#Data security solutions
Explore tagged Tumblr posts
Text
Bots Now Dominate the Web: Why This Growing Problem Demands Urgent Action

The digital world, once a bustling marketplace of human interaction, has undergone a silent, pervasive transformation. Data from 2024 and early 2025 reveals a startling reality: bots now dominate web traffic, accounting for over 50% of all internet activity. While some of these automated programs are "good" – diligently indexing content for search engines or enabling helpful chatbots – a significant and escalating proportion are "bad bots," mimicking human behavior for malicious purposes. This widespread bot dominance web traffic presents a serious and ever-growing problem for businesses, cybersecurity, and the overall integrity of the web. The sheer volume and sophistication of these malicious bots internet traffic are redefining the landscape of online security.
The rise of bot traffic on the internet is significantly fueled by rapid advancements in Artificial Intelligence (AI) and Large Language Models (LLMs). These technologies simplify the creation and scaling of sophisticated, evasive bots, allowing even less skilled malicious actors to launch high-volume attacks. As of early 2025, malicious bots account for a staggering 37% of all internet traffic, a substantial increase from previous years, signaling a deepening bot problem online.
The Unseen Majority: How Bots Came to Dominate the Web
For the first time in a decade, automated traffic has surpassed human activity. This shift is primarily attributed to the proliferation of AI and LLMs, which have democratized bot development, making it more accessible to a wider range of actors. These advancements enable bots to mimic human interaction with startling accuracy, often bypassing traditional security measures.
The sophistication of these bad bots internet traffic is constantly evolving. They employ techniques like IP rotation, mimicking legitimate browser fingerprints, and distributing attacks across vast networks of compromised devices (botnets). The goal is simple: evade detection by blending in with legitimate web traffic automation. This makes it increasingly difficult for organizations to differentiate between genuine human users and malicious automated scripts, amplifying the bot problem online.
The Multifaceted Problem: Impacts of Bot Dominance

The pervasive presence of malicious bots internet traffic creates a myriad of complex and costly issues across various aspects of the digital economy. Understanding the full scope of the impact of bots on business is crucial for developing effective defense strategies.
Financial Drain & Fraud
The direct financial implications of bot fraud are staggering. Malicious bots are instrumental in various fraudulent activities that directly hit a business's bottom line:
Credential Stuffing and Account Takeovers (ATOs): Bots automate login attempts using stolen username/password combinations from data breaches. Successful ATOs lead to financial theft, misuse of loyalty points, and damage to customer trust.
Carding and Gift Card Fraud: Bots test stolen credit card numbers against e-commerce sites or attempt to drain balances from stolen digital gift cards, leading to chargebacks and direct financial losses.
Ad Fraud and Click Fraud: Bots simulate clicks and impressions on online advertisements, depleting advertisers' budgets without generating genuine leads or conversions. This distorts analytics and wastes significant marketing spend.
Scalping and Inventory Hoarding: In industries with high-demand, limited-stock items (like concert tickets, sneakers, or popular gaming consoles), bots rapidly purchase inventory, only for it to be resold at inflated prices on secondary markets. This infuriates legitimate customers and damages brand reputation.
Cybersecurity Risks & Data Integrity
Cybersecurity bot attacks represent a fundamental threat to an organization's digital infrastructure and sensitive data. Bots are often the first line of attack in broader cyber campaigns:
Vulnerability Scanning and Exploitation: Bots automatically scan websites and APIs for known vulnerabilities (e.g., SQL injection, cross-site scripting), identifying weak points that can then be exploited for unauthorized access or data exfiltration.
Distributed Denial-of-Service (DDoS) Attacks: Botnets, vast networks of compromised devices controlled by attackers, flood target websites, servers, or networks with overwhelming volumes of traffic, rendering them inaccessible to legitimate users.
API Abuse: With the rise of API-driven applications, bots increasingly target APIs to scrape data, create fake accounts, exploit business logic, or launch sophisticated fraud schemes that bypass traditional web application firewalls.
Data Scraping: Competitors or malicious actors use bots to steal valuable data, including pricing information, product catalogs, customer reviews, and proprietary content, leading to competitive disadvantage and intellectual property theft.
Operational & Performance Disruptions
The sheer volume of web traffic automation from bots places immense strain on IT infrastructure:
Server Strain and Increased Costs: High bot traffic consumes valuable server resources, bandwidth, and computing power, leading to increased hosting expenses and the need for costly infrastructure upgrades.
Degraded Website Performance: Overwhelmed servers result in slower loading times, timeouts, and poor responsiveness for legitimate users, severely impacting user experience and conversion rates.
Skewed Analytics: Bot traffic contaminates website and application analytics, inflating metrics like page views, unique visitors, and clicks while distorting bounce rates and conversion rates. This leads to flawed business decisions based on inaccurate data.
Brand Reputation & Trust
Beyond the technical and financial impacts, bot dominance web traffic erodes trust and damages brand reputation:
Spam and Misinformation: Spam bots flood comment sections, forums, and social media platforms with unsolicited advertising, malicious links, or propaganda, harming a website's credibility and user experience.
Customer Frustration: When legitimate customers are unable to access services due to DDoS attacks, or when they can't purchase items due to bot-driven scalping, their frustration can quickly turn into negative reviews and a damaged brand image.
SEO Penalties: Google and other search engines penalize websites with low-quality or duplicate content, which can result from content scraping by bots, negatively impacting search engine rankings and organic traffic.
Industries Under Siege: Where Bot Threats are Most Acute

While the bot problem online affects nearly every sector, certain industries consistently face a higher proportion and more sophisticated online bot threats:
Financial Services: A primary target due to the sensitive nature of data and high-value transactions. They face relentless account takeover bots, credential stuffing, and fraud attempts.
Retail: Highly susceptible to bot fraud related to inventory scalping, gift card fraud, price scraping, and loyalty program abuse.
Travel: Experiences a significant percentage of bad bots internet traffic, used for competitive price scraping, account takeovers, and fraudulent bookings.
Gaming: Often sees the highest proportion of sophisticated bot traffic, including bots used for cheating, account compromise, and inventory manipulation within in-game economies.
Media and Entertainment: Targeted for content scraping, ad fraud, and credential stuffing on streaming platforms.
Fighting Back: Strategies for Bot Management and Mitigation

Combating bot dominance requires a proactive, multi-layered, and continuously evolving defense strategy. Relying on outdated methods is no longer sufficient against today's sophisticated malicious bots internet attacks.
Advanced Bot Management Solutions: The cornerstone of modern bot defense. These specialized platforms utilize a combination of behavioral analysis (distinguishing human-like patterns from automated ones), machine learning (adapting to new bot tactics), device fingerprinting, and real-time threat intelligence. They go beyond simple IP blocking or CAPTCHAs to detect and mitigate even the most evasive bots.
Robust API Security: Given that 44% of advanced bot traffic targeted APIs in 2024, securing these digital gateways is paramount. Implementing strong authentication mechanisms (like OAuth, API keys), strict access controls, and rate limiting on API endpoints can significantly reduce the attack surface for API security bots. Regular API penetration testing is also crucial.
Multi-Factor Authentication (MFA): Implementing MFA adds a critical layer of security beyond just passwords. Even if bots manage to acquire stolen credentials through credential stuffing, MFA can prevent unauthorized access by requiring a second verification step (e.g., a code from a mobile app), drastically reducing account takeover bots success rates.
Continuous Monitoring and Analytics: Businesses must actively monitor their web traffic automation for unusual patterns. This includes spikes in requests from a single IP, abnormally high failed login attempts, unusual user-agent strings, or suspicious conversion rates. Real-time dashboards and automated alerts are essential for early detection of online bot threats.
Regular Security Audits and Patching: Proactive vulnerability management is key. Regularly auditing web applications, APIs, and underlying infrastructure for security flaws, and promptly patching identified vulnerabilities, closes potential entry points for bots.
User-Agent and Proxy Analysis: Many simpler bots still rely on outdated browser user-agent strings or operate through known dubious proxy services. Implementing rules to block traffic from such indicators can filter out a significant portion of commodity bot attacks. Detecting traffic from residential proxies, which more advanced bots now use, requires more sophisticated analysis.
Rate Limiting and Throttling: While not a complete solution, judiciously applying rate limits on specific endpoints (e.g., login pages, search functions, API calls) can prevent brute-force attacks and resource exhaustion caused by excessive bot requests.
Conclusion: Securing the Human-Centric Web
The landscape of the internet has fundamentally shifted. Bots now dominate the web, and this poses a significant, evolving bot problem online for businesses, their customers, and the integrity of digital interactions. From sophisticated bot fraud schemes to debilitating cybersecurity bot attacks, the impact is wide-ranging and costly.
Ignoring this reality is no longer an option. As AI continues to empower bots to become even more evasive and intelligent, businesses must embrace comprehensive and adaptive bot management solutions. Investing in robust API security, implementing strong authentication, and continuously monitoring for unusual patterns are not merely best practices; they are essential for survival in the current digital climate.
The future of the web depends on our ability to effectively differentiate between humans and machines, safeguarding digital assets and ensuring a secure, reliable, and authentic online experience for everyone. By adopting proactive strategies, organizations can protect their revenue, reputation, and customer trust from the pervasive and growing threat of malicious web traffic automation. The time for urgent action is now.
#Cyber Security Services Company | Data Security Solutions#Top-rated Cyber Security Services Company Offering Advanced Protection#Threat Detection#Risk Assessment#Data Security Solutions For Businesses Worldwide.#Cybersecurity services company#Data security solutions#Managed cybersecurity services#Enterprise cyber protection#Data breach prevention services#Cyber threat protection#IT security solutions provider#Endpoint security services#Network security services#Cybersecurity consulting company
0 notes
Text
Explore VoxTBV robust data security and protection solutions Safeguard your data with our comprehensive data protection technologies and services
0 notes
Text
Why Did India’s Finance Ministry Restrict the Use of AI Tools in Offices? A Closer Look at the Decision
In a significant move, India’s Finance Ministry recently issued an advisory restricting the use of artificial intelligence (AI) tools, such as ChatGPT, Bard, and other generative AI platforms, in government offices. This decision has sparked widespread debate, with many questioning the rationale behind it. Why would a government, in an era of rapid technological advancement, curb the use of tools that promise efficiency and innovation? Let’s delve into the logic and reasoning behind this decision, including the geopolitical implications and the growing global AI race, particularly with China. Read more
#Finance Ministry India AI ban#AI tools restriction India#data security and AI#geopolitical AI race#China AI development#AI governance India#ChatGPT and DeepSeek ban in government#AI and national security#indigenous AI solutions#ethical AI use in government.
3 notes
·
View notes
Video
youtube
🌈 Ready to Start Earning with GotBackUp? Here’s Your Guide! 💰
Imagine combining data security with financial freedom. GotBackUp isn’t just another backup service—it’s a whole new way to secure your data and earn an income by sharing it with others. 📂✨
What’s GotBackUp All About?
💼 Earn Residual Income by referring people to secure their files and memories.
🌍 Work from Anywhere—GotBackUp is perfect for remote workers, network marketers, and anyone looking for extra income.
🔒 Peace of Mind knowing that your data is safe and accessible whenever you need it.
How to Get Started:
Share GotBackUp with your network.
Help people see the value of protecting their digital lives.
Watch your income grow with every referral!
Curious? Reach out to me for more details, or click the link to explore how GotBackUp can start working for YOU today!
👉 https://bit.ly/3XNMpzO
Let’s make 2024 your year of financial growth and digital peace of mind! 🌟
#GotBackUp #PassiveIncome #DataSecurity #NetworkMarketing #RemoteWorkLife #EarnWithGotBackUp #FinancialFreedom #SideHustle #DigitalProtection #BackupSolutions
(via 🔥 Ready to Start Earning with GotBackUp? Here’s How! 💰)
#gotbackup#passive income#data security#network marketing#remote work life#earn with gotbackup#financial freedom#side hustle#digital protection#backup solution
3 notes
·
View notes
Text
RFID library Automation for tracking, security and inventory management
LIBSYS Limited, a software as a service(SAAS) company based in Gurugram, Delhi-NCR, India, was founded in 1984 by Mr. Anil Jain to cater the needs of Identity, Tracking and Security purpose for various Indian industries. With the aim to automate the process and minimizing the human errors to zero, the Libsys offers a wide range of solutions that include Library Management Systems for institutions and government bodies, RFID based customized applications from small business to multinational organizations, Common Admission Platform and ERP for Academic Institutes, Omni-channel Retailing solution, E-Commerce Framework, CRM, Design & Architecture and other on demand solutions.
The experience of 40 years and counting along with in-depth understanding of the Indian markets, we are the proud leaders of quality and innovation. Through the experience we have, we have the ability to respond quickly to the customized client requirements with an innovative solutions that meet those needs efficiently and cost effectively. Our experience and strong mission-first work ethic has helped us develop capabilities, insights, and skills to provide the best solution one can have. Backed by our strong quality processes and rich experience in managing clients across various domains, we strive for continuous innovations in our offerings, and we take pride in being the pioneer and market leader for RFID based automation solution in India.
To name a few, software products like LIBSYS 10 LMS, LSEase, LSmart-RFID, LSRemote, LSDiscovery, LSe-RMS, symphonyX, TargetX, LSNetX (E-Com) and LSales1 CRM are the benchmarks in India serving across the domains and delivering the best operational efficiency solutions for all organizations and enterprises.
TRANSFORMING LIBRARIES
Elevate your Library
LIBSYS 10 caters to all the needs of library automation improving the efficiency of libraries and providing a delightful library experience through continuous technological innovations
Smooth Library Operations
LIBSYS 10 simplifies and automates essential library management tasks, allowing for efficient cataloging, circulation, and inventory management.
Enhanced Accessibility
Libsys 10 offers a user-friendly interface and robust search capabilities, enabling patrons to easily discover and access library resources.
Comprehensive Reporting
Libsys 10 generates detailed reports on library usage, collection statistics, and circulation trends, facilitating decision-making and resource allocation
Seamless Integration
Libsys 10 seamlessly integrates with various library systems, ensuring smooth interoperability and minimizing disruptions in existing work-flows
LIBSYS10
LIBRARY MANAGEMENT SIMPLIFIED
Step into the future
A web based library management solution to enhance the total library experience through value added features and services.
The present times demand Library Management System to deliver much more than operational efficiency. It needs to create appreciable staff satisfaction and a delightful experience for the patrons every time they interact with the system. LIBSYS is committed to delivering value to the libraries through its products. In-depth understanding of library operations, implicit needs of the patrons, and dedicated R&D efforts have guided us to deliver high-quality products that have found wide acceptance in the market space.
Its seamless work-flow enables library staff to manage library operations efficiently.
New purchase approvals, collection development, material handling, SDI services, bindery management, and a host of other functions form an integral part of the system.
MARC21 / RDA interface, Cooperative Cataloguing along with controlled authority files helps in Cataloguing on the fly.
Federated Searching brings other libraries of similar collection within your reach.
REQUEST A DEMO
MODULES
GO BEYOND THE LIBRARY
Modernize Your Library
LIBSYS 10 is a smart library management system covering all the needs of library automation in India and abroad.
Acquisition
LIBSYS 10 automated library acquisition system is capable of efficiently managing all kinds of work-flow
Cataloguing
Catalogue your records smarter and faster way with user friendly yet powerful cataloguing module.
Serial Control
Easily control and maintain your library’s serials collection in the most efficient way.
Circulation
Easy and powerful interface to handle circulation transactions, alerts, greetings, reminders, fine etc.
KEY FEATURES
Check Out Capabilities
LIBSYS 10 is a feature-rich Library Management System that empowers libraries to effectively manage their collections, streamline operations, provide enhanced services to patrons, and embrace modern technologies for a seamless library experience. Our automated acquisition system in library reduces time consuming work and enhances the overall efficiency in ordering and provides necessary management information reports.
Online Public Access Catalog (OPAC)
Digital Resource Management
Reporting and Analytics
Integration and Interoperability
Mobile Accessibility
BENEFITS
30+ YEARS
Scale Your LMS
LIBSYS 10 empowers libraries to optimize their operations, improve user satisfaction, and adapt to evolving technological advancements in the library field. It enhances the overall library experience for both librarians and patrons.
Streamlined Operations
Libsys 10 automates various library tasks, reducing manual efforts and saving time for librarians.
Efficient Resource Management
The system helps librarians effectively manage library resources, including books, journals, multimedia, and digital materials.
Enhanced User Experience
Libsys 10 enhances the experience for library patrons through its user-friendly OPAC interface.
Accessibility Anytime, Anywhere
Libsys 10's mobile accessibility ensures that library services and resources are available to patrons anytime, anywhere.
LIBSYS10
HARNESS THE POTENTIAL OF OUR LIBRARY MANAGEMENT SYSTEM!
#1 Library Management System
Unlock the Power of Efficiency and Innovation with Libsys
The present times demand Library Management System to deliver much more than operational efficiency. It needs to create appreciable staff satisfaction and a delightful experience for the patrons every time they interact with the system. LIBSYS is committed to delivering value to the libraries through its products. In-depth understanding of library operations, implicit needs of the patrons, and dedicated R&D efforts have guided us to deliver high-quality products that have found wide acceptance in the market space.
The new Web-based Library Management System ‘LIBSYS 10’ provides a greatly enhanced user experience through value-added features and services. LIBSYS 10 is built on international standards and open technologies, i.e. JAVA. It covers Acquisition, Cataloguing, Circulation, Serials, Articles Indexing, E-Books, Dean and Vendor Portals along with an enriched OPAC. Its seamless work-flow enables library staff to manage library operations efficiently. New purchase approvals, collection development, material handling, SDI services, bindery management, and a host of other functions form an integral part of the system. MARC21 / RDA interface, Cooperative Cataloguing along with controlled authority files helps in Cataloguing on the fly. Federated Searching brings other libraries of similar collection within your reach.
LIBSYS 10 gives you the opportunity to take your automated library circulation system to new heights by use of RFID / EM / Hybrid Technology. Choose LSmart / KSmart system as per your budget and requirements. Use of these technologies will help in hassle free, accurate and faster issue / return of books, inventory visibility, accuracy and efficiency, increases security function in the library, improved utilization of resources like manpower, infrastructure etc., give flexible library timings. The bottom line is that the synergy between the latest technology like RFID and libraries can create wonders resulting in empowerment of both users as well as librarians.
LIBSYS Library Management System in India has been deployed in many prestigious institutes. LIBSYS 10 caters to all the needs of library automation improving the efficiency of libraries and providing a delightful library experience through continuous technological innovations. With rich experience of more than three decades along with continuous innovation, LIBSYS has emerged as the best library management system in India.
We also undertake special projects which include multi-location library automation and RFID system implementation. The projects are executed by specialized teams comprising of experienced professionals from Library and IT domains. Our customer-focused services also include consulting to meet individual needs, organizing User meets, and providing regular software updates.
For more details connect at [email protected] or +91-0124-4894100
#rfid#rfid solutions#rfid technology#rfid reader#rfid tags#library#inventorymanagement#inventory software#assets#assetprotection#assetmanagement#tracking tag#data security#software#technology#trackinghome#cyber security#social security#cybersecurity
2 notes
·
View notes
Text

In this article, we’ll explore what GDPR is, why it’s essential for businesses to comply, and how AI can help with data privacy protection and GDPR compliance. Learn More...
#cloud technology#ai data privacy#ip phones#unified communications#hotel hospitality#VoIP#ip telephony#hotel phone system#voip solutions#GDPR#Protection#Data Security#EU Regulation#Technology News#phonesuite pbx#hotel phone installation#technology#hotel pbx
2 notes
·
View notes
Text
Cybersecurity Made Easy: Sigzen Technologie’s Approach to Effective Vulnerability Management
In today’s digital age, cybersecurity is paramount to safeguarding sensitive data and maintaining business continuity. As cyber threats continue to evolve, organizations must adopt comprehensive strategies to mitigate risks effectively. Sigzen Technologies offers cutting-edge solutions in Vulnerability Management, making cybersecurity easy and effective for businesses of all sizes. Vulnerability…

View On WordPress
#Cybersecurity Solutions#Data Privacy#Information Security#Network Vulnerabilities#Security Solutions#Vulnerability Management
3 notes
·
View notes
Text
Epilouge:




In a fantasy setting, my job would be exactly the same
#in my irl job to “brick” a device is to send a signal to it so as soon as it's turned on the hard drive encrypts itself#making the device useless and unusable#it's a security measure to ensure that if someone finds the device they can't access sensitive company data#yeah sure they can wipe the device and reinstall an OS and use it then#but IMPORTANTLY the company data is gone#we'll claim back the cost of the lost device from insurance#in a fantasy setting the solution to lost devices is more elegant#myart
38K notes
·
View notes
Text
Business IT Solution for Digital Transformation Success
Modern leaders must act fast because change never slows. Moreover, IT solutions for business now shape every growth plan. As digital tools take over daily work, every business must adopt the right strategy to stay ahead. From cloud systems to data protection, smart moves make a big difference . Small steps bring big results when paired with a clear vision. Digital transformation is not just a tech shift—it is a cultural shift. Therefore, success depends on smart planning, strong support, and the right tools. This post shows clear steps, simple tools, and steady wins that let any firm thrive.
Why a Business IT Solution Drives Continuous Value
However, every market shifts daily, and data grows hourly. Therefore, a Business IT Solution guides teams, aligns systems, and cuts waste. Moreover, clear dashboards reveal gaps; thus, leaders adjust in time. Consequently, profits rise while risks fall.
Business IT Solution for Cloud Adoption
Furthermore, cloud shifts the cost from capital to usage. Hence, teams pay only for real demand. Because of this, apps scale during peaks and shrink during dips. Consequently, users enjoy smooth service without extra spending.
#business IT solutions#digital transformation#IT strategy#cloud adoption#secure data#system integration#agile methods#data-driven decisions#technology for business#IT for growth#business innovation#digital tools#IT support#enterprise technology#process automation.
0 notes
Text
Kriptone Data Loss Protection: The Ultimate Smart Security Solution

In today’s digital world, data is more valuable than ever—it powers business growth but is also at constant risk. It can be lost or stolen through mistakes, system failures, or internal leaks. Like gold needs to be stored safely, your data needs strong protection. That’s where Kriptone Data Loss Protection (DLP) comes in—a smart, flexible solution designed to safeguard your most valuable digital assets.
What is Data Loss Protection (DLP)?
(DLP) keeps your sensitive information safe from leaks, misuse, or unauthorized access—ensuring it stays where it belongs.
Exploring the Difference Between Data Loss and Leakage
Data loss is permanent, like when a hard drive fails and erases customer records. Data leakage, however, is sneaky—it’s when sensitive info leaks through weak points like unapproved apps or human mistakes. Loss is harsh, but leakage is slow and often more harmful over time. Kriptone’s DLP technology prevents both, stopping leaks before they spread and protecting against data loss.
The Top Threats to Your Data Today
Data threats can come from everywhere—from cybercriminals to well-meaning employees. Let’s dive into the major risks that can impact your information.
External Attacks: Hackers, Malware, and Phishing
Cybercriminals are now part of organized groups using advanced tools like AI-driven malware and phishing attacks. Their goal is to steal and profit from your data. Kriptone’s DLP uses threat intelligence to detect and stop these attacks before they can steal your information.
The Business Impact of Data Loss
A single data breach can cause major damage, harming systems, reputations, and even leading to legal issues. Data loss isn’t only a technical issue; it’s a crisis that affects the entire business.
From Revenue to Reputation: The Fallout of a Breach
When data is lost, trust is shattered clients back off, investors worry, and competitors take advantage. Similarly Extra costs from legal actions, fines, and system breaks make the problem worse. Kriptone helps businesses avoid this by providing constant, smart protection that’s always on and defending.
Key Features of a Strong DLP Strategy
Not all DLP tools are the same. A strong defence needs to be smart, proactive, and adaptable—just like the threats it’s meant to stop.
Real-Time Monitoring and Alerts: Eyes Everywhere
Kriptone monitors data 24/7 across endpoints, networks, and the cloud. If something unusual happens, it quickly locks down files, alerts security teams, and tracks the breach.
Types of DLP Solutions Explained
Choosing the right DLP depends on where your data is stored, how it moves, and who needs access. Kriptone offers solutions designed for today’s flexible, decentralized workspaces.
Endpoint DLP: Securing Devices at the Edge
Endpoint DLP protects data on employee devices. Kriptone’s solution blocks unauthorized copying, printing, or transferring of data, whether the device is online or offline.
The Future of Data Loss Protection
Cyber threats move fast, and DLP must keep up. Kriptone is shaping the future of data protection with Smart Data Security automation and predictive analytics.
AI and Machine Learning in Next-Gen DLP
Kriptone uses Smart Data Security AI to stop threats before they start. However, It learns from past events, adapts to user behavior, and spots unusual activity in real-time, creating a DLP system that’s not just reactive, but smart and adaptive.
Conclusion
In conclusion,Data loss will happen eventually, but proactive defense can limit the damage. Kriptone Data Loss Protection isn’t just a tool—it’s a promise to defend your valuable data with intelligence and precision. Security should be relentless, not reactive. Whether you’re a global enterprise or a startup, Kriptone helps you protect your most critical asset before it’s too late. In addition, Today, protecting your data smartly is essential, not a choice.
#it security services#data loss prevention solutions#endpoint security#It cyber security services#data loss protection
0 notes
Text
We offer AWS Security Services that help protect your data, applications, and infrastructure in the Amazon Web Services (AWS) cloud. protect your data with our Data Security Solutions.
0 notes
Text
Why Managed IT Services for Cloud Scalability are Essential for Modern Enterprises
In the rapidly evolving technology landscape, managed IT services for cloud scalability have become the cornerstone of successful digital transformation initiatives. As IT professionals and decision-makers navigate increasingly complex cloud environments, the strategic importance of partnering with specialized managed service providers cannot be overstated.
Furthermore, the challenges facing today's IT departments extend far beyond simple infrastructure management. Consequently, organizations require comprehensive solutions that address scalability, security, and operational efficiency simultaneously. This is precisely where managed IT services for cloud scalability demonstrate their transformative value.
Understanding the Technical Foundation of Managed IT Services for Cloud Scalability
Managed IT services for cloud scalability represent a sophisticated approach to infrastructure management that combines deep technical expertise with strategic business alignment. Unlike traditional IT support models, these services focus specifically on creating elastic, responsive cloud environments that can adapt to changing business demands.
Moreover, the technical complexity of modern cloud architectures requires specialized knowledge across multiple domains. Therefore, managed service providers invest heavily in developing expertise in containerization, microservices architecture, auto-scaling technologies, and hybrid cloud deployments. This comprehensive technical foundation enables them to deliver scalable solutions that traditional in-house teams often struggle to implement effectively.
Additionally, the integration of emerging technologies such as Kubernetes orchestration, serverless computing, and edge computing requires continuous learning and adaptation. Consequently, managed service providers maintain dedicated teams of cloud architects and engineers who specialize in these cutting-edge technologies.
The Strategic Advantages of Professional Cloud Scalability Management
Advanced Infrastructure Optimization and Cost Engineering
One of the most significant benefits of managed IT services for cloud scalability lies in sophisticated cost optimization strategies. Specifically, experienced MSPs employ advanced analytics and monitoring tools to identify inefficiencies and optimize resource allocation across your cloud infrastructure.
Furthermore, professional cost engineering involves implementing intelligent auto-scaling policies, rightsizing instances, and leveraging spot instances and reserved capacity strategically. As a result, organizations typically achieve 20-40% cost reductions while simultaneously improving performance and reliability.
Additionally, MSPs utilize advanced FinOps methodologies to provide detailed cost attribution and chargeback mechanisms. This transparency enables IT leaders to make informed decisions about resource allocation and budget planning.
Enterprise-Grade Security and Compliance Architecture
Security considerations in scalable cloud environments require multi-layered approaches that extend beyond basic perimeter protection. Therefore, managed IT services for cloud scalability implement comprehensive security frameworks that include zero-trust architecture, advanced threat detection, and automated incident response capabilities.
Moreover, compliance requirements such as SOC 2, ISO 27001, GDPR, and HIPAA demand specialized expertise and continuous monitoring. Consequently, managed service providers maintain dedicated compliance teams and invest in advanced security tools that many organizations cannot justify internally.
In addition, the implementation of Infrastructure as Code (IaC) and DevSecOps practices ensures that security controls are embedded throughout the development and deployment lifecycle. This approach significantly reduces vulnerabilities and improves overall security posture.
Proactive Performance Engineering and Capacity Planning
The difference between reactive and proactive infrastructure management often determines the success or failure of critical business applications. Therefore, managed IT services for cloud scalability emphasize predictive analytics and performance engineering to prevent issues before they impact operations.
Furthermore, advanced monitoring and observability platforms provide real-time insights into application performance, infrastructure utilization, and user experience metrics. This comprehensive visibility enables proactive optimization and capacity planning that ensures optimal performance during peak demand periods.
Additionally, the implementation of chaos engineering principles and automated testing frameworks helps identify potential failure points and improves system resilience. Consequently, organizations experience significantly reduced downtime and improved service reliability.
Technical Expertise and Specialized Knowledge Areas
Cloud-Native Architecture and Microservices Implementation
Modern managed IT services for cloud scalability require deep expertise in cloud-native architecture patterns and microservices design principles. Specifically, this includes proficiency in container orchestration platforms, service mesh technologies, and API gateway management.
Moreover, the successful implementation of microservices architectures requires understanding of distributed systems challenges, including service discovery, load balancing, and distributed tracing. Therefore, managed service providers invest in specialized training and certification programs to maintain current expertise.
Additionally, the integration of continuous integration and continuous deployment (CI/CD) pipelines with cloud-native technologies requires sophisticated automation and orchestration capabilities. This expertise enables rapid deployment cycles while maintaining high quality and reliability standards.
Multi-Cloud and Hybrid Cloud Strategy Implementation
The complexity of multi-cloud and hybrid cloud environments demands specialized expertise in integration, data synchronization, and workload optimization across diverse platforms. Consequently, managed IT services for cloud scalability providers develop comprehensive multi-cloud strategies that leverage the strengths of different cloud providers.
Furthermore, the implementation of hybrid cloud architectures requires deep understanding of network connectivity, data gravity considerations, and latency optimization techniques. This expertise enables organizations to optimize workload placement and achieve optimal performance across diverse environments.
Additionally, the management of multi-cloud environments requires sophisticated orchestration and automation tools that can operate consistently across different cloud platforms. This capability enables organizations to avoid vendor lock-in while maximizing the benefits of each cloud provider.
Strategic Implementation Methodologies
DevOps Integration and Automation Excellence
The successful implementation of managed IT services for cloud scalability requires seamless integration with existing DevOps processes and toolchains. Therefore, managed service providers develop comprehensive automation frameworks that enhance rather than disrupt existing workflows.
Moreover, the implementation of GitOps principles and declarative infrastructure management enables consistent, repeatable deployments across multiple environments. This approach significantly reduces configuration drift and improves system reliability.
Additionally, the integration of advanced monitoring and logging solutions with DevOps toolchains provides comprehensive visibility into the entire application lifecycle. Consequently, development teams can identify and resolve issues more quickly and efficiently.
Performance Optimization and Scaling Strategies
Advanced performance optimization requires deep understanding of application architecture, database design, and caching strategies. Therefore, managed IT services for cloud scalability providers employ specialized performance engineers who focus on optimizing every aspect of the technology stack.
Furthermore, the implementation of intelligent auto-scaling policies requires careful analysis of application behavior, traffic patterns, and resource utilization metrics. This analysis enables the development of sophisticated scaling strategies that maintain optimal performance while minimizing costs.
Additionally, the optimization of database performance in cloud environments requires expertise in both traditional relational databases and modern NoSQL solutions. This knowledge enables organizations to select and optimize the most appropriate data storage solutions for their specific use cases.
Measuring Success and ROI
Key Performance Indicators and Metrics
The effectiveness of managed IT services for cloud scalability must be measured through comprehensive KPIs that align with business objectives. Specifically, these metrics include system availability, response time, throughput, cost per transaction, and scalability efficiency ratios.
Moreover, the implementation of advanced analytics and business intelligence tools provides real-time visibility into these metrics and enables data-driven decision making. Therefore, organizations can continuously optimize their cloud infrastructure based on actual performance data.
Additionally, the establishment of service level agreements (SLAs) and service level objectives (SLOs) provides clear expectations and accountability frameworks. This transparency ensures that managed service providers deliver consistent, measurable value.
Business Impact and Competitive Advantage
The strategic value of managed IT services for cloud scalability extends beyond technical metrics to include business impact measurements such as time-to-market improvements, innovation velocity, and competitive positioning. Therefore, successful implementations focus on aligning technical capabilities with business objectives.
Furthermore, the ability to rapidly scale infrastructure in response to market opportunities or unexpected demand spikes provides significant competitive advantages. This agility enables organizations to capitalize on growth opportunities that might otherwise be missed due to infrastructure constraints.
Unlock Your Cloud Potential with Managed IT Services
Managed IT services for cloud scalability represent a strategic imperative for organizations seeking to leverage cloud computing effectively. Furthermore, the technical complexity and rapid evolution of cloud technologies make specialized expertise essential for achieving optimal results.
Additionally, the strategic benefits extend beyond cost optimization to include improved agility, enhanced security, and competitive positioning. Therefore, organizations that invest in professional managed services position themselves for long-term success in an increasingly digital marketplace.
Moreover, the partnership with experienced managed service providers enables IT teams to focus on strategic initiatives and innovation rather than routine infrastructure management. Consequently, this alignment of resources and expertise drives both operational efficiency and business growth.
Ready to transform your cloud infrastructure with professional managed services? Explore our comprehensive managed services solutions and discover how we can help your organization achieve scalable cloud success.
Frequently Asked Questions
What expertise should I expect from managed IT services for cloud scalability? Expect expertise in cloud-native architectures, Kubernetes, Infrastructure as Code (Terraform), multi-cloud integration, and certifications from AWS, Azure, GCP.
How are managed IT services for cloud scalability different from traditional IT outsourcing? Managed IT services focus on proactive, scalable cloud solutions, whereas traditional IT outsourcing is often reactive and less flexible.
What role does automation play in managed IT services for cloud scalability? Automation ensures consistent cloud performance through scaling, monitoring, and incident response.
How can I evaluate potential managed service providers? Evaluate their expertise in cloud architecture, automation, security, and ability to integrate with your systems.
What key factors should be considered for cloud scalability in enterprise environments? Consider compliance, system integration, multi-cloud management, security, and SLA adherence.
#technology#hardwin software solutions#data security#devops services#it consulting#managed it services
0 notes
Text
Senior Backend Engineer - Web3
Job title: Senior Backend Engineer – Web3 Company: Certus Recruitment Job description: growing independent research and advisory client is a guiding force in the ever-changing world of Crypto. As experts in MEV… architecture for efficiency and reliability. Ensure Security & Reliability: Implement best practices for security, monitoring… Expected salary: £130000 – 160000 per year Location: Greater…
#Aerospace#Bioinformatics#Broadcast#cloud-native#Crypto Security Specialist#data-privacy#DevOps#dotnet#edtech#ethical-hacking#generative AI#govtech#iOS#Machine learning#Networking#NFT#prompt-engineering#proptech#Python#qa-testing#remote-jobs#rpa#Salesforce#SoC#software-development#solutions-architecture#system-administration#visa-sponsorship#vr-ar
0 notes
Text
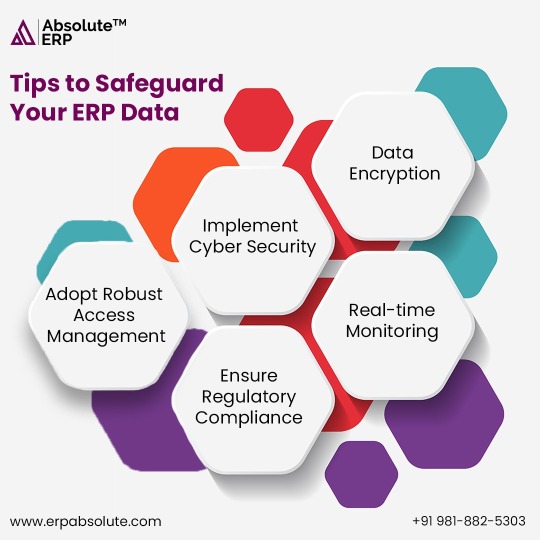
#ERP Data#ERP Safety#ERP Solutions#Enterprise Resource Planning Software#Data Management#Data Security
1 note
·
View note
Text
Why IoT Testing is Essential for Reliable and Secure Connected Solutions
The Importance of IoT Testing for Seamless Connected Experiences
The Internet of Things (IoT) is transforming how organizations operate, from home automation, wearables, and industrial automation to smart cities. IoT products have unique characteristics that require reliable communication, high performance, and properly secured implementation to maximize overall effectiveness. GQATTech has the expertise in IoT testing to ensure these products and/or systems undergo test scenarios that resemble a real environment with proper connections to reliant components. This blog will explain the importance of testing IoT components and how our methodology in testing enables organizations to deliver reliable, secure, and scalable experiences with connected products.
What is IoT Testing?
Internet of Things (IoT) testing involves testing an entire IoT ecosystem, such as the devices, networks, protocols, and applications, in terms of functionality, interface, performance, security, interoperability, and usability. IoT testing differs from traditional software testing as it deals with the challenge of various devices communicating via different protocols (e.g., MQTT, CoAP, HTTP) over a variety of platforms and in different environments. It ensures IoT systems perform consistently, protecting confidential information and being able to work with and integrate with other systems.
Why IoT Testing Matters
1. Verifying Device Functionality
IoT devices need to do what they are supposed to do, whether it's a smart thermostat adjusting temperature or an industrial sensor monitoring a piece of equipment. The purpose of functional testing is to verify that each device works correctly in a variety of situations, including reliable data collection, processing, and communication. If a device malfunctions, workflow or user experience can be completely disrupted, so rigorous testing is a must.
2. Validating Performance
IoT ecosystems can include thousands of devices processing massive data and transactions in real-time. Performance testing verifies that the device or system can process data at scale, maintain low latency, and react easily to avoid bottlenecks. If you think about the holiday season (for smart retail), like Black Friday, performance testing verifies that the devices will work during high traffic times, remain responsive, and stable.
3. Data and Privacy Security
IoT devices typically capture many types of private or sensitive information, from personal health data to industrial insights about operations. Security testing basically finds weak points, whether hardware (i.e., device firmware), communication (i.e., protocols), or cloud, by identifying vulnerabilities in integrations and configurations. Compliance with regulations like GDPR or HIPAA is instrumental, and our testing program at GQATTech focuses on making sure your IoT solutions either establish compliance or meet requirements where they exist, protecting users' trust
4. Verifying Interoperability
IoT devices need to integrate efficiently through different hardware types, software types, and network protocols. Interoperability testing will ensure everything from the device itself to the platforms (iOS, Android, cloud) and communication standards will be compatible. Conducting interoperability tests can prevent integration issues, such as getting a smart home device to connect to your smartphone/mobile application or connecting to a cloud platform. Ensuring a user experience flows as a whole, as opposed to segregated aspects working independently, can further limit user frustration.
5. Enhancing the User Experience
In terms of positively influencing acceptance and adherence to an IoT system, the user experience must be seamless. User experience studies can help identify and validate how usable/easy to use the devices and applications built around them are to the end user. User experience testing can evaluate how simple the user can navigate through the initial setup process and continue through real-time post-deployment interaction and control of the IoT system. Enhancing the usability of the IoT system will positively influence how satisfied the user is with the end product, which will ultimately drive user engagement.
Key Types of IoT Testing We Offer
At GQATTech, we customize our IoT testing services to meet the unique needs of your business. The main types of testing we provide are as follows:
Functional Testing: Confirms the behavior and functionality of the device.
Performance Testing: Tests how the complete system works during high data volume and concurrent traffic.
Security Testing: Tests the security of the hardware, software, and cloud for potential vulnerabilities.
Interoperability Testing: Verifies the system's performance when integrated with all components.
Usability Testing: Determines how easy the IoT solutions are to use.
Regression Testing: Verifies that new updates do not break the existing functionality.
Why Choose GQATTech for IoT Testing?
At GQATTech, we offer comprehensive, consistent IoT solutions by leveraging experience, as well as an established testing process to take the guesswork out of your IoT solutions. We use both manual and automated testing methodologies, with one mission: to find defects as early as possible to minimize any chances of costly remediations while still meeting your time-to-market expectations. Whatever your scenario, launching, upgrading your devices, or integrating third-party platforms, we have a bespoke testing plan for your specific planned use case, so that you have peace of mind when launching and the reliability, security, and scalability of your devices have been thoroughly tested.
Our testing process entails:
Tailored Testing Plans: Tailored to the customer so that it mirrors your IoT use case. Whether that be smart homes, healthcare, or industrial IoT, we can build a solution that mirrors your use case.
Modern Tools: Utilize state-of-the-art test cases and current testing frameworks, such as JMeter and Cucumber, that simulate real-world situations, and also validate APIs, cloud deployments, and varied use case situations.
End-to-End Testing: Including all devices, network, cloud platform, and user interface to create an acceptable baseline against client validations.
Compliance Oversight: Legal compliance with GDPR, HIPAA compliance, and ensuring IoT implementations against the proper protocols.
Conclusion
Not only is IoT testing a necessity in technology, but it is an area you need to invest in before you begin to build secure, reliable, and user-centric connected experiences. When you engage GQATTech to test your IoT, you will feel comfortable knowing you can grow or scale your IoT ecosystem with a deliberate approach towards security, performance, efficacy, and user experience.
Are you prepared to confidently build out your IoT solutions? Get in touch with the GQATTech team today to see how our IoT testing services can realize your digital transformation aspirations.Visit Us: https://gqattech.comContact Us:[email protected]
#IoT Testing#Internet of Things#Device Testing#Functional Testing#Performance Testing#Security Testing#Interoperability Testing#Usability Testing#Regression Testing#IoT Security#Smart Devices#Connected Systems#IoT Protocols#GQATTech#IoT Solutions#Data Privacy#System Integration#User Experience#IoT Performance#Compliance Testing
0 notes