#Unified Extensible Firmware Interface
Explore tagged Tumblr posts
Text
How to fix a vulnerable Trusted Platform Module [TPM]
The Trusted Platform Module (TPM) technology provides hardware-based security functions. A TPM chip performs cryptographic operations securely on your device. In this article, we will discuss the various steps on how to fix a vulnerable Trusted Platform Module [TPM]. Here is an exciting article on Manage TPM Protector: How to encrypt additional drives on an MBAM-protected device, and how to…
#Dell Firmware Update Utility#Determine if my TPM is Vulnerable#firmware#Firmware Update#fix a Vulnerable TPM#Install Windows Updates#Microsoft Windows#Unified Extensible Firmware Interface#Windows#Windows 10#Windows Server#Windows Server 2012#Windows Server 2016#Windows Server 2019#Windows Server 2022#Windows Server 2025
0 notes
Text
tech mfs be like she unify with my firmware interface till im extensible
2 notes
·
View notes
Text
Enterprise-Class Power in 1U: HPE DL360 Gen11 Server (P72987-005)
In the modern data center, performance, scalability, and efficiency are non-negotiable. The HPE DL360 Gen11 Server (P72987-005) is designed to deliver on all three fronts. With powerful processing, next-gen memory, and robust storage capabilities packed into a compact 1U chassis, this server is built to meet the needs of high-performance computing and virtualization workloads.
The P72987-005 model comes equipped with a 12-core Intel Xeon Silver 4510 processor running at 2.4 GHz. This processor delivers efficient, multi-threaded performance ideal for demanding enterprise applications, virtualization tasks, and data-driven workloads.
Backing the compute power is 64 GB of DDR5 Smart Memory, ensuring faster data access and improved energy efficiency. The server supports up to 8 TB of DDR5 RAM, giving you plenty of room to scale memory as your applications grow.
For storage, the DL360 Gen11 (P72987-005) includes two 1.2 TB SAS 10K RPM hard drives, configured in an 8-bay SFF chassis. The included MR408i-o RAID controller enhances data protection and performance by managing storage at the hardware level. This makes the server a reliable choice for organizations handling critical data and large file operations.
Designed for resilience and uptime, the server features dual 1000W Titanium hot-plug redundant power supplies. These help maintain operations during power fluctuations or hardware failures, making the system highly dependable in mission-critical environments.
The P72987-005 also features PCIe Gen5 slots for expansion, offering support for high-speed I/O, networking cards, or even GPU acceleration. With advanced security features such as Silicon Root of Trust and Unified Extensible Firmware Interface (UEFI) Secure Boot, the server ensures data integrity and protection from unauthorized access.
Integrated Lights-Out (iLO 6) management capabilities enable administrators to monitor, manage, and troubleshoot the server remotely, reducing downtime and simplifying routine maintenance tasks.
Conclusion
The HPE DL360 Gen11 Server (P72987-005) combines powerful compute, scalable memory, secure management, and efficient power design—all in a slim 1U form factor. It is the ideal choice for businesses looking to support virtualization, cloud computing, and enterprise applications with confidence and room to grow.
0 notes
Text
Why ONVIF Cameras Are Critical for Enhancing Security in Commercial Networks
In today’s interconnected world, the demand for secure, reliable, and scalable surveillance systems has never been more pressing. For commercial networks, video surveillance plays a pivotal role in safeguarding assets, employees, and sensitive information. However, as the complexity of surveillance systems grows, so does the challenge of integrating disparate devices into a unified network. This is where ONVIF cameras come into play, offering standardized solutions that enhance interoperability and streamline operations in commercial settings.
The Need for Standardized Security Solutions in Commercial Networks
Commercial networks often encompass a wide range of surveillance requirements, from monitoring expansive warehouses to securing corporate offices and retail spaces. These environments frequently rely on devices from various manufacturers, leading to compatibility issues and inefficiencies. ONVIF (Open Network Video Interface Forum)standards address these challenges by enabling seamless communication between devices, regardless of brand or model. This standardization simplifies system integration, reduces deployment time, and ensures consistent performance across all components.
By adopting ONVIF-compliant cameras, businesses can future-proof their surveillance infrastructure. These cameras are designed to support evolving security needs while maintaining compatibility with the latest technologies. This adaptability is crucial in an era where security threats are continually evolving.
Key Features of ONVIF Cameras That Drive Their Importance
ONVIF cameras offer a suite of features tailored to the unique demands of commercial networks. Some of the most critical attributes include:
Interoperability Across Devices: ONVIF cameras adhere to universal standards, allowing them to integrate seamlessly with other ONVIF-compliant devices. This eliminates the need for proprietary solutions and fosters a more flexible and scalable system.
Enhanced Cybersecurity Measures: Cybersecurity is a top priority for commercial networks, and ONVIF cameras incorporate advanced security protocols to protect against unauthorized access and data breaches. These measures include encrypted communications, secure firmware updates, and user authentication features.
Scalability for Growing Businesses: As companies expand, their security systems must scale accordingly. ONVIF cameras support this growth by providing a standardized framework that can accommodate additional devices without extensive reconfiguration.
Remote Monitoring and Management: Many ONVIF cameras come equipped with remote access capabilities, enabling businesses to monitor their premises in real-time from anywhere in the world. This feature is particularly valuable for multi-site operations and global enterprises.
Real-World Applications of ONVIF Cameras in Commercial Networks
ONVIF cameras have proven their effectiveness across a diverse array of industries. Here are some examples of how they are enhancing security in commercial networks:
Retail: Retailers face constant challenges in preventing theft, managing foot traffic, and ensuring customer safety. ONVIF cameras provide comprehensive coverage and integrate with point-of-sale systems to detect anomalies and improve operational efficiency.
Healthcare: Hospitals and clinics require robust surveillance systems to protect sensitive patient data, monitor high-risk areas, and ensure staff safety. ONVIF cameras support these needs by offering high-resolution imaging and secure data transmission.
Industrial Facilities: Manufacturing plants and warehouses benefit from ONVIF cameras’ ability to monitor production lines, track inventory, and enhance worker safety. Their rugged design ensures reliable performance in challenging environments.
Corporate Offices: In office settings, ONVIF cameras help secure entry points, monitor parking lots, and protect confidential business information. They integrate seamlessly with access control systems, creating a cohesive security ecosystem.
How ONVIF Cameras Enhance Operational Efficiency
Beyond security, ONVIF cameras contribute to the overall efficiency of commercial networks. By standardizing communication protocols, they reduce the need for complex configurations and technical expertise during installation. This streamlined setup translates to cost savings and faster deployment.
Additionally, ONVIF cameras enable centralized management of surveillance systems. Administrators can configure and monitor multiple cameras from a single interface, reducing the time and effort required to maintain the network. This level of control is especially beneficial for large-scale operations spanning multiple locations.
The Role of AI and Analytics in ONVIF Cameras
The integration of artificial intelligence (AI) and advanced analytics has elevated the capabilities of ONVIF cameras. Features such as facial recognition, license plate detection, and behavioral analysis empower businesses to proactively address security threats. These AI-driven tools provide actionable insights, helping organizations make informed decisions and optimize their security strategies.
Moreover, ONVIF cameras equipped with analytics can identify patterns and anomalies in real-time, enabling quicker responses to potential incidents. This level of intelligence is essential for maintaining a safe and secure commercial environment.
Future-Proofing Commercial Security with ONVIF Standards
The adoption of ONVIF standards ensures that commercial networks are prepared for future advancements in surveillance technology. As the industry evolves, ONVIF continues to update its specifications to incorporate emerging trends and innovations. This commitment to progress provides businesses with the confidence that their investment in ONVIF cameras will remain relevant and effective for years to come.
By aligning with ONVIF standards, organizations can also reduce their reliance on proprietary systems, which often come with limitations and higher costs. Instead, they gain access to a global ecosystem of compliant devices, fostering greater innovation and competition within the market.
Take the first step toward revolutionizing your commercial security by integrating ONVIF cameras into your surveillance strategy.
0 notes
Text
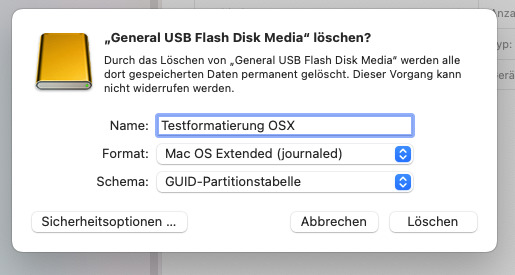






Hackintosh: OSX Installationsstick vorbereiten
Option "Schema" nicht sichtbar
Um eine Betriebssystem (OSX) von einem USB Stick zu installieren, sind diverse Schritte notwendig. Zuerst sollte ein USB Stick formatiert werden.
Es kann aber die Situation auftreten, dass die Option "Schema" nicht existiert. Im Festplattendienstprogramm muß unter dem Menü Darstellung die Option "Alle Geräte einblenden" aktiv sein.
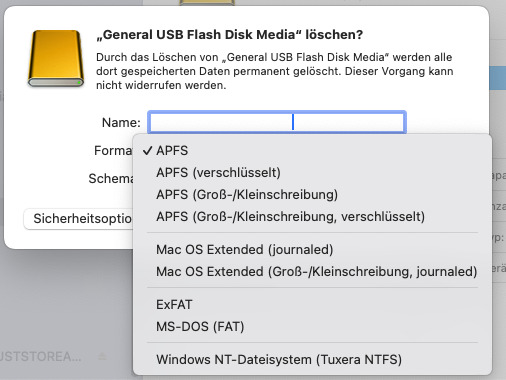
Nur so taucht das Dropdownmenü "Schema" auf mit den Optionen: GUID Partitionstabelle (GPT), Master Boot Record (MBR) und Apple Partitionstabelle (APT). Für Installationen auf dem PC oder Mac ist GPT die richtige Wahl mit der Formatierung Mac OS Extended (journaled). Als Formate stehen die folgenden grundsätzlich zur Verfügung; für alle Formate ist im Test auch das Schema "GUID" möglich:
APFS
Mac OS Extended (journaled)
ExFAT
MS-DOS
NTFS
Es ist zu bedenken, dass eine Formatierung "Mac OS Extended (journaled)" mit dem Schema "Master Boot Record" dazu führt, dass der Stick dann über keine EFI Partition verfügt, die zum Booten des Installationsstick aber notwendig ist. Kurz: die Mac Installationsdatei kann nicht ausgeführt werden.
Aber: in einem Test mit einem solchen Stick (also mit Schema MBR) hatte ich meinen vorbereiteten EFI Ordner einfach in das Rootverzeichnis des Sticks kopiert; der Ordner lag also neben der "install Mac OS Sequoia" Datei. Tatsächlich war eine Installation möglich und erfolgreich. Aber ich würde die Standardroutine empfehlen mit der GUID Partitionstabelle.
Über "Terminal" kann man mit einem "sudo" Befehl (dies habe ich an anderer Stelle bereits beschrieben) die OSX Installationsdatei auf den Stick kopieren, der zugleich nochmal formatiert und auch einen neuen Namen bekommt (z.B. Install macOS Sequoia).
Begriffe (Mehr Infos)
UEFI = Unified Extensible Firmware Interface (einheitliche erweiterbare Firmware-Schnittstelle)
EFI = Extensible Firmware Interface
Um eine vorbereitete, also für die individuelle Hardwarekomponenten abgestimmte ESP (EFI-Systempartition) auf den Stick zu bekommen, nutzt ich beispielsweise Opencore Configurator, suche den Stick und klicke auf "mounten". Dann taucht im Finder EFI auf. Hier nun die eigenen Daten (Kexte, congif.plist u.a.) kopieren.
Der bootfähige USB Stick ist nun fertig für die Installation.
Ergänzende Anmerkungen
Dieser spezielle EFI Ordner ist für PC User zwingend erforderlich ("Hackintosh"). Die Mac-User benötigen einen speziellen EFI Ordner meines Wissen für eine Installation nicht. Entsprechend ist es für sie etwas einfacher, wenn sie optional ein neues OS vom Stick installieren wollen. Mit der Hardware Serie der "M" Prozessoren und Weiterentwicklungen der eigenen Hardware (Intel Prozessoren werden schon länger nicht mehr im MAC verbaut), ist das Ende des Hackintosh irgendwann erreicht. Jedenfalls konnte ist das derzeit aktuelle OSX 15.1.1 (Sequoia) ohne Probleme auf meinem Intel PC installieren.
Dr. Andreas U. Korn, 28.11.2024
+ + +
0 notes
Text
9 Most Important Components Of a Computer And Their Functions Products
Computers Component And Their Functions have become critical to modern existence, powering the whole lot from communique and training to entertainment and paintings. But behind every computer's capability is a group of critical additives, every playing a critical position in its operation. Whether you’re building your personal PC or simply curious about what makes your laptop run, information the key hardware additives is vital. function.

Central Processing Unit (CPU)
The Central Processing Unit (CPU), frequently referred to as the brain of the computer, is one of the most critical additives. The CPU contains out most of the processing interior a computer, executing instructions from software and performing calculations. It handles records from reminiscence and enter/output devices, orchestrating obligations to ensure the system features easily.
Intel Core i9-13900K – High-end CPU for gaming and heavy workloads.
AMD Ryzen 9 7900X – Powerful processor with excellent multi-core performance.
Intel Core i5-13600K – Mid-range processor ideal for gaming and productivity.
AMD Ryzen 5 5600X – Budget-friendly CPU for general computing and light gaming.
Key Features of a CPU
Cores
Modern CPUs have multiple cores, letting them manner a couple of tasks simultaneously. Dual-core, quad-middle, and octa-core processors are commonplace.
Clock Speed
This determines how rapid a CPU can manner instructions, usually measured in GHz (gigahertz). The better the clock pace, the quicker the CPU can carry out responsibilities.
Threads:
Some processors help multithreading, allowing every core to deal with a couple of thread of execution simultaneously, boosting overall performance in multitasking and intensive packages.
Examples of famous CPUs include Intel’s Core i-collection (i3, i5, i7, i9) and AMD’s Ryzen processors.
Motherboard
The motherboard is the backbone of the laptop, connecting all of the components and letting them speak with every other. It homes the CPU, reminiscence, storage, and different peripherals. The motherboard additionally carries a chipset that manages statistics float between the processor, reminiscence, and external devices.
ASUS ROG Strix Z690-E – High-end motherboard for Intel 12th Gen CPUs, packed with gaming features.
MSI MAG B550 TOMAHAWK – Reliable motherboard for AMD Ryzen CPUs, offering great value for money.
Gigabyte X570 AORUS Master – High-performance motherboard for AMD builds with PCIe 4.0 support.
ASRock B450M PRO4 – Affordable motherboard for budget PC builds.
Key Components of a Motherboard:
CPU Socket
This is wherein the CPU is installed. The socket kind need to fit the specific CPU you’re the usage of.
RAM Slots
These slots are where the computer's memory (RAM) modules are inserted.
PCI e Slots:
Used to connect expansion cards like photos cards (GPUs), sound playing cards, or community cards.
SATA Ports: These ports join garage gadgets like difficult drives and SSDs (Solid State Drives).
BIOS/UEFI:
The Basic Input/ Output System (BIOS) or Unified Extensible Firmware Interface (UEFI) is firmware that allows initialize the hardware at some stage in the boot method.
The motherboard dictates the computer's compatibility with sure additives, inclusive of the CPU, RAM, and garage devices.
Random Access Memory (RAM)
Random Access Memory (RAM) is the computer's quick-term reminiscence. It stores data that is currently getting used or processed via the CPU, allowing short get right of entry to to that records. The more RAM a pc has, the extra applications it could run simultaneously without slowing down.
Key Features of RAM:
Capacity
Measured in gigabytes (GB), the quantity of RAM a laptop has can substantially effect performance. For instance, 8GB of RAM is taken into consideration good enough for most responsibilities, at the same time as 16GB or greater is often required for gaming, video modifying, or other aid-extensive sports.
Speed:
RAM velocity, measured in MHz (megahertz), determines how speedy statistics can be study from or written to reminiscence. Faster RAM can enhance machine responsiveness.
DDR Versions
DDR4 is the maximum commonplace kind of RAM in present day computers, with DDR5 being the subsequent generation, providing better velocity and performance.
While RAM is crucial for multitasking, it's far unstable reminiscence, that means it loses all saved records once the pc is powered off.
Storage Devices
Storage gadgets are in which all of your statistics, documents, and programs are stored. There are predominant types of storage devices: Hard Disk Drives (HDDs) and Solid State Drives (SSDs).
Hard Disk Drives (HDDs):
Mechanical Storage:
HDDs use spinning disks, or platters, to study and write records using a mechanical arm.
Capacity:
HDDs commonly provide large garage capacities at lower fees as compared to SSDs, making them best for storing huge files like films, games, or pics.
Speed:
While HDDs offer adequate garage, they are slower than SSDs due to the mechanical nature of data get entry to.
Solid State Drives (SSDs):
Flash Storage:
SSDs use NAND flash reminiscence, which allows them to access information a lot quicker than HDDs.
Speed:
SSDs drastically improve machine performance, lowering boot times and speeding up the loading of packages and documents.
Capacity and Cost: While SSDs are more high-priced in step with GB than HDDs, they've emerge as increasingly lower priced and are often used as the primary storage device for the operating system and regularly used applications.
Some computers use a combination of each, with an SSD for the working system and important applications and an HDD for bulk garage.
Graphics Processing Unit (GPU)
The Graphics Processing Unit (GPU), or video card, is responsible for rendering pix, films, and animations for display at the display. For gaming, video enhancing, and different graphically intensive responsibilities, a effective GPU is important.
Types of GPUs:
Integrated Graphics:
Many CPUs come with included photographs, that are enough for simple tasks like surfing the internet, looking films, or operating with documents. However, they're now not suitable for excessive-stop gaming or professional photo design work.
Dedicated Graphics Card:
A dedicated GPU is a separate card mounted in the computer, providing advanced performance for gaming, 3-D rendering, and video enhancing. Examples consist of NVIDIA's GeForce and AMD's Radeon series.
GPUs have their personal memory, known as VRAM (Video RAM), which helps manage photos-extensive programs greater efficiently.
Power Supply Unit (PSU)
The Power Supply Unit (PSU) converts the electrical electricity out of your wall outlet into a form that the pc can use. It distributes power to all of the components, which includes the CPU, GPU, motherboard, and storage devices.
Key Features of a PSU:
Wattage: The PSU’s wattage shows how lots electricity it can offer to the machine. It’s important to select a PSU that may supply sufficient strength for all of the components on your construct.
Efficiency Rating: The efficiency of a PSU is measured by using its eighty PLUS score, with ranges like Bronze, Silver, Gold, Platinum, and Titanium. Higher performance approach less electricity is wasted as warmness.
A right-satisfactory PSU is essential for ensuring the longevity and balance of your laptop.
Cooling System
Computers generate warmth even as working, specially during intensive responsibilities like gaming, rendering, or jogging complicated applications. To prevent overheating, a cooling gadget is important.
Types of Cooling Systems:
Air Cooling: Air coolers use fanatics to burn up warmness from the CPU and GPU. These are the most not unusual and fee-effective cooling solutions.
Liquid Cooling: Liquid cooling systems use a coolant to take in warmth from additives. They are more efficient than air cooling but also are more steeply-priced and require careful installation.
Proper cooling is essential to keep ideal performance and save you harm to touchy additives.
Input and Output Devices (I/O)
Input and output gadgets permit customers to have interaction with the pc.
Input Devices:
Keyboard and Mouse: The keyboard and mouse are the most common input gadgets, used to type instructions and navigate the gadget.
Touchscreen: Some computers, specifically drugs and a couple of-in-1 laptops, have touchscreens that allow customers to interact at once with the display.
Output Devices:
Monitor: The monitor shows the visible output from the laptop. Monitors are available in numerous resolutions and refresh charges, with 1080p, 1440p, and 4K being the most common resolutions.
Printers and Speakers: Printers provide bodily output inside the shape of files or photos, whilst speakers output sound.
Computer Case
Best budget computer components for gaming in 2024 the computer case homes all the components and protects them from dirt, debris, and harm. It also gives airflow to maintain components cool and consists of ports for connecting peripherals.
Case Types:
Full Tower: Large cases that may accommodate more than one GPUs and additional cooling systems.
Mid Tower: The most not unusual kind, supplying sufficient area for most builds.
Mini Tower: Compact instances for small form-element builds.
0 notes
Text
Gelekte key nekt integriteit Secure Boot op talloze pc’s en servers
Een perongeluk gelekte private key compromitteerde de bescherming van Secure Boot in 2022. Andere keys werden eveneens expliciet ongeschikt verklaard, maar dat weerhield OEM’s er niet van honderden systemen ermee uit te rusten. De integriteit van Secure Boot komt daardoor in het geding. Secure Boot draait op het niveau van UEFI (Unified Extensible Firmware Interface), […] http://dlvr.it/TB5k1R
0 notes
Quote
パソコンやサーバにおいて起動制御に用いられるPhoenix Technologies製のファームウェア「UEFI(Unified Extensible Firmware Interface)」に脆弱性が明らかとなった。 「CVE-2024-0762」は、「TPM(Trusted Platform Module)」を構成する変数処理のコードに明らかとなった脆弱性で、バッファオーバーフローが生じるおそれがある。脆弱性を発見、報告したEclypsiumは、「UEFIcanhazbufferoverflow」と名付けている。 Eclypsiumによれば、当初Lenovoの一部機種において脆弱性を発見したが、その後、特定のIntelプロセッサファミリにおいて実行される「Phoenix SecureCore UEFIファームウェア」に影響があることが判明したという。 具体的には「AlderLake」「CoffeeLake」「CometLake」「IceLake」「JasperLake」「KabyLake」「MeteorLake」「RaptorLake」「RocketLake」「TigerLake」などが対象となる。 ローカル環境より脆弱性を悪用すると権限の昇格が可能となり、ファームウェアにバックドアを埋め込まれると、上位レイヤーで動作するOSなどのセキュリティ対策を回避されるおそれがある。
【セキュリティ ニュース】Phoenix製「UEFI」に脆弱性 - TPM保護を回避されるおそれ(1ページ目 / 全2ページ):Security NEXT
1 note
·
View note
Text
Glupteba Botnet Evades Detection with Undocumented UEFI Bootkit
The Hacker News : The Glupteba botnet has been found to incorporate a previously undocumented Unified Extensible Firmware Interface (UEFI) bootkit feature, adding another layer of sophistication and stealth to the malware. "This bootkit can intervene and control the [operating system] boot process, enabling Glupteba to hide itself and create a stealthy persistence that can be extremely difficult to http://dlvr.it/T2hgz7 Posted by : Mohit Kumar ( Hacker )
0 notes
Text
Glupteba-Botnet umgeht Erkennung mit nicht dokumentiertem UEFI-Bootkit
Das Glupteba-Botnetz wurde mit einer zuvor nicht dokumentierten Funktion namens Unified Extensible Firmware Interface (UEFI) Bootkit entdeckt, was dem Malware einen weiteren Grad an Raffinesse und Tarnung verleiht. Das Bootkit kann den Boot-Prozess des Betriebssystems beeinflussen und kontrollieren, was es Glupteba ermöglicht, sich zu verstecken und eine heimliche Persistenz zu erzeugen, die…

View On WordPress
0 notes
Text
Video on how to Fix the Boot Failed UEFI SCSI Device on HyperV
Video on how to fix the “Boot Failed. UEFI SCSI Device” error UEFI (Unified Extensible Firmware Interface) SCSI refers to the usage of the UEFI firmware interface in conjunction with SCSI (Small Computer System Interface) technology. We shall discuss in this Video on how to Fix the Boot Failed UEFI SCSI Device on HyperV. Please see how to fix “Failed to Power on with Error ‘A virtual machine…

View On WordPress
#hyperV#HyperV VMs#Microsoft Windows#Windows#Windows 10#Windows Server#Windows Server 2016#Windows Server 2022#Windows Server 2025
0 notes
Text
UEFI bien explicado
UEFI, que significa “Interfaz de Firmware Extensible Unificada” en inglés (Unified Extensible Firmware Interface), es una interfaz de firmware estándar que reemplaza al BIOS (Sistema Básico de Entrada/Salida) en muchos sistemas modernos, especialmente en computadoras personales. UEFI proporciona una interfaz entre el sistema operativo y el firmware de la computadora durante el proceso de…

View On WordPress
1 note
·
View note
Link
0 notes
Text
Memahami BIOS dan UEFI pada Komputer PC Desktop
Pernahkah penasaran tentang apa sebenarnya BIOS dan UEFI yang sering disebut dalam dunia komputer? Sebelumnya, ketika membicarakan bagian inti dari komputer desktop, BIOS (Basic Input/Output System) adalah elemen kunci yang bertanggung jawab atas inisialisasi sistem saat dinyalakan. Namun, sekarang, BIOS mulai bergeser posisinya dan memberi jalan pada UEFI (Unified Extensible Firmware Interface),…

View On WordPress
0 notes
Text
How to Access BIOS on Windows 11

How to Access BIOS on Windows 11 -The BIOS (Basic Input/Output System) is a crucial component of your computer's hardware that provides essential information and settings to your operating system. Accessing the BIOS can be necessary when you need to make changes to hardware configurations, set up boot options, or troubleshoot certain issues. In Windows 11, the process of accessing the BIOS is slightly different from previous versions. This article will guide you through the steps to access the BIOS on your Windows 11 computer.

How to Access BIOS on Windows 11
Table of Contents
- Introduction - Restart Your Computer - Accessing BIOS during Boot - Accessing BIOS from Windows Settings - Troubleshooting: Unable to Access BIOS - Conclusion - FAQ How to Access BIOS on Windows 11 The BIOS serves as an interface between your computer's hardware and the operating system. While Windows 11 introduces a fresh and modern user interface, the method to access the BIOS remains an essential skill for users who need to make hardware-related changes.
Restart Your Computer
To access the BIOS, you'll need to restart your computer. Ensure you've saved any ongoing work before proceeding.
Accessing BIOS during Boot
- Restart Your Computer: Click on the "Start" menu and select the power icon. Hold down the "Shift" key while clicking "Restart." - Troubleshoot Menu: Once your computer restarts, you'll be presented with the "Choose an Option" screen. Click on "Troubleshoot." - Advanced Options: In the Troubleshoot menu, select "Advanced options." - UEFI Firmware Settings: Click on "UEFI Firmware Settings." This will restart your computer and take you to the BIOS settings.
Accessing BIOS from Windows Settings
- Open Windows Settings: Click on the "Start" menu and select the gear icon (Settings). - Update & Security: In the Settings menu, click on "Update & Security." - Recovery: In the left sidebar, click on "Recovery." - Advanced Startup: Under the "Advanced startup" section, click on "Restart now." Your computer will restart into the advanced startup mode. - UEFI Firmware Settings: In the advanced startup menu, click on "Troubleshoot," then "Advanced options," and finally, "UEFI Firmware Settings." This will restart your computer and take you to the BIOS settings.
Troubleshooting: Unable to Access BIOS
If you find that you're unable to access the BIOS using the above methods, it's possible that your computer manufacturer uses a different key or method to access the BIOS. Common keys to access the BIOS include F2, F10, DEL, ESC, or a specific function key unique to your computer model. Refer to your computer's manual or the manufacturer's website for specific instructions.
Conclusion
Accessing the BIOS on Windows 11 is essential for managing hardware settings and troubleshooting. Whether you choose to access it during boot or through Windows Settings, having this knowledge empowers you to make necessary adjustments to your computer's configuration.
FAQ
What is BIOS, and why is it important?
BIOS stands for Basic Input/Output System, and it's a firmware that initializes and manages hardware components when your computer starts. It's essential for hardware configuration, system booting, and low-level functions.
Is accessing the BIOS risky?
Accessing the BIOS itself isn't risky, but making incorrect changes to settings can cause problems. It's important to know what you're doing or consult a professional if you're not sure.
Can I access the BIOS on any computer?
Most computers allow access to the BIOS, but the method may vary. Refer to your computer's manual or manufacturer's website for specific instructions.
Do I need to restart my computer to access the BIOS?
Yes, accessing the BIOS usually requires restarting your computer. Save your work before attempting to access it.
What's the difference between BIOS and UEFI?
UEFI (Unified Extensible Firmware Interface) is a modern replacement for BIOS. It provides more advanced features and a graphical interface.
Can I change any setting in the BIOS?
While you can change many settings, it's recommended to only adjust settings you're familiar with. Incorrect changes could affect your computer's performance.
How do I know which key to press to access the BIOS?
Common keys to access the BIOS include F2, F10, DEL, ESC, or a specific function key. Check your computer's manual or manufacturer's website for the correct key.
Can I reset BIOS settings to default if I mess something up?
Yes, there's usually an option to reset BIOS settings to default. This can help if you make changes that cause issues.
Is it safe to update BIOS?
BIOS updates can provide bug fixes and improvements. However, they should be done carefully following the manufacturer's instructions, as a failed update can cause problems.
What if I forget my BIOS password?
If you set a BIOS password and forget it, you might need to contact your computer's manufacturer for assistance. Some motherboards have jumper pins to reset the BIOS password. Read the full article
1 note
·
View note
Text
Power of Beta Intel Xeon Processors on IBM Cloud

Users of virtual servers appreciate, and for good reason, crave output that is consistent and high-performing across all profiles at any one time. The elimination of latency problems makes application management, as well as the running of development and test procedures, far less taxing. Because of this, we are delighted to let you know that the beta program for 4th Generation Intel Xeon Scalable processors on IBM Cloud Virtual Servers for VPC is now officially operational. Customers will have the ability to explore one of the newest microarchitectures in the market within their very own virtual private cloud at no additional cost. In addition, customers will have access to a plethora of core computing advancements, such as more memory per virtual CPU than has ever been made accessible on IBM Cloud.
Is this beta program something I should be participating in?
Excellent question. Let’s go over some of the features and options that are available to you. Your baseline would operate on IBM Cloud Virtual Servers for the Virtual Private Cloud. This is our platform that caters to developers and features rapid provisioning, high network speeds, and the highest level of software-defined resource security that IBM has to offer. Your virtual server profile families would be hosted only on 4th Generation Intel Xeon Scalable processors (8474c), which were introduced to the public for the first time on IBM Cloud Bare Metal Servers only a few short months ago.
Before enrolling in this program, it is essential to carefully assess the requirements for your workload and performance. Take a look at what’s down here. You can choose between two pre-set, NUMA-aligned profile families (depending on how many vCPU instances, how much RAM you have, and how much bandwidth you need). Instances boot using the Open Virtual Machine Format (OVMF), and they operate in the Unified Extensible Firmware Interface (UEFI) mode for increased safety:
The purpose of a balanced profile is to provide an optimal combination of performance and scalability. They come with a ratio of 1 vCPU for every 5 GiB of RAM, making them an excellent choice for workloads that are more typical.
Memory profiles are ideal for use with workloads that require a significant amount of memory, such as large-scale caching and database applications as well as in-memory analytics. They come with a memory capacity of 10 Gigabytes per Virtual CPU (vCPU) that can be computed.
A significantly consistent experience at the baseline level will be provided to you by the consistent NUMA topology that is built into each profile option. Each available profile choice also includes 32.5 gigabytes of high-performance, local storage that is based on NVMe. This allows for quick access to both temporary storage and swap space. In addition to the storage for your instances, you will be provided with DDR-5 memory DIMMs as well as PCI Gen 5 if you require faster interconnects.
If you’re interested in putting some of Intel’s newest accelerators to the test on some of your more demanding applications, you’re in luck because they’re built right into the processor:
The purpose of Intel Crypto Acceleration is to help lessen the impact of pervasive data encryption and circumvent the difficulties posed by overhead in areas such as SSL web servers, 5G networks, and virtual private networks and firewalls. You will require the most recent version of the RHEL or Ubuntu operating system. When your workloads encounter a need that is dependent on the crypto libraries, the accelerators will intelligently run and complete their work.
The Intel Advanced Matrix Extensions (Intel AMX) architecture was developed to enhance the performance of training and inference, making it ideally suited for tasks such as natural language processing, recommendation systems, and image recognition. You will be able to make use of Intel AMX by utilizing extensions from your preferred artificial intelligence frameworks, such as PyTorch and Tensorflow.
In general, we believe that this beta program offers a clever, no-cost entry point onto premium hardware for those individuals who are wanting to develop and test the performance of heavy applications as well as research performance uplifts when migrating their applications to new platforms. You will have complete access to IBM Cloud Support if you enroll in this program before the 25th of September in 2023. Registration is open till then. Following the conclusion of the beta test, your virtual server instances will require a restart in order to function properly within our production-level environment. The first of the month, October 2023, will mark the beginning of your usage-based invoicing.
Getting things rolling
Do you have an account with the IBM Cloud? You are going to need one in order to validate your participation in the beta program. After you’ve created an account, you’ll be able to join up by completing a straightforward registration form that tells us about you and the requirements of your task. You will then be “allow-listed” with location deployment access and sent an email containing an official acceptance of your application. Please get in touch with either Alise Spence or Chris Carter if you’d like to have a one-on-one conversation with one of our beta onboarding managers.
0 notes