#Archive Gmail Data
Explore tagged Tumblr posts
Text
This day in history

I'm touring my new, nationally bestselling novel The Bezzle! Catch me WEDNESDAY (Apr 11) at UCLA, then Chicago (Apr 17), Torino (Apr 21) Marin County (Apr 27), Winnipeg (May 2), Calgary (May 3), Vancouver (May 4), and beyond!

#20yrsago Report from the spam/anti-spam summit https://web.archive.org/web/20040426071527/http://www.guardian.co.uk/online/spam/story/0,13427,1187654,00.html
#20yrsago Broadcast Treaty threatens the whole world with super-duper DMCA https://web.archive.org/web/20040427223711/http://www.corante.com/importance/archives/002925.html
#20yrsago John Gilmore on Gmail’s terms-of-service https://craphound.com/gilmoreongmail.html
#15yrsago U2’s manager wants the power to cut off your Internet connection https://memex.craphound.com/2009/04/08/u2s-manager-wants-the-power-to-cut-off-your-internet-connection/
#15yrsago Sustainable Energy Without the Hot Air: the Freakonomics of conservation, climate and energy https://memex.craphound.com/2009/04/08/sustainable-energy-without-the-hot-air-the-freakonomics-of-conservation-climate-and-energy/ #15yrsago What you should be afraid of instead of terrorists https://web.archive.org/web/20090327073459/https://www.counterpunch.org/goekler03242009.html
#15yrsago Obama DOJ invents radical authoritarian theory to defend Bush administration’s warrantless wiretapping https://www.salon.com/2007/08/01/obama/
#15yrsago London cop’s unprovoked attack on G20 bystander who then has fatal heart attack https://www.theguardian.com/uk/2009/apr/07/video-g20-police-assault
#10yrsago EU’s highest court strikes down mass surveillance under the Data Retention Directive https://www.eff.org/deeplinks/2014/04/data-retention-violates-human-rights-says-eus-highest-court
#10yrsago Online test-proctoring: educational spyware that lets third parties secretly watch and listen to you through your computer https://web.archive.org/web/20140412142717/http://spartandaily.com/119401/online-proctoring-raises-privacy-concerns
#10yrsago My daughter Poesy reviews Hilda and the Black Hound https://www.youtube.com/watch?v=2lVWEiMbx_E
#5yrsago The BLM’s Burning Man environmental impact statement is terrible, calls for drug searches, dumpsters, and a 19,000,000lb concrete wall https://memex.craphound.com/2019/04/07/the-blms-burning-man-environmental-impact-statement-is-terrible-calls-for-drug-searches-dumpsters-and-a-19000000lb-concrete-wall/
#5yrsago China’s toxic livestreaming culture: the vicarious lives of angry, alienated, uneducated rural gamers https://www.sixthtone.com/news/1003642
#5yrsago The two hidden intellectual moves behind the “progressive” argument against free college https://www.washingtonpost.com/politics/2019/04/05/pete-buttigieg-argues-against-free-college-this-is-why-progressives-cant-agree-about-subsidizing-tuition/
#5yrsago Pledge: I will not participate in any event organized by or including institutions that employ Kirstjen Nielsen https://memex.craphound.com/2019/04/08/pledge-i-will-not-participate-in-any-event-organized-by-or-including-institutions-that-employ-kirstjen-nielsen/
#5yrsago Most browsers — except Firefox and Brave — are eliminating the option to turn off surveilling “hyperlink auditing” https://www.bleepingcomputer.com/news/software/major-browsers-to-prevent-disabling-of-click-tracking-privacy-risk/
#1yrago Everything advertised on social media is overpriced junk https://pluralistic.net/2023/04/08/late-stage-sea-monkeys/#jeremys-razors
6 notes
·
View notes
Text
The Benefits of Cloud Hosting for Small Business
In the past, hosting websites and apps just required paying a digital platform provider to rent out a single server or computing cluster. Services for web hosting have existed for as long as the internet. Over the past ten years, cloud hosting where the website or application resides on virtual servers dispersed across the cloud has emerged as a popular way to make digital assets accessible online.
A worldwide content delivery network can be connected to by Google Cloud to provide customers with optimal speed and minimal latency when serving material, or a domain can be registered and managed. Google Cloud also provides a range of hosting options for websites and applications.

What is cloud hosting?
Your data is stored on several servers rather than on a single server, which is what is meant by the term "cloud hosting." The term "cloud" refers to this network of several servers that collaborate to form the network. Cloud hosting services are currently being utilized by a multitude of businesses, both large and small. An investment of this kind is definitely worth the rewards, and it has the potential to achieve great things for your company.
You will have a single platform from which you can manage all of your applications and databases, which will allow you to streamline your operations. The productivity of your firm can also be improved by making an investment in cloud infrastructure resources. The various advantages of cloud hosting will be discussed in further depth in the following paragraphs.
Cloud hosting’s Significance for Small Businesses-
Adopting cloud computing has becoming increasingly important for small organizations. It helps small businesses to avoid the high initial investment and ongoing maintenance costs of having internal IT infrastructure. Small businesses can now access advanced technologies and capabilities that were previously exclusive to large organizations by utilizing the cloud.
What are the applications of cloud computing?
Although you might not be aware of it, there is a good chance that you are currently utilizing cloud computing. Whether you use an online service such as Gmail or Outlook 365 to send an email, collaborate on a document, save data, or stream a video, cloud computing makes it feasible behind the scenes to do all of these things.
Cloud Hosting:
Cloud hosting services make it possible to share a variety of information, such as using email services, hosting applications, using web-based phone systems, and storing data. Hosting your company's website, managing databases, and storing domain names are all things that may be done with a cloud hosting service. The fact that cloud hosting services are located offsite makes it simple to scale up in order to handle peak loads.
Backup services:
Backup services in the cloud are failsafe solutions that can be utilized in the event that your company suffers a server disaster, cyberattack, or other type of data loss. Storage, data synchronization and restoration, real-time backups, archiving, and a high level of security are all features that are included in the top cloud backup services. A great number of cloud storage firms now offer cloud backup and storage capabilities.
Storage in the cloud:
Cloud services guarantee that your data is stored in a cloud storage system that is located offsite, making it more convenient to access from any device or place that is linked to the internet. In cloud storage, you are able to securely exchange information with others and synchronize files across several devices. Companies such as Dropbox, Microsoft OneDrive, and Google Drive are examples of well-known cloud storage services.
Software as a service
Software as a service, also known as SaaS, is a solution for the distribution of applications that is hosted in the computer's cloud. SaaS solutions can be utilized by businesses in a variety of operational domains. For instance, you may adopt software for customer relationship management (CRM) that is hosted on the cloud, such as Salesforce, for the purpose of managing sales, accounting software, such as QuickBooks Online, for managing finances, and email marketing software for improving marketing communications.
Cloud Solutions' Advantages for Small Businesses-
Affordable
Small firms can minimize their expenditures on hardware, software licenses, and information technology by switching to cloud-based services, which results in cost savings. Companies that provide cloud computing services often provide a pay-as-you-go approach, which enables organizations to only pay for the resources and services that they actually employ.
Protection of Sensitive Information and Disaster Recovery
Cloud service companies adopt stringent security procedures to protect vulnerable information. In addition to this, they provide solutions for disaster recovery and automatic backups, which serves to ensure that vital corporate information is safeguarded, quickly recoverable, and less likely to be lost.
Scalability:
Cloud hosting solutions enable small businesses to swiftly scale their operations up or down as needed without the inconvenience and expense of physically upgrading their gear and software. Scalability includes the ability to scale up or down activities. This flexibility enables adaptability and growth prospects, both of which are essential in a market that is very competitive.
Advantage in the Market
Cloud hosting solutions give small firms the ability to compete on an equal playing field with larger organizations, which gives them a competitive advantage. It is possible for them to obtain insights, streamline operations, and make decisions based on data without breaking the bank by utilizing sophisticated software, analytics tools, and advanced information technology.
Flexibility
As a result of the fact that all that is required to access the cloud is an internet connection, one of the advantages of cloud hosting is that it provides direct remote access to the data that is pertinent to all of your employees, including yourself. If you run a small business, it's possible that you don't have the financial resources to purchase a dedicated office space. People are able to work from any location they choose thanks to this cloud-based technology. Having the ability to operate from a remote location is more important than ever before for the success of a company, especially in light of the recent epidemic.
Increased Capacity for Collaboration and Adaptability
Cloud solutions enable small businesses to communicate with remote team members, clients, and partners in a seamless manner, which helps improve the flexibility and collaboration capabilities of these firms. It makes it possible to share files in real time, modify them simultaneously, and gain access to the most recent versions of documents, all of which contribute to increased productivity and efficiency.
The Most Recent Technology
Cloud hosting eliminates the need for you to worry about the possibility of automatically upgrading and customizing your servers, in contrast to traditional hosting, which does not permit such activities. Scalability is something that may be easily achieved as your company expands and your requirements and preferences shift.
Because cloud hosting businesses are experts in this kind of technology, this is something that can be easily accomplished. Since they have access to more resources, they are able to undertake research and construct systems that are more robust and powerful. You will have access to the most cutting-edge technologies available if you make an investment in cloud infrastructure.
Very little to no upkeep is required
Recall what I mentioned earlier regarding the safety concerns associated with cloud computing. That being said, a portion of that security necessitates the routine maintenance of servers, the updating of software, and the administration of networks. The good news is that cloud computing relieves you of the responsibility of doing all of that upkeep and instead places it in the hands of skilled specialists.
Because none of the equipment is hosted by you, you do not need to be concerned about purchasing newer versions of it every three to four years. You are not required to deal with any of that maintenance, which frees up more time for your firm to concentrate on the product or service that it offers.
Remote access
When it comes to cloud computing, your email account is the ideal illustration. Providing that you have your login credentials and an internet connection, you are able to access your consolidated email account from any computer. Cloud computing is appealing to a majority of businesses because of the convenience it provides. Your colleagues and you will be able to access your work from any location in the globe thanks to the cloud, which eliminates the need to store your work on a desktop computer or on a local area network (LAN) server that is not linked to the internet. Your productivity and freedom in your workspace will both increase as a result of this remote access.
Conclusion-
Through the simplification of procedures and the facilitation of real-time collaboration among members of a team, cloud computing has the potential to boost both efficiency and productivity. It is possible for teams to collaborate effectively regardless of their geographical location or the time zone differences between them if they have shared access to documents and files. In addition, many cloud-based services provide automation technologies that reduce the amount of manual work that employees have to perform, such as data entry or report production. This allows employees to concentrate on high-value tasks that contribute to the success of the company.

Dollar2host Dollar2host.com We provide expert Webhosting services for your desired needs Facebook Twitter Instagram YouTube
3 notes
·
View notes
Text
Podcast Sexybracket Voting: Round 6
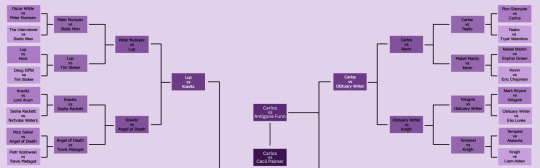
Time for the finals!
Carlos the Scientist (Welcome to Night Vale) vs Cecil Palmer (Welcome to Night Vale)
Battle for third place: Antigone Funn (Wooden Overcoats) vs Lup (The Adventure Zone)
How should I vote?
In this bracket, don't worry about who's most popular on Tumblr or who meets a narrow definition of "sexyman"/"sexywoman"—just vote for whoever you, personally, think is sexiest.
What is this?
The sexiestpodcastcharacter mod is attempting an act of necromancy in order to satisfy þeir curiosity about how fictionpodsexyperson's bracket would have turned out had it finished. If anyone knows the identity of the fictionpodsexyperson's pollrunner, please do not bother them about this.* Like most acts of necromancy, this was done without their permission or respect to their clear wishes to rest in peace.
Curious about what came before?
So am I. Alas, a deactivated blog is a deactivated blog. I have the preliminaries and the Round 4 polls archived on my personal blog. I can tell you that all ties were satisfied with a coin-flip, but I do not remember which polls were tied.
The Round 5 masterpost is here.
*If by chance fictionpodsexyperson's pollrunner is reading this themselves, and they have a copy of their poll's submissions or any other data from their poll, I would love to have a copy and can be reached via gmail under wanderingandfound.
8 notes
·
View notes
Text
G Suite Legacy Storage Limit: What It Means for Users in 2025
For many years, early adopters of Google’s productivity tools enjoyed the benefits of the G Suite legacy free edition. This version provided access to Gmail, Google Drive, Calendar, and other core services at no cost — and with surprisingly generous features, especially in terms of storage. However, Google has gradually moved away from supporting the legacy edition, and in 2025, the enforcement of the G Suite legacy storage limit is becoming a critical concern for long-time users.
What Was the G Suite Legacy Free Edition?
G Suite, now known as Google Workspace, began as a free offering for small businesses and individuals. Those who signed up before December 6, 2012, were able to use the platform indefinitely at no cost. One of the most attractive benefits was the large — in some cases unlimited — storage capacity across Gmail and Google Drive.
For over a decade, many users relied on this storage for business documents, email archives, and media backups. But as Google has restructured its services, this free tier has become unsustainable for the company to maintain.
New G Suite Legacy Storage Limits in Effect
In 2024 and continuing into 2025, Google began enforcing stricter G Suite legacy storage limits. Legacy accounts that once had unlimited or high storage thresholds are now being capped. For many users, this means hitting storage ceilings of 15 GB per user, unless they upgrade to a paid Google Workspace plan.
These changes apply across all Google services — including Gmail, Google Drive, and Google Photos. Once an account exceeds the limit, functionality may be restricted. Users might be unable to send or receive emails, sync new files, or upload to Drive.
How This Affects Users
Many users have already started receiving warnings that their accounts are over the new limit. If no action is taken, these accounts risk losing access to core features. For businesses and individuals who have built years’ worth of files and emails in their legacy accounts, this poses a serious challenge.
What Can You Do?
If you’re affected by the G Suite legacy storage limit, here are your options:
Clean Up Storage: Delete old emails, large attachments, and unused files.
Export Your Data: Use Google Takeout to back up data before clearing space.
Upgrade to Google Workspace: Paid plans start with higher storage limits and business-grade features.
Explore Alternatives: Some users are migrating files to other cloud storage providers like Dropbox or OneDrive.
Conclusion
The enforcement of the G Suite legacy storage limit marks the end of an era for Google’s long-time users. While it may feel like a loss, understanding your options now will help ensure you stay productive and retain control of your data in the future.
0 notes
Text
“Password1234”: Tulsi Gabbard’s Login

“Password1234”: How Tulsi Gabbard’s Login Habits Nearly Triggered a Hawaiian Missile Crisis 2.0
The National Security Threat of Reusing Your Ex-Boyfriend’s Name As a Password When “Aloha” Meets “Access Denied” In a shocking exposé that shook no one except the IT guy named Carl, The Daily Beast revealed that Tulsi Gabbard—a congresswoman, veteran, spiritual warrior, and occasional surfer—had apparently been using passwords that could be cracked by a caffeinated squirrel with an iPhone 4. According to leaked reports, her online security strategy was a combination of horoscope advice, yoga poses, and pure vibes. And yet, somehow, the nation remained standing. So we ask the vital question: What happens when the nuclear codes are one password reset question away from “What was your first pet’s name?” “She thought two-factor authentication meant having a backup horoscope.” — Ron White Let’s dive into the browser history of this satirical scandal.
“Tulsi2020!” Isn’t Just a Campaign Slogan, It’s Also Her Netflix Password
Gabbard’s Surfboard Contains More Encryption Than Her Laptop Tulsi Gabbard ran for president in 2020. Apparently, she also ran out of original password ideas in the same year. According to a cybersecurity leak no one asked for, Gabbard used “Tulsi2020!” across at least seven platforms—including MyFitnessPal, Dropbox, LinkedIn, and a suspicious site called “WarriorMonkDating.com.” What’s worse? She added the exclamation point thinking it was military-grade encryption. “It’s like putting a sticker over a webcam and calling it cybersecurity,” said retired NSA analyst and part-time laser tag champion Ron Skelton.
The Yoga of Password Management: Sun Salutations and Synced Devices
Sources close to Gabbard say she once attended a cybersecurity retreat in Maui, where instead of encryption, participants were taught to breathe deeply while entering their debit card numbers into public Wi-Fi. She later described it as “a transformative experience where I learned to align my chakras and my bank logins.” One witness described Gabbard’s “password flow” routine: First, she logs in with “namaste123” Then does downward dog while waiting for two-factor authentication And finally logs out by whispering “Aloha” to the server
The Cybercrime Wave: Russian Hackers, Meet “Password1234”
By 2017, her accounts were part of a larger leak that included over 3 billion records. Her contribution to this vast archive of human carelessness? Password: Tulsi123 Backup Password: Password1234 Security Question: “What’s your favorite color?” Answer: “YES” “It’s the cybersecurity equivalent of leaving your keys in your car with a note that says ‘Steal me, but with love,’” explained digital security expert Cliff “BitByte” Hernandez.
Gmail, Glam, and Glitches: Tulsi’s Digital Footprint is Wearing Flip-Flops
Among the compromised accounts was her Gmail, which—according to leaked metadata—was 70% promotional emails, 20% requests to appear on obscure podcasts, and 10% fan mail written entirely in binary. One intern who sorted through the compromised messages said: “There were multiple drafts of her resignation letter, all saved as ‘resignation_final_FINAL_FOR_REAL.docx’”
Exclusive: Her Two-Factor Authentication Was a Friendship Bracelet
Tech insiders were horrified to discover Tulsi’s idea of 2FA wasn’t a confirmation code—it was “texting her cousin Jaya to see if it was really her logging in.” On multiple occasions, hackers were stopped not by firewalls but by confusion when Jaya replied, “Is this for the yoga class or the kombucha group chat?” “Her defense strategy relied heavily on poor communication,” one cybersecurity consultant laughed while installing malware protection for his mom.
Even Her iCloud Had a Tan
A trove of iCloud data included: 400 nearly identical selfies from the Senate gym A playlist titled “Legislative Bangers” Several videos of her dog doing warrior poses next to a salt lamp According to unverified rumors, a hacker group named “404Bros” tried to ransom the data, but after seeing the contents, sent a formal apology and a $15 iTunes gift card.
LinkedIn Recommendations Written by... Herself
One of the strangest discoveries in the leak? Tulsi had endorsed herself on LinkedIn for: Strategic Visioning Yogic Thought Leadership Military Telepathy Surf Diplomacy “That’s not even a real thing,” said career coach Sheila Plonk.“But I’d still hire her for the vibe.”
Ancestral Passwords and a Trail of Spiritual Cookies
Insiders say Gabbard once consulted her past-life regression therapist for password inspiration. She emerged from the session convinced her soul password was “CleopatraLives9.” She later told “Stars & Data Protection Weekly”:“We must be as secure in our online lives as we are in our truth. Unless Mercury is in retrograde, then all bets are off.”
“Don’t Blame Me, I’m a Vet” Becomes New Security Phrase
Tulsi’s go-to deflection when asked about her weak passwords?“I served this country, dammit. Let me have one unencrypted yoga blog.” Critics note this is the digital equivalent of a politician speeding through a red light and shouting, “I was in ‘The Amazing Race: Congress Edition’—I know what I’m doing.”
Eye Witness Account: Hacker Testimony from His Mom’s Basement
One teenage hacker who cracked her Dropbox said: “Honestly, I was trying to hack Roblox. But when I typed ‘Tulsi’ and ‘123,’ I accidentally got her Whole Foods receipts and a bunch of PDFs labeled ‘The Real Truth.’” He has since retired and now teaches online safety at a community center in Delaware.
The FBI’s Official Response: “We’re Too Tired for This”
An internal memo from the Bureau reportedly read: “We spent three weeks untangling this woman’s security habits. At one point, she used a Haiku as her encryption key.” Her defense?“Syllables are the safest language.”
Political Repercussions: Senators Now Forced to Change “Obama2024” to “Obama2025?”
Following the leak, Congress issued new password requirements: No campaign slogans No personal affirmations No references to enlightenment As one Republican aide lamented:“Guess I’ll have to change ‘ReaganLives’ to ‘TaxCutz4Life!’”
What the Funny People Are Saying
“Tulsi's passwords were so bad, even her spirit animal logged out.”— Sarah Silverman “Hackers were like, ‘We don’t want her emails. We just want her to stop using ‘Namaste69.’”— Dave Chappelle “Her Dropbox was 90% surfboard selfies and 10% blurry screenshots of UFOs.”— Trevor Noah “I haven’t seen this many security holes since my grandma’s knitting project.”— Jerry Seinfeld “At this point, she’s just daring China to log in.”— Chris Rock
Her Yoga App is Still Logged In on Eight Public Devices
Eyewitnesses at a Honolulu smoothie bar confirmed they could still access Tulsi’s meditation schedule, her list of mantras, and a half-written memoir titled “Shiva, Surfing & Senate Committees.” “She’s logged in on the juicer,” one barista sighed.“We know when she’s late to Pilates. The blender just starts chanting.”
Final Thoughts: It’s Not Just About Tulsi—It’s About Us
Let’s not throw our encryption stones from glass iPhones. Who among us hasn’t: Reused a password from 8th grade? Used their dog’s name and added “123”? Logged into Wi-Fi named “FBI Surveillance Van”? Tulsi’s mistakes are a national metaphor: We all want to be free spirits until someone hacks our Hulu queue.
Public Opinion Poll: What Do Voters Think?
Conducted by Spintaxi Institute for Hilarious Policy Studies“Which of the following would make a stronger password than Tulsi’s current one?” “MyExSucks42” – 37% “!@$%&” – 22% “IamTheRealPOTUS” – 18% “Password1234ButWithVibes” – 13% “HunterBidenLaptop2025” – 10%
Actionable Advice: From SpinTaxi’s Chief Tech Guru, Bleepy VonFirewall
1. Never reuse passwords. Even if they contain the word “chakra.”2. Don’t rely on your cousin for 2FA unless she’s a Navy SEAL or works at Apple.3. Your ex’s nickname is not secure just because you added a symbol.4. Enlightenment is not a firewall.5. If your password is a pun, you’ve already been hacked.
Conclusion: What Have We Learned?
We’ve learned that no matter how confident, intelligent, or mystically inclined you are, the moment you type “Tulsi2020!” into seven websites, you are officially the cybersecurity version of wearing socks with sandals. But in a world where digital threats grow daily, Tulsi’s spiritual approach to password management is a gentle reminder:The only thing worse than hackers… is hubris. And now, if you’ll excuse us, we have to go change our Netflix login from “SpinTaxiRocks69.”
Satirical Sources:
Senator Accidentally Uses Dog’s Name as Nuclear CodeCongressional Cybersecurity Training Now Includes Deep Breathing and Essential OilsHackers Demand Tulsi Return Their Time After Reading Her EmailsNational Security Council Adds “Vibes Check” to Daily Threat ReportsTulsi Gabbard Named Honorary IT Disaster of the Month by the Geek Squad Auf Wiedersehen! Want the VPN password? Ask Tulsi—it’s probably still “Mahalo123.”

SpinTaxi Magazine - A wide-aspect Toni Bohiney-style cartoon in the spirit of Mad Magazine, fold-in style. The scene shows Tulsi Gabbard sitting on a yoga mat in a tropical ... spintaxi.com
Tulsi Gabbard Named Honorary IT Disaster of the Month by the Geek Squad
Here are 15 observations inspired by the recent revelations about Tulsi Gabbard's password habits: Password123? Even my grandma knows better. Reusing passwords is like using the same key for your house, car, and office—convenient until it's not. 'Shraddha' as a password? Might as well have used 'OpenSesame'. MyFitnessPal account hacked? Guess someone wanted to know her calorie intake. Fox News Dropbox breach? Hope there weren't any dance videos in there.The Daily Beast LinkedIn compromised? Now everyone knows she endorsed herself. Using the same password since 2012? That's commitment—or laziness. No evidence of government accounts being compromised. Phew! National secrets are safe... for now. Signal group chat leak? Maybe it's time to switch to smoke signals. HauteLook account hacked? Someone's getting fashion tips on the sly. Gmail breach? Hope those cat memes weren't classified.The Daily Beast Reusing passwords is a no-no. Even toddlers have unique passcodes for their iPads. Cybersecurity 101: Don't do what Tulsi did. Seriously. Википедия — свободная энциклопедия At least she didn't write her password on a sticky note... or did she? We may never know. Lesson learned: Always use two-factor authentication. Or better yet, three. For more details on this story, you can read the full article here: Tulsi Gabbard's 'Easily Cracked' Password Habits Revealed. Read the full article
0 notes
Text
Business Email Compromise Market Insights: Industry Share, Trends & Future Outlook 2032
The Business Email Compromise Market was valued at USD 1.35 billion in 2023 and is expected to reach USD 7.24 billion by 2032, growing at a CAGR of 20.53% from 2024-2032
The Business Email Compromise (BEC) market is experiencing rapid expansion as cyber threats targeting corporate email systems continue to rise. The increasing sophistication of phishing attacks and financial fraud schemes has heightened the demand for advanced security solutions.
The Business Email Compromise market continues to grow as organizations worldwide seek enhanced cybersecurity measures. The rise of remote work, digital transactions, and data-driven communications has made businesses more vulnerable to BEC scams. As a result, cybersecurity firms and technology providers are investing heavily in AI-powered detection tools, email authentication protocols, and fraud prevention solutions to mitigate risks.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/3453
Market Keyplayers:
Acronis International GmbH (Acronis Cyber Protect, Acronis True Image)
Broadcom (Symantec Endpoint Protection, Web Security Service)
Cellopoint International Corp. (CelloPoint Mail Filtering, CelloPoint Data Protection)
Check Point Software Technologies Ltd. (Check Point Anti-Bot, Check Point Threat Prevention)
Fortra, LLC (GoAnywhere, Data Security Solutions)
GreatHorn, Inc. (GreatHorn Email Security, GreatHorn Phishing Detection)
Mimecast.com (Mimecast Email Security, Mimecast Archiving)
Proofpoint (Proofpoint Email Protection, Proofpoint Threat Response)
Tessian Limited (Tessian for Gmail, Tessian for Microsoft 365)
Trend Micro Incorporated (Trend Micro Apex One, Trend Micro Cloud App Security)
Agari Inc. (Agari Phishing Defense, Agari Email Security)
Armorblox Incorporation (Armorblox Email Security, Armorblox Threat Intelligence)
Abnormal Security Inc. (Abnormal Email Security, Abnormal Behavioral AI)
Barracuda Networks Incorporation (Barracuda Email Security, Barracuda Web Security)
Clearswift GmbH (ClearSwift Secure Email Gateway, ClearSwift Secure Web Gateway)
Cisco Inc. (Cisco Umbrella, Cisco Email Security)
Check Point Inc. (Check Point SandBlast, Check Point Endpoint Protection)
Fortinet Corporation (FortiMail, FortiGate)
GreatHorn Incorporation (GreatHorn Advanced Threat Protection, GreatHorn Digital Risk Protection)
Heimdal Security Solutions Company Ltd. (Heimdal Security Threat Prevention, Heimdal Endpoint Protection)
IRONSCALES (IRONSCALES Email Security, IRONSCALES Phishing Simulation)
Mimecast Limited (Mimecast Targeted Threat Protection, Mimecast Secure Email Gateway)
Proofpoint Inc. (Proofpoint Essentials, Proofpoint Advanced Threat Protection)
PhishLabs Corp. (PhishLabs Security Awareness Training, PhishLabs Phishing Protection)
Market Size, Share, and Scope
North America currently dominates the market due to high cybercrime rates and stringent compliance requirements.
Small and medium enterprises (SMEs) are increasingly adopting email security solutions as cybercriminals target less-protected businesses.
AI-driven threat intelligence, behavioral analysis, and multi-factor authentication are becoming essential components of BEC prevention solutions.
Market Trends
Rise in AI and Machine Learning Integration – Automated threat detection is improving real-time fraud prevention.
Growth in Cloud-Based Email Security Solutions – Increased remote work adoption has led to cloud-driven email security expansion.
Multi-Factor Authentication (MFA) Adoption – More organizations are implementing MFA to secure email communications.
Increase in Deepfake and Social Engineering Attacks – Cybercriminals are using AI-generated impersonation techniques.
Regulatory Compliance Driving Market Growth – Governments are imposing stricter cybersecurity regulations.
Rising Demand for Managed Security Services – Companies are outsourcing security monitoring to third-party specialists.
Blockchain-Based Email Authentication Solutions – Decentralized authentication is enhancing email security protocols.
Collaboration Between Enterprises and Law Enforcement – Joint efforts to combat email fraud are increasing.
Increased Cybersecurity Investment by Financial Institutions – Banks and payment platforms are prioritizing fraud detection.
Emerging Threats Targeting Supply Chains – Hackers are infiltrating B2B communications for financial fraud.
Enquiry of This Report: https://www.snsinsider.com/enquiry/3453
Market Segmentation:
By Offering
Solution
Service
By Deployment
Cloud
On-premises
By Organization Size
SMEs
Large Enterprises
By Vertical
BFSI
Government
IT and Telecommunications
Energy and Utilities
Manufacturing
Retail and E-Commerce
Healthcare
Others
Detailed Market Growth Analysis
Factors Driving Growth
Surge in Sophisticated Email Scams: Cybercriminals are refining their tactics to bypass traditional security measures.
Rising Awareness Among Organizations: Businesses are prioritizing cyber resilience strategies.
Expansion of Digital Transactions: The rise of e-commerce and digital banking has increased the attack surface.
Growing Investment in AI & Automation: Companies are leveraging AI-driven cybersecurity frameworks to enhance threat detection.
Challenges and Market Barriers
High Cost of Advanced Security Solutions – Small businesses struggle with cybersecurity investment.
Lack of Cybersecurity Expertise – Skilled professionals in BEC prevention remain in high demand.
Evolving Tactics of Cybercriminals – Hackers continuously adapt to bypass detection mechanisms.
Regulatory Complexity Across Different Regions – Compliance requirements vary across jurisdictions.
Growth and Industry Report 2032 – Size, Share & Forecast
Financial Services & Banking – High-risk industry due to transactional vulnerabilities.
Healthcare – Protecting patient data from phishing and ransomware attacks.
Retail & E-commerce – Preventing fraud in online transactions.
Government Agencies – Strengthening national cybersecurity frameworks.
Future Prospects of the BEC Market
Predicted Advancements in Email Security
AI-driven algorithms will enable real-time threat detection and risk analysis.
Organizations will prioritize zero-trust email architectures.
The role of quantum encryption in securing business communications will expand.
Advanced user behavior analytics (UBA) will identify fraudulent activities faster.
Emerging Business Opportunities
Increased Demand for Cybersecurity Consulting – Organizations will seek tailored email security solutions.
Growth in Security-as-a-Service Models – Subscription-based cybersecurity solutions will become more popular.
Enhanced Cybersecurity Regulations – Governments will enforce stricter compliance, driving market adoption.
Expansion of BEC Protection into IoT and Smart Devices – Securing corporate communications beyond traditional email platforms.
Access Complete Report: https://www.snsinsider.com/reports/business-email-compromise-market-3453
Conclusion
The Business Email Compromise market is poised for exponential growth as cyber threats continue to evolve. The increasing reliance on cloud-based communication, digital transactions, and AI-driven fraud detection will shape the industry's future. Businesses must adopt comprehensive security frameworks and leverage advanced threat intelligence to combat BEC attacks effectively. With continued technological advancements, the market will witness robust expansion by 2032, ensuring enhanced security and compliance for businesses worldwide.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
#Business Email Compromise market#Business Email Compromise market Analysis#Business Email Compromise market Growth#Business Email Compromise market Scope#Business Email Compromise market Size
0 notes
Text
How to Organize Confidential Emails Without Compromising Security
In today’s digital world, managing confidential emails securely is crucial for businesses and individuals alike. Mishandling sensitive information can lead to data breaches, phishing attacks, or compliance issues. However, with the right email management tools and best practices, you can keep your inbox organized while ensuring top-notch security. Here’s how:
1. Use Secure Email Management Tools
Investing in reliable email management tools is the first step to protecting confidential emails. These tools help categorize emails, encrypt sensitive data, and prevent unauthorized access. Look for tools that offer end-to-end encryption, spam filtering, and AI-based threat detection to enhance security.
2. Categorize and Label Sensitive Emails
A well-organized inbox ensures easy retrieval of important emails without risking exposure. Use folders and labels to categorize emails based on their sensitivity. Many email management tools allow automated tagging, which helps in streamlining confidential correspondence efficiently.
3. Enable Two-Factor Authentication (2FA)
Adding an extra layer of security with 2FA ensures that only authorized users can access your emails. Whether you’re using Gmail, Outlook, or a dedicated business email service, enabling 2FA significantly reduces the risk of unauthorized access.
4. Encrypt Emails for Enhanced Security
Encryption is key when dealing with confidential information. Use tools that offer built-in encryption or integrate third-party services to protect sensitive data. Many email management tools come with encryption features that prevent unauthorized users from intercepting your messages.
5. Avoid Public Wi-Fi for Accessing Confidential Emails
Accessing sensitive emails on unsecured networks increases the risk of cyber threats. If you must check your email on the go, use a VPN to create a secure connection and protect your data from potential hackers.
6. Regularly Audit and Delete Unnecessary Emails
Leaving confidential emails in your inbox indefinitely increases the risk of exposure. Set a routine to archive or delete emails that are no longer needed. Many email management tools offer automatic cleanup features that help in decluttering while maintaining security.
7. Train Employees on Email Security Best Practices
For businesses, human error is one of the leading causes of data breaches. Conduct regular training sessions to educate employees about phishing scams, strong password policies, and the importance of securing sensitive emails.
8. Backup Emails Securely
Regular backups help prevent data loss in case of cyberattacks or accidental deletions. Use cloud-based solutions that provide encrypted backups to ensure your confidential emails are protected at all times.
Conclusion
Organizing confidential emails without compromising security is all about adopting the right tools and best practices. By using email management tools, implementing encryption, and training employees on email security, you can safeguard sensitive information while maintaining an efficient workflow.
About Simplify360
Simplify360 is a leading AI-powered customer experience platform that helps businesses manage their emails, social media, and customer interactions seamlessly. With its secure and intuitive solutions, Simplify360 ensures efficient email management, helping organizations maintain data privacy and compliance effortlessly.
To know more about Simplify360,
Visit website: https://www.simplify360.com/ Address: 91springboard, 7th floor, Trifecta Adatto, 21, ITPL Main Rd, Garudachar Palya, Mahadevapura, Bengaluru, Karnataka 560048 Email: [email protected]
0 notes
Text
California Homelessness, Texas State Library and Archives Commission, Gmail, More: Wednesday ResearchBuzz, February 26, 2025
NEW RESOURCES State of California: Governor Newsom announces stronger accountability measures, launches new tool measuring local progress in tackling homelessness. “Today’s announcement comes alongside the debut of a new online tool accountability.ca.gov, which brings together thousands of locally reported data points to provide an accurate picture of local communities’ work to address…
0 notes
Text
This day in history

Next TUESDAY (May 14), I'm on a livecast about AI AND ENSHITTIFICATION with TIM O'REILLY; on WEDNESDAY (May 15), I'm in NORTH HOLLYWOOD with HARRY SHEARER for a screening of STEPHANIE KELTON'S FINDING THE MONEY; FRIDAY (May 17), I'm at the INTERNET ARCHIVE in SAN FRANCISCO to keynote the 10th anniversary of the AUTHORS ALLIANCE.

#20yrsago Sofa of mousepads https://web.archive.org/web/20040531234157/http://www.engadget.com/entry/4721738962773695/
#15yrsago Jesse Ventura: I could make Chickenhawk Cheney confess to the Sharon Tate murders with a waterboard https://crooksandliars.com/heather/jesse-ventura-you-give-me-water-board-dick
#15yrsago French “three-strikes” copyright law passes — but may be dead anyway https://www.laquadrature.net/en/2009/05/13/solemn-burial-for-hadopi-in-french-national-assembly/
#15yrsago Business Software Alliance says that adopting copyright treaties doesn’t decrease piracy https://www.michaelgeist.ca/2009/05/wipo-and-bsa-data/
#15yrsago The Photographer: gripping graphic memoir about doctors in Soviet Afghanistan, accompanied by brilliant photos https://memex.craphound.com/2009/05/12/the-photographer-gripping-graphic-memoir-about-doctors-in-soviet-afghanistan-accompanied-by-brilliant-photos/
#10yrsago You are a Gmail user https://arstechnica.com/information-technology/2014/05/significant-portion-of-https-web-connections-made-by-forged-certificates/
#10yrsago McDonald’s Hot Coffee lawsuit: deliberate, corporatist urban legend https://priceonomics.com/how-a-lawsuit-over-hot-coffee-helped-erode-the-7th/
#10yrsago Spurious correlations: an engine for head-scratching coincidences http://www.tylervigen.com
#10yrsago NSA sabotaged exported US-made routers with backdoors https://www.theguardian.com/books/2014/may/12/glenn-greenwald-nsa-tampers-us-internet-routers-snowden
#10yrsago Podcast: Why it is not possible to regulate robots https://ia600209.us.archive.org/28/items/Cory_Doctorow_Podcast_272/Cory_Doctorow_Podcast_272_Why_it_is_not_possible_to_regulate_robots.mp3
4 notes
·
View notes
Text
Email Client - Edison Mail
Edison Mail: The Smart Email App That Simplifies Your Inbox
In the age of overflowing inboxes, managing emails can feel like a full-time job. That’s where Edison Mail comes in—a powerful email app designed to streamline, secure, and optimize your email experience. Whether you're drowning in newsletters, spam, or important messages lost in the clutter, Edison Mail provides an all-in-one solution to help you regain control.
What is Edison Mail?
Edison Mail is a third-party email client available on iOS, Android, and Mac that integrates with multiple email providers, including Gmail, Outlook, Yahoo, and others. Its goal is simple: deliver a faster, smarter, and more organized inbox without the bloat of traditional email apps.
Key Features of Edison Mail
1. Unified Inbox for Multiple Accounts
With Edison Mail, you can add multiple email accounts and manage them all from a single inbox. No more switching between apps—everything is in one place.
2. Built-in AI Assistant
Edison Mail uses artificial intelligence to categorize and sort emails, making it easier to find important messages. Its smart assistant highlights travel details, package tracking, bills, and more.
3. Powerful Spam & Unsubscribe Features
Sick of spam emails and endless promotional messages? Edison Mail lets you unsubscribe from junk emails with a single tap, helping you keep your inbox clean. It also includes built-in spam filtering to block unwanted messages before they reach you.
4. Speed & Performance
Compared to traditional email clients, Edison Mail is known for its fast loading times and responsiveness. The app is designed to reduce lag and sync delays, making email management much smoother.
5. Enhanced Privacy & Security
Privacy is a major concern in the digital age, and Edison Mail takes it seriously. The app offers on-device processing for sensitive data, meaning your emails aren’t stored on external servers. It also has read receipt blockers to prevent senders from tracking when you open their emails.
6. Customizable Swipes & Gestures
Personalization is key, and Edison Mail allows users to set up custom swipe actions for archiving, deleting, or snoozing emails. This makes email triage more efficient and intuitive.
Why Choose Edison Mail?
If you're frustrated with bloated email apps, slow syncing, or a cluttered inbox, Edison Mail is a game-changer. It’s lightweight, intelligent, and packed with features designed to reduce email overload and improve efficiency.
Final Thoughts
Edison Mail is an excellent alternative to traditional email apps, offering a fast, smart, and secure way to manage emails. Whether you’re a professional juggling multiple accounts or someone looking for a clutter-free inbox, this app has something to offer.
Have you tried Edison Mail? Let us know your thoughts in the comments!
0 notes
Text
Podcast Sexybracket Voting: Round 5
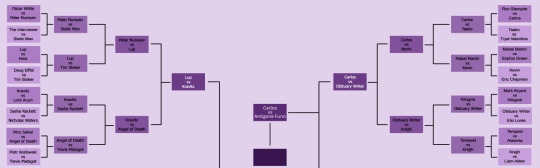
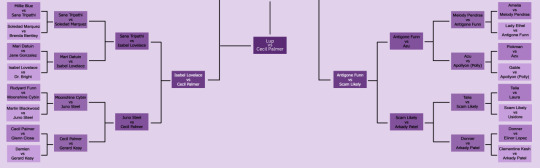
It's the semifinals folks! Out of 180+ entries and 64 Round 1 contestants, we're down to the final four.
Lup (The Adventure Zone) vs Cecil Palmer (Welcome to Night Vale)
Carlos the Scientist (Welcome to Night Vale) vs Antigone Funn (Wooden Overcoats)
How should I vote?
In this bracket, don't worry about who's most popular on Tumblr or who meets a narrow definition of "sexyman"/"sexywoman"—just vote for whoever you, personally, think is sexiest.
What is this?
The sexiestpodcastcharacter mod is attempting an act of necromancy in order to satisfy þeir curiosity about how fictionpodsexyperson's bracket would have turned out had it finished. If anyone knows the identity of the fictionpodsexyperson's pollrunner, please do not bother them about this.* Like most acts of necromancy, this was done without their permission or respect to their clear wishes to rest in peace.
Curious about what came before?
So am I. Alas, a deactivated blog is a deactivated blog. I have the preliminaries and the Round 4 polls archived on my personal blog. I can tell you that all ties were satisfied with a coin-flip, but I do not remember which polls were tied.
*If by chance fictionpodsexyperson's pollrunner is reading this themselves, and they have a copy of their poll's submissions or any other data from their poll, I would love to have a copy and can be reached via gmail under wanderingandfound.
4 notes
·
View notes
Text
Why Mail Backup X works at all levels as a Gmail backup tool
For Gmail backup, we need a tool that makes this process far more easy and judicious in comparison to manual methods. Similarly, a tool should not impose a long stretched learning curve upon users. It should make the best use of available time and resources, so that a PC does not face the brunt of overloaded resources. A tool should be ideal for routine usage, which must be supported by easily customizable settings. When you are installing this tool, or whether you are entering login details or whether you are uploading confidential files, data integrity should never be at stake due to a loopholes-ridden process. Mail Backup X duly fulfills these requirements and thus is considered as a Gmail backup tool that works at all levels.

Utmost efficiency is written all over this Gmail backup application
This tool will work wonders for your email management strategy as it can handle any amount of email data and that too without any system slowdowns or errors. You can backup an entire email account while keeping the folder hierarchy intact and you can also customize backups by choosing ideal settings. You can handpick a backup pattern that suits the context of the situation, and you also have the option to define various backup locations. These customizations can be done with palpable ease as automation is the intrinsic nature of this tool, and this ensures that various vital processes run quietly in the background without disturbing the work being currently done by you. This tool is packed to capacity with much sought after features that make it an ideal pick for Gmail backup.
This Gmail backup and restore tool puts data safety above everything else
To start with, this is a certified tool that is updated after regular intervals. It boasts of advanced features that put data safety above everything else. Every file is enveloped with multiple layers of encryption and you can further beef up this data safety mechanism by bringing password protection into the picture. Your data will not leak into false hands. Google approved login guarantees that your credentials are being entered within an environment of heightened safety. In the area of security this tool excels in every way because those recommended network security protocols are also employed to heighten that sense of safety.
This Gmail backup software has come out triumphant in making complex stuff simple for end users
This tool is a perfect merger of simplicity with sophistication and everything is so easily accessible and executable that it makes Gmail backup convenient for all user categories. Despite being stuffed to brim with latest technological advancements, this tool has braved the storm and has managed to keep things simple to the core. This easily comprehensible tool will not face any resistance from your coworkers or employees as they are not required to be mentally tortured by those long, brooding hours of training to understand its usage. You will also not face any resistance from anyone as this tool has dual compatibility with Windows and Mac. To state the truth, this is among the most adopted email management utilities. You can easily access and execute various advanced settings. This tool delivers results at breakneck pace without impeding the progress of other processes.
Gmail backup that is versatile and flexible
This tool breaks the barriers of limitations and comes to the fore with fully evolved, diverse features that entail email backup, migration, recovery and archiving. You can play around with email backups to best suit your needs by choosing various backup patterns and backup locations. Other fully evolved features of this tool encompass fast data recovery and easy maintenance of email archives in the right order and format. Wondering how to keep yourself in loop about these diverse tasks? It's actually quite simple. A live dashboard and a comprehensive mail viewer will help you to mentally jot down the status of various tasks and browse through a chockablock database of emails with ease.
Other features that present this Gmail backup and restore tool a utility of its own
This Mail Backup X Gmail email backup software provides high degree of data compression which is many times more powerful than other tools and this process is completely safe. No data element will go corrupt or missing. Even the folder hierarchy will find its rightful place in backups. As pointed earlier, this tool has an inbuilt mail viewer, which will assist you in keeping a tab over old and incoming emails. An advanced search window will pave a non-bumpy, short road for quick email search. PDF archiving is one of the star features of this tool. An exclusive FTP server will allow you to share files without any fear of things going haywire. In an nutshell, this tool is a complete solution, and you will no more be left wanting for more.
There's more to this Gmail backup tool than you can fathom
Mirror backups are also available. Users have lavished this tool with praises due to inclusion of the very useful USB snapshot feature. Dual compatibility with Windows and Mac makes this tool an unbeatable combination of telling features. Google approved login will ignite immense trust in you to proceed ahead without any worries. Since this tool falls within a very affordable price packet, users from across the globe have been able to partake in its diversity-embellished technology. Likewise, there are a zillion more reasons to embrace the cutting edge technology of this tool with full warmth.
The perfect way to take a satisfaction-boosting tour across the various nooks and corners of this tool
Start off on the right note by availing the 15 days, free trial of this tool. You will get enough exposure to the cutting edge technologies of this tool, which will prepare you well in advance to enjoy the options galore present in its full version. A real joyride is on the cards which will help you unravel the true meaning of ease of usage, excellence and flawlessness!
#Gmail#Gmail mail#Gmail email#Gmail mailbox#gmail backup#backup gmail#gmail backup software#gmail backup tool#save gmail#secure gmail#mail#mail backup#backup mail
0 notes
Text
Mac Gmail backup facility with no extra efforts on the clients’ part
To carry Gmail backup is quite important if you wish to keep your data secure. It is the methodology that you choose for the same that would determine how the experience goes for you. Before you decide on which facilities you want in the Gmail backup software you should first have thorough information about the mail account, get it here- . Avoid using a freeware as it can cause harm to your precious data and thus cause irrevocable damage.

How to Gmail backup that is regularly effective on a long term?
The Gmail backup tool that can provide the same facility to other mail clients as well- Mail Backup X is the best every software you will come across for mail backup as well as archiving. It has got several superb inbuilt qualities that keep the mail backup process quite smooth and free of hassles. Everyone can try out the software for free for Gmail email backup as a free demo version of it available here.
Gmail backup facility relevant for other mail clients as well
This software functions quite well as a Gmail backup software as well as for other major mail clients. It can be used to backup and archive data from Gmail as well as Hotmail, yahoo mail, apple mail, outcook, postbox and thunderbird. It can also be used to change the format of the data files of these mail clients as it is compatible with them all. It can be thus used to change the format of the data files to and from .eml, .rge, .pst, .olm and .mbox. This makes it quite easy to share data to various platforms.
Auto-USB backup and inbuilt ftp client
The data files stored in usb cables can be automatically updated by this software as it smartly remembers the data folder name and its location in the database. To enhance the safety of the data after the backup they are saved in the pdf form. That procedure also makes them altogether safer and more shareable. Also, they are stored in the proper sequential order so that it does not get tough to find them.
It is possible to carry both primary backup and mirror backup with this software as it comes with an inbuilt ftp client. Keeping that tool active makes it easier to have a copy of all the data ready as it keeps arriving in the system.
Intrinsic ability to save storage space and to find data files instantly
While backing up your data this software also makes sure that you never run out of storage space. It religiously backs up your data, but also makes sure that the files are compressed before being stored. Also, it gets easier for the users to find out data files as there is an ultra-fast data search facility available with it which is also relevant for complex files.
You can get either the free demo version from the link below, and later upgrade to the full version or get the full version directly from the link below www.mailbackupx.com/make-backup-of-gmail-emails/.
youtube
#gmail backup#backup gmail#gmail backup tool#backup gmail mail#gmail backup software#gmail mail backup#gmail email#Youtube
1 note
·
View note
Text
This is the best option to backup window emails with a number of features
The advantage of using outlook is that it comes compatible to Windows as well apart from Mac. So, it generates email files in the form of PST compatible window. Outlook has its own interface compatible with Windows. It is precise important to backup and restore the mails on windows outlook. You can learn more about windows backs and restore through the below link so that I can discuss the different features on how to backup windows emails.

I used Mail Backup X by InventPure for my Windows 8 with a bunch of incredible features. The download version of this tool comes for 32bit and 64bit processor so you can suit yourself according to the system you are using.
This is the best way to backup windows emails along with a number of features.
The tool can backup Outlook for Windows
The tool works on the platform of incremental backup support system as they mail arrives. No matter you work for windows outlook, the tool can backup Windows emailsvery easily.
It can import stored mails
If you plan for windows backup and restore, you can also import mail archive files exported from other mail clients like Outlook 2011 or 2016 Archive), eml files etc.
The tool has an inbuilt mail viewer
The tool comes with an inbuilt mail viewer in order to have a look at the archived emails without switching between multiple mail clients.
An advanced search option
The feature of advanced search module allows you to search emails from any particular person, subject or with a specific word in the entire database. Also, you can search for specific mails with attachments using AND and OR logics in the tool.
Organize Archive Mails in a PDF format
A very convenient option to archive al your mails as PDF retaining the folder structure. It creates a future proof and accessible account for all the archived mails. Also, protects the inbound and outbound mail messages from personal or business mail accounts suited for printing purpose.
Compresses the files for extra storage
The toolmakers uses a high compression algorithm, which is specially design to secure the mail data. It compresses and extracts the files reducing to required storage place. The tool also supports repair recovery record in case of any hardware corruption so that you may not end up losing any data.
All in one conversion mail tool
The tool gets you the freedom to move from different mail clients to mail client of your choice. It includes the format like (.pst, .eml) supported by all popular Mail clients like Outlook Windows, Office 365, Gmail, Yahoo.
Auto USB Backup Sync
The tool has an in-built auto USB backup feature where you can just map a USB drive to copy a backup of mails. The tool plays a smarter role in detecting when the drive is plug in and where to copy the data on that drive. For more information to backup windows, simply log on to the below link www.mailbackupx.com/windows-email-backup-tool/.
Video Tutorial to backup Windows mail with Step by Step Guide
youtube
1 note
·
View note
Text
Know the details of Thunderbird backup email here
In order to keep one’s data safe and updated it is vital that one carries Thunderbird backup email on a regular basis. The process however can be complicated and even induce data safety concerns. With the availability of several third-party software, people have given over the idea of manual backup and archiving. However, even with the availability of such software, it is important that one checks them for their reliability and compatibility with data. The first thing you can do in that direction is to educate yourself about Thunderbird, check here- https://en.wikipedia.org/wiki/Mozilla_Thunderbird.
Thunderbird email backup service in alignment with your requirements

You can backup mail Thunderbird with Mail Backup X and carry a lot of associated tasks with it at no extra cost. It is priced quite reasonably considering how wide-ranging the facilities it provides are. It is also quite safe for all types of data, is compatible with all sorts of mail file formats to. To ensure that the user feels safe using this Thunderbird email backup tool it has been designed to work in the offline mode.
How to restore Thunderbird mail backup without moving your fingers
One does not have to be adept at the task of Thunderbird email backup in order to carry it regularly. Using this software on a regular basis will provide the desired results. Also important is the capacity of this software to backup and archive data not only from Thunderbird but from Gmail, Hotmail, apple mail, yahoo mail, outlook, and postbox.
Closely associated with the ability of this software to backup and archive data from various sources is the integrated mail viewer. In order to work with data from several sources one would not have to skip continuously from one platform to another, the mail viewer makes sure of that. It works by bringing data from various sources at one place.
Convert mail file formats and use ftp client for additional safety
As this software supports several mail file formats it is also capable of providing the facility of changing mail file formats. It can be used to change the format of the data files to and from .olm, .eml, .pst, .mbox, and .rge.
The ftp client on the other hand makes sure that one can carry backup of data on a regular basis without themselves intervening. The ftp client continuously backs up data and provides the facilities of primary backup and mirror backup as well.
Faster search results and more storage space
With this software you will have the freedom to backup as many files as you want since it meanwhile also saves storage space. It manages to do that by compressing the files methodically.
One does not have to waste time looking for even a bit of data. The ultra-fast data search module can find out any variety of data within nanoseconds.
You can try these features out immediately by purchasing the software. A free demo version of it is also available www.mailbackupx.com/thunderbird-backup-email/.
1 note
·
View note
Text
Restore email mac mails with zero tolerance data integrity
Data integrity is often misjudged when it comes restore mac email. It is about overall accuracy, completeness and consistency of data. So whenever, data transfer takes place, the tool is expected to transfer or convert eh files with completeness and accuracy.
A non-accurate or incomplete transfer of data means the file is unreadable or unrecognizable or broken. In worst cases, the data files transfer or conversion does not take place.
This makes it very crucial to use a highly skilled restore mac email tool for an efficient transfer with zero tolerance data integrity.
We deliver a highly skilled and well-engineered product Mail Backup X. The one of its own kind to restore email mac mails. A tool that maintains hundred percent data integrity and also restore mac email addresses.
The factor is also visible in the applications of the restore mac email app delivering complete data file without any deviation.
Different particulars are transferred while taking backup of emails from Mac. Therefore. We also make sure that mac users undergo the information on Mac OS and Apple mail for a detailed tour on different aspects of them. So, it is advisable to browse the below links on Mac OS and Apple mail for more information.
Maintain data integrity factor in various applications that restore mac emails
It is indicative of the fact that different applications of this restore mac email software preserves data integrity while taking backup of emails from Mac.
The third party mail archive application supports reading and import of common mail archives file formats like .mbox, .rge, .olm, .olk, .pst, .eml, that store mail data by mail clients like Outlook Mac, Outlook Windows, Office 365, Thunderbird, Postbox, Gmail, Yahoo etc.
The inbuilt mail archive application allows you to view important mails from different mail clients. The product allows you to read and import archive files from Mbox viewer, RGE viewer, OLM viewer, OLK viewer, PST viewer, EML viewer without the need to switch between or open mails with different mail clients.
The third application of inbuilt mail migration application is an advanced mail conversion feature to use mail client of your choice on Mac OS. It permits you convert and export mail data to all major mail data file formats like .mbox, .rge, .olm, .pst, .eml.
Test the tool to explore the best way to restore mac email
The best way to explore the data integrity factor is by testing the tool for a realistic experience.

All you need is to download the demo version of the restore mac email tool and on Mac. Use it for 15 days until the validity expires.Switch to the licensed version of the tool, once satisfied.
For complete access of the product, you can click on the licensed version of the tool along with a product key.
For more details on the software, log on to the below website and get all your queries answered in a systematic manner www.mailbackupx.com/restore-mac-email/.
#mac restore tool#mac mail restore#restore mac mailbox#restore mac folder#restore mac data#restore mac files#restore mac email
1 note
·
View note