#What is Data Encryption and How Does it Work?
Explore tagged Tumblr posts
Note
thoughts on using library computers to disguise your digital footprint? because if the machine gets wiped when you log out, and the library doesn't keep detailed records of what machine you were using when, then all someone else would have is IP data unconnected to a person and also mixed in with whatever else folks were doing on the library computers
The machine absolutely does not get wiped when you log out and there's very little chance that a library computer will let you fire up Tor. You're better off using a traffic anonymizer than you are trying to use public computers to cover your tracks. The IP address IS the big risk here.
Libraries are generally really good about protecting their patrons' privacy and I respect the hell out of them for that but computers log everything that you do and can be subpoenaed as evidence even if the library wants to protect user privacy.
Also, I love libraries but you should treat every public computer you come across like it has a keylogger installed on it because it might. Your city could have an overzealous city council that has more control than it should over the library board and has taken it upon themselves to add covenanteyes to the library computers. Your library crew could be fantastic but less tech-savvy than is ideal and may not realize it if malware is installed on one of the machines. The library may clear browser history twice a day but the ISP still has a record of where you went and what time you went there. Somebody could have literally plugged a keylogger into a USB port on the back of the machine.
The point of a traffic anonymizer is it hides where the traffic originated; each node knows where the previous hop came from and where the next hop went, but not what came BEFORE the previous hop or what happened after, or how long the chain was, so there is no way to tell if a message originated in the US or Brazil or Vietnam or Sweden. Sending traffic from a library does the opposite of this, and very clearly says "the person who sent this message did so from this geographic area; they sent messages from these five libraries so we know they're probably within X distance of these libraries" which is a hell of a lot easier to look for than "I can't even say what continent these messages originated from."
Let us say that you go to a library to log in to your protonmail account and email a journalist a link to a file that you've saved in cryptpad. You have the link written down so you don't have to go to a secondary site and you just go sit down directly at the computer and log in to protonmail and fire off your email to the journalist. The email is encrypted, so you know the contents of the email are safe. Let's say the browser history gets automatically wiped every time you close it, and you close it as soon as you stand up and walk away. Here's the incriminating information that generated:
IP address where you accessed your protonmail account
Your protonmail email address, the journalist's address, the time you sent the email, the subject line of the email
And here are the people who can be subpoenaed to share some or all of that information with the government:
The Library's ISP
The Library, who may not carefully track users but who do have event logs on the computers and traffic logs on the firewall
Protonmail
IF you only ever logged in to your protonmail account from that ISP one time, and if you've never logged in to your protonmail account anywhere that is close to your house or your job, you may be fine. But if you logged in to your protonmail on your personal cellphone at work so that you could send photos of documents to yourself, there's some data tying that account to a local IP address. If you set up the protonmail account on a whim at a coffee shop, there's some data tying that account to a local IP address. If you get an email back from the journalist and go to another local library to open it, there's some data tying that account to another local IP address.
And that gets narrowed down very quickly. "Who has access to these sensitive and leak-worthy documents through working at this entity who also lives within a 100 mile radius of these three login locations? Is it 50 people? Is it 5 people? Of the 15 people who have access to these sensitive and leak-worthy documents who work at this entity and live within 100 miles of the three login locations, who is likely to be doing the leaking? Do we fire them all? Do we interview them? Do we compare IP addresses that they've used to log in to work remotely and find that two of them have logged in at the coffee shop? Of those two, one has facebook selfies in a maga hat and the other has a less visible online presence. Let's check their traffic history. Did they check tumblr on a lunch break? Maybe once or twice? Maybe a few times? Sure seems like they are pretty dead-set against the administration. Let's double-check the access logs for this information. Let's review security footage. Let's install the monitoring on their workstation."
The thing is, they're not going to catch you leaking and then track down all the data you left behind to confirm it; they're going to see a leak and get a bunch of digital footprints and use that to narrow down suspect pools. They already know that access to the data is limited and will be reviewing prior access and carefully monitoring future access. You are already in their suspect pool by already being one of the people with known access to the data. Adding an IP address that is geographically close to you, even if it isn't your home IP address, to that is not going to make it *harder* to find you, it can only make it easier.
So just use Tor. You're safer using an anonymizer, which you likely can't do on a library computer. Create the leak email address when you're in a Tor browser, and only EVER access that email account from Tor.
Also I don't mean to jump on you about this, but between the post I've got about why you shouldn't use your work computer to torrent and the safer leaking practices post it's clear that people really don't understand what information they're leaving behind when they use computers and the internet, or how it can be a risk to them.
Accessing burner accounts from a clear IP address means that they're not burner accounts anymore, they're burned.
742 notes
·
View notes
Note
Hello, I had an idea for fic but it's a bit different to what you typically write so I understand if you wouldn't want to write it.
Imagine some rebels...maybe members of ghost crew intercepts some of Thrawns correspondence thinking that it's really important intel only to find it's some sweet back and forth between him and his SO.
They would be so surprised to find the big bad Grand Admiral being all cute in his messages. 👀
Interesting idea, let's see what it looks like!

⁺ . ✦ Thrawn x F!reader ✦ . ⁺
Tags: Kallus POV, pregnancy mention, Thrawn and reader are secretly married

Kallus types on the keys, eyes fixed on the screen.
Everyone is asleep in the Ghost but Kallus cannot sleep. They have been hunted mercilessly and now they are exhausted, Hera found a hideout and everyone fell face first in their pillows.
But Kallus is obsessed with a thought, something he did not have time to investigate while he was still a mole in the Empire.
He still needs to prove himself to his new rebel companions and he hopes that lead could be his ticket! Back when he was under the Empire he noticed ghost communications emanating from Grand Admiral Thrawn’s personal comms and terminals and while he found them suspicious they were not coded as orders that he needed to dig for the rebellion.
But now those communications shine in a very suspect light and he wants to get to the bottom of it.
He is no master hacker and Thrawn evidently changed all the codes of his ship to prevent Kallus from recovering them now that he is a rebel, but Thrawn cannot decide how to modify such encryptions, it obeys a very specific bureaucratic imperial logic.
Logic Kallus grew accostumed to.
For 4 weeks he tried to break the code, spending sleepless nights on this forsaken screen destroying his eyes in the dark and tonight he finally got it!
This is a one-time thing, knowing Thrawn as he does he will realize someone broke his security and stole his secrets.
And considering the encryptions on those communications, he will be absolutely furious and the hunt will get worse.
Kallus knows it
He enters, gathers a maximum of information, eliminates as many proofs of his presence, and runs to wake up Hera to change hideouts immediately!
He thought he would discover a one-way channel through which Thrawn transferred his plans to the Imperial palace to the Navy’s siege or even Lord Vader or the Emperor...
But he noticed those data left the Chimaera to return straight back to it...
Internal ship discussions do not use the triads to be sent and use an intranet and a computer to communicate informations. But Thrawn decided to muddy his trail by sending the data to a triad that recodes it again before sending the data back to the Chimaera.
With whom was he communicating and about what!?
He finishes typing his command and a new window pops up before his eye
A Discussion
To a certain “Ch’acah”
He never encountered that word. Is that a title? Nobody on the Chimaera is named Ch’acah.
...
What the hell...?
Ch’acah: ”How was your day, Thrawn?”
Thrawn: “Uneventful. My planning brought us to victory again and we are gaining in the rebels. Only Konstantine remains a wild card.”
Ch’acah: “Again? When will he learn that we need his cooperation for the plans to work as intended? He can’t allow himself to do what he wants like that!”
Thrawn: “I agree.”
Ch’acah: “I will try to have a word with him.”
Thrawn: “Thank you for your concern Ch’acah, but I would prefer you refrain. It will only had to your stress, and you do not need stress right now.”
Ch’acah: “I am pregnant, not dying, silly.”
Thrawn: “I prefer to be safe than sorry.”
...
Kallus blinks and reread all of that.
Pregnancy? Daring to call Thranw ‘silly’?
What did he stumble across?
He keeps reading
Thrawn: “I would never forgive myself if something happened to our baby.”
Ch’acah: “Nothing is going to happen to me or the baby, especially when I am with you on the Chimaera. I know you will do your best to protect us.”
Thrawn: “I am doing my best. Nothing will ever reach you two while I am alive, I swear it Ch’acah.”
Ch’acah: “Hihi, I know my love, I know.”
Thrawn: “I miss you daily even though we see each other every day. Hiding ourselves from the world tear my heart to pieces.”
Ch’acah: “You can reenact your marriage proposal on the bridge before everyone else if you want! <3”
Thrawn: “ (Y/n)... You know I cannot.”
Kallus almost spat out his caff
YOU?
You and... Thrawn are together? A couple? And you are pregnant?!
He remembers chatting with you from time to time and honestly praising your performance when he was still loyal to the Empire, when he turned to the rebellion he started avoiding you, judging you as a danger to his cover.
He always found you competent and intelligent, and visibly Thrawn thought the same and got seduced.
He would have never guessed Thrawn would get his heart stolen! And by you?
You were more dangerous than he first judged!
Thrawn: “If we are revealed you would become a target. The rebels and the Empire will try to get to you, to the baby, to reach me.”
Ch’acah: “I know... I was joking. Me too I would prefer to be free to hug you whenever I want...”
Thrawn: “Soon, Ch’acah, soon... When my true plans will succeed, when I know everyone in the galaxy is safe from that exterior threat, we will be together and free. I love you, ch’eo Ch’acah, more than anything.”
Ch’acah: “Me too, my love, more than anything.”
Kallus takes a minute
This is not what he expected
Not at all even
He feels like he walked in on something he should have never seen...
He never suspected that... softer... side of the Grand Admiral Thrawn.
He doesn’t know if that humanizes him in his eyes or gives him the creeps.
Thrawn is deadly and Kallus doesn’t really want to discover how he is when someone were to stand between him and you...
Between him and his baby...
Kallus thinks, does he even have it in himself to target a pregnant woman?
Would it not be what an Imperial would do? A rebel would probably have more morals than that...
Kallus contemplates the messages, the love that was hidden even to his eyes. He remembers you as a diligent and loyal officer to Thrawn and the Chiss showed respect to your person and gave a lot of consideration to your opinions on his tactics and plans in retrospect.
Now that Kallus has those informations, a lot of things click in his mind, about you and Thrawn’s behaviors in the presence of the other.
A secret couple
A hidden pregnancy
Thrawn is right about one thing, the Emperor will certainly try to get that baby, the offspring of his most prized tactician
This is literally a death sentence for you, it is only a matter of time. No rebel will even need to intervene: if Thrawn does nothing, the Emperor will get to him himself.
Kallus decides to exit the conversation
Destroys as much proof of his visit as he can
And stand up to wake up Hera and flee somewhere safe.
Thrawn will never allow such secret to spread and will do his best to hunt the intruder until he slits his throat
But somehow
For some reason
Kallus sympathizes with his new enemy, he would not want to be in his position
Never.

@bluechiss @justanothersadperson93 @thrawnspetgoose @thrawnalani @twilekchiss @dance-like-russia-isnt-watching @obbicrystaleo @elise2174@davesrightshoe @holylonelyponyeatingmacaroni @princesslunamoon19 @janjtje @helrose8
#thrawn#grand admiral thrawn#mitth’raw’nuruodo#thrawn x reader#thrawn x you#thrawn x f!reader#thrawn x y/n#fanfic#vibratingskull
107 notes
·
View notes
Text
HELP STOP KOSA,CALL YOUR HOUSE REPS

With the end of the year approaching, we are expecting KOSA to be slipped into an end of the year spending bill. We cannot allow it to pass. There has been push by parents to bring KOSA back, not aware how dangerous KOSA actually is for children online. It would make it mandatory for platforms online to enforce age verification via ID, and deeming any content "inappropriate" for kids to be banned.This could range from not safe for work content, to health ressources, to climate change. It'll be up to politicians to dictate what is and isn't proper for kids,and, of course, killing encryption. Imagine the damage. Please focus on the entire leadership of the House,as well as reps generally, telling them to not bring KOSA up. Speaker Johnson must also be contacted, whos number is: (202) 225-2777 Heres a list of House reps to contact: https://docs.google.com/document/d/1IyBUe6frFGF44rJQU3TahZ5zyG3tC7jai_hPneAKlnM/edit?tab=t.0 Use the call tool to call the House : https://www.stopkosa.com/ https://www.badinternetbills.com/#kosa
Here are scripts you can use : if your rep is GOP : I am urging you to VOTE NO on KOSA, the Kid’s Online Safety Act. This is a dangerous bill that will harm children. Many news organizations have reported that this bill actively harms kids by exposing their private data to strangers under the guise of protecting them. We need to hold Big Tech accountable, but KOSA is not the solution. The bill let any state attorney general and the FTC to sue any website for “harmful” content. Do we really want blue state lawyers deciding what can and can’t be allowed online? Big Tech is already censoring us. That’s why they support KOSA. This is massive government overreach. We need a bill that actually protects children by creating better security measures instead of bringing about more censorship. Multiple experts agree this bill pushes age verification, even with the new language. KOSA hands more private data of children to third party companies, which would put them in further danger. How is this protecting children’s privacy? What parent would want their child’s private data in the hands of strangers like this? KOSA is actively putting kids in danger. Do NOT support this bill. Thank you. if your rep is DEM: I am urging you to VOTE NO on KOSA. Nearly 200 human rights and LGBT organizations total came out in an open letter opposing it. The ACLU is against it. Hundreds of thousands of Gen Z, who actually live online, are against it. We know the harms of social media, and we know this is not the solution. The new language does NOT meet any concerns brought up, in fact many organizations were ignored. Major news have reported that this bill actively harms kids. We do not want this. The rewritten bill would still allow any state attorney general, and now the FTC, to sue any website for “harmful” content. When you have Republicans calling anything LGBT “sexual exploitation” or anything about race “CRT” to successfully ban books and teachers, then they will use any justification to censor the internet. The Missouri attorney general used “mental health” successfully to ban gender-affirming care with backed up research. Suicide rates will skyrocket for marginalized youth with this bill restricting content. Multiple experts agree this bill pushes age verification, even with the new language. KOSA hands more private data of children to third party companies. Furthermore, updated language threatens encryption the same way the Earn It Act does. How is this protecting children’s privacy? KOSA actively harms kids. Do NOT support this bill. Thank you.
Tell them you'll vote for your reps if they vote no on KOSA,anything goes. But most importantly it's crucial that KOSA is not being brought at all for any vote. Also,to note, Biden supports KOSA: You could try asking your GOP rep why they would support a bill that has Biden's support,and that he could use it to his advantage somehow (we know GOP does not like Biden,so it should be utilized somehow). We need to ensure the bill doesnt pass at all.
Last but not least: COME JOIN OUR ANTI KOSA SERVER ! we organize to help fight against bad Internet bills ! https://discord.gg/pwTSXZMxnH
143 notes
·
View notes
Text
Echos of The Fallen

Chapter 3: Crimson Heist Shadow the Hedgehog x Reader Warnings: A little firting but thats it

September 30th - 7:45 AM - G.U.N. Headquarters
The remnants of the explosion still hung in the air, the scent of charred metal and burnt rubber clinging to Shadow’s uniform as he stepped into the war room. The monitors on the walls flickered with the latest updates—feeds from the wreckage site, reports from analysts trying to piece together what little information they had. The entire building seemed to hum with tension, the weight of last night’s failure pressing down on everyone inside.
Rouge was already seated at the long metal table, idly examining her nails as she waited for him. Omega stood nearby, his mechanical frame motionless save for the occasional whir of servos adjusting his position. The moment Shadow entered, Rouge glanced up, arching a perfectly sculpted brow.
“Well, well,” she mused, tilting her head. “You look like hell.”
Shadow ignored her, dropping into the chair across from her and flicking open the latest intel file. “We lost her.” His voice was clipped, edged with irritation.
“No kidding.” Rouge smirked, leaning forward. “You let a woman get the best of you. Now that’s a first.”
Shadow’s crimson eyes narrowed. “She was ten steps ahead. The explosion was a diversion, and we took the bait.” His fingers drummed against the table, betraying his frustration. “She’s not just some rogue mercenary. She knows how we operate.”
Omega’s monotone voice rumbled to life. “RECOMMENDATION: TERMINATION OF TARGET UPON IDENTIFICATION.”
Rouge scoffed. “So dramatic. We don’t even know who she really is yet. ‘Danny’s wife’ doesn’t exactly lead us anywhere.”
Shadow turned the file toward her. “She’s connected to Cipher. That’s all we need to know.”
Rouge’s expression darkened slightly at the mention of the name. “So, Cipher’s making moves again. Last time he popped up, it took half of G.U.N.’s intelligence division to track down just one of his hideouts. If she’s working with him, she’s dangerous.”
“Obviously.” Shadow’s voice was tight. “The question is why. What does Cipher want with G.U.N.’s classified weapons project?”
Rouge shrugged, leaning back in her chair. “Power? Leverage? Or maybe he’s just bored. But something tells me your little rooftop admirer is more than just an errand girl.”
Shadow frowned. “What do you mean?”
Rouge’s smirk returned, playful and knowing. “She could’ve killed you last night, but she didn’t.”
Shadow remained silent, his jaw tightening. He had considered that already. The explosion had been designed to wound, to scatter forces, not to kill. If she had truly wanted him dead, she wouldn’t have left it to chance.
Omega interrupted the thought. “QUERY: NEXT COURSE OF ACTION?”
Shadow pushed the file toward the center of the table. “We find her. We stop her. No more games.”
September 30th - 10:12 PM - Underground Safehouse
The glow of multiple monitors bathed the dimly lit room in a soft blue hue, casting flickering shadows against the exposed concrete walls. The safehouse was tucked beneath the remnants of an abandoned subway station, far from prying eyes.
I sat in front of the main screen, scanning through lines of encrypted data as Zero worked his magic on the G.U.N. servers. The room was filled with the soft clacking of keys, the occasional beeping of software processes running in the background. Scar stood near the entrance, arms crossed, her gaze flicking between me and the screens.
“G.U.N. is scrambling,” Zero announced, his fingers flying across the keyboard. “They’ve got teams sweeping the city, but they’re running in circles.”
Scar smirked. “Shadow must be pissed.”
I didn���t react, my eyes still focused on the data. “Let him be. It won’t change anything.”
Zero’s hands stilled for a moment, his brow furrowing. “Hold up... This is new.”
I leaned forward. “What?”
He pulled up a series of documents, most of them redacted, but one detail stood out. A shipment manifest. Destination: G.U.N. Research Facility - Grid Sector Seven. Contents: Prototype X-09.
Scar whistled lowly. “Well, that sounds interesting.”
I exhaled slowly, my mind racing. “That’s what Carson was talking about.”
Zero nodded. “Whatever X-09 is, they’re keeping it locked down tight. I can't seem to find information on it. If G.U.N. wants it then that just makes it automatically bad.”
I tapped my fingers against my arm, calculating the next steps. “Then we move first. we break into the G.U.N. bank and steal some of their assets so they will be unable to fund this project anymore"
Scar raised an eyebrow. “You sure about that? If we intercept, we’ll be putting ourselves directly in Shadow’s path.”
A part of me hesitated, just for a fraction of a second. Then I pushed the thought aside. “Let him come. this time he won't know I know his turf.”
Zero cracked his knuckles, already preparing the next phase of the operation. “Then let’s get to work.”
Viper stood up, stretching her arms. "Alright, I’m grabbing food. Try not to blow anything up while I’m gone."
She slammed the door behind her, making the walls shake slightly. Nova immediately huffed, turning toward the door with an irritated glare. "Can you not? I’m working on an experiment!"
Viper’s voice called from the hallway, "Oh, I’m sorry, Princess! Didn’t mean to disrupt your evil genius time."
Nova scoffed. "At least I actually use my brain."
I rolled my eyes, shaking my head. "Guys, let’s be real. Unless you’re both on your period, let’s not bicker like this."
Nova shot me a glare, and Viper's laughter echoed from down the hall. "You wish, sweetheart!"
I smirked but turned back to the screens, my fingers hovering over the keyboard. The banter was familiar, almost comforting, but the weight of our situation pressed heavy on my mind. G.U.N. was moving fast, and we didn’t have time to waste.
Zero leaned back in his chair, exhaling sharply. "You really think we can pull this off?"
I didn’t answer right away, my eyes scanning over the shipment details. The security routes, the escort patterns—it was tight, but not impenetrable.
"We don’t have a choice," I finally said. "I do not trust them to have that weapon"
Scar crossed her arms, her gaze sharp. "And what happens when Shadow shows up?"
A beat of silence filled the room. That was the real problem. Shadow wasn’t like the grunts G.U.N. usually sent after us. He didn’t make mistakes. He didn’t let people slip through his fingers twice.
I exhaled. "Then we adapt."
The tension settled in the air, thick and unspoken. This wasn’t just another job—this was a battle waiting to happen.
The door creaked open again, and Viper strolled back in, holding a bag of takeout. "Alright, nerds, eat up. If we’re gonna risk our lives in forty-eight hours, you might as well not do it on an empty stomach."
Nova snatched the bag from her hands. "Finally, you’re useful for something."
Viper smirked. "Careful, Princess. Keep talking like that, and I might ‘accidentally’ forget your order next time."
As they bickered, I stared at the screens, the blueprint of the G.U.N. transport route flashing in front of me. This was it. The moment we made our move, there was no turning back.
I clenched my jaw, determination settling in.
We had forty-eight hours to pull off the impossible.
And failure wasn’t an option.

1:45 AM – G.U.N. Financial Holdings, Downtown
Everything had been going smoothly—too smoothly. Scar and I had just finished loading the last of the stolen assets into our bags when a sharp, high-pitched beep cut through the silence.
"Tell me that wasn’t you," Scar muttered.
I looked down at my wrist device, where a flashing red warning glowed across the screen. Silent alarm triggered.
"Shit," I hissed. "We need to move—now."
We bolted for the exit, weaving through the dimly lit corridors of the underground vault. But as we reached the stairwell, the sound of approaching footsteps echoed through the space. Heavy. Coordinated. Armed.
Scar gritted her teeth. "They’re fast."
"They’re G.U.N.," I shot back. "Of course they are."
We reached the main hall just as the security doors slammed shut behind us. A single figure stepped through the haze of flashing red lights. Black and red. Sharp crimson eyes locked onto mine.
Shadow.
Behind him, his team—Rouge and Omega—stood ready, blocking the only other exit.
"You really thought you could just waltz in and take what you wanted?" Shadow’s voice was low, measured, but there was an edge of irritation in it. "You’re getting sloppy."
Scar and I exchanged glances before moving in opposite directions. Shadow’s eyes flicked between us, assessing. Calculating.
"Take them," he ordered.
Rouge lunged for Scar while Omega charged forward, aiming straight for me. I dodged, ducking behind a pillar as his massive arm smashed through it like it was paper.
As Omega charged toward me, I tried to dodge his powerful swing again, but this time I had a better idea.
"Geez, Omega, you ever think about toning it down?" I taunted, hoping to get under his circuits. He growled in response, tightening his grip.
"NEGATIVE," Omega boomed, his voice full of pure mechanical rage. "FULL DESTRUCTION MODE ENGAGED."
I couldn’t avoid his next hit in time, so I took a deep breath, waiting for the right moment. Omega swung harder, and this time, his fist collided with a wall near Rouge, sending debris flying everywhere.
A vulnerable moment.
Before he could adjust, I whipped out a small device from my belt. With a quick motion, I slapped it onto Omega's back. The device activated with a small electric buzz, sending a surge of energy into his system, causing his circuits to short-circuit and his movements to freeze.
Omega's massive frame shuddered, and his body froze in place. The once-booming voice became erratic. "ERROR. SYSTEM MALFUNCTION..."
I gave a sly grin. "Guess I’ll have to remind you how to play nice."
I turned just in time to see Shadow coming for me. Fast. I barely managed to block his first strike, but the sheer force sent me skidding back. He was relentless, each blow more precise than the last.
He feinted left before sweeping my legs out from under me. Before I could react, I was flat on my back, Shadow pinning me down, one knee pressing into my ribs, his hand gripping my wrist.
I struggled, but he didn’t budge. "Give it up," he said. "You’re done."
My mind raced. I needed a distraction. Something to throw him off—just for a second.
I locked eyes with him, smirking. "You gonna kiss me or something, handsome?"
Shadow’s expression flickered. Just for a second. A flash of confusion.
That was all I needed.
I drove my knee into his stomach, making him grunt in surprise. Using the momentum, I twisted us around, grabbing a pair of cuffs from my belt. Before he could recover, I snapped them around his wrist and slammed the other end to a reinforced pipe. The cuffs magnetized instantly, locking him in place.
His eyes widened slightly as he tested the restraints.
I grinned. "Gotta say, I didn’t expect you to be so easy to trap."
Shadow glared at me, but there was the faintest trace of pink on his face.
Scar broke free from Rouge’s grip, sprinting toward me. "We need to go!"
I pulled a smoke bomb from my belt, slamming it against the ground. Thick clouds engulfed the room, obscuring everything.
"See you around, handsome," I teased, before grabbing Scar’s wrist and making a break for the exit.
We darted through the emergency hatch we had scoped out earlier, leaving chaos in our wake. The sound of Shadow yanking at the cuffs and Omega’s booming voice echoed behind us, but we were already gone, disappearing into the night.
2:30 AM – Warehouse Hideout
We crashed through the doors, breathless, adrenaline still surging through our veins.
Zero looked up from his laptop. "I take it things didn’t go as planned?"
Scar dropped her bag onto the table, grinning. "Oh, it went great. Got the goods, fought Shadow, and someone got a little flirty mid-fight."
I rolled my eyes, slumping into a chair. "It was a tactical distraction."
Scar snorted. "Sure it was."
Viper raised an eyebrow. "Wait—you flirted with Shadow?"
Nova nearly choked on her drink. "Hold on, back up. Shadow the Hedgehog?"
I groaned, burying my face in my hands. "I’m going to regret this later."
Scar smirked, kicking her feet up onto the table. "Maybe. But for now? Totally worth it."

3:00 AM – G.U.N. Financial Holdings, Downtown
Shadow's POV
The smoke was thick, the echoes of their escape still ringing in my ears. I yanked futilely at the cuffs, feeling the cold metal dig into my wrist. They were designed to hold even the strongest, and for once, it seemed they might have me. But I didn’t have time to waste on my restraints. I had a bigger problem on my hands.
Omega was down, his system glitching from whatever trick that woman had pulled on him. He was muttering about malfunctions as Rouge approached me, her footsteps sharp and mocking.
“Well, that was quite the show, Shadow,” she said, her voice dripping with amusement.
I narrowed my eyes at her, trying to ignore the frustration bubbling inside me. “Save it, Rouge.”
She leaned in closer, her lips curling into a playful smirk. “Not so tough when you're distracted, huh? You got all flustered with her little stunt. Was that... flirtation? You know, I’ve seen you fight harder. Looks like someone’s got a soft spot.”
I could feel my pulse spike, irritation mixing with something I couldn’t quite place. "This isn't the time for your games."
Rouge raised an eyebrow, clearly enjoying my discomfort. "Oh, I’m not joking. You practically let her tie you up. Seems like you let your guard down for something more than just the mission."
I grit my teeth, pushing back the surge of heat in my chest. “She got lucky. That’s all.”
But Rouge wasn’t done. “Sure, sure. I mean, she’s pretty good, I’ll give her that. Had to be quick thinking to get you like that.” Her eyes twinkled as she surveyed the room, her gaze shifting from me to Omega’s malfunctioning state. "But the real question is—how did she even know how to get past all the security systems? Couldn’t have been just luck."
A thought clicked into place, something I hadn’t fully processed in the heat of the moment. The woman’s movements, the way she seemed to be one step ahead, even the tech on her person—it all seemed too familiar. My mind whirred.
“Wait...” I muttered, looking toward Rouge. “She... she knew too much about our systems. She moved like someone who’d been trained to break into places like this.”
Rouge leaned against a wall, watching me. “You think she was G.U.N. trained?” she asked, raising an eyebrow, clearly amused.
“Impossible,” I muttered under my breath, but the more I thought about it, the more it made sense. Her style, her tactics—everything about her reeked of G.U.N. precision, just twisted in a way I hadn’t expected.
“I don’t know, Shadow,” Rouge said, her voice softer now, more serious. “Maybe we should start asking the right questions. Why would someone like her target a G.U.N. facility... and why are we just now seeing her face?”
I clenched my fists, the truth dawning on me. “We’re missing something. Whoever she is, she’s connected to G.U.N. in ways we don’t understand yet.”
Rouge gave me a knowing look, her smirk fading into something more thoughtful. “You think this is the beginning of something bigger?”
I nodded, my gaze shifting back to where Scar and the woman had vanished. “It’s more than just a heist. It’s personal now.”

Guys be honest im trying to find a good length for the chapters i believe this is fine but please let me know
- Caty
58 notes
·
View notes
Text
Day 16 | Diana Ravenscroft | Day 18

31 days of FF 7 Headcanons: Day 17: Legacy and Future
Today's prompt asks what kind of mark our OCs hope to leave behind, and what vision they hold for the days ahead. For Diana Ravenscroft, legacy isn’t about sentiment, remembrance, or inspiring future generations. It’s about being undeniable.
Today’s entry explores the cold ambition driving this Shinra scientist to defy both ethical boundaries and corporate limits in her pursuit of the divine. Expect morally gray science, clinical obsession, and the kind of future that doesn't involve a rocking chair or retirement unless it comes with a microscope and a screaming god.

Trigger Warnings: blood extraction, body horror, death (implied), dissection, medical experimentation, obsessive behavior, psychological detachment, torture (implied), unethical science

Diana Ravenscroft does not dream of a legacy in the traditional sense. She does not crave remembrance, adoration, or even recognition. Her vision of the future is sterile, clinical, and precise: to be the one who cracked the code of divinity at a molecular level. She wants her name etched into the footnotes of scientific history, not for vanity, but because it would mean she succeeded where others failed. Legacy, to her, is not about being loved or hated. It’s about being undeniable. If, a century from now, her data is still being dissected by minds lesser than hers, she will have achieved immortality in the only way that matters to her through her work.
To accomplish this, Diana walks a line that others fear to tread. The future she envisions is not a passive dream. It’s a mission. Every day she spends under Hojo’s mentorship (or, more accurately, side by side with him in a silent rivalry) is a calculated step forward. Her projects, particularly the experimentation on Bianca Moore, are engineered not just to meet Shinra's demands, but to surpass them. She wants to develop a blueprint for merging divine essence with human biology, and in doing so, redefine what is possible in both science and warfare.
Each failed subject, each successful splice, each horrific test is a rung on the ladder she’s climbing, one she’s willing to stain with blood to reach the top.
But Diana is no idealist. She knows that Shinra is not eternal, and neither is her position within it. That’s why her true investments lie in her private archives, encrypted backups, and falsified project files. She's already laying the foundation for a post-Shinra future, one in which she could operate independently. She will be free from board oversight, Hojo’s paranoia, or corporate leash-holders with no understanding of her vision. If the company collapses, she intends to walk away not empty-handed, but holding a legacy Shinra will regret ever letting slip through its fingers. Her loyalty has always been transactional. Once the transaction no longer serves her, she’ll burn the bridge and keep walking.
In terms of emotional legacy? There is none. Diana doesn’t believe in being remembered fondly. She has no children, no partner, and no desire to inspire the next generation. If she leaves anything behind beyond her research, it will be fear. It will be the fear among those who knew her and the awe from those who uncover her work decades later and wonder how such brilliance was allowed to flourish in such darkness. Her legacy is a challenge to anyone who dares to follow: surpass me if you can, but know the cost.
Ultimately, Diana’s future is as cold and controlled as her demeanor. She doesn’t fantasize about retirement, companionship, or peace. She envisions a lab lit by sterile lights, filled with data, samples, and the divine screaming under a microscope. She will chase understanding until her last breath, and if that understanding eludes her, she will die unsatisfied but never defeated. Because for someone like Diana Ravenscroft, the legacy is not in what she built, but in what she dared to pursue. Not many people get to challenge the gods. Fewer survive it. Diana intends to do both.

@themaradwrites @shepardstales @megandaisy9 @watermeezer
@prehistoric-creatures @creativechaosqueen @chickensarentcheap
@inkandimpressions @arrthurpendragon @projecthypocrisy @serenofroses
#31 days of headcanons#31 doh: ff#31 doh: diana ravenscroft#31 doh: day 17#fwc: ff#ff vii oc#characters: fwc#characters: fwc: ff#au: canon divergent#bardic tales#bardic-tales#headcanon: fwc: ff#By🔥⚔️#By🌸🌙#BladeAndBloom#oc: diana ravenscroft
15 notes
·
View notes
Text
Random Cog Headcanons: Memories
I'm back again with a slightly shorter yap than the last one, this time focusing on how suits process and store memories! Tried to go for the bullet point format again since my last post was pretty dense. Summary: Suits have different kinds of memories, with the two main kinds being consolidated and unconsolidated. Both serve different purposes and function in different ways, allowing suits to balance the preservation of disk space with the preservation of detailed memories deemed to be the most important.
The memories of suits are all contained in memory chips connected to a memory processor that interprets, sorts, and consolidates memories. ⠀
>> Damage to the former can result in loss of current memories, while damage to the latter can cause impairments forming new memories. ㅤ
Memories are immediately processed in a 1:1 visual form, but are quickly stripped down to the essentials and encrypted for the sake of both data security and saving valuable disk/memory space. This process is known as memory consolidation. ⠀
Due to this process, cogs often cannot 'replay' moments in their minds, especially if they're mundane. They may intuitively know what happened, when it happened, how it happened, how it made them feel, etc., but it's not like they're mentally seeing it. ⠀ㅤ
That being said, if a moment is really important to a suit, they can consciously choose to record memories and keep them in their original form. It's a sacrifice of space, but if it's something they really want to remember and be able to play back with every present detail, it might be worth it. Real wholesome potential for that, honestly. Though there's painful potential there, too. ⠀ㅤ
>> For example, some may choose to save precious moments from their wedding day, while others can’t stop mulling over a nasty breakup, unable to decide if they should just consolidate those old memories for their own good. Video evidence of workplace misconduct always makes reports stronger, too, so there’s that. ㅤ
>> Given that any process can be subject to malfunction, it may be possible under some circumstances for a memory to be unable to be consolidated by no fault of the suit themselves. This could, in theory, result in PTSD-like flashbacks when the memory is triggered (though that doesn’t mean consolidated memories cannot also be traumatic). ㅤ
Memories that have not been encrypted and consolidated can be accessed and shared between suits if desired. Typically, they are just transferred to an external device and projected in a video format, as one would a normal file. ⠀
Emotional data in unconsolidated memories is ignored when processed by normal machines, such as an office computer or projector, but can be experienced by another directly if two suits link up. ⠀ㅤ
The process of linking up is quite literal, being a wired or wireless connection established between two or more suits. Wired is most common, though some fancier suits may have some equivalent to Bluetooth. ㅤ
Because all memories start out as unconsolidated and unencrypted, it’s possible to feel another’s emotions or experiences in real time through linking up as well if that happens to be the goal. ㅤ
Linking up is considered to be very intimate, but typically non-sexual. It can occur among trusted friends or family in addition to partners. ㅤ
Linking up will not work if one or more parties does not want to participate. It is by definition two or more machines communicating with one another, with information requests going back and forth that can be easily denied at any time. ㅤ
Memory chips are physical, and are therefore subject to degradation and/or reorganization over time. Consolidated memories may lose some factual details or end up purged for space if deemed unimportant, while unconsolidated memories that are exceptionally old may begin to have a decrease in clarity or become a bit fuzzy, as if recorded on an old camera.
18 notes
·
View notes
Text
Critical Mass, Pt. 8
Speaking of having to do unpleasant things to save lives, McKay joins Cadman on the control platform following their meeting in the conference room and as he seems to be walking up from there, it is possible that the others continued their meeting while he moved on to more urgent matters. He is not too busy not to berate Cadman, however, and we may note that he is much more like "always like this" McKay than he has been in a long time, seeming to be exceptionally short and snappy with everyone working under him.


McKay: What are you doing? Cadman: I was going over the systems command logs for the past few months. McKay: Why? Cadman: I noticed a gap in one of the data stream sequences from several weeks ago. It's probably nothing but I thought it might indicate a... McKay: ...a deletion point, yes. Believe it or not, I have had some experience with these systems; more, say, than a tap-dancing explosives expert. Cadman: I was just trying to help, Rodney. McKay: Hey, here's a thought: failsafe code. Why don't you help with that?
One thing to note here is that while McKay does have very personal reasons to be wary of Cadman, to be "creeped out" by her, he also has perfectly valid reasons to suspect that she might be their mole, and the main reason for this is that she is clearly the most qualified person to do the kind of sabotage that has been done to them. This is also why he seems hypersensitive to Cadman doing things of her own initiative rather than just doing what he has instructed her to do. McKay is literally expecting the whole city, possibly the entire planet, to blow up in the near future, so he simply does not have time to hold her hand through her work experience programme here regardless of how much Sheppard might trust her. And because McKay seems not to have caught on to the reason why Sheppard had paired Cadman off with him -- to make sure that if there was a bomb, the bomb expert would be there to save him from it -- he may even feel like Sheppard is messing with him for what ever reason. By now, he knows that "the kidding" is the man's love language.
Now, the Goa'uld hosted by Caldwell actually had accessed their database so Cadman was onto something here. But at the same time, McKay being this touchy about the logs and possible deletions therein also begs the question of whether McKay has some other reason to not want her to dig into them. Cadman says that the deletion she detected was from several weeks ago and assuming that Caldwell had still been himself during the events of The Hive (S02E11), it is doubtful this particular deletion had anything to do with the Goa'uld. We are given little indication of what it might have been but let us recall that during his quarantine in Conversion (S02E08), Sheppard had his laptop open in his room and McKay certainly seemed to know things about his condition that he should not have known given how they had not seen each other for most of the episode. McKay was also the one who had been tasked in finding Sheppard when he escaped his quarters and the pursuers had been given permission to use what ever force necessary to detain him. Here, McKay is acting shifty enough that it certainly seems as though he has personally deleted something and it is highly doubtful he had been in communication with Kavanagh, who was accused of sending encrypted messages to someone on Atlantis previously. Kavanagh's encrypted messages appear to be pure misdirection that does not seem to have any bearing on anything.

McKay: Elizabeth. Weir: Yes, Rodney? McKay: The cruisers are getting closer. I think it's time to reconnect the ZPM and cloak the city. Weir: Go ahead.
McKay's entirely normal and proportionate to their current situation meltdown over Cadman digging into the deletions is interrupted as he glances over at the screen showing the advancing of the wraith cruisers. He informs Weir, needing to obtain her permission for reconnecting the ZPM. Both times that he has been to the power core he has been there alone which makes it seem like other people are not allowed to go there more than anything. And so the city is cloaked again, just as it was at the end of The Siege (S02E01) when the subtextual narrative was likewise made to vanish from sight for a while. But the cloak thrown over the city this time is only temporary.
When Weir joins them on the control platform, McKay and Cadman have settled into a more amicable working relationship, Cadman likely working on the failsafe codes as instructed by McKay although, as misdirection, she does seem curious as to what McKay is doing on his workstation. Weir walks in behind McKay and looks at what he is doing over his shoulder and this is almost the opposite of what we have seen Sheppard do many times, which is to park himself in front of McKay so that he is able to look at him, to see his face. Many times it seems like Sheppard is much more interested in looking at McKay than at his screen -- which is also the opposite of what we saw Sheppard do in Weir's office earlier, looking at her screen and not at her. McKay sounds extremely relieved that his plan seems to be holding up so far.


Weir: How are we doing? McKay: Well, I've powered down several of the secondary systems but so far? ZPM levels are holding below overload. Huh. I think we're gonna be OK.
Seeming to have no more pressing matters to attend to Weir stays on the control platform with McKay and Cadman, and we find her watching the screen with the sensor readout showing where the wraith cruisers are in real time. Although she is standing exactly where Sheppard had been standing earlier, we may note that her body is oriented toward the screen where Sheppard had positioned himself in a way that allowed him to watch McKay as he was moving from one end of the platform to the other. There is an obvious contrast in their body language here.

McKay: They're here! Two wraith cruisers, just outside our atmosphere. Weir: So far they don't behave in a way that would indicate they're aware of us. Cadman: Rodney? McKay: What? Cadman: The city's inertial dampeners just began powering up. McKay: What?! Cadman: I-I-I'm trying to shut it down...
They keep having to play whack-a-mole with the Trust operative who seems to have anticipated all of their moves, Cadman alerting them to the fact that they had again switched between the frying pan and the fire. But before that, there is an interesting aural reference in the way McKay says "They're here!" in the exact same sing-song way as the little girl in Poltergeist.

On the one hand, this is curious because the blonde little girl might resemble either McKay's sister or McKay himself as a child. The film came out when McKay was 15 and it seems as though he and his sister have somewhat of an age difference so he might well remember his sister like this from the time that the film had come out. What is more, if we recall Letters from Pegasus (S01E17), it had been the horror film The Sixth Sense that reminded McKay of his sister, even though he had only seen the beginning of the film that deals with a child seeing a child psychiatrist and who is a suspected victim of child abuse. In Poltergeist, the little girl Carol Anne is abducted by the malevolent spirit but although she is later saved, this kind of fear and worry over his little sister might well have been McKay's experience during his teenage years. It is obvious he has seen the film.
But the thing is, even though the film features the suburban nuclear family of the Regan era, it is also almost like a deconstruction of the trope. There were several gay people involved in making the film, and what would have been the most significant to a 15 year old gay youth coming from a troubled home would have been the character played by actress Zelda Rubinstein who also featured in a whole slew of AIDS awareness informercials in the 80's.
youtube
In these ads she plays a mother who cares about her gay son, and given that McKay's parents hated each other and took it out on him, he may well have learned about gay sex and safe sex from her. She is the caring, compassionate mother he never had but definitely needed in his life. McKay reached adulthood at a very tumultuous time in gay history, and having reached his sexual maturity during the height of the AIDS epidemic would indubitably have left its mark on him. It might even be one among a whole host of reasons why he is not comfortable with Sheppard tapping alien floozies -- they don't know what kind of space herpes these women might have.
Regardless, it is interesting that the reference only requires him to sing two notes and those who know, know whereas people who do not get the reference as such are still able to follow his meaning, just divorced from the broader intertextual context.

Cadman: ...but it's requiring a code. McKay: Get out of there! It's the star drive! Look, the city, as you know, is just a giant spaceship with a star drive capable of faster than light travel, which means that it also has inertial dampeners. Weir: Yes, I know that.
McKay is laying down some exposition not just for this episode but for the finale of the series as, while they had to do it much more quickly than they had intended, it seems like the plan had always been to fly the city back to save Earth from the wraith. This is why we get not only this exposition but a reminder of the three ZPMs required to fully power the city in this episode. They were most likely meant to quest for the ZPMs using the list that Old Weir had provided for them but because they did not get renewed for a sixth season, they found the necessary ZPMs using an ass-pull at the eleventh hour, rushing the story over the finish line.
What we may note here is that while McKay is not at all comfortable touching Cadman, he also thinks nothing of removing people from his space when lives are on the line. He has good reason to forego politeness at times such as this. And again this is misdirection, Cadman just happening to be present when ever things go awry (from McKay's point of view; Cadman herself had very likely been instructed by Sheppard to keep close to McKay and so that is what she does).


McKay: One of the precursors of the star drive's power-up phase is the activation of the dampeners... which may very well affect our cloaking. Look, but that's not the worst part of it. Weir: It'll overload the ZPM. McKay: Way overload it. Weir: How soon before that happens? McKay: Thirty minutes at the most, and this city will be vapourised.
We may note again McKay's use of "Look!" here, confirming that this is something that he is bound to say in very intense situations, has likely said to Sheppard more than a few times, and Sheppard having a Pavlovian reaction of giving his full focus automatically to anyone who speaks the word to him these days makes all kinds of sense.
It seems that now they are on an actual, literal deadline. And we can now see the fear in McKay's eyes because even though he is practiced in keeping his emotions from affecting this work, he feels helpless here. Everything that he has tried to do, everything he has thought of, the Trust operative has bean one step ahead of him, and the despair is starting to take hold of him. He knows that they are all looking at him to fix this and even if he could deal with that pressure, the thought that in spite of all of his efforts he might not be able to save Sheppard is starting to fill him with dread.
Continued in Pt. 9
#stargate atlantis#john sheppard#sga#sga meta#sheppard is bi#rodney mckay#rodney is gay#mcshep#ep. critical mass#ep. the hive#ep. conversion#ep. the siege#ep. letters from pegasus
12 notes
·
View notes
Text
CrowdStrike'd and BitLocker'd
With yesterday's CrowdStrike outage. I'm sure a number of you are probably wondering "what does BitLocker have to do with any of this?" Well, it all has to do with an added layer of security many organizations use to keep data from being stolen if a computers ends up in the hands of an "unauthorized user."
To start, let me briefly explain what the CrowdStrike driver issue did and what the fix for it is.
After the update was automatically installed to computers running the CrowdStrike Falcon Sensor, a faulty driver file caused the Windows kernel on those computers to crash and display a Blue Screen of Death. How Windows typically handles a crash like this is to create a crash log file, then perform a reboot. Since this driver would launch shortly after Windows finished booting, it would cause the operating system to crash and reboot again. When two crashes have occurred in sequence, Windows will automatically boot into Recovery Mode. Hence why we say several pictures of the Recovery Mode screen across social media yesterday.

Unfortunately, this update was automatically pushed out to around 8.5 million computers across several organizations, causing widespread chaos within the matter of a few hours. And the fix for this issue had to be performed by physically accessing each computer, which required those of us working in I.T. to have to run around several facilities, locate each affected computer, and apply the fix one by one.
The short and simple of the fix is either one of two options. You can either use the Recovery Mode that Windows was already booted into to navigate to Start-Up Setting, and launch Safe Mode. Once Windows boots into Safe Mode, the technician can navigate to C:\Windows\System32\Drivers\CrowdStrike, and delete the file C00000291-*.sys. After that the computer can be rebooted as normal, and the crashing will stop.
Or the technician can open System Restore from Recovery Mode. And, assuming there is a recovery point, restore the computer back to a good known working state.
Now, this may all seem simple enough. So why were so many organizations having trouble running this fix? That all has to do with BitLocker. As an added security measure, many organizations use BitLocker on their computers to perform a full hard disk encryption. This is done so that if a computer ends up being lost or stolen, and ends up in the hands of an "unauthorized user" they will not be able to access any of the data stored on the computer without a password to log into the computer, or the computer's BitLocker recovery key.
This presented a problem when trying to restore all of these affected computers, because when either trying to launch Safe Mode or System Restore, the user would be prompted for the BitLocker recovery key.
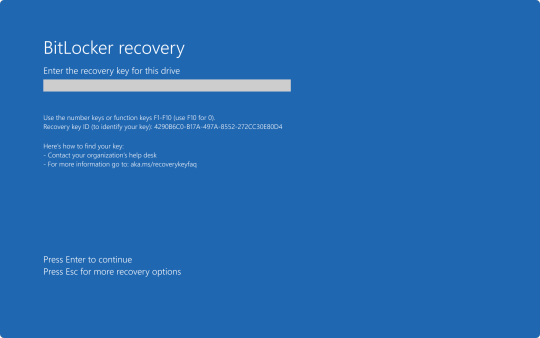
In my organization's case, we found we could save time by providing our end user the steps to perform one of the two fixes on their own to save time. But the problem we still continue to run into is the need for these BitLocker recovery keys. In my case, I've been fielding several calls where I've had end users walking from one computer to another while I provide them with the key as they walk through reverting back to a previous restore point.
Again, a pretty long story, but hopefully that can provide some context as to what's been happening over the past 48 hours.
30 notes
·
View notes
Text
Contingency Plan
I am hopeful that we will miraculously be smart enough to not allow a fascist to be elected president again.
I am hopeful that people will realize everything will be worse under Republican rule - read up on project 2025 to give you a clearer idea what that looks like. Listen to the awful rally at MSG last weekend.
I am hopeful the arrogance of the privileged that are aiming to "protest" by not voting will change their mind as they will be the reason for more blood to be shed. Not just in Palestine, but also right here. School shootings will increase. Deaths among women, be it by abuse or being forced to carry to term. Deaths among minorities.
I am hopeful, however.
But if this election turns to shit, you're going to need to understand how to stay safe - as safe as you are able.
There are many things you need to change regarding your online and offline life.
Online:
If you feel you are a target of republican policies, you'll want to purge or just simply stop posting data about yourself regarding your online presence.
selfies
pictures of your home inside or out
pictures of trips you've been on and posted online
any reference to your real name
any reference to your real home address or general area
jobs (where you work or what you do)
Privacy is REALLY important to me.
update your DNS settings, preferably on the router you use, but you can also do it on your PC, to use cloudflare dns 1.1.1.1 and 1.0.0.1 Updating the DNS to cloudflare will prevent your ISP seeing some traffic and will actually improve website response times too)
please use a VPN like NordVPN or something. There's a lot of them out there. Using a VPN will not only encrypt data, it will also hide your ip.
Use a more secure browser - Tor Browser is good for that given it goes through the onion network - but it can make websites harder to use because of how strict it is. You can use LibreWolf as an alternative which comes with pretty secure settings "right out of the box".
Use offline Password Managers (don't use or let your browser remember them). I use KeePass
Get off any app that tracks anything. This includes but not limited to period trackers, fitness trackers, anything that tracks your location and uploads it to the app developers. An app that says "We don't track your data" today does NOT mean that they won't update and start tracking you tomorrow. Be VERY wary of all app privacy policies. You will need to literally read them now. If they share your data, don't use it. Because these companies sell your data to not only advertisers but also law enforcement.
[Please take some time to search and understand the above by yourself, otherwise this will be a gargantuan post if I have to explain it all.]
Offline
You're going to have to accept that convenience is no longer possible or feasible. Everyone's situation is different and I can only recommend looking to the people you trust the most for help in any which way you can. Even crossing state boarders is dangerous for some people.
Breathe. Think it through. Ask for help.
Please also provide resources if you have any to this post so we can send it around.
14 notes
·
View notes
Note
Hi! You’re in the LA area, right? I hope you and your family are okay.
Unrelatedly, I ran across a thread on Mastodon about Proton Mail, which I think you’ve talked about before, and was curious what you make of it / how credible it is: https://code4lib.social/@[email protected]/113838748729664639
I'm fine thanks! Worried about some friends but I'm good.
I think that thread is not incorrect, but is also bullshit.
Email protocols do not allow for 100% anonymous communication and never will, when Proton was subpoenaed for user data that ended up with some French climate activists getting prosecuted they were transparent about what was requested and updated their logging rules to store less data. *Starting* from the assumption that protonmail is supposed to be totally secure OR sells itself as totally secure is disingenuous.
The great thing about open source software is that you never have to trust a shithead CEO when they talk about what the software does. I get why people are angry at the CEO (I think the CEO is at least half wrong in that he is claiming that Republicans will challenge monopolies, but he's not wrong about the destructive corporatism of the Democratic party even if he is *in essence* wrong about which party is more likely to gesture in the direction of breaking up tech monopolies) but A) the thread says that proton's software is "opaque" and it just. Literally is not. and B) that thread links to another thread talking about how what proton is selling is trust and nope. They don't have to sell trust; you can see what their software does if you choose to investigate it, there's no need for trust when you can verify. What they're selling is transparency and from where i'm standing they are indeed quite transparent.
God. Imagine thinking that a zero trust service is selling trust.
So I think the argument that "protonmail actually isn't as secure as it claims" is bullshit that people bring up whenever they're mad at the company (whether they have legitimate reasons to be mad at the company or not).
For the record: you should never, ever, EVER treat email as a secret. Nothing you do over email is really secret because *the rules that allow email to function as a service* require at least some very sensitive information to be an open part of the protocol.
The Proton page on end to end encryption is *very* clear that it is the contents of your email messages that are encrypted, not your email as a whole, and in the image they use to illustrate this the parts of your email that *cannot* be made private (sender, recipient, subject line, time sent) are shown unencrypted:

They're not subtle about letting people know this. Nor are they quiet about the fact that replies to encrypted emails are not encrypted by default.
So the thread is *technically* correct in that all the security "holes" described reflect reality, but it's correct like saying "McDonald's says that you can eat their food for every meal and you'll put on ten pounds of muscle but ACTUALLY putting on ten pounds of muscle requires a huge amount of dedication and a very careful diet and a lot of resistance exercise" - like, I guess yeah that's what you have to do to put on ten pounds of muscle but where exactly was McDonald's making that claim? Did they actually make that claim or are general statements like "I'm Lovin' It" being misinterpreted in bad faith by people on the internet who are mad at something a CEO did?
So. Like. Yeah the CEO is being a shithead, the social media team made a pretty bad fuckup by doubling down on his shitheadery, the product still works as described, AND the thread discussing all of that is deeply annoying.
So.
I think this thread actually does a great job of explaining why I've never seen a "hackers for social justice" group that has lasted. This reminds me a LOT of when someone tried to say that you shouldn't use firefox because the former CEO was a homophobe. There are a lot of deeply shitty people who have made important contributions to our tech ecosystem and if we threw the baby out with the bathwater every time Notch from Minecraft ended up being Notch from minecraft you'd lock yourself out of a lot of really important tools. And this isn't the same as "buying harry potter merch funds transphobia" because it literally doesn't; especially with open source tools you can continue using the software and cheerfully hate the CEO because A) fuck that guy and B) what the fuck are you going to do about it, guy, this shit's encrypted.
I don't want to get too deeply into a discussion about what is or is not cancel culture, but what I'm seeing in that thread (and what I see coming up every time someone brings up the "But the French Climate Activists!" thing) is an attempt to prioritize political alignment over real-world utility. It's attempting to cancel a *genuinely useful tool* because someone involved in the development is an asshole.
By all means, don't give protonmail money if the CEO's trump-positive comments make you feel unsafe.
However: What service are you going to use that is as accessible and as secure to ensure that you actually *are* safe? There are alternatives out there. Do they actually do more than proton? Are they easier to use? Are they open source? One of the responses to that thread was "yeah, that dude seems shitty; i'd switch to another service if there was another one that I felt was as secure" and that's pretty much what I think the correct attitude is. (If you really, really still want to switch, Tuta has been the broadly recommended alternative to protonmail for years but at this point Proton has a suite of services that some users would need to replace, not just email)
IDK i think shit like this contributes to a lot of the bad kind of security nihilism where people are like "oh no, things will never be secure and even my scrappy little open source product is headed by an asshole, i may as well use google because everything sucks" when they should have the good kind of nihilism which is like "man, there are a lot of assholes out there and they're never going to stop being assholes; i'd better take proactive steps to act like the people who make tech stuff are assholes and operate from a better base of security at the start"
so the takeaways are:
Proton never claimed that anything but the message contents of your e2e encrypted messages are encrypted; as far as these things go, they do a pretty good job of being both secure and easy to use compared to other offerings.
Yeah the CEO is being kind of a shithead and I'm not a huge fan of that.
If you think the CEO is being a shithead and don't want to give the company your money, don't pay for their services, but the CEO being a shithead doesn't actually mean you can't trust their services; their services are literally built on zero trust, if the CEO literally wanted to hunt you down personally he wouldn't be any more able to decrypt your emails than he was before and he wouldn't be any more likely to respond to a subpoena than he was before (proton does respond to subpoenas when required but not otherwise; they've been compelled to produce more data in the last decade than before because law enforcement finally realized who they needed to yell at - one of the bigger issues here is the Swiss courts being more willing to grant subpoenas to international complainants than they were before)
The reason we don't go see hogwarts movies is because doing so gives JK money and that does actual real world harm; using firefox does not have an impact on Brendan Eich's ability to materially change the world. It is very weird that we're in a place where we're treating *open source encryption software that is simple enough for your grandma to use it* as though it is Orson Scott Card.
Sorry i'm still stuck on people thinking that proton, famously open source, is opaque, and that an encryption service with zero trust architecture is selling trust.
Anyway if you've ever got questions about security/privacy/whatever services privacyguides.org is a very reliable source.
OH I FIGURED OUT WHAT WAS BUGGING ME
There are a bunch of people discussing this talking about how the CEO's social media is what has made them feel unsafe and I'm going to be a dick here and say that facts don't care about your feelings.
The CEO saying stupid shit doesn't actually make you unsafe in a situation like this; if the CEO was a violent transphobe or aggressive racist or horribly misogynist that wouldn't actually make any of the users of the product less safe. That's why the SJ hacker stuff I've seen hasn't had much staying power; I think that groups that focus on making people feel included and welcome and safe to be themself within the group run into really big problems when there's a conflict between people in the group FEELING unsafe because of (genuinely important in many ways) cultural signifiers like political alignment and so in order to accommodate that feeling they end up doing things (like some kinds of collaboration/accountability practices, abandoning useful tools, WAY too much personal transparency and radical vulnerability for people who are doing crime shit) that ACTUALLY make them less safe.
The CEO being a shithead may make you feel bad, but moving to a less secure platform may actually be dangerous. One of these things can have a big impact on your life, and it is not the one that is happening on twitter.
Anyway. Email is inherently insecure and if you want a secure messaging tool use Signal.
If you are doing crime shit don't talk about it on the internet and DEFINITELY don't talk about it in any kind of unencrypted platform.
If you are a French climate activist who would like to not get arrested if Tuta gets a subpoena for data, use the email service in concert with tor and be cautious about senders/receivers and subject lines.
244 notes
·
View notes
Text
Okay, so how does the bat communication system work
They could use signal but tbh. That might be to much functionality on what we would need.
Authentication is like in this case pretty trivial, because they are like 2 dozent people who can all be in the same room at some time and get their devices in person. Maybe they have some kind of rsa token for that. And also they build their own devices (again like 2 dozent or something so)
Also the serverlessness of signal is great, if you dont want your data in some server, but also again. They probably have their own servers anyway. And soemtimes the bat communication network is written like if someone is offline they just never get the message so very normal client2client would work.... I would prefer using the batservers instead however.
Anyway so the signal protocol implements perfect forward secrecy (so if the key got into attackers hands the earlier send messages are save) and perfect backwards secrecy (future messages are safe). So you would keep these parts...
Because again they are only like max 2 dozent people the major drawback of signal (it not scaling well for big group communications) this also does not apply.
Okay now to the part of the wireless communication.... We do have the problem here that most of batman canon is before 2018. After thinking a lot about that and crying a bit i decided, to make any of this work we have to make an au in which Wayne enterprises build a 5G network in gotham in the 90s. In this au 5G would be the first one someone invented, so downgrade attacks would not work.
I also asked my friend for suggestions and he said maybe Wayne Enterprises did build a totally second Network additionall to the normal Gotham wireless network with own bts for the bats. And so the bats can just use their own build protocoll (using Dragonfly and ECDH). The Batman Protocoll would use own headers so the normal bts will just ignore that, and we will encrypt the header, so the headers can not be tracked.
I know some 90s comics also said Oracle is talking to the bats per phone, but for the sake of my sanity we are ignoring that.
Anyway so what do the bats for sure not use:
Fax: many things which irl would need to be somewhat private are send over fax, because this is client2client and not saved on any servers which belong to some external company. However!!! It is also not encrypted and just sends the message on clear text. Everyone with access to the connection could just read that
Wifi (i mean. the batcave might be bigger than 50 meter radius so, maybe they can actually use it there.)
Bluetooth
SMS
like normal phone calls
27 notes
·
View notes
Text
VPNs aren't just for pirates and company data anymore
A friend complained to me that they couldn't access pr0n anymore because the government is now requiring ID to verify age where they are, and due to data leaks and privacy issues, didn't want to share their ID even though they're of legal age.
Shit like this doesn't work on the intended target. It only frustrates people who are aren't tech savvy while a lot of kids have already found their way around it because that's what kids do ¯\_(ツ)_/¯
When I talk about VPNs (virtual private networks), non-tech savvy people's eyes glaze over 😂
It sounds like complicated, unknowable magic. It's not! And you don't even have to understand it to use it!
With the government and ISPs (internet service providers) invading privacy more and more and hackers breaking in and stealing user data from companies, VPNs are becoming necessary.
Some Things a VPN Does for You:
hides your data from others
can make your internet speeds faster if your ISP does speed throttling (purposely making your speed slower)
hides what you're doing from your ISP
keeps you safer from some malware, viruses, hackers, and trackers
allows you to access things that are either restricted in your area or not available in your area (such as content in other countries)
keeps you safer when you're out in public connected to wifi
Below is a basic infographic on how VPNs work. When you access the internet, a VPN encrypts your data - making it into a secret code that can't be read by anyone else including your ISP.
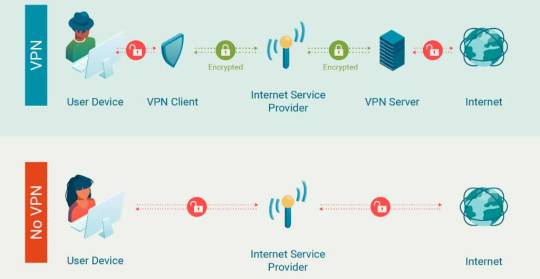
Tech companies, ISPs, etc. want you to think VPNs are complicated so that you won't use them.
When searching for a free VPN, please be aware that a lot of the free VPN services out there are malware or full of viruses and trackers.
Either do some research into which one to choose or use a paid VPN service. You can either pay monthly or yearly - the yearly is always cheaper in the long run.
Some of the Top Rated VPN Services:
ExpressVPN $7 - $13/month
NordVPN $3 - $13/month
Surfshark $2 - $14/month
PrivateInternetAccess $2 - $12/month
ProtonVPN (some sites block this one) $4 - $10/month
CyberGhost $2 - $13/month
I use ExpressVPN, so for the purposes of this post, I'm going to use screenshots from ExpressVPN.
Once you have an account, download the program from the website to your desktop/laptop or find the app on Android or iOS app stores.
Signing in requires a code that the VPN will email to you that unlocks all the features. Pay attention when the program installs because it'll ask you about preferences, and you can easily check yes on blocking pr0n when that's the reason you wanted a VPN in the first place 😂
When the program is open, you'll see this:

As you can see in the screenshot, not only do I have the program, but I have an ExpressVPN icon on my browser. The program installs this automatically, and when the program is running, the icon will have a green checkmark on it so you know it's working in your browser.
You'll notice I've recently connected using Japan. I did this so I could watch a series that isn't available outside of Japan.
The program automatically chooses a location near you, but if you want to access things that are restricted to you, make sure you click on the three dots to the right of the selected location (see screenshot below) and search for a state/country/place that your content will be available in.

Once your location is selected, click on the start/power button, and you'll get a popup notification from your computer that ExpressVPN is connected.
Go to the site you want to use and use it like you normally would.
Here's what it should look like when it's running correctly:

Keep in mind that if you leave a VPN running all the time (which is perfectly fine to do), search engines like Google will assume you live wherever ExpressVPN tells it you live, so searching for "stores near me" will give you results that aren't close to you.
When you're done using the VPN, just hit the power button again and it shuts off.
I use this on all my handheld devices, my desktop, and my laptop for business and personal reasons. I'm a pirate, and I've been using VPNs for a long time, yet none of the ISPs I've used have ever given me a warning about torrenting.
Good luck, and enjoy all the new things you can access!
BTW for anybody wondering, my desktop wallpaper is a map of the world's time zones. So pretty!! 😍
75 notes
·
View notes
Text

These people are who you know them to be. This story will begin the only way it can.
Hanagi Cheong is at work, messaging Bee on her computer. She is typing, slowly, methodically. Sometimes pausing to simply stare at the screen. Sometimes pausing to backspace and start over. No matter how she spins it, it will be clear to the violetblood she is in desperate need of someone competent in statistics. Bee’s minor Hanagi has a habit of mocking as useless. She will likely not shut up about it for a thousand sweeps. Yet this silly, caliginous worry is but a mask for a deeper, more pressing one.
[HEY] The message reads. [I’VE BEEN FUCKING, SIFTING THROUGH THE NUMBERS WE GOT FROM WHEN I DID THAT HACKING AT THE ACADEMY. ABOUT ABIDEL, AND THE INTOXICANT, AND I COULD USE A FRESH SET OF EYES TO CONFIRM YOU’RE SEEING WHAT I’M SEEING.]
The doctor's head rests on her arched hands, the husktops glow lighting up her glasses. How much exactly does she trust the violetblood progress here? She does not worry about Bee turning them into the fleet. She worries about her slipping onto this project and gripping it so tightly in manic paranoia and fear and guilt she doesn’t sleep for weeks. But how much longer can she talk to nobody about what she has found, what she has seen? Monark is not the only one susceptible to paranoia. And every time she dares venture into these files, Hanagi only finds more reasons to be afraid. Slowly, she lifts her head, and presses send.
[are you Sure?] Bee answers, a couple minutes later.
[WHY ASK ME? DO YOU THINK YOU CAN HANDLE IT?]
[i’m not always a Successful Arbitrator of what i can and Cannot handle.]
[WELL NEITHER AM I. YOU KNOW I WOULDN’T BE HERE IF I WASN’T DESPERATE.]
[am I interpreting it here correctly, that you’re coming to me with a Statistics related problem? :)<]
[HA HA HA. LIVE IT UP.]
[It’s Almost As If There Are Compelling Reasons For Someone To Minor In Such A Thing]
[DON’T TAKE THIS JUST OUT OF SPITE AND PRIDE IF YOU CAN’T HANDLE IT.]
[i can handle Math.]
[IT’S NOT JUST MATH. IT’S A LOT OF SHIT. OKAY? IT’S HORRIFYING.]
[hanagi,]
[i’ve got your back. i’ll tap out if i need. Okay?]
Hanagi pauses, and then links her to the drive where her ongoing snooping has been taking place.
.
.
.
.
.
[Hanagi.] Bee says, several hours later.
[UH OH, WHY ARE WE USING THE MORE SECURE CHANNEL?]
[when you asked me to Confirm what you were seeing in this data, what Exactly did you want me to confirm?]
[WELL, FROM MY BAREBONES CURSORY GLANCE IT REALLY SEEMED LIKE THEY SAID SHE HAD KILLED LIKE, FORTY SEVEN PSSIONICS IN THE LAST SWEEP. WHICH FELT VERY HIGH TO ME. I COULDN’T STOMACH LOOKING DEEPER]
[i don’t have Good News]
[LAY IT ON ME MISS STATISTICS.]
[i don’t know if this is complicated enough to Actually count as statistics, Doctor, more me Looking at something you didn’t want to look at, but sure]
[in ∅ ∈ KFx]
[those forty seven encrypted files are not individual patients. they are groups.]
[WHAT?]
[she killed 47 groups of four pssionics. there would be two controls and two standards in each group. after the two standards died, and she had her data, she’d make the remaining unaffected control trolls the new standard group for two new control pssionics. she repeated this process 47 times, killing a total of 98 pssionics.]
[...]
[FUCK]
[the amount of energy she’s siphoning off into those two suns. is Insane. you were right about her bullshitting her averages. whatever she’s doing to those pssionics, Really Works.]
[YOU’RE SURE?]
[that’s not even the half of it, Hanagi. can you come Home? i feel like i’m losing my mind looking at these files.]
[OF COURSE.]
.
.
.
.
.
“You should really go to bed, Hanagi,” Bee says, several hours later.
“I can’t believe you’re fucking saying that to me.” Hanagi retorts.
“How the student becomes the teacher.” The violetblood says, continuing to pin stuff on the ongoing corkboard the two of them had put up.
“I’ll be fine.”
“You have work in four hours.”
“And you don’t?”
“We’re… in over our heads.”
“You think I’ve never pulled a fucking all nighter before? I went to med school.”
“I mean we're in over our heads with this, Hanagi.” She huffs, rapping her knuckle on the board. “So The Intoxicant has, for sweeps, been synthesizing Abidel’s blood to create a dangerous addictive and incredibly powerful pssionic enhancer.”
“So?” She retorts.
“So how are we going to get Abby out?” She says. “WIthout alerting her? Without her turning up every rock in the universe to find the troll on top which this entire deranged plan centers?” Bee says, gesturing.
“A bridge we’ll cross when we get to it.”
“Why am I the voice of reason here?” She says.
“It was your plan. You’d give up so easily?”
“We’d need help to do this. A lot of it.” She answers.
“How can you just look at this shit? I’m a doctor. You’re a scientist.”
“A stretch of the definition of the word. I had a bachelors. You don’t need a job to feel empathy. I’m a person, Hanagi. Any person with a bloodpusher couldn’t stand to look at this but needs to. If I didn’t want to be here I wouldn’t be.”
“I’ll call in sick,” Hanagi says.
“Your grave” She answers. And the girls continue to work in silence.
.
.
.
.
.
“You get it too, don’t you?” Hanagi says, curled up in a ball as the sun sets, marking the early beginning of the next night. “You understand from these charts-”
“I know how close she is.” Bee answers, morosely. As much of a statistician as she ever was.
“What are you looking at?” Cheong prompts, glancing over her shoulder.
“Longse’s history with the fleet. So we know what we’re dealing with.” She replies, typing. “You know. Big picture.”
A lot of the documents of The Intoxicants rise to power are public. A career that kicked off with a long stint in the propaganda ministries, an exponential rise to head of the department. Only for her to resign at the top of her game. A grant for scientific achievement and funding, a long hundred sweeps spent in the field, where Longse would throw out new chemical and physical weapon patents every ten or so sweeps. This constant juggling of her life as a general, and a scientist, and a politician, continues for centuries. Longse seems well inclined to give others the spotlight. She has quietly been perfecting her work for a lifetime, her accomplishments becoming more impressive as the centuries pass by.
Right about 50 sweeps ago, there is a black hole in the data.
It makes sense, knowing how much about this colony's existence had been carefully kept from the public eye. Maybe they should have quit looking then. Yet, with the morbid curiosity that keeps trolls eyes on car wrecks happening on the street, the two women keep digging. Into deeply classified documents. By about 25 sweeps ago, the war on this planet had been long since over. But that doesn’t mean The Intoxicant stopped bombing it, no. The entire planet was repurposed as a massive weapons testing ground for the inventor, getting her fleet patents at an unprecedented rate, until eventually, she blew it up, six sweeps ago, beyond repair. You see, after Hascha had been discharged from the fleet for his embarrassing surrender and consequent defeat, the fleet's ruling control over Corsica had been given fully to Faeria Longse.
They are silent as they both stare at Bee’s Husktop screen. They know the name of Mondes' colony as well as any of the Cheongs. The two of them remain here for a long while, or a short while. In the end they can’t recall how long it was. The borders of minutes are blurred the less a mind has sleep. It’s even more difficult to define time when trying to understand something that feels so much bigger than it. It has started to really sink in for both of them now. The genocide of the past. The genocide of the present.
The looming chilling prophecy of the genocide of the future.
.
.
.
.
.
There is a knock at the door.
“Hanagi?” Mondes asks.
“Yeah? What? What are you doing up this late?” she calls back.
“I’m up the same time I always am.” The oliveblood says, entering the room the two shared, illuminating it with a sudden burst of hallway light. Hanagi groans, squinting, and Bee hurriedly shuts her husktop.
“Did you guys stay up all day?” He asks.
The man stands there for a second, processing what the girls have done to their room.
“...okay” He says slowly. “Just what exactly am I looking at here?”
“It’s a lot,” Hanagi manages.
“Yeah, we don’t wanna dump it on you right before class.” Bee pipes up.
“Mondes doesn’t have class.” Hanagi reminds.
“It’s summer” He retorts, folding his arms. “I’ve been out for nearly a perigee. Did you really not notice?”
“I have a full time job,” Bee says.
“Fine. I’ll give you that one. But do I really not get an explanation for this? You’re being so suspicious.”
Hanagi gestures at their asymmetric piles of paper and corkboard.
“This was ME” She defends. “ALL MY shit. And Bee told me to go to bed. I didn’t listen.”
“You both have work in thirty minutes” Mondes replies. “I’m gonna call you in so you don’t pass out midway through a fitting and put someone's leg on backwards. Or pour boiling coffee on yourself”
“Ha Ha Ha.” Hanagi complains. “Ha. Fine.”
“Go to bed” Mondes orders. “And as soon as your pans are both working again, tell me what the fuck you’re doing.” He finishes, and exits the room.
.
.
.
.
.
Two six hour naps later, Hanagi sits at the end of the kitchen tables as Bee makes her coffee across the room.
“I’m trying to think, of how to fucking say this” She exhales. The two of them continue to move through space as if in some kind of shock. Dissociative and careful.
“Okay” The rust huffs as Bee sets down a mug in front of her.
“From the beginning,” She says. “When Bee was at the fleet academy she met a limeblood there, Abidel Tevian, a pssionic amplifier who Nandor put through a lot of horrifying cybernetic augmentation to their physical body.” She pauses.
“...okay” Mondes says, his hands laying immovable at the table.
“Bee, since she was revived, has wanted to rescue them. I agreed, knowing it would be difficult and maybe risky, but not able to stand such a malpractice, terrifying misuse of prosthetics technology. So lately, I’ve been poking around Fleet files to find more information on this.”
“Okay.” Mondes repeats.
“And we kind of just found” Hanagi cuts herself off, silent for a moment before continuing.
“-something that really raises both the stakes and the difficulty of this situation.”
“Ah,” He responds
Hanagi glances at him, and then back at Bee. “Tap out.” She says, requesting Bee take over the explanation. “You know the math better.” She lies, not wanting to dive too deep into what she had seen, that all consuming sinking feeling in her chest.
“Okay.” Bee answers “Do you know the fleet general, The Intoxicant?”
Mondes blinks, momentarily, a rapid surge of emotion consuming him.
“Yes.” He says quietly.
The girls share a glance as if not sure how deep Mondes’s knowledge went, not sure how to continue. He doesn’t not elaborate. So, eventually, Bee continues.
“Okay” She says, poised like a soldier giving a report. Having more practice than Hanagi in weaponizing her detachment against her horror and grief.
“Since Abby was a grub, The Intoxicant has been synthesizing their blood to make a pssionic enhancer. An incredibly powerful one. That increases output by tenfold. It is addictive to the user, to the point the physical dependance makes their bodies degrade until death. The formula works, Longse is just attempting to make it safe past a certain threshold. She has calculated the budget of the Alternian fleet. She has calculated how much the increased energy output would benefit them financially. And how much the short life spans of pssionics would lose them money. And by way of these variables, and many more, created an …equation” Bee pauses to breathe, for just a moment.
“...An equation that can be solved to discover the ideal number of sweeps the pssionics need to last. If they live to this certain point, that's when the enhancer begins to be well worth its financial detriments, and actually starts saving the fleet a lot of money. After she reaches this point, Longse intends to patent the enhancer, and… roll it out to be used by the fleet. Something that would increase the fleets financial gain from their contest, but also increase the pace the fleet burns through pssionics dramatically. It would make their lives absolutely miserable, and more difficult to escape, due the formula’s addictive qualities, and due to the fleet being the only one that has access to Abidel, and the patent for Culucaminegic Ampheparietakinetic Pssiopote-” She narrates, with all the range of emotion of a text to speech program.
“You don’t have to say the whole fucking thing, Bee. Longse just calls it CAP in her notes.” Hanagi pitches in, bristling at her formality.
“I’m sorry.” Bee pauses, continuing to act so reservedly. “CAP’s patent” She says, “I just wanted to give you a better idea of it’s chemical makeup. Longse accomplishing this would be bad, because-”
“I don’t need to know it’s chemical makeup… But I think I understand why it’s bad.” Mondes says softly. “What are we gonna do?”
“You’re-” Hanagi stumbles. “Not gonna tell us not to do this shit?”
“Why would I tell you not to try and stop a genocide?” He says quietly.
“Okay but” Hanagi stumbles. “The fucking scale of this thing is- are we really gonna play those odds again? We were SECONDS from dying in the prison break.” She says, seeming to have become more trepidatious since getting some real sleep.
“Well,” Bee begins. Funny, how they seem to have switched places in the argument since waking. “Considering-” She continues.
“I just! I’m a fucking prosthetics doctor! I’m not a fucking, rebel mastermind. We barely scraped by. Barely.” She rambles.
“Give yourself a little credit Hanagi” Bee replies, stubbornly. “You had five nights. You made it work. Even in her most generous estimates, The Intoxicant thinks it will take few perigees for CAP to go public. You had no resources when you broke into the prison. Right now, we have money. We have access to Longse and Nandor’s files. We have connections with several talented individuals. And most importantly. We have time.”
“Says Bee Monark, the voice of reason” Hanagi retorts, bitingly.
“You said the same thing” She retorts. “Last night. Bridges we’ll cross when we get to them. But now that Mondes is in the room we’re not friends anymore?”
“Did you want me to tell you not to do it?” Mondes answers, after a pause. “Do you want me to say no, it’s totally fine if everyone in this room just forgets what they know? I won’t.”
There is a long silence. Neither Hanagi nor Bee able to think of how to respond to that. Hanagi stares at the foam of her coffee, it is probably getting cold by now. Losing herself in the intricacies of lines of the heart in bubbles. Watching them pop and fade at a snails pace.
“I don’t even know where to fucking start to try.” Hanagi says, setting down her mug, having drunk none of it. “We’d need so many things. We’d need to know a way to get to her satellite without being tracked by the fleet.”
“I can rig Mondes’s ship to be more stealthy.” Bee offers.
“Okay, but, we still gotta find the plans for the satellite, figure out how to break into it. We might need a guy on the inside, honestly! We gotta figure out how to survive the security measures. How to have alibis. How to keep this all secret after having been- in the public eye for so long!”
“Maybe we could make some kind of smoke screen.” Bee says, ever the tactician. Mondes has stood up silently, and is pacing.
“Something to distract the Alternian public and cloak our actions.” She elaborates.
Mondes has pulled a tiny paper card, long since forgotten, from a pocket in his wallet. Holding it in his hands as he paces.
“Like, start some drama with one of the other siblings or some shit?” Hanagi extrapolates.
Mondes halts suddenly.
“Okay” He says. “I’ve got it”
The other two trolls stare at him.
“What?” Bee asks.
The oliveblood sits back down. He places his old music teacher's card on the table.
“It’s probably get a lot of media attention,” He says. “If I attempted to be the first lowblood to enter a very prestigious orchestra contest, wouldn’t it?”
#EHEHEHEHEHE#and then the drabble i've been saying ill make for a year was ddone#and i was free of the curse#oh my gooddddd i cant believe I waited this long#and im still excited all the same#anyways#bee writing#hanagi writing#mondes writing#my writing#fantroll#fantroll rp#homestuck#homestuck oc#homestuck rp#genocide#<-----not fucking around#addiction
13 notes
·
View notes
Text
so, in order. left the house where the person who's ruining my life's at. came back home.
decided to stop by the post office. packages are still at the customs, whatever, it's fine, i'm back home so i'm having a grand day. come back home.
arrive to my neighbors saying i got a letter in the mail from america two hours ago. my stickers have arrived in the most a most thoroughly lovingly crafted and signed envelope ever. i open them, geek out, put them somewhere safe. also put my notebook in front of the heater so as to make sure it doesn't absorb moisture from the air.
circa 6:30. ohhh SHIT, oh SHIT, my bowie tapes have been at the post office for six days now, i'd better go pick them up! leave around 6:50, be there around 7, 7:10. "hello, i'm back, minus the luggage. can you check for another package, please?"
they have it.
i pick up the small air packet. i cannot believe it's in my hands, after two whole months of waiting. i store it in my puffer jacket so as to protect it from the rain in addition to the umbrella above me. it's a very precious package.
midway down the road, i get a call for my brother. "[REDACTED] my dearest, how are you?!" "My DEEEAREST [BROTHER]!!!!" we gush at each other for a while because we haven't spoken in so long and texts have been scarce, so as to not get me in trouble.
yesterday he mentioned having good news. i thought it might have to do with the thing that damn near destroyed my life, but nay, i dare not look forward to what i cannot see lies ahead of me. but i still hope a little bit.
i ask him if it's alright to call him when i get back home in 5-10 minutes. he says it's fine, but he'll spoil me on the best of news a little bit.
"It's got [something] to do with Android. (Cue unbeLIEVABLY large gasp from yours truly.) Nothing solved yet, but we're on a very very good path!"
i walk back home at a brisk but stiff pace (because i'm carrying my package just a taaad bit under my forearm, so i'm very stiff and a bit hunched over to prevent it from falling down my jacket), with a fuzzy head, in total disbelief and completely elated.
i enter my home, drop everything, enter my room, call up my brother. (promptly forgetting about the package, which i only notice when it softly lands on my bed from the jacket. check for damage then place it away.) i ask him to tell me about his day first like he had intended, he does. some daily bummers, but talking helps.
he then tells me the news. he, ironically, found the greatest answer at an apple service clinic. oh, the irony here is stellar - i resent iphones and other apple devices, but let's just say they're called "genius bar" for a reason. they knew exactly what me and my brother have been chasing after for months, and suggested two paths - chip-off (risky, but hella reliable if it works), and something called j-tag. brother subsequently found two people who do this - one being a british group who does chip-off but doesn't specialize in encrypted data recovery, the other being a literal counterintelligence group based in australia that does literally everything we could ask them to. currently they just need to check if they have the appropriate software for my exact phone model (a huawei make) and state the price.
i report the good news about all the packages i received today, plus the artbook i ordered. then my brother has to go eat dinner and stop by the convenience store, so we part.
i walk around the kitchen mostly on my toe tips listening to "i wonder" with my eyes closed and my arms spread out as if i'm ascending to heaven. my happy ending. finally at my doorstep. i feel like i'm about to fly up and into the ceiling.
i'm tired. i'm really tired, and it took me an hour to write this, but this is the contender for the best day in my entire life. i still can't believe that.
#logs#this is the most hopeful happiness-infused post i'll ever make on here. drink it in‚ fellas. drink it alllll in.
7 notes
·
View notes
Text
Exploring the Innovative Technologies of AMD's Ryzen Processors
Are you curious about the cutting-edge technologies behind AMD's Ryzen processors? In this in-depth article, we will delve into the innovative features that set AMD apart from the competition. From advanced AI capabilities to superior GPU performance, AMD is revolutionizing the world of computing. Let's take a closer look at what makes AMD's Ryzen processors so special.
Introduction to AMD's Ryzen Processors
AMD has been Learn more making waves in the tech industry with its Ryzen processors, which offer a powerful combination of performance and efficiency. These processors are designed to meet the demands of modern computing, whether you're a casual user or a hardcore gamer. With features like simultaneous multithreading (SMT) and precision boost technology, AMD's Ryzen processors deliver exceptional speed and responsiveness.
What Sets AMD Apart from the Competition?
When it comes to performance, AMD stands out from the competition with its Ryzen processors. Compared to other brands, AMD offers higher core counts and better multitasking capabilities. This means you can run multiple applications simultaneously without experiencing lag or slowdowns. Additionally, AMD's processors are known for their overclocking potential, allowing users to push their systems to the limit for maximum performance.
AMD's Innovations in GPU Technology
In addition to its impressive CPU performance, AMD is also a leader in GPU technology. With its Radeon graphics cards, AMD delivers stunning visuals and smooth gameplay for gamers and content creators alike. Whether you're playing the latest AAA titles or editing high-resolution videos, AMD's GPUs provide the power you need to get the job done.
The Role of AI in AMD's Ryzen Processors
AI is becoming increasingly important in modern computing, and AMD is at the forefront of this trend. By integrating AI capabilities into its Ryzen processors, AMD is able to deliver smarter and more efficient performance. From predictive algorithms that optimize power usage to voice recognition software that enhances user interaction, AI plays a crucial role in enhancing the overall user experience.
youtube
Key Features of AMD's Ryzen Processors
Let's take a closer look at some of the key features that make AMD's Ryzen processors stand out:
Simultaneous Multithreading (SMT): SMT allows each processor core to run two threads simultaneously, maximizing multitasking capabilities. Precision Boost Technology: This feature dynamically adjusts clock speeds based on workload demands, ensuring optimal performance at all times. Infinity Fabric Interconnect: The Infinity Fabric interconnect provides high-speed communication between processor cores and other components for seamless operation. Enhanced Security Features: With built-in security measures like Secure Memory Encryption and Secure Boot Support, AMD ensures that your data stays safe and protected. FAQs About Exploring the Innovative Technologies of AMD's Ryzen Processors
Q: How does AMD's precision boost technology work? A: Precision boost technology monitors workload demands in real time and adjusts clock speeds accordingly for optimal performance.

2 notes
·
View notes
Text
Exploring the Innovative Technologies of AMD's Ryzen Processors
Are you curious about the cutting-edge technologies Go to this site behind AMD's Ryzen processors? In this in-depth article, we will delve into the innovative features that set AMD apart from the competition. From advanced AI capabilities to superior GPU performance, AMD is revolutionizing the world of computing. Let's take a closer look at what makes AMD's Ryzen processors so special.
Introduction to AMD's Ryzen Processors
AMD has been making waves in the tech industry with its Ryzen processors, which offer a powerful combination of performance and efficiency. These processors are designed to meet the demands of modern computing, whether you're a casual user or a hardcore gamer. With features like simultaneous multithreading (SMT) and precision boost technology, AMD's Ryzen processors deliver exceptional speed and responsiveness.
What Sets AMD Apart from the Competition?
When it comes to performance, AMD stands out from the competition with its Ryzen processors. Compared to other brands, AMD offers higher core counts and better multitasking capabilities. This means you can run multiple applications simultaneously without experiencing lag or slowdowns. Additionally, AMD's processors are known for their overclocking potential, allowing users to push their systems to the limit for maximum performance.
AMD's Innovations in GPU Technology
In addition to its impressive CPU performance, AMD is also a leader in GPU technology. With its Radeon graphics cards, AMD delivers stunning visuals and smooth gameplay for gamers and content creators alike. Whether you're playing the latest AAA titles or editing high-resolution videos, AMD's GPUs provide the power you need to get the job done.
The Role of AI in AMD's Ryzen Processors
AI is becoming increasingly important in modern computing, and AMD is at the forefront of this trend. By integrating AI capabilities into its Ryzen processors, AMD is able to deliver smarter and more efficient performance. From predictive algorithms that optimize power usage to voice recognition software that enhances user interaction, AI plays a crucial role in enhancing the overall user experience.
Key Features of AMD's Ryzen Processors
Let's take a closer look at some of the key features that make AMD's Ryzen processors stand out:
Simultaneous Multithreading (SMT): SMT allows each processor core to run two threads simultaneously, maximizing multitasking capabilities. Precision Boost Technology: This feature dynamically adjusts clock speeds based on workload demands, ensuring optimal performance at all times. Infinity Fabric Interconnect: The Infinity Fabric interconnect provides high-speed communication between processor cores and other components for seamless operation. Enhanced Security Features: With built-in security measures like Secure Memory Encryption and Secure Boot Support, AMD ensures that your data stays safe and protected. FAQs About Exploring the Innovative Technologies of AMD's Ryzen Processors
Q: How does AMD's precision boost technology work? A: Precision boost technology monitors workload demands in real time and adjusts clock speeds accordingly for optimal performance.
youtube

2 notes
·
View notes