#IBM Streams
Explore tagged Tumblr posts
Link
Stream processing has existed for decades. The adoption grows with open source frameworks like Apache Kafka and Flink in combination with fully managed cloud services. This blog post explores the past, present and future of stream processing, including the relation of machine learning and GenAI, streaming databases, and the integration between data streaming and data lakes with Apache Iceberg. The post The Past, Present and Future of Stream Processing appeared first on Kai Waehner.
#Apache Flink#Apache Kafka#Artificial Intelligence#Cloud#Middleware#Stream Processing#Streaming Analytics#Streaming Database#AI#Apama#Confluent#Data Streaming#flink#GenAI#IBM Streams#kafka#kafka streams#machine learning#open source#Software AG#Storm#StreamBase#TIBCO
0 notes
Photo
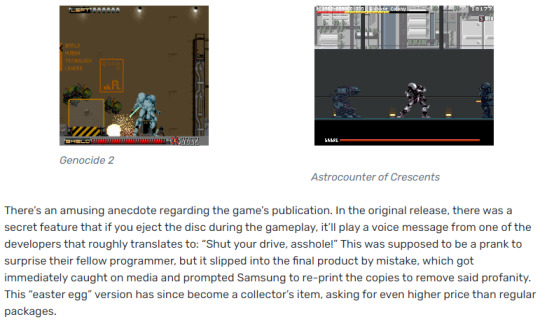

Astrocounter of Crescents (불기둥 크레센츠) (S&T On-Line / Samsung - IBM PC - 1996)
#gonna stream this game eventually#Astrocounter of Crescents#불기둥 크레센츠#IBM PC#IBM#PC game#PC games#mechs#mech games#easter egg#korean games#korean game#robots#beat em up
42 notes
·
View notes
Text


M T C 2 4 0 1
Commissioned storage cabinet inspired by Magnetic Tape Units, specifically the IBM 2401 (1964)
The tape mechanism is decoration only and does not function. DC motors, blinking LEDs and audio streaming(vintage computer sound samples) are run by an Arduino board inside the control unit on top of the cabinet.
Source: https://www.lovehulten.com/
125 notes
·
View notes
Text

In the early 1980s, personal computers were transitioning from text-based interfaces to more visually engaging environments. Sierra On-Line’s King’s Quest: Quest for the Crown, developed in 1984 for the IBM PCjr, was a landmark achievement in this evolution. It was not just another adventure game; it redefined the genre by leveraging the limited hardware capabilities of the time to create an immersive, interactive experience that felt years ahead of its contemporaries. Technical Innovations in King's Quest
1. The Birth of a 3D Adventure Game
At a time when most games were either text-based or limited to simple 2D visuals, King’s Quest introduced a pseudo-3D graphical environment. Players could guide the protagonist, Sir Graham, through a dynamic, scrolling landscape, where he could walk behind or in front of objects—an innovation known as "2.5D."
Pseudo-3D Effect: Achieved through creative use of layers, the AGI (Adventure Game Interpreter) engine divided the screen into foreground, background, and player layers. This gave the illusion of depth and interactivity.
Character Movement: The freedom to move in eight directions and interact with objects in a visually convincing space set a new standard for adventure games.
2. Adventure Game Interpreter (AGI) Engine
Sierra developed the AGI engine specifically for King’s Quest. This software framework was groundbreaking for its time, allowing:
Cross-Platform Compatibility: AGI was portable across different systems, from the IBM PCjr to later platforms like the Apple II and Tandy 1000.
Event-Driven Programming: AGI allowed designers to script events and interactions, decoupling game logic from graphical rendering—a novel approach in the early 80s.
3. Advanced Graphics for the IBM PCjr
The IBM PCjr was an ambitious but underpowered machine, featuring:
Intel 8088 Processor (4.77 MHz): A modest CPU that could struggle with heavy computations.
16-Color Graphics (CGA Palette): While most PCs supported only four colors in CGA mode, the PCjr's extended graphics capabilities allowed for richer visuals.
3-Voice Sound (TI SN76496 Chip): This was a significant improvement over the beeps of the PC speaker, enabling a more immersive auditory experience.
King’s Quest took full advantage of these features:
Rich Color Palette: By designing scenes with careful attention to the 16-color limit, Sierra created lush, vibrant environments that brought the fairytale world to life.
Smooth Animation: Despite hardware limitations, the game’s character animations and environment transitions were fluid and detailed.
4. Text Parser and Command System
While maintaining the classic adventure game tradition of text input, King’s Quest improved upon the interface:
Contextual Parsing: The text parser was more forgiving and sophisticated than previous games, interpreting a wider range of player inputs like "Take sword" or "Open door."
Visual Feedback: Unlike purely text-based games, the parser’s output was directly reflected in the graphical world, making the player’s actions feel meaningful and connected.
5. Disk Streaming and Memory Optimization
Given the IBM PCjr's limited 128 KB of RAM and floppy disk storage, Sierra engineers implemented innovative solutions to manage resources:
Dynamic Asset Loading: Only the necessary graphics, animations, and logic were loaded into memory at a time, minimizing RAM usage.
Compression Techniques: Graphics and animations were heavily compressed to fit on the game’s floppy disks, requiring clever algorithms to decompress assets on-the-fly.
The Impact of King’s Quest
The technical achievements of King’s Quest went beyond its hardware. It had a profound impact on the gaming industry and paved the way for future innovations.
Pushing Hardware to Its Limits: By making the most of the IBM PCjr’s unique capabilities, King’s Quest demonstrated what was possible with even modest computing power.
Setting a Standard for Interactive Storytelling: The game’s rich narrative, combined with its visuals and player agency, set the benchmark for future adventure games.
Expanding the Gaming Audience: The colorful, family-friendly design attracted a broader audience, including casual gamers and younger players.
Influencing Game Design: The AGI engine became the foundation for future Sierra titles, including Space Quest, Police Quest, and Leisure Suit Larry.
#IBM#IBM PCjr#PCjr#Sierra On-line#Sierra Online#On-line Systems#King's Quest#KQ 1#Impact#Pixel Crisis
4 notes
·
View notes
Text
Modern Cryptography
(stemandleafdiagram long-form post!)
~ 2900 words
As you may have guessed, I love cryptography and ciphers even though I still don’t know much about them. I think classical ciphers are super interesting stuff and I love breaking them but I realised I knew nothing cipher-y after the end of World War 2, so I sought to rectify that!
(This is SO long - I got quite carried away (I do apologise), and as I wanted to cover so much here there are some concepts I don’t explain very thoroughly, but there are so many resources online if you want to learn more! When explaining how different forms of encryption work, I will often use the names commonly used by other cryptographers in my examples. Alice and Bob are two people trying to communicate, while Eve (an eavesdropper) is trying to intercept their messages.)
Symmetric Encryption
The start of modern cryptography is not a definite thing (obviously so, as the “eras” of cryptography are just labels people use to refer to them generally) but I decided to start my timeline for modern cryptography in the 1960s, as during this time, research projects at the American company IBM (International Business Machines) led to the creation of a cipher called the Lucifer cipher.
This cipher was one of the first block ciphers to be made. A block cipher is a cipher that operates on blocks of 128 bits at a time. This is in contrast to a stream cipher, which encrypts 1 bit of data at a time. (In a way, you could consider classical ciphers stream ciphers) If the plaintext (un-encrypted data) is smaller than 128, padding schemes will add random data to it to make it up to 128. Modes of operation define how large amounts of data are encrypted. For example, the blocks of data can be encoded separately, or maybe the encryption of one block is affected by the previous encoded block of data.
The Lucifer cipher underwent a lot of alterations, and eventually the National Bureau of Standards adopted this altered version of Lucifer as the Data Encryption Standard, or DES, in 1977. Some of the alterations made that led to DES were actually quite controversial! For example, the key size in Lucifer was 128 bits, but only 56 in DES, which worried people who thought it would have been easier to brute force as it was shorter. It’s actually rumoured that the NSA (National Security Agency) did this so that the DES wasn’t too strong for them to break. Another change they added was the inclusion of something called S-boxes, which are effective at protecting against a form of attack called differential cryptanalysis. What I found really cool was that its effectiveness wasn’t talked about until much after, which suggests that the NSA knew about differential cryptanalysis 13 years before this information went public!
The DES is no longer secure enough for modern use, and in 2001 was replaced by the AES, or the Advanced Encryption Standard, which is its direct successor and is still used today. The reason that AES is more secure than DES is that the algorithm itself is more complex, but more importantly it uses longer key lengths. Using keys that are 128, 192, or 256-bit long means that the encryption is much stronger than using the 56-bit DES.
Lucifer, DES, and AES are all symmetric ciphers as well as being block ciphers. This means that the key used to encrypt the plaintext is the same key that is used to decrypt the data. Only some block ciphers are known publicly. DES and AES are the most famous of the lot, but other ones such as IDEA, Twofish, and Serpent exist too.
As a whole, encrypting with block ciphers is slower as the entire block must be captured to encrypt or decrypt, and if just 1 mistake is made the whole block can be altered. But, they are stronger than other ciphers. Each mode of operation also has its own pros and cons. If each block is encoded by itself then they can be encrypted in parallel (which is faster), but it’s prone to cryptoanalysis as two identical blocks of plaintext would produce two identical blocks of ciphertext, therefore revealing patterns. The other ways are much more complex and take more time to encrypt but are more secure.
For symmetric encryption to be used, both parties need to agree on the same key for the message to be shared secretly, which is a massive problem. How can the key be transferred securely?
Key Exchange
A year before the implementation of DES, in 1976, another massive breakthrough was made. Researchers Whitfield Hellman and Martin Diffie created the Diffie-Hellman key exchange, which was a method to share encryption and decryption keys safely across an unsecured network. The way it works depends on one-way functions. Typically in maths, most functions are two-way, as using a function on a number is pretty easy to undo. However, Hellman and Diffie found out that while multiplying two prime numbers was very easy, factorising the product down to its primes again was excruciatingly difficult, and the difficulty only increases as the numbers get bigger.
Say Alice and Bob are trying to share a key using the Diffie-Hellman exchange. Firstly, both of them need to execute a function in the form G^a mod P. P must be prime, and G and P are shared publicly so Alice and Bob can agree on them. The numbers are massive (usually 2048 bits) to make it harder to brute force, and they are generated randomly. Alice and Bob each choose different numbers for a, and run their functions. They will get different answers and they share their answers with each other publicly. (This is the public key) Then, Alice and Bob run another function in the form G^a mod P, but G is set to the other person’s answer. The value of a and P stay the same, and Alice and Bob arrive at the same secret answer. The secret answer can then be used to encrypt the message! (This is the private key)
Now, let’s say Eve wanted to find out what the key was. She intercepts their messages, but even though she has the exact information Alice and Bob shared with each other, she doesn’t know what the secret key is unless she solved the original equation, making this key exchange very secure! Modular arithmetic (the mod P part of the equation) is notoriously hard to reverse. If 2048-bit numbers are used, then brute forcing it requires 2^2048 numbers.
Asymmetric Encryption
The Diffie-Hellman key exchange was huge - I mean, any technology created 50 years ago that’s still in use must be pretty good, but it really only shone for sharing keys, not for encryption. For example, the issue with sending communication such as emails using Diffie-Hellman was that both parties needed to be online for a key to be generated as information needs to be mutually shared in the process, so you couldn’t just send an email using it whenever you wanted, which was a shame. However, one particular thing it did lead to was the invention of asymmetric encryption.
In 1977, the idea of public key cryptography (also invented by Diffie) came to fruition in the form of RSA. Named after its creators (Ron Rivest, Adi Shamir, and Leonard Adleman), the RSA works by all users having a public key, which is accessible by everyone, so anyone wanting to send that user a message just needed to search for it. The sender encrypts the message with the recipient’s public key, and then when the recipient comes online they are able to decrypt it with their own private key that’s not shared with anyone. It also uses an one-way function like the Diffie-Hellman exchange, albeit a more complex one. RSA is still used today for things like sending messages or visiting secure websites, and the keys tend to be 2048 or 4096 bits long so that they are hard to break. 1024-bit RSA was disallowed in 2013.
Encrypting via public key and decrypting via private key is great for keeping sensitive information safe, but what if you encrypted with your private key and the message was decrypted with your public key? The purpose of this encryption is to prove the sender is who they say they are - if the public key can’t decrypt the message then either the wrong key was used or the message has been meddled with in transit. To keep the message secure the sender could encrypt with their private key and also the recipient’s public key so only they could decrypt and read it. If the message is particularly long, the digital signature can be applied to a hash of the original message, rather than the whole thing. The RSA was the first to have this dual functionality.
So, there we go - the two main encryption types used today: symmetric and asymmetric. Symmetric encryption is useful for large amounts of data in particular, while asymmetric is more secure, but is slower and requires more resources and therefore can be more expensive. In practice, many secure systems will use both symmetric and asymmetric ciphers. Although, the actual security of a message comes down to the length of the key used - the longer or more complex it is, the more secure the encryption is. As the number of bits increases, the total number of arrangements for these bits increases exponentially. The IBM website states that a 56-bit key could be brute forced in around 400 seconds, a 128-bit key would take 1.872 x10^37 years, while a 256-bit key would take 3.31 x10^56 years.
Going Quantum
It goes without mention as to how important modern cryptography is. These encryption methods are used to keep confidential information such as credit card details, messages, and passwords safe for users like you and me, but also maintains government security on a national level. It’s also vital for cryptocurrency and digital signatures (as mentioned before), as well as browsing secure websites.
A big threat to current cryptographic standards is the development of quantum computing, which are computers based on principles of quantum mechanics. I won’t go into detail on how quantum computers work, but using quantum mechanics they are able to do massive numbers of calculations simultaneously. Although quantum computers already exist, they aren’t powerful or capable enough to threaten our current encryption algorithms yet. But, researchers suggest that they could be able to within a decade. People could use a technique called “store now, decrypt later”, where they keep currently encrypted messages so that they can decrypt them when quantum computers are available. This could cause many problems in the future, particularly if they involve secrets on an international level.
Quantum mechanics can also be used in cryptography as well! Quantum cryptography, originally theorised in 1984 by Charles Bennett and Gilles Brassard, can be used to exchange keys even more securely than Diffie-Hellman, and is called QKD, or Quantum Key Distribution. The reason it’s so incredible is that data that’s secured using it is immune to traditional cryptographic attacks. Now, I’m no quantum physicist (or any type of physicist!) but I will try my best to explain how it works. It works by sending photons, which are light particles, from the sender (eg. Alice) to the receiver (eg. Bob). These photons are sent at different orientations and Bob can measure the photon’s polarisation when he gets them.
Let’s say that photons can be in a vertical, horizontal, or one of the two diagonal orientations. We can pass them through a polarised filter to find out what orientation they are in. The filters are also specifically oriented. A vertical filter would let the vertical photons through, block the horizontal ones, and let the diagonal ones in 50% of the time but at the cost of the ones that pass through being reoriented. Therefore, when a particular photon successfully passes through, it’s impossible to know whether it was originally diagonal or vertical. This is important as it means that it’s possible to detect if someone else has been eavesdropping as the polarisations would have been changed.
Bob can use two measurement bases to receive the photons Alice sent. One will capture vertical and horizontal orientations, and one will capture diagonal ones. Bob has no idea what orientation Alice used for each photon, so he switches between his bases randomly, and will get it wrong some of the time. This is fine, as Alice and Bob then compare to see which ones Bob got right, and the ones he correctly guessed are used as a key (each photon representing 1 bit). The key can then be used for other encryption methods, such as AES.
The reason this works is that if Eve wanted to pry, she has to guess which base to use as well when she intercepts the photons (so she will also make mistakes), but she has no way of checking whether her records are correct or not, unlike Bob. It’s impossible for her to obtain the key as well. What’s more, when she guesses wrong she will change the photon polarisation, so Alice and Bob know that she’s eavesdropping.
Quantum cryptography would have huge security benefits if implemented on a wide scale due to its ability to prevent eavesdroppers, and the fact that it would be resistant to quantum computers. However, it is still in development. One key drawback is the specific infrastructure that is needed, and fiber optic cables have a limited range. This means that the number of destinations the data could be sent to is limited, and the signal cannot be sent to more than 1 recipient at any time.
As well as quantum cryptography, the NIST (The National Institute of Standards and Technology) and other cryptographers are working on other cryptographic algorithms that would stay secure even in the face of quantum computers. Ideas include lattice-based cryptography, hash-based cryptography, and code-based cryptography among others but none of them are at a point where they can actually be implemented yet.
However, one new idea that isn’t post-quantum but is gaining traction is Elliptic Curve Cryptography. Elliptic curve cryptography (ECC) is a form of asymmetric encryption that uses different points on an elliptic curve graph to generate keys in a more efficient manner than traditional methods. It creates shorter encryption keys, which means that less resources are needed while making the keys harder to break simultaneously. Improving the security of current systems just involves lengthening the keys, which slows down the encryption/decryption process, so the fact that ECC doesn’t need to do this gives it a big advantage. It is already used by the US government, iMessage, and Bitcoin, among others.
Sidenotes
With the maths of these encryption methods being so strong, one key vulnerability is the people that utilise these methods, which is no surprise. Side channel attacks are a way to break cryptography by using information physically leaked from it. One attack, called a TEMPEST attack, is a technique that can pick up electromagnetic transmissions from a device as far as 300m away. These are often done by the FBI, but honestly can be done quite easily by some nerd who has some money to spare and can sit in a car outside your window. By monitoring the radiation emitted from your computer screen, the attacker can spy on you and your data. Another thing that can be monitored is your power consumption. Cryptography is energy intensive, and this attack has been able to recover RSA private keys in testing. Other forms of attacks include measuring amount of time required to encrypt data, which can perhaps be used to find factors or exponents. To combat this, encryption methods can add timing noise as a countermeasure. Or, an attacker can listen to someone type to find out their passwords, but to distinguish different key presses a sophisticated machine learning model is needed. Side channel attacks have actually been around for ages but its use has been severely limited in that the attacker needs to be physically close to the victim. They could get easier with time, however, as smartphones and drones can act as microphones remotely.
Another cool thing I haven’t covered yet are hash functions, which can take in an input and map it to a string of characters that’s random but unique to the original data. The output is called a hash digest or hash value. A good hash function will mean that no two different inputs will have the same hash value, and all outputs are the same length, making it hard to guess original text length. It’s vital for digital signatures and storing passwords securely.
Finally, if anyone managed to get to the end, then thank you! I really love cryptography and I find it astounding that we’ve been able to develop it into such a complex yet intrinsic part of daily life. Honestly, I had so much fun researching for this post! Encryption and cybersecurity and the future of computing is so interesting and I’m really glad I decided to write this :)
Final final note you should totally go and read the Code Book by Simon Singh! Trust me trust me it’s so good...
4 notes
·
View notes
Note
Legitimately really curious about the music question from that kin ask meme you just reblogged. I'd love an answer about any of your kintypes, but I'm especially interested to know if there's any music that you associate with/really resonates with your experience as an isopod.
THANK YOU
See, here's the thing, I never really associate music with any of my theriotypes. Animalistic species specifically. I get into an animalistic mindset by being in nature or acting out instincts, and music (or any other form of art) is going to take me out of that, especially if there's lyrics. There's no bird music to me, no bug music or mustelid music. I just don't associate it, positively or negatively. I guess no, to answer your question. To be in an isopod shift I'd rather be by the ocean or eat foods similar to what we eat in the wild (seaweed salad I guess), since that's what feels the most animalistic to me. Especially for isopod shifts, an animal that does not have a traditional chordate's sense of hearing, I'm not going to vibe with music. I'd share MyNoise generators that have those vibes for me before any songs.
Music-related shifts for me are all about the sapient kintypes, i.e. computer, Novakid, or fictotypes. But I liked this particular ask meme's music question because it differentiated songs, bands, and genres! And I love to talk genre so!
Individual songs are gonna be (Link) Blame by Air Traffic Controller, Never Existed by Keldian, Take 3 by Inner Wave, Lonesome Dreams by Lord Huron, (for Novakid) S.T.A.R. Child by The Orion Experience, Lightning Riders by AWOLNATION, Space Western by Rich Aucoin, Propane Nightmares by Pendulum, Nova by VNV Nation, (...other) Dreams by Joakim Karud (I cannot concisely explain why it puts me in a computer mindset)
Coincidentally, today (after reblogging that!) I just happened upon a song I didn't know about before, from a band with only 1 album and 10 listeners on Spotify, only available for streaming on a single website in the depths of the obscure music Internet, which catapulted me into a Novakid shift, so here's that, obviously
But I feel like I've listed those songs a million times and never mentioned that genres in general are what "computer kintype music" is for me. My computer kintype is an IBM 7090 so I heavily associate it with 1970s electronic music particularly, so that playlist is a lot of vintage electronica, Space Art, Mort Garson, moog synths, songs with Casio instruments, and recent stuff that takes inspiration from that era like Eyeliner, Jack Stauber, MNQN, and certain synthwave artists. I also associate it a lot with computer animation (pre-Disney-Pixar) so that's a lot of vaporwave and also every soundtrack album for all the Mind's Eye films (those are by James Reynolds, Jan Hammer and Thomas Dolby). I've never been able to find a really good version online of the song from Fabricated Rhythm, which I think is just called Fabricated Rhythm, but I like that too.
Post-punk reminds me of autumn/whatever my weird cryptic kintype is that's associated with the season, but maybe that's just because I'm happiest in fall and I love post-punk. However if anyone can help explain why Figure In the Background by Snake Pool gives me species euphoria lmk
#ask#music talk#sorry if you didn't get the answer you were hoping for! music just really does not make me feel more animal#I used to try and force it to‚ I kept a raven playlist but I eventually realized it was really all just aesthetic and wasn't actually shift#and it was almost entirely Louie Zong anyways
8 notes
·
View notes
Text
Blockchain takes Bollywood by storm
Did you know, there is an ensuing legal battle between a major Hollywood production company and a near bankrupt Indian movie maker on copyright infringement? The story plot revolves around a telephone booth. Guess the name of both the movies and leave it in the comments below.
Up until now, rights and royalties have always been a truly manual process - requiring stakeholders on both ends to manage letters of perpetual ownership, sustainable source approvals that validate the use of intellectual property within the recording (with piles upon piles paperwork confirming your stake) with high risk for errors or disputes at every level. Media asset management is a major issue in movie industry. Movie, music, a script, distribution rights including the proceeds for streaming or airplay are all subject to lease and sale agreements in contracts that quickly get out of hand. This complexity often leads to slow payments for artists, producers and other stakeholders.
Blockchain to the Rescue
Technology consulting companies like Brane Enterprises, Accenture, IBM provide custom solutions built on blockchain technology to enable digital transformation. This technology is an innovative approach based on the decentralized and nonadjustable nature of the ledger, can provide an effective solution to the problems of managing the rights to media assets. With the help of blockchain, all the processes related to operations with media assets can be registered safely and transparently. This is helpful in allowing all the stakeholders to refer to a common source of information, thereby reducing conflicts and inaccuracies.
Recently, a traditionally operated production company based in Hyderabad adopted services offered by Brane Enterprises to create a media assets rights management solution. It details that the production house has lowered its administrative expenses, gained much quicker and reasonably precise royalty payments, and diminished conflicts regarding media asset ownership.
The Future of Blockchain in Bollywood
Given the brilliant outcome of s blockchain implementation in media asset rights management concerning Bollywood, other areas in the entertainment industry may pursue similar strategies. As more organizations get a chance to taste the future through the management of rights on the block chain, it becomes the new norm not only for Bollywood but also other film industries in the rest of the world.
#Blockchain#Rights Management Solution#Media Asset Management#Bollywood#Technology Consulting#Custom Solutions#Copyright Laws#Digital Transformation#Brane blockchain solutions#Blockchain technology by Brane#Brane blockchain development
3 notes
·
View notes
Text
not the red carpet live stream being sponsored by IBM’s AI so yuck
5 notes
·
View notes
Text
AI model speeds up high-resolution computer vision
The system could improve image quality in video streaming or help autonomous vehicles identify road hazards in real-time.
Adam Zewe | MIT News
Researchers from MIT, the MIT-IBM Watson AI Lab, and elsewhere have developed a more efficient computer vision model that vastly reduces the computational complexity of this task. Their model can perform semantic segmentation accurately in real-time on a device with limited hardware resources, such as the on-board computers that enable an autonomous vehicle to make split-second decisions.
youtube
Recent state-of-the-art semantic segmentation models directly learn the interaction between each pair of pixels in an image, so their calculations grow quadratically as image resolution increases. Because of this, while these models are accurate, they are too slow to process high-resolution images in real time on an edge device like a sensor or mobile phone.
The MIT researchers designed a new building block for semantic segmentation models that achieves the same abilities as these state-of-the-art models, but with only linear computational complexity and hardware-efficient operations.
The result is a new model series for high-resolution computer vision that performs up to nine times faster than prior models when deployed on a mobile device. Importantly, this new model series exhibited the same or better accuracy than these alternatives.
Not only could this technique be used to help autonomous vehicles make decisions in real-time, it could also improve the efficiency of other high-resolution computer vision tasks, such as medical image segmentation.
“While researchers have been using traditional vision transformers for quite a long time, and they give amazing results, we want people to also pay attention to the efficiency aspect of these models. Our work shows that it is possible to drastically reduce the computation so this real-time image segmentation can happen locally on a device,” says Song Han, an associate professor in the Department of Electrical Engineering and Computer Science (EECS), a member of the MIT-IBM Watson AI Lab, and senior author of the paper describing the new model.
He is joined on the paper by lead author Han Cai, an EECS graduate student; Junyan Li, an undergraduate at Zhejiang University; Muyan Hu, an undergraduate student at Tsinghua University; and Chuang Gan, a principal research staff member at the MIT-IBM Watson AI Lab. The research will be presented at the International Conference on Computer Vision.
A simplified solution
Categorizing every pixel in a high-resolution image that may have millions of pixels is a difficult task for a machine-learning model. A powerful new type of model, known as a vision transformer, has recently been used effectively.
Transformers were originally developed for natural language processing. In that context, they encode each word in a sentence as a token and then generate an attention map, which captures each token’s relationships with all other tokens. This attention map helps the model understand context when it makes predictions.
Using the same concept, a vision transformer chops an image into patches of pixels and encodes each small patch into a token before generating an attention map. In generating this attention map, the model uses a similarity function that directly learns the interaction between each pair of pixels. In this way, the model develops what is known as a global receptive field, which means it can access all the relevant parts of the image.
Since a high-resolution image may contain millions of pixels, chunked into thousands of patches, the attention map quickly becomes enormous. Because of this, the amount of computation grows quadratically as the resolution of the image increases.
In their new model series, called EfficientViT, the MIT researchers used a simpler mechanism to build the attention map — replacing the nonlinear similarity function with a linear similarity function. As such, they can rearrange the order of operations to reduce total calculations without changing functionality and losing the global receptive field. With their model, the amount of computation needed for a prediction grows linearly as the image resolution grows.
“But there is no free lunch. The linear attention only captures global context about the image, losing local information, which makes the accuracy worse,” Han says.
To compensate for that accuracy loss, the researchers included two extra components in their model, each of which adds only a small amount of computation.
One of those elements helps the model capture local feature interactions, mitigating the linear function’s weakness in local information extraction. The second, a module that enables multiscale learning, helps the model recognize both large and small objects.
“The most critical part here is that we need to carefully balance the performance and the efficiency,” Cai says.
They designed EfficientViT with a hardware-friendly architecture, so it could be easier to run on different types of devices, such as virtual reality headsets or the edge computers on autonomous vehicles. Their model could also be applied to other computer vision tasks, like image classification.
Keep reading.
Make sure to follow us on Tumblr!
#artificial intelligence#machine learning#computer vision#autonomous vehicles#internet of things#research#Youtube
3 notes
·
View notes
Text
The stupid part of this is that if they're all, as the media proclaims, 'afraid of Trump's backlash', then they shouldn't be. As a collective power, they could tear him down so quickly. And they wouldn't even lose a fucking dollar. Because the support they'd get from people just happy to be free again would pay their collective rents forever. Trump's crap wouldn't even touch these six. They could so totally support us if they really wanted to - so I guess they're not really 'afraid of Trump' - they're afraid of 'us'. Just more queerphobic bullshit.
Glad I've never spent a dollar with any of them.
(Should clarify that I've never spent a 'knowing' dollar with any of them - never owned an Apple product, never knowingly owned an IBM product, never flown American, don't buy streaming services, and Vogue magazine is so far from my interest catalogue that they don't even register. That being said, I understand that they may have had an influence over my purchases that I'm not aware of.)

It was always performative anyway. At least now we know.
4K notes
·
View notes
Text
Warangal’s Top College for Data Science Education
The Smart Choice for Future Innovators
As data becomes the new currency in the global digital economy, mastering data science is no longer a luxury—it’s a necessity. From e-commerce to healthcare, logistics to entertainment, data-driven insights are reshaping how the world operates. At the heart of this transformation, Bharathi Degree College has emerged as the best degree college in Warangal for those pursuing data science education.
Whether you're a student setting out on a tech journey, a groom or bride planning a future in digital business, or an entrepreneur scaling with analytics, this 2500-word article explores how Bharathi Degree College leads Warangal’s data revolution with academic excellence, innovation, and career success.Data Science in India: The Growth Story
According to NASSCOM, the Indian analytics industry is expected to reach $16 billion by 2025. Top industries driving demand include:
IT & Consulting
BFSI (Banking, Finance, Insurance)
Healthcare
Retail & E-commerce
With over 11 million job openings in data science and AI globally, India is positioning itself as a major talent hub.Why Bharathi Degree College Leads the Way 1. Industry-Relevant Curriculum
Bharathi Degree College offers one of the most up-to-date data science programs in Telangana. The curriculum is built around:
Programming: Python, R, SQL
Statistics & Mathematics for Data Science
Machine Learning Algorithms
Big Data Tools: Hadoop, Spark
Data Visualization: Power BI, Tableau
The syllabus is NEP 2020-aligned and designed for both academic depth and industry application.2. Practical Projects and Analytics Labs
Hands-on training is a cornerstone at Bharathi:
Mini-projects every semester based on real-world datasets
Capstone projects with business problem statements
Use of cloud-based platforms like Google Colab and AWS
Students graduate with GitHub repositories and digital portfolios that showcase their abilities.3. Faculty with Real-World Data Science Experience
The data science faculty at Bharathi Degree College includes:
Professionals certified in AI/ML and data engineering
Researchers in applied statistics and predictive modeling
Mentors with hands-on analytics consulting experience
Their guidance helps students bridge theory and practice—just like a wedding photographer captures both emotion and composition in one frame.Connecting Trends: Data Science Meets Wedding Photography
Modern wedding photography is driven by:
Facial recognition for tagging photos
AI-powered photo editing
Real-time video analytics for livestreams
The same data science principles used in global business are now shaping Indian cultural experiences. Bharathi Degree College ensures students see this connection—and use it creatively.Career Support and Placement Guidance
As the best degree college in Warangal, Bharathi has a strong placement ecosystem:
Resume-building for data science roles
Mock interviews with analytics professionals
Career fairs featuring tech companies and startups
Students land roles such as:
Data Analyst
Business Intelligence Developer
Data Engineer
ML Intern
Add-On Certifications That Make You Global-Ready
Students can enhance their credentials with:
Google Data Analytics Certificate
IBM Data Science Professional Certificate
Microsoft Power BI Certification
These certifications, paired with classroom learning, prepare students for global job markets.Alumni Success in Analytics
Graduates from Bharathi Degree College have gone on to:
Join MNCs as junior data scientists and data analysts
Pursue master’s in Data Science in the US, Germany, and Canada
Work in tech-based wedding startups, retail analytics firms, and healthcare AI companies
These stories reinforce the college’s reputation as the top choice for data-centric education.FAQs: Data Science Education at Bharathi Degree College
Q1: What background is needed to pursue Data Science? A strong interest in logic, math, and digital tools. Streams like BSc (CS), BSc (MPCs), and BCom (Analytics) are ideal.
Q2: Are there workshops and coding events? Yes. Regular hackathons, analytics bootcamps, and data challenges are part of campus culture.
Q3: Can students pursue internships during graduation? Yes, virtual and in-person internships are supported with guidance.
Q4: What programming languages are emphasized? Primarily Python and R, with SQL and visualization tools for data manipulation.
Q5: Is placement assistance available for analytics careers? Absolutely. From resume prep to interview guidance, full support is provided.Conclusion: Your Data-Driven Future Starts in Warangal
In a world where data powers decisions, marketing, innovation, and even art, choosing the right college is key. Bharathi Degree College not only gives you a solid academic base but nurtures analytical thinking, tech fluency, and creativity.
For India’s next wave of data professionals, this is where the journey begins. Without a doubt, Bharathi Degree College is the best degree college in Warangal for aspiring data scientists and digital leaders.
0 notes
Text

Top 10 Strategies for Integrating AI into Mobile App Development
AI is considered a futuristic application in mobile technology. It has become the enabler that operates all the faster and smartly in engineering mobile applications for each sector. But what makes them intelligent and intuitive nowadays? That is AI. According to a recent prediction made in 2025, the mobile application market is expected a grow to $ 2.63 trillion in 2029!
So the growing popularity of AI in mobile app development helps businesses offer better, faster, and more personalized experiences, thereby causing a lot of challenges and competition among many mobile app development companies. It's time to learn 10 strategies for using AI in mobile app development, which we'll take a deeper look at in the blog.
1. Personalized User Experiences Using Machine Learning
Machine learning lets your app learn what users may want, even before they ask for something! Actually, it analyzes every tap, scroll, and purchase of a user to figure out possible future actions and provide hyper-personalized user experiences.
For Example, Amazon will recommend products that you may be interested in, whereas Spotify may choose your next favorite track for you just before you hit the "skip" button. AI Tools to Power Personalization:
TensorFlow Lite: Brings machine learning directly onto the mobile device for speedy recommendations without an Internet connection.
AWS Personalize: An out-of-the-box recommendation system that ingests user data and offers real-time suggestions.
Google AI: Helps analyze user behavior, rank content, and make more intelligent personalization decisions.
Firebase Predictions: Predicts the possibility of users churning and instantly triggers in-app offers or messages that are personalized for retaining them.
Why Does It Matters? Use of AI for mobile app personalization means user retention and being less prone to churn, contributing fast to app revenue, which helps transform the average user into an avid customer.
2. Smart Recommendations with Collaborative Filtering
AI-powered recommendation engines really boost app usability and app engagement levels that will make the user happy. The engine works on algorithms that look for patterns in enormous data sets for the suggested product, content, or action.
Use Case: Streaming apps apply collaborative filtering for the selection of shows or music, and can be mimicked in product discovery for mobile commerce apps.
Advantages: Increases average session duration by 60%. And reduces bounce rate significantly by showing relevant content.
Tools to Use: Apache Mahout, LensKit, IBM Watson Discovery
Those who are building feature-rich apps may wish to partner with mobile app development agencies possessing AI expertise for high-quality integration.

3. Voice-Enabled Interfaces and Virtual Assistants
Building any modern mobile app these days requires great attention to voice commands and virtual assistants since they establish another sort of hands-free activity. According to a user study, 71% of users prefer using voice search rather than typing; hence, a voice UI must be incorporated. If you find the best mobile app development company like us, they can give these services.
For example, Voice control-granting features to the user through natural language commands can be harnessed in synergy with Google Assistant/Siri.
Tools to Use: Dialogflow, Amazon Lex, or Apple's Speech framework could be employed to develop customized voice experiences. Industries Powered by Voice AI:
Retail apps (for quick ordering)
Banking apps (for balance inquiries)
Travel apps (for bookings and reminders)
4. AI-Powered Chatbots for Customer Support
AI chatbots simulate human interaction to provide immediate assistance, thereby reducing support costs and the trauma of the user.
Real-World Use: AI chatbots can, in the banking domain, respond to queries, initiate transactions, and address problems around the clock. About 64% of the population said one of the best features of an app would be that it offers 24/7 support.
Tip: Use NLP (Natural Language Processing) engines such as Microsoft Bot Framework or IBM Watson to develop conversational interfaces that feel human.
AI Tools for building chatbots: Microsoft Bot Framework, Rasa, Google Assistant SDK
Joint work with an experienced mobile app development agency would give you a smooth integration of the chatbot, trained on your business data.
5. Real-Time Language Translation
Communication barriers of real-time AI translation are crushed and are occasions for inclusion when applied globally. Local-language content experiences a 60% release.
Example: Travel apps moving menus from restaurant onto the screens, from signboards through camera, or to conversations through voice inputs using Google Translate API.
Benefits: One can increase the market reach, plus they get the trust of the end users and their appreciation.
Tools to Use: Google Cloud Translation API, Amazon Translate, Microsoft Translator
6. Predictive Analytics for Decision Making
Thus, when future events are forecasted based on epochs of user incidents in the past and their training, decisions are made such as that may increase engagement or prevent user churn.
Example: In reality, eCommerce apps predict the time of purchase for a particular product and accordingly push the notification for that purchase.
Tools to Consider: Azure ML and AWS SageMaker can provide backend prediction engines.
Stat Insight: Customer lifetime value can grow by 30% with the use of predictive analytics.
Now, when these insights are assimilated well through the expertise of mobile app development Services, they provide even greater ROI and retention.
7. Automated Code Generation & Testing
AI-powered mobile app makers and automated coding assistants can now assist developers by generating code, running tests, and applying intelligent features at rapid speed.
Hence, to speed up software product development and allow teams to ship faster yet with higher code quality, AI tools for mobile app development are listed below:
GitHub Copilot: An AI-powered coding assistant, it helps developers by providing accurate code snippets as they type and helps to write cleaner, simpler, and more efficient code faster.
Testim.io: Automates app testing workflows, catches bugs very fast prior to release, thus improving app stability.
Applitools: Performs visual UI testing with the use of AI for design inconsistencies across devices.
Why Matter? The major essence is that getting codes generated and tests done helps to reduce errors from human intervention, improves the app quality, and cuts down on the cost of development-then the teams can focus on innovation rather than repetitive activities.
8. AI-Driven AR/VR Experiences
Artificial intelligence in mobile apps will take AR/VR experiences further into instant recognition of objects within the environment or scene.
The ensuing possibilities are much more interactive and individualized experiences being offered to the end-user across industries such as retail, gaming, education, and healthcare.
For example, IKEA AR apps let clients visualize how an item of furniture would fit in their homes, while other fitness AR apps create interactive arenas for workouts. Listed below are AI tools for AR/VR experiences:
Google ARCore: Brings AR functionalities such as motion tracking and environmental understanding to mobile apps.
Unity ML-Agents: Bridges AI with AR/VR to create intelligent and interactive virtual environments.
Niantic Lightship: Enables developers to build location-based, real-world AR experiences.
9. Intelligent Automation of App Functions
This very AI service assists in automating the mundane tasks, hence increasing the effectiveness and joy in the use of app offerings. So why not describe automation as making things easier and giving manual time back to a user? According to the survey, 65% of mobile users considered emphasis on an easier interface a major concern.
Some Examples:
Calendar apps automatically suggest times for meetings
Email apps sort inboxes on the basis of usage behavior
Expense apps categorize transactions automatically
Popular Features:
Smart responses for messaging apps
AI-based organization of photos in galleries
Voice-to-text note-taking
Integrate Note: Using background processing APIs with a local AI engine for quick and careful private responses.
Toolbox: IFTTT, Zapier (API-based), Siri Shortcuts, Tasker (Android).
10. AI-Driven Sentiment Analysis
This approach involves having computers study user reviews on apps, feedback, and comments on social media to truly get an understanding of the ambience or sentiment and then adjust mobile offerings accordingly. More than 80% of users read reviews before downloading an app. Hence, a company's ability to understand public sentiment is of extreme importance.
Example: A Shopping app uses review data to find standard complaints or praises about a particular feature.
Value:
Sets feature changes by priority.
Increases user satisfaction level by 40%.
Improves App Store ratings and visibility.
Tool to Use: MonkeyLearn, Amazon Comprehend, Google Cloud Natural Language, Lexalytics

Conclusion A cogent realization comes up—users have no patience with apps and tend to grow restless whenever functionality goes astray. Users don't just trust apps that work; they also trust apps that understand them. And that is what AI the ability for an app to anticipate user needs, interact in real time, and provide ambiently human-type experiences. If you are looking for an AI features mobile app company, here at World India helps you. We are the top mobile app development agency in Mumbai that merges AI with strategic, very human-centered design. Contact us, and let's create wonders!
0 notes
Text
Oil and Gas Data Management Market Redefining Efficiency in Exploration and Drilling
The Oil and Gas Data Management Market was valued at USD 26.9 billion in 2023 and is expected to reach USD 91.4 billion by 2032, growing at a CAGR of 14.59% from 2024-2032.
Oil and Gas Data Management Market is undergoing significant transformation as companies across the upstream, midstream, and downstream sectors embrace digital solutions to improve operational efficiency. As data volumes surge from exploration activities, IoT sensors, and remote operations, energy firms are prioritizing robust data management systems for real-time decision-making and compliance.
U.S. Drives Adoption with Real-Time Analytics and Cloud Integration
Oil and Gas Data Management Market is being reshaped by the demand for scalable, secure, and integrated platforms that can handle complex geological, geophysical, and production data. With growing environmental regulations and shifting energy dynamics, data has become a key asset in managing costs, risks, and sustainability across global operations.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/6713
Market Keyplayers:
Schlumberger – Techlog
Halliburton – Landmark
Baker Hughes – JewelSuite
IBM – IBM Maximo
Oracle – Oracle Oil & Gas Solutions
SAP SE – SAP Oil & Gas Suite
Honeywell – Honeywell Forge
AVEVA Group – AVEVA Unified Operations Center
Cognite – Cognite Data Fusion
Merrick Systems – Merrick Production Manager
TIBCO Software – TIBCO Spotfire
Seeq Corporation – Seeq Workbench
Quorum Software – Quorum Energy Suite
CGG – GeoSoftware
Kongsberg Gruppen – Kognifai
Market Analysis
The market is being propelled by the increasing need for structured data integration, improved asset performance, and predictive maintenance in the oil and gas industry. In the U.S., companies are rapidly digitizing their workflows, enabling better data sharing and automation across departments. Meanwhile, European firms are focusing on data-driven sustainability and regulatory reporting. The competitive landscape is also witnessing increased investments in AI-powered analytics, digital twins, and cloud-based platforms.
Market Trends
Surge in adoption of cloud-based E&P (exploration & production) data platforms
Integration of AI and machine learning for reservoir modeling and risk prediction
Emphasis on cybersecurity to safeguard critical operational data
Real-time data streaming from offshore rigs and pipelines
Use of digital twins to simulate and optimize asset performance
Data governance tools to meet ESG and regulatory standards
Collaboration platforms for seamless data sharing across geographies
Market Scope
With exploration becoming more complex and energy markets more volatile, the Oil and Gas Data Management Market is emerging as a cornerstone of digital transformation. Companies seek end-to-end solutions that deliver insights across the lifecycle—from drilling to refining.
Centralized data hubs for upstream and downstream operations
Workflow automation for seismic and subsurface data
Scalable data lakes supporting real-time analytics
Vendor-neutral platforms for system interoperability
Advanced visualization tools for strategic planning
Modular architecture to support hybrid cloud environments
Forecast Outlook
The Oil and Gas Data Management Market is expected to accelerate in the coming years, fueled by growing investments in digital infrastructure and the need for enhanced operational visibility. As energy firms across the U.S. and Europe seek to optimize production, reduce downtime, and drive sustainability, data will remain central to innovation. The future lies in smart, connected platforms capable of delivering accurate insights and adapting to evolving industry demands.
Access Complete Report: https://www.snsinsider.com/reports/oil-and-gas-data-management-market-6713
Conclusion
In a sector where milliseconds matter and decisions are billion-dollar bets, the Oil and Gas Data Management Market is setting the foundation for a smarter, safer, and more sustainable energy future. As the industry navigates its digital evolution, companies that prioritize data as a strategic asset will lead the charge—minimizing risks, maximizing returns, and future-proofing operations across continents.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Related Reports:
U.S.A Media Asset Management Market fuels innovation in broadcast, OTT, and enterprise media systems
USA brands are investing heavily in Loyalty Management Market to boost customer retention and engagement
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
Mail us: [email protected]
0 notes
Text
Boston Institute of Analytics: The Best IT Education Franchise Opportunities to Invest In
In 2025, as India cements its role as a global technology powerhouse, one sector continues to see explosive growth—IT education and professional training. From AI and Data Science to Cloud Computing and Cybersecurity, the demand for next-gen tech skills is outpacing traditional education. For aspiring entrepreneurs and education investors, IT education franchise opportunities are the gateway to building a profitable and impactful business.
Among the top players leading this revolution is the Boston Institute of Analytics (BIA)—a global leader in future-ready skill development. If you're looking for the best IT education franchise to invest in, BIA offers unmatched credibility, scalability, and profitability.
In this article, we’ll explore why BIA stands out, what makes its franchise model successful, and how you can become part of India’s tech education boom.
Why the IT Education Franchise Market Is Booming?
India’s digital economy is expected to reach $1 trillion by 2030, and with it, a critical need for skilled professionals in AI, Machine Learning, Cybersecurity, and Business Analytics. This makes IT education franchise opportunities one of the most lucrative and future-proof investments available today.
Key Market Drivers:
Massive skill gap in new-age technologies
Corporate upskilling demand driven by AI and automation
Government initiatives like Skill India and Digital India
Higher disposable income among students and professionals for premium training
But succeeding in this space requires more than offering courses. You need a trusted brand, industry-aligned curriculum, and a proven franchise support system.
Meet Boston Institute of Analytics: The Gold Standard in IT Education
🌍 Global Recognition
Boston Institute of Analytics is a globally renowned education company with a strong presence in 30+ cities across India and overseas. It is best known for its advanced career-focused courses in:
Artificial Intelligence
Data Science
Machine Learning
Business Analytics
Digital Marketing
Cybersecurity
Generative AI (ChatGPT, DALL·E, Midjourney)
🎓 Industry-Focused Curriculum
BIA designs its programs in collaboration with top industry professionals and academic experts. Every course is job-ready and tailored to meet real-world business needs.
💼 Strong Placement Network
BIA’s students are placed in top companies like Accenture, IBM, Amazon, and KPMG—strengthening its brand and franchise demand even further.
Why BIA Offers the Best IT Education Franchise Opportunities?
Let’s break down what makes BIA a top choice for entrepreneurs:
1. High Demand, High Ticket Courses
Unlike basic coaching centers, BIA offers premium programs in AI, ML, and Data Science—fields with strong market demand and excellent earning potential.
Course Fees: ₹60,000 to ₹2,00,000
Course Duration: 3 to 6 months
Target Audience: College students, working professionals, upskilling seekers
2. Proven Business Model
The BIA franchise model is designed for success:
Low upfront investment (starting from ₹7–₹10 lakhs)
Break-even point in 12 to 18 months
Franchise support for marketing, operations, and faculty hiring
Ready-to-use curriculum, LMS, branding kits, and certification process
3. Hybrid Training Model
BIA delivers both classroom and online courses, expanding your reach and allowing multiple revenue streams—ideal for today’s hybrid learners.
In-person training at your center
Online classes via BIA's platform
Corporate training programs for enterprises
4. Extensive Franchise Support
Owning a BIA franchise means you’re never alone. Franchisees receive:
Instructor training & onboarding
Marketing strategy, local ad support & creatives
CRM & Learning Management System (LMS) access
Dedicated regional manager support
Leads from national-level promotions
5. Brand Credibility
BIA is recognized by international and national education bodies. Its alumni success stories, media mentions, and growing global presence make it a trusted choice for both learners and investors.
Who Should Invest in a BIA IT Education Franchise?
Whether you're a seasoned entrepreneur, a tech educator, or a first-time investor looking to enter the education industry, BIA is a powerful opportunity.
Ideal for:
Education entrepreneurs seeking scalable models
IT professionals transitioning into business
Franchise investors looking for high-margin businesses
Institutions or coaching centers wanting to upgrade their brand
No prior teaching experience? No problem. BIA equips you with all the tools and training you need.
Top Cities & Regions for Franchise Growth in 2025
BIA is currently expanding into new Tier-1 and Tier-2 cities with strong demand for IT skills:
Bengaluru
Hyderabad
Pune
Chennai
Delhi NCR
Ahmedabad
Kochi
Indore
Lucknow
Chandigarh
If you’re located in or near these tech-savvy markets, you’re perfectly placed to benefit from a BIA franchise.
Final Thoughts: A Future-Proof Business in a Growing Industry
In a rapidly evolving world driven by AI and automation, the only constant is education—especially IT education. By investing in a franchise like Boston Institute of Analytics, you’re not only tapping into a profitable business but also contributing to India's tech future.
With BIA, you get the rare blend of premium content, real-world demand, global reputation, and strong franchise support. It’s no surprise that BIA is rated among the best IT education franchise opportunities in India.
#IT Education Franchise Opportunities#Education Franchise Owner Opportunities#Most Profitable Franchise In India
0 notes
Text
Real-Time Cyber Threat Intelligence: How EDSPL Detects and Neutralizes Breaches Before They Happen

Introduction: Why Real-Time Cyber Threat Intelligence Is No Longer Optional
In today’s hyperconnected world, cybersecurity has shifted from a passive necessity to an active business differentiator. Every second, organizations face a barrage of threats—from phishing emails and malware to ransomware and zero-day exploits. The question is no longer if a business will be targeted, but when. That’s where Real-Time Cyber Threat Intelligence (RTCTI) becomes the ultimate game-changer.
For modern enterprises, simply having network security or firewalls is no longer enough. You need an intelligence-driven, always-on, proactive system that can detect, analyze, and stop threats before they even get close to your data.
At EDSPL, we don’t just respond to cyber threats—we anticipate them. We predict attacks before they unfold, using real-time threat intelligence to shield your enterprise against both known and emerging risks.
What Is Real-Time Cyber Threat Intelligence (RTCTI)?
Real-Time Cyber Threat Intelligence refers to the collection, processing, and analysis of cyber threat data as it happens, enabling immediate threat detection and faster response. RTCTI goes far beyond traditional threat feeds. It uses automation, machine learning, and deep analytics to identify patterns, uncover malicious intent, and neutralize attacks in progress.
The High Stakes: What Happens Without Real-Time Intelligence
Imagine a scenario where a phishing email slips through filters. Within minutes, credentials are stolen, malware is planted, and lateral movement begins within your network. If you're relying on weekly scans or daily logs, by the time you catch it—your data is already gone.
Now contrast that with EDSPL's real-time approach:
A suspicious login pattern is detected in milliseconds. Threat intelligence confirms correlation with known malicious IPs. Automated response isolates the endpoint, cuts off access, and alerts the SOC team. Breach attempt thwarted—before any data is touched.
This is the power of EDSPL’s Real-Time Cyber Threat Intelligence.
How EDSPL Powers RTCTI: A Behind-the-Scenes Look
1. Global Threat Intelligence Feeds
At EDSPL, we integrate real-time threat feeds from:
Industry-leading platforms (FireEye, IBM X-Force, AlienVault, etc.)
Open-source intelligence (OSINT)
Government and ISAC advisories
Proprietary honeypots and decoys deployed worldwide
These sources constantly update our threat intelligence database, ensuring we stay ahead of even the most advanced threat actors.
2. Security Operations Center (SOC) 24x7x365
Our in-house SOC is the nerve center of our RTCTI system. With round-the-clock vigilance, our analysts monitor anomalies, respond to alerts, and hunt threats proactively. Every activity, from system logs to endpoint behavior, is streamed live into our monitoring environment, enabling real-time decision-making.
Explore our full range of services
3. SIEM + SOAR Integration
We use top-tier Security Information and Event Management (SIEM) tools to correlate data across endpoints, cloud security, application security, and on-prem systems.
But we don’t stop there. Our Security Orchestration, Automation, and Response (SOAR) tools automate the playbooks. This ensures:
Faster incident triage
Reduced Mean Time to Detect (MTTD)
Reduced Mean Time to Respond (MTTR)
4. AI-Powered Anomaly Detection
Static rules and signatures aren’t enough. Our AI/ML models learn and adapt continuously, identifying deviations from “normal” behavior. Whether it's an employee logging in from an unusual location or a file being downloaded at an odd time, our system catches the smallest red flags.
5. Endpoint Detection & Response (EDR)
Our RTCTI stack includes next-gen EDR, which monitors every action on your devices in real time. From USB connections to command-line activity, EDR ensures no breach goes unnoticed.
Real-Life Use Case: How EDSPL Prevented a Ransomware Attack
In early 2025, a client’s internal user unknowingly downloaded a malicious attachment disguised as an invoice. The malware silently tried to encrypt files and escalate privileges. Within 4 seconds:
EDSPL's SIEM flagged anomalous activity.
Our SOAR platform triggered an auto-isolation of the device.
The malware was quarantined, and logs were sent for forensic analysis.
No data was lost. No operations were disrupted.
That’s what real-time threat intelligence looks like in action.
RTCTI Is Not Just for Enterprises—SMEs Need It Too
It’s a myth that only large corporations need advanced threat intelligence. In fact, small and mid-sized enterprises are often prime targets—because they have weaker defenses.
At EDSPL, we’ve designed scalable RTCTI packages to suit organizations of all sizes, backed by our expertise in mobility, compute, storage, and backup.
Key Benefits of EDSPL’s Real-Time Threat Intelligence
Proactive Threat Detection
Stop threats before they reach critical systems.
Rapid Incident Response
Our automation ensures no time is wasted during an attack.
Intelligent Insights
Go beyond alerts—understand the context behind every threat.
AI-Driven Accuracy
Eliminate false positives. Focus only on real threats.
Customizable for Your Industry
From finance and healthcare to retail and manufacturing—we tailor defenses to your risk landscape, including switching, routing, and data center switching infrastructure security.
Industries That Trust EDSPL for RTCTI
We serve organizations across sectors, including:
BFSI (Banking, Financial Services, Insurance)
Healthcare
E-commerce
EdTech
Manufacturing
Government and Public Sector
How EDSPL Stays Ahead of Cyber Criminals
Cyber criminals evolve every day—but so do we. Here’s how EDSPL maintains a competitive edge:StrategyHow It HelpsThreat Hunting TeamsActively search for hidden threats before they strike.Red Team SimulationsSimulate real attacks to test & improve defenses.Zero-Day Threat MitigationHeuristic detection + rapid signature updates.Dark Web MonitoringTrack stolen credentials and brand mentions.Incident Drill PlaybooksBe ready with tested, automated response plans.
Why EDSPL Is the Right RTCTI Partner for You
Choosing a cyber partner is about trust. With EDSPL, you get:
✅ Experienced Cybersecurity Professionals ✅ Real-Time Visibility Across All Layers ✅ Custom Playbooks and Reporting Dashboards ✅ Compliance-Ready Solutions ✅ Managed and maintenance services that ensure long-term protection
Conclusion: Stop Attacks Before They Even Begin
The threats are getting smarter, faster, and more dangerous. If you’re waiting to react to a breach, you’re already too late.
With Real-Time Cyber Threat Intelligence from EDSPL, you gain an unfair advantage. You move from being a passive target to a proactive defender.
Don’t wait for the breach—predict it, detect it, and neutralize it with EDSPL.
Want to Get Started?
Reach Us or Get In Touch to future-proof your cybersecurity infrastructure. Understand our background vision and commitment to enterprise security excellence.
Ready to secure your business? Contact our experts today and get a free consultation tailored to your organization’s needs.
📧 Email: [email protected] 🌐 Website: www.edspl.net
Follow us on social media for the latest updates and insights:
🔗 Facebook | LinkedIn
0 notes
Text
North America Digital Twin Market Size, Share | CAGR 40.3% during 2023-2030
The North America Digital Twin Market industry in North America ranks second globally and is projected to expand at a CAGR of 40.3% over the forecast period. Globally, the industry is set to surge from USD 8.60 billion in 2022 to USD 137.67 billion by 2030. North America ranks as the second largest region in the global digital twin market, propelled by high industrial automation, strong investment in IoT infrastructure, and early adoption of AI and advanced simulation technologies.
Key Market Highlights:
• 2022 Global Market Size: USD 8.60 billion
• 2030 Global Market Size: USD 137.67 billion
• North America CAGR (2023–2030): 40.3%
• Market Outlook: Innovation-driven growth, supported by smart manufacturing and predictive maintenance initiatives.
Market Analysis:
North America is expected to maintain its strong position in the global digital twin market due to early technology adoption, cross-industry applications, and robust digital ecosystems. The market is especially promising in sectors such as automotive, energy, aerospace, and healthcare.
Request Free Sample PDF: https://www.fortunebusinessinsights.com/enquiry/request-sample-pdf/north-america-digital-twin-market-107453
Key Market Players in North America:
Microsoft Corporation
IBM Corporation
General Electric (GE Digital)
PTC Inc.
ANSYS, Inc.
Oracle Corporation
Dassault Systèmes (North America)
Siemens USA
Altair Engineering
Rockwell Automation
Twinswift
Twin Health, Inc.
Market Drivers:
The North America digital twin market is experiencing robust growth, driven by the region's strong foundation in advanced technologies such as IoT, AI, cloud computing, and edge analytics. A key driver is the rising adoption of digital twins in manufacturing, automotive, and aerospace sectors, where virtual models are improving operational efficiency, predictive maintenance, and product innovation.
Market Opportunities:
The North America digital twin market is changing with a growing number of opportunities for sector-specific applications, especially in healthcare, energy, and logistics. In healthcare, digital twins are being explored to model patient conditions and personalize treatment pathways. In the energy sector, they are enabling more efficient grid management and renewable energy integration. Startups and technology providers have the opportunity to create modular, scalable digital twin platforms tailored for small and mid-sized enterprises (SMEs) seeking cost-effective entry points.
Market Trends in North America:
• Surging use of digital twins in electric vehicle (EV) development
• Emergence of AI-powered twins for autonomous system simulation
• Advancements in interoperability with IoT, BIM, and ERP systems
• Focus on sustainability through simulation of energy-efficient systems.
Speak to Analyst: https://www.fortunebusinessinsights.com/enquiry/speak-to-analyst/north-america-digital-twin-market-107453
Technology Scope:
• Core Components: 3D modeling, real-time simulation, sensor integration, data visualization
• Deployment Modes: On-premises, cloud-based, and hybrid
• End Users: Manufacturing, aerospace & defense, automotive, healthcare, energy, and smart infrastructure
• Applications: Predictive maintenance, product lifecycle management, supply chain optimization, and diagnostics
Recent Developments:
November 2023 – A leading U.S. aerospace company launched a digital twin ecosystem for its next-generation aircraft engines, reducing development costs by 25%.
June 2023 – A Canadian smart infrastructure firm partnered with a U.S. tech startup to integrate real-time data streams into municipal digital twins for energy optimization.
#North America Digital Twin Market Share#North America Digital Twin Market Size#North America Digital Twin Market Industry#North America Digital Twin Market Analysis#North America Digital Twin Market Driver#North America Digital Twin Market Research#North America Digital Twin Market Growth
0 notes