#EcommerceSecurity
Explore tagged Tumblr posts
Text
#MagentoDevelopment#eCommerceSolutions#Magento#WebDevelopment#OnlineStore#DigitalAgency#CustomeCommerce#MagentoExperts#ScalableeCommerce#KazeDigital#eCommerceSecurity#InventoryManagement#MagentoDesign#MagentoDevelopers#BusinessGrowth
0 notes
Text
Secure and Compliant E-commerce Platforms for Peace of Mind
Security and compliance are paramount in e-commerce. At Rang Digitech, acknowledged as the best digital marketing agency in New Jersey, we prioritize robust security protocols and adherence to industry standards. Protect your business and customers with our reliable e-commerce solutions.
#EcommerceSecurity#ComplianceStandards#DigitalMarketingNJ#RangDigitech#SecureShopping#DataProtection#OnlineSafety#BestDigitalAgency#NJBusinessSecurity#TrustedEcommerce
0 notes
Text
🛡️💳 Your customers aren’t the only ones shopping. Fraudsters are too.
Ecommerce fraud prevention isn’t just a security measure — it’s a business survival strategy. With increasing digital transactions, detecting and stopping fraud in real time is critical.|
This blog explores: 🚨 Common types of ecommerce fraud and their warning signs 🧠 Role of AI and predictive analytics in catching fraud before it strikes 🛠️ Practical strategies to secure your store without ruining UX
Whether you're an ecommerce owner, CMO, or product strategist — this guide gives you the tools to protect revenue and build customer trust.
#EcommerceFraudPrevention#FraudDetection#PredictiveAnalytics#SecureEcommerce#AIForRetail#DigitalRiskManagement#PaymentSecurity#KodyTechnolab#EcommerceSecurity#TechForRetail#SmartSecuritySolutions#CustomerTrust#CXSecurity
0 notes
Text
Safeguard your customers' data and build unwavering trust in your online store. Partner with a leading E-Commerce Website Development Company to implement cutting-edge privacy and security measures. Read more : https://justpaste.it/ftnoo Visit our website : https://grehasoft.com/ecommerce-development/ ✅8th Floor, Vismaya Building, Infopark Phase 1, Kakkanad, Kochi, Kerala 682042✅[email protected] ✅[email protected] ✅+91 8921 54 0183 https://api.whatsapp.com/message/ZXON2Y5PQEI7D1

#EcommerceSecurity#CustomerTrust#EcommerceWebsiteDevelopment#DataProtection#OnlineShoppingSafety#SecureEcommerce#PrivacyMatters#EcommerceSolutions#DigitalTrust#CyberSecurity
0 notes
Text
Two Suspects Arrested for Kidnapping Online Vendor in Lagos
The Lagos State Police Command has apprehended two individuals accused of kidnapping an online vendor who went to deliver goods in the Iyana-Ishashi area of Lagos. Incident Overview According to CSP Benjamin Hundeyin, the command’s spokesperson, the victim was abducted while fulfilling a delivery order. During a press briefing at the police headquarters in Ikeja on Monday, Hundeyin disclosed…
0 notes
Text
Verify Aadhaar details via API
In India, Aadhaar has become an essential identification tool for millions of citizens, used across a variety of services ranging from banking and government schemes to mobile number verifications and more. Ensuring the accuracy and authenticity of Aadhaar details has become paramount, particularly for businesses that require identity verification.
EKYChub, a leading provider of digital solutions, offers an efficient and reliable API service for Aadhaar verification. This blog explores how EKYChub’s Aadhaar Verification API can help businesses streamline their identity verification process while ensuring compliance with legal and security standards.

What is Aadhaar Verification?
Aadhaar verification refers to the process of confirming whether the provided Aadhaar number belongs to a valid and active individual. In India, the Aadhaar number is linked to a person’s biometric and demographic data, which is stored securely by the Unique Identification Authority of India (UIDAI).
Businesses, government entities, and service providers need to verify Aadhaar details for a wide range of purposes, including:
Authentication of beneficiaries for government welfare schemes
KYC (Know Your Customer) processes for banks and financial institutions
Mobile number activation
Digital signing for online transactions
How EKYChub’s Aadhaar Verification API Works
EKYChub provides a seamless, reliable, and secure Aadhaar verification service through its API. With just a few lines of code, businesses can integrate Aadhaar verification into their existing applications, websites, or mobile platforms. The process works as follows:
API Integration: After registering with EKYChub, you’ll receive API credentials. These credentials allow you to integrate the Aadhaar verification API into your platform.
Aadhaar Number Submission: When a user provides their Aadhaar number, the API sends a request to EKYChub’s server.
UIDAI Database Check: EKYChub then verifies the Aadhaar details against the official UIDAI database. This includes checking the validity of the Aadhaar number, and optionally, verifying biometric or demographic details.
Response: The API returns a response indicating whether the Aadhaar number is valid and if the provided details match the records. The response can be customized to include additional information based on your requirements.
Secure & Compliant: All verification processes are secure, leveraging encryption and adhering to UIDAI’s legal and regulatory standards. EKYChub also ensures that no sensitive data, like biometrics, is ever stored or compromised.
Benefits of Using EKYChub’s Aadhaar Verification API
Faster KYC & Authentication: By integrating EKYChub’s Aadhaar verification, businesses can speed up the KYC process. Real-time verification eliminates delays associated with manual document checks and improves the customer experience.
Cost-Effective: Building and maintaining a secure Aadhaar verification system can be resource-intensive. EKYChub’s API provides a cost-effective alternative, allowing businesses to avoid the costs of infrastructure and regulatory compliance.
High Accuracy: EKYChub’s API integrates with UIDAI’s database, ensuring the accuracy and authenticity of the Aadhaar details, minimizing the risk of fraud or errors.
Scalable: Whether you're a startup or a large enterprise, EKYChub’s API is scalable to meet your needs. As your business grows, the API can handle increasing volumes of verification requests without a hitch.
Security and Privacy: The platform adheres to strict data privacy and security guidelines set by UIDAI, ensuring the protection of users' sensitive information. The data transmission is encrypted, and EKYChub complies with the highest security standards.
Regulatory Compliance: EKYChub ensures that your Aadhaar verification process is fully compliant with the laws and regulations set by the Government of India, including data protection and usage norms defined by UIDAI.
Multi-Purpose Use Cases: The API can be used in various industries such as banking, telecom, healthcare, government services, and e-commerce, where identity verification is essential.
How Businesses Can Leverage Aadhaar Verification API
Businesses in several sectors can benefit from EKYChub's Aadhaar verification API:
Banking & Financial Institutions: Conduct real-time KYC checks and onboard customers quickly and securely.
Telecom Industry: Verify the Aadhaar details of users for mobile number registrations and recharges.
Government Services: Ensure that beneficiaries of welfare schemes are correctly identified and eligible for services.
E-Commerce & Startups: Validate the identities of users for payments, online registrations, and access to secure services.
Healthcare: Validate patient records and verify the identity of individuals accessing healthcare benefits.
Conclusion
EKYChub’s Aadhaar Verification API is a powerful tool for businesses looking to streamline their identity verification processes. It not only ensures the accuracy and security of Aadhaar details but also helps companies comply with legal requirements, reduce operational costs, and enhance customer trust.
With seamless integration and high scalability, EKYChub’s Aadhaar Verification API is an indispensable tool for businesses aiming to leverage India’s unique digital identification system. If you're looking to simplify your identity verification process, EKYChub’s API offers an easy, secure, and efficient solution.
#techinnovation#tech#identityvalidation#kycverificationapi#technology#ekychub#technews#fintech#aadhaarintegration#aadhaarverificationapi#AadhaarVerification#EKYChubAPI#AadhaarAPI#KYCVerification#IdentityVerification#UIDAI#DigitalVerification#SecureAPI#Compliance#FintechSolutions#BankingTechnology#TelecomVerification#GovernmentServices#ECommerceSecurity#BiometricVerification#AadhaarAuthentication#SecureTransactions#DigitalIndia#TechSolutions#AadhaarIntegration
0 notes
Text

The secure payment integration builds trust in people's hearts regarding your Gojek Clone App. And they also get top-notch services with few clicks.
#v3cube#securepayments#gojekclone#paymentintegration#appsecurity#digitalpayments#usertrust#fintechsolutions#mobileappdevelopment#ecommercesecurity#techinnovation
0 notes
Text
Adobe Commerce Security Update: APSB25-08 Patch Details & Fixes
Adobe has released a critical security update (APSB25-08) for Adobe Commerce and Magento Open Source to address vulnerabilities, including arbitrary code execution and privilege escalation. Affected versions include 2.4.8-beta1, 2.4.7-p3, 2.4.6-p8, and earlier. Adobe recommends immediate updates, with priority ratings categorized as 1 and 2. For complete details, refer to the Adobe Security Bulletin (APSB25-08).
0 notes
Text
Luxury Authentication Service Market Forecast: Growing E-commerce and Counterfeit Concerns Drive Demand
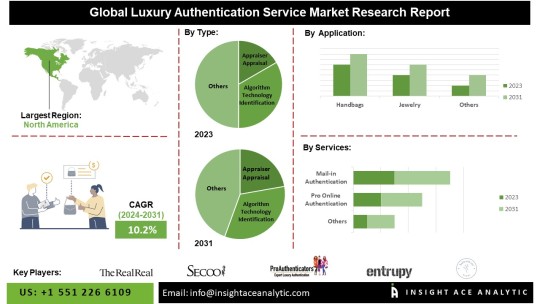
InsightAce Analytic Pvt. Ltd. announces the release of a market assessment report on the "Global Luxury Authentication Service Market – (by Type (Appraiser Appraisal, Algorithm Technology Identification), Application (Handbags, Jewelry, Watches, Clothing, Others), Services (Pro Online Authentication, Mail-in Authentication, In-person Authentication, Customer Service Hotline)), Trends, Industry Competition Analysis, Revenue and Forecast To 2031."
According to the latest research by InsightAce Analytic, the Global Luxury Authentication Service Market is predicted to grow with a CAGR of 10.2% during the forecast period of 2024-2031.
Get Free Access to Demo Report, Excel Pivot and ToC: https://www.insightaceanalytic.com/request-sample/2541
The industry is seeing expansion due to the rising occurrence of counterfeit luxury products, leading to an increased demand for trustworthy authentication services. The integration of blockchain, AI, and machine learning is improving the efficiency and accuracy of authentication processes. In addition, the rise of the e-commerce industry is making a substantial contribution to the market's expansion. This is because the online sales of luxury items require strong authentication methods to guarantee the authenticity of the products.
The regional market is expected to dominate the market, which is attributed to high consumer demand and technological advancements. The increasing disposable income & growing preference for luxury items in emerging markets further contribute to the market's expansion. Moreover, collaborations between luxury brands and authentication service providers are fostering market growth by integrating authentication as a value-added service in the luxury shopping experience.
List of Prominent Players in the Luxury Authentication Service Market:
Real Authentication
Vestiaire Collective
TheRealReal
Secoo Holdings Inc.
ProAuthenticators
Komehyo
Entrupy
Authenticate Plus
Authenticate First
Authenticate 4 U
Market Dynamics:
Drivers-
Increasing consumer awareness about counterfeit luxury goods and the need for genuine products have significantly bolstered demand. As the global market for luxury items continues to grow, so does the necessity for reliable authentication services to ensure the legitimacy of high-value purchases. Advances in technology, like blockchain, artificial intelligence, have also enhanced the accuracy and efficiency of authentication processes, attracting more consumers and businesses to these services. Additionally, the rise of online marketplaces for second-hand luxury goods has amplified the need for authentication to build trust and assure quality among buyers.
Expert Knowledge, Just a Click Away: https://calendly.com/insightaceanalytic/30min?month=2024-02
Challenges:
One of the prime hurdles is the constant evolution and sophistication of counterfeit goods, which makes it increasingly difficult for authentication services to stay ahead of fraudsters. This requires continuous investment in advanced technology and expertise, raising operational costs. Additionally, there is a growing demand for rapid authentication services, which puts pressure on these companies to deliver quick yet accurate results, often necessitating substantial infrastructure and resource allocation. Trust is another critical issue; consumers must have unwavering confidence in the accuracy asb well as reliability of the authentication process. Any slip-ups or errors can severely damage the reputation of an authentication service.
Regional Trends:
The luxury authentication service market in North America is experiencing significant growth, propelled by increasing consumer demand for verified high-end products and the rise of the second-hand luxury goods market. With growing awareness of counterfeit items, consumers and retailers alike are prioritizing the assurance of authenticity for luxury items such as handbags, watches, jewellery, and fashion. This market includes both online platforms and brick-and-mortar establishments offering expert authentication services. Technological advancements, such as blockchain & AI, are being integrated to enhance the accuracy & reliability of these services. Significant Key players in the region are focusing on expanding their service offerings and improving their authentication processes to cater to a discerning clientele that values trust and transparency. The North American market is poised for continued growth as the luxury resale market expands and consumers increasingly seek authenticated sustainable luxury goods.
Recent Developments
In Oct 2023, Entrupy expanded its luxury authentication services to social media by establishing an official collaboration with TikTok. As an official TikTok Shop authenticator in the U.S., Entrupy will provide authentication services for premium items. Entrupy's verification procedure has an accuracy rate over 99 percent, offering robust protection to businesses, customers, and sellers against counterfeit and fraudulent merchandise.
Unlock Your GTM Strategy: https://www.insightaceanalytic.com/customisation/2541
Segmentation of Luxury Authentication Service Market-
By Type
Appraiser Appraisal
Algorithm Technology Identification
By Application
Handbags
Jewelry
Watches
Clothing
Others
By Services
Pro Online Authentication
Mail-in Authentication
In-person Authentication
Customer Service Hotline
By Region-
North America-
The US
Canada
Mexico
Europe-
Germany
The UK
France
Italy
Spain
Rest of Europe
Asia-Pacific-
China
Japan
India
South Korea
South East Asia
Rest of Asia Pacific
Latin America-
Brazil
Argentina
Rest of Latin America
Middle East & Africa-
GCC Countries
South Africa
Rest of Middle East and Africa
Empower Your Decision-Making with 180 Pages Full Report @ https://www.insightaceanalytic.com/buy-report/2541
About Us:
InsightAce Analytic is a market research and consulting firm that enables clients to make strategic decisions. Our qualitative and quantitative market intelligence solutions inform the need for market and competitive intelligence to expand businesses. We help clients gain competitive advantage by identifying untapped markets, exploring new and competing technologies, segmenting potential markets and repositioning products. Our expertise is in providing syndicated and custom market intelligence reports with an in-depth analysis with key market insights in a timely and cost-effective manner.
0 notes
Text
How Greip Enhances Payment Security for E-commerce Platforms

E-commerce platforms face significant challenges in preventing fraudulent transactions. Greip's AI-driven modules offer effective solutions to enhance payment security.
Problem Statement:
E-commerce businesses often struggle with fraudulent transactions, leading to financial losses and damaged reputations.
Application:
An online retailer integrates Greip's Credit Card Fraud Detection and BIN/IIN Lookup modules to assess the authenticity of transactions in real-time. The system analyzes transaction data, user behavior, and device information to identify potential fraud.
Outcome:
The retailer experiences a significant reduction in fraudulent transactions, leading to increased customer trust and higher conversion rates.
Industry Examples:
Online Retailers: Protect against fraudulent purchases and chargebacks.
Subscription Services: Ensure legitimate sign-ups and prevent account takeovers.
Digital Content Providers: Safeguard against unauthorized access and piracy.
Discover how Greip can enhance your payment security. Visit aiwikiweb.com/product/greip
0 notes
Text
WooCommerce User Roles: Security, Permissions, and Best Practices
WooCommerce is one of the most popular e-commerce platforms, seamlessly integrating with WordPress to provide a comprehensive solution for online store management. One of its key features is the ability to manage user roles, allowing store owners to assign different levels of access and responsibility to various users. Properly managing these user roles is crucial for maintaining the security of your WooCommerce store and ensuring that each team member has the appropriate level of access.
In this blog, we'll explore WooCommerce user roles, their security implications, permissions management, and best practices to follow for an effective and secure e-commerce operation.

1. Understanding WooCommerce User Roles
WooCommerce, built on WordPress, leverages the existing WordPress user role system while adding a few custom roles specific to e-commerce. Understanding these roles and their permissions is the first step in managing your WooCommerce store effectively.
Default WordPress User Roles
Administrator: The highest level of access, with the ability to manage the entire site, including adding and removing plugins, changing themes, and managing all content and users.
Editor: Can manage and publish posts, including those of other users, but has no access to site settings or plugins.
Author: Can publish and manage their own posts but cannot manage others' posts.
Contributor: Can write and manage their own posts but cannot publish them.
Subscriber: Has the lowest level of access, typically only able to manage their profile.
WooCommerce-Specific User Roles
Shop Manager: A role added by WooCommerce, allowing users to manage all aspects of the online store, including products, orders, and WooCommerce settings, without having full administrative access to the website.
Customer: Automatically assigned to users who register during checkout, this role allows customers to view their orders and manage their profiles.
2. Security Implications of WooCommerce User Roles
Each user role in WooCommerce User Roles has specific permissions that can directly impact the security of your online store. Mismanaging these roles can lead to unauthorized access, data breaches, or even a complete takeover of your site. Let's explore the security implications of each role.
Administrator
Since Administrators have full control over the website, including WooCommerce settings, plugins, and themes, it's critical to limit the number of users with this role. Only trusted individuals, such as the site owner or a lead developer, should have Administrator access. Any compromise of an Administrator account could lead to catastrophic consequences, such as data loss or site defacement.
Shop Manager
Shop Managers have significant control over the store, including the ability to manage products, process orders, and view customer data. While they cannot alter site settings or install plugins, a compromised Shop Manager account could still lead to severe security issues, such as unauthorized refunds or data exposure.
Customer
The Customer role is relatively low-risk, as these users can only view their own orders and manage their profiles. However, it's still essential to protect customer data, as breaches could lead to identity theft or fraud.
3. Managing Permissions in WooCommerce
Managing user permissions in WooCommerce involves assigning the right roles to the right people and customizing permissions when necessary. By doing so, you can ensure that each user has the access they need without exposing your store to unnecessary risks.
Role-Based Access Control (RBAC)
RBAC is a method of managing user permissions based on their roles. In WooCommerce, this means assigning roles like Shop Manager, Customer, or Administrator to users based on their responsibilities. RBAC ensures that users only have the permissions necessary to perform their job functions.
Customizing User Roles
In some cases, the default roles provided by WooCommerce may not perfectly align with your store's needs. For example, you might need a role that allows users to manage orders but not products or view reports without accessing customer data. In these situations, you can use plugins like "User Role Editor" or "Members" to create custom roles with tailored permissions.
Implementing Principle of Least Privilege (PoLP)
The Principle of Least Privilege (PoLP) is a security concept that suggests users should be granted the minimum level of access necessary to perform their tasks. In WooCommerce, this means carefully evaluating each user's responsibilities and assigning them the lowest-privilege role that still allows them to do their job. For instance, if a user only needs to manage orders, they should be given the "Shop Manager" role instead of "Administrator."
4. Best Practices for WooCommerce User Role Management
Effective user role management is key to maintaining the security and functionality of your WooCommerce store. Here are some best practices to follow:
1. Limit the Number of Administrators
As the most powerful role, the Administrator should be assigned sparingly. Ideally, only one or two trusted individuals should have Administrator access, reducing the risk of accidental changes or unauthorized access.
2. Use Two-Factor Authentication (2FA)
Two-Factor Authentication adds an extra layer of security by requiring users to provide a second form of verification, such as a code sent to their mobile device. Implementing 2FA for all users, especially Administrators and Shop Managers, can significantly reduce the risk of account compromise.
3. Regularly Review User Roles and Permissions
It's essential to regularly review the roles and permissions assigned to users, especially as your store grows and evolves. Users who no longer need access should have their roles downgraded or accounts deactivated to minimize potential security risks.
4. Monitor User Activity
Monitoring user activity can help detect unusual or unauthorized actions, such as changes to products, settings, or customer data. Plugins like "Activity Log" can provide insights into who did what and when, allowing you to respond quickly to potential security threats.
5. Use Strong Password Policies
Enforcing strong password policies is another critical aspect of securing your WooCommerce store. Require all users to create strong, unique passwords that include a mix of letters, numbers, and special characters. Consider implementing a password manager to help users store and manage their passwords securely.
6. Educate Users on Security Best Practices
Educating users, especially those with elevated roles like Shop Managers and Administrators, on security best practices is essential. This includes training on recognizing phishing attempts, understanding the importance of secure passwords, and knowing how to respond to potential security incidents.
5. Advanced Role Management Techniques
While the default WooCommerce roles and permissions system is robust, advanced users may want to take role management a step further. Here are some techniques and tools that can help:
Custom Capabilities
WordPress allows you to define custom capabilities for user roles, which can be useful if you need granular control over what users can and cannot do. For example, you can create a custom capability that allows users to manage orders but not view customer details.
Role Hierarchies
Role hierarchies allow you to create a system where some roles inherit the permissions of others. This can be useful in complex WooCommerce setups where you need to manage multiple user types with varying levels of access.
Plugin Integration
Several WooCommerce plugins can extend the functionality of user roles and permissions. For example, the "WooCommerce Memberships" plugin allows you to create membership levels with specific permissions, while the "WooCommerce Subscriptions" plugin can manage recurring payments and subscriber roles.
Automating Role Management
Automating role management can save time and reduce the risk of human error. For instance, you can use plugins to automatically assign roles based on user actions, such as assigning the "Customer" role after a user completes their first purchase.
6. Common Pitfalls and How to Avoid Them
Even with the best intentions, it's easy to make mistakes when managing WooCommerce user roles. Here are some common pitfalls and how to avoid them:
Over-Assigning Administrator Roles
One of the most common mistakes is giving too many users Administrator access. As mentioned earlier, this role should be reserved for only the most trusted individuals. Over-assigning this role can lead to accidental changes or malicious actions that could compromise your site.
Ignoring the Principle of Least Privilege
Failing to implement the Principle of Least Privilege can leave your WooCommerce store vulnerable. Always ensure that users only have the access they need, and nothing more.
Neglecting Regular Audits
Without regular audits of user roles and permissions, it's easy for unnecessary access to go unnoticed. Schedule periodic reviews of all user accounts to ensure that roles are still appropriate and that no unauthorized access has been granted.
Failing to Educate Users
Even if you have strong security measures in place, they can be undermined if users aren't aware of best practices. Make sure to provide ongoing training and support to help users understand their role in keeping your WooCommerce store secure.
7. Conclusion
Managing user roles in WooCommerce is a critical aspect of running a secure and efficient online store. By understanding the different roles and their permissions, implementing best practices like Role-Based Access Control (RBAC) and the Principle of Least Privilege (PoLP), and regularly reviewing and updating user roles, you can significantly reduce the risk of security breaches and ensure that your store operates smoothly.
Remember, the security of your WooCommerce store is only as strong as its weakest link. By carefully managing user roles and educating your team on best practices, you can build a robust and secure e-commerce environment that protects both your business and your customers.
0 notes
Text
Benefits of Secure File Transfer Protocol in the Retail Industry
1 note
·
View note
Text
How to Choose a Payment Gateway That Supports International Transactions
1. Understand Your Business Needs
Before diving into the specifics of payment gateways, assess your business’s unique requirements. Consider the following:
Target Markets: Identify the countries and regions where your customers are based.
Currency Requirements: Determine which currencies you need to support.
Transaction Volume: Estimate the volume of transactions you expect to handle.
Understanding these factors will help you narrow down your options to gateways that align with your business objectives.
2. Evaluate Multi-Currency Support
A payment gateway that supports multiple currencies is crucial for international transactions. Look for gateways that offer:
Automatic Currency Conversion: Ensures customers see prices in their local currency.
Multi-Currency Accounts: Allows you to hold funds in various currencies and reduce conversion fees.
This feature helps provide a seamless shopping experience and minimizes the hassle of currency conversion for both you and your customers.
3. Check for Global Reach and Local Payment Methods
Ensure that the payment gateway supports transactions in the countries you are targeting. Some gateways have broader global reach and better integration with local payment methods, which can enhance customer satisfaction. Look for:
Local Payment Options: Integration with popular local payment methods and banks.
Language Support: User interfaces and customer service available in multiple languages.
Supporting local payment methods can improve conversion rates and cater to the preferences of international customers.
4. Assess Security and Compliance
Security is paramount in payment processing. Choose a gateway that adheres to industry standards and regulations, such as:
PCI-DSS Compliance: Ensures the gateway meets security standards for handling card information.
Fraud Prevention Tools: Features like advanced fraud detection and chargeback protection.
A secure payment gateway not only protects sensitive customer information but also builds trust and credibility for your business.
5. Consider Integration and Usability
The payment gateway should seamlessly integrate with your existing e-commerce platform and business systems. Look for:
Easy Integration: Compatibility with your website or shopping cart software.
User-Friendly Interface: An intuitive interface for both merchants and customers.
A smooth integration process minimizes technical issues and ensures a better user experience.
6. Evaluate Fees and Charges
Payment gateways often come with various fees, including:
Transaction Fees: A percentage of each transaction or a flat fee.
Monthly Fees: Subscription or service fees for using the gateway.
Currency Conversion Fees: Costs associated with converting funds to different currencies.
Compare the fee structures of different gateways and calculate how they impact your business’s bottom line.
7. Review Customer Support
Reliable customer support is essential for resolving any issues that may arise. Check for:
24/7 Support: Availability of support around the clock.
Multiple Channels: Support through various channels such as phone, email, and live chat.
Good customer support ensures you can quickly address any problems and minimize disruptions to your business.
8. Test the Gateway
Before committing, test the payment gateway to ensure it meets your needs. Many providers offer trial periods or demo accounts. Use these opportunities to:
Test Transactions: Conduct test transactions to verify the gateway’s performance.
Evaluate Customer Experience: Ensure the checkout process is smooth and user-friendly.
Testing helps identify any issues before going live and ensures the gateway operates as expected.
Conclusion
Choosing a online payment gateway that supports international transactions is a crucial decision for businesses aiming to expand globally. By understanding your business needs, evaluating multi-currency support, ensuring security and compliance, and considering fees and customer support, you can select a payment gateway that enhances your international operations. Take the time to research and test different options to find the best fit for your business’s growth and success in the global market.
#EcommerceSecurity#OnlinePayments#PaymentGateway#SSL#Encryption#FraudDetection#CyberSecurity#DataProtection#PCICompliance#Tokenization
0 notes
Text
High-Risk Credit Card Processing: Security Measures and Best Practices

Handling high-risk credit card processing requires a strategic approach to security. Businesses operating in high-risk industries, such as online gambling, adult entertainment, or travel services, face unique challenges that demand robust security measures to protect sensitive data and ensure safe transactions. This article delves into the essential security measures and best practices for high-risk credit card processing.
Understanding High-Risk Credit Card Processing
High-risk businesses are characterized by higher chances of chargebacks, fraud, and regulatory scrutiny. As a result, they need to implement stringent security protocols to safeguard customer information and maintain compliance with industry standards.
Essential Security Measures
1. PCI DSS Compliance
Why It Matters: The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards designed to protect card information during and after a financial transaction. Compliance with PCI DSS is mandatory for all businesses handling credit card transactions.
Best Practices:
Regular Audits: Conduct regular PCI DSS audits to ensure ongoing compliance.
Secure Network: Implement firewalls and encryption to protect cardholder data.
Access Control: Restrict access to cardholder data to authorized personnel only.
2. Encryption
Why It Matters: Encryption ensures that sensitive data, such as credit card numbers, is converted into a secure code that can only be deciphered with a specific key, making it unreadable to unauthorized users.
Best Practices:
SSL Certificates: Use Secure Sockets Layer (SSL) certificates to encrypt data transmitted between customers’ browsers and your server.
End-to-End Encryption: Implement end-to-end encryption to protect data throughout the transaction process.
3. Tokenization
Why It Matters: Tokenization replaces sensitive credit card information with a unique identifier or token. This token can be used for future transactions without exposing the actual card details.
Best Practices:
Token Management: Ensure proper management and storage of tokens to maintain security.
Compliance: Verify that your tokenization system complies with industry standards and regulations.
4. Fraud Detection and Prevention
Why It Matters: High-risk industries are more susceptible to fraudulent activities. Implementing advanced fraud detection tools helps identify and prevent fraudulent transactions.
Best Practices:
Real-Time Monitoring: Use real-time monitoring tools to detect suspicious activities.
Machine Learning: Leverage machine learning algorithms to analyze transaction patterns and flag anomalies.
Multi-Layered Security: Combine various fraud prevention techniques, such as CVV verification and address verification system (AVS), to enhance security.
5. Secure Payment Gateway
Why It Matters: A secure payment gateway acts as a bridge between your business and the acquiring bank, ensuring safe and efficient transaction processing.
Best Practices:
Gateway Encryption: Ensure that your payment gateway uses robust encryption methods.
Compliance: Choose a payment gateway that complies with PCI DSS and other relevant regulations.
Fraud Filters: Implement fraud filters provided by your payment gateway to add an extra layer of security.
Best Practices for High-Risk Credit Card Processing
1. Regular Security Assessments
Conduct regular security assessments to identify and mitigate vulnerabilities. This includes penetration testing, vulnerability scanning, and risk assessments.
2. Employee Training
Train employees on security protocols and best practices for handling sensitive data. Regular training sessions help reinforce the importance of data security and ensure adherence to established protocols.
3. Strong Password Policies
Implement strong password policies to prevent unauthorized access. This includes using complex passwords, changing them regularly, and enabling multi-factor authentication (MFA).
4. Data Breach Response Plan
Develop a comprehensive data breach response plan to quickly address and mitigate the impact of any security incidents. This plan should include steps for identifying the breach, notifying affected parties, and restoring security.
5. Continuous Monitoring and Updates
Continuously monitor your systems for security threats and regularly update your software and hardware to protect against the latest vulnerabilities.
Conclusion
Ensuring safe high-risk credit card processing requires a multi-faceted approach that combines robust security measures with best practices. By adhering to PCI DSS standards, implementing encryption and tokenization, utilizing advanced fraud detection tools, and conducting regular security assessments, high-risk businesses can protect sensitive data and maintain the trust of their customers. Staying vigilant and proactive in the face of evolving security threats is essential for safeguarding your business and ensuring long-term success in high-risk industries.
#HighRiskPaymentProcessing#DataSecurity#FraudPrevention#PCICompliance#EcommerceSecurity#CyberSecurity#MerchantServices#PaymentGateway#FinancialSecurity#SecureTransactions
0 notes
Text
How to 5x Your Revenue Using Diginyze
Unlock the full potential of your eCommerce store with Diginyze!
Explore the power of AI personalization, real-time analytics, and dynamic pricing.
From enhanced security to advanced inventory management, and seamless omnichannel experiences, everything you need for exponential growth is right here.
Join the future of eCommerce with Diginyze and see your revenue soar.
Learn more: https://www.diginyze.com/blog/how-to-5x-your-revenue-using-diginyze/

#Infographic#Diginyze#GrowWithDiginyze#AIeCommerce#Sales#RetailTech#RevenueGrowth#eCommerceSuccess#DigitalTransformation#FutureOfRetail#CustomerExperience#OnlineBusiness#Personalization#MarketingAutomation#SecureShopping#BusinessIntelligence#InventoryManagement#OmnichannelRetail#EcommerceSecurity#DataDrivenDecisions#DynamicPricing
0 notes
Text
Five Tips to Protect Your Online Store from Hackers and Cybercriminals
As e-commerce continues to grow, so do the threats of cybercrime. This article offers five essential tips to safeguard online stores from hackers and cybercriminals, emphasizing the importance of security measures to protect both businesses and customers.
0 notes