#and brute force attacks.
Explore tagged Tumblr posts
Text
Securing Your Website: Best Practices for Web Developers
As the digital landscape continues to evolve, website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated, it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this article, we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potential threats.
Introduction
In today's interconnected world, websites serve as the digital storefront for businesses, making them vulnerable targets for cyber attacks. From data breaches to malware infections, the consequences of a security breach can be severe, ranging from financial loss to damage to reputation. Therefore, prioritizing website security is essential for maintaining the trust and confidence of users.
Understanding Website Security
Before diving into best practices, it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measures taken to protect websites from cyber threats and unauthorized access. Common threats include malware infections, phishing attacks, SQL injection, cross-site scripting (XSS), and brute force attacks.
Best Practices for Web Developers
Keeping Software Updated
One of the most fundamental steps in website security is keeping all software, including the content management system (CMS), plugins, and server software, updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can be exploited.
Implementing HTTPS
Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users, ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors, as indicated by the padlock icon in the browser's address bar.
Using Strong Authentication Methods
Implementing strong authentication methods, such as multi-factor authentication (MFA) and CAPTCHA, adds an extra layer of security to user accounts. MFA requires users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device, reducing the risk of unauthorized access.
Securing Against SQL Injection Attacks
SQL injection attacks occur when malicious actors exploit vulnerabilities in web applications to execute arbitrary SQL commands. Web developers can prevent SQL injection attacks by using parameterized queries and input validation to sanitize user inputs effectively.
Protecting Sensitive Data
It's essential to employ encryption techniques to protect sensitive data, such as passwords, credit card information, and personal details, stored on the website's servers. Encrypting data at rest and in transit mitigates the risk of data breaches and unauthorized access.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and weaknesses in the website's infrastructure and codebase. Penetration testing, vulnerability scanning, and code reviews enable web developers to proactively address security issues before they are exploited by attackers.
Choosing a Secure Hosting Provider
Selecting a reputable and secure hosting provider is critical for ensuring the overall security of your website. When evaluating hosting providers, consider factors such as security features, reliability, scalability, and customer support.
Evaluating Security Features
Choose a hosting provider that offers robust security features, such as firewalls, intrusion detection systems (IDS), malware scanning, and DDoS protection. These features help protect your website from various cyber threats and ensure continuous uptime.
Ensuring Regular Backups
Regularly backing up your website's data is essential for mitigating the impact of security incidents, such as data breaches or website compromises. Choose a hosting provider that offers automated backup solutions and store backups securely offsite.
Customer Support and Response to Security Incidents
Opt for a hosting provider that provides responsive customer support and has established protocols for handling security incidents. In the event of a security breach or downtime, prompt assistance from the hosting provider can minimize the impact on your website and business operations.
Implementing Firewall Protection
Firewalls act as a barrier between your website and external threats, filtering incoming and outgoing network traffic based on predefined security rules. There are several types of firewalls, including network firewalls, web application firewalls (WAF), and host-based firewalls.
Configuring and Maintaining Firewalls
Properly configuring and maintaining firewalls is crucial for effective security. Define firewall rules based on the principle of least privilege, regularly update firewall configurations to reflect changes in the website's infrastructure, and monitor firewall logs for suspicious activity.
Educating Users about Security
In addition to implementing technical measures, educating users about security best practices is essential for enhancing overall website security. Provide users with resources, such as security guidelines, tips for creating strong passwords, and information about common phishing scams.
Importance of User Awareness
Users play a significant role in maintaining website security, as they are often the targets of social engineering attacks. By raising awareness about potential threats and providing guidance on how to recognize and respond to them, web developers can empower users to stay vigilant online.
Providing Training and Resources
Offer training sessions and educational materials to help users understand the importance of security and how to protect themselves while using the website. Regularly communicate updates and reminders about security practices to reinforce good habits.
Monitoring and Responding to Security Incidents
Despite taking preventive measures, security incidents may still occur. Establishing robust monitoring systems and incident response protocols enables web developers to detect and respond to security threats in a timely manner.
Setting Up Monitoring Tools
Utilize monitoring tools, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and website monitoring services, to detect abnormal behavior and potential security breaches. Configure alerts to notify you of suspicious activity promptly.
Establishing Incident Response Protocols
Develop comprehensive incident response plans that outline roles, responsibilities, and procedures for responding to security incidents. Establish clear communication channels and escalation paths to coordinate responses effectively and minimize the impact of security breaches.
Securing your website requires a proactive approach that involves implementing a combination of technical measures, choosing a secure hosting provider, educating users about security best practices, and establishing robust monitoring and incident response protocols. By following these best practices, web developers can mitigate the risk of security breaches and safeguard their websites and the sensitive data they handle.
#website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated#it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this#we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potenti#Introduction#In today's interconnected world#websites serve as the digital storefront for businesses#making them vulnerable targets for cyber attacks. From data breaches to malware infections#the consequences of a security breach can be severe#ranging from financial loss to damage to reputation. Therefore#prioritizing website security is essential for maintaining the trust and confidence of users.#Understanding Website Security#Before diving into best practices#it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measur#phishing attacks#SQL injection#cross-site scripting (XSS)#and brute force attacks.#Best Practices for Web Developers#Keeping Software Updated#One of the most fundamental steps in website security is keeping all software#including the content management system (CMS)#plugins#and server software#updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can#Implementing HTTPS#Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users#ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors#as indicated by the padlock icon in the browser's address bar.#Using Strong Authentication Methods#Implementing strong authentication methods
0 notes
Text
With the new update out, I love the idea of Wild playing more defensive well Wars is more offensive.
#like it fits a lot with their games#like yeah botw u can brute force a lot but this was like the first time you could really be more defensive attack wise i feel#heavy on the arrow usage and just all the stuff u could do with the slate before meele fighting an enemy#where like hw is very meele especially with wars#hes always right up in everyones business when fighting#linked universe update#linked universe#lu wild#lu warriors#moon emissary thoughts
30 notes
·
View notes
Text
when a battle can't be solved with dark nova yakumo

#me at the sorceror's trials when i can't brute force it#there are probably better attackers out there since DN yaku got released a while ago#but i don't have them.#so every time there's a problem#i throw my nerdworm at the enemies to make them go away LOL#then the gimmick has the AUDACITY to be like#(. ❛ ᴗ ❛.) teehe.e. the enemies counter 300% every turn#or#(*/ω\*) oh no ! your attacker in that slot can't do anything but guard!#[irritably starts shuffling my units around the roster like i'm a cup sliding scam artist]#STOP THAT. IF I CAN'T MELEE MY WAY OUT OF THIS I'LL HAVE TO uSE MY BRAIN#AND NO ONE WILL LIKE THAT#IF I CAN'T TAKE DOWN AT LEAST 40% OF THE ENEMY'S HP IN ONE HIT THEN THE DOPAMINE AINT GONNA CASCADE DOWN MY SYNAPSES LIKE TROPICAL RAIN#nu carnival yakumo
100 notes
·
View notes
Text
in my mind i like creating not only fakemons but also like fake moves/abilities/stat spreads. i especially have fun thinking about what i would give characters if they were pokémon. like it’s normal to imagine your oc as a dnd character obviously or something else from a game like that but me i’m out here pokémonifying people. the thing is i’m always like ohhh is this too overpowered would this entirely hypothetical fake thing that will never be real break the meta. then i remind myself how bad gen 9 power creep is and i feel better. it could be real someday
#would it be too much to have a signature move that 1. uses the user’s defense stat instead of attack#(and the user has a high defense and otherwise good access to defense buffs)#2. has a flinch chance and 3. deals recoil damage#like i’m thinking like a move where you just absolutely smash into the target with your whole body#brute force#see in terms of balancing i don’t think that’s too ridiculous#you’d probably nerf it by giving it low pp or even low accuracy#it’s your average powerful recoil move just a little different#the real issue is the flavor text. you would need a lot of words to cover all of that lol#that’s the unrealistic part#that’s probably the one thing stopping gamefreak from creating some real monsters. they’re limited by their own character limit probably#or you could do what they did in gsc or rse days and give the worst and least descriptive descriptions ever#‘‘super effective’’ hits. ‘ups attack if suffering’. son what do those mean#and even then sometimes you need a full bulbapedia page to explain the internal nuances of how it works#like dragon darts for example lol#pokémon#pokeposting
11 notes
·
View notes
Text
Im playing Dark revival on hard mode and I am hating this so much. Why are there so many lost ones back off for five minutes DAMN
#I cant even do any stealth/sneak attacks because there's too many and I'll get spotted immediately#You just have to run through them. No fun stealth missions and sneaking around#It's not fun at all#What is it with bendy devs and “haha duuuhh brute force and violence = fun and scary”??? NO#batim#bendy#batdr#bendy and the ink machine#bendy and the dark revival
9 notes
·
View notes
Text

D is not a tall or well-built man. He stands about 5'5 at most and that is quite generous given his poor biological health as his grandfather's clone. Others assume him to be a mild-mannered asian male but D is quite capable of being vicious when need be, albeit as a last resort due to the energy it takes out of him.
#🐾 || headcanons#🐾 || musings#You'll rarely see D being aggressive in the manga or the anime unless absolutely provoked#He's no brute force or unstoppable wall but he has some mad agility and supernatural abilities#And a very close connection to nature#If others threaten him in the pet shop then all his pets are ready to throw down#Dragons and totetsus and all manners of critters#D really doesn't like resorting to violence though that's the funny thing#He's quite happy for people to take bad decisions whatever they may be but against his pets or innocent animals no no no#Reading more of the manga this week between storms and SDV playthroughs#Never realised D actually had bad health#He is very much the DND equivalent of “Are you sure you want to attack this guy?”
8 notes
·
View notes
Text
my elden ring character is such a dummie, they'll immediately start worshipping the witch lady with the cool hat trying to destroy death, but then one (1) guy is being mean to us and NOW we gotta attack him with a sword, potentially destroying that entire questline.
#mse's playing elden ring#i didn't even know you can attack NPCs???#i was half doing it for shits and giggles#and then gideon was like 'consider double-crossing that dude' and my dummie character of course said nothing#about already burning that bridge#we're a suave bandit except we brute force everything lmao
8 notes
·
View notes
Text
being a cs student is just like. googles github issue. googles github issue. googles github issue. googles github issue. googles github issue. googles github issue. googles github issue
#i am dying.#computer science#no i will NOT read the fucking git book#yes i KNOW it would be helpful.#i refuse out of spite#and will continue to have panic attacks about this until i solve my problems through sheer brute force
3 notes
·
View notes
Text
something something being in a situation that you know isn't dangerous but your mind is screaming at you to run run run hide fight run get away get out of there . but you don't want to make things worse so you sit there and close your eyes and let it happen !!
#<< THIS IS ABOUT MY EVILDEAD FIC. ITS FROM ASHE POV BUT IM JUST. THINKING ABT WILLIAM. GOD.#something something brute forcing your way through a panic attack !!!!!!!#i have a lot of feelings about this scene!!!!!!!!!!! i wanna get this fic done tonight
5 notes
·
View notes
Text
*covered in blood* ijve been playing ffta nonstop for 2 days
#pete blabs#videos games..... good#the thing abt these tactical games is that i can never learn how to use a tactic i always just brute force it#even in pokemon i would always delete all the status moves n only have attacking moves#itss hard for me to figure out#this game kinda makes it hard to know wtf im doing sometimes bc all the items dont have goddamn descriptions n shit#guy who is complaining as if the game isnt super fun anyway#this is one of my childhood games ive never played a normal ff game ive only ever played ffta GSGSJFHSKG#hm. it occured to me that maybe by watching a lets play it could help me figure out how all this stuff works#but i dont wanna watch someone else play I WANNS PLAYYYYY#ok i just checked out a random lets play video#this guy be like#''and keep in mind if youre gonna be making a blue mage you gotta give them the blue saber so they can learn [learning] because this#is what makes it so when they get hit by a monster attack they learn it''#HOW DO YOU KNOW ALL OF THIS. WHERE DOES IT TELL YOU ALL OF THIS#this game is so much More than i remember
3 notes
·
View notes
Text
Nobody has sent any more asks but I’m still working on my self insert kit and I have failed at my attempts to give myself negative synergy w jing yuan LMFAOOOOOO
#pattering on the roof#I def wouldn’t be his best support I’m v much better with a BE or follow-up team#but I actually. would fix some issues w lightning lord I fear#by manually controlling which enemies take more dmg from his bounce attacks#rip to that idea LMFAOOOOOO idk it’s hard to give chars Negative synergy when one is a support and the other is a dps#like u can always brute force that if u rlly wanna
4 notes
·
View notes
Text
Mental health issues are SOOO funny.
Me: Well, I'm not actively trying to kill myself and I'm not in the hospital so it's probably all just in my head and I'm just making it up for attention. I think if I was faced with a real crisis this wouldn't matter.
Anyone I'm speaking to (Concerned): Can you get some medication? Can you quit your job ASAP?
#goat talk#personal#I go 'well if I was faced with a *REAL* crisis I would feel worse so this can't be one'#and 'well I'm forcing myself to do all the things I'm supposed to. I'm exercising and socializing so it can't be that bad'#Like I *do* work on my hobbies#I just don't get into a flow very well#and I sleep 10+ hours a day and my shit is weird and I'm always about to cry#so I must be fine right?#it's probably a good time to consider something like that#I had my panic attacks under control starting in 2020 when covid hit#but now that Covid 'isn't an issue' they're back. full force. 4+ times a week with tears each night.#It's incredibly lucky I can still brute force willpower myself into situations that *help*#I imagine if I wasn't working every mental health tip under the sun from 'find religion' to 'get enough sunlight' to 'dye your hair'#I would be worse off
2 notes
·
View notes
Text
PassBreaker - Command-line Password Cracking Tool Developed In Python
PassBreaker is a command-line password cracking tool developed in Python. It allows you to perform various password cracking techniques such as wordlist-based attacks and brute force attacks.�� Features Wordlist-based password cracking Brute force password cracking Support for multiple hash algorithms Optional salt value Parallel processing option for faster cracking Password complexity…
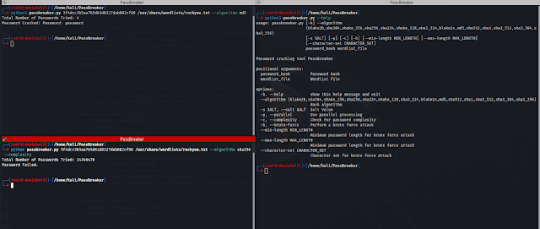
View On WordPress
#Brute Force Attacks#Bruteforce Password Cracker#ethical hacking#Hacking Tool#Kali Linux#KitPloit#PassBreaker#Python Scripts
1 note
·
View note
Text
im going to do abyss floor 12 vs damn maguu kenki got hands
1 note
·
View note
Text
Art fight is doing crazy amounts of work getting me to get out of my artistic comfort zone and get more used to digital art. This is awesome
#Like I could make decently ok stuff when i was using medibang and procreate but my laptop shat itself so much that i#couldnt draw with much regularity#and messing with the file system every time was such a pain#and i didnt have access on my phone to send or post stuff right away#blah blah blah#anyway#procreate is what i needed#it felt bad at first but its gotten significantly better from just brute forcing trial and error for art fight refs and attacks
1 note
·
View note
Text
How to Secure Your WordPress Login Page from Hackers
[et_pb_section fb_built=”1″ _builder_version=”4.27.4″ _module_preset=”default” global_colors_info=”{}”][et_pb_row _builder_version=”4.27.4″ _module_preset=”default” global_colors_info=”{}”][et_pb_column type=”4_4″ _builder_version=”4.27.4″ _module_preset=”default” global_colors_info=”{}”][et_pb_text _builder_version=”4.27.4″ _module_preset=”default” hover_enabled=”0″ global_colors_info=”{}”…
#brute force attack#brute force attack prevention#cyber-security#cybersecurity#cybersecurity best practices#disable xml-rpc#firewall for wordpress#malware protection#protect wordpress website#secure wordpress hosting#secure wordpress login#secure wp-config file#security#site hacking prevention#SSL encryption#two-factor authentication#web application firewall#web development#Website Builders#Wordpress#wordpress brute force protection#wordpress hosting security#wordpress password security#wordpress security#wordpress security best practices#wordpress security plugins#wordpress security tips
0 notes