#Norton for iOS
Explore tagged Tumblr posts
Text
0 notes
Text
-2
Il fine settimana è passato veloce tra spedizione dei pacchi (YEAH) e serate intere passate al bar. Venerdì pienone con serata dj e per la prima volta in questo posto ho speso del tempo con 3 persone che sono più grandi di me. La serata poi è andata a sfumare e alle 3 di notte, erano anni che non facevo così tardi, con il pizzaiolo ubriaco e quelle 4/5 persone che sedute ancora al bancone parlavano, mi sono tornate in mente tutte quelle nottate passate a bere, fumare, ascoltare musica, discutere e ridere del passato dove però spesso eravamo noi Stronzi, nome che abbiamo dato al gruppetto degli italiani che gravitava attorno al bar, poi spesso finivo a dormire nel divano perché il giorno dopo lavoravo al ristorante sempre della medesima compagnia e nello stesso stabile. Alla fine sono andato a casa stanco. Ieri al contrario era semi vuoto ma ho passato la serata con un'amica a parlare del più e del meno, almeno questo lo pensavo io, poi fuori mentre fumavamo mi ha detto che sono 6 mesi che non fa sesso, ah, io quasi un anno, ho realizzato che siccome erano 2 notti che dormiva dal pugliese perché adesso per il fatto che non ha lavoro vive in una fattoria di amici molto fuori città, le serviva un posto dove dormire, allora perché non mi chiedi? Stamane pensavo alla scena iniziale di fight club quando Norton spende ore a parlare con Pit e alla fine lui aveva capito e gli dice proprio "Chiedimelo, basta chiederlo". Che dire avrei potuto approfittare di una donna di 40 anni bellissima, molto bella, ma psicopatica bipolare, la stessa che mesi fa in una situazione analoga dopo che le feci una domanda, non ricordo quale, si alzò prese il cappotto mi mandò a fanculo e andò via, restai basito, al che il pugliese da dietro il bancone mi disse "E' psicopatica", lo so, lavorava anche lei per lui ma al bar. Francamente me ne infischio, è andata a farsi una passeggiata e magari su un altro locale ha trovato quello che cercava. Altra cosa che ieri mi ha un pò irritato è sta tizia che vuole prendere la bicicletta, lunedì l'ha vista e mi ha detto la prendo, "mi dai il numero del conto bancario?" "Non ho niente sul telefono", visto che aveva il telefono in mano, qua fanno tutto col telefono, si è stranita, beh strano trovare uno che non vive come voi mezze seghe amminchiati sul telefono come se fosse l'oracolo di Delfi, fatto sta che le ho scritto dopo cena e mi ha risposto con un semplice si e ora mi tocca riscriverle per sapere quando, dimmi tu cazzo io non so che impegni hai e ti ho detto che io sono libero da ogni impegno, sta gente meriterebbe l'isolamento per 100 anni.
Levando ste ultime cazzate perché francamente non me ne fotte un cazzo delle vostre paranoie, oggi piove e ho anche perso il conto dei giorni autunnali di questa estate estone che ne ho anche le palle piene, voglio il sole, il mare e il vulcano, a molti ho detto che mercoledì mattina vado al mare, il mare nostrum, piegano la testolina da una parte stringendo le labbra e chiedono "Ma la temperatura?", "beh 30 gradi ma penso che salirà", ci restano male.
Oramai è finita e non me ne fotte un cazzo li lascio sguazzare nel loro brodo primordiale del vuoto mentale cosmico.
youtube
5 notes
·
View notes
Text
Wes Anderson várva-várt filmje, az Asteroid City január 6-tól elérhető – kizárólag a SkyShowtime-on

A film főszereplői Jason Schwartzman, Scarlett Johansson és Tom Hanks, és a kisebb szerepeket is népszerű és kritikusok által is elismert színészek játsszák. https://youtu.be/UB376bobhSQ?si=HHZ-vSPkQMJ8ES4d Az Asteroid City, Wes Anderson legújabb filmje Jason Schwartzman (The French Dispatch, The Grand Budapest Hotel), Scarlett Johansson (Black Widow, Jojo Rabbit), és Tom Hanks (Elvis, News of the World) főszereplésével január 6-ától elérhető – kizárólag a SkyShowtime kínálatában. A hétszeres Oscar®-jelölt Wes Anderson (Isle of Dogs, Moonrise Kingdom) által írt és rendezett, a Focus Features által forgalmazott Asteroid City főszerepeiben világhírű sztárok brillíroznak, a mellészereplői gárda pedig olyan népszerű, kritikusok által is elismert színészeket vonultat fel, mint Jeffrey Wright (Westworld, No Time To Die), Tilda Swinton (Suspiria, Michael Clayton), Adrien Brody (The Pianist, The Darjeeling Limited), Bryan Cranston (Breaking Bad, Trumbo) és Edward Norton (Glass Onion, Birdman). A történet 1955 körül játszódik egy fiktív sivatagi városban, Amerika délnyugati részén. Az évente megrendezett Aszteroida-napi ünnepségre az ország minden tájáról összegyűlnek az ifjú csillagászok és űrkadétok – ám a tudományos versenyt fenekestül felforgatják a bekövetkező események. Az ifjú csillagászok eredményeinek tiszteletére rendezett ünnepségen ugyanis váratlan látogató jelenik meg: egy földönkívüli. Az Asteroid Cityt lezárják, és a hadsereg hamis fedősztorival igyekszik leplezni az igazságot, de a koraérett zsenik – Spielberg klasszikus filmjeinek ifjú hőseihez hasonlóan – kieszelnek egy tervet, hogy a külvilág tudomást szerezzen az eseményekről. Ám Andersonr��l lévén szó, a történet természetesen ennél jóval többről szól. Visszatérve keletre, az Asteroid City szereplői egy színdarab bemutatására készülnek, amelynek a címe „Asteroid City”. Itt 1955 körül kukkantunk be a kulisszák mögé, és ismerjük meg az előadókat. A színházi színészek, akiknek nevét hamarosan szárnyára kapja a hírnév, épp színészi játékukat csiszolják tökéletesre. A film kétségtelenül ugyanolyan vicces, mint Anderson bármelyik műve, de kozmikusabb is: a bonyolult családi kapcsolatok és új románcok, szülők és gyerekek, titkok, felfedezések és a felnőttek kijátszásának befelé forduló, személyes vizsgálata, a széles Nyugat és a szürke Kelet, mindez olyan tökéletes egyensúlyban egymással, amire csak Wes Anderson képes. A népszerű mellékszereplő-gárda olyan színészeket vonultat fel, mint Liev Schreiber (Ray Donovan, X-Men Origins: Wolverine), Hope Davis (Your Honor, Succession), Stephen Park (The French Dispatch, Fargo), Rupert Friend (The Young Victoria, Pride & Prejudice), Maya Hawke (Stranger Things, Do Revenge), Steve Carell (The Office, The Morning Show), Matt Dillon (There’s Something About Mary, The House That Jack Built), Hong Chau (The Whale, The Menu), Willem Dafoe (Spider-Man-filmek , The Florida Project), Margot Robbie (Barbie, Suicide Squad, I, Tonya), Tony Revolori (The Grand Budapest Hotel, A Marvel-moziverzum Spider-Man-filmjei ), Jake Ryan (Moonrise Kingdom, Eighth Grade) és Jeff Goldblum (Jurassic Park-filmek , Independence Day). A SkyShowtime az előfizetők számára közvetlenül elérhető a SkyShowtime alkalmazáson keresztül Apple iOS, tvOS és Android-eszközökön, Android TV-n, Google Chromecaston, LG és Samsung tévéken, valamint a www.skyshowtime.com/hu honlapon keresztül. A reklámmentes SkyShowtime-előfizetés ára havi 1999 Ft. További információk a szolgáltatással kapcsolatban: Honlap: www.skyshowtime.com/hu A SkyShowtime-ról A SkyShowtime Európa következő nagy streamingszolgáltatója. A Comcast és a Paramount Global közös vállalkozásaként a SkyShowtime saját sorozatai mellett elhozza a legjobb hollywoodi produkciókat és helyi szórakoztató műsorokat, filmeket és eredeti sorozatokat a Universal Pictures, a Paramount Pictures, a Nickelodeon, a DreamWorks Animation, a Paramount+, a SHOWTIME®, a Sky Studios és a Peacock kínálatából. A SkyShowtime a prémium szórakoztatás új európai otthona. A SkyShowtime szolgáltatása Európában 2023-ban indult és jelenleg Albániában, Andorrában, Bosznia-Hercegovinában, Bulgáriában, Horvátországban, Csehországban, Dániában, Finnországban, Magyarországon, Koszovóban, Montenegróban, Észak-Macedóniában, Norvégiában, Hollandiában, Lengyelországban, Portugáliában, Romániában, Szerbiában, Szlovákiában, Szlovéniában, Spanyolországban és Svédországban érhető el a választott televíziós szolgáltatónál vagy Apple iOS, tvOS és Android-eszközökön, Android TV-n, Google Chromecaston, LG és Samsung okostévéken, illetve az interneten. Read the full article
2 notes
·
View notes
Text
Oh man I remember doin this on my 2ds (i don't have a 3ds :( I want one tho)
Ao3 took foreverrrrr to load, and ff.net worked great until my 2ds wasn't supported or somethin, so I was left with only ao3 lol
I had to use my 2ds bc I had monitoring software on my phone (strict parents. That's a whole nother story that I don't wanna get into rn) and it was the only way I could read my yaoi lmao
Now I read it on pretty much every device that I have. I've also gotten back into writing since I went so long without being able to properly write a fanfiction.
My life would've been so different when i was 16-18 if I didn't have that damned software.
(Also a word of advice to anyone who has/knows someone who has Norton monitoring software installed on their devices: you can turn the wifi off on your device to bypass the device lock at certain times, at least on ios. You do have to have a passcode tho! But that can literally just be a bunch of zeroes. What matters is that the passcode is there so that the software can't stow your apps away until it's unlocked. ig turning the wifi off prevents the software from accessing something, but I'm not sure what. Now i will say that's its been like 2 years since it was removed from my devices, so it might've changed, but it's worth a shot!)
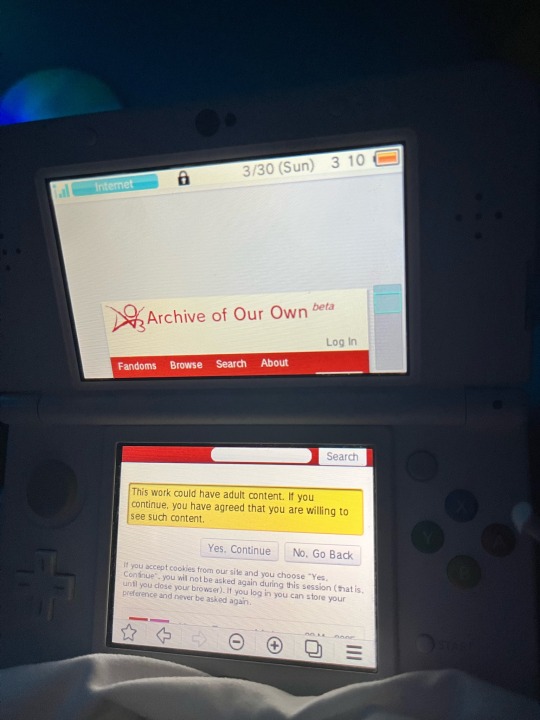
43K notes
·
View notes
Text
Bí Kíp Chống Hack Điện Thoại Bạn Nên Biết
Trong thời đại số, điện thoại không chỉ là phương tiện liên lạc mà còn là “kho báu” lưu trữ vô số thông tin cá nhân, tài chính, công việc và các dữ liệu nhạy cảm. Tuy nhiên, chính vì vậy mà điện thoại ngày càng trở thành mục tiêu tấn công của hacker. Vậy bảo vệ điện thoại khỏi hacker bằng cách nào? *** viết dưới đây sẽ hướng dẫn bạn chi tiết những phương pháp hiệu quả nhất giúp giữ an toàn cho thiết bị di động của mình.
1. Vì sao cần bảo vệ điện thoại khỏi hacker?
Hầu hết người dùng đều nghĩ rằng điện thoại của mình không đủ “hấp dẫn” để hacker tấn công. Tuy nhiên, thực tế cho thấy hacker không chỉ nhắm vào người nổi tiếng hay doanh nhân, mà bất kỳ ai có dữ liệu cá nhân cũng đều có nguy cơ bị tấn công.
Một số lý do cần bảo vệ điện thoại khỏi hacker bao gồm:
Lộ thông tin cá nhân (số CMND/CCCD, địa chỉ, tài khoản ngân hàng...)
Mất quyền kiểm soát các tài khoản mạng xã hội, email, ứng dụng thanh toán
Thiết bị bị mã hóa tống tiền (ransomware)
Bị theo dõi vị trí, nghe lén, quay lén
2. Những hình thức tấn công phổ biến của hacker vào điện thoại
Để biết cách bảo vệ điện thoại khỏi hacker, bạn cần hiểu các hình thức tấn công mà họ thường dùng:
2.1. Phishing (lừa đảo qua đường link)
Hacker gửi tin nhắn hoặc email chứa liên kết giả mạo trang web ngân hàng, Facebook, Zalo… nhằm đánh cắp thông tin đăng nhập.
2.2. Malware (mã độc)
Tải ứng dụng không rõ nguồn gốc hoặc click vào quảng cáo độc hại có thể khiến điện thoại bị cài phần mềm gián điệp.
2.3. Kết nối Wi-Fi công cộng
Wi-Fi miễn phí không bảo mật là môi trường lý tưởng để hacker theo dõi hoạt động và đánh cắp dữ liệu từ điện thoại.
2.4. SIM Swap
Hacker giả mạo danh tính bạn để yêu cầu nhà mạng cấp lại SIM mới, từ đó chiếm quyền điều khiển tài khoản và OTP ngân hàng.
3. cách bảo vệ điện thoại khỏi hacker hiệu quả
3.1. Luôn cập nhật hệ điều hành và ứng dụng
Những bản cập nhật không chỉ bổ sung tính năng mới mà còn vá các lỗ hổng bảo mật. Đừng bỏ qua thông báo cập nhật từ iOS, Android hoặc ứng dụng bên thứ ba.
3.2. Sử dụng mật khẩu mạnh và sinh trắc học
Thiết lập mật khẩu khó đoán: ít nhất 8 ký tự gồm chữ hoa, chữ thường, số và ký hiệu đặc biệt.
Kích hoạt Face ID, vân tay để tăng lớp bảo vệ.
3.3. Cài đặt phần mềm diệt virus uy tín
Một số phần mềm diệt virus tốt cho điện thoại như:
Avast Mobile Security
Kaspersky Mobile Antivirus
Norton Mobile Security
3.4. Không cài ứng dụng ngoài Google Play hay App Store
Tránh tải APK từ các nguồn không rõ ràng vì có thể chứa mã độc. Luôn kiểm tra đánh giá và số lượt tải trước khi cài đặt.
3.5. Tắt Bluetooth và Wi-Fi khi không dùng
Bluetooth và Wi-Fi mở liên tục có thể là cánh cửa cho hacker truy cập trái phép. Tốt nhất chỉ bật khi cần thiết.
3.6. Không đăng nhập tài khoản cá nhân trên thiết bị
Tránh đăng nhập vào tài khoản Google, Facebook hay email cá nhân trên thiết bị công cộng như máy tính ở tiệm net, quán photo, điện thoại người khác.
3.7. Kích hoạt xác thực 2 yếu tố (2FA)
Đây là lớp bảo mật bổ sung, yêu cầu mã OTP hoặc ứng dụng xác thực như Google Authenticator ngoài mật khẩu khi đăng nhập
3.8. Định vị và khóa thiết bị từ xa
Cả Android và iPhone đều có tính năng định vị thiết bị từ xa, cho phép bạn xóa dữ liệu, khóa máy nếu bị mất hoặc bị đánh cắp:
Android: Find My Device
iPhone: Find My iPhone
3.9. Kiểm tra quyền truy cập ứng dụng định kỳ
Nhiều ứng dụng yêu cầu quyền truy cập camera, micro, vị trí mà không thực sự cần. Hãy thường xuyên kiểm tra và thu hồi nếu không cần thiết.
3.10. Cảnh giác với tin nhắn lạ, liên kết độc hại
Không click vào các liên kết không rõ nguồn gốc, đặc biệt là từ SMS, email hay Zalo lạ. Khi nghi ngờ, hãy tra cứu link hoặc liên hệ người gửi xác minh.
4. Dấu hiệu cho thấy điện thoại có thể đã bị hack
Máy hao pin bất thường, nóng máy không rõ lý do
Xuất hiện ứng dụng lạ mà bạn không cài
Tự động gửi tin nhắn hoặc email lạ cho người khác
Tài khoản mạng xã hội bị đăng xuất hoặc hoạt động bất thường
Phí dữ liệu di động tăng đột biến
Nếu bạn thấy một hoặc nhiều dấu hiệu trên, hãy thực hiện quét virus và kiểm tra toàn bộ ứng dụng, tài khoản ngay lập tức.
5. Khi bị hack điện thoại cần làm gì?
Xem chi tiết tại: ATS Tech
6. Những hiểu lầm thường gặp khi bảo vệ điện thoại khỏi hacker
“Tôi dùng iPhone thì không bị hack”: Sai. Dù iOS bảo mật tốt hơn Android, nhưng hacker vẫn có cách tấn công qua iCloud, app giả mạo hoặc phishing.
“Chỉ cần cài phần mềm diệt virus là đủ”: Không đúng. Phần mềm chỉ là một lớp bảo vệ. Bạn cần kết hợp nhiều biện pháp khác.
“Tôi không lưu gì quan trọng trong điện thoại”: Những thông tin tưởng chừng nhỏ (số điện thoại, email, định vị) cũng có thể bị lợi dụng để lừa đảo.
1 note
·
View note
Text
Protect Your Digital Life with Norton Antivirus: Complete Security for Every Device
In an age where cyber threats are more sophisticated than ever, having robust digital protection is no longer optional—it’s essential. Norton Antivirus stands out as a trusted and comprehensive security solution, helping individuals and families stay safe from viruses, malware, ransomware, and online fraud. If you're looking for top-tier protection, the Norton 360 Premium package available on OmniSoft is the ideal choice.
What Is Norton Antivirus?
Norton Antivirus is a globally recognized cybersecurity software developed to provide real-time protection against a wide range of online threats. With over three decades of experience, Norton has continuously evolved to offer intelligent, proactive defense systems that protect your privacy, personal information, and devices from digital dangers.
Key Features of Norton 360 Premium
The Norton 360 Premium edition is more than just antivirus software—it’s an all-in-one digital protection suite. Here are some of the standout features:
Comprehensive Antivirus Protection: Detects and removes viruses, spyware, malware, and ransomware.
Multi-Device Coverage: Safeguard up to 10 devices including Windows, Mac, Android, and iOS.
75 GB Cloud Backup: Keep your important files secure in the cloud to prevent data loss due to ransomware or hard drive failure.
Firewall for PC and Mac: Adds an additional layer of security to block unauthorized access to your private data.
Password Manager: Securely stores and manages your passwords, credit card information, and other credentials.
Parental Control: Help your kids safely explore the internet by monitoring online activity and limiting access to inappropriate content.
Secure VPN: Browse anonymously and securely even on public Wi-Fi with an integrated virtual private network.
Why Choose Norton from OmniSoft?
OmniSoft is a trusted digital software provider offering licensed and affordable security solutions. When you purchase Norton Antivirus 360 Premium from OmniSoft, you benefit from:
Immediate digital delivery
One-year full protection
Romanian customer support
Reliable and secure payment methods
Who Needs Norton Antivirus?
Whether you're a student, a remote worker, a business professional, or managing a household, you likely rely on multiple devices daily. Cybercriminals target everyone—from casual browsers to corporate executives. Norton 360 Premium provides peace of mind, knowing your data, identity, and online activity are protected around the clock.
Final Thoughts
Don’t leave your digital life vulnerable. With cyber threats growing each day, investing in powerful and reliable protection like Norton Antivirus is a smart and necessary step. Secure your online world today with Norton 360 Premium from OmniSoft—because your privacy, files, and peace of mind are worth it.
For more info visit here:- total security
1 note
·
View note
Text
How FlashGet Kids and Other Tools Protect Children’s Safety
Key Features in Parental Control App
Not all parental control apps are same. Here are many different features:
Content Filtering: Blocks adult websites, violent content, and social media platforms.
Screen Time Management: Schedules device usage and enforces bedtime restrictions.
Location Tracking: Provides real-time GPS updates and geofencing alerts.
App Blocking: Restricts access to distracting or unsafe apps.
Activity Reports: Summarizes browsing history, app usage, and screen time trends.
SOS Alerts: Allows children send emergency notifications.

FlashGet Kids: A Deep Dive
FlashGet Kids is robust parental control app designed to help parents monitor and manage children’s internet lives.
Includes many useful features such as:
Real-Time Location Tracking: Uses GPS to track child’s whereabouts, providing live updates and historical location data. If child enters or leaves designated area, Geofencing alerts will notify parents.
Advanced Screen Time Management: Parents can set daily screen limits, block devices during homework hours, or pause internet access. Not only thay, It also allows custom schedules for weekdays and weekends.
App and Website Blocking: FlashGet Kids lets parents block specific apps, Filter websites by category.
SOS Emergency Alerts: Children can press a panic button, Send immediate alert to parents, Show kids current location.
Cross-Platform Compatibility: The app works on Android and iOS devices, Monitoring is consistent across smartphones and tablets.
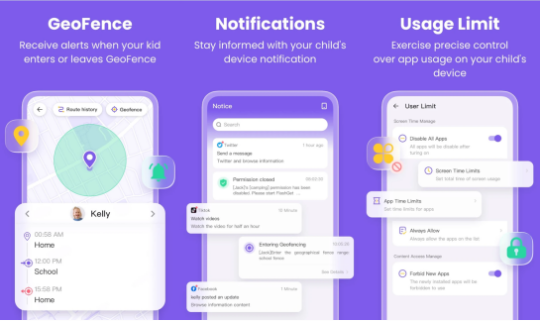
Parental control apps like FlashGet Kids are useful for now modern parenting, providing peace of mind without stifling child's independence. Eventhought alternatives like Qustodio and Norton Family have their own advantages, But FlashGet Kids is better choice, because it have rich features and affordable price.
FAQ
1.Will child know they’re being monitored?
Most parental control apps, including FlashGet Kids, operate discreetly. However, recommend transparent communication with child to build trust. The app can be configured to show notification icon, depending on your preference.
2.Can I set different rules for multiple children?
Yes. FlashGet Kids allows parents to create individual profiles for each child, tailoring screen time limits, app restrictions, and content filters based on age or needs.
3.Are parental control apps safe from hackers?
Reputable apps like FlashGet Kids use end-to-end encryption to protect data. Always choose apps with clear privacy policies and avoid tools that store sensitive information on unsecured servers.
1 note
·
View note
Text
Sr. iOS Engineer
Who Are We? We are a team that brought you Norton, Avast, LifeLock, Avira, AVG, ReputationDefender, and CCleaner, dedicated to providing cybersecurity, privacy, and identity protection to over 500 million users in 150 countries. At Gen, we offer flexible working options, generous time off, and competitive benefits in a diverse and inclusive environment where every team member is valued and…
0 notes
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] Norton 360 Premium provides comprehensive malware protection for up to 10 PCs, Mac, Android or iOS device, plus Cloud Backup4, ‡‡ for PC to help prevent data loss due to ransomware or hard drive failures and a Password Manager to store and manage your passwords. Norton 360 Deluxe also includes a VPN that enables you to browse the web more securely and anonymously, even on public Wi-Fi, and SafeCam for PC that alerts and help you block unauthorized access to your webcam. Norton360 for Working, Banking & Shopping from home. Help protect your personal & financial information & get all-in-one protection. Includes Anti-virus, Anti-Spyware, Anti-Malware & Ransomware protection. Innovative security technology powered by artificial intelligence & machine learning monitors online threats across the globe. 100 GB SECURE PC CLOUD BACKUP Automatic, secure PC cloud backup — store and help protect important files as a preventative measure to hard drive failures, stolen devices and even ransomware The moment you subscribe; a Norton expert is available to help keep your device virus-free or give you a refund. If your device gets a virus our experts can’t remove, you get your money back Also includes Secure VPN with Bank grade encryption, Safe Cam for PC Alerts you to attempts to access your webcam, Password Manager to easily generate,store,manage passwords & a Smart Firewall for PCs For sale, distribution & use only in India, Bangladesh, Nepal & Srilanka [ad_2]
0 notes
Text

E ci baciammo. E io, in un attimo, capii i baci di tutte le favole che conoscevo. La bella addormentata, Cenerentola… Quel bacio li comprendeva tutti. Perché ci sono baci che sanno di lieto fine e anche di inizio di tutto.
|| Laura Norton
0 notes
Text

🇬🇧 Fight Club (Chuck Palahniuk)
❓What do you think about the movie's ending? I prefer the one in the book 📙 by #Palahniuk
Film Ending (1999) In David Fincher’s movie, the protagonist (Edward Norton) realizes that Tyler Durden is a hallucination and tries to stop him.
However, he fails to prevent Project Mayhem’s final plan from unfolding. After shooting himself in the mouth to "kill" Tyler, he sees Marla enter the room and takes her hand. As the city lights up with explosions, buildings collapse, and financial systems are destroyed.
👉 The movie seems to suggest that the rebellion against the system has succeeded, with an almost romantic sense of destruction and rebirth.
Book Ending (1996)
In Chuck Palahniuk’s novel, the sequence is similar up to the final confrontation between the protagonist and Tyler.
However, Project Mayhem’s plan fails because the protagonist has sabotaged the explosives, making them ineffective. After shooting himself to eliminate Tyler from his mind, he wakes up in a psychiatric hospital, believing he is in paradise. But the nurses and doctors reveal themselves as Project Mayhem members, telling him they are waiting for him to recover so they can "carry on with the plan."
👉 The book’s ending is more ambiguous and unsettling: there is no clear victory for the protagonist, and the system remains intact. The cycle of violence seems destined to continue.
📌 Fun fact: Palahniuk has stated that he prefers the movie’s ending over the one in his book. 😅
💬 Drop your thoughts below 👇🏼
🇮🇹 Fight Club (Chuck Palahniuk)
❓Cosa ne pensate del finale del film? Io preferisco quello del libro 📙 di #Palahniuk
Finale del film (1999)
Nel film di David Fincher, il protagonista (Edward Norton) si rende conto che Tyler Durden è una allucinazione e cerca di fermarlo.
Tuttavia, non riesce a impedire che il piano finale del Project Mayhem si realizzi. Dopo essersi sparato in bocca per "uccidere" Tyler, vede Marla entrare nella stanza e le prende la mano. Mentre la città si illumina di esplosioni, gli edifici crollano e i sistemi finanziari vengono distrutti.
👉 Il film sembra suggerire che la ribellione contro il sistema sia riuscita, con un senso quasi romantico di distruzione e rinascita.
Finale del libro (1996) Nel romanzo di Chuck Palahniuk, la sequenza è simile fino al confronto finale tra il protagonista e Tyler.
Tuttavia, il piano del Project Mayhem fallisce perché il protagonista ha sabotato gli esplosivi, rendendoli inefficaci. Dopo essersi sparato per eliminare Tyler dalla mente, si risveglia in un ospedale psichiatrico, credendo di essere in paradiso. Ma gli infermieri e i dottori si rivelano membri del Project Mayhem, dicendogli che stanno aspettando che si riprenda per "portare avanti il piano."
👉 Il finale del libro è più ambiguo e inquietante: non c’è una vera vittoria del protagonista, e il sistema rimane intatto. Il ciclo di violenza sembra destinato a continuare.
📌 Curiosità: Palahniuk ha dichiarato di preferire il finale del film rispetto a quello del suo libro. 😅
💬 Scrivete la vostra opinione nei commenti 👇🏼
#chuck palahniuk#fight club#books and reading#books#book blog#reading community#book recommendations#libri#librichepassione#libri consigliati#libridaamare#libridaleggere#cinema#cinematography#movies#film#Instagram#film vs book#movie analysis#cult movies#philosophy#nihilism#film comparison#ai artwork#ai art#ai art gallery#ai image#ai generated#ai creation#ai
0 notes
Text
Security for Remote Work: Safeguarding Your Digital Workspace

Remote work has become a standard in many industries, offering flexibility and convenience. However, it also brings unique cybersecurity challenges, as employees often work outside of secured office environments. Protecting sensitive information and maintaining robust security measures is essential for both organizations and individuals.
This guide outlines best practices for ensuring security in remote work settings.
Why Security for Remote Work Is Important
1. Protects Company Data
Prevents unauthorized access to sensitive files, emails, and databases.
2. Mitigates Cyber Threats
Defends against phishing, malware, and ransomware attacks targeting remote workers.
3. Ensures Compliance
Maintains adherence to data protection regulations like GDPR, HIPAA, or PCI DSS.
4. Builds Trust
Reassures clients and stakeholders that their data is handled securely.
Common Security Risks in Remote Work
1. Unsecured Wi-Fi Networks
Public Wi-Fi can expose sensitive data to interception by hackers.
2. Weak Passwords
Easily guessable passwords increase the risk of unauthorized account access.
3. Phishing Attacks
Remote workers may be more vulnerable to phishing scams due to the reliance on email communication.
4. Unencrypted File Sharing
Sending files without encryption can lead to data breaches.
5. Use of Personal Devices
Devices lacking proper security measures can introduce vulnerabilities.
Best Practices for Secure Remote Work
1. Use Strong and Unique Passwords
Secure all accounts with strong, unique passwords to prevent unauthorized access.
Tips for Passwords:
Use at least 12 characters with a mix of letters, numbers, and symbols.
Avoid reusing passwords across different accounts.
Use a password manager like LastPass, Dashlane, or Bitwarden for secure storage.
2. Enable Two-Factor Authentication (2FA)
Add an extra layer of protection to online accounts.
How 2FA Works:
Requires a password and a secondary verification method, such as a code sent via SMS or generated by an authenticator app.
3. Secure Wi-Fi Networks
Ensure home or public Wi-Fi networks are protected.
How to Secure Wi-Fi:
Use WPA3 encryption for your home network.
Change default router credentials to strong, unique passwords.
Avoid accessing sensitive data on public Wi-Fi without using a VPN.
4. Use a Virtual Private Network (VPN)
Encrypt your internet connection to protect sensitive data from interception.
Recommended VPNs:
NordVPN
ExpressVPN
ProtonVPN
Tip: Ensure your VPN is enabled whenever working remotely.
5. Keep Software Updated
Regular updates patch security vulnerabilities in operating systems, apps, and devices.
What to Update:
Operating systems (Windows, macOS, iOS, Android).
Applications like browsers, collaboration tools, and antivirus software.
Tip: Enable automatic updates whenever possible.
6. Install Antivirus Software
Protect devices from malware, ransomware, and other cyber threats.
Recommended Antivirus Tools:
Norton 360
Malwarebytes
Bitdefender
Tip: Schedule regular scans and enable real-time protection.
7. Use Encrypted Communication Tools
Ensure secure communication with team members and clients.
Recommended Tools:
Messaging: Signal, WhatsApp (end-to-end encryption enabled).
Video Calls: Zoom (with encryption enabled), Microsoft Teams.
Email: ProtonMail, Tutanota.
8. Avoid Phishing Scams
Be vigilant against fraudulent emails and messages.
How to Spot Phishing Attempts:
Generic greetings like "Dear Employee."
Urgent requests to click links or share information.
Suspicious URLs or attachments.
Tip: Verify requests by contacting the sender directly through official channels.
9. Restrict Access to Sensitive Information
Limit data access to only those who need it.
Key Practices:
Use role-based access controls (RBAC).
Revoke access for former employees or unused accounts.
Encrypt sensitive files before sharing.
10. Use Company-Approved Devices
Work on devices configured with security policies, such as antivirus and encryption.
Tips for Secure Device Use:
Avoid using personal devices for work tasks unless authorized.
Report lost or stolen devices immediately to IT administrators.
For Organizations: Establishing a Secure Remote Work Policy
1. Develop a Cybersecurity Policy
Outline rules for secure remote work, including password requirements, approved software, and reporting protocols.
2. Train Employees on Cybersecurity
Provide regular training sessions to educate employees about identifying threats and maintaining security.
3. Implement Endpoint Security Tools
Use software to monitor and protect devices connected to the company network.
Recommended Tools:
CrowdStrike Falcon
Sophos Endpoint Protection
4. Monitor Network Activity
Use tools like firewalls and intrusion detection systems (IDS) to identify suspicious behavior.
5. Backup Critical Data
Regularly back up files to secure, offsite locations to prevent data loss.
Backup Solutions:
Cloud storage (e.g., Google Drive, OneDrive).
Physical storage (e.g., encrypted external hard drives).
Conclusion
Security for remote work requires a combination of tools, policies, and proactive habits. By using strong passwords, enabling 2FA, encrypting communications, and following best practices, both employees and organizations can minimize risks and maintain a secure digital workspace.
Take the necessary steps today to ensure your remote work environment is safe, productive, and resilient against cyber threats.
FAQs
1. Is a VPN necessary for remote work? Yes, a VPN encrypts your internet connection, protecting sensitive data from interception.
2. How can I secure my personal device for work? Install antivirus software, keep software updated, and avoid sharing the device with others.
3. What should I do if I suspect a phishing attempt? Do not click on links or download attachments. Report the email to your IT department immediately.
4. Are public Wi-Fi networks safe for remote work? Public Wi-Fi is risky; always use a VPN if you must connect to such networks.
5. How often should I update my passwords? Change passwords every 3–6 months or immediately if you suspect a breach.
0 notes
Text
Protecting Your Device: Best Practices for Safe App Downloads
The convenience of mobile apps has transformed how we interact with technology, providing solutions for productivity, entertainment, and communication. However, this convenience comes with risks if you’re not careful about where and how you download apps. In this blog, we’ll dive into the best practices for ensuring secure app downloads and protecting your personal data on mobile devices.
Why You Should Stick to Official App Stores
The simplest and most effective way to ensure safe app downloads is by using trusted platforms like the Google Play Store and Apple App Store. Here’s why:
Rigorous Security Measures: Both Google and Apple invest heavily in security protocols to vet apps before they’re made available. Apps are scanned for malware, phishing attempts, and other harmful behaviors. While some malicious apps occasionally slip through, they’re quickly identified and removed.
Regular Updates: Official app stores ensure that apps are regularly updated to patch vulnerabilities, add features, and improve performance. Downloading from unofficial sources often means missing these critical updates, leaving your device exposed to security risks.
Trustworthy Reviews and Ratings: App stores have extensive user reviews and ratings that can help you identify problematic apps. Fake reviews are still possible, but by checking for consistent patterns, you can spot genuine feedback.
Protection Against Malware: Third-party sources often distribute modded or pirated versions of apps that may include malware. Official stores significantly reduce this risk by monitoring for suspicious activity and enforcing strict developer guidelines.
Takeaway: If an app isn’t available on the official store, it’s worth questioning whether it’s safe to download at all.
Tips for Spotting Fake or Malicious Apps
Even when using official app stores, it’s essential to stay vigilant. Fake apps can mimic legitimate ones, tricking users into downloading harmful software. Here’s how to spot and avoid them:
Check the Developer’s Name: Always verify the app’s developer. For example, if you’re downloading Truecaller, ensure the developer is “Truecaller” or an officially affiliated name. Fake apps often use similar-sounding names to deceive users.
Scrutinize Reviews and Ratings:
Red Flags: Apps with overwhelmingly positive reviews that lack detail or context may have fake ratings.
Read Critical Reviews: Negative reviews often reveal issues with malware or misleading features.
Pay Attention to the Download Count: Popular apps usually have millions of downloads. A low download count for an app claiming to be well-known is suspicious.
Examine Permissions: Be cautious of apps that request excessive or unnecessary permissions. For example, a calculator app shouldn’t need access to your contacts or location.
Review the App Description: Legitimate apps typically have well-written descriptions without spelling errors or vague information. Poor grammar can be a sign of a hastily developed fake app.
Using Antivirus Software on Mobile Devices
Antivirus software isn’t just for computers anymore — it’s an essential tool for mobile devices too. Here’s how it helps:
Real-Time Protection: Antivirus apps can scan downloads in real time to detect malware or phishing attempts before they affect your device.
Blocking Unsafe Websites: Many antivirus apps offer browsing protection, alerting you to malicious websites or downloads while you’re online.
Scanning Existing Files: If you suspect you’ve downloaded a harmful app, antivirus software can scan your device and remove threats.
Added Features: Some antivirus solutions include VPNs, identity theft monitoring, and data breach alerts, providing a comprehensive security suite.
Top Antivirus Apps for Mobile Devices:
Android: Norton Mobile Security, Avast Mobile Security, Bitdefender Mobile Security.
iOS: While iPhones have strong built-in security, apps like McAfee or Lookout can add an extra layer of protection.
How to Secure Your Device in Case of Accidental Downloads
Sometimes, despite your best efforts, you may unknowingly download a harmful app. Here’s how to mitigate the damage:
Uninstall the App Immediately: Go to your device settings, locate the app, and uninstall it. Don’t just delete the icon from your home screen — ensure the app is entirely removed.
Revoke App Permissions: Before uninstalling, revoke any permissions the app may have had access to, such as your camera, contacts, or storage.
Scan Your Device: Use trusted antivirus software to perform a complete scan of your device. This will help identify and remove lingering malware or files left behind by the app.
Reset Passwords: If the app may have accessed sensitive data, change passwords for your accounts. Enable two-factor authentication (2FA) for added security.
Monitor Your Accounts: Keep an eye on bank accounts, email, and social media for any suspicious activity. If you notice anything unusual, report it to the relevant service provider immediately.
Perform a Factory Reset (If Necessary): In extreme cases where malware persists, a factory reset may be required. Ensure you back up important data first, and restore only from a clean backup.
Additional Tips for Secure App Usage
Enable Automatic Updates: Keeping your apps and operating system updated ensures you’re protected against known vulnerabilities.
Avoid Clicking Unknown Links: Phishing scams often lure users into downloading harmful apps or providing personal information. Be cautious about links received via email, SMS, or social media.
Use App Permissions Wisely: Periodically review and revoke permissions for apps you no longer use.
Be Skeptical of Free Offers: Apps promising “premium features for free” are often too good to be true and may compromise your security.
Conclusion
In today’s digital age, safeguarding your device from harmful apps is more critical than ever. By sticking to official app stores, scrutinizing downloads, using antivirus software, and taking swift action in case of accidental downloads, you can significantly reduce the risk of security breaches.
Your mobile device holds a treasure trove of personal data — treat it with care, and you’ll enjoy a safer, worry-free app experience. Remember, when it comes to security, a little vigilance goes a long way!
0 notes
Text

Norton Antivirus ek prasiddh antivirus software hai jo aapke computer ko viruses, malware, spyware, aur anya cyber threats se surakshit rakhta hai. Yeh software advanced security features ke sath aata hai, jo real-time protection pradan karta hai aur internet par safe browsing aur downloading ke liye scanning aur monitoring bhi karta hai. Norton Antivirus ka built-in firewall aapke network ko unauthorized access se bachata hai aur phishing websites aur risky downloads ko block karta hai. Yeh software Windows, macOS, Android, aur iOS platforms ke liye available hai aur aapke devices ko har tarah ke online aur offline dangers se bachane mein madadgar hai.
#AntivirusSoftware#NortonAntivirus#CyberSecurity#MalwareProtection#VirusProtection#InternetSecurity#RealTimeProtection#PCSecurity#NetworkSecurity#OnlineSafety#PhishingProtection#DeviceProtection
0 notes
Text
Internet-Zugang für Kinder einschränken - Aber wie?

Wenn die Kinder auf eigenen Wegen im Internet unterwegs sind, ob mit Smartphone oder Tablet, ist immer wieder die Rede davon, man solle dann Kindersicherungen einrichten. Um Kinder von ungeeigneten Websites fernzuhalten. So einfach es klingt, ist das in der Praxis nicht immer ganz einfach. Tatsächlich erlauben sowohl die WLAN-Router im Haus als auch viele Smartphones, den Internet-Zugang zu beschränken. Und das ist gerade bei jüngeren Kindern durchaus sinnvoll. Der erste Schritt zur Einrichtung von Kindersicherungen beginnt oft beim WLAN-Router, dem zentralen Knotenpunkt Ihres Heimnetzwerks. Moderne Router bieten integrierte Funktionen zur Kindersicherung, die Ihnen ermöglichen, bestimmte Websites zu blockieren, den Internetzugang auf bestimmte Zeiten zu beschränken und Aktivitäten zu überwachen. Ein bisschen technisches Grundlagen-Wissen ist trotzdem dazu notwendig. Um diese Schutz-Funktionen zu nutzen, melden Sie sich zunächst in der Weboberfläche Ihres Routers an. Dies erfolgt normalerweise durch die Eingabe der IP-Adresse des Routers in Ihren Webbrowser. Die steht meistens auch auf dem Gerät. Dann benötigen Sie das Kennwort, das Sie bei der Einrichtung des Routers bekommen haben, um Änderungen vorzunehmen. In den meisten Fällen finden Sie diese Optionen zur Kindersicherung im Bereich „Sicherheit“ oder „Elterneinstellungen“. Hier können Sie Profile für jedes Ihrer Kinder erstellen, spezifische Webseiten blockieren und Zeitlimits für die Internetnutzung festlegen. Als Beispiel hier die Kindersicherungsfunktionen für die weit verbreitete Fritz!Box. Sie bietet eine benutzerfreundliche Oberfläche unter der Adresse „fritz.box“, mit der Eltern Websites filtern, Zeitpläne erstellen und die Nutzung überwachen können. Durch die Aktivierung dieser Funktionen können Eltern sicherstellen, dass ihre Kinder nur auf altersgerechte Inhalte zugreifen. Dazu gehen Sie von der Startseite der Fritz!Box auf die Funktion „Internet“, dort finden Sie einen weiteren Menüpunkt „Filter“. Jetzt können Sie sogenannte Zugangsprofile einrichten. Diese Profile beinhalten Uhrzeiten, wann der Zugang erlaubt ist, ebenso können Sie Webseiten sperren, die nicht zugänglich sein sollen. Zum Beispiel „tiktok.com“. Die Fritz!Box bietet noch einen besonderen Service. In diesem Zugangsprofil können Sie automatisch alle Seiten sperren, die von der „Bundeszentrale für Kinder- und Jugendmedienschutz“ indiziert wurden. Also als ungeeignet eingestuft. Haben Sie ein solches Profil angelegt, speichern Sie es und weisen es dann dem Gerät Ihres Kindes auf der Filter-Seite zu. Neben den Router-basierten Lösungen gibt es auch zahlreiche Softwareoptionen, die auf den Geräten Ihrer Kinder installiert werden können. Diese Programme bieten oft erweiterte Funktionen, wie detaillierte Berichte über die Online-Aktivitäten, die Möglichkeit, bestimmte Anwendungen zu blockieren und Benachrichtigungen bei verdächtigen Aktivitäten. Ein Beispiel für solche Software ist „Norton Family“. Diese Anwendung ermöglicht es Eltern, die Online-Aktivitäten ihrer Kinder zu überwachen, unangemessene Inhalte zu blockieren und Bildschirmzeiten festzulegen. Ähnliche Programme wie „Kaspersky Safe Kids“ bieten ebenfalls umfassende Kindersicherungsfunktionen und sind einfach zu konfigurieren. Bedenken Sie nur das dies eine russische Software ist und das zur Zeit Krieg ist, was gegen deutsche Server eingesetzt werden könnte. Auf Android-Geräten können Eltern die App „Google Family Link“ verwenden. Diese App ermöglicht es, die Bildschirmzeit zu überwachen, Apps zu genehmigen oder zu blockieren und den Standort des Geräts zu verfolgen. Ähnlich bietet Apple mit „Screen Time“ auf iOS-Geräten eine Funktion, mit der Eltern Nutzungszeiten festlegen, bestimmte Inhalte blockieren und Aktivitäten überwachen können. Um diese Funktionen zu aktivieren, müssen Eltern die jeweilige App herunterladen und ein Konto mit Passwort erstellen. Nach der Einrichtung können sie die Geräte ihrer Kinder hinzufügen und die gewünschten Einstellungen vornehmen. Wenn Sie noch tiefer ins Thema einsteigen möchten, besuchen Sie einmal die Website „www.mimikama.org“. Dort finden Sie unter dem Suchwort „Kindersicherung“ noch weitere Artikel, wie Sie den Umgang mit dem Internet für Ihre Kinder sicherer gestalten können. Ebenso natürlich über die Website des Sicher-Stark-Teams. Lesen Sie auch unseren Artikel über Abenteuerland Internet. Lesen Sie den ganzen Artikel
0 notes