#Using tor browser
Explore tagged Tumblr posts
Text
Summon Night: Swordcraft Story (ATLUS, 2003)
#my actual posts lol#haha what if i made a daily diary post thing like nico#..i was just thinking#today was a good day#and i thought of this song#ive been playing summon night swordcraft story a lot as of late.. though none today actually#its still on my mind though#i considered using dweller empty path's song flying through a stary sky instead.. but this is what i thought of first#i think it fits best to use it#i actually had to jump through some hoops to upload music!#cus my tumblr app is kinda old.. i cant properly upload music. i could only put a link#which isnt exactly ideal#so i tried in my web browser.. but maybe its cus i havent updated it in a while or maybe just cus its tor.. it didnt work#so i downloaded firefox and did it on there lol#now im editing it in my drafts back on the app#dont ask why im not just doing it on my computer... shes having some technical difficulties. we're working on it#but not today#...#today was pretty eventful.. even if not very productive. but ive never been a very productive person#we went and saw some light festival thing! it was rly nice.. a little simple at times but it was fun#we went and got some yummy snacks earlier too! tho ive already eaten them all hehe#and i started up animal crossing new leaf. i hadnt played it in ages! its startling how much better it is than new horizions.. imo at least#only problem is i couldnt make it the same as my island.. and i didnt remember why i named my last town#we searched for a while for some reference or somfin to name it after.. but we ended up just going with ''faraway''#cus i liked the idea of being asked where im going.. and just saying far far away#and as beth said it has a kinda fairytail vibe!#...only after i named it did i realize i accidentally named it after the town in omori. oops!#...im about to hit the tag limit. so whoevers still listening i just want u to know..#i love you. ok?#goodnight
394 notes
·
View notes
Text







FTU vanity browser & search engine userboxes by me.
#buttons#userboxes#web#browsers#search engines#startpage#ask.com#internet explorer#microsoft edge#firefox#lynx#links#tor#everyone use startpage. duckduckgo is a solid browser but it's an abysmal search engine.#stop telling people to use ddg. such a useless search engine#+
7 notes
·
View notes
Text
How to Use Tor Browser
youtube

#how to#how to use tor browser#tor browser#tor#fyi#psa#internet#free#guide#guides#education#humanrights#ausgov#politas#auspol#tasgov#taspol#australia#neoliberal capitalism#fuck neoliberals#anthony albanese#albanese government#fuck the gop#fuck the police#fuck the supreme court#fuck the patriarchy#class war#classwar#anti capitalism#antifascist
9 notes
·
View notes
Text

Tor is actually a derivative of Firefox! So if no Firefox derivatives work on your computer, neither will Tor. And if it's only the original Firefox somehow (although ngl idk what would break only Firefox and not also other browsers based on it), there are probably better Firefox derivatives to use than Tor. Icr specifics, I saw some on a post going around a few weeks ago, but you can probably look up Firefox derivatives
in b4 95% of all websites in june 2024 announce that "for security" they will only work with browsers that use manifest v3
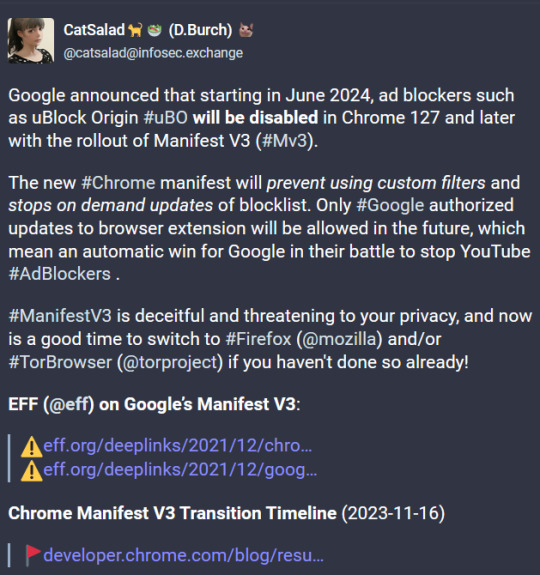
#Tor is to Firefox what Edge is to Chromium kinda#In reality there are basically two options chrome or firefox#I think I've heard of maybe one that was neither but icr what it was#If anyone knows browsers that are neither chrome nor Firefox pls let us know!
112K notes
·
View notes
Text
got ip blocked by fucking goodwill

0 notes
Text
Yeah tumblr user, you report the rainbow capitalism ad as offensive and inappropriate. On the trans-women-are-inherently-sexual website. I'm sure nothing will go wrong.
#the experience#get firefox get an adblocker and use your browser for tumblr if it bugs you that much smdh#id rather have tor publishing than fucking. Protect Yourself White Woman ads...
0 notes
Text
~
#man i wish i could set up a vpn on my ereader so i could actually use the rss.....#best i can do in the meantime is try to figure out how to set up tor on it But. but. whoever was working on this originally hasnt touched#the code since 2021 so it's a bit outdated. I'm sure i can figure out what needs to be tweaked if id just focus a little more....sigh.......#it'll be a fun day project. maybe I'll work on it for the next hour if im procrastinating anyway#so (1) get tor set up (2) set it up so tor is the default browser
1 note
·
View note
Text
I love knowing that every single college student pirates shit because the university could never come after me for this shit
#their student body would drop to 0#also I just use a tor browser so they don’t know shit#I love r/piracy
1 note
·
View note
Text
dear americans,
as a polish queer woman and human rights activist, i know exactly how you're feeling right now and what to expect from these elections. i lived through the 2015-2023 regime of pis, a right-wing populist party that divided families in the same way trump did. i’ve experienced the rise of fascism in poland, the influence of far-right parties like konfederacja, and their “santa’s little helpers”—ordo iuris, an ultra-conservative catholic organization (banned in many countries, mind you) that helped enforce a near-total abortion ban and runs anti-queer campaigns in public spaces. i supported the black protests in 2016 as a middle schooler when they first tried to ban abortion. as an adult, i actively participated in the 2020 women’s strike, running from police tear gas daily after they finally passed the ban. i supported friends who faced charges.
i’ve lived through intense homophobia in poland as a queer teen and adult. i survived the first pride march in my hometown, where far-right extremists threw stones and glass at us. i endured the anti-queer propaganda spread by the ruling party in state-owned media. i survived the “rainbow night,” poland’s own stonewall moment in summer 2020, when police arrested around 50 queer activists following the arrest of margo, a nonbinary activist. i survived the "lgbt-free zones," the targeted violence, the slurs from strangers on the street, and the protests i held against queerphobia. it was hard as fuck, but i survived.
but just because i survived, it doesn’t mean others did. many women died because of the abortion ban—marta, justyna, izabela, dorota, joanna, maria, and many others who didn’t survive pis’s draconian anti-abortion laws. milo, kacper, michał, zuzia (she was 12), wiktor, and other queer and trans kids and young adults took their own lives because of the relentless queerphobia.
despite all of this, our experience in poland can serve as a guide now. here are some tips for staying safe and how we, polish queers and women, organized under the regime:
safety first, always. if you know someone who’s had an abortion, no you don’t. if you know someone is trans, no you don’t. if you know people who help with safe abortions, no you don’t—at least not until you know it’s 100% safe to share. if you are queer or have had an abortion, only share this with people you trust fully. most importantly, not everyone has to be an activist just because they’re part of a minority. if it feels unsafe to share that you're queer, trans, etc., then don’t. it doesn’t make you any less queer.
use secure, encrypted messaging like signal for conversations on potentially risky topics, such as queerness, abortion, organizing counter-actions, protests—anything that might be used against you.
stay anonymous online. if you want to research or report something without surveillance, do not use regular internet. get a vpn (mullvad is affordable and reliable), download the tor browser (for both onion and standard links), and if you plan to whistleblow, consider using a riseup email account.
organize and build networks. community is everything now. support each other, foster independence, because your government won’t have your back. set up collectives, grassroots movements. create lists of trusted professionals—lawyers, doctors, etc.—who can offer support.
to lawyers and doctors: please consider pro-bono work. this is what got us through poland’s hardest times. your work will be needed now more than ever.
for protests or risky actions: always write a pro-bono lawyer’s number on your arm with a permanent marker.
get to know the anarchist black cross federation and other resources on safety culture: "Starting an anarchist black cross group: A guide"; Still We Rise - A resource pack for transgender and non-gender conforming people in prison; Safe OUTside the system by the Audre Lorde Project;
for safe abortion info or involvement: get familiar with womenhelpwomen.
stay radical, stay strong, stay informed: The Anarchist Library
if i forgot to (or didn't) include something, don't hesitate to reblog this post with other resources.
#kinda heartbroken i've gotta post something like this#but now my experience is needed more than ever and i AM going to share it#we are going to get through this#together#activism#anarchism#grassroots#anarchist#resources#useful#helpful#human rights#abortion#abortion rights#reproductive rights#queer#trans#transgender#lgbtq#us politics#usa#us elections#america#donald trump#kamala harris#stay safe#moira speaks
12K notes
·
View notes
Text
A few years ago I had a phase of being REALLY into digital privacy, using tor, duckduckgo, etc before suffering some burnout because I was trying to be 100% secure. So I'm by no means a expert I'm just relaying experience.
The culture of a lot of left leaning and "fandommy" sites (tumblr, twitter, etc) tends to fear/dislike (or just not know about) a lot of the IT stuff used by people into online privacy because they asscoiate it with "techbros". ESPECIALLY anything even remotely involving cryptocurrency. But if Trump is going to start censoring things and making morning after pills harder to get now might be a VERY good time for Americans to get into online privacy and how to avoid being tracked as well as avoiding censorship. Perhaps even some crypto to buy things discretly (or perhaps if ICE agents start caring about cash?) and because many activists groups also take donations in crypto. Never dealt with crypto myself but from what I know Monero was designed to be more untracable than Bitcoin. Don't know how succesfull that is though. Definetly get into privacy in general though.
I'll leave some useful links to get started. Words of advice:
Don't install a fuckton of privacy extensions on your browser, your unique combination of extensions will give your browser a unique fingerprint. Instead read up on and pick a few commonly used ones.
The BIGGEST annoyance for me was acedemic/proffesional settings because noone wants to switch over to some software they never heard off for one group project. Personally I use some normie software for exclusivly proffesional purposes with NO other information on me and do my actual browsing/leisure computer use more privatly.
https://www.privacytools.io/os: General software/browser/etc recomendations.
https://coveryourtracks.eff.org/: Test how private your browser is.
https://www.torproject.org/: THE gold standard for privacy focused browsers. Also obscures ip. Might not always be practical. Has the disadvantage of being notoriously slow and is blocked by some services/websites to avoid people bypassing ip bans and whatnot. Probably don't use this as your everyday browser but if you ever need to look up anything without censorship use tor.
https://tails.net/: Install a portable mini operating system on a usb stick to browse privately from any computer.
https://www.eff.org/ Electronic frontier foundations website.
https://mastodon.social/explore Don't have experience with it myself. But open source social media that should be much harder to censor.
Tumblr probably won't like me talking too directly about this because of ties to piracy but for people interested in banned books https://en.wikipedia.org/wiki/Shadow_library should be an interesting read...
3K notes
·
View notes
Text
A Closer Look at the Dark Web
In the vast realm of the internet, where the surface web serves as a bustling marketplace of information and commerce, there exists a hidden, mysterious underworld known as the dark web. This enigmatic space, concealed from traditional search engines, has earned a reputation for harboring both illicit activities and a haven for privacy enthusiasts. In this blog post, we’ll delve into the depths…

View On WordPress
#Cryptocurrency transactions#Cybercrime#Cybersecurity#Dark Web#Dark web myths and realities#Darknet marketplaces#Deep web exploration#Digital shadows#Encrypted communication#Ethical use of technology#Hidden Internet#Illicit online activities#Internet privacy#Internet security#Navigating the dark web#Online anonymity#Privacy online#Silk road#Tor browser#Tor Network
1 note
·
View note
Note
thoughts on using library computers to disguise your digital footprint? because if the machine gets wiped when you log out, and the library doesn't keep detailed records of what machine you were using when, then all someone else would have is IP data unconnected to a person and also mixed in with whatever else folks were doing on the library computers
The machine absolutely does not get wiped when you log out and there's very little chance that a library computer will let you fire up Tor. You're better off using a traffic anonymizer than you are trying to use public computers to cover your tracks. The IP address IS the big risk here.
Libraries are generally really good about protecting their patrons' privacy and I respect the hell out of them for that but computers log everything that you do and can be subpoenaed as evidence even if the library wants to protect user privacy.
Also, I love libraries but you should treat every public computer you come across like it has a keylogger installed on it because it might. Your city could have an overzealous city council that has more control than it should over the library board and has taken it upon themselves to add covenanteyes to the library computers. Your library crew could be fantastic but less tech-savvy than is ideal and may not realize it if malware is installed on one of the machines. The library may clear browser history twice a day but the ISP still has a record of where you went and what time you went there. Somebody could have literally plugged a keylogger into a USB port on the back of the machine.
The point of a traffic anonymizer is it hides where the traffic originated; each node knows where the previous hop came from and where the next hop went, but not what came BEFORE the previous hop or what happened after, or how long the chain was, so there is no way to tell if a message originated in the US or Brazil or Vietnam or Sweden. Sending traffic from a library does the opposite of this, and very clearly says "the person who sent this message did so from this geographic area; they sent messages from these five libraries so we know they're probably within X distance of these libraries" which is a hell of a lot easier to look for than "I can't even say what continent these messages originated from."
Let us say that you go to a library to log in to your protonmail account and email a journalist a link to a file that you've saved in cryptpad. You have the link written down so you don't have to go to a secondary site and you just go sit down directly at the computer and log in to protonmail and fire off your email to the journalist. The email is encrypted, so you know the contents of the email are safe. Let's say the browser history gets automatically wiped every time you close it, and you close it as soon as you stand up and walk away. Here's the incriminating information that generated:
IP address where you accessed your protonmail account
Your protonmail email address, the journalist's address, the time you sent the email, the subject line of the email
And here are the people who can be subpoenaed to share some or all of that information with the government:
The Library's ISP
The Library, who may not carefully track users but who do have event logs on the computers and traffic logs on the firewall
Protonmail
IF you only ever logged in to your protonmail account from that ISP one time, and if you've never logged in to your protonmail account anywhere that is close to your house or your job, you may be fine. But if you logged in to your protonmail on your personal cellphone at work so that you could send photos of documents to yourself, there's some data tying that account to a local IP address. If you set up the protonmail account on a whim at a coffee shop, there's some data tying that account to a local IP address. If you get an email back from the journalist and go to another local library to open it, there's some data tying that account to another local IP address.
And that gets narrowed down very quickly. "Who has access to these sensitive and leak-worthy documents through working at this entity who also lives within a 100 mile radius of these three login locations? Is it 50 people? Is it 5 people? Of the 15 people who have access to these sensitive and leak-worthy documents who work at this entity and live within 100 miles of the three login locations, who is likely to be doing the leaking? Do we fire them all? Do we interview them? Do we compare IP addresses that they've used to log in to work remotely and find that two of them have logged in at the coffee shop? Of those two, one has facebook selfies in a maga hat and the other has a less visible online presence. Let's check their traffic history. Did they check tumblr on a lunch break? Maybe once or twice? Maybe a few times? Sure seems like they are pretty dead-set against the administration. Let's double-check the access logs for this information. Let's review security footage. Let's install the monitoring on their workstation."
The thing is, they're not going to catch you leaking and then track down all the data you left behind to confirm it; they're going to see a leak and get a bunch of digital footprints and use that to narrow down suspect pools. They already know that access to the data is limited and will be reviewing prior access and carefully monitoring future access. You are already in their suspect pool by already being one of the people with known access to the data. Adding an IP address that is geographically close to you, even if it isn't your home IP address, to that is not going to make it *harder* to find you, it can only make it easier.
So just use Tor. You're safer using an anonymizer, which you likely can't do on a library computer. Create the leak email address when you're in a Tor browser, and only EVER access that email account from Tor.
Also I don't mean to jump on you about this, but between the post I've got about why you shouldn't use your work computer to torrent and the safer leaking practices post it's clear that people really don't understand what information they're leaving behind when they use computers and the internet, or how it can be a risk to them.
Accessing burner accounts from a clear IP address means that they're not burner accounts anymore, they're burned.
741 notes
·
View notes
Text
Kindly take a break from scrolling to read this, it's important.
Take your time to grieve and come to terms with the election results, but once you've done that, it's time to get to work. We have two months. And a lot to do in that time. We have to prepare, to be ready.
Be careful about what you post or say online. Anything potentially incriminating should be avoided. Threatening language, even if clearly a joke, can be used against you.
Know someone who's trans? Someone who's had an abortion? Someone who's LGBTQIA+? Someone who's an immigrant? Someone who attends protests? Someone who's disabled? Someone who might in any way be at risk due to laws being put into place? No you don't.
Move away from social media platforms and browsers that require you to use your real identity or input a large amount of personal information. Now's a good time to find alternate means of communicating online. Tails, Element, Tor, Mastodon, Firefox, and Lemmy are all decent options.
Find a community. Someone you can talk to, either online or in real life, that you'll have reliable contact with. We need to try and create a network, but one that's as anonymous as possible.
Start scrubbing your trail as much as possible. Get rid of old accounts that can still be traced to you but are no longer used, delete personal data off the internet. There are websites out there that will freely remove your data from the internet, but be careful about which one you use, make sure it's safe and legitimate first.
Change any usernames that you can that contain any personal information. Names, birthdays, anything.
Plan B has a four year shelf life. Stock up, but don't take more than you you'll need. We don't want a COVID repeat where everyone buys an excessive amount of things and leaves none for everybody else.
There are doctors that will sterilize you, if that's the way you want to go.
Stop using online period trackers right now. Delete all data from it if possible first, then delete the app itself. If you must, write it down, but in a subtle manner and on something you keep at home. Don't label it, just put the dates. If you're really worried, discard older records and only keep the most recent few, and label the dates as other random events, like "go to mall" or "chicken salad for dinner this night"
Get your vaccines now.
Save money.
Archive. We have to start collecting records, media, data, books, and articles now. On racism, on fascism, on homophobia, on gender, on self-reliance, on survival, on safe travels routes, on equality, on justice, on anything that may be useful and/or censored soon. We can't let them erase it.
Collect those online resources. Bookmark them, copy files into your storage, Screenshot pages. Create a decentralized library where everyone is working to be part of a whole, storing what they can individually and sharing it between one another. Again, be careful about doing this.
Second-hand bookstores are your best friend. Books are usually very cheap in them, and they often have a decent stock. See what you can find.
When buying ANYTHING I have mentioned above, or anything else that maybe put you in danger, try to use cash to reduce your spending trail.
Check your car information online, many newer models can be remotely tracked.
Turn your phone completely off if you may be at risk due to your location and current activities. Turning off your GPS also helps.
Take note of where you are. Who are your friends? Who's a safe person? Where can you go besides your own home that you know you'll be safe? Establish these connections now.
Who around you is not safe? Who and where do you need to avoid? Do you need to move? If you cannot afford moving but need to, there are fundraisers that can help you. If even that is not an option, at least try to make sure your home is secure. Have someone who can help you. Have a fallback safe place.
And finally, I want anyone with resources to put them in the replies. Flood it with useful links, information, tips, anything. We're in this together. Do not panic. Organize.
EDIT: Please be civil in the replies.
#us politics#punk#protest#lgbtq#lgbt#lgbtqia#women rights#women's rights#online archival effort#censorship#internet censorship#internet#shtf#anonymity#safety#important#serious#presidential election#2024 presidential election#do not let them erase us#fight back#human rights#we fight
1K notes
·
View notes
Text
not to be 'that gal' but there are alternatives to chrome that aren't just chrome wearing a trench coat. safari is a big one, but only applies to people on mac or iOS, and there is also a bunch of browsers based on firefox (similarly to how there's a bunch based on chrome). i don't use them but there's a list here. most seem to have ancient looking UIs, but they do exist

download firefox
#i'm one of those safari bitches#they finally added profiles and it's made my life so much fucking easier man#the tor browser is also firefox based#but not as easy to set up because of all the networking shenanigans it needs#it frustrates me to no end that the arc browser is chrome based because that’s the only reason i won’t use it#otherwise it’s such an interesting looking browser
36K notes
·
View notes
Text
ONİONSİTES - DRAGON+

Onion sites, also known as Tor sites, are a unique type of website that can only be accessed through the Tor network. The term "onion site" specifically refers to websites that are exclusively accessible via Tor, distinguishing them from traditional websites that can be reached through standard web browsers. These sites utilize a special-use top-level domain name.onion, which designates them as anonymous onion services previously known as "hidden services". The Tor network, short for The Onion Router, is a free and open-source platform that enables users to browse the internet anonymously and access content not typically available through conventional means.
The functionality of onion sites is based on the encryption and routing protocols of the Tor network. When a user attempts to access an onion site, their connection is routed through a series of volunteer-operated servers, or nodes, to conceal their identity and location. This process helps to protect the privacy and anonymity of both the user and the site they are visiting. Onion web list offer enhanced security and privacy compared to traditional websites, making them attractive to individuals seeking to safeguard their online activities from surveillance, censorship, or tracking.
What are onion sites presents both benefits and risks for users navigating the dark web. Understanding the potential advantages and drawbacks is essential for making informed decisions about online activities. Some key points to consider include: Benefits:
- Enhanced privacy and anonymity
- Access to content not available on the clear web
- Protection against surveillance and tracking Risks:
- Exposure to illegal or harmful content
- Potential security vulnerabilities
- Increased likelihood of encountering malicious actors
By weighing these factors and exercising caution while browsing onion sites, users can leverage the unique capabilities of the Tor network while minimizing potential risks to their online security and well-being.
1K notes
·
View notes
Text
diy hrt: how to safely search & order online
BEFORE YOU DO ANYTHING ONLINE RELATING TO DIY read this <3
as many institutions seem to be already complying in advance and without resistance to gender affirming care bans (eye roll) i wanted to back into posting on here about accessing diy t.
first of all, stop using Google as your search engine. google search histories HAVE ALREADY been used in court, meaning law enforcement could request your search history and use it against you. incognito browsers do not actually give you any meaninful privacy either.
here's your mini digital security checklist:
-download TOR (aka the onion router) a free, privacy-focused browser. it's legit, it's used by many, many people for many different reasons. it has important features that help keep you more private online - their webpage has a great description of how it works.
-download a good VPN. (no VPN you've seen advertised in a youtube video will actually be good.) often they require payment, for a free one the ProtonVPN is fine. as long as you're in a country where usage of TOR is common it's less of a big deal, but still good. launch your VPN before launching TOR.
-while on TOR and your VPN, create a private email. ProtonMail is fine, there are other options if you want to look more deeply. only access this email through TOR, and create a very strong password. when you're shopping for your diy, you'll need to create an account with an email, so use this email for that and not for other things.
-get some bitcoin. it's annoying especially when that pay with paypal/bank transfer/credit card option is so easy, but it's really worth it. we go way into depth about this in the guide but the more familiar you get with using crypto for privacy, the more protected you can be when making purchases online.
the guide in our pinned post has more info including lots of places to look for different btc, mail, vpn, and other privacy services. and add on if you have other digisec checklist items!!
#digital security#diy hrt#diy testosterone#diy t#trans#transmasc#ftm#mutual aid#trans men#midwest#ftm hrt
446 notes
·
View notes