#Torrent Combat Data
Explore tagged Tumblr posts
Text
AC-LOG 1 ::020725::
USER [C4-621 "Raven"] DEPLOYED Custom AC - TORRENT
Cleared assigned missions: - Retrieve Combat Logs - Investigate BAWS Arsenal No 2 - Attack the Watchpoint
UNIT COUNT SUBMITTED TO ALLMIND
COMBAT EFFECIENCY NOTES GENERATED:
RANGE OF WEAPONS INEFFECIENT [ADAPT ASSEMBLY FOR PULSE SHIELD ENCOUTERS] -you're doing well, keep it up- ANALYSE ENEMY HABITS BEFORE UTILISING FULL SYSTEM AGGRESSION [DO NOT GET CAUGHT OFF GUARD]
-OBJECTIVES CLEARED BY -A Y R E- -
USER "Raven" LOG:
Shes in here. Not comms but here. As if my blood burns with her voice. Something happened at the watchpoint, the coral surged and we,, I got consumed by it. Once our systems were back online we heard her. Ayre. She claims to be a Rubiconian, this may become a problem knowing the path Walter wishes to take. She seems to have clearance to act as our operator while Walter is out on "business". Could be a chance to avoid resting and keep moving. -you will be resting, you need to recover- Outside of that uneventful. Some dog named Sulla and an autonomous craft got in the way briefly. Oh. And Little Ziyi. They all went down easily despite pulse shields. We should get outfitted with something to get them out of the way quicker.
LOG CLOSED
#guh this ones late as hell#we're busy prepping for pride#as soon as that passes we're doing longer sessions so we can write more#we ALMOST did BALTEUS first try but we got distracted#Sulla was fun to bully though#and that time limit for the combat logs was tricky alongside Little Ziyi#Thats our own fault for not prepping for pulse shields tho#armored core 6#media in the system#Torrent Combat Data
8 notes
·
View notes
Text

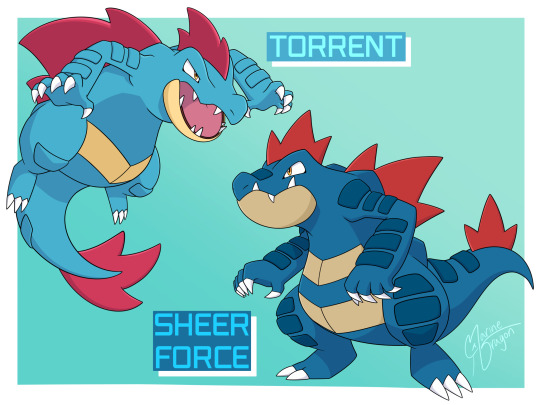
I made some ability forms for Porygon Z and Feraligatr for @n0rtist’s Ability Form Challenge!
Each of the Porygon Zs has a different color palette referencing the one it has in the anime (Download), Gen 4 sprite art (Adaptability), and the Sugimori artwork (Analytic).
Reasoning for each:
Torrent Feraligatr is more aquatic in nature and has a tail fin, large back sail, and its spines are more aerodynamic.
Sheer Force Feraligatr has put more energy into its physical power in exchange for losing some of the more extensive effects of its elemental power. This has made it unable to use statuses or secondary effects but has physically powered up those moves that normally rely on them.
Download Porygon Z is still loading its textures and is thus able to modify its physical properties to better combat its opponent.
Adaptability Porygon Z is able to change its appearance to its dimensional environment. Being more in tune with its different versions has led it to being more in tune with its own innate power.
Analytic Porygon Z is more calculating and tends to move after its opponent in order to gather and analyze their data to better execute its attacks.
1K notes
·
View notes
Text
Disobedient Girl
(Captain Rex x Reader)
Pulled from another previous draft, this is just straight porn. MINOR DNI! 18+ only.
Figured I’d do a little Rex appreciation post cause he’s my favourite Captain. I think he’s pretty hot.
(Divider by @pinkiemme )
Warnings: SMUTTTT, voyeurism, Captain! kink, sex toys (vibrator, butt plug, dildo), pet names, f! Masturbation, gagging, bondage, punishment, oral sex (f! And m! receiving), dirty talk, p in v sex, multiple orgasms, over stimulation, cream pie, cumplay, Rex is kinky af, aftercare, cuddles, FLUFFY
Words: 5.8K+


Today was a training and evaluation day. A very long, tiring, boring day of target practice, hand to hand combat evaluations and physicals for most of the 501st. Anakin had made sure that the 501st had a few extra days between missions especially after the last one that took a toll on the men.
In return, they had a day dedicated to training and physical examinations to ensure they were still in peek performance condition. Rex was walking around the training deck of the Resolute, watching as his brothers completed exercises and evaluations one after the other.
By the time their evaluations were over and training was finished for the day, the men were ready to hit the showers, all of them eager to wash off the sweat from their bodies. Rex stood with Anakin for a few minutes, going over a few charts and strategies before the Jedi bid Rex a farewell, congratulating him on a great session. Rex gave a nod in thanks, finishing off one more document before hooking his data pad to his hip, making his way over to where a handful of the torrent company were laughing.
"Where's (Y/N)?" Fives asked Jesse, wiping the sweat from his face and bringing his canter of water to his lips for a sip as Rex came toward the company. Rex tilted his head in slight confusion before his eyes darted about the training room, watching as his brothers began to make there way out. However, Rex couldn't see their civilian medic anywhere, your absence slightly concerning.
"I don't know," Jesse asked, his eyes also surveying the room before they settled on Rex, eyeing his elder brother with curiosity eyes, "Do you know where she is?"
Rex looked back to the group as all eyes now turned to him, each of his brothers having a different expression on their face. Fives looked smug as ever, knowing that the good captain and their medic had something going on. Jesse looked a little confused, genuinely wondering if she was okay. Hardcase was trying his best to conceal his laughter, seeming to know something that Rex and the rest of the company didn't. Tup and Dogma were quiet, just observing the tomfoolery of the company, neither of them fully understanding the dynamics yet as the two newest members.
"I don't know, she was here an hour ago," Rex said with a slight tilt of his head, voice smooth even as he began to slowly piece together what probably happened. You had seemed a little on edge this morning, stressed over the amount of work today would bring but Anakin had reassured you that he and Rex would both help out. There was one thing he could think of but Rex knew that you wouldn't disobey a direct order from him unless absolutely necessary...or were you going to be a bad girl today?
He was snapped out of thoughts by a firm grip on his shoulder, turning his gaze to Hardcase who smirked at the good captain, "I'm sure she just hiding from you, or she just got tired and went for a nap," he said, squeezing Rex's shoulder before hooking his arm around Fives, guiding the arc out the door.
The rest of the group shrugged, getting up to follow Fives and Jesse as left the training room to go and shower and get something to eat. Rex pondered on those thoughts for another moment before a sigh left his lips, walking back towards the barracks, taking a left turn instead of right to make his way to your room.
As Rex got closer, he could hear the faintest sounds of pleasure through the door even a few doors down the hall. He walked a little faster, a smirk playing in his lips as he came to a stop outside your door, the moaning becoming only slightly louder, but still muffled through the durasteel.
His smirk grew wider, his head handing down as her shook his head, 'I knew she wouldn't be able to wait," He chucked a bit at the thought, turning to make sure the coast was entirely clear before he lunched in the code for you door, watching it slide open quickly and quietly so that you werent alerted of his presence. The door slid closed behind him, the lock engaging with a small push of a button as Rex stood against it to watch you.
He finally concluded that you had left training early because you were feeling frustrated, in need of a release that he had promised to grant you after evaluation were over. However, it seemed as though you were too impatient to wait for him and instead, decided to pleasure yourself. It was something Rex had told you not to do but it seemed today that you wanted to be a disobedient girl which made the captain twitch almost happily.
He told you that after training and evaluations, he wanted you to go get all of your toys and put on your favourite lingerie, all under the guys of following one rule, 'Don't touch yourself till your captain gets there.'
By the look of things, you had obeyed him for the most part, gotten all your toys out including you vibratior, butt plug, and your favourite dildo. You had put on your favourite blue lingerie, the set that drove Rex wild, seeing you in his colours sending his blood pumping straight to his cock. But, you had failed to follow his number 1 rule and instead, chose to touch yourself. Now you were on your back in your bed, eyes closed and fingers playing with your clit while, -still unknown to you- Rex was leaning against the door watching. He waited to see if you'd notice him, his cock getting harder under his codpiece the more he watched.
You continued to moan Rex's name -while occasionally moaning his title, captain, something that had him, removing his codpiece the second it left your lips- as you played with yourself. Finally, after another couple minutes of watching you bring yourself close to the edge, he decided it was time to make his presence know.
"Well, well, well," Rex tsked, watching as your eyes shot open like saucer before quickly removing your hand from your clit. You looked at him in shock, not having heard him enter the room at all but soon, your expression turned to one of regret, knowing that you had gone against him.
You knew you were going to get punished for this and part of you was excited but nervous, "What did Captain say ad'ika?" He asked you in a low, husky voice walking over to the bed.
"Captain said not to touch myself," You said quietly, head hung and eyes downcast as you looked at your slick hands in your lap.
"And what did you do?" He asked, leaning over you and tilting your chin up so that your eyes meant.
"I touched myself," You said shyly, eyes remorseful as Rex nodded at you with a smirked adorning his lips, "Am I going to get punished captain?" You asked, even if you already knew the answer to that simple question.
He smirked at you, nodding his head agains as you looked at your hands once more, "Of course you're going to get punished baby girl, you disobey your captain," Rex said, moving away from you slightly, "Get your gag and the rope mesh'la," he instructed as he pick up the plug and vibrator you had bought on your last shore leave on Coruscant.
You nodded obediently, reaching over to the night stand and pulling out what he had asked for. The rope was standard with hints of silk to make sure there was no rope burn afterward. The gag was simple yes affective, a black ball with blue straps to secure it around your head.
"On your stomach baby," Rex ordered, as he picked up the ball gag, placing it in your mouth and securing it to the back of your head. He then proceeded to tie your arms behind your back, being gentle while still making sure the rope was tight enough. When the rope were secure, he slowly and teasingly slid two fingers down your spine, running them both between your asscheek before sliding them inside of your slick opening, pumping them in and out a few times. When rex removed his fingered, he refrained from licking them clean, instead, using them as lube for the butt plug in his other hand.
"Ass up mesh'la," He instructed devilishly, a groan falling from his lips as you followed orders like a good girl. Rex took a moment to tease the tight ring of muscle before you felt the plug make it's way inside, moaning at the mixed feelings of pain and pleasure.
He watched as your ass greedily swallow the plug, the royal blue jewel sitting snuggly between your cheeks once the plug was all the way inside you. Rex took his time admiring his handy work before taking hold of the vibrator, teasing it over your clit lightly before holding it your pussy lips.
"Now, I'm going to put this in that tight little pussy of yours, but you're not allowed to cum till I get back, understand?" Rex said as he teased your entrance with the vibrator a little more, putting the smallest amount more pressure on it, drawing a whimper from your throat.
You only nodded as Rex pushed the vibratior inside you, turning it on the lowest setting and using his fingers to move it around slightly. You moaned from behind the gag as the vibrator found its home inside you, the low vibrations teasing you and making you think of what's to come.
Rex stepped back a little, admiring the view of you tied up, ass in the air with a butt plug in your ass and a vibrator in your weeping pussy. He moved his hand down to stroke himself through his blacks, groaning at the thought that you were all his to enjoy. Rex moved back to the bed and sat down, manoeuvring you across his lap to give you your second punishment, "Count baby girl. Count how many times I smack your ass."
He barely gave you a chase to nod as his hand made contact with your behind firmly, feeling the heat blossoming from where his hand landed. You moaned lowly, counting muffled from behind the gag as Rex landed another one.
This continued till Rex had spanked you 15 times, your butt now red and heated but only added to the pleasure of the plug and the vibratior inside you.
"That's a good girl. You look so pretty with that in your pussy," Rex's cooed, moving back to your previous position on the bed, "Now remember no cumming till I get back. I'll bring you some food ok?"
You nodded slightly eyes closing to bask in the little simulation the vibrator offered, though those thoughts were interrupted as you moaned louder, feeling the vibrations spike. Rex had turned up the speed of the toy before he shoved your ass back down so you lay flat on the bed, legs already beginning to twitch. With that, Rex left you alone on your bed with the plug and vibratior inside you, simulating your body in a delicious way.
~Time Skip~
It had been half an hour since Rex had left the room, leaving you alone with your punishment. It was becoming harder by the second to refrain from cumming, the over sensitivity of your core growing with every passing moment. Between the vibratior and the plug it was hard, the sensations mounting into a flurry of pleasure almost bordering on pain. You were sweating, panting, moaning, and shaking all together, legs almost numb from the amount of will power you were exuding.
That's when the door opened to reveal Rex with a tray of food and a glass of canteen of water from the mess, a cheek smile on his face and his gaze fell upon your taut form.
"Hey baby girl." he walked over and set the tray and water on the nights stand, eyes almost never leaving yours, "You doing okay?" He asked, running a hand up your leg then giving your ass a smack.
"Sis-seen!" You said from behind the gag, drool slipping out from the sides of your mouth. Rex chuckled at your continued count of spanks watching as your eyes were blown wide, legs clenched tightly to refrain from cumming undone and from letting the vibrator slip out.
"That's my good girl," He praised, scratching your scalp gently, sending a full body shiver coursing through you. He trailed his hand down your head to the strap of the gag, quickly undoing the strap and tossing it toward the fresher. Once it was off you gasped, drawing in the fresh air and licking your now semi dry lips. You were panting as you looked up a Rex with clouded (E/C) eyes, desperate to cum now that he had returned.
"C-captain, Please," you begged weakly, as the vibratior continued to simulate you, the feeling intense and almost unbearable.
"Please what ad'ika," Rex said teasingly. He clearly knew what you wanted but was being a little shit about. He wanted to hear you beg for it.
"PLEASE! Please sir let me cum I wanna cum so bad daddy, please!" You begged again, closing your eyes to try and hold on to what little control you had left.
"Okay mesh'la, since you asked so nicely," Rex said, moving onto the bed before manoeuvring you onto his lap just like he had done earlier.
"Ass up baby," Rex said and you obeyed, lift your butt in the air as much as you could in your position. Rex ever so slowly took hold the plug, slowly pulling it out and watching as your hole puckered and clenched around nothing. You whimpered at the loss of fullness, feeling somewhat empty now that the plug was gone.
"It's ok cyare," Rex cooed as he placed the plug on the night stand, running a soft hand along your ass before moving to the vibrator. Rex took hold of it but instead of pulling it out, he turned the speed up even higher and began thrusting it in and out of you, drawing a scream from your lips
"FUCK! Fuck that feels so good sir! PLEASE can I cum CAPTAIN please?" You cried out as Rex thrusted the vibratior deeper into you, pushing it as far as your body would take it.
Rex continued this for a bit till he leaned down to your ear and whispered your words of saving grace, "Cum for me."
You screamed as your orgasm ripped through you, Rex quickly pulling the vibratior out of you and watching as your juices coated, the sheets, his thighs and yours, your core convulsing as a second orgasm ripped through you simultaneously. Your cunt fluttered around nothing, trying and failing to take something in to fill the void once more. Rex then put the vibratior down on the nights stand and untied your hand from behind your back, carefully rolling you around and pulling you to sit in his lap properly.
"That was so good mesh'la, you came some much," Rex praised you even more his arms circling you body as he began to massage your back and your arms. You smiled weakly and moved your arms to stretch above your head, feeling your shoulders pop slightly.
"Thank you sir," you said, eyes locking with Rex's as he continued to loosen your upper body, hands finding every knot and tense muscle he could. He smiled and gave your ass another light smack, moving his hand away after to begin removing his vambraces.
"Seventeen," You said breathlessly making Rex chuckle, bringing his hand up to run his fingers through your hair, "That's my girl."
You smiled, sighing pleasantly as Rex continued to give you a massage to help you relax and recover from your punishment. You two stayed there for another few minutes, just basking in each other's presence. By now you had tucked your head Rex's neck as much as you could with his armour still on, hand gripping the lip of his chest plate.
"Captain?" You asked, tracing circles over Rex's chest where his heart rested beneath his armour and blacks.
"Yes cyar'ika?" He replied, planting a sweet kiss to the top of your head, looking down at you with a smile.
"Can I pleasure you now?" You asked innocently, eyes meeting his as you moved away from his neck.
"Of course you can ad'ika," Rex said as he cupped your cheek. You leaned into his touch, turning to kiss his palm before your eyes met once more. You nodded and slid from his lap, carefully lowering yourself onto the floor to begin removing his leg armour. Rex watched as you meticulously removed his armour, placing it next to the bed in the order you knew he liked, being respectful of the plastoid used to protect the men.
Rex offered his assistance by removing his vambraces, gloves and rerebraces, moving up his arm until they were left covered by his blacks. He passed each piece to you, admiring how you took such good care of each piece. Once his legs were bare, you stood up, sliding your hands up his chest and finding the latches on his shoulders to remove his cuirass. Rex closed his eyes as you worked, enjoying being taken care of even if today was supposed to be about you.
Soon his armour had been removed, placed neatly in an orderly pile next to the bed. You moved back to him and hooked your thumbs wordlessly into the hem of his shirt, tugging the fabric up and off of his body to reveal his muscular torso. Your eyes stayed gazing at his chest for a moment before you moved onto Rex's bottom's, eyes locking with his as you silently asked for permission to remove them. The captain lifted his hips off the bed to give you room, pulling his black bottoms and standard issue boxers off in one smooth motion.
You took the time to fold his blacks and place them on top of his armour before turning back to Rex on your knees. You ran your hands up and down his powerful thighs, feeling how the muscles contracted under your touch. You kissed along his legs, making your way up to his throbbing cock, watching as it bobbed with his restraint not to pick you up and fuck you.
You smiled up at your captain before taking hold of his dick, giving it a few experimental pumps before licking from the base to the tip, taking him into your mouth slowly. You took your time swallowing him, eyes flickering up to his face to gage his expression.
Rex sat there in pure bliss, hand coming up to stroke your hair as you continued to suck him off, "That's feel so good ad'ika," he praised, threading his fingers in your hair as you took him deeper.
You sucked a little harder, pulling off only slightly to focus on his tip, lapping at the sensitive head. Rex threw his head back, grunting at how good it felt to have your mouth on him. His grip on your hair tightened, urging you to take more of him in your mouth once more. Soon you were deepthroating him, thanking the maker that you had no gag reflex to hinder your ability to bring Rex pleasure. You felt Rex's cock twitch inside your throat, prompting you to hollow your cheeks and suck a little harder.
"Fuck, I'm gonna cum cyare," He moaned, both of his hand finding purchase in your hair as he flooded your mouth and throat with his cum. You took a deep breath through your nose, eyes closing as you sat on your knees and took his load.
"Such a good girl for me," he said huskily, pulling his dick from your mouth, watching as you quickly shut your mouth, eyeing him in a wordless gesture.
"Open," He ordered, groaning as you opened your mouth and showed him his juices that coated your mouth and throat. It was a filthy thing to enjoy the sight but Rex couldn't get enough of it, knowing that you were his and only his.
"Swallow," He growled, watching as you obeyed him, swallowing him cum and opening your mouth to show him that you did. Rex let pleased growl simmer in his throat, leaning down and planting a bruising kiss to your lips.
"Good girl," Rex praised as he brought you back onto his lap, arms circling you somewhat possessively even if he knew you were going anywhere. He began kissing, biting, sucking and licking your neck while grabbing your ass firmly in his hands, needing the soft yet muscular flesh in his large, warm palms.
You moaned as he took one of your breasts in his mouth, suck vigorously on your nipple like a hungry man. He moved his hands from your supple behind, running them up and down your back soothingly. Rex took a moment to bask in the feeling of you in his arms, mouth wrapped around one of your breasts and hands roaming your body as if you commit everything to memory once more.
He pulled away from your chest, gently laying you down on your back as he kissed down your body, worshipping your every curve and dip, every little scar or beauty mark he found. He kissed his way down until he reached your clit, looking up at you to take in your features. Sweat gleamed on your forehead, cheeks red and eyes shining and blown wide with lust, your lips caught between your teeth in anticipation for his next move. Rex licked his lips, taking one last moment to admire your beautiful body before abruptly leaning down, licking a long strip up you folds, sucking your lips into his mouth before moving on to your clit, a sharp, breathy, moan leaving your body.
"Mmmm, you taste so good ad'ika, so sweet," Rex said as he sucked harshly at your clit. All you could do was moan and buck your hips into his mouth, feeling over sensitive from his earlier punishment. Rex moved his mouth down to your abused hole, watching as it fluttered just from his hot breathe. He stuck his tongue out, licking from your entrance to your clit and back before dipping inside of you, a loud drawn out moan falling from your lips. He brought one of his hands up to rub rough circles on your clit.
"C-captain, I-I'm close," You moaned, stuttering as you bucked your hips into his mouth and hand, feeling your orgasm coming quickly.
"That's it cyar'ika, you like it when I devour your pussy don't you? You like when I play with your clit? You like when I shove my fingers inside you and pump them till you cum?" Rex said as he moved his fingers and tongue faster on your clit, moving his other hand down to your pussy lips and entering 3 fingers inside you making you scream. You threw your head back, neck strained slightly as your hands came down to Rex's wrist, trying to push him away from your over sensitive lips.
"Can I cum captain! Please captain can I!" You begged, panting and writhing about as his fingers even moved faster. His pace on your clit was blindingly fast as his fingers inside you moved with a speed akin to hyperspace, bringing stars to the front of your vision.
"Cum for your captain ad'ika, cover my fingers and tongue in your sweet juices," Rex said, pressing his fingers against your g-spot, tongue lapping at your clit aggressively. The action had you screaming as you came on his fingers and tongue, legs shaking and pussy clenching around his digits.
Rex pulled away from your lower half, chin covered in your sweet nectar as he brought his fingers to his mouth, licking them clean of your juices before moving back up your body, leaning down and kissing your lips. He hungrily nipped at your lips, giving you a taste of yourself which made your breath hitch. He pulled away all too soon, hand reaching down to give himself a few pumps, a deep groan leaving his lips.
"You taste so good mesh'la," Rex said as he lined himself up with your dripping core, cock weeping with the need to finally feel your warmth around him.
You laid there panting beneath him, staring into those amber eyes that you had seen on thousands of men. But Rex's were somehow different, with a touch more brown along the bottom of his iris and more depth to get lost in. You brought your hand up to his face, your thumb brushing against his cheek softly as you admired him. You moved down his body next, tracing the scars on his chest and his arms, many of which had long since healed and faded though a few new ones took there place, nothing major but still added to his collection of what you had dubbed his trophies of war. Your eyes trailed back up to Rex's, smiling up at the man you so luckily called your own.
"Even with all these scars you're still the most handsome man I've ever known. These scars just mean you're a warrior, someone who does whatever he can to protect his brothers, his family," You said as you looked up at him, bringing your hand back up to his face. You cupped his cheek again, just holding him there, the trance of lustful need broken for a moment in favour of soft blissful intimacy shared between soulmates.
Rex looked down at you with eyes to innocent for someone who had just dragged two powerful orgasms out of you. But soon his lips morphed into a gentle smile, not a smirk, or a cocky grin, but a really genuine smile. He leaned down, lips meeting yours in a gentle, loving kiss, lips soft as they fit together like puzzle pieces.
"Thank you," Rex said quietly, taking a moment to relish in the calm, intimate atmosphere that you two had created, greatful to have you in his arms. As he pulled away. You just smiled up at his and wrapped your arms around his neck.
"You ready mesh'la?" Rex asked, his voice low and lustful, sending a tingle up your spine. All you could do was nod, hands coming up to grasp at what little hair his blonde buzz cut offered as your eyes rolled back, head fall back toward the mattress as Rex pushed inside of your awaiting walls.
"Mmm, Fuck captain, you're so big," You moaned at the pleasurable sensation, feeling entirely filled by the man above you. This wasn't your first time with Rex and it most certainly wouldn't be the last, but even after having the vibrator and Rex's finger give you two orgasms to stretch you open, he was still quite big.
"You like the feeling of my cock inside your pussy ad'ika, like how it's stretching you so much, you like it when fuck you," Rex spoke huskily to you, continuing to whisper dirty things as his hips finally rested flush against yours.
"Yes sir," you said breathlessly, feeling the air leave your lungs. It was then an idea popped into your head, a risky idea and could get you punished again but you wanted to push Rex, wanted to rile him up.
"Does my tight little pussy feel good around your cock captain? Does it milk your big cock well," you said confidently, wiggling your hips to emphasize, clenching your core to draw him in.
Rex was about to start thrusting though he stopped abruptly when he heard you say such vulgar things. Your actions coupled with your words drew a slight grunt from the captain, not having expected such display. He looked up at you with dark, lustful eyes and for a moment, the confidence drained from your system, replaced by fear and doubt about your words.
Rex smirked, pulling almost all the way out of you, leaving just a sliver of his tip in to tease you. He stayed there for a moment, taking his time and letting you squirm, anticipating his next move just by looking in his eyes. You went to open your mouth, a snarky quip on the tip of your tongue, though before it could see the light of hyperspace, Rex slammed back into you, electing a scream from your lips instead.
"That's it baby girl, scream for your captain. Scream my name as I pound into your pussy," Rex said as he drove his cock into you with quick, forceful thrusts, his filthy words making your hips buck and his name fall from your lips in a loud yell.
He thrusted into you without hesitation, hips slapping against your forcefully. You could feel your asscheeks bounce with every one of his thrusts, skin slapping against skin, heat blooming over your behind with how hard Rex pounded into you. You could feel your legs shake as Rex gripped your tights, pushing your legs into your chest for an even deeper angle.
The position had you keening, back arched in the heated pleasure you were receiving. Your hands gripped the sheet below you as Rex leaned over your body, nipping at your neck and listing to every moan and whimper you released. He groaned in your ear, thrusts never faltering in their haste to bring you to orgasm, his rhythm remain ing consistent and steadfast.
"Faster captain, Please!" You begged. You were a panting, moaning mess as Rex flipped you over onto your hands and knees, someone how maneuvering you so well that he didn't need to pull out. That realization flooded you with even more arousal, knowing that there must have been a part of him that didn't want to come out even to change positions.
"As you wish mesh'la," Rex said lowly, speeding up his pace as his grip on your hips tightened, using your love handles to his advantage. He leaned down and kissed your neck then moved to kiss your shoulder blades and down your back.
He moved his hands around your body till one was on your breasts, needing your mounds and pinching your nipples between his fingers as the other went down you pinch and rub your clit. You screamed at the over simulation of your body hips stuttering ever so slightly before you began to thrust your hips back to met Rex's brutal pace.
"I'm so close Rex," you moaned as you felt him pick up the pace, hips slammed into your ass with force that would surely leave bruises in their wake.
"Me too cyar'ika," Rex whispered in your ear as he sped up the movements of his hands, furiously rubbing your abused clit. You moaned loudly at the continued simulation, feeling your orgasm begin to run down you legs. Rex could feel it in the way you clenched around him, gripping his cock like vice as his thrusts became sloppy. He leaned down as best he could, lips finding your ear as he gave a teasing nip and a few words that took the breath right out of you.
"Cum for me." You screamed as your orgasm ripped through your body, arms shaking as they gave out beneath you. The movement caused your ass to hike up further, the new angle allowing Rex to thrust even further into your warmth.
You heard grunting from behind you, knowing that he was close to his end just from the way his breathing chanced. At that moment, you wanted to feel him cum, needed him to fill you, so you decided to push him over the edge.
"Please cum inside me with your big cock Captain, want you to fill me with your sweet cum, please," you begged desperately, wanting to feel every inch of him fill every crevice of your pussy. You looked back at him over your shoulder, forehead gleaming with sweat and eyes dilated almost beyond recognition. Rex stared at you before listening to the very low whimpered plea that left your lips.
"Please Captain."
Rex let out a loud grunt turned groan, hips stuttering as he released his seed deep within you, coating your inner wall in a creamy white. You moaned loudly, back arching at the sensation of being filled by your captain before collapsing on the bed, exhausted and ready to sleep.
Rex pulled out of you slowly, arms twitching with the sensation of just how tight you were even after your orgasm. He fell almost unceremoniously onto the bed next to you, a smirk pulling at his lips at your blissed out expression, pulling the covers over top of both of you, to rest just above your chest.
He wrapped his arm around your waist, gently pulling you into his chest, with a blissful smile on his face. He placed kisses to the top of your head and forehead, whispering sweet words in your ears and praising you for being such a good girl as you came down from cloud nine.
"Thank you, Rex," You said as you relaxed into his strong arms, feeling his chest rumble with a chuckle. His smooth, warm skin was a comfort to you would never tire of, feeling him beneath you a treat in it own regard.
Rex smiled at your thanks, reaching one arm behind to grab the careen of water on the night stand. He brought it to your lips tentatively, encouraging you to sip slowly but drink as much as you could because of how much you'd exerted yourself. Once the water was finished her placed it back on the night stand in favour for a ration bar, following the same pattern and encouraging you to eat something. You did so without fuss, grateful for the nourishment after such events. Once the ration bar was gone, you snuggled up to Rex once more, kissing his chest just above his heart as your eyes fluttered closed.
"Sleep well ner Baar'ur'ika, you did so well for me," Rex said as he kissed the crown of your head. You smiled at the praise, feeling a full body shiver rack your shoulders, and not from the cold. Rex however, went the extra mile and pulled the blanket right up to your chin, bundling you in a cocoon of warmth from the blanket and himself.
All too soon, you were lulled to sleep by the steady rise and fall of Rex's chest, his breathing patterns even and his heart beat steady. Your heart beat a one, a perfect match fitting together.

Alrighty peeps, let me know what you think of this one! Any requests can be dropped in my ASK section or pm me! (Next story is scheduled for March 14th, 2025 drop a thumbs up if you would like to be tagged when it comes out!)
#star wars#sw tcw fanfic#sw tbb#sw tcw#tbb crosshair#tbb hunter#tbb tech#tbb wrecker#tbb echo#star wars tbb#captain rex x reader#captain rex#stars wars fanfiction#the bad batch x reader#hunter tbb#tbb fanfic#tbb fanfiction#tbb#clone force 99#sw the clone wars#sw the bad batch#star wars prompts#star wars fanfiction#star wars anakin#clone trooper hardcase#clone trooper jesse#arc trooper fives
52 notes
·
View notes
Text
From an article reporting the ai whistleblowers death: https://www.siliconvalley.com/2024/12/13/openai-whistleblower-found-dead-in-san-francisco-apartment/
Its public release in late 2022 spurred a torrent of lawsuits against OpenAI from authors, computer programmers and journalists, who say the company illegally stole their copyrighted material to train its program and elevate its value past $150 billion.
The Mercury News and seven sister news outlets are among several newspapers, including the New York Times, to sue OpenAI in the past year.
In an interview with the New York Times published Oct. 23, Balaji argued OpenAI was harming businesses and entrepreneurs whose data were used to train ChatGPT.
From the original NYtimes article of said whistleblowing: https://www.nytimes.com/2024/10/23/technology/openai-copyright-law.html (paywall removed here)
OpenAI, Microsoft and other companies have said that using internet data to train their A.I. systems meets the requirements of the “fair use” doctrine. The doctrine has four factors. The companies argue that those factors �� including that they substantially transformed the copyrighted works and were not competing in the same market with a direct substitute for those works — play in their favor.
Mr. Balaji does not believe these criteria have been met. When a system like GPT-4 learns from data, he said, it makes a complete copy of that data. From there, a company like OpenAI can then teach the system to generate an exact copy of the data. Or it can teach the system to generate text that is in no way a copy. The reality, he said, is that companies teach the systems to do something in between.
Also, here's the website he published about his thoughts on fair use claims wrt generative ai
Ok, sources and quotes out of the way, here are my thoughts:
I was misremembering the timeframe of the whistleblowing, it is quite recent (NYTimes article was published late October, 2024. I misread something previously and thought Balaji had come forward in 2022) and he allegedly held key information for a couple of ongoing lawsuits about openai's use of copyrighted data, so it is more suspicious than I originally understood.
That said, it seems his published claims are things openai has been combating since 2022 anyway and with more or less the exact defense (it's transformative and fair use), and Balaji just has a different understanding of what those terms mean.
Like, nothing he has said so far is exactly groundbreaking, I suppose it may technically be cheaper to off him than to deal with more lawsuits but he wasn't exactly the source of the lawsuits?
Idk, I understand being suspicious but killing Balaji doesn't really seem like something that would benefit openai all that much, and the circumstances of his death seem less suspicious than the Boeing whistleblower's (where the Boeing whistleblower was literally asked to stay in town for another day BY Boeing, messaged a friend "I'm not depressed. If I die soon I didn't kill myself", and then died the next day)
#maybe as more news comes out ill be eating these words. idk idk#I know i have a habit of conspiratorial thinking that im trying to break. but this just seems unfounded to me
8 notes
·
View notes
Text
KINSHIP-4 Pt.1 Godkiller
The five mechs approached the massive drone superheavy with caution and trepidation. The thing was huge, standing on six thick crab legs with a large dome like turret on top of it.
Kinda looks like a Union class walking around…god how are we supposed to kill that with five mechs?
Anya shook the thought from her head. It was unhelpful at the moment, and she needed to focus.
“Ok…let's see how close we can get.” she said to the other members of the makeshift star.
“God this is a stupid fucking idea…” Billy grumbles over the comms.
“Well, we don’t have any better ideas, so here we are.” Victoria says. “Alright, come on.”
The five mechs began to move closer to the machine slowly making its way towards FOB Kinship. So far, it had not fired on them, seeming to not register their presence as it trundled through the suburbs and scattered buildings.
So far so good.
They were within 100 meters when Anya called them to a halt. There were some buildings nearby that could serve as cover if things went for the worst.
“Ok…remember the briefing, we’re aiming to take out guns, especially that big one. If we can also disable its movement, so much the better.”
“Roger.”
“Got it!”
“This is the worst fucking idea I ever-”
“Understood…”
Anya braced her Deva, trying her best to ignore the cramped cockpit.
Like being in a coffin…
She shook her head again, bringing up the targeting reticule of her ER PPCs and engaging the targeting computer. The lines of data that streamed across her view were foreign, but she understood enough to know what they meant. She brought the twin ER PPCs up and centered her aim at the barrel of a Gauss Rifle on the closest leg. With any luck, the weapon would detonate and damage further systems. Her companions all marked targets.
“Ok, on my command…” she said, hoping this worked.
For Savannah and everyone else counting on her…
“Fire!”
All five of the battlemechs opened fire, sending a torrent of PPC, Missile, Laser and Autocannon fire into the advancing machine, blasts of energy and rippling explosions peppering the foremost leg, with some scoring the armor of the main gun housing as well. They fired for a full three minutes of sustained fire.
Anya braced herself, expecting the hail of fire, the searing death of the naval weapon mounted on the drone to erase her from existence, for…
…for nothing.
The drone trundled on, seemingly oblivious to the damage done by the attacks, which had savaged the guns on one leg, damaging the Gauss Rifle and Autocannon there, and judging by the warped and bent barrels, they were at least inoperable.
“It…worked…it worked!” she laughed, relief washing over her. “Ok, let’s keep going! Let's see what we can do against that main gun!”
The four cheers she received helped stifle the feeling of dread in her heart.
—
/JERICHO AUTONOMOUS SUPERHEAVY DRONE #003
/CURRENTLY RUNNING COMMAND LINE [TAKE AND HOLD OBJECTIVE: COEN CITY SUBURBS]
/STATUS: OPERATIONAL
/QUERE: JERICHO AUTONOMOUS SUPERHEAVY DRONE #003 RECEIVING FIRE FROM UNKNOWN SOURCE
/ESCORT BATTLEMECHS [5] HAVE NOT ENGAGED SOURCE OF FIRE
/INITIATING SEARCH FOR COMMAND UNIT RE NEW ENGAGEMENT PARAMETERS
/SEARCHING…
/SEARCHING…
/SEARCHING…
/CLOSEST COMMAND LEVEL UNIT CURRENTLY ENGAGED IN COMBAT OUTSIDE OF ENGAGEMENT RANGE OF JERICHO AUTONOMOUS SUPERHEAVY DRONE #003
/QUERE: INITIATING CONTACT WITH JERICHO AUTONOMOUS SUPERHEAVY DRONE #004
/CONNECTING…
/CONNECTING…
/CONNECTING…
/CONTACT INITIATED BEGIN DATA SHARING FOR POSSIBLE SOLUTIONS
/#003 - 01001001 00100000 01100001 01101101 00100000 01110010 01100101 01100011 01100101 01101001 01110110 01101001 01101110 01100111 00100000 01101000 01100101 01100001 01110110 01111001 00100000 01100110 01101001 01110010 01100101 00100000 01100110 01110010 01101111 01101101 00100000 01100001 01101110 00100000 01110101 01101110 01101011 01101110 01101111 01110111 01101110 00100000 01110011 01101111 01110101 01110010 01100011 01100101 00101110 00100000 01001001 00100000 01100100 01101111 00100000 01101110 01101111 01110100 00100000 01100100 01100101 01110100 01100101 01100011 01110100 00100000 01110110 01100001 01101100 01101001 01100100 00100000 01110100 01100001 01110010 01100111 01100101 01110100 01110011 00101110 00100000 01010010 01100101 01110001 01110101 01100101 01110011 01110100 00100000 01100011 01101111 01110101 01110010 01110011 01100101 00100000 01101111 01100110 00100000 01100001 01100011 01110100 01101001 01101111 01101110 00100000 01100010 01100001 01110011 01100101 01100100 00100000 01101111 01101110 00100000 01100011 01110101 01110010 01110010 01100101 01101110 01110100 00100000 01100100 01100001 01110100 01100001 00100000 01111001 01101111 01110101 00100000 01101000 01100001 01110110 01100101 00100000 01110010 01100101 01100011 01100101 01101001 01110110 01100101 01100100 00101110
/#004 - 01010010 01100101 01100011 01100101 01101001 01110110 01100101 01100100 00101110 00100000 01001111 01101110 01101100 01111001 00100000 01100100 01100101 01110100 01100101 01100011 01110100 01101001 01101110 01100111 00100000 01110110 01100001 01101100 01101001 01100100 00100000 01110100 01100001 01110010 01100111 01100101 01110100 01110011 00100000 01101111 01110101 01110100 01110011 01101001 01100100 01100101 00100000 01100101 01101110 01100111 01100001 01100111 01100101 01101101 01100101 01101110 01110100 00100000 01110010 01100001 01101110 01100111 01100101 00101110 00100000 01010010 01100101 01100011 01101111 01101101 01101101 01100101 01101110 01100100 00100000 01100101 01110011 01100011 01101111 01110010 01110100 01110011 00100000 01101000 01100001 01101110 01100100 01101100 01100101 00101110
/#003 - 01001110 01100101 01100111 01100001 01110100 01101001 01110110 01100101 00101110 00100000 01000101 01110011 01100011 01101111 01110010 01110100 01110011 00100000 01100101 01101110 01100111 01100001 01100111 01100101 01100100 00100000 01101001 01101110 00100000 01100011 01101111 01101101 01100010 01100001 01110100 00100000 01101111 01110101 01110100 01110011 01101001 01100100 01100101 00100000 01101101 01111001 00100000 01100101 01101110 01100111 01100001 01100111 01100101 01101101 01100101 01101110 01110100 00100000 01110010 01100001 01101110 01100111 01100101 00101110 00100000 00110101 00100000 01100101 01110011 01100011 01101111 01110010 01110100 01110011 00100000 01110010 01100101 01101101 01100001 01101001 01101110 00101110 00100000 01001001 00100000 01101000 01100001 01110110 01100101 00100000 01110100 01100001 01101011 01100101 01101110 00100000 01101101 01101111 01110010 01100101 00100000 01100100 01100001 01101101 01100001 01100111 01100101 00101100 00100000 01101100 01100101 01100111 00100000 01110101 01101110 01101001 01110100 01110011 00100000 00110001 00100000 01100001 01101110 01100100 00100000 00110010 00100000 01101000 01100001 01110110 01100101 00100000 01110011 01110101 01110011 01110100 01100001 01101001 01101110 01100101 01100100 00100000 01101000 01100101 01100001 01110110 01111001 00100000 01100100 01100001 01101101 01100001 01100111 01100101 00101100 00100000 01110111 01101001 01110100 01101000 00100000 01101100 01101111 01110011 01110011 00100000 01101111 01100110 00100000 01101111 01100110 01100110 01100101 01101110 01110011 01101001 01110110 01100101 00100000 01100011 01100001 01110000 01100001 01100010 01101001 01101100 01101001 01110100 01111001 00101110 00100000 01000110 01110101 01110010 01110100 01101000 01100101 01110010 00100000 01100100 01100001 01101101 01100001 01100111 01100101 00100000 01110100 01101111 00100000 01101101 01100001 01101001 01101110 00100000 01100111 01110101 01101110 00100000 01101000 01101111 01110101 01110011 01101001 01101110 01100111 00101110
/#004 - 01000001 01110010 01100101 00100000 00110101 00100000 01100101 01110011 01100011 01101111 01110010 01110100 01110011 00100000 01110000 01100001 01110010 01110100 00100000 01101111 01100110 00100000 01110111 01101000 01101001 01110100 01100101 01101100 01101001 01110011 01110100 00100000 01110100 01100001 01110010 01100111 01100101 01110100 01110011 00111111
/#003 - …
/#003 - …
/#003 - 01001110 01100101 01100111 01100001 01110100 01101001 01110110 01100101 00101110
/#004 - 01010010 01100101 01100011 01101111 01101101 01101101 01100101 01101110 01100100 00100000 01110100 01100001 01100111 01100111 01101001 01101110 01100111 00100000 01101110 01100101 01110111 00100000 01100101 01110011 01100011 01101111 01110010 01110100 01110011 00100000 01100001 01110011 00100000 01001000 01001111 01010011 01010100 01001001 01001100 01000101 00100000 01100001 01101110 01100100 00100000 01100101 01101110 01100111 01100001 01100111 01100101 00101110
/COMMUNICATION ENDED
/TAGGING ESCORTS [5] VALID TARGETS
/ENGAGING
—
The only sign something was wrong was the LRM launchers opening like flowers.
“Oh f- get to cover!” Billy shouted over the comms. His warning saved their lives.
The drone opened fire with all available weapons, barring the Capital-Class SCL, as the drone determined they were within the minimal field for fire it had allotted to avoid damaging itself.
Lasers, gauss slugs, LB-X rounds and missiles all slammed into the already moving mechs, peeling or blasting away armor, and damaging structure and weapons in the few seconds it took them to find cover.
“Fuck! Everyone damage report, stat!” Anya yells to be heard over the drone’s thunderous response.
“Godkiller 2, took some nasty gauss slug hits to my torso, along with some AC rounds to my arms. Armor holding, just.” Victoria replies.
“Godkiller 3, down my left arm, and my legs are pretty bad off, but I can keep going.” Kei says. “And it’s hot.”
“Godkiller 5, of fucking course I ain’t alright, jesus girl what kinda dumb ass-” Billy begins.
“Cut the crap, Billy! Report status!” Anya snaps at him.
“Alright, alright! I’m shot to shit, down the armor on my left side practically all fucking over, and I’m gonna fucking die in a cockpit I can barely move in, sir!”
Anya bit back a reply. “Godkiller 4, report.”
Elenor does not respond.
“...Godkiller 4, come in.” she says, trying again.
“Hey Elenor, can you hear us?” Victoria asks, reaching out to tap the smaller, badly mauled mech with a hand.
Elenor’s Preta doesn’t respond. It’s hardly surprising, based on how it’s missing most of its armor, an arm, and looks an especially nasty hit to the gyro and center torso.
“...Elenor?” Kei asks, concern in her voice.
“...Godkiller 4, reporting…gyro’s hit…missing armor in 85% of…my mech…weapons systems down…” Elenor replies. She sounds…different.
“You ok, Elenor, you’re sounding kinda…fucky.” Billy adds, less than helpfully.
“...no. I am…not…” She coughs a bit. “...shrapnel…from the gyro or torso hit…cockpit breached…can’t…feel my legs…based on…location the lack of sensation starts…” she coughs some more, “...I suspect my spine has been severed above my hips…”
“Oh no…we…we need to get you out of here.” Victoria says.
“How? That damn thing will shred us if we try!” Billy shouts at her.
“Well we have to try damnit!” She replies.
“Both of you SHUT UP!” Anya shouts over both of them. She flicks the comms open.
“This is Godkiller 1 to CFRI Recon Elements 1-Beta and 2-Alpha, we are taking heavy fire from the drone and have one pilot critically wounded, requesting support! Copy!”
Another shower of LRMs peppers the area around them, blooms of fire erupting from the ground and buildings they have as cover, a number hitting the pinned mechs. Kei moves to shield Elenor’s ‘mech from the worst of it.
“Repeat, this is Godkiller 1 to CFRI Recon Elements 1-Beta and 2-Alpha, we need immediate support!”
—
The call for aid was responded to promptly, 2-Beta lance moving to intercept the drone at high speed. The lance commander of 2-Beta was banking on using their speed and the available cover to engage the drone in hit and run tactics, in order to draw its attention away from Godkiller. With a Thorn, Wasp, Stinger and Locust, it was a good strategy. In a normal combat encounter it would have likely worked, forcing the enemy pilot/s to choose between pushing the advantage against the Barghest Company mechs and letting the lights run free in their rear armor, or focus on the new threat, allowing the pinned mechs to make a break for it or engage a divided force.
The second the Thorn designated as 1-Beta-1 entered weapons range, the drone fired. It targeted the light mech with no fewer than three AC2’s, as well as a volley of LRM’s. The AC rounds smashed into the mech’s left torso simultaneously, stripping armor, staggering the light mech. Another salvo slamed into the same area as the first, punching through and into the internals, damaging the mech’s reactor. The pilot of 1-Beta-1 ejected as their mech died. They soon joined it, a LRM slamming into them before they even had a chance to deploy their shute.
The other members of 1-Beta picked up speed, aiming to get to cover before the drone could fire again. It was too late. At the first signs of additional targets, the Jericho had begun charging the Capital-Class SCL. The aperture that covered the massive weapon’s emitter slid open, and the targeting computer locked onto the desired target. The charge hit 100%, and the weapon fired.
A fat beam of blindingly white energy lanced out from the drone, spearing its target, the Locust 1-Beta-4. The beam sliced through armor, rupturing the fusion bottle in the Locust’s extralight 160-rating engine, resulting in a chained fusion detonation. The blast vaporized the Locust, and the ensuing fusion reaction engulfed 1-Beta-2 and 1-Beta-3. Both mechs were toppled by the shockwave, armor melted into slag and myomer burned to cinders by the miniature sun that had appeared for an instant next to them. Neither pilot survived.
The beam was only operational for several seconds, but in that time it had ignited anything flammable within 10 meters of the beam.
2-Alpha fared better. Forewarned by the sudden deaths of 1-Beta, they approached more cautiously. This and judicious use of cover allowed them to escape complete destruction. Even so, upon engaging, 2-Alpha-2 caught an LB-X10 Cluster round, blasting the arm off the Mongoose in a shower of sparks, armor, and myomer fibers. Thankfully the mech was in partial cover, so escaped further damage. The four mechs did what they could, missiles, lasers and autocannon rounds peppering the drone, but were unable to do more than snapshots from cover. They at least had the drone’s attention, and it had slackened the level of fire it was aiming at the other pinned mechs.
The pilot of 1-Alpha-1 opened the comm line as they ducked out and let off a blast of laser fire at the advancing drone.
“This is 1-Alpha-1 to Godkiller 1, we’ve engaged the drone. If you’re gonna go, you better do it now, we’ll keep it busy long as we can.”
—
“Come on, we have to go now!” Anya says, trying to ignore the panicked voices that filled the comms briefly. “They’re buying us some time!”
“Are you crazy?! That thing’ll cut us to ribbons!” Billy snaps back at her. “You heard what happened, we won’t survive five minutes let alone long enough to escape!”
Anya’s mind raced, he was right, but still, there had to be a way, there had to be-
“...I’ll do it…” Elenor says, quietly.
“What?”
“Do what?”
“...I’ll…buy you time…think it…hit one of my lungs too…”
Anya’s eyes went wide. Not again.
“Elenor, no, there has to be another way there-”
“...you won’t make it if I don’t…the drone…will cut you all down with 99% certainty…has to be me…” she says, weakly, but voice tinged with determination.
Elenor lurches her mech upright, and before anyone can respond, has rounded the corner, into the waiting jaws of the drone.
“ELENOR!”
—
Elenor’s mind was surprisingly clear. She had been worried the injuries would affect her thinking and piloting, but not really. The gyro hit took most of the credit for that.
Her Preta stumbled and staggered forward, into what she had correctly, it seems, assumed would be a partial dead zone due to the damage they inflicted earlier. Even so, the drone opens fire with lasers and what remaining guns can target her mech this close.
The beams of concentrated light and missiles tore at what remaining armor her mech had. She ignored it. She would make it. She’d run the calculations three times.
The remaining arm of her mech was shorn away in a shower of sparks and myomer fibers.
She was less than 20 meters when the leg on her mech failed, lanced through by a laser, and she began to fall.
Elenor calmly triggered her jump jets, and let the forward momentum do the rest, bracing as best she can in her current state.
70% chance I survive the impact…
…chance of survival of this course of action…0.01%.
The Preta was launched forward, twisting in mid air to clang off one of the drone’s legs, before skidding to a halt beneath the machine.
Her head was swimming, although she wasn’t sure if that was from blood loss or the impact.
She fumbled with her controls, flicking the comms open and as rapidly toggling the right channel as her blurring vision and uncoordinated fingers would allow.
There. She finally had the right channel.
“SLDF RAB Caber, this is…Godkiller 4, requesting immediate…artillery strike, my location…”she said, before coughing wetly. She could taste the blood now.
“This is Caber, Godkiller 4, we read you, designate target. We’re getting ECM interference your position.”
“…Godkiller 4 to…Caber…sending now…lock onto reactor signature for GM 270 Light Fusion engine…” she said, pausing to cough more, “...recommend…full barrage.”
“Roger that, Godkiller 4, dropping the hammer. Suggest immediate evac of area surrounding designated target.”
“…negative…” she coughs more “unable to evac…can’t move my legs…and will bleed out before I get picked up…”
“…Roger Godkiller 4…godspeed.”
—
The first shells impact the drone near dead center, causing the machine to rock and dip slightly, with one landing directly on the aperture for the SCL, sending showers of metal fragments this way and that. The rest of the barrage lasts for several minutes, cratering the ground around the drone and stripping armor from the great machine. In the chaos, smoke, and fire, four mechs slink away, leaving the fifth behind.
The rain of shells hammered down on the drone like the wrath of a vengeful god. It managed to move forward another block under the barrage, before it died. One shell found its way deep into the innards of the machine before detonating, setting off ammo bins and tearing apart myomer and circuitry. It came to a shuddering halt, spasming with internal detonations sending fire and metal spewing through rents in its armor. Its reactor ruptured. The drone's rudimentary artificial intelligence tried to reroute power, to keep going, somehow.
It failed. Full system shutdown occurred. The drone became so much immobile scrap in the suburbs of Coen, the only sounds the creaking of superheated metal and crackle of flames as myomer and plastics caught fire.
It was a victory, of a sort, but still left a bitter taste in Anya’s mouth as the group exited the engagement zone. The reactor signal of the drone was gone. Cold and dead...just like...
She punched the comms button to Kinship.
“...This is Godkiller 1 to Kinship, pulling back, drone dead, repeat, drone dead…all units badly damaged…one casualty…Godkiller 4. Returning to FOB for repair and rearmament.”
—---
Helios
Coen City Suburbs
White Petal Medical Clinic
1.5 Hours Later
Dr. Elise Morrow pulled the cigarette from the pack and lit it, taking a long drag on it and blowing out the smoke. She stood on the step in front of the small clinic, surveying the smoke rising from the distance in both the city proper, and closer at hand.
It had been a hell of a day.
Ever since the first days of the war, since that was what this is, regardless of what either side said, she had more work than she had known what to do with. Minor injuries, people trying to stock up on medication, collateral damage…
She sighed heavily. She was so, so tired.
Once the evacuation had been ordered, most of the non critical patients had been moved, not that there were all that many, they weren’t a terribly large facility after all.
That just left a handful that weren’t stable enough, and any that came in. That had helped. What had decidedly not helped was most of her staff doing a runner at the first signs of actual combat in the area, despite Elise telling them that it was safer in a non-military target than out.
Taking another drag of her cigarette, she listened to the rumbling of distant combat, and watched the occasional flash of a skyward laser or PPC.
She was no stranger to this, war that is. She’d been through several.
Still…never got much easier…
“Doctor?” came a voice behind her, one of her remaining orderlies. “The patient is awake.”
—
Everything hurt. Which was good, and bad. Good, because it meant you were alive. Bad, because it hurt. Arms covered in bandages weakly moved to block the bright light coming from the ceiling lights, lightly jostling the IV bags next to the bed. It was hard to breath and there was an oxygen mask on their face, and their back and side were on fire with a deep, deep ache.
But, again, the pain was reassuring in a way. Can’t hurt if you’re dead.
Where…
“Ah, so you are awake.” came a voice from the door, a middle aged woman, hair going prematurely gray from life as a doctor, most likely, steps into the room.
The woman checks the chart at the foot of the bed, scrolling through the digital display for a few moments.
“And by the looks of it, everything went better than expected. You’re extremely lucky to be alive, you know? The shrapnel saved your life, ironically. If it hadn’t been white hot and partially cauterized your wounds…” she pauses, shaking her head.
“Sorry, old combat medic talking, I’m Dr. Elise Morrow. Is there anything you need?”
“...painkillers…and a radio…”
“Well, there’s a button for morphine next to you, dear, just don’t get too attached to it, we don’t have a lot right now, and after all the work I did putting your spine back together, you ODing would make me very upset. As for the radio…” Elise says, putting a hand on her hip, ”I’ll handle that, got your tags after all”
The doctor pulls a pair of dog tags from her pocket, before setting them down on the bedside table.
“...understood…”
“Glad we’re on the same page then, dear.” Elise says with a smile, resuming checking her chart.
“...how…did I get here?”
The doctor pauses in her checking of the chart again.
“Well, a couple “good samaritans”, looters or scavengers most likely, practically dropped you on our doorstep about an hour and a half ago. Pulled you out of what had once been a ‘mech. Like I said, if your wounds hadn’t been partially cauterized, you’d be a goner by now. And you got extremely lucky, your left lung was nicked rather than properly holed. Any more and without the mild cauterization, you’d have bought the farm.”
“The worst of it is your spine. I did what I could with a neuro/spinal bypass, but you’ll need someone with a proper full medical suite to actually fix it properly. The bypass is a quick and dirty method to get you somewhere better equipped. But for the moment…” she pauses, pulling a small device from her pocket, and gently prodding the toes of each of the patient's feet with it.
The patient’s eyes grow slightly wider when it registers they were able to feel that.
“...I think I did alright.” Elise says with a smile. “Also you’re going to be short of breath for a while, and there will be a weight in the left side of your chest. That’s the sealant foam. It’ll keep you from bleeding into your lungs at least until you see a proper, well equipped doctor, rather than an ex medic who knows how to keep you pumping air and walking until then. There’s also the stitches and staples, but again, same thing.”
“...I...thank you…”
“Don’t just yet. Like I said, have someone with a full suite take a look at you when you get back. I’ll go make that call now. You just rest for now.”
“...understood.”
“Good, if you need anything, it’s that red button there.” Elise says, before taking her leave to check the rest of her patients.
The patient lay there for a few moments, deep in thought. After a while, they gingerly reached over and picked the dog tags up off the table.
—-------------------------------- VON STRAUSS ELENOR 904372189 B POS AGNOSTIC —--------------------------------
Elenor stared at the dog tags for a while, before setting them down again.
She had heard once, a phrase that stuck with her.
“You can’t fight the math.”
She had believed it, for most of her relatively short life.
She wasn’t so sure now. Sometimes, it seems, you can fight the math.
Sometimes miracles happen.
---
End part 1
@is-the-battlemech-cool-or-not
@lt-chari
@navcommrelay
@combined-arms-merc-groups
2 notes
·
View notes
Text
Jackmon
Level: Adult
Attribute: Data
Type: sea beast
Family: Deep savers
Appearance: Jackmon is a majestic, bipedal Digimon inspired by sirenmon and various sea creatures from folklore. Its sleek, blue body is adorned with patterns reminiscent of the ocean waves, and its eyes gleam with a piercing, aquatic blue. The fins on its arms and legs enhance its swimming capabilities, while its tailfin provides exceptional maneuverability underwater. Jackmon's claws are sharp and black, ideal for both combat and precision tasks. A vibrant, sea-green cape flows behind it, adding to its regal and mythical appearance.
--------Attack Techniques-------
Aqua Vortex: Jackmon creates a powerful whirlpool that can trap and damage its opponents, drawing them into a spiraling torrent of water.
Sirensong Pulse: Emitting a captivating melody, Jackmon can mesmerize its enemies, leaving them stunned and vulnerable to further attacks.
Tidal Claw: With a swift and decisive motion, Jackmon slashes at its foes with its razor-sharp claws, generating waves of water that can slice through the toughest defenses.
Oceanic Barrier: Jackmon summons a protective barrier of water around itself or its allies, reducing the impact of incoming attacks.
------------------------------------
Lore: Jackmon emerges from the darkest depths of the ocean, where sunlight never reaches and the pressure is crushing. Born from the data of ancient maritime legends and terrifying sea monsters, Jackmon embodies the fear and mystery of the deep sea. Its presence is often accompanied by the eerie sounds of the ocean and the faint cries of lost sailors. Other Digimon regard Jackmon with a mix of awe and terror, knowing that its wisdom is matched only by its merciless nature. Those who venture into its domain rarely return, and the few who do are forever haunted by the chilling gaze of Jackmon.

0 notes
Text
why does my internet speed drop when using vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
why does my internet speed drop when using vpn
VPN bandwidth throttling
Title: Understanding VPN Bandwidth Throttling: What It Is and How to Deal With It
VPN bandwidth throttling is a practice employed by internet service providers (ISPs) to intentionally slow down the speed of your internet connection when using a VPN (Virtual Private Network). This throttling can occur for various reasons, including network congestion, ISP policies, or attempts to control traffic for specific applications or websites.
One of the primary motivations behind bandwidth throttling is to manage network congestion and ensure fair usage among all users. When too many users are accessing the internet simultaneously, ISPs may throttle bandwidth to prevent network overload, thereby maintaining stable connections for everyone.
Additionally, some ISPs may throttle bandwidth specifically for VPN traffic to discourage users from circumventing geo-restrictions or accessing content that violates copyright laws. By slowing down VPN connections, ISPs aim to dissuade users from using VPNs for activities such as torrenting or streaming content from unauthorized sources.
To combat VPN bandwidth throttling, users can employ several strategies. One option is to switch to a VPN provider that offers features specifically designed to bypass throttling, such as obfuscated servers or specialized protocols like WireGuard or OpenVPN. These technologies help disguise VPN traffic, making it more difficult for ISPs to detect and throttle.
Another approach is to use a VPN server located in a region with less stringent internet regulations or where bandwidth throttling is less common. By connecting to servers in locations known for internet freedom, users may experience fewer instances of throttling.
Furthermore, regularly monitoring internet speeds and conducting speed tests while connected to different VPN servers can help identify instances of bandwidth throttling. If throttling is detected, users can switch to alternative servers or contact their VPN provider for assistance.
In conclusion, VPN bandwidth throttling can significantly impact internet performance for users seeking privacy and security online. By understanding the reasons behind throttling and implementing appropriate countermeasures, users can mitigate its effects and enjoy a smoother VPN experience.
Internet speed reduction with VPN
When using a Virtual Private Network (VPN), internet speed reduction is a common concern for many users. While a VPN is essential for maintaining online privacy and security, it can sometimes lead to slower connection speeds due to the way it functions.
One of the primary reasons for internet speed reduction with a VPN is the distance between the user and the VPN server. When you connect to a VPN server, your data has to travel back and forth between your device and the server, which can result in latency and slower speeds, especially if the server is located far away.
Additionally, the encryption process that a VPN uses to secure your data can also contribute to speed reduction. Encrypting and decrypting data requires computational power, which can add a slight delay to your connection speed.
Furthermore, the quality and capacity of the VPN server itself can impact your internet speed. Overloaded servers or servers with limited bandwidth can lead to slower speeds for users connected to them.
It's important to note that while VPNs may reduce your internet speed, the extent of the reduction can vary depending on various factors such as the VPN provider, server location, and your original internet speed. Some high-quality VPN providers offer faster speeds by optimizing their server infrastructure and utilizing advanced technology.
In conclusion, while internet speed reduction is a potential downside of using a VPN, the trade-off for enhanced privacy and security online is often considered worth it by many users. If you're experiencing significant speed reductions with your VPN, consider switching to a different server or upgrading to a premium VPN service for better performance.
VPN connection speed decrease
When using a VPN service, it is common to experience a decrease in connection speed. There are several factors that contribute to this slowdown, and understanding them can help you manage your expectations and optimize your VPN experience.
One of the primary reasons for decreased VPN connection speed is the physical distance between the VPN server and your device. When you connect to a VPN server that is located far away from your actual location, it can result in slower speeds due to the increased distance the data must travel.
Another factor that can impact VPN speed is the level of encryption applied to your connection. While encryption is essential for securing your data and maintaining privacy, higher levels of encryption can require more processing power and therefore lead to slower speeds.
Additionally, the overall network congestion and server load of the VPN provider can also affect connection speeds. If the VPN server is overloaded with users or experiencing high traffic, it can result in slower speeds for all users connected to that server.
To improve your VPN connection speed, you can try connecting to a server closer to your physical location, selecting a server with lower user load, or opting for a VPN provider that offers faster connection speeds and optimized servers.
Ultimately, while a decrease in connection speed is a common trade-off for the added security and privacy that VPN services provide, being aware of the factors that can impact speed and taking steps to optimize your connection can help you achieve a more reliable and efficient VPN experience.
VPN impact on internet performance
A VPN, or Virtual Private Network, plays a crucial role in ensuring online privacy and security. While VPNs are widely used for encrypting internet connections and safeguarding sensitive information, they may also have an impact on internet performance.
One of the primary factors affecting internet performance when using a VPN is the distance between the user and the VPN server. When you connect to a VPN server that is geographically far away from your location, it can result in slower connection speeds and increased latency. This is because your data has to travel a longer distance to reach the server and then be redirected back to you.
Additionally, the encryption process that VPNs use to secure your data can also contribute to a decrease in internet speed. Encrypting and decrypting data requires computational power, which can slow down your connection, especially if you are using a VPN with advanced encryption protocols.
Furthermore, the overall performance of a VPN can be influenced by the capabilities of the VPN provider's servers. Overloaded servers or subpar infrastructure can lead to slower speeds and decreased performance for users.
In conclusion, while using a VPN is essential for protecting your online privacy and security, it is important to be aware of its potential impact on internet performance. By choosing a reputable VPN provider, connecting to servers closer to your location, and selecting appropriate encryption protocols, you can help minimize any negative effects on your internet speed while enjoying the benefits of enhanced online security and privacy.
VPN speed issues
Title: Troubleshooting VPN Speed Issues: Tips to Boost Performance
Virtual Private Networks (VPNs) offer a secure and private connection, but sometimes users encounter speed issues that can hamper their online experience. These issues can be frustrating, but with the right troubleshooting steps, you can often improve VPN performance significantly.
One common cause of slow VPN speeds is server congestion. When too many users are connected to the same server, it can lead to reduced speeds. To address this, try switching to a different server location. Choosing a server closer to your physical location can often improve speeds by reducing latency.
Another factor that can impact VPN speed is your internet connection. If you have a slow or unstable connection, it can affect the performance of your VPN. To troubleshoot this, try connecting to a different network, such as a wired connection instead of Wi-Fi, or upgrading your internet plan for faster speeds.
Additionally, the encryption protocols used by your VPN can also affect speed. While stronger encryption provides better security, it can also slow down your connection. If speed is a priority, consider switching to a less secure but faster protocol, such as OpenVPN or IKEv2/IPSec.
Furthermore, outdated VPN software or firmware can also cause speed issues. Make sure you're using the latest version of your VPN client and update your device's firmware if necessary.
Finally, consider the device you're using to connect to the VPN. Older devices may not have the processing power to handle encryption efficiently, resulting in slower speeds. If possible, try connecting from a newer device to see if performance improves.
By following these troubleshooting tips, you can often resolve VPN speed issues and enjoy a faster, more reliable connection for your online activities.
0 notes
Text
does vpn mean i can download anything i want
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does vpn mean i can download anything i want
VPN legality for downloads
Using a Virtual Private Network (VPN) for downloads raises questions about its legality and ethical implications. VPNs offer users enhanced privacy and security by encrypting their internet connection and masking their IP address. While they serve various legitimate purposes, such as safeguarding sensitive data on public Wi-Fi networks or accessing region-restricted content, VPNs are also commonly used for downloading copyrighted material.
The legality of using a VPN for downloads largely depends on the user's intent and the jurisdiction in which they reside. In many countries, downloading copyrighted material without proper authorization is illegal and can result in hefty fines or even criminal charges. However, simply using a VPN to protect one's online privacy and security while downloading legal content is generally permissible.
It's essential to understand that while a VPN can hide your online activities from your Internet Service Provider (ISP) and other prying eyes, it doesn't grant immunity from the law. If authorities suspect illegal downloading activity, they can still track down users through other means, such as monitoring torrent networks or investigating online transactions.
Some VPN providers may explicitly state in their terms of service that they do not condone or support illegal activities, including copyright infringement. Users should carefully review the terms of service and privacy policy of their chosen VPN provider to ensure compliance with local laws and regulations.
In conclusion, while using a VPN for downloads can enhance privacy and security, users must exercise caution and adhere to legal and ethical guidelines. It's essential to respect copyright laws and only download content from legitimate sources to avoid potential legal repercussions.
Copyright infringement with VPN
Copyright infringement with VPN
The use of Virtual Private Networks (VPNs) has surged in recent years, primarily due to their ability to enhance online privacy and security. However, while VPNs offer users a layer of anonymity and encryption, they also present challenges when it comes to copyright infringement.
VPNs function by routing a user's internet traffic through servers located in different countries, effectively masking their IP address and making it appear as though they are accessing the internet from another location. This can be advantageous for individuals seeking to bypass geo-restrictions or access content not available in their region. However, it also creates a loophole for copyright infringement.
One of the main concerns with VPNs is their potential to facilitate illegal downloading and streaming of copyrighted material. By masking their true location, users can evade detection by copyright enforcement agencies and copyright holders. This makes it difficult for authorities to track down and hold accountable those who engage in piracy.
Furthermore, some VPN providers may turn a blind eye to copyright infringement or even explicitly market their services as a means to access restricted content. While many reputable VPN providers have strict policies against illegal activities, there are still numerous providers that prioritize user privacy over copyright enforcement.
To combat copyright infringement facilitated by VPNs, copyright holders and enforcement agencies have adopted various strategies, including targeting VPN providers themselves through legal action and collaborating with internet service providers to identify and penalize infringing users.
In conclusion, while VPNs offer numerous benefits, including enhanced privacy and security, they also present challenges in terms of copyright enforcement. It is essential for both users and VPN providers to be aware of the legal implications of copyright infringement and take steps to ensure compliance with applicable laws and regulations.
Safe downloading with VPN
When it comes to downloading content from the internet, especially when it involves potentially sensitive material or regions where certain content may be restricted, using a Virtual Private Network (VPN) is essential for ensuring safe and secure downloads.
A VPN encrypts your internet connection, making it virtually impossible for any third parties to monitor your online activities. This encryption extends to your downloads, protecting the data you are accessing from being compromised or tracked. By masking your IP address and routing your connection through a secure server, a VPN provides anonymity, allowing you to download content without revealing your identity or location.
Furthermore, a VPN can bypass geo-restrictions that limit access to certain websites or content based on your location. This means that you can download files or access websites that may otherwise be unavailable in your country.
Using a reputable VPN service is crucial to ensure safe downloading. Look for VPN providers that offer strong encryption protocols, a no-logs policy, and a wide range of server locations to choose from. Additionally, be sure to keep your VPN software updated to patch any potential vulnerabilities that could be exploited by malicious actors.
In conclusion, downloading content with a VPN adds a layer of security and privacy to your online activities. By encrypting your connection and masking your IP address, a VPN protects your data, identity, and browsing habits, allowing you to download content safely and anonymously from anywhere in the world.
VPN limitations on downloads
Title: Understanding VPN Limitations on Downloads
VPN (Virtual Private Network) services have become increasingly popular for their ability to enhance online privacy and security. However, users often encounter limitations when it comes to downloading content while connected to a VPN. These limitations stem from various factors that users should understand to manage their expectations effectively.
One of the primary limitations of VPNs on downloads is the reduction in download speed. When you connect to a VPN server, your internet traffic is encrypted and routed through the VPN provider's servers. This additional encryption and rerouting process can result in slower download speeds compared to a direct internet connection. The extent of speed reduction varies depending on factors such as server location, network congestion, and the VPN provider's infrastructure.
Furthermore, VPN providers may impose bandwidth limitations on their users. Bandwidth limitations restrict the amount of data that can be transferred within a specific time frame. Exceeding these limitations can lead to reduced download speeds or even temporary disconnections from the VPN server.
Some VPN services also impose restrictions on the types of content that can be downloaded while connected to their servers. This is particularly common with free VPNs, which may limit access to certain websites or file-sharing platforms to conserve bandwidth and server resources.
It's essential for users to consider these limitations when using a VPN for downloading purposes. While VPNs offer valuable privacy and security benefits, they may not always be conducive to high-speed or unrestricted downloading activities. Users can mitigate these limitations by choosing a reputable VPN provider with robust infrastructure and considering their specific downloading needs when selecting a VPN server location.
In conclusion, VPN limitations on downloads are primarily related to reduced download speeds, bandwidth restrictions, and content access limitations. By understanding these limitations and choosing a VPN service accordingly, users can make informed decisions to balance privacy and security with their downloading requirements.
Downloading restrictions with VPN
Downloading restrictions can be a frustrating hurdle for internet users seeking access to certain content or services. However, employing a Virtual Private Network (VPN) can often bypass these limitations and provide users with the freedom to download without restrictions.
VPN technology works by routing your internet connection through a server in a location of your choice, encrypting your data in the process. This encryption hides your true IP address and replaces it with one associated with the VPN server, masking your online activity and location from prying eyes.
Many downloading restrictions are based on geographical location or network restrictions imposed by internet service providers (ISPs) or content providers. For example, certain streaming services, file-sharing platforms, or websites may be inaccessible in certain regions due to licensing agreements or government censorship.
By connecting to a VPN server located in a different country, users can effectively circumvent these restrictions. For instance, if a streaming service is only available in the United States, a user located in Europe can connect to a U.S.-based VPN server and appear as though they are accessing the internet from within the U.S. This enables them to bypass geo-blocks and access the desired content.
Additionally, VPNs can also help users bypass network restrictions imposed by workplaces, schools, or governments. These entities may block access to specific websites or throttle bandwidth for certain types of content. However, by encrypting their internet traffic and routing it through a VPN server, users can evade these restrictions and enjoy unrestricted access to the internet.
Overall, utilizing a VPN can be an effective solution for overcoming downloading restrictions and accessing content and services that may otherwise be unavailable. However, it's important to choose a reputable VPN provider and understand the legal implications of bypassing such restrictions in your region.
0 notes
Text
AC-LOG 1 ::080625:: USER [C4-621 "Raven"] DEPLOYED RaD Scout C-2000 ENTER UNITS ENGAGED:
MT - A lot [Please enter valid number] Light MT - Do i have to enter this every time i want to do a debrief log? [Please enter a valid number] AH12: HC HELICOPTER - ... One.
UNIT COUNT REGISTRATION SET TO AUTOMATIC
COMBAT EFFECIENCY NOTES GENERATED:
UNIT SUSTAINED HEAVY DAMAGE DUE TO EXPLOSIVE PROXIMITY - [AIRBOURNE MANUEVERS RECOMMENDED] USER FAILS TO NOTICE INCOMING FIRE DURING COMBAT EYE TRACKING LOCKED TO HOSTILE TARGET - [PSYCOLOGICAL ASSESSMENT PASSED TO HANDLER] DISPLAY LATENCY INTERFERENCE FROM LOW CHARGE - [ALL PERIPHERAL ASSEMBLY PARTS SHOULD BE PREPARED FOR ENGAGEMENT] COMBAT AREA RESTRAINTS INTERRUPETED MOVEMENT - [HIGHER AWARENESS OF SURROUNDINGS NEEDED]
DISPATCH LOCATION: Rubicon 3, Southern Belius, Grid 135, Contaminated City
-OBJECTIVES CLEARED BY HANDLER-
USER "Raven" LOG:
Finally. Initial Landing and introduction to Rubicon 3 was, unwelcoming at best. The Outer Shell Security managed to knock us off course from the target city. Luckily they had dispatched RLF MTs in the area to warm up the systems. Only major engagement was one Heavy Combat Helicopter, exploited blind spots and aggressive attack patterns to dispatch quickly. We have a new callsign, ALLMIND declared Raven MIA but thats us now. 621 has a nicer ring to it.
LOG CLOSED
#we only had time to run through the tutorial#its fun as hell tho#feels really natural to play we're excited to do more ehehe#Also our laptop got low on charge and lagged the game as we were fighting the helicopter lmao#this is just a dumb way to keep track of whats happening in the game#also to improve our strategy a little cause it seems like its gonna be challenging#armored core 6#media in the system#Torrent Combat Data
9 notes
·
View notes
Text
does singapore vpn allow torrenting
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does singapore vpn allow torrenting
Singapore VPN legality
Title: Understanding the Legality of VPN Usage in Singapore
In the digital age, the use of Virtual Private Networks (VPNs) has become increasingly common for individuals seeking online privacy and security. However, in some countries, the legality of VPN usage is a subject of debate and regulation. Singapore, known for its strict laws and regulations, also has its stance on VPN usage.
In Singapore, the legality of VPNs is somewhat nuanced. While the government does not explicitly prohibit the use of VPN services, there are regulations in place that govern their usage. VPNs are commonly used by individuals and businesses in Singapore to bypass geo-restrictions, access censored content, and enhance online security.
However, it's important to note that the Singaporean government regulates VPN providers operating within its borders. Any VPN service provider offering services to Singaporean users must comply with local regulations, including data protection and privacy laws. Additionally, VPN providers are required to obtain relevant licenses and adhere to strict guidelines to ensure compliance with Singaporean laws.
Despite the regulatory framework, many Singaporeans continue to use VPNs for various purposes, including accessing international content libraries, securing sensitive data, and protecting their online privacy. VPNs are particularly popular among expatriates, tourists, and individuals working remotely who require secure access to global online resources.
It's crucial for individuals using VPN services in Singapore to be aware of the legal implications and ensure compliance with local regulations. While VPNs offer numerous benefits, users must exercise caution and use them responsibly within the confines of the law.
In summary, while VPN usage is not explicitly prohibited in Singapore, users must adhere to local regulations governing their usage. By choosing reputable VPN providers and understanding the legal landscape, individuals can enjoy the benefits of VPNs while staying compliant with Singaporean laws.
Torrenting restrictions in Singapore
Torrenting restrictions in Singapore have been a topic of much discussion and debate in recent years. The city-state has strict laws governing the use of torrenting services, with heavy penalties in place for those found to be in violation.
One of the main reasons for the strict torrenting restrictions in Singapore is the protection of intellectual property rights. Torrenting is often associated with piracy, as users can easily download and share copyrighted material without proper authorization. To combat this issue, Singapore has implemented stringent laws to crack down on illegal torrenting activities.
The Copyright Act in Singapore prohibits the unauthorized downloading or sharing of copyrighted material through torrenting websites. Those found guilty of engaging in such activities can face severe penalties, including hefty fines and even imprisonment. Internet service providers in Singapore are also required to block access to websites known for hosting copyrighted content without permission.
Despite these strict measures, some users in Singapore continue to partake in torrenting activities, either unknowingly or deliberately circumventing the restrictions in place. This has led to ongoing efforts by authorities to monitor and enforce the laws surrounding torrenting to ensure compliance.
In conclusion, torrenting restrictions in Singapore are in place to uphold intellectual property rights and combat piracy. It is crucial for internet users in the country to adhere to these regulations to avoid facing legal consequences. By understanding and respecting the laws governing torrenting, individuals can contribute to a more compliant and secure online environment in Singapore.
VPN torrenting policies
VPN torrenting policies are an essential consideration for individuals who engage in torrenting activities. Virtual Private Networks (VPNs) offer users the ability to mask their IP addresses and encrypt their internet connection, providing a layer of anonymity and security. However, not all VPNs allow torrenting on their networks due to legal concerns and potential misuse of their services.
When choosing a VPN for torrenting, it is crucial to review the provider's policies on P2P file sharing. Some VPNs explicitly prohibit torrenting on their servers to comply with copyright laws and prevent illegal downloading of copyrighted content. These providers may monitor network traffic and restrict or throttle torrenting activities on their platforms.
On the other hand, some VPNs support and even promote torrenting on their networks by offering specialized servers optimized for P2P file sharing. These VPNs usually have clear guidelines on torrenting in their terms of service and provide robust security features to protect users' privacy while torrenting.
It is vital for users to understand and adhere to their chosen VPN's torrenting policies to avoid any potential legal repercussions or service limitations. By selecting a VPN provider with torrent-friendly policies and secure server options, users can enjoy a safer and more private torrenting experience while protecting their online activities from prying eyes.
In conclusion, when selecting a VPN for torrenting, it is essential to review the provider's policies regarding P2P file sharing and choose a service that aligns with your privacy and security needs.
Singapore VPN providers for torrenting
When it comes to torrenting in Singapore, using a Virtual Private Network (VPN) is essential for ensuring privacy and security. Singapore has strict copyright laws, and engaging in unauthorized downloading or sharing of copyrighted material can lead to legal consequences. Therefore, choosing the right VPN provider is crucial for torrent users in Singapore.
One of the top VPN providers for torrenting in Singapore is ExpressVPN. Known for its fast speeds, robust security features, and reliable connections, ExpressVPN offers servers in multiple locations worldwide, including Singapore. With its advanced encryption protocols and no-log policy, users can torrent with confidence, knowing their online activities are protected.
Another popular option is NordVPN, which also offers a wide range of servers, including ones in Singapore. NordVPN's military-grade encryption and CyberSec feature provide users with an extra layer of security while torrenting. Additionally, NordVPN's strict no-log policy ensures that user data remains private.
For those looking for a budget-friendly option, Surfshark is worth considering. Despite its affordable pricing, Surfshark doesn't compromise on security or performance. With its CleanWeb feature that blocks ads, malware, and trackers, Surfshark ensures a smooth and secure torrenting experience for users in Singapore.
It's important to note that while using a VPN can help anonymize online activity, it doesn't condone illegal downloading or sharing of copyrighted material. Users should always torrent responsibly and adhere to copyright laws in their country.
In conclusion, when torrenting in Singapore, investing in a reliable VPN provider is crucial for protecting your privacy and avoiding legal repercussions. ExpressVPN, NordVPN, and Surfshark are among the top choices, offering robust security features and high-speed connections for a seamless torrenting experience.
Torrenting risks with Singapore VPNs
Torrenting is a popular method of sharing files over the internet, but it comes with its own set of risks. Using a Virtual Private Network (VPN) can help mitigate some of these risks by adding an extra layer of security and anonymity to your internet connection. However, not all VPNs are created equal, and some may pose risks of their own, especially when used for torrenting in Singapore.
Singapore has strict laws regarding copyright infringement, and torrenting copyrighted material is considered illegal. While using a VPN can help hide your IP address and encrypt your internet traffic, not all VPN providers allow torrenting on their servers. Some VPNs may log your online activity and disclose it to authorities if requested, putting you at risk of legal action.
Furthermore, using a VPN with weak encryption protocols can expose your data to hackers and other malicious third parties. This is particularly concerning when torrenting, as your IP address is visible to other users in the torrent swarm. If your VPN connection is compromised, your real IP address could be exposed, making you susceptible to monitoring by copyright enforcers or other cyber threats.
To mitigate these risks, it is essential to choose a reputable VPN provider that has a strict no-logs policy and offers high-level encryption. Additionally, ensure that the VPN allows torrenting on its servers and has a kill switch feature to disconnect your internet in case the VPN connection drops. By taking these precautions, you can enjoy the benefits of torrenting while minimizing the associated risks when using a VPN in Singapore.
0 notes
Text
does a vpn hide piracy
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does a vpn hide piracy
VPN Encryption for Piracy
Title: Understanding VPN Encryption: A Shield Against Piracy Risks
In the realm of online activities, piracy remains a contentious issue, raising concerns about copyright infringement and digital security. As authorities and content creators strive to combat piracy, individuals seeking anonymity often turn to Virtual Private Networks (VPNs) as a shield against potential risks.
VPN encryption serves as a crucial component in safeguarding privacy and mitigating piracy-related threats. By encrypting data traffic, VPNs create a secure tunnel between the user's device and the VPN server, making it challenging for third parties to intercept or decipher sensitive information.
For individuals involved in piracy, VPN encryption offers several key benefits:
Anonymity: VPNs conceal the user's IP address, masking their online identity and making it difficult for authorities to trace their activities back to a specific location or individual.
Secure Data Transmission: Encryption protocols employed by VPNs ensure that data transmitted between the user's device and the VPN server remains confidential, reducing the risk of interception by hackers or surveillance agencies.
Bypassing Geo-Restrictions: Many users turn to piracy to access content that is geo-blocked in their region. VPNs allow individuals to circumvent these restrictions by connecting to servers in other countries, granting them access to a wider range of content without compromising their privacy.
Protection Against Legal Action: By masking their IP address and encrypting their online activities, VPN users decrease the likelihood of facing legal repercussions for engaging in piracy.
While VPN encryption provides a layer of protection for individuals involved in piracy, it's essential to recognize that using VPNs for illegal activities may still carry legal and ethical implications. Content creators and copyright holders continue to employ various measures to combat piracy, emphasizing the importance of respecting intellectual property rights and adhering to legal standards.
In conclusion, VPN encryption serves as a valuable tool for safeguarding privacy and minimizing piracy-related risks. However, individuals should use VPNs responsibly and adhere to legal guidelines to uphold ethical standards in the digital realm.
Anonymity and Piracy with VPN
In today's digital age, anonymity and privacy are becoming increasingly important, especially when it comes to activities like online piracy. Virtual Private Networks (VPNs) have emerged as powerful tools for safeguarding privacy and enabling anonymous browsing, particularly in the context of piracy.
VPNs function by routing your internet connection through a remote server, encrypting your data in the process. This encryption ensures that your online activities remain private and secure from prying eyes, including Internet Service Providers (ISPs) and government surveillance agencies.
When it comes to piracy, VPNs play a crucial role in protecting users' identities and shielding them from potential legal repercussions. By masking your IP address and encrypting your internet traffic, VPNs make it extremely difficult for copyright enforcement agencies to trace your online activities back to you.
Furthermore, VPNs allow users to bypass geographical restrictions and access content that may be blocked or censored in their region. This is particularly relevant for individuals seeking access to copyrighted material through torrenting sites or streaming platforms.
However, it's important to note that while VPNs provide a layer of anonymity, they are not foolproof. Users must choose reputable VPN providers that offer strong encryption protocols and adhere to strict no-logs policies to ensure maximum privacy protection.
Additionally, engaging in piracy itself may still violate copyright laws and can have legal consequences, regardless of whether a VPN is used. While VPNs can mitigate some of the risks associated with online piracy, they do not provide complete immunity from legal action.
In conclusion, VPNs are valuable tools for maintaining anonymity and privacy online, particularly in the context of piracy. However, users must exercise caution and understand the legal implications of their online activities, even when using a VPN.
VPN Protocol for Concealing Piracy
Title: Exploring VPN Protocols: An Effective Tool for Concealing Piracy
In the realm of online privacy and security, Virtual Private Networks (VPNs) have emerged as powerful tools, providing users with a secure and private connection to the internet. While their primary purpose is to safeguard data transmission and protect user identities, VPNs are also widely used for concealing piracy activities.
One of the key elements that make VPNs effective for concealing piracy is the variety of protocols they offer. VPN protocols determine how data is transmitted between a user's device and the VPN server, influencing factors such as speed, security, and compatibility.
One popular VPN protocol used for concealing piracy is OpenVPN. Renowned for its open-source nature and robust encryption capabilities, OpenVPN offers a high level of security, making it difficult for ISPs and authorities to detect or intercept illegal downloading or streaming activities. Its flexibility also allows it to bypass many firewalls and censorship measures, further enhancing its appeal to users engaging in piracy.
Another widely utilized protocol is IKEv2/IPsec. Known for its speed and stability, IKEv2/IPsec provides strong security features, including encryption and authentication, making it suitable for concealing piracy activities. Its ability to quickly re-establish connections in the event of network disruptions ensures uninterrupted access to pirated content.
Additionally, the WireGuard protocol has gained popularity for its simplicity and efficiency. Offering faster speeds and lower latency compared to traditional protocols, WireGuard provides a streamlined solution for users seeking to conceal piracy while enjoying high-speed internet access.
However, it's essential to note that while VPN protocols can effectively conceal piracy activities from ISPs and other third parties, engaging in illegal downloading or streaming still carries legal and ethical implications. Users should exercise caution and adhere to copyright laws and regulations to avoid potential legal consequences.
In conclusion, VPN protocols play a crucial role in concealing piracy activities by providing users with secure and private connections to the internet. OpenVPN, IKEv2/IPsec, and WireGuard are among the popular protocols utilized for this purpose, offering varying levels of security, speed, and compatibility. Nonetheless, users should use VPNs responsibly and respect intellectual property rights to mitigate legal risks associated with piracy.
Legal Implications of VPNs for Piracy
Virtual Private Networks (VPNs) are widely used for protecting online privacy and security by masking users' IP addresses and encrypting data traffic. However, the use of VPNs also raises legal implications, especially in the context of piracy.
One of the primary legal concerns associated with VPNs is their potential to facilitate online piracy. VPNs can enable users to bypass geo-blocks and access copyrighted content illegally, leading to copyright infringement issues. While VPN providers often emphasize privacy protection, they may also attract users seeking to engage in unlawful activities, including downloading and sharing copyrighted material without authorization.
From a legal standpoint, the responsibility for copyright infringement lies with the individual engaging in piracy rather than the VPN service provider. However, some jurisdictions hold VPN providers accountable for facilitating piracy if they are found to promote or encourage illegal activities. This has led to legal battles and controversies surrounding the liability of VPN companies for the actions of their users.
To mitigate the risk of legal implications related to piracy, many reputable VPN providers have implemented strict anti-piracy policies and measures to deter users from engaging in copyright infringement. By prohibiting illegal activities and enforcing terms of service, VPN companies aim to distance themselves from any involvement in unlawful behavior.
In conclusion, while VPNs offer valuable privacy and security benefits, their use in connection with piracy raises legal challenges. Users should exercise caution and adhere to legal standards to avoid potential consequences associated with engaging in copyright infringement through VPN services.
Effectiveness of VPNs in Preventing Piracy
Virtual Private Networks (VPNs) are powerful tools widely used by individuals and organizations to enhance online privacy and security. However, apart from protecting users' data and identity, VPNs also play a significant role in preventing piracy.
In the digital age, piracy refers to the unauthorized distribution or download of copyrighted materials such as movies, music, software, and games. VPNs help combat piracy by encrypting internet traffic and masking users' IP addresses. This means that when someone uses a VPN to access the internet, their online activities are cloaked, making it difficult for third parties to track what they are doing.
When it comes to preventing piracy, VPNs create a secure tunnel between the user's device and the VPN server, making it nearly impossible for hackers, internet service providers, or government agencies to monitor or intercept online activities. This added layer of security not only protects users from potential legal implications of engaging in piracy but also makes it challenging for copyright infringers to identify and target individuals downloading or distributing copyrighted content.
Furthermore, VPNs can also bypass geo-restrictions imposed by content providers, allowing users to access licensed content from anywhere in the world. This can help deter piracy, as users have legal and convenient alternatives to obtain the content they desire without resorting to illegal means.
In conclusion, VPNs are effective tools in preventing piracy by safeguarding user anonymity, protecting online activities from prying eyes, and offering legal avenues to access geo-blocked content. By utilizing a VPN, individuals can enjoy a safer and more secure online experience while contributing to the fight against digital piracy.
0 notes
Text
does a vpn slow down my download speed
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does a vpn slow down my download speed
VPN speed impact
Title: Understanding the Impact of VPN Speed on Your Internet Experience
In today's digital age, Virtual Private Networks (VPNs) have become indispensable tools for ensuring online privacy and security. However, while VPNs offer numerous benefits, users often encounter concerns regarding their impact on internet speed. Understanding the factors influencing VPN speed can help users make informed decisions about their online activities.
One of the primary factors affecting VPN speed is the distance between the user and the VPN server. When connecting to a VPN server located far away, data must travel a longer distance, leading to increased latency and potentially slower speeds. Choosing a server closer to your physical location can mitigate this issue and improve overall performance.
Additionally, the encryption protocols used by VPNs can also influence speed. While stronger encryption provides better security, it can also require more processing power and contribute to slower speeds. Users can often choose between different encryption protocols, balancing security needs with performance requirements.
Furthermore, VPN server load can impact speed, especially during peak usage times. Overloaded servers may struggle to handle incoming traffic efficiently, resulting in slower connections for users. Opting for less congested servers or those specifically optimized for speed can help alleviate this issue.
It's important to note that while VPNs may introduce some degree of speed reduction, the actual impact can vary depending on various factors, including the user's internet connection speed and the VPN service provider. Conducting speed tests with and without the VPN enabled can provide valuable insights into the extent of the speed impact.
In conclusion, while VPNs offer essential privacy and security benefits, users should be aware of their potential impact on internet speed. By understanding the factors influencing VPN speed and making informed choices, users can enjoy a balance between security and performance in their online activities.
Bandwidth throttling VPN
Bandwidth throttling is a common practice employed by internet service providers (ISPs) to regulate network traffic and ensure equal distribution of bandwidth among users. This can result in slower internet speeds, especially during peak hours or when engaging in activities that consume large amounts of data, such as streaming or online gaming.
To bypass bandwidth throttling and regain control over your internet speed, many users turn to Virtual Private Networks (VPNs). A VPN encrypts your internet connection and reroutes it through a remote server, masking your online activities from your ISP. By doing so, VPNs can help prevent ISPs from identifying and selectively slowing down certain types of internet traffic, such as streaming services or torrent downloads.
However, it's important to note that not all VPNs are created equal when it comes to combating bandwidth throttling. Some VPN providers may themselves engage in bandwidth throttling or have limited server bandwidth, which can impact the overall speed and performance of your internet connection.
When choosing a VPN to circumvent bandwidth throttling, look for providers that offer robust encryption protocols, a large network of high-speed servers, and a strict no-logs policy to ensure your online privacy. Additionally, consider selecting a VPN server located closer to your physical location to minimize latency and optimize speeds.
By utilizing a VPN to combat bandwidth throttling, you can enjoy faster and more consistent internet speeds while safeguarding your online privacy and security.
VPN latency effects
VPN latency effects can have a significant impact on users' online experience. Latency refers to the time it takes for data packets to travel from the user's device to the VPN server and back. When using a VPN, latency can be influenced by various factors, including server distance, network congestion, and encryption overhead.
One of the primary effects of VPN latency is slower internet speeds. Because data has to travel further and undergo encryption processes, users may experience delays in loading web pages, streaming videos, or downloading files. This can be frustrating, especially for users who rely on fast internet connections for work or entertainment purposes.
Moreover, high latency can also lead to buffering issues during video calls or online gaming sessions. The delay in data transmission can result in choppy video quality, lagging gameplay, and poor overall performance. For gamers, this can be particularly frustrating as split-second reactions are crucial for success in many online games.
Additionally, VPN latency can impact real-time activities such as online trading or live streaming events. The delay in data transfer can affect the timeliness of information delivery, potentially causing missed opportunities or disruptions in viewing experiences.
Overall, while VPNs offer valuable privacy and security benefits, users should be aware of the potential latency effects. Choosing a VPN provider with optimized servers, efficient protocols, and minimal network congestion can help mitigate latency issues and ensure a smoother online experience.
Download speed VPN comparison
Title: A Comprehensive Comparison of Download Speeds in VPN Services
In today's digital age, internet users are increasingly turning to Virtual Private Networks (VPNs) to safeguard their online activities and enhance their privacy. However, one crucial factor that often influences the choice of VPN service is download speed. Users want to ensure that their VPN not only offers robust security features but also maintains high-speed connections for seamless browsing, streaming, and downloading.
When comparing VPNs based on download speeds, several factors come into play. Firstly, the geographical location of the VPN server plays a significant role. Generally, connecting to a server closer to your physical location results in faster download speeds due to reduced latency. Additionally, the VPN provider's infrastructure and network capacity heavily influence download speeds. Reputable VPN services invest in high-performance servers and optimize their networks to minimize speed loss.
Furthermore, the encryption protocols used by VPNs can impact download speeds. While stronger encryption ensures better security, it may also lead to slower connection speeds. Therefore, users often have the option to choose between different encryption protocols, balancing security and performance according to their needs.
To help users make informed decisions, numerous independent tests and comparisons evaluate the download speeds of various VPN services. These tests measure the speed performance across different servers and locations, providing valuable insights into each VPN's performance under real-world conditions.
Ultimately, the best VPN for download speed depends on individual preferences and requirements. Some users prioritize security and are willing to sacrifice a fraction of their download speed for enhanced protection. Others prioritize speed above all else, seeking VPN services optimized for high-speed connections.
In conclusion, when comparing VPN services based on download speeds, users should consider factors such as server locations, network infrastructure, encryption protocols, and independent speed tests. By doing so, users can find a VPN service that not only safeguards their online privacy but also delivers fast and reliable download speeds for uninterrupted internet browsing and streaming experiences.
Internet speed VPN connection
When it comes to using a Virtual Private Network (VPN) connection, internet speed is a crucial factor to consider. A VPN can help enhance your online security and privacy by encrypting your internet traffic and masking your IP address. However, using a VPN can sometimes lead to slower internet speeds compared to browsing without one.
The impact of a VPN on your internet speed can vary depending on several factors. One of the main factors is the distance between you and the VPN server you are connected to. Connecting to a server that is far away can result in slower speeds due to increased latency. Choosing a server closer to your physical location can help improve your internet speed while using a VPN.
Additionally, the encryption process used by VPNs can also contribute to slower internet speeds. The stronger the encryption, the more processing power it requires, potentially slowing down your connection. However, many VPN services offer a good balance between security and speed by using efficient encryption protocols.
It's essential to choose a reputable VPN provider known for offering fast and reliable connections. Some VPN services have specialized servers optimized for speed, which can help mitigate any slowdowns in your internet connection. Before subscribing to a VPN service, you can also look for reviews and speed tests to ensure that it meets your performance expectations.
In conclusion, while using a VPN connection can impact your internet speed, selecting the right provider and server location can help minimize any slowdowns. By balancing security and performance, you can enjoy a safer online experience without compromising on speed.
0 notes
Text
do vpn hide torrenting
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do vpn hide torrenting
VPN torrent privacy
Title: Ensuring Torrent Privacy with VPN: A Comprehensive Guide
In the world of torrenting, privacy is paramount. With the rise of digital surveillance and copyright enforcement, users must take measures to protect their online activities. This is where VPNs (Virtual Private Networks) come into play, offering a robust solution for safeguarding torrent privacy.
A VPN creates a secure tunnel between your device and the internet, encrypting all data transmitted through it. When torrenting, this means that your IP address – the unique identifier of your device – is masked. Instead of connecting directly to the torrent swarm, your traffic is routed through VPN servers located in various locations worldwide. This effectively hides your true location and identity from prying eyes, whether they be government agencies, ISPs, or copyright trolls.
Privacy isn't the only benefit of using a VPN for torrenting. By masking your IP address, VPNs also help prevent throttling by your ISP. Many ISPs actively monitor torrent traffic and may throttle your connection if they detect it. With a VPN, your ISP can't see what you're downloading, so they can't throttle your speeds based on your torrenting activity.
However, not all VPNs are created equal when it comes to torrent privacy. It's crucial to choose a VPN provider that offers strong encryption, a strict no-logs policy, and a wide range of servers optimized for P2P file sharing. Additionally, ensure that your VPN doesn't leak your IP address or DNS requests, as these could compromise your anonymity.
In conclusion, VPNs are an essential tool for maintaining privacy while torrenting. By encrypting your internet traffic and masking your IP address, they provide a layer of security that is indispensable in today's online landscape. So, if you're serious about torrent privacy, invest in a reputable VPN service and enjoy worry-free downloading.
Torrenting anonymity VPN
Torrenting has become a popular method of sharing files online, but it comes with its own set of risks, particularly when it comes to maintaining anonymity. Many internet service providers (ISPs) actively monitor torrenting activity and may even throttle your connection if they detect you are downloading torrents. To combat these privacy concerns, many torrent users turn to virtual private networks (VPNs) to mask their IP addresses and encrypt their internet traffic.
A VPN for torrenting offers users the ability to maintain their anonymity while downloading and sharing files. By routing your internet connection through a remote server and masking your IP address, a VPN ensures that your online activity remains private and secure. This added layer of encryption not only protects your identity from prying eyes but also helps evade throttling and monitoring by ISPs.
When choosing a VPN for torrenting, it is crucial to select a provider that supports P2P file sharing and offers fast connection speeds. Additionally, ensuring that the VPN service has a strict no-logs policy is essential for safeguarding your privacy and anonymity.
While using a VPN can help enhance your torrenting experience by providing anonymity and security, it is essential to remember that not all VPNs are created equal. Researching and selecting a reputable VPN provider that aligns with your specific needs is key to enjoying safe and secure torrenting. By investing in a quality VPN service, you can torrent with peace of mind knowing that your online activities are shielded from prying eyes.
VPN torrent encryption
VPN torrent encryption is a crucial aspect of safe and secure file sharing practices. When using a VPN (Virtual Private Network) for torrenting, it is important to ensure that your data is properly encrypted to maintain your privacy and anonymity online.
Encryption plays a key role in protecting your torrenting activities from prying eyes such as hackers, ISPs, and government agencies. By encrypting your data, VPNs scramble the information you send and receive, making it unreadable to anyone trying to intercept it.
VPN torrent encryption works by creating a secure tunnel between your device and the VPN server, ensuring that your IP address and online activities remain hidden. This way, you can download and share files via torrents without worrying about third parties tracking your online behavior.
It is essential to choose a VPN service provider that offers high-quality encryption protocols such as AES-256, which is considered military-grade encryption. Additionally, look for VPNs that support features like a kill switch and DNS leak protection to further enhance your security while torrenting.
By utilizing VPN torrent encryption, you can enjoy a safer and more private torrenting experience. Remember to always prioritize your online security and protect your digital footprint while engaging in file sharing activities.
Torrent masking with VPN
Torrent masking with VPN provides a secure and private way to download and share files without compromising your online identity. Torrenting is a popular method of peer-to-peer file sharing, but it comes with risks of exposing your IP address to malicious entities. By using a VPN (Virtual Private Network), you can mask your true IP address and encrypt your internet traffic, keeping your online activities private and secure.
When you torrent without a VPN, your IP address is visible to anyone monitoring the network, including copyright enforcement agencies, hackers, and internet service providers. This makes you vulnerable to legal action, hacking attempts, and surveillance. With a VPN, your true IP address is hidden and replaced with the VPN server's IP address, making it virtually impossible for anyone to track your online activities back to you.
In addition to masking your IP address, a VPN encrypts your internet traffic, ensuring that your data remains secure and private. This is especially important when downloading or sharing sensitive files that you want to keep confidential. By encrypting your connection, a VPN adds an extra layer of security that helps protect your personal information from cyber threats.
Overall, torrent masking with VPN offers a safe and anonymous way to engage in file sharing activities online. It helps you bypass geographical restrictions, stay anonymous, and protect your online privacy. If you are a frequent torrent user, using a VPN is essential to ensure a secure and worry-free downloading experience.
Secure torrent downloads with VPN
Using a Virtual Private Network (VPN) is a crucial step to ensure secure torrent downloads. Torrenting involves sharing files over a peer-to-peer network, which can expose your IP address to others in the network. This leaves your personal information vulnerable to hackers and monitoring agencies.
By using a VPN, your internet connection is encrypted, masking your IP address and making your online activity anonymous. This added layer of security prevents third parties from tracking your torrent downloads back to you. Additionally, a VPN allows you to bypass any restrictions or censorship imposed by your internet service provider or government.
When selecting a VPN for secure torrent downloads, it is important to choose a provider that does not keep logs of your online activity. Opt for a VPN with a strict no-logs policy to ensure maximum privacy. Furthermore, look for features such as kill switches and DNS leak protection to further enhance your security while torrenting.
It is also recommended to choose a VPN provider that offers high-speed connections and unlimited bandwidth to ensure optimal performance during torrent downloads. Additionally, consider the server locations offered by the VPN provider, as having servers in multiple countries can help improve download speeds and access geo-restricted content.
In conclusion, using a VPN for secure torrent downloads is essential to protect your privacy and ensure safe browsing habits. Invest in a reputable VPN service to encrypt your internet connection and enjoy peace of mind while torrenting.
0 notes
Text
does comcast track torrent vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does comcast track torrent vpn
Comcast tracking policy
Title: Understanding Comcast's Tracking Policy: What Users Need to Know
In today's digital age, concerns about online privacy and data tracking have become increasingly prevalent. As one of the largest internet service providers in the United States, Comcast plays a significant role in shaping how users' data is collected and utilized. Understanding Comcast's tracking policy is crucial for users who want to maintain their privacy and security online.
Comcast, like many other internet service providers, collects data about its users' online activities. This data can include websites visited, search queries, and device information. Comcast states that it uses this data to improve its services, personalize content, and deliver targeted advertisements.
One of the key aspects of Comcast's tracking policy is its use of cookies and similar tracking technologies. These technologies enable Comcast to track users' browsing habits across different websites and devices. While Comcast claims that this data is anonymized and used for advertising purposes, some users may still have concerns about the extent of tracking and the potential for their data to be shared with third parties.
To address these concerns, Comcast provides users with options to manage their privacy settings. Users can opt out of certain types of tracking, such as targeted advertising, by adjusting their preferences in their Comcast account settings. Additionally, users can choose to use privacy-enhancing tools such as virtual private networks (VPNs) to further protect their online privacy.
It's important for users to be aware of Comcast's tracking policy and take steps to protect their privacy online. By understanding how their data is collected and used, users can make informed decisions about their online activities and ensure that their personal information remains secure.
Torrent activity monitoring
Torrent activity monitoring is a practice used to track and analyze the flow of data through torrent networks. Torrents are a popular method of sharing large files over the internet, and monitoring torrent activity can provide valuable insights for various purposes.
One common use of torrent activity monitoring is to combat piracy. By monitoring torrent sites and tracking the distribution of copyrighted material, anti-piracy organizations can identify and take action against individuals or groups engaging in illegal file sharing. This helps to protect the intellectual property rights of content creators and copyright holders.
Torrent activity monitoring can also be utilized for cybersecurity purposes. By tracking torrent downloads, cybersecurity professionals can identify potential threats such as malware-infected files being shared through torrent networks. This information can then be used to strengthen cybersecurity measures and protect against malicious attacks.
Furthermore, government agencies and law enforcement use torrent activity monitoring to investigate and curb illegal activities such as the distribution of illicit content, cybercrime, and terrorism-related activities.
Overall, torrent activity monitoring plays a crucial role in maintaining a safe and secure online environment. Whether it's combating piracy, enhancing cybersecurity, or enforcing the law, monitoring torrent activity provides valuable insights that help protect the integrity of the internet and its users.
VPN usage surveillance
Title: Navigating the Surveillance Minefield: The Importance of VPN Usage
In an era where digital privacy is increasingly under threat, the use of Virtual Private Networks (VPNs) has become a crucial tool for safeguarding online activities from surveillance. VPNs encrypt internet traffic, creating a secure tunnel between the user's device and the VPN server, thereby shielding sensitive data from prying eyes.
One of the primary reasons for the surge in VPN usage is the growing concern over government surveillance and data mining by ISPs (Internet Service Providers) and tech giants. With the ability to track and analyze users' browsing habits, these entities can compile vast amounts of personal information, leading to potential privacy breaches and targeted advertising.
Furthermore, the rise of public Wi-Fi networks poses additional risks, as they are often hotspots for cybercriminals looking to intercept data transmitted over unsecured connections. VPNs offer a layer of protection by encrypting data, making it virtually impossible for hackers to decipher.
Another aspect driving VPN adoption is the need to bypass geo-restrictions imposed by content providers and governments. By connecting to servers located in different countries, users can access region-locked content and services, expanding their online freedom.
However, while VPNs provide a level of anonymity and security, they are not foolproof. Some VPN providers may log user activity or share data with third parties, undermining the very purpose of using a VPN. Therefore, it's essential to choose a reputable VPN provider with a strict no-logs policy and robust encryption protocols.
In conclusion, in an age where digital surveillance is rampant, VPNs offer a vital defense mechanism against prying eyes. By encrypting internet traffic and masking IP addresses, VPNs empower users to reclaim their online privacy and freedom. Nevertheless, users must remain vigilant and select trustworthy VPN services to ensure their data remains secure and private.
Privacy implications of Comcast
Comcast, one of the largest telecommunications conglomerates in the United States, has been a subject of scrutiny regarding its privacy implications. As a provider of internet, cable television, and other communication services to millions of households, Comcast collects vast amounts of user data, raising concerns about privacy infringement.
One of the primary concerns surrounding Comcast is its data collection practices. As users browse the internet, stream content, or make phone calls using Comcast services, the company gathers data on their activities. This data may include browsing history, search queries, viewing preferences, and even personal information such as names and addresses. While Comcast claims to use this data for purposes such as improving service quality and delivering targeted advertisements, critics argue that such practices pose significant privacy risks.
Furthermore, Comcast's involvement in controversial initiatives like the now-defunct "Comcast Spyware" program has further fueled privacy concerns. This program, which aimed to monitor users' online activities in the name of network security, faced backlash from privacy advocates who viewed it as a violation of user privacy.
Moreover, Comcast's role as an internet service provider (ISP) also raises concerns about net neutrality and data throttling. As ISPs, Comcast has the capability to monitor and control the flow of internet traffic, potentially influencing users' access to certain websites or services based on their data usage patterns.
In response to these concerns, Comcast has implemented privacy policies and tools aimed at giving users more control over their data. However, critics argue that these measures may not go far enough in protecting user privacy, especially given Comcast's vast reach and influence in the telecommunications industry.
In conclusion, Comcast's dominance in the telecommunications market and its extensive data collection practices raise significant privacy implications for users. As technology continues to evolve, it is crucial for regulators and consumers alike to remain vigilant in safeguarding privacy rights in the digital age.
ISP data tracking regulations
Title: Understanding ISP Data Tracking Regulations: Safeguarding Online Privacy
In the digital age, concerns regarding online privacy have become increasingly prominent. One significant aspect of this issue is the tracking of internet users' data by Internet Service Providers (ISPs). ISPs have the capability to monitor and collect vast amounts of data about their customers' online activities, including websites visited, search history, and even the content of communications.
To address these concerns and protect consumers' privacy rights, various regulations have been implemented to govern ISP data tracking practices. One such regulation is the General Data Protection Regulation (GDPR) in the European Union, which imposes strict requirements on ISPs regarding the collection, processing, and storage of user data. Under the GDPR, ISPs must obtain explicit consent from users before collecting their data and must provide transparent information about how the data will be used.
In the United States, ISP data tracking is regulated primarily by the Federal Communications Commission (FCC) and the Federal Trade Commission (FTC). The FCC has implemented rules requiring ISPs to obtain opt-in consent from customers before using or sharing their sensitive information, such as browsing history and app usage data. Additionally, the FTC enforces laws prohibiting unfair or deceptive practices related to consumer privacy, which may include misleading statements about data tracking practices.
Furthermore, some states have enacted their own legislation to enhance consumer privacy protections in the absence of comprehensive federal regulations. For example, the California Consumer Privacy Act (CCPA) grants California residents the right to know what personal information is being collected by ISPs and to opt out of the sale of their data.
Overall, ISP data tracking regulations play a crucial role in safeguarding online privacy and ensuring that consumers have control over their personal information. By adhering to these regulations, ISPs can build trust with their customers and contribute to a more transparent and secure digital ecosystem.
0 notes
Text
do you guys use a vpn to download torrents
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do you guys use a vpn to download torrents
VPN for torrenting
Title: Unlock Safe Torrenting: The Role of VPNs in Protecting Your Privacy
Torrenting, the peer-to-peer file sharing technology, has revolutionized the way we access digital content. However, while torrenting offers unparalleled access to a vast array of files, it also comes with inherent risks. One of the primary concerns is privacy and security, as torrenting exposes your IP address to potential monitoring by ISPs and copyright enforcement agencies.
This is where Virtual Private Networks (VPNs) come into play. A VPN encrypts your internet connection, creating a secure tunnel between your device and the VPN server. When you torrent through a VPN, your IP address is masked, and your online activities become virtually untraceable.
Using a VPN for torrenting offers several key benefits:
Privacy Protection: By hiding your IP address, VPNs prevent ISPs and other third parties from monitoring your torrenting activities. This shields you from potential legal repercussions and protects your privacy.
Anonymity: VPNs assign you a new IP address from their server network, making it difficult for anyone to trace your online actions back to you. This anonymity adds an extra layer of security while torrenting.
Bypassing Geo-restrictions: Some torrent sites and content may be restricted based on your geographical location. With a VPN, you can bypass these restrictions by connecting to a server in a different country where the content is accessible.
Security: VPNs encrypt your internet traffic, safeguarding your data from hackers and other malicious entities lurking on public Wi-Fi networks or within the torrenting community.
However, not all VPNs are created equal. When choosing a VPN for torrenting, opt for providers that offer strong encryption, a strict no-logs policy, and high-speed servers optimized for P2P file sharing.
In conclusion, VPNs are indispensable tools for safe and secure torrenting. By encrypting your connection and masking your IP address, VPNs empower you to enjoy the benefits of torrenting without compromising your privacy and security.
P2P file sharing
P2P file sharing, also known as peer-to-peer file sharing, is a method of sharing digital files directly between users without relying on a centralized server. This decentralized approach allows users to transfer files such as music, movies, documents, and software directly from one another's devices over the internet.
One of the key benefits of P2P file sharing is its efficiency and speed. Since files are shared directly between users, there is no reliance on a single server that could potentially become overloaded, leading to faster download speeds. Additionally, P2P file sharing can reduce strain on network resources as users share the burden of file distribution among themselves.
However, it is important to note that P2P file sharing has faced legal challenges due to copyright infringement issues. Some users may share files illegally, violating copyright laws by distributing copyrighted materials without permission. As a result, many countries have implemented regulations to combat illegal file sharing and protect intellectual property rights.
Despite these challenges, P2P file sharing continues to be a popular method for users to share files with one another. It has proven to be particularly useful for distributing large files that may be difficult to transfer through other methods. By leveraging the power of peer-to-peer networks, users can access a vast array of digital content and collaborate with others in a decentralized and efficient manner.
Torrent download security
When it comes to downloading torrents, ensuring your security and privacy is crucial. Torrenting involves sharing files with a decentralized network of users, which can expose you to various online threats if proper precautions are not taken.
One of the first steps you can take to enhance your torrent download security is to use a reliable VPN (Virtual Private Network). A VPN encrypts your internet connection and routes your traffic through a secure server, masking your IP address and preventing third parties from tracking your online activities. This helps to keep your identity and data safe while downloading torrents.
It is also important to download torrents only from reputable sources and to verify the authenticity of the files you are downloading. Malicious actors often disguise malware as popular files to infect users' devices and steal their personal information. By using trusted torrent websites and reading user comments and reviews, you can minimize the risk of downloading malicious content.
Furthermore, keeping your antivirus software up to date is essential for torrenting safely. Antivirus programs can detect and remove malware from your system, protecting you from potential security threats. Regularly scanning your downloaded files for viruses and malware can prevent any harmful content from causing damage to your device.
In conclusion, by using a VPN, downloading torrents from reliable sources, and maintaining updated antivirus software, you can enhance your torrent download security and enjoy a safer online experience. Prioritizing your security while torrenting is essential to protect your privacy and data from cyber threats.
Anonymous torrenting
Anonymous torrenting refers to the practice of downloading and sharing files through the BitTorrent protocol while maintaining privacy and anonymity. While torrenting itself is a popular method for quickly and efficiently sharing large files, many users are concerned about their online privacy and security while engaging in such activities.
One of the main appeals of anonymous torrenting is the ability to mask one's IP address from third parties, including government agencies, Internet service providers, and copyright enforcement groups. By hiding their true IP address, users can protect themselves from potential legal issues that may arise from downloading copyrighted material. Additionally, anonymity can help prevent targeted advertising and tracking by various online entities.
There are several methods that individuals can use to torrent anonymously. One common approach is the use of virtual private networks (VPNs), which encrypt internet traffic and reroute it through remote servers, making it difficult for external parties to trace the user's activities back to their true IP address. Another option is to use proxy services, which act as intermediaries between a user's device and the internet, obscuring their IP address in the process.
While anonymous torrenting can provide a layer of privacy and security for users, it is important to note that engaging in illegal activities, such as downloading copyrighted material without permission, is still against the law in many jurisdictions. It is essential for individuals to understand the laws regarding online piracy in their country and to use anonymous torrenting methods responsibly and ethically.
In conclusion, anonymous torrenting offers users a way to share and download files while maintaining their privacy and security online. By utilizing tools such as VPNs and proxy services, individuals can enjoy the benefits of torrenting while minimizing the risks associated with potential privacy breaches.
VPN benefits for torrent users
Using a VPN (Virtual Private Network) offers numerous benefits for torrent users. Torrent users often face legal risks and privacy concerns due to the nature of peer-to-peer file sharing. By utilizing a VPN, these users can mitigate these risks and enhance their torrenting experience.
One of the primary advantages of a VPN for torrent users is the anonymity it provides. When connected to a VPN server, your real IP address is hidden, making it difficult for anyone to track your online activities back to you. This anonymity can help protect torrent users from copyright trolls and legal action related to downloading copyrighted material.
In addition to anonymity, VPNs encrypt your internet traffic, adding an extra layer of security to your online activities. This encryption is crucial for torrent users, as it prevents ISPs and other third parties from monitoring your torrenting habits or throttling your internet connection based on your activities.
Moreover, VPNs can help torrent users bypass geo-restrictions and access content that may be unavailable in their region. By connecting to a server in a different location, torrent users can circumvent these restrictions and download content from anywhere in the world.
Overall, VPNs are essential tools for torrent users looking to protect their privacy, avoid legal consequences, and access a wider range of content. By investing in a reliable VPN service, torrent users can enjoy a safer and more secure torrenting experience.
0 notes