#Parse Outlook Message Files
Explore tagged Tumblr posts
Text
PST File Size Improvements & Enhanced Contacts Retrieval from Exchange Server using Java
What’s new in this release?
Aspose team is pleased to announce the new release of Aspose.Email for Java 17.8.0. This month’s release includes the same enhancements and improvements. Specifically, it provides complete support for working with Microsoft Exchange Server 2016 using EWS. It also supports conversion of email messages to HTML without embedding message resources in output file. Aspose team is glad to share that Aspose.Email for Java API now provides complete support for working with Microsoft Exchange Server 2016 using its EWS client. This was earlier limited by certain features where the API didn’t support the functionality completely. With this month’s release, users can now get benefit of working with all the functionality of Exchange Server 2016. Aspose.Email for Java API lets users convert messages to HTML. This month’s version further enhances this functionality by saving message resources (attachments, inline images, etc.) to user defined destination. This allows to save the message resources without embedding into the output html file. The main improved features & bug fixes added in this release are listed below
Ability to save images inside a message (as embedded image) as separate files next to html file while converting MSG to HTML
Add support Exchange 2016
Pop3Client connection - process not finishing.
Smtp functionality with System.Threading
Saving message from server as eml throws format exception
EML to MSG results in malformed output
PDF attachment can't be recognized from attachments
Attachments not recognized in MSG file
Timezone property for recurrence
Fetch PST properties PR_LAST_VERB_EXECUTED and PR_CALENDAR_MEETING_STATUS
Pop3.FetchMessage raises exception with FIPS compliant environment
Other most recent bug fixes are also included in this release.
Newly added documentation pages and articles
Some new tips and articles have now been added into Aspose.Email for Java documentation that may guide users briefly how to use Aspose.Email for performing different tasks like the followings.
Saving as HTML without Embedding Resources
Manage Conversation Items on Exchange Server
Overview:Aspose.Email for Java
Aspose.Email for Java is a Non-Graphical Java component that enables Java applications to read and write Microsoft Outlook documents without utilizing Microsoft Outlook. It enables developers to create new MSG file from scratch, update an existing MSG file, read Outlook MSG file & get it's properties like subject, body, recipients in to, cc and bcc, Adding or removing attachment, sender information and MAPI properties. Aspose.Email for Java can be used with Web as well asDesktop Application.
More about Aspose.Email for Java
Homepage of Oulook component Aspose.Email for Java
Download Aspose.Email for Java
Online documentation of Aspose.Email for Java
#PST File Size Improvements#Parse Outlook Message Files#retrieve Exchange Server contacts#EML to EMLx conversion#Reading multiple events#MSG with RTF body#Java email API
0 notes
Text
Become an Email Champion by Spending Less Time Dealing with Email

Email is important, but it seems to steal so much of your valuable time, doesn’t it?
Conquering your never-ending inbox can seem like a feat all in itself—let alone having it done before lunchtime. There’s an easier way, and when done properly, you’ll be able to spend less time sifting through your email and more time on the more important stuff. ________________________________________ Make Your Inbox Do the Work for You You’ve got better things to do than organizing and prioritizing your emails manually. Granted, you’ll still need to respond to important emails, but most email clients have everything you need to set up a system that automatically parses and sorts emails based on a whole slew of different factors. It will take a little time, and likely a few rounds of adjustments to get your inbox to work the way you want it to, but we’re going to show you the tools that will help get you there.
Most businesses either use Microsoft Outlook, or Google’s Gmail, so we’re going to cover these two email platforms. Gmail’s Labels and Filters If you use Gmail, there are two tools that you’ll want to get familiar with: Labels and Filters.
A label is exactly what it sounds like. Applying a label to an email will essentially categorize it. If you used to use Outlook in the past, think of these as Folders (we’ll get to Outlook next).
You can organize labels based on a wide variety of topics—maybe you have a label for each project you are working on, or a label for different types of correspondence (invoices, reports, employee evals, etc.). Organizing your email into labels makes it easier to pull up specific emails later without having to rely on searching for them. More than one label can be applied to any particular email.
To create a label, just select Create new label in the sidebar (hidden under the More link) in Gmail or select the Tag Icon Box that appears when an email is selected. You’ll be able to select any labels you already have or create a new one. You’ll also be able to color-code each label.
But remember, we want to save time, so instead of having to manually move emails to a label, you can create filters to automatically apply labels to certain types of messages. Once you have some labels created, go to Settings, and click the Filters and Blocked Addresses tab. Once there, select Create a new filter.
You can also start this process by doing a Search from the top of your Gmail. Click the little dropdown arrow in the search box at the top of your email, and you can fill out the form to search for specific emails. You can create filters based on who the email is from, what email address the email is sent to, the subject line, words within the email, and more.
If I wanted to send all correspondence from Bob to a certain label, I’d just put his email in the To: line and click Create Filter. Then Gmail will allow me to choose what to do to all emails from Bob. I could star it to make it stand out, apply a label, or a variety of other options. Microsoft Outlook’s Rules and Folders Microsoft Outlook’s process is pretty similar. Instead of filters and labels, Microsoft calls them rules and folders. Here are the steps to set up new rules:
● Right-click the message and select Rules, then, select Create Rule. ● Then you need to select the conditions that activate the rule, and what that means. ● Make sure you select Run this new rule now on messages already in the current folder (if you wish) and click OK to finalize your rule.
This means that you will need to have a folder to file these messages in. While the option will be presented to you as you create a rule, you can also set up your folders separately in advance.
● In the Mail pane, right-click where you want to add your folder and select New Folder… from the menu that appears. ● Name your folder, and press Enter.
It takes time to build all of the rules (or filters) you need to streamline your inbox, but it will ultimately save you hours of time that would otherwise be wasted sifting through your inbox by hand. It’s all about becoming more efficient!
For more tips and tricks, bookmark our blog, and if you need help with your technology, give us a call at 800.394.2301.
https://www.infradapt.com/news/become-an-email-champion-by-spending-less-time-dealing-with-email/
0 notes
Text
Office Insider for Windows Version 2007 release notes

Office Insider for Windows Version 2007 release notes.
Build 13001.20002 (June 5, 2020)
Excel
Sheet View You can now sort and filter your Excel file while collaborating with others with Sheet View. This new feature prevents you from being impacted by other user’s sorts and filters while coauthoring the document. Create PivotTables from Datasets in Power BI You can create PivotTables in Excel that are connected to datasets stored in Power BI with a few clicks. Doing this allows you get the best of both PivotTables and Power BI. Calculate, summarize, and analyze your data with PivotTables from your secure Power BI datasets. Learn more. Notable fixes: We fixed an issue where custom values on the chart axis would not get applied correctly.We fixed an issue where worksheets containing multiple formulas with defined names was resulting in longer times when saving files.
Outlook
Quickly reopen items from previous session We added an option to quickly reopen items from a previous Outlook session. Whether Outlook crashes or you close it, you’ll now be able to quickly relaunch items when you reopen the app. This feature is on by default. To turn it off, go to Options > General > Start up Options.

Notable fixes: We fixed an issue where the IME (Input Method Editor) window would overlap the underlying text being entered via the IME when using multiple monitors with different resolutions.We fixed an issue where viewing a template when composing a new email message would result in a crash.We fixed an issue where users were unable to Exchange 2010 public folders after Outlook version 1911.We fixed an issue where the Categorize button for group calendars in the Office Ribbon was disabled.We fixed an issue that caused users to experience a crash in Outlook when working with hyperlinks in plain text emails.We fixed an issue that caused Outlook to be unable to parse long file names encoded with RFC2231.We fixed an issue that was causing Outlook users to experience intermittent hangs when using screen readers.We fixed an issue that resulted in the Online Archive dropdown in folder properties to be missing for users on high DPI monitors.We fixed an issue that would cause users with conflicting contacts to experience crashes in Outlook.
Word
Notable fixes: We fixed an issue where timestamps in Comment panes were not based on the system locale time.We fixed an issue where comments between the web app and the desktop application were not in sync.
PowerPoint
Notable fixes: We fixed an issue where the slide editor from one slide would overlap on to the next slide.We fixed an issue where a Comment pane that had been closed by the user would re-open automatically.We fixed an issue where PowerPoint files with embedded charts/workbooks could result in failures when saving the file.We fixed an issue with opening files from server-configured with Forms-based authentication.
Project
Notable fixes: We fixed an issue that prevented orphaned tasks from being deleted or reassigned after the parent plan was deleted. Read the full article
#MicrosoftAccess#MicrosoftExcel#MicrosoftOffice365#MicrosoftOfficeInsider#MicrosoftOneDrive#MicrosoftOneNote#MicrosoftOutlook#MicrosoftPowerPoint#MicrosoftProject#MicrosoftPublisher#MicrosoftSharePoint#MicrosoftVisio#MicrosoftWord#OfficeProPlus#Windows#Windows10
0 notes
Text
Stellar Converter for OST - Review, Test-Drive and Benchmarks

In this post we'll take an extensive look at Stellar Converter for OST, a powerful recovery software that can be used to convert inaccessible OST files into accessible Outlook PST files. Truth to be told, it's not the first time we're talking about it: we already mentioned Stellar Utilities, and more precisely their MS Exchange EDB Recovery Tool, in this post. In this article we're going to talk about MS Outlook, which is currently the #4 most used e-mail client:

Source: emailclientmarketshare.com, November 2019
OST and PST, aka MS Outlook data files
When you add an e-mail account to Outlook, a local copy of all the e-mail message you download is stored on your computer: this feature allows you to access your previously downloaded or synchronized email messages, calendar information, contacts, and tasks without an internet connection. Now, certain types of accounts, such as POP accounts, store their information in Outlook Data Files, which are stored on the filesystem with the .pst extension: those are the PST files. Other types of accounts, such as Outlook 365 accounts, Exchange accounts, IMAP accounts, and Outlook.com accounts store their information in Offline Outlook Data Files, which are stored with the .ost file extension: those are the OST files. Let's now briefly review the most relevant differences between these two formats. Outlook Data File (PST) An Outlook Data File (PST) contains your messages and other Outlook items and is saved on your computer. Outlook Data Files can also be used to backup or export items from any type of email account, or to import email messages, calendar, contact, and task data from another Outlook Data File. Because these files are saved on our computer, they aren’t subject to mailbox size limits on a mail server; this means that, by moving items to an Outlook Data File (.pst) on our computer, we can free up storage space in the mailbox on our mail server. However, this also means that those items will only be available on the computer where the file is saved. Offline Outlook Data File (OST) Most other account types, such as IMAP accounts, Office 365 accounts, Exchange accounts, and Outlook.com accounts use an Offline Outlook Data File (OST) file to store a synchronized copy of our mailbox information on our local computer. When our connection to the mail server is interrupted, for example, when we're on an airplane without WiFi or if your internet connection disconnects, we can still access all emails, calendar data, contacts, and tasks that have been previously downloaded. This means that we can read and compose messages, create appointments, and add contacts: however, if we're offline, our email messages won't be sent and no new messages will be downloaded until our internet connection is restored. When the connection is restored, changes are automatically synchronized, and the folders and items on the server and on our computer will be identical again in a matter of seconds (or so, depending on our connection speed).
Stellar Converter for OST
Stellar Converter for OST is a conversion tool able to convert all OST mailbox items – emails, attachments, contacts, calendars & deleted items - and extracts them as PST while retaining their overall structure. The resulting PST file will be an exact replica of the mailbox data that user would have access to in normal conditions when her OST could be synchronized with Exchange. The conversion speed is also relatively fast: from our tests with an average i3 desktop machine, the software took approximately 40 minutes to convert a 5GB OST into a PST (8 minutes per GB). Such performances arguably make this tool the fastest converter available on the market nowadays, at least according to these official benchmarks. Its main features include: Search and save individual emails within the same OST file Converts encrypted OST files into PST files. Also works on IMAP OST files Converts large OST files to PST - No file size limitation Free OST to PST conversion for first 20 emails per folder Easily exports OST file to Office 365 & Live Exchange (Tech version only) Converts multiple OST files to PST format (Tech version only)
Common usage scenarios
Being able to convert our e-mail data from OST to PST files is not a everyday task by any means, but it can be very important in some specific scenarios, such as the following ones.

Stellar Converter for OST - initial screen Inaccessible or Orphaned OST File It’s common for IT administrators to come across situations like Exchange Server crash or mailbox synchronization problems which make OST file inaccessible or orphan. Likewise, a user’s desktop may fail to boot due to hardware problem or malware infection, or the storage drive containing OST file may have large number of bad sectors. The outcome of these situations is an inaccessible OST, with risk of losing mailbox data such as emails, attachments, contacts, etc. Stellar Converter for OST converts inaccessible OST file & extracts mailbox data in PST file. Migration to New Email Service When you migrate to a new email service or platform, it’s a challenge to gain access to the mailbox data stored in OST files of user accounts configured with older email service. This becomes a critical situation when there’s no PST backup of these OST files. In this case, you would lose the mailbox data stored in such OST files unless you convert the OST to an accessible format like PST. Our OST to PST converter software converts inaccessible OST file and extracts complete mailbox data - emails, attachments, contacts, notes, etc. - in PST format. Migration to a New Computer The OST file is local cache of the user’s Exchange mailbox, which can’t be directly imported in Outlook or opened on any another system. So when you change over to a new computer, the data stored in the OST will be lost unless you find a way to extract the OST data in a format like PST which can then be opened in Outlook client installed on the new machine or anywhere else. The OST PST conversion tool serves as a powerful software to convert OST file and extract the mailbox data in PST format. The software ensures that complete mailbox data is extracted Difficulties with Using Outlook Import/Export Wizard Outlook built-in Import/Export Wizard is an amazing utility for migrating OST data to PST format. But the tool requires users to have considerable technical proficiency and spend time to get the expected results. It also needs the same original Exchange account for this task, and you cannot convert inaccessible OST files with the help of Import/Export Wizard. Stellar Converter for OST software provides an easy and fast way to convert the OST file into PST via a rich Graphical User Interface. The OST PST conversion tool extracts OST data with 100% precision and original integrity.
Basic Features Breakdown
Here's a detailed features breakdown for all versions of the Stellar Converter for OST tool: Extracts Mailbox Items from Inaccessible OST to PST There could be several situations when you may need to export the data from OST file to PST format. These could include inaccessible OST file, organization migrating to another email platform, user changing over to a new system, and more. OST PST converter quickly extracts mailbox data from inaccessible OST file and saves it in a fresh PST which can be imported in Outlook to restore mailbox access. It extracts all mailbox items including emails, attachments, contacts, calendars & deleted items. See steps to convert OST file into PST using Stellar Converter for OST. Extracts Exchange Objects from OST with High Precision The OST PST Converter Software extracts all Exchange mailbox objects such as emails, contacts, attachments, notes, journals, calendar entries, etc. from OST files and saves them in PST format. The tool performs 100% precise OST 2 PST conversion, and maintains original integrity of mailbox items. Its advanced scan engine parses OST files of any size (no file size limitation) and extracts complete mailbox data including emails, attachments, contacts, and calendars. The software offers administrators most precise OST conversion at speed, So, it offers administrators the best of precision & speed, thereby freeing up their valuable time & efforts for more strategic projects.

After being performed, OST scans can be saved and then retrieved for later use Converts OST Data in Multiple File Formats The Powerful OST to PST Converter Software also provides the option to search and save individual email messages from within OST files. In case you do not have time or do not wish to convert all OST items to PST, you can choose specific email messages to be extracted from the OST based on various parameters such as 'To', 'From', 'Subject', and 'Date' and convert them into a variety of formats including MSG, EML, RTF, HTML, and PDF formats. This feature lends this tool a high degree of flexibility, making it stand above its competition. Organizes Mailbox Messages to Improve Readability The OST PST Converter Software extracts mailbox data in an organized manner while maintaining the original format and arrangement of items. Once OST scanning is completed and all recoverable items have been discovered, the product allows you to sort and organize your email messages by Date, From, To, Subject, Type, Attachment, Importance, etc. Additionally, it lets you improve scan result readability by allowing you to segregate emails in groups by using a convenient “Show in Groups” feature. Outlook-Like GUI for Seamless OST Conversion The software is equipped with a familiar Outlook-like GUI that makes working with it a breeze. Helpful instructions and proper labeling of tasks and buttons at every step simplify & enrich the experience for all users. Smart preview of objects before conversion, choice to save converted data at any desired location on the system or network, multiple formats to save individual mail messages, etc. make OST to PST Converter software one of the best tools in its category. Conversion of Encrypted OST file Users encrypt OST file to keep their important information secure from unauthorized access. Sometimes you may experience an error that it is not an Outlook Data file when trying to open encrypted OST file. In such situation, you may lose access to the data stored on your encrypted OST file. To overcome such issues, you would need to convert the encrypted OST file to PST format. OST converter tool converts encrypted OST file to PST and regain access of mailbox data. Free OST to PST Converter The converter tool allows free OST file to PST file Conversion for 20 emails per folder. All you need to do is download the Free version of the software and scan your OST Files. After scanning, the software shows the preview of converted OST file & supports free conversion for only OST to PST file format. To save free 20 emails per folder, just click on ‘Save converted file’ button & the converted OST file will be saved at your specified location. Wide Compatibility with Microsoft Office One of the highlights of this tool is its compatibility with a number of MS Office versions. It supports MS Office 2019, 2016, 2013 (32 bit version and 64 bit versions), MS Office 2010 (32 bit and 64 bit versions) / 2007 / 2003 / 2002 (XP) / 2000. OST Conversion at Your Pace & Convenience The software allows to save the scanned information as a DAT file which can be loaded anytime later to reinstate OST to PST conversion process. Through this feature, users can split the scan and preview instances in the process, and save the mailbox in PST without the need to repeat the scanning process. This is particularly used when a user is too busy to carry out the whole operation at one-go; furthermore, DAT file ensures that time is not wasted in repeat scanning of the same data.
Technician Edition Features Breakdown
These advanced features are only available in the Stellar Converter for OST - Technician Edition and are specifically designed for System Administrators that frequently work with OST files. Batch conversion Module Batch Conversion procedure involves selection of multiple OST files and their subsequent conversion into PST files through a single process. This option to save the corresponding PST at the same location helps in tracing the PST files with ease. An option to save PST file at preferred (user-specified) location is also available. All OST files can be directly converted into PST files or it can be done by splitting the PST files on the basis of either “Split by Date” or “Split by Size” option. Exports Mailbox Data from OST to Office 365 Migration to Office 365 is easier with this software as it can directly export the OST to PST converted files to Office 365. All you need to have is Office 365 account with valid login credentials. This software relieves you from the lengthy and time-taking mailbox migration procedure. Splits and Compacts Large PST Files The Software provides two advanced options for newly created PST file: Split & Compact. To compress the converted PST file, you just need to click on “Compact & Save PST” option, and it decreases the size of PST file in the disk. The ‘Split’ feature is helpful if you have a bigger PST file and you want to split it into smaller PSTs to reduce the possibilities of PST file corruption.
Software Download
Stellar Converter for OST can be downloaded from the official site at the following URLs: Stellar Converter for OST - Basic edition - $99 retail price (free download available) Stellar Converter for OST - Technician edition - $299 retail price, available at $249 with a discount (free demo available) The Basic Edition Free Download enables you to preview the converted file and save 20 items per folder; the Technician Edition Free Demo allows you to check preview all the mail items & save 20 items per folder. Other Downloads Stellar Converter for OST - User Manual Stellar Converter for OST - Installation Guide
About Stellar Data Recovery
Stellar Data Recovery (formerly Stellar Phoenix, now simply known as Stellar) is a leading data care corporation based in India, with presence in the US and Europe. It's a ISO 9001 & ISO 27001 certified organization specializes in Data Recovery, Data Erasure, Mailbox Conversion, and File Repair software and services. Over the past 25 years, the company has consistently organized their resources and efforts around developing innovative, future-ready solutions that are unrivalled on capability and built with the core purpose of enabling comprehensive data care for users in the consumers and enterprise segments.
Conclusion
We tested Stellar Data Recovery for OST against a single MS Outlook OST file containing roughly 5GB of e-mail messages from a MS Exchange Online account and it successfully performed the task of converting them out to PST in less than 40 minutes with flawless results: all in all we were very happy of what we've seen and can't but recommend it to anyone - from MS Outlook users to System Administrators - who needs to perform these kind of conversions. Read the full article
#EMail#MSExchange#MSOutlook#OST#OutlookDataFile#PST#Stellar#StellarConverter#StellarDataRecovery#StellarPhoenix
0 notes
Text
Something awesome 3
Week 3 - Worms
Blog
What is a worm?
Although computer worms are one of the most common types of malware, they are one of the most ill-defined concepts in Network Security. There is still no universal consensus on the definition of the worm. Usually worms and viruses display similar characteristics and their intention is also similar. These are some key characteristics I could find around the internet that defined a worm and differentiated it from a virus.
A computer worm is a standalone malware computer program that replicates itself in order to spread to other computers. Often, it uses a computer network to spread itself, relying on security failures on the target computer to access it.
Many worms are designed only to spread, and do not attempt to change the systems they pass through. However, as the Morris worm and Mydoom showed, even these “payload-free” worms can cause major disruption by increasing network traffic and other unintended effects. Worms almost always cause at least some harm to the network, whereas viruses almost always corrupt or modify files on a targeted computer.
Computer worms are classified as a type of computer virus, but there are several characteristics that distinguish computer worms from regular viruses. A major difference is the fact that viruses spread through human activity (running a program, opening a file, etc) while computer worms have the ability to spread automatically without human initiation. In addition to being able to spread unassisted, computer worms have the ability to self-replicate. This means that worms can create multiple copies of themselves to send to other computers. This often happens through the sending of mass emails to infected users’ email contacts.
Any code designed to do more than spread the worm is typically referred to as the “payload”. Typical malicious payloads might delete files on a host system (e.g., the ExploreZip worm), encrypt files in a ransomware attack, or exfiltrate data such as confidential documents or passwords.
Probably the most common payload for worms is to install a backdoor. This allows the computer to be remotely controlled by the worm author as a “zombie”. Networks of such machines are often referred to as botnets and are very commonly used for a range of malicious purposes, including sending spam or performing DoS attacks
Phases of a worm
Phases of a worm are pretty much the same as that of a virus.
ILOVEYOU
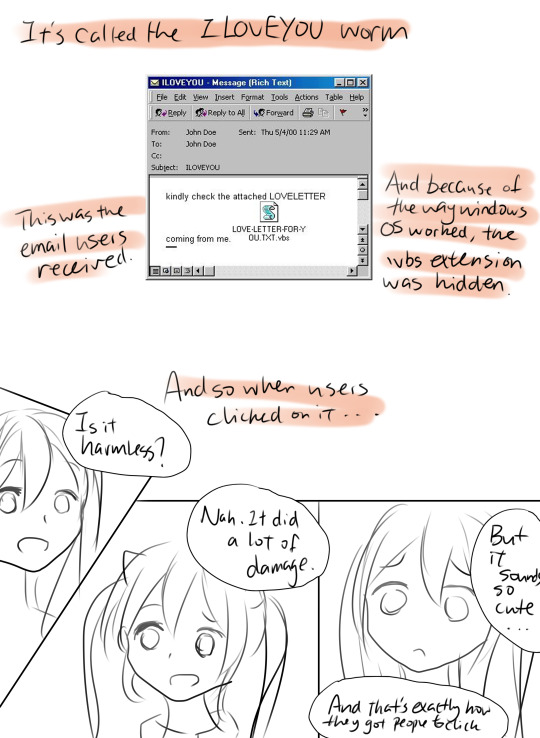
ILOVEYOU, sometimes referred to as Love Bug or Love pak, is a computer worm that attacked tens of millions of Windows personal computers on and after 5 May 2000.
The ILOVEYOU worm initially travelled the Internet by e-mail. The subject of the e-mail said that the message was a love letter from a secret admirer. An attachment in the e-mail was what caused all the trouble. The original worm had the file name of LOVE-LETTER-FOR-YOU.TXT.vbs. when the users opened this attachment,
· It copied itself several times and hid the copies in several folders on the victim’s hard drive.
· It added new files to the victim’s registry keys.
· It replaced several different kinds of files with copies of itself.
· It searched all the drives connected to the host for all files with extensions *.JPG, *.JPEG, *.VBS, *.VBE, *.JS, *.JSE, *.CSS, *.WSH, *.SCT, *.DOC *.HTA, *.MP3, *.MP2 and rename them to .VBS.
· It sent itself through Internet Relay Chat clients as well as e-mail.
· It downloaded a file called WIN-BUGSFIX.EXE from the Internet and executed it. Rather than fix bugs, this program was a password-stealing application that e-mailed secret information to the hacker’s e-mail address.
ILOVEYOU was the first worm to take the cost of damage to billions of USD. An estimated damage caused by this worm was between 5 and 10 billion USD. The worm propagated across the network by using the addresses present in the address book of the user. Since the worm activated immediately and also on restart of the PC, the amount of email it generated crippled many mail servers and also individual PCs. The worm was allegedly authored by Irene, Onel de Guzman and Reomel Lamores from Philippines.
Stuxnet
Stuxnet is a malicious computer worm, first uncovered in 2010, thought to have been in development since at least 2005. Stuxnet targets SCADA systems and is believed to be responsible for causing substantial damage to Iran’s nuclear program. Although neither country has openly admitted responsibility, the worm is believed to be a jointly built American/Israeli cyberweapon.
Its purpose was not just to infect PCs but to cause real-world physical effects. Specifically, it targets centrifuges used to produce the enriched uranium that powers nuclear weapons and reactors.
Stuxnet has three modules: a worm that executes all routines related to the main payload of the attack; a link file that automatically executes the propagated copies of the worm; and a rootkit component responsible for hiding all malicious files and processes, preventing detection of the presence of Stuxnet.
1. Getting onto the network
· Probably arrived at Iran’s nuclear plant Natanz via infected USB
· Not sure if it was an insider attack, or inserted unknowingly, but someone had to physically plug the USB into a computer attacked to the network for the worm to upload itself onto the plant’s computer system.
2. Spreading through the computers
· The worm then propagates across the network, scanning for Siemens Step7 software on computers controlling a centrifuge. In the absence of either criterion, Stuxnet becomes dormant inside the computer.
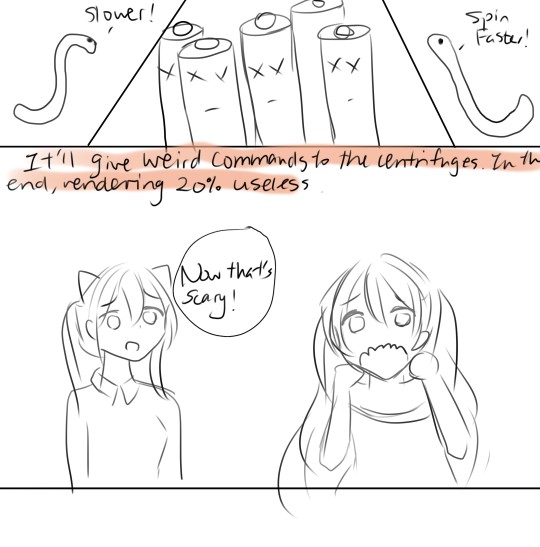
3. Re-programming centrifuges
· If both the conditions are fulfilled, Stuxnet introduces the infected rootkit onto the centrifuge and Step7 software, modifying the code and giving unexpected commands to the centrifuge while returning a loop of normal operations system values feedback to the users.
· It carried out 2 separate attacks
o Making centrifuges spin dangerously fast for about 15 mins before returning to normal speed
o About a month later, slows the centrifuges down for around 50 minutes
o This was repeated for several months
Over time, the strain from the excessive speeds caused infected machines to disintegrate.
It is reported that Iran decommissioned around 20 per cent of its centrifuges in the Natanz plant during the attack.
Reflection
What techniques do worms usually employ to attack?
Worms spread by exploiting vulnerabilities in operating systems as well as exploiting humans through social engineering. Some common vulnerabilities exploited include zero-day attacks.
How can we combat these?
Users need to be wary of opening unexpected email, and should not run attached files or programs, or visit web sites that are linked to such emails. However, as with the ILOVEYOU worm, and with the increased growth and efficiency of phishing attacks, it remains possible to trick the end-user into running malicious code.
Anti-virus and anti-spyware software are helpful but must be kept up to date with new pattern files at least every few days. The use of a firewall is also recommended.
Users can minimize the threat posed by worms by keeping their computers’ operating system and other software up to date, avoiding opening unrecognized or unexpected emails and running firewall and antivirus software.
What did ILOVEYOU exploit?
On the machine system level, ILOVEYOU relied on the scripting engine system setting (which runs scripting language files such as .vbs files) being enabled and took advantage of a feature in Windows that hid file extensions by default, which malware authors would use as an exploit. Windows would parse file names from right to left, stopping at the first period character, showing only those elements to the left of this. The attachment, which had two periods, could thus display the inner fake “txt” file extension. Text files are considered to be innocuous, as they are normally incapable of running executable code. The worm used social engineering to entice users to open the attachment (out of actual desire to connect or simple curiosity) to ensure continued propagation. Systemic weaknesses in the design of Microsoft Outlook and Microsoft Windows were exploited that allowed malicious code capable of complete access to the operating system, secondary storage, and system and user data simply by unwitting users clicking on an icon.
What did stuxnet exploit?
Stuxnet specifically targets programmable logic controllers (PLCs), which allow the automation of electromechanical processes such as those used to control machinery and industrial processes including centrifuges for separating nuclear material. Stuxnet also exploited four zero-day flaws.
What was it back then that made this attack possible?
Since there were no laws in the Philippines against writing malware at the time, both Ramones and de Guzman were released with all charges dropped by state prosecutors. To address this legislative deficiency, the Philippine Congress enacted Republic Act No. 8792, otherwise known as the E-Commerce Law, in July 2000, just two months after the worm outbreak. As of 2012, the ILOVEYOU virus was regarded as the tenth-most virulent computer virus.
What do we have nowadays that is making this attack hard/still possible?
Worms are still very destructive to this day due to the fact that users need not to do anything for their device to be infected by the malware. However, in the April–June 2008 issue of IEEE Transactions on Dependable and Secure Computing, computer scientists described a new and potentially effective way to combat internet worms. The researchers discovered how to contain worms that scanned the Internet randomly, looking for vulnerable hosts to infect. They found that the key was to use software to monitor the number of scans that machines on a network send out. When a machine started to send out too many scans, it was a sign that it has been infected, which allowed administrators to take it offline and check it for malware. In addition, machine learning techniques can be used to detect new worms, by analysing the behaviour of the suspected computer.
Also, vulnerabilities that were exploited by the ILOVEYOU and Stuxnet worm such as the hiding of extensions and other zero-day flaws have since then been fixed, meaning that a similar attack is hard to occur again, and even if it does, would not be on such a large scale.
On the other hand, both the ILOVEYOU and Stuxnet employed some form of social engineering, in ILOVEYOU’s case, exploited human curiosity, and in Stuxnet’s case, most likely used an insider attack. Unlike bugs and vulnerabilities, this form of attack is very hard to prevent against and is still very much prevalent. In fact, most malwares employ this tactic to this day.
Comics





1 note
·
View note
Text
Original Post from Trend Micro Author: Trend Micro
by Jaromir Horejsi and Daniel Lunghi (Threat Researchers)
We observed a recent campaign that primarily targets financial institutions and governmental organizations in the South American region, particularly in Colombia. This blog post covers the activities we observed, the remote access tools (RATs) used, the campaign’s techniques and procedures, and its indicators of compromise (IoCs). Our findings indicate that the campaign appears to be the work of a group involved in business email compromise (BEC) or cybercrime, and unlikely to be an advanced persistent threat (APT).
It’s worth noting that the group uses YOPmail, a disposable email address service, for its command and control server (C&C). The payload, written in Visual Basic 6, is a customized version of a remote access tool called “Proyecto RAT.” Our in-depth analysis of the malware is detailed in this appendix.
The delivery emails
The infection starts with an email sent to a target, as seen in the screenshot below (Figure 1). In multiple instances, we noticed the attacker used open or compromised mail servers in South America to facilitate the campaigns. The attacker also connected to the compromised servers from IP addresses that were linked to dynamic domain names used as C&Cs by the delivered payloads. This suggests that the attacker uses the same infrastructure to send emails and control victims.
The sender of the email is usually spoofed, and we saw multiple email subjects enticing the receiver to open the attachment, which is an RTF file. Examples of such subjects are:
“Hemos iniciado un proceso en su contra por violencia laboral.” (Loosely translates to “We have filed a lawsuit against you for workplace violence.”)
“Se hara efectivo un embargo a su(s) cuenta(s) Bancarias.” (Loosely translates to “Your banking accounts are going to be blocked.”)
“Almacenes exito te obsequia una tarjeta regalo virtual por valor de $500.000.” (Loosely translates to “Exito shops offer you a virtual gift worth $500.000.”)
Figure 1. Delivery email
The attached RTF file contains one line of text and a link. The text relates to the email subject, such as “You can see the complaint against you below.” or “See the complaint online.” Note that the link to the malware uses the URL shortener cort.as, which belongs to the El País newspaper. Unfortunately, this service only enables statistics on demand, and the attacker never enabled them.
Figure 2. RTF document attached to the delivery email
Figure 3. URL shortener cort.as
Clicking on the link redirects the victim to a file on a file-sharing service. The file is a delivery document that contains macros.
Figure 4. Shortened URL redirects to a file hosted on a cloud file-sharing service
The delivery documents
The majority of the documents we analyzed were in MHTML format, which contains macros. The macro code is a simple downloader for the payload. However, Office files in OLE format were also observed. Most of the document designs have already been published in Qihoo360’s blog post; this post will discuss designs that the post did not cover. The documents, which appeared between 2017 and 2019, all asked users to enable macros. The macros will download and execute a RAT.
Figure 5. Delivery document purports to come from Migración Colombia, a government website for the Colombian migration authority
Figure 6. Delivery document purports to come from DataCrédito, a service that allows access to credit history and profile
Figure 7. Delivery document with a generic Adobe Flash Player Installer
First stage payload: Remote Access Tool (RAT)
The main payload is usually Imminent Monitor RAT; however, at the beginning of 2018, we also observed the use of LuminosityLink RAT, NetWire RAT, and NjRAT. In a case in June 2019, we also noticed Warzone RAT being used. Warzone RAT is the newer RAT from the list and supports keylogger, web browser-, and Outlook password-stealing features in addition to standard RAT functions.
All of these RATs are standard malware that can be bought for under US$100 or downloaded from various malware repositories.
After the download of Imminent Monitor RAT and observing its network behavior, we noticed an instruction to download and execute another executable file, which is the second stage payload.
Figure 8. Imminent Monitor RAT traffic
Second stage payload: Proyecto RAT
The second stage payload is written in Visual Basic 6, and has an interesting feature — a C&C URL address acquired from the disposable email service YOPmail. The malware connects to a mailbox, reads the only available email message, parses it, and then extracts the subject of the email. The C&C server URL is between the ‘¡’ characters (upside-down exclamation sign), a character used in the Spanish language. This is the first time we noticed disposable email services being abused this way.
Figure 9. A disposable email with C&C address and email subject
During our analysis, we found three mailboxes related to the malware. We have since reached out to YOPmail and informed them of this threat. YOPmail has responded, saying that they would place specific restrictions.
A detailed technical analysis of the classes, forms, and modules revealed when the malware is decompiled can be found in this appendix.
Searching for the malware family
Seeing the many features of the malware, we tried to match it to a known RAT.
The communication between client and server is via TCP, is unencrypted, and uses pipe “|” characters and “¡@#@!” as a separator. This description fits quite well with Xpert RAT. Searching for the x86 hex string from cTimer class also leads to links with Xpert RAT. This tweet from a malware researcher even mentions Xpert RAT.
An online search found two versions of Xpert RAT were found: “XpertRAT v3.0.10 By Abronsius” and “XpertRAT v3.0.9 By Abronsius”. After building the payload and infecting the test machine, we could observe the communication in figure 10. Notice the different colors between the incoming and outgoing communication and the separator between both communication streams. However, in Xpert RAT builder, we did not notice any reference to a disposable email, searches for banking website captions, or information written to the configuration file. In addition, Xpert RAT samples generated by the builder have even more functions such as keylogger, runPE, WebCam, Audio, Wipe module, and Remote Desktop.
Figure 10. Original Xpert RAT communication snippet
It seems that the aforementioned Visual Basic malware is an old and limited version of the Xpert RAT — either a custom modification of Xpert RAT or a malware with source code based on Xpert RAT’s.
Figure 11. Xpert RAT builder
Figure 12. Functions available to an Xpert RAT operator
When searching for class names from the Visual Basic malware, the keyword “ClsRemoteRegistry” leads to a discussion on a Spanish hacking forum (Figure 13). The user, who in his profile offers Prodigy Bot, an IRC bot written in VB6, has a question related to the code from Leandro Ascierto’s project called “Proyecto RAT.”
Figure 13. Discussion about ClsRemoteRegisty class on a hacking forum
After downloading and examining the project, we noticed familiar class names, delimiters, strings, and more.
Figure 14. Proyecto RAT website
Figure 15. Familiar class, form, and module names
Figure 16. Several delimiters used by Proyecto RAT, file ClsRemoteRegistry.cls
Figure 17. Hex code from cTimer class, with original comments in German, because this code was taken from a different project
Based on these details, we believe this is a customized version of Proyecto RAT.
Affected regions and verticals
Colombia is by far the most targeted country, with other South American countries added to the list. This is consistent with the fact that this actor uses the Spanish language in all the spear phishing documents we observed. However, we also noticed targets in other countries:
Figure 18. The regions targeted by the spear-phishing documents
In one instance, the attacker used the URL shortener bit.ly, which confirmed that Colombia is the main target. As anyone can follow the link, some of these countries could also be the result of researchers’ sandboxes.
Figure 19. Clicks and locations related to the bit.ly link
Recent campaigns targeted different industries. The most prevalent were government entities, healthcare/pharmaceutical institutions, followed by financial/banking/insurance and agro-industry/food/packaging organizations.
Notably, we noticed that multiple employee savings funds (called “Fondo de empleados” in Colombia) were targeted. These entities barely have access to sensitive information, but they are likely to possess a reasonable amount of money.
Conclusion and mitigation
Xpert RAT reportedly first appeared in 2011. The first version of “Proyecto RAT” was published at the end of 2010. Both projects share similarities, and it is likely that “Proyecto RAT” was inspiration for Xpert RAT and at least a few more malware projects, including the Visual Basic malware in the campaign we previously described.
We can’t say for sure what this actor is particularly looking for, but multiple facts lead us to believe it is designed for BEC or cybercrime rather than as an APT:
These campaigns are noisier and more prevalent than usual APT campaigns.
The same IP address, which is dynamic, is used to send spear-phishing emails and act as C&C. This is more common to cybercrime.
Some of the targeted industries might not have access to sensitive information, but are likely to handle a decent amount of money.
The windows titles that are listed in the configuration file are almost all related to financial services.
Our research shows that this campaign can deliver malware with multiple capabilities that can affect different organizations and industries. It also highlights the importance of securing online infrastructures, particularly the email gateways, to avoid targeted spam campaigns. Organizations should adopt best practices on messaging-related threats and regularly update systems to prevent attackers from taking advantage of any security gaps. Employing additional security mechanisms such as enabling firewalls and intrusion detection and prevention systems will help prevent suspicious network activities that may lead to data exfiltration or C&C communication.
Organizations can also turn to Trend Micro endpoint solutions such as Trend Micro Smart Protection Suites and Worry-Free Business Security. Both solutions can protect users and businesses from threats by detecting malicious files and spammed messages as well as blocking all related malicious URLs. Trend Micro Deep Discovery has an email inspection layer that can protect enterprises by detecting malicious attachments and URLs.
Trend Micro Hosted Email Security is a no-maintenance cloud solution that delivers continuously updated protection to stop spam, malware, spear phishing, ransomware, and advanced targeted attacks before they reach the network. It protects Microsoft Exchange, Microsoft Office 365, Google Apps, and other hosted and on-premises email solutions.
Our technical analysis of the malware, IoCs, and other spam email samples related to the campaign can be found in this appendix.
The post Spam Campaign Targets Colombian Entities with Custom-made ‘Proyecto RAT,’ Uses Email Service YOPmail for C&C appeared first on .
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Trend Micro Spam Campaign Targets Colombian Entities with Custom-made ‘Proyecto RAT,’ Uses Email Service YOPmail for C&C Original Post from Trend Micro Author: Trend Micro by Jaromir Horejsi and Daniel Lunghi (Threat Researchers)
0 notes
Text
Using Gmail with OAUTH2 in Linux and on an ESP8266
One of the tasks I dread is configuring a web server to send email correctly via Gmail. The simplest way of sending emails is SMTP, and there are a number of scripts out there that provide a simple method to send mail that way with a minimum of configuration. There’s even PHP mail(), although it’s less than reliable.
Out of the box, Gmail requires OAUTH2 for authentication and to share user data, which has the major advantage of not requiring that you store your username and password in the application that requires access to your account. While they have an ‘allow less secure apps’ option that allows SMTP access for legacy products like Microsoft Outlook, it just doesn’t seem like the right way forward. Google documents how to interact with their API with OAUTH2, so why not just use that instead of putting my username and password in plaintext in a bunch of prototypes and test scripts?
Those are the thoughts that run through my head every time this comes up for a project, and each time I’ve somehow forgotten the steps to do it, also forgotten to write it down, and end up wasting quite a bit of time due to my own foolishness. As penance, I’ve decided to document the process and share it with all of you, and then also make it work on an ESP8266 board running the Arduino development environment.
Before we continue, now would be a good time for a non-technical refresher on how OAUTH works. The main differences between OAUTH and OAUTH2 are that the latter requires HTTPS, and the access tokens that allow an application to use specific services in a user account have an expiry.
To use Gmail with OAUTH2, we will need to start with five things: An application registered in the Google APIs, its client ID and client secret, a computer running LAMP (a by-the-hour VPS works just fine here), and a domain name that points to it.
Registering an application with Google API is easy. Go to the Google API console, log in, create a new project, and enter it. Enable the Gmail API; it should be suggested on the front page.
With the project created and the Gmail API enabled, the dashboard should look something like this
Then click on ‘credentials’ on the sidebar, create credentials, and finally ‘create OAUTH Client ID’. Before you can continue, you need to create a consent screen. The only entry you really need to fill out at this time is ‘Product Name Shown to Users’.
After saving that form, select ‘Web Application’ as your application type. Note the field called ‘Authorized redirect URIs’, we’ll return to it later. It’s important that it be correctly set for us to be able to receive a refresh token later on in this process.
For now, just press ‘Create’. A pop-up will display containing your Client ID and Client secret. You’ll need them soon, so best to copy/paste them into a local file on your computer for now.
Next, we will use those two pieces of data to request an access token and refresh token. We may as well accomplish two things at the same time here by installing the popular PHP email sender called PHPMailer on our web server. It includes a tool to request an OAUTH2 access/refresh token as well as being easily capable of sending a quick test email. To install it, we’ll use the Composer PHP dependency management tool:
$sudo apt-get install composer
Then we should navigate to our web-accessible directory, in my case /var/www/html, and install a few PHP scripts. Note that this should not be done as root, so create another user if needed and give them access to the directory:
$composer require phpmailer/phpmailer $composer require league/oauth2-client $composer require league/oauth2-google
Now enter the directory vendor/phpmailer/phpmailer. There will be a script called get_oauth_token.php. Move this script up three directories into the directory you just ran the ‘composer’ commands from. The location of this script as seen from the web needs to be entered into the ‘Authorized redirect URIs’ field of the Google API that we saw earlier. In this case it would have been https://mydomain.com/get_oauth_token.php. Public IP addresses will not work, this is why a domain name pointed to your web server is a requirement.
Now, open get_oauth_token.php in a text editor and paste in your Client ID and Client Secret where needed. Don’t try to run the script locally, it will fail. Open up a web browser on any computer, and navigate to the URL you entered as the ‘Authorized redirect URI’. Then select Google from the list of email services – at this point if it worked you will be asked to log in and then authorize the unverified application, under ‘Advanced’ under the warning prompt, at which point you will finally receive a refresh token. If you only want an access token for some reason you’ll have to edit the script to echo it back.
If that didn’t work, there are two common reasons: a wrong redirect URI or the script cannot find its dependencies. In the former case, the error message from Google will tell you the script URL as it sees it, and you can use that information to update the redirect URI in the Google API Console to fix the issue. For the latter, check your apache error log, probably located in /var/log/apache2/error.log, to see what dependency is not being found. You might see something like this:
PHP Warning: require(vendor/autoload.php): failed to open stream: No such file or directory in /var/www/html/mydomain/get_oauth_token.php on line 59, referer: http://mydomain.com/get_oauth_token.php
If you have received your refresh token, congratulations: the painful part is over. You can just go to the PHPMailer Github page and fill out their OAUTH2 example (gmail_xoauth.phps), and it ought to just work. If all you needed to do is send mail from a project on your VPS, you’re more or less ready to move on to more interesting parts of your project:
$email = '[email protected]'; $clientId = 'RANDOMCHARS-----duv1n2.apps.googleusercontent.com'; $clientSecret = 'RANDOMCHARS-----lGyjPcRtvP'; //Obtained by configuring and running get_oauth_token.php //after setting up an app in Google Developer Console. $refreshToken = 'RANDOMCHARS-----DWxgOvPT003r-yFUV49TQYag7_Aod7y0';
Remember to clean up any unnecessary scripts that contain your refresh token and other sensitive data before continuing.
ESP8266: We Don’t Need No Stinking Servers
Now what if we wanted to use these tokens to send email directly from project on a Raspberry Pi without needing a server in the middle? It turns out that once we have the client ID, client secret, and refresh token, we no longer require the server and domain name we’ve been using so far, and a mail-sending application, e.g. PHPMailer, can be installed on a computer anywhere with Internet access as long as it is configured with those values.
Things get a little more complicated when we try to do this on an ESP8266. OAUTH2 requires that we use SSL, and access tokens regularly expire and need to be refreshed. Thankfully, [jalmeroth] generously wrote a proof-of-concept and published it on GitHub. If provided with an access token, it can access your Gmail account and use it to send an email. It can also directly update/get data from Google Sheets, but I didn’t test this. However, if the access token was expired, it couldn’t detect that, although it did include working code to actually request a new token, but not parse it out and use it.
In an attempt to add to the functionality of that proof of concept, I forked the project and made a few changes. First, I changed to order of operations in the code to make it check if the current access token was valid before doing anything else. Second, Google API was responding ‘400 Bad Request’ if the access token was invalid, and everything but ‘200 OK’ responses were being filtered out by the code. Finally, I wrote a couple of JSON parsers that check the reason for the ‘400 Bad Request’ and extract and use the access token returned by Google API when a new one is requested.
It works, but it’s hardly reliable – not surprising considering I’ve never really used the Arduino platform before. Notably, the SHA1 fingerprint for Google API fails often. Checking from my local machine, the SHA1 fingerprint varies between two signatures there too. It would be fairly easy to check for either of them, or just keep trying, but I’d rather understand what’s going on first. (Is it just a CDN or something else?) Or perhaps I should rewrite the whole application in Lua where I’m more competent.
A fun little application built on the above was to place a button on my office that sends an email to my phone. I don’t want people to contact me at that email address frivolously, but do want to know immediately if someone is waiting outside my office. The big red button is for normal requests, but urgent requests require lockpicking. If it’s urgent it better also be interesting.
Finally, did you know that Hackaday provides an API for accessing hackaday.io? It uses the simpler OAUTH (not OAUTH2) authentication, so should be more straightforward than the above to implement on the ESP8266. Have any of you used it?
Filed under: Arduino Hacks, google hacks, how-to, Original Art
Using Gmail with OAUTH2 in Linux and on an ESP8266 was originally published on PlanetArduino
0 notes
Text
Aspose.Newsletter May 2018: Enterprise Applications Development using Aspose Native APIs & Other News
Aspose Newsletter for May 2018 has now been published that highlights all the newly supported features offered in the recent releases. It includes information about business file format APIs for all Major platforms, launching Soon Aspose.3D for Java API to work with 3D formats, work with password-Protected ODT and OTT files in .NET, Java and Android applications, embed all fonts when converting presentation to HTML, add text and Image in AutoCAD DWG files within Java Applications & many more.
Business File Format APIs for all Major Platforms: Build the best applications using Aspose Native APIs
Manipulate Microsoft Word, Excel, PDF, PowerPoint, Outlook, Visio, Project, HTML, Images and 100+ other file formats using Aspose native APIs for .NET, Java, Android, C++, SharePoint, Reporting Services and JasperReports. Developers can easily create, edit, render, print and convert between popular document formats within their own application by adding just a few lines of code. Download Free Trial
Launching Soon: Aspose.3D for Java API to work with 3D Formats
Aspose.3D for .NET is already enabling to work with 3D formats within .NET applications. Now Aspose is ready to launch Aspose.3D for Java that will empower developers to import and export 3D models into the supported formats, access 3D elements for editing purposes and build a 3D model from scratch. They can also build GPU and CAD friendly geometries as well as skeletal animation and morphing. Read more details
Work with Password-Protected ODT and OTT Files in .NET, Java and Android Applications
Aspose.Words now supports working with encrypted OpenDocument Text (ODT) and document template files (OTT) in .NET, Java and Android applications. The OdtSaveOptions class can be used to specify additional options when saving a document into the ODT or OTT format. Also use OdtSaveOptions.Password property to get or set password to encrypt document:
Embed all Fonts when Converting Presentation to HTML
Aspose.Slides now supports exporting presentation to HTML by embedding all fonts used in presentation within .NET, Java, C++, SharePoint, SSR and JasperReports. A new HTML controller EmbedAllFontsHtmlController has been added that is used to embed all presentation fonts in HTML document. Using Aspose.Slides APIs – experience improved chart, text and shapes rendering support in API along with improvement in exported PDF outputs.
Support for Subscript, SmallCap PSD and exporting CMYK PSD to CMYK TIFF in .NET and Java
Using Aspose.Imaging APIs – developers can convert CMYK PSD file to CMYK tiff format within .NET and Java applications. Just load image of any format and then you can set various properties using TiffOptions class and save the image. The new version also supports working with Subscript and adds the SmallCap option parsing and rendering for PSD text layer.
How to: Find & refresh children Pivot Tables and Group Pivot Fields in the Pivot Table?
Aspose.Cells for Android via Java finds the children pivot tables of a parent pivot table using the PivotTable.getChildren() and then refreshes them one by one. You can also avoid exporting various types of Document, Workbook and Worksheet properties while exporting Microsoft Excel files to HTML. Try out fully functional code examples.
How to: Determine Line Break in PDF and Clone TextFragments with Identical Formatting?
Aspose.Pdf for .NET now supports logging (tracking) background processing (line breaking) of multi-line text fragments in text adding scenarios. You can use GetNotifications(), a new method of Page Class in order to achieve the functionality. You can also clone a TextFragment with segments formatting identical to the original fragment, use TextFragment.Clone() method to achieve this. Try out fully functional code examples here.
How to: Renumber WBS Codes of Tasks in a Java Project File?
Aspose.Tasks for Java provides support for renumbering WBS Codes of tasks in a project (associated with tasks like Microsoft Project’s “Renumber” function) and eliminate gaps between tasks list and page footer while rendering project data. Try out fully functional C# code examples.
How to: Control Image Quality Compression during OneNote Document Conversion to PDF?
Aspose.Note for Java adds the capability to control the compression ratio of images during conversion to PDF. It lets you select the image compression type and quality using the SaveOptions class of the API. Image quality can be set from 0 to 100 using the JpegQuality property of SaveOptions. Try out fully functional code examples
How to: Add Text and Image in AutoCAD DWG files within Java Applications?
Aspose.CAD for Java announces plenty of new features related to: adding text in DWG file, exporting DWG entity to image, saving DXF files and importing image to DWG file. Try out fully functional code examples.
How to: Display Geographic Data by Google Earth within .NET applications?
Aspose.GIS for .NET now support KML file format that is used to display geographic data by Google Earth. Developers can create or read KML files, add attributes as well as features to it using the API. Try out fully functional code examples
Updates about new Product Releases
Aspose.Total for .NET - a compilation of Aspose latest .NET products
Aspose.Total for Java – a compilation of Aspose latest Java products.
Aspose.Total for Android – all the latest versions of Aspose Android APIs.
Aspose.Total for SharePoint – a compilation of Aspose latest SharePoint products.
Aspose.Total for Reporting Services– a compilation of Aspose latest Reporting Services products
Aspose.Total for JasperReports – The latest versions of Aspose JasperReports products.
Aspose.Total for C++ – The latest versions of our C++ products packaged into one product suite.
Aspose.Words for SharePoint 18.3 – Improved reflection effect for 3D rotated WordArt objects and rendering of DML charts in Word documents.
Aspose.Pdf for .NET 18.3 – Improved Image Quality in PDF to HTML Conversion and Repeating Column in Table.
Aspose.BarCode for .NET 18.3 – Improved recognition of barcode from image and from PDF file.
Aspose.Pdf for Java 18.3 – Improved and Enhanced Java Library to Create and Manipulate PDF Documents.
Aspose.Words for Java 18.3 – Fixed issues related to incorrect page number in exported Word document.
Aspose.Email for .NET 18.3 – Introduced the capability of setting the participant status of a meeting that lets you add the same information to output ICS file in the form of PARTSTAT property.
Aspose.Diagram for .NET and Java 18.3 – Move page position in Visio drawing and enhanced export of Visio drawing to XPS.
Aspose.Tasks for .NET 18.4 – Improved project recalculations and extended Aspose.Tasks collections to support BCL collection interfaces.
Aspose.BarCode for Java 18.3 – Enhanced barcode generation process in this release.
Aspose.3D for .NET 18.3 – Enhanced texture-transparency and retrieval of entity bounding box among 3D file formats.
Aspose.BarCode for JasperReports 18.3 – Fixed issues related to evaluation message displayed when customer is using a free version of Aspose.BarCode API.
Aspose.HTML for .NET 18.4 – Enhanced support for rendering HTML files to image files in .NET
Supporting User Groups and Conferences
Aspose is sponsoring a number of user groups and upcoming events, including:
April 21: Brisbane Global Azure Bootcamp – Brisbane, Australia
April 21: Global Azure Bootcamp – Singapore
May 22 – 23: de:code Japan – Tokyo, Japan
Sponsor a user group? Get in contact: [email protected]
Collect a copy of Aspose Newsletter, February 2018 edition
Collect the English version of this newsletter
#Enterprise Applications development#File Format APIs for all Platforms#Build apps using Aspose Native APIs#handle Password-Protected ODT files#Converting Presentation to HTML#refresh children Pivot Tables
0 notes
Text
Original Post from FireEye Author: James T. Bennett
In this blog, we will take a closer look at the powerful, versatile backdoor known as CARBANAK (aka Anunak). Specifically, we will focus on the operational details of its use over the past few years, including its configuration, the minor variations observed from sample to sample, and its evolution. With these details, we will then draw some conclusions about the operators of CARBANAK. For some additional background on the CARBANAK backdoor, see the papers by Kaspersky and Group-IB and Fox-It.
Technical Analysis
Before we dive into the meat of this blog, a brief technical analysis of the backdoor is necessary to provide some context. CARBANAK is a full-featured backdoor with data-stealing capabilities and a plugin architecture. Some of its capabilities include key logging, desktop video capture, VNC, HTTP form grabbing, file system management, file transfer, TCP tunneling, HTTP proxy, OS destruction, POS and Outlook data theft and reverse shell. Most of these data-stealing capabilities were present in the oldest variants of CARBANAK that we have seen and some were added over time.
Monitoring Threads
The backdoor may optionally start one or more threads that perform continuous monitoring for various purposes, as described in Table 1.
Thread Name
Description
Key logger
Logs key strokes for configured processes and sends them to the command and control (C2) server
Form grabber
Monitors HTTP traffic for form data and sends it to the C2 server
POS monitor
Monitors for changes to logs stored in C:NSBCoalitionLogs and nsb.pos.client.log and sends parsed data to the C2 server
PST monitor
Searches recursively for newly created Outlook personal storage table (PST) files within user directories and sends them to the C2 server
HTTP proxy monitor
Monitors HTTP traffic for requests sent to HTTP proxies, saves the proxy address and credentials for future use
Table 1: Monitoring threads
Commands
In addition to its file management capabilities, this data-stealing backdoor supports 34 commands that can be received from the C2 server. After decryption, these 34 commands are plain text with parameters that are space delimited much like a command line. The command and parameter names are hashed before being compared by the binary, making it difficult to recover the original names of commands and parameters. Table 2 lists these commands.
Command Hash
Command Name
Description
0x0AA37987
loadconfig
Runs each command specified in the configuration file (see the Configuration section).
0x007AA8A5
state
Updates the state value (see the Configuration section).
0x007CFABF
video
Desktop video recording
0x06E533C4
download
Downloads executable and injects into new process
0x00684509
ammyy
Ammyy Admin tool
0x07C6A8A5
update
Updates self
0x0B22A5A7
Add/Update klgconfig (analysis incomplete)
0x0B77F949
httpproxy
Starts HTTP proxy
0x07203363
killos
Renders computer unbootable by wiping the MBR
0x078B9664
reboot
Reboots the operating system
0x07BC54BC
tunnel
Creates a network tunnel
0x07B40571
adminka
Adds new C2 server or proxy address for pseudo-HTTP protocol
0x079C9CC2
server
Adds new C2 server for custom binary protocol
0x0007C9C2
user
Creates or deletes Windows user account
0x000078B0
rdp
Enables concurrent RDP (analysis incomplete)
0x079BAC85
secure
Adds Notification Package (analysis incomplete)
0x00006ABC
del
Deletes file or service
0x0A89AF94
startcmd
Adds command to the configuration file (see the Configuration section)
0x079C53BD
runmem
Downloads executable and injects directly into new process
0x0F4C3903
logonpasswords
Send Windows accounts details to the C2 server
0x0BC205E4
screenshot
Takes a screenshot of the desktop and sends it to the C2 server
0x007A2BC0
sleep
Backdoor sleeps until specified date
0x0006BC6C
dupl
Unknown
0x04ACAFC3
Upload files to the C2 server
0x00007D43
vnc
Runs VNC plugin
0x09C4D055
runfile
Runs specified executable file
0x02032914
killbot
Uninstalls backdoor
0x08069613
listprocess
Returns list of running processes to the C2 server
0x073BE023
plugins
Change C2 protocol used by plugins
0x0B0603B4
Download and execute shellcode from specified address
0x0B079F93
killprocess
Terminates the first process found specified by name
0x00006A34
cmd
Initiates a reverse shell to the C2 server
0x09C573C7
runplug
Plugin control
0x08CB69DE
autorun
Updates backdoor
Table 2: Supported Commands
Configuration
A configuration file resides in a file under the backdoor’s installation directory with the .bin extension. It contains commands in the same form as those listed in Table 2 that are automatically executed by the backdoor when it is started. These commands are also executed when the loadconfig command is issued. This file can be likened to a startup script for the backdoor. The state command sets a global variable containing a series of Boolean values represented as ASCII values ‘0’ or ‘1’ and also adds itself to the configuration file. Some of these values indicate which C2 protocol to use, whether the backdoor has been installed, and whether the PST monitoring thread is running or not. Other than the state command, all commands in the configuration file are identified by their hash’s decimal value instead of their plain text name. Certain commands, when executed, add themselves to the configuration so they will persist across (or be part of) reboots. The loadconfig and state commands are executed during initialization, effectively creating the configuration file if it does not exist and writing the state command to it.
Figure 1 and Figure 2 illustrate some sample, decoded configuration files we have come across in our investigations.
Figure 1: Configuration file that adds new C2 server and forces the data-stealing backdoor to use it
Figure 2: Configuration file that adds TCP tunnels and records desktop video
Command and Control
CARBANAK communicates to its C2 servers via pseudo-HTTP or a custom binary protocol.
Pseudo-HTTP Protocol
Messages for the pseudo-HTTP protocol are delimited with the ‘|’ character. A message starts with a host ID composed by concatenating a hash value generated from the computer’s hostname and MAC address to a string likely used as a campaign code. Once the message has been formatted, it is sandwiched between an additional two fields of randomly generated strings of upper and lower case alphabet characters. An example of a command polling message and a response to the listprocess command are given in Figure 3 and Figure 4, respectively.
Figure 3: Example command polling message
Figure 4: Example command response message
Messages are encrypted using Microsoft’s implementation of RC2 in CBC mode with PKCS#5 padding. The encrypted message is then Base64 encoded, replacing all the ‘/’ and ‘+’ characters with the ‘.’ and ‘-’ characters, respectively. The eight-byte initialization vector (IV) is a randomly generated string consisting of upper and lower case alphabet characters. It is prepended to the encrypted and encoded message.
The encoded payload is then made to look like a URI by having a random number of ‘/’ characters inserted at random locations within the encoded payload. The malware then appends a script extension (php, bml, or cgi) with a random number of random parameters or a file extension from the following list with no parameters: gif, jpg, png, htm, html, php.
This URI is then used in a GET or POST request. The body of the POST request may contain files contained in the cabinet format. A sample GET request is shown in Figure 5.
Figure 5: Sample pseudo-HTTP beacon
The pseudo-HTTP protocol uses any proxies discovered by the HTTP proxy monitoring thread or added by the adminka command. The backdoor also searches for proxy configurations to use in the registry at HKCUSoftwareMicrosoftWindowsCurrentVersionInternet Settings and for each profile in the Mozilla Firefox configuration file at %AppData%MozillaFirefoxprefs.js.
Custom Binary Protocol
Figure 6 describes the structure of the malware’s custom binary protocol. If a message is larger than 150 bytes, it is compressed with an unidentified algorithm. If a message is larger than 4096 bytes, it is broken into compressed chunks. This protocol has undergone several changes over the years, each version building upon the previous version in some way. These changes were likely introduced to render existing network signatures ineffective and to make signature creation more difficult.
Figure 6: Binary protocol message format
Version 1
In the earliest version of the binary protocol, we have discovered that the message bodies that are stored in the field are simply XORed with the host ID. The initial message is not encrypted and contains the host ID.
Version 2
Rather than using the host ID as the key, this version uses a random XOR key between 32 and 64 bytes in length that is generated for each session. This key is sent in the initial message.
Version 3
Version 3 adds encryption to the headers. The first 19 bytes of the message headers (up to the field) are XORed with a five-byte key that is randomly generated per message and stored in the field. If the field of the message header is greater than one, the XOR key used to encrypt message bodies is iterated in reverse when encrypting and decrypting messages.
Version 4
This version adds a bit more complexity to the header encryption scheme. The headers are XOR encrypted with and combined and reversed.
Version 5
Version 5 is the most sophisticated of the binary protocols we have seen. A 256-bit AES session key is generated and used to encrypt both message headers and bodies separately. Initially, the key is sent to the C2 server with the entire message and headers encrypted with the RSA key exchange algorithm. All subsequent messages are encrypted with AES in CBC mode. The use of public key cryptography makes decryption of the session key infeasible without the C2 server’s private key.
The Roundup
We have rounded up 220 samples of the CARBANAK backdoor and compiled a table that highlights some interesting details that we were able to extract. It should be noted that in most of these cases the backdoor was embedded as a packed payload in another executable or in a weaponized document file of some kind. The MD5 hash is for the original executable file that eventually launches CARBANAK, but the details of each sample were extracted from memory during execution. This data provides us with a unique insight into the operational aspect of CARBANAK and can be downloaded here.
Protocol Evolution
As described earlier, CARBANAK’s binary protocol has undergone several significant changes over the years. Figure 7 illustrates a rough timeline of this evolution based on the compile times of samples we have in our collection. This may not be entirely accurate because our visibility is not complete, but it gives us a general idea as to when the changes occurred. It has been observed that some builds of this data-stealing backdoor use outdated versions of the protocol. This may suggest multiple groups of operators compiling their own builds of this data-stealing backdoor independently.
Figure 7: Timeline of binary protocol versions
*It is likely that we are missing an earlier build that utilized version 3.
Build Tool
Most of CARBANAK’s strings are encrypted in order to make analysis more difficult. We have observed that the key and the cipher texts for all the encrypted strings are changed for each sample that we have encountered, even amongst samples with the same compile time. The RC2 key used for the HTTP protocol has also been observed to change among samples with the same compile time. These observations paired with the use of campaign codes that must be configured denote the likely existence of a build tool.
Rapid Builds
Despite the likelihood of a build tool, we have found 57 unique compile times in our sample set, with some of the compile times being quite close in proximity. For example, on May 20, 2014, two builds were compiled approximately four hours apart and were configured to use the same C2 servers. Again, on July 30, 2015, two builds were compiled approximately 12 hours apart.
What changes in the code can we see in such short time intervals that would not be present in a build tool? In one case, one build was programmed to execute the runmem command for a file named wi.exe while the other was not. This command downloads an executable from the C2 and directly runs it in memory. In another case, one build was programmed to check for the existence of the domain blizko.net in the trusted sites list for Internet Explorer while the other was not. Blizko is an online money transfer service. We have also seen that different monitoring threads from Table 1 are enabled from build to build. These minor changes suggest that the code is quickly modified and compiled to adapt to the needs of the operator for particular targets.
Campaign Code and Compile Time Correlation
In some cases, there is a close proximity of the compile time of a CARBANAK sample to the month specified in a particular campaign code. Figure 8 shows some of the relationships that can be observed in our data set.
Campaign Code
Compile Date
Aug
7/30/15
dec
12/8/14
julyc
7/2/16
jun
5/9/15
june
5/25/14
june
6/7/14
junevnc
6/20/14
juspam
7/13/14
juupd
7/13/14
may
5/20/14
may
5/19/15
ndjun
6/7/16
SeP
9/12/14
spamaug
8/1/14
spaug
8/1/14
Figure 8: Campaign code to compile time relationships
Recent Updates
Recently, 64 bit variants of the backdoor have been discovered. We shared details about such variants in a recent blog post. Some of these variants are programmed to sleep until a configured activation date when they will become active.
History
The “Carbanak Group”
Much of the publicly released reporting surrounding the CARBANAK malware refers to a corresponding “Carbanak Group”, who appears to be behind the malicious activity associated with this data-stealing backdoor. FireEye iSIGHT Intelligence has tracked several separate overarching campaigns employing the CARBANAK tool and other associated backdoors, such as DRIFTPIN (aka Toshliph). With the data available at this time, it is unclear how interconnected these campaigns are – if they are all directly orchestrated by the same criminal group, or if these campaigns were perpetrated by loosely affiliated actors sharing malware and techniques.
FIN7
In all Mandiant investigations to date where the CARBANAK backdoor has been discovered, the activity has been attributed to the FIN7 threat group. FIN7 has been extremely active against the U.S. restaurant and hospitality industries since mid-2015.
FIN7 uses CARBANAK as a post-exploitation tool in later phases of an intrusion to cement their foothold in a network and maintain access, frequently using the video command to monitor users and learn about the victim network, as well as the tunnel command to proxy connections into isolated portions of the victim environment. FIN7 has consistently utilized legally purchased code signing certificates to sign their CARBANAK payloads. Finally, FIN7 has leveraged several new techniques that we have not observed in other CARBANAK related activity.
We have covered recent FIN7 activity in previous public blog posts:
FIN7 Spear Phishing Campaign Targets Personnel Involved in SEC Filings
FIN7 Evolution and the Phishing LNK
To SDB, Or Not To SDB: FIN7 Leveraging Shim Databases for Persistence
The FireEye iSIGHT Intelligence MySIGHT Portal contains additional information on our investigations and observations into FIN7 activity.
Widespread Bank Targeting Throughout the U.S., Middle East and Asia
Proofpoint initially reported on a widespread campaign targeting banks and financial organizations throughout the U.S. and Middle East in early 2016. We identified several additional organizations in these regions, as well as in Southeast Asia and Southwest Asia being targeted by the same attackers.
This cluster of activity persisted from late 2014 into early 2016. Most notably, the infrastructure utilized in this campaign overlapped with LAZIOK, NETWIRE and other malware targeting similar financial entities in these regions.
DRIFTPIN
DRIFTPIN (aka Spy.Agent.ORM, and Toshliph) has been previously associated with CARBANAK in various campaigns. We have seen it deployed in initial spear phishing by FIN7 in the first half of 2016. Also, in late 2015, ESET reported on CARBANAK associated attacks, detailing a spear phishing campaign targeting Russian and Eastern European banks using DRIFTPIN as the malicious payload. Cyphort Labs also revealed that variants of DRIFTPIN associated with this cluster of activity had been deployed via the RIG exploit kit placed on two compromised Ukrainian banks’ websites.
FireEye iSIGHT Intelligence observed this wave of spear phishing aimed at a large array of targets, including U.S. financial institutions and companies associated with Bitcoin trading and mining activities. This cluster of activity continues to be active now to this day, targeting similar entities. Additional details on this latest activity are available on the FireEye iSIGHT Intelligence MySIGHT Portal.
Earlier CARBANAK Activity
In December 2014, Group-IB and Fox-IT released a report about an organized criminal group using malware called “Anunak” that has targeted Eastern European banks, U.S. and European point-of-sale systems and other entities. Kaspersky released a similar report about the same group under the name “Carbanak” in February 2015. The name “Carbanak” was coined by Kaspersky in this report – the malware authors refer to the backdoor as Anunak.
This activity was further linked to the 2014 exploitation of ATMs in Ukraine. Additionally, some of this early activity shares a similarity with current FIN7 operations – the use of Power Admin PAExec for lateral movement.
Conclusion
The details that can be extracted from CARBANAK provide us with a unique insight into the operational details behind this data-stealing malware. Several inferences can be made when looking at such data in bulk as we discussed above and are summarized as follows:
Based upon the information we have observed, we believe that at least some of the operators of CARBANAK either have access to the source code directly with knowledge on how to modify it or have a close relationship to the developer(s).
Some of the operators may be compiling their own builds of the backdoor independently.
A build tool is likely being used by these attackers that allows the operator to configure details such as C2 addresses, C2 encryption keys, and a campaign code. This build tool encrypts the binary’s strings with a fresh key for each build.
Varying campaign codes indicate that independent or loosely affiliated criminal actors are employing CARBANAK in a wide-range of intrusions that target a variety of industries but are especially directed at financial institutions across the globe, as well as the restaurant and hospitality sectors within the U.S.
#gallery-0-6 { margin: auto; } #gallery-0-6 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-6 img { border: 2px solid #cfcfcf; } #gallery-0-6 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: James T. Bennett Behind the CARBANAK Backdoor Original Post from FireEye Author: James T. Bennett In this blog, we will take a closer look at the powerful, versatile…
0 notes
Text
Original Post from FireEye Author: James T. Bennett
In this blog, we will take a closer look at the powerful, versatile backdoor known as CARBANAK (aka Anunak). Specifically, we will focus on the operational details of its use over the past few years, including its configuration, the minor variations observed from sample to sample, and its evolution. With these details, we will then draw some conclusions about the operators of CARBANAK. For some additional background on the CARBANAK backdoor, see the papers by Kaspersky and Group-IB and Fox-It.
Technical Analysis
Before we dive into the meat of this blog, a brief technical analysis of the backdoor is necessary to provide some context. CARBANAK is a full-featured backdoor with data-stealing capabilities and a plugin architecture. Some of its capabilities include key logging, desktop video capture, VNC, HTTP form grabbing, file system management, file transfer, TCP tunneling, HTTP proxy, OS destruction, POS and Outlook data theft and reverse shell. Most of these data-stealing capabilities were present in the oldest variants of CARBANAK that we have seen and some were added over time.
Monitoring Threads
The backdoor may optionally start one or more threads that perform continuous monitoring for various purposes, as described in Table 1.
Thread Name
Description
Key logger
Logs key strokes for configured processes and sends them to the command and control (C2) server
Form grabber
Monitors HTTP traffic for form data and sends it to the C2 server
POS monitor
Monitors for changes to logs stored in C:NSBCoalitionLogs and nsb.pos.client.log and sends parsed data to the C2 server
PST monitor
Searches recursively for newly created Outlook personal storage table (PST) files within user directories and sends them to the C2 server
HTTP proxy monitor
Monitors HTTP traffic for requests sent to HTTP proxies, saves the proxy address and credentials for future use
Table 1: Monitoring threads
Commands
In addition to its file management capabilities, this data-stealing backdoor supports 34 commands that can be received from the C2 server. After decryption, these 34 commands are plain text with parameters that are space delimited much like a command line. The command and parameter names are hashed before being compared by the binary, making it difficult to recover the original names of commands and parameters. Table 2 lists these commands.
Command Hash
Command Name
Description
0x0AA37987
loadconfig
Runs each command specified in the configuration file (see the Configuration section).
0x007AA8A5
state
Updates the state value (see the Configuration section).
0x007CFABF
video
Desktop video recording
0x06E533C4
download
Downloads executable and injects into new process
0x00684509
ammyy
Ammyy Admin tool
0x07C6A8A5
update
Updates self
0x0B22A5A7
Add/Update klgconfig (analysis incomplete)
0x0B77F949
httpproxy
Starts HTTP proxy
0x07203363
killos
Renders computer unbootable by wiping the MBR
0x078B9664
reboot
Reboots the operating system
0x07BC54BC
tunnel
Creates a network tunnel
0x07B40571
adminka
Adds new C2 server or proxy address for pseudo-HTTP protocol
0x079C9CC2
server
Adds new C2 server for custom binary protocol
0x0007C9C2
user
Creates or deletes Windows user account
0x000078B0
rdp
Enables concurrent RDP (analysis incomplete)
0x079BAC85
secure
Adds Notification Package (analysis incomplete)
0x00006ABC
del
Deletes file or service
0x0A89AF94
startcmd
Adds command to the configuration file (see the Configuration section)
0x079C53BD
runmem
Downloads executable and injects directly into new process
0x0F4C3903
logonpasswords
Send Windows accounts details to the C2 server
0x0BC205E4
screenshot
Takes a screenshot of the desktop and sends it to the C2 server
0x007A2BC0
sleep
Backdoor sleeps until specified date
0x0006BC6C
dupl
Unknown
0x04ACAFC3
Upload files to the C2 server
0x00007D43
vnc
Runs VNC plugin
0x09C4D055
runfile
Runs specified executable file
0x02032914
killbot
Uninstalls backdoor
0x08069613
listprocess
Returns list of running processes to the C2 server
0x073BE023
plugins
Change C2 protocol used by plugins
0x0B0603B4
Download and execute shellcode from specified address
0x0B079F93
killprocess
Terminates the first process found specified by name
0x00006A34
cmd
Initiates a reverse shell to the C2 server
0x09C573C7
runplug
Plugin control
0x08CB69DE
autorun
Updates backdoor
Table 2: Supported Commands
Configuration
A configuration file resides in a file under the backdoor’s installation directory with the .bin extension. It contains commands in the same form as those listed in Table 2 that are automatically executed by the backdoor when it is started. These commands are also executed when the loadconfig command is issued. This file can be likened to a startup script for the backdoor. The state command sets a global variable containing a series of Boolean values represented as ASCII values ‘0’ or ‘1’ and also adds itself to the configuration file. Some of these values indicate which C2 protocol to use, whether the backdoor has been installed, and whether the PST monitoring thread is running or not. Other than the state command, all commands in the configuration file are identified by their hash’s decimal value instead of their plain text name. Certain commands, when executed, add themselves to the configuration so they will persist across (or be part of) reboots. The loadconfig and state commands are executed during initialization, effectively creating the configuration file if it does not exist and writing the state command to it.
Figure 1 and Figure 2 illustrate some sample, decoded configuration files we have come across in our investigations.
Figure 1: Configuration file that adds new C2 server and forces the data-stealing backdoor to use it
Figure 2: Configuration file that adds TCP tunnels and records desktop video
Command and Control
CARBANAK communicates to its C2 servers via pseudo-HTTP or a custom binary protocol.
Pseudo-HTTP Protocol
Messages for the pseudo-HTTP protocol are delimited with the ‘|’ character. A message starts with a host ID composed by concatenating a hash value generated from the computer’s hostname and MAC address to a string likely used as a campaign code. Once the message has been formatted, it is sandwiched between an additional two fields of randomly generated strings of upper and lower case alphabet characters. An example of a command polling message and a response to the listprocess command are given in Figure 3 and Figure 4, respectively.
Figure 3: Example command polling message
Figure 4: Example command response message
Messages are encrypted using Microsoft’s implementation of RC2 in CBC mode with PKCS#5 padding. The encrypted message is then Base64 encoded, replacing all the ‘/’ and ‘+’ characters with the ‘.’ and ‘-’ characters, respectively. The eight-byte initialization vector (IV) is a randomly generated string consisting of upper and lower case alphabet characters. It is prepended to the encrypted and encoded message.
The encoded payload is then made to look like a URI by having a random number of ‘/’ characters inserted at random locations within the encoded payload. The malware then appends a script extension (php, bml, or cgi) with a random number of random parameters or a file extension from the following list with no parameters: gif, jpg, png, htm, html, php.
This URI is then used in a GET or POST request. The body of the POST request may contain files contained in the cabinet format. A sample GET request is shown in Figure 5.
Figure 5: Sample pseudo-HTTP beacon
The pseudo-HTTP protocol uses any proxies discovered by the HTTP proxy monitoring thread or added by the adminka command. The backdoor also searches for proxy configurations to use in the registry at HKCUSoftwareMicrosoftWindowsCurrentVersionInternet Settings and for each profile in the Mozilla Firefox configuration file at %AppData%MozillaFirefoxprefs.js.
Custom Binary Protocol
Figure 6 describes the structure of the malware’s custom binary protocol. If a message is larger than 150 bytes, it is compressed with an unidentified algorithm. If a message is larger than 4096 bytes, it is broken into compressed chunks. This protocol has undergone several changes over the years, each version building upon the previous version in some way. These changes were likely introduced to render existing network signatures ineffective and to make signature creation more difficult.
Figure 6: Binary protocol message format
Version 1
In the earliest version of the binary protocol, we have discovered that the message bodies that are stored in the field are simply XORed with the host ID. The initial message is not encrypted and contains the host ID.
Version 2
Rather than using the host ID as the key, this version uses a random XOR key between 32 and 64 bytes in length that is generated for each session. This key is sent in the initial message.
Version 3
Version 3 adds encryption to the headers. The first 19 bytes of the message headers (up to the field) are XORed with a five-byte key that is randomly generated per message and stored in the field. If the field of the message header is greater than one, the XOR key used to encrypt message bodies is iterated in reverse when encrypting and decrypting messages.
Version 4
This version adds a bit more complexity to the header encryption scheme. The headers are XOR encrypted with and combined and reversed.
Version 5
Version 5 is the most sophisticated of the binary protocols we have seen. A 256-bit AES session key is generated and used to encrypt both message headers and bodies separately. Initially, the key is sent to the C2 server with the entire message and headers encrypted with the RSA key exchange algorithm. All subsequent messages are encrypted with AES in CBC mode. The use of public key cryptography makes decryption of the session key infeasible without the C2 server’s private key.
The Roundup
We have rounded up 220 samples of the CARBANAK backdoor and compiled a table that highlights some interesting details that we were able to extract. It should be noted that in most of these cases the backdoor was embedded as a packed payload in another executable or in a weaponized document file of some kind. The MD5 hash is for the original executable file that eventually launches CARBANAK, but the details of each sample were extracted from memory during execution. This data provides us with a unique insight into the operational aspect of CARBANAK and can be downloaded here.
Protocol Evolution
As described earlier, CARBANAK’s binary protocol has undergone several significant changes over the years. Figure 7 illustrates a rough timeline of this evolution based on the compile times of samples we have in our collection. This may not be entirely accurate because our visibility is not complete, but it gives us a general idea as to when the changes occurred. It has been observed that some builds of this data-stealing backdoor use outdated versions of the protocol. This may suggest multiple groups of operators compiling their own builds of this data-stealing backdoor independently.
Figure 7: Timeline of binary protocol versions
*It is likely that we are missing an earlier build that utilized version 3.
Build Tool
Most of CARBANAK’s strings are encrypted in order to make analysis more difficult. We have observed that the key and the cipher texts for all the encrypted strings are changed for each sample that we have encountered, even amongst samples with the same compile time. The RC2 key used for the HTTP protocol has also been observed to change among samples with the same compile time. These observations paired with the use of campaign codes that must be configured denote the likely existence of a build tool.
Rapid Builds
Despite the likelihood of a build tool, we have found 57 unique compile times in our sample set, with some of the compile times being quite close in proximity. For example, on May 20, 2014, two builds were compiled approximately four hours apart and were configured to use the same C2 servers. Again, on July 30, 2015, two builds were compiled approximately 12 hours apart.
What changes in the code can we see in such short time intervals that would not be present in a build tool? In one case, one build was programmed to execute the runmem command for a file named wi.exe while the other was not. This command downloads an executable from the C2 and directly runs it in memory. In another case, one build was programmed to check for the existence of the domain blizko.net in the trusted sites list for Internet Explorer while the other was not. Blizko is an online money transfer service. We have also seen that different monitoring threads from Table 1 are enabled from build to build. These minor changes suggest that the code is quickly modified and compiled to adapt to the needs of the operator for particular targets.
Campaign Code and Compile Time Correlation
In some cases, there is a close proximity of the compile time of a CARBANAK sample to the month specified in a particular campaign code. Figure 8 shows some of the relationships that can be observed in our data set.
Campaign Code
Compile Date
Aug
7/30/15
dec
12/8/14
julyc
7/2/16
jun
5/9/15
june
5/25/14
june
6/7/14
junevnc
6/20/14
juspam
7/13/14
juupd
7/13/14
may
5/20/14
may
5/19/15
ndjun
6/7/16
SeP
9/12/14
spamaug
8/1/14
spaug
8/1/14
Figure 8: Campaign code to compile time relationships
Recent Updates
Recently, 64 bit variants of the backdoor have been discovered. We shared details about such variants in a recent blog post. Some of these variants are programmed to sleep until a configured activation date when they will become active.
History
The “Carbanak Group”
Much of the publicly released reporting surrounding the CARBANAK malware refers to a corresponding “Carbanak Group”, who appears to be behind the malicious activity associated with this data-stealing backdoor. FireEye iSIGHT Intelligence has tracked several separate overarching campaigns employing the CARBANAK tool and other associated backdoors, such as DRIFTPIN (aka Toshliph). With the data available at this time, it is unclear how interconnected these campaigns are – if they are all directly orchestrated by the same criminal group, or if these campaigns were perpetrated by loosely affiliated actors sharing malware and techniques.
FIN7
In all Mandiant investigations to date where the CARBANAK backdoor has been discovered, the activity has been attributed to the FIN7 threat group. FIN7 has been extremely active against the U.S. restaurant and hospitality industries since mid-2015.
FIN7 uses CARBANAK as a post-exploitation tool in later phases of an intrusion to cement their foothold in a network and maintain access, frequently using the video command to monitor users and learn about the victim network, as well as the tunnel command to proxy connections into isolated portions of the victim environment. FIN7 has consistently utilized legally purchased code signing certificates to sign their CARBANAK payloads. Finally, FIN7 has leveraged several new techniques that we have not observed in other CARBANAK related activity.
We have covered recent FIN7 activity in previous public blog posts:
FIN7 Spear Phishing Campaign Targets Personnel Involved in SEC Filings
FIN7 Evolution and the Phishing LNK
To SDB, Or Not To SDB: FIN7 Leveraging Shim Databases for Persistence
The FireEye iSIGHT Intelligence MySIGHT Portal contains additional information on our investigations and observations into FIN7 activity.
Widespread Bank Targeting Throughout the U.S., Middle East and Asia
Proofpoint initially reported on a widespread campaign targeting banks and financial organizations throughout the U.S. and Middle East in early 2016. We identified several additional organizations in these regions, as well as in Southeast Asia and Southwest Asia being targeted by the same attackers.
This cluster of activity persisted from late 2014 into early 2016. Most notably, the infrastructure utilized in this campaign overlapped with LAZIOK, NETWIRE and other malware targeting similar financial entities in these regions.
DRIFTPIN
DRIFTPIN (aka Spy.Agent.ORM, and Toshliph) has been previously associated with CARBANAK in various campaigns. We have seen it deployed in initial spear phishing by FIN7 in the first half of 2016. Also, in late 2015, ESET reported on CARBANAK associated attacks, detailing a spear phishing campaign targeting Russian and Eastern European banks using DRIFTPIN as the malicious payload. Cyphort Labs also revealed that variants of DRIFTPIN associated with this cluster of activity had been deployed via the RIG exploit kit placed on two compromised Ukrainian banks’ websites.
FireEye iSIGHT Intelligence observed this wave of spear phishing aimed at a large array of targets, including U.S. financial institutions and companies associated with Bitcoin trading and mining activities. This cluster of activity continues to be active now to this day, targeting similar entities. Additional details on this latest activity are available on the FireEye iSIGHT Intelligence MySIGHT Portal.
Earlier CARBANAK Activity
In December 2014, Group-IB and Fox-IT released a report about an organized criminal group using malware called “Anunak” that has targeted Eastern European banks, U.S. and European point-of-sale systems and other entities. Kaspersky released a similar report about the same group under the name “Carbanak” in February 2015. The name “Carbanak” was coined by Kaspersky in this report – the malware authors refer to the backdoor as Anunak.
This activity was further linked to the 2014 exploitation of ATMs in Ukraine. Additionally, some of this early activity shares a similarity with current FIN7 operations – the use of Power Admin PAExec for lateral movement.
Conclusion
The details that can be extracted from CARBANAK provide us with a unique insight into the operational details behind this data-stealing malware. Several inferences can be made when looking at such data in bulk as we discussed above and are summarized as follows:
Based upon the information we have observed, we believe that at least some of the operators of CARBANAK either have access to the source code directly with knowledge on how to modify it or have a close relationship to the developer(s).
Some of the operators may be compiling their own builds of the backdoor independently.
A build tool is likely being used by these attackers that allows the operator to configure details such as C2 addresses, C2 encryption keys, and a campaign code. This build tool encrypts the binary’s strings with a fresh key for each build.
Varying campaign codes indicate that independent or loosely affiliated criminal actors are employing CARBANAK in a wide-range of intrusions that target a variety of industries but are especially directed at financial institutions across the globe, as well as the restaurant and hospitality sectors within the U.S.
#gallery-0-6 { margin: auto; } #gallery-0-6 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-6 img { border: 2px solid #cfcfcf; } #gallery-0-6 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: James T. Bennett Behind the CARBANAK Backdoor Original Post from FireEye Author: James T. Bennett In this blog, we will take a closer look at the powerful, versatile…
0 notes
Text
Work with Extended Attributes of Message using EWS & Enhanced MSG to EML Conversion using Java
What’s new in this release?
Aspose team is pleased to announce the new release of Aspose.Email for Java 17.11.0. This release introduces a new feature of working with Extended attributes of messages using API’s Exchange Web Service (EWS) client. In addition, it also brings several fixes to other functionality of the API that further stabilizes the overall behavior of the API in terms of expected behavior. For a complete list of what is new and fixed. This version of Aspose.Email for Java provides the capability to work with Extended Attributes of messages using the API’s EWS client. Extended attributes can be added to message in the same way as adding Named properties to messages. The API now has FetchMapiMessage method that allows to retrieve a message from Exchange server along with such properties associated with it. In addition to new feature, this release of API also includes several improvements in terms of bug fixes. This further adds to the overall stability of the API in terms of expected output. The main improved features & bug fixes added in this release are listed below
EWS: Support for create, retrieve and update Extended Attributes for Emails
Item moved event not fired for sub-folders
Imap client attachment names issue. Content-Disposition filename is not parsed properly.
EMLX attachments (MSG/EML) saved as separate emails in MBOX
The (subject, to and from) disappears form converted MailMessage from MapiMessaage
The exception occurs while loading MapiMessage from MailMessage.
MapiRecipientType shows Unknown for all message recipients
Mails not read from MBOX
MSG attachment extensions changed to EML while converting MSG to EML
Notes added to PST don't retain correct information
Notes created from 2016 Note file don't open in MS Outlook
Fetch calendar items returns error "Input string was not in a correct format"
Other most recent bug fixes are also included in this release.
Newly added documentation pages and articles
Some new tips and articles have now been added into Aspose.Email for Java documentation that may guide users briefly how to use Aspose.Email for performing different tasks like the followings.
Working with Exchange Extended Attributes of Exchange Items
Filter Appointments from Exchange Server
Overview:Aspose.Email for Java
Aspose.Email for Java is a Non-Graphical Java component that enables Java applications to read and write Microsoft Outlook documents without utilizing Microsoft Outlook. It enables developers to create new MSG file from scratch, update an existing MSG file, read Outlook MSG file & get it's properties like subject, body, recipients in to, cc and bcc, Adding or removing attachment, sender information and MAPI properties. Aspose.Email for Java can be used with Web as well asDesktop Application.
More about Aspose.Email for Java
Homepage of Oulook component Aspose.Email for Java
Download Aspose.Email for Java
Online documentation of Aspose.Email for Java
#Work with Exchange Extended Attributes#update Extended Attributes for Emails#create Extended Attributes for Emails#saving EMLX attachment#converting MSG to EML#Java email API
0 notes
Text
Create/Update Extended Attributes using EWS & Enhanced MSG to EML Conversion using .NET
What's New in this Release?
Aspose team is pleased to announce the release of Aspose.Email for .NET 17.11.0.This month’s release introduces a new feature of working with Extended Attributes using the API’s EWS client. It also fixes several bugs that further improve the overall API functionality. This release of API brings an exciting feature where messages from Exchange server can retrieved as Outlook Messages. This implies that users can manipulate extended attributes of messages using the API’s EWS client. Developers can create, retrieve and update extended attributes using the EWS API. The retrieved item is obtained as MapiMessage from Exchange server and contains all the attributes information contained in the message. This release also includes fixes to several API malfunctions related to various functional areas. Fixing these not only improves the overall usability of the API, but also adds to the overall stability of the API. The main bug fixes & improved features added in this release are listed below
EWS: Support for create, retrieve and update Extended Attributes for Emails
Item moved event not fired for sub-folders
Imap client attachment names issue. Content-Disposition filename is not parsed properly.
EMLX attachments (MSG/EML) saved as separate emails in MBOX
The (subject, to and from) disappears form converted MailMessage from MapiMessaage
The exception occurs while loading MapiMessage from MailMessage
MapiRecipientType shows Unknown for all message recipients
Mails not read from MBOX
MSG attachment extensions changed to EML while converting MSG to EML
Notes added to PST don't retain correct information
Notes created from 2016 Note file don't open in MS Outlook
Fetch calendar items returns error "Input string was not in a correct format"
Newly added documentation pages and articles
Some new tips and articles have now been added into Aspose.Email for .NET documentation that may guide users briefly how to use Aspose.Email for performing different tasks like the followings.
Working with Extended Attributes of Messages using EWS
Creating and setting contents of Emails
Overview:Aspose.Email for .NET
Aspose.Email for .NET is a set of .net email components allowing developers to easily implement email functionality within their ASP.NET web applications, web services & Windows applications. It Supports Outlook PST, EML, MSG & MHT formats. It allows developers to work with SMTP, POP3, FTP & MS Exchange servers. It supports mail merge, iCalendar, customized header & body, header information, embedded files, Twitter & many more. It makes it easy to work with HTML or plain text emails & their attachments.
More about Aspose.Email for .NET
Homepage of Aspose.Email for .NET C#
Download Aspose.Email for .NET
Online documentation of Aspose.Email for .NET
#create extended attributes using EWS#EMLX attachments enhanced#loading MapiMessage from MailMessage#reading emails from MBOX#.NET Email API#retrieve Exchange message as Outlook
0 notes
Text
Outlook EML to HTML Conversion & Improved PST Functionality inside Android Apps
What’s new in this release?
Aspose team is pleased to announce the new release of Aspose.Email for Android via Java 17.10.0. Ported from Aspose.Email for Java, this release includes the same bug fixes as were available in the parent API. It is basically sort of maintenance release that fixes several issues reported with the equivalent Java API. Android developers, who want to provide rich email processing features in their applications, can use Aspose.Email for Android via Java. Following the footprint of Aspose.Email for Java, this API lets you manipulate popular email file formats including Outlook MSG file format. This release include important enhancements and bug fixes such as, Enhanced EMLx to EML conversion, Attachment name encoding issues have been fixed, Issues with MapiMessage API have been fixed resulting in correct retrieval of message body information, Certain issues with PST files have been fixed that were losing properties of Calendar items upon merging, Issues with calendar items in terms of all day events have been fixed and. The main features added in this release are listed below
Attachment name jibbrish on Non-Japanese Windows
MapiMessage.BodyHtml does not return correct value
Attached Word document in Outlook message is corrupted on Save
Multi-octet character split across adjacent encoded-word with UTF8 encoding
Mht empty when converting from msg with SkipInlineImages = true
Duplicated recipients when saving EML as MHTML
Content-disposition filename duplicated
Merging PST with sample PST loses Properties of Calendar
Creating message body from HTML includes header information in output
Converting EML to HTML resulting in incorrect HTML
After EML file is opened and re-saved, in output EML file From and Sender are null
Calendar added to PST doesn't open in MS Outlook
Wrong attachment name read by API
Start and End Date same for full day event
Some characters garbled while conversion from EMLX to EML
Newly added documentation pages and articles
Some new tips and articles have now been added into Aspose.Email for Android documentation that may guide users briefly how to use Aspose.Email for performing different tasks like the followings.
Advance Parsing Features
Import/Export Features
Overview: Aspose.Email for Android via Java
Aspose.Email for Android API enables developers to design Android applications for managing & manipulating Outlook email file formats without using MS Outlook. It provides tools to create, read & convert Outlook MSG, PST, EML, EMLX, OST & MHT file formats. It manages recipients, subject, message body, attachments in MSG documents. It creates & save appointments in draft format, extract & save calendar items from a PST, add Mapi Items such as Messages, Contacts, Notes, Journals & Tasks to a PST.
More about Aspose.Email for Androidvia Java
Homepage of Aspose.Email for Androidvia Java
Download Aspose.Email for Androidvia Java
Online documentation of Aspose.Email for Android via Java
#Attachment name encoding#EMLx to EML conversion#Merging PST with sample PST#Converting EML to HTML#Calendar added to PST#android email API#Attached Word document in Outlook
0 notes