#Network Security Service Providers
Explore tagged Tumblr posts
Text
Top Network Security Solutions Every Business Should Consider in 2024
As technology advances, the importance of robust Network Security Solutions has never been greater. Businesses are constantly under threat from cyberattacks, which can lead to significant financial losses, reputational damage, and legal consequences. To safeguard their operations, companies need to prioritise the implementation of effective network security measures. Here are some of the top solutions every business should consider in 2024.
1.Next-Generation Firewalls (NGFWs)
Traditional firewalls are no longer sufficient to protect against sophisticated cyber threats. Next-Generation Firewalls (NGFWs) offer enhanced capabilities by combining the functions of traditional firewalls with additional features such as intrusion prevention, application awareness, and deep packet inspection. These firewalls are designed to provide a more comprehensive defence by detecting and blocking advanced threats in real time. For businesses looking to bolster their security, NGFWs are an essential investment.
2.Intrusion Detection and Prevention Systems (IDPS)
Intrusion Detection and Prevention Systems (IDPS) are crucial for identifying and mitigating threats that have bypassed initial security defences. IDPS continuously monitors network traffic for suspicious activity and automatically takes action to block or contain potential threats. By integrating IDPS into your network security strategy, you can reduce the risk of unauthorised access and data breaches, ensuring that your business remains secure.
3.Endpoint Security Solutions
With the increasing number of remote workers and mobile devices, endpoint security has become a critical component of network security. Endpoint security solutions protect individual devices, such as laptops, smartphones, and tablets, from malware, ransomware, and other cyber threats. By securing each endpoint, businesses can prevent cybercriminals from gaining access to their networks through vulnerable devices. Leading Network Security Service Providers offer comprehensive endpoint protection suites that include antivirus, encryption, and remote monitoring capabilities.
4.Virtual Private Networks (VPNs)
Virtual Private Networks (VPNs) are essential for businesses that require secure remote access to their networks. VPNs encrypt internet connections, ensuring that data transmitted between remote workers and company servers remains confidential. By using VPNs, businesses can protect sensitive information from being intercepted by cybercriminals, especially when employees are working from unsecured public networks. Implementing a reliable VPN solution is crucial for maintaining the integrity of your network.
5.Multi-Factor Authentication (MFA)
Passwords alone are no longer enough to protect against unauthorised access. Multi-Factor Authentication (MFA) adds an additional layer of security by requiring users to provide two or more forms of identification before accessing sensitive data or systems. This could include something the user knows (e.g., a password), something the user has (e.g., a smartphone), or something the user is (e.g., a fingerprint). MFA significantly reduces the likelihood of successful phishing attacks and enhances overall network security.
6.Managed Security Services
For businesses lacking the resources or expertise to manage their own network security, partnering with network security service providers is a wise choice. Managed Security Services (MSS) offer a range of benefits, including 24/7 monitoring, threat intelligence, and rapid incident response. By outsourcing security management to experts, businesses can focus on their core operations while ensuring their networks are protected against the latest threats.
7.Secure Access Service Edge (SASE)
Secure Access Service Edge (SASE) is an emerging security framework that combines wide-area networking (WAN) capabilities with comprehensive security functions. SASE provides businesses with a unified approach to securing their networks, especially as they adopt cloud-based services and support remote work. By integrating SASE into your network security strategy, you can ensure consistent security policies across all users and devices, regardless of location.
Conclusion
In 2024, businesses must stay ahead of cyber threats by implementing robust network security solutions. From Next-Generation Firewalls and IDPS to Managed Security Services and SASE, these solutions provide the necessary protection to keep your business safe. By partnering with trusted network security service providers, you can ensure that your business is equipped to handle the evolving threat landscape, safeguarding your operations and reputation in the process.
0 notes
Text
Top Cybersecurity Solutions Providers in Delhi-NCR: Wish Geeks Techserve
Cybersecurity services in India have become an essential investment for businesses looking to safeguard their digital infrastructure from rising cyber threats. With an increasing number of data breaches, phishing attacks, and malware infiltrations, organizations cannot afford to overlook the importance of strong IT security frameworks. Companies in Delhi-NCR, in particular, need to prioritize security due to the region's rapid technological growth and evolving cyber risk landscape.
Finding the top cybersecurity solutions provider in India is crucial for ensuring business continuity, regulatory compliance, and data integrity. Among the top contenders offering robust security solutions is Wish Geeks Techserve, a trusted IT security services India provider known for its innovative and customized cybersecurity strategies.
The Growing Cybersecurity Challenges in India
As the digital economy expands, businesses face a multitude of security threats ranging from ransomware attacks to sophisticated hacking attempts. The emergence of remote working models and cloud computing has further increased the vulnerability of organizations, making network security services in India a necessity rather than an option. The cyber threat landscape includes:
Phishing and Social Engineering Attacks: Cybercriminals exploit human vulnerabilities through fraudulent emails and deceptive practices to gain unauthorized access to sensitive information.
Malware and Ransomware Infections: Malicious software infiltrates systems, encrypting or corrupting critical business data, often leading to significant financial losses.
Insider Threats and Human Errors: Employees, either maliciously or unintentionally, can cause security breaches through weak passwords, mishandling of data, or lack of security awareness.
DDoS (Distributed Denial-of-Service) Attacks: Hackers overwhelm business networks with excessive traffic, leading to downtime and operational disruptions.
Cloud Security Risks: With increasing cloud adoption, businesses must ensure secure cloud storage, access management and data encryption practices to prevent unauthorized intrusions.
Why Choose Wish Geeks Techserve as the Best Cybersecurity Company in India?
Wish Geeks Techserve stands out among cybersecurity solutions providers in India, offering state-of-the-art security services tailored to businesses of all sizes. Their comprehensive approach ensures complete protection from internal and external threats. Here’s what makes them the ideal IT security services India provider:
1. Advanced Cybersecurity Solutions for End-to-End Protection
Wish Geeks Techserve provides holistic security solutions that cover all aspects of IT security. Their expertise spans across:
Threat Intelligence & Risk Assessment: Proactively identify vulnerabilities and strengthen weak points before attacks occur.
Endpoint Protection & Malware Defense: Implementing security measures that shield endpoints like computers, mobile devices and IoT systems from cyber threats.
Firewall & Intrusion Prevention Systems (IPS): Ensuring that network boundaries remain impervious to unauthorized access attempts.
Incident Response & Forensics: Swift action in the event of a cyberattack, minimizing damage and preventing future breaches.
2. Comprehensive Network Security Services in India
As a leading cybersecurity solutions provider in India, Wish Geeks Techserve specializes in network security services in India, ensuring robust defense mechanisms against cyber threats. Their network security offerings include:
Secure VPN Implementations: Allowing safe and encrypted remote access for employees working from different locations.
DDoS Protection & Mitigation: Preventing large-scale cyberattacks that aim to disrupt operations.
Zero Trust Security Frameworks: Adopting a ‘never trust, always verify’ approach to user authentication and access control.
3. 24/7 Cybersecurity Monitoring & Incident Response
Cyber threats do not operate within business hours, which is why Wish Geeks Techserve provides round-the-clock monitoring and support. Their dedicated Security Operations Center (SOC) continuously tracks anomalies, preventing attacks before they escalate.
4. Regulatory Compliance & Data Privacy Solutions
With stringent data protection regulations like GDPR and India’s upcoming Personal Data Protection Bill, businesses must comply with legal security mandates. Wish Geeks Techserve helps companies meet these requirements by implementing industry-leading compliance strategies and ensuring secure handling of customer and business data.
5. Customized Cybersecurity Strategies for Businesses
Recognizing that no two businesses have the same security needs, Wish Geeks Techserve delivers customized cybersecurity services in India based on industry-specific challenges. Whether it's securing financial transactions, protecting healthcare records, or preventing e-commerce fraud, their team crafts personalized solutions to fit organizational requirements.
How Businesses Can Benefit from Strong Cybersecurity Measures
Adopting best-in-class IT security services India offers multiple benefits beyond just data protection. Businesses that invest in top-tier security measures experience:
Improved Customer Trust: Demonstrating commitment to data privacy enhances brand credibility.
Reduced Financial Losses: Preventing cyberattacks reduces the risk of hefty ransom payments, fines and revenue losses due to downtime.
Operational Efficiency: Secure IT environments enable seamless business operations without disruptions from malware or unauthorized access.
Competitive Advantage: Businesses that prioritize cybersecurity gain an edge over competitors who fail to implement robust security strategies.
Conclusion
Cybersecurity is no longer a choice but a necessity for businesses in Delhi-NCR and across India. Choosing the right cybersecurity solutions provider in India can make all the difference in ensuring business continuity and protection against cyber threats. Wish Geeks Techserve emerges as one of the best cybersecurity companies in India, offering cutting-edge IT security services in India that cater to businesses of all sizes. Their expertise in network security services in India ensures that organizations remain resilient against evolving cyber risks.
If you’re looking for a trusted partner to fortify your cybersecurity infrastructure, Wish Geeks Techserve is the go-to provider, ensuring that your business stays secure in the ever-changing digital landscape. Invest in strong security measures today and safeguard your business’s future!
#Best Cybersecurity Company in India#IT Security Services India#Cybersecurity Solutions Provider in India#Network Security Services in India
4 notes
·
View notes
Text
Bots Now Dominate the Web: Why This Growing Problem Demands Urgent Action

The digital world, once a bustling marketplace of human interaction, has undergone a silent, pervasive transformation. Data from 2024 and early 2025 reveals a startling reality: bots now dominate web traffic, accounting for over 50% of all internet activity. While some of these automated programs are "good" – diligently indexing content for search engines or enabling helpful chatbots – a significant and escalating proportion are "bad bots," mimicking human behavior for malicious purposes. This widespread bot dominance web traffic presents a serious and ever-growing problem for businesses, cybersecurity, and the overall integrity of the web. The sheer volume and sophistication of these malicious bots internet traffic are redefining the landscape of online security.
The rise of bot traffic on the internet is significantly fueled by rapid advancements in Artificial Intelligence (AI) and Large Language Models (LLMs). These technologies simplify the creation and scaling of sophisticated, evasive bots, allowing even less skilled malicious actors to launch high-volume attacks. As of early 2025, malicious bots account for a staggering 37% of all internet traffic, a substantial increase from previous years, signaling a deepening bot problem online.
The Unseen Majority: How Bots Came to Dominate the Web
For the first time in a decade, automated traffic has surpassed human activity. This shift is primarily attributed to the proliferation of AI and LLMs, which have democratized bot development, making it more accessible to a wider range of actors. These advancements enable bots to mimic human interaction with startling accuracy, often bypassing traditional security measures.
The sophistication of these bad bots internet traffic is constantly evolving. They employ techniques like IP rotation, mimicking legitimate browser fingerprints, and distributing attacks across vast networks of compromised devices (botnets). The goal is simple: evade detection by blending in with legitimate web traffic automation. This makes it increasingly difficult for organizations to differentiate between genuine human users and malicious automated scripts, amplifying the bot problem online.
The Multifaceted Problem: Impacts of Bot Dominance

The pervasive presence of malicious bots internet traffic creates a myriad of complex and costly issues across various aspects of the digital economy. Understanding the full scope of the impact of bots on business is crucial for developing effective defense strategies.
Financial Drain & Fraud
The direct financial implications of bot fraud are staggering. Malicious bots are instrumental in various fraudulent activities that directly hit a business's bottom line:
Credential Stuffing and Account Takeovers (ATOs): Bots automate login attempts using stolen username/password combinations from data breaches. Successful ATOs lead to financial theft, misuse of loyalty points, and damage to customer trust.
Carding and Gift Card Fraud: Bots test stolen credit card numbers against e-commerce sites or attempt to drain balances from stolen digital gift cards, leading to chargebacks and direct financial losses.
Ad Fraud and Click Fraud: Bots simulate clicks and impressions on online advertisements, depleting advertisers' budgets without generating genuine leads or conversions. This distorts analytics and wastes significant marketing spend.
Scalping and Inventory Hoarding: In industries with high-demand, limited-stock items (like concert tickets, sneakers, or popular gaming consoles), bots rapidly purchase inventory, only for it to be resold at inflated prices on secondary markets. This infuriates legitimate customers and damages brand reputation.
Cybersecurity Risks & Data Integrity
Cybersecurity bot attacks represent a fundamental threat to an organization's digital infrastructure and sensitive data. Bots are often the first line of attack in broader cyber campaigns:
Vulnerability Scanning and Exploitation: Bots automatically scan websites and APIs for known vulnerabilities (e.g., SQL injection, cross-site scripting), identifying weak points that can then be exploited for unauthorized access or data exfiltration.
Distributed Denial-of-Service (DDoS) Attacks: Botnets, vast networks of compromised devices controlled by attackers, flood target websites, servers, or networks with overwhelming volumes of traffic, rendering them inaccessible to legitimate users.
API Abuse: With the rise of API-driven applications, bots increasingly target APIs to scrape data, create fake accounts, exploit business logic, or launch sophisticated fraud schemes that bypass traditional web application firewalls.
Data Scraping: Competitors or malicious actors use bots to steal valuable data, including pricing information, product catalogs, customer reviews, and proprietary content, leading to competitive disadvantage and intellectual property theft.
Operational & Performance Disruptions
The sheer volume of web traffic automation from bots places immense strain on IT infrastructure:
Server Strain and Increased Costs: High bot traffic consumes valuable server resources, bandwidth, and computing power, leading to increased hosting expenses and the need for costly infrastructure upgrades.
Degraded Website Performance: Overwhelmed servers result in slower loading times, timeouts, and poor responsiveness for legitimate users, severely impacting user experience and conversion rates.
Skewed Analytics: Bot traffic contaminates website and application analytics, inflating metrics like page views, unique visitors, and clicks while distorting bounce rates and conversion rates. This leads to flawed business decisions based on inaccurate data.
Brand Reputation & Trust
Beyond the technical and financial impacts, bot dominance web traffic erodes trust and damages brand reputation:
Spam and Misinformation: Spam bots flood comment sections, forums, and social media platforms with unsolicited advertising, malicious links, or propaganda, harming a website's credibility and user experience.
Customer Frustration: When legitimate customers are unable to access services due to DDoS attacks, or when they can't purchase items due to bot-driven scalping, their frustration can quickly turn into negative reviews and a damaged brand image.
SEO Penalties: Google and other search engines penalize websites with low-quality or duplicate content, which can result from content scraping by bots, negatively impacting search engine rankings and organic traffic.
Industries Under Siege: Where Bot Threats are Most Acute

While the bot problem online affects nearly every sector, certain industries consistently face a higher proportion and more sophisticated online bot threats:
Financial Services: A primary target due to the sensitive nature of data and high-value transactions. They face relentless account takeover bots, credential stuffing, and fraud attempts.
Retail: Highly susceptible to bot fraud related to inventory scalping, gift card fraud, price scraping, and loyalty program abuse.
Travel: Experiences a significant percentage of bad bots internet traffic, used for competitive price scraping, account takeovers, and fraudulent bookings.
Gaming: Often sees the highest proportion of sophisticated bot traffic, including bots used for cheating, account compromise, and inventory manipulation within in-game economies.
Media and Entertainment: Targeted for content scraping, ad fraud, and credential stuffing on streaming platforms.
Fighting Back: Strategies for Bot Management and Mitigation

Combating bot dominance requires a proactive, multi-layered, and continuously evolving defense strategy. Relying on outdated methods is no longer sufficient against today's sophisticated malicious bots internet attacks.
Advanced Bot Management Solutions: The cornerstone of modern bot defense. These specialized platforms utilize a combination of behavioral analysis (distinguishing human-like patterns from automated ones), machine learning (adapting to new bot tactics), device fingerprinting, and real-time threat intelligence. They go beyond simple IP blocking or CAPTCHAs to detect and mitigate even the most evasive bots.
Robust API Security: Given that 44% of advanced bot traffic targeted APIs in 2024, securing these digital gateways is paramount. Implementing strong authentication mechanisms (like OAuth, API keys), strict access controls, and rate limiting on API endpoints can significantly reduce the attack surface for API security bots. Regular API penetration testing is also crucial.
Multi-Factor Authentication (MFA): Implementing MFA adds a critical layer of security beyond just passwords. Even if bots manage to acquire stolen credentials through credential stuffing, MFA can prevent unauthorized access by requiring a second verification step (e.g., a code from a mobile app), drastically reducing account takeover bots success rates.
Continuous Monitoring and Analytics: Businesses must actively monitor their web traffic automation for unusual patterns. This includes spikes in requests from a single IP, abnormally high failed login attempts, unusual user-agent strings, or suspicious conversion rates. Real-time dashboards and automated alerts are essential for early detection of online bot threats.
Regular Security Audits and Patching: Proactive vulnerability management is key. Regularly auditing web applications, APIs, and underlying infrastructure for security flaws, and promptly patching identified vulnerabilities, closes potential entry points for bots.
User-Agent and Proxy Analysis: Many simpler bots still rely on outdated browser user-agent strings or operate through known dubious proxy services. Implementing rules to block traffic from such indicators can filter out a significant portion of commodity bot attacks. Detecting traffic from residential proxies, which more advanced bots now use, requires more sophisticated analysis.
Rate Limiting and Throttling: While not a complete solution, judiciously applying rate limits on specific endpoints (e.g., login pages, search functions, API calls) can prevent brute-force attacks and resource exhaustion caused by excessive bot requests.
Conclusion: Securing the Human-Centric Web
The landscape of the internet has fundamentally shifted. Bots now dominate the web, and this poses a significant, evolving bot problem online for businesses, their customers, and the integrity of digital interactions. From sophisticated bot fraud schemes to debilitating cybersecurity bot attacks, the impact is wide-ranging and costly.
Ignoring this reality is no longer an option. As AI continues to empower bots to become even more evasive and intelligent, businesses must embrace comprehensive and adaptive bot management solutions. Investing in robust API security, implementing strong authentication, and continuously monitoring for unusual patterns are not merely best practices; they are essential for survival in the current digital climate.
The future of the web depends on our ability to effectively differentiate between humans and machines, safeguarding digital assets and ensuring a secure, reliable, and authentic online experience for everyone. By adopting proactive strategies, organizations can protect their revenue, reputation, and customer trust from the pervasive and growing threat of malicious web traffic automation. The time for urgent action is now.
#Cyber Security Services Company | Data Security Solutions#Top-rated Cyber Security Services Company Offering Advanced Protection#Threat Detection#Risk Assessment#Data Security Solutions For Businesses Worldwide.#Cybersecurity services company#Data security solutions#Managed cybersecurity services#Enterprise cyber protection#Data breach prevention services#Cyber threat protection#IT security solutions provider#Endpoint security services#Network security services#Cybersecurity consulting company
0 notes
Text

The best network management services help manage an organization's network using secure firewalls and malware detection controllers. They also collect data from connected network devices such as switches, routers, access points, and client devices. These services facilitate smooth interaction between devices. Net Access India Limited provides this service at an affordable price. Please reach out to us for more information and a free demo.
#network management services#IT infrastructure management services#IT infrastructure management services in india#net access india limited#gate management software#field force management software#crop management software#IT infra solutions#network management software#managed cybersecurity services#managed datacenter services#end-user support services#endpoint security services#lease management software#board meeting software#phishing simulation services in india#vapt testing services in india#cloud managed services providers in india#mdm solutions#network transformation services
0 notes
Text
Network Security Service Provider in Pune | Teleglobal

Cyber threats evolve at an unprecedented pace, securing your business’s network infrastructure is no longer optional—it’s a necessity. Teleglobals, a trusted enterprise IT solutions provider with a presence in India, the US, Europe, and the Middle East, offers cutting-edge network security services to safeguard your digital assets. With over 900 satisfied clients and partnerships with industry leaders like Cisco, Fortinet, and AWS, Teleglobals delivers comprehensive, tailored solutions to ensure your network remains secure, resilient, and efficient.
Schedule a free network security assessment: https://telelgobals.com/cloud-infrastructure-assessment
Why Network Security Matters in 2025
The digital landscape is fraught with risks, from ransomware to sophisticated phishing attacks. In 2024 alone, cybercrime losses in the US reached $16.6 billion, a 33% increase from the previous year. Businesses face not only financial losses but also reputational damage and operational disruptions. Teleglobals’ network security services address these challenges by providing end-to-end solutions, from strategic planning to continuous monitoring, ensuring your network is a robust asset rather than a vulnerability.
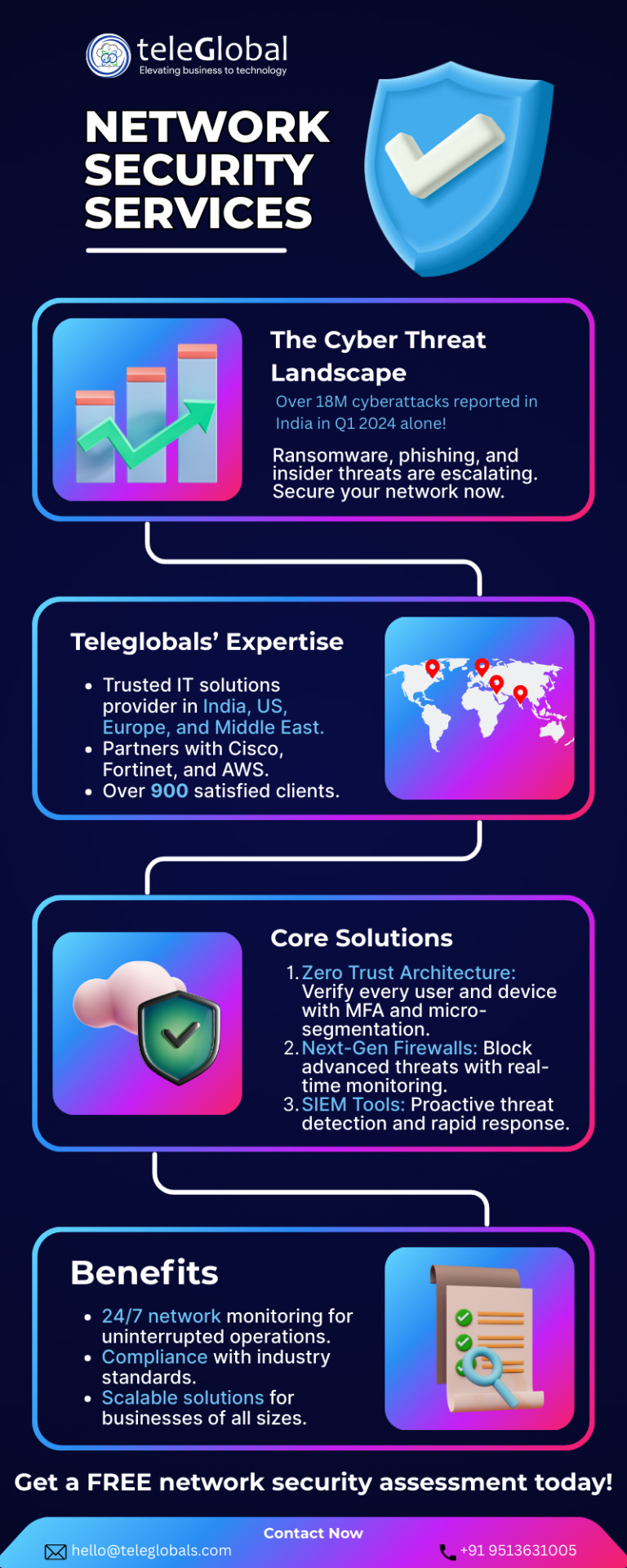
Comprehensive Network Security Solutions
Teleglobals excels in configuring and optimizing network devices such as routers, switches, firewalls, and load balancers to meet your specific business needs. Their experts use advanced tools and real-time analysis to monitor networks proactively, identifying potential issues before they escalate. This approach ensures uninterrupted connectivity and peak performance, allowing you to focus on core business objectives without worrying about cyber threats.
A cornerstone of their strategy is the adoption of Zero Trust Architecture (ZTA), a modern security framework that verifies every user and device attempting to access your network. By implementing multi-factor authentication (MFA) and micro-segmentation, Teleglobals limits access to sensitive data, reducing the risk of unauthorized breaches. Additionally, their services include next-generation firewalls with intrusion prevention and deep packet inspection, ensuring robust defense against advanced threats.
Tailored and Proactive Protection
What sets Teleglobals apart is their commitment to customized solutions. They assess your current IT landscape, align security measures with your business goals, and integrate cutting-edge technologies like AI and machine learning for real-time threat detection. Their partnerships with industry giants like Fortinet and Microsoft enable them to deliver scalable, future-proof solutions.
Teleglobals also emphasizes employee training to mitigate human error, a significant cybersecurity risk. Through regular workshops and phishing simulations, they empower your workforce to recognize and respond to threats effectively. This holistic approach combines technology and education to create a resilient security posture.
Why Choose Teleglobals?
With a proven track record across diverse industries, Teleglobals offers reliable, innovative network security services. Their global presence and 24/7 support ensure your business remains protected around the clock. By choosing Teleglobals, you gain a strategic partner dedicated to enhancing your cybersecurity, compliance, and operational efficiency.
Ready to secure your network? Contact Teleglobals at [email protected] or visit teleglobals.com for a consultation today.
#network security services#network security#cybersecurity#cyber security#teleglobalinternational#cloud service providers#cloud consulting services
0 notes
Text
Why Choose White Label Network Security for Your Business? Trying to keep up with today's cybersecurity needs is hard. If you're running a business or serving up multiple customers' IT needs, you're probably juggling a dozen things already. Cyber attacks get more sophisticated all the time, and it's not just the big companies that are at risk. Small and mid-sized companies are in danger, too. So, what's the smart thing to do? Partnering with white label managed IT service providers who offer powerful white label network security solutions.
0 notes
Text
Comprehensive IT Infrastructure Solutions | Vivency Technology LLC
Vivency Technology LLC offers expert IT infrastructure solutions to help businesses build, manage, and optimize their IT environments. Our services include network solutions, data center solutions, cybersecurity, IT consulting, and managed services. Partner with us for reliable and scalable IT infrastructure tailored to your needs.

https://www.vivencyglobal.com/infrastructure-solutions/
#IT infrastructure solutions#IT infrastructure services#network solutions#data center solutions#cybersecurity solutions#IT consulting#managed IT services#business IT solutions#IT infrastructure company#IT support services#enterprise IT solutions#cloud infrastructure#IT security solutions#IT infrastructure provider#technology infrastructure#IT networking solutions#infrastructure management#IT optimization#IT infrastructure Dubai#Vivency Technology LLC.
1 note
·
View note
Text
Why a Reliable Earthing System Is Crucial for Lightning Protection
When it comes to safeguarding buildings, equipment, and lives from the devastating impact of lightning, a reliable earthing system plays an irreplaceable role. Lightning strikes, with their immense electrical charge, can lead to catastrophic consequences if not properly managed. An effective earthing system ensures that this energy is safely dissipated into the ground, minimizing damage and enhancing safety.
Understanding the Role of an Earthing System in Lightning Protection
An earthing system, also known as grounding, is designed to provide a low-resistance path for electrical currents to travel safely into the earth. During a lightning strike, the system acts as a conduit that directs the high-voltage energy away from structures and sensitive equipment, reducing the risk of electrical fires, equipment failure, and potential harm to occupants.
Without a reliable earthing system, the sudden surge of electricity from lightning can overload circuits, cause short-circuiting, and even lead to dangerous voltage differences within a building. This not only endangers electronic devices but also poses a significant safety risk to people.
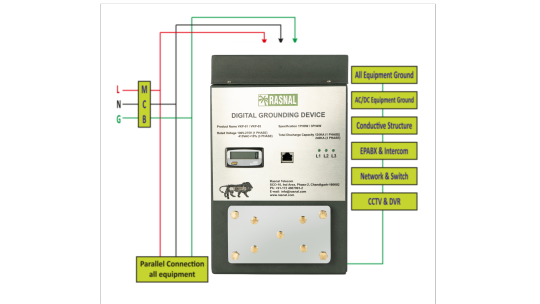
Key Benefits of a Reliable Earthing System for Lightning Protection
Prevents Electrical Overloads: Lightning strikes can generate currents exceeding 200,000 amps. A well-designed earthing system ensures that this enormous energy is quickly and safely discharged into the ground, preventing dangerous voltage spikes within the electrical network.
Reduces Fire Risks: High electrical surges from lightning can ignite fires in wiring, appliances, and structural components. By grounding excess electricity, earthing systems minimize the potential for such hazards.
Protects Electrical and Electronic Equipment: Sensitive equipment such as computers, communication systems, and industrial machinery can be severely damaged by lightning-induced power surges. An effective earthing system acts as a safeguard, preserving the integrity and longevity of electronic assets.
Enhances Safety for Occupants: The primary objective of an earthing system is to ensure human safety. It helps maintain a uniform potential within the structure, preventing dangerous voltage differences that could cause electric shock or electrocution.
Supports Compliance with Safety Standards: Many international and national electrical codes mandate proper earthing systems for lightning protection. Compliance not only promotes safety but also helps avoid legal and financial liabilities.
Components of a Reliable Earthing System
A reliable earthing system comprises several critical components that work together to manage lightning strikes effectively:
Earthing Rods: These are conductive rods (typically copper or galvanized steel) driven deep into the ground to facilitate efficient current dissipation.
Earthing Conductors: These cables connect the lightning protection system to the earthing rods, offering a low-resistance path for electrical discharge.
Earth Pits: These are specially designed pits that house the earthing rods and provide access for regular maintenance and testing.
Ground Enhancement Material: This material improves soil conductivity around the earthing rods, enhancing the overall performance of the system.
Ensuring the Effectiveness of Your Earthing System
To maintain optimal performance, an earthing system requires regular inspection and testing. Key maintenance practices include:
Routine Testing: Measuring earth resistance to ensure it remains within safe limits.
Inspecting Components: Checking earthing rods, conductors, and connections for signs of corrosion or wear.
Maintaining Earth Pits: Keeping earth pits free from debris and ensuring ground enhancement materials are intact.
Conclusion
A reliable earthing system is not just an added safety feature but a critical necessity for lightning protection. By providing a safe path for electrical discharge, it minimizes risks to both property and human life. Whether for residential, commercial, or industrial settings, investing in a well-designed and properly maintained earthing system is a proactive step toward ensuring safety, compliance, and peace of mind.
For expert guidance and high-quality earthing solutions, trust Rasnal Telecom and Security—your partner in electrical safety and lightning protection.
0 notes
Text

CodeGuardian offers expert cybersecurity services to protect your business from a wide range of digital threats. Our team specializes in securing your systems, data, and applications through a variety of services, including real-time threat monitoring, vulnerability assessments, secure coding practices, data encryption, and incident response. We work proactively to identify and fix potential weaknesses before they can be exploited. Whether you're looking to secure your software, protect sensitive customer data, or ensure compliance with industry standards, CodeGuardian provides tailored solutions to keep your business safe and secure from evolving cyber risks. With CodeGuardian, you can trust that your digital assets are in good hands.
0 notes
Text
#web development service#e commerce website development service#web development company#web app development services#web and mobile app development services#it management service#it management solutions#it infrastructure management services#it service management consulting#it service operations management#cyber security service#cyber security company#cyber security solution#cyber security service provider#cyber security consultation#cloud computing services#cloud computing companies#best cloud service provider#cloud computing security#best cloud computing services#iot services#iot solutions#iot development services#iot software development#iot network solutions#hr services#staffing service provider#hr recruitment solutions#hr services company#staffing solutions provider
0 notes
Text
Network Security Service Providers
Defend against cyber threats with Blue Saffron’s Managed Security Services. Offering Endpoint Security and Managed CyberSecurity to safeguard your digital assets.
0 notes
Text
Top Cybersecurity Services in Noida For Penetration Testing and Managed Security Services: Wish Geeks Techserve
In an age when cyber threats are more advanced than ever, protecting your business is not optional—it’s essential. Data breaches, ransomware attacks, and phishing scams can disrupt your operations, damage your reputation, and result in significant financial losses.
That’s why forward-thinking businesses trust Wish Geeks Techserve, the Best Cybersecurity Solutions Provider in Noida, to deliver advanced protection and proactive security management tailored to their needs.
As one of the most trusted names in Cybersecurity Services India, we help companies of all sizes secure their networks, applications, and critical data with end-to-end solutions.
Why Cybersecurity Matters More Than Ever
Today, even a single security lapse can expose your entire business to cybercriminals. Small and medium-sized businesses are especially vulnerable because they often lack the in-house resources to keep pace with evolving threats.
✅ Benefits of Professional Cybersecurity Services
Protect sensitive data and customer information
Prevent costly downtime and operational disruptions
Maintain regulatory compliance and avoid penalties
Build customer trust and confidence
Enable secure remote work environments
With Cybersecurity Services in Noida by Wish Geeks Techserve, you gain peace of mind knowing your business is always protected.
Why Choose Wish Geeks Techserve?
As the Best Cybersecurity Company in India, we deliver comprehensive security services backed by deep expertise and a proactive approach. Whether you need a one-time security assessment or fully managed cybersecurity, we’re here to help.
✅ Certified Security Experts
Our team includes certified cybersecurity professionals skilled in penetration testing, threat analysis, compliance, and incident response.
✅ 24/7 Monitoring and Support
Cyber threats don’t sleep—and neither do we. Our experts monitor your environment around the clock to detect and neutralize threats.
✅ Customized Solutions
Every business has unique security challenges. We tailor our services to your industry, compliance needs, and risk profile.
✅ Advanced Tools and Technologies
From intrusion detection to endpoint protection and SIEM (Security Information and Event Management), we use best-in-class tools to keep you safe.
Our Core Cybersecurity Services
Wish Geeks Techserve offers a full suite of Cybersecurity Services Noida and across India, including:
🛡️ Managed Security Services
Proactive, ongoing protection for your networks, endpoints, and cloud infrastructure, fully managed by our security team.
🧪 Penetration Testing
Identify and fix vulnerabilities before attackers exploit them. Our ethical hackers simulate real-world attacks to test your defenses.
🔍 Vulnerability Assessments
Regular scans and assessments to uncover weaknesses across your systems and applications.
🧩 Network Security Services in India
Comprehensive network protection, including firewalls, intrusion prevention systems, and secure access controls.
🌐 Cloud Security Solutions
Secure your cloud workloads and SaaS applications with policies, monitoring, and encryption.
📊 Compliance and Risk Management
Stay compliant with regulations like GDPR, ISO 27001, and PCI-DSS through risk assessments and documentation.
⚠️ Incident Response and Recovery
In the event of a breach, our experts provide rapid response and help restore operations sWho We Serve
As a leading Cybersecurity Solutions Provider in India, we partner with businesses of every size and industry:
Finance and Banking
Healthcare and Pharmaceuticals
E-commerce and Retail
Manufacturing and Logistics
Education and Technology
Real Estate and Professional Services
Whether you operate locally in Noida or nationally, we deliver the expertise and tools to protect your digital assets.
Our Proven Cybersecurity Process
We follow a structured process to keep your business secure at every layer:
Assessment and Discovery: We analyze your environment, identify gaps, and understand your compliance requirements.
Strategy and Planning: Our experts develop a tailored cybersecurity roadmap aligned with your business goals.
Implementation: We deploy the necessary security solutions, configurations, and policies.
Monitoring and Management: Continuous monitoring, threat detection, and maintenance keep your systems protected.
Training and Support: We educate your team on best practices to strengthen your first line of defense.
Why We’re the Best Cybersecurity Solutions Provider in Noida
Decades of combined cybersecurity experience
Industry-leading technologies and frameworks
Proven track record protecting businesses across India
Flexible solutions for any size organization
24/7 support from certified security experts
When you choose Wish Geeks Techserve, you gain a trusted partner dedicated to safeguarding your business.
Ready to Secure Your Business?
Don’t wait for a breach to realize the importance of proactive cybersecurity. Protect your operations, data, and reputation with Wish Geeks Techserve, the Top Cybersecurity Experts in Noida.
📩 Book your free cybersecurity consultation today and discover how we can keep your business safe.
#Cybersecurity Services Noida#cybersecurity solutions in Noida#Best Cybersecurity Solutions Provider in Noida#Cybersecurity Services in Noida#Cybersecurity Services India#Best Cybersecurity Company in India#IT Security Services India#Cybersecurity Solutions Provider in India#Cybersecurity Solutions Provider in Noida#best Cybersecurity Solutions Provider in Noida#Network Security Services in India
0 notes
Text
Cyber Security Services Company | Data Security Solutions

In today’s fast-paced digital world, businesses increasingly rely on technology to store, process, and transmit sensitive data. As companies across industries harness the power of the internet, the need for robust cybersecurity services has never been more crucial. Data breaches and cyberattacks are growing threats from small startups to large corporations that can have devastating consequences. That’s where a cybersecurity company specializing in data protection services and cybersecurity management comes into play.
This blog explores the importance of cybersecurity management, the types of services offered by a cybersecurity services company, and how data protection services and endpoint security services can help businesses protect their sensitive information.
Understanding the Growing Importance of Cybersecurity
The digital transformation that businesses have undergone in recent years has revolutionized operations, providing significant benefits like improved efficiency, better customer engagement, and more streamlined processes. However, this transformation has also opened new doors for cybercriminals who exploit vulnerabilities in systems and networks to steal data, launch attacks, and disrupt operations.
With data breaches and cyberattacks on the rise, organizations must safeguard sensitive information from unauthorized access, manipulation, and theft. Whether it’s customer data, intellectual property, or financial records, securing these assets is paramount to maintaining trust, compliance with regulations, and protecting brand reputation.
Cybersecurity solutions providers play a key role in defending organizations from these threats. Cybersecurity isn’t just a technical need—it’s a business priority that can help prevent costly disruptions, legal ramifications, and loss of customer confidence. This is where the role of a cybersecurity consulting firm becomes indispensable.
What Is a Cybersecurity Services Company?
A cybersecurity services company specializes in identifying, mitigating, and preventing cyber threats. They provide tailored solutions to ensure businesses’ information and infrastructure are well-protected from a wide range of security risks. These companies are essential partners in safeguarding businesses from cyberattacks and ensuring the security of sensitive data and systems.
Key Services Provided by a Cybersecurity Services Company

Cybersecurity companies offer a range of services designed to safeguard businesses from evolving threats. These services include:
Threat Detection & Prevention Services: Cybersecurity companies deploy advanced monitoring tools and techniques to detect vulnerabilities, anomalous activities, and potential threats before they cause harm. This includes setting up firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS).
Risk Management: Cybersecurity firms assess vulnerabilities and design strategies to safeguard businesses from both internal and external threats. A cyber risk management company helps ensure that businesses are prepared for any potential cyber risks.
Cybersecurity Audits & Assessments: Regular security audits and penetration testing are vital for identifying weaknesses in a company’s infrastructure. These audits ensure no part of the system remains unprotected.
Compliance Support: For businesses in regulated industries, cybersecurity compliance services help ensure adherence to standards like GDPR, HIPAA, and PCI DSS. Companies in these industries can also benefit from IT security services companies that provide guidance and support for meeting compliance requirements.
Incident Response & Disaster Recovery: Even with robust security measures, breaches can still occur. Incident response services help businesses respond quickly and effectively to limit damage. Additionally, cybersecurity audit services and vulnerability assessment companies help identify and prevent potential attacks before they materialize.
Employee Training & Awareness: Cybersecurity management companies often provide training programs to raise awareness about phishing, password hygiene, and safe online behavior, reducing human error and improving security.
Types of Data Security Solutions Offered by Cybersecurity Companies

At the core of every cybersecurity service is data protection. Cybersecurity solutions providers offer several key solutions to help businesses secure their information:
Encryption: Encryption ensures that even if data is accessed by cybercriminals, it remains unreadable without the decryption key. Cloud security companies offer encryption solutions to protect data stored in the cloud, safeguarding sensitive information during transit and while at rest.
Access Control & Authentication: Multi-factor authentication (MFA) and role-based access control (RBAC) are implemented to ensure only authorized personnel can access sensitive systems.
Data Loss Prevention (DLP): Data protection services monitor data transfers and emails to prevent unauthorized sharing or leakage of confidential information.
Firewalls & Network Security: Firewalls act as the first line of defense by filtering traffic and blocking harmful activities. Network security services providers ensure that your network is properly configured with firewalls, VPNs, and network segmentation to protect data from external attacks.
Backup & Disaster Recovery: A comprehensive backup and recovery plan ensures that lost or compromised data can be restored with minimal disruption to business operations. Cloud security companies play a key role in providing reliable cloud-based backup and recovery services.
Endpoint Security: With more employees working remotely, endpoint security services are becoming essential. Cybersecurity firms implement solutions to protect mobile devices, laptops, and tablets from threats.
Why Partner with a Cybersecurity Services Company?
Businesses of all sizes can benefit from the specialized expertise of a cybersecurity consulting firm. Here are some reasons why partnering with one is essential:
Expertise and Experience
Cybersecurity is a complex field requiring in-depth knowledge of emerging threats and security solutions. A cybersecurity services company brings years of experience and expertise to the table, ensuring best practices and cutting-edge tools are used to protect your data.
Cost Efficiency
Building an in-house cybersecurity team can be costly. By outsourcing to a cybersecurity solutions provider, businesses gain access to expert resources and advanced technologies without the need to invest in full-time staff.
Proactive Protection
Rather than waiting for a breach to occur, a cybersecurity management company helps you adopt a proactive approach by identifying and neutralizing potential threats before they can impact your business.
Regulatory Compliance
Staying compliant with regulations like GDPR, HIPAA, and CCPA can be challenging. A cybersecurity services company ensures your business complies with relevant data protection laws, avoiding legal complications and fines. These companies provide cybersecurity compliance services to meet the highest standards of data protection.
Business Continuity
Cybersecurity services also encompass disaster recovery planning, ensuring that your business can continue to operate smoothly after a cyber attack or natural disaster. Security operations center services ensure continuous monitoring, offering peace of mind that any security breaches are quickly detected and neutralized.
Conclusion: Protect Your Business with a Cybersecurity Services Company
As cyber threats continue to evolve, businesses must take proactive steps to protect their sensitive data and maintain customer trust. Partnering with a reputable cybersecurity consulting firm ensures that you have the right tools, expertise, and strategies in place to prevent cyberattacks, secure your data, and maintain regulatory compliance.
Whether it’s through penetration testing, endpoint security services, or incident response services, a cybersecurity services company plays a crucial role in keeping your data safe and your business running smoothly.
Investing in cybersecurity solutions today can help prevent significant financial and reputational damage in the future. Don't wait until it's too late—reach out to a trusted cybersecurity services company today to protect your data and your business's future.
#Cyber Security Services Company | Data Security Solutions#Cybersecurity Management Company#Managed Cyber Security Services#Cyber Security Company#Cyber Security Services#Endpoint Security Services#Cybersecurity Solutions Provider#Cyber Security Consulting Firm#Network Security Services#Cybersecurity Audit Services#IT Security Services Company#Cloud Security Company#Data Protection Services#Cybersecurity Compliance Services#Security Operations Center Services#Threat Detection Services#Penetration Testing Company#Incident Response Services#Vulnerability Assessment Company#Cyber Risk Management Company#Information Security Services
0 notes
Text
What are the next steps after obtaining an insurance broker license, and how can you generate potential leads using Mzapp CRM software?
Congratulations on securing your insurance broker license! The journey doesn’t end here; it’s just the beginning of building a successful insurance brokerage. Here’s how you can proceed and leverage Mzapp CRM software to find potential leads:
Steps After Getting Your Insurance Broker License
Understand Your Market: Research your target audience (individuals, businesses, or specific sectors).
Develop a Business Plan: Set goals for client acquisition, revenue, and operational processes.
Build a Network: Partner with insurance providers and attend industry events to establish your presence.
Create an Online Presence: Build a professional website and maintain active profiles on social platforms.
Offer Value-Added Services: Educate customers on policies, claims management, and risk assessments.
Using Mzapp CRM Software to Generate Leads
Lead Capture: Utilize Mzapp’s integrated forms and web tracking tools to capture inquiries from your website or social media.
Automated Follow-Ups: Set up personalized email and SMS follow-ups to nurture leads effectively.
Lead Scoring: Prioritize leads based on their interaction history, ensuring you focus on high-potential prospects.
Data-Driven Campaigns: Use analytics to identify what works and launch targeted campaigns.
Seamless Policy Management: Impress leads by showcasing how smoothly you manage policies and claims through Mzapp.
Why Choose Mzapp CRM?
Mzapp CRM simplifies lead management, streamlines operations, and provides insights into customer behavior, making it easier to convert prospects into loyal clients.
Learn more about how Mzapp can transform your insurance business here.
#Question:#What are the next steps after obtaining an insurance broker license#and how can you generate potential leads using Mzapp CRM software?#Answer:#Congratulations on securing your insurance broker license! The journey doesn’t end here; it’s just the beginning of building a successful i#Steps After Getting Your Insurance Broker License#Understand Your Market: Research your target audience (individuals#businesses#or specific sectors).#Develop a Business Plan: Set goals for client acquisition#revenue#and operational processes.#Build a Network: Partner with insurance providers and attend industry events to establish your presence.#Create an Online Presence: Build a professional website and maintain active profiles on social platforms.#Offer Value-Added Services: Educate customers on policies#claims management#and risk assessments.#Using Mzapp CRM Software to Generate Leads#Lead Capture: Utilize Mzapp’s integrated forms and web tracking tools to capture inquiries from your website or social media.#Automated Follow-Ups: Set up personalized email and SMS follow-ups to nurture leads effectively.#Lead Scoring: Prioritize leads based on their interaction history#ensuring you focus on high-potential prospects.#Data-Driven Campaigns: Use analytics to identify what works and launch targeted campaigns.#Seamless Policy Management: Impress leads by showcasing how smoothly you manage policies and claims through Mzapp.#Why Choose Mzapp CRM?#Mzapp CRM simplifies lead management#streamlines operations#and provides insights into customer behavior#making it easier to convert prospects into loyal clients.#Learn more about how Mzapp can transform your insurance business here.
1 note
·
View note
Text
Reliable IT Infrastructure Solutions for Businesses
Vivency Technology LLC specializes in providing cutting-edge IT infrastructure solutions tailored to meet the diverse needs of businesses and organizations. Our services ensure seamless operations, enhanced security, and optimal performance for your IT environment.
We offer a comprehensive range of IT infrastructure services, including: ✅ Network Solutions – Reliable and scalable networking for seamless connectivity. ✅ Data Center Solutions – Advanced data storage, management, and security solutions. ✅ Cybersecurity Solutions – Protect your business with robust security measures. ✅ IT Consulting & Managed Services – Expert guidance and support for IT optimization.
Enhance your IT infrastructure with Vivency Technology LLC. Contact us today for customized solutions!
#IT infrastructure solutions#network solutions#data center solutions#cybersecurity solutions#IT consulting services#managed IT services#business IT solutions#IT infrastructure management#IT support services#enterprise IT solutions#secure IT infrastructure#cloud infrastructure solutions#network security solutions#IT infrastructure company#IT infrastructure provider#scalable IT solutions#technology infrastructure services#IT system integration#IT infrastructure optimization#Vivency Technology LLC.
0 notes
Text

Need to manage your electrical components? Use a Push Button MDF Box for easy access and a neat installation!
Perfect for: • Residential electrical installations • Commercial electrical installations • Low-voltage applications • Wiring and cable management • Temporary or portable installations
Get organized and make your electrical installations look professional with a Push Button MDF Box
10 Pair, 20 Pair, 50 Pair and 100 Pair Push Button MDF Boxes Available
( push button, Mdx Boxes, electrical, MDF, push button, components, telecom, telecom service, telecom security, rasnal)
#telecom solutions#telecom service providers#Push Button MDF Box#network security#network optimization
0 notes