’t want to talk about the wasteland. Instead, she began typing into her computer, “So, Miss... Free... What is your first language?”
“I don’t believe that you have a word for it. I’ll call it wolfen. I doubt it is in your machine.”
Shani furrowed her eyebrows. “No. I’ve never heard of that before. Where did it originate? If you know...”
“Hmmm... The Epic of Gilgamesh, maybe.”
Shani frowned and clasped her hands over each other. “Ma’am. What is this meeting about?”
“I remember you, but you don’t remember me. It’s because you didn’t see me. You didn’t know to look for me. But, I knew to look for you. I’m here, because I have finally found you... Did you think it was right? For them to come in that way? They sent us food. We ate, then they attacked and took my people, took your people, took the wolf with the hair like flames...”
“What are you talking about?” Shani whispered.
“Your mate. He was torn open, then he tasted blood. He became as we are. Not fully, but enough. He became a man who is no longer a man, a man who is now a wolf.”
“Atlas.”
“They took my people. They took your people. You.. were special, somehow. You didn’t go where others went. Why were you special? Why were you spared?” Shani had never considered that she had been either of these things. She lamented over Atlas for so long, she figured that she, too, had been made to suffer. “They were taken to a cage. Some as beasts, some as feed. You were taken to a cottage, and given gifts. Are you a queen?”
“Far from it...” Shani tried to remember what happened in those moments. She vaguely recalled a voice saying, “She was falsely accused. She shouldn’t have been there in the first place, much less get taken to the Kennel. She’s got an arm cuff. She belongs to somebody.” The school. She had been property of the school. She still owed them money and had their equipment on her person, to indicate such...
Her schooling was paid off, not as a means to keep her quiet... but to keep the school quiet. To ensure that they got what she was worth and not ask questions about potential damages she faced while serving a bogus sentence. Sure, she made the most of that, but it had less to do with her and more to do with money.
“They... took them to a cage?”
“A cage big enough for hundreds.”
Tears poured from her eyes and Free took the initiative to offer the woman’s own tissues to her, as she must’ve forgotten that they were on her desk, in her... emotional release. Shani snatched two and tried to clean her face up. They took Atlas to a prison? “A prison! They... took Atlas to a prison?”
Whenever Free said this, her dark brown eyes glowed amber and at that moment, Shani knew. This... is a wolf. This woman is what she described. A person who is not a person, but a person who is a wolf. “They took everyone there. Everyone but us.”
NOTES: I enjoy the idea of Free being far removed enough from human society that she doesn’t know anything about mannerisms and only has a limited amount of English, that she’s picked up since she’s been scavenging through the wasteland, but that she’s smart (I’d say the smartest wolfen in the series), and she’s adaptable and quick. She’s like a wolfen counterpart to Shani, and that’s why they eventually get on so well. They’re in similar positions, but with vastly different backgrounds. @tiarathief (You are still the first name that comes up whenever I at somebody. Let me know if you don’t want to be tagged to these, please. @shslargue @jacksope-lives
#BFCD Story Concepts by Nesha#story concept#stories#original content#Shani Saviors#A Savior is Born: Rise of the Rebels#writing#Free Saviors#A Cage Big Enough for Hundreds#Story Concept 01: No Saviors in the Wild
20 notes
·
View notes
Text
✨ Internet Safety ✨
For our generation today, the internet is probably the safest place to be in. People can be whoever they want, express whatever they want, and enjoy themselves however they want. I must admit, I would also say that I couldn’t live without the internet. Internet is just the solution to every problem, right? Now, we can even earn money in the comfort of our rooms with the help of the internet. Should we spend hours travelling just to buy stuff? Nah, we got the internet! With just several clicks we can already make an order and just wait on our couch to receive it. Oh no, COVID-19 ruled the world! No worries, we are backed up by the internet. Online classes, online transactions, online dating. You name it. The internet is there for us, or is it? Is it our safe haven?
We have put so much trust in the internet, but we didn’t know it can also be our biggest predator. Online transactions were fun until you got scammed and lost all your money. Online dating them feel loved until the person they were talking to is a catfish. Streaming online made him famous and rich, until his account got hacked. And there are still millions of stories out there that should awake us from believing that the internet is the safest thing in the world.

Below are some possible dangers you could encounter online.
1. Cyberbullying
I’m sure many of you have heard of this. But even though we are fully aware of it, it is still one of the major problems until now. As we casually scroll in our social media feeds, it is already normal for us to see people making fun of or “bashing” other people. It became so prevalent that we could call it a normal thing. According to UNICEF (2019), one in three young people has said that they have been a victim of cyberbullying and that it affected almost half of the Filipino children aged 13-17. We need to know that even a single word like “tanga” or “bobo” we see in our social media platforms and online gaming worlds could affect or traumatize us greatly.

2. Data Being Stolen
Some people nowadays are getting better at doing this. They can steal your money from your accounts, apply for a loan or credit card using your name, or sell your information to an online criminal as well. The hidden website is packed with criminals who purchase and sell stolen personal data. If your data is stolen, you can experience spam attacks. But most of these data thefts try to steal sensitive information, such as your credit card or personal information to commit identity theft.

3. Exposure to Inappropriate Material
Another risk especially for children and teenagers are exposure to inappropriate materials that are sexual, hateful, or violent. The chance and probability for children to look at anything inappropriate rely on how much they do online as they get more active online at a younger age. Whether it's a free-time graphic pop-up commercial, children's cartoon characters in adult circumstances or a self-harm forum, an innocent search might expose these children to contents that make them feel puzzled and angry. Some of the inappropriate content includes pornographic material, content containing swearing, sites that encourage racism, violence, terrorism, or even suicide, sexism sites, or gambling sites, and so on.

Based on my own experiences, here are some tips I would like to share to you to look after your privacy and secure your internet safety:
1. Keep your software up-to-date
Not only will you get a better program experience, but you will also be able to iron out your security issues. But the reason why you must keep it updated is that hackers are fast enough to become aware of certain software’s vulnerabilities, thus could harm your computer system and personal data. If you avoid doing these updates, you are bound to face persistent bugs, data loss, malware infection, and of course security issues.
2. Update your passwords
Why do we need to constantly change our passwords? So that we can reduce the risk of other people having access to our accounts, thus corrupt our personal data. Using strong passwords is necessary for us to prove our identity in our accounts, websites, or our computer itself (Wright, 2021). My tip in creating passwords is random characters with a symbol, number, and at least one capital letter. The reason for this is that using weak passwords, such as patterns of letters and numbers, or simply your name and some important date you know can cause hackers to guess and open your account, hence impersonate you to commit fraud and other crimes.
3. Use two-factor authorization
Familiar with this term? Yes, a two-factor authorization (2FA) is an extra step to keep your accounts more secure and avoid getting hacked by others. One of the most common 2FA methods is one-time codes sent through SMS or email, authenticator apps such as Google Authenticator, and security keys such as U2F tokens (Drozhzhin, 2018). This one for me is the best 2FA authorization because only your private key will confirm your login. If someone will try to log in to your account with the wrong security key, they will not be granted access to your account. So, there you go. A series of two-factor authorizations that will secure your accounts the best way possible. You’re welcome!
4. Be careful what you click on
Have you heard of phishers? They are attackers that send a fraudulent message designed to trick and victimize us into revealing sensitive information to them. As scary as it sounds, we need to be aware of what we click on to avoid experiencing this. Phishing is usually done in an email when they get your email address from somewhere. These phishers try to create a fake website to trick you into typing in your personal information. It’s much easier for them to hack our accounts this way. To avoid this, you can check the URL’s legitimacy by using the Google Transparency Report or simply avoid suspicious emails which require your personal information. Think before you click!
5. Back-up your data
Data back-up and recovery has many advantages. Some of these are protecting and saving your data, provides ease of management, ensures accurate information of your data, quick access to data, scalability, and such (Becker, 2021). There are many other ways to back up your data, but here’s a simple way to manually back up your data in your phone is to open your phone’s settings app, tap system and click backup or search backup in your settings app, then tap back-up now. It’s that simple.
6. Set up notifications for your most important bank accounts
As online bank account holders, it is our responsibility to making sure our accounts are protected. Online accounts are one of the easy targets of hackers to whisk away our money with just a couple of keystrokes. To safeguard our online banking, we may choose an industrial-standard security bank or credit union that utilizes text or e-mail warnings avoids the use of public Wi-Fi access and periodically changes your password.
7. Protect your personal information
This might be difficult for those who like to express themselves on social media, but we must protect our personal identity to avoid any sort of online threats. To protect our identity, we must limit the amount of personal information we share or provide. We shouldn't share or provide this information online: exact home address, your place and schedules of classes or work, birthday, cellphone number, and most importantly our passwords or account information. Another tip is to write down in a small notebook all your passwords and keep them safe in a secure place away from your computer.

8. Use parental controls and stay present
With the pandemic going on right now, parents should be extra careful of what their children see and hear about themselves and who they encounter on the internet. To protect your children from internet risks, talk to them frequently, utilize tools to safeguard them and watch out for their work. Monitor the time of your child, especially the younger ones, about when and how long they stay online. Keep your computer at a central location in your house, where it's easy to watch what your children do and look at online. You may configure them for mobile devices to forget Wi-Fi passcodes for your kids not to go online without knowledge. Review privacy and location settings, parental control and use secure browsers, apps, search engines and YouTube search settings. Lastly, limit camera and video to prevent your children from accidentally taking photos or videos of themselves or others.

The internet does not usually hurt us unless we react to suspect material and websites. The first reason you don't know what you're doing is because of internet damage. Secondly, you may react or click on links such as appealing advertisements, infected software and communications when you have other forces. To ensure internet safety, just remember those tips above and these three things: secure your network, be responsible, and make the internet child-safe.
References:
Becker, D. (2021). 6 Advantages of Data Backup and Recovery. IT Central Station. Retrieved from https://www.itcentralstation.com/articles/6-advantages-of-data-backup-and-recovery
Drozhzhin, A. (2018). SMS-based two-factor authentication is not safe — consider these alternative 2FA methods instead. Kaspersky Daily. Retrieved from https://www.kaspersky.com/blog/2fa-practical-guide/24219/
Wright, J. (2021). Why Is it Important to Change Your Password? Small Business Chron. Retrieved from https://smallbusiness.chron.com/
Online bullying remains prevalent in the Philippines, other countries (2019). Unicef Philippines. Retrieved from https://www.unicef.org/philippines/press-releases/online-bullying-remains-prevalent-philippines-other-countries
25 Best Internet Safety Tips for Every Situation (2021). The Neeva Team. Retrieved from https://neeva.com/learn/25-best-internet-safety-tips-for-every-situation
3 notes
·
View notes
Text
MODERN FIXATION

If you’re reading this, it’s too late. Your device has already taken you. It’s going to be up to you now how easy or hard it will be for you to fight the urge to stay on it. One thing is for sure, technology is inevitable. From the very moment you tried reading this, you were already enjoying the benefits of technology. You used technology to do something that you wanted. Besides, you wouldn’t even be reading this without technology. Everywhere you go, whatever you do, there is technology. Technology has already become an essential part of our everyday lives and whether you like it or not, social media is a huge part of it.
Now, social media is vitally useful in various ways. In fact, this is what helps us survive nowadays. Looking for jobs, finding solutions, deciding on what to eat, searching for a place to live, and most especially, getting connected with the people we know. Social media satisfies the needs of humans of having the desire of being part of something big. As a result of this, social media specifically produces identity that is akin to mob mentality allowing humans to be hyper-connected and unable to spend their time with real family and friends. (Koo, 2015).
For students like me, social media is a must. There is no way you can efficiently accomplish a group task without using social media. Students of today were raised in an increasingly media-rich environment. (Perse & Lambe, 2017). It is inevitable for them to use any form of media for communication, connection, research, and many more. However, this could lead students to the overuse of media for it will inevitably be part of their everyday needs. Social media users specifically Facebook users tend to admit their excessive normal, usual, or planned amounts of time online. (Koo, 2015) Certainly, social media users like me are unable to take control of their online activity; hence, leading them to have negative academic, professional, and social consequences.

Since technology plays an important role to me as a student, and to me as an individual, it is without a doubt that I need it every single day. With this, I can pretty much relate myself to the portrayals of young people using social media in the documentary The Social Dilemma. Even if it is not for the purpose of education, I still spend most of my time on my phone, if not, have my phone by my side, at all times of the day. This is because certain gadgets nowadays are most effectively and conveniently used for entertainment, communication, security, and most especially, for an emergency. Despite this, I grew up and was raised with the discipline to put limitations in everything. It has been part of the house rules that when we eat or when we spend time with family, we do not use our phones unless it is of great urgency and importance.
The documentary The Social Dilemma reveals an essential portion of what you need to know inside the digital space. You may not have known yet but technology is getting way bigger and more advanced than you could have ever imagined. Everything you see on social media, what you’re seeing now, what you’re reading, what you’re looking at – all these are just tiny fragments of what the internet actually is. The Social Dilemma presents you with the adverse effects of technology and how it can actually be used as a system of manipulation that leads people into believing something that is not true. Because of the freedom that we can access in social media, businesses and politicians tend to overexploit the platform which, in effect, they use to create false publicities and deceptive propaganda that results in an overall sense of illusion for the vulnerable users of social media. After all, social media itself is a form of business.
With the power of technology, I believe businessmen and politicians will continue to use it in the same way they are using it now. This is because technology has no limitations. As businesses, social media platforms earn through the running of advertisements. The only way they can grow their business further is to improve their method of revenue which is what they are doing now: use of cookies and personalization of advertisements. Anyhow, businesses need people and people need businesses. What makes the market mutually efficient for both parties is through the use of social media. As was mentioned in the documentary, people are the products of social media and that is how it really works. The time you spend on social media. which is the time you spend for your personal benefit, equates to earnings for the platform. Businesses will continue to advertise, whether it is for manipulation or promotion, because from the very nature of it that is how it works; this is explained by a common economic principle that nothing really is for free.

As for politicians, the spread of fake news and cyber propaganda is prevalent. However, I believe that it will not be as prevalent as what it is now in the future. This is because social media nowadays, especially Facebook, have developed a capability to detect news or articles that portray false news, misinformation, and any suspicious posts and activities. Facebook created Temporal Interaction EmbeddingS research (TIES) as an effort to improve its detection of fake accounts and misinformation and the enforcement regulations. This has enabled the company to eliminate more than 135 million fake accounts in April 2020. This may not have completely removed all existing fake news due to diverse engagement, but this serves as a stepping stone for Facebook and other social media platforms to build a system of rectification on the issue of information fallacies across the internet (Hutchinson, 2020). Therefore, yes, the politicians will still try to take advantage of technology in the future because they have the freedom to do so, but the movement has already begun for it to battle upon in this respect.

In the end, it may be beneficial for us to use technologies in our everyday lives but it is still part of our responsibilities to put certain limitations to it. Additionally, it is part of our due diligence to verify the information we encounter in the digital space. When you buy a certain product in the mall, you check whether it is fake or original before purchasing. This goes the same when you encounter articles, news, or any information on social media. You always have to verify the information before buying into it. This action must always be kept in mind when you browse the internet. Failure to do so can lead to detrimental repercussions that influence you and your decisions on life matters. Businesses and politicians will always try to play tricks on us but the only way we can push back against unethical practices of using social media is through our actions ourselves. Engaging our critical thinking skills and educating people about social media literacy are our best tools to defend ourselves from modern harm.
There are certain lines from the film that give a powerful impact. One of these lines is “If you’re not paying for the product, then you’re the product.” This statement is indeed agreeable. Like I said in the previous paragraphs, nothing is for free. Everything has an opportunity cost and trade-off which is an economic principle. Even when you say you have free lunch available at the canteen, falling in line to get it is the cost of it. This is why if you are not paying for a product, then you should already expect that something from you is taken in exchange. Another line from the film states that “There are only two industries that call their customers 'users': illegal drugs and software." To me, this can be associated with the same effect that comes with both industries: addiction. Both drugs and software impart chemicals that trigger the release of dopamine or our happy hormones from our brain. When we use drugs, our neurotransmitters from our brains detect a sense of pleasurable experience in which it changes the behavior of our brain in a way it increases the odds of us repeating the activity again and again; thus, it goes the same with our usage of the software.
There is another line from the film that I find to be agreeing with. It was the line that says “Social media is a marketplace that trades exclusively in human futures." This is evident from the many circumstances the film presented. The one reason why social media knows exactly how to keep you engaged on the platform is that they analyze your behavior pattern. And when they know the kind of behavior you have; they move on to advance their trading scheme. They sell your personal data and give them to large companies which is why there exist personalized advertisements as you scroll through your media feed. The last line from the film that hooked me is the statement: "The very meaning of culture is manipulation." Since our culture is filled with social media and the internet, it can be deduced that everything can now be tracked and monitored. People can now easily manipulate you into liking something or into having different sets of views, may this be in business or politics. As long as social media exist, so does manipulation. Our culture has become associated with the use of technology. It now depends on how we perceive information online that guides our beliefs and that what makes us who we are.
Personal SWOT Analysis Worksheet
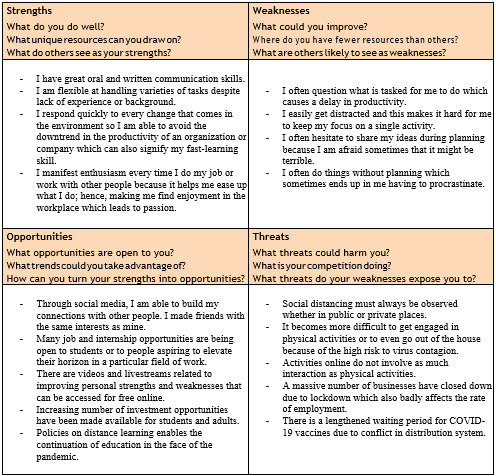
Illustrated above is my personal SWOT Analysis. I would say that the political, economic, and social factors are crucial to my growth. Because of these factors, I can determine steps that I can take to maintain my sanity and to improve on what I am lacking. The technological factors play a significant influence on the political, economic, and social factors found in both of my opportunities and strengths. This is because technology boosts everything around you, most especially in a time of a pandemic. Although I cannot go out because of COVID-19, technology allows me to stay connected with my friends and keep myself updated with the nation’s news. Because of technology, distance learning has been integrated into educational institutions to continue the delivery of education to all students like me. However, technology also contributes to factors under threats. Technological factors reduce personal interaction and increase the odds of people getting influenced by fake news considering that people, nowadays, turn to social media to obtain news.
With all the aforementioned circumstances, I would say that there are similarities and differences between my personal assessment and what the documentary, The Social Dilemma, says about the influence of technology on our lives. In a similar aspect, both my assessment and the documentary have presented significant improvements in daily lives with technology such as communication, research, broadcasting, data exploration, labor, and many more especially in a time of difficulty. On the contrary, both my assessment and the documentary presented adverse effects of technology specifically on our mental health and decision-making. This just goes to prove that technology is not always what it seems.

References:
Hutchinson, A. (2020, August 26). Facebook Outlines New System for Detecting Fake Accounts and Misinformation Based on Interactions. https://www.socialmediatoday.com/news/facebook-outlines-new-system-for-detecting-fake-accounts-and-misinformation/584228/.
Perse, E. M., & Lambe, J. (2017). Media effects and society. London: Routledge.
Koo, G. S. (2015). Lights and Shadows of Digital Technologies. Makati City: Church Strengthening Ministry, Inc.
2 notes
·
View notes
Text
234. Sonic the Hedgehog #166

DON'T. PANIC. I know. It's back. Don't worry too much though - it only lasts for two issues, so even if you detest this AU with all your heart and soul you only have to deal with it for a couple days. To be perfectly honest, I don't actually find the plot of this installment of Mobius 25 Years Later to be that much more interesting than the previous one. I find everyone to be a little too out of character, for one thing. However, it does at the very least provide a bit of closure to a story that was left wiiide open previously, so there's that.
Mobius 25 Years Later (Part One): Tempus Fugit
Writer: Ian Flynn Pencils: Tracy Yardley Colors: Jason Jensen
Last time on Mobius 25 Years Later, we left off with the timeline seeming to dissolve and rip itself apart while Sonic went back in time to fix the temporal and spatial instabilities of Mobius. Well, he fixed the threat of time coming to an end all right, but in the process somehow caused the timeline to skew wildly from how it was previously. In this new future, Shadow is a brutal and ruthless dictator, worship of Maria as an angelic guardian figure is officially sanctioned by his government, the Chaotix patrol the streets headed by King Shadow's chief enforcer Knuckles, and perhaps most bizarrely of all, Sally is married to Shadow as his queen. I have to note here that no explanation is given at all for how the timeline could have gotten messed up so badly - like, it doesn't really say anything about Sonic destabilizing specific events in the past, he just did something apparently, and stuff got messed up as a result. I'm personally not a fan at all of the idea of Shadow becoming so brutal like this, because it's just so out of character for who he's shown to become in the games (and in the comics coming up in a few issues), but at the very least there's the potential excuse of oh, well, this is a timeline where he didn't discover his true purpose in life and thus got led astray by darker influences or whatever. Regardless, things are very bad, and now Tails is on the scene, trying to figure out a way to fix it.
You see, he actually is able to remember the old timeline due to some kind of protective armband, and knows that this one isn't right. So he decides to go about recruiting some of his old allies to fix things, first starting with Knuckles. He walks in as Knuckles is instructing Lara-Su in her Guardian abilities, and Knuckles, once he realizes why Tails is here, ushers his daughter out grimly so they can talk alone. Tails tries to get Knuckles to listen to him, explaining that he took measures to protect himself, his wife Mina (remember? They got married in this timeline) and their kids from the time shift, and that he knows that everyone who was near the time machine when it freaked out still has memories of the other timeline. This merely pisses Knuckles off for some reason, and he yells at Tails to get out before he arrests him. Tails leaves the room dejectedly, but Lara-Su cheekily tries to cheer him up outside the door, clearly having overheard everything.

I already like this version of Lara-Su way better than the old one. The old one was weirdly whiny and selfish, while this one is immediately more assertive and ready to jump into action. As this is going on, we move to the dungeons beneath "Castle Mobius," where King Shadow is currently carrying out a rather… rough interrogation of Rotor, who's chained up to a wall. Shadow curtly acknowledges Rotor's strength of will in not "cracking" yet (it's not explained what information exactly he's trying to get out of him, but we can assume it relates to the timeline shift), and tells him he knows he will break eventually and leaves - and who is outside the cell to greet him but Lien-Da? She's apparently the one who captured Rotor for him, and she too remembers the old timeline, thanks to Cobar - we finally find out what she did when she confronted Rotor and Cobar back then!

Yeah, really don't like this version of Shadow. The juxtaposition of worshipping Maria as a gentle protective goddess, and Shadow's use of brutal torture tactics and authoritarianism is kind of… bizarre. A Legion mook runs up with information that Lara-Su has joined up with Tails, and Shadow orders Lien-Da to contact Knuckles to conduct an arrest of the two. Meanwhile, the two in question have managed to find Sonic, bedraggled and sitting next to a bunch of trash in a back alley, looking pretty awful. He, of course, is the same Sonic from the old timeline who went back to "fix" everything, and is horrified at how everything has turned out in this version of the future. It's once again worth noting that he sheds a few tears here, especially because this is around the time Sega started interfering more in the comics to make sure things were portrayed to their liking. There's a sketch version of the below page floating around somewhere showing Sonic crying substantially more than he is in the final product, which honestly, I don't know why Sega felt they had to force the artists to tone it back here, because I think if there's any circumstance where a normally cheerful and stoic person might truly lose it, it's losing their two children forever to the abyss of time.

Lara-Su urges the others to get up so they can go defeat King Shadow and save the day, but a sudden blinding light engulfs them. Sure enough, it's Knuckles, backed by what looks like half of Portal's police force, telling the three of them to surrender immediately as they're under arrest for treason…
The Chaotix Connection
Writer: R. Chacon and Ian Flynn Pencils: J. Axer Colors: Jason Jensen
This story is a bit bizarre - for one, it opens with a shot of Knuckles tied up and apparently coming to after being knocked out, only to immediately pull back a full day to show us what led up to this moment. That's a perfectly legitimate storytelling tactic, but it has to be done right for it to work, dammit, and the execution here is mostly just awkward and confusing. And for another, though someone is listed as the letterer for this story, very little of it is actually hand-lettered - the vast majority of it is machine-lettered. Seriously, out of the dozens and dozens of speech bubbles in this one story, which takes up half the issue's page span, only seven are hand-lettered (yes, I counted). I'm really not sure why this would be, nor why they bothered actually having someone letter only seven speech bubbles in the entire story when a computer was apparently doing that job perfectly well, but oh well. Anyway, here's the rundown - yesterday in Station Square, Rouge (sporting her Heroes getup) was snooping around for any juicy information when she got her hands on a nice little tidbit - namely, that Renfield T. Rodent is back. Remember him?

Aw, it's nice to see Sally and Sonic actually joking around with and teasing each other a bit. Things have been so frosty between them for so long, I forgot how nice it is to just see them being sweet and silly. The next day, Renfield's foreman oversees a delivery of slot machines to the new casino while Renfield himself watches from behind a screen, still sporting his capitalist tycoon grin and definitely seeming very shady as he talks to himself about putting on a grand show with this new scheme. The Chaotix and Rouge all arrive at the venue, and Rouge and Julie-Su nearly come to blows when Rouge insinuates that her only reason for coming is to show Knuckles that she's "gone legit." Knuckles breaks up the fight before it begins, and the group is let in early when they bluff to the guards that Renfield is expecting a meeting with them. They agree to split up and search for anything suspicious, checking in every few minutes to make sure none of them goes missing. Knuckles heads off on his own, and soon discovers an elevator that takes him to a secure room where the foreman is discussing the shipment with the help. When he hears Eggman's name mentioned, Knuckles knows this operation is rigged, so he leaps into action and begins to fight everyone present… alone. Seriously, man, couldn't have waited one whole minute to call in your backup? Speaking of the backup, Mighty in particular has decided it's prudent to check the food given what happened last time, while several of the others go for the slot machines as customers begin to file in.

Gotta love Mighty - no time to test anything scientifically, let's just shove potentially poisoned food into our mouths and see if we pass out! Knuckles, upstairs, finishes punching out the mooks and goes for the foreman, but when his fist makes a clanging noise against his nose he realizes that he's one of Eggman's auto-automatons. Things only get worse when said auto-automaton punches back, knocking him clean out. While the foreman ties him up and calls Renfield, Rouge, Vector, and Espio all check the slots, noticing that people seem to be acting weird while playing them. Sure enough, one glance at a screen later, the three of them are hypnotized as well. Knuckles wakes up with Renfield gloating over him, and naturally the rat immediately launches into a villainous monologue about how Eggman is paying him to use his fake slot machines to scan the brains of the patrons, allowing him to turn that data into a blueprint for what basically amounts to a Terminator. In fact, the whole casino is built on top of a factory that will start spitting out robots the moment the scans upload! Suddenly, the writers realize in horror that they only have two more pages to wrap this plot up, and so they go into overdrive figuring out a way to solve it in this limited amount of space.

I love the idea that Mighty just casually crunched up a whole factory and carried it around with him just to prove a point here. The police show up out of nowhere to arrest a fuming Renfield, and Julie-Su and Mighty explain that they knew something was wrong when Knuckles didn't check in, and even more hilariously, apparently on their way up here they just randomly passed the factory and Mighty was like "Yo, that doesn't fit the décor," hence him crunching it up. The president pops in out of the ether to congratulate the Chaotix on a job well done, and as Julie-Su and Rouge bicker some more, the curtain falls on one of the weirdest and most out of place stories we've experienced in some time. Bravo, Romy and Ian, we've officially learned that when you two collaborate, crap gets bizarre!
#nala reads archie sonic preboot#archie sonic#archie sonic preboot#sonic the hedgehog#sth 166#writer: ian flynn#writer: romy chacon#pencils: tracy yardley#pencils: jeff axer#colors: jason jensen
10 notes
·
View notes
Text
There was a big hack on Twitter yesterday, and there’s the news about the little poor pharmaceutical companies that can’t protect their networks. So, I think today is a good day to bring you some general pieces of advice about internet security.
For context, I am not a security expert. What I am is a system administrator and web developer who had to learn all of this to manage and protect 200+ small businesses that had websites and email on our webserver. That said, I think I have simplified a lot of what I had to learn into items that are relatively digestible regardless of technical knowledge.
99% of all hacking done today is about making money somehow. Unfortunately, information can mean profit, so that doesn’t make anyone immune, but it’s important to understand that if someone gets into your systems they are looking for ways to profit, either by using your system to do something, or from the information contained therein.
90% of internet security threats are just old confidence schemes dressed up for modern times. Seriously, look at this Wikipedia article, I can think of a spam email I’ve filtered out for clients that matches just about every single item on this list: https://en.wikipedia.org/wiki/List_of_confidence_tricks
90% of internet security failure points are people, not systems. The only way to combat this is to limit what people have access to. This is why you’re told not to re-use passwords. If one site gets hacked, you want to limit the amount of information they can reveal about you.
Really clever hacks do happen and they’re hard to defend against, but they also are a rarity, and are frequently only employed against high value targets. It isn’t worth your time or money to focus on these exclusively. Many less scrupulous security companies will market their ability to defend against these attacks. If they don’t also defend against every day mundane threats they aren’t worth the money.
Windows Defender gets a lot of flack, but with more and more free anti-malware companies pushing their advertising in potentially malicious ways, it’s a good thing Microsoft have made a push to improve the product. If it’s the only anti-malware you have, you’re not in the worst hands. Microsoft already has all the personal data they want about you, so it’s in their best interest to defend your system from external threats.
The best passwords are long. Special characters and numbers don’t actually do as much for your password security as length does, and they also have a tendency to make passwords hard to remember for users, which makes it more likely that they will either re-use passwords or change it to something weaker. If you’re designing password systems, allow for and encourage greater length in the password fields. 12 characters is not enough. 24 - 50 sounds like a lot, but if you choose a long password that sticks in your head, it isn’t bad, especially once the habit sets in.
Consider using a password manager. On one hand, putting all your passwords in one central location is risky, and makes a higher value target. But on the other hand, using a password manager means that you are more likely to use unique passwords for sites, many of whom spend far less on securing themselves than someone who is selling a dedicated password manager. Personally, I use LastPass, but there are free options, and most browsers include them. The browser option isn’t bad if you set a master password. Mozilla’s is a personal favorite as it encrypts the passwords on your system so if it’s a multi-user system it’s even less likely they’ll be able to break into your password store. I’ve used it on every work computer that would let me.
Be suspicious of everything. If it’s an email from an unknown address. If a friend suddenly starts messaging you in a way they don’t normally. These are warning signs. The human brain is really good at identifying patterns and noticing when they’re broken. If something feels weird, be extra suspicious. Don’t click on links given to you, don’t open random attachments unless you’re sure of what they are. Reach out through alternate forms of communication if possible to ensure the other party actually sent them and that they are what they say they are. If your work won’t prevent it, ensure that document macros are off by default for your Microsoft Office programs, and as annoying as it is, don’t turn off the Windows feature that asks you before running a program as an administrator.
Update your software. If there is a new update for Windows, or anything, update it as soon as possible. This is a weird one because Man-in-the-middle attacks are on the rise for people compromising update servers and using them to install malware, but these are still relatively rare and quickly dealt with. If you want to be extra careful put off updates for two to three days at most. This is a good compromise between staying on top of recently fixed exploits and giving people time to discover and remove malicious updates, but entirely relies on your ability to remember to update. Additionally, I know this is annoying, especially since a lot of companies tend to change their UI around with updates, add/remove features we grow to depend on, but retraining or finding alternate solutions is cheaper than recovering from a hack 100% of the time.
You will get hacked. It isn’t acceptable to plan that you won’t. Have a plan in place for when it happens, and take precautions to limit how bad it can get for you. It’s not fair, but it’s the reality we live in. If you’re responsible for the security of other people’s information this goes double if not triple.
Security is expensive, and it will feel frivolous if it is working. But hacks can and do cost far more, no matter the scale of the system. A website database that gets hacked can cost thousands of dollars to clean up, investigate, and recover, and that’s before the multi-million dollar legal fees and fines you could be looking at if it is found that you were negligent in your security. Even if it’s just a personal computer, you could lose months, even years, trying to stop identity thieves.
The dystopia of information we live in is a direct result of marketing and ecommerce. If you don’t like that you have to spend money on this shit, blame Google, Facebook, Amazon, Apple, and Microsoft. These tech giants showed how valuable the internet and information about people who are on the internet could be. Think strongly about your support for these companies and what that means for the future and your assumed responsibilities as a consumer. We’ve reached an odd equilibrium where it is now in these companies’ best interest to protect us from the problems they helped cause (to protect their investments), but that doesn’t mean this isn’t their fault. Unfortunately, now that this is out of the bag, I don’t know that it can go back in, and if it wasn’t them it very well could have been others.
If you have any corrections on the above, or additional information, please feel free to add them. I’ll try to reblog the best additions.
1 note
·
View note
Text
Spitefic, because Jane Foster deserved better....
Jane had grieved when Erik was lost to the Snap, but obstacles tended to only make her more determined. With Darcy for emotional support and to remind her to eat and sleep, she put aside her work on the Bifrost and time-space travel between realms and focussed on what little research existed regarding the Infinity Stones. She had Erik’s notes on the Tesseract, and her own experience with the Aether, plus several days in Asgard’s library, when she had been limited in how much she could exert herself. Thor had preferred physical pursuits to academics, but he had been happy to discuss the research she found. Despite her life being at risk, those days had been some of the happiest...
Jane forced herself back to the present.
Most of the world’s experts of Quantum Physics, and the leaders in studies on Infinity Stones, had been lost in The Snap. Jane found that suspicious, at best, but at least it cut down on the amount of time she had to spend fighting for grants. (If it brought them back, Jane would happily go back to living off Ramen and cobbling equipment together out of store-bought parts) Jane knew a lot of hackers and counter-hackers, and employed several, especially after people actually started taking her seriously and wanted their name on her work. She sent out feelers to the survivors, and set them to winnowing through SHIELD’s dumped files, especially the HYDRA experiments, for every scrap of data to do with extra-terrestrial studies. The most trustworthy ones were sent to hack into Stark Industries discarded files about the ULTRON project, and Vision by association. With Tony Stark retired from being Iron Man, or at least focused predominantly on making things for himself, there were fewer safeguards on his old, discarded files.
A few other hackers were sent to chase up potential alien sightings, and make contact in the hopes of getting information from other parts of the galaxy.
With that taken care of, Jane set her attention to fine-tuning a new scanner for Quantum and time-space travel.
It took five years, but she found one. In San Francisco, in a storage garage, a portal opened, and someone came through.
_____
The time traveller was gone by the time Jane got there, but the residual traces were still there, and she followed them.
Scott Lang was confused and horrified at all he had missed, at what had happened, but he was absolutely down to do something about it. Darcy returned the rental car, Jane and Scott following in his beat-up old van, and they headed to the Avengers Compound.
Scott had a mastery in electrical engineering, a talent for putting MacGyvering and improvisation, and some knowledge of quantum physics thanks to his work with the Pyms. Jane had first-hand knowledge of infinity stones, a lifetime of work on Einstein-Rosen Bridges, and access to extensive research notes. By the time they reached the Compound, they had the basics of a workable plan.
Jane’s access codes, from when she and Thor had been co-habitating, were still in the system, and they got in without issue. Jane found the lab, still functional despite out-dated systems and a lack of use, and fired it up. Darcy started tracking the current location of the remaining Avengers, and Scott waited outside for them to come back.
______
Startling Captain America was probably a rare feat, but they managed it. Darcy’s social media account was probably going to explode with the amount of reactions, but that didn’t matter right now.
They were skeptical at the idea of time travel - understadable - and hesitant about using technology that hadn’t yet been tested. They listened, though, and gathered the others.
Thor had changed drastically in the years since the Snap, and froze when he saw her. They had separated amicably when Thor had left to search for information about the Infinity Stones, unable to say when or if he would be back and not wanting her to feel obligated to wait for him, but a part of Jane had never stopped loving him. “Hi, Thor.”
He shrunk into himself, reinforcing Jane’s suspicion of severe PTSD. Not that she could fault him for it; there was barely a person on the planet who wasn’t grieving or recovering from some kind of trauma, these days. “Jane. I… I didn’t-“
She stepped forward and took his hand. “Life has been unkind to you, hasn’t it?”
The defensive attitude that Thor had aimed at everyone else faded. “One might say that. Or they might say that I lost everything and became a shell.”
Jane had some familiarity with that. Being possessed by the Aether had been a constant battle to stop it from taking her over entirely, making her a passenger in her own body. “If I recall correctly, that’s how we met in the first place. I don’t know what happened, but I believe in you, and I don’t think that you’ve given up yet.”
There was a painful vulnerability in Thor’s voice, that of a man struggling to be confident in himself. “How do you know?”
Jane tried to project nonchalance. “You’re here, aren’t you? You’re alive, and we’re going to change it. Deal?”
Finally, Thor smiled, even if it was a shadow of it’s former brilliance. “Deal.”
Behind them, someone snickered. “Well, at least letting himself go didn’t change everything.”
Jane whirled around, fierce and angry. “One more fat-shaming joke, and the person voicing it gets punted out the nearest window! Thor, can you tell me what you discovered about the stones, and I’ll add it to my database.”
Thor followed her willingly, and submitted to a fierce hug from Darcy. Thor hadn’t found much, but there had been some helpful things useful information from Space Monks who had tried to replicate the effects of the Time Stone. Well, the ruins of what had been their temple, anyway. At least Jane knew a few things to avoid in her tests.
They lapsed into silence, Thor warring with himself over something. Finally, he looked at her, as serious as she had ever seen him. “I - you need to be careful around me. Certain things… I struggle to recognise friend from foe, and see only Thanos, telling me that I have failed.”
Jane nodded. “PTSD, I can’t say I’m surprised. What are your known triggers?”
Thor blinked, and Jane wanted to hit everyone who had treated him like he was broken or worthless. The Avengers, at the very least, should have known better. “Snapping fingers, so far as I know. I isolated myself, after I nearly killed Brunhilda, thinking she was Thanos. I thought, if I lacked my former skill and reflexes…”
Jane had exactly zero objections to the long hair and beard, as much as she had enjoyed the shorter version, too. Besides, she had dealt with enough comments on her appearance from ‘totally not hot enough to have Thor’s babies’ to ‘unprofessional clothing and not bothered with her appearance’ and all the other double standards that male scientists never had to deal with. She wasn’t about to judge him on some extra weight and whatever helped him get through the day. “Honestly, I’m kind of enjoying the Viking look. Besides, weight didn’t stop Volstagg from being a formidible warrior, if I recall correctly.”
He smiled briefly, the shy and almost boyish grin reserved exclusively for her. “Thank you. Seeing you alive gives me hope that this will work.”
Jane blushed. “We never let the seemingly-impossible stop us before. Why start now?”
#Thor#Jane foster#Avengers endgame#endgame spoilers#Jane foster deserved better#anti-fat-shaming#because seriously?#everyone deserved better#mocking PTSD?#ptsdsurvivor
70 notes
·
View notes
Photo
Get more followers on Facebook in 2020
Easy steps to get 10000+ Auto followers on Facebook
With the constant changes in Facebook algorithms, it’s becoming harder and harder to survive on BOTS . The algorithms are on a constant lookout for suspicious activities and boy, are bots suspects. With bought followers, you risk penalties from Facebook and at worst a ban may occur. This will limit your accounts’ potential to get more followers on Facebook.
Facebook Automation is the most successful way of getting more followers on Facebook. How? Well besides automation you need to ensure you have great content that is captivating to your target audience. So let’s get the steps right.
Content creation The key to developing a superb Facebook page and scaling your business to greater heights is to post content that genuinely interests your customers or clients. By providing valuable information to your readers you will build a stronger relationship with current and prospective customers. Take time to see what other people in your niche are doing. Let’s face it, in whichever area there’s got to be someone else who is doing it better than you. So follow the trend and find a means to leveraging the content for your page. Post a variety of content, i.e press release, high quality, and relevant photos and videos and so forth.
Allow fans to post on your wall In a bid to get more followers on facebook, It’s very important to allow users to post on your wall, infant its the whole idea of having a fan page. this allows you to get valuable feedback about your brand and ensure necessary adjustment and improvements are made.
Call to action button Call to action buttons are customized URL buttons that redirect users to a website or blog. this enables them to get more detailed information towards your brand. this way you are able to drive valuable traffic and enhance your market reach. they include ‘book now’, ‘learn how’, get it now’ and so forth.
Improve Your Facebook Organic Reach
The Facebook Organic reach is the number of unique Facebook users you can reach with your Facebook content for free and not as a result of ads.
When you post something on Facebook, your content will be displayed only to some of your followers (people that liked your Facebook Page) or friends. It will not be visible to all your fan base, but to a certain percentage, depending on your organic reach. Your organic reach is therefore based on the number of engagement you get on your post as well as the amount of other competitive content that tries to out win your fans at the same time.
Your organic reach is calculated based on the engagement you get on your posts. As well on the amount of other competitive content that tries to win the attention of your fans at the same time. First, you need to make sure your engagement rates are as high as possible. Lots of engagement translates into great content, and great content is highly appreciated by Facebook’s algorithm.
And second, you need to schedule your posts and try to avoid the “peak hours” – when everybody else is posting their own content. But of course, you also need to take into consideration your followers’ time zone and their online habits (when they actually show up to read their feeds).
READ ALSO: How to make money on Tik Tok in 2020
How then do you achieve this? Alright, now that we have the content right, let see how we can set up a Facebook automation software and get more followers on Facebook. While there are numerous tools in the market for this function, I personally use JARVEE due to its numerous features, ease of use and its affordability.
JARVEE is an intelligent tool that mimics normal human behavior and runs on autopilot. This is to say that, after successfully setting up, you sit back while JARVEE does the job for you.
PS also automates Instagram , Quora , Twitter , Pinterest , Tumblr, LinkedIn, and Youtube as well
Go here and download a free trial of this advanced social media automation tool for free. The trial period is 5 days which is time to test and review its benefits (No credit card details required)
Once you’ve registered and installed the tool, use the details sent to your email to log in to the app. Here you are going to add your Instagram account (s)-depending on the downloaded package you can automate as many Instagram accounts as possible. To add your account on JARVEE , click on SOCIAL PROFILE on the left Menu bar. Now click on ADD PROFILE and select FACEBOOK Facebook automation and what the tool will do for you
JARVEE will help you interact with your audience with a powerful set of Facebook automation tool. These tools are specially designed to plan, manage and analyze all your social interactions. If you’re into Facebook marketing JARVEE is the tool for you. It will grow your business with real Facebook followers.
Posts Scheduling With JARVEE you will be able to create month-long content and schedule them for automatic posting at times when your fans are most engaged. Furthermore, they will be posted at a specific time of day such that you fans know exactly when to expect your post.
You can schedule the posts on your personal accounts, Facebook pages or any group you can post to.
Auto-hashtag keywords JARVEE will allow you to set up niche-oriented keywords that are eventually converted to hashtags once your posts are published.
Campaigns insights and statistics JARVEE will provide you with statistics and insights for your strategy. This data is essential in evaluating the extent to which your strategy is working. obviously if it isn’t you save time by adopting a different one. This is a key tool in ensuring you achieve audience reach and eventually get 10000+ Auto followers on Facebook.
Find Groups and Pages in your niche Using intelligent algorithms, JARVEE has the best group finder around. Using group finder, you are able to search for thousands of groups that are unique to your target niche.
Join/Un-join Groups in your niche JARVEE allows you to join the groups that you have been able to derive from the group finder option. You then have the discretion to automatically un-join the ones you find useless and retain the beneficial ones.
Ignore Groups This tool has an option to ignore groups that you don’t wish to interact with. These are ideally competitor groups or other groups that are detrimental to your account in any way.
Make sure you never interact with certain groups, be it your competitor’s group or your school’s classmates group.
Auto-Share posts on your Groups You will also be able to Auto-share your Facebook post and attain maximum reach for your brand by sharing them on other groups that you are a member of.
Schedule posts from RSS feed RSS stands for “rich site summary.” At its heart, RSS is just simple text files with basic updated information — news pieces, articles, that sort of thing. That stripped-down content is usually plugged into what is called a “feed reader” or an interface that quickly converts the RSS text files into a stream of the latest updates from around the web. JARVEE will allow you to import high-quality content from this source. You are then at liberty to schedule the post on your Facebook page.
Auto-Invite friends to your groups Tired on inviting your friends to all of your groups, well this tool has you sorted, it will automatically invite them to these groups and enhance your brand identity.
You can also Auto-accept new members to your groups.
Auto-Invite friends to Pages/Events JARVEE allows you to automatically invite friends to your pages/events. This way you have a substantial audience to your events. That’s not all, your page will also grow faster.
Auto-Comment and Like The tool will do the commenting and liking for you in various pages, groups or walls. This will trigger a domino effect on your account growth and bring you closer to getting 10000+ Auto followers on Facebook.
Auto-Accept friend requests Save yourself tremendous time by the auto-accept friends feature on JARVEE. You can use this time to focus on content creation or other issues.
Auto-Reply to new messages JARVEE comes with an auto-reply feature. This is especially useful when you are not online all the time. JARVEE will respond to all your message. This feature is enhanced with the use of creative SYNTAX to avoid monotony. You afforded some time to come back later and continue the conversation at your convenience.
Send Friend Requests JARVEE will use intelligent algorithms to extend friend request to people in your unique niche. This will further the objective f getting 10000+ auto followers on Facebook. Targeting will greatly increase the chances of these request being accepted because you are reaching to an audience which is interested in your content.
Contact other people in your niche Search for people in your niche that are interested in your business and contact them using JARVEE. This is a well known Facebook marketing tactic and one of the most efficient methods to expand your reach and increase your traffic and sales. With JARVEE you will find and contact niche-specific real people.
Auto-Unfriend Tool When the circumstances deem it necessary, set JARVEE to automatically unfriend people that do not add value to your business.
Auto-Change cover photo It’s important to update your cover photo at least once every two months to keep your page fresh . When you upload a new cover photo it will also be posted on your timeline, giving your page greater visibility. Again JARVEE has you sorted, you just need to create multiple cover photos and JARVEE will automatically rotate them.
Bump your group posts Bump is an online slang term for the practice moving a post to the top of a discussion thread, increasing a message or thread’s status and visibility. JARVEE will periodically do this for your posts ensuring they stay relevant. You avoid posting the same content multiple times which is quite frankly annoying.
Birthday Tool It’s a bad social signal when you fail to wish your friends the best of wishes on their special day. wishing them is actually an indicator of your cohesive bond. Its however human nature to forget and this doesn’t necessarily mean we don’t like these individuals. JARVEE developers had this in mind while coding the tool. Set these functions on autopilot, again with creative use of the spintax feature.
Spin syntax Spintax is the format (or syntax) that is used by various software spinners and article submission sites that create or use spun articles. There are various spintax formats depending on what software/services you use. This feature on JARVEE will ensure unique messages are published on each account response.
Proxy Support JARVEE supports the use of proxy, you can run each individual account on a separate proxy. This will greatly enhance privacy and security for these accounts.
Better Account Management With JARVEE you can set up custom sleep times for your Facebook accounts, randomize and limit the number of posts per day.
This will ensure a more human-like behavior and reduces the risk of Facebook restriction.
Turn Off Group notifications If you’re into a lot of groups you’ll probably get flooded with all those group notifications, reduce the noise by turning them off automatically.
https://socialtipster.co/how-to-get-10000-auto-followers-on-facebook-in-2019/?utm_source=rss&utm_medium=rss&utm_campaign=how-to-get-10000-auto-followers-on-facebook-in-2019
#SEO #entrepreneurship #branding #startup #webdesign #marketingtips #contentmarketing #onlinemarketing #seo
1 note
·
View note
Text
We’ll sweep out the ashes in the morning |CHAPTER 1|
Heeeere comes the Peraltiago scandal !
This story takes place in an alternative universe, where Amy applied for and got the job as 'data analyst' for for Major Crimes (See episode 1.15: 'Operation Broken Feather' for further reference). This means that Jake and Amy no longer work together and havent for a few years. This also means that I don't know what right and technical job title this new job would get Amy, so I'm just going with/imagining that she was still a detective even after her transfer.
Read it on AO3 or simply enjoy it here! I appreciate comments more than you know <3
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
CHAPTER 1: I didn't mean to start this fire and neither did you
It really had been the best yet also most disastrous kind of accidental occurrence that day. Best back then, when Amy Santiago was promptly striding down the sidewalk on a just as coincidental cold, February morning.
Her head was dipped in a downwards adjustment, simply enough for her to absorb the new information on her phone which had just led her to pick it up from the pocket of her navy blue coat just a few seconds ago. Out of what seemed to be nowhere, it all came to a halt. Maybe more a thud and burst actually, when suddenly her phone flew out of her hand in one direction meanwhile the still warm coffee in her other hand travelled in the opposite direction. It took her a much startled second to realise that herself, her coffee, phone and a stranger suddenly had one thing in common; they were thrown off their respective paths with quite the vivacity. All that her eyes managed to grasp in the few fatal seconds was a black coat covering a masculine figure and chestnut-like hair. The remaining details remained undefined in her state of shock. All she knew was that she’d ignorantly stumbled into someone.
“Oh my goodness, I am so so sorry, sir!” She exclaimed immediately after her brain had put all the facts together and suddenly felt the guilt of being just another typical phone-addict; she used to be so good at limiting the amount of attention she’d give it. “I was reading an email and wasn’t paying attention to where I was going.” She kneeled to pick up her phone from the icy sidewalk as well as the now empty cup (even an accident like this was no excuse to be a litterbug).
“Wow, Santiago. Who would’ve thought I’d ever experience you on your knees and calling me sir?”
As she was practically on her knees, the figure standing in front and above her allowed himself to speak; right then and there Amy Santiago could’ve sworn that she felt a scrap of familiarity rush through her body’s nervous system. The octave of the voice, deep enough for man’s but not enough to hide the manchild behind; Calling her Santiago? No one else would do that without a preceding ‘Sergeant’; the facility of the fall of the joke? Like it came from a place of practice and habit? It could only be…
“Peralta?” In contrast to how her head had previously been tilted forwards and down, it was now tilted backwards to look up at the half-stranger and take in the indeed chestnut-like hair (still messy and curly), cinnamon eyes and surprisingly unsurprisingly mischievous smile.
“The one and only,” the chuckle was just as familiar as the rest of him. “Here,” he kneeled down to her level and started to pick up things she hadn’t even realised she’d dropped. “Let me help you out.” He started reaching out for her keys and lipstick that’d been resting safely (or so she thought) in her purse.
Meanwhile Amy was still kneeling but with her back now straightened in bewilderment whilst her eyes followed his every movement with the purpose of figuring out if he was actually real. For how long she did this exactly, she doesn’t recall, but next thing she knew he’d followed her example and straightened his back as well. Still on his knees and eyes directed at her whilst holding her stuff in his hands. Rushing people walking by, or rather around, the kneeling couple didn’t seem to give in to their New York-curiousness. It was 8 AM and everyone had places to go. Including Amy herself, she suddenly realised and snapped out of her until now absent state of mind.
“Oh, wow! Uhm- thank you,” she fumbled with her words and hands as she grabbed her things from him before hastily standing back up. Once both back on their feet it hit her that she was being suspiciously far-flung considering the fact that Jake Peralta was no stranger and had been looking at her with nothing but kind and inviting eyes ever since she took a first dive into them approximately 30 seconds ago. Her body’s response to this realisation was a swift shake of the head. “And oh my goodness- hi!” She stuttered overwhelmed and awkwardly (Santiago-stylez) in the act of finally smiling for the first time post collision.
“Hi,” the reply was followed by his figure instantly leaning in to hug her like he’d been holding it back since realising who he’d collided with. Of course she automatically let her arms wrap their way back around his broad shoulders, hating how completely right and practically overwhelmingly good it felt. Almost like something that’d been missing had made its way back home. This was only proved right by the fact that it almost, just almost, made her heart drop when he pulled back.
“How are you doing? It’s been forever!” There was a swift switch in the direction of his gaze upon noticing a few drops of coffee on his coat, provoking him to quickly brush them off before redirecting his attention back to her. She could’ve sworn he’d fumbled just a bit too much in the process. Almost like he’d hoped that she hadn’t noticed him taking his eyes off of her for just a second. Attentive as always, she thought.
“I’m good! And yeah it has been a while, hasn’t it?..” she couldn’t help but notice that the present dread in her voice was on the edge of obvious. Ever since Amy had gotten the job and transferred to Major Crimes to be a data analysts (with the Vulture), she had barely to never seen Jake since. Sure, they’d texted a bit back and forth, sent the occasional joke or meme, but even this had died out once they’d gotten used to the other’s absence at work and each their new life-partner: Teddy and Sophia.
“I’m glad to hear that,” Jake smiled brightly and Amy could never doubt the fact that he fully meant it. “…And I’m sorry I haven’t texted or called. Life, yanno?” He shot a look down at his carefully shuffling feet.
“Hey,” an impulse within her, like an overwhelming craving, brought her left hand to reach out across the space between them to gently squeeze his arm. “No worries. I’ve also been super busy and haven’t reached out. We’re cool.” To her delight his shoulders dropped in a sign of relaxation, his eyes rose back to hers and everything seemed to be as it should be, when you run into someone you used to know so well and maybe even used to consider your best friend. Pleased with this she allowed her hand to drop from its spot on him.
“No wonder why you’re out here running into people then, Santiago,” they both had to laugh at the comment, relishing in the resurfacing of familiar banter that used to and once again lead Amy to push a lock of her dark, freely hanging hair behind her ear. This triggered a thought that couldn’t help but welcome into his mind: would she still wear her hair up in the famous pony-tail he still remembered? Or was this lose hair her new thing? Her hair was so much longer now. Gosh, he had so many questions.
“Yeah, sorry about that. I got an email from work and had to check it,” she bit her bottom lip nervously, briefly holding up her phone as emphasis of her explanation.
“Always so devoted to duty,” Jake could barely tell if he was smiling again or just hadn’t stopped since he realised who he’d bumped into. “Anyways… I’m sure you have tons of things to catch up on, like emails and whatnot…” They both chuckled nervously, dancing around the fact that they both logically needed to go but seemed to lack the will. “… So I’ll let you get to work, detec-“
“Sergeant, actually,” there was a sense of pride and authority behind her correcting. Both in her voice and eyes. Something Jake couldn’t deny suited her incredibly well.
“Of course,” he picked up his now corrected point with a cheesy smile. “Why doesn’t that surprise me? I always knew you’d outrank me…” Jake couldn’t entirely tell if it was because of the cold or if it was because she was flattered, but her cheeks definitely bloomed with a shade of pink; just a tiny bit and enough for him to notice. “Anyways, I will let you get to work then, Sergeant…” he made sure to emphasise her new title, which to his enjoyment and suddenly lightly racing heart earned him an even wider smile in return. “Bye then.”
“Bye, Jake,” she smiled, before stepping beside him and picking up where her path had been interrupted.
With each clack of her heeled boots, each sound of her walking away and out of his life again, Jake felt his heart race beneath his increasingly clenching chest. Not that this had to mean anything specific, but it definitely brought along the manifestation of curiosity and the feeling of wanting to know more; he wanted to have a real conversation with her; he wanted to sit down and know her again… He felt his body push him to edge of actually asking which was oddly similar to wanting to throw up. There was nothing to lose or dangerous about catching up, right? They weren’t strangers, simply friends who’d drifted a part. Now was not the time to strive away from his otherwise so straightforward personality.
“Hey! Santiago!” He turned around on the spot, calling for her attention before she could get too far away and drown in New York’s sea of oh so important and busy people. Luckily she hadn’t been in a rush to get away from him and was simply a few feet away. “Would you like to catch up over a drink? Or crappy Chinese food?”
Hating how aware of his question he was, he was thrilled to see her smile at his last comment, resulting in the deflating of his question’s denseness.
“That…” She paused for a second, before realising that she was about to overthink it all which would mean giving the situation more meaning than actually needed. They were old colleagues, for Christ’s sake! Catching up was normal. Not weird. Not meaningful. Just… normal. Besides that there was this muted, constant thumping in her chest and gut. Somehow it was telling her that saying no would be betraying herself more than anything or anyone else. He had been her friend before, so it made sense that he hypothetically could become it again. “That would be nice, Peralta. Let’s do that. You still have my number right?”
Almost like he’d been holding his breath in anticipation (which he hadn’t ‘cause this was just Amy; Amy his old partner and friend), Jake breathed out a reply. “Yes! Awesome uh- I’ll text you!”
Her smile was accompanied by an approving nod, before she turned back away from him to continue her already twice interrupted journey to work. Apparently Amy Santiago still provoked his blabber mouth; two interruptions wouldn’t let her go without a third. “Or I’ll send an email since you’re apparently so absorbed by those these days.” His half-yelled comment fought its way through the noisy crowd and earned him the impeccable sight of Amy Santiago doing a quick 360 mid-stride, only to send him an iconic eye roll and ‘annoyed but it’s funny’-smile. It all happened so fast, yet in slow motion if you’d asked Jake, and before he knew it Amy continued straight ahead like nothing had happened. Jake could’ve almost (just almost!) sworn to God that he’d never seen anything more thrilling and satisfying than those three seconds that it took her to do that.
She hadn’t changed, had she? And neither had they, had they?
#jake x amy#peraltiago#peraltiago fanfiction#fanfiction#brooklyn nine-nine#b99#fanfic#jake peralta#amy santiago#jake and amy
20 notes
·
View notes