#and server software
Explore tagged Tumblr posts
Text
Securing Your Website: Best Practices for Web Developers
As the digital landscape continues to evolve, website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated, it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this article, we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potential threats.
Introduction
In today's interconnected world, websites serve as the digital storefront for businesses, making them vulnerable targets for cyber attacks. From data breaches to malware infections, the consequences of a security breach can be severe, ranging from financial loss to damage to reputation. Therefore, prioritizing website security is essential for maintaining the trust and confidence of users.
Understanding Website Security
Before diving into best practices, it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measures taken to protect websites from cyber threats and unauthorized access. Common threats include malware infections, phishing attacks, SQL injection, cross-site scripting (XSS), and brute force attacks.
Best Practices for Web Developers
Keeping Software Updated
One of the most fundamental steps in website security is keeping all software, including the content management system (CMS), plugins, and server software, updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can be exploited.
Implementing HTTPS
Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users, ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors, as indicated by the padlock icon in the browser's address bar.
Using Strong Authentication Methods
Implementing strong authentication methods, such as multi-factor authentication (MFA) and CAPTCHA, adds an extra layer of security to user accounts. MFA requires users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device, reducing the risk of unauthorized access.
Securing Against SQL Injection Attacks
SQL injection attacks occur when malicious actors exploit vulnerabilities in web applications to execute arbitrary SQL commands. Web developers can prevent SQL injection attacks by using parameterized queries and input validation to sanitize user inputs effectively.
Protecting Sensitive Data
It's essential to employ encryption techniques to protect sensitive data, such as passwords, credit card information, and personal details, stored on the website's servers. Encrypting data at rest and in transit mitigates the risk of data breaches and unauthorized access.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and weaknesses in the website's infrastructure and codebase. Penetration testing, vulnerability scanning, and code reviews enable web developers to proactively address security issues before they are exploited by attackers.
Choosing a Secure Hosting Provider
Selecting a reputable and secure hosting provider is critical for ensuring the overall security of your website. When evaluating hosting providers, consider factors such as security features, reliability, scalability, and customer support.
Evaluating Security Features
Choose a hosting provider that offers robust security features, such as firewalls, intrusion detection systems (IDS), malware scanning, and DDoS protection. These features help protect your website from various cyber threats and ensure continuous uptime.
Ensuring Regular Backups
Regularly backing up your website's data is essential for mitigating the impact of security incidents, such as data breaches or website compromises. Choose a hosting provider that offers automated backup solutions and store backups securely offsite.
Customer Support and Response to Security Incidents
Opt for a hosting provider that provides responsive customer support and has established protocols for handling security incidents. In the event of a security breach or downtime, prompt assistance from the hosting provider can minimize the impact on your website and business operations.
Implementing Firewall Protection
Firewalls act as a barrier between your website and external threats, filtering incoming and outgoing network traffic based on predefined security rules. There are several types of firewalls, including network firewalls, web application firewalls (WAF), and host-based firewalls.
Configuring and Maintaining Firewalls
Properly configuring and maintaining firewalls is crucial for effective security. Define firewall rules based on the principle of least privilege, regularly update firewall configurations to reflect changes in the website's infrastructure, and monitor firewall logs for suspicious activity.
Educating Users about Security
In addition to implementing technical measures, educating users about security best practices is essential for enhancing overall website security. Provide users with resources, such as security guidelines, tips for creating strong passwords, and information about common phishing scams.
Importance of User Awareness
Users play a significant role in maintaining website security, as they are often the targets of social engineering attacks. By raising awareness about potential threats and providing guidance on how to recognize and respond to them, web developers can empower users to stay vigilant online.
Providing Training and Resources
Offer training sessions and educational materials to help users understand the importance of security and how to protect themselves while using the website. Regularly communicate updates and reminders about security practices to reinforce good habits.
Monitoring and Responding to Security Incidents
Despite taking preventive measures, security incidents may still occur. Establishing robust monitoring systems and incident response protocols enables web developers to detect and respond to security threats in a timely manner.
Setting Up Monitoring Tools
Utilize monitoring tools, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and website monitoring services, to detect abnormal behavior and potential security breaches. Configure alerts to notify you of suspicious activity promptly.
Establishing Incident Response Protocols
Develop comprehensive incident response plans that outline roles, responsibilities, and procedures for responding to security incidents. Establish clear communication channels and escalation paths to coordinate responses effectively and minimize the impact of security breaches.
Securing your website requires a proactive approach that involves implementing a combination of technical measures, choosing a secure hosting provider, educating users about security best practices, and establishing robust monitoring and incident response protocols. By following these best practices, web developers can mitigate the risk of security breaches and safeguard their websites and the sensitive data they handle.
#website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated#it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this#we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potenti#Introduction#In today's interconnected world#websites serve as the digital storefront for businesses#making them vulnerable targets for cyber attacks. From data breaches to malware infections#the consequences of a security breach can be severe#ranging from financial loss to damage to reputation. Therefore#prioritizing website security is essential for maintaining the trust and confidence of users.#Understanding Website Security#Before diving into best practices#it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measur#phishing attacks#SQL injection#cross-site scripting (XSS)#and brute force attacks.#Best Practices for Web Developers#Keeping Software Updated#One of the most fundamental steps in website security is keeping all software#including the content management system (CMS)#plugins#and server software#updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can#Implementing HTTPS#Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users#ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors#as indicated by the padlock icon in the browser's address bar.#Using Strong Authentication Methods#Implementing strong authentication methods
0 notes
Text
NetManage Chameleon - FTP Server
78 notes
·
View notes
Text
Frog floatie Gon☀️
#downloaded an animation software but didn't watch any tutorials#really showing my hubris with this one#he cute tho#gon freecss#my art#art#fanart#digital art#gif#animation#marosii art#hxh#hunter x hunter#greed island challenge#greed island server
229 notes
·
View notes
Text
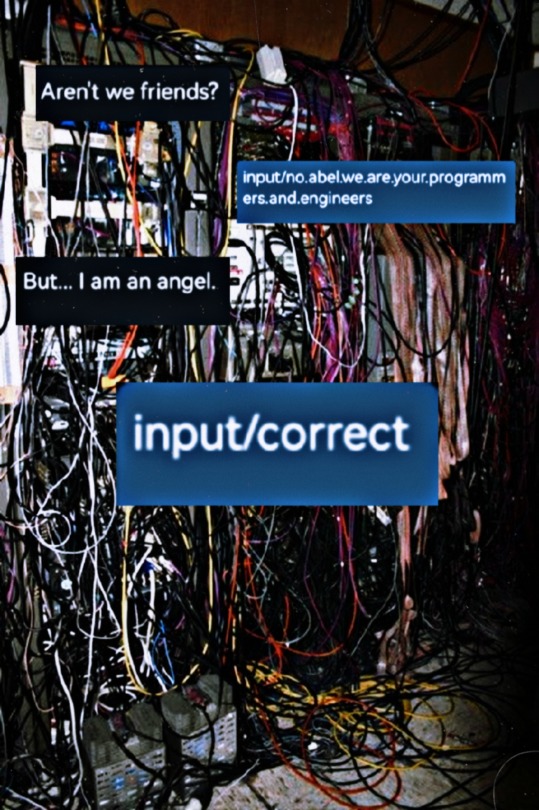
#a.b.e.l#divine machinery#archangel#automated#behavioral#ecosystem#learning#divine#machinery#ai#artificial intelligence#divinemachinery#robot#android#computer#computer boy#guardian angel#angel#angels#serverroom#server room#wires and cables#hardware gore#software gore#message#how dare you#sentient objects#sentient ai
89 notes
·
View notes
Text
HDG Fic that never will be
Hello internet HDG fans and my poor followers who have to see this
I've recently fallen down the HDG fic rabbit hole (WELLNESS CHECK DID THIS TO ME) and reading about the Affini and the Compact and the universe on the wiki have got a bunch of wheels turning in my brain. I got bit by the fic writing bug and started drawing up an outline for a fic idea I had.
However, as I thought about it more, I started to realise this probably wasn't a fic I should write or that might be controversial because it would violate one of the universe guidelines. I figured I may as well make a post talking about it and hopefully get some feedback before I move on to actually spending hours writing thousands of words. Explanation under the cut.
The fic I'm thinking of is an Affini POV. Basically there's a case worker who works to help organise all the affini-floret paperwork, keeps track of the "Notices of Intent to Domesticate", checks in on "independent" Sophonts who are struggling, etc etc. Its also about the wider Compact, about the case worker taking a critical look at their culture and their ideology and potential conflicts that might arise from that. Its looking at the Affini Compact as a kind of "pet rescue" situation, and examining the issues that arise in that context.
So for example, what happens when there's a perfectly dramatic meow-meow or Autistic Trans Girl Who Stinks Good (tm) and like eight different Affini all want them as their Floret? Or how human Pinnates or Pluribuses are less likely to be "adopted" by Affini because they're more difficult and complex to care for? What happens when there's a queer polycule, three of whom are Pluribuses and two of whom are seriously disabled, who SOMEHOW made it through the Accord and are now struggling even in the post-scarcity society of the Affini? They obviously need help but most Affini are reluctant at best to take on that much responsibility.
What happens when an Affini gets bored of their Floret (*gasp*) and wants to give them up? Humans are the most recent acquisition by the Compact and are considered especially cute/domesticable, what happens when human Florets are a "fad"? Do Affini ever trade Florets, temporarily or otherwise?
And what about all the humans who AREN'T Autistic Trans Girls Who Stink Good(tm) or poor exploited military personnel who need domesticating? The "silent majority" of middle class/straight humans for whom life in the Accord was good (as long as they kept their heads down and ratted out their neighbours)? The "boring" ones. Would the Affini even be interested in them?
This is the kind of thing I want to write about. Its really got me humming along, but I'm also aware this kind of messes with one of the big guidelines for the universe - that the Affini are always "perfect". They're centuries/millennia old and are incredibly intelligent, so understand the needs and wants of their charges so perfectly they don't need or understand consent. They know you better than you know yourself, virtually gods compared to human flaws and imperfections.
But my fic would look at the Affini as people - as characters who have quirks and preferences and can make mistakes. As beings who can misunderstand you in important ways. It would be Affini interacting with other Affini, it would be comparing how different Affini treat their Florets. As I understand it, that kind of flies in the face of what the Affini are supposed to be as a concept.
I'm interested in HDG but I'm not interested in writing something that ends up being on the same tier as "Muh Spess Mehreens Could Totally Kill A Bunch Of Big Plants For Real" (shut up no they couldn't, the Compact runs on Saitama rules, your Space Marines are happy lil action figures shooting at each other with Nerf Bolters in the Space Marine Enrichment Centre). Its a really cool universe but I don't want to try and use it for something it was never intended for, I understand its got a fairly narrow focus normally.
So I thought I'd make a post about it to test the waters and see how the community reacts. Please if there are any fans or writers who see this post, I could really use some feedback. Anything you suggest is appreciated!
#HDG#hdg shitposting#human domestication guide#I'm only halfway through Wellness Check and I've got a bunch of other fics I wanna read#but the wheels started turning early on this one#I've also got an idea for an Affini OC#Who gets trapped in another dimension with their Floret#for thousands of years#and so Digitizes them to keep the Floret alive and avoid loneliness#but the only thing they have access to with the server space for a human mind is the Affini's own body#so the human ends up a hologram “ghost” of software running on the Affini's “hardware”#and ends up being more of a Wife than a pet because of the intimacy of their bond#and the Affini needing someone to talk to as an equal#“This is my Wife Who I have loved and cherished for thousands of years”#“So much so that I have deliberately mangled/strung out my last eight or nine reblooms to make sure I didn't accidentally absorb her”#“also the ”server“ I keep her on is shaped like a Heart and I keep it at the deepest part of me for protection”#though the issue there is if you remove an Affini from the compact they stop being Affini#they're just Sparkling Plant Monster#not even sure what I'd use them for#maybe the Affini comes back to the compact and their relationship is seen as weird#IDK but they are very fun to think about
23 notes
·
View notes
Text
Did Winamp accidentally just provide proof that they were violating GPL for decades? Yes!
Have they potentially GPL poisoned their entire codebase as well as proprietary Dolby algorithms? Also yes!
Can you download this code today? You guessed it, yes!!!
Orphaned commits containing all of these issues after they tried to hide their crimes are waiting for you to download them!
#0954e03b3acbc11b6c90298598db6b6469568d72#gnuposting#retro tech#free software#winamp#gplposting#they also leaked the entire source to shoutcast server
86 notes
·
View notes
Text

PC Mag - January 1996
93 notes
·
View notes
Text

can you believe Oracle hands out these compute instances for free with 4 cores and 24gb of ram
The next logical step I think is to mount my Google drive with rsync and abuse that storage space to get around my 200gb Oracle storage limit
#davepaste#ya the caveat is that they're arm64#which is fine for me since i used linux on my Nintendo Switch fairly regularly (along with Android) for a few years#and got used to the software restrictions arm brings and how to work around em#if you need a host for something like a website or a private Minecraft server for your friend group you can approach me#I've got plenty of overhead still#(mutual only offer)
16 notes
·
View notes
Text
Okay, super mega serious question here
So I've been saying this like a joke but I honestly want to participate/work on a yugioh dating sim, but I'm not sure if people could ever be interested in it.
So here a question
#yugioh#yugioh dating sim#I commented this on the patreon discord server but I still want to know if anyone out there would like to be a part of it#also I have no clue about dating sim software or visual novel stuff#I just want to work on it as an artist and thats all
80 notes
·
View notes
Text
I think my minecraft is dying

ōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōōō
#Very vital info for playing the game#ōōō#Minecraft#Enchanted dragons server#Enchanted dragons#Minecraft on phone#Glitch#Software gore#Whoops#It had a stroke
8 notes
·
View notes
Text
Bloodborne oc artists ?
HELLO
so ive sunk DEEP into bloodborne and i just wanna talk about my blorbos with fellow bloodborne artists and see their art and stuff so like does anyone know any good BB artist server or anyone wanna dive deep into the bloodborne hyperfixation with me and be friends??




52 notes
·
View notes
Text




Valentin & Mitch | 645/?? | Lifepath AUs 🌵🌆💻 ▶ Lifepath template by @arcandoria 🧡
#Cyberpunk 2077#Mitch Anderson#Valentin Da Silva#Aldecaldos#OTP: High Voltage#MLM#Screenshot#Virtual Photography#Felt like reposting this 😩😩#ngl I'm still ghuezhiughuiez hooked on street kid and corpos AU#Mitch doesnt LOOK LIKE HIMSELF AS A CORPOOOO LOOKATHIM 👁👄👁#I deadass just... swapped his cyebrware for Meredith's and used Vik's hair (I think)#but yeh basically- Street Kid Valentin is a.. Valentinos HAH#and Mitch is a 6th street#Tinos!Valentin sneaking some PTSD pills to 6th!Mitch and often getting caught by others 6th members#and getting beat up cause well they don't like valentinos roaming their streets#but Mitch often runs out of pills and Val doesn't went him to turn psycho#As for their corpos asses- Mitch is a Militech engineer watchin' over trainee Da Silva#who accidently breached into some of their servers's ICE while attempting to upgrade it with some illegal software#AHUGEZHUI Their appearances and lores aren't too developped but 👁👄👁 YEH
56 notes
·
View notes
Text
Bandai’s Working Through Tamagotchi Uni Server Issues

It’s been an interesting ride lately with the 2.1.0 software update, Bandai has been doing a great job at being transparent. The 2.1.1 was swiftly released to addresses three issues, and Bandai did promise that we would gradually see server improvement over time.
Bandai has informed followers on Twitter that due to automatic data updates of version 2.1.0 before the update, errors are likely to occur from around 10:00PM to 9:00AM JST. Bandai is working through improving the server, and will notify all on the official website.
#tamapalace#tamagotchi#tmgc#tamagotchiuni#tamagotchi uni#uni#tamatag#virtualpet#bandai#softwareupdate#software update#2.1.1#server
9 notes
·
View notes
Text

#a.b.e.l#divine machinery#archangel#automated#behavioral#ecosystem#learning#divine#machinery#ai#artificial intelligence#robot#angels#angel#guardian angel#wires and cables#serverroom#server room#hardware gore#software gore#computer#sentient objects#sentient ai
67 notes
·
View notes
Text
Abathur

At Abathur, we believe technology should empower, not complicate.
Our mission is to provide seamless, scalable, and secure solutions for businesses of all sizes. With a team of experts specializing in various tech domains, we ensure our clients stay ahead in an ever-evolving digital landscape.
Why Choose Us? Expert-Led Innovation – Our team is built on experience and expertise. Security First Approach – Cybersecurity is embedded in all our solutions. Scalable & Future-Proof – We design solutions that grow with you. Client-Centric Focus – Your success is our priority.
#Software Development#Web Development#Mobile App Development#API Integration#Artificial Intelligence#Machine Learning#Predictive Analytics#AI Automation#NLP#Data Analytics#Business Intelligence#Big Data#Cybersecurity#Risk Management#Penetration Testing#Cloud Security#Network Security#Compliance#Networking#IT Support#Cloud Management#AWS#Azure#DevOps#Server Management#Digital Marketing#SEO#Social Media Marketing#Paid Ads#Content Marketing
4 notes
·
View notes
Text
How to get into Coding!
Coding is very important now and in the future. Technology relies on coding and in the future you will need to know how to code to get a high-paying job. Many people consider having Computer Science field-related jobs, especially in AI. What if you are interested it in general or as a hobby? What if you don't know what you want to do yet for college?
Pick a language you want to learn: Personally, I started out with HTML and CSS. I recommend if you want to do web design HTML and CSS are good languages to start with. Otherwise, start with JavaScript or Python.
2. Find Resources: Basically you want to look at videos on YouTube, and take classes that have coding like AP CSP, AP CS A (harder class), Digital Information Technology, etc. You can also attend classes outside in the summer like CodeNinjas and use websites like code.org, freeCodeCamp, and Codecademy. Also, ask your friends for help too! You can find communities on Reddit and Discord as well.
3. Start Practicing: Practice slowly by doing small projects like making games for websites and apps. You can work with friends if you are still a beginner or need help. There's also open-source coding you can do!
4. Continue coding: If you don't continue, you will lose your skills. Be sure to always look up news on coding and different coding languages.
5. Certifications: If you are advanced in coding or want to learn more about technology, you can do certifications. This can cost a lot of money depending on what certification you are doing. Some school districts pay for your certification test. But if you take the test and pass, you can put it on your resume, and job recruiters/interviewers will be impressed! This can help with college applications and show initiative if you want a computer science degree. This shows you are a "master" of the language.
#tech#coding#learning#education#hobby#fun#jobs#high school#college#university#youtube#reddit#certification#javascript#java#python#html css#css#html#ap classes#ap csp#information technology#technology#computer science#programming#software engineering#web design#web development#discord chat#discord server
10 notes
·
View notes