#IP Address Assignment
Explore tagged Tumblr posts
Text
Absolute Secure Access and IPv6
Absolute Secure Access (formerly NetMotion Mobility) is a premium enterprise secure remote access solution with deep user and application insight supporting Windows, Mac, iOS (iPhone and iPad), and Android devices. Although Absolute Secure Access supports IPv6 for remote network connections and client IP address assignment, the latter is not enabled by default. Administrators must make additional…

View On WordPress
#Absolute#Absolute Secure Access#DHCPv6#enterprise mobility#IP#IP address#IP Address Assignment#IPv6#IPv6 prefix#Mobility#NetMotion#NetMotion Mobility#Remote Access#security#SLAAC#split tunnel#split tunneling#VPN#Zero Trust#Zero Trust Network Access#ZTNA
0 notes
Text
imagining ur comfort character with you doesnt have to be emotional or serious sometimes youre dragging a warhammer character into studying for a computer science exam
#ramblings#WHYD I REALISE I CAN JUST TALK TO THE LITTLE GUYS IN MY HEAD ABOUT THIS#THE DAY OF THE EXAM#MY TEACHER SAYS 'oh just practice in front of a mirror' BUT I HATE THAT BECAUSE ITS EMBARRASSIGN#I TALK TO MY GUYS ALL THE TIMEEEEE#me: okay so dhcp is a protocol that automatically assigns ip addresses to devices that enter its network so you dont have to do it manually#the warhammer blorbos (visibly shaking): WHAT ARE YOU TALKING ABOUTTTT#me: and computers are kind of stupid (dont tell the admech) and communicate differently from us#they work with ips while we prefer domain names so we have dns to make sure we connect to the right ip addresses when we use domain names#them: WHAT. WHAT#i love my little dystopian fantasy fantasy guys masquerading as scifi imagining them learning about networking is incredible
3 notes
·
View notes
Text
.
#yes hello. hi.#WHAT DO YOU MEAN ANOTHER DEVICE IS USINGY DEVICE’S IP ADDRESS?? Is that why my laptop won’t connect to the frikken wi-fi???#What the FUCK is happening#what do you mean I need to change my ip address THE NETWORK IS SUPPOSED TO ASSIGN THOSE#WHY ISN’T IT ASSIGNING ME ONE#if I have to *manually* find an IP address that’s not in use on this stupid network I am going to SCREAM
0 notes
Text
does anyone here know how to change your default zoom name. i changed my name in my account profile to my new name. i made a new account whose name has only ever been my new name. i went into my laptop settings and changed my user profile to my new name. and still, every time i meet w/ my therapist or voice coach the meeting uses my old name
1 note
·
View note
Text
Veeam backup for aws Processing postgres rds failed: No valid combination of the network settings was found for the worker configuration
In this article, we shall discuss various errors you can encounter when implementing “Veeam Backup for AWS to protect RDS, EC2 and VPC“. Specifically, the following error “veeam backup for aws Processing postgres rds failed: No valid combination of the network settings was found for the worker configuration” will be discussed. A configuration is a group of network settings that Veeam Backup for…

View On WordPress
#AWS#AWS SSM Service#AWS System State Manager#Backup#Backup and Recovery#Create Production Worker Node#EC2#Enable Auto Assign Public IP Address on AWS#rds#The Worker Node for region is not set#VBAWS#VBAWS Session Status#Veeam Backup for AWS#Veeam backup for AWS Errors
0 notes
Text
Happy (maybe belated or early)birthday DHCP
you've been making everything on the networking side significantly less difficult for what's probably been a *rough* 26 years.
#seriously#before this you had to manually assign ip addresses.#and subnet masks#and like everything#so even thought you're a protocol#thanks for being a good one
1 note
·
View note
Text
lan wangji, upon learning that students in his class are cheating on their assignments with ChatGPT, engineers a way of phrasing his homework questions such that they cannot be answered by ChatGPT. this does not prevent people from rephrasing the questions and then asking ChatGPT anyways, but it at least catches the students who just copy/paste everything into ChatGPT.
wei wuxian, upon learning that students in his class are cheating on their assignments with ChatGPT, builds a fake ChatGPT-imitation site that logs the IP address of anyone who accesses it, and then bribes some of the reliable students in his class to spread the link among the rest of the student population. while he does not report anyone to the school's disciplinary body for cheating, he does succeed in scaring several students rather badly.
nie huaisang, upon learning that students in his class are cheating on their assignments with ChatGPT, offers 15% extra credit to any student who turns in another student for using ChatGPT. then he sits back and watches the chaos unfold.
479 notes
·
View notes
Text
Prompt Voting is now Open!
Thank you to everyone who submitted their prompt ideas for Jercy Week 2025! Now it's time to vote for your favourites out of everyones suggestions
How to vote:
Voting is held on Strawpoll & here's the link: vote here
Select your favourite seven prompts from the multiple choice options as if you were creating your own ideal Jercy Week Prompt List
You have to select seven prompts. This is to ensure I collect enough votes
Strawpoll is completely anonymous but you are limited to one vote per IP address
Deadline to submit your vote is the 7th March
What happens next?
The seven prompts with the most votes will go forward and I will assign them each to a date during Jercy Week
Plus the three runner-up prompts will make up an Extra Prompts list that you can pick from instead of one of the main seven or combine with a main prompt
Once everything is collected and sorted, I'll make an announcement post containing the prompts + rules & information on how to submit your works
Disclaimer: if you don't see your specific prompt it may be because I felt it fit under another prompt, I worded it slightly differently or that it wasn't suitable for this event (most likely due to it being too specific). Feel free to send in an ask or DM if you need further clarification
New to Jercy Events? Check out the pinned post for more details
#pjo#pjo hoo toa#percy jackson and the olympians#heroes of olympus#percy jackson#jason grace#jercy#jason x percy#percy x jason#pjo event#jercy event#jercy week 2025
25 notes
·
View notes
Text
Hi! We'd quickly like to address some rumors that have been spreading about IPS-H!
Rumor 1: IPS-H is staffed by pirates.
While it is true that IPS-H employs a number of former pirates, no active pirates work for IPS-H. IPS-H offers a work rehabilitation program for pirates captured by or who surrender to IPS-N. The recidivism rate for participants in this program is extremely low compared to other options.
Rumor 2: IPS-H is run by underperforming managers.
Entirely untrue, though understandable where the rumor comes from. Some managers thrive under the work conditions that IPS-H offers, and IPS-N makes an effort to make sure that such managers end up here so that their talents may be fully utilized and their potential fully realized.
Rumor 3: IPS-N banishes anyone who talks about unionizing to the Heron System.
Also untrue! This would be decidedly against several laws. Other than the aforementioned work rehabilitation program and efforts to assign managers who would work well in the Heron system here, assignment to IPS-H is completely random. Any observed trends with worker reassignment are completely coincidental. Remember, correlation does not imply causation!
36 notes
·
View notes
Text
multiple someone's need to see this, so here y'all go. The tone of this post / reply is completely neutral, please do not assign emotions or read that deeply into it.
the rules page https://fictionkinfessions.tumblr.com/rules
Rules for confessions and ask responses to confessions
In general…
Don’t attack or invalidate other people [ie fakeclaim of kintype duplicated, the ableism of calling systems or system members false]. Do not send responding confessions which invalidate or negatively vague post about other people’s confessions.
Source calls. This is not a call blog. Here is a list of call blogs. [blog page] [blog post] Don’t sign confessions with blogurls or @/mentions. Don’t leave social media links to oneself, such as discord IDs, twitter user names, etc. Don’t ask people to reblog, comment, like, or interact with ask messages in order to make contact with others. These messages will be deleted. Suicide notes. I will block your ip address. Please do not. Hate speech Such as racial, lgbtphobic, classist, or ableist slurs, pejoratives, derogatory language, suicide / rape baiting, and death threats towards specific named people. You cannot reclaim slurs on this blog. It breaks the website’s own TOS and will get it permabanned. Special Text Formatting Please don’t use font colors, tumblr’s optional ‘quote’, ‘chat’, or ‘Lucille’ fonts, tumblr’s Header font style, or excessive bolding or italics, or generated text such as zalgo text or ‘fancy styled fonts’. Confessions in colored font, the above tumblr fonts, or excessive bolding or italics will be posted as unformatted text posts. Some colored text is alright, but full paragraphs will be posted as unformatted text posts. Confessions in generated text will not be posted. [EG Zalgo text] Confessions in typing quirks, such as homestuck typing quirks, are permitted. Please do not make the name(s) and source signatures text extra small, bolded, italicized, or colored. I cannot read small fonts very well. No Delusional Attachments or IRLs in the non alterhuman context People with psychosis and/or delusions are very much welcome here. But DAs aren’t kintypes or system members, and conflating them would be harmful. “Kin is seperate from delusional attachments as being kin is not inherently caused by Psychosis, although some Psychotics do refer to their Identity Delusions as being Kin. Having a delusional attachment doesn’t make one more ‘real’ than one who is Kin.” “Introjects are separate from Delusional Attachments as Introjects are members of plural systems, while Delusional Attachments are caused by psychosis.” Above text from a previous version of this defunct carrd. das.crd.co Please refer to this post for a more information of DAs. https://fictionkinfessionsarchived.tumblr.com/post/708803715909517313/this-carrd-has-some-elements-of-reality-checking Link Content warning. Contains reality checking, racism, ableism, stalking / harassment. Image heavy, mobile users proceed with caution. Call outs, warning posts, or documentation on social media users. We will not manage call outs as a third party. Make your own blog / post about it. Explicit nsfw content This blog is for all ages. Please limit oneself to superficial discussion. Syscourse This blog is not for discourse and we are not here to moderate for you. Factive / Factkin confessions. This is a blog for fictional sources only. Vague post confessions about terminated relationship / friendships Please do not air ‘dirty laundry’ or vague post regarding recent or past break ups / friendships / dissolution of acquaintance(s) that happened in this life.
This is not the appropriate place to…
make others of the former friend group / relationship defend their reasoning or actions regarding the end of the relationship(s). discussion intimate details of the relationship(s).
leave backhanded ‘dear john’ letters because you got blocked first.
continue to stalk, harass, guilt trip, or emotionally abuse / manipulate former acquaintance(s).
anything else I might have missed.
Ask Response Rules For ask responses specifically, feel free to come off anon in ask messages to ask anons to contact you. You are also welcome to reply to, or reblog the post asking for contact.
Ask Responses do not receive source, name or fictotype / fictive tags [eg marvelkin, mollyfictive, fictionkin, fictive, soulbond, etc] unless specifically requested for all encompassing blacklisting purposes.
Please include in Ask Responses the ‘@’ symbol, a post link, or any indication that you are respondng to a confession so we know it’s an Ask Response and can tag / post it asap. Otherwise they will be posted as confessions.
Rewritten 2024. Consolidated Ask Response Rules into this page.
The tone of this post / reply is completely neutral, please do not assign emotions or read that deeply into it.
23 notes
·
View notes
Text
Always On VPN Static IP Address Assignment
A question that occasionally arises when I’m conducting an Always On VPN planning and design workshop for a customer is static IP address assignment options for VPN connections. Typically, the use case is a specific user that requires special access to a sensitive system internally. Assigning a static IP address to the user allows administrators to create firewall rules restricting access to this…

View On WordPress
#Active Directory#AD#Always On VPN#AOVPN#firewall#IP#IP address#IP Address Assignment#multisite#NPS#security#VPN
0 notes
Text
very brief torrent security primer
some brief comments on piracy safety for @goblin-thembo who has been asking a lot of questions in the notes of that post...
OK, so when you download a torrent, you are downloading some files. The BitTorrent protocol makes it almost impossible to substitute a different file than the one you request, but you have no way to be absolutely certain that the original file is 'safe' - that depends on the properties of the file, and what you do with it. Some types of file are safer than others.
Here's some jargon you may find useful.
torrent: a file that describes how to download some files through the BitTorrent protocol. we won't go into the technicalities, but when you load a torrent into your torrent client, you will connect to other people who have parts of the files, download the pieces, and reassemble the files you want.
seeding: providing a copy of the files in a torrent to other people.
ISP: Internet Service Provider, the company that connects you to the internet.
IP address: your computer's identity on a network, notably the public internet. When you connect to a website, they know your IP address. Your IP address is assigned by your ISP.
From an IP address, you can determine someone's broad geographical location (which country they're connected in) and which ISP they are using. You can contact the ISP, who will be able to associate it with a specific user.
swarm: the collection of users downloading or seeding a particular torrent.
VPN: Virtual Private Network, a relay service which hides your IP address from the public internet. People who connect to you will see the VPN's IP instead of your real IP. Your ISP will be able to know that you connected to a VPN, but not what you send through it. So they wouldn't be able to tell if you are using BitTorrent. VPNs usually cost a fairly small amount of money as a subscription service.
Threat model
In security we talk about a 'threat model', which is what you think you need to protect yourself from. There are two major threats when downloading files using BitTorrent.
copyright claims: your computer's IP is broadcast when you use BitTorrent. Copyright holders will often put 'sniffers' on the network which will monitor the IPs in the swarm of popular torrents. They will then send a takedown letter to your internet service provider (ISP), who will usually send you an email to stop sharing copyrighted media on their network, and then cut off your internet on multiple offences. This can easily be circumvented using a VPN. I strongly recommend using a VPN if you download any copyrighted content through BitTorrent.
attacks through the file you download: someone might upload a virus as a torrent, presenting it as a file you might be looking for (e.g. cracked software). So let's go over different types of file you might download and how they could be used to attack you.
Executable files, such as pirated software, are not safe. If you download a program and run it, you are potentially giving the author full control over your computer. So you should make damn sure the uploader is trustworthy. If you're downloading open source software from the maintainer's github release page, you're probably good. If you're downloading cracked art programs or games... good luck lol.
On a public torrent tracker, to which anyone can upload, there is no guarantee that any file is what anyone says. You have to make your own determination of which uploaders are trustworthy. I can't give you great advice on this, since I generally do not download cracked executables. For games, FitGirl Repacks is generally a pretty good source.
If you are on Windows, the default Windows Defender software should be used to scan any file you download. (Paid antivirus software is of somewhat dubious utility, often pushing ads and using CPU resources in its own right.) Fewer attackers will target desktop Linux or OSX, which doesn't mean you're guaranteed safe, but Windows is the biggest target as the most widely used operating system.
Videos, music and images are generally safe. I say 'generally' because it's possible, in theory, to create a video that exploits a vulnerability in your video player (e.g. mpv or VLC) and uses it to execute code. So far as I know this is largely theoretical, and known vulns have been patched, but make sure to keep your player up to date to mitigate against known vulnerabilities.
Any compressed archives (zip, rar, 7zip) can be used to create something called a 'zip bomb', which is a file which goes into an infinite loop when you try to decompress it, swallowing up more and more memory and hard drive space. I've never seen this actually be done, but it's possible. More subtle attacks would attempt to attack the program you use to decompress the file. Keep your software up to date to mitigate against known vulnerabilities.
Besides taking care about what you download, on Windows you should either not run your main account as an admin account, or make sure to set User Account Control to require a credentials check for admin operations, and also keep your operating system and software up to date. Make sure file extensions are visible so you don't get fooled by a file disguised as a different file type. And y'know, if the torrent tracker has comments, check to see if a lot of people are saying it's a virus.
What could happen if your computer gets infected? Well, they might use your computer to mine crypto at the cost of your CPU performance, they might encrypt and ransom your files, and they might steal your credentials for online services (including banking and the like). There are various measures you can take against this, such as making sure to encrypt sensitive data such as passwords, but the best defense is to not infect your computer in the first place.
The most likely time for people to upload viruses is when something is in high demand and there isn't a single authoritative high-quality source out yet.
Ultimately you get to decide what you consider an acceptable level of risk. There is no such thing as perfect safety. I would recommend using your own initiative to learn about computer security and not badger random tumblr users to explain it to you, but hopefully the above guidelines should help you avoid doing anything too dangerous.
189 notes
·
View notes
Text


found this and couldn't reblog so I'm reposting

image id:
first image: two-part meme of joey from friends. first part is a picture of him smiling at something out of frame, captioned "The hotel's free WiFi is really fast". second part is him staring wide eyed in horror, captioned "Your IP address starts with 172.16.42.x".
second image: lain from the anime "serial experiments lain" sitting in a chair in a dim room, in front of a glowing computer screen, and smiling at the camera. the text boxes in the image say:
Hey, guys. Lain Iwakura here to explain the joke.
You see, when a computer like your laptop or smartphone connects to wifi, the router assigns it a "local IP address" to distinguish it from other machines on the network.
Most routers use IPv4 for this, where an IP address is four numbers separated by periods. The first two or three numbers of your local IP address are usually the same for all machines on the LAN, and the most common schemas for local IP addresses are 192.168.0.x or 10.0.0.x. Those are just common defaults - they can be set to anything in the router's configuration.
The address schema 172.16.42.x is not a common default for a normal router. It is the default for a device called a "WiFi Pineapple", which is a hacking tool primarily intended for "pentesting", i.e. finding exploitable vulnerabilities in a computing or networking system. The WiFi Pineapple acts as a router from the perspective of the computers on the local network, but a malicious actor can use it to passively scan those computers for vulnerabilities, and can even spy on network traffic going through it. Thus, the joke is that the person in the hotel, finding that their local IP address is under 172.16.42.x., realizes to their horror that the hotel's LAN has been pwned by a (likely malicious) rogue access point, possibly causing their computer to be cracked and their sensitive information to be stolen by cybercriminals. In light of this breach, their panic is understandable! Always keep your software up to date and never connect to a suspicious or unsecured wifi network!
/end id
61 notes
·
View notes
Text
diy router update
basically the same as last time. ive been at it for days and just cant figure it out. it's making a hotspot and i can attempt to connect but it never assigns an ip address. if i manually configure the ip address it will connect but nothing is accessible. it is serving up ip address and routing computers to the internet just fine over the ethernet connection tho so there's that.
11 notes
·
View notes
Text
MARSTON. ━︎━︎ ZSAKUVA STRICT PROFESSOR !
chapter two - ❝chewing gum.❞

← previous chapter: chapter one - "four eyes." next chapter: chapter three - "boo!" →
fanfic info / read it on wattpad
SYNOPSIS / Andrew finds out the person behind the review. A student pays a visit during office hours.
TAGS - mentions of Andrew's backstory with the teacher.
──────── ✧ ────────
"I'VE ALWAYS valued the sentiment behind poetry. But now when I look down and read the poems I wrote during my youth, I can't bare to look. Only a seven-year-old writes, 'roses are red, violets are blue', and students who couldn't care less about poetry use that line over and over just to get the assignment over with. Students in the classes I were in used that as a prompt, and last year a student used that but just switched up the words. Violets cannot be red.
But this topic is for another time. I won't be teaching poetry until next semester. Right now, the first topic before I could even jump into The Odyssey or The Iliad is the history behind literature, and because literature existed during the beginning of civilization: we go way back." I press the forward arrow key to go to the next slide. "History plays a huge role in literature, and without history, no literature. Without literature, no history. Without either, I am unemployed."
Another round of giggles erupts.
"We will cover history, and if you're in a program such as English and Liberal studies, you would very likely have that required course in your schedule."
Speaking of schedules, the Dean requested to see me before my office hours. I have opened them for week 1, despite it only being syllabus. But because I jump right into the topics, students would want to come during the hours and ask me pretty much anything.
As I entered the Dean's office, I let out a breathy sigh. "Any luck?"
She nodded her head. I rush over to her desk.
"I want to stress this to you, Andrew. Once we track down this person, they will be under investigation. Think about all the paperwork that comes with it. The poor kid is probably-"
"Childish? Very much so." I fold my arms. "I would never do anything to jeopardize my relationship with my students."
"Even though you claim to be innocent, you will still be under investigation. They require proof." The Dean opened her email, then split the tabs so we could see both the report she filed as well as a document shared on Google Drive.
I begin tapping my foot, agitated. "Is there a new review posted?"
Dean stares. "Andrew."
"Right."
"The more paranoid you get, the more you will keep feasting on the negativity. That's unhealthy."
"Yes, but having the nerve to come up with a fake allegation is just as unhealthy and quite bloody dangerous to my job. I am hiring a lawyer if this doesn't resolve by the time it snows."
The Dean opened the new tab. "Here."
"Read it to me, please."
"They said they carefully reviewed the page where it was posted, and they were able to track down the IP address. Their offense violated the policies and guidelines, and the review has since been removed after you have contacted the site's personnel and reporting the rating as additional efforts for faster evaluation." The Dean smiled at me. "Now it's up to you to take more legal action."
"A name?" I ask, almost ready to bite my nails.
The Dean scrolled down the report. "They will report a name later on."
"I'm trying very hard here to not pace around like a student."
"Once I get the name, I'll forward it to you right away. That's all, please go pace around in your office."
──────── ✧ ────────
MY PARENTS took legal action when they found out about what my teacher did back at my old school. I try to erase that awful memory from my head as much as I can, but it trails behind me like footprints whenever I think of what has gotten me stressed right at the beginning of the new school year. It was enough that my peers looked at me like I had six heads on my body because I was much more gifted that it made me move up a grade.
I had to deal with stares and whispers every time I walked past people. Not just back then, but even now. How ironic is it to have students stare and talk about me over such a sensitive situation as a child, to gush about how "attractive" I look for a professor. I shouldn't let that deceive them for the type of teacher I am, I value myself more than my looks.
The quirky Maths professor looks at me as I turn to corridor to my office on the second floor. His office is all the way on the other side, crammed with students who struggle the most with simplifying fractions or dilutions (the majority of his students are in the health sciences field). So thankfully, he never bothers me.
I picked up my pace. I should be at least a minute late, which I will learn to actually be present inside for office hours at the dot next time. They're always in the afternoon, and students should be at alert. But then again, this is week 1. I shouldn't expect too many students already coming in to-
My eyes fixated on the student standing by my door. The only student who showed up.
It was them.
They turned around when they realized I was standing behind them. I fumble for my office keys and unlocked the door. "Come in."
My computer was still on when I left for the Dean. The tab that was open were the slides for English Composition 201. I hid the tab.
They sat down at the chair across the desk.
"How can I help you?" I ask.
The student shrugs. "Just wanted to say hi, was checking to see if you remember me."
My face lit up, as did theirs. "Of course I remember you," I pull back the rolling chair and sat down, unbuttoning my suit. "You were in my literature class last year. It's nice to see a familiar face. You're Y/N, if I'm correct."
They nod. "Yeah."
"You did so well in my class. Every submission never ceased to amaze me. I actually saw you attending my Literature 101... that's the class you were in, and passed. I was confused on why you were there."
"I came to campus super early. Thought I could kill some time."
Y/N was always careful with time. Always handed things on time, always arrived to my lectures on time, always attended office hours or private tutorials when needed. A very gifted student sits before me, it felt like seeing myself through another point of view, in awe of me. As I remembered what they said to me during one of our private tutorials, "You're one hell of an ace professor. Or whatever." It was no wonder people stared.
"Well, welcome back!" I smile at them. "I hope you do well this year, as you did the last. I must say, your critical analysis on The Odyssey was something I re-read a couple times. It was beautifully crafted."
They wave their hand. "Oh. I remember stressing over that assignment."
"And you managed to pull through. Working under pressure is a strength, it seems."
I could hear Y/N chewing their gum like they were a greaser. I could have some tendency of being a misophonic, but I just hate the sounds of gum chewing. Gum chewing, gum popping, food smacking, fidgeting, tapping, it makes me want to tear my hair out of my scalp in a fit of rage. I had to learn to tolerate keyboard clicks once as a student and now a professor, and heavy breathing whenever I took the tube back in England.
It was kind of rude to do that in front of me, not etiquette if you were to go professional in the workplace... but I just ate a snack.
I held out my hand. "You got any gum?"
A notification popped up on my laptop. "Just a moment, please." I skim through the little bar. It was the forwarded email from the Dean. I inhaled sharply and clicked it open.
Zylos, James.
I stared at the name for a moment as my eyes began to widen.
"Uh-" Y/N looks at me weirdly. "Am I taking too much of your time?"
"N-no!" I shook my head. "I mean, I'm all right."
"Are you sure? You turned so pale just now."
I glanced at the detailed email, which was a scanned copy of the report in Courier text. "I just thought I clicked something that could have been a potential computer virus."
There was indeed a virus in the form of a student of mine. A former student, who plagiarized an assignment I had given last year. The Dean had to inform me that James Zylos intentionally stole someone else's work and passed it off as his own. I was able to catch it right away. It was painfully obvious. The tone of the writing was definitely not written by him, and I made sure he understood why I was angry, and why the university had a valid reason to withdraw him.
I may have expected some kind of outcome, though it was his choice to cheat, but I did not expect this. Especially from that kid.
Y/N nods slowly, popping the gum in their mouth. "You still want that gum?"
"Oh, yes. Yes, of course. Thank you." I held my hand out and Y/N handed over the aluminum wrapper from the pack. Goodness...
"Professor," Y/N sat back in their seat. "I can come back another time. You seem to be in some kind of distress."
"It's nothing to worry about, truly. My brain likes to display illusions."
"Like Macbeth?"
"Like Macbeth." I cleared my throat. "You're right. I should get back to this," I gestured to the laptop. "I don't expect a lot of students to actually show up for office hours in week 1, it's quite silly on my behalf. But you're more than welcome to stop by when I'm available. In the meantime, I'll see you in tomorrow's class."
Y/N got up, slinging the strap of their bag over their shoulder. "Right. Take it easy, prof."
I nodded and they went on their way. The door closed, and I looked at the email once more... and fell into an abyss of dread.
──────── ✧ ────────
#zsakuva#zsakuva andrew#professor andrew marston#andrew marston x darling#sakuverse#strict professor#strict professor series#andrew marston fanfiction#fanfic
7 notes
·
View notes
Text
Case study and analysis of the 1992 Good Omens movie screenplay (“the shitscript”) in light of the ongoing WGA strike
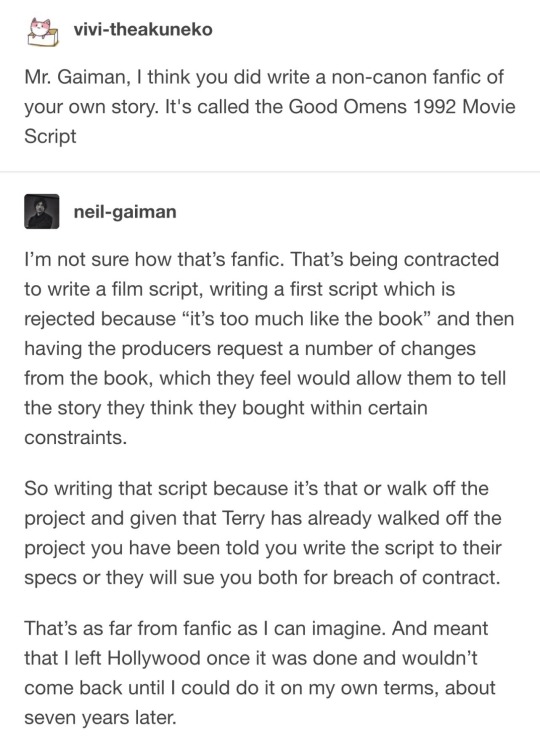
As one could suspect, the topic of the 1992 Good Omens movie screenplay and its infamy has recently emerged from the depths of the fandom. In light of the ongoing WGA strike it’d be good to properly address this issue, starting with Neil Gaiman’s own recollection written in 2004:


It’s basically the same old story — of brilliant creative workers struggling under the pressure of detached studio executives and being legally forced to mutilate their work again and again for no artistic or economic reason — we’ve heard before in many different contexts.
If you’re reading this and somehow still wondering why writers are fighting for their rights at the moment, their job security hasn’t changed much since then. Please follow the WGA, SAG-AFTRA, and other unions’ official channels for detailed information and ways to help the cause.

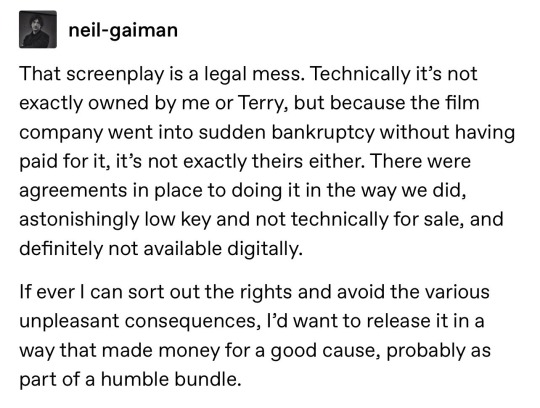
Anyway, it took over a decade and an enormous effort to print the screenplay in a limited edition of 552 copies. It can’t be distributed otherwise due to IP law, but some fans shared its fragments online and heavily criticized them, dubbing the 1992 source material #shitscript
There’s been obviously a lot of controversies over the changes in the plot and the relationship between the main characters. And rightfully so — the number of iterations has created something very different from the beloved book and the award-winning show we can all enjoy today.
It’s… objectively not good. Wouldn’t be considered a hit back then and certainly not by today’s standards. I don’t think I would watch it in any other way than through channel surfing. However, it’s not a monstrosity some people believe it to be and not a case of low effort.
Let’s start with the world building: the setting wasn’t changed to the US. It’s still very much based in the UK, mostly London and Tadfield, although the latter lies now by the sea and seems much more ominous. Interestingly, the British Museum becomes a prominent location as well.
The main character and the designated hero is not surprisingly Crowley, this time in his 90s anti-hero glory. If you haven’t watched many movies of this era, esp. dark fantasy, this trope involves middle-age disenchantment, cynicism, as well as hefty doses of sarcasm and brooding.
90s anti-heroes are a dark, grim, and unnecessarily violent embodiment of power fantasy, matching the destructive ideology of that time. Combined with uber-masculinity and performative strength over weaker characters, nowadays they naturally evoke more cringe or worry than awe.
1992 iteration of Crowley is basically in his Furfur era. Deeply unhappy and stuck in a dead end job, all he talks about is how he hates Earth and his assignment here, considering a transfer to Alpha Centauri as his one and only possibility of career advancement. Or life, really.
The talking part is important here, because he clearly compensates by insulting everything and everyone. He hates on the whole planet at length only to confess that he’d rather stay here with Aziraphale due to “no good restaurants”, “no decent bottle of wine” in Alpha Centauri.
Yes, he’s verbally abusive in his automatic response to stress. But doesn’t hate Aziraphale. In one particular scene he calls Azi stupid twice only to assure him that they are friends and to offer to solve the problem when he sees that his words were taken seriously and hurt him.
Crowley refers to him as “my angel” and “my dear Aziraphale”, agrees to Aziraphale’s suggestion of sharing a room, praises the angel as a “miracle worker around the home”, drinks the tea he makes for him, and generally proves to be much softer towards him than he wants to admit.
Aziraphale, on the contrary, wears his heart on his sleeve. He’s the one engineering ways to spend more time together, following Crowley around, checking up on him (including miracling himself into his apartment and office when no one answers the door), offering help right away.
He’s successfully calming Crowley down through his anxiety attacks, overcomes his dislike of heights (!) for Crowley, directly challenges him and even breaks rules only to make Crowley stay with him. Crowley seems to be his main motivation in this movie, not the saving the world.
1992 Aziraphale also has the most badass scene in the whole Good Omens multiverse to date, taking a 180 degree turn from the typical guardian angel we all know and love to the real angel of wrath protecting Crowley from harm in his true form.
But there’s no Their Side in this universe. The only semblance of that concept appears in the context of Anathema not representing either of their respective bosses, but humanity. “That’s the trouble with the humans. They’re on their own side.”
This Crowley appears not as much on Hell’s side as under Satan’s heel. He’s scared of him and subservient, and needs Aziraphale to prevent his escape as a pretext to do what is right. He lets the angel stop him by pretending that he doesn’t even see him cheating during their duel.
By finally standing up to his toxic boss (Satan is like Gabriel during the body-swapped trial, suave and cruel) and leaving Hell’s side to do good, Crowley takes an emancipated and employee-focused stance instead of fighting for his relationship with Aziraphale like shown in S1.
Which is a shame, but matches the overall tone of the screenplay and the times it was written in. The concept of free will, while simplified in a true Hollywood-style to issues like mind control and fear, is still crucial to this interpretation of the Good Omens original plot.
Especially the character of Anathema is seen fighting both of these things. There’s no Agnes Nutter with her prophecies here, only a 21-year-old witch and her will to thwart the ultimate evil versus her fear of doing it at a cost of one boy’s life, versus Satan’s brainwashing.
Madame Tracy appears slightly redesigned as a new character as well, but isn’t 𝘲𝘶𝘪𝘵𝘦 𝘵𝘩𝘦𝘳𝘦 for the most part. She’s been enjoying her youth way too much to see how fast it was fleeting, and this sudden realization left her in shock from which she denies to come back.
Unfortunately she’s also the one who took in baby Adam and now stays under his care. The level of his parentification is unnerving, much like his bullying and loneliness. He struggles to be loved and ask for love, which becomes his main quest beyond, y’know, the apocalypse thing.
Don’t worry, despite everything all ends well just like in the book. The family of two gets a chance to start again on much healthier terms and Anathema to live for herself for the first time in years. Our heroes get back in their car, Crowley tempting Aziraphale with an apple.
All in all, this whole post is a very long reminder for Amazon Prime to #PayYourWriters, #PayYourActors, and #RenewGoodOmens! The strike is still ongoing and crucial for any new content for this and many other fandoms #GiveMeS3orGiveMeDeath

102 notes
·
View notes