#Asymmetric-key cryptography
Explore tagged Tumblr posts
Text
Cryptography’s three primary categories
Cryptography, from the Greek words meaning “hidden writing,” encrypts sent data so only the intended recipient can read it. Applications for cryptography are numerous. Cryptography is essential to our digital world and protects sensitive data from hackers and other cybercriminals, from WhatsApp’s end-to-end message authentication to legal form digital signatures to cryptocurrency mining’s CPU-draining ciphers.
One of the first cryptologists was Julius Caesar. Modern cryptosystems are more advanced yet work similarly. Most cryptosystems start with plaintext, which is encrypted into ciphertext using one or more encryption keys. The recipient receives this ciphertext. If the ciphertext is intercepted and the encryption algorithm is strong, unauthorized eavesdroppers cannot break the code. The targeted receiver can simply decipher the text with the correct decryption key.
Let’s start with robust cryptography frameworks’ key features:
Confidentiality: Only the intended recipient can access encrypted information.
Integrity: Encrypted data cannot be altered in storage or transit between sender and receiver without detection.
Non-repudiation: Encrypted information cannot be denied transmission.
Authentication: Sender, receiver, and information origin and destination are verified.
Key management: Data encryption and decryption keys (and related duties like key length, distribution, generation, rotation, etc.) are secure.
Three encryption types
Hybrid systems like SSL exist, although most encryption methods are symmetric, asymmetric, or hash functions.
Key symmetric cryptography
Symmetric key encryption, also known as private key cryptography, secret key cryptography, or single key encryption, employs one key for encryption and decryption. These systems need users to share a private key. Private keys can be shared by a private courier, secured line, or Diffie-Hellman key agreement.
Two types of symmetric key algorithms:
Block cipher: The method works on a fixed-size data block. If the block size is 8, eight bytes of plaintext are encrypted. Encrypt/decrypt interfaces usually call the low-level cipher function repeatedly for data longer than the block size.
Stream cipher: Stream ciphers convert one bit (or byte) at a time. A stream cipher creates a keystream from a key. The produced keystream is XORed with plaintext.
Symmetrical cryptography examples:
DES: IBM developed the Data Encryption Standard (DES) in the early 1970s. While it is vulnerable to brute force assaults, its architecture remains relevant in modern cryptography.
Triple DES: By 1999, computing advances made DES unsecure, however the DES cryptosystem built on the original DES basis provides protection that modern machines cannot break.
Blowfish: Bruce Schneer’s 1993 fast, free, public block cipher.
AES: The only publicly available encryption certified by the U.S. National Security Agency for top secret material is AES.
Asymmetric-key cryptography
One secret and one public key are used in asymmetric encryption. This is why these algorithms are called public key algorithms. Although one key is publicly available, only the intended recipient’s private key may decrypt a message, making public key cryptography more secure than symmetric encryption.
Examples of asymmetrical cryptography:
RSA: Founded in 1977 by Rivest, Shamier, and Adleman, the RSA algorithm is one of the oldest public key cryptosystems for secure data transfer.
ECC: ECC is a sophisticated kind of asymmetric encryption that uses elliptic curve algebraic structures to create very strong cryptographic keys.
One-way hash
Cryptographic hash algorithms convert variable-length input strings into fixed-length digests. The input is plaintext, and the output hash is cipher. Good hash functions for practical applications satisfy the following:
Collision-resistant: A new hash is generated anytime any data is updated, ensuring data integrity.
One-way: The function is irreversible. Thus, a digest cannot be traced back to its source, assuring data security.
Because hash algorithms directly encrypt data without keys, they create powerful cryptosystems. Plaintext is its own key.
Consider the security risk of a bank password database. Anyone with bank computer access, authorized or illegal, may see every password. To protect data, banks and other companies encrypt passwords into a hash value and save only that value in their database. Without the password, the hash value cannot be broken.
Future of cryptography
A quantum cryptography
Technological advances and more complex cyberattacks drive cryptography to evolve. Quantum cryptography, or quantum encryption, uses quantum physics’ natural and immutable laws to securely encrypt and transfer data for cybersecurity. Quantum encryption, albeit still developing, could be unhackable and more secure than earlier cryptographic systems.
Post-quantum crypto
Post-quantum cryptographic methods use mathematical cryptography to generate quantum computer-proof encryption, unlike quantum cryptography, which uses natural rules of physics. Quantum computing, a fast-growing discipline of computer science, might exponentially enhance processing power, dwarfing even the fastest super computers. Although theoretical, prototypes suggest that quantum computers might breach even the most secure public key cryptography schemes in 10 to 50 years.
NIST states that post-quantum cryptography (PQC) aims to “develop cryptographic systems that are secure against both quantum and classical computers, and [that] can interoperate with existing communications protocols and networks.”
The six main quantum-safe cryptography fields are:
Lattice-based crypto
Multivariate crypto
Cryptography using hashes
Code-based cryptography
Cryptography using isogeny
Key symmetry quantum resistance
IBM cryptography helps organizations protect crucial data
IBM cryptography solutions offer crypto agility, quantum-safety, and robust governance and risk policies through technology, consulting, systems integration, and managed security. End-to-end encryption tailored to your business needs protects data and mainframes with symmetric, asymmetric, hash, and other cryptography.
Read more on Govindhtech.com
#technology#govindhtech#technews#news#cryptography#symmetric cryptography#ibm#Post-quantum cryptography#Asymmetric-key cryptography#One-way hash#Quantum computing
0 notes
Text
my security professor is so cute :3
#men who r super passionate abt what they do :D#very nice for me guy who likes to turn off brain and listen to ppl like a podcast#watching him struggle to explain asymmetric key cryptography :33#yap
4 notes
·
View notes
Text

The dawn of asymmetric key encryption via Phil Zimmermann's "Pretty Good Privacy" software.
In 1991, Phil Zimmermann, a software engineer and privacy advocate, released Pretty Good Privacy (PGP), a groundbreaking encryption software that provided individuals with the means to secure their digital communications. The creation and distribution of PGP marked a pivotal moment in the field of cryptography, fundamentally altering the dynamics of privacy, security, and governmental oversight on a global scale.
Technical Innovations of PGP
PGP introduced a robust, accessible encryption method to the general public, using a combination of asymmetric (public key) and symmetric encryption systems to enhance security and ease of use. The software implemented the RSA algorithm for its public key cryptography, which allowed users to encrypt data with a public key that could only be decrypted by a corresponding private key. For the actual data encryption, PGP used symmetric key cryptography, which was faster than asymmetric methods. The innovation did not stop there; PGP also introduced the use of digital signatures, allowing users to verify the integrity and origin of encrypted data.
One of the significant technical impacts of PGP was its use of a "web of trust," a decentralized trust model that allowed users to assign and verify the trustworthiness of public keys through a network of users rather than relying on a central authority. This approach was revolutionary in promoting user-driven security verification and managing public key authentication.
NSA's Concerns and the Broader Implications
The release of PGP did not go unnoticed by government entities, particularly the National Security Agency (NSA), which had long held a dominant role in cryptographic standards and intelligence gathering. The NSA and other law enforcement agencies were concerned about the implications of widespread access to strong encryption. Their primary fear was that encryption technologies like PGP would severely hinder their ability to conduct surveillance for national security purposes.
The concern was not unfounded. Before PGP, high-grade encryption was generally available only to government agencies and large corporations. By democratizing access to encryption technology, PGP enabled ordinary citizens to shield their communications from both governmental and non-governmental prying eyes. This shift posed a direct challenge to the NSA's capabilities, particularly in the areas of wiretapping and intercepting electronic communications, as encrypted content could not be easily decoded without access to the private keys.
Legal and Political Fallout
The distribution of PGP also led to significant legal and political repercussions for Zimmermann. Shortly after its release, Zimmermann became the subject of a criminal investigation by the U.S. government under the International Traffic in Arms Regulations (ITAR), which at the time restricted the export of cryptographic software deemed to be military-grade. The case highlighted the tension between national security interests and the right to privacy, stirring a global debate on the reach of U.S. export controls over software and the definition of "arms" in the context of cryptography.
Legacy and Continuing Impact
The controversy and subsequent legal battles surrounding PGP fueled a broader discussion about encryption, privacy, and civil liberties. It led to the relaxation of some export controls on cryptographic software in the late 1990s and helped pave the way for modern encryption protocols used over the internet, such as SSL/TLS for secure web browsing.
Moreover, PGP's influence extends beyond its technical contributions. It has played a crucial role in debates over privacy rights and surveillance, inspiring a new generation of encryption tools aimed at protecting individual privacy and securing communications in an increasingly digital world.
Conclusion
Phil Zimmermann's PGP software did not just provide a practical encryption tool—it sparked a significant societal shift towards individual privacy and security consciousness. The NSA's fears regarding the widespread availability of such technology underscore the ongoing tension between privacy rights and government surveillance capabilities. PGP remains a seminal work in the history of cryptography, symbolizing the power of individual empowerment against overarching surveillance.
#cryptography#asymmetric key encryption#PGP#Pretty Good Privacy#Phil Zimmermann#Wired#1993#Encryption#Too Many Secrets
1 note
·
View note
Text
What is Blockchain Technology & How Does Blockchain Work?

Introduction
Gratix Technologies has emerged as one of the most revolutionary and transformative innovations of the 21st century. This decentralized and transparent Blockchain Development Company has the potential to revolutionize various industries, from finance to supply chain management and beyond. Understanding the basics of Custom Blockchain Development Company and how it works is essential for grasping the immense opportunities it presents.
What is Blockchain Development Company
Blockchain Development Company is more than just a buzzword thrown around in tech circles. Simply put, blockchain is a ground-breaking technology that makes digital transactions safe and transparent. Well, think of Custom Blockchain Development Company as a digital ledger that records and stores transactional data in a transparent and secure manner. Instead of relying on a single authority, like a bank or government, blockchain uses a decentralized network of computers to validate and verify transactions.
Brief History of Custom Blockchain Development Company
The Custom Blockchain Development Company was founded in the early 1990s, but it didn't become well-known until the emergence of cryptocurrencies like Bitcoin. The notion of a decentralized digital ledger was initially presented by Scott Stornetta and Stuart Haber. Since then, Blockchain Development Company has advanced beyond cryptocurrency and found uses in a range of sectors, including voting systems, supply chain management, healthcare, and banking.
Cryptography and Security
One of the key features of blockchain is its robust security. Custom Blockchain Development Company relies on advanced cryptographic algorithms to secure transactions and protect the integrity of the data stored within it. By using cryptographic hashing, digital signatures, and asymmetric encryption, blockchain ensures that transactions are tamper-proof and verifiable. This level of security makes blockchain ideal for applications that require a high degree of trust and immutability.
The Inner Workings of Blockchain Development Company
Blockchain Development Company data is structured into blocks, each containing a set of transactions. These blocks are linked together in a chronological order, forming a chain of blocks hence the name of Custom Blockchain Development Company. Each block contains a unique identifier, a timestamp, a reference to the previous block, and the transactions it includes. This interconnected structure ensures the immutability of the data since any changes in one block would require altering all subsequent blocks, which is nearly impossible due to the decentralized nature of the network.
Transaction Validation and Verification
When a new transaction is initiated, it is broadcasted to the network and verified by multiple nodes through consensus mechanisms. Once validated, the transaction is added to a new block, which is then appended to the blockchain. This validation and verification process ensures that fraudulent or invalid transactions are rejected, maintaining the integrity and reliability of the blockchain.
Public vs. Private Blockchains
There are actually two main types of blockchain technology: private and public. Public Custom Blockchain Development Company, like Bitcoin and Ethereum, are open to anyone and allow for a decentralized network of participants. On the other hand, private blockchains restrict access to a select group of participants, offering more control and privacy. Both types have their advantages and use cases, and the choice depends on the specific requirements of the application.
Peer-to-Peer Networking
Custom Blockchain Development Company operates on a peer-to-peer network, where each participant has equal authority. This removes the need for intermediaries, such as banks or clearinghouses, thereby reducing costs and increasing the speed of transactions. Peer-to-peer networking also enhances security as there is no single point of failure or vulnerability. Participants in the network collaborate to maintain the Custom Blockchain Development Company security and validate transactions, creating a decentralized ecosystem that fosters trust and resilience.
Blockchain Applications and Use Cases
If you've ever had to deal with the headache of transferring money internationally or verifying your identity for a new bank account, you'll appreciate How Custom Blockchain Development Company can revolutionize the financial industry. Custom Blockchain Development Company provides a decentralized and transparent ledger system that can streamline transactions, reduce costs, and enhance security. From international remittances to smart contracts, the possibilities are endless for making our financial lives a little easier.
Supply Chain Management
Ever wondered where your new pair of sneakers came from? Custom Blockchain Development Company can trace every step of a product's journey, from raw materials to manufacturing to delivery. By recording each transaction on the Custom Blockchain Development Company supply chain management becomes more transparent, efficient, and trustworthy. No more worrying about counterfeit products or unethical sourcing - blockchain has got your back!
Enhanced Security and Trust
In a world where hacking and data breaches seem to happen on a daily basis, Custom Blockchain Development Company offers a beacon of hope. Its cryptographic algorithms and decentralized nature make it incredibly secure and resistant to tampering. Plus, with its transparent and immutable ledger, Custom Blockchain Development Company builds trust by providing a verifiable record of transactions. So you can say goodbye to those sleepless nights worrying about your data being compromised!
Improved Efficiency and Cost Savings
Who doesn't love a little efficiency and cost savings? With blockchain, intermediaries and third-party intermediaries can be eliminated, reducing the time and cost associated with transactions. Whether it's cross-border payments or supply chain management, Custom blockchain Development Company streamlined processes can save businesses a ton of money. And who doesn't want to see those savings reflected in their bottom line?
The Future of Blockchain: Trends and Innovations
As Custom Blockchain Development Company continues to evolve, one of the key trends we're seeing is the focus on interoperability and integration. Different blockchain platforms and networks are working towards the seamless transfer of data and assets, making it easier for businesses and individuals to connect and collaborate. Imagine a world where blockchain networks can communicate with each other like old friends, enabling new possibilities and unlocking even more potential.
Conclusion
Custom Blockchain Development Company has the potential to transform industries, enhance security, and streamline processes. From financial services to supply chain management to healthcare, the applications are vast and exciting. However, challenges such as scalability and regulatory concerns need to be addressed for widespread adoption. With trends like interoperability and integration, as well as the integration of Blockchain Development Company with IoT and government systems, the future looks bright for blockchain technology. So strap on your digital seatbelt and get ready for the blockchain revolution!
#blockchain development company#smart contracts in blockchain#custom blockchain development company#WEB#websites
3 notes
·
View notes
Text
Blockchain: what it is, how it works and the most common uses
What is blockchain?
It literally means blockchain is a database or public registry that can be shared by a multitude of users in peer-to-peer mode (P2P or peer network) and that allows the storage of information in an immutable and organized way.
It is a term associated with cryptocurrencies because, apart from being the technology that supports them, it was born with the first virtual currency in history in 2009, Bitcoin . In this case, the data added to the blockchain is public and can be consulted at any time by network users.
However, it is important to remember that cryptocurrencies are just that, currencies! Just as happens with the euro, the dollar or any type of paper money. Each one is a simple material with a printed value, but what allows its use and generates value are the economic laws that support them.
Something similar happens with virtual currencies. In this case, it is blockchain technology that allows it to function. Its main objective is to create an unchangeable record of everything that happens in the blockchain, which is why we are talking about a secure and transparent system.
Bitcoin (BTC), Ethereum (ETH) or any other cryptocurrency is simply a virtual currency built on the blockchain and used to send or receive the amount of money that each participant has. This technology is what keeps transactions publicly recorded, but keeping the identity of the participants anonymous.
However, although it was created to store the history of Bitcoin operations, over the years it has identified great potential to be applied in other areas and sectors due to the possibilities it offers.
Features of blockchain technology
The progress of this system has been a mystery since its origin, but little by little we are learning more details about its operation:
Security
Cryptography is a fundamental pillar in the operation of the blockchain application development company, which provides security for the data stored in the system, as well as the information shared between the nodes of the network. When we are going to make a transaction, we need a set of valid asymmetric keys to be able to carry it out on the blockchain. It is also known as public key cryptography.
Trust
By representing a shared record of facts, this technology generates trust in users. Not only that, but it eliminates the possibility of manipulation by hackers and generates a ledger of operations that all members of the network can access.
Immutability
When information is added to the distributed database, it is virtually impossible to modify it. Thanks to asymmetric cryptography and hash functions, a distributed ledger can be implemented that guarantees security. In addition, it allows consensus on data integrity to be reached among network participants without having to resort to an entity that centralizes the information.
Transparency
It is one of the basic requirements to generate trust. Transparency in blockchain consulting services is attained by making the chain's software code publicly available and by fostering a network of nodes that use it. Its application in different activities, such as supply chains, allows product traceability from origin.
Traceability
It allows knowledge of all operations carried out, as well as the review of transactions made at a specific time. Traceability is a procedure that allows us to follow the evolution of a product in each of its stages, as well as who, how, when and where it has been intervened on. This is one of the main reasons why many sectors are beginning to apply blockchain technology.
3 keys to understanding how the blockchain works
It will only take you a single step to become an expert on the blockchain consulting services. Now that you know its definition and the main characteristics and related terms, it is time to put everything you have learned together to discover how it works. Take note!
The jack, horse, king of transactions
Networks use peer-to-peer data exchange technology to connect different users who share information. That is, the data is not centralized in a central system, but shared by all users of the network. At the moment a transaction is made, it is recorded as a block of data transmitted to all parties with the objective of being validated.
The transaction is the movement of an asset and the block can record the information of your choice, from what, who, when, to where, how much and how. Like an irreversible record, each block joins the preceding and following ones to form a chain (blockchain). Every new block removes the chance of manipulation and strengthens the previous one's verification. Finally, the transaction is completed.
The structure of the blocks
The chain stores a lot of information, which allows it to grow over time. This is the reason why it has been necessary to create efficient query mechanisms without having to download all the information: the Merkle hash tree.
It is a tree data structure that allows a large number of separate data to be related to a single hash value, providing a very efficient method of verifying the contents of large information structures.
Generation of chain blocks
First of all, it is a decentralized process. And to do this, a distributed consensus is needed in which the nodes have the ability to generate valid data. In order for users to initiate new operations, they must turn into nodes within the system. If what they want is to become miners and create blocks, then they must compete with others. The validation process is based on asymmetric cryptography, with a public key and a private key. The issued transactions are validated by the nodes in the new mined block, as well as their correct linking to the previous block (it must contain the hash).
The most common uses of blockchain
“But this technology was created for cryptocurrency operations.”
That's right, but the passage of time, research and social needs have seen great potential in this technology to be applied in other areas:
Voting systems
Some states such as West Virginia are implementing electronic voting through blockchain, although it is still a framework to be regulated. But that's not necessary to go that far. After the last elections to the Madrid Assembly, as well as the COVID-19 pandemic situation and its restrictions on mobility and the gathering of people, they have proposed the establishment of electronic voting with blockchain.It is an extremely appealing voting system because of its traceability and immutability.Not only would it increase transparency and reliability, but you could audit in real time.
Smart Contracts
They are programs that allow you to fulfill and execute registered agreements between the parties automatically. They can be applied in any type of transaction where a registered agreement is necessary, such as a security deposit or the contracting of a product, among others. Among its main characteristics we find: self-execution and immutability.
Supply chain
Supervision and monitoring in food chains, as well as in production, is one of the main applications proposed with blockchain. Some examples of this technology in the food and agricultural industry are: Walmart China, with food production constituted by IBM; or the Australian AgriDigital, which works with distributed ledgers, blockchain and Smart Contracts.
It is not what has already been done, but what is yet to come. At Occam Agencia Digital , as a blockchain development company, we are convinced that it is not just about programming, but about analyzing the client's needs and designing a unique user experience.
What are some ways that your business can benefit from blockchain technology? Tell us your questions, we can help you solve them.
Tokenization of real estate and assets
Thanks to the transparency of the blockchain, the tokenization of assets is revolutionizing traditional sectors such as real estate investment, democratizing their purchase.
This breaks the barrier to investing in safer assets, since, until now, if you wanted to buy a property, you had to do it alone or among a very small group of people. Thanks to tokenization, now you can buy an apartment between 100, 200, 1000 people by making a small contribution.
This also allows you to diversify and minimize risk, being able to invest €100 in several properties.
It is very important to choose a blockchain development company that has developed a project using this technology, since these are complex developments with very little documentation on the internet to help developers.
How to do good blockchain development?
We invite you to take note of the steps necessary for the development of the blockchain:
The first thing to do is a briefing between both parties . The client provides the information on the business model, and the blockchain development company offers the expertise to design the platform using the most optimal technology.
It is very important to choose the technologies to be used, since in blockchain each transaction has a cost. Depending on the blockchain chosen, it can cost between €10 or €0.0001 each.
It is imperative that the blockchain development company determines which components of the platform need to function in order to have a well-balanced security, user experience, and cost per use system that is suitable and tailored to the client's suggested business model.
For example, if you want to develop a platform to tokenize real estate so that investors can buy tokens from these, the most recommended thing is that all the functionality related to the purchase or investment is developed on blockchain technology, and the rest of the functionalities are developed using the traditional way. In this way, you will achieve a good user experience, great security in purchases and low costs.
Once the briefing is finished, we move on to the design phase . With the briefing in hand, it's time for the UX and UI experts to get to work. With the information collected, you must design a platform with a great user experience and a friendly interface to convey confidence to the user and allow them to operate very easily. You'll be able to stay on the platform and avoid getting frustrated or giving up.
#blockchain#blockchain development#blockchain technology#blockchain development company#private blockchain development
3 notes
·
View notes
Text
Idly musing about post-quantum encryption algorithms. Suppose you had a system where there were public servers - effectively numbers stations - that constantly emitted a stream of random bytes (perhaps literally generated via radioactive decay), broadcast them publicly, and recorded them for a long period of time. Suppose also that any two parties that want to communicate negotiate a small shared secret out-of-band, say a 256-bit AES key. When Alice wants to send Bob an encrypted message, she records the current time from the numbers station, listens for bytes from the numbers station, and encrypts them with that shared secret. Alice then uses this new stream of random bytes as a one-time-pad and encrypts her message. When finished, she records the stop time and sends the encrypted message, start time, and stop time to Bob. Bob can use the start and stop times, his small shared secret, and the public records of the numbers station to reconstruct the stream of random bytes Alice used, and then XOR that against his received cyphertext to recover the plaintext. If there was a way to remove the initial small shared secret step, I think this sort of scheme would be a way that people could continue to do effective asymmetric cryptography even in a post-quantum world, albeit with the requirement that these numbers stations exist and keep records for a long period of time.
2 notes
·
View notes
Text
Post Quantum Security: Future-Proof Data From Quantum Threats

What becomes of encryption today when quantum computers are capable of cracking it? As we race toward a future driven by the next generation of technology, one urgent question hangs over cybersecurity. The solution is to use Post Quantum Security, a new generation of cryptography capable of resisting the brute power of quantum computing.
In a world where sensitive information — from personal identities to national secrets — is increasingly vulnerable, Post Quantum Security is not just an upgrade, but a necessity. This article explores how to future-proof your data and systems against quantum threats.
Understanding the Quantum Threat Landscape
The Birth of Quantum Computing
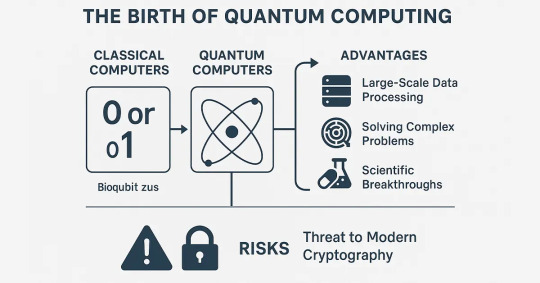
Quantum computing seems to quickly evolve from a new scientific theory into a change- and results-driven technology. Old computers use the binary digit as 0 or 1, whereas quantum computers operate using qubits, which can occupy several states simultaneously owing to superposition and entanglement. As a result, such cutting-edge machines provide an exceptional ability for quick, advanced computations.
Quantum computing excels using its capability of handling large data volumes and solving issues too complicated for existing best classical supercomputers. In particular, quantum computers can effectively address complex logistics tasks, analyze the structure of molecules to invent new medicines, and enhance the approach undertaken in financial forecasting.
But with that potential comes a warning: quantum computing puts modern cryptographic systems at serious risk. The same computational benefits that make quantum computers a breakthrough for scientific research are the ability to compromise classical encryption methods used in our online security.
Implications for Current Cryptography
The dominant modalities of the modern digital infrastructure are based on the use of public key cryptography, and such systems as RSA and ECC are among the most widespread representations that people use. These encryption systems are based on mathematically difficult problems for conventional systems — factorizing huge numbers or solving discrete logarithm problems. These are exactly the sorts of problems a quantum computer is designed to demolish with impunity using expert algorithms.
Shor’s Algorithm, created in 1994, is likely the most famous quantum algorithm that targets RSA and ECC directly. It can factor big numbers exponentially quicker than the best-known classical algorithms. When quantum computers are ready — usually called “quantum supremacy” — they will be able to decrypt secure communications, financial transactions, and private information that are now thought to be secure.
Another significant algorithm, Grover’s Algorithm, doesn’t shatter symmetric crypto systems but narrows down their security levels significantly. It indeed cuts a symmetric key’s bits in half, so 256-bit keys would provide only 128-bit security in the quantum age. Less devastating than Shor’s impact on asymmetric crypto, though, Grover’s Algorithm does mean a reconsideration of the dominant symmetric encryption algorithms.
This new threat brings to the forefront the need for post quantum security solutions in an immediate manner. Unlike conventional cryptographic practices, post quantum security is about designing and deploying algorithms that are secure even when quantum computing resources are available. These algorithms are based on challenging mathematical problems for which quantum computers are not yet known to solve efficiently.
The Urgency for Transition
Post quantum security is not a theoretical concept; it’s an urgent, real-life issue. RSA- or ECC-breaking large-scale quantum computers don’t exist yet, but breakthroughs are on the move. The collaborative efforts of governments, corporations, and research bodies across the globe to create quantum technology imply that these machines will soon become real.
There is a dire need to secure the digital infrastructure of organizations, for when quantum technology is available. Transitioning to post quantum security protocols is difficult and time-consuming, not only swapping cryptographic algorithms but also rewriting software, hardware, and communication protocols. Waiting for fully functional quantum computers may expose systems and data to attacks.
Further, hacked encrypted data today can be stored and decoded at a later date after computers develop the capability — the “harvest now, decrypt later” attack. As a countermeasure post quantum security ensures valuable information is safeguarded both today and in the foreseeable future.
The U.S. National Institute of Standards and Technology (NIST) has already started standardizing quantum-resistant algorithms with its Post-Quantum Cryptography Standardization Project. Organizations can standardize their security approach with international best practices for post quantum security using NIST-recommended solutions.
What Is Post Quantum Security?
Post Quantum Security is a term that is used to refer to cryptographic methods that are resistant to attacks carried out by entities that can run large quantum computers. Besides, this category includes the quantum-resistant hash algorithms, encryption algorithms, and digital signature algorithms. These systems are being standardized by efforts such as NIST’s Post-Quantum Cryptography Project.
Embracing Post Quantum Security guarantees that long-lived sensitive information, such as medical records or financial contracts, is still protected even when intercepted today and decrypted in the future quantum world.
ncog.earth incorporates Post Quantum Security into its core blockchain protocol. It provides data security for decades in a post-quantum secure environment.
Core Principles of Post Quantum Security
Below are the fundamental principles that constitute this new field and how they interact with each other to protect digital property during the era of quantum computing.
1. Quantum-Resistant Algorithms
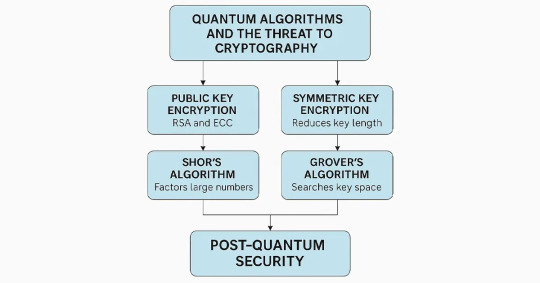
Post quantum security is centered around quantum-resistant algorithms, which are designed to stand up to attacks both from traditional attack methodologies as well as attacks performed with a quantum computer. These algorithms don’t depend on the weak assumptions of the classical encryption methods like RSA or ECC, which can be attacked and broken by quantum algorithms like Shor. Post quantum security instead depends on mathematical problems with cryptographically amicable properties that are difficult for an efficient quantum computer to solve.
Among the most promising quantum-resistant solutions are-
Lattice-based cryptography: Lattice-based cryptosystems rely on the computational subtlety of such problems as the Shortest Vector Problem (SVP) and the Learning With Errors (LWE) problem. They are classical and quantum resistant and thus well positioned to protect encryption, digital signatures, and key exchanges.
Hash-based cryptography: Founded on extensively studied hash functions, this method effectively generates secure digital signatures. Because hash functions are one-way functions, they are extremely secure even against quantum attackers.
Code-based cryptography: Founded on error-correcting codes, this method has stood the test of time for more than four decades. It is strong, well-established, and extremely efficient for encryption and digital signatures in a post quantum security scenario.
Multivariate polynomial cryptography: The hardness of these problems is essentially dependent on the intricacies of solving multivariate quadratic systems of equations, which are intractable for quantum and classical systems.
Deployment and selection of these algorithms are being standardized by bodies such as NIST, which is finalizing a suite of post-quantum cryptographic standards for ease of global implementation of post quantum security protocols.
2. Forward Secrecy
Forward secrecy is yet another significant post quantum security parameter. In the conventional crypto paradigm, it might be possible that breaking a private key today can expose attackers to decrypted communications in the past and future, and it is highly risky if, in a quantum paradigm where harvested encrypted data from today can be broken using quantum computers in the future.
Post quantum security addresses this issue by guaranteeing that even when an encryption key is finally breached, past messages cannot be decoded after the fact. The method is to repeatedly generate ephemeral keys that don’t survive and aren’t easily linked up with each other. Forward secrecy is significant not just for private individuals but for protecting business networks, government files, and money networks as well.
Essentially, forward secrecy reconfigures the way we approach long-term data secrecy, particularly considering the danger represented by “harvest now, decrypt later” attacks facilitated by quantum advancements. In post quantum security, it’s a solid pillar of real future-proofing.
3. Hybrid Cryptographic Models
With the indefinite time frame of quantum progress, most organizations are taking a hybrid approach that brings together classical and post-quantum-resistant cryptography. The cryptographic models are created to fill the security gap during the transition phase when the existing traditional algorithms exist side by side with the post quantum security algorithms.
In a hybrid method, two sets of algorithms are run in parallel. One set offers backwards compatibility with current infrastructures, and the other offers immunity to future quantum attacks. As a simple example, an end-to-end communication channel could employ RSA in conjunction with a lattice-based encryption scheme at the same time. This means that even if the classical part is compromised in the future, the post quantum security layer still protects the underlying data.
This method has some advantages-
Gradual roll-out: Businesses can deploy systems gradually without affecting current services.
Redundancy: Having several levels of encryption offers a backup in case one algorithm is compromised.
Testing ground: Testing the deployment of quantum-resilient tools identifies real-world problems and solutions before mass deployment.
Hybrid deployments are not long-term, but they are essential stepping stones. With increasing trust and confidence in post quantum security technology, hybrid deployments will ultimately make way for fully quantum-resistant architectures.
Why Businesses Must Act Now

In the unfolding digital age, while cyberattacks increase in scale and sophistication, quantum computing’s emergence is at once a dazzling technological advancement and an intrinsic cybersecurity challenge. To companies — particularly those holding sensitive customer data or conducting business in highly regulated industries — the time to prepare is not in the future but today. Post-quantum security is no longer an idealistic aspiration but rather a concrete reality. Forward-thinking companies need to take action today to ensure that they will be able to withstand future cryptographic shocks.
Quantum Threats Are Nearer Than They Seem
The power of quantum computers is that they can use superposition and entanglement to exceed classical machines in certain forms of mathematical operations. The possible advantages that such technology could offer to drug discovery and logistics, as well as machine learning, are substantial, but this danger also undermines the encryption protection that enshrines secure digital communication, financial systems, medical records, and contracts.
Algorithms such as RSA and ECC, the basis of modern public-key cryptography, could be made obsolete by quantum algorithms such as Shor’s. In practical terms, what that would mean is to make information currently encrypted under these systems decrypted within seconds if there existed a sufficiently large quantum computer. The potential effect would be disastrous to companies experiencing huge-scale data breaches, litigations, and erosion of customer confidence.
That’s why post quantum security must be implemented far ahead of the wholesale arrival of quantum computing. Companies that delay are not only taking a risk — they’re deliberately putting their businesses, data, and reputations in long-term jeopardy.
Data Longevity Brings the Risk into the Present
One of the least considered measures of quantum risk is data longevity concern. Whereas real-time data spoils at a fast pace, some forms of data — medical history, legal papers, government agreements, and intellectual property — are priceless for decades or years. If today a cyberattacker got hold of encrypted information, they would be unable to decipher it. But with the advent of quantum power, the same information can be accessed in the foreseeable future. The label is also applicable when talking about attacks referred to as “harvest now, decrypt later”.
On this front, post quantum security plays a twofold role: it safeguards against the threat at hand, but also against potential attempts to decrypt in the future. For businesses tasked with securing data over the long term — insurance providers, banks, and law firms, for example — it is critical that it is pre-emptive. Delaying the implementation of quantum-resistant practices creates a bombshell situation where encrypted files stored could be cracked open at any moment.
Consumer confidence is perhaps the most precious asset of the online marketplace. With high-profile breaches becoming the norm, customers are growing more attuned to where their information lives and how it is secured. Companies that act early to publish quantum security standards communicate that they are serious about leading-edge data protection and customer privacy. This method contributes to the creation and preservation of a reliable brand and earns the loyalty of the clients.
Additionally, regulatory landscapes are changing. Global data privacy legislation like the GDPR, HIPAA, and CCPA demands secure data security procedures, and compliance systems will shortly be following close behind in counteracting quantum-age attacks. Adopting post quantum security today allows organizations to protect themselves against future compliance mandates and sidestep the prohibitively cost-intensive exercise of currency flows.
Smooth Transition Through Strategic Planning
Post quantum migration is not a flip-of-the-switch transition — it requires thoughtful planning, testing, and staged deployment. Businesses must assess their existing cryptographic infrastructure, identify vulnerable endpoints, and decide which quantum-resistant algorithms will best meet their operational needs.
Fortunately, most businesses are not beginning from the ground up. Hybrid crypto designs — blends of conventional and quantum-resistant solutions — permit phased and secure adoption. Post quantum security is viable through hybrid approaches that support organizations in adopting post quantum security without sacrificing current system performance or compatibility. Phase by phase is the way, causing as little disruption as possible while providing security for important information at each stage.
They also must spend on training and awareness programs. Decision-makers, developers, and cybersecurity staff must be made aware of the effects of quantum risk and the pragmatic actions that go into minimizing it. Post quantum security incorporated into cybersecurity roadmaps now will have companies not lag when the quantum era is in full force.
Building Quantum-Resilient Ecosystems
The truth is, cybersecurity is not an isolated practice. A majority of businesses employ third-party suppliers, cloud computing providers, and digital platforms that touch or have access to sensitive information. Having a secure digital environment is a matter of discussing post quantum security with partners and suppliers.
Leading organizations are now starting to measure their supply chains and expect quantum-readiness from their partners. Organizations can minimize systemic vulnerabilities and foster increased collective resilience by establishing post-quantum security as an expectation within ecosystems.
Integrating Post Quantum Security into Your Infrastructure
With continued advances in quantum computing, the danger that it poses to classical cryptographic schemes is more dire. Companies and enterprises cannot afford to wait. There is a need for a transparent and systematic adoption of post quantum security protocols into existing IT infrastructures so that data confidentiality, integrity, and availability are preserved under quantum computing. This has to be done with a strategic roadmap of action covering technology and operations transformation across the digital landscape.
For this transition to be made possible, organizations can utilize a multi-step process that will establish quantum resilience without disrupting essential services. Below, we outline the four main steps of incorporating post-quantum security in your infrastructure.
Audit Your Current Cryptographic Inventory
Before any change is implemented by companies, they must start by defining the scope and utilization of current cryptographic assets. Any effective post quantum security project is based on a thorough cryptographic inventory. This process entails determining where and how cryptographic algorithms are utilized — on SSL/TLS certificates, database encryption, secure email, authentication protocols, digital signatures, API gateways, mobile applications, VPNs, and IoT devices.
This audit must encompass-
Encryption Algorithms Used: Assess if systems are using RSA, ECC, or other vulnerable algorithm-based encryption.
Key Sizes and Expiration Policies: Document existing key sizes and assess how often they are being replaced.
Cryptographic Libraries and APIs: Check for dependencies and assess compatibility with quantum-resistant alternatives.
Certificate Authorities and Issuance Policies: Examine methods of distributing, retaining, and withdrawing digital certificates.
When such data is analyzed, it is possible to identify weak points and establish priorities for strategic transition to post-quantum security. Notably, the process helps organizations to review the data lifecycle and determine long-term sensitive data that needs to be secured today against tomorrow’s quantum decryption power.
Select Quantum-Resistant Algorithms
After identifying your cryptographic footprint, the next step is to select quantum-resistant alternatives. NIST has worked with others to initiate multi-year standardization efforts that will evaluate and promote post-quantum cryptography algorithm recommendations. These algorithms are designed so that they can resist attack by both classical and quantum computers and include key encapsulation processes and digital signature protocols.
Among the most promising contributions to come out of the NIST project are-
CRYSTALS-Kyber (for public-key cryptography and KEM)
CRYSTALS-Dilithium (for digital signatures)
FALCON and SPHINCS+ (signature schemes with performance profiles of differing types)
In choosing algorithms, implementations must consider performance, resource efficiency, complexity to implement, and the extent to which the solution they choose fits their infrastructure. For instance, IoT devices that have little power may need lightweight algorithms, but high performance servers are more than capable of handling complex computing activities.
Selection of the best algorithms is immensely important for effective post quantum security integration. Future-proofing should also be a consideration for security teams as quantum-resistant cryptography develops. Modular architecture solutions for cryptography allow for a seamless switch or upgrade of algorithms as new standards become available.
Use Hybrid Cryptographic Systems
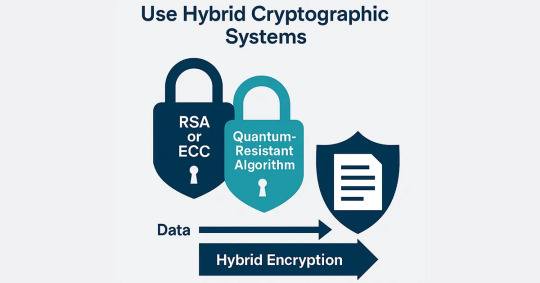
It is not necessary to move away from classical to quantum-resistant cryptography completely. One of the most recommended practices while transitioning to post quantum security is the use of hybrid cryptographic systems. These use current (classical) cryptographic algorithms and couple them with quantum-safe algorithms to provide a multi-layered defense.
In a hybrid system, data is encrypted with both RSA (or ECC) and a quantum-resistant algorithm. It makes the system both backward compatible as well as future-proof against attacks based on quantum. Although quantum computers are unable to break today’s classical encryption now, hybrid encryption protects the data from being exposed in the future, most beneficial for long-shelf-life sensitive data.
Hybrid deployments also enable companies to pilot the in-the-wild usage of post-quantum-safe algorithms without removing trusted current defenses. Phase-in of post quantum security in this manner prevents service disruption, lowers operational risk, and enables incremental testing and tightening.
Key libraries and frameworks increasingly start to include hybrid support. For example-
OpenSSL (with quantum-safe branches)
Cloudflare and Amazon Web Services, which have begun to experiment with post-quantum TLS deployments
Mozilla and Google, pioneering early hybrid deployments in their browsers
These initial hybrid adoption attempts show the growing traction for post-quantum security and offer in-the-wild blueprints for companies willing to make the transition.
Upgrade Key Management Systems (KMS)
The key to the efficiency of encryption lies entirely in the responsible use of its keys. Infrastructures that are quantum-resilient need updates to legacy Key Management Systems (KMS) to accommodate the special needs of post quantum security…
#post quantum#post quantum security#technology#ncog#post quantum blockchain#post quantum encryption#post quantum cryptography#decentralized database#quantum computer#quantum computing#quantum computers#post quantum secure blockchain#rsa#shor algorithm#quantum-resistant cryptography#ECC
1 note
·
View note
Text
How Blockchain Secures Data Through Cryptography

In this episode of Unpacking Blockchain Technology, we explore one of the most critical components of blockchain: cryptography — the invisible shield that protects digital data, ensures transaction integrity, and powers trustless systems.
What Is Cryptography, and Why Does It Matter?
At its core, cryptography is the science of secure communication. It converts data into a coded format that only authorized parties can understand. In the world of blockchain, cryptography ensures that:
Transactions are secure and tamper-proof
Identities are protected
Data cannot be altered retroactively
Without cryptography, blockchain as we know it simply wouldn’t work.
Two Key Types of Cryptography in Blockchain
1. Hashing (e.g., SHA-256): Every piece of data in a blockchain is run through a hash function. This generates a fixed-length string of characters (the hash) that acts like a digital fingerprint. Even the slightest change to the data produces a completely different hash, ensuring data integrity.
2. Public-Key Cryptography (Asymmetric Encryption): This system uses two keys: a public key (shared with others) and a private key (kept secret).
You sign a transaction with your private key
Anyone can verify it using your public key
This mechanism ensures authenticity, non-repudiation, and secure value transfer between users.
Real-World Application: Bitcoin and Ethereum
In Bitcoin, each transaction is hashed and linked to the one before it — creating an unbreakable chain of trust.
In Ethereum, cryptography also secures smart contracts, automating interactions without revealing sensitive data.
Why Should You Care?
Whether you’re a developer, investor, policymaker, or just blockchain-curious, understanding cryptography helps you appreciate how:
Blockchain eliminates the need for third-party trust
Transactions stay secure, verifiable, and transparent
Your digital identity and assets are protected in Web3
Cryptography isn’t just a technical feature — it’s the foundation of digital trust in decentralized systems.
Tune in to Episode 7 now to demystify the cryptographic magic behind blockchain security.
Let’s Talk:
Do you think most people truly understand how their digital data is protected? Reply in the comments
#blockchaininnovation#blockchaintechnology#blockchainafrica#blockchainforgood#blockchainpodcast#cryptoeducation#decentralization#digitaltransformation#thabisonjoko#eswatini
0 notes
Text
F5 Launches Post-Quantum Cryptography Tools & API Secu

F5, a global leader in application and API delivery and security, announced the launch of comprehensive Post-Quantum Cryptography (PQC) ready solutions integrated into its Application Delivery and Security Platform. This strategic disclosure provides organisations with the tools they need to safeguard their apps and APIs from quantum computing dangers while preserving great speed and scalability. The effort addresses a major cybersecurity shift as the quantum era threatens conventional asymmetric encryption.
Quantum Imperative: Cybersecurity Growing Threat
Quantum computing will eliminate classical computer's limits, making it a turning point for cybersecurity. No one can overstate how urgent this change is. Quantum computing will make asymmetric cryptography unsafe by 2029 and breakable by 2034, according to Gartner. This looming vulnerability has led malicious actors to use a “harvest now, decrypt later” attack approach.
A cunning technique harvests encrypted data, including sensitive user, financial, personal health, intellectual property, and company records, with the purpose of decrypting them once quantum computing capabilities are generally available. This makes long-lived, essential data vulnerable if not safeguarded immediately.
Kunal Anand, F5 Chief Innovation Officer, says “post-quantum threats aren’t a distant problem; they’re a forcing function to modernise security now.” F5 emphasises its practicality by saying, “Our platform makes PQC adoption practical so enterprises can future-proof their apps, APIs, and trust models without slowing down”.
F5's Integrated Platform: Quantum Transition Simplified
F5 realises that PQC represents a fundamental cybersecurity architectural shift, hence it has devised solutions to simplify this complex process. F5 ADSP provides integrated and scalable application delivery and security. Through poorly managed transitions among hybrid, multicloud, and legacy systems, this platform-based strategy seeks to lower the risk of costly outages, application lags, compliance problems, and user annoyance.
Key F5 Features and Benefits
F5's comprehensive PQC preparedness solutions ensure security and ongoing operations:
Using NIST-standardized PQC algorithms and regular encryption methods, the platform provides trusted post-quantum encryption. This safeguards IP, customer data, and operational assets without slowing system performance. Proactive threat mitigation improves data security, privacy, and compliance.
Full-spectrum PQC server-side and client-side encryption from F5 protects on-site, cloud, and edge apps and APIs. This comprehensive solution comprises proactive threat intelligence, high-availability application delivery, encrypted threat protection, access security, and high-performance firewalls. According to insiders, guarding merely the client or server is insufficient because quantum threats could still affect data.
Consistent Operations and Crypto-Transition: The solutions integrate legacy, multicloud, and hybrid environments smoothly, allowing gradual system updates without disrupting business. F5's proxy capabilities let organisations to shift to post-quantum protocols and hybrid cryptographic frameworks at their own pace. This solution simplifies quantum-safe cryptography transition by reducing complexity and downtime.
Visibility uniform Across settings: F5's platform centralises administration and visibility across settings using AI, telemetry, and automation. This provides complete views of applications, APIs, and encrypted interactions, improving threat detection during PQC migrations.
F5 safeguards important assets, consumer confidence, and compliance using NIST-approved algorithms and quantum-resistant encryption. Breaches and outdated cryptography cause legal, financial, and reputational concerns.
Next steps and availability
In addition to being a technological prerequisite, post-quantum cryptography allows enterprises to innovate now and prepare for the future. F5's tailored hybrid cryptographic model support helps businesses deploy applications efficiently while preparing for post-quantum protocols and cybersecurity changes.
F5 Application Delivery and Security Platform solutions support Post-Quantum Cryptography. PQC preparation solutions, blog insights, and in-depth studies like “The State of PQC on the Web” from F5 Labs may help businesses prepare for the quantum danger.
F5 is the industry leader in application and API provision and security. After 30 years, F5's Application Delivery and Security Platform (ADSP) is the industry's leading platform for delivering and securing any application or API, whether on-premises, in the cloud, at the edge, or in hybrid and multicloud environments. F5 invents and works with the world's biggest and most innovative firms to build fast, secure, and accessible digital experiences to improve the digital world.
#PostQuantumCryptography#APIs#F5#quantumthreats#quantumcomputing#multicloud#cybersecurity#News#Technews#Technology#Technologynews#Technologytrends#Govindhtech
0 notes
Text
Cyber Security Summer Internship | Top Skills You’ll Learn

As the digital world grows, so does the need for skilled cybersecurity professionals. Organizations constantly seek individuals who can effectively protect their systems, detect vulnerabilities, and respond to cyber threats. For students and fresh graduates, enrolling in a Cyber Security Summer Internship is one of the best ways to build a strong foundation in this field.
At WebAsha Technologies, the Cyber Security Summer Internship program in Pune is designed to equip participants with the practical skills and knowledge needed to succeed in today’s cybersecurity landscape. In this article, we highlight the top skills you will learn during the internship.
Network Security Basics
One of the first areas you will explore is network security. This involves understanding how data moves across networks and learning to protect it from interception and attacks.
Learn the fundamentals of network architecture and protocols.
Understand how firewalls, routers, and switches function to secure networks.
Identify common network vulnerabilities and how to mitigate them.
Study intrusion detection and prevention systems (IDS/IPS).
Ethical Hacking Techniques
Ethical hacking teaches you to think like a hacker, but to strengthen system security. This skill is critical for finding and fixing vulnerabilities before they can be exploited.
Get familiar with various hacking methodologies and tools.
Learn reconnaissance, scanning, gaining access, maintaining access, and covering tracks.
Practice using tools such as Nmap, Metasploit, and Burp Suite.
Explore real-world hacking scenarios and practice ethical response methods.
Vulnerability Assessment and Penetration Testing (VAPT)
VAPT is a key component of any cybersecurity strategy. It helps organizations identify weaknesses in their systems through systematic testing.
Learn to conduct vulnerability assessments to discover security gaps.
Perform penetration tests to simulate real-world attacks.
Understand the phases of VAPT: planning, scanning, exploitation, and reporting.
Gain experience in documenting findings and suggesting remediation steps.
Web Application Security
With web applications being a major target for attackers, web security is a crucial skill.
Study common web application vulnerabilities, including SQL injection and cross-site scripting (XSS).
Learn how to test web apps for security flaws using automated and manual techniques.
Understand how to secure APIs and manage user authentication securely.
Get hands-on practice in identifying and mitigating web security risks.
Malware Analysis and Threat Detection
Another essential skill is the ability to analyze malware and detect potential threats before they cause damage.
Learn about different types of malware: viruses, worms, trojans, ransomware, and spyware.
Understand how malware behaves and propagates.
Use tools to detect, analyze, and remove malicious code.
Study case examples of high-profile malware attacks and their impacts.
Cryptography and Data Protection
Protecting sensitive data is a critical part of cybersecurity. You will gain an understanding of cryptography and how it ensures data security.
Learn the basics of encryption and decryption.
Understand the differences between symmetric and asymmetric encryption.
Explore digital signatures, certificates, and secure key management.
Study how cryptography is used in securing communications and transactions.
Incident Response and Handling
Responding quickly and effectively to a cyber incident is vital in minimizing damage.
Learn the stages of incident response: preparation, detection, containment, eradication, and recovery.
Practice creating incident response plans.
Understand how to preserve evidence and maintain the chain of custody.
Study real-world case studies to learn best practices.
Security Compliance and Best Practices
In addition to technical skills, understanding security standards and compliance is essential.
Get familiar with key standards like ISO 27001, GDPR, and PCI-DSS.
Learn best practices for creating security policies and procedures.
Understand the role of audits and risk assessments in maintaining compliance.
Final Thoughts
The Cyber Security Summer Internship at WebAsha Technologies is more than just a learning opportunity—it’s a stepping stone to a successful career in cybersecurity. By the end of the program, participants will have hands-on experience, a deep understanding of essential security practices, and the confidence to tackle real-world security challenges.
For students and IT enthusiasts looking to build a strong career foundation, this internship provides everything needed to get started. Enroll today and take the first step toward becoming a skilled cybersecurity professional.
#Cyber Security Summer Internship#Ethical Hacking Summer Training#VAPT Internship#Cyber Security Summer Course#Cyber Security Internship with Placement#Cyber Security Summer Bootcamp#Summer Internship in Cyber Security
0 notes
Text
Let's Learn About Asymmetric Encryption 👀

-> We have a pair of keys (public + private key).
-> Two major uses: encryption and signature.
-> In web3, your wallet is derived from your public key.
-> When you send a transaction, you sign it with your private key.
-> Blockchain nodes verify it using your public key and confirm it’s really you.
Learn More about Asymmetric Encryption & SSL Cryptography \/
0 notes
Text
Looking for Cyber Security Training and Cybersecurity Courses in Dadar, Mumbai?
In today's digital world, data security is more critical than ever. With cyberattacks becoming increasingly sophisticated, businesses and individuals alike require trained professionals to protect sensitive information. The demand for cybersecurity experts is rapidly growing. If you are looking to break into this exciting and lucrative field, Cyber Security Training in Dadar, Mumbai, is the perfect starting point for your career. Whether you're looking to enhance your current skills or embark on an entirely new career path, Cybersecurity courses in Dadar, Mumbai, provide you with the knowledge and expertise needed to succeed in the ever-evolving cybersecurity landscape.
Why Cyber Security Training Is Essential in Today's World
The world is becoming more connected through the internet, and with this increased connectivity comes greater vulnerability. Cyber threats such as hacking, identity theft, ransomware, and data breaches are real concerns that can cause devastating consequences for businesses and individuals. As a result, organizations worldwide are investing heavily in cybersecurity to protect themselves from these threats.
Cybersecurity professionals are in high demand across various industries, including finance, healthcare, government, and e-commerce. According to industry reports, the global cybersecurity workforce gap is expected to grow, meaning there will be an increasing need for skilled professionals. By enrolling in Cyber Security Training in Dadar, Mumbai, you position yourself to meet this demand and build a rewarding career.
What Are Cybersecurity Courses in Dadar, Mumbai?
Cybersecurity courses in Dadar, Mumbai, are designed to teach you the essential skills needed to protect organizations and individuals from cyber threats. These courses cover a wide range of topics, from basic security concepts to advanced techniques used by professionals to safeguard digital assets.
Here are some of the core areas typically covered in Cyber Security Training in Dadar, Mumbai:
1. Introduction to Cybersecurity
The foundation of any cybersecurity course is an understanding of the basic principles of digital security. This includes learning about:
Cyber threats: Common attacks like malware, phishing, and ransomware.
Security protocols: Encryption, firewalls, and secure communication protocols.
Types of cybercrimes: Understanding different ways cybercriminals exploit vulnerabilities.
2. Network Security
A significant portion of any cybersecurity curriculum focuses on network security, which involves protecting the network infrastructure from unauthorized access. This includes:
Firewall configurations and security measures.
Intrusion detection systems to monitor and identify potential threats.
Virtual private networks (VPNs) to create secure connections over the internet.
3. Ethical Hacking and Penetration Testing
Ethical hacking is an essential skill in cybersecurity, where professionals simulate attacks to find vulnerabilities before malicious hackers can exploit them. In Cybersecurity courses in Dadar, Mumbai, you'll learn how to:
Conduct penetration tests.
Identify and fix system vulnerabilities.
Understand standard hacking techniques and how to defend against them.
4. Cryptography
Cryptography plays a critical role in securing data. You'll learn how to protect sensitive information by encrypting it and understand various encryption algorithms, such as:
Symmetric and asymmetric encryption methods.
Public-key infrastructure (PKI) for secure communications.
5. Incident Response and Disaster Recovery
In the event of a cyberattack, having a solid incident response and disaster recovery plan is essential. You'll be trained in:
Responding quickly and effectively to security breaches.
Creating and testing recovery plans to restore systems after an attack.
6. Compliance and Risk Management
In cybersecurity, it's vital to understand regulatory requirements and risk management strategies to ensure compliance with laws like GDPR, HIPAA, and PCI-DSS. Most cybersecurity courses in Dadar, Mumbai, cover these areas in depth, teaching students how to protect sensitive data and avoid legal repercussions.
Why Dadar, Mumbai Is a Great Place to Start Your Cybersecurity Career
Dadar is a bustling area in the heart of Mumbai, offering a blend of commercial and residential spaces, making it a strategic hub for businesses and professionals. The area is home to several educational institutions and training centres offering top-tier Cyber Security Training in Dadar, Mumbai. The key advantages of pursuing cybersecurity courses in Dadar, Mumbai, include:
Proximity to tech companies: Many IT firms and businesses are based in Mumbai, providing plenty of job opportunities for cybersecurity professionals.
Networking opportunities: Dadar is well-connected, making it easy to attend industry events, meet professionals, and build a strong network within the cybersecurity field.
Access to experienced trainers: The training centres in Dadar offer instructors with real-world experience in cybersecurity, ensuring that you learn from experts in the field.
Career Opportunities After Completing Cybersecurity Training in Dadar, Mumbai
Upon completing Cyber Security Training in Dadar, Mumbai, a wide range of career opportunities opens up for you. Cybersecurity professionals are needed in every industry, and here are a few roles you can pursue:
1. Cybersecurity Analyst
Cybersecurity analysts are responsible for monitoring and protecting an organization's networks and systems from cyber threats. They implement security measures, analyze security breaches, and conduct regular system audits.
2. Ethical Hacker / Penetration Tester
Ethical hackers use their skills to identify vulnerabilities in a system before cybercriminals can exploit them. This role requires an in-depth understanding of hacking techniques and the ability to think like a hacker to defend systems.
3. Security Architect
A security architect designs robust security systems for an organization and ensures that all networks, applications, and devices are properly secured.
4. Incident Responder
Incident responders are crucial in mitigating the damage caused by cyberattacks. They are responsible for investigating security breaches, conducting forensic analysis, and implementing recovery strategies.
5. Chief Information Security Officer (CISO)
The CISO is responsible for overseeing an organization's entire cybersecurity strategy. They lead security teams, develop policies, and ensure compliance with legal and regulatory requirements.
Why Choose Mr Web Secure for Cyber Security Training in Dadar, Mumbai?
At Mr Web Secure, we offer comprehensive Cyber Security Training in Dadar, Mumbai, designed to equip you with the skills needed to excel in the cybersecurity field. Our courses are structured to cover everything from the basics to advanced security measures, ensuring that you gain practical knowledge that can be immediately applied in real-world situations.
Key Features of Our Courses:
Industry-experienced trainers who bring practical knowledge to the classroom.
Hands-on training using real-world tools and techniques.
Job placement assistance to help you secure a position in the cybersecurity industry.
Comprehensive curriculum covering ethical hacking, risk management, cryptography, and more.
Conclusion: Step Into the Future of Cybersecurity
As cyber threats become more sophisticated, the demand for cybersecurity professionals will continue to rise. If you're looking to kickstart your career in cybersecurity, Cyber Security Training in Dadar, Mumbai, is the perfect place to begin your journey. Whether you are just starting or looking to advance your skills, enrolling in cybersecurity courses in Dadar, Mumbai, will give you the knowledge and expertise to thrive in this high-demand field.
Ready to take the next step in your cybersecurity career? Contact Mr Web Secure today and enroll in our expert-led training programs. Let us help you unlock a prosperous future in cybersecurity.
#CyberSecurityTrainingInDadarMumbai
#CyberSecurityCoursesInDadarMumbai
#EthicalHackingCourseMumbai
#CyberSecurityCertificationDadar
#CyberSecurityJobsMumbai
0 notes
Text
Grok'
Cybersecurity Subjects List
Here’s a numbered list of 54 cybersecurity subjects, covering key areas like technical skills, risk management, and career development:
NIST Cybersecurity Framework
CIS Top 20 Controls / CIS Benchmarks
ISO 27001 / 27017 / 27018
OWASP Top 10
MITRE ATT&CK Framework
S-SDLC
Security UX
Security QA
API Security
Source Code Scan
Data-Flow Diagram
Vulnerability Scan
Assets Inventory
3rd Party Risk
Penetration Test
Risk Monitoring Services
Risk Treatment Actions
Risk Acceptance Statement
Cyber Insurance
Lines of Defense
Risk Register
Risk Appetite
Crisis Management
BCP/DR
Laws and Regulations
Executive Management Involvement
Company Written Policy
External Threat Intelligence
Internal Threat Intelligence
Training
Awareness
Cyber Security Table-Top Exercises
Vulnerability Management
Active Defense
Incident Response
Security Operation Centers
SIEM
Threat Hunting
IoT Security
Network Design
Secure System Build
Cryptography
Security Engineering
Access Control
Cloud Security
Container Security
Endpoint Hygiene
Data Protection
__________________________________________
Gemini
Comprehensive List of Cybersecurity Subjects
To provide a structured overview of the vast cybersecurity landscape, the identified subjects can be grouped into logical categories. This categorization helps to create a mental model of the field and understand the relationships between different areas. The following table presents a comprehensive list of cybersecurity subjects organized under relevant categories, along with a brief description of each.
Technical Security
Network Security
Protecting the integrity, confidentiality, and availability of network infrastructure and data. Key concepts include firewalls, IDS/IPS, VPNs, and network protocols.
Application Security
Securing software applications throughout their development lifecycle. Includes secure coding, vulnerability assessment, and web application firewalls.
Data Security
Protecting data at rest, in transit, and in use. Involves encryption, data loss prevention, data masking, and access control.
Endpoint Security
Securing individual user devices such as desktops, laptops, and mobile devices. Includes antivirus, EDR, and patch management.
Cloud Security
Addressing the security challenges and considerations specific to cloud computing environments, including IaaS, PaaS, and SaaS security.
Operational Technology (OT) Security
Securing industrial control systems (ICS) and other operational technology used in industries like manufacturing and energy.
Mobile Security
Protecting mobile devices, their data, and the networks they connect to. Includes MDM and mobile application security.
Cryptography
The study and practice of techniques for secure communication in the presence of adversaries. Includes symmetric and asymmetric encryption, hashing, and digital signatures.
Vulnerability Management
The process of identifying, classifying, prioritizing, remediating, and mitigating software vulnerabilities.
Security Architecture
Designing and planning the overall security infrastructure of an organization, considering various security domains and technologies.
Security Engineering
Implementing and maintaining security systems and infrastructure based on the security architecture.
Governance, Risk, and Compliance
Security Governance
Establishing and maintaining the overall direction and control of an organization's security efforts, including policies and procedures.
Risk Management
Identifying, assessing, and mitigating cybersecurity risks to an organization's assets and operations.
Regulatory Compliance
Ensuring adherence to relevant laws, regulations, and industry standards such as GDPR, HIPAA, and PCI DSS.
Security Auditing
Assessing the effectiveness of security controls and compliance with policies and regulations through systematic examination.
Business Continuity and Disaster Recovery (BC/DR)
Planning for and recovering from disruptive events, including cyberattacks, to ensure business operations can continue.
Policy Development and Implementation
Creating and deploying security policies, standards, and guidelines within an organization.
Human Factors in Security
Security Awareness and Training
Educating users about security threats and best practices to reduce human error and improve the overall security posture.
Social Engineering Awareness
Understanding and mitigating the risks associated with social engineering attacks such as phishing, vishing, and pretexting.
Insider Threat Management
Implementing strategies and controls to detect, prevent, and respond to security threats originating from within the organization.
Offensive Security
Ethical Hacking
Using hacking techniques legally and ethically to identify vulnerabilities and improve security.
Penetration Testing
Simulating cyberattacks on systems and networks to assess their security posture and identify exploitable vulnerabilities.
Vulnerability Analysis and Exploitation
The process of examining systems and applications to identify security weaknesses and developing methods to exploit them for testing purposes.
Threat Hunting
Proactively searching for undetected threats that may have bypassed traditional security defenses.
Digital Forensics & Incident Response
Incident Response Planning
Developing and documenting procedures for handling and recovering from security incidents in a coordinated and effective manner.
Digital Evidence Collection and Analysis
Gathering and analyzing digital evidence in a forensically sound manner to understand security incidents and support investigations.
Malware Analysis
Examining malicious software to understand its functionality, behavior, and potential impact.
Security Operations Center (SOC) Management
The management and operation of a centralized team responsible for monitoring and responding to security events.
Threat Intelligence Analysis
Gathering, analyzing, and disseminating information about current and emerging cyber threats to inform security decisions and proactive defenses.
Emerging Security Domains
Artificial Intelligence (AI) and Machine Learning (ML) in Cybersecurity
Applying AI and ML techniques for threat detection, anomaly detection, automated incident response, and predictive security analytics.
Internet of Things (IoT) Security
Securing the growing number of interconnected devices, including their hardware, software, and communication protocols.
Blockchain Security
Understanding and securing blockchain technologies and their applications, including cryptocurrencies and decentralized applications (dApps).
DevSecOps
Integrating security practices throughout the software development lifecycle, from design to deployment and operation.
Zero Trust Security
Implementing a security model based on the principle of "never trust, always verify," requiring strict identity verification for every user and device.
Quantum Computing and Post-Quantum Cryptography
Addressing the potential impact of quantum computers on current cryptographic algorithms and developing new, quantum-resistant cryptographic methods.
Cyber-Physical Systems (CPS) Security
Securing systems that integrate computational and physical processes, such as autonomous vehicles and smart grids.
Privacy Engineering
Designing and implementing systems and processes with privacy considerations embedded throughout.
1 note
·
View note
Text
CS 6260 – Applied Cryptography
CS 6260 is an advanced course dedicated to the design, application, and analysis of cryptographic protocols. It teaches students how cryptographic systems work in practice, covering core concepts such as symmetric and asymmetric encryption, hash functions, digital signatures, message authentication, and key exchange protocols. The course also explores real-world applications like TLS, blockchain…
0 notes
Text
Cryptography: The Science of Securing Digital Information

Data security is now a top concern in today's digital environment. Whether it's online banking, social media, or business transactions, protecting sensitive information is essential. Here's when cryptography comes into play. Cryptography is the science of encrypting and decrypting data to ensure that only authorized users can access it. From securing personal messages to safeguarding national security, cryptography has become a fundamental pillar of cybersecurity.
What is Cryptography?
Cryptography involves transforming data into an unreadable format (ciphertext) using encryption techniques. The data can only be converted back into its original form using a special decryption key. This guarantees that hackers will be unable to decode the data even if they manage to intercept it.
With advancements in technology, cryptography has evolved from simple manual ciphers to highly complex mathematical algorithms. Today, it is widely used in securing emails, online banking, cloud storage, and digital signatures.
Types of Cryptography
Symmetric Cryptography: Uses a single key for both encryption and decryption. It is fast but requires secure key-sharing between sender and receiver.
Asymmetric Cryptography: Uses two keys—one public and one private. It is commonly used in secure email communication and digital signatures.
Hash Functions: Converts data into a fixed-length hash value that cannot be reversed. It is used to store passwords and secure blockchains.
The Importance of Cryptography in Cybersecurity
As cyber threats increase, cryptography has become essential in securing sensitive information. Here’s why cryptography is crucial:
Data Privacy: Prevents unauthorized access to critical information.
Authentication: Ensures that only legitimate users have access to data.
Data Integrity: Detects any alterations or tampering in sent data.
Secure Communication: Protects digital interactions from cyber threats.
Cryptography in Online Transactions
Cryptography plays a significant role in securing online transactions. It ensures the safety of financial transactions by encrypting credit card details and personal information. Online banking and digital payments would be extremely vulnerable to fraud if encryption were not used.
In the e-commerce industry, cryptographic techniques such as SSL/TLS encryption secure transactions, protecting users from cyber threats like phishing and identity theft.
Cryptography in Blockchain and Cryptocurrency
Blockchain technology relies heavily on cryptography for security. Digital currencies like Bitcoin and Ethereum use cryptographic hashing and digital signatures to secure transactions. Each transaction is encrypted, making it nearly hard for hackers to alter the data.
Digital signatures verify the authenticity of transactions, ensuring that only the rightful owner can access and transfer digital assets. This makes cryptography a critical element in securing decentralized financial systems.
Building a Career in Cryptography with Professional Training
With the rising demand for cybersecurity experts, cryptography has become a highly sought-after skill. Companies worldwide are looking for professionals who can implement encryption techniques to secure digital assets. Enrolling in Training programs in cryptography can open career opportunities in roles such as:
Cybersecurity Analyst
Cryptographic Engineer
Blockchain Developer
Ethical Hacker
Security Consultant
Learning cryptographic techniques through Training programs provides hands-on experience in encryption, digital security, and hacking prevention. As cyber threats continue to grow, having expertise in cryptography can give professionals a competitive edge.
Conclusion
Cryptography is a critical component of digital security, protecting personal and corporate data from cyber threats. From securing online transactions to ensuring the integrity of blockchain networks, encryption techniques are essential for safeguarding digital assets.
If you're interested in a career in cybersecurity, gaining expertise in cryptography is a smart move. Enroll in a Training program to develop essential skills and stay ahead in this rapidly evolving field. To explore courses and certification programs, visit EasyShiksha.com today!
0 notes
Text
Key Steps for a Successful Migration to Post-Quantum Cryptography
With quantum computing progressing, transitioning to post-quantum cryptography (PQC) is crucial. Quantum computers threaten current cryptographic systems by efficiently solving complex mathematical problems used in asymmetric Public Key Cryptography (PKC). Post-Quantum Cryptography (PQC), or quantum-resistant cryptography, develops algorithms secure against quantum computer attacks, which uses…
0 notes