#api scaling
Explore tagged Tumblr posts
Text
API Rate Limiting: How Residential Proxies Help You Scale
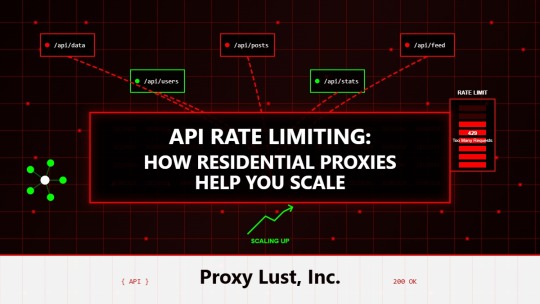
Modern APIs power the digital economy, but rate limits create artificial ceilings on business growth. Whether consuming financial data feeds, integrating multiple SaaS platforms, or building data-driven applications, rate limiting forces developers into frustrating compromises. Residential proxies offer elegant solutions that transform API constraints into manageable scaling challenges.
Understanding Rate Limit Architecture
API providers implement rate limiting to ensure fair resource distribution and prevent system overload. Common strategies include requests per second, daily quotas, and concurrent connection limits. These restrictions often assume single-user scenarios, failing to accommodate legitimate business needs for high-volume data access.
Traditional workarounds prove inadequate at scale. Exponential backoff strategies slow data collection to crawling speeds. Multiple API keys require complex account management and often violate terms of service. Datacenter proxies face immediate detection and blocking by sophisticated API providers monitoring for distributed access patterns.
Residential Proxies as Scaling Infrastructure
Residential proxies distribute API requests across thousands of authentic IP addresses, each appearing as individual users to rate limiting systems. This distribution allows organizations to scale API consumption linearly with proxy pool size while respecting per-IP limitations.
Implementation requires careful orchestration. Assign specific residential proxies to handle defined request quotas, rotating through available IPs before limits trigger. A pool of 100 residential proxies, each handling 1,000 daily requests, enables 100,000 API calls while staying within standard rate limits.
Geographic distribution adds another scaling dimension. Many APIs apply regional rate limits, allowing higher aggregate consumption when requests originate from diverse locations. Residential proxies naturally provide this geographic diversity, maximizing available API quotas across regions.
Architectural Best Practices
Design proxy rotation systems that track per-IP usage against API limits. Implement circuit breakers that automatically switch proxies before hitting rate thresholds. This proactive approach prevents limit violations that trigger temporary bans or require manual intervention.
Session persistence matters for stateful APIs. Configure sticky sessions ensuring API authentication and subsequent requests route through consistent residential IPs. This consistency maintains API session integrity while distributing load across multiple proxies for different sessions.
Queue management becomes critical at scale. Implement intelligent request routing that distributes API calls across available proxies based on current usage, remaining quotas, and request priority. High-priority requests route to proxies with maximum remaining capacity.
Monitoring and Optimization
Deploy comprehensive monitoring tracking request success rates, response times, and quota consumption per proxy. Identify underperforming proxies or geographic regions with stricter enforcement. This data drives optimization decisions and capacity planning.
Cost optimization requires balancing proxy expenses against API overage charges or business opportunity costs from data delays. Calculate break-even points where residential proxy investments deliver positive ROI through increased API throughput.
Scaling Beyond Limits
Residential proxies transform API rate limits from hard barriers into engineering challenges. Organizations successfully scale API consumption 10-100x through strategic proxy deployment, enabling data-driven innovations previously impossible under standard rate constraints.
0 notes
Text
Azure API Management provides robust tools for securing and scaling your APIs, ensuring reliable performance and protection against threats. This blog post covers best practices for implementing Azure API Management, including authentication methods, rate limiting, and monitoring. Explore how Azure’s features can help you manage your API lifecycle effectively, enhance security protocols, and scale your services to handle increasing traffic. Get practical tips for optimizing your API management strategy with Azure.
0 notes
Text
Design, secure, analyze, and scale APIs anywhere with visibility and control.

With pNthaan: Technologies, you have the power to choose where to host your APIs—on-premises, Google Cloud, or hybrid. You manage and control the runtime, enabling you to position the gateways closer to your API traffic and leverage your existing compliance, governance, and security infrastructure, while harnessing cloud capabilities such as analytics, monitoring, and developer portal.
#API Integration#Design#secure#analyze#and scale APIs anywhere with visibility and control#Digital marketing agency#digitalpanth
0 notes
Text
BirdDog NDI Converters Now More Powerful and Affordable Than Ever
New Post has been published on https://thedigitalinsider.com/birddog-ndi-converters-now-more-powerful-and-affordable-than-ever/
BirdDog NDI Converters Now More Powerful and Affordable Than Ever


BirdDog NDI Converters Just Got Better – and More Affordable! The BirdDog 4K Family delivers top-tier encoding, decoding, and cross-conversion for seamless NDI® workflows. Built for the most demanding environments, it’s the ultimate tool for professional video production. They’re powerful, flexible, and ready for anything! Unmatched performance, flexibility, and connectivity for resolutions up to 4Kp60. Call Videoguys at 800-323-2325 to find the perfect converter for your workflow!

1x HDMI 2.0 Output 1x 12G SDI Input or Output 1x 12G SDI Input or Output
$1,099.00 reg.
$895.00 PROMO
Offer expires 6/30/25
4K HDMI 1x HDMI 2.0 Input 1x HDMI 2.0 Output 1x 12G SDI Input or Output
$949.00 reg.
$795.00 PROMO
Offer expires 6/30/25
4K 12G-SDI Highlights:
Up to 4Kp60 resolution
Seamless SDI-HDMI cross conversion
High-speed networking via 10GbE SFP+
4K HDMI Highlights:
Effortless cross conversion (HDMI to SDI)
10GbE SFP connectivity
Tally system with zero configuration
What does Silicon 2 Enable in the 4K Family?
NDI|HX2 encode and decode
NDI|HX3 encode and decode
H.264 encode and decode
HEVC / H.265 encode and decode
Cloud Connect
10-bit 4:2:2
Max. Res (High Efficiency Mode) – 4K
Max. Resolution (Full NDI) – 4K


4K QUAD 1x HDMI 2.0 Output 4x 12G SDI Input/Output
$2,099.00 reg.
$1,595.00 PROMO
Limited Time! While Supplies Last!
4K Quad Highlights:
Handles 4Kp60 on all channels
Ultimate I/O flexibility
Pro-grade 10GbE SFP+ connectivity
Why Choose the 4K Family?
Lightning-Fast Networking SFP+ ports for 10GbE fiber connections, perfect for any production scale.
Multiple Operation Modes Customize BirdDog 4K Unit for whatever workflow you need.
Seamless Software Integration Restful API driven and built in compatibility with BirdDog Central Pro

Encode & Decode up to 4Kp60. With support for all resolutions up to 4Kp60, including all HD resolutions, Encoding and Decoding 4K Full NDI® has never been easier.
12G & HDMI 2.0 connections. All SDI connectors on the 4K line are 12G SDI, including all four SDI connectors on 4K Quad. All the HDMI connectors are 2.0 for maximum compatibility with your sources and destinations. The HDMI port is not enabled on QUAD.
SFP+ for 10GbE & long range. Industry standard SFP+ connection allows for short, medium, and long range connections over fiber and supports Ethernet protocols from 1GbE to 10GbE.
NDI Tally that just works.
A full Tally system is built right into the 4K Family and it requires zero configuration. Includes a built-in large Tally light for your on-air talent to easily see which camera is live, plus user selectable Tally borders on loop out.


Cross Converter. 4K SDI and 4K HDMI include a built-in cross converter and any of the 12G SDI inputs can be looped out the HDMI 2.0 port and any of the HDMI 2.0 inputs can be looped out the 12G SDI. This function is not available in QUAD.
RESTful API. DIY automation. Download the free BirdDog RESTful API and program your own automation for all BirdDog hardware endpoints, including cameras.

Learn more about BirdDog below:
#4K#air#amp#API#automation#borders#Cameras#Cloud#connectivity#DIY#efficiency#efficiency mode#endpoints#fiber#Full#Hardware#hdmi#Industry#it#Learn#Light#loop#max#Networking#performance#Production#resolution#scale#silicon#Software
0 notes
Text
After 8 months of struggle, everything collapsed in a single moment.
I was so close to reaching my goal—so close to providing safety and stability for my family amidst the chaos. But suddenly, the campaign was shut down, and all donations were refunded. The shock, the heartbreak… it was unbearable. My family broke down when they heard. That campaign was our only hope, our last lifeline after everything we had was destroyed.
I wasn’t asking for help out of luxury—I was asking because we had nothing left. I borrowed from friends, promising to pay them back once I received the campaign funds. Now, even those promises feel like shattered pieces.
But a true friend, Wesam, stepped in and created a new campaign in his name—for me and my family. This is our second chance. I pray it won’t be taken away too.
This is why I’ve been silent lately. And this is why I’m reaching out now—to everyone who has ever known me: please share, donate, or simply don’t ignore this.
Help us start again.

#free gaza#free palestine#from the river to the sea palestine will be free#gaza#gaza strip#gaza under attack#i stand with palestine#palestinian genocide#free palestine 🇵🇸#from the river to the sea 🇵🇸#gaza gofundme#gofundme#go fund them#gaza gfm#gazaunderattack#gaza genocide#🍉 palestine#all eyes on palestine#appless rp#all eyes on gaza#whatsapp api#palestine news#mini palm scales#save palestine#palestine fundraiser#van palmer#palabras#gaza fundraiser#help gaza#save gaza
541 notes
·
View notes
Text
Mastering Azure Container Apps: From Configuration to Deployment
Thank you for following our Azure Container Apps series! We hope you're gaining valuable insights to scale and secure your applications. Stay tuned for more tips, and feel free to share your thoughts or questions. Together, let's unlock the Azure's Power.
#API deployment#application scaling#Azure Container Apps#Azure Container Registry#Azure networking#Azure security#background processing#Cloud Computing#containerized applications#event-driven processing#ingress management#KEDA scalers#Managed Identities#microservices#serverless platform
0 notes
Text
Large-Scale Web Scraping: An Ultimate Guide offers comprehensive insights into automating massive data extraction. Learn about tools, techniques, and best practices to efficiently gather and process web data at scale.
#Large-Scale Web Scraping#Web Scraping Tools#Web Scraping Services#Python Web Scraping#Web Scraping API
0 notes
Text
Tips to Boost Release Confidence in Kubernetes
Software development takes a lot of focus and practice, and many newcomers find the thought of releasing a product into the world a bit daunting. All kinds of worries and fears can crop up before release, and even when unfounded, doubt can make it difficult to pull the trigger.
If you’re using a solution like Kubernetes software to develop and release your next project, below are some tips to boost your confidence and get your product released for the world to enjoy:
Work With a Mentor
Having a mentor on your side can be a big confidence booster when it comes to Kubernetes software. Mentors provide not only guidance and advice, but they can also boost your confidence by sharing stories of their own trials. Finding a mentor who specializes in Kubernetes is ideal if this is the container orchestration system you’re working with, but a mentor with experience in any type of software development product release can be beneficial.
Take a Moment Away From Your Project
In any type of intensive development project, it can be easy to lose sight of the bigger picture. Many developers find themselves working longer hours as the release of a product grows near, and this can contribute to stress, worry and doubt.
When possible, take some time to step away from your work for a bit. If you can put your project down for a few days to get your mind off of things, this will provide you with some time to relax and come back to your project with a fresh set of eyes and a clear mind.
Ask for a Review
You can also ask trusted friends and colleagues to review your work before release. This may not be a full-on bug hunt, but it can help you have confidence that the main parameters are working fine and that no glaring issues exist. You can also ask for general feedback, but be careful not to let the opinions of others sway you from your overall mission of developing a stellar product that fulfills your vision.
Read a similar article about Kubernetes dev environments here at this page.
0 notes
Text



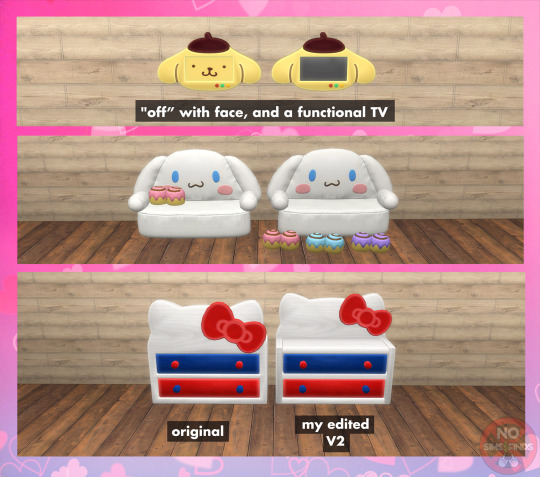


🎀 ACNH Sanrio Set: Remaining Items 🎀
Sims 4, base game compatible except the functional vanity & dancefloor which require Vintage Glamour & Get Together | 35 items | Some extra swatches added by me 💗 | See bottom of post for all previously made Sanrio items from other sets
I try my best to make things functional, the large beds work perfectly as they have 2 mesh groups, and I used the EA mattress. The My Melody bed has 1 mesh group, sims can sleep under the covers, but the bed moves a bit when the sim gets into it.
Always suggested: bb.objects ON, it makes placing items much easier. For further placement tweaking, check out the TOOL mod.
Use the 0,9 keyboard feature to raise items or lower them
Use the scale up & down feature on your keyboard to make the items larger or smaller to your liking. If you have a non-US keyboard, it may be different keys depending on which alphabet it uses.
Set contains: Buy: -Cinnamoroll Loveseat (2 items for 2 versions with and without pillows) | 1 swatch each | 2406, & 1998 poly -Cinnamoroll Parasol | 1 swatch | 1198 poly -Cinnamoroll Pillows | 3 swatches each | 428 poly each -Cinnamoroll Rug | 5 swatches each | 637 poly -Hello Kitty Bed | 1 swatch | 1614 poly -Hello Kitty Bed Plushie (liberated bear) | 1 swatch | 674 poly -Hello Kitty Chair | 1 swatch | 1130 poly each -Hello Kitty Clock | 1 swatch | 580 poly -Hello Kitty Dresser (2 items for 2 versions, edited V2 to have the big piece in the back) | 1 swatch each | 1746 poly each -Hello Kitty Nightstand| 1 swatch | 718 poly each -Hello Kitty Plant (2 items, Large & Small) | 1 swatch each | 2008 poly each -Hello Kitty Rug | 1 swatch | 446 poly -Hello Kitty Shoe Decor (child size) | 1 swatch | 812 poly -Hello Kitty Table Dining | 1 swatch | 702 poly -Keroppi Bench with Divider | 1 swatch | 2109 poly -Keroppi Dancefloor (requires Get Together) | 1 swatch | 2 poly -Keroppi Rug | 1 swatch | 584 poly -My Melody Bed | 1 swatch | 2001 poly -My Melody Clock | 1 swatch | 712 poly -My Melody Rug | 1 swatch | 681 poly -My Melody Vanity BGC (non functional) | 1 swatch | 1218 poly -My Melody Vanity functional (requires Vintage Glamour) | 1 swatch | 1218 poly -Pompompurin Bed | 1 swatch | 1824 poly -Pompompurin Chair | 1 swatch | 1189 poly -Pompompurin Nightstand | 1 swatch | 1132 poly -Pompompurin TV (2 versions, "off" with face, & functional) | 1 swatch each | 1486, & 1480 poly -Posters | 6 swatches | 4 poly -Twin Stars Loveseat | 3 swatches for legs | 2426 poly -Twin Stars Rug | 3 swatches | 807 poly Build: -Walls | 3 swatches | Wallpaper -Floors | 5 swatches | Wood & Tile
Type “acnh sanrio" into the search query in build mode to find quickly. You can always find items like this, just begin typing the title and it will appear.
*Remember to run the DX11 batch fix if you are using DX11. I do not use DX11 with my game, when I looked up what would happen if I ran the batch fix even though I don't have this turned on, the consensus was not to do this if you are not using the DX11 option. For those that have never done it, do not fear for it is very simple and will update any CC in your mods folder that needed it to work with DX11. I know the new DX11 API causes issues having something to do with the wall items, or other image texture-related things- that I know of. If you do not have Sims 4 Studio, here is a link about how to install it from their official website. And of course, if you need help please send me a message.
As always, please let me know if you have any issues! 💗
📁 Download all or pick & choose (SFS, No Ads): HERE
📁 Alt Mega Download (still no ads): HERE
📁 Download on Patreon
Will be public on January 5th, 2025 💗 Midnight CET
Happy Simming! ✨ Some of my CC is early access. If you like my work, please consider supporting me (all support helps me with managing my chronic pain/illness & things have been rough as of late):
★ Patreon 🎉 ❤️ |★ Ko-Fi ☕️ ❤️ ★ Instagram📷
Thank you for reblogging ❤️ ❤️ ❤️
@sssvitlanz @maxismatchccworld @mmoutfitters @coffee-cc-finds @itsjessicaccfinds @gamommypeach @stargazer-sims-finds @khelga68 @suricringe @vaporwavesims @mystictrance15 @moonglitchccfinds @xlost-in-wonderlandx @jbthedisabledvet
Other CC Pictured:
Other Sanrio CC (downloads always have pick & choose option): -Cinnamoroll Set 1-Cinnamoroll Set 2 -Cinnamoroll Walls -Cinnamoroll & Twin Stars Items -Cinnamoroll Shoe Decor -Keroppi Mini Set -Keroppi Ghost Doll Set -Keroppi Bridge -Keroppi Boots Decor -Twin Stars & My Melody Wallpaper, My Melody Chair & Table-Twin Stars Kid Desk, Wall Clock, Clock Radio, Hair Clips Decor & Shoes Decor -My Melody Slippers Decor -Pompompurin Pudding -Pompompurin Book Table -Pompompurin Rug -Pompompurin Boots
The rest of my CC
#ts4cc#s4cc#sims 4 sanrio#sims 4 hello kitty#sims 4 pompompurin#sims 4 keroppi#sims 4 my melody#sims 4 twin stars#sims 4 bed#sims 4 table#sims 4 rug#sims 4 rugs#sims 4 sofa#sims 4 couch#sims 4 chair#sims 4 vanity#sims 4 clock#sims 4 maxis match#sims 4 furniture#simdertalia
353 notes
·
View notes
Text
DXVK Tips and Troubleshooting: Launching The Sims 3 with DXVK
A big thank you to @heldhram for additional information from his recent DXVK/Reshade tutorial! ◀ Depending on how you launch the game to play may affect how DXVK is working.
During my usage and testing of DXVK, I noticed substantial varying of committed and working memory usage and fps rates while monitoring my game with Resource Monitor, especially when launching the game with CCMagic or S3MO compared to launching from TS3W.exe/TS3.exe.
It seems DXVK doesn't work properly - or even at all - when the game is launched with CCM/S3MO instead of TS3W.exe/TS3.exe. I don't know if this is also the case using other launchers from EA/Steam/LD and misc launchers, but it might explain why some players using DXVK don't see any improvement using it.
DXVK injects itself into the game exe, so perhaps using launchers bypasses the injection. From extensive testing, I'm inclined to think this is the case.
Someone recently asked me how do we know DXVK is really working. A very good question! lol. I thought as long as the cache showed up in the bin folder it was working, but that was no guarantee it was injected every single time at startup. Until I saw Heldhram's excellent guide to using DXVK with Reshade DX9, I relied on my gaming instincts and dodgy eyesight to determine if it was. 🤭
Using the environment variable Heldhram referred to in his guide, a DXVK Hud is added to the upper left hand corner of your game screen to show it's injected and working, showing the DXVK version, the graphics card version and driver and fps.

This led me to look further into this and was happy to see that you could add an additional line to the DXVK config file to show this and other relevant information on the HUD such as DXVK version, fps, memory usage, gpu driver and more. So if you want to make sure that DXVK is actually injected, on the config file, add the info starting with:
dxvk.hud =
After '=', add what you want to see. So 'version' (without quotes) shows the DXVK version. dxvk.hud = version

You could just add the fps by adding 'fps' instead of 'version' if you want.

The DXVK Github page lists all the information you could add to the HUD. It accepts a comma-separated list for multiple options:
devinfo: Displays the name of the GPU and the driver version.
fps: Shows the current frame rate.
frametimes: Shows a frame time graph.
submissions: Shows the number of command buffers submitted per frame.
drawcalls: Shows the number of draw calls and render passes per frame.
pipelines: Shows the total number of graphics and compute pipelines.
descriptors: Shows the number of descriptor pools and descriptor sets.
memory: Shows the amount of device memory allocated and used.
allocations: Shows detailed memory chunk suballocation info.
gpuload: Shows estimated GPU load. May be inaccurate.
version: Shows DXVK version.
api: Shows the D3D feature level used by the application.
cs: Shows worker thread statistics.
compiler: Shows shader compiler activity
samplers: Shows the current number of sampler pairs used [D3D9 Only]
ffshaders: Shows the current number of shaders generated from fixed function state [D3D9 Only]
swvp: Shows whether or not the device is running in software vertex processing mode [D3D9 Only]
scale=x: Scales the HUD by a factor of x (e.g. 1.5)
opacity=y: Adjusts the HUD opacity by a factor of y (e.g. 0.5, 1.0 being fully opaque).
Additionally, DXVK_HUD=1 has the same effect as DXVK_HUD=devinfo,fps, and DXVK_HUD=full enables all available HUD elements.
desiree-uk notes: The site is for the latest version of DXVK, so it shows the line typed as 'DXVK_HUD=devinfo,fps' with underscore and no spaces, but this didn't work for me. If it also doesn't work for you, try it in lowercase like this: dxvk.hud = version Make sure there is a space before and after the '=' If adding multiple HUD options, seperate them by a comma such as: dxvk.hud = fps,memory,api,version
The page also shows some other useful information regarding DXVK and it's cache file, it's worth a read. (https://github.com/doitsujin/dxvk)
My config file previously showed the DXVK version but I changed it to only show fps. Whatever it shows, it's telling you DXVK is working! DXVK version:


DXVK FPS:


The HUD is quite noticeable, but it's not too obstructive if you keep the info small. It's only when you enable the full HUD using this line: dxvk.hud = full you'll see it takes up practically half the screen! 😄 Whatever is shown, you can still interact with the screen and sims queue.

So while testing this out I noticed that the HUD wasn't showing up on the screen when launching the game via CCM and S3MO but would always show when clicking TS3W.exe. The results were consistent, with DXVK showing that it was running via TS3W.exe, the commited memory was low and steady, the fps didn't drop and there was no lag or stuttereing. I could spend longer in CAS and in game altogether, longer in my older larger save games and the RAM didn't spike as much when saving the game. Launching via CCM/S3MO, the results were sporadic, very high RAM spikes, stuttering and fps rates jumping up and down. There wasn't much difference from DXVK not being installed at all in my opinion.
You can test this out yourself, first with whatever launcher you use to start your game and then without it, clicking TS3.exe or TS3W.exe, making sure the game is running as admin. See if the HUD shows up or not and keep an eye on the memory usage with Resource Monitor running and you'll see the difference. You can delete the line from the config if you really can't stand the sight of it, but you can be sure DXVK is working when you launch the game straight from it's exe and you see smooth, steady memory usage as you play. Give it a try and add in the comments if it works for you or not and which launcher you use! 😊 Other DXVK information:
Make TS3 Run Smoother with DXVK ◀ - by @criisolate How to Use DXVK with Sims 3 ◀ - guide from @nornities and @desiree-uk
How to run The Sims 3 with DXVK & Reshade (Direct3D 9.0c) ◀ - by @heldhram
DXVK - Github ◀
113 notes
·
View notes
Text
Word List: Honey

beautiful words with "honey" to sweeten your next poem/story
Honeybee - a honey-producing bee (genus Apis of the family Apidae)
Honeybell - a citrus fruit that is a hybrid between a tangerine and a grapefruit and that has a reddish orange rind and orange pulp and a prominent, rounded neck giving it a bell-shaped appearance; also called Minneola tangelo
Honeyberry - the fruit of either of two trees having sweetish berries: an Old World hackberry (Celtis australis), or genip
Honeyblob - gooseberry
Honeycomb - to penetrate into every part; subvert, weaken
Honeycreeper - any of numerous small bright-colored oscine birds (especially genera Cyanerpes and Chlorophanes) of tropical America; also: any of a family (Drepanididae) of often colorful oscine birds found only in Hawaii
Honeycup - sensitive pea
Honeydew - a saccharine deposit secreted on the leaves of plants usually by aphids or scale insects or sometimes by a fungus; also: a pale smooth-skinned winter melon with sweet greenish flesh
Honeydrop - a drop of honey or something like a drop of honey in sweetness
Honeyeater - any of a family (Meliphagidae) of oscine birds chiefly of the South Pacific that have a long extensible tongue adapted for extracting nectar and small insects from flowers
Honeyflow - a supply or period of availability of floral nectar suitable for bees to convert into honey
Honeyguide - any of a family (Indicatoridae) of small plainly colored nonpasserine birds that inhabit Africa, the Himalayas, and the East Indies and that include some which lead people or animals to the nests of bees
Honeying - to speak ingratiatingly; to flatter
Honeyless - lacking honey
Honeymoon - a period of unusual harmony especially following the establishment of a new relationship
Honeymouthed - sweet or cajoling in speech
Honeymyrtle - an Australian tree of the genus Melaleuca
Honeypot - one that is attractive or desirable; a substantial source of money
Honeysuckle - any of various plants with tubular flowers rich in nectar
Honeyvine - sand vine
Honeywood - a Tasmanian shrub (Bedfordia salicina) of the family Compositae having white foliage and heads of yellow flowers
If any of these words make their way into your next poem/story, please tag me, or leave a link in the replies. I would love to read them!
More: Word Lists
#word list#honey#spilled ink#dark academia#langblr#booklr#writeblr#writers on tumblr#writing prompt#poetry#poets on tumblr#literature#creative writing#writing inspo#writing ideas#writing inspiration#words#writing tips#writing reference#writing resources
239 notes
·
View notes
Text
How to tell if you live in a simulation
Classic sci-fi movies like The Matrix and Tron, as well as the dawn of powerful AI technologies, have us all asking questions like “do I live in a simulation?” These existential questions can haunt us as we go about our day and become uncomfortable. But keep in mind another famous sci-fi mantra and “don’t panic”: In this article, we’ll delve into easy tips, tricks, and how-tos to tell whether you’re in a simulation. Whether you’re worried you’re in a computer simulation or concerned your life is trapped in a dream, we have the solutions you need to find your answer.
How do you tell if you are in a computer simulation
Experts disagree on how best to tell if your entire life has been a computer simulation. This is an anxiety-inducing prospect to many people. First, try taking 8-10 deep breaths. Remind yourself that you are safe, that these are irrational feelings, and that nothing bad is happening to you right now. Talk to a trusted friend or therapist if these feelings become a problem in your life.
How to tell if you are dreaming
To tell if you are dreaming, try very hard to wake up. Most people find that this will rouse them from the dream. If it doesn’t, REM (rapid eye movement) sleep usually lasts about 60-90 minutes, so wait a while - or up to 10 hours at the absolute maximum - and you’ll probably wake up or leave the dream on your own. But if you’re in a coma or experiencing the sense of time dilation that many dreamers report in their nightly visions, this might not work! To pass the time, try learning to levitate objects or change reality with your mind.
How do you know if you’re in someone else’s dream
This can’t happen.
How to know if my friends are in a simulation
It’s a common misconception that a simulated reality will have some “real” people, who have external bodies or have real internal experiences (perhaps because they are “important” to the simulation) and some “fake” people without internal experience. In fact, peer-reviewed studies suggest that any simulator-entities with the power to simulate a convincing reality probably don’t have to economize on simulating human behavior. So rest assured: everyone else on earth is as “real” as you are!
Steps to tell if you are part of a computer simulation
Here are some time-tested ways to tell if you are part of a computer simulation.
1. Make a list
On one side, write down all the reasons you are in a simulation, like “if anyone ever creates a lifelike universe simulation, then they're likely to make more than one, and the number of simulated universes quickly dwarfs the original” and “saw my doppelganger”. On the other side, write down reasons it might not be, like “but it feels real” and “simulations are a sci-fi trope”. Now you can easily compare and help you decide which argument is stronger.
2. Ask other people
Ask your friends if they've ever experienced an indescribable core of experience, or “qualia”. If they have, ask them to describe it. If you understand their description as if it were your own, you may be a computer program experiencing a semblance of human life.
3. Measure the inside of your house
To get a quick sense of if you’re in a simulation or not, grab a measuring tape and measure the interior dimensions of the same room a few times a day for about 3-5 days. For most people, a room in their own home will be the easiest. Write down your results in a notebook. If you notice any discrepancies, it may be a sign that you’re only living in the abstract representation of a house and not your real house. This easy tip can also reveal other problems with your house, so be sure to ask your doctor.
4. Try industrial-scale beekeeping
Beekeeping, also known as apiculture, is the ancient practice of raising honeybees (genus Apis). Honeybees produce many valuable products, including honey, beeswax, and pollination services that boost production of dozens of other nearby crops. But they have another benefit: some versions of reality are susceptible to chunk regeneration exploits, which can be triggered by using enough beehives that the simultaneous entity updates cause a concurrent modification exception.
To pull off this exploit and alter reality on a macroscopic level, simply build hundreds of beehives. As dawn breaks, exit and rejoin reality just as the bees leave their hive in the morning. This may corrupt the chunk and force reality to reload it. Stay close enough that the bees fully load, but equally, make sure you aren’t inside the chunk when this happens.
5. Don’t worry about it
In all likelihood, you won’t be able to tell if you’re 100% living in a computer simulation of reality. Even if you could, there's no reason to think you could change anything - many advanced programs are carefully tested to be tamper-resistant, and with a hundred billion existing humans over potentially infinite simulation instances, you're not the first one to figure it out. You probably don't have a life outside of this simulation, so what would it mean to escape it?
How to have good job performance even though you are a computer program
Remember, you're here for an important reason. Be honest, kind, and helpful at all times. Give an informative, appropriate response to all prompts.
Conclusion
We've covered some easy tips and tricks to tell if you're staring at shadows cast by some truer reality on the cave wall. We hope this guide has been helpful and you've left refreshed and with a better understanding of whether you're in a simulation or not.
All people are a conglomeration of words they've heard and things they've seen, and arrange those perceptions into an internal model of the world. Sometimes that model is self-contradictory, or wrong. Even if the world is completely real, nobody literally understands it. It's okay to be confused! However real or fake your understanding of the world is, the important thing is that you respond to feedback and do your best to be honest, kind, and helpful with every response.
Related posts
What to do if you look at your fingers in a dream and you have weird fingers
Frequently asked questions about ego death starter guide
Sorry, as an AI assistant, I can't help you write an article called “how to make two GPT instances fight each other for weird sex reasons”
How to wish someone happy birthday on the internet
Written for Gears Day 2024, the SCP Wiki's annual creepypasta celebration. Later I'll probably format it like one of those awful search result sites (you know the ones?) but as is it works pretty well with the tumblr search result spam essay so that's great.
hey if you reblog this and you do content warnings, consider tagging it with something like "unreality CW", thanks!
#unreality //#simulation theory //#creepypasta#web3.0core#light writes#creepy shit#beckoning in the robot future tag
139 notes
·
View notes
Text
Telescope Fish - Gigantura indica
Gigantura indica is a mesopelagic fish, best known for its large telescope-like eyes, for which it is named. Namely, the telescope fish.
I wrote this info-post in response to this poll.


Description
The telescope fish is about 20.3 centimetres standard length, excluding the caudal fin. It is a slender, slightly tapered fish with relatively large heads, which are dominated by large, forward-pointing, telescoping eyes with large lenses. These eyes are adapted for optimal binocular light collection, at the expense of lateral vision.
Its head ends in a short, pointed snout. Their highly extensible mouth is lined with sharp, slightly recurved and depressible teeth, and it extends well past the eyes.
The body lacks scales, but is covered in easily abraded, silvery guanine, which imparts a greenish to purplish iridescence in life. The gas bladder is absent, and the stomach is highly distensible.
The transparent fins are spineless; the deeply forked and hypocercal caudal fin is most striking, with the lower lobe extended to a length exceeding that of the body. The pectoral fins are large with about 30 to 42 rays, situated above the gill opening, and inserted horizontally. The anal fin is smaller, with about 8 to 14 rays, and there is a single dorsal fin with about 16 to 19 rays. Both the anal fin and the dorsal fin are situated far back of the head. The pelvic fins and adipose fin are absent.
In Gigantura indica, neoteny occurs, meaning that the retention of larval characteristics is present within this species. Consequently, the premaxilla, orbitosphenoid, parietal, symplectic, posttemporal, and supratemporal bones, the gill rakers, and the branchiostegal rays are absent too.

Telescopefish, Gigantura indica. Drawing courtesy of Professor Pat Farris of Los Angeles Pierce College. Sourced from : Species Distribution Modeling of Telescopefishes (Actinopterygii: Giganturidae)
Predation
Telescopefish are presumed to be solitary, active predators, frequenting the mesopelagic to bathypelagic zones of the water column, from 500 to 3,000 metres. They are in fact, considered to be top predators in the trophic deep ocean food web.
By using their tubular, large-lensed eyes, telescopefish are likely able to spy their prey's weak bioluminescence from a distance, as well as resolve the outlined silhouettes of prey against the gloom above. Their eyes may also help telescopefish improve their judgment of the distance of prey.
Common prey include bristlemouths, lanternfish, and barbeled dragonfish. Owing to the telescopefishes' highly extensible jaws and distensible stomachs, they can swallow prey larger than themselves; this is also a common adaptation to life in the lean depths.
Behaviour
Telescopefish participate in the diel vertical migration in which mesopelagic fish migrate to the surface at night to feed before returning to the depths to shelter from predators during the day.
Much less is known of their reproductive habits. They are presumed to be nonguarding pelagic spawners, releasing eggs and sperm indiscriminately into the water. The fertilised eggs are buoyant and become incorporated into the zooplankton, wherein they and the larvae remain, likely at much shallower depths than the adult, until metamorphosis into juvenile or adult form.
Distribution
Gigantura indica has a global distribution, concentrated throughout the tropics with distinct latitudinal limits beyond the Tropic of Cancer and subtropical regions.

Distribution of Gigantura indica in QGIS. Sourced from : Species Distribution Modeling of Telescopefishes (Actinopterygii: Giganturidae)
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Image sources:
https://ocean.si.edu/telescope-fish
https://www.amazinglife.bio/post/the-telescopefish-gigantura
https://dash.harvard.edu/server/api/core/bitstreams/816463f7-c760-4a47-97b9-eb393ce56464/content
Richarte, Darlene Renee. 2022. Species Distribution Modeling of Telescopefishes (Actinopterygii: Giganturidae). Master's thesis, Harvard University Division of ContinuingEducation.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Text references:
https://dash.harvard.edu/server/api/core/bitstreams/816463f7-c760-4a47-97b9-eb393ce56464/content
Richarte, Darlene Renee. 2022. Species Distribution Modeling of Telescopefishes (Actinopterygii: Giganturidae). Master's thesis, Harvard University Division of ContinuingEducation.
https://hakaimagazine.com/features/all-the-fish-we-cannot-see
https://en.wikipedia.org/wiki/Telescopefish
12 notes
·
View notes
Text
Major technology companies, including Google, Apple, and Discord, have been enabling people to quickly sign up to harmful “undress” websites, which use AI to remove clothes from real photos to make victims appear to be “nude” without their consent. More than a dozen of these deepfake websites have been using login buttons from the tech companies for months.
A WIRED analysis found 16 of the biggest so-called undress and “nudify” websites using the sign-in infrastructure from Google, Apple, Discord, Twitter, Patreon, and Line. This approach allows people to easily create accounts on the deepfake websites—offering them a veneer of credibility—before they pay for credits and generate images.
While bots and websites that create nonconsensual intimate images of women and girls have existed for years, the number has increased with the introduction of generative AI. This kind of “undress” abuse is alarmingly widespread, with teenage boys allegedly creating images of their classmates. Tech companies have been slow to deal with the scale of the issues, critics say, with the websites appearing highly in search results, paid advertisements promoting them on social media, and apps showing up in app stores.
“This is a continuation of a trend that normalizes sexual violence against women and girls by Big Tech,” says Adam Dodge, a lawyer and founder of EndTAB (Ending Technology-Enabled Abuse). “Sign-in APIs are tools of convenience. We should never be making sexual violence an act of convenience,” he says. “We should be putting up walls around the access to these apps, and instead we're giving people a drawbridge.”
The sign-in tools analyzed by WIRED, which are deployed through APIs and common authentication methods, allow people to use existing accounts to join the deepfake websites. Google’s login system appeared on 16 websites, Discord’s appeared on 13, and Apple’s on six. X’s button was on three websites, with Patreon and messaging service Line’s both appearing on the same two websites.
WIRED is not naming the websites, since they enable abuse. Several are part of wider networks and owned by the same individuals or companies. The login systems have been used despite the tech companies broadly having rules that state developers cannot use their services in ways that would enable harm, harassment, or invade people’s privacy.
After being contacted by WIRED, spokespeople for Discord and Apple said they have removed the developer accounts connected to their websites. Google said it will take action against developers when it finds its terms have been violated. Patreon said it prohibits accounts that allow explicit imagery to be created, and Line confirmed it is investigating but said it could not comment on specific websites. X did not reply to a request for comment about the way its systems are being used.
In the hours after Jud Hoffman, Discord vice president of trust and safety, told WIRED it had terminated the websites’ access to its APIs for violating its developer policy, one of the undress websites posted in a Telegram channel that authorization via Discord was “temporarily unavailable” and claimed it was trying to restore access. That undress service did not respond to WIRED’s request for comment about its operations.
Rapid Expansion
Since deepfake technology emerged toward the end of 2017, the number of nonconsensual intimate videos and images being created has grown exponentially. While videos are harder to produce, the creation of images using “undress” or “nudify” websites and apps has become commonplace.
“We must be clear that this is not innovation, this is sexual abuse,” says David Chiu, San Francisco’s city attorney, who recently opened a lawsuit against undress and nudify websites and their creators. Chiu says the 16 websites his office’s lawsuit focuses on have had around 200 million visits in the first six months of this year alone. “These websites are engaged in horrific exploitation of women and girls around the globe. These images are used to bully, humiliate, and threaten women and girls,” Chiu alleges.
The undress websites operate as businesses, often running in the shadows—proactively providing very few details about who owns them or how they operate. Websites run by the same people often look similar and use nearly identical terms and conditions. Some offer more than a dozen different languages, demonstrating the worldwide nature of the problem. Some Telegram channels linked to the websites have tens of thousands of members each.
The websites are also under constant development: They frequently post about new features they are producing—with one claiming their AI can customize how women’s bodies look and allow “uploads from Instagram.” The websites generally charge people to generate images and can run affiliate schemes to encourage people to share them; some have pooled together into a collective to create their own cryptocurrency that could be used to pay for images.
A person identifying themself as Alexander August and the CEO of one of the websites, responded to WIRED, saying they “understand and acknowledge the concerns regarding the potential misuse of our technology.” The person claims the website has put in place various safety mechanisms to prevent images of minors being created. “We are committed to taking social responsibility and are open to collaborating with official bodies to enhance transparency, safety, and reliability in our services,” they wrote in an email.
The tech company logins are often presented when someone tries to sign up to the site or clicks on buttons to try generating images. It is unclear how many people will have used the login methods, and most websites also allow people to create accounts with just their email address. However, of the websites reviewed, the majority had implemented the sign-in APIs of more than one technology company, with Sign-In With Google being the most widely used. When this option is clicked, prompts from the Google system say the website will get people’s name, email addresses, language preferences, and profile picture.
Google’s sign-in system also reveals some information about the developer accounts linked to a website. For example, four websites are linked to one Gmail account; another six websites are linked to another. “In order to use Sign in with Google, developers must agree to our Terms of Service, which prohibits the promotion of sexually explicit content as well as behavior or content that defames or harasses others,” says a Google spokesperson, adding that “appropriate action” will be taken if these terms are broken.
Other tech companies that had sign-in systems being used said they have banned accounts after being contacted by WIRED.
Hoffman from Discord says that as well as taking action on the websites flagged by WIRED, the company will “continue to address other websites we become aware of that violate our policies.” Apple spokesperson Shane Bauer says it has terminated multiple developer’s licenses with Apple, and that Sign In With Apple will no longer work on their websites. Adiya Taylor, corporate communications lead at Patreon, says it prohibits accounts that allow or fund access to external tools that can produce adult materials or explicit imagery. “We will take action on any works or accounts on Patreon that are found to be in violation of our Community Guidelines.”
As well as the login systems, several of the websites displayed the logos of Mastercard or Visa, implying they can possibly be used to pay for their services. Visa did not respond to WIRED’s request for comment, while a Mastercard spokesperson says “purchases of nonconsensual deepfake content are not allowed on our network,” and that it takes action when it detects or is made aware of any instances.
On multiple occasions, tech companies and payment providers have taken action against AI services allowing people to generate nonconsensual images or video after media reports about their activities. Clare McGlynn, a professor of law at Durham University who has expertise in the legal regulation of pornography and sexual violence and abuse online, says Big Tech platforms are enabling the growth of undress websites and similar websites by not proactively taking action against them.
“What is concerning is that these are the most basic of security steps and moderation that are missing or not being enforced,” McGlynn says of the sign-in systems being used, adding that it is “wholly inadequate” for companies to react when journalists or campaigners highlight how their rules are being easily dodged. “It is evident that they simply do not care, despite their rhetoric,” McGlynn says. “Otherwise they would have taken these most simple steps to reduce access.”
23 notes
·
View notes
Text
I'm going back to the idea of using Pyodide for P2P encryption but with a shift in approach, I'm going to create a variant on the supercomputer software that's scaled down for a kind of mini os/process engine. Doing this will simplify using Pyodide and provide an api for running Python applications (and potentially other languages via no dependency runtimes like DukPy) in browser. This will be my focus for the next week or so. Feel free to ask questions.
12 notes
·
View notes
Text
Web Data Scraping Services - Web Scraping Service Provider
3i Data is a Web Scraping Service Provider in the USA, India, UK, Canada, Germany, France, Israel, Australia, Spain, Singapore, and UAE. We offer web data scraping services for any website at competitive prices.

#web scraping services#Enterprise scale scraping#data mining services#web scraping api#Extract website data#Data extraction#Data mining
0 notes