#Prevent Computer Viruses
Explore tagged Tumblr posts
Text
How to Protect Your Computer from Unauthorized Access?
Today, we live our lives online and on gadgets that are connected to the internet. We use the internet to do research, shop, bank, do assignments, play games, and connect with loved ones through social media. Because of this, our gadgets are filled with a
Continue reading How to Protect Your Computer from Unauthorized Access?
#Hackers#How To Prevent Unauthorized Computer Access#How To Protect Your Computer From Unauthorized Access#How To Save From Hacking#Methods For Preventing Unwanted Access To Your Computer#Protect Your Computer From Viruses
0 notes
Text
oh my god do not click links in emails that tell you to verify your data or your bank account gets locked or click links in messages telling you your safety protocol is ending, like, tomorrow, you will get SCAMMED SO BAD AND YOU WILL LOSE A LOT OF FUCKING MONEY never ever let anyone pressure you into giving away login information especially to your online banking by creating a sense of urgency oh my GOD
some things to look out for
1. spelling mistakes. do you know how many rounds of marketing and sales experts these things go through? if theres a spelling mistake dont click it
2. not using your name. if an email adresses you with "dear customer" or, even worse, a generic "ladies and gentlemen", it is most likely not actually targeted to you
3. verifying or login links. even IF your bank was stupid enough to send these to customers, dont EVER click those. look at me. they can legally argue that youve given your data away and thus they dont have to pay you anything back DONT CLICK THAT FUCKING LINK
4. creating a sense of urgency. do this or we lock your account next week. do this or your ebanking stops working tomorrow. give us all your money in cash or your beloved granddaughter will get HANGED FOR MURDERING BABIES. no serious organisation would ever do something like that over email or sms. ever. hands off.
5. ALWAYS CHECK WHO SENT YOU THE EMAIL. the display name and the email adress can vary a LOT. anyone can check the display name. look at the email adress. does it look weird? call the fucking place it says its from. you will likely hear a very weary sigh.
6. if its in a phonecall, scammers love preventing you from hanging up or talking to other people to have a little bit of a think about whats happening. there should always be a possibility to go hey i wanna think about this ill call back the official number thanks.
7. do not, i repeat, do NOT a) call a phone number flashing on your screen promising to rid your computer of viruses after clicking a dodgy link and b) let them install shit on your computer like. uh. idk. teamviewer.
7.i. TEAM VIEWER LETS PEOPLE USE YOUR COMPUTER HOWEVER THEY WANT AS LONG AS THEYRE CONNECTED. IF YOU DONT KNOW FOR FUCKING SURE YOURE TALKING TO ACTUAL TECH SUPPORT DONT GIVE ANYONE ACCESS TO YOUR COMPUTER.
fun little addendum: did you know a link can just automatically download shit? like. a virus? an app you can't uninstall unless you reset your entire device? dont click links unless youre extremely sure you know where they lead. hover your mouse over it and check the url.
thanks.
#'oh i was so stressed in the moment' thats what theyre counting on PLEASE dont do this you will lose so much money#sometimes money you dont even have#do you know how much overdraft your bank account comes with?#sometimes the answer is 15k fucking euros
17K notes
·
View notes
Text

Horses are among the world’s most elite athletes: When galloping, they can consume twice as much oxygen per kilogram as the fittest humans. All that oxygen supercharges horses’ cells’ energy-producing compartments as they crank out ATP, the chemical needed to power their impressive muscles. But making so much cellular fuel so quickly comes with a catch: the manufacture of pernicious byproduct molecules called reactive oxygen species (ROS), which can wreak havoc in cells.
How horses dealt with this biological trade-off and evolved into premier endurance athletes has long intrigued biologists. Researchers report today in Science that they have uncovered a big part of it, identifying a key mutation that lets horses safely produce so much ATP. The trait helped pave the way for horses to go from dog-size critters millions of years ago to the high-endurance athletes we know today.
The study’s detailed molecular work makes it “exceptional,” says José Calbet, an expert on the cellular responses to exercise at the University of Las Palmas de Gran Canaria who wasn’t involved with the study.
The mutation in question occurs in the gene that encodes a protein called KEAP1, which acts as a biochemical bouncer, binding to a different protein called NRF2 to prevent it from entering the cell’s nucleus, where it would otherwise activate stress-response genes that help blunt cell damage.
But ROS can help NRF2 sneak in by causing KEAP1 to release its bind on the protein, allowing it to enter the nucleus and trigger the cell’s stress-response genes.
Johns Hopkins University ophthalmologist and clinician scientist Elia Duh, a senior author of the new study, didn’t set out to study horses. Initially, Duh was interested in the KEAP1-NRF2 system because its role in activating stress-response genes makes it a tempting target for treating inflammation—and aging-related conditions, such as blinding retinal diseases, irritable bowel syndrome, and neurodegeneration.
Duh wondered whether any insights could be gleaned from studying the evolution of these proteins in different animals. So, he teamed up with Gianni Castiglione, an evolutionary biologist and biochemist at Vanderbilt University. Together, they scanned hundreds of vertebrate genomes looking for notable mutations to the gene for KEAP1.
The team’s genomic work revealed birds had almost completely lost the gene, presumably an adaptation to the extreme demands of flight. When they looked in horses, researchers noticed what initially appeared to be a DNA sequence that encoded an unusually short—and therefore presumably nonfunctional—version of the KEAP1 protein. But when Duh’s and Castiglione’s team grew horse cells in culture, it discovered the protein was very much there and working. “Naturally, I was worried I was doing something wrong,” Castiglione says. “Then one day, a light bulb went off.”
As it turns out, the computer algorithm scientists had used to scan the horse genome had made a mistake. The algorithm had spotted a specific kind of mutation in the part of the KEAP1 gene that changed the messenger RNA from CGA—which codes for the amino acid arginine—to UGA, which is what’s known as a “stop codon.”
Normally, the cellular machinery interprets UGA as a sign to stop translating the RNA into a protein. But instead, the horses’ genetic machinery recodes the stop codon into a different amino acid, cysteine, causing it to ignore that order. This phenomenon, known as a stop codon read-through, is common among viruses but rare in multicellular organisms.
“The identification of this evolutionarily significant UGA recoding event represents a potentially seminal finding, offering a model for uncovering other yet-unidentified cases of stop codon read-through,” says Hozumi Motohashi, a biologist at Tohoku University who has studied KEAP1 and NRF2.
That the replacement is a cysteine is particularly notable, Castiglione says. KEAP1 senses cellular stress through its cysteines, which contain sulfur atoms whose reactions with ROS, induce the chemical changes that cause KEAP1 to let go of NRF2. The mutation the researchers had identified adds another place on KEAP1 for ROS to interact, which makes the protein more sensitive to stress—and lets horse cells respond much faster to the cellular stress of intense exercise. “It does make complete sense [that] by introducing another cysteine, another sulfur, you would have heightened sensitivity,” Castiglione says.
What’s more, this tweaking of KEAP1 is a “[key] genetic component to the puzzle of the evolution of horses,” Duh says. “Once they figured out how to run, they could occupy all kinds of ecological niches,” Castiglione adds.
The finding could also point the way toward new kinds of drugs to treat diseases by targeting the specific parts of the KEAP1 protein that help horses hoof it. “By looking at what evolution has figured out, we know this is a viable strategy,” Castiglione says.
Source
836 notes
·
View notes
Text
How to Burn Your Own CDs - a guide for Windows users
Are you--yes, you!--tired of paying money to stupid shit like spotify for your music? Do you hate the way that the music industry takes almost all the profit that bands make through streaming and leaves them with pennies? Have you ever wanted to fire up that old CD-Radio in the corner of your bedroom, only to be stopped because all you have on CD is Weezer's blue album and a copy of Kidz Bop 16 that you don't remember buying? Well this guide just might be for you!
Materials you'll need:
A computer. Can't do it without this one.
A CD drive. It can be internal or external, but you'll need one either way. You can find them at Office Depot for fairly cheap and I've heard that some Walmarts carry them.
A pack of CD-Rs. CD-Rs, or CD Recordables, come in packs of 20, 50, or 100. A proper 100-pack should cost you no more than $30, so unless there's some special shortage in your area, don't buy from anywhere selling them at a markup. CD blanks are literally 50c a piece.
CD cases. Sold wherever CD-Rs are, but you can also find these at thrift stores pretty easily.
A sharpie or some kind of permanent marker
Software you'll need:
Jdownloader. You can acquire mp3s through Bandcamp if you're dedicated to righteousness, but for everyone else, install jdownloader or some other kind of open-source download program. I will be proceeding as if you have jdownloader available.
Windows media player. This should open automatically when you insert a CD-R into your CD drive.
Fre:ac audio converter. This is only for the occasion that you encounter OPUS or mp4a files that cannot be interpreted by your CD player.
Note: If you're very determined not to download software onto your computer, you can use free youtube downloaders and audio converters, but these are subject to viruses and other issues such as download speed. I will be proceeding as if you have the programs I listed.
The process:
Decide what you want to burn--anything goes, but keep in mind the time limit on your CD-Rs. Most will record 90 minutes or less.
Open jdownloader, switch to the linkgrabber tab, then paste youtube links in any order until you have all the music you want. I'd personally recommend doing it song-by-song instead of a full album stream, because a massive file will require a lot of work to separate back into searchable tracks.
De-select all files except audio on the right-hand side options menu.
Make a folder inside the music folder of your laptop and label it with the name of your mix CD.
In the properties tab of each song on jdownloader, change the destination folder to the folder you've just created.
Hit "start all downloads".
Once finished, open each folder. If everything is an .mp3 or a .wav, skip the next 2 steps.
Open Fre:ac audio converter to convert all audio files that aren't .mp3 or .wav into .mp3 or .wav.
Drop the converted files next to the unconverted files in your folder. If you wish, you can delete the originals to make the folder easier to browse.
Put your blank CD-R into the CD drive. If external, plug in your CD drive first or the tray will refuse to open.
Windows media player will open automatically. On the right-hand side, you will see the tracklist of your CD-R (which should be blank). On the left, you will see the audio that your computer is able to find in the music folder. Put your selected tracks IN ORDER onto the tracklist.
Listen to the beginning and ending of each track to make sure there isn't a significant time gap. This also prevents accidentally burning a youtuber's stupid outro if you missed it before.
When satisfied, hit "start burn".
On an external drive, the CD tray will open upon completion. You can reinsert it to ensure that the burning went smoothly.
Once satisfied, remove the CD from your drive. With your sharpie or permanent marker, write the name of the album on the front, then store safely inside a CD case.
you did it👍
Ask me if you run into any issues.
Legal disclaimer: this guide is purely for educational purposes and I do not admit to or take responsibility for any piracy committed using the instructions given.
Illegal disclaimer: cops suck my dick
551 notes
·
View notes
Text
Also preserved on our archive
By Pandora Dewan
COVID-19 may leave some people with lasting memory problems long after their infection has cleared, new research has found, with the findings particularly pronounced among those who suffered from the earliest variants of the virus.
COVID-19 is known for its respiratory symptoms. But we are increasingly learning that SARS-CoV-2—the virus that causes the infection—can affect our brains too. Brain fog, cognitive deficits, and loss of smell and taste are commonly reported symptoms of the virus and some report these neurological symptoms long after the initial infection has subsided.
Scientists aren't entirely sure why the virus causes these symptoms, although lab-based studies have shown that the virus can disrupt the protective barrier that surrounds our brains and prevents foreign substances, like viruses, from entering. Research has also shown that the virus appears to affect the ability of our brain cells to communicate with each other, producing either too much or too little of key signaling molecules in the brain.
In a new study, published in the journal eClinicalMedicine, researchers from Imperial College London, King's College London and University College London Hospital in the United Kingdom set out to investigate the persistence of these cognitive symptoms even after milder COVID-19 infections.
In the study, 18 consenting unvaccinated volunteers with no prior exposure to SARS-CoV-2 were intentionally infected with the virus and monitored regularly over a 360-day period. Their cognitive function was measured at different points throughout the study and compared to what it had been before they were infected. They were also compared against 16 volunteers who were not infected with the virus.
This type of study is called a human challenge study and offer valuable insights into the onset of diseases and how they develop in a controlled medical environment.
"This is the first and probably will be the only Human Challenge Study to be conducted with Wildtype SarS-CoV-2 in people who were unvaccinated and who had not previously had the virus," the study's lead author Adam Hampshire, a professor of cognitive and computational neuroscience at King's College London and visiting professor at Imperial College London's Department of Brain Sciences, told Newsweek.
He added: "It also is the first study to apply detailed and sensitive assessments of cognitive performance from pre to post infection under controlled conditions. In this respect, the study provides unique insights into the changes that occurred in cognitive and memory function amongst those who had mild COVID-19 illness early in the pandemic."
During the study, the volunteers who were infected showed statistically significant reductions in cognitive and memory functions compared to those who did not receive the virus. These symptoms did not emerge right away but lasted for at least a year after the initial infection. This aligns with previous research from Hampshire's lab that sampled data from over 100,000 adults.
"Our previous research has shown that cognitive effects were the most pronounced for people who were ill with early virus variants, those who had persistent symptoms and those who were hospitalized," Hampshire said.
However, in the recent study, these long-lasting cognitive impacts were even seen in those who experienced milder symptoms (although it is worth noting that this may not be the case with newer variants of the virus).
So, how does the virus cause these cognitive impairments? Well, we still don't know for sure, but Hampshire said that those who had been infected with the virus showed an increase in a protein in the brain that is often associated with a brain injury.
"Future research should examine the biological mechanisms that mediate this relationship, determine how they differ to those observed for other respiratory infections, and explore whether targeted interventions can normalize these memory and executive processes," the researchers write in their study.
References Proust, A., Queval, C. J., Harvey, R., Adams, L., Bennett, M., & Wilkinson, R. J. (2023). Differential effects of SARS-CoV-2 variants on central nervous system cells and blood-brain barrier functions. Journal of neuroinflammation, doi.org/10.1186/s12974-023-02861-3
Trender, W. et al. (2024) Changes in memory and cognition during the SARS-CoV-2 human challenge study. eClinicalMedicine, doi.org/10.1016/j.eclinm.2024.102842
Hampshire, A., Azor, A., Atchison, C., Trender, W., Hellyer, P. J., Giunchiglia, V., Husain, M., Cooke, G. S., Cooper, E., Lound, A., Donnelly, C. A., Chadeau-Hyam, M., Ward, H., & Elliott, P. (2024). Cognition and Memory after Covid-19 in a Large Community Sample. The New England journal of medicine. doi.org/10.1056/NEJMoa2311330
#mask up#covid#pandemic#covid 19#wear a mask#public health#coronavirus#sars cov 2#still coviding#wear a respirator
163 notes
·
View notes
Text
🖥️ A Witch's Computer
Refresh your memory of your password by having a bag of lavender next to your computer.
Let snakes and dragons guard and protect your computer by either having them as your pause/desktop background or having statues near it.
Sprinkle cornflower to prevent evil spirits coming from your computer's reflective surface and into your home.
Much like a mirror, your computer screen is reflective too, so spiritually cleanse, protect, and lock it to prevent spirits to seep in and out.
Attach stickers of sigils (or draw them ) onto your computer, they can be of anything such as "focused work", "fast internet", "safe from viruses", etc.
Charge rubbing alcohol and clean your computer with it regularly.
Draw sigils in ms paint (or other drawing programs) and save the PNGs and have them on your desktop to see.
Lucky charms near your computer to ensure a good time on the internet.
Keep your grimoire digitally as well for easy fetching or write your stuff digitally first and refine until it's just right for you to put it on paper.
Scare away malevolant spirits by playing music from your computer speakers.
Glamour spells for your webcam.
#witchcraft#spells#my spells#grimoire#herbs#witch tips#witch computer#computer spells#protection spell#computer#witch#witchblr#witches of tumblr#luck spells#cleansing spells#sigils#magic#magick#luck spell
45 notes
·
View notes
Text
Jade Palace + Social Media
Basically, I thought up of a bunch of silly headcanons about if Po + the Furious Five had social media because I thought it would be funny. Enjoy!
Viper has the most followers. Like, she has millions of followers. She was also the first one to ask Shifu if they could get social media accounts, as she wanted to keep in contact with her family. Shifu kept telling her no, thinking such a thing would be a distraction for them. (Viper, then Monkey and Mantis, went behind his back and got accounts anyways. After Po came along and Shifu found inner peace and became a lot less strict to his students, he allowed them to get social media. They wisely pretended as if they never had it when they made their accounts public.) Viper was originally fine with just commenting on and sharing what her sisters and other family posted, but then she discovered ASMR, and fell absolutely in love with it. She developed a strong attachment to ASMR, and began practicing it, and people love it, thinking her voice and the rattles she makes when she moves are perfect for ASMR. She also gives excellent affirmations.
Monkey and Mantis also downloaded social media before Shifu allowed it. They both have a substantial amount of followers, with Monkey having slightly more than Mantis. Monkey posts selfies/pictures but also spams the group chat with memes. Mantis advertises his acupuncture services and sends extremely cursed memes to their group chat, which Monkey appreciates. Tigress is not so amused. She has threatened to block both of them multiple times in order to not see their constant cursed memes.
Po has the second most followers. He had social media before he became the Dragon Warrior that he used to market his dad’s business, but after he became the Dragon Warrior, naturally his follower account exploded, as did his dad’s business. Po fills his stories and posts with selfies and pictures of Shifu (despite him trying to avoid appearing on social media posts), the Furious Five, and shares all the content that his friends make. Naturally, whenever he posts pictures of him and the Five eating at Mr. Ping’s restaurant, Mr. Ping experiences a boom in business. Po also posts pictures of his food just as much--if not more--than his pictures of his friends and family.
Crane was somewhat hesitant to get social media, and his account was private for quite a while. He eventually made his account public after being peer pressured into it. He’s the least active of Po and the Five online, and Viper and Po (especially the latter) are trying to convince him to post his calligraphy and artwork, considering it to be quite skilled. His self-consciousness has prevented him from doing so thus far.
Tigress has the third most followers. She’s very no-nonsense on social media, and surprisingly, Po managed to talk her into getting it fairly soon after Shifu allowed it. Now, Tigress posts manageable workouts on her accounts for the average person, focusing especially on self-defense skills that women can use. Her popularity online has certainly grown quite well. Po also talked her into doing a couple lives with her followers, keeping everything professional and answering questions relevant to the content she posts. Po keeps trying to talk her into teaching a kung fu class for girls or a self-defense class for women in general. (“Come on! They think you’re awesome! They love you! You’re so hardcore!”) She may be considering it.
Shifu is not terribly technologically literate. He is definitely a boomer who would struggle to figure out how to download something to a flash drive. He also has a habit of taking pictures that are very off-center, or otherwise do not look great (his thumb has covered the camera several times before). He doesn’t have social media, and is constantly asking Po to teach him how to take good pictures (Po takes the best ones) and has accidentally downloaded viruses onto the Jade Palace computers twice. Oogway is chuckling at him from the Spirit Realm.
#kung fu panda#po ping#kung fu panda po#master po#dragon warrior po#master tigress#kung fu panda tigress#furious five#master crane#kung fu panda crane#master viper#kung fu panda viper#kung fu panda monkey#master monkey#kung fu panda mantis#master mantis#shifu#master shifu#master oogway#kung fu panda oogway
62 notes
·
View notes
Note
Mac, if you (or any sentient device) gets a virus, is that the equivalent of getting sick like humans? Or is there another analogy that we humans don't know about? And if the virus can't be fixed, is that basically like a fatal illness/injury for devices??? (I did remember in one of Mac's dialogue, they mentioned that the way computers sleep isn't the same as humans, or as simple as just shutting down or putting your computer to sleep.)
Ps. Same person who asked about if Mac had any wires in them. 😜
I guess it isn’t too indifferent from how humans become sick, it can be shared when interfacing with other electric based Things. Viruses are a more.. complex version of an illness, they can range from something terrible, it can be something that slowly shuts down our system over time to just a slight hiccup with processing power every now-and-then. There are always ways to prevent Viruses, running scans to check for malware and not downloading from sketchy websites are always excellent places to start.

But in the more serious case where it has already imbedded it’s roots in our software it may call for something akin to a uhh.. factory reset.

13 notes
·
View notes
Text
Glitch and Virus are everything to meeee
Sometimes I see minor characters, go "is anyone going to obsess over them", and not wait for an answer.
I know I've talked about my pet headcanon of Glitch and Virus being twins. And possibly their father being named Bug. And of Virus being Machina's weird mad scientist on retainer.
I think it would also be fun if Glitch and Virus both struggled to be functional. This is partially supported by Virus' personality in-canon as a mad scientist who behaves in a very bubbly manner despite committing crimes against the Iron Realm's nonexistent board of ethics. Very easy to say she has some sort of mood instability, and if GlitchandVirus (singular item) are related, there's a decent chance it could run in the family, with Virus simply having much more prominent symptoms. But also, the place of a glitch or virus in computer science is at its core, something malignant. They are things that are meant to be fixed or prevented. Especially glitches— viruses are at least made intentionally, even if its for the sake of harming something else, but no one wants a glitch in their system. So it is very possible that it runs deeper.
Which brings me to my theory that while both Glitch and Virus share some issues with emotional regulation and obsessive tendencies that made everyone in the Iron Kingdom a little afraid of them, Glitch is also physically disabled. Compared to everyone else in the Iron Kingdom, especially the Lieutenants, we don't see Glitch using glamor hardly at all, and I think it's because glamor makes someone more powerful. And if someone's very nature is a code mistake, that same power makes the mistake more prominent. For the sake of the electrical theme of the iron realm, I would propose that Glitch has something very similar to autoimmune epilepsy/convulsions that are triggered by glamor usage. So can he use glamor? Aboslutely. Is he going to? Not if he has literally any other option, because there's only so long he can use it before it rebounds and starts to hurt.
(Which makes their place as Machina's Lieutenant/A rebel leader/Meghan's First Lieutenant even more impressive: not only does he command respect of Iron Fey, but he does so while not being able to use the glamor that everyone around him takes for granted.)
This would also add an interesting layer to Virus being the Iron Realm's mad scientist. Because they grew up in the Eugenics Kingdom. They drank the Koolaid about the oldbloods dying out because they couldn't evolve to survive, and the Iron Fey being right to push for an invasion because it's natural for the strong to supplant the weak. So both of them being mentally unstable and one of them being physically disabled gives Virus a lot of motivation to look into how glamor works and why Iron glamor is incompatible with oldbloods but compatible with humans, because she wants to understand what went wrong with both of them. Maybe it will lead to fixing her brother, or fixing herself. Or at least limiting their symptoms.
And it explains why both of them decided to A) usurp Ferrum, and B) Antagonize Meghan even after she inherited Machina's iron glamor. Neither of them are blindly loyal to whoever sits on the throne and wields the glamor of the Iron Ruler, because they know better than to trust whoever happens to wield the most power. They know their survival isn't a guarantee in a kingdom that would see people like them as a drain on resources the moment they're no longer beneficial, and have to be cutthroat and back the ruler that will keep them alive rather than the one who has a "divine right" to power.
(No wonder, then, that Virus would want that power for herself.)
#iron fey#Virus (Iron Fey)#Glitch (Iron Fey)#am I making things up? Maybe so#look the Iron Realm is full of eugenics philosophy so I have to peel back how it impacts disability#And Glitch was in a full war and STILL not using glamor! There should be a reason for that!#Jkags give me an iron realm prequel I promise I'll be normal about it#<<<absolute bullshit lies
10 notes
·
View notes
Text
Prevention Techniques for Top 10 Common Cyber Attacks

In the ever-escalating war against cybercriminals, staying informed about the most common attack vectors is half the battle. The other half is implementing robust prevention techniques. As we navigate 2025, the threat landscape continues to evolve, but many foundational attack methods remain prevalent due to their effectiveness.
Here's a breakdown of the top 10 common cyber attacks and the essential prevention techniques to keep you and your organization secure.
1. Phishing & Smishing (SMS Phishing)
The Attack: Attackers impersonate trusted entities (banks, colleagues, popular services) via email or text messages to trick recipients into revealing sensitive information, clicking malicious links, or downloading malware. Modern phishing often uses AI to generate hyper-realistic content.
Prevention Techniques:
Vigilant User Education: Train employees to scrutinize sender email addresses, hover over links to check destinations, and be suspicious of urgent or generic requests. Conduct regular simulated phishing tests.
Multi-Factor Authentication (MFA): Even if credentials are stolen, MFA can block unauthorized access. Enforce it widely.
Email & SMS Security Solutions: Deploy advanced email filters (e.g., Microsoft Defender for Office 365, secure email gateways) that scan for suspicious patterns, attachments, and URLs. Forward suspicious texts to 7726 (SPAM).
DMARC, SPF, DKIM: Implement these email authentication protocols to prevent email spoofing of your own domain.
2. Malware (Viruses, Worms, Trojans)
The Attack: Malicious software designed to disrupt, damage, or gain unauthorized access to computer systems. Malware can be delivered via downloads, malicious websites ("drive-by" attacks), or attachments.
Prevention Techniques:
Antivirus/Endpoint Detection & Response (EDR): Install and keep robust antivirus and EDR solutions updated on all devices.
Regular Software Updates: Patch operating systems, applications, and browsers promptly to close security loopholes that malware exploits.
Firewalls: Use network and host-based firewalls to control incoming and outgoing network traffic.
Download Caution: Only download software and files from trusted, official sources. Scan all downloads before opening.
3. Ransomware
The Attack: A type of malware that encrypts a victim's files or locks their system, demanding a ransom (usually in cryptocurrency) for decryption or restoration of access. It often enters via phishing or exploiting unpatched vulnerabilities.
Prevention Techniques:
Robust Backups: Implement a 3-2-1 backup strategy (3 copies, on 2 different media, with 1 copy off-site and isolated/immutable). Regularly test recovery.
MFA & Strong Passwords: Crucial for protecting remote access services (like RDP) often targeted by ransomware operators.
Vulnerability Management: Continuously scan for and patch vulnerabilities, especially on internet-facing systems.
Network Segmentation: Divide your network into isolated segments to prevent ransomware from spreading laterally if it gains a foothold.
Security Awareness Training: Educate employees about ransomware's common entry points (phishing).
4. Distributed Denial of Service (DDoS) Attacks
The Attack: Overwhelming a target server, service, or network with a flood of internet traffic from multiple compromised computer systems (a botnet), aiming to disrupt normal operations and make services unavailable.
Prevention Techniques:
DDoS Protection Services: Utilize specialized DDoS mitigation services (e.g., Cloudflare, Akamai) that can absorb and filter malicious traffic.
Content Delivery Networks (CDNs): CDNs distribute traffic and cache content, helping to absorb some attack volume and improve resilience.
Rate Limiting: Configure servers and network devices to limit the number of requests they will accept from a single IP address or source over a given time.
Network Redundancy: Ensure your infrastructure has redundant systems and sufficient bandwidth to handle traffic spikes.
5. Man-in-the-Middle (MitM) Attacks
The Attack: An attacker secretly relays and possibly alters the communication between two parties who believe they are directly communicating with each other. This often happens over unsecured Wi-Fi.
Prevention Techniques:
Always Use HTTPS: Ensure websites you visit use HTTPS (look for the padlock icon in the browser address bar) to encrypt communication.
Avoid Public Wi-Fi for Sensitive Tasks: Refrain from accessing banking, email, or other sensitive accounts over unsecured public Wi-Fi networks.
Use VPNs (Virtual Private Networks): VPNs encrypt your internet traffic, creating a secure tunnel even over public networks.
Strong Authentication: Implement MFA and passwordless authentication to mitigate credential theft even if traffic is intercepted.
6. SQL Injection (SQLi)
The Attack: An attacker injects malicious SQL code into input fields of a web application to manipulate the database, potentially leading to unauthorized access, data theft, or data corruption.
Prevention Techniques (primarily for developers):
Prepared Statements & Parameterized Queries: The most effective defense. Treat user input as data, not executable code.
Input Validation & Sanitization: Validate and sanitize all user input on both the client and server sides to ensure it conforms to expected formats and removes malicious characters.
Least Privilege: Grant database accounts only the minimum necessary privileges required for their function.
Web Application Firewall (WAF): WAFs can detect and block common web-based attacks like SQLi.
7. Cross-Site Scripting (XSS)
The Attack: Attackers inject malicious client-side scripts (e.g., JavaScript) into web pages viewed by other users. This can lead to session hijacking, defacement of websites, or redirection to malicious sites.
Prevention Techniques (primarily for developers):
Output Encoding/Escaping: Properly encode or escape all user-supplied data before rendering it in HTML to prevent it from being interpreted as executable code.
Input Validation: Validate user input to ensure it doesn't contain malicious scripts.
Content Security Policy (CSP): Implement a CSP to restrict which sources are allowed to execute scripts on your website.
Sanitize HTML: If your application allows users to input HTML, use robust libraries to sanitize it and remove dangerous tags/attributes.
8. Zero-Day Exploits
The Attack: Exploits that target newly discovered software vulnerabilities for which a patch is not yet available. They are extremely dangerous because there's no immediate defense.
Prevention Techniques:
Layered Security (Defense-in-Depth): Rely on multiple security controls (firewalls, EDR, IDS/IPS, network segmentation) so if one fails, others can still detect or contain the attack.
Behavioral Analysis: Use security tools (like EDR, UEBA) that monitor for anomalous behavior, even if the specific exploit is unknown.
Application Whitelisting: Allow only approved applications to run on your systems, preventing unauthorized or malicious executables.
Rapid Patch Management: While a patch doesn't exist initially, be prepared to deploy it immediately once released.
9. Insider Threats
The Attack: A security breach or data loss caused by a person with authorized access to an organization's systems and data, whether malicious or accidental.
Prevention Techniques:
Principle of Least Privilege (PoLP): Grant users only the minimum access necessary to perform their job functions.
User Behavior Analytics (UBA/UEBA): Monitor user activity for anomalous behaviors (e.g., accessing unusual files, working outside normal hours).
Data Loss Prevention (DLP): Implement DLP solutions to prevent sensitive data from leaving the organization's controlled environment.
Employee Training: Educate employees on security policies, data handling best practices, and recognizing social engineering.
Offboarding Procedures: Have strict procedures for revoking access immediately when an employee leaves.
10. Brute Force & Credential Stuffing
The Attack:
Brute Force: Systematically trying every possible combination of characters until the correct password or encryption key is found.
Credential Stuffing: Using lists of stolen usernames and passwords (from previous breaches) to try and log into accounts on other services.
Prevention Techniques:
Multi-Factor Authentication (MFA): The most effective defense, as attackers need a second factor beyond just the password.
Strong Password Policies: Enforce complex, unique passwords that are difficult to guess.
Account Lockout Mechanisms: Implement policies that temporarily lock accounts after a certain number of failed login attempts.
Rate Limiting: Restrict the number of login attempts from a single IP address over a period.
CAPTCHA Challenges: Introduce CAPTCHAs or other challenge-response mechanisms during login to differentiate humans from bots.
Threat Intelligence: Monitor dark web forums for compromised credentials and prompt affected users to reset their passwords.
By proactively addressing these common attack vectors with a layered and comprehensive security strategy, individuals and organizations can significantly strengthen their defenses and foster a more secure digital environment. Stay informed, stay vigilant, and make cybersecurity a continuous priority.
2 notes
·
View notes
Text
Daily Lives of Jujutsu High Students
Time set in around 2006-2007.
This story tells the daily lives and youthful troubles of four students from a certain year at Tokyo Jujutsu High.
Various x F. Reader!
Other chapters: 01

02 - Online Chatting Requires Caution
Although the curriculum at Tokyo Jujutsu High is different from other schools, it covers basic subjects such as Japanese, mathematics, science, and social studies to ensure students' comprehensive development. With the rapid development of information technology, the use of computers has also increased. In order to prevent students from becoming too disconnected from the non-sorcerer world, the school has recently added a new subject - Computer Class!
However, only a few students take this class seriously. Most students use computer class time to play games. Unfortunately, this has led to many students downloading pirated games from illegal websites, resulting in a large number of infected computers at the school. It wouldn't be an exaggeration to call the computer room a den of viruses.
"Darn it!" You mutter as you stare at the blue screen of the computer. "This one got infected too!"
"Forget about playing World of Warcraft," Gojo, sitting next to you, says. "I heard there's something popular these days that everyone is playing."
You turn your head and look at Gojo curiously. "What is it?"
"It's a random chat room," Gojo explains. "You can go in and have random video chats with people from other countries."
"Really? Let's give it a try then!"
Without hesitation, Gojo types a string of English letters into the search engine, and the computer quickly loads a website with a simple design. The website's name is written in large letters in the upper left corner, and there are two button options below it.
"You can choose to use text or video," Gojo says.
"It would be too embarrassing to start with video on the first try. Let's go with text," you say.
Gojo slides the mouse and clicks on the button labeled "TEXT."
With a click on the "TEXT" button, the page turns into a chat interface. There's a message box at the top with the words "Matching now..." displayed. Within a few seconds, a new pop-up message appears saying, "Start chatting!"
Excitedly, you pat Gojo on the shoulder and exclaim, "Oh, we've got a match!"
Gojo, with a disdainful snort, says, "You're getting excited so easily. You really are an inexperienced bumpkin."
Ignoring Gojo's sarcasm, you focus your attention on the computer screen. Another message pops up in the chat interface, displaying the username of the matched person.
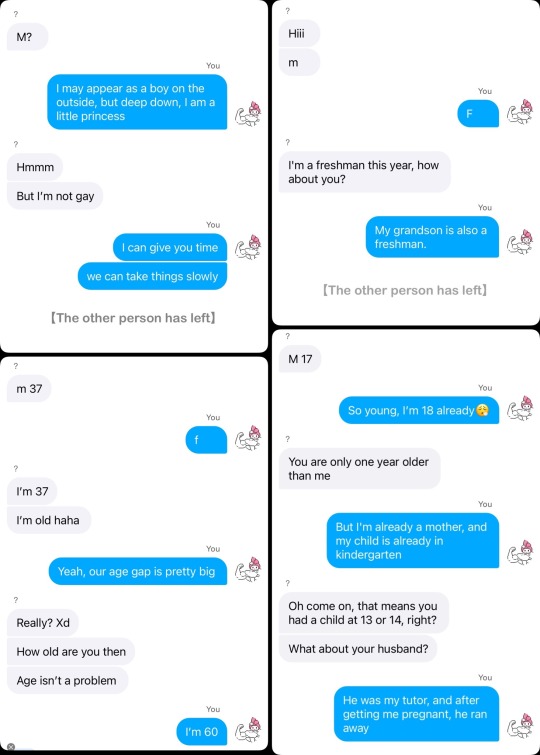
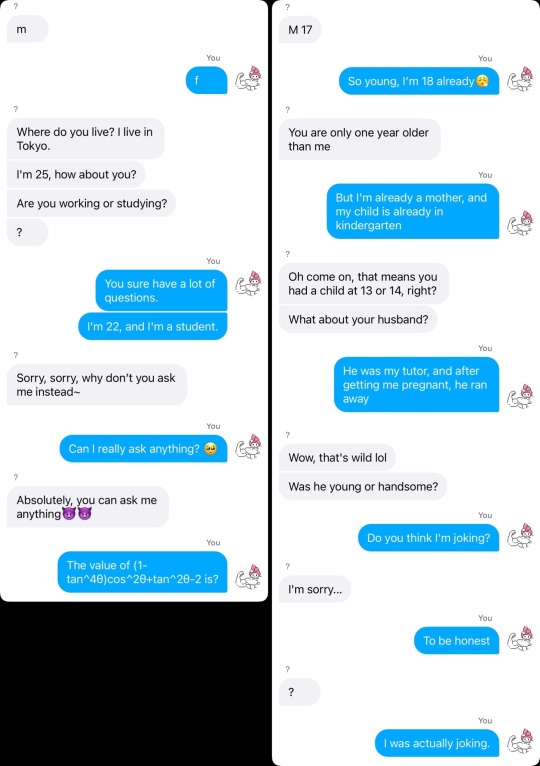
Florida Man:Hi
"Oi, oi!" You point at the chat box, looking at Gojo in panic. "He said hi! What should we do?!"
"Calm yourself, Just reply to him!" Gojo says dismissively.
"Um, then..."
You type a sentence on the keyboard, a versatile English phrase that you've been using from elementary school to now, guaranteed to be appropriate in any situation:
You: Hello, nice to meet you and you^_^?
The system immediately displays the message, "The other person has left the chat room."
"Damn, are you a grade schooler?!" Gojo curses.
"Well, how else should I respond?!" you retort, displeased.
"Let me handle it. You're still too inexperienced."
With that, Gojo starts a new match with another chat partner.
You: Hi^_^!
The dark urge: Hello~
The dark urge: mf?
As you and Gojo look at the newly popped-up chat box, both of you have a puzzled expression on your faces.
"What does 'mf' mean?" Gojo asks.
You ponder for a moment, then suddenly have an epiphany. "I know! It's probably short for 'male or female.'"
"Oh! You're quite smart!" Gojo compliments.
You run your hand through your hair and raise your nose, saying, "Duh."
Then you start typing on the keyboard again.
You: f
The dark urge: m34 horny?
"'Horny'? What does that mean?" This time it's your turn to ask.
"Hold on, let me get someone who's good at English." As soon as Gojo finishes speaking, he pulls Geto, who was sitting in the front row, engrossed in watching a pirated version of "Naruto," to the back of the classroom.
"What idiotic thing are you two up to again?" Geto says, while being pushed by Gojo towards the computer.

"Suguru, can you help us translate this message into Japanese?" you point at the English message that both you and Gojo couldn't understand.
"You guys are really troublesome," even though Geto complains, he still looks at the text in the chat box. "Oh, this means—'Do you want to get naughty?'"
Just as Geto finishes speaking, the chat room immediately receives a barrage of messages all at once.
The dark urge: I wanna f___ u so damn hard kitten
The dark urge: i wanna lick u so hard that you start peeing uncontrollably babygurl
The dark urge:*babygirl
The dark urge: let me see ur p___
"Wait, what is he saying?" You feel a sense of shock as the messages keep coming in.
The dark urge: wanna s___ my hard disco stick?
The dark urge: horny?
The dark urge: horny?
"Oi! Is this person insane?" Gojo also appears astonished.
However, Geto remains unfazed and calmly translates every word and phrase from the stranger's messages into Japanese. "He's saying he wants to f___ you hard, then wants to lick you until you start losing control, and he wants to see your ___, and then asks you to look at his ___."
"So disgusting, so disgusting, so disgusting!" You cross your arms in front of your chest, feeling as if you've been sexually harassed by the online user. Goosebumps immediately form on your arms, and your mind feels like it's being bitten and itchy, as if by countless ants.
Gojo keeps clicking the refresh and match buttons while frowning, saying, "Next one, next one!"
Geto simply shrugged, seemingly unfazed. "You should expect to encounter weirdos like this when you play these chat matching games."
"That's not an excuse for harassing others online!" you replied without hesitation.
The next few matches were almost all starting with the phrase "Horny?" In fact, as soon as you told them you were male, they would immediately leave the chat room. It felt like a complete adult chat room, as if all the horny foreigners had gathered in one place.
After two days of browsing this website with Gojo, you both learned a lot of English words and phrases that kids your age shouldn't be learning. Your English vocabulary skyrocketed.
"Yo, yo, check it out! Satoru, wanna s___ my d___? Mine d___ is huge!" you imitated the tone of an American hip-hop artist on TV.
"Ayo, Y/n, you wanna [censored] with me? Just [censored] my [censored]," Gojo responded in the same tone.
Listening to your conversation, Geto sighed and rubbed his forehead. "Are these two the future pillars of the Jujutsu world? I'm starting to worry about the future of Jujutsu world."
"Maybe it would be better for me to go to medical school?" Ieiri muttered, unusually serious. "If the Jujutsu world collapses, I can still become a doctor."
Nanami frowned as he listened to your and Gojo's nonsense. "What on earth have these two gotten into?"
As soon as you saw your junior, Nanami, you smiled and reached out your hand to him. "Nanamin! Let's have [censored] with us!"

Gojo also took off his sunglasses, revealing his blue eyes that resembled the clear sky and white clouds. He extended an inviting gesture towards Nanami and said in a slightly exaggerated accent, "Yesu, yesu, Nanami, let us [censored] your [censored]!"
For the next week, Nanami would immediately have a dark expression and run away whenever he saw you and Gojo.
After realizing that chatting about explicit content in the chat room was boring, you and Gojo came up with a new game.
"Hey, how about we wait for a chat and directly give them our English assignments?" you suggested.
"That's a good idea!" Gojo clapped his hands. "So, you do have a brain hidden under that skull of yours."
"Shut up, or I'll cut off your [Censored]." you threatened.
You thought Gojo would be scared after hearing your words, as that area is of great importance to men, almost as much as their life. However, Gojo not only wasn't scared, but he even blushed and said shyly, "Oh, if you want to see it, just say it directly, no need to be so subtle."
Your mind couldn't come up with any other words. You really weren't good at dealing with Gojo.
Instead of wasting precious time in computer class playing around with Gojo, you quickly posted the English assignment question in the chat room.
John: m 22
You: Which of the following is the correct definition of the word "ephemeral"?
A) Long-lasting
B) Temporary
C) Permanent
D) Reliable
John: B
Impressed by the swift response from the user named John, you exclaimed, "This foreigner's English is really impressive!"
"Idiot, what did you expect? He's a foreigner, of course his English is good," Gojo said.
"So let's quickly give few more questions to him!" you exclaimed excitedly, holding your English assignment in your hand.
As a result, the two of you used the chat room as a tool for completing your assignments, and the foreigner on the other side genuinely explained the questions in English.
"What should we do? He seems like a smart and handsome guy," you daydreamed, imagining a man with a handsome face, flowing golden hair, and a smooth British accent.
"Get real, Y/n," Geto's cold voice mercilessly shattered your imaginary image of the handsome man. "How could someone like that play in a random chat room?"
"No, you're totally wrong, Suguru," you immediately retorted. "Even a beauty like me is playing in this kind of random chat room."
Geto and Gojo looked at you with disdainful expressions.
"You are too full of yourself." Gojo said.
Just as you were about to say something, a new message appeared in the chat room.
John: So that's all?
You: Yeah! Thanks ;-)
John: It's not a big deal.
John: Cam?
"Cam?" Gojo paused for a moment. "Does that mean video chat?"
"Quick! I want to see what that person looks like!" you eagerly said.
"But...is it okay to—"
You interrupted Gojo's words and impatiently shouted, "Let me see my future husband already!"
Reluctantly, Gojo opened the video chat, but what appeared on the screen was the other person's genitals, and they were in an erect state.
"There you go!" Gojo frowned, pointing at the bright red and erect disco stick. "I told you, these people are abnormal! They're nothing but sex-starved beasts!"
You silently stared at the computer screen and after a while, said with a serious expression, "Seems pretty big."
"It is indeed quite big, estimated to be around 8 inches. The first time must be painful," Ieiri commented, appearing out of nowhere.
Gojo snorted disdainfully. "But it's still far inferior to mine."
"Really?" You remained skeptical and to confirm whether Gojo was really as impressive as he claimed, you looked at Geto and asked, "Suguru, is what he said true?"
Geto's face twitched. "Why are you asking me?"
"Because you and Satoru are close male friends. Don't guys usually compare each other's [censored]?" you asked, tilting your head.
"That's absolutely not true!" Geto shouted in frustration. "And where the hell did you hear about such things anyway?"
"Oi, you brats."
At that moment, a voice that didn't belong to any of the four of you spoke up.
You and the others mechanically turned your heads to see Yaga Masamichi, your homeroom teacher, standing behind you four, glaring at you four with anger.
"The computer teacher reported to me that you're often not paying attention in class, so I came to see what's going on. Turns out, you're all using the computers for these kinds of websites during class! Each of you will write a reflective essay of no less than a thousand words for me. It must be submitted by Friday, and if it's late, you'll have to add five hundred words! Understand?"
Under the absolute authority of your homeroom teacher, you four dared not rebel and could only nod obediently.
From that day on, you were haunted by the shadow of these chatting rooms. Whether it was the reflective essays that Yaga-sensei relentlessly returned or John's massive cannon, every time you thought about it, you felt like peeing yourself.
※※※
Epilogue:
Many years later, even though you had long graduated from Jujutsu High, and many of your friends had already carried away by the flowing river of time over the past decade, you, the old classmates, still kept in touch and occasionally gathered for meals.
Tonight, you all met at an izakaya as usual. The attendees included you, Gojo, Ieiri, Nanami, Ijichi, and Utahime and Mei Mei, who were several years ahead of you.
Since Gojo didn't like to drink and Ijichi had to drive, only you, Ieiri, Nanami, Utahime, and Mei Mei ordered alcohol, while the other two opted for non-alcoholic beverages.
You looked at the melon soda, french fries, and fried chicken in front of Gojo and couldn't help but mock, "Satoru, this won't do. What if your future father-in-law is a heavy drinker? You'll have to drink then, right? Practice your tolerance now and finish this bottle of vodka in one gulp!"
You raised the transparent glass bottle in your hand and placed it in front of Gojo, who then returned the bottle to you. "Instead of worrying about my future father-in-law, why don't you worry about yourself first?" he said. "Isn't your mom pressuring you? Miss still single at 27 years old."
As soon as this topic came up, you let out a groan and covered your head with both hands. "Ah, please don't mention it anymore! My mom recently forced me into a blind date!" Then you released your hands and looked at Nanami, who was sipping whiskey, with a serious expression. "Nanamin, why don't we get married?"
"No, thank you," Nanami refused without hesitation.

Laughter immediately erupted from the table, with Gojo being the loudest of them all.
"Of course, Nanami mercilessly rejecting you again!" Gojo exclaimed loudly, as if afraid others wouldn't hear.
"You're not doing much better than me either! Isn't your mom pressuring you to get married? Saying it's time to continue the Gojo lineage and produce another Six Eyes successor. I heard all of this from my mom," you glared angrily at Gojo, then turned to Utahime sitting next to you and deliberately spoke in a dejected tone, "Forget about Satoru, but why are you laughing too, Utahime?"
Utahime wiped away a tear from the corner of her eye and chuckled, saying, "Sorry, sorry. No matter how many times I hear it, it's still funny."
"Sigh, go ahead and laugh. You won't be laughing when I marry some old, greasy geezer," you said.
"You don't have to be so despairing, Y/n," Mei Mei said. "Marrying an old geezer has its benefits. After all, the old geezer will die soon, and then you'll inherit his fortune."
"I think the same," Ieiri, who had already finished a large glass of beer, nodded.
"But I want someone who's handsome, whose parents died early, and who has a family fortune," you said.
Gojo laughed again. "Aren't you describing Batman?"
"Haha, very funny," you replied sarcastically.
"Let me tell you guys," Utahime said, "I actually met a cute guy on a dating app recently."

"Huh? A dating app? Isn't that for sex or something?"
Upon hearing your blunt remark, Nanami and Ijichi, who were drinking at the time, both choked and coughed several times.
"But I still prefer getting to know people proactively," you said with a smile. "The connection between people is still more important, hahaha!"

"Y/n is right," Gojo crossed his arms and nodded. "I also prefer genuine connections, ahahaha!"

That night, as soon as you returned home, you immediately registered an account on the dating app and matched with a guy. You started chatting.
You: Hi there, I'm from Tokyo 😊😊
Infinity: Hi👋🏻 I'm also in Tokyo, what a coincidence~
You: Really? What are your interests?
Infinity: I like reading books in my free time, and I also play the violin when I have the chance.
You: Violin? That's impressive~ 🤭
You: So, what do you like to eat?
Infinity: I have a sweet tooth, I drink my bubble tea with full sugar, and I put eight cubes of sugar in my coffee. I'm also the Japan's second-best fan of buttered potatoes. I don't smoke or drink. I sleep at 11 p.m. and make sure to get less than 8 hours of sleep every day. Before bed, I always have a glass of warm milk and do 20 minutes of stretching. Once I get into bed, I immediately suffer from insomnia. I stay up all night until morning, but I never carry fatigue and stress into the next day. Doctors say I'm perfectly normal.
You: Wait a minute.
You: Horny?
Infinity: GOD DAMN
These are the conversations you and Gojo had with strangers on that chat website during your computer class:
#anime#jjk#jujutsu kaisen#jjk x reader#gojo satoru x reader#geto x reader#nanami x reader#shoko x reader#jujutsu kaisen x reader
37 notes
·
View notes
Note
https://www.tumblr.com/moons-of-milo/784010840264294400/yall-wanna-hear-about-the-fucken-uhh-into-the <- IM ONE HOUR LATE BUT YES
HELL YEA OK !!!! TW for like bullying and mentions of suicide bee tee double you !!! more under cut yay
Mylo C. (UTMV s/i) is the main one !! he dates Night ofc (though sometimes I will just draw errormare bc I kin error!!). "MyloMare"
He lives in night's castle and hangs out with the 'bad sanses' and is a very silly werewolf werecat thing.
he has the most lore (which I may write and post eventually) but basically if we reeally dumb it down: NM is drawn to Mylo's AU "Undersky" due to the negativity -> he reminds NM of his younger self -> Mylo's bullies try to drown him -> NM takes Mylo in -> yaoi -> Mylo learns that NM is low-key a terrorist after getting kidnapped by the star sanses & they have a whole angst arc -> The bad sanses and dream truce -> MORE YAOI :)
Mylo "Warden" C. (Creepypasta s/i) is slenderman's adoptive son and lateeeerr Jack's bf "KidneyKeeper" is their ship name lol
He's the most simular to me in physical appearance since he's meant to be an older version of an alternate universe me.
Basically he lives basically the same life as me (but is being stalked by Slenderman) -> but at 14/15 he tries to commit a double suicide with an AU version of my current bf -> bf succeeds but Mylo fails & ends up spending a month in the psych ward -> The literal second he gets out he buys an axe, makes a mask, and kills his whole family in the middle of the night. He becomes the "warden" of the creepypasta manor and makes sure that nobody gets in or out who shouldn't !! he meets jack and they start dating after Mylo gets hurt and has to spend a while under jack's supervision bc I'm a stubborn mf
Mylo Vermin (Helluvaverse s/i) is either Vox's bf or Alastor's weird pet freak depending on the route. Their ship names r "StaticRat" & "RadioRat" respectively
He's a rat demon who died and went to hell for making viruses that cost several companies billions of dollars in damages & committing hella fraud !!! He was also probably low-key a scammer.
The minute he gets to hell he creates a computer virus that costs voxtek MILLIONS IN DAMAGES ^__^. Depending on which AU this is he's either is snagged by Al to prevent Vox from getting his hands on the rat boi's computer skills, OR Vox takes him and forces him to use these computer skills on his behalf. Either way, shenanigans ensue.
Mylo "Doc" C. (Pokemon s/I) Is GUZMA'S BF !!! their ship name is "Phasmid" or "Exoskeleton" bc they specialize in ghost and bug types respectively
I lied he's actually probably the one who looks most like me considering that he is literally just an older me. He's also 1/2 zoroark. His Pokemon team consists of Decidueye , Ditto , Gengar , mimikyu , and 2 twin lycanrocs if u were wondering :3 also bonus trevenant but his typing is redundant and I considered giving him a pallosand but again redundant-
Basically !!! He's from Unova but gets yoinked by CPS because he's basically an orphan -> gets adopted by a lady in Alola where he meets Guzma when they're both like 12 -> gets taken by CPS AGAIN bc the lady low-key sucks so he has to go back to Unova -> then moves BACK TO ALOLA to study and become a pokemon biologist where he and guzma reunite awww
Mylo C. (FNAF s/i) He dates Sundrop and Moondrop ! their ship name is "Skyzone"
He's again basically just an older version of an AU me-
AuDHD dysfunctional rat of a college student somehow lands a job w/ fazbear entertainment !!! He's basically their "handler" and does nightly repairs on the boyz !! when the pizzaplex burns down he lowkey steals them and they live 2gether yayyy
#sorry my brain started melting towards the end of this#/nf to read this I'm just happy to yap !!!#<🦇> s/i
2 notes
·
View notes
Text
Okayokayokayokay more brainrot for my headcanons of the Addisons time except this is probably turning into an AU-
So you know how computers and other electronics have a Safe Mode setting right? Limited functions and capabilities usually for the purpose of finding viruses?
Okay so like WHAT IF ADDISONS HAVE THAT... when they get infected with a virus they can set their systems to Safe Mode until they get to a repair shop to limit the spread of the virus? And it affects them in such a way that they're either A) loopy, or B) more salesman-like than normal (or the secret third option of 'what's funnier for the bit') since it would reduce their minds to mostly the bare minimum requirements to function. Maybe they can't perceive or think of certain things properly - like it being replaced with a blob of ones and zeroes in their vision and minds - since some things wouldn't be considered 'essential' to perceive. And then this is effectively like how our bodies fight off infections and fevers naturally, except for them it's moreso preventing it from spreading too fast until they can be repaired. When they're not in Safe Mode, virus effects are far more prominent and debilitating.
Aaaaaand now I want to make art of how different viruses affect an Addison when they're not in Safe Mode so like- that would be fun to depict :D
#yet another headcanon to add to my 14 page Google Doc of Addison headcanons#deltarune#the addisons#addisons#headcanons#spamton
17 notes
·
View notes
Text
One of the (many) reasons I think people need to use libraries more is that it would seriously reduce the "need" for chatgpt/similar AIs.
Sometimes a topic IS difficult to research and it CAN be hard to know where to start.
Anecdote: I know someone who, when confronted by a whole lotta irrelevance in their first several online searches, will then plug their whole, wordy, unpolished question with several synonyms per term into an AI and get a fairly clear, if flawed, summary and then they ignore that and ask it for source suggestions and seach terms to learn more about it and look up those seperately. I don't advocate for that, but it shows a usecase I think most of the "people are just using chatgpt to cheat on homework" crowd are ignoring. (And yeah, I agree, a lot of people are using chatgpt to cheat on homework, that happens too.)
Many libraries have research assistants, and even in those that don't, most librarians are more than happy to point you to good sources.
Worried the library is unlikely to have books on the topic you're researching? I've been there, given the number of recent case studies on hyper-specific forensics topics I've written for college. But you know what librarians are great at? Library science. Libraries have computers, and often libraries will have subscriptions/access to some journals and academic databases. Librarians are very, very good at using those databases, and research in general, and they're usually very enthusiastically willing to help, especially if you go on a quiet day.
Fun fact: library computers are also a fairly anonymous way to do research. Libraries might have usage guidelines for their computers to prevent things like people downloaded a massive number of viruses on them, but I promise you the librarians are not judging you. Think of them like the doctors of academia (not to be confused with PhD in Education, that's totally different). Doesn't matter what your research is, ask for help if you need it.
If your search engine is giving you nothing, or if you're stuck, go to a library.
#libraries#librarians#chatgpt#gen ai#artificial intelligence#academia#research#school#college#google#search engines#duckduckgo#bing#long post#hal rambles#informative#yeah i was somewhat annoyed at my friend Insisting perplexity and the like is the future of research...#the only reason it's filling a niche is because of the enshittification of search engines#but even with that...there's still libraries and academic databases#colored text#(moderate use for readability)#green text
2 notes
·
View notes
Text
Also preserved in our archive
By Jess Thomson
Samples from wastewater in several U.S. states have tested "very high" or "high" for levels of the virus that causes COVID-19.
SARS-CoV-2 levels were found by the U.S. Centers for Disease Control and Prevention (CDC) to be "very high" in New Mexico for the period November 10 to November 16, 2024, and "high" in Arizona, Kentucky, Minnesota, Oklahoma, Pennsylvania, and South Dakota.
"Moderate" levels of the virus were detected in Colorado, Idaho, Maine, Maryland, Ohio, Oregon, Rhode Island, Utah, and Wyoming.
More From Newsweek Vault: What Is a Health Savings Account?
19 states had "low" levels detected, while "minimal" levels were spotted in 14 states and D.C.
(follow the link for an interactive map!)
However, the data from Arizona, Oklahoma, South Dakota, Mississippi, and Ohio all have limited coverage, meaning that it is "based on a small segment (less than 5 percent) of the population and may not be representative of the state/territory," the CDC explained. North Dakota also has no data for this period.
The week prior, between November 3 and November 9, "very high" levels of viral activity were also detected in New Mexico, with "high" levels being found in Montana, Wyoming, and South Dakota.
Many viruses are excreted in feces, even if the infected individual has no symptoms. This includes SARS-CoV-2, which has been shown to be present in the gastrointestinal tract of infected individuals. Once in the wastewater system, viral particles, or fragments of their genetic material, are carried to treatment plants. Testing of this wastewater can detect these fragments, providing valuable information about the presence of the virus in a community.
By regularly testing wastewater, the CDC can track trends in viral levels, helping public health officials assess whether COVID-19 cases are increasing, decreasing, or remaining stable in a community.
"Wastewater monitoring can detect viruses spreading from one person to another within a community earlier than clinical testing and before people who are sick go to their doctor or hospital. It can also detect infections without symptoms. If you see increased wastewater viral activity levels, it might indicate that there is a higher risk of infection," the CDC explains.
CDC data shows that COVID virus levels have hugely dropped since the summer months, with most regions still trending downwards. However, there is a slight uptick in virus activity in the Northeast and the Midwest
As of November 16, subvariant KP.3.1.1 made up 34 percent of COVID-19 cases in U.S. wastewater over the previous two weeks. New XEC variant made up 21 percent, KP.3 made up 18 percent, JN.1 made up 13 percent, and "other" made up 15 percent.
"There is no evidence, and no particular reason to believe, that XEC causes different symptoms than all the other SARS-CoV-2 currently in circulation," Francois Balloux, a profesor of computational systems biology at University College London in England, previously told Newsweek. "XEC is not expected to cause more (or less) severe symptoms than other lineages currently in circulation."
#mask up#public health#wear a mask#covid#pandemic#wear a respirator#covid 19#still coviding#coronavirus#sars cov 2
29 notes
·
View notes
Text
What is a Trojan Horse? Types & Prevention
In the realm of cybersecurity, the term "Trojan horse" is frequently used, often causing confusion with other forms of malware like viruses or worms. Named after the ancient Greek story of the deceptive wooden horse, a Trojan horse in the digital world is a type of malicious software (malware) that disguises itself as legitimate or desirable software to gain access to a user's system.

Unlike viruses, Trojans do not self-replicate by infecting other files. Unlike worms, they do not spread autonomously across networks. Instead, Trojans rely on deception and user interaction to propagate. A user must be tricked into downloading and executing the Trojan, believing it to be something harmless or useful, such as a free game, a legitimate software update, an email attachment, or even an advertisement.
Once inside, a Trojan can perform a variety of malicious actions, often without the user's immediate knowledge, potentially leading to significant data loss, privacy breaches, and system compromise.
How Does a Trojan Horse Work?
The modus operandi of a Trojan horse typically involves several stages:
Infiltration: The Trojan is disguised as a legitimate file or program and delivered to the victim, often via phishing emails, malicious websites, infected downloads, or compromised software.
Execution: The user, unaware of the hidden malicious payload, executes the seemingly innocuous program.
Payload Delivery: Once executed, the Trojan installs its malicious component onto the system. This payload can vary widely in its function.
Malicious Activity: The Trojan then performs its intended harmful actions, which could range from stealing data to providing remote access to the attacker.

Common Types of Trojan Horses
Trojans are versatile and can be designed to achieve various malicious goals. Here are some common types:
Backdoor Trojans: These create a "backdoor" on the victim's computer, allowing remote access and control to the attacker. This enables the attacker to perform various actions, such as uploading, downloading, and executing files, deleting data, or even rebooting the computer.
Exploit Trojans: These contain data and code designed to exploit vulnerabilities within legitimate software applications running on the computer. By exploiting these flaws, they can gain unauthorized access or elevate privileges.
Rootkit Trojans: These are designed to conceal the presence of other malicious software on the system. They modify operating system files to hide processes, files, and network connections from detection, making it difficult for antivirus software to find and remove them.
Downloader Trojans: Their primary function is to download and install other malicious programs (like more Trojans, adware, or spyware) onto the victim's computer without their consent.
Dropper Trojans: Similar to downloaders, droppers contain the malicious payload within their own code. Once executed, they "drop" or install the malicious program directly onto the system.
Fake Antivirus Trojans: These masquerade as legitimate antivirus software, often displaying fake alerts about infections and demanding payment to "clean" the system. In reality, they are either doing nothing or actively installing more malware.
Game-Thief Trojans: Specifically designed to steal user account information (usernames, passwords) from online gamers.
Mailfinder Trojans: These harvest email addresses from the victim's computer, which can then be used for spam campaigns or further phishing attacks.
Ransomware Trojans: Encrypt files on the victim's computer and demand a ransom (usually in cryptocurrency) for their decryption. If the ransom is not paid, the files may be permanently lost.
SMS Trojans: Primarily target mobile devices, sending expensive SMS messages to premium-rate numbers without the user's knowledge, leading to unexpected charges.
Spy Trojans: Designed to spy on user activity, collecting sensitive information such as browsing history, keystrokes, screenshots, and financial data, which is then sent to the attacker.
Web-Page Defacer Trojans: Modify web pages, often by injecting malicious code or defacing the content.
Prevention Strategies
Protecting yourself from Trojan horses requires a multi-layered approach and constant vigilance:
Use Reputable Antivirus/Anti-Malware Software: Install and maintain a high-quality antivirus program from a trusted vendor. Ensure it's always up-to-date with the latest virus definitions and performs regular scans.
Be Wary of Email Attachments and Links: Exercise extreme caution with unsolicited emails, especially those with attachments or links. Verify the sender's identity before opening anything. If it looks suspicious, delete it.
Download Software from Trusted Sources Only: Only download applications, games, and files from official and reputable websites or app stores. Avoid third-party download sites that might bundle legitimate software with Trojans.
Keep Your Operating System and Software Updated: Software updates often include patches for security vulnerabilities that Trojans might exploit. Enable automatic updates whenever possible.
Use a Firewall: A firewall monitors incoming and outgoing network traffic and can block unauthorized access attempts, preventing Trojans from communicating with their command-and-control servers.
Enable Pop-Up Blockers: Malicious websites often use pop-ups to trick users into downloading Trojans. A pop-up blocker can help prevent these deceptive tactics.
Be Skeptical of "Too Good to Be True" Offers: Free software, incredible deals, or urgent security alerts that appear out of nowhere are often a sign of a scam.
Regularly Back Up Your Data: In the event of a Trojan infection, especially ransomware, having recent backups of your important files can save you from permanent data loss.
Educate Yourself: Stay informed about the latest cybersecurity threats and best practices. Understanding how Trojans and other malware operate is your first line of defense.
By combining robust security software with careful online habits, you can significantly reduce your risk of falling victim to a Trojan horse attack.
Source: https://interdata.vn/blog/trojan-la-gi/
1 note
·
View note