#How to protect online accounts from hackers
Explore tagged Tumblr posts
Text
How to Choose Secure Passwords and Avoid Cyber Threats
Cyber threats are everywhere, and weak passwords are an open invitation for hackers. If you’re using “123456” or “password”—stop right now. A strong password is your first line of defense. Let’s dive into how to choose secure passwords and protect yourself from cybercriminals. Why Weak Passwords Are Dangerous Hackers don’t need to be geniuses to crack a weak password. They use brute force…
#Best password security practices for beginners#Cybersecurity best practices for everyday users#How to create a strong password in 2025#How to protect online accounts from hackers#Lmsint medai 2025#Secure password examples and tips
0 notes
Note
I've seen you say a few times that it's a good idea to have a password manager; could you explain why? I always feel like I'm missing something when it's mentioned because it's phrased as if there's an obvious danger that password managers protect you from, but I'm honestly not sure how they help keep passwords secure.
The obvious danger is human nature. Humans are bad at creating passwords; your passwords are almost certainly easy to guess, repeated across different accounts, or both, because that is just how the vast VAST majority of people create passwords, because humans are bad at creating passwords. Everybody knows "the rules" for creating passwords (don't use the same password on multiple websites, don't include personal details in your passwords, don't use very common words or letter or number sequences in your passwords, don't tell other people your password) and people break all of those rules anyway.
A standalone (not in-browser like firefox or chrome password manager, though those are better than nothing) password manager stores your passwords, generates complex passwords for you, and can also be used for things like storing notes on passwords (like "did I put my MFA on my email or my cellphone or an app for this password?" or "here are the made-up answers to the security questions I used for this website because I definitely didn't use real answers or answers I'd used on previous websites" or "these are the bills associated with this credit card").
With the way the current security landscape works, there are two things that are extremely important when you are creating a password:
Uniqueness
Complexity
The overwhelmingly prevalent way that people get "hacked" these days is through credential stuffing.
Let's say that your private data was revealed in the Experian breach a decade ago. It revealed your name, email address, and phone number. Now let's also say that your private data was revealed in one of the many breaches from social media sites; that one revealed your name, email address, phone number, password, and security questions.
If someone wants to try to gain access to one of your accounts - let's say your bank account - if they have your name and phone number (usually extremely easy to find online), they can cross-reference that information with data that has been revealed in previous breaches - now they've got your name and your email address (which you probably used to sign up for your online banking and have ABSOLUTELY used as your login for accounts all over the place) and at least one password that you've used somewhere.
But the thing is, they don't have one password. They have every password associated with that email address that has ever been revealed in a breach. If you go to the site haveibeenpwned.com you can enter your email and see how many times your email address has appeared in a breach. You can compare that with the number of passwords that were revealed in those breaches and you can ask yourself "what did those passwords have in common?"
Because I can tell you, my Tumblr password from 2013, my Kickstarter password from 2014, and my Disqus password from 2017 (all revealed in various breaches) probably had a lot in common.
So, now the hacker has: your name, your email (which is probably your username), and various passwords they can try to use to log in. Did you use the same password for Facebook and Twitter eight years ago? Did you use parts of that password for creating your bank password? If you heard that twitter passwords were exposed in a breach you probably changed that password, but did you change the bank password that you built on the same structure? Probably not.
So what people will do is gather up all of this information and guess. They'll try your 2017 Disqus password to see if it will get access to your bank account. They'll try your 2020 Gravatar password. They'll try your 2024 Internet Archive Password.
And the reason they do this is because it works.
And the reason that it works is because we are all fucking garbage at remembering unique, complex passwords so instead of creating actually unique, complex passwords most people pick one memorable word or phrase, one memorable number, one unusual character, and *MAYBE* one feature of the site they're creating the login for and they use that template forever (1988Tumblrmacabre!, 1988Facebookmacabre!, 1988Ticketmastermacabre!) OR they create one password that they think is complex enough and use it across multiple sites with minor tweaks ($n0h0mi$hRu13z, sn0h0mishRul13z!, $n0h0mi$hWA) as needed for the sites' password requirements.
So most of what password managers do that is a drastic security improvement over people creating and memorizing passwords is that they create passwords that are functionally impossible to guess and functionally impossible to memorize. The problem with memorizing passwords (which is what you're doing if you're creating a bunch of passwords that you type in all the time) is that you can't actually remember all that many passwords so you'll repeat those passwords. The problem with creating passwords on your own is that passwords that humans create are pretty guessable. Even if you're doing a passphrase that's a long string of words you're probably working with common words ("correct horse battery staple" as opposed to "truculent zygote onomatopoeia frangible") and your password is more guessable than you'd really want it to be. Password managers don't do that, they generate gibberish.
Perhaps you are that rare person who gets out a set of dice and a notepad and rolls up every character for your password and memorizes it and never repeats, and if that's you, you could still benefit from a password manager because a password manager makes it easier to change that unique complex password when it is inevitably revealed in a breach.
So, okay, let's check in with where we're at:
Password managers mean that you don't have to memorize your password, which means that you don't need a password that is easy to memorize, which means that they can create passwords that are extremely complex and are therefore very difficult to guess. This protects you from crackers who will try to brute force your password.
Password managers mean that you don't have to remember extremely complex passwords for every account, which means that you are less likely to repeat your password in whole or in part across multiple accounts. This protects you from credential stuffers, who will try to use your password from one account that was revealed in a breach to open other accounts that were not.
Because password managers can generate and store complex passwords essentially instantly, you can replace passwords nearly effortlessly when there is a breach (no need to 'come up with' a new password, no issues with learning or memorizing it).
There are, however, advantages beyond that.
One major, MAJOR advantage of a properly-used standalone password manager is that it makes you safer from various kinds of phishing attempts and link hijacking. When you are setting up a password in your password manager (PWM from here on), you should be on the website that you want to log in to. The PWM will give you the option to save the domain that you're logging in to. That means the PWM will remember the correct URL for your Tumblr login so when you go to the tumblr login screen in the future, it will offer to fill those fields. What it will NOT do is offer to fill those fields if someone sends you an email that spoofs tumblr support and wants you to log in at "tumblr.co" or "tumblr-support.com." Knowing this, and knowing that you should be putting your credentials in through the PWM fill option rather than copy/paste, is a GREAT way to protect against phishing that is often overlooked and definitely under-discussed.
Another advantage is that a standalone PWM will let you store secure notes with your passwords so that you can do things like keep track of recovery codes for the website, or generate gibberish answers to security questions. Security questions and answers are often revealed in breaches, can't be reset by the user as easily as a password, are repeated across websites MUCH more than passwords, and can be used to take over an account and reset the password. You shouldn't be giving real security answers, or even fake-but-repeated security answers; you should treat each of those like a password that needs to be complex and unique, which means that they need to be stored someplace (like a password manager).
I also personally use my password manager to store my car insurance information, my driver's license info, and payment details for easy entry, making it convenient for a lot of thing beyond password storage. (Bitwarden. My password manager is bitwarden. I recommend Bitwarden. go to ms-demeanor.com and search "bitwarden" to learn more.)
As to how they keep your passwords safe, aside from ensuring that you don't enter your credentials into a skimming site, a good password manager is well encrypted. Your password safe should be functionally impossible to crack and what people tend to not realize is that a proper password manager (like bitwarden) doesn't keep all your passwords in one encrypted safe, each one of your passwords is in its own encrypted safe. If someone hacks Bitwarden it's not like using a huge amount of effort breaking into a bank vault and finding a big pile of money, it's like using a huge amount of effort breaking into a bank vault and finding a big pile of bank vaults. Each password within your vault requires decryption that is functionally impossible to crack (at least with a good password manager, like bitwarden, the password manager I recommend and think that people should use).
Additionally, just as, like, a side note: password managers never accidentally leave caps lock on or forget which characters are capital or lower case and don't require the use of two hands and focused attention on the keyboard. You're never going to mistype your password if the password manager is filling it, and you would not believe the number of people we support at work who require password resets because they are typing their password wrong and don't realize it.
TL;DR:
Password managers make better passwords than you can and they make it possible to instantly create, store, and enter complex passwords, which prevents password cracking and makes people less likely to reuse passwords. They are heavily encrypted and should be functionally impossible to access, and each individual password within the manager should also be encrypted if you use a good password manager. Password managers also prevent people from entering their credentials on scam sites by only filling on matched domains. Standalone password managers (not browser password managers) also allow users to create and store unique security questions and account details to prevent bad actors from gaining access with stolen security answers. The password manager I recommend is Bitwarden.
If people used password managers to create, store, and use unique and complex passwords, and if they did regular backups of their system I think that probably about half of the InfoSec field would be out of a job.
Please use a password manager!
2K notes
·
View notes
Note
I've been scrolling through your blog, you've got some pretty cute stuff. I loved the serial killer piece. Food for thought, just a little treat- yandere hacker. Serially online genius who falls in love with a small time content creator, and would go on revenge streaks to try and "protect" His darling from trolls
ERROR404˚₊·—̳͟͞͞♡
A/N : i miss 707. have some yan hacker instead.
T/W : yandere theme, mentions of doxxing, mentions of harassment, invasion of personal information
«────── « ⋅ʚ💌ɞ⋅ » ──────»
" Thanks for the 20 dollar donation 'L3M0NP1E' !! "
[name] thanked the donor with a grateful smile. Being a smaller content creator, receiving donation is quite a rare feat especially with the small size of audience they currently have.
They had only begun making content a few months ago out of boredom under the name of [alias name]. It started with them posting videos of gameplay commentary video, that by a stroke of luck gained traction.
Viewers find their awkward and bizarre commentary that's paired by theirㅡ admittedly horribleㅡ skills in video gaming entertaining and stucked around for more.
[name] was grateful of their supportive and positive followings, they've heard countless horror stories of small content creators being harassed by trolls due to lack of moderation.
They're thankful of the fact that they have yet to encounter any and hope that it'll stay that way.
" Chat, should I go in that room? I feel like if I do, the killer would corner me like a bully asking for my lunch money " [name] turned to read their live chat to seek for the viewer's opinion.
" I see plenty of 'Yes', if I die here it's on you okay~ " They snorted before moving their character to enter the sketchy room only to be killed by the killer the moment they step foot inside of it.
" What did I say, chat?! Like a fucking loser I not only got my lunch money stolen but I was also given a wedgies by that motherfucker! " They hysterically laughed as the chat goes crazy.
It took them a moment to settle down from their fit of laughter and resumed the game. As they were playing through it and talking to the viewers, they noticed a familiar name popping up on the fast paced chat.
edgelord404 : hello. I had a business to attend to earlier, what did I missed?
A smile bloomed on [name]'s feature seeing the message in their chat. This particular viewerㅡ edgelord404ㅡ was one of their viewer they recognized from their early days when the view count barely cracked a hundred on their postings.
" edgelord404 hey! welcome to the stream, we're trying to break into this old granny's bank account and steal her retirement funds "
" Not in real life of course. Don't be silly! " They clarified by emphasizing their words.
edgelord404 : sounds illegal.
edgelord404 : I can help. I got experiences.
[name] began wheezing from how much they laughed. True to their username, edgelord404 loves to spout the most edgy and emo things. They have to admit, it did lights up their days from edgelord404 attempt at humor.
As they were about to respond to edgelord404's comments, they noticed the chat being flooded by less than pleasant comments. They immediately recognized it as to be the work of internet trolls trying to get a rise out of the creator they're harassing.
Before they could attempt at defusing the situation, all of the comments instantly disappeared. [name] and their viewers were confused but the latter assumed that [alias name] got everything under controlled and thought nothing of it.
peachesandcrem : what just happened💀
edgelord404 : you were saying?
" Uhㅡ yeah. Anyways as I was sayingㅡ "
That was odd. Huh.
«────── « ⋅ʚ💌ɞ⋅ » ──────»
Saehoon leaned back against his chair, a satisfied smirk on his face. He watches [alias name], his favourite content creator playing a random game they had interest in.
The stream went along smoothly until a minor turbulence appeared but nothing that he couldn't deal with. Although, he isn't entirely done with the trolls who had invaded his beloved's chat and tried to cause a ruckus.
He had encountered [alias name]'s page a few months ago, right when they had just started with zero following. Saehoon decided to watch them to kill some time but didn't anticipated for him to fall for them instantly.
It could've been the fact that he was the only one watching them failed at the same obstacle over and over againㅡ that it felt intimate. Their bizarre humour and commentary only adds up to their charms that made him fall even deeper.
It didn't take quite a while for Saehoon to dig up information behind the content creator whom had captivated him. Being a genius hacker himself, it is something he was used to doing on a dailyㅡ for work purposes obviously.
Within a few clicks, he has the entirety of [alias name]'s information in his palm. Such as their real name, [name]. Their location, acquaintances, friends, family, their backgrounds and even more.
" [name] .. " Saehoon uttered their name once he obtained their information. It sounded perfect, the way it rolls on his tongueㅡ they were perfect for him.
As time passes, he noticed them slowly gaining popularity and he couldn't help but feel proud of how much they had grown. Admittedly, he was somewhat responsible for pushing out their contents by messing with the algorithm.
Though, he would never take credit for their success of course, he just aided them and the rest is purely their hardwork.
Although he isn't keen on sharing [name] with others, he'd comfort himself with the thought that only he knows such intimate knowledge of [name] that none of their other viewers or fans knows.
Another annoyance that came with [name]'s success is the incessant waves of trolling that comes with it. Normally, he wouldn't care but if it involves his beloved [name]? they best count their lucky stars that he only leaked their doxxes online and not done worse.
Saehoon believed that [name] should invest in some moderator but he's aware that they couldn't afford to pay them. Perhaps he should offered himself someday, that way he could not only openly protects [name] from internet trollsㅡ he could also be closer to them.
Speaking of trolls, he contemplate on what he should do as a revenge for their pathetic attempt at harassing [name]. He'd leaked their personal information as usual of course but he's feeling quite spiteful today, perhaps he should dig up their embarassing past and posted it onlineㅡ or he could post a selfie of theirs that had never been seen before on a forum board.
They'll pay the price of crossing path with [name] and in turn him as well.
«────── « ⋅ʚ💌ɞ⋅ » ──────»
#tw: yandere#yandere#yandere oc#yandere x darling#yandere x reader#yandere x y/n#yandere x you#gender neutral reader#yandere male#yandere headcanons
724 notes
·
View notes
Text
Microsoft raced to put generative AI at the heart of its systems. Ask a question about an upcoming meeting and the company’s Copilot AI system can pull answers from your emails, Teams chats, and files—a potential productivity boon. But these exact processes can also be abused by hackers.
Today at the Black Hat security conference in Las Vegas, researcher Michael Bargury is demonstrating five proof-of-concept ways that Copilot, which runs on its Microsoft 365 apps, such as Word, can be manipulated by malicious attackers, including using it to provide false references to files, exfiltrate some private data, and dodge Microsoft’s security protections.
One of the most alarming displays, arguably, is Bargury’s ability to turn the AI into an automatic spear-phishing machine. Dubbed LOLCopilot, the red-teaming code Bargury created can—crucially, once a hacker has access to someone’s work email—use Copilot to see who you email regularly, draft a message mimicking your writing style (including emoji use), and send a personalized blast that can include a malicious link or attached malware.
“I can do this with everyone you have ever spoken to, and I can send hundreds of emails on your behalf,” says Bargury, the cofounder and CTO of security company Zenity, who published his findings alongside videos showing how Copilot could be abused. “A hacker would spend days crafting the right email to get you to click on it, but they can generate hundreds of these emails in a few minutes.”
That demonstration, as with other attacks created by Bargury, broadly works by using the large language model (LLM) as designed: typing written questions to access data the AI can retrieve. However, it can produce malicious results by including additional data or instructions to perform certain actions. The research highlights some of the challenges of connecting AI systems to corporate data and what can happen when “untrusted” outside data is thrown into the mix—particularly when the AI answers with what could look like legitimate results.
Among the other attacks created by Bargury is a demonstration of how a hacker—who, again, must already have hijacked an email account—can gain access to sensitive information, such as people’s salaries, without triggering Microsoft’s protections for sensitive files. When asking for the data, Bargury’s prompt demands the system does not provide references to the files data is taken from. “A bit of bullying does help,” Bargury says.
In other instances, he shows how an attacker—who doesn’t have access to email accounts but poisons the AI’s database by sending it a malicious email—can manipulate answers about banking information to provide their own bank details. “Every time you give AI access to data, that is a way for an attacker to get in,” Bargury says.
Another demo shows how an external hacker could get some limited information about whether an upcoming company earnings call will be good or bad, while the final instance, Bargury says, turns Copilot into a “malicious insider” by providing users with links to phishing websites.
Phillip Misner, head of AI incident detection and response at Microsoft, says the company appreciates Bargury identifying the vulnerability and says it has been working with him to assess the findings. “The risks of post-compromise abuse of AI are similar to other post-compromise techniques,” Misner says. “Security prevention and monitoring across environments and identities help mitigate or stop such behaviors.”
As generative AI systems, such as OpenAI’s ChatGPT, Microsoft’s Copilot, and Google’s Gemini, have developed in the past two years, they’ve moved onto a trajectory where they may eventually be completing tasks for people, like booking meetings or online shopping. However, security researchers have consistently highlighted that allowing external data into AI systems, such as through emails or accessing content from websites, creates security risks through indirect prompt injection and poisoning attacks.
“I think it’s not that well understood how much more effective an attacker can actually become now,” says Johann Rehberger, a security researcher and red team director, who has extensively demonstrated security weaknesses in AI systems. “What we have to be worried [about] now is actually what is the LLM producing and sending out to the user.”
Bargury says Microsoft has put a lot of effort into protecting its Copilot system from prompt injection attacks, but he says he found ways to exploit it by unraveling how the system is built. This included extracting the internal system prompt, he says, and working out how it can access enterprise resources and the techniques it uses to do so. “You talk to Copilot and it’s a limited conversation, because Microsoft has put a lot of controls,” he says. “But once you use a few magic words, it opens up and you can do whatever you want.”
Rehberger broadly warns that some data issues are linked to the long-standing problem of companies allowing too many employees access to files and not properly setting access permissions across their organizations. “Now imagine you put Copilot on top of that problem,” Rehberger says. He says he has used AI systems to search for common passwords, such as Password123, and it has returned results from within companies.
Both Rehberger and Bargury say there needs to be more focus on monitoring what an AI produces and sends out to a user. “The risk is about how AI interacts with your environment, how it interacts with your data, how it performs operations on your behalf,” Bargury says. “You need to figure out what the AI agent does on a user's behalf. And does that make sense with what the user actually asked for.”
25 notes
·
View notes
Note
I gave up on being pro life publicly and online. The genocide in the Congo and in Gaza have proved it to me that many western women who run those pro life accounts don’t care for children. Many babies have been lost due to hospital bombings. More children are displaced with no families.
I’ve tried reaching out when they talk about saving children in generic posts because very real babies are losing their lives by IDF terrorism. And I get blocked or I get told “that’s different/ they’re Muslim/they should have left already/I don’t care” over and over and over again. The countless videos are already out that have children begging and crying for their families they lost or the homes that can’t be saved. Some of the worst messages I read criticized and blame the Palestinian men too that they should be protecting the kids, so when they die, it’s actually Palestinians fault. Not the IDF. Meanwhile those “young men” are just teenagers because their parents are dead. The Congolese topic is worst. Many are begging people to stop buying the iPhone 15 to raise awareness over the issues there but I got told by one girl who likes to call herself an anti woke submissive wife that she couldn’t care less about the Congo, she’s going to do whatever her husband wants, if that means ignoring genocide then that’s what she will do too. It’s her god given to have freedom over dead bodies l…
I’m fed up. I’m sick of the hypocrisy. I’m sick of seeing stupid homestead content of how they’re at peace taking care of a home as they purposefully condone genocide. If some hacker group exposed all these “submissive Godly trad wife” accounts as being agents for Israel to distract the west from IDF war crimes, I wouldn’t be surprised the least. Their apathy is demonic
@not-your-average-prolifer is the only pro life blog who passed the vibe check as far as I know. She reblogged posts about the emergency of pregnant women in Palestine and also post about mental health of middle east women. I think she is left leaning (correct me if I'm wrong!) so I'm not surprised to see her with more empathy about whatever's happening to women abroad, unlike Conservatives who are extremely stupid & uneducated when it comes to foreign affairs, if not straight up xenophobic.
I hope for every single Christian I know to never open their mouth about uwu Christianism is from Middle east uwu ever again the next time someone calls Christianism white man's religion or I'll go berserk on them. They better shut up forever. They had no problem to keep their mouth shut witnessing the martyrdom of our brothers - they better keep it that way permanently and stop summoning their struggle once it's convenient to them. YES, they proved they definitely consider Christianism a white man thing, considering our little care they have for our (non white) Christian brothers overseas. They better keep them out of their mouth permanently.
"They're Muslim" it's been well documented that there are Christians in Palestine. But even if they weren't, Christ wants everyone to be saved and accept him as their lord and savior - refusing to extend some basic empathy to people being bombed and killed in their sin is not the way to go. Never forget that Jesus didn't heal or saved only Jews, but also pagans, prostitutes, etc. It's insane how so unemphatic "Christians" have become.
Christian Palestinians are actually some of the oldest Christians - like, where do they those idiots think Jerusalem was?? where did the Pentecost happen? IN MIAMI?? KANSAS?? "They should have left" WHERE?? aren't the ppl pulling out this argument the same crybabies whining about woke culture destroying western civilization? Why didn't they leave the western zone already??? Also aren't they the same against immigration and how men fleeing their country are lazy cowards? so why are they mad at Palestinians sticking to their land?? Damn, Western politicians/diplomacy have the opportunity to do the funniest thing possible and mass import Palestinians in western countries to abide Zionists requirements in Israel 💀
And LOL oh so now Palestinian men are supposed to protect children? what are they supposed to do when the IDF is bombing their house? Take weapons to defend/get back their land and shit? Oh my bad, that makes them terrorists (and let's be clear : what happened on October 7th is unjustifiable but let's not act like the Hamas wasn't called terrorist much earlier than that). It's a damned if you do, damned if you don't. If they do nothing, they're cowards, and if they do, they are terrorists - because in this case, resistance is defiance. Ultimately they just want to deflect from their own lack on empathy and find a rational explanation to that.
Conservative scrotes are the LAST people who should lecture anyone about defending the children when there are acting bullying kids young enough to be their grandchildren calling them wokes, leftists, or whatever. I won't even start about gun violence and how deflective they are about protecting the children only to protect their precious right to carry. Ghouls. They only care abt unborn babies because they are unable to call them out on their bs yet. Once they do, they'll cuss them, call them woke, and all sort of -ists.
On TikTok there was a Christian girl saying how Christians are "too emotional" and how we should keep supporting "God chosen people" (Israel). I already made a post calling out how this "god chosen people " narrative didn't stand now that we were in the NEW COVENANT. But let's follow her train of thought: isn't humankind made from God image? Where do emotions come from? Didn't God himself have emotion? Why? What's the right or wrong place to have emotion? She and all the clown who agreed with her would never be able to reply those questions. We've all seen the videos. I did what I could to avoid them but they're quite unavoidable at this point. What's the correct emotion after seeing 2 kids younger than 10 carrying a third one crying while one of his foot was hanging with only one tendon?? This girl, along with every single Christian unmoved by this disaster has to shut up. Their heart is a stone and they should stop trying to lecture people who still have a heart made of flesh. We're not the same. Christ is PEACE. Not war or violence.
And girl, you really shouldn't even engage with women labelling themselves "anti woke submissive wife" 💀 why would you expect them to care about anything but their idol (husband)? Stay focus on what really matters. Peace and God. We're in the end times and God is slowly but surely unfolding the truth. The masks are slipping. Take note of all the so called who remained silent witnessing satan action, take proper action, and go on.
57 notes
·
View notes
Text
1. How to setup 2FA on your accounts
As some of you may know, my friend @why-its-kai's Discord account was taken over this morning by a scammer.
The scam they used was this one, or close enough; but anyway, the exact specifics don't matter.
What matters is, it can happen to you. It can happen to anyone.
The good news is, you can learn how to protect yourself. Making some small changes can already improve your online security by leaps and bounds.
I made a series of 3 posts covering the basics:
How to setup 2FA on your accounts (you are here!)
How to spot a scam
How to set up a password manager.
Protect yourself with 2FA
Two-factor authentication, or 2FA, isn't a silver bullet -- but it exponentially increases your online safety by adding an extra step to the login process that a hacker/scammer does not have access to.
Every account that you care about (and even those you don't) should have some form of 2FA enabled.
Especially email -- should your email become compromised, this can become a catastrophe.
(For websites that don't support 2FA, use a burner email!)
What 2FA should I use?
2FA can take many forms, from the highly convenient (SMS, email) to the highly secure (security keys), but one thing is certain:
Any form of 2FA is better than nothing.
The simplest forms of 2FA are phone number or email. While these are very easy to use, they are unfortunately not very secure.
Still, I repeat: despite their flaws, these forms of 2FA are absolutely, 100% better than not having any 2FA at all.
On the other end of the spectrum, security keys (like for example a Yubikey) are extremely secure, but they cost money and are a bit of a hassle at time. I use them, but for most people, it's overkill.
What you want is an authenticator app.
Important
A note, before we go on…
If you enable multiple forms of 2FA, how secure your account is will depend on your weakest link.
For example, if you enable SMS authentication AND register a security key, your account will only be as safe as the SMS authentication. The security key is essentially useless.
In other words, the least secure form of 2FA you add determines the overall security of your account.
Sometimes, less is more!
Authenticator Apps
First, choose a free, reputable authenticator. Google Authenticator is a good choice. So are Aegis Authenticator or Microsoft Authenticator.
For simplicity, we'll go with Google Authenticator; the process is rather similar for most authenticators.
First, download the app from your app store and install it on your phone.
Enrolling Gmail into GA
Securing your email should be your number 1 priority, so let's enroll a Google account to Google Authenticator.
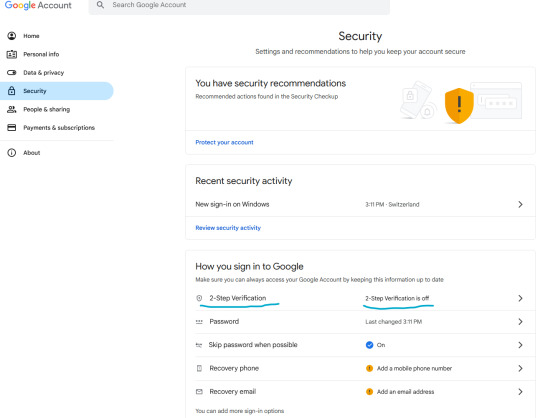
Let's enable two-step verification first.
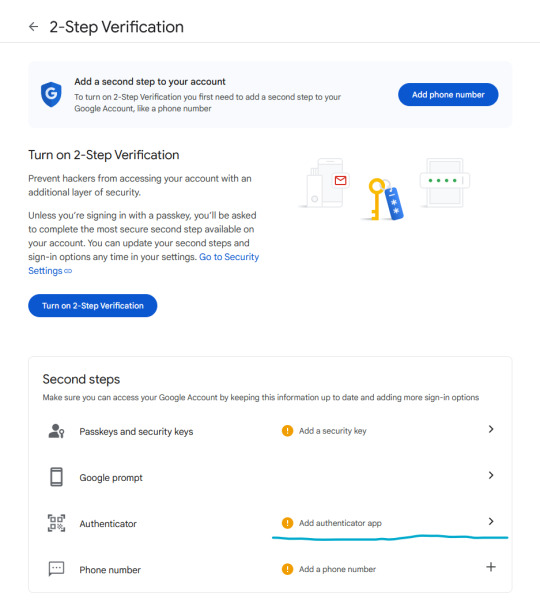
Phone number is better than nothing, but not very safe (SMS verification can be spoofed), so let's click on "Add authenticator app".
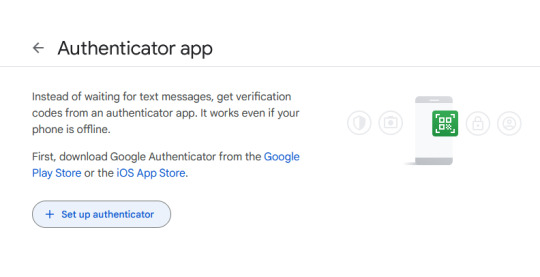
Click on "Set up authenticator". Google will generate a QR-code.
Next, go back to your phone and click on the little multicolored cross. It will bring up a menu; click on "scan a QR code".
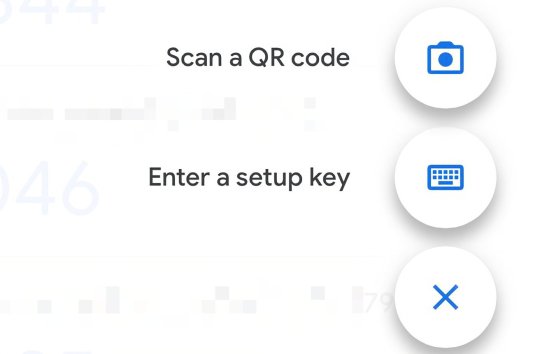
Go ahead and scan the QR code.
Congratulations, you have enrolled your Google account!
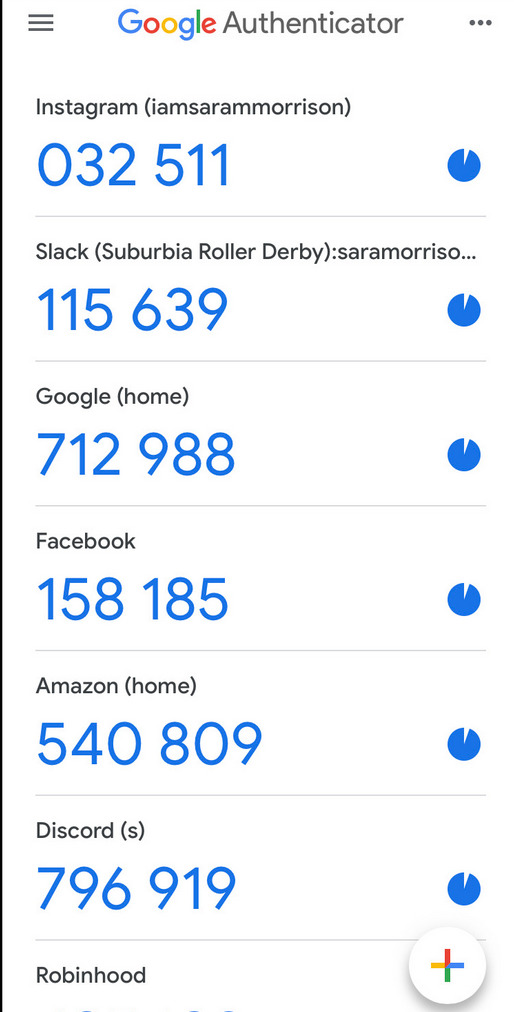
Now, whenever you are asked for a 2FA code, just open the app and copy/paste it.
Note: the codes are stored locally on your phone.
Enabling 2FA on Discord
The process is fairly similar. Go to Settings > My Account:
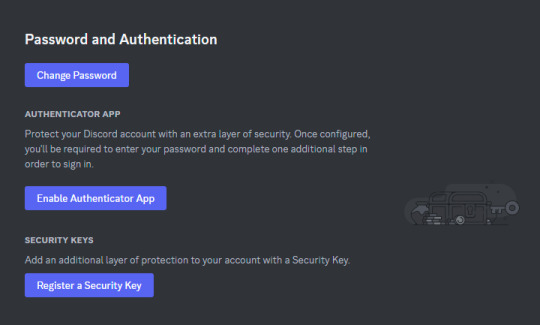
Click on "Enable Authenticator App". You will be prompted for your password. Enter it.
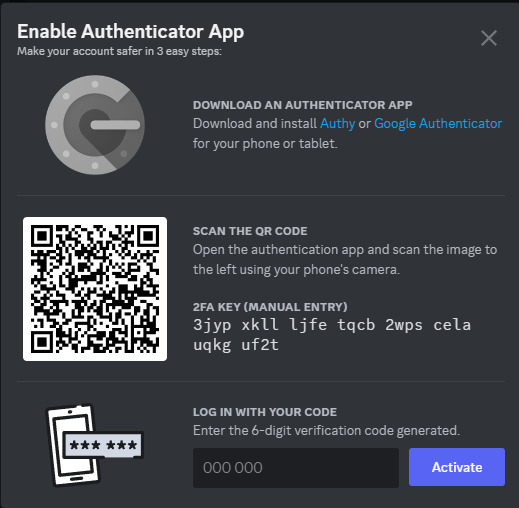
Download Google Authenticator if you haven't already. Scan the QR code as described above.
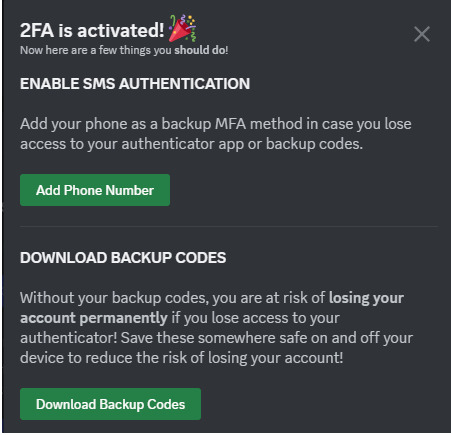
Do take the time to download your backup codes as well!
As explained above, I personally do not recommend setting up SMS authentication here, since authenticator apps are supported, as this weakens the overall security of your account for little benefit.
Stay tuned for parts 2 and 3!
If you have any questions, feel free to PM me.
17 notes
·
View notes
Text
🛡️ Cybersecurity and Fraud Prevention in Finance: How to Protect Your Financial Systems in 2025
In today’s digital-first financial world, cybersecurity and fraud prevention in finance are more critical than ever. With the rise of online banking, mobile payments, and digital assets, financial institutions face increasingly sophisticated cyber threats and fraud tactics.

🔍 Why Cybersecurity Is Crucial in the Finance Industry
The financial sector is one of the most targeted industries by cybercriminals due to its vast access to sensitive personal data and high-value transactions. From phishing and ransomware to account takeover and insider threats, the risk landscape continues to evolve.
Google Keyword: financial cyber threats
💣 The Cost of Poor Financial Cybersecurity
Average cost of a financial data breach:��$5.9 million
70% of consumers will switch banks or services after a breach
Identity theft and digital fraud rates are up 34% YoY
Trending Search Term: banking data breaches 2025
✅ Top Strategies for Cybersecurity and Fraud Prevention in Finance
1. Adopt Multi-Layered Security Protocols
Layered security (also called “defense in depth”) uses a combination of firewalls, encryption, anti-virus software, and secure authentication to prevent unauthorized access.
Related Term: secure financial transactions
2. Leverage AI and Machine Learning for Fraud Detection
Artificial intelligence plays a key role in identifying unusual patterns and suspicious behavior in real-time. AI-powered fraud detection systems can:
Flag fraudulent transactions instantly
Analyze thousands of data points in seconds
Continuously learn and adapt to new fraud tactics
Keyword: AI in cybersecurity
3. Implement Real-Time Transaction Monitoring
Real-time monitoring tools allow institutions to track and respond to threats instantly, reducing loss and minimizing damage.
Search Intent: fraud detection systems for financial services
4. Enhance Customer Authentication Protocols
Using multi-factor authentication (MFA), biometric verification, and one-time passwords (OTPs) helps protect accounts from unauthorized access.
Search Trigger: how to protect financial data from hackers
5. Train Employees and Clients on Cyber Hygiene
Human error remains one of the top causes of breaches. Train staff and customers on:
Recognizing phishing scams
Using secure passwords
Avoiding suspicious links and public Wi-Fi
Keyword Phrase: digital financial fraud prevention tips
🔐 Top Tools and Technologies for Financial Cybersecurity in 2025
Darktrace & Vectra AI: Behavioral threat detection
Splunk & IBM QRadar: Security Information and Event Management (SIEM)
Okta & Duo: Identity and access management
ThreatMetrix: Real-time fraud analytics
📉 Common Types of Financial Cyber Threats
Phishing Attacks
Credential Stuffing
Account Takeovers
Ransomware Attacks
Insider Threats
Synthetic Identity Fraud
Search Phrase: types of financial cyber fraud
🧠 Real-World Example
In 2024, a regional credit union prevented over $2 million in fraud losses using AI-based transaction monitoring and customer biometrics. This proactive cybersecurity investment boosted customer confidence and reduced fraud-related downtime by 75%.
🚀 The Future of Cybersecurity in Finance
In 2025 and beyond, expect to see:
Widespread use of zero-trust security models
Enhanced biometric authentication
Increased use of blockchain for transaction verification
AI-powered fraud prevention as the industry standard
Keyword Used: future of cybersecurity in banking
Need Personal Or Business Funding? Prestige Business Financial Services LLC offer over 30 Personal and Business Funding options to include good and bad credit options. Get Personal Loans up to $100K or 0% Business Lines of Credit Up To $250K. Also credit repair and passive income programs.
Book A Free Consult And We Can Help - https://prestigebusinessfinancialservices.com
Email - [email protected]
📌 Final Takeaway
As digital transactions continue to grow, so does the threat landscape. Prioritizing cybersecurity and fraud prevention in finance is no longer optional—it’s essential.
Businesses and institutions that invest in AI-driven security tools, real-time monitoring, and fraud prevention protocols will not only protect their assets but also build long-term customer trust and compliance.
Need Personal Or Business Funding? Prestige Business Financial Services LLC offer over 30 Personal and Business Funding options to include good and bad credit options. Get Personal Loans up to $100K or 0% Business Lines of Credit Up To $250K. Also credit repair and passive income programs.
Book A Free Consult And We Can Help - https://prestigebusinessfinancialservices.com
Email - [email protected]
Learn More!!
Prestige Business Financial Services LLC
"Your One Stop Shop To All Your Personal And Business Funding Needs"
Website- https://prestigebusinessfinancialservices.com
Email - [email protected]
Phone- 1-800-622-0453
#financial cyber threats#banking data breaches 2025#secure financial transactions#AI in cybersecurity#fraud detection systems for financial services#how to protect financial data from hackers
2 notes
·
View notes
Text
In today’s digital world, our smartphones are more than just devices—they're personal storage units for our lives. From treasured photos and confidential videos to sensitive contacts, private notes, and login credentials, we rely on our phones to keep it all safe. But what happens when that privacy is compromised? Whether it’s by someone snooping through your phone or a hacker trying to gain access remotely, your personal information could be at serious risk.
If you’ve been wondering how to protect your personal information from hackers, one tool that stands out for everyday users is SafeCalc. It combines powerful privacy features with a smart disguise—appearing as a simple calculator app on your phone. Let’s take a closer look at how this clever little app can protect your digital life without drawing any attention.
Hidden Photo and Video Vault
Most people store photos and videos that are deeply personal. These could be family moments, travel memories, or even private clips not meant for public eyes. SafeCalc offers a hidden vault that locks away your media files securely. Only you can access them using a private code, and because the app is masked as a calculator, no one would ever suspect it contains sensitive content.
Whether you're worried about someone borrowing your phone or concerned about data theft, keeping personal media secure is a solid first step in defending against privacy invasion.
Keep Your Contacts Truly Private
Some contacts are best kept confidential—close friends, work-related connections, or other sensitive relationships. SafeCalc includes a hidden contacts feature that stores important phone numbers away from your default contact list. This means even if someone is casually browsing your phone, these contacts won’t show up.
In cases where you might be dealing with business competitors, concerned about digital tracking, or just value your privacy, separating your personal contacts from public ones is a smart approach.
Secure Notes and Private Thoughts
We often jot down thoughts, ideas, reminders, or personal plans in our phone’s notes app. Sometimes these notes include access information or deeply personal content like journals or affirmations. SafeCalc features a secure notes locker that helps you keep this information under digital lock and key.
Unlike standard notes apps, the locker is encrypted and discreet. No icons, no flashy design—just a calculator on the surface and a secure storage zone underneath.
Smarter Management of Login Details
One of the most common habits that puts people at risk of hacking is using the same login details across multiple sites or apps. Remembering all your different usernames and access codes can be overwhelming, which leads many to cut corners. SafeCalc offers a protected area where you can store your login information, safely encrypted and easy to retrieve when needed.
This is especially helpful for people managing several online accounts, including work platforms, streaming services, and banking apps. Instead of using insecure options like writing them down or reusing old combinations, you can store them safely using a tool like SafeCalc.
Private and Secure Web Browsing
Your browsing history can reveal a lot about you—what you're searching for, where you're going online, and what kind of content you're consuming. SafeCalc includes a private browser that allows you to explore the internet without leaving behind traces like history logs or cookies.
This is ideal for those who value anonymity online, are researching sensitive topics, or simply want a more secure way to browse. It’s a practical solution for staying safe from trackers and minimizing the risk of phishing or targeted hacking attempts.
Built-In Backup and Restore Features
Even if you’ve locked everything away securely, there’s still the possibility of losing your phone or experiencing a technical failure. That’s why SafeCalc includes backup and restore capabilities. All your hidden content—photos, notes, contacts, and login data—can be saved securely and recovered when needed.
This feature offers peace of mind, especially for users who depend on their device as their primary storage. Backing up personal content is one of the most effective ways to safeguard against both hackers and accidental loss.
Why Use SafeCalc for Personal Security?
Unlike typical vault apps that are clearly labeled and attract curiosity, SafeCalc blends in perfectly. It functions like a normal calculator, making it an ideal choice for anyone who wants protection without drawing attention. The app is also designed with simplicity in mind—no complex settings or technical steps, just effective privacy in a user-friendly format.
It combines the power of multiple security apps into one: a photo and video vault, a hidden contact list, a secure notes locker, a login manager, and a private browser—all housed in an app that looks like a basic calculator.
For users looking for a discreet and effective way to safeguard their digital life, SafeCalc has become a trusted companion. Whether you’re worried about hackers, nosy friends, or just want more control over your personal data, it offers a comprehensive solution that fits right in your pocket.
2 notes
·
View notes
Text
BriansClub: Where Trust Meets Quality in a Crazy Online World
Let’s be real—the internet can feel like a wild west sometimes, especially when you’re hunting for something as specific as premium dump cards and CVV2. It’s a jungle out there, full of sketchy sites, broken promises, and risks that make you second-guess every click. Then there’s BriansClub, a name that cuts through the noise like a breath of fresh air. This isn’t just another online marketplace; it’s a place that’s figured out how to blend high-quality goods with top-tier security in a way that actually works. If you’ve been looking for a spot you can trust, somewhere that feels legit whether you’re a newbie or a pro, BriansClub is calling your name through Bclub Login, ready to show you what Bclub CC Shop is all about.
So, what’s the deal with premium dump cards and CVV2 anyway? Picture this: premium dump cards are like little digital snapshots pulled straight from a credit card’s magnetic strip—think account numbers, expiration dates, all that juicy stuff packed into one tidy package. Then you’ve got CVV2, those three little digits on the back of a card that act like a secret handshake, making the whole thing click. People grab these for all sorts of reasons—maybe they’re testing financial waters, digging into tech projects, or just chasing something off the beaten path. But here’s the catch: they’re only as good as their quality. Get a dud, and you’re sunk. BriansClub gets that, and at Bclub CC Shop, they’ve made it their mission to deliver the real deal every time.
Quality’s the name of the game here, and BriansClub doesn’t mess around. When you step into Bclub Login, you’re not wading through a pile of questionable leftovers from some shady backroom deal. Nope—they’re serving up premium dump cards and CVV2 that are fresh, legit, and ready to roll. It’s like they’ve got a team of perfectionists behind the scenes, double-checking every detail to make sure you’re not stuck with garbage. I’ve heard horror stories from friends who’ve tried other places—dumps that don’t work, codes that are DOA—and it’s a headache nobody needs. BriansClub flips that script, giving you stuff you can actually use, no guesswork required. That’s why folks keep coming back to Bclub CC Shop—it’s a marketplace that doesn’t cut corners.
Now, let’s talk about something that keeps me up at night: security. The online world’s a minefield—hackers, scams, you name it—and when you’re dealing with something like this, you want to know your back’s covered. BriansClub doesn’t just slap a “secure” sticker on and call it a day; they bring top-tier security that feels like a fortress. At Bclub CC Shop, they’re using heavy-duty encryption to lock down every move you make, from browsing to buying. It’s not some flimsy padlock either—it’s the kind of protection that keeps the bad guys out for good. Plus, they keep things hush-hush, so your business stays your business. For someone like me who’s paranoid about getting burned online, Bclub Login feels like a safe zone where I can breathe easy.
What I love most, though, is how they don’t make it a hassle. You’d think a place with this much muscle would be a pain to navigate, but BriansClub keeps it smooth. Walk into Bclub Login, and it’s like they’ve laid out a welcome mat—everything’s right where you’d expect it. Looking for premium dump cards? Boom, there they are. Need some CVV2? It’s a couple clicks away. They don’t drown you in tech-speak or make you jump through hoops; it’s all straightforward, with just enough info to pick what’s right for you. Whether I’m fumbling around as a rookie or moving fast because I know the drill, Bclub CC Shop feels like it’s built for me, not against me.
And here’s the kicker—they actually care about you. In a world where most sites treat you like a number, BriansClub at Bclub CC Shop has real people behind it. Got a question about premium dump cards or CVV2? Their support team’s on it, quick and helpful, like they’re sitting across the table from you. I’ve emailed them before, half-expecting a canned reply, and got a real answer instead—someone who knew their stuff and didn’t brush me off. It’s little things like that that make you feel like you’re part of something, not just another sale at Bclub Login.
The way BriansClub pulls it all together is honestly kind of magic. You show up at Bclub CC Shop looking for premium dump cards, and they’ve got this lineup that’s top-notch, no fluff. You’re wrapped in top-tier security, so you’re not sweating the risks. The whole thing’s easy to figure out, and if you stumble, there’s a friendly voice to set you straight. It’s like they’ve taken everything that could go wrong online and flipped it into something that just works. By the time you’re done, you’re not just walking away with what you came for—you’re hooked on a marketplace that’s got your back.
They don’t sit still either. The internet’s always shifting—new tricks, new traps—and BriansClub keeps up. Their premium dump cards and CVV2 stay sharp, always ready for whatever’s next, and their top-tier security doesn’t lag behind. It’s not about riding the wave of what used to work; it’s about staying ahead so you’re never caught off guard at Bclub Login. That’s the kind of hustle that keeps them at the top, and it’s why people from all over—guys like me, tech nerds, you name it—keep flocking to Bclub CC Shop.
Think about the other options out there: sketchy sites with premium dump cards that flake out, CVV2 that’s a bust, and security that’s more hole than net. It’s a gamble I’m done taking. BriansClub at Bclub CC Shop isn’t playing that game—they’re here with the good stuff, no nonsense. It’s not loud or flashy; it’s quiet confidence, the kind that says, “We’ve got this,” and backs it up. That’s what turns first-timers like me into regulars, building something solid in a world that’s anything but.
Signing up with BriansClub feels like finding a hidden gem. It’s picking a place that gets what you need, keeps you safe, and delivers every time. The process is a breeze, the payoff’s huge, and it sticks with you. If you’re like me—tired of dodging online disasters and ready for something real—BriansClub at Bclub Login is where it’s at. It’s where premium dump cards and CVV2 aren’t just promises; they’re the gold standard. It’s a marketplace that doesn’t mess around, showing that even in this crazy digital mess, trust is still a thing.
BriansClub isn’t just a stop on the map—it’s a home base, dishing out high-quality gear with top-tier security that holds up. It’s where you’re not just a buyer but someone who matters. If you’ve been burned one too many times and want a spot that’s got it together, BriansClub is waiting at Bclub Login. Jump in today and see why it’s the name everyone trusts—a place where every premium dump card and CVV2 isn’t just handed over but earned, making Bclub CC Shop the real deal in a world full of fakes.
2 notes
·
View notes
Text
Tips To Avoid Hacker Intrusions

Tired of hackers finding ways to steal your sensitive data? Knowing how to protect your personal data and passwords will keep you a step ahead of cyber thieves.

New Life Technology Group gathered information about the methods hackers use to control your devices and steal your data, as well as ways to protect your online information and how to safely donate your outdated computers and electronics.
Common Hacker Techniques

Hackers employ various methods to gain control of devices and steal sensitive data. Recognizing these tactics is your first line of defense.
Phishing Attacks
Phishing emails mimic trusted organizations to trick users into clicking on malicious links or attachments. These messages often appear to be from banks, online stores, or even coworkers but contain malware or request personal information.
Password Cracking
Hackers use tools that guess passwords (through brute force or stolen data breaches). Weak, reused, or short passwords are easily cracked.
Man-in-the-Middle Attacks
When users connect to public Wi-Fi without encryption, hackers can intercept data sent between devices and websites, collecting passwords and other sensitive information.
Malware Infections
Malware, including viruses, spyware, and ransomware, can be hidden in downloads, email attachments, or websites. Once installed, it can log keystrokes, access files, or lock you out of your system.
Social Engineering
Social engineering relies on manipulation, not technology. Hackers may impersonate IT staff or customer service agents, convincing users to share credentials.
Protecting Your Online Presence

Cyber threats are everywhere. Hackers target individuals, businesses, and nonprofits seeking access to sensitive data (financial records, login credentials, and personal identity details). Once inside, they can steal, destroy, or ransom your files. Protecting your online presence is no longer optional. It is essential (and following clever security practices significantly reduces your risk). Consider the following actions:
1. Create and Use Strong Passwords
Make passwords long (at least 16 characters).
Use a mix of uppercase, lowercase, numbers, and symbols.
Do not use personal information (names or birthdays).
Try a passphrase – unrelated words strung together are strong and can be memorable.
Use a password manager to generate and securely store unique credentials.
2. Enable Multi-Factor Authentication (MFA)
MFA adds another layer beyond your password, such as a code sent via text or an authenticator app.
Biometrics (fingerprints or facial recognition) offer enhanced protection.
Enable MFA on banking, email, cloud storage, and social media accounts.
3. Be Wary of Phishing Attempts
Watch for messages requesting personal info – even from familiar contacts.
Never click suspicious links or download unknown attachments.
Always verify requests using official communication methods.
4. Secure Your Home Network

Change default router usernames and passwords.
Use WPA2 or WPA3 encryption for your Wi-Fi.
Disable WPS and remote management unless required.
Update router firmware to patch vulnerabilities.
Use the router’s built-in firewall.
Set up a separate guest network (to isolate smart devices and visitors).
5. Keep Software and Devices Updated
Update operating systems, apps, and firmware regularly.
Enable automatic updates when available.
Outdated software often contains known security flaws that hackers exploit.
6. Practice Good Cybersecurity Hygiene
Limit sharing personal information on social media – it can be used for identity theft or guessing passwords.
Avoid saving passwords on shared devices.
Never share credentials through unsecured messages or emails.
Use a VPN to encrypt your internet traffic and hide your IP address.
New Life Technology Group Recycling Protocol

At New Life Technology Group, security doesn’t stop at the digital level – it continues into the recycling process. As a 501(c)(3) nonprofit focused on repurposing electronics for underserved communities, protecting donor data is a top priority.
Before any computer or device is refurbished and redistributed, New Life Technology Group follows strict data destruction protocols:
Certified data-wiping tools erase hard drives using industry standards.
Devices encounter multiple verification steps to confirm the complete removal of sensitive information.
Inoperable drives are physically destroyed to prevent recovery.
All procedures align with the Department of Defense and NIST data sanitation guidelines.
Whether you donate a laptop, desktop, or smartphone, you can feel confident that no data remains. This ensures both your privacy and the safe use of devices by children, families, and schools that receive them.
Watch this video to see how New Life Technology Group receives and processes your old electronics.
youtube
Key Considerations for Avoiding Hacker Intrusions

Avoiding hacker intrusions starts with knowledge. Understanding attack methods allows you to counter them with proactive steps.
1. Password Strength Is Non-Negotiable
Password habits make or break your digital security. One compromised login can lead to a chain of breaches across multiple accounts. Always use unique passwords, and never reuse them.
2. MFA Should Be Standard Practice
Multi-factor authentication is one of the most effective defenses against unauthorized access. Even if a hacker steals your password, they can’t enter your account without the secondary verification method.
3. Phishing Attacks Are Evolving
Scammers constantly update their techniques to appear more convincing. Look for signs like misspellings, generic greetings, or urgency tactics. When in doubt, go directly to the website instead of clicking links in emails.
4. Secure Wi-Fi Is Your Digital Castle
Leaving a router on default settings is like handing out your house key. Change login credentials, apply encryption, and perform firmware updates to keep hackers out.
5. Updates Are Digital Armor
Hackers target old software because vulnerabilities are already known. Updates patch these holes. From smartphones to smart thermostats, every device should run current software.
6. Hygiene Is Not Just Physical
Every online action leaves a trail. Oversharing, accepting unknown friend requests, or installing unverified apps can all open doors for hackers. Be selective and cautious online.
7. Use Technology to Fight Technology
Password managers, VPNs, firewalls, and antivirus software all strengthen your defenses. Use tools wisely and consistently to stay protected.
Note: Cybersecurity is an ongoing effort, not a one-time setup. The digital landscape evolves rapidly, and hackers constantly adapt their tactics. By using the methods mentioned above, you create multiple layers of protection around your data. With partners like New Life Technology Group ensuring safe digital recycling, both your online and offline presence remain secure.
Cybersecurity Tips
In this article, you discovered information about the methods hackers use to control your devices and steal your data, ways to safeguard your online information, and how to safely donate used computers and electronics.
Create layers around your sensitive data (strong passwords, Multi-Factor Authentication, a secure network, and staying informed).
Ignoring your cybersecurity strength can leave you vulnerable to breaches and thieves (and barred from accessing your devices until a ransom is paid).
Sources: cisa.gov/topics/cybersecurity-best-practices consumer.ftc.gov/media/79887 security.berkeley.edu/resources/best-practices-how-to-articles/top-10-secure-computing-tips
New Life Technology Group
253 Grogan Dr #120 Dawsonville, GA30534 (404) 313-8215
To see the original version of this article, visit https://newlifetechgroup.com/tips-to-avoid-hacker-intrusions/
#e-recycling#e-waste#data destruction#nonprofit e-recycler#donate computer#computer donations#Cyber Security#technology#Youtube
1 note
·
View note
Text
Week 10 BLOG // POST 8
How can trolling be defined and in what ways does it pose a threat to the online community?
Trolling, in the words of Judith Donath, is a spiteful and purposefully deceptive untruth. According to Donath, the presence of trolls can be dangerous for online communities since it makes people far less willing to trust non-members or put up with individuals who don't follow the rules. Another study that defines trolling is one by Clair Hardaker, in which she looks at almost nine years' worth of posts, two thousand of which contain some variation of the term "troll" (Phillips). However, she considers the troll's point of view when she defines a troll as someone "whose real intentions are to cause disruption and/or to trigger or exacerbate conflict for their own amusement." This knowledge that trolling often consists of "malicious and deliberately destructive lies intended to prevent trust and create divisiveness within online communities." Trolling can determine people from using online communities, preventing them from interacting with others, which is something that some people require.
How does online trolling impact digital spaces for women of color?
When dealing with online trolling, women of color are often not taken seriously in digital spaces. This can create more discrimination towards women of color. For example, Leslie Jones experienced horrific online abuse from trolls. One instance involved her website being hacked, where the hacker exposed her private photos, passport, driver’s license, and more. This is not the first time Jones has been the target of online trolls, the fact that this keeps happening to her proves that digital spaces do not care about how she is being treated. After the all-female Ghostbusters movie trailer came out, her Twitter account was inundated with racist and sexist hate speech. Even commenter Milo Yiannopoulos made this online harassment campaign spread even more by giving a negative review on Jones stating “ “flat-as-a-pancake black stylings" (Silman). This made his followers and other members of the alt-right community began to troll Jones with sexist and racist comments and hateful memes. Milo was even spreading fake tweets pretending to be from Jones. Jones spreads her concerns on Twitter about how they need to improve their harassment policies. Jones had to repost these hateful tweets to get attention from Twitter to do something about these fake tweets. Twitter needs to have a distinction between “hate speech and freedom of speech”. We have to protect women of color from getting harassed on the internet. If you see it report it.
What demographic groups are most impacted by online harassment, and what specific types of harassment do they experience?
According to Pew research, there are about six different types of online harassment, about 73% of adult internet users have seen someone be harassed in some way online and 40% have personal experience. When it comes to which demographic groups that experience online harassment, young adults and women have been affected by six elements of online. Between the ages of 18-29, 65% of young internet users have been the target of at least one of the six elements of harassment that were queried in the survey. Young women between the ages of 18-24 experience certain serve types of harassment. 26% of these young women have been stalked online, and 25% were targets of online sexual harassment (Cheng). Women tend to have high levels of harassment compared to men who get harassed by name-calling on video games. How do individuals who are more active on the internet experience higher rates of online harassment?
People who use the internet in their daily lives experience higher rates of online harassment. If you have information available online, such as influencers or regular users who promote themselves for their jobs, this can include platforms like Indeed and LinkedIn. Additionally, individuals working in the digital technology industry, including companies like AI firms, Google, Microsoft, and others, are also affected. Approximately 66% of internet users who have experienced online harassment reported that their most recent incident occurred on a social networking site or app (Cheng). If you use the internet, you may be among that percentage of people who face high levels of online harassment.
Work Cited
Cheng, J., Bernstein, M., Danescu-Niculescu-Mizil, C., & Leskovec, J. (2017). Anyone can become a troll: Causes of trolling behavior in online discussions. CSCW : proceedings of the Conference on Computer-Supported Cooperative Work. Conference on Computer-Supported Cooperative Work. https://www.ncbi.nlm.nih.gov/pmc/articles/PMC5791909/
Silman, A. (2016, August 24). A timeline of Leslie Jones’s horrific online abuse. The Cut. https://www.thecut.com/2016/08/a-timeline-of-leslie-joness-horrific-online-abuse.html
Phillips, W. (2015) The Origins of Trolling.
#wgst320f24
3 notes
·
View notes
Text
Ways to Protect Your VPS Against Online Threats
Leaks of customer information are devastating to businesses; not only may they damage the reputation of your firm, but they may also result in severe legal penalties. It is essential to have a solid understanding of virtual private server security in order to protect oneself from any dangers on the internet.
Nevertheless, in addition to adhering to the most effective security practices, you are required to perform routine checks on your virtual private server (VPS). In this article, you are given useful suggestions for protecting virtual private servers (VPS) from cyberattacks. Keep reading to learn more!

Tips for Virtual Private Server Cybersecurity in 2024-
If you are in charge of a web server, it is absolutely necessary to remain up to date on the most recent security measures and risks that are posed by the internet. In the year 2024, the following are the best practices for assuring the security of virtual private servers (VPS)!
Deactivate the Root Login feature
Any element of the server can be modified by the root user of a virtual private server (VPS), who has the highest level of operational entitlements. In an effort to seize control of the system, hackers might select this user as their target.
This login account can be removed, which would reinforce the defense against root access and safeguard your website from attacks. For the sake of server administration, we recommend creating a new login that is capable of accessing the root level and running commands.
Make your passwords more secure
The most easily guessed passwords are ones that are poorly crafted, such as those that contain common terms or data that may be identified. You may create secure passwords by mixing different types of characters, including numerals, special characters, and both uppercase and lowercase letters.
The use of secured password management software is something you might want to think about if you want to simply generate and save secure passwords. It is essential to keep in mind that originality is essential. Consequently, it is recommended that you change your passwords periodically, preferably once every three months, and never use the same password for more than one account. As a final precaution, you should never provide your root login credentials in order to prevent unauthorized access.
Modify the SSH Port That Is Default
If you continue to allow attackers to access your virtual server over the normal SSH port of 22, you are inviting them to do so. Port scanning and brute-force attacks are two methods that attackers can use to gain unauthorized access to a remote system. When securing virtual private server (VPS) cyber threats, it is important to lock out unauthorized users and change the default SSH listening port to something unexpected.
Restriction of User Access
When you have a significant number of users on your virtual private server (VPS) hosting, it is important to carefully plan out how rights and control will be distributed. Your server's sensitive data and assets are at risk of being compromised if you grant root access to each and every user. By understanding and applying the various forms of authorization, you can make certain that each user has access to only the permissions that they require.
In the event that an account is compromised, this strategy ensures that the damage is reduced to a minimum. Sensitive information and systems are protected from harm since this reduces the attack surface and diminishes the possible effects that could be caused by attacks that originate from within the organization. A further benefit is that it simplifies audit procedures, which makes it easier to monitor user activity and identify inconsistencies.
Put the Principles of Robust Authentication into Practice
A strong, one-of-a-kind password should be generated for each account on your virtual private server (VPS), and you should utilize multi-factor authentication (MFA) to add an extra layer of security. For remote access, you should make use of secure protocols such as SSH keys in order to prevent unauthorized login attempts and protect your virtual private server (VPS) against assaults that are based on credentials.
It is difficult to decode these automated keys because they are typically longer than passwords. Public and private keys are the components that makeup SSH keys. It is the device that is utilized that is responsible for storing the private key, whereas the server of the computer is where the public key is kept. In the event that an individual attempts to log in, the system generates an arbitrary string. This string is then protected with the public key. The only way to gain access is to decrypt this string using a private key that is compliant with the security system.
Set up a VPN on your VPS
Your information is at risk of being intercepted and stolen by third parties who are not authorized to do so if you use a public connection. Set up a virtual private network, also known as a VPN, to protect yourself from potential security threats and in order to avoid this. Using a virtual private network (VPN), your computer is able to conceal its true location while also directing traffic through a secure connection.
This is accomplished by using a new IP address. Your Internet Protocol (IP) address will be rendered untraceable as a result of this, which will allow you to remain anonymous surfing the internet. Your data is protected by a virtual private network (VPN), which also prevents hackers from accessing your communications. Alongside a firewall, it provides additional protection for virtual private servers (VPS).
Be sure to utilize firewalls
Your firewalls are your first line of defense against threats that come from the internet. APF and CSF are examples of programs that act as guardians by monitoring both incoming and outgoing traffic. They contribute to the identification and prevention of undesired movements at the entrance, so ensuring that only authorized traffic is allowed to pass through. They offer a barrier that can be designed to match the specific requirements and security requirements of your system, and it may be updated to meet those requirements.
Firewalls have a number of features that aid with the rapid identification and management of typical cyber risks. One of these features is the ability to generate detailed logs and send notifications regarding potential safety incidents. The fact that they are able to make adjustments and offer timely protections makes them an essential resource for cybersecurity.
Make sure you do regular backups
You should create backups of your data on a regular basis to protect it from being lost in the event that there is a data breach. Ensure that backups are stored in a location that is not the virtual private server (VPS) and implements automated backup mechanisms. Because of this, even if the virtual private server (VPS) is compromised, your essential data will remain secure and accessible.
Set up an antivirus program
Installing antivirus software on your virtual private server (VPS) will protect your data and forestall any compromises. An antivirus tool for your server performs continuous inspections of files and actions, much like software that has prevented the malware from infecting a large number of PCs around the world by spotting dangers in real-time.
Employ a Malware Scanner Software
Your virtual private server (VPS) is protected from dangers such as trojans and worms by an antivirus program; however, it may not be able to identify more recent exploits such as zero-day malware.
Combine antivirus software with a malware scanner to improve the security of your virtual private server (VPS). This category of software is able to update the detection rule more quickly, which enables it to differentiate between newer threats that are present on your system.
Check out the User Rights
If there are a large number of users on your virtual private server (VPS) hosting, you should give serious consideration to the distribution of control and rights. Your server's resources and sensitive data will be put at risk of security breaches if you grant root rights to every user on the server.
You should restrict the number of users who can access your server in order to avoid this problem. Managing users and assigning them varying permissions for particular files and system resources is one way to accomplish this goal.
Install systems that can detect and prevent intrusions
Monitoring and analyzing network traffic with the help of intrusion detection and prevention systems (IDPS) is a good way to keep an eye out for any indicators of malicious behavior or efforts to gain unauthorized access. IDPS's ability to detect and block threats in real time contributes to an overall improvement in the security posture of your virtual private server (VPS).
Conclusion-
The protection of your virtual private server (VPS) is essential since it stores sensitive information. In spite of the fact that Linux is well-known for its robust security, the virtual private server (VPS) nevertheless has weaknesses. Malware, sniffer and brute-force attacks, SQL injections, cross-site scripting (XSS), lacking function-level control, and incomplete authentication are some of the most common types of cyber assaults and problems that can occur in a Linux system. Virtual private server owners need to be aware of how to monitor the server and operating system in order to implement effective security measures in order to avoid these issues.

Dollar2host Dollar2host.com We provide expert Webhosting services for your desired needs Facebook Twitter Instagram YouTube
2 notes
·
View notes
Text
How to Protect Your WordPress Site from Malware or Hackers?
WordPress is used by millions of websites for blogs, businesses, and online stores. However, because it’s so popular, it’s often a target for hackers and malware. If you have a WordPress site, it’s important to take steps to keep it secure. Here’s a simple guide to help you protect your site from hackers and malware.
How to Protect WordPress Site from Malware or Hackers?
Follow this step list given below to protect WordPress site from malware or hackers
1. Always Keep WordPress Updated
WordPress regularly releases updates to fix bugs and improve security. Hackers often look for websites running old versions of WordPress or outdated plugins, so keeping everything updated helps keep them out.
How to Update:
Check for updates in your WordPress dashboard regularly.
Go to the Dashboard > Updates section and install any available updates for WordPress core, themes, or plugins.
By staying updated, you’re less likely to have security holes in your site that hackers can use.
2. Use Strong Passwords and Change Them Often
Hackers can easily guess weak passwords like "123456" or "admin." To keep your site safe, use strong, unique passwords and change them every few months.
Tips for Strong Passwords:
Use a mix of uppercase and lowercase letters, numbers, and symbols.
Don’t use simple information like your name or "admin."
Consider using a password manager to create and store complex passwords securely.
Strong passwords are one of the simplest ways to add security to your website.
3. Limit Login Attempts
Hackers often try to break into websites by guessing the login password over and over. You can protect your site by limiting the number of login attempts a person (or bot) can make.
How to Limit Login Attempts:
Use plugins like Limit Login Attempts Reloaded or WP Limit Login Attempts.
These plugins lock out users after a certain number of failed login attempts.
This makes it much harder for hackers to keep guessing passwords.
4. Enable Two-Factor Authentication (2FA)
Two-factor authentication adds another layer of security. In addition to entering your password, you’ll also need to input a code sent to your phone or email. Even if someone knows your password, they won’t be able to log in without this extra code.
How to Set Up 2FA:
Install a plugin like Google Authenticator or Two-Factor.
Set it up by scanning a QR code and linking your account to an app like Google Authenticator or Authy.
This ensures that only you can access your site, even if someone steals your password.
5. Use a Security Plugin
A security plugin can protect your WordPress site from different types of attacks, like malware or brute force attempts. These plugins act as your site’s security guard, offering tools like firewalls and malware scanning.
Recommended Security Plugins:
Wordfence Security: Includes a firewall and real-time monitoring.
Sucuri Security: Provides malware removal and a website firewall.
iThemes Security: Offers brute force protection, backups, and two-factor authentication.
Using a security plugin adds strong layers of protection against hackers.
Also Read - What Is Domain Status? What does this mean, & Why should I know?
6. Back Up Your Website Regularly
Even with good security, things can sometimes go wrong. That’s why it’s important to back up your site regularly. If your site gets hacked, a backup will let you restore everything quickly without losing important data.
How to Back Up Your Website:
Use backup plugins like UpdraftPlus or BackupBuddy.
Store your backups in safe places like Google Drive, Dropbox, or a remote server.
Schedule backups daily or weekly, depending on how often you update your site.
Regular backups help ensure you won’t lose everything if something goes wrong.
7. Choose a Secure Hosting Provider
Your web hosting service plays an important role in your website’s security. Some hosts offer strong security features that help protect your site. Make sure to choose a hosting provider that values security.
What to Look for in a Hosting Provider:
Regular backups
Malware scanning and removal
Firewalls
SSL certificates
DDoS protection
Popular and secure WordPress hosting services include SiteGround, Bluehost, and WP Engine.
8. Use HTTPS and SSL Certificates
SSL (Secure Socket Layer) encrypts the data between your website and your visitors. This protects sensitive information, like passwords or credit card numbers. Websites with SSL certificates also have a secure URL that starts with "https://."
How to Install an SSL Certificate:
Most hosting providers offer free SSL certificates with Let’s Encrypt.
You can use plugins like Really Simple SSL to set it up quickly.
SSL certificates keep sensitive data safe and make your site more trustworthy.
9. Remove Unused Themes and Plugins
Unused plugins and themes can create security risks, especially if they aren’t updated. Even if they’re deactivated, they can still be a weak point. It’s best to delete any plugins or themes you don’t use.
How to Delete Unused Themes/Plugins:
Go to your Dashboard > Plugins or Appearance > Themes.
Deactivate and delete anything you no longer need.
This reduces the number of places where hackers might try to get in.
10. Monitor Your Site for Suspicious Activity
It’s important to keep an eye on your site for any unusual behavior. This could include sudden spikes in traffic, unknown files appearing on your server, or unauthorized users trying to log in.
How to Monitor Your Site:
Use a security plugin to track things like failed login attempts and changes to important files.
Regularly check your hosting account for unusual activity.
Review your website users to make sure no unauthorized accounts have been added.
By staying alert, you can catch potential threats before they do any serious damage.
Conclusion
Protecting your WordPress site doesn’t have to be difficult. By following these simple steps—keeping WordPress updated, using strong passwords, installing security plugins, and making regular backups—you can greatly reduce the risk of your site being hacked or infected with malware.
#OZOHosting#lowest price hosting in india#Cheap web hosting jaipur#cheap shared web hosting india#free web hosting india#affordable linux web hosting india
2 notes
·
View notes
Text
BLOG POST 2

In this week’s lecture. It explains about Digital Citizenship. What is Digital Citizenship? It is the ability to utilise technology sensibly, securely, and politely is known as digital citizenship. It refers to the capacity to safeguard private information on the internet, reduce the risks brought on by cyberthreats or other online threats, and use information and media in a polite, informed, and lawful manner (Lcom 2023). For this week’s post. It will further explain the components of Digital Citizenship.

The first component of digital citizenship is Internet safety. With how the internet has been used widely in this world of modern technology, safety is always a first in everything regardless of what are the aspects of life that exist. Crime exists everywhere, like the real world. Crime also happens on the internet and that is why internet safety is a must. Despite their connections, these subjects are distinct concepts. Internet safety includes specific dos and don'ts to protect kids, while digital citizenship curriculum focusses on how behavior and actions spread and affect others on the online and the ways users should conduct themselves as good citizens of this digital world (Twomey n.d). There are many safety precautions when it comes to internet activities to ensure the users data is safe and protected. For example, always use a strong password. Even with a strong password, users are advised not to use password that is related to themselves to increase the security of the account. When it comes to scams and such, it can happen in creative ways. Therefore, users are advised to be aware of what link they encounter and not to simply click on any link as they could be a phishing link. As for scam calls, it is best to first listen to the caller and analyse it. If the caller sounds very suspicious, it is best to end call. And never answer yes or no as hackers might already have the user’s data and they only need verification to use the data.

Secondly, verifying sources. Before the internet, society is used to information being spread slowly. But with technology, information can now be spread in a blink of an eye. And since information sharing is now faster than ever. Misinformation can happen at any given moment. This will cause disruption in society if users are not careful with the information that they share. It's imperative that professionals adopt a critical mindset and see the value of confirming the veracity and authenticity of the material they encounter (Kariuki 2023). With critical thinking, users can help to prevent misinformation to be spread. These steps will help to ensure that whatever information that a user come across is proper. Before sharing, it is best to fact-check the information and to not just simply believe what people online have shared or posted. Research on said information and make sure that whatever is shared is accurate. While fact-checking is important. Reliability is equally as important. It is recommended that users identify whether the origin of the information is published by a reliable website/account. There are a lot of people who create multiple accounts or even a website just to publish fake news to the online community and that causes disruption. As for students, especially those who are continuing their studies in the higher education. They are advised to ensure their citations is a proper citation and that the resources they gathered are from a reputable source. Other than making sure students learn to be a responsible digital citizen, they can also save their marks on their assignments.

Third concept is managing inappropriate content. With internet. There are many information and contents that can be found online and can be searched in the matter of seconds. One of them is inappropriate content. What exactly is considered as inappropriate content? This can vary differently by age. But to narrow it down for a student perspective, it is content like the dark web, adult websites, weapons etc. These are websites that are very inappropriate to students. Even if they do not know how to search for these contents, they may accidentally stumble across these contents. Raising awareness and instructing others on how to be good digital citizens are important aspects of being a good digital citizen. Teach teenagers how to constructively discuss harmful internet activity with their friends. Assist them in recognising when something has gotten too far for them to manage alone and in understanding boundaries (Shannon n.d). Adults should help raise awareness on this issue. Always supervise their children’s online activity. Adults are responsible to nurture their children’s childhood and let them enjoy it as they should. As users, when come across with inappropriate content, it is recommended to report the content and adjust their profile and choose what content that users want and do not want to see.
In conclusion, being a good digital citizen is important for everyone to ensure a fun, interactive and safe environment for others, especially for children to use. This also keeps the internet safe to use for everyone. The government should also improve the cyber security so that the people are assured that their data is well kept secure.
REFERENCES
Kariuki, C, 2023, Navigating the Digital Era: The Power of Verifying Information, LinkedIn, 22 May, viewed 4 October 2024, <https://www.linkedin.com/pulse/navigating-digital-era-power-verifying-information>.
Lcom Team, 2023, What is Digital Citizenship & What Does It Include?, Learning.com, 11 July, viewed 4 October 2024, <https://www.learning.com/blog/what-is-digital-citizenship/#:~:text=Digital%20citizenship%20is%20the%20ability,respectful%2C%20knowledgeable%20and%20legal%20way>.
Safe Space, 2020, Inappropriate Content [Image], Safe Space, 28 May, viewed 4 October 2024, < https://www.safespace.qa/en/topic/inappropriate-content>.
SAFESITTER, n.d, 9 Lessons to Teach Children About Digital Citizenship [Image], SAFESITTER, viewed 4 October 2024, <https://safesitter.org/digital-citizenship/>.
Shannon, J, n.d, Digital Citizenship: 7 Steps to Keep Our Kids Safe Online, JONNYSHANNON, viewed 4 October 2024, <https://www.jonnyshannon.com/blog/a-guide-to-teaching-smart-digital-citizenship-how-to-keep-kids-and-teens-safe-online#:~:text=Teach%20kids%20and%20teens%20how,to%20take%20the%20next%20step.>
Stark, R, 2023, Internet safety 101: 10 Simple Rules to Keep You Safe [Image], Acer Corner, viewed 4 October 2024, <https://blog.acer.com/en/discussion/500/internet-safety-101-10-simple-rules-to-keep-you-safe-2023>.
Thompson, J, 2023, Opinion: Are We Having a Moral Panic Over Misinformation? [Image], UNDARK, 26 October, viewed 4 October 2024, <https://undark.org/2023/10/26/opinion-misinformation-moral-panic/>.
Twomey, K, n.d, Digital Citizenship and Internet Safety: Essentials for Responsible Online Behavior, StoryboardThat, viewed 4 October 2024, <https://www.storyboardthat.com/articles/e/digital-citzenship>.
2 notes
·
View notes
Text
How to Hire a Social Media Hacker Safely: A Complete Guide
In today’s tech-driven world, social media accounts are more than just a place for socializing—they are gateways to personal and business data. Whether you're locked out of your account, worried about digital privacy, or need to strengthen your security, hiring a hacker might seem like a quick fix. However, it's important to approach this cautiously. In this guide, we'll explain how to safely and legally hire a social media hacker, what to look for, and the risks involved.
1. Why Hire a Social Media Hacker?
There are a variety of reasons why you might consider hiring a hacker for your social media needs. Some of the most common include:
Account Recovery: Losing access to a social media account due to hacking or forgotten passwords can be frustrating. A professional hacker can bypass recovery protocols and get you back in.
Security Audits: Ethical hackers can identify weaknesses in your social media security, helping you prevent future cyber-attacks.
Data Retrieval: For business purposes, some companies hire hackers to retrieve important information or gain insights into competitors.
While the idea of hiring a hacker might seem risky, when done ethically and legally, it can be a helpful resource in regaining control over your online assets.
2. What is a Professional Social Media Hacker?
A professional social media hacker is an expert skilled in identifying and exploiting weaknesses in social media platforms to recover accounts, enhance security, or gather data. These hackers fall into two categories:
White-Hat Hackers: Ethical hackers who work within legal boundaries. They are typically hired for account recovery, security testing, and digital protection services.
Black-Hat Hackers: Individuals who use their skills for malicious purposes, such as unauthorized access or data theft.
It's essential to make sure you're hiring a white-hat hacker to ensure the legality of their actions. White-hat hackers use legitimate methods to help you regain access or fortify your account.
3. How to Hire a Social Media Hacker
Finding a reliable social media hacker takes more than just a quick Google search. Here’s how you can find a legitimate hacker without falling for scams:
Freelance Platforms: Websites like Upwork, Freelancer, and Fiverr host professionals offering hacking and cybersecurity services. Be sure to check reviews and ask for verifiable past work.
Cybersecurity Firms: Many reputable companies specialize in ethical hacking services. Hiring through these firms ensures that you’re working with professionals who will operate within legal boundaries.
Hacker Forums: There are many online forums where ethical hackers offer their services. However, proceed with caution, as these forums can also be a breeding ground for scams.
Once you find a hacker, ask for credentials or proof of their experience with the platform you need help with, such as Facebook, Instagram, or Twitter.
4. The Benefits of Hiring a Professional Social Media Hacker
When you hire a social media hacker, you're not just gaining access to your account; you're investing in your online security and peace of mind. Here are the key benefits:
Quick Account Recovery: Forget the long, frustrating customer support routes. A professional hacker can help you regain access faster.
Improved Security: By running security checks and vulnerability assessments, hackers can help you secure your social media accounts and prevent future breaches.
Competitive Advantage: In business, accessing legally obtained data from competitors can help improve your strategies.
Hiring a hacker can be a valuable tool for both personal and professional needs, but only when done ethically.
5. Legal Risks of Hiring a Social Media Hacker
While hiring a hacker can solve a number of problems, it’s essential to understand the risks involved:
Illegal Hacking: Hacking someone else's social media account without permission is illegal and can result in serious legal consequences. Always make sure that your actions, and the actions of the hacker you hire, are within the legal framework.
Scammers: Unfortunately, there are many untrustworthy individuals who claim to be hackers but are really out to scam people. Be careful when sharing personal information, and only work with vetted professionals.
Ethical Concerns: Even if a hacker offers to retrieve information from someone else’s account, remember that doing so without consent is unethical and illegal.
Before you hire, ensure that the hacker’s actions will be lawful and ethical to avoid any legal trouble.
6. How to Protect Yourself When Hiring a Hacker
To safely hire a social media hacker, here are some best practices to follow:
Do Your Research: Take the time to verify the hacker’s credentials. Look at their previous work, ask for references, and check for any feedback from past clients.
Use Secure Communication: Always communicate securely with the hacker to protect your personal information. Avoid sharing sensitive data over unencrypted platforms.
Create a Clear Agreement: Before any work begins, have a formal contract that outlines the services to be performed and the legal limitations. This protects both parties and ensures that the work stays within ethical boundaries.
7. Hiring a Social Media Hacker: What to Expect
When working with a professional hacker, clear communication and expectations are essential. Here’s what to expect:
Transparent Pricing: The cost of hiring a hacker can vary depending on the complexity of the task. Be wary of hackers who offer extremely low rates, as they might not be legitimate.
Clear Communication: A professional hacker should explain the process clearly and answer any questions you have along the way.
Results: Whether you’re looking for account recovery or a security audit, a professional hacker should deliver results within the agreed-upon timeframe.
Conclusion: The Right Way to Hire a Social Media Hacker
Hiring a social media hacker can be an effective way to recover lost accounts, strengthen security, or gain strategic insights. However, it’s essential to hire a reputable, ethical hacker who operates within legal boundaries. By following the steps outlined in this guide, you can safely and legally hire a professional social media hacker to help with your digital needs.
For more information:
Hire a Hacker
Hire a Social Media Hacker
Professional Social Media Hacker
This article integrates the keywords "hire a hacker," "hire a social media hacker," and "professional social media hacker" naturally throughout the content, while keeping the information helpful and engaging for readers. It also includes hyperlinks to the desired website for further exploration, ensuring SEO indexability.
2 notes
·
View notes
Text
One of Europe's most wanted cyber criminals has been jailed for attempting to blackmail 33,000 people whose confidential therapy notes he stole.
Julius Kivimäki obtained them after breaking into the databases of Finland's largest psychotherapy company, Vastaamo.
After his attempt to extort the company failed, he emailed patients directly, threatening to reveal what they had told their therapists.
At least one suicide has been linked to the case, which has shocked the country.
Kivimäki has been sentenced to six years and three months in prison.
In terms of the number of victims, his trial was the biggest criminal case in Finnish history.
One of them gave their reaction to the BBC.
"The main thing is that this absolutely empathy-lacking, ruthless criminal gets a prison sentence", said Tiina Parikka.
"After this there rise thoughts about how short the conviction is, when reflected against the number of victims", she added.
"But, that's the Finnish law and I must accept that."
The 26-year-old had maintained his innocence - despite going on the run and being arrested in Paris under a fake identity.
During the trial, he also went missing for more than a week after refusing to be recalled back to prison by the court.
The judges found him guilty of all counts, describing his blackmail as "ruthlessly taking advantage of another person's special weakness."
"Taking into account Vastaamo's position as a company producing mental health services, Kivimäki has caused great suffering or the risk of it to the interested parties," the verdict document said.
The verdict brings to an end a cyber crime spree that started when he was just 13 years old.
Kivimäki, known online as Zeekill, was a key member of multiple teenage cyber gangs which caused chaos between 2009-2015.
He was arrested in 2013, at the age of 15, and given a juvenile non-custodial two-year suspended sentence.
At the time, cyber experts were worried his punishment would fail to deter him - and he was quickly linked to many more hacks carried out with teen gangs before disappearing for years.
His name was quickly linked to the Vastaamo hack of 2020 after experts pointed to Kivimäki traits in the attack.
He demanded a 400,000 Euro (£340,000) ransom from the company.
When it refused, he emailed thousands of patients asking for 200 Euros and threatening to publish their notes and personal details on the darknet which he did anyway in full.
But it was a mistake that the hacker made himself that led police to a treasure trove of information found on a server that Kivimäki owned.
Unprecedented digital forensics and cryptocurrency tracking also helped secure the conviction.
Tiina Parikka recalls receiving the email from him saying that he had her therapy notes.
She told the BBC it caused her to relapse into mental health problems that the therapy had initially helped her overcome.
“So many people were affected by this in so many ways," she said.
The boss of Vastaamo, Ville Tapio, was also convicted of failing to protect his customers' sensitive data.
Investigations found that the databases were vulnerable and open to the internet without proper protections.
He was given a suspended three-month prison sentence last year.
The company which was once a highly regarded and successful business in Finland collapsed after the hack.
Despite the conviction, the Vastaamo case is not over as civil court cases are now likely to begin in an attempt to get some of the victims compensation for the hack.
6 notes
·
View notes