#NETWORK SECURITY
Explore tagged Tumblr posts
Text
Person of Interest (2011-2016)
#person of interest#cyberpunk aesthetic#hacking#graphic design#surveillance#science fiction#surveillence state#hackers#cybersecurity#scifi#mobile hacker#code breaker#data manipulation#network security#infosecurity#10s#command line
81 notes
·
View notes
Text
Ha már ISMS auditor lennék
Az ember eljön egy viszonylag méretes szállodaláncba és naívan rákérdez, hogy mi is a Wifi? Flegma recepciós odavágja, hogy csak a közös területen van Wifi. Ha a szobába is akarok a akkor, leszek szíves 7 fontot leszúrni a kasszánál és 24 órára kapok valamit.
Aha, hát kösz nem. Nézzük a Wifi-t a biztonságos gépről, amin nincs olyan adat amiben kárt tenne valami fosadék net. Már ott elbukik, hogy a security rendszer óbégat, hogy nem biztonságos, nyilván wiresharkkal látnám az összes forgalmat. Mutatom bárisnyának a recepciónál, hogy látod nyuszika, itt óbégat a riasztás, hogy fosadék a hálózatotok. Erre ő, hogy meg kall adni az email címet, majd akkor kapcsolódhatók rendesen. Kapott eldobható email címet szórakozzanak azzal. Kapcsolódtam, de továbbra sem biztonságos a net. Mucikának mondom, hogy így sem jó, egy kalap fos a hálózatotok, erre ő, hogy lehet netezni nem? Különben sem kötelező használni.
Na itt triggerelt be. Most gyűjtöm ki az összes evidenciát, hogy milyen minősítésük van, milyen policyket adtak ki, milyen certificate-jeik vannak és minek nem felel meg a kurva hálózatuk. Kapnak olyan review-t, hogy a fal adja a másikat. Szarjanak aprószöget és beizzítom a hordozható hálózatot majd használom azon keresztül.
Ha tehetném befizetnék ide @muszeresz részére egy pár napos tanulmányutat, szerintem lubickolna.
20 notes
·
View notes
Text
Print "Hello World"
Who I Am
My name is Emmanuel Igboanusi, and I’ve always had a passion for technology, particularly in the realm of security. Outside of tech, one of my biggest hobbies is riding motorcycles, which allows me to appreciate both speed and precision. I’m currently taking a technology program because I want to dive deeper into how we can protect sensitive data and improve cybersecurity systems. Through this class, I hope to gain valuable insights that will help me become a better security professional.
Areas of Interest and Strength
I’m especially interested in cybersecurity. My focus is on protecting data, analyzing potential threats, and ensuring that confidential information is safe from unauthorized access. I find it fascinating to explore different ways to confiscate compromised data and mitigate risks before they escalate. I also enjoy hands-on experiences like working with servers, configuring networks, and ensuring they meet compliance standards. I hope to develop my skills further, especially in the areas of ethical hacking and encryption technologies.
Emerging Technologies
Emerging technologies refer to cutting-edge developments that have the potential to disrupt industries and change the way we live and work. These can include advancements like artificial intelligence (AI), and blockchain. I believe staying up to date on these technologies is crucial, especially as they play a major role in enhancing security frameworks. Understanding and integrating these innovations will help to better protect systems and data in the future.
9 notes
·
View notes
Text
Deception Technology: The Cybersecurity Paradigm We Didn’t Know We Needed
In an age of ever-evolving cyber threats, traditional security measures are no longer sufficient to protect critical digital assets. To stay ahead of sophisticated attackers, organizations are turning to more innovative and proactive solutions. One such approach gaining momentum globally is Deception Technology — a cybersecurity strategy that shifts the paradigm from reactive defenses to…
#AI in Cybersecurity#breach detection#business#Business Intelligence#Cloud Security#cyber defense#cyber threat#cyber traps#cyber warfare#cybersecurity#data privacy#deception#Deception Technology#decoy systems#enterprise security#insider threat detection#Machine Learning#Network Security#proactive threat detection#Security#technology#threat intelligence
2 notes
·
View notes
Text
Abathur

At Abathur, we believe technology should empower, not complicate.
Our mission is to provide seamless, scalable, and secure solutions for businesses of all sizes. With a team of experts specializing in various tech domains, we ensure our clients stay ahead in an ever-evolving digital landscape.
Why Choose Us? Expert-Led Innovation – Our team is built on experience and expertise. Security First Approach – Cybersecurity is embedded in all our solutions. Scalable & Future-Proof – We design solutions that grow with you. Client-Centric Focus – Your success is our priority.
#Software Development#Web Development#Mobile App Development#API Integration#Artificial Intelligence#Machine Learning#Predictive Analytics#AI Automation#NLP#Data Analytics#Business Intelligence#Big Data#Cybersecurity#Risk Management#Penetration Testing#Cloud Security#Network Security#Compliance#Networking#IT Support#Cloud Management#AWS#Azure#DevOps#Server Management#Digital Marketing#SEO#Social Media Marketing#Paid Ads#Content Marketing
3 notes
·
View notes
Text
Thinking About Moving Into Security? Here’s What You Need to Know
Are you planning to transition into the security domain? This applies whether you are a scrum master, program manager, developer, tester, cloud administrator, or database administrator. The good news is that moving into security doesn’t have to be a complex leap. The security field offers a wide range of options. Your existing skills already make you a natural fit for certain areas. Compliance,…
#CSPM#Cybersecurity#Endpoint Protection#IAM#Network Security#PCI#Risk Management#SOC2#Vulnerability Management
2 notes
·
View notes
Text
IMPORTANT QUESTIONS OF ELECTRONICS FOR COMPETITIVE TEST PREP. ❤️
Impact of Semiconductor Technology on Everyday Life Discuss the influence of semiconductors on modern communication and connectivity. Explain how they power artificial intelligence and machine learning. Highlight the role of semiconductors in the development of advanced medical technologies. The primary knoledge you nee to know about curcuits , diode , register and transister , also know about , how does it works?

LEARN ABOUT NETWORKING WITH SEMI-CONDUCTOR 👈
The most used semiconductor material is silicon, which is widely used in producing integrated circuits (ICs), also known as microchips. These chips contain multiple transistors, which act as switches that allow the flow of electricity to be controlled, enabling complex electronic functions.
Current in a Parallel Circuit
Problem:vA 24V battery is connected to three resistors in parallel: R₁ = 4Ω, R₂ = 6Ω, and R₃ = 12Ω. Find the current through R₂.
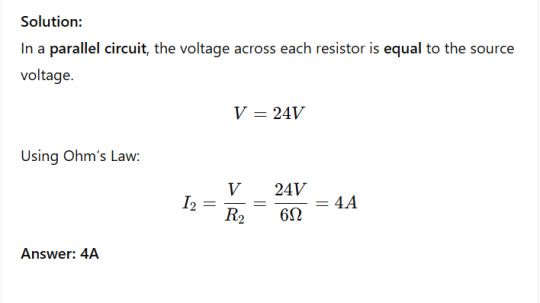
JOIN US WITH US FOR FREE VIDEO TUTORIAL 👈
#electronics components#electronics store#electronics manufacturing#electronics industry#appliances#surfaces#semiconductor#technologie#electricalsafety#network marketing#network security#services#online tutoring#online education#online courses#digital learning
3 notes
·
View notes
Text
OSS Security, Myth, or Major Concern?
Open Source Software (OSS) is inside some of the most essential companies and applications for society worldwide. However, a persistent stigma around OSS security continues to hinder both innovation and widespread adoption. When it came to asking people what their main concern about OSS is, 53% said security.
Many people become worried when they see that the code base is open to anyone or that it could be unmaintained or written by people with bad coding habits. There is also concern that companies may neglect to track updates to the source code, leaving them with outdated versions that pose security risks. But are these concerns truly valid? And if so, does that necessarily make proprietary software safer than OSS? Let's look a little deeper into some of the main security concerns in OSS and then look at why OSS may be a lot safer than people think.
One of the main reasons people feel that OSS is unsafe is because the code base is not proprietary, meaning that anyone can look at all of the code that makes up the application. This worries people because if attackers can look at the code of an application, they believe that it would be very easy to find its vulnerabilities. Another reason people are often worried about the security of OSS is whether or not the code is maintained. Although rare, people fear that the contributors to the software they are using will either stop maintaining certain parts of their software or leave the project entirely. Another worry is that even if the code is being maintained, the company using the software might not update to the latest versions that are being put out.
Outdated software, whether it is from the contributors not maintaining their software, or the company not acquiring the new updates, can lead to significant security risks. When a new update of software comes out companies will often publicly post the bugs and issues they fixed, which is informing all attackers what was wrong with the older versions. Some people also believe that those contributing to OSS are often immature and have bad developer practices. If the contributors were to have bad coding habits they could cause a lot of vulnerabilities such as hardcoding credentials or improper error handling.
While these concerns hold some validity, discussions around OSS security often overlook that many of these risks also apply to proprietary software. Let's start with some security risks that don’t apply to proprietary software. An open code base is something unique to OSS, however, I believe that this aspect of OSS benefits its level of security more than it compromises it.
There is a law called Linus’s Law named after Linus Torvalds (The creator of Linux) that says “Many eyes make any bug shallow”. This law refers to the thought that with enough contributors and coding enthusiasts looking at your code, a small amount of them might try and exploit the vulnerabilities they find, but the majority will alert the developers or fix it themselves. I believe in this law and that with many eyes looking at a codebase, vulnerabilities are more likely to be found but also addressed and remediated quickly.
Another concern of those who feel that OSS is unsafe fear that companies may not keep up to date with the source code updates. Although this is a valid concern, it is not an issue with OSS, it is a problem with a company's internal processes. This should not be listed as a security concern of OSS because it is up to the individual to regularly update the newest software that is available.
All of these reasons for OSS being unsafe or safe can be debated and argued about, but physical data is much harder to ignore. The Coverity Scan Open Source Report is an annual report that analyzes the quality and security of OSS. This report states that the average OSS is of a higher quality than proprietary software. This data not only proves that contributors to OSS do not have bad coding habits, but it also proves that OSS, even though not perfect, is of a higher standard when it comes to security than proprietary software.
I believe the stigma that OSS is unsafe has limited the level of innovation and progress society has made in all realms of software. Who knows how many beneficial pieces of software could’ve been created if it weren't for this stigma, and how that software would affect the world?
The misconception that OSS is inherently unsafe has discouraged its adoption in many sectors, which limits opportunities for societal progress. This hesitancy has most likely curbed the development of groundbreaking solutions in areas like healthcare, education, and environmental sustainability, where open-source innovation could provide affordable and scalable tools for global challenges.
Addressing these misconceptions opens the door to greater innovation, allowing open-source communities to create secure, high-quality software that meets society's evolving needs.
3 notes
·
View notes
Text
Comprehensive IT Security Services: Why You Need a Trusted IT Security Company
In today’s rapidly evolving digital landscape, securing your business’s data and IT infrastructure is more important than ever. With cyber threats growing more sophisticated, partnering with a professional IT security services company is essential for protecting your business. This article explores the key services provided by an IT security company, why businesses need them, and how a reliable provider like Gronteq can safeguard your organization from cyber risks.

Comprehensive IT Security Services: Why You Need a Trusted IT Security Company
As businesses become more reliant on digital tools and systems, the threat of cyberattacks has grown significantly. Whether you’re a small startup or a large corporation, protecting your sensitive data and IT infrastructure is no longer optional—it’s a necessity. This is where a professional IT security services company comes in. Their role is to safeguard your business from cyber threats, protect your data, and ensure your systems are running smoothly and securely.
In this article, we will discuss the various IT security services offered by reputable providers, why businesses need these services, and how partnering with a trusted IT security company like Gronteq can help you maintain a secure and resilient digital environment.
1. Understanding the Importance of IT Security
The growing frequency and sophistication of cyber threats are major concerns for businesses worldwide. Hackers, cybercriminals, and malicious insiders are always on the lookout for vulnerabilities in your IT infrastructure. From phishing attacks and data breaches to ransomware and DDoS attacks, the risks are constantly evolving.
Without the right IT security services, businesses risk losing valuable data, experiencing system downtime, and suffering reputational damage. Moreover, data protection regulations, such as GDPR and HIPAA, require businesses to implement robust security measures to avoid penalties and fines.
This is where an experienced IT security company can help. By working with a trusted provider, businesses can implement proactive security strategies that prevent attacks before they occur, ensuring a safe, compliant, and resilient online environment.
2. Key IT Security Services Offered by Companies
The scope of IT security services provided by security companies varies, but some common services include:
a. Network Security
Network security involves implementing measures to protect your internal network from unauthorized access, attacks, and data breaches. This includes firewalls, intrusion detection systems (IDS), intrusion prevention systems (IPS), and secure VPNs. With strong network security, your business can defend against external and internal threats.
b. Data Protection and Encryption
Protecting sensitive data is critical to prevent unauthorized access or leaks. IT security agencies provide encryption services to ensure that data is stored and transmitted securely. By implementing data loss prevention (DLP) tools, businesses can safeguard intellectual property, customer information, and financial data from cybercriminals.
c. Vulnerability Management
Vulnerability management involves identifying and addressing weaknesses in your systems before they can be exploited. This includes regular security assessments, penetration testing, and patch management. A thorough vulnerability management program helps keep your business ahead of potential threats.
d. Endpoint Security
With more employees working remotely, endpoint security has become a top priority. This includes securing devices like laptops, smartphones, and tablets that access your company’s network. Endpoint security services protect these devices from malware, phishing attacks, and unauthorized access, ensuring the integrity of your entire IT infrastructure.
e. Incident Response and Disaster Recovery
In the event of a cyberattack or data breach, having a well-defined incident response plan is essential. IT security services companies offer incident response and disaster recovery services to help businesses quickly recover from cyberattacks. This includes identifying the source of the breach, mitigating damage, and restoring normal operations.
f. Managed Security Services
For businesses that lack an in-house security team, managed security services (MSS) are an excellent solution. These services provide 24/7 monitoring, threat intelligence, and proactive response to security incidents. MSS ensures continuous protection for your business without the need for an internal team.
3. Why Your Business Needs IT Security Services
The question remains: why is it so critical for your business to partner with a reliable IT security company? Here are the main reasons:
a. Proactive Threat Prevention
A trusted IT security services company works proactively to protect your business. By continuously monitoring your systems, implementing security protocols, and conducting regular security audits, a professional provider helps to prevent potential attacks before they happen.
b. Protecting Business Reputation
A cyberattack can lead to loss of trust from customers, partners, and stakeholders. With IT security services, your company can protect its reputation and avoid the costly consequences of a data breach.
c. Legal and Regulatory Compliance
Cybersecurity isn’t just about protecting your data—it’s also about complying with industry regulations. An IT security company helps ensure that your business complies with relevant laws like GDPR, HIPAA, and PCI-DSS, avoiding fines and penalties.
d. Cost Savings in the Long Run
While the upfront costs of IT security services may seem significant, they can actually save your business money in the long run. By preventing attacks, reducing downtime, and avoiding the cost of data breaches, investing in security is a smart financial decision.
e. Expertise and Knowledge
Cybersecurity is a complex field that requires specialized knowledge and expertise. A reputable IT security company brings in-depth understanding of the latest threats, tools, and strategies to ensure your business is always protected.
4. How Gronteq Can Help Protect Your Business
At Gronteq, we specialize in providing comprehensive IT security services to businesses of all sizes. Our team of cybersecurity professionals is dedicated to safeguarding your business from cyber threats, ensuring compliance with regulations, and helping you maintain a secure and resilient IT environment.
We offer customized IT security solutions, including network security, data protection, vulnerability management, endpoint security, and disaster recovery. With our proactive approach to cybersecurity and 24/7 monitoring, we ensure your business is always one step ahead of potential threats.
5. Contact Gronteq for Your IT Security Needs
If you’re ready to take your business’s security to the next level, Gronteq is here to help. Our IT security experts are ready to provide tailored solutions that meet your unique needs. Contact us today to learn more about how we can protect your business from cyber threats and ensure your IT systems are secure, compliant, and optimized for success.
Conclusion The digital landscape is constantly evolving, and so are the risks that come with it. Partnering with a professional IT security services company like Gronteq ensures your business is well-protected, compliant, and prepared for any challenges that arise. From proactive threat prevention to disaster recovery, our team provides end-to-end security solutions to keep your business safe.
Contact Gronteq today to learn how our IT security services can protect your organization and give you peace of mind knowing your business is secure.
#IT security#cybersecurity#IT services#data protection#network security#IT security company#IT consulting#digital security#cyber threats#business security
2 notes
·
View notes
Text
The Evolving Threat of AI in the Public Housing Sector

The Evolving Threat of AI in the Public Housing Sector: How to Protect Your Organization
Read Blog:https://centurygroup.net/the-evolving-threat-of-ai-in-the-public-housing-sector-how-to-protect-your-organization/
#artificialintelligence #ai #machinelearning #technology #cyberthreats #cybersecurity #cyberattack #cybercrime #ransomware #networksecurity #technology #dataprivacy #hackers #cybersecurityexpert #itsecurity #threatintelligence #cybersecuritytraining #hacked
#artificial intelligence#ai generated#Machinelearning#Cyberthreats#Cyberattack#managed it services#ransomware#network security#dataprotection
3 notes
·
View notes
Text
Cyber Crime
Introduction
Crime and wrongdoing have been connected to people since ancient times. Even as societies develop, crime tries to hide itself. Different countries deal with crime in various ways, depending on their situation. It’s clear that a country with a lot of crime can’t grow or progress because crime goes against development. It has bad effects on society and the economy.
Cybercrime is when people commit crimes on the internet using computers. It’s hard to put crimes into specific groups since new ones come up often. In the real world, crimes like rape, murder, or theft can sometimes overlap. Cybercrimes involve both the computer and the person using it as victims. For example, hacking attacks a computer’s information and resources.
Computer as a Tool
When cybercriminals target individuals, the computer becomes a tool rather than the main goal. These crimes exploit human weaknesses and often cause psychological harm. Legal action against these crimes is challenging due to their intangible nature. Similar crimes have existed offline for centuries, but technology has given criminals new tools to reach more victims and evade capture.
Computer as a Target
Only a particular group of individuals carry out these actions. Unlike crimes where computers are merely tools, these activities demand the technical expertise of those involved. These kinds of crimes are relatively recent, coming into existence as long as computers have been around. This explains the lack of readiness in society and the world at large to combat these offenses. Such occurrences take place on the internet frequently. However, it’s worth noting that Africans and Nigerians, in particular, have not yet developed the technical knowledge required to engage in this type of activity.
Conventional Crime
Crime has been a part of human society for a long time and affects both society and the economy. It’s a term defined by the law and is subject to legal punishment. Crime is essentially a legal wrongdoing that can lead to criminal proceedings and penalties. The key aspect of a crime is that it breaks the criminal law. According to Lord Atkin, the determining factor for whether an act is criminal is whether it’s prohibited with penalties attached. A crime can be seen as any action or lack of action that goes against the law and results in legal penalties.
Cyber Crime
Cybercrime is the newest and most complex issue in the digital world. It can be understood as a type of crime where computers are either used as tools or are the focus of the criminal activity. Any illegal action that involves a computer as a means, target, or tool to commit further crimes falls under the category of cybercrime. A simple definition of cybercrime is “illegal activities where computers are involved as tools, targets, or both.” Computers can be tools in various activities like financial crimes, selling illegal items, pornography, online gambling, intellectual property theft, email deception, forgery, cyberbullying, and cyber harassment. On the other hand, computers can also be the target in cases like unauthorized access, stealing electronic information, email attacks, data manipulation, fraudulent actions, and physical harm to computer systems.
Distinction Between Conventional and Cyber Crime
Distinguishing between conventional and cybercrime might not seem obvious, but a closer look reveals an appreciable difference. The key distinction lies in the use of technology in cybercrime cases. The essential factor for cybercrime is the involvement of the virtual cyber medium at some point. In other words, cybercrime requires the use of digital platforms or the internet in its commission.
2 notes
·
View notes
Text
The Data Link Layer is the second layer of the Open Systems Interconnection (OSI) model, which serves as a conceptual framework that standardizes communication system functions. This layer focuses on the reliable transfer of data between adjacent network nodes over a physical link.
4 notes
·
View notes
Text
Top Networking Solutions for Seamless Business Communication

In today’s fast-paced business environment, effective communication is the backbone of success. As organizations expand and adopt new technologies, the need for reliable and efficient networking solutions has become more critical than ever. The right networking solution can significantly improve business operations, streamline communication, and enhance collaboration among teams, regardless of their location.
What Are Networking Solutions?
Networking solutions refer to a suite of technologies and strategies designed to establish, manage, and optimize communication channels within a business. These solutions encompass everything from network infrastructure to software that enables seamless data sharing, communication, and collaboration among employees, clients, and partners. Whether you're setting up a local area network (LAN), implementing a wide area network (WAN), or securing remote connections, networking solutions help ensure that your communications remain fluid and uninterrupted.
1. Cloud-Based Networking Solutions
Cloud-based networking solutions are revolutionizing how businesses approach communication. By utilizing the cloud, companies can access scalable network infrastructure without the need for heavy upfront investments in hardware. Cloud networking provides flexibility, allowing businesses to expand and scale their network needs as they grow. It also simplifies data storage and management, making collaboration across departments and teams more efficient.
Key Benefits:
Cost-effective and scalable
Easy integration with existing systems
Remote access for remote workers
2. Wireless Networking Solutions
Wireless networks have become an essential part of modern business environments. With the advent of Wi-Fi 6 and other advancements in wireless technology, businesses can offer faster internet speeds, improved connectivity, and enhanced user experiences. Wireless networking solutions eliminate the need for bulky cables and allow for greater mobility, making it easier for employees to stay connected regardless of where they are in the office or on the go.
Key Benefits:
Increased mobility for employees
Reduced hardware costs (no need for extensive wiring)
Seamless communication without connectivity issues
3. Virtual Private Networks
For businesses with remote teams or branches in different locations, maintaining secure communication is paramount. A VPN (Virtual Private Network) is one of the best networking solutions to ensure secure data transfer between devices over the internet. VPNs encrypt communication channels, making it impossible for third parties to access sensitive data. Whether you have employees working from home or offices spread across different regions, a VPN ensures that all communications are safe and protected.
Key Benefits:
Secure communication channels
Protection of sensitive data
Access to company resources from remote locations
4. Unified Communications
Unified Communications (UC) solutions integrate various communication tools—such as voice calls, video conferencing, messaging, and email—into a single platform. This unified approach streamlines communication within the organization and enhances collaboration across departments. With UC, businesses can ensure that employees stay connected and productive, whether they’re in the office or working remotely.
Key Benefits:
Centralized communication tools
Improved collaboration and decision-making
Reduced communication barriers across teams
5. Network Security Solutions
In an age where data breaches and cyberattacks are frequent concerns, businesses cannot afford to overlook network security. Robust network security solutions, such as firewalls, intrusion detection systems, and multi-factor authentication, are essential for protecting sensitive business data. By securing communication channels, businesses can prevent unauthorized access, safeguard customer information, and ensure regulatory compliance.
Key Benefits:
Protects against cyber threats and data breaches
Ensures compliance with security regulations
Enhances trust with clients and stakeholders
7. Fiber Optic Networking
For businesses that require high-speed, reliable communication, fiber optic networking solutions are an excellent choice. Fiber optics offer significantly faster speeds and higher bandwidth than traditional copper-based systems. This is crucial for businesses handling large volumes of data, running cloud applications, or engaging in video conferencing.
Key Benefits:
High-speed internet and data transfer
Increased bandwidth for large-scale operations
Reduced network latency for better user experience
Why Choose Rasnal Telecom for Your Networking Solutions
Rasnal Telecom offers customized, high-performance networking solutions designed to meet your business's unique needs. With years of experience, we provide reliable and scalable network infrastructure that enhances connectivity and supports seamless communication. Our team works closely with you to deliver solutions that optimize performance and drive business growth. Choose Rasnal Telecom for cutting-edge technology, personalized service, and trusted expertise.
Conclusion
Choosing the right networking solution for your business is vital to achieving seamless communication and driving overall success. Whether you’re looking for scalable cloud solutions, secure VPNs, or cutting-edge unified communication tools, there are numerous options available to meet your unique needs. By investing in the best networking technologies, you can improve collaboration, boost productivity, and stay ahead of the competition.
1 note
·
View note
Text
Positioned within the vibrant cityscape of Lubbock, Texas, Precision Managed IT stands as a beacon of technological prowess and reliability in the realm of outsourcing IT support. Our strategically located office embodies accessibility and expertise, catering to businesses seeking seamless and comprehensive IT solutions in this dynamic city.
Strategically situated within Lubbock's thriving business districts, our office serves as a central hub for businesses across diverse industries, from the healthcare sector near the medical facilities to the academic enterprises surrounding Texas Tech University. This strategic placement underscores our commitment to serving the varied tapestry of Lubbock's business community.
The physical space of Precision Managed IT is meticulously designed to exude professionalism and innovation. Boasting state-of-the-art infrastructure and a conducive workspace, our office cultivates an environment that fosters collaboration, trust, and ease for businesses seeking top-tier IT support services.
Beyond merely being a physical office, Precision Managed IT embodies a team of expert professionals deeply entrenched in the intricacies of the modern IT landscape. Each team member brings forth a wealth of technical knowledge, integrity, and proactive problem-solving skills to ensure that every client receives tailored, forward-thinking solutions to their IT needs.
Precision Managed IT isn't merely a service provider; it's a strategic partner invested in the success of the businesses we serve. We actively engage with our clients, forging strong partnerships aimed at elevating their technological infrastructure, optimizing operations, and ensuring seamless growth in an increasingly digital world.
Lubbock's dynamic business environment, educational institutions, and diverse industries align perfectly with Precision Managed IT's commitment to excellence and adaptability in the outsourcing IT support realm. We strive to remain at the forefront of technological advancements, empowering businesses to thrive amidst digital transformations and challenges.
In essence, Precision Managed IT represents more than just an IT support provider—it embodies trust, expertise, and efficiency in managing and optimizing technological infrastructure. Our presence in Lubbock signifies our unwavering dedication to simplifying IT complexities for businesses while upholding values of reliability, transparency, and a steadfast commitment to exceeding expectations.
Website: http://www.precisionmanagedit.com/lubbock-tx
Address: 5307 W Loop 289 Acc Rd, Lubbock, TX, 79414
Phone Number: +1 806-692-2884
Business Hours: Monday - Sunday : 07:00 AM - 07:00 PM
2 notes
·
View notes
Photo
Here's something you need to hear from an IT person that you're being lied to about:
VPN's are not security software. They don't secure private data from people who are actually looking.
If you're truly worried about your data only visit your sensitive account sites from closed networks that you control.
Relatable
307K notes
·
View notes
Text
5G Cybersecurity Guide - Read Before You Deploy

The arrival of 5G Network brings transformative changes with faster speeds more reliable connections and millions more devices online. This evolution paves the way for advancements in smart cities autonomous vehicles industrial Internet of Things healthcare and more But with this leap in capability comes greater responsibility to address cyber security challenges and protect digital assets.
This is not just a faster version of 4G It’s a complete redesign built for flexibility efficiency and connectivity across diverse devices. As information technology trends drive demand for more dynamic infrastructure security risk grows exponentially.
1. Explosive Growth of IoT Devices
2. Untrusted Hardware and Software Risks
3. Protecting Data and Privacy
4. Escalation of Cyber Threats
Attackers are moving fast Exploits targeting the weakest point in 5G environments have multiplied Meanwhile regulations around data privacy are tightening Non compliance can result in financial penalties and reputational damage Companies must act now to secure their infrastructure and data.
Read the Full Blog Here@ https://teleglobals.com/blog/addressing-cybersecurity-challenges-in-the-era-of-5g-networks
5G wireless technology unlocks enormous benefits but introduces complex Cyber Security Challenges Businesses must invest in layered defenses from network security to cloud infrastructure to and not rely on older protections alone A proactive approach guided by trusted cyber security services makes it possible to connect people devices and systems safely at scale
#5G Security#Cyber Security 2025#Network Security#Security Risk#Infrastructure Security#Cyber Threats#Data Privacy#Wireless Technology#Teleglobal International
0 notes