#Windows Active Directory
Explore tagged Tumblr posts
Text
How to change Active Directory Group Scope
How to change Active Directory Group Scope
How to Change Active Directory Group Scope Active Directory (AD) groups are essential for managing permissions and access within an organization’s IT environment. The group scope defines how permissions and memberships are applied and propagated across domains and forests. There are three types of group scopes: Universal, Global, and Domain Local. Each has its own characteristics and use cases.…
#Active Directory#Active Directory Accounts#Active Directory Users and Computers#Active Directory Users and Computers (ADUC)#Windows Active Directory#Windows Server#Windows Server 2016#Windows Server 2019#Windows Server 2022
0 notes
Text
Azure: We made server management on Windows EASY.
Linux: We have plenty of open source options for you to choose from!
Active Directory: Kill yourself
5 notes
·
View notes
Text
2 notes
·
View notes
Text
Exploring Kerberos and its related attacks
Introduction
In the world of cybersecurity, authentication is the linchpin upon which secure communications and data access rely. Kerberos, a network authentication protocol developed by MIT, has played a pivotal role in securing networks, particularly in Microsoft Windows environments. In this in-depth exploration of Kerberos, we'll delve into its technical intricacies, vulnerabilities, and the countermeasures that can help organizations safeguard their systems.
Understanding Kerberos: The Fundamentals
At its core, Kerberos is designed to provide secure authentication for users and services over a non-secure network, such as the internet. It operates on the principle of "need-to-know," ensuring that only authenticated users can access specific resources. To grasp its inner workings, let's break down Kerberos into its key components:
1. Authentication Server (AS)
The AS is the initial point of contact for authentication. When a user requests access to a service, the AS verifies their identity and issues a Ticket Granting Ticket (TGT) if authentication is successful.
2. Ticket Granting Server (TGS)
Once a user has a TGT, they can request access to various services without re-entering their credentials. The TGS validates the TGT and issues a service ticket for the requested resource.
3. Realm
A realm in Kerberos represents a security domain. It defines a specific set of users, services, and authentication servers that share a common Kerberos database.
4. Service Principal
A service principal represents a network service (e.g., a file server or email server) within the realm. Each service principal has a unique encryption key.
Vulnerabilities in Kerberos
While Kerberos is a robust authentication protocol, it is not immune to vulnerabilities and attacks. Understanding these vulnerabilities is crucial for securing a network environment that relies on Kerberos for authentication.
1. AS-REP Roasting
AS-REP Roasting is a common attack that exploits weak user account settings. When a user's pre-authentication is disabled, an attacker can request a TGT for that user without presenting a password. They can then brute-force the TGT offline to obtain the user's plaintext password.
2. Pass-the-Ticket Attacks
In a Pass-the-Ticket attack, an attacker steals a TGT or service ticket and uses it to impersonate a legitimate user or service. This attack can lead to unauthorized access and privilege escalation.
3. Golden Ticket Attacks
A Golden Ticket attack allows an attacker to forge TGTs, granting them unrestricted access to the domain. To execute this attack, the attacker needs to compromise the Key Distribution Center (KDC) long-term secret key.
4. Silver Ticket Attacks
Silver Ticket attacks target specific services or resources. Attackers create forged service tickets to access a particular resource without having the user's password.
Technical Aspects and Formulas
To gain a deeper understanding of Kerberos and its related attacks, let's delve into some of the technical aspects and cryptographic formulas that underpin the protocol:
1. Kerberos Authentication Flow
The Kerberos authentication process involves several steps, including ticket requests, encryption, and decryption. It relies on various cryptographic algorithms, such as DES, AES, and HMAC.
2. Ticket Granting Ticket (TGT) Structure
A TGT typically consists of a user's identity, the requested service, a timestamp, and other information encrypted with the TGS's secret key. The TGT structure can be expressed as:
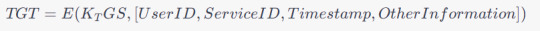
3. Encryption Keys
Kerberos relies on encryption keys generated during the authentication process. The user's password is typically used to derive these keys. The process involves key generation and hashing formulas.
Mitigating Kerberos Vulnerabilities
To protect against Kerberos-related vulnerabilities and attacks, organizations can implement several strategies and countermeasures:
1. Enforce Strong Password Policies
Strong password policies can mitigate attacks like AS-REP Roasting. Ensure that users create complex, difficult-to-guess passwords and consider enabling pre-authentication.
2. Implement Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring users to provide multiple forms of authentication. This can thwart various Kerberos attacks.
3. Regularly Rotate Encryption Keys
Frequent rotation of encryption keys can limit an attacker's ability to use stolen tickets. Implement a key rotation policy and ensure it aligns with best practices.
4. Monitor and Audit Kerberos Traffic
Continuous monitoring and auditing of Kerberos traffic can help detect and respond to suspicious activities. Utilize security information and event management (SIEM) tools for this purpose.
5. Segment and Isolate Critical Systems
Isolating sensitive systems from less-trusted parts of the network can reduce the risk of lateral movement by attackers who compromise one system.
6. Patch and Update
Regularly update and patch your Kerberos implementation to mitigate known vulnerabilities and stay ahead of emerging threats.
4. Kerberos Encryption Algorithms
Kerberos employs various encryption algorithms to protect data during authentication and ticket issuance. Common cryptographic algorithms include:
DES (Data Encryption Standard): Historically used, but now considered weak due to its susceptibility to brute-force attacks.
3DES (Triple DES): An improvement over DES, it applies the DES encryption algorithm three times to enhance security.
AES (Advanced Encryption Standard): A strong symmetric encryption algorithm, widely used in modern Kerberos implementations for better security.
HMAC (Hash-based Message Authentication Code): Used for message integrity, HMAC ensures that messages have not been tampered with during transmission.
5. Key Distribution Center (KDC)
The KDC is the heart of the Kerberos authentication system. It consists of two components: the Authentication Server (AS) and the Ticket Granting Server (TGS). The AS handles initial authentication requests and issues TGTs, while the TGS validates these TGTs and issues service tickets. This separation of functions enhances security by minimizing exposure to attack vectors.
6. Salting and Nonces
To thwart replay attacks, Kerberos employs salting and nonces (random numbers). Salting involves appending a random value to a user's password before hashing, making it more resistant to dictionary attacks. Nonces are unique values generated for each authentication request to prevent replay attacks.
Now, let's delve into further Kerberos vulnerabilities and their technical aspects:
7. Ticket-Granting Ticket (TGT) Expiry Time
By default, TGTs have a relatively long expiry time, which can be exploited by attackers if they can intercept and reuse them. Administrators should consider reducing TGT lifetimes to mitigate this risk.
8. Ticket Granting Ticket Renewal
Kerberos allows TGT renewal without re-entering the password. While convenient, this feature can be abused by attackers if they manage to capture a TGT. Limiting the number of renewals or implementing MFA for renewals can help mitigate this risk.
9. Service Principal Name (SPN) Abuse
Attackers may exploit misconfigured SPNs to impersonate legitimate services. Regularly review and audit SPNs to ensure they are correctly associated with the intended services.
10. Kerberoasting
Kerberoasting is an attack where attackers target service accounts to obtain service tickets and attempt offline brute-force attacks to recover plaintext passwords. Robust password policies and regular rotation of service account passwords can help mitigate this risk.
11. Silver Ticket and Golden Ticket Attacks
To defend against Silver and Golden Ticket attacks, it's essential to implement strong password policies, limit privileges of service accounts, and monitor for suspicious behavior, such as unusual access patterns.
12. Kerberos Constrained Delegation
Kerberos Constrained Delegation allows a service to impersonate a user to access other services. Misconfigurations can lead to security vulnerabilities, so careful planning and configuration are essential.
Mitigation strategies to counter these vulnerabilities include:
13. Shorter Ticket Lifetimes
Reducing the lifespan of TGTs and service tickets limits the window of opportunity for attackers to misuse captured tickets.
14. Regular Password Changes
Frequent password changes for service accounts and users can thwart offline attacks and reduce the impact of credential compromise.
15. Least Privilege Principle
Implement the principle of least privilege for service accounts, limiting their access only to the resources they need, and monitor for unusual access patterns.
16. Logging and Monitoring
Comprehensive logging and real-time monitoring of Kerberos traffic can help identify and respond to suspicious activities, including repeated failed authentication attempts.
Kerberos Delegation: A Technical Deep Dive
1. Understanding Delegation in Kerberos
Kerberos delegation allows a service to act on behalf of a user to access other services without requiring the user to reauthenticate for each service. This capability enhances the efficiency and usability of networked applications, particularly in complex environments where multiple services need to interact on behalf of a user.
2. Types of Kerberos Delegation
Kerberos delegation can be categorized into two main types:
Constrained Delegation: This type of delegation restricts the services a service can access on behalf of a user. It allows administrators to specify which services a given service can impersonate for the user.
Unconstrained Delegation: In contrast, unconstrained delegation grants the service full delegation rights, enabling it to access any service on behalf of the user without restrictions. Unconstrained delegation poses higher security risks and is generally discouraged.
3. How Delegation Works
Here's a step-by-step breakdown of how delegation occurs within the Kerberos authentication process:
Initial Authentication: The user logs in and obtains a Ticket Granting Ticket (TGT) from the Authentication Server (AS).
Request to Access a Delegated Service: The user requests access to a service that supports delegation.
Service Ticket Request: The user's client requests a service ticket from the Ticket Granting Server (TGS) to access the delegated service. The TGS issues a service ticket for the delegated service and includes the user's TGT encrypted with the service's secret key.
Service Access: The user presents the service ticket to the delegated service. The service decrypts the ticket using its secret key and obtains the user's TGT.
Secondary Authentication: The delegated service can then use the user's TGT to authenticate to other services on behalf of the user without the user's direct involvement. This secondary authentication occurs transparently to the user.
4. Delegation and Impersonation
Kerberos delegation can be seen as a form of impersonation. The delegated service effectively impersonates the user to access other services. This impersonation is secure because the delegated service needs to present both the user's TGT and the service ticket for the delegated service, proving it has the user's explicit permission.
5. Delegation in Multi-Tier Applications
Kerberos delegation is particularly useful in multi-tier applications, where multiple services are involved in processing a user's request. It allows a front-end service to securely delegate authentication to a back-end service on behalf of the user.
6. Protocol Extensions for Delegation
Kerberos extensions, such as Service-for-User (S4U) extensions, enable a service to request service tickets on behalf of a user without needing the user's TGT. These extensions are valuable for cases where the delegated service cannot obtain the user's TGT directly.
7. Benefits of Kerberos Delegation
Efficiency: Delegation eliminates the need for the user to repeatedly authenticate to access multiple services, improving the user experience.
Security: Delegation is secure because it relies on Kerberos authentication and requires proper configuration to work effectively.
Scalability: Delegation is well-suited for complex environments with multiple services and tiers, enhancing scalability.
In this comprehensive exploration of Kerberos, we've covered a wide array of topics, from the fundamentals of its authentication process to advanced concepts like delegation.
Kerberos, as a network authentication protocol, forms the backbone of secure communication within organizations. Its core principles include the use of tickets, encryption, and a trusted third-party Authentication Server (AS) to ensure secure client-service interactions.
Security is a paramount concern in Kerberos. The protocol employs encryption, timestamps, and mutual authentication to guarantee that only authorized users gain access to network resources. Understanding these security mechanisms is vital for maintaining robust network security.
Despite its robustness, Kerberos is not impervious to vulnerabilities. Attacks like AS-REP Roasting, Pass-the-Ticket, Golden Ticket, and Silver Ticket attacks can compromise security. Organizations must be aware of these vulnerabilities to take appropriate countermeasures.
Implementing best practices is essential for securing Kerberos-based authentication systems. These practices include enforcing strong password policies, regular key rotation, continuous monitoring, and employee training.
Delving into advanced Kerberos concepts, we explored delegation – both constrained and unconstrained. Delegation allows services to act on behalf of users, enhancing usability and efficiency in complex, multi-tiered applications. Understanding delegation and its security implications is crucial in such scenarios.
Advanced Kerberos concepts introduce additional security considerations. These include implementing fine-grained access controls, monitoring for unusual activities, and regularly analyzing logs to detect and respond to security incidents.
So to conclude, Kerberos stands as a foundational authentication protocol that plays a pivotal role in securing networked environments. It offers robust security mechanisms and advanced features like delegation to enhance usability. Staying informed about Kerberos' complexities, vulnerabilities, and best practices is essential to maintain a strong security posture in the ever-evolving landscape of cybersecurity.
12 notes
·
View notes
Text
For all the time I've spent working with active directory, which self admittedly isn't so long...about a year or two- I've come to realize- I hate Active Directory xD
Just this week I was doing WDS deployments like a noob does, and changing the computer names manually cuz of a small lil woops I did when making the image (causing me to need to change all names manually) and it turns out I now have to:
Leave the domain.
Reset.
Join the domain and rename the PC at the same time.
Reset
Boot and log into the user's profile.
Shutdown.
Deploy the PC to the work area.
Fun in IT.
2 notes
·
View notes
Text
Mastering Certificates with Microsoft Intune August 2025
I’m excited to announce that I will be delivering another edition of the Mastering Certificates with Microsoft Intune course, hosted by ViaMonstra Online Academy. This is a three-day live online training course that takes place August 26-28, 2025. This course dives deep into issuing and managing certificates using Microsoft Intune, covering both on-premises and cloud-based solutions. Course…

View On WordPress
#Active Directory Certificate Services#AD CS#authentication#certificate#certificates#Cloud PKI#CloudPKI#education#identity#InTune#learning#machine identity#masterclass#Microsoft#online training#PKI#public key infrastructure#training#ViaMonstra#ViaMonstra Online Academy#Windows
0 notes
Text
i kind of hate my job like i like helping people with their computers but sometimes i'm like can't we just shoot the computer. like with a gun
#it doesn't help that my department consists of insane people who don't know what they're doing#the dev team and my boss specifically are like. incompetent? but in a way that is just baffling#like my boss knows how to code and shit but then he doesn't follow basic IT procedures like idk replacing old equipment#like a lot of problems rn are being caused by old docking stations and the company is too cheap to buy new ones#also we don't have a computer image. like the most basic IT shit you can think of. a company image to refresh the machine#we're using windows' built-in reset feature as if we're home users it's insane#also the fact that there was no documentation for ANYTHING before i started working here#i started writing docs and my coworker who is the IT admin started writing docs and like this company is twenty years old or something#and they have no documentation and all of their shit is outdated and don't even get me started on their active directory. it's a MESS
1 note
·
View note
Text
(2024-12-16) Breaking The Glass Of Your “Get-Out-Of-Jail-For-Free” AD Account – Monitoring/Auditing It (Part 4)
In part 3 I described how to use it after having it secured as described in part 2. To make sure, the default domain administrator account is not misused, you need to monitor/audit every action against that account. This (final) part of the series will therefore focus on monitoring the “use” of the default domain administrator account and obviously any changes against it. You should obviously…

View On WordPress
#Active Directory#Auditing#breakglass account#cybersecurity#default domain administrator account#directory services protector#Disaster Recovery#Microsoft#monitoring#Security#windows
0 notes
Text
Windows Server 2025 Active Directory New Features
Windows Server 2025 Active Directory New Features @vexpert #windowsserver2025 #activedirectory #vmwarecommunities #addomain #domaincontroller #homelab #homeserver #windowsserver #windowsserversummit #windowsforest #windowsdomain
Windows Server 2025 contains many great new improvements from previous versions of Windows Server. One of the areas where we are seeing many new features and capabilities introduced is Active Directory, including a new domain functional level and forest functional level. In this post, we will take a deep dive into Windows Server 2025 new Active Directory features in the latest release. Table of…

View On WordPress
0 notes
Text
CENGİZYİLMAZ

Yeni nesil yapı ve inşaat çözümleri sunan Cengiz Yılmaz, teknolojinin sunduğu imkanlar�� iş süreçlerine entegre ederek, profesyonel hizmetler ile müşterilerine destek olmaktadır. İster veri yönetim sistemleri, ister iletişim altyapıları konusunda ihtiyaçlarınızı belirleyin; Exchange Server, Active Directory ve Windows Server çözümleri ile iş verimliliğinizi artıracak geniş bir yelpaze sunmaktayız. Ayrıca, bulut tabanlı Exchange Online hizmetimizle, esnek ve güvenli bir iletişim ortamı sağlayarak, iş gücünüzü daha verimli hale getiriyoruz. İnovasyon ve müşteri memnuniyetine odaklanan yaklaşımımızla, inşaat projelerinizi teknolojiyle buluşturarak, başarıya giden yolda yanınızdayız.
Exchange Server
Exchange Server, işletmeler için iletişim ve işbirliği süreçlerini yönetmekte kritik bir rol oynayan güçlü bir platformdur. Bu sistem, kullanıcıların e-posta gönderip almasını, takvimlerini organize etmesini ve dosya paylaşmalarını sağlar. Active Directory ile entegrasyonu sayesinde, kullanıcı yönetimi ve güvenlik politikaları çok daha verimli bir şekilde uygulanabilir.
Windows Server ile uyumluluğu, Exchange Server’ın performansını artırarak sistem kaynaklarını en iyi şekilde kullanmasına olanak tanır. Kullanıcılar, Exchange Online ile bulutta yer alan ek avantajlardan faydalanarak, her yerden kolayca erişim sağlayabilirler. Bu sayede iş süreçleri kesintisiz bir şekilde devam eder.
Gelişmiş güvenlik özellikleri, verilerinizi korurken, verimliliğinizi artırmanıza yardımcı olur. E-postalarınızı güvenli bir şekilde yönetmek ve iletişim süreçlerinizi optimize etmek için Exchange Server’ı tercih etmek, rekabet avantajı sağlar.
İşletmenizin iletişim altyapısını güçlendirmek istiyorsanız, Exchange Server çözümleri tam da ihtiyacınız olan güvenilirlik ve esnekliği sağlar. Hızla gelişen teknoloji dünyasında, modern iş ihtiyaçlarını karşılamak için Exchange Server ile adım atın.
Active Directory
Active Directory, organizasyonlar içinde kullanıcı yönetimi ve kaynakların düzenlenmesi için kritik bir yapı taşını temsil eder. Windows Server ile entegre çalışan bu sistem, kullanıcıları, grupları ve diğer nesneleri merkezi bir şekilde yönetmeyi kolaylaştırır.
Exchange Server ile birlikte kullanıldığında, Active Directory, e-posta hesaplarının ve iletişim bilgilerinin etkin bir şekilde yönetilmesine olanak tanır. Bu, kullanıcı deneyimini iyileştirir ve idari yükü hafifletir.
Ayrıca, Active Directory sayesinde güvenlik politikalarını uygulamak da son derece basit hale gelir. Örneğin, kullanıcıların hangi kaynaklara erişebileceği ve hangi izinlere sahip olacağı gibi detaylar, merkezi bir platformdan kontrol edilebilir.
Exchange Online ile birleştiğinde, bu sistem, mobil ve uzaktan çalışma ihtiyaçlarına yönelik esneklik sunar, böylece kullanıcılar herhangi bir yerden güvenli bir şekilde e-postalarına erişebilirler.
Gelişmiş özellikleri ve sağlam yapısıyla Active Directory, modern işletmelerin ihtiyaçlarını karşılamak için vazgeçilmez bir araçtır.
Windows Server
Windows Server, işletmelerin veri yönetimini, uygulama yayınlamasını ve ağ kaynaklarını güvenli bir şekilde kontrol etmesini sağlayan güçlü bir platformdur. Bu gelişmiş sunucu işletim sistemi, ağı optimize etmenin yanı sıra kullanıcılar için esneklik sunar. Özellikle, Exchange Server ve Active Directory ile entegrasyonu sayesinde, işletmeler tüm iletişim ve kimlik yönetim süreçlerini daha verimli hale getirebilirler.
Windows Server'ın sunduğu çoklu yönetim özellikleri, sistem yöneticilerine değerli zaman kazandırarak, güncellemeleri ve güvenlik taramalarını kolaylaştırır. Kullanıcı deneyimini artıran bu özellikler, güvenilir bir iş ortamı yaratırken, ağ güvenliğini de üst düzeye çıkarır. Özellikle Exchange Online ile entegrasyon, bulut tabanlı hizmetlerin kullanımını kolaylaştırarak, işletmelerin esnekliğini arttırır.
İşletmenizin ihtiyaçlarına uygun Windows Server çözümleri ile ilgili daha fazla bilgi almak ve profesyonel destek almak için web sitemizi ziyaret edin. Teknolojinizin yönetimini kolaylaştıran çözümlerimizle tanışın ve işletmenizi geleceğe taşıyacak adımları atın.
Exchange Online
Exchange Online, Microsoft'ın bulut tabanlı e-posta hizmetidir ve iş süreçlerinizi daha verimli hale getirmek için güçlü bir araçtır. Kullanıcılar, sadece bir internet bağlantısıyla e-postalarına, takvimlerine ve diğer işbirliği araçlarına her yerden erişim sağlayabilir. Bu, zaman ve mekan kısıtlamalarını ortadan kaldırarak, çalışanların üretkenliğini artırır.
Gelişmiş güvenlik özellikleri ile Exchange Online, önemli verilerinizi korumanıza yardımcı olur. Phishing ve diğer zararlı yazılımlara karşı güçlü koruma sunarak bilgi güvenliğinizin sağlanmasına katkı sağlar. Ayrıca, yerleşik veri kaybı önleme (DLP) özellikleri ile hassas bilgilere daha fazla koruma ekler.
Exchange Online, kullanıcı deneyimini en üst düzeye çıkarmak için kapsamlı bir özelleştirme sunar. Takvim paylaşımları, görev yönetimi ve ekip içinde dosya paylaşımı gibi özelliklerle, işlerinizin akışını iyileştirebilirsiniz. Aynı zamanda, diğer Microsoft 365 uygulamaları ile entegrasyon sağlayarak sorunsuz bir iş akışı yaratır. Exchange Server Active Directory Windows Server Exchange Online ile iş süreçlerinizi bulut ortamında modernize ederek, daha esnek ve verimli bir çalışma ortamı yaratmış olursunuz. Daha fazla bilgi için cengizyilmaz.net web sitemizi ziyaret edebilirsiniz.
919 notes
·
View notes
Text
Get MBAM BitLocker Recovery Keys from Microsoft SQL Server
Microsoft BitLocker Administration and Monitoring (MBAM) provides a simplified administrative interface that you can use to manage BitLocker Drive Encryption. Therefore, customers find this solution very useful for managing client PCs with BitLocker that are domain-joined on-premises. In this article, we shall discuss how to Get MBAM BitLocker Recovery Keys from Microsoft SQL Server. Please see…
#Active Directory#Active Directory BitLocker Recovery Keys#Active Directory Domain Services#Force BitLocker Recovery#MBAM#MBAM and BitLocker#MBAM for Bitlocker Administration#MBAM Help Desk#Microsoft Endpoint Configuration Manager#Microsoft SQL#Microsoft Windows#SQL#SQL Database#Windows#Windows 10#Windows 11
0 notes
Text
Father's Faults
Pairing: Tim Bradford x fem!cop!reader
Summary: Tim is distracted by his memories of his father, so you find an unprecedented way to keep him focused. After he lashes out at you for overstepping, he realizes that you understand and have your own memories to battle. Rather than bonding over that, you accept what's been between you since you first met.
Warnings: discussion of child abuse, domestic violence, Tim and r have a lot of childhood and job-related trauma, angst to fluff, confessions and kisses
Word Count: 3.8k+ words
A/N: @nevereclipse inspired this with magnificent ideas about Tim and a traumatized reader. I hope you like it!!🤍
Masterlist Directory | Tim Bradford Masterlist | Request Info

There’s a scuff in the dashboard of Tim’s shop. It’s been there for as long as you can remember, but there’s something different about it today. Tracing the ragged scrape marks with your eyes, you try to come up with a story about how it got there or an explanation for its appearance. Anything other than acknowledging the tense silence in the car or your partner's tight grip on the steering wheel.
“7-Adam-100,” dispatch radios, “there’s an active home invasion in your area.”
“7-Adam-100 responding,” Tim replies, dropping the radio after he finishes.
You don’t speak, opting to look out the window as Tim drives to the address with the blue lights spinning. Part of you feels like you should know what’s bothering Tim, but he’s not exactly easy to read, nor is he willing to admit that something is going on. So, until - or if - you can deduce what’s making him so distant and easily angered this week, you’ll give him the room and the quiet he clearly desires.
“Side gate is open,” Tim says as he parks beside the neighbor’s house. “We’ll use it for entry, split up and clear the house. I’ll go right.”
“Yes, sir,” you reply, opening your door.
As you follow Tim through the gate and duck under windows lining the side of the house, you focus on the job. Tim’s back muscles are tense beneath his uniform, and if you aren’t careful, you’ll think about him and let your guard down. Entering the broken back door, you tap Tim’s shoulder before you turn left into a small dining area. With your gun raised, you move quickly but carefully through the room. A crash sounds down the hall, so you press your back to the wall and move toward the noise, keeping your steps light and breathing quiet.
Tim exits a door behind you, and you drop your gun as soon as you realize it’s him. Moving together, you prepare to enter the room where the intruder is shouting demands.
“On three,” Tim whispers, covering the door so you can enter. “One. Two. Three.”
He pushes the door open, stepping into the doorway as you move inside.
“LAPD!” you announce. “Put your hands up!”
The large man - whose boot likely matches the shoe print on the back door - bares his teeth at you before he turns to the woman guarding her son. They’re both sporting bruises and a wound at the woman’s hairline drips blood down her cheek.
“Let me see your hands!” you demand, stepping toward the man.
Tim doesn’t move, his eyes bouncing between the suspect and the young boy cowering behind his mother.
“It’s my house,” the man says.
“Not anymore,” the woman interjects. “We have a restraining order.”
With his jaw clenched, Tim lowers his gun and steps forward. “Last chance. You walk out with us or you can keep being a coward and we’ll drag you out.”
The man sneers, turning toward Tim as he prepares to lunge. You holster your weapon quickly, pulling your taser out instead. Pointing it at the larger man’s chest, you shake your head.
“Is that your son?” you ask. “Do you really want him to remember you like this?”
He hesitates, then swings. Tim ducks out of his reach at the last second, and you depress the trigger on the taser, sending 1,500-volt pulses through his body as he folds in on himself and collapses.
Tim steps over the man’s leg to cuff him, and you set your taser down to approach the man’s son and his ex-wife. The boy clings to his mother but looks up at your shield with a small smile.
“We’re Code 4, need an RA at this location,” Tim alerts. “One in custody.”
“This card has my number on it,” you say, offering a large cardstock square to the woman before you. “There’s also a list of numbers on the back that can help support you during this time. The domestic violence hotline can give you information about keeping your address private and hopefully preventing something like this in the future.”
“Thank you,” she replies. “He just showed up out of nowhere.”
You pull a tissue off a nearby table and offer it to her, watching her son as she presses it to her bleeding forehead. The ambulance is only a few minutes away, but you kneel to check on the boy.
“Let’s go,” Tim murmurs, hauling the abusive father to his feet.
“I need an ambulance!” he moans. “She tased me.”
“You will be seen, but you’re trespassing.”
“I can’t walk,” he argues.
“Then I’ll drag you,” Tim snaps.
The man stands then, his head hanging toward his chest as he pulls his feet rather than taking normal steps. You notice that Tim has his hand on the handcuffs rather than the suspect’s arm. Tim's past, you remember. Tim has been in this situation before, he knows precisely what this mother and child are thinking, and that’s why he reacted like he did. There has to be more to it, though.
Tim is thinking about something and he endangers himself every time the thought surfaces.

“Bradford is all yours,” Angela says, shaking her head as she exits Wade’s office. “I know he’s going through some stuff, but how do you deal with him when he’s like this?”
“What’s he going through?” you ask, looking through the glass door.
“It’s almost the anniversary of his dad’s death,” she explains. “I understand being a little touchy, but-”
“We took a domestic call this morning,” you complain, pressing your thumb and forefingers against your eyes. “I didn’t realize the date. I should have told him to let someone else handle it.”
“He’s a cop, he can handle the job,” Angela assures you. She looks at Tim and sighs. “I just… none of us can get through to him. It’s like he’s holding himself hostage in his own memories.”
“I- I’ll see what I can do,” you offer.
“Don’t beat yourself up if he won’t talk. And don’t take anything he says this week personally.”
“You ready?” Tim asks, exiting Wade’s office.
“Yeah,” you answer, nodding to Angela as you follow Tim back to the shop. If he’s thinking about his dad too much, maybe you can give him something else to consider.

The corner store is silent as you walk down the center aisle. At midnight, the building is empty, the radio is off, and the cashier sits silently at the register, earbuds in as she stares at her phone. You should find the silence enjoyable after being yelled at by Tim four times in one night. Instead, it makes you uncomfortable, desperate for something to happen.
“Aha,” you murmur when you find the small selection of cleaning products.
It’s probably a bad idea, you think while you fill the small, handheld shopping basket with various items. You tried to get Tim’s mind off his dad, and their strained past, but none of your attempts were successful. He thought about you long enough to yell, accuse you of overstepping, and make vague threats to discourage you from attempting to make small talk with him. But even then, he retreated into his mind as soon as you agreed and fell quiet again.
“Uh,” the cashier mumbles when you place the basket on the counter. “Is this… you good?”
You look at the odd collection of items ranging from candy and a Dodgers sweatshirt to twine and a spray bottle, smiling. “Yeah.”
“Whatever you say.”

Tim glances at your bag as you place it on the floorboard of the shop but doesn’t say anything. You’ll let him reach his own conclusions about its contents for now. After double-checking with Angela this morning, you learned that there are two days until the actual anniversary of Tom Bradford’s death, and you plan to help Tim through the next forty-eight hours, no matter what it takes.
Now that you've been reminded of the date, it’s clear that Tim is thinking about his father. His tight jaw, distant stare, defiant act of threatening an abusive father, and how he stands at least a foot away from everyone, even if it’s someone he knows and trusts, it's all indicative of his trauma response. Thinking back to yesterday, you remember that he stiffened when you touched his back during calls, and it all begins to make sense.
Tim has a tell, you discover. When he’s thinking about his past, his nostrils flare. You will never admit to watching him that closely, especially not to someone like Angela or Nell, who are convinced you’re in love with him. Yet, you observed him enough yesterday afternoon and during roll call to confirm your suspicion. Even as you watch him now, his fingers tighten around the steering wheel, and his nostrils flare quickly.
“What’s your opinion on stop and frisk?” you inquire.
His hand relaxes as he furrows his brows and asks, “As a policing technique or in general?”
“Policing.”
“So, Terry stops. I think that if there’s reasonable suspicion and no bias it is a useful and protective tactic.”
“Interesting. How can you tell if there’s bias, though? And what makes suspicion reasonable?”
“What are you doing?” Tim asks.
“I’m making conversation, getting opinions, learning,” you list dramatically. “Is that so bad?”
“When we’re in this shop, we’re partners. I’m not your personal podcast.”
“That would actually be really nice,” you reply. “Anyone ever told you your voice is soothing?”
“Stop.”
“It’s just a question!”
“Stop.”
You lift your hands in surrender and turn into your seat properly again. Tim drives through a green light, sees a father walking his son into a playground, and the look returns. You sigh and pull your bag open.
“What was that?!” Tim exclaims, swerving slightly as his right hand raises to his face.
“It’s water,” you answer, shaking the spray bottle. “I need you focused. I can’t worry about you or we’ll both get killed.”
“Focused? I am your superior!” Tim argues as he wipes his hand on his pants.
“Then work with me,” you plead.
“What makes you think I’m unfocused?” he inquires.
“You’re thinking about other things. Just… keep your mind in this shop today, and I won’t spray you again.”
“If you like this job you won’t spray me again,” Tim amends.
“If that’s what you need to hear.”

“She bought Wesley a tie with lobsters on it,” Angela tells Nyla.
“My dad has a tie with fish,” Lucy says. “What’s wrong with that?”
“You called?” you interrupt as you follow Tim to the detectives' desks.
“Yeah, we need you to run down a lead,” Nyla answers. “Unless you’d rather hear about Lucy’s dad’s ugly ties.”
“Hey, I chose some of those ties! Father’s Day is coming up if you want to know where I got them,” she offers.
“Oh, I already bought James a gift,” Nyla answers with faux disappointment.
“What lead?” Tim asks.
Standing behind Tim with one hand behind your back, you spray him without anyone noticing. He turns his head toward you, his eyes warning you to stop. You smile, nodding along with Nyla’s explanation.
“I am not a cat,” Tim whispers as you exit the station.
“Then take the hint,” you reply softly.

Nyla’s lead was indeed helpful, and you deliver a new suspect to the station before you return to patrol. In the shop, you hold the spray bottle in your lap as Tim drives. When you move your fingers toward the top, Tim slams on the brakes and snatches it out of your hand.
“You don’t get to decide what I think about!” he exclaims. “If you’re so worried that I can’t do this job right now, then get out and go back to the station.”
“Tim, that’s not what-”
“It is not your business,” he continues. Loudly. You flinch, but he's too mad to notice. “It is not your place to be my therapist and tell me to only think about good things or to stay in the moment. Whatever it is you think is on my mind is not worth this!”
You take several breaths, watching Tim’s chest heave.
“I know it’s almost the anniversary,” you say, forcing your voice to stay level as you press your palms against your thighs. “Your dad… he clearly got to you, your childhood affects you. And that’s okay. I’m not saying to forget everything or let those experiences become meaningless.”
“Then let it go.”
You look down at your hands as Tim drops the spray bottle beside your feet and begins driving again.
“I’m sorry,” you offer after several minutes. “It was affecting you, and I thought giving you something else to think about would help.”
“Not your call,” Tim grumbles.
Nodding, you locate the scuff on the dashboard, staring at it until your vision blurs.
“How’d that mark get there?” you whisper.
“What?” Tim asks, glancing toward you. “I don’t know.”
“There were marks on my mom’s dash, too,” you say. “Nobody knew how they got there. Nothing we would admit while my dad was around, anyway.”
Tim’s eyes find you again, his gaze different. But you’re still looking at the scratched plastic.
“It was like a switch was flipped,” you confess. “One day, he was at a recital, cheering on his baby. And the next… there were marks on the dashboards and new scars that- that I didn’t ask for. So, I have an idea of how painful the memories can be, how far and how fast they can drag you under until it feels like you’re drowning. I went about it wrong, and I can see that now, so I’m sorry. But my intentions are still the same. I don’t want to sit by while a memory of being hurt keeps hurting you.”
Tim doesn’t reply as he shifts his eyes back to the road. You don’t watch him during the remainder of your shift to know if his nostrils flare or if his breathing returns to normal after his outburst. What you do know is that if Tim is willing to let himself be controlled by memories, you can’t stay close enough to watch it happen.

Scrolling through your notifications as you exit the station, you let your body run on autopilot as you make your way home. You’re nearly across the parking lot when someone says your name. You stop and look up, surprised to see Tim’s full attention on you.
“Lopez thinks you were flirting with me,” Tim says, leaning against the tailgate of his truck.
“When?” you ask. There are several feet between you, and you’d prefer to keep it that way.
“Well, she says it pretty often, but the spray bottle. She noticed that my back was wet, saw it in the shop, put it together.”
You nod, holding your phone with both hands so you don’t fidget and expose how uncomfortable you are.
“Could we talk?” Tim asks.
“Not if it’s about me flirting with you,” you reply lightly.
Tim’s lips quirk up. “No. I’m pretty sure I’ve seen you flirt, and that wasn’t it.”
“Then, what do you want to talk about?”
“What I’m not supposed to think about.” Tim slides his hands into his front pockets and shrugs. “I should talk to someone, not just retreat into who I used to be, dissect what could have been different. I just thought… If I’m going to talk, I need to tell someone I trust. Someone who understands.”
“And that’s me? Last I heard, I was overstepping and needed to let it go.”
Tim nods, stepping back toward his driver’s door.
“But,” you call after him, “if you’ve changed your mind, we can talk.”

Tim’s house is warm, comfortable, manly, and everything you expected. Yet, it’s awkward as you lower onto his couch and watch him move in his kitchen. It’s oddly domestic, but the connection between you and Tim is hanging on by a thread.
“I’m not mad at you,” Tim says suddenly. With his hands spread on the counter, he watches you. “I shouldn’t have lashed out like that. I… my mind feels like my archenemy some days, and I fight that battle alone. You tried to help, and I didn’t know what to do. I’m sorry.”
“No one knows the mess we’re in,” you agree. “The voices in my head say I’m being paranoid, but I know it will pull me under someday if I let it. You don’t have to apologize, Tim. I get it.”
“I don’t know what hurts worse, letting go or remembering,” Tim adds, walking to the couch with two glasses. He sets one in front of you, then sits beside you. There’s not as much distance between you now, but the vulnerability makes it feel like you’re exposed face-to-face.
“You were right,” Tim admits. “I’ve been thinking about what happened when I was a kid, wondering where everything went wrong, trying to identify something I could have done differently. Now that he’s gone, I guess I’ll never know.”
“Tim,” you breathe out, your heart breaking for him. “That was not your fault. None of it was because of you.”
“You’ve never wondered?”
“I didn’t say that.” You lift your glass, holding it between your hands to look down at it. “I used to lay awake at night trying to figure out what part of me was so broken that someone would do that to me. Especially someone I loved and who was supposed to love me.”
“But it’s not our fault,” Tim repeats. “It’s theirs.”
“And we can’t save everyone.”
“We shouldn’t have had to save anyone. Not even ourselves. I think back now, and I don’t remember my dad ever hitting my mom. He was verbally abusive, threatened to go farther, exhausted her emotionally and mentally. I tried to stay between him and Genny.”
“From what I’ve heard, you protected Genny from more than the bruises,” you offer. “You’re an incredible person, Tim.”
Tim smiles, turning his head toward you as his elbows rest on his thighs. “Was that flirting?”
“You’ll know when I’m flirting, Bradford,” you answer with a smile.
“When I was deployed, there were a couple guys whose wives divorced them,” Tim begins. “I found myself wondering why my mom didn’t do that. My dad would disappear for a week or so here and there. She could have left, but she didn’t.”
“I think moms try to fix everything in the only way they know how. If my mom even knew, she never showed it. But, I wondered the same thing. 20/20 hindsight, I guess.”
Tim empties his glass, then says, “Thank you.”
“For what?” you inquire, setting your cup beside his.
“The stuff in my locker? No one else would have put it there.”
You duck your chin to hide your smile. “It’s what I wanted when I was stuck in this cycle as a kid. I had panic attacks for a while. Music, something comfortable to wear, something rough to hold and ground myself with, and snacks I wouldn’t get otherwise felt like an escape to a world where I was safe, different.”
“I saw a therapist who told me to find ‘a portal to a better world’ when my PTSD was at its worst,” Tim says, leaning back against the couch, his hand falling toward you. “I was reliving memories that were killing me, and couldn’t figure out how to stop the bloodshed long enough to discover Narnia.”
“Narnia?” you repeat. “I didn’t realize you were a man of taste.”
“Next time, you won’t try to distract me with sports.”
“No. Although, I’d prefer a world where there isn’t a next time.”
“That’s a world we’d have to make.”
You lock eyes with Tim, shifting closer to him as the soft hum of his air conditioner fills the room.
“Are you okay?” you whisper, brushing your fingers against Tim’s.
“Would it sound like I was flirting if I said I am now?” he questions, leaning toward you as he smiles.
“Maybe,” you admit. “But would that be such a bad thing?”
“I don’t think so.”
“Me neither. After all, you trust me and I understand.”
Tim rolls his eyes at your teasing, and when you inhale, preparing to continue, he raises his right hand to your face, holding your jaw. You silence, watching Tim’s eyes.
“I don’t…” he begins. “I don’t want to be crutches.”
“Tim,” you breathe. “We’re not showing each other our scars to learn how to support each other. I’m telling you who I am because you make me better. You help me see who I am now, not who I force myself to see in the mirror. You aren’t my salvation, but I think you could be something.”
“I’ve lived in fear for most of my adult life that I couldn’t love someone, that I could tell them the truth about everything, about me. With you… telling the truth is as easy as breathing.”
“Breathing before, after, or during a panic attack?” you clarify.
“Why are we even having this conversation?” Tim jokes, shrugging. “You’ve been flirting with me for years, you clearly want me.”
“Then I guess it’s up to you,” you reply. “We’re at the edge, Tim. It’s your call. Are we going over the edge or running back to safety?”
“Tell me something about yourself,” Tim requests, pushing your hair over your shoulder.
You hum, dragging your fingers along his forearm. “I thought I was undesirable until I was, like, mid-20s.”
“What changed?”
You shrug. “Put on the uniform, met a few badge bunnies, I don’t know. I still feel it sometimes.”
“With me?”
“No,” you whisper. “But I think you see more than my face. Your turn.”
Tim licks his lips as he thinks. “You know all my secrets now.”
“Then tell me something that isn’t a secret.”
“I didn’t think I’d be able to fall in love after Isabel. Not until a few years ago.”
“You had a girlfriend?”
Tim laughs. “What else changed a few years ago?”
You trace your own life back one year, then two, then… “Oh. Me?”
“Oh. You,” Tim repeats. “I was also called Reaper in the Army.”
“That’s so much cooler than falling in love with me. How’d you get that name?”
Tim’s lips are mere inches from you as he asks, “Is that really what you want to focus on right now?”
“Promise you know we’re not crutches?” you request.
Tim takes your hand and says, “I know. You’re clearly more of a walker.”
You huff, but Tim closes the distance - finally - and kisses you slowly. With his hand on your face, your hands joined, and your knees against his thigh, you forget everything except Tim Bradford and the future you want with him.
He pulls back first, searching your eyes before you drop your chin and kiss a scar on his neck. Tim takes a shaky breath as you sit back on your socked feet. You’d felt so out of place when you first arrived, and now you’re not sure you want to leave the comfort and seclusion of Tim’s home and his arms.
“You know we’re not going to be allowed to ride together anymore, right?” Tim asks.
“Yeah. Now we can do so much more,” you reply.
“Such a flirt,” Tim murmurs.
“I’m here for you,” you remind him. “No matter when, no matter what.”
Tim smiles as he pulls you closer. “Prove it.”
#tim bradford x reader#tim bradford x y/n#tim bradford x you#tim bradford fic#tim bradford the rookie#tim bradford imagine#tim bradford oneshot#tim bradford#the rookie x reader#the rookie abc#fem!reader#hanna writes✯
268 notes
·
View notes
Text
The Siren, or The Heart of the Matter Masterlist

Pairing: Bucky Barnes x OFC
Tags: Romance, fluff, smut, mental health, healing from trauma, enemies to lovers, slow burn, canon-typical violence, angst with a happy ending.
MINORS DNI.
* This story is complete *
Chapter Directory:
The Book, or Inez is a Fucking Goddess
The Mission, or Is Barfing on Captain America's Shoes Treason?
The Hospital Room, or Give My Best to Ovid
The Beginning, or Tin Man, Beefcake, Man Bun, and Natasha
The Beginning's Beginning, or The Abridged and Heavily Redacted Life and Times of Cleo Blake
The Crystal, or Cleo's Mother is Right for the First Time in Recorded History
The Neighbor, or Meg's Goldfish Might Need a New Godmother
The Assignment, or In Defense of the Mighty Ovary
The Lie, or The Truth Without the Calories
The Run, or To the Window, to the Wall, 'Til the Sweat is Fucking Everywhere
The Test, or Clint's No Good Very Bad Day
The Power, or The Mandatory Forced Proximity Event
The Theories, or Overwhelmed by the Power of Quarterflash
The Question, or I'll Make an Avenger Out of You
The Name, or A Return to My Natural Habitat
The Philosopher, or If You Want Peace, Prepare for War
The Phone Call, or Hey Look, Ma, I Made It
The Text, or As Easy as Biting off Your Own Finger
The Bar, or Good Company and Bad Jokes
The Interruption, or An Abundance of Party Crashers - Part One
The Interruption, or An Abundance of Party Crashers - Part Two
The Haircut, or Level Two Friendship Activities
The Appointment, or Therapy is One Hell of a Drug
The Lamp, or Making a Habit
The Visitor, or Eight Harry Potter Movies and One Second of Bravery
The File, or Secrets, Sparring, and Escapes
The Fuck-Up, or The Road so Far is Full of Mistakes
The Friend, or Low Times at Sneaky Pete's
The Moment
The Note, or The Thesis Defense from Hell
The Soldier, or I Fucking Love You
The Intervention, or Righting Some Wrongs
The Miracle, or Ten Words and a Thousand Kisses
Bonus Content:
Character Doodle - Cleo
Avengers Karaoke Jams Playlist
Character Doodle - The Siren Suit
Character Doodle - The Philosopher
Angry Feminist Killjoy Playlist
Poll - What comes next?
Character Doodle - The Siren Suit with Helmet
#fanfiction#fanfic#marvel fanfiction#mcu#marvel#mcu fanfiction#james buchanan barnes#bucky barnes#bucky barnes fanfiction#enemies to lovers#slow burn#original female character#original superhero character#mental health#ptsd#healing from trauma#cross posted on ao3#steve rogers is a good bro#implied sa#canon typical violence#natasha romanov is a good bro#clint barton is a good bro#angst#the siren#the heart of the matter#protective bucky barnes#angst with a happy ending#smut#bucky barnes smut
109 notes
·
View notes
Text
I'd been seeing videos on Tiktok and Youtube about how younger Gen Z & Gen Alpha were demonstrating low computer literacy & below benchmark reading & writing skills, but-- like with many things on the internet-- I assumed most of what I read and watched was exaggerated. Hell, even if things were as bad as people were saying, it would be at least ~5 years before I started seeing the problem in higher education.
I was very wrong.
Of the many applications I've read this application season, only %6 percent demonstrated would I would consider a college-level mastery of language & grammar. The students writing these applications have been enrolled in university for at least two years, and have taken all fundamental courses. This means they've had classes dedicated to reading, writing, and literature analysis, and yet!
There are sentences I have to read over and over again to discern intent. Circular arguments that offer no actual substance. Errors in spelling and capitalization that spellcheck should've flagged.
At a glance, it's easy to trace this issue back to two things:
The state of education in the United States is abhorrent. Instructors are not paid enough, so schools-- particularly public schools-- take whatever instructors they can find.
COVID. The two year long gap in education, especially in high school, left many students struggling to keep up.
But I think there's a third culprit-- something I mentioned earlier in this post. A lack of computer literacy.
This subject has been covered extensively by multiple news outlets like the Washington Post and Raconteur, but as someone seeing it firsthand I wanted to add my voice to the rising chorus of concerned educators begging you to pay attention.
As the interface we use to engage with technology becomes more user friendly, the knowledge we need to access our files, photos, programs, & data becomes less and less important. Why do I need to know about directories if I can search my files in Windows (are you searching in Windows? Are you sure? Do you know what that bar you're typing into is part of? Where it's looking)? Maybe you don't have any files on your computer at all-- maybe they're on the cloud through OneDrive, or backed up through Google. Some of you reading this may know exactly where and how your files are stored. Many of you probably don't, and that's okay. For most people, being able to access a file in as short a time as possible is what they prioritize.
The problem is, when you as a consumer are only using a tool, you are intrinsically limited by the functions that tool is advertised to have. Worse yet, when the tool fails or is insufficient for what you need, you have no way of working outside of that tool. You'll need to consult an expert, which is usually expensive.
When you as a consumer understand a tool, your options are limitless. You can break it apart and put it back together in just the way you like, or you can identify what parts of the tool you need and search for more accessible or affordable options that focus more on your specific use-case.
The problem-- and to be clear, I do not blame Gen Z & Gen Alpha for what I'm about to outline-- is that this user-friendly interface has fostered a culture that no longer troubleshoots. If something on the computer doesn't work well, it's the computer's fault. It's UI should be more intuitive, and it it's not operating as expected, it's broken. What I'm seeing more and more of is that if something's broken, students stop there. They believe there's nothing they can do. They don't actively seek out solutions, they don't take to Google, they don't hop on Reddit to ask around; they just... stop. The gap in knowledge between where they stand and where they need to be to begin troubleshooting seems to wide and inaccessible (because the fundamental structure of files/directories is unknown to many) that they don't begin.
This isn't demonstrative of a lack of critical thinking, but without the drive to troubleshoot the number of opportunities to develop those critical thinking skills are greatly diminished. How do you communicate an issue to someone online? How do look for specific information? How do you determine whether that information is specifically helpful to you? If it isn't, what part of it is? This process fosters so many skills that I believe are at least partially linked to the ability to read and write effectively, and for so many of my students it feels like a complete non-starter.
We need basic computer classes back in schools. We need typing classes, we need digital media classes, we need classes that talk about computers outside of learning to code. Students need every opportunity to develop critical thinking skills and the ability to self-reflect & self correct, and in an age of misinformation & portable technology, it's more important now than ever.
536 notes
·
View notes
Text
There has been more than enough drama about this whole situation so I will be as direct and concise as I can. This will be my last post about the matter regarding Myka/codslut. This will likely be my last post on this blog period.
This fandom community has crucified me over a story that has fallen apart over what I can only describe as the lightest scrutiny. FOIA requests, when expedited, have a ten day window to be granted, not a twelve hour window, and normally take months to even years to grant. Americans do not call small towns villages. Crisis workers do not have unfettered, immediate access to clients' personal information, let alone that of complete strangers on the internet.
I am not exaggerating when I say I have feared for my safety for the past week. The three people who have lead the charge against me have slandered, harassed, and outright stalked me—keeping track of posts I've made and deleted, changes I've made to my directory, and even the time between posts I have made. I have genuinely feared that the next step these people were going to take would be to search both of my blogs (because I have not, in the past, been very concerned about hiding my main) for my personal information in order to dox me.
I believe this campaign has been racist ("gaz erasure my ass") and ableist in nature. I believe my being autistic—and my trouble communicating in a way that could satisfy the aforementioned people this entire week—has played a part in the way this fandom has victimized me.
I believe in particular that sheheal has a personal vendetta against me, although I do not know why. I believe that their claim that they must leave their blog up as "evidence" is false—I believe they are keeping it active in order that it should always be digitally connected to me, and thus risk my safety and peace in whatever online space I choose to be in next. I am entertaining the belief that she even intends for it to follow me in real life, although that may be more paranoia than possibility.
I am aware of the mistakes I have made. I regret them. I am sorry for them. If what has happened to me is representative of what happened to Myka, I have nothing but empathy for her. Even before this happened, I would not wish this on anyone. I do not believe that dogpiling is justice, and have fought against it when I have seen it happening in this fandom in the past. I did not and do not want this to happen to anyone, ever, no matter their sins.
I want to extend a gratitude I find difficult to express the depth of to everyone who reached out to check on me. I especially want to thank Early for being the first person to stick their neck out for me, and for everything after. I hope to be friends with you all for a long time. You mean more to me than you know. You have made a lonely and difficult week feel less lonely and difficult.
I do not want to be a part of this fandom anymore. I have poured over a year and a half of work and creative energy into this community and it has meant nothing. I have loved this community and it has meant nothing. I have fought for this community and it has meant nothing.
If fandom was ever a safe space, it is not anymore. It is not safe for those affected by racism and it is not safe for those affected by disability. It is not safe for anyone who makes mistakes. It is not safe for me, and reader, it is not safe for you. I did not think this would happen to me. Do not make the mistake of thinking this won't happen to you.
214 notes
·
View notes