#restore mac data
Explore tagged Tumblr posts
Text
Restore email mac mails with zero tolerance data integrity
Data integrity is often misjudged when it comes restore mac email. It is about overall accuracy, completeness and consistency of data. So whenever, data transfer takes place, the tool is expected to transfer or convert eh files with completeness and accuracy.
A non-accurate or incomplete transfer of data means the file is unreadable or unrecognizable or broken. In worst cases, the data files transfer or conversion does not take place.
This makes it very crucial to use a highly skilled restore mac email tool for an efficient transfer with zero tolerance data integrity.
We deliver a highly skilled and well-engineered product Mail Backup X. The one of its own kind to restore email mac mails. A tool that maintains hundred percent data integrity and also restore mac email addresses.
The factor is also visible in the applications of the restore mac email app delivering complete data file without any deviation.
Different particulars are transferred while taking backup of emails from Mac. Therefore. We also make sure that mac users undergo the information on Mac OS and Apple mail for a detailed tour on different aspects of them. So, it is advisable to browse the below links on Mac OS and Apple mail for more information.
Maintain data integrity factor in various applications that restore mac emails
It is indicative of the fact that different applications of this restore mac email software preserves data integrity while taking backup of emails from Mac.
The third party mail archive application supports reading and import of common mail archives file formats like .mbox, .rge, .olm, .olk, .pst, .eml, that store mail data by mail clients like Outlook Mac, Outlook Windows, Office 365, Thunderbird, Postbox, Gmail, Yahoo etc.
The inbuilt mail archive application allows you to view important mails from different mail clients. The product allows you to read and import archive files from Mbox viewer, RGE viewer, OLM viewer, OLK viewer, PST viewer, EML viewer without the need to switch between or open mails with different mail clients.
The third application of inbuilt mail migration application is an advanced mail conversion feature to use mail client of your choice on Mac OS. It permits you convert and export mail data to all major mail data file formats like .mbox, .rge, .olm, .pst, .eml.
Test the tool to explore the best way to restore mac email
The best way to explore the data integrity factor is by testing the tool for a realistic experience.

All you need is to download the demo version of the restore mac email tool and on Mac. Use it for 15 days until the validity expires.Switch to the licensed version of the tool, once satisfied.
For complete access of the product, you can click on the licensed version of the tool along with a product key.
For more details on the software, log on to the below website and get all your queries answered in a systematic manner www.mailbackupx.com/restore-mac-email/.
#mac restore tool#mac mail restore#restore mac mailbox#restore mac folder#restore mac data#restore mac files#restore mac email
1 note
·
View note
Link
if you want to Restore Data from FireWire External Drive on Mac then we suggest you to read this written article.
0 notes
Text

TECHNOLOGY ID PACK

NAMES︰ admin. ajax. alexa. am. atari. audio. auto. bailey. binary. blank. blu. blue. bluesse. browser. browsette. bug. byte. cache. calware. chip. circe. click. clicker. clickie. clicky. cloud. coda. code. codette. codie. cody. computette. crypt. cursor. cy. cyber. cybernet. cybernetica. cyberweb. cypher. cypherre. data. dell. digi. digitalia. digitelle. digitesse. disc. dot. electronica. electronique. emoticon. emoticonnie. fax. file. gig. gizmo. glitch. glitche. glitchesse. glitchette. graphique. hacker. hal. halware. hijack. index. informationne. intelligette. internette. interweb. java. javascript. juno. key. link. linuxe. lotus. lovebytes. mac. mal. malakai. malware. malwaria. memorette. memorie. meta. mic. micah. mickey. morphe. mouse. mousette. myspace. nano. neo. net. netette. nett. netty. paige. pascal. payton. peyton. pixel. programatha. programette. programme. pulse. reboot. rom. router. ruby. sam. sammy. screene. screenette. sean. shock. solitaire. spy. static. stutter. talia. tap. tecca. tech. techette. tessa. tetris. trojan. troubleshoot. ts. user. vir. virus. virusse. volt. vyrus. webbe. wheatley. whirr. widget. will. wirehead. wiresse. zap. zett. zetta. zip.

PRONOUNS︰ ai/ai. alt/alt. anti/antivirus. arc/archive. audio/audio. bat/battery. beep/beep. beep/boop. bit/bit. bit/byte. blue/blue. board/board. bright/bright. brow/browser. browser/browser. brr/brr. bu/bug. bug/bug. buzz/buzz. byt/byte. byte/byte. c/cpu. charge/charger. cir/circuit. cli/click. click/clack. click/click. click/scroll. co/code. code/code. color/color. com/com. com/computer. comp/computer. compute/computer. computer/computer. cor/corrupt. corrupt/corrupt. CPU/CPU. crash/crash. cre/creeper. crtl/crtl. cy/cyber. cyb/cyber. cyber/cyber. da/data. data/data. delete/delete. di/disk. dig/digital. digi/digi. digi/digital. digital/digital. dra/drag. e/exe. electronic/electronic. enter/enter. er/error. err/error. error/error. exe/exe. fi/file. file/file. gi/gif. gli/glitch. glit/glitch. glitch/glitch. graphic/graphic. hac/hacker. hack/hack. hard/hardware. head/phone. hij/hijacker. ho/home. info/info. information/information. int/internet. intelligent/intelligence. intelligent/intelligent. inter/net. internet/internet. it/it. jpg/jpg. key/board. key/cap. key/key. key/keyboard. key/keylogger. lag/lag. lap/laptop. ligh/light. linux/linux. load/load. log/login. main/mainframe. mal/malware. me/media. memory/memorie. mon/monitor. mou/mouse. nano/nano. net/net. net/network. org/org. over/overwrite. page/page. pix/pix. pix/pixel. pixel/pixel. plu/plug. png/png. pop/popup.��port/port. pow/power. pro/program. program/program. ram/ram. ran/ransom. reboot/reboot. reload/reload. res/restore. ret/retro. route/router. sca/scan. scr/scroll. scre/screen. scre/screencap. scree/screen. screen/screen. scri/script. script/script. sentient/sentience. shift/shift. site/site. skip/skip. soft/software. spa/spam. space/space. spy/spyware. stop/stop. te/tech. tech/nology. tech/tech. technology/technology. tou/touchpad. txt/txt. typ/type. upload/upload. user/user. vi/viru. vi/virus. vir/virtual. web/page. web/web. whir/whir. wi/wire. win/dow. win/window. wire/wire. wire/wired. zip/zip . ⌨ . ☣ . ⚙ . ⚠ . 🎞 . 🎨 . 🎭 . 🎮 . 🎵 . 👀 . 👁 . 💔 . 💡 . 💢 . 💣 . 💳 . 💵 . 💻 . 💽 . 💾 . 💿 . 📀 . 📱 . 🔇 . 🔈 . 🔉 . 🔊 . 🔋 . 🔌 . 🔎 . 🖥 . 🖱 . 🗡 . 🗯 . 🛠 . 🧿 .

#pupsmail︰id packs#id pack#npt#name suggestions#name ideas#name list#pronoun suggestions#pronoun ideas#pronoun list#neopronouns#nounself#emojiself#techkin#robotkin#internetkin
458 notes
·
View notes
Note
okay so like I know you already have a lot of requests and I already sent one for malware mac so you can totally ignore this if you want
But like imagine one day your just working on your computer and suddenly there's a glitch or something and the whole PC data is wiped out, and while you try to recover your data and restore your computer back to normal.
mac just doesnt know you like thinks your a new user or something like amnesia and while your working on trying to fix Mac and your computer they just fall in love with you again (like in those cheesy memory loss fic) It can end in whatever you think is best
BUT LIKE DO YOU SEE MY VISON LIKE IM COOKING TRUST LIKE YOU GET ME RIGHT??
i have to reply to this because i have to let you know��� that YOURE COOKING.
I SEE IT I SEE IT.

this is such a cute idea. i’m on the floor crying.
#veryfruity asks#THIS IS AWESOME#WRITING THIS ON MY NOTES#GET ME IN THERE#your mind.#it’s too powerful.
9 notes
·
View notes
Text
Buy Apple ID Accounts What Is Apple ID Accounts?Buy Apple ID Accounts. An Apple ID is a user account that allows access to various Apple services and products, such as the App Store, iCloud, iTunes, Apple Music, and more. It serves as a single sign-in across all Apple devices and services. The account is tied to the user’s email address and is used to manage personal information, make purchases, and synchronize data across devices like iPhones, iPads, Macs, and more.Key features of an Apple ID account include:Access to Apple Services: With an Apple ID, users can access Apple services like iCloud for data storage, Apple Music for streaming, iTunes for media purchases, and the App Store for downloading apps.Device Synchronization: Apple ID allows users to sync their settings, photos, contacts, and apps across all their Apple devices using iCloud.Security Features: Apple ID comes with security features like two-factor authentication (2FA) to protect against unauthorized access.Purchase Management: Users can store payment information and make purchases through Apple’s digital stores, including apps, music, movies, and other content.Backup and Recovery: With iCloud, Apple ID provides a way to back up device data and restore it if the device is lost or replaced.Find My iPhone/Mac: This feature helps users locate their devices in case they are lost or stolen by using their Apple ID credentials.Essentially, an Apple ID acts as a digital identity within Apple’s ecosystem, allowing seamless use of Apple’s hardware, software, and services.
24 Hours Reply/Contact Telegram: @smmvirals24 WhatsApp: +6011-63738310 Skype: smmvirals Email: [email protected]
2 notes
·
View notes
Text
What Is Apple ID Accounts?
Buy Apple ID Accounts. An Apple ID is a user account that allows access to various Apple services and products, such as the App Store, iCloud, iTunes, Apple Music, and more. It serves as a single sign-in across all Apple devices and services. The account is tied to the user’s email address and is used to manage personal information, make purchases, and synchronize data across devices like iPhones, iPads, Macs, and more.
Key features of an Apple ID account include:
Access to Apple Services: With an Apple ID, users can access Apple services like iCloud for data storage, Apple Music for streaming, iTunes for media purchases, and the App Store for downloading apps.
Device Synchronization: Apple ID allows users to sync their settings, photos, contacts, and apps across all their Apple devices using iCloud.
Security Features: Apple ID comes with security features like two-factor authentication (2FA) to protect against unauthorized access.
Purchase Management: Users can store payment information and make purchases through Apple’s digital stores, including apps, music, movies, and other content.
Backup and Recovery: With iCloud, Apple ID provides a way to back up device data and restore it if the device is lost or replaced.
Find My iPhone/Mac: This feature helps users locate their devices in case they are lost or stolen by using their Apple ID credentials.
Essentially, an Apple ID acts as a digital identity within Apple’s ecosystem, allowing seamless use of Apple’s hardware, software, and services.
24 Hours Reply/Contact Telegram: @smmvirals24 WhatsApp: +6011-63738310 Skype: smmvirals Email: [email protected]
2 notes
·
View notes
Text
Complete Guide to Disable Find My iPhone on iOS 10 Without Any Password
Disabling Find My iPhone on iOS 10 without any password can often seem like a daunting task, particularly if you’ve forgotten the Apple ID associated with your device. Apple's security measures are designed to protect user data, which can make the process feel intimidating. However, there are legitimate reasons for wanting to turn off this feature, such as when selling or giving away your device or dealing with a locked iPhone that you no longer use. This comprehensive guide aims to equip you with the necessary steps to navigate this challenge smoothly and effectively, focusing specifically on disabling Find My iPhone on iOS 10 without any password.
In this article, we will explore various methods to disable Find My iPhone on iOS 10 without any password required. From utilizing recovery options to employing specialized tools, we will outline the strategies you can employ to regain control over your device. Whether you’re a tech novice or a seasoned user, our step-by-step instructions will help ensure that you can disable this feature safely and effortlessly. By the end of this guide, you will have the confidence and knowledge to manage your iOS device and its security settings with ease, all while successfully disabling Find My iPhone on iOS 10 without any password.
What is Find My iPhone?
Find My iPhone is a robust feature developed by Apple that helps users locate, manage, and secure their Apple devices, including iPhones, iPads, Macs, Apple Watches, and AirPods. It is part of the larger Find My service, which combines location tracking for all Apple devices associated with an Apple ID. Below is a detailed overview of its functionalities, features, and requirements:
Key Features:
Location Tracking: Users can see the current location of their device on a map. If the device is nearby, they can play a sound to help locate it.
Lost Mode: If the device is lost or stolen, users can enable Lost Mode, which locks the device and displays a custom message with a contact number on the screen.
Remote Erase: In case of theft or loss, users can remotely erase all data on the device to protect their personal information.
Find Other Devices: Besides iPhones, Find My can also locate iPads, Macs, Apple Watches, and AirPods.
Activation Lock: When Find My iPhone is enabled, it also activates a security feature that prevents anyone from using the device without the owner’s Apple ID and password, making it harder for thieves to access or sell the device.
Why To Disable Find My iPhone on iOS 10?
Disabling Find My iPhone on iOS 10 can be useful in certain situations where you need to remove the security feature. Below are some common reasons why users might disable it, along with important considerations.
Preparing to Sell or Transfer the Device
If you're planning to sell, gift, or transfer your iPhone to someone else, it's crucial to disable Find My iPhone before doing so. This step is necessary to remove your Apple ID from the device and disable Activation Lock, which ties the iPhone to your Apple ID. Without disabling this feature, the new owner would be unable to access or use the iPhone fully, as they would need your Apple ID credentials to unlock it.
Restoring or Resetting the Device
When you need to perform a full restore or reset on your iPhone, whether for troubleshooting or preparing the device for resale, Find My iPhone must be turned off. iTunes or Finder on a Mac will not allow a full factory reset or software restore if Find My iPhone is enabled because of the Activation Lock feature, which is designed to prevent unauthorized use of the phone.
Without disabling Find My iPhone, any attempt to restore the phone would be halted, requiring you to first enter your Apple ID password to proceed with the process.
Troubleshooting and Repairs
Certain troubleshooting steps and repairs may also require disabling Find My iPhone. For example, if your iPhone encounters a serious issue and you need to restore it via recovery mode, the process won't fully work unless Find My iPhone is disabled first. Additionally, some third-party repair services may require it to be turned off before working on the device to ensure they can perform necessary functions like hardware testing or software restoration.
Reducing Battery Drain
Although less common, some users may disable Find My iPhone to reduce battery drain, particularly if location services are frequently active. Since Find My iPhone relies on tracking the device's location using GPS and other location services, it can cause a minor increase in battery usage. For users who don't find themselves frequently needing the feature, turning it off might help conserve battery power.
Disable Find My iPhone on iOS 10 With Passixer:
Here’s a simple and effective method to disable Find My iPhone on iOS 10 without any password with Passixer, using a trusted iOS unlocking tool like Passixer iPhone Unlocker and a reliable USB cable. This solution is perfect for users looking for a straightforward way to unlock their devices without hassle.
Passixer iPhone Unlocker is an intuitive application designed specifically for iPhone and iPad users who need to bypass security features effortlessly. Whether you’ve forgotten your passcode or need to dissociate an old Apple ID, this powerful software can effectively disable the Find My iPhone feature without the need for the original password. This capability is particularly advantageous for individuals purchasing second-hand devices still linked to a previous owner’s Apple ID.
Key Features
Unlock Any iOS Screen Lock: Easily removes screen locks like 4-digit/6-digit PINs, Face ID, and Touch ID, ensuring you can regain access to your device without complications.
Remove Apple ID Without Password: Unlink an Apple ID without needing the original password, enabling seamless access to all Apple services. This is especially helpful for users with second-hand devices still linked to a previous owner’s Apple ID.
Bypass iCloud Activation Lock: With Passixer, you can bypass the iCloud Activation Lock, simplifying the process of using previously owned devices.
Remove MDM Lock: This software offers two methods to remove Mobile Device Management (MDM) restrictions from devices that belong to companies or educational institutions, without needing passwords or jailbreaking.
Remove Screen Time Passcode: Quickly bypass the Screen Time passcode while ensuring no data is lost, making it ideal for managing family devices.
Remove iTunes Backup Encryption: Access encrypted iTunes backup passwords to retrieve your backup data without risk of information loss.
Device Compatibility: Supports a wide range of devices, including iPhone 4 to iPhone 15, all iPads, and iPod Touch models, and is compatible with iOS 17 and earlier versions.
Cross-Platform Support: Passixer works seamlessly on Windows (11/10/8.1/8/7) and Mac (OS X 10.7 and later, including macOS Big Sur and Monterey).
How To Use:
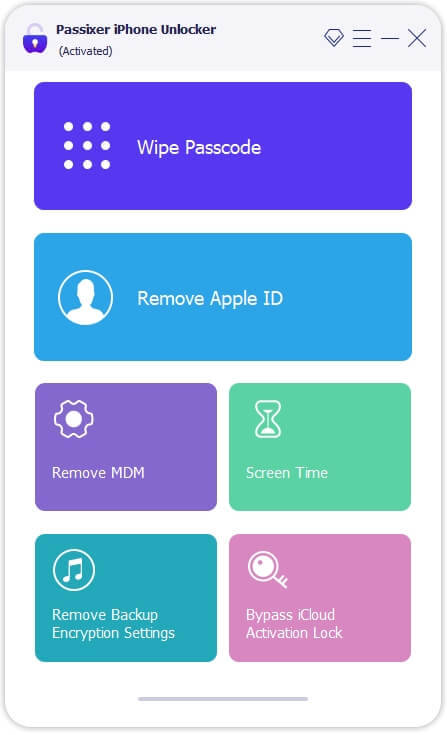
Step 1: Download and Install Passixer
Head to the official Passixer website to download the program. Complete the installation and launch the software, then select "Remove Apple ID" from the main menu.
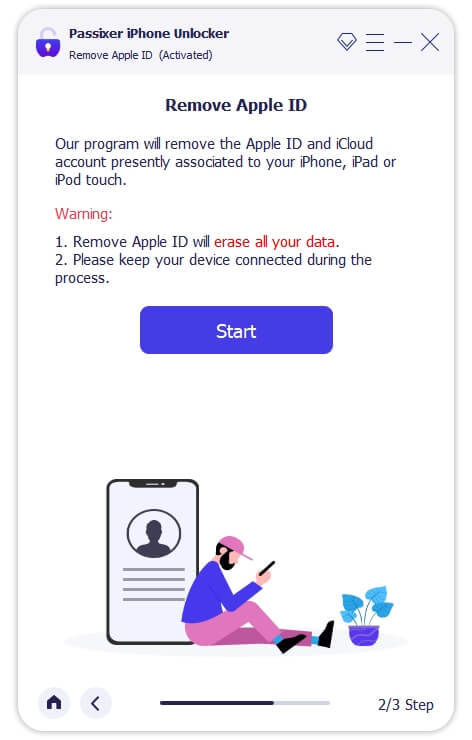
Step 2: Connect Your iPhone
Use a USB cable to connect your iPhone (with Find My iPhone enabled) to your PC or Mac. Click "Start" in the software to initiate the unlocking process.
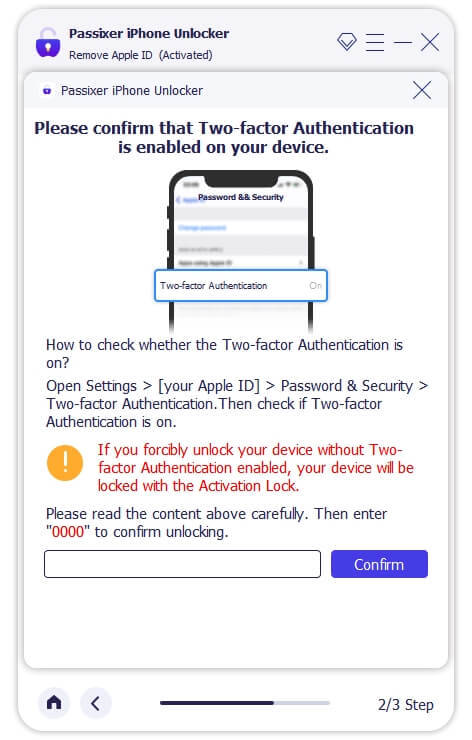
Step 3: Remove Your Apple ID
For iPhones running iOS 11.4 or later, ensure that Two-Factor Authentication is enabled. Verify device information, download the required firmware, and start the Apple ID removal process. This will also automatically deactivate the Find My iPhone feature.
Reset your iPhone settings by opening the Settings app, navigating to General, and selecting Reset > Reset All Settings. Once completed, Passixer will unlink the associated Apple ID.
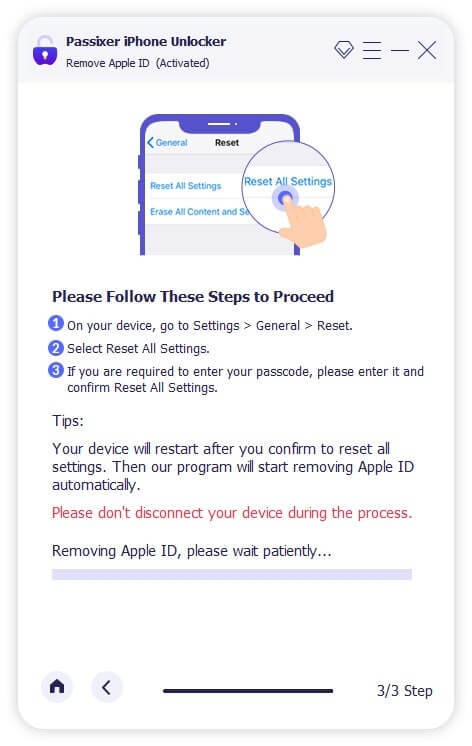
Disabling your Apple ID on an iPhone will also automatically turn off the Find My iPhone feature.
Pros:
No Password Needed: Removes the Apple ID without needing the original password, making it perfect for second-hand devices.
Bypasses Activation Lock: Unlocks iCloud Activation Lock to access devices linked to another user’s Apple ID.
Versatile: Also removes screen locks, bypasses MDM restrictions, and disables Screen Time passcodes without erasing data.
Broad Device Compatibility: Supports a wide range of devices, from iPhone 4 to iPhone 15, as well as iPads and iPod Touch devices.
Cross-Platform Availability: Works on both Windows and Mac.
Cons:
Costs Involved: While some versions offer free trials, full functionality typically requires a paid version.
Pricing Plan:
Enjoy secure and immediate email delivery, along with complimentary customer support. This software is designed specifically for Mac users.
Pricing Options: Select from the following plans: a 1-year license for $39.99, a 1-month license for $29.99, or a one-time lifetime license for $69.99. Each plan allows you to unlock up to 6 iOS devices on a single PC (taxes not included).
Discount Offers: Get up to $20 off on the 1-year and 1-month licenses, with original prices being $59.99 and $39.99, respectively.
Other Ways To Disbale Find My iPhone on iOS 10
Disabling Find My iPhone on iOS 10 without a password can be a complex process due to Apple's robust security measures. However, if you find yourself in a situation where you need to disable this feature, there are several methods you might consider. Below are detailed step-by-step instructions for each method, along with important considerations.
Method 1: Restore via iTunes
Requirements:
A computer with iTunes installed.
A USB cable to connect your iPhone to the computer.
How To Use:
Install iTunes: Make sure you have the latest version of iTunes installed on your computer. You can download it from the Apple website.
Connect Your iPhone: Use a USB cable to connect your iPhone to the computer. Launch iTunes once your device is connected.
Put iPhone into Recovery Mode:
For iPhone 6s and earlier: Press and hold the Home button and the Power button simultaneously until you see the recovery mode screen.
For iPhone 7 and 7 Plus: Press and hold the Volume Down and the Power buttons until you see the recovery mode screen.
For iPhone 8 and later: Quickly press and release the Volume Up button, then the Volume Down button, and finally press and hold the Side button until you see the recovery mode screen.
Restore iPhone: In iTunes, a message will appear indicating that a device in recovery mode has been detected. Choose the option to Restore. This will erase all content and settings from your iPhone, including the Find My iPhone setting.
Set Up iPhone: After the restore is complete, you can set up your iPhone as new or restore from a backup. Note that if Find My iPhone is still activated, it may ask for the Apple ID and password associated with the device.
Method 2: Jailbreak the Device
Warning: Jailbreaking voids your warranty and can expose your device to security risks. Use this method with caution.
Requirements:
A computer with a jailbreaking tool (e.g., Pangu, unc0ver).
How To Use:
Backup Your Data: Before attempting to jailbreak, make sure to back up your data using iTunes or iCloud, as this process may erase your device.
Download Jailbreaking Tool: Download a reputable jailbreaking tool that is compatible with iOS 10.
Connect Your iPhone: Use a USB cable to connect your iPhone to your computer.
Run the Jailbreaking Tool: Launch the jailbreaking software and follow the on-screen instructions to initiate the jailbreak. This usually involves clicking a button to start the process.
Complete the Jailbreak: Once the jailbreak is complete, your device will restart. You may need to install a Cydia app for further customization.
Disable Find My iPhone: After jailbreaking, you can use certain tweaks in Cydia to disable Find My iPhone. Search for relevant tools and follow their instructions.
Method 3: Contact Apple Support
How To Use:
Gather Documentation: Collect any documents that prove your ownership of the device, such as the original receipt or invoice.
Contact Apple Support: Visit the Apple Support website or call their support line. Explain your situation and provide the necessary documentation.
Follow Their Instructions: Apple Support may guide you through the process of disabling Find My iPhone. They may ask for your device's serial number and other identifying information.
Wait for Resolution: Depending on your situation, Apple may take some time to resolve the issue. Follow up as needed.
Conclusion:
In conclusion, disabling Find My iPhone on iOS 10 without a password may seem like a challenging endeavor, but with the right tools and guidance, it can be achieved effectively. Understanding the various legitimate reasons for wanting to disable this feature—such as preparing a device for sale, performing a factory reset, or troubleshooting issues—helps users navigate the process with purpose. By utilizing specialized tools like Passixer or following alternative methods, individuals can confidently regain access to their devices and manage their settings without the burden of forgotten passwords.
Ultimately, the key takeaway from this guide is that while Apple's security measures are designed to protect user data, there are practical solutions available for those in need. Whether you're a tech novice or an experienced user, our comprehensive instructions empower you to tackle this challenge head-on. By following the steps outlined in this guide, you can disable Find My iPhone on iOS 10, ensuring a smooth transition as you either pass on your device or regain control over it. With the right approach and resources, you can successfully navigate the complexities of Apple’s security features and regain full access to your device.
2 notes
·
View notes
Text
Microsoft Outage: CrowdStrike and the 'Blue Screen of Death' Affecting Users Worldwide

photo microsoft
Global Impact
Microsoft Windows users across the globe, including those in India, Australia, Germany, the United States, and the UK, are experiencing a critical issue leading to the infamous 'Blue Screen of Death' (BSOD). This problem causes systems to restart or shut down automatically. Notably, companies like Dell Technologies have attributed this crash to a recent update from CrowdStrike, although Microsoft has yet to confirm this as the root cause of the outage.
Affected Sectors
The outage, which began Thursday evening, primarily impacted Microsoft's Central US region. Essential systems for numerous airlines were crippled, affecting American Airlines, Frontier Airlines, Allegiant, and Sun Country in the US, as well as IndiGo and other airlines in India. Additionally, the disruption extended to banks, supermarkets, media outlets, and other businesses, highlighting the significant reliance on cloud services for critical infrastructure.
CrowdStrike: An Overview
CrowdStrike is a prominent cybersecurity platform that offers security solutions to both users and businesses. It employs a single sensor and a unified threat interface with attack correlation across endpoints, workloads, and identity. One of its key products, Falcon Identity Threat Protection, is designed to prevent identity-driven breaches in real time.
The Issue with CrowdStrike's Update
Reports indicate that a buggy update caused CrowdStrike’s Falcon Sensor to malfunction and conflict with the Windows operating system. This has led to widespread BSOD errors. CrowdStrike has acknowledged the problem, stating, “Our Engineers are actively working to resolve this issue and there is no need to open a support ticket.” The company has promised to update users once the issue is resolved.
Microsoft's Response
Microsoft confirmed that the Azure outage was resolved early Friday. However, this incident serves as a stark reminder of the potential consequences when critical infrastructure heavily relies on cloud services. The outage underscores the need for robust and reliable cybersecurity measures to prevent such widespread disruptions in the future.
Understanding the Blue Screen of Death
The Blue Screen of Death (BSOD) is a critical error screen on Windows operating systems that appears when the system crashes due to a severe issue, preventing it from operating safely. When a BSOD occurs, the computer restarts unexpectedly, often resulting in the loss of unsaved data. The error message typically states, “Your PC ran into a problem and needs to restart. We are just collecting some error info, then we will restart for you.”
This type of error is not exclusive to Windows; similar issues can be seen across Mac and Linux operating systems as well.
While the exact cause of the widespread BSOD errors remains unclear, the incident highlights the interconnectedness and vulnerability of modern digital infrastructure. Both Microsoft and CrowdStrike are working to resolve the issues and restore normalcy to affected users and businesses worldwide.
2 notes
·
View notes
Text
It would be kind of nice to have NixOS or Guix declarations for all these machines but I just can't get into it (yet). I'll try on my mom's macbook once i have a reliable way to recover all her data (she's dead but I'd like to be able to restore how her computer was, in less than an hour).
Had absolutely negative luck with booting macos on a VM so far, let alone transferring data. I do have a Time Machine backup (mostly readable on Linux plus u can boot a Mac from it), and a dd image of the whole drive. It's PROBABLY safe to just wipe the thing and restore it later - but what if it's not? What will I do if I lose all those nasty tradcath propaganda emails and copies of copies of excel sheets?
3 notes
·
View notes
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] From the manufacturer Why Choose One Touch Hub? Connect Your World Front-facing intelligent USB-C and USB 3.0 ports offer easy access for connecting and recharging devices — even if your computer is off. Abundant Capacity Tons of room to store countless photos, videos, files, and more. Password Protected The perfect external hard drive with USB hub to secure your digital life. Cross-Platform Out-of-the-box compatibility with Windows and Mac computers. Backup Your Way Includes Seagate Toolkit backup software for one-click and scheduled backups and file mirroring. DROPBOX BACKUP PLAN Automatically back up one computer and one external drive with a 6-month free trial of the Dropbox Backup plan. Keep a copy of your files in the cloud and quickly restore any accidentally deleted data. (Not available in all areas, including China. For new customers and existing Dropbox Basic users only.) Mylio Create Enjoy a six-month complimentary subscription to Mylio Create — an intuitive and powerful app that helps organise photos into a life calendar and offers easy protection, editing, sharing and syncing across multiple devices. (Must redeem within 1 yr of drive registration. Not available in all countries.) We’ve Got Your Back When the unexpected happens — Rescue Services help you defend against data loss and retrieval costs so you can rest easier.
Add to Cart Add to Cart Customer Reviews 3.6 out of 5 stars 18 4.3 out of 5 stars 2,079 4.4 out of 5 stars 19,916 Price — no data ₹51,999.00₹51,999.00 ₹11,299.00₹11,299.00 Max Capacity Up to 20TB Up to 18TB Up to 5TB Extra Ports 2 0 0 Works with Windows/Mac (exFAT) Windows/Mac (exFAT) Windows/Mac (exFAT) Connects with USB 3.2 Gen 2 (USB-C), USB 3.0 USB 3.0 USB 3.2 Gen 2 (USB-C), USB 3.0 Customizable Backup Yes No Yes Password Encryption Yes No Yes Rescue Data Recovery Services Yes Yes Yes Mylio Create plan Yes No Yes A front-facing USB C and USB 3.0 port for connecting and recharging devices—even if your computer is off Password-protected external hard drive with USB hub to secure your digital life Out-of-the-box compatibility with Windows and Mac computers Includes Seagate Toolkit backup software for one-click and scheduled backups and file mirroring Enjoy long-term peace of mind with the included 3-year limited warranty and 3-year Rescue Data Recovery Services [ad_2]
0 notes
Text
TechFix.ae – Professional Gadget Repairs & IT Services in Dubai
When your devices stop working, TechFix.ae is the expert you can rely on in Dubai. We provide fast, affordable, and certified repair services for individuals and businesses. Whether you need a phone fix or enterprise-level IT assistance, our team is here to help.
We specialize in Apple MacBook Repair Near Me, offering comprehensive MacBook Repair Near Me and MacBook Screen Repair Near Me. If you’re using a desktop, our iMac Repair Near Me ensures your system runs smoothly again.
Worried about data loss? Our secure Data Recovery Near Me, Mac Data Recovery Near Me, and RAID Data Recovery Near Me services can restore your important files quickly.
For mobile users, we provide trusted iPhone Repair Near Me, iPhone Repair Service Near Me, and iPhone Repair Shop Near Me. We also handle all models of iPad Repair Near Me.
Need computer help? Our Laptop Repair Near Me and Computer Repair Services Near Me are ideal for all types of issues—software or hardware.
Gamers can bring their consoles to us for Nintendo Switch Repair Near Me, PS4 Repair Near Me, and PS5 Repair Near Me.
Businesses trust us for IT Migrations Service Near Me, IT Relocation Services Near Me, IT Security Service Near Me, and Printer Installation Near Me.
Call Us +971 50 2010998 Mail Address [email protected] Website https://www.techfix.ae/
0 notes
Text
How to prevent ransomware attacks a guide for Jacksonville organizations
How to Prevent Ransomware Attacks: A Guide for Jacksonville Organizations
Ransomware attacks have become a big problem for businesses of all sizes, including right here in Jacksonville. These attacks can lock up your important files until you pay a ransom, and even then, there’s no guarantee your data will be returned. But the good news is that there are simple steps you can take to lower the risk. Whether you're running a small shop or a larger company, being prepared can go a long way. We spoke to the folks over at nettechconsultants.com to gather a few helpful ideas.
Start with the Basics
First, make sure all your computers have up-to-date antivirus software. This helps stop bad software, like ransomware, before it has a chance to do any damage. It’s also important to keep all your systems – including Windows or Mac software – updated with the latest patches. Hackers love outdated systems because they’re easier to break into.
Train Your Team
Employees can accidentally welcome ransomware into your system by clicking suspicious links or downloading files from unknown email senders. Regular training can help your team spot these tricks early. Teach them to look out for emails that don’t feel right – maybe the wording is strange, or there's unexpected pressure to click on a link right away.
Back Up Your Data
One of the best defenses is having a backup of your important data. Store a copy in the cloud or on a separate device not connected to your main network. If you’ve got a backup, you won’t have to pay anyone to get your files back – you can simply restore them yourself.
Use Strong Passwords and Multi-Factor Authentication
Make sure each account has a strong password that isn’t easy to guess. Better yet, add an extra layer of protection by using something called multi-factor authentication. That’s where you need a password plus a code sent to your phone – this makes it much harder for hackers to break in.
Stay Alert
Ransomware methods are changing all the time, so stay up to date with what's going on. You don’t need to be a tech expert – just being curious and alert can make a big difference.
By taking these steps, Jacksonville businesses can protect themselves and their customers from the headaches of ransomware. A little effort now can save you a lot of trouble later.
0 notes
Text

As the housing crisis worsens, members of Congress seek answers As the housing crisis deepens across the nation, policymakers are increasingly searching for answers. June 24th, D-Mich. Rep. Rashida Tlaib of the company raised concerns about how housing costs would not affect her components. More than half of the county’s black women, and more than half of the counties that Tlaib represents, have experienced some sort of eviction, she said. These numbers are “terrifying,” she said, considering how traumatic evictions will be, and how they will reduce access to fair housing conditions. But that’s one statistic. A report released Tuesday from Harvard University’s Center for Communal Housing Research highlights challenges across the country. Insurance premiums and property taxes are rising rapidly, high rents are burdened with costs, many people are burdened with the homeless, and mortgage rates with sustained high mortgage rates lock first-time buyers out of the market. Against this backdrop, Tlaib pressed Powell to explain the Fed’s rationale for monetary policy that keeps interest rates high. She asked, high rates don’t cover new construction, so if supply doesn’t keep up with demand, will prices be higher? “There’s nothing the Fed can do in the US when housing is long,” Powell replied. “The fees are higher in the short term,” he admitted. “It weighs housing activities, but the best thing you can do in the housing market is to restore price stability so that prices go down.” “Both are correct,” said Selma Hepp, chief economist with Cotality, a real estate data provider. “It’s natural to see the issue of mortgage fees because it’s a drooping fruit, but this is a long-term issue,” Hep told USA Today. In fact, since the subprime housing bubble burst almost 20 years ago, the level of new home construction has been consistently short each year. Meanwhile, construction costs like land and workers have been inflated over the past few years, Hep said, rising nearly twice the overall inflation rate. Tariffs on construction materials only make it worse. more: Why are homes so expensive? There simply isn’t enough home. Tlaib is not the only one looking for outdoor solutions for the housing crisis. A bipartisan group of representatives, including Wisconsin Republican Scott Fitzgerald and New York Democrat Grace Meng, urged the Trump administration to free Fannie Mae and Freddie Mac from government sanctuaries and invest $250 billion in pimples from transactions into middle class housing. “We are pleased that members of Congress have raised this issue,” Hep said. Tlaib and others added that it is correct to point out the human costs of the housing crisis they see in their districts for renters and owners. “Ideally, I would like to have fewer points and more solutions,” Hep said. The post As the housing crisis worsens, members of Congress seek answers appeared first on US-NEA. Tags and categories: Economy via WordPress https://ift.tt/FInHmWt June 24, 2025 at 10:47PM
0 notes
Text
Find Reliable and Professional Computer Repair Services in 2025
When your computer, game console, or phone encounters issues, locating professional repair services quickly and confidently becomes essential. Whether you need a laptop screen replaced, virus removal, or game console repairs, knowing where to turn and what to expect can save you time, money, and stress. This guide dives deep into finding trusted computer repair, mobile repair, and electronics repair near you — empowering you with knowledge to make the best choice for your tech.
What Types of Professional Computer Repair Services Are Available Near Me?
Professional computer repair shops offer a broad range of services tailored to fix both hardware and software issues across devices like PCs, laptops, Macs, and more.
Hardware Repair: Includes motherboard repair, screen repair, power supply repair, RAM upgrade, hard drive repair, and peripheral repair such as keyboard or printer fixes. These repairs address physical damages or parts failures affecting device functionality. Software Repair: Encompasses virus removal, operating system troubleshooting, system restore, software installation, and computer diagnostics to detect underlying system problems. Specialty Repairs: Mac repair and Apple repair services require specific expertise and authorized parts, while Windows repair technicians often handle a wide variety of brands. Many tech repair shops also offer mobile repair for phones and tablets, alongside game console repairs. Onsite vs In-Shop Repair: Onsite repair or in-home repair allows technicians to come directly to your location for quick fixes or diagnostics, whereas traditional repair shops offer comprehensive equipment and controlled environments for complex repairs. Emergency repair
Understanding these options will help you select the appropriate service based on your technical needs and convenience preferences.
How Do I Choose the Best Computer Repair Shop or Technician?
Choosing a reliable repair technician involves considering certifications, experience, customer feedback, and service guarantees to ensure quality repair outcomes.
Certifications and Experience: Look for certified repair professionals or authorized repair centers that have undergone specialized training, especially for brand-specific repairs like Apple or high-end gaming PCs. Customer Reviews and Ratings: Online reviews on platforms like Google Maps and Yelp provide insights into the technician’s reliability, professionalism, and success rate in computer virus removal, hardware repair, and other services. Price Comparisons and Guarantees: Request detailed quotes that include parts and labor. Compare prices between local repair shops and national chains. Check if they offer warranty or service guarantees to protect your investment. Key Questions to Ask Before Booking: Inquire about the repair turnaround time, how they handle data privacy and backup, and whether repairs include post-service support.
Choosing a trustworthy technician ensures your PC repair or laptop repair is done right the first time, minimizing down
0 notes
Text
How to Troubleshoot Computer Problems: A Complete Step-by-Step Guide
Experiencing computer problems can be frustrating, whether it’s a slow startup, unexpected crashes, or network connectivity issues. This comprehensive guide will walk you through how to troubleshoot these common problems effectively—empowering you with the knowledge to fix your PC or Mac yourself before seeking costly repairs. Whether you're a beginner or an intermediate user, understanding how to diagnose and resolve computer troubles is essential to keep your system running smoothly.
Understanding Common Computer Problems
Computer problems can range from minor annoyances to critical failures. Some of the most frequent issues users face include slow computer performance, system errors, blue screen crashes, software freezes, and startup or boot problems. Error messages often give clues about what’s wrong, recommended best repair but their meanings can be cryptic without proper context.
Common symptoms include:
Blue Screen of Death (BSOD) indicating serious system errors System freezes or crashes during use Slow response times when opening apps or files Startup failures or boot loops preventing system access Unusual noises from hardware components like fans or hard drives Peripheral malfunctions such as keyboard or mouse issues
Understanding these symptoms helps pinpoint whether the problem is caused by software glitches or hardware faults.
Preparing to Troubleshoot Your Computer
Before diving into fixes, preparation is key to avoid data loss and further complications. Running diagnostics to gather system information, backing up important files, and knowing how to perform system restores are crucial first steps.
Key preparatory actions include:
Backing up critical data to an external drive or cloud service Creating a system restore point or bootable rescue USB for recovery Running built-in diagnostic tools to identify hardware or software faults Reviewing recent changes like new software installations or updates Ensuring your operating system and antivirus software are current
Proper maintenance and backup strategies not only facilitate easier troubleshooting but also protect your data in emergencies.
Step 1 - Identify the Type of Problem Software Issues
Software problems are often related to corrupted applications, update failures, viruses, or malware infections. These can cause security issues, unexpected errors, and degraded performance.
Common signs of software-related issues:
Frequent error messages or popup warnings Slow program launches or unresponsiveness Automatic restarts after updates fail Suspicious activity indicating virus or malware presence
Identifying software problems early allows for targeted virus removal, software updates, and security scans to restore stability.
Hardware Issues
Hardware problems involve physical components such as hard drives, memory modules, fans, or peripherals. Issues like overheating, power Phone repair supply failures, and faulty keyboards affect overall performance and usability.
Common hardware-related symptoms:
Hard drive
0 notes
Text
Hard Drive Failure Data Recovery in Singapore by Intelligent Computer Services
Reliable, Fast & Professional Data Recovery Solutions
Hard drive failure can happen without warning and often leads to sudden loss of important data — whether it’s personal memories, business documents, or critical system files. In such situations, fast and expert intervention can make all the difference. At Intelligent Computer Services, we specialize in hard drive failure data recovery in Singapore, offering professional, efficient, and secure services to restore lost data from all types of drives and systems.
Understanding Hard Drive Failures and Their Impact
A failed hard drive is one of the most common — and most devastating — forms of data loss. Mechanical malfunctions, firmware corruption, electrical issues, accidental drops, and wear and tear can render your drive unreadable. In many cases, users try to restart the device or run basic software tools, only to make the damage worse. That’s why choosing a professional data recovery service is critical when your hard drive fails. At Intelligent Computer Services, we use advanced diagnostic tools and cleanroom technology to safely recover your files without causing additional harm to the drive.
Trusted Experts in Computer Hard Drive Recovery
Whether it’s a desktop PC or a laptop, hard drive failure can interrupt your workflow and lead to the loss of years of important data. Our team has extensive experience handling all brands and types of hard drives, including HDDs, SSDs, and hybrid models. With a deep understanding of file systems and data structures, we provide complete computer hard drive recovery services across all operating systems — Windows, macOS, and Linux included. As a leading name in data recovery services Singapore, we offer solutions that are both high in quality and fast in execution.
The Best Hard Drive Recovery Service in Singapore

Specialized Solutions for Mac Hard Drive Failures
Mac systems have unique drive formats like HFS+ and APFS, and in many newer devices, drives are soldered directly to the motherboard or include built-in encryption. Our engineers are trained specifically in data recovery for Mac hard drive scenarios and use proprietary tools to safely extract data without compromising system integrity. Whether it’s an iMac, MacBook Pro, or Mac mini, our tailored services provide Apple users in Singapore with reliable recovery from all kinds of failures.
Emergency Data Recovery Service When Every Minute Counts
In urgent situations, waiting simply isn’t an option. That’s why we offer emergency data recovery service 24/7 for clients across Singapore. When you’re facing a business-critical crisis or a personal data emergency, our team is ready to respond immediately. We prioritize your case and begin the recovery process without delay, working to return your files in the shortest time possible. Our fast-track services are ideal for businesses that rely heavily on uninterrupted access to data.
Affordable Data Recovery for All Budgets
Many people assume that professional data recovery is expensive, but we believe that getting your data back shouldn’t cost a fortune. At Intelligent Computer Services, we provide affordable data recovery Singapore solutions with full transparency. You’ll receive a detailed diagnosis and cost estimate before any work begins, and we maintain a strict no data, no charge policy. This means you only pay if we successfully recover your data, giving you peace of mind throughout the process.
Mobile Memory Card and External Drive Recovery Also Available
While our primary focus is on hard drive failure data recovery, we also recover data from other storage devices such as SD cards, microSD cards, USB drives, and external hard drives. Our mobile memory card recovery service is perfect for recovering lost photos, videos, and files from phones, cameras, drones, and other portable devices. Whether your device has been damaged, formatted, or corrupted, we offer fast, effective recovery services for all storage media.
Why Choose Intelligent Computer Services for Data Recovery in Singapore
Choosing the right partner for your data recovery needs is crucial. At Intelligent Computer Services, we combine years of experience, cutting-edge technology, and exceptional customer care to deliver results you can rely on. Our team is made up of certified data recovery specialist who are passionate about helping clients regain access to their valuable data. We are proud to be a trusted name in data recovery Singapore, serving individuals, SMEs, corporations, and government institutions alike.
Start Your Recovery with a Free Consultation
If your hard drive has failed, don’t wait and risk further damage. Contact Intelligent Computer Services today to schedule a free consultation. Our friendly team will assess your situation, provide a detailed recovery plan, and walk you through every step of the process. We’re here to restore your peace of mind along with your data.
0 notes